Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "256"
-
The highest data transfer rate today - 256 gigabytes per second - was achieved when the cleaner's vacuum cleaner accidentally sucked the flash drive in from the floor.9
-
Am I the only one who hesitates to ++ a rant with 32, 64, 128, 256, etc ++'s?
I mean there's something satisfying about seeing 2^n numbers as an all-around computer nerd...13 -
Working with a radio chip we selected because it had built-in encryption. Cannot make the encryption work, thus in contact with the manufacturer:
"- I cannot make the encryption work, it's like the chip doesn't want to take a key.
- which key do you use?
- does it matter?
- well yes, you can't just use any key!
- why not?
- you need to get an approved key from us.
- why is that?
- so that your competitors can't read your data!
- ...
- ...
- so the way to get working keys is to get them from you?
- of course!
- keys are 256 bits. Can we potentially use all of them?
- OF COURSE NOT!
- how many can we get from you?
- one! We reserve it from your company.
- are you telling me that all units within a company will need to have the exact same encryption key?
- yes!
- so anyone with our product could eavesdrop another same product?
- well yes, but it's all within your own products.
- ...
- ...
- that's not how encryption is supposed to work.
- but it's safe, your competitors cannot eavesdrop!
- I'm out of here."
(We finally found a satisfactory work-around, but i am still pissed at them)9 -
I don't get 50 shades of grey.
They should have called it: "256 shades of gray unless you're on 10bit HDR, then its 1024 shades of grey"
That would have made much more sense9 -
We've password protected a file and forgot the password we need it cracking asap.
Sorry we can't crack passwords on files.
If we don't get access to the file it'll cost the company up to 250k.
Well you should've thought about that before encrypting the fucking file with 256 bit encryption.8 -
@dfox @trogus How about ++ milestones?
F.e.:
404 ++'s: “Error 404“
255 ++'s: “256 Bytes“
69 ++'s: (Well you know...)
And so on... (be creative)20 -
Since everybody is posting a picture of their hardware and DE here's mine!
Xiaomi notebook air 13 with Elementary OS
i5-6200U @2.8 GHz
NVIDIA GeForce 940MX
8 GB DDR4 Ram
256 PCIe SSD
1.28kg 31
31 -
The 256th day of every year is celebrated as Programmers’ Day.
Interestingly, 256 is the highest power of two that is less than 365.
It falls on September 13 during common years and September 12 in leap years.
This day is an international professional day recognized in many companies and organizations.
It’s even officially recognized in Russia as the “Day of the Programmer.” 3
3 -
There is only one important rule to live by:
Never lend anyone your 256 GB USB-C/USB-B combo memory stick. There is a 100% scientifically-backed certainty that you will never, in your meager existence, see it again.11 -
My "new desktop PC".
6 core xeon CPU with hyperthreading x2 (24 virtual cores) over clocked to 3.9ghz
128gb ddr3 ecc ram
256gb SCSI hard drives in RAID 0
256 Samsung ssd
AMD r9 something something 8gb ddr5 vram gpu
Got it for £120 on eBay (except for the ssd and gpu). Still missing a sound card :(
I have no idea on what to use it yet except for development but I thought it'd be cool to build a pretty good "desktop pc" for around £350-£400. 14
14 -
The website for our biggest client went down and the server went haywire. Though for this client we don’t provide any infrastructure, so we called their it partner to start figuring this out.
They started blaming us, asking is if we had upgraded the website or changed any PHP settings, which all were a firm no from us. So they told us they had competent people working on the matter.
TL;DR their people isn’t competent and I ended up fixing the issue.
Hours go by, nothing happens, client calls us and we call the it partner, nothing, they don’t understand anything. Told us they can’t find any logs etc.
So we setup a conference call with our CXO, me, another dev and a few people from the it partner.
At this point I’m just asking them if they’ve looked at this and this, no good answer, I fetch a long ethernet cable from my desk, pull it to the CXO’s office and hook up my laptop to start looking into things myself.
IT partner still can’t find anything wrong. I tail the httpd error log and see thousands upon thousands of warning messages about mysql being loaded twice, but that’s not the issue here.
Check top and see there’s 257 instances of httpd, whereas 256 is spawned by httpd, mysql is using 600% cpu and whenever I try to connect to mysql through cli it throws me a too many connections error.
I heard the IT partner talking about a ddos attack, so I asked them to pull it off the public network and only give us access through our vpn. They do that, reboot server, same problems.
Finally we get the it partner to rollback the vm to earlier last night. Everything works great, 30 min later, it crashes again. At this point I’m getting tired and frustrated, this isn’t my job, I thought they had competent people working on this.
I noticed that the db had a few corrupted tables, and ask the it partner to get a dba to look at it. No prevail.
5’o’clock is here, we decide to give the vm rollback another try, but first we go home, get some dinner and resume at 6pm. I had told them I wanted to be in on this call, and said let me try this time.
They spend ages doing the rollback, and then for some reason they have to reconfigure the network and shit. Once it booted, I told their tech to stop mysqld and httpd immediately and prevent it from start at boot.
I can now look at the logs that is leading to this issue. I noticed our debug flag was on and had generated a 30gb log file. Tail it and see it’s what I’d expect, warmings and warnings, And all other logs for mysql and apache is huge, so the drive is full. Just gotta delete it.
