Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "data security"
-
buzzword translations:
"cloud" -> someones computer
"big data" -> lots of somewhat irrelevant data
"ai" -> if if if if if if if if if if if if if else
"algorithm" -> something that works but you don't know why
"secure" -> https://
"cyber security" -> kali linux + black hoodie
"innovation" -> adding something completely irrelevant such as making a poop emoji talk
"blockchain" -> we make lots of backups
"privacy" -> we store your data, we just don't tell you about it40 -
My mentor/guider at my last internship.
He was great at guiding, only 1-2 years older than me, brought criticism in a constructive way (only had a very tiny thing once in half a year though) and although they were forced to use windows in a few production environments, when it came to handling very sensitive data and they asked me for an opinion before him and I answered that closed source software wasn't a good idea and they'd all go against me, this guy quit his nice-guy mode and went straight to dead-serious backing me up.
I remember a specific occurrence:
Programmers in room (under him technically): so linuxxx, why not just use windows servers for this data storage?
Me: because it's closed source, you know why I'd say that that's bad for handling sensitive data
Programmers: oh come on not that again...
Me: no but really look at it from my si.....
Programmers: no stop it. You're only an intern, don't act like you know a lot about thi....
Mentor: no you shut the fuck up. We. Are. Not. Using. Proprietary. Bullshit. For. Storing. Sensitive. Data.
Linuxxx seems to know a lot more about security and privacy than you guys so you fucking listen to what he has to say.
Windows is out of the fucking question here, am I clear?
Yeah that felt awesome.
Also that time when a mysql db in prod went bad and they didn't really know what to do. Didn't have much experience but knew how to run a repair.
He called me in and asked me to have a look.
Me: *fixed it in a few minutes* so how many visitors does this thing get, few hundred a day?
Him: few million.
Me: 😵 I'm only an intern! Why did you let me access this?!
Him: because you're the one with the most Linux knowledge here and I trust you to fix it or give a shout when you simply can't.
Lastly he asked me to help out with iptables rules. I wasn't of much help but it was fun to sit there debugging iptables shit with two seniors 😊
He always gave good feedback, knew my qualities and put them to good use and kept my motivation high.
Awesome guy!4 -
The new Dutch mass surveillance law goes into action on the first of May. I'll of course have a good security setup ready but that does not stop the bulk data collection.
I just setup a website which (still in English at the moment) requests a random search result from bing, google or DuckDuckGo every 3 seconds.
Will work on making it more 'real' :)
If stopping the surveillance isn't an option, let's add more data to filter out for them!38 -
1. Humans perform best if they have ownership over a slice of responsibility. Find roles and positions within the company which give you energy. Being "just another intern/junior" is unacceptable, you must strive to be head of photography, chief of data security, master of updating packages, whatever makes you want to jump out of bed in the morning. Management has only one metric to perform on, only one right to exist: Coaching people to find their optimal role. Productivity and growth will inevitably emerge if you do what you love. — Boss at current company
2. Don't jump to the newest technology just because it's popular or shiny. Don't cling to old technology just because it's proven. — Team lead at the Arianespace contractor I worked for.
4. "Developing a product you wouldn't like to use as an end user, is unsustainable. You can try to convince yourself and others that cancer is great for weight loss, but you're still gonna die if you don't try to cure it. You can keep ignoring the disease here to fill your wallet for a while, but it's worse for your health than smoking a pack of cigs a day." — my team supervisor, heavy smoker, and possibly the only sane person at Microsoft.
5. Never trust documentation, never trust comments, never trust untested code, never trust tests, never trust commit messages, never trust bug reports, never trust numbered lists or graphs without clearly labeled axes. You never know what is missing from them, what was redacted away. — Coworker at current company.9 -
I guess that is what you get for bringing up security issues on someones website.
Not like I could read, edit or delete customer or company data...
I mean what the shit... all I did was try to help and gives me THIS? I even offered to help... maybe he got angry cause I kind of threw it in his face that the whole fucking system is shit and that you can create admin accounts with ease. No it's not a framework or anything, just one big php file with GET parameters as distinction which function he should use. One fucking file where everything goes into. 21
21 -
Newspaper: This CEO is one of the top entrepreneurs in the country, a true tech visionary shaping the future.
--- 3 months previous ---
Lead dev: O2 have said they are will pre-install the app on all their Androids but they need documentation from us.
CEO: documentation? on what?
Lead dev: Our unit test coverage, bugs found / fixed, security scan results, performance assessment, if and where its storing any data etc.
CEO: Ah were not doing any of that crap, bloody unit tests, its not necessary, tell them no.
lead dev: ..... eh ok
O2: *approved*
... true visionary, well done to everyone involved.3 -
Another incident which made a Security Researcher cry 😭😭😭
[ NOTE : Check my profile for older incident ]
-----------------------------------------------------------
I was invited by a fellow friend to a newly built Cyber Security firm , I didn't asked for any work issues as it was my friend who asked me to go there . Let's call it X for now . It was a good day , overcast weather , cloudy sky , everything was nice before I entered the company . And the conversation is as follows :
Fella - Hey! Nice to see you with us .
Me - Thanks! Where to? *Asking for my work area*
Fella - Right behind me .
Me - Good thing :)
Fella - So , the set-up is good to go I suppose .
Me - Yeah :)
*I'm in my cabin and what I can see is a Windows VM inside Ubuntu 12.4*
*Fast forward to 1 hour and now I'm at the cafeteria with the Fella*
Fella - Hey! Sup? How was the day?
Me - Fine *in a bit confused voice*
Fella - What happened mate , you good with the work?
Me - Yeah but why you've got Windows inside Ubuntu , I mean what's the use of Ubuntu when I have to work on Windows?
Fella - Do you know Linux is safe from Malwares?
Me - Yeah
Fella - That's why we are using Windows on VM inside Linux .
Me - For what?
Fella - To keep Windows safe from Malwares as in our company , we can't afford any data loss!
Me - 😵 *A big face palm which went through my head and hit another guy , made me a bit unconscious*
I ran for my life as soon as possible , in future I'm never gonna work for anyone before asking their preferences .7 -
Hello!
I'm a member of an international hacker group.
As you could probably have guessed, your account [cozyplanes@tuta.io] was hacked, because I sent message you from it.
Now I have access to you accounts!
For example, your password for [cozyplanes@tuta.io] is [RANDOM_ALPHABET_HERE]
Within a period from July 7, 2018 to September 23, 2018, you were infected by the virus we've created, through an adult website you've visited.
So far, we have access to your messages, social media accounts, and messengers.
Moreover, we've gotten full damps of these data.
We are aware of your little and big secrets...yeah, you do have them. We saw and recorded your doings on porn websites. Your tastes are so weird, you know..
But the key thing is that sometimes we recorded you with your webcam, syncing the recordings with what you watched!
I think you are not interested show this video to your friends, relatives, and your intimate one...
Transfer $700 to our Bitcoin wallet: 13DAd45ARMJW6th1cBuY1FwB9beVSzW77R
If you don't know about Bitcoin please input in Google "buy BTC". It's really easy.
I guarantee that after that, we'll erase all your "data" :)
A timer will start once you read this message. You have 48 hours to pay the above-mentioned amount.
Your data will be erased once the money are transferred.
If they are not, all your messages and videos recorded will be automatically sent to all your contacts found on your devices at the moment of infection.
You should always think about your security.
We hope this case will teach you to keep secrets.
Take care of yourself.
>> RE >>
Well f### you, thanks for telling my password which is obviously fake. I have sent your details to the local police department, shall rest in peace. Don't earn money by this kind of action. STUPID!17 -
haveibeenpwned: MASSIVE SECURITY BREACH AT COMPANY X, MILLIONS OF RECORDS EXPOSED AND SOLD, YOUR DATA IS AT RISK, please change your password!
Company X website: Hey your password expired! Please change it. Everything's fine, wanna buy premium? The sun is shining. Great day.1 -
"Hey nephew, why doesn't the FB app work. It shows blank white boxes?"
- It can't connect or something? (I stopped using the FB app since 2013.)
"What is this safe mode that appeared on my phone?!"
- I don't know. I don't hack my smartphone that much. Well, I actually do have a customised ROM. But stop! I'm pecking my keyboard most of the time.
"Which of my files should I delete?"
- Am I supposed to know?
"Where did my Microsoft Word Doc1.docx go?"
- It lets you choose the location before you hit save.
"What is 1MB?"
- Search these concepts on Google. (some of us did not have access to the Internet when we learned to do basic computer operations as curious kids.)
"What should I search?"
- ...
"My computer doesn't work.. My phone has a virus. Do you think this PC they are selling me has a good spec? Is this Video Card and RAM good?"
- I'm a programmer. I write code. I think algorithmically and solve programming problems efficiently. I analyse concepts such as abstraction, algorithms, data structures, encapsulation, resource management, security, software engineering, and web development. No, I will not fix your PC.7 -
Example #1 of ??? Explaining why I dislike my coworkers.
[Legend]
VP: VP of Engineering; my boss’s boss. Founded the company, picked the CEO, etc.
LD: Lead dev; literally wrote the first line of code at the company, and has been here ever since.
CISO: Chief Information Security Officer — my boss when I’m doing security work.
Three weeks ago (private zoom call):
> VP to me: I want you to know that anything you say, while wearing your security hat, goes. You can even override me. If you need to hold a release for whatever reason, you have that power. If I happen to disagree with a security issue you bring up, that’s okay. You are in charge of release security. I won’t be mad or hold it against you. I just want you to do your job well.
Last week (engineering-wide meeting):
> CISO: From now on we should only use external IDs in urls to prevent a malicious actor from scraping data or automating attacks.
> LD: That’s great, and we should only use normal IDs in logging so they differ. Sounds more secure, right?
> CISO: Absolutely. That way they’re orthogonal.
> VP: Good idea, I think we should do this going forward.
Last weekend (in the security channel):
> LD: We should ONLY use external IDs in urls, and ONLY normal IDs in logging — in other words, orthogonal.
> VP: I agree. It’s better in every way.
Today (in the same security channel):
> Me: I found an instance of using a plain ID in a url that cancels a payment. A malicious user with or who gained access to <user_role> could very easily abuse this to cause substantial damage. Please change this instance and others to using external IDs.
> LD: Whoa, that goes way beyond <user_role>
> VP: You can’t make that decision, that’s engineering-wide!
Not only is this sane security practice, you literally. just. agreed. with this on three separate occasions in the past week, and your own head of security also posed this before I brought it up! And need I remind you that it is still standard security practice!?
But nooo, I’m overstepping my boundaries by doing my job.
Fucking hell I hate dealing with these people.14 -
"We don't need to invest in security - noone is going to hack us anyway" == "We don't need a fire department in our city - fire is not going to start here anyway"
We don't need to invest in security - everything is public anyway" == "We don't need a fire department in our city - our buildings are made out of straws anyway"
-- my thoughts after seing a line in client's spec: "sensitive data is transferred via a secure tcp channel (https) and all the public data is transferred via an unencrypted tcp (http) channel"3 -
A group of Security researchers has officially fucked hardware-level Intel botnet officially branded as "Intel Management Engine" they did so by gathering it all the autism they were able to get from StackOverflow mods... though they officially call it a Buffer Overflow.
On Wednesday, in a presentation at Black Hat Europe, Positive Technologies security researchers Mark Ermolov and Maxim Goryachy plan to explain the firmware flaws they found in Intel Management Engine 11, along with a warning that vendor patches for the vulnerability may not be enough.
Two weeks ago, the pair received thanks from Intel for working with the company to disclose the bugs responsibility. At the time, Chipzilla published 10 vulnerability notices affecting its Management Engine (ME), Server Platform Services (SPS), and Trusted Execution Engine (TXE).
The Intel Management Engine, which resides in the Platform Controller Hub, is a coprocessor that powers the company's vPro administrative features across a variety of chip families. It has its own OS, MINIX 3, a Unix-like operating system that runs at a level below the kernel of the device's main operating system.
It's a computer designed to monitor your computer. In that position, it has access to most of the processes and data on the main CPU. For admins, it can be useful for managing fleets of PCs; it's equally appealing to hackers for what Positive Technologies has dubbed "God mode."
