Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 jonii25586yWTF Microsoft! Why not tell the user to use their username as password, because it's easier to remember.
jonii25586yWTF Microsoft! Why not tell the user to use their username as password, because it's easier to remember.
P.S.: Why does nobody know how to take a screenshot lately?! -
Sometimes I am really shocked how much Microsoft tries everything to prevent exploit attacks. ASLR as a great example.
But then again they somehow manage to disappoint me with this type of insane bullshit.
What the fricking hell is going on in the Microsoft company?
Do they all smoke weed before starting their work? Lol -
 620hun84036y@h4xx3r @24th-Dragon generate a hash before encryption every time a password is created, store it in an unrelated table. Then you can count the frequency of a given hash. It’s really not rocket science.
620hun84036y@h4xx3r @24th-Dragon generate a hash before encryption every time a password is created, store it in an unrelated table. Then you can count the frequency of a given hash. It’s really not rocket science. -
@620hun no, I'm dead serious. "generate a hash before encryption" implies that you think that MS stores encrypted pws (which i don't think they do)
Don't ever store passwords, not even encrypted ones https://youtu.be/8ZtInClXe1Q -
@620hun then you should really work on your wording skills
Still, even with hashes they shouldn't be able to count the occurrences of a particular password ^^ -
 620hun84035y@Krokoklemme
620hun84035y@Krokoklemme
You input a password, let's say it's 1234. Microsoft generates a hash, let's say an MD5, 81dc9bdb52d04dc20036dbd8313ed055. It then increases the count for that specific hash in a table. That's how they know frequencies. For authentication they only store a secure hash (bcrypt or whatever). They very obviously don't store passwords in any shape or form.
I hope that satisfies your wording requirements. You got me, I said encryption instead of hashing. I'm not a fucking security expert, just a dude with a minimal common sense. -
 620hun84035y@Krokoklemme (The whole part about encryption/hashing wasn't even relevant to my point, which was regarding password frequency count.)
620hun84035y@Krokoklemme (The whole part about encryption/hashing wasn't even relevant to my point, which was regarding password frequency count.)
Related Rants

 Did you say security?
Did you say security?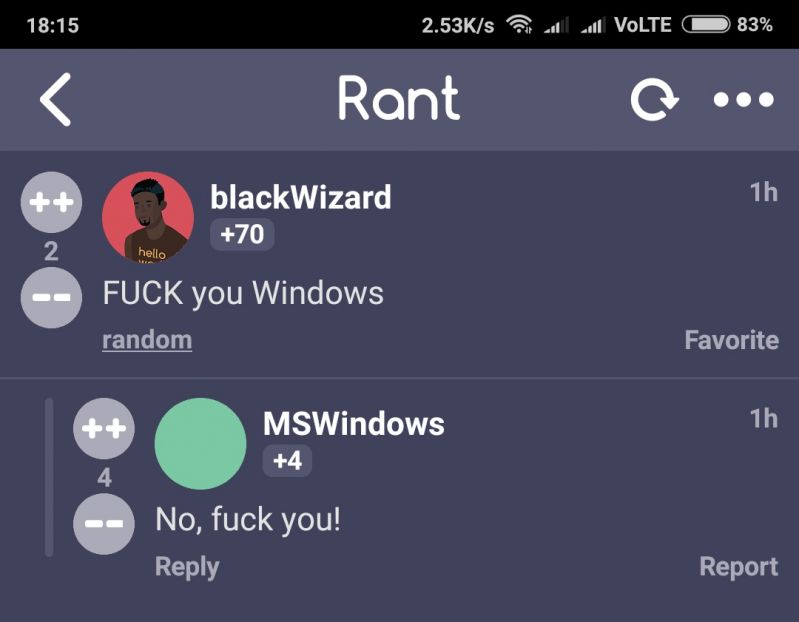 Made my day 😂😂
Made my day 😂😂
Microsoft seriously hates security, first they do enforce an numer, upper and lowercase combined with a special character.
But then they allow no passwords longer than 16 characters....
After that they complain that "FuckMicrosoft!1" is a password they've seen to often, gee thanks for the brute force tips.
To add insult to injury the first displayed "tip" take a look at the attached image.
rant
password
security
security 101
security fail
annoyance
passwords
passwords stupid practices
microsoft