I quietly start apache and mysql, see the website is working fine, shut it down and just take a copy of the var/lib/mysql directory and etc directory just go have backups.
Starting to connect a few dots, but I wasn’t exactly sure if it was right. Had the full drive caused mysql to corrupt itself? Only one way to find out. Start apache and mysql back up, and just wait and see. Meanwhile I fixed that mysql being loaded twice. Some genius had put load mysql.so at the top and bottom of php ini.
While waiting on the server to crash again, I’m talking to the it support guy, who told me they haven’t updated anything on the server except security patches now and then, and they didn’t have anyone familiar with this setup. No shit, it’s running php 5.3 -.-
Website up and running 1.5 later, mission accomplished.6 -
Day 256.
I've tried everything. Going on airplane mode, uninstalling everything but the essentials, blocking all other links on my internet except what I need. I got distracted by the undo feature from my IDE instead. FML. -
„I have secured our mongodb by setting the dbpath deeper than 20 folders by using more than 256 chars. To protect us from windows hacker boys.“
😂4 -
256 kbps internet from Iran Telecommiunication Center ISP
i download 50mb archive in 30 minutes
should i suicide ???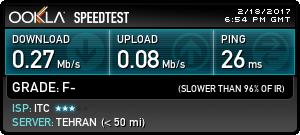 21
21 -
The newest IPhone (Which specwise is good) is more expensive than the newest graphics cards that are coming out... h.o.l.y. s.h.i.t
and you know what? THE BEST MODEL IS 400 BUCKS MORE EXPENSIVE THAN A FUCKING 2080TI!
And you know what?
WHATS UP WITH STORAGE!
you go from 64Gb to 256 and 512 GIGABYTES OF DATA!!
Its like, Midrange storage to a Ton of Storage to HOLY SHIT WHO NEEDS THIS MUCH?!
and you know WHY they are doing this?
Because most of the people will buy the 256 or 512 model GUARANTEED! People behave like this! you dont believe me?
What if you gave a Big Popcorn box for 15 Bucks and the smallest one for 5 bucks, which one would you buy? The smaller one. (Most of the time) and why? because you only have 2 choices! If I gave you 3 choices: 5 for small, 10 for medium and 15 for large?
You wont buy the smallest one, because it doesnt make sense! THATS WHY AND NOW FUCK OFF AND YOU TOO APPLE GO SUCK COCKS OF YOUR FUCKING FANBOYS WHICH WILL PAY MORE!4 -
while(apocalypses)
{
if(today.getDayOfYear == 256)
{
programmers.congratulate();
programmersDay.celebrate();
}
} 2
2 -
- popunder background bitcoin miners did become a thing
- keybase android beta uploaded your privatekey to google servers "accidentally"
- you can spoof email headers via encoded chars, because most apps literally just render them apparently
- imgur leaked 1.7 million user accounts, protected by sha-256 "The company made sure to note that the compromised account information included only email addresses and passwords" - yeah "only", ofcourse imgur, ofcourse.
I guess the rant I did on Krahk etc. just roughly a month ago, can always be topped by something else.
sources:
https://www.mailsploit.com/index
https://bleepingcomputer.com/news/...
https://blog.malwarebytes.com/cyber...
https://helpnetsecurity.com/2017/... undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6
undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6 -
I’m back for a fucking rant.
My previous post I was happy, I’ve had an interview today and I felt the interviewer acted with integrity and made the role seem worthwhile. Fuck it, here’s the link:
https://www.devrant.io/rants/889363
So, since then; the recruiter got in touch: “smashed it son, sending the tech demo your way, if you can get it done this evening that would be amazing”
Obviously I said based on the exact brief I think that’s possible, I’ll take a look and let them know if it isn’t.
Having done loads of these, I know I can usually knock them out and impress in an evening with no trouble.
Here’s where shit gets fucked up; i opened the brief.
I was met with a brief for an MVP using best practice patterns and flexing every muscle with the tech available...
Then I see the requirements, these fucking dicks are after 10 functional requirements averaging an hour a piece.
+TDD so * 1.25,
+DI and dependency inversion principle * 1.1
+CI setup (1h on this platform)
+One ill requirement to use a stored proc in SQL server to return a view (1h)
+UX/UI design consideration using an old tech (1-2h)
+unobtrusive jquery form post validation (2h)
+AES-256 encryption in the db... add 2h for proper testing.
These cunts want me to knock 15-20h of Work into their interview tech demo.
I’ve done a lot of these recently, all of them topped out at 3h max.
The job is middling: average package, old tech, not the most exciting or decent work.
The interviewer alluded to his lead being a bit of a dick; one of those “the code comes first” devs.
Here’s where shit gets realer:
They’ve included mock ups in the tech demo brief’s zip... I looked at them to confirm I wasn’t over estimating the job... I wasn’t.
Then I looked at the other files in the fucking zip.
I found 3 of the images they wanted to use were copyright withheld... there’s no way these guys have the right to distribute these.
Then I look in the font folder, it’s a single ttf, downloaded from fucking DA Font... it was published less than 2mo ago, the license file had been removed: free for Personal, anything else; contact me.
There’s no way these guys have any rights to this font, and I’ve never seen a font redistributed legally without it’s accompanying licence files.