The flaws cited by Intel could let an attacker run arbitrary code on affected hardware that wouldn't be visible to the user or the main operating system. Fears of such an attack led Chipzilla to implement an off switch, to comply with the NSA-developed IT security program called HAP.
But having identified this switch earlier this year, Ermolov and Goryachy contend it fails to protect against the bugs identified in three of the ten disclosures: CVE-2017-5705, CVE-2017-5706, and CVE-2017-5707.
The duo say they found a locally exploitable stack buffer overflow that allows the execution of unsigned code on any device with Intel ME 11, even if the device is turned off or protected by security software.
For more of the complete story go here:
https://blackhat.com/eu-17/...
https://theregister.co.uk/2017/12/...
I post mostly daily news, commentaries and such on my site for anyone that wish to drop by there 19
19 -
!(short rant)
Look I understand online privacy is a concern and we should really be very much aware about what data we are giving to whom. But when does it turn from being aware to just being paranoid and a maniac about it.? I mean okay, I know facebook has access to your data including your whatsapp chat (presumably), google listens to your conversations and snoops on your mail and shit, amazon advertises that you must have their spy system (read alexa) install in your homes and numerous other cases. But in the end it really boils down to "everyone wants your data but who do you trust your data with?"
For me, facebook and the so-called social media sites are a strict no-no but I use whatsapp as my primary chating application. I like to use google for my searches because yaa it gives me more accurate search results as compared to ddg because it has my search history. I use gmail as my primary as well as work email because it is convinient and an adv here and there doesnt bother me. Their spam filters, the easy accessibility options, the storage they offer everything is much more convinient for me. I use linux for my work related stuff (obviously) but I play my games on windows. Alexa and such type of products are again a big no-no for me but I regularly shop from amazon and unless I am searching for some weird ass shit (which if you want to, do it in some incognito mode) I am fine with coming across some advs about things I searched for. Sometimes it reminds me of things I need to buy which I might have put off and later on forgot. I have an amazon prime account because prime video has some good shows in there. My primary web browser is chrome because I simply love its developer tools and I now have gotten used to it. So unless chrome is very much hogging on my ram, in which case I switch over to firefox for some of my tabs, I am okay with using chrome. I have a motorola phone with stock android which means all google apps pre-installed. I use hangouts, google keep, google map(cannot live without it now), heck even google photos, but I also deny certain accesses to apps which I find fishy like if you are a game, you should not have access to my gps. I live in India where we have aadhar cards(like the social securtiy number in the USA) where the government has our fingerprints and all our data because every damn thing now needs to be linked with your aadhar otherwise your service will be terminated. Like your mobile number, your investment policies, your income tax, heck even your marraige certificates need to be linked with your aadhar card. Here, I dont have any option but to give in because somehow "its in the interest of the nation". Not surprisingly, this thing recently came to light where you can get your hands on anyone's aadhar details including their fingerprints for just ₹50($1). Fuck that shit.
tl;dr
There are and should be always exceptions when it comes to privacy because when you give the other person your data, it sometimes makes your life much easier. On the other hand, people/services asking for your data with the sole purpose of infilterating into your private life and not providing any usefulness should just be boycotted. It all boils down to till what extent you wish to share your data(ranging from literally installing a spying device in your house to them knowing that I want to understand how spring security works) and how much do you trust the service with your data. Example being, I just shared most of my private data in this rant with a group of unknown people and I am okay with it, because I know I can trust dev rant with my posts(unlike facebook).29 -
Privacy & security violations piss me off. Not to the point that I'll write on devRant about it, but to the point that coworkers get afraid from the bloodthirsty look in my eyes.
I know all startups proclaim this, but the one I work at is kind of industry-disrupting. Think Uber vs taxi drivers... so we have real, malicious enemies.
Yet there's still this mindset of "it won't happen to us" when it comes to data leaks or corporate spying.
Me: "I noticed we are tracking our end users without their consent, and store not just the color of their balls, but also their favorite soup flavor and how often they've cheated on their partner, as plain text in the system for every employee to read"
Various C-randomletter-Os: "Oh wow indubitably most serious indeed! Let's put 2 scrumbag masters on the issue, we will tackle this in a most agile manner! We shall use AI blockchains in the elastic cloud to encrypt those ball-colors!"
NO WHAT I MEANT WAS WHY THE FUCK DO WE EVEN STORE THAT INFORMATION. IT DOES IN NO WAY RELATE TO OUR BUSINESS!
"No reason, just future requirements for our data scientists"
I'M GRABBING A HARDDRIVE SHREDDER, THE DB SERVER GOES FIRST AND YOUR PENIS RIGHT AFTER THAT!
(if it's unclear, ball color was an optimistic euphemism for what boiled down to an analytics value which might as well have been "nigger: yes/no")12 -
I wonder why banks are always so terribly insecure, given how much money there's for grabs in there for hackers.
Just a while ago I got a new prepaid credit card from bpost, our local postal service that for some reason also does banking. The reason for that being that - thank you 'Murica! - a lot of websites out there don't accept anything but credit cards and PayPal. Because who in their right mind wouldn't use credit cards, right?! As it turns out, it's pretty much every European I've spoken to so far.
That aside, I got that card, all fine and dandy, it's part of the Mastercard network so at least I can get my purchases from those shitty American sites that don't accept anything else now. Looked into the manual of it because bpost's FAQ isn't very clear about what my login data for their online customer area now actually is. Not that their instruction manual was either.
I noticed in that manual that apparently the PIN code can't be changed (for "security reasons", totally not the alternative that probably they didn't want to implement it), and that requesting a forgotten PIN code can be done with as little as calling them up, and they'll then send the password - not a reset form, the password itself! IN THE FUCKING MAIL.
Because that's apparently how financial institutions manage their passwords. The fact that they know your password means that they're storing it in plain text, probably in a database with all the card numbers and CVC's next to it. Wouldn't that be a treasure trove for cybercriminals, I wonder? But YOU the customer can't change your password, because obviously YOU wouldn't be able to maintain a secure password, yet THEY are obviously the ones with all the security and should be the ones to take out of YOUR hands the responsibility to maintain YOUR OWN password.
Banking logic. I fucking love it.
As for their database.. I reckon that that's probably written in COBOL too. Because why wouldn't you.23 -
Worst legacy experience...
Called in by a client who had had a pen test on their website and it showed up many, many security holes. I was tasked with coming in and implementing the required fixes.
Site turned out to be Classic ASP built on an MS Access database. Due to the nature of the client, everything had to be done on their premises (kind of ironic but there you go). So I'm on-site trying to get access to code and server. My contact was *never* at her desk to approve anything. IT staff "worked" 11am to 3pm on a long day. The code itself was shite beyond belief.
The site was full of forms with no input validation, origin validation and no SQL injection checks. Sensitive data stored in plain text in cookies. Technical errors displayed on certain pages revealing site structure and even DB table names. Server configured to allow directory listing in file stores so that the public could see/access whatever they liked without any permission or authentication checks. I swear this was written by the child of some staff member. No company would have had the balls to charge for this.
Took me about 8 weeks to make and deploy the changes to client's satisfaction. Could have done it in 2 with some support from the actual people I was suppose to be helping!! But it was their money (well, my money as they were government funded!).1 -
Root rents an office.
Among very few other things, the company I'm renting an office from (Regus) provides wifi, but it isn't even bloody secured. There's a captive portal with a lovely (not.) privacy policy saying they're free to monitor your traffic, but they didn't even bother using WEP, which ofc means everyone else out to the fucking parking lot four floors down can monitor my traffic, too.
Good thing I don't work for a company that handles sensitive data! /s But at least I don't have access to it, or any creds that matter.
So, I've been running my phone's connection through a tor vpn and sharing that with my lappy. It works, provides a little bit of security, but it's slow as crap. GET YOUR SHIT TOGETHER, REGUS.
AND WHILE YOU'RE AT IT, CLEAN THE SHIT OUT OF THE FUCKING BATHROOM FFS.
Ugh. $12/day to work in a freaking wind tunnel (thanks, a/c; you're loud as fuck and barely work), hear other people's phone conversations through two freaking walls, pee in a bathroom that perpetually smells like diarrhea, and allow anyone and everyone within a 50+ meter radius to listen to everything my computer says.
Oh, they also 'forgot' to furnish my office, like they promised. Three freaking times. At least I have a table and chair. 🙄
Desk? What desk?
Fucking hell.20 -
!rant
The change log from notepad++ update. The last paragraph is the cream!
" The issue of a hijacked DLL concerns scilexer.dll (needed by Notepad++) on a compromised PC, which is replaced by a modified scilexer.dll built by the CIA. When Notepad++ is launched, the modified scilexer.dll is loaded instead of the original one.
It doesn't mean that CIA is interested in your coding skill or in your sex message content typed in Notepad++, but rather it prevents raising any red flags while the DLL does data collection in the background.
It's not a vulnerability/security issue in Notepad++, but for remedying this issue, from this release (v7.3.3) forward, notepad++.exe checks the certificate validation in scilexer.dll before loading it. If the certificate is missing or invalid, then it just won't be loaded, and Notepad++ will fail to launch.
Checking the certificate of DLL makes it harder to hack. Note that once users’ PCs are compromised, the hackers can do anything on the PCs. This solution only prevents from Notepad++ loading a CIA homemade DLL. It doesn't prevent your original notepad++.exe from being replaced by modified notepad++.exe while the CIA is controlling your PC.
Just like knowing the lock is useless for people who are willing to go into my house, I still shut the door and lock it every morning when I leave home. We are in a f**king corrupted world, unfortunately. "2 -
Not exactly a security bug, but there was a company that made a Django app for some internal work and later open sourced it. I was browsing through the code and I saw that the config file had an IP address and a hashed password for the database credentials
When I tried to use them, I was able to login directly to their read replica RDBMS, I had access to all their customer data (including phones & home addresses)
Being the saint I am, I informed them of the ignorance made by their developer and was presented with some cool swag.5 -
Got laid off on Friday because of a workforce reduction. When I was in the office with my boss, someone went into my cubicle and confiscated my laptop. My badge was immediately revoked as was my access to network resources such as email and file storage. I then had to pack up my cubicle, which filled up the entire bed of my pickup truck, with a chaperone from Human Resources looking suspiciously over my shoulder the whole time. They promised to get me a thumb drive of my personal data. This all happens before the Holidays are over. I feel like I was speed-raped by the Flash and am only just now starting to feel less sick to the stomach. I wanted to stay with this company for the long haul, but I guess in the software engineering world, there is no such thing as job security and things are constantly shifting. Anyone have stories/tips to make me feel better? Perhaps how you have gotten through it? 😔😑😐14
-
Although it might not get much follow up stuffs (probably a few fines but that will be about it), I still find this awesome.
The part of the Dutch government which keeps an eye on data leaks, how companies handle personal data, if companies comply with data protection/privacy laws etc (referring to it as AP from now on) finished their investigation into Windows 10. They started it because of privacy concerns from a few people about the data collection Microsoft does through Windows 10.
It's funny that whenever operating systems are brought up (or privacy/security) and we get to why I don't 'just' use windows 10 (that's actually something I'm asked sometimes), when I tell that it's for a big part due to privacy reasons, people always go into 'it's not that bad', 'oh well as long as it's lawful', 'but it isn't illegal, right!'.
Well, that changed today (for the netherlands).
AP has concluded that Windows 10 is not complying with the dutch privacy and personal data protection law.
I'm going to quote this one (trying my best to translate):
"It appears that Microsofts operating system follows every step you take on your computer. That gives a very invasive image of you", "What does that mean? do people know that, do they want that? Microsoft should give people a fair chance for deciding this by themselves".
They also say that unless explicit lawful consent is given (with enough information on what is collected, for what reasons and what it can be used for), Microsoft is, according to law, not allowed to collect their telemetrics through windows 10.
"But you can turn it off yourself!" - True, but as the paragraph above said, the dutch law requires that people are given more than enough information to decide what happens to their data, and, collection is now allowed until explicitly/lawfully ok'd where the person consenting has had enough information in order to make a well educated decision.
I'm really happy about this!
Source (dutch, sorry, only found it on a dutch (well respected) security site): https://security.nl/posting/534981/...8 -
!rant
*me logging into the demo system*
Me: so what is the login data?