This fucking company is constantly talking about its ethical behaviours.
Given that I know what I’m doing; I know it would have taken less time to find free-for-commercial images and use a google font... this sloppy bullshit is beyond me.
Anyway, I said I’d get back to the recruiter, he wasn’t to know and he’s a good guy. I let him know I’d complete the tech demo over the weekend, he’s looked after me and I don’t want him having trouble with his client...
I’ll substitute the copyright fuckery with images I have a license for because there’s no way I’m pushing copyright stolen material to a public github repo.
I’ll also be substituting the topic and leaving a few js bombs in there to ensure they don’t just steal my shit.
Here’s my hypotheses, anyone with any more would be greatly welcomed...
1: the lead dev is just a stuck up arsehole, with no real care for his work and a relaxed view on stealing other people’s.
2: they are looking for 15-20h free work on an MVP they can modify and take to market
3: they are looking for people to turn down this job so they can support someone’s fucking visa.
In any case, it’s a shit show and I’ll just be seeing this as box checking and interview practice...
Arguments for 1: the head told me about his lead’s problems within 20mn of the interview.
2: he said his biggest problem was getting products out quickly enough.
3: the recruiter told me they’d been “picky”, and they’re making themselves people who can’t be worked for.
I’m going to knock out the demo, keep it private and protect my work well. It’s going to smash their tits off because I’m a fucking great developer... I’ll make sure I get the offer to keep the recruiter looked after.
Then fuck those guys, I’m fucking livid.
After a wonderful interview experience and a nice introduction to the company I’ve been completely put off...
So here’s the update: if you’re interviewing for a shitty middle level dev position, amongst difficult people, on an out of date stack... you need people to want you, don’t fuck them off.
If they want my time to rush out MVPs, they can pay my day rate.
Fuuuuuuuuck... I typed this out whilst listening to the podcast, I’m glad I’m not the only one dealing with shit.
Oh also; I had a lovely discriminatory as fuck application, personality test and disability request email sent to me from a company that seems like it’s still in the 90s. Fuck those guys too, I reported them to the relevant authorities and hope they’re made to look at how morally reprehensible their recruitment process is. The law is you don’t ask if the job can be done by anyone.6 -
Small random update regarding my ISP and how they call your speed if you use all of your data.
I actually sent them a small complaint (more of a suggestion but) that 256 Kbps is just too slow even for a capped penalty speed and that at least 1 Mbps so that the internet is still usable but still slow... And mother fucker if that isn't exactly what they did!
It's nice being able to sync my code and have more than 1 device connected to the wifi at once... It's a strange feeling when a company actually listens to feedback and takes measures on them...5 -
Finally got ceph up and running, so far it does look really great!
At the moment we have 45 TB in the cluster, but we are able to expand it extremely easy.
Two servers with 256 GB RAM and 24 cores, three more with 32 GB and 12 cores.
Dedicated gigabit WAN connection.
The project is going forward strong, I'll let you know when it is time for beta testing.7 -
Cs101 - a 3 hour Friday morning lecture. 1st at uni doing computer science. Half asleep. I'm awoken by the professor
"You at the back - what's the answer!"
Alarmed but not too bothered I just say "I don't know"
He replies "yes you do! We just went over it"
I say I really don't know. Someone behind me says "64". So I say "64".
Professor sighs and says "no - 2 to the power 8 is 256!"
He never liked me after that.4 -
Just found this in our code:
UINT8 variableName = 500;
Any developer who is getting paid should know the largest value an unsigned 8 bit integer can hold12 -
You know what just gets to me about garbage-collected languages like c# and Java? Fucking dynamic memory allocation (seemingly) on the stack. Like it's so bizzare to me.
"Hey, c#, can I have an array of 256 integers during run-time?"
"Ya sure no prob"
"What happens when the array falls out of scope"
"I gotchu fam lol"8 -
When you've been coding for what seems like an hour and when you finally look up it's dark outside 😛

-
trying to do anything on the PS2 is almost fucking impossible
i imagine a board meeting where they were designing the hardware
"how can we make this insanely hard to use?"
"let's make decentralized partition definitions, allow fragmenting of entire partitions, and require all partitions to be rounded to 4MB. If you delete a partition, don't wipe the partition out, just rename it to "_empty" and the system will do it for you, except it actually won't because fuck you"
"let's require 1-bit serial registers to be used for memory card access and make sure you can't take more than 8 CPU cycles to push each bit or it'll trash the memory card"
"let's make the network module run on a 3-bit serial register and when initialized it halves the available memory but only after 8 seconds of activity"
"let's require the system to load feature modules called "IOPs" and require the software to declare which of the 256 possible slots it wants to use (max of 8 IOPs) then insert stubs into those. Any other IOP you call will hang the system and probably corrupt the HDD. You also have to overwrite the stubbed IOPs with your own but only if you can have the stubs chainload the other IOPs on top of themselves"
"let's require you to write to the controller registers to update them, but you have to write the other controller's last-polled state or the controller IOP will hang"
of course this couldn't make sense, it's
s s s s
o o o o
n n n n
y y y y 4
4 -
This is my first rant here, so I hope everyone has a good time reading it.
So, the company I am working for got me going on the task to do a rewrite of a firmware that was extended for about 20 years now. Which is fine, since all new machines will be on a new platform anyways. (The old firmware was written for an 8051 initially. That thing has 256 byte of ram. Just imagine the usage of unions and bitfields...)
So, me and a few colleagues go ahead and start from scratch.
In the meantime however, the client has hired one single lonely developer. Keep in mind that nobody there understands code!
And oh boy did he go nuts on the old code, only for having it used on the very last machine of the old platform, ever! Everything after that one will have our firmware!
There are other machines in that series, using the original extended firmware. Nothing is compatible, bootloaders do not match, memory layouts do not match, code is a horrible mess now, the client is writing the specification RIGHT NOW (mind, the machine is already sold to customers), there are no tests, and for the grand finale, the guy canceled his job and went to a different company. Did I mention the bugs it has and the features it lacks?
Guess who's got to maintain that single abomination of a firmware now?1 -
Installing my company's microsystems architecture to run locally is a pita because it is 60 GB of docker containers. With my 256 GB Macbook, that's a scaling problem for the years to come.6
-
What was your most ridiculous story related to IT?
Mine was when I was quite small (11yo) and wanted a graphics card (the epoch of ATI Radeon 9800), looked at the invoice to know what kind of ports I had in the pc (did not open it), then proceeded to brat to my dad to get me a new GPU
So we where in Paris, we went to a shop, vendor asked me "PCI or AGP?" and said AGP.
Paris > London > Isle of Skye roadtrip followed, then as my dad brought me back home in Switzerland, we opened my pc...
And we couldn't fit the GPU in the basic old PCI port. My Dad was pissed. He frustratedly tried fitting the GPU in the PCI slot, but nope. (He's a software engineer though)
At least the GPU had 256 mb of ram :D
Gave it to my brother 6 months later at family gathering
To this day, my Dad still thinks I cannot handle hardware, although I have successfully built 10+ pc, and still cringes with a laughing smile when I talk to him about it haha
Ah well.1 -
It's 1:00( 1 am) here now...I wanted to get some coding done since 20:00(8 pm for the weird people ;P)
Got distracted by Dev rant all the time -.- and didn't write a single line of code...fml5 -
OpenSSH 8.2 is out. This release removes support for the ssh-rsa key algorithm. The better alternatives include:
1. RSA SHA-2 signature algorithms rsa-sha2-256/512. These algorithms have the advantage of using the same key type as "ssh-rsa" but use the safe SHA-2 hash algorithms (now used by default if the client and server support them).
2. The ssh-ed25519 signature algorithm.
3. ECDSA algorithms: ecdsa-sha2-nistp256/384/521.
In this release, support for FIDO/U2F hardware tokens. Also noteworthy, a future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms.19 -
Idea: Hiding a 3D object in an image by making a list how often every color appears and then displaying that as density information in a 256³ cube (aka using a 3D histogram to encode a 3D object)15
-
My girl friend was complaining that I care more about programming than her.
I told her,
"Trust me baby, in the array of my interests you are [1]."
She was satisfied.3 -
Called to maintain a WordPress site. Site has 100 plugins, two to disable right click. Somebody kill me already 😂😂😂1
-
Anyone want a free Python, PHP, or Assembly book?
Well how about all 3???
https://fanatical.com/en/bundle/... 7
7 -
Not sure how to handle this one. My new company gave me a surface laptop to do dev ops work.
16 gigs of Ram but only a 256 SSD?
Nothing is installed so far except for MS office and acrobat and I am already running into memory issues.
My last work machine had 1TB HDD and 128 gigs of RAM (i know overkill but I could have several VM’s up and running at once).
What the fuck? Apparently the CTO ordered this piece of shit.
Also no mirco SD card like other models so I have no idea how this is going to fucking work.15 -
Is it just me or does it also bother anyone else when manufacturers pull shit like this (using Apple as example but I've also seen it from Google/Samsung).
 9
9 -
What's wrong with the idea of having a huge computational network like in Watch Dogs to bruteforce encryption ?
I mean suppose having 500 or more million cores , how long does it actually take to bruteforce a 256 bit key ?11 -
If anyone has used the super Mario 64 online mod, it's extremely easy to crash all clients connected to any server. You have to send a chat message payload with a length greater than 256 characters. The clients do not do any bound checking and write the payload directly to super Mario 64 memory. This causes all clients connected to the game to crash. I will leave how to send a chat payload > 256 characters up to you. I've confirmed my method works!2
-
A Rant that took my attention on MacRhumors forum.
.
I pre-calculated projected actual overall cost of owning my i5/5/256 Haswell Air, which I got for $1500.
After calculations, this machine would cost me about $3000 for 3 years of use.
(Apple Care, MS Office Business, Parallels, Thunderbolt adapter to HDMI, Case... and so on).
Yea... A lot of people think it's all about the laptop with Apple. nah... not at all. There's a reason Apple is gradually dropping the price of their laptops.
They are slowly moving to a razor and blade business model... which basically is exactly what it sounds like - you buy the razor which isn't too expensive, but you've got no choice but to buy expensive additional blades.
I doubt Apple is making much money from laptop sales alone... well definitely not as much as they were making 5 years or so ago (remember the original air was about $1800 for base model, and if i remember correctly - $1000 additional dollars to upgrade to 64GB SSD from the base HDD.