Boss: we are a security company, what do you think?
Me: admin admin?
Boss: admin admin.3 -
My team was sharing an API key to our company's microservice containing all our customer data.
I say "was" because one team member accidentally published the key online so the security team disabled our key and won't give us a new one.
I don't know whether to laugh or cry4 -
Long story short, I'm unofficially the hacker at our office... Story time!
So I was hired three months ago to work for my current company, and after the three weeks of training I got assigned a project with an architect (who only works on the project very occasionally). I was tasked with revamping and implementing new features for an existing API, some of the code dated back to 2013. (important, keep this in mind)
So at one point I was testing the existing endpoints, because part of the project was automating tests using postman, and I saw something sketchy. So very sketchy. The method I was looking at took a POJO as an argument, extracted the ID of the user from it, looked the user up, and then updated the info of the looked up user with the POJO. So I tried sending a JSON with the info of my user, but the ID of another user. And voila, I overwrote his data.
Once I reported this (which took a while to be taken seriously because I was so new) I found out that this might be useful for sysadmins to have, so it wasn't completely horrible. However, the endpoint required no Auth to use. An anonymous curl request could overwrite any users data.
As this mess unfolded and we notified the higher ups, another architect jumped in to fix the mess and we found that you could also fetch the data of any user by knowing his ID, and overwrite his credit/debit cards. And well, the ID of the users were alphanumerical strings, which I thought would make it harder to abuse, but then realized all the IDs were sequentially generated... Again, these endpoints required no authentication.
So anyways. Panic ensued, systems people at HQ had to work that weekend, two hot fixes had to be delivered, and now they think I'm a hacker... I did go on to discover some other vulnerabilities, but nothing major.
It still amsues me they think I'm a hacker 😂😂 when I know about as much about hacking as the next guy at the office, but anyways, makes for a good story and I laugh every time I hear them call me a hacker. The whole thing was pretty amusing, they supposedly have security audits and QA, but for five years, these massive security holes went undetected... And our client is a massive company in my country... So, let's hope no one found it before I did.6 -
@JoshBent suggested that I'd make a blog about security.
Nice idea, fair enough!
*registers domain at provider with discounts at the moment*
*tries to find whois protection option*
"You can add WHOIS protection to your account as an upgrade"
*requests authorization token*
*logs into usual domain name provider account*
*transfers domain name*
*anonymizes WHOIS details within two seconds*
I could've stayed and ask them about the cost etc but the fact that they even HAVE a price for protecting WHOIS data is a no-go for me.
Fuck domain name resellers which ask money for protecting ones WHOIS information (where possible).35 -
Dropped my youngest off at the childminder today and her husband asked me what I'm doing for a job now
.. Explained its security and data science... His reply was to ask if I can setup a printer....5 -
What I'm posting here is my 'manifesto'/the things I stand for. You may like it, you may hate it, you may comment but this is what I stand for.
What are the basic principles of life? one of them is sharing, so why stop at software/computers?
I think we should share our software, make it better together and don't put restrictions onto it. Everyone should be able to contribute their part and we should make it better together. Of course, we have to make money but I think that there is a very good way in making money through OSS.
Next to that, since the Snowden releases from 2013, it has come clear that the NSA (and other intelligence agencies) will try everything to get into anyone's messages, devices, systems and so on. That's simply NOT okay.
Our devices should be OUR devices. No agency should be allowed to warrantless bypass our systems/messages security/encryptions for the sake of whatever 'national security' bullshit. Even a former NSA semi-director traveled to the UK to oppose mass surveillance/mass govt. hacking because he, himself, said that it doesn't work.
We should be able to communicate freely without spying. Without the feeling that we are being watched. Too badly, the intelligence agencies of today do not want us to do this and this is why mass surveillance/gag orders (companies having to reveal their users' information without being allowed to alert their users about this) are in place but I think that this is absolutely wrong. When we use end to end encrypted communications, we simply defend ourselves against this non-ethical form of spying.
I'm a heavy Signal (and since a few days also Riot.IM (matrix protocol) (Riot.IM with end to end crypto enabled)), Tutanota (encrypted email) and Linux user because I believe that only those measures (open source, reliable crypto) will protect against all the mass spying we face today.
The applications/services I strongly oppose are stuff like WhatsApp (yes, encryted messages but the metadata is readily available and it's closed source), skype, gmail, outlook and so on and on and on.
I think that we should OWN our OWN data, communications, browsing stuffs, operating systems, softwares and so on.
This was my rant.17 -
I'm working on a project with a teacher to overview the project at my school to be responsible for the confidential student data...
Teacher: How are we going to authenticate the kiosk machines so people don't need a login?
Me: Well we can use a unique URL for the app and that will put an authorized cookie on the machine as well as local IP whitelisting.
Teacher: ok but can't we just put a secret key in a text file on the C drive and access it with JavaScript?
Me: well JavaScript can't access your drive it's a part of the security protocol built into chrome...
Teacher: well that seems silly! There must be a way.
Me: Nope definately not. Let's just make a fancy shortcut?
Teacher: Alright you do that for now until I find a way to access that file.
I want to quit this project so bad4 -
Had a discussion with a developer about security. His software transfers all user data (password and files) unencrypted, so anyone can grab them with wireshark. I told him that this is a severe issue. He said no its no problem because if you get hacked its your own fault, because you probably used an insecure network. NO ! YOU FUCKING MALADJUSTED SHEEP-MOLESTING OBJECT OF EXECRATION, YOU SHOULD ALWAYS ENCRYPT SENSITIVE USERDATA NO MATTER WHAT NETWORK YOU USE. FUCKING KILL ME ALREADY.
Not implementing encryption is one thing but then acting like its no problem is a fucking nother one. Why do people not understand that security of userdata is important???11 -
M - Me
F - Family member
F: So you study computer science... Could you recover my Gmail login data? I don't remember my email address, password or security question. (7th request to me like that from the same person, they don't bother to write down the recovered pw)
M: I can't do it if I don't know any of the above
F: Wow, I thought you're a good student... Could you at least create a new account for me?
M: But you won't even remember the new... [gets interrupted]
F: So, are you going to talk trash or get to work? You would have already been 50% done
PLEASE I'M SO TIRED OF IT. HOW DO I DEAL WITH THESE OTHER THAN TELLING THEM WHAT I THINK ABOUT THEM. I SEEK HELP12 -
Currently working on the privacy site CMS REST API.
For the curious ones, building a custom thingy on top of the Slim framework.
As for the ones wondering about security, I'm thinking out a content filtering (as in, security/database compatibility) right now.
Once data enters the API, it will first go through the filtering system which will check filter based on data type, string length and so on and so on.
If that all checks out, it will be send into the data handling library which basically performs all database interactions.
If everything goes like I want it to go (very highly unlikely), I'll have some of the api actions done by tonight.
But I've got the whole weekend reserved for the privacy site!20 -
A Month ago...
Me: when are you going to complete the report
Friend: we can do it in minutes
Me: you can't Ctrl + c and Ctrl +v as there is plagiarism check
Friend: we have spin bot
Me: you do that now itself . if something happens? You can join me .
Friend: just chill
Now ...
Me: done with report
Friend: feeding it to spin bot!
Feeds text related to database security....
Spin bot:
Garbage collector == city worker
SQL statements == SQL explanation
SQL queries == SQL interrogation
SQL injection == SQL infusion
Attack == assault
Malicious == noxious
Data integrity == information uprightness
Sensitive == touchy
.....
Me: told you so...
**spin not == article rewriter3 -
Root gets ignored.
I've been working on this monster ticket for a week and a half now (five days plus other tickets). It involves removing all foreign keys from mass assignment (create, update, save, ...), which breaks 1780 specs.
For those of you who don't know, this is part of how rails works. If you create a Page object, you specify the book_id of its parent Book so they're linked. (If you don't, they're orphans.) Example: `Page.create(text: params[:text], book_id: params[:book_id], ...)` or more simply: `Page.create(params)`
Obviously removing the ability to do this is problematic. The "solution" is to create the object without the book_id, save it, then set the book_id and save it again. Two roundtrips. bad.
I came up with a solution early last week that, while it doesn't resolve the security warnings, it does fix the actual security issue: whitelisting what params users are allowed to send, and validating them. (StrongParams + validation). I had a 1:1 with my boss today about this ticket, and I told him about that solution. He sort of hand-waved it away and said it wouldn't work because <lots of unrelated things>. huh.
He worked through a failed spec to see what the ticket was about, and eventually (20 minutes later) ran into the same issues Idid, and said "there's no way around this" (meaning what security wants won't actually help).
I remembered that Ruby has a `taint` state tracking, and realized I could use that to write a super elegant drop-in solution: some Rack middleware or a StrongParams monkeypatch to mark all foreign keys from user-input as tainted (so devs can validate and un-taint them), and also monkeypatch ACtiveRecord's create/save/update/etc. to raise an exception when seeing tainted data. I brought this up, and he searched for it. we discovered someone had already build this (not surprising), but also that Ruby2.7 deprecates the `taint` mechanism literally "because nobody uses it." joy. Boss also somehow thought I came up with it because I saw the other person's implementation, despite us searching for it because I brought it up? 🤨
Foregoing that, we looked up more possibilities, and he saw the whitelist+validation pattern quite a few more times, which he quickly dimissed as bad, and eventually decided that we "need to noodle on it for awhile" and come up with something else.
Shortly (seriously 3-5 minutes) after the call, he said that the StrongParams (whitelist) plus validation makes the most sense and is the approach we should use.
ffs.
I came up with that last week and he said no.
I brought it up multiple times during our call and he said it was bad or simply talked over me. He saw lots of examples in the wild and said it was bad. I came up with a better, more elegant solution, and he credited someone else. then he decided after the call that the StrongParams idea he came up with (?!) was better.
jfc i'm getting pissy again.9 -
I'm fixing a security exploit, and it's a goddamn mountain of fuckups.
First, some idiot (read: the legendary dev himself) decided to use a gem to do some basic fucking searching instead of writing a simple fucking query.
Second, security ... didn't just drop the ball, they shit on it and flushed it down the toilet. The gem in question allows users to search by FUCKING EVERYTHING on EVERY FUCKING TABLE IN THE DB using really nice tools, actually, that let you do fancy things like traverse all the internal associations to find the users table, then list all users whose password reset hashes begin with "a" then "ab" then "abc" ... Want to steal an account? Hell, want to automate stealing all accounts? Only takes a few hundred requests apiece! Oooh, there's CC data, too, and its encryption keys!
Third, the gem does actually allow whitelisting associations, methods, etc. but ... well, the documentation actually recommends against it for whatever fucking reason, and that whitelisting is about as fine-grained as a club. You wanna restrict it to accessing the "name" column, but it needs to access both the "site" and "user" tables? Cool, users can now access site.name AND user.name... which is PII and totally leads to hefty fines. Thanks!
Fourth. If the gem can't access something thanks to the whitelist, it doesn't catch the exception and give you a useful error message or anything, no way. It just throws NoMethodErrors because fuck you. Good luck figuring out what they mean, especially if you have no idea you're even using the fucking thing.
Fifth. Thanks to the follower mentality prevalent in this hellhole, this shit is now used in a lot of places (and all indirectly!) so there's no searching for uses. Once I banhammer everything... well, loads of shit is going to break, and I won't have a fucking clue where because very few of these brainless sheep write decent test coverage (or even fucking write view tests), so I'll be doing tons of manual fucking testing. Oh, and I only have a week to finish everything, because fucking of course.
So, in summary. The stupid and lazy (and legendary!) dev fucked up. The stupid gem's author fucked up, and kept fucking up. The stupid devs followed the first fuckup's lead and repeated his fuck up, and fucked up on their own some more. It's fuckups all the fucking way down.rant security exploit root swears a lot actually root swears oh my stupid fucking people what the fuck fucking stupid fucking people20 -
Paranoid Developers - It's a long one
Backstory: I was a freelance web developer when I managed to land a place on a cyber security program with who I consider to be the world leaders in the field (details deliberately withheld; who's paranoid now?). Other than the basic security practices of web dev, my experience with Cyber was limited to the OU introduction course, so I was wholly unprepared for the level of, occasionally hysterical, paranoia that my fellow cohort seemed to perpetually live in. The following is a collection of stories from several of these people, because if I only wrote about one they would accuse me of providing too much data allowing an attacker to aggregate and steal their identity. They do use devrant so if you're reading this, know that I love you and that something is wrong with you.