Yes, ONE THOUSAND DOLLARS FOR 64GB SSD!
Well, anyways, the point is that Apple no longer makes them BIG bucks from the laptop alone, but they still make good profits from upgrades. $300 to go to 512GB SSD from 256, $100 for 4GB extra ram, and $150 for a small bump in processor. They make good profits from these as well.
But that's not where they make mo money. It's once you buy the Macbook, they've got you trapped in their walled garden for life. Every single apple accessory is ridiculously overpriced (compared to market standards of similar-same products).
And Apple makes their own cables and ports. So you have to buy exclusively for Apple products. Every now and then they will change even their own ports and cables, so you have to buy more.
Software is exclusive. You have no choice but to buy what apple offers... or run windows/linux on your Mac.
This is a douche level move comparable to say Mircrosoft kept changing the usb port every 2-3 years, and have exclusive rights to sell the devices that plug in.
No, instead, Intel-Microsoft and them guys make ports and cables as universal as possible.
Can you imagine if USB3.0 was thinner and not backwards compatible with usb2.0 devices?
Well, if it belonged to Apple that's how it would be.
This is why I held out so long before buying an apple laptop. Sure, I had the ipod classic, ipod touch, and more recently iPad Retina... but never a laptop.
I was always against apple.
But I factored in the pros and cons, and I realized I needed to go OS X. I've been fudged by one virus or another during my years of Windows usage. Trojans, spywares. meh.
I needed a top-notch device that I can carry with me around the world and use for any task which is work related. I figured $3000 was a fair price to pay for it.
No, not $1500... but $3000. Also I 'm dead happy I don't have to worry about heat issues anymore. This is a masterpiece. $3000 for 3 years equals $1000 a year, fair price to pay for security, comfort, and most importantly - reliability. (of course awesome battery is superawesome).
Okay I'm going to stop ranting. I just wish people factored in additional costs from owning an a mac. Expenses don't end when you bring the machine home.
I'm not even going to mention how they utilize technology-push to get you to buy a Thunderbolt display, or now with the new Air - to get a time capsule (AC compatible).
It's all about the blades, with Apple. And once you go Mac, you likely won't go back... hence all the student discounts and benefits. They're baiting you to be a Mac user for life!
Apple Marketing is the ultimate.
source: https://forums.macrumors.com/thread...3 -
Okey, so the recruiters are getting smarter, I just clicked how well do you know WordPress quiz (I know it's from a recruiter, already entered a php quiz An might win a drone)
So the question is how to solve this issue:
Fatal error: Allowed memory size of 33554432 bytes exhausted (tried to allocate 2348617 bytes) in /home4/xxx/public_html/wp-includes/plugin.php on line xxx
A set memory limit to 256
B set memory limit to Max
C set memory limit to 256 in htaccess
D restart server
These all seem like bad answers to me.
I vote E don't use the plug-in, or the answer that trumps the rest, F don't use WordPress 4
4 -
When your teacher tells you to run a model that uses a 1gb dataset on a computer that has 256 mb ram.
Ah, what sin have I done, my lord? :/ -
First World problems. Do I upgrade my 120gb (with 40gb free) to a 256 or replace my 1tb platter (700gv free) with a 500gb SSD.6
-
Well... I recorded my boss's talk at a small tech conference. Everything went just fine until I tried downloading the video from my camera.
It turns out under-priced 32 GB SD cards from eBay may actually only contain 256 MB worth of memory, while quite happily accepting recordings that are far larger than that.4 -
Joined small scale-up months ago. I literally want to punch one of my coworker. Constant mental harassement, self-declared lead, rude and impolite. That coworker is socially awkward in the baddest and meanest way.
Oh boi.
Founders seems to not give a crap even if they told me they want a flat hierarchy. They let that coworker off the hook.
Not even mentioning that culture of oppression and repression.
If you're late you must bring chocolate and they'll remind you 256 times a day. Oh boy, I'm not late... I just don't want to come in the office.
Also, the code is atrocious.
What seemed like a dream job at first turned out to be a nightmare. Never been bullied since I started working. Now, I have a bully and a nemesis.
Ooooh boy.8 -
I will soon move to Belgium for a few months due to my wife's job and I will go back to Germany once in a while for a few weeks. Of course I'll need a computer and I can't take my tower back and forth all the time, thus I'll need something more mobile. Since most notebooks <1000€ are shit and I'll also need at least two external monitors, I went for a small (USFF) PC instead; for about 350€ I got a HP ProDesk 400 G5 with a i5-9500T, 8 GB RAM (to be upgraded), 256 GB NVME (also to be upgraded), B360 chipset. I would have liked a Ryzen, but then I could only get the predecessor with a 2400GE...
Hopefully Linux (Qubes OS in particular) will work fine.20 -
I found a vulnerability in an online compiler.
So, I heard that people have been exploiting online compilers, and decided to try and do it (but for white-hat reasons) so I used the system() function, which made it a lot harder so i decided to execute bash with execl(). I tried doing that but I kept getting denied. That is until I realized that I could try using malloc(256) and fork() in an infinite loop while running multiple tabs of it. It worked. The compiler kept on crashing. After a while I decided that I should probably report the vulnerabilites.
There was no one to report them to. I looked through the whole website but couldn't find any info about the people who made it. I searched on github. No results. Well fuck.7 -
spend better part of my day processing about 400M rows of data with MySql, woo ain't no single line of code that can do that in 12hrs 😊
-
Why do SAMBA network drives have to suck this much? Yeah I understand that compiling to a network drive is probably a bad idea just for performance reasons alone but can't you at least not fuck with my git repo?
$ git gc
Enumerating objects: 330, done.
Counting objects: 100% (330/330), done.
Delta compression using up to 24 threads
Compressing objects: 100% (165/165), done.
Writing objects: 100% (330/330), done.
Total 330 (delta 177), reused 281 (delta 151), pack-reused 0
error: unable to open .git/objects/7e: Not a directory
error: unable to open .git/objects/7e: Not a directory
fatal: unable to mark recent objects
fatal: failed to run prune
$ git gc
error: unable to open .git/objects/00: Not a directory
fatal: unable to add recent objects
fatal: failed to run repack
$ git gc
Enumerating objects: 330, done.
Counting objects: 100% (330/330), done.
Delta compression using up to 24 threads
Compressing objects: 100% (139/139), done.
Writing objects: 100% (330/330), done.
Total 330 (delta 177), reused 330 (delta 177), pack-reused 0
Removing duplicate objects: 100% (256/256), done.
error: unable to open .git/objects/05: Not a directory
error: unable to open .git/objects/05: Not a directory7 -
Had a buy a salesperson a desktop to replace the one he has that has a bad HDD. I discovered he uses no storage on the thing and that buying a computer with 12 GB RAM and 256 GB SSD, was cheaper than 8 GB with any size HDD I could find at the store so we got that.
Now I'm jealous of his 10 seconds or less boot time while I have to struggle every morning waiting at least a full minute for my computer to get to login, and another one once I put in my password.6 -
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
Going to design a contract for my services it's going to include additional costs for additional changes because with clients the job is never done 😉😉3
-
This morning I was exploring dedekind numbers and decided to take it a little further.
Wrote a bunch of code and came up with an upperbound estimator for the dedekinds.
It's in python, so forgive me for that.
The bound starts low (x1.95) for D(4) and grows steadily from there, but from what I see it remains an upperbound throughout.
Leading me to an upperbound on D(10) of:
106703049056023475437882601027988757820103040109525947138938025501994616738352763576.33010981
Basics of the code are in the pastebin link below. I also imported the decimal module and set 'd = Decimal', and then did 'getcontext().prec=256' so python wouldn't covert any variable values into exponents due to overflow.
https://pastebin.com/2gjeebRu
The upperbound on D(9) is just a little shy of D(9)*10,000
which isn't bad all things considered.4 -
Should i get a macbook pro no touchbar 2017 with 512 GB SSD or is 256 GB fine enough? Only for coding primarily focused on mobile development16
-
I finally attempted php, I wrote a bunch of scripts to fetch data... I feel like I have betrayed myself 😞😞😞
I should have just absorbed the cost of azure 😭😭😭 now am a php dev.... The things I'm about to do, the horrors I'm about to put out into the world.... Pulling your hair out will be the least of your worries, dear maintainer forgive us all, always and forever. 😳1 -
A toast to the perks of backend, to never being bothered again with every single ui change.... Just you and your code 😏😀2
-
For starters - I like Windows 10. I seldom have any problems with it. But...
For fucking fuck sake how did this fucking happen. I tried to make a carbon copy of my small 128 SSD with Windows and Linux on it onto a bigger, 256 GB one using Partition Wizard. Something went so fucking wrong that Windows started showing me, for the first time in a looooooong time, BSODs. It wouldn't be so bad if after restoring Windows grub stopped functioning and now I can't access any OS on this drive. And all I wanted was to migrate to bigger disk...2 -
3ds Max Python API Documentation.
No function has a single word explaining what it does.
The Documentation seems like it is completely auto generated and while writing the API they forgot to add Docstrings....2 -
Something that irks me is the misinformation that the DOGE proof of work is less complex and more energy saving than the BTC proof of work.
BTC: SHA-256
DOGE: SCRYPT (SHA-256 + Some additional steps and higher memory consumption)11 -
cbc vs gcm vs ... for my app?
currently ive get ecb 256 bit already implemented and working well, but i want an extra layer of privacy. if you had to send your ssn or credit card number over a vulnerable network, would you be more comfortable encrypting it with cbc or gcm?9 -
Ok so i just bought a 256 GB SSD macbook pro and long story short i actually have 200 GB of free space when you take everything that takes up the space.
The fucking Catalina OS upgrade takes 8 GB.
Is this enough memory for programming/work related stuff???23 -
https://frankforce.com/city-in-a-bo...
I couldn't even come up with this without the size limitation1 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
!rant/story:
Aaayoo issya boi the OG rapper straight outta Compton, wassup?!
Nah, for real, though.: How are y'all doing? It has been a long time. I hope y'all are having a great time (can sense some peoples' incoming negative comments due to corona).
I built my completely new first gaming rig like a few weeks ago after my school laptop stopped showing any signals.