That time when...
He wrote a social media network with end-to-end encryption before it was cool.
He wrote custom 64kb encryption for his academic HDD.
He removed the 3 HDD from his desktop and stored them in a safe, whenever he left the house.
He set up a pfsense virtualbox with a firewall policy to block the port the student monitoring software used (effectively rendering it useless and definitely in breach of the IT policy).
He used only hashes of passwords as passwords (which isn't actually good).
He kept a drill on the desk ready to destroy his HDD at a moments notice.
He started developing a device to drill through his HDD when he pushed a button. May or may not have finished it.
He set up a new email account for each individual online service.
He hosted a website from his own home server so he didn't have to host the files elsewhere (which is just awful for home network security).
He unplugged the home router and began scanning his devices and manually searching through the process list when his music stopped playing on the laptop several times (turns out he had a wobbly spacebar and the shaking washing machine provided enough jittering for a button press).
He brought his own privacy screen to work (remember, this is a security place, with like background checks and all sorts).
He gave his C programming coursework (a simple messaging program) 2048 bit encryption, which was not required.
He wrote a custom encryption for his other C programming coursework as well as writing out the enigma encryption because there was no library, again not required.
He bought a burner phone to visit the capital city.
He bought a burner phone whenever he left his hometown come to think of it.
He bought a smartphone online, wiped it and installed new firmware (it was Chinese; I'm not saying anything about the Chinese, you're the one thinking it).
He bought a smartphone and installed Kali Linux NetHunter so he could test WiFi networks he connected to before using them on his personal device.
(You might be noticing it's all he's. Maybe it is, maybe it isn't).
He ate a sim card.
He brought a balaclava to pentesting training (it was pretty meme).
He printed out his source code as a manual read-only method.
He made a rule on his academic email to block incoming mail from the academic body (to be fair this is a good spam policy).
He withdraws money from a different cashpoint everytime to avoid patterns in his behaviour (the irony).
He reported someone for hacking the centre's network when they built their own website for practice using XAMMP.
I'm going to stop there. I could tell you so many more stories about these guys, some about them being paranoid and some about the stupid antics Cyber Security and Information Assurance students get up to. Well done for making it this far. Hope you enjoyed it. 26
26 -
Creating an anonymous analytics system for the security blog and privacy site together with @plusgut!
It's fun to see a very simple API come alive with querying some data :D.
Big thanks to @plusgut for doing the frontend/graphs side on this one!20 -
At the company I worked for earlier, they'd blocked two USB ports citing security policies. The third USB, was unblocked because the system admin didn't know a laptop can have more than 2 USBs .
Gigabit LAN was open.
They just wanted you to copy stuff at higher speed, I think.
If you think blocking a couple of USB ports is going to stop a dev from copying data, well either you're unbearably stupid, or think too less of your devs. It is just gonna hinder their productivity, nothing else.5 -
One of our newly-joined junior sysadmin left a pre-production server SSH session open. Being the responsible senior (pun intended) to teach them the value of security of production (or near production, for that matter) systems, I typed in sudo rm --recursive --no-preserve-root --force / on the terminal session (I didn't hit the Enter / Return key) and left it there. The person took longer to return and the screen went to sleep. I went back to my desk and took a backup image of the machine just in case the unexpected happened.
On returning from wherever they had gone, the person hits enter / return to wake the system (they didn't even have a password-on-wake policy set up on the machine). The SSH session was stil there, the machine accepted the command and started working. This person didn't even look at the session and just navigated away elsewhere (probably to get back to work on the script they were working on).
Five minutes passes by, I get the first monitoring alert saying the server is not responding. I hoped that this person would be responsible enough to check the monitoring alerts since they had a SSH session on the machine.
Seven minutes : other dependent services on the machine start complaining that the instance is unreachable.
I assign the monitoring alert to the person of the day. They come running to me saying that they can't reach the instance but the instance is listed on the inventory list. I ask them to show me the specific terminal that ran the rm -rf command. They get the beautiful realization of the day. They freak the hell out to the point that they ask me, "Am I fired?". I reply, "You should probably ask your manager".
Lesson learnt the hard-way. I gave them a good understanding on what happened and explained the implications on what would have happened had this exact same scenario happened outside the office giving access to an outsider. I explained about why people in _our_ domain should care about security above all else.
There was a good 30+ minute downtime of the instance before I admitted that I had a backup and restored it (after the whole lecture). It wasn't critical since the environment was not user-facing and didn't have any critical data.
Since then we've been at this together - warning engineers when they leave their machines open and taking security lecture / sessions / workshops for new recruits (anyone who joins engineering).26 -
--- iOS-Jailbreak-AppStore "Cydia" shuts down ---
This Friday, Jay Freeman, the maintainer of the iOS-Jailbreak-AppStore "Cydia", announced that he will shut-down his services.
"Cydia" is a app store for people that jailbreaked their iPhones and allows them to buy and download apps. Apple's AppStore doesn't allow jailbreaked apps, that's the reason it was created in 2009.
Jay Freeman, also known as "Saurik", explained that he wanted to shut down the service at the end of 2018 anyways.
Now, a recent security issue, threatening the data of all users, caused that the store no longer existed with immediate effect.
In addition to the security issue, "Cydia" was said to be no more profitable.
To calm you breakers down: Previous purchases can still be downloaded!
The software itself will continue to exist, but without a back-end for payments and stuff like that. Users are still able to do payments through third-party repositories, which already happened anyway, so that lowers the impact of the shut-down.
Just like "Cydia", other services are shutting down too.
One of the three big Cydia-repositories, ModMyi, said they wont allow any new apps and archived all existing ones.
ZodTTD and MacCiti will also be discontinued.
"Bigboss" is the only repository remaining.
Jailbreaks just lost their popularity over the last years. There's still no jailbreak for iOS 11! This shows that Apple is getting better and better at preventing jailbreaks.
On the other hand, it shows that the need for jailbreaks is not quite as high anymore and therefore the developers don't spend too much energy for breaking up iOS anymore.
Did you use Cydia, or any of the other services? Write us in the comments!
Thanks for reading! 12
12 -
The day I discovered Schrödinger's lesser known paradox of simultaneously being fired and not fired.
This isn't really much of a dev story, but I figured I'd share it anyway.
About two minutes into signing into all my stuff, I suddenly was kicked out of everything. I tried logging in a few more times, and then suddenly started getting the error, "Your account has been disabled for security reasons." I couldn't sign into chat, and co-workers confirmed that I was missing from the company directory. My manager didn't come in for another two hours, and we couldn't get anyone else to answer what the hell was going on. So I was kinda panicking.
Eventually, we found out from one of our coordinators that someone else with the same name as me was leaving the company, and they had deactivated the wrong person.
It ended up getting a lot better. They told me that it could take up to 48 hours to restore my access (it took longer), so I found stuff to do so I could maintain my paycheck. One of those things was assisting someone with data collection and processing, where I eventually said, "Dude, I could totally automate this," and now that's what I'm getting paid to do.1 -
Can someone explain to me why the fuck I should even care about the fact, that some companies collect, use and sell my data? I'm not famous, I'm not a politician and I'm not a criminal, I think most of us aren't and won't ever be. We aren't important. So what is this whole bullshittery all about? I seriously don't get it and I find it somewhat weird that especially tech guys and IT "experts" in the media constantly just make up these overly creepy scenarios about big unsafe data collecting companies "stealing" your "private" information. Welcome to the internet, now get the fuck over it or just don't be online. It's your choice, not their's.
I honestly think, some of these "security" companies and "experts" are just making this whole thing bigger than it actually is, because it's a damn good selling point. You can tell people that your app is safe and they'll believe you and buy your shit app because they don't understand and don't care what "safe" or "unsafe" means in this context. They just want to be secure against these "evil monster" companies. The same companies, which you portrayed them as "evil" and "unfair" and "mean" and "unrepentant" for over a decade now.
Just stop it now. All your crappy new "secure" messenger apps have failed awesomely. Delete your life now, please. This isn't about net neutrality or safety on the internet. This is all about you, permanently exaggerating about security and permanently training people to be introverted paranoid egoistic shit people so that they buy your elitist bullshit software.
Sorry for my low english skills, but please stop to exist, thank you.64 -
Dear Australian Government and National Authorities, you can go fuck the right away with this shit!
It’s bad enough we are a country of national data collection with flimsy laws of obtaining access to said data, but to then go that one step further and shove back doors into everything is going too far.
https://news.com.au/technology/...
Under the proposed new laws, Australian government agencies could compel companies to provide technical information such as design specifications to help in an investigation, remove electronic protections, assist in accessing material on a device subject to a warrant and even build or install software or equipment that could help authorities gather information.
What could possibly go wrong 🤷♂️2 -
This happened via mail thread today.
Boss: we need this new brilliant feature I just made up and running asap! Top priority, it has to be done well, for my reputation is on the line!
Me: *looks at the specifics* 'kay, looks easy enough, this evening max and it will be ready. I just nees some extra info about what kind of data validations (I speak no accountant) are needed, and some other details (a total of 3 questiona).
B: Sure! Remember, it needs to be perfect, as my reputation is at stake. Call me on the phone and I'll give you the details!
M: Can't you answer via mail? Thua way both me and the other devs will have clewr guidelines
B: Just call me! Why do you need it to be written down? It's faster this way!
...Fine. I'll keep asking until you're ready to give me a written answer to my questions. No way I'll take security details via phone for something you want in production this evening. No chance in Hell I'll take responsibility for "misunderstanding" what you said on the phone. Why does it always has to be like that?8 -
The IT head of my Client's company : You need to explain me what exactly you are doing in the backend and how the IOT devices are connected to the server. And the security protocol too.
Me : But it's already there in the design documents.
IT Head : I know, but I need more details as I need to give a presentation.
Me : (That's the point! You want me to be your teacher!) Okay. I will try.
IT Head : You have to.
Me : (Fuck you) Well, there are four separate servers - cache, db, socket and web. Each of the servers can be configured in a distributed way. You can put some load balancers and connect multiple servers of the same type to a particular load balancer. The database and cache servers need to replicated. The socket and http servers will subscribe to the cache server's updates. The IOT devices will be connected to the socket server via SSL and will publish the updates to a particular topic. The socket server will update the cache server and the http servers which are subscribed to that channel will receive the update notification. Then http server will forward the data to the web portals via web socket. The websockets will also work on SSL to provide security. The cache server also updates the database after a fixed interval.
This is how it works.
IT Head : Can you please give the presentation?
Me : (Fuck you asshole! Now die thinking about this architecture) Nope. I am really busy.11 -
CR: "Add x here (to y) so it fits our code standards"
> No other Y has an X. None.
CR: "Don't ever use .html_safe"
> ... Can't render html without it. Also, it's already been sanitized, literally by sanitize(), written by the security team.
CR: "Haven't seen the code yet; does X change when resetting the password?"
> The feature doesn't have or reference passwords. It doesn't touch anything even tangentially related to passwords.
> Also: GO READ THE CODE! THAT'S YOUR BLOODY JOB!
CR: "Add an 'expired?' method that returns '!active'?"
> Inactive doesn't mean expired. Yellow doesn't mean sour. There's already an 'is_expired?' method.
CR: "For logging, always use json so we can parse it. Doesn't matter if we can't read it; tools can."
CR: "For logging, never link log entries to user-readable code references; it's a security concern."
CR: "Make sure logging is human-readable and text-searchable and points back to the code."
> Confused asian guy, his hands raised.
CR: "Move this data formatting from the view into the model."
> No. Views are for formatting.
CR: "Use .html() here since you're working with html"
> .html() does not support html. It converts arrays into html.
NONE OF THIS IS USEFUL! WHY ARE YOU WASTING MY TIME IF YOU HAVEN'T EVEN READ MY CODE!?
dfjasklfagjklewrjakfljasdf5 -
MAINTENANCE OF STACKOVERFLOW PLANNED
SHARE TO YOUR NEAREST DEV FRIENDS
Stackoverflow and its relative partners will be closed for two days due to maintenance, new design, and moving server infrastructure from United States to 1km below the Switzerland Alps for extra layers of security. This decision was made by the recent CloudFlare data leak.
Now our servers will be able to handle data leaks because even though the data was leaked, it will fill the empty places in the rocks resulting inaccessible from attackers.
Stackoverflow and its relative partners' maintenance estimated time is February 29 - 30. We will try to finish as fast as possible and bring you guys the best experience. If the maintenance delayes, we will tweet via @StackStatus or post details in our status blog.
Thank you for your support and have a happy day.
Best regards,
Stack Exchange team6 -
Me : I should start building user authentication system.
inner self : there are enough free and secure ones out there, just go read the documentation.
Me : fuck I'm not reading 10000 pages of documentation written in alien language.
inner self : well then you better start building
Me : **writes code
Inner self : you better add the data validation and security while coding
Me : I just want it to work !
Me after a few days trying not to suicide : the site is hacked, the code is bugged, hello darkness my friend5 -
Ten Immutable Laws Of Security
Law #1: If a bad guy can persuade you to run his program on your computer, it's not solely your computer anymore.
Law #2: If a bad guy can alter the operating system on your computer, it's not your computer anymore.
Law #3: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore.
Law #4: If you allow a bad guy to run active content in your website, it's not your website any more.
Law #5: Weak passwords trump strong security.
Law #6: A computer is only as secure as the administrator is trustworthy.
Law #7: Encrypted data is only as secure as its decryption key.
Law #8: An out-of-date antimalware scanner is only marginally better than no scanner at all.
Law #9: Absolute anonymity isn't practically achievable, online or offline.
Law #10: Technology is not a panacea.3 -
So my boss is staring a new security oriented product and he asked one of my colleagues to prepare a presentation about the possible attacks on the product.
During the presentation there was a section on DoS attacks. The boss didn't know what DoS was and after a brief explanation, he interrupted the presentation and said DDoS is not a threat because there is no data stolen. This is a webapp.6 -
I start with the features I want for sure and then i start looking at what data I really really need to store. Then I start looking at what data I don't have to store because of privacy reasons anyways.
Next stop is looking at the security.
When that all looks good, I simply start programming!5 -
Okay, That right there is pathetic https://thehackernews.com/2019/02/... .
First of all telekom was not able to assure their clients' safety so that some Joe would not access them.
Second of all after a friendly warning and pointing a finger to the exact problem telekom booted the guy out.
Thirdly telekom took a defensive position claiming "naah, we're all good, we don't need security. We'll just report any breaches to police hence no data will be leaked not altered" which I can't decide whether is moronic or idiotic.
Come on boys and girls... If some chap offers a friendly hand by pointing where you've made a mistake - fix the mistake, Not the boy. And for fucks sake, say THANK YOU to the good lad. He could use his findings for his own benefit, to destroy your service or even worse -- sell that knowledge on black market where fuck knows what these twisted minds could have done with it. Instead he came to your door saying "Hey folks, I think you could do better here and there. I am your customes and I'd love you to fix those bugzies, 'ciz I'd like to feel my data is safe with you".
How on earth could corporations be that shortsighted... Behaviour like this is an immediate red flag for me, shouting out loud "we are not safe, do not have any business with us unless you want your data to be leaked or secretly altered".
Yeah, I know, computer misuse act, etc. But there are people who do not give a tiny rat's ass about rules and laws and will find a way to do what they do without a trace back to them. Bad boys with bad intentions and black hoodies behind TOR will not be punished. The good guys, on the other hand, will.
Whre's the fucking logic in that...
P.S. It made me think... why wouldn't they want any security vulns reported to them? Why would they prefer to keep it unsafe? Is it intentional? For some special "clients"? Gosh that stinks6 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
So I have seen this quite a few times now and posted the text below already, but I'd like to shed some light on this:
If you hit up your dev tools and check the network tab, you might see some repeated API calls. Those calls include a GET parameter named "token". The request looks something like this: "https://domain.tld/api/somecall/..."
You can think of this token as a temporary password, or a key that holds information about your user and other information in the backend. If one would steal a token that belongs to another user, you would have control over his account. Now many complained that this key is visible in the URL and not "encrypted". I'll try to explain why this is, well "wrong" or doesn't impose a bigger security risk than normal:
There is no such thing as an "unencrypted query", well besides really transmitting encrypted data. This fields are being protected by the transport layer (HTTPS) or not (HTTP) and while it might not be common to transmit these fields in a GET query parameter, it's standard to send those tokens as cookies, which are as exposed as query parameters. Hit up some random site. The chance that you'll see a PHP session id being transmitted as a cookie is high. Cookies are as exposed as any HTTP GET or POST Form data and can be viewed as easily. Look for a "details" or "http header" section in your dev tools.
Stolen tokens can be used to "log in" into the website, although it might be made harder by only allowing one IP per token or similar. However the use of such a that token is absolut standard and nothing special devRant does. Every site that offers you a "keep me logged in" or "remember me" option uses something like this, one way or the other. Because a token could have been stolen you sometimes need to additionally enter your current password when doings something security risky, like changing your password. In that case your password is being used as a second factor. The idea is, that an attacker could have stolen your token, but still doesn't know your password. It's not enough to grab a token, you need that second (or maybe thrid) factor. As an example - that's how githubs "sudo" mode works. You have got your token, that grants you more permissions than a non-logged in user has, but to do the critical stuff you need an additional token that's only valid for that session, because asking for your password before every action would be inconvenient when setting up a repo
I hope this helps understanding a bit more of this topic :)
Keep safe and keep asking questions if you fell that your data is in danger
Reeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee5 -
If you discount all the usual sql injections the most blatant was not our but a system one customer switched to after complaining over cost.
The new system was a bit more bare bones featurewize but the real gem was the profile page for their customers.
The only security was an id param pointing to the users primary key, which was an auto incrementing integer :)
And not only could you access all customer data but you could change it to.
But since the new system was built by their it chief’s son we realized it was not much we could do.2 -
I used to do audits for private companies with a team. Most of them where black box audits and we were allowed to physically manipulate certain machines in and around the building, as long as we could get to them unnoticed.
Usually when doing such jobs, you get a contract signed by the CEO or the head of security stating that if you're caught, and your actions were within the scope of the audit, no legal action will be taken against you.
There was this one time a company hired us to test their badge system, and our main objective was to scrape the data on the smartcards with a skimmer on the scanner at the front of the building.
It's easy to get to as it's outside and almost everyone has to scan their card there in order to enter the building. They used ISO 7816 cards so we didn't even really need specified tools or hardware.
Now, we get assigned this task. Seems easy enough. We receive the "Stay-out-of-jail"-contract signed by the CEO for Company xyz. We head to the address stated on the contract, place the skimmer etc etc all good.
One of our team gets caught fetching the data from the skimmer a week later (it had to be physically removed). Turns out: wrong Building, wrong company. This was a kind of "building park" (don't really know how to say it in English) where all the buildings looked very similar. The only difference between them was the streetnumber, painted on them in big. They gave us the wrong address.
I still have nightmares about this from time to time. In the end, because the collected data was never used and we could somewhat justify our actions because we had that contract and we had the calls and mails with the CEO of xyz. It never came to a lawsuit. We were, and still are pretty sure though that the CEO of xyz himself was very interesed in the data of that other company and sent us out to the wrong building on purpose.
I don't really know what his plan after that would have been though. We don't just give the data to anyone. We show them how they can protect it better and then we erase everything. They don't actually get to see the data.
I quit doing audits some time ago. It's very stressful and I felt like I either had no spare time at all (when having an active assignment) or had nothing but spare time (when not on an assignment). The pay also wasn't that great.
But some people just really are polished turds.4 -
Well, for starters there was a cron to restart the webserver every morning.
The product was 10+ years old and written in PHP 5.3 at the time.
Another cron was running every 15 minutes, to "correct" data in the DB. Just regular data, not from an import or something.
Gotta have one of those self-healing systems I guess.
Yet another cron (there where lots) did run everyday from 02:00 to 4ish to generate the newest xlsx report. Almost took out the entire thing every time. MySQL 100%. CPU? Yes. RAM? You bet.
Lucky I wasn't too much involved at the time. But man, that thing was the definition of legacy.
Fun fact: every request was performed twice! First request gave the already logged-in client an unique access-token. Second request then processed the request with the (just issued) access-token; which was then discarded. Security I guess.
I don't know why it was build this way. It just was. I didn't ask. I didn't wanted to know. Some things are better left undisturbed. Just don't anger the machine. I became superstitious for a while. I think, in the end, it help a bit: It feels like communicating with an alien monster but all you have is a trumpet and chewing gum. Gentle does it.
Oh and "Sencha Extjs 3" almost gave me PTSD lol (it's an ancient JS framework). Followed by SOAPs WSDL cache. And a million other things.5 -
Found that out that one of our company's internal API (I hope it's only internal) is exposing some personal data. After finally getting the right people involved they said they'd fix it 'immediately'.
5 days later I check and now there is more personal data exposed...which includes personal security questions and the hashed answers to said questions.
And of course they are using a secure hashing mechanism...right? Wrong. md5, no salt
Sigh...5 -
DEAR CTOs, PLEASE ASK THE DEVELOPER OF THE SOFTWARE WHICH YOU ARE PLANNING TO BUY IN WHAT LANGUAGE AND WHAT VERSION THEY ARE WRITTEN IN.
Background: I worked a LONG time for a software company which developed a BIG crm software suite for a very niche sector. The softwary company was quite successfull and got many customers, even big companies bought our software. The thing is: The software is written in Ruby 1.8.7 and Rails 2. Even some customer servers are running debian squeeze... Yes, this setup is still in production use in 2022. (Rails 7 is the current version). I really don't get it why no one asked for the specific setup, they just bought it. We always told our boss, that we need time to upgrade. But he told every time, no one pays for an tech upgrade... So there it is, many TBs of customer data are in systems which are totally old, not updated and with possibly security issues.9 -
A popular social media website in my country (which my friends and I were working on it's new design) was hacked and everyone on the dev side of the website was invited to the ministry of communications, believing we were going to discuss security of user data. The other guys (working on the back-end) were friends with the CEO (if you want to call it that) and naturally came to the meeting. They started to talk about the girls of their city. Meanwhile about 1.2 million user data encrypted with MD5 was out there.6
-
Necessary context for this rant if you haven't read it already: https://devrant.com/rants/2117209
I've just found my LUKS encrypted flash drive back. It was never stolen.. it somehow got buried in the depths of my pockets. No idea how I didn't look into my jacket for the entire time since that incident happened... But I finally found it back. None of my keys were ever compromised. And there's several backups that were stored there that have now been recovered too. Time to dd this flash drive onto a more permanent storage medium again for archival. Either way, it did get me thinking about the security of this drive. And I'll implement them on the next iteration of it.
For now though.. happy ending. So relieved to see that data back...
Full quality screenshot: https://nixmagic.com/pics/... 11
11 -
iPhones are ridiculously picky when it comes to finding a mate- um charger. And knowing why doesn't really make it any easier to understand why. If anything it baffles me more.
So, let's start with appliances that are not phones. Think Bluetooth headsets, keyboards, earbuds, whatever. Those are simple devices. They see 5V on the VCC line and 0V on ground, and they will charge at whatever current they are meant to. Usually it will not exceed 200mA, and the USB 2.0 spec allows for up to 500mA from any USB outlet. So that's perfectly reasonable to be done without any fuss whatsoever.
Phones on the other hand are smarter.. some might say too smart for their own good. In this case I will only cover Android phones, because while they are smarter than they perhaps should be, they are still reasonable.
So if you connect an Android phone to the same 5V VCC and 0V ground, while leaving the data lines floating, the phone will charge at 500mA. This is exactly to be within USB 2.0 spec, as mentioned earlier. Without the data lines, the phone has no way to tell whether it *can* pull more, without *actually* trying to pull more (potentially frying a charger that's not rated for it). Now in an Android phone you can tell it to pull more, in a fairly straightforward way. You just short the data lines together, and the phone will recognize this as a simple charger that it can pull 1A from. Note that shorting data lines is not a bad thing, we do it all the time. It is just another term for making a connection between 2 points. Android does this right. Also note that shorted data lines cannot be used to send data. They are inherently pulled to the same voltage level, probably 0V but not sure.