The specifications are the following.:
- Mobo: MSI B450 TOMAHAWK MAX
- CPU: AMD Ryzen 5 3600 (no iGPU)
- dGPU: KFA2 RTX 2070 SUPER OC
- 2nd dGPU: GTX 550 TI (this one gets a new rant/post)
- RAM: 2x G.SKILL Ripjaws V 8 GB 3600 MHz
- PSU: Be quiet 650 W (It was the platinum edition afaik. I originally bought the 600 Watt Gold edition, but somehow they sent me the 650 Watt for no additional charge... which is great for me haha)
- HDD: 2x 4TB NAS HDD in RAID1 configuration (to load all of my games around 2 TB right now. Got the two HDDs for 110 Euro including the SATA Data cables)
- SSD: One Intenso 240 GB SSD and a reused Samsung 256 GB SSD from my old broken Lenovo laptop
- Case: Be quiet Pure Base 500 black with a glass panel on the side
While building my first PC, it was one hell of a challenge. I knew how it all was working in theory, but to put it all together, practically, was a bit of a challenge, but it was a nice challenge. I learned a lot and have a performance gain I could only ever dream of.
I used to play my games first on a Toshiba satellite l750d laptop (around 40 fps in cs:go with the lowest gfx settings) and then on a Lenovo e51-80 laptop (around 30 fps max minecraft with no shaders and texture packs).
Now I play cs:go on Kubuntu with 400 fps at peak with ultra high graphics. It is unbelievable.
I couldn't trust the system when I turned on the fps display the first time I saw it. 6
6 -
instagrams "based on likes" is total bullshit, I don't like shit those suggestions like but if you scroll through your contacts you'll find those suggestions. Why not just say it like it is: "from your contacts or from your friends contacts"
 3
3 -
Current dream PC:
Dual EPYC at 128 core/256 thread or higher
1TB of RAM or more
Dual AMD GPUs
Massive RAID 10 array of 7200RPM HDDs, something like 24TB or better
A few standalone SSDs, to taste (at least one of a sizeable capacity, like 1TB?)
Total cost, like $30k or so?51 -
hi everyone just want your input planing to get a cheap laptop for development
Usage:
PHP
Nodejs
Yarn
Photoshop
Option1: Lenovo IdeaPad 330
Specs: Intel Core i3-7020U / 4GB DDR4 / 1TB HDD
Option2: Lenovo IdeaPad 330
Specs: AMD Ryzen 3 2200U / 4GB DDR4 / 256 SSD
Option3: ASUS X407UA
Specs: Intel Core i3-7020U / 4GB DDR4 / 1TB
im going cheapest as possible but it you guys think going to i5 would benefit more let me know18 -
Windows machine i5 7th gen with 12Gigs Ram and 4Gigs graphics (2 dedicated + 2 shared) and 1TB HDD+ 256 Gb SSD vs low budget MacMiNi for heavy dev? usage- JDK, Android SDK, node, containers etc.9
-
More linux driver woes:
Driver is passed a file position and byte count when asked to read from a device. Sounds easy, right? FUCK no.
For reads, driver is passed struct `filp` with field `f_pos`, a direct pointer to the same struct field, int `count` as a number of bytes to read, and `buf` to return those bytes with. Problem is, requesting, say, 256 bytes from location 10000000h will give the driver `filp->f_pos = 0`, `f_pos = 256`, and `count = 0`. I don't know how to fix this and there's NO help for this shit. None whatsoever.
This shit, right here, is why Linux drivers suck ass.4 -
Day of the programmer should be tomorrow, because it should be a zero-based index to the day on position 256
-
!rant
I'm in the lookout for a new laptop for my dev work and occasional gaming (Dota 2 only), needs to have at least 16GB, 256 SSD, decent battery life and portable.
Which laptop do own?
Which do you recommend?8 -
I'm creating a bitmap font right now and wanted to automatically generate a image with some text so I can track my progress how it looks. gnome-font-viewer displays it fine, but it'd nothing compared to some real text. Well, how hard can it be?
First attempt: Use ImageMagick to create an image and draw some text. I found a forum post in the ImageMagick forums from 2017 claiming incorrect rendering of BDF fonts, which was promised to be fixed. Yet convert does exactly nothing besides saying “couldn't read font”.
Looking around, there is exactly one tool for the job I'm looking to get done: pbmtext. It works, but doesn't support Unicode. Egh.
Maybe I could write a short script to do it, then? Python's Pillow can import Bitmap fonts (cairo can't). Halfway done I notice it can't deal with anything outside of the character range 0..256.
Using FreeFont directly is out of the question as that seems to be equally much work as creating the font in the first place. I briefly tried SDL, but the font formats it understands are limited.
So how about converting the font then, you ask? Everyone seems to be only concerned about the other way (like OTF to BDF). I tried loading the font into FontForge and exporting an OTF or TTF but couldn't get anything out of it that ImageMagick recognizes as a font.
It seems fucking impossible to render text to an image with an Unicode BDF font in some automated way.
To add insult to injury, my searches containing “bdf” are always interpreted as with “pdf”. I'm not even a Franconian, I can distinguish B and P!4 -
https://accessurl.com
[...] All session data is encrypted using (salted) AES-256, the same encryption algorithm used by the U.S. Government to protect TOP SECRET data. [...]
FUCK!! But perfect for Netflix!! ;)4 -
Lots of thumb drives. My laptop used to not have much storage and most of my files would be on those thumb drives.
My first one was 8GB, then 16, then 32, 64, 128, now 256.