And then the iPhones come in, Thinking Different. The iPhones require you to pull the data lines to some very specific voltage levels. And of course it's terribly documented because iSheep just trying to use their Apple original white nugget charger overseas and shit like that. I do not know which voltage levels they are (please let me know!), but it is certainly not a regular short. Now you connect the iPhone to, say, a laptop or something to charge. An Android phone would just charge while keeping data transmission disabled (because they can be left floating or shorted). This is for security reasons mostly, preventing e.g. a malicious computer from messing with it. An iPhone needs to be unlocked to just charge the damn thing. I'm fairly sure that that's because the data lines need to be pulled up, which could in theory enable a malicious computer to still get some information in or out of it. USB data transmission works at at least 200mV difference between the data lines. It could be more than that. So you need to unlock it.
Apple, how about you just short your goddamn data lines too like everyone else? And while you're at it, get rid of this Lightning connector. I get it, micro USB was too hard for your users. I guess they are blind pigs after all. But USB-C solved all of that and more. The only difference I can think of is that the Lightning connector can be a single board with pads on either side on the connector, while in USB-C that could be at the socket end (socket being less common to be replaced). And at the end of the day, that really doesn't matter with all the other things that will break first.
Think Different. Think Retarded. Such tiny batteries and you can't even fucking charge them properly.6 -
Can https be decrypted easily?
(Or even by spending some time)
Plus what other security methods banks apply to prevent theft of sensible data?
Do they encrypt data using thair own private key thet is changed automatically?29 -
WTF!!!!! I officially have someone trying to extort me just had this in my email box this morning!
--------
Hello,
My name is [name removed], I'm an IT security expert and I found a security issue on your website.
This email is personal and in no way related to any of my employers.
I was able to access to a lot of files which contains sensitive data.
I attached a screenshot of the files I found to this email.
I would be happy to give you the method I used to access these files in order to let you fix it.
Would be a monetary compensation possible?
Please forward this email to the right person, if your are not responsible for the security of the website.
Best Regards,
[name removed]
---
He can basically see the contents of my wp-config.php. How has he managed this?71 -
I work in big data and security analytics... So naturally I am a very detail oriented and analytical person.... Something that I constantly get told off about for 'over analysing' every personal situation.... Especially by my wife!
Today she was chatting to our best friend on WhatsApp who's been travelling Europe for 6 months seeing how life is etc... At the end of the conversation I point out he never once told her where he was and avoided the questions.... And that I was sure he was gonna turn up tonight....
She tells me I'm over analysing and full of it as she's in Spain.... Not even an hour later he walked through our front door and we are in the pub having an awesome catch up!
Who said I'm over analytical! More like right!?4 -
YouTube: SPENDING 24 HOURS IN PRISON CHALLENGE (GONE WRONG) (GONE SEXUAL) (COPS CALLED)
devRant: SPENDING 24 HOURS STRAIGHT ON DEVRANT TELLING EVERYONE THAT APPLE IS BAD AND MY SECURITY IS BETTER (GONE WRONG) (DATA BREACHED) (DFOX CALLED)21 -
Thank God the week 233 rants are over - was getting sick of elitist internet losers.
The worst security bug I saw was when I first started work as a dev in Angular almost year ago. Despite the code being a couple of years old, the links to the data on firebase had 0 rules concerning user access, all data basically publicly available, the API keys were uploaded on GitHub, and even the auth guard didn't work. A proper mess that still gives me the night spooks to this day.3 -
I’m LOLing at the audacity of one of our vendors.
We contract with a vendor to build and maintain a website. Our network security team noticed there was a security breach of the vendor’s website. Our team saw that malicious users gained access to our Google Search console by completing a challenge that was issued to the vendor’s site.
At first, the vendor tried to convince us that their site wasn’t comprised and it was the Google search Console that was compromised. Nah dude. Our Search Console got compromised via the website you maintain for us. Luckily our network team was able to remove the malicious users from our search console.
That vendor site accepts credit card payments and displays the user’s contact info like address, email, and phone. The vendor uses keys that are tied to our payment gateway. So now my employer is demanding a full incident report from the vendor because their dropping the ball could have compromised our users’ data and we might be responsible for PCI issues.
And the vendor tried to shit on us even more. The vendor also generates vanity urls for our users. My employer decided to temporarily redirect users to our main site (non vendor) because users already received those links and in order to not lose revenue. The vendor’s solution is to build a service that will redirect their vanity urls to our main site. And they wanted to charge us $5000 usd for this. We already pay them $1000 a month already.
WTAF we are not stupid. Our network service team said we could make the argument that they do this without extra charge because it falls in the scope of our contract with them. Our network team also said that we could terminate the contract because the security breach means they didn’t render the service they were contracted to do. Guess it’s time for us to get our lawyer’s take on this.
So now it looks like my stakeholders want me to rebuild all of this in house. I already have a lot on my plate, but I’m going to be open to their requests because we are still in the debrief phase.2 -
"I found this tool that we should use because I'm a manager and its simple enough that my tiny little manager brain could set it up!"
Oh wow good for you, Mr. Manager! And what, praytell, does the tool require?
"All proprietary and cost-ineffecient products: MSSQL Server and Windows IIS! What do you mean we have to get the data out in order for it to be scalable? Look at it! I set up a website by clicking on an EXE i downloaded from github!"
Amazing, Mr. Manager. So you violated our security practices AND want to pocket even MORE of our budget?
Kindly fuck right off and start suggesting things instead of making people embarrass you into stoping your fight for your tool (has happened on more than one occassion).3 -
First year: intro to programming, basic data structures and algos, parallel programming, databases and a project to finish it. Homework should be kept track of via some version control. Should also be some calculus and linear algebra.
Second year:
Introduce more complex subjects such as programming paradigms, compilers and language theory, low level programming + logic design + basic processor design, logic for system verification, statistics and graph theory. Should also be a project with a company.
Year three:
Advanced algos, datastructures and algorithm analysis. Intro to Computer and data security. Optional courses in graphics programming, machine learning, compilers and automata, embedded systems etc. ends with a big project that goes in depth into a CS subject, not a regular software project in java basically.4 -
WARNING: There is a dangerous malware out in the wild, and chances are, you have it installed on your computer.
It's called Windows Update, and it is marketed as a software that "delivers security patches to your PC". Wrong. What it actually does is hard-reboot your computer at randomly picked time intervals without asking for your consent, or even showing any type of warning, basically deleting all unsaved progress that you've made in your programs or games. It also deletes/undoes all registry tweaks that you might have made (e.g. to the context menu), it deletes your nvidia display configurations, uninstalls any custom themes that you might have installed, possibly even downloads another malware disguised as "Microsoft Edge" and shoves it in your face on next boot without giving a possibility to close it. Oh and it might also make your computer unbootable so you have to go to the advanced recovery settings to fix it manually.
Yes, everything I just mentioned above happened to me about an hour ago. This LITERALLY classifies the software as a malware (Google: "software that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system"). If we throw in all the data collection that happens without your consent, Microsoft actually manages to check not only one, but all three boxes in the "malware" definition.
Pleas, stop using microshit, and switch to linux as soon as possible if you can.24 -
The security on my school computers is a joke.
The standard student accounts have no user rights, but the "guest" account has admin rights???
The teachers private data is not secured, it's just hidden from explorer, so if you manually type in the folder location into the explorer bar, you can access the teacher's data. Not to mention everything is running on Windows 7 machines from 10 years ago.1 -
Got a job as a database manager, they wanted me to update their sql server and some of their .net apps. Turns out their sql server had no databases and all their data was stored in an ms access 2003 applications that was using windows for workgroups security!!! It also had no interface, hundreds of tables and queries and there were multiple access db it was connected to. To make things worse the person who built all this stuff used acronyms for everything he did, table names, variables, queries and even bloody window folders!!! It was hard as hell to figure out what anything ment. Oh and the .net apps were asp sites that heavily used dll for storing his code and no one knows where the original source code for them are. Did I also mention there were no comments for any of the code, no database dictionary, no notes or anything.
So apparently I'll be rebuilding everything from scratch and transferring over the data to sql server. AND NO MORE F**KING ACRONYMS!!!!!!!2 -
I have a few of these so I'll do a series.
(1 of 3) Public privates
We had a content manager that created a content type called "news item" on a Drupal site. There where two file fields on there. One called "attachments" and the other called "private attachments". The "private attachments" are only for members to see and may contain sensitive data. It was set to go trough Drupals security (instead of being directly hosted by the webserver) but because the permissions on the news items type where completely public everybody had access. So basically it was a slow public file field.
This might be attibuted to ow well Drupal is confusing. Howerver weeks earlier that same CM created a "private article". This actually had permissions on the content type correctly but had a file field that was set to public. So when a member posted the URL to a sensitive file trough unsafe means it got indexed by google and for all to read. When that happend I explained in detail how the system worked and documented it. It was even a website checklist item.
We had two very embarrassing data leaks :-(1 -
What you are expected to learn in 3 years:
power electronics,
analogue signal,
digital signal processing,
VDHL development,
VLSI debelopment,
antenna design,
optical communication,
networking,
digital storage,
electromagnetic,
ARM ISA,
x86 ISA,
signal and control system,
robotics,
computer vision,
NLP, data algorithm,
Java, C++, Python,
javascript frameworks,
ASP.NET web development,
cloud computing,
computer security ,
Information coding,
ethical hacking,
statistics,
machine learning,
data mining,
data analysis,
cloud computing,
Matlab,
Android app development,
IOS app development,
Computer architecture,
Computer network,
discrete structure,
3D game development,
operating system,
introduction to DevOps,
how-to -fix- computer,
system administration,
Project of being entrepreneur,
and 24 random unrelated subjects of your choices
This is a major called "computer engineering"4 -
I think I finally found a reason to have a phone with 8GB of RAM.
So that when TWRP craps out on data decryption and decides not even to ask for a password, at least I can push a whole fucking ROM into RAM to unfuck the phone. Because why not?! Why on Earth would software work properly when you can just throw more hardware at it?
Long live FBE, TWRP what craps out on it, and you remember those things.. SD cards for data storage? I could've used an unencrypted SD card so fucking badly right now, you know... Long live soldered in storage that's encrypted, "for security". Except for when the person who owns said data actually wants to use the bloody data.
FUCK!2 -
PyTorch.
2018: uh, what happens when someone uses a same name attack? - No big deal. https://github.com/pypa/pip/...
2020: I think that's a security issue. - Nanana, it's not. https://github.com/pypa/pip/...
2022: malicious package extracts sensitive user data on nightly. https://bleepingcomputer.com/news/...
You had years to react, you clowns.6 -
Fuck you Intel.
Fucking admit that you're Hardware has a problem!
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data"
With Meltdown one process can fucking read everything that is in memory. Every password and every other sensible bit. Of course you can't change sensible data directly. You have to use the sensible data you gathered... Big fucking difference you dumb shits.
Meltown occurs because of hardware implemented speculative execution.
The solution is to fucking separate kernel- and user-adress space.
And you're saying that your hardware works how it should.
Shame on you.
I'm not saying that I don't tolerate mistakes like this. Shit happens.
But not having the balls to admit that it is because of the hardware makes me fucking angry.5 -
Indian outsourcing web companies on their websites be like:
"We provide services in IOT, Machine Learning, Data Analysis, Web security analysis, blah blah"
Me excitingly joins the company and finds out, they all are PHP developers developing unsecured websites.1 -
There you are, fiddling with next.js webpack settings, because your isomorphic JS-in-CSS-in-JS SSR fallback from react-native-web to react-dom throws a runtime error on your SSR prerendering server during isomorphic asynchronous data prefetching from Kubernetes backend-for-frontend edge-server with GraphQL.
You have all that tech to display a landing page with an email form, just to send spam emails with ten tracking links and five tracking beacons per email.
Your product can be replaced by an Excel document made in two days.
It was developed in two years by a team of ten developers crunching every day under twelve project managers that can be replaced with a parrot trained to say “Any updates?”
Your evaluation is $5M+. You have 10,000 dependency security warnings, 1000 likes on Product Hunt, 500 comments on Hacker News, and a popular Twitter account.