Each time I got a new one I would copy the old files to it, kinda like these crabs https://youtube.com/watch/...
All of them are in a little box on my desk right now, I use the old ones for backups. I replaced the laptop's hard drive a few months ago so now I'm less dependent on thumb drives :)2 -
By starting the company I think I just dissolved, perfect opportunity to start a new one... Software company name suggestions anyone3
-
and so today almost an hour ago I became the left one... I guess she went with the right one 😂😂😂... How many days have passed between my previous "relationship" post and this one ending... but in truth I was in the "babe" zone 😂😂😂
On to the next one, with the lessons from mistakes of the previous, hopefully she will last longer 🙏1 -
when you are using javascript frameworks and plugins in mvc and you have ReSharper, for your own safety and sanity exclude *.js
-
using System;
using System.Text;
using System.Text.Encodings;
//Bitwise XOR operator is represented by ^. It performs bitwise XOR operation on the corresponding bits of two operands. If the corresponding bits are same, the result is 0. If the corresponding bits are different, the result is 1.
//If the operands are of type bool, the bitwise XOR operation is equivalent to logical XOR operation between them.
using System.Text.Unicode;
using System.Windows;
using System.IO;
namespace Encryption2plzWOrk
{
class Program
{
static void Main(string[] args)
{
//random is basically a second sepret key for RSA exhanges I know there probaley is a better way to do this please tell me in github comments.//
Random r = new Random();
int random = r.Next(2000000,500000000);
int privatekey = 0;
int publickey = 0;
string privateKeyString = Console.ReadLine();
byte[] bytes3 = Encoding.ASCII.GetBytes(privateKeyString);
foreach(byte b in bytes3)
{
privatekey = b + privatekey;
}
int permutations = random/ 10000;
if(privatekey < 256)
{
while(permutations > 0)
{
foreach (byte b in bytes3)
{
privatekey = privatekey + (privatekey ^ permutations)*20;
}
}
}
publickey = privatekey*random;
Console.WriteLine("your public key is {0}",publickey);
}
}
}
would this be considerd ok HOBBYIST encryption and if not how would I do a slow improvment I used bitwise to edit bits so thats a check :D12 -
I once wrote a whole lot of classes with lots of functions and pushed them to the live server without testing... There were no errors 😎1
-
Project manager, knows nothing/little about the project... Always sends new features to be added only to be removed 1hr later 😣😣, you have experienced nothing until you work under 1
-
Would you get a new laptop with Intel Celeron N3450, or slightly older with Intel Core i5 4310U? I'm talking both having 256 GB SSD, 8GB RAM and only iGPU? Both for pretty much same price.9
-
Should i turn back my new macbook pro i7 15" 2019 256 gb and buy i9 15" 2019 512 gb ?? ????
Pls say very urgent
What i want to do:
Only use the laptop for work and progreamming. Unity node spring angular xcode android studio for now mainly.
Is my 256 gb enough to handle all of that or have i fucked up and should have taken 512?12 -
Hello Devs, Please Suggest Me A Good Laptop.
Specs I Probably Need:
256 or 512 SSD
i7 6th gen
8 or 16 GB DDR4 RAM
Dedicated Graphics or Touch Screen(Ultrabook or something)
Really Confused between Yoga 910 and Lenovo Y700. Or what will be the best device(Portable and Powerful) for us?6 -
Hello Everyone,
I am trying to learn to create apps with Android Studio and Swift5. However, my current laptop is not okay to work with its 4 GB RAM.
My question is, i am planning to buy a MacBook Air I5 8GB RAM 256 GB SSD. Do you think it is enough for me to learn coding in the first place and create apps?
Let me also state the fact that additional RAMs like 16 GB and bigger SSD size are really expensive in my country. So i’m looking for something that can work Swift and Android Studio (with Emulator) with no problem.
It would be great to hear from you about your experiences and advices.
Cheers!13 -
Currently on the market for a new laptop for work.
I'm thinking of Asus Vivobook 15 with 12GB ram and 256 GB SSD config. I don't trust Windows and it's performance on HDD. Since I'm coming from Macbook, I would really hate having to wait about 5 mins for system to be usable after boot up.
Slightly tempted to spend more money and go for a gaming laptop for that I can play Spintires sometimes. But not sure if it's a good idea to have a gaming config laptop for work.
It fucking sucks that there is not much selection of laptops or even let you try demo of laptops that are put for display in the shops here.2 -
I got a new babe today, Lenovo Yoga 550, i7, 256 SSD...hw do u advice I utilize.. should i partition and have windows OS and my sweet Ubuntu & Arch linux(s) on d base or just vm them on windows..cuz honestly if not for few wares, i hv no business with windows..pls advice.3
-
[FE] Does anyone have any experience with web development on a 256/8 m1 macbook air?
Also, what's with the conflicting opinions about 8 or 16 gigs of ram?
Need to buy a new laptop and honestly I have no idea which one I should choose.28 -
Any recommendations for decent 13 inch laptop under 1400$ USD
- Atleast 8 gigs of RAM and option to upgrade
- resolution >= full HD
- storage >= 256 GB SSD
- battery >= 6 hrs heavy chrome usage
- Linux compatibility
- Cpu- nothing heavy - browser and docker containers, no building or compiling15