Your future looks bright. You finish your coffee, crack your knuckles and carry on writing unit tests. 5
5 -
Fucking shit i just had a 3 days chat with google's cloud engineer about an issue i had in a project. eventually the issue occured due to an update they made on some projects involving IAM changes that required some changes from my part in my security toles. Like wtf haven't you heard of data fixes when you roll out such changes?! I just had my production env down for 72hours for their fuckup.
At least send an email regarding it so we could set it up in time1 -
Hey, we need a service to resize some images. Oh, it’ll also need a globally diverse cache, with cache purging capabilities, only cache certain images in the United States, support auto scaling, handle half a petabyte of data , but we don’t know when it’ll be needed, so just plan on all of it being needed at once. It has to support a robust security profile using only basic HTTP auth, be written in Java, hosted on-prem, and be fully protected from ddos attacks. It must be backwards compatible with the previous API we use, but that’s poorly documented, you’ll figure it out. Also, it must support being rolled out 20% of the way so we can test it, and forget about it, and leave two copies of our app in production.
You can re-use the code we already have for image thumbnails even though it’s written in Python, caches nothing and is hosted in the cloud. It should be easy. This guy can show you how it all works.2 -
TL:DR
Why do so shitty "API"s exist that are even harder to write than proper ones? D:
Trying to hack my venilation at home.
This API is so horrible D:
The API is only based on POST requests no matter if you want to write values or get values and the response only contains XML with cryptic values like:
<?xml version="1.0" encoding="UTF-8"?>
<PARAMETER>
<LANG>de</LANG>
<ID>v01306</ID>
<VA>00011100000000000000000010000001</VA>
<ID>v00024</ID>
<VA>0</VA>
<ID>v00033</ID>
<VA>2</VA>
<ID>v00037</ID>
<VA>0</VA>
Also there are multiple API routes like
POST /data/werte1.xml
POST /data/werte2.xml
POST /data/werte3.xml
POST /data/werte4.xml
And actually the real API route is only given in the request body and not in the path.
Why is this so shitty? D:<
Btw in terms of security this is also top notch. It just globally saves if one computer sends the login password.
I mean why even ask for a password then? D:
That made me end up with a cronjob to send a login request so I don't have to login on any device.
PS:
You see, great piece of German engineering.3 -
So I just started a part time job in a hospital research center - because the processing is long I got a temporary user name and password (that belong to the main HR secretary) so I can start work straight away (mainly data analytics)
The kick?
Administrator privileges.
I can access edit create or delete everything in the entire fucking database. On my first God damn day.
In the 2nd largest hospital in the fucking country.
Agh. How do systems survive with so many dumb security breaches?4 -
Around 2 years ago, I had first discovered DevRant.
I was an intern in a startup then, and I was working on ElasticSearch. I remember making rants about it. The internship ended. So did my relationship with ElasticSearch.
This week, a new intern joined our organisation (a different organisation). He was assigned the task of deploying ElasticSearch, with me as his mentor. All was going good, we migrated data from MongoDB to ElasticSearch and all.
Back then, I used to curse the team lead (leading a team of interns mostly), for not helping me properly...
I wanted a publicly accessible dashboard, since we can't really see the Kibana dashboard with SSH :P... So, we implemented user authentication using X-Pack security. And here we are, stuck... Again... I'm unable to help the intern. The World has come to a full circle.
PS: I have to just guide him while doing my own User Stories.
https://stackoverflow.com/questions... -
!(!(!(!(!(!(!(!rant)))))))
My new HTC smartphone hates me.
First it started to shut down all of the sudden yesterday night, when I was solving quadratic equations on my laptop.
I thought that it might be due to low battery. So I have restarted it. After putting itself into a bootloop for 4 start sequences, it was able to fully start to the page where it told me to enter the security pin to decrypt my files. I also had 30 attempts left. Like a ransomware.
I was like "tf I didn't set anything up".
So I decided to use my first attempt as I had 30 attempts left.
I entered the pin (I can swear that it's correct) and it told me that it has to wipe the /data partition.
I did that. I pressed that button. After waiting for 30 minutes I gave up and rebooted into the bootloader.
Bootloader -> Download Mode -> wipe /data (stock rom + stock recovery btw.)
Some error with "e: mount /cache failed[...]e: mount /data failed"
So, I tried using the adb sideload - no success.
Fastbooted into RUU Mode - HTC keeps rebooting itself into the RUU Mode - no success
Tried to flash the firmware and twrp recovery from Download mode - no success
Then I tried to flash all these things from the sd card - no success
Searched for revolutionary (I know this from my old HTC sensation device).
It wasn't big of any help.
Then someone on xda recommended htcDev (htc's <b>developer-friendly</b> lol site)
I followed every step. Everything seemed to be okay.
I got to the last step.
I needed to get my encrypted token by entering "fastboot oem get_identifier_token" to be able to submit it to HTC, and after they would send me an e-Mail with an .bin file that would let me unlock the bootloader to be able to flash my way through all this headache giving fucking piece of dog shit!
But since I can't back to the phone settings to select the bootloader activation box that would let me get my token... but nah.
FML
------------
Sent by using the devRant web app (:\)8 -
The amount of "full stack" developers I've seen that know nothing about networking, servers or security has broken me inside over the years. Like cmon man either learn that stuff or stick to doing frontend. Don't put user's data at risk just because you wanna earn a bit more money11
-
When you can finally leave work after a long day and then your security card's data gets erased and you can't leave the building8
-
So I enventually spent 2 years working for that company with a strong b2b market. Everything from the checkouts in their 6 b2c stores to the softwares used by the 30-people sales team was dependant on the main ERP shit home-built with this monstruosity we call Windev here in France. If you don't know it just google and have some laugh : this is a proprieteray FRENCH language. Not french like made by french people, well that too, but mostly french like the fucking language is un fucking french ! Instructions are on french, everything. Hey that's my natural language okay, but for code, really ?
The php website was using the ERP database too, even all the software/hardware of the massive logistic installation they had (like a tiny Amazon depot), and of course the emails of all employees. Everything was just handled by this unique shitty and so sloooooow fucking app. When there was to many clients on the website or even too many salespeople connected to the ERP at the same time, every-fuckin-piece of the company was slowing down, and even worse facing critical bugs. So they installed a monitor in the corner of a desk constantly showing the live report page of Google analytics and they started panic attacks everytime it was counting more than 30 sessions on the website. That was at the time fun and sad to observe.
The whole shit was created 12 years ago and is since maintened locally by one unique old-fashion-microsoft dev who also have to maintain all the hardware of all the fucking 150+ people business. You know, when the keyboard of anyone is "broken" cause it's unplugged... That's his job too. The poor guy was totally overstressed on a daily basis and his tech knowledge just saddly losts themeselves somewhere in the way. He was my n+1 in a tech team of 3 people : him, a young and inexperimented so-called "php developer" who was in charge of the website (btw full of security holes I discovered and dealed with when I first arrive at the job), and myself.
The database was a hell of 100+ tables of business and marketing data with a ton of specific logic added on-the-go during years. No consistent data model or naming. No utf8. Fucked up relations that ends with queries long enough to fill books. And that's not all, all the customers passwords was just stored there uncrypted. Several very big companies and administrations were some of these clients. I was insisting on the passwords point litterally all the time, that was an easy security fix and a good start... But no, in two years of discussions on the subject I never achieved to have them focusing on other considerations than "our customers like that we can remind them their password by a simple phone call if they lost it". What. The. Fuck. WHATTHEFUCK!
Eventually I ran myself out of this nightmare. I had a few bad jobs already, and worked on shitty software already. But that one really blows my mind (and motivation for a time too). Happy it's over.1 -
Rant considering the latest Cyber attack and the news around it.
(A recap: a lot of Windows computers were infected with ransomware (due to security hole on Windows), which demanded 300$ in bitcoins to unlock data. After 3 days the price would double, and after 7 days the data was to be deleted)
1) In our country, one of the biggest companies was attacked (car factory). The production stopped and they got for around 1 000 000€ damage in less than 24h (1300 people without work). The news said that they were attacked because they are such a big company and were charged more, as the hackers "knew who they were dealing with" - another reason being the fact that the text was in croatian (which is our neighbor country), but noone realized that it is just a simple google translate of english text - which is obviously not true. The hackers neither know nor care who is hacked, and will charge everyone the same. They only care about the payment.
2) In UK whole (or large part) of medical infrastructure went down. The main thing everyone was saying was: "Nobody's data is stolen". Which, again, is obvious. But noone said anything about data being deleted after a week, which includes pretty much whole electronic medical record of everyone and is pretty serious.
And by the way, the base of the ransomware is code which was stolen from NSA.
All that millions and millions of dollars of damage could be avoided by simply paying the small fee.
The only thing that is good is that (hopefully) the people will learn the importance of backups. And opening weird emails.
P.S. I fucking hate all that 'hacky thingys' they have all over the news.5 -
Whelp. I started making a very simple website with a single-page design, which I intended to use for managing my own personal knowledge on a particular subject matter, with some basic categorization features and a simple rich text editor for entering data. Partly as an exercise in web development, and partly due to not being happy with existing options out there. All was going well...
...and then feature creep happened. Now I have implemented support for multiple users with different access levels; user profiles; encrypted login system (and encrypted cookies that contain no sensitive data lol) and session handling according to (perceived) best practices; secure password recovery; user-management interface for admins; public, private and group-based sections with multiple categories and posts in each category that can be sorted by sort order value or drag and drop; custom user-created groups where they can give other users access to their sections; notifications; context menus for everything; post & user flagging system, moderation queue and support system; post revisions with comparison between different revisions; support for mobile devices and touch/swipe gestures to open/close menus or navigate between posts; easily extendible css themes with two different dark themes and one ugly as heck light theme; lazy loading of images in posts that won't load until you actually open them; auto-saving of posts in case of browser crash or accidental navigation away from page; plus various other small stuff like syntax highlighting for code, internal post linking, favouriting of posts, free-text filter, no-javascript mode, invitation system, secure (yeah right) image uploading, post-locking...
On my TODO-list: Comment and/or upvote system, spoiler tag, GDPR compliance (if I ever launch it haha), data-limits, a simple user action log for admins/moderators, overall improved security measures, refactor various controllers, clean up the code...
It STILL uses a single-page design, and the amount of feature requests (and bugs) added to my Trello board increases exponentially with every passing week. No other living person has seen the website yet, and at the pace I'm going, humanity will have gone through at least one major extinction event before I consider it "done" enough to show anyone.
help4 -
Oh boy I got a few. I could tell you stories about very stupid xss vectors like tracking IDs that get properly sanitized when they come through the url but as soon as you go to the next page and the backend returns them they are trusted and put into the Dom unsanitized or an error page for a wrong token / transaction id combo that accidentally set the same auth cookie as the valid combination but I guess the title "dumbest" would go to another one, if only for the management response to it.
Without being to precise let's just say our website contained a service to send a formally correct email or fax to your provider to cancel your mobile contract, nice thing really. You put in all your personal information and then you could hit a button to send your cancelation and get redirected to a page that also allows you to download a pdf with the sent cancelation (including all your personal data). That page was secured by a cancelation id and a (totally save) 16 characters long security token.
Now, a few months ago I tested a small change on the cancelation service and noticed a rather interesting detail : The same email always results in the same (totally save) security token...
So I tried again and sure, the token seemed to be generated from the email, well so much about "totally save". Of course this was a minor problem since our cancelation ids were strong uuids that would be incredibly hard to brute force, right? Well of course they weren't, they counted up. So at that point you could take an email, send a cancelation, get the token and just count down from your id until you hit a 200 and download the pdf with all that juicy user data, nice.
Well, of course now I raised a critical ticket and the issue was fixed as soon as possible, right?
Of course not. Well I raised the ticket, I made it critical and personally went to the ceo to make sure its prioritized. The next day I get an email from jira that the issue now was minor because "its in the code since 2017 and wasn't exploited".
Well, long story short, I argued a lot and in the end it came to the point where I, as QA, wrote a fix to create a proper token because management just "didn't see the need" to secure such a "hard to find problem". Well, before that I sent them a zip file containing 84 pdfs I scrapped in a night and the message that they can be happy I signed an NDA.2 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
Got fucking graduated, a whole day wasted, fucking ass hole literally trapped us cannot even got to release some water.
To get a fucking degree you have to bear with fucking teacher who don't shit about privacy, security.
And answering fucking theroy questions which has fucking string Match with the fucking textbook paragraph.
Do a fucking report which will be fucking 100 pages and take fucking 2 copy (10 rough copies)
The register to fucking leaky placement centre. Who leak you data to all hiring companies as well as your co-students.
Then fucking attend the fucking ass hole ceremony where some old guy lectures for fucking long time about some civil infrastructure , road and other stuff.
And I have not mentioned other fucking ass hole slutty stuff.i don't know fucking until what time I can hold on.
This Fucked the fuck out of me10 -
Comment a 1 if you’re a web dev.
Comment a 2 if you’re a game dev.
Comment a 3 if you’re a data scientist.
Comment a 4 if you’re in cyber security.
Comment a 5 if you’re in IT.
Comment a 6 if you don’t fit any of the above categories and you code only in PHP and refuse to learn any other language because you think PHP is the future.50 -
My university has a internal developed system, where everything is managed from e-mails, exams to personal data.
What I'd like most about it, they talk all day about Internet Security and store our passwords in plain text and if you press the "I've forgott my Password button", they even send your password unencrypted, plaintext via e-mail. (Hello Wiresharks)
I don't know how to feel about this, it just hurts :(1 -
My boss did not care about making things secure in our early development stage, even though I told him several times.
After 1 day our elastic search cluster was filled with random crappy data.
Fix: Apply security schemes provided by AWS1 -
Ok, here goes...
I was once asked to evaluate upgrade options for an online shop platform.
The thing was built on Zend 1, but that's not the problem.
The geniuses that worked on it before didn't have any clue about best practices, framework convention, modular thinking, testing, security issues...nothing!
There were some instances when querying was done using a rudimentary excuse for a model layer. Other times, they would just use raw queries and just ignore the previous method. Sometimes the database calls were made in strange function calls inside randomly loaded PHP files from different folders from all over the place. Sometimes they used JOINs to get the data from multiple tables, sometimes they would do a bunch of single table queries and just loop every data set to format it using multiple for loops.
And, best of all, there were some parts of the app that would just ignore any ideea of frameworks, conventions and all that and would be just a huge PHP file full of spagetti code just spalshed around, sometimes with no apparent logic to it. Queries, processing, HTML...everything crammed in one file...
The most amazing thing was that this code base somehow managed to function in production for more than 5 years and people actualy used it...
Imagine the reaction I got from the client the moment I said we should burn it to the ground and rebuild the whole thing from scratch...
Good thing my boss trusted me and backed me up (he is a great guy by the way) and we never had to go along with that Frankenstein monster... -
To provide excellent customer service and provide extra services, we collect your personal information.
Bullshit. You're not using my personal information for customer service, otherwise your call center wouldn't suck so badly.3 -
Forgot to turn off mobile hotspot when I connected my phone with a Windows PC. Fucking windows used all my data to download 'security' updates. Bhenchod.9
-
IPAY88 is the worst payment integration. They parse html data and encoded it into xml for return the data, it is not even singlet or server to server communication , tey called it the ADVANCED BACKEND SYSTEM (My arse!) For security, they ENCODE THE STRING into BASE64 and called it ENCRYPTION ! WHAT THE FUCK?
Encoding is not encryption! I qas expecting they used diffie hellman or AES or RSA etc. THEY TOLD BE ENCODING IS ENCRYPTION? WHAT THE FUCK?1 -
About to start my real first Java project to learn the language in-depth: a virtual ATM featuring a GUI and a networking system for the transmission of banking data to and from a server. Since I particularly care about security this will surely help me get a better understanding of everything involved. Wish me luck.16
-
I am doing some freelance work for a client who is thankfully mindful about security. I found out that they are so strict with their access because they had a huge data breach last year.
Today I was given access to their repo for connecting to their AS400. In the docker file the username and password were included and were the same for dev and prod. They also are performing no sql injection prevention. They are just joining strings together.1 -
I really love Mr Robot.
The show though... not the guy...
But there's one thing that bugs me since the beginning:
For security reasons Elliot destroys all his drives and puts his RAM into the microwave which of course is effective but why would you even consider frying volatile memory?
Sure... the data can remain for some time but not that long that he would risk anything...
Any ideas?
Oh and btw... SEASON 3 IS NOT THE END??? LIKE WHAAAAAT?4 -
One of our customers wants our mobile app to log out the user after 15 minutes of inactivity because of SeCuRiTy…
Why? The phones protect the apps with their hardware encryption from any malicious access.
And we are not dealing with super sensitive data here like some banking app or so.
Why do some people want to have bad UX for no reason?12 -
Update on the bank I’m working for: their security is shit and the way they manage customer data and credentials is sickening. On top of it all, there’s about 10 windows XP computers still online not to mention the ATM is running Windows XP. What the flying fuck.1
-
Course title: Advanced Database Management
Course Objectives:
-Create a database with SQL.
-Describe data normalization of database information.
-Describe distributed database management system.
-Design databases based on Entity Relationship modeling.
-Discuss connecting to databases with server-side scripts.
-Discuss database administration and security.
-Discuss database systems
Like. Come. On.7 -
I had a wonderful run-in with corporate security at a credit card processing company last year (I won't name them this time).
I was asked design an application that allowed users in a secure room to receive instructions for putting gift cards into envelopes, print labels and send the envelopes to the post. There were all sorts of rules about what combinations of cards could go in which envelopes etc etc, but that wasn't the hard part.
These folks had a dedicated label printer for printing the address labels, in their secure room.
The address data was in a database in the server room.
On separate networks.
And there was absolutely no way that the corporate security folks would let an application that had access to a printer that was on a different network also have access to the address data.
So I took a look at the legacy application to see what they did, to hopefully use as a precedent.
They had an unsecured web page (no, not an API, a web page) that listed the addresses to be printed. And a Windows application running on the users' PC that was quietly scraping that page to print the labels.
Luckily, it ceased to be an issue for me, as the whole IT department suddenly got outsourced to India, so it became some Indian's problem to solve.2 -
So apparently some major vpn connection providers got compromised some time ago.
https://twitter.com/hexdefined/...
https://twitter.com/cryptostorm_is/...
adding the fact that major enterprise vpn network providers had security flaws earlier this year
https://sdxcentral.com/articles/...
Sums up what was the major topic in security this year.
At the end I see something like cloud act that allows wiretapping anyone.
https://justice.gov/opa/pr/...
And when we multiply this by number of companies that have services in cloud that sums up privacy these days.
Non existent.6 -
Testers in my team have been told like 1000 times to follow the style guides that we all follow. That's not that big a deal. The big deal is that they were put on this project without having any mathematics background when the project is all about geometric stuff. So after me as a developer having to put so many hours to explain to them why the tests are not covering the requirements or why the tests are red because they are initializing the data completely wrong, I ask them pretty please to do the checks for the coding style and I have already been 4 hours reviewing code because not only I have to go through the maths and really obscure testing code to ensure that the tests are correct, but every line I have to write at least 4 or 5 style corrections. And some are not even about the code being clean, but about using wrong namespaces or not sticking to the internal data types. For fuck shake, this is embedded software and has to obey to certain security standards...3
-
PM asked me to develop an application to fetch data from the customer's DB, which would require an access security token provided by the customer. To get the token, I would have to travel to Germany (I live in Portugal) to get it personally (it's not possible to have someone else pick it up for me).
It turns out the security token is a completely closed environment, with its own OS, without the possibility of installing any application or communicating with the exterior. The laptop itself would boot from the token's OS.
It was concluded I would have to hack the security token, which is completely non compliant. So the PM decided not to go forward with it.
But now, I have to go Germany anyway to pick up the security tokens because they forgot to order them for these other guys who would be using them to access the customer's DB manually and they don't want to delay the project anymore.
Oh, and the security tokens cost the project 500€/month each...3 -
fuck..fuck..FUCK..FUCK YOU MANTIS!!!
fuck you and your fucking invalid security token... fucking cunt...
yeah i love extracting my notes from POST data via the browser dev console cause you fucking delete it when hitting the back button...
THANKS FOR NOTHING -
I don't know why is that everytime you guys find a security bug or a data leak or that someone is saving plain passwords on their database, you try to cover and censor the company name. Listen people, fuck the company and their name and their brand if someone's data might be in danger. Everybody should be aware of what is happening with their personal information.
Also, maybe would be great if devRant would let users to post anonymous rants for this kind of issues or a special thread with latest news about our online security.3 -
Have you ever had the moment when you were left speechless because a software system was so fucked up and you just sat there and didn't know how to grasp it? I've seen some pretty bad code, products and services but yesterday I got to the next level.
A little background: I live in Europe and we have GDPR so we are required by law to protect our customer data. We need quite a bit to fulfill our services and it is stored in our ERP system which is developed by another company.
My job is to develop services that interact with that system and they provided me with a REST service to achieve that. Since I know how sensitive that data is, I took extra good care of how I processed the data, stored secrets and so on.
Yesterday, when I was developing a new feature, my first WTF moment happened: I was able to see the passwords of every user - in CLEAR TEXT!!
I sat there and was just shocked: We trust you with our most valuable data and you can't even hash our fuckn passwords?
But that was not the end: After I grabbed a coffee and digested what I just saw, I continued to think: OK, I'm logged in with my user and I have pretty massive rights to the system. Since I now knew all the passwords of my colleagues, I could just try it with a different account and see if that works out too.
I found a nice user "test" (guess the password), logged on to the service and tried the same query again. With the same result. You can guess how mad I was - I immediately changed my password to a pretty hard.
And it didn't even end there because obviously user "test" also had full write access to the system and was probably very happy when I made him admin before deleting him on his own credentials.
It never happened to me - I just sat there and didn't know if I should laugh or cry, I even had a small existential crisis because why the fuck do I put any effort in it when the people who are supposed to put a lot of effort in it don't give a shit?
It took them half a day to fix the security issues but now I have 0 trust in the company and the people working for it.
So why - if it only takes you half a day to do the job you are supposed (and requires by law) to do - would you just not do it? Because I was already mildly annoyed of your 2+ months delay at the initial setup (and had to break my own promises to my boss)?
By sharing this story, I want to encourage everyone to have a little thought on the consequences that bad software can have on your company, your customers and your fellow devs who have to use your services.
I'm not a security guy but I guess every developer should have a basic understanding of security, especially in a GDPR area.2 -
Sometimes human stupidity still surprises me.
Today I was able to stop the release of a ticket at the last moment that intended to put urls WITH A SECURITY TOKEN TO ACCESS USER DATA through a link shortener.
Some PM assumed that it would be a reasonable course of action to map an url secured via jwt through to a 4 character, countable, base64 string so that we don't have to send multiple sms if they contain this url. I can accept that the implications might slip through one person but the fact that this was put into a ticket by a pm, prioritized by PO, estimated by an entire team, implemented by a professional developer, reviewed by a senior and then scheduled for release without anyone asking themselves if there might be a reason for a security token to be long, that one shocks me.8 -
So it's required by law to chip and register your dog. I just got a puppy so I had to change the owner of the dog from the kennel to me. And the only thing I needed was my chipvalue and the registration number.
So all I have to do is scan the dog and try the registration numbers and then I can change the owner. Like wtf. And it does not even send a confirmation email. I checked by changing owner and email again.
My registration number is only in the 600K so other registered pets should be easy enough to bruteforce.
Or am I missing something?7 -
Remember kids when setting up data security, don't be an Equifax.
Since they can't honestly answer yes to the data at rest question, it probably means the resting data was not encrypted.
How did these guys get put in charge? This is a basic data security standard.
https://m.hardocp.com/news/2017/...1 -
Oh my fucking god. Austria wants to sell the data of it's citizens to schools, universities museums, and: Companies with enough money. What the fuck?
The data contains shit from the central register of residents, information about name, date of birth, sex/gender, nationality, recidence, health data (!), education, social security/insurance, tax data, E-Card/ELGA Data (system where your doctor visits, prescribed medicines/drugs, all these things, are saved), and other shit.
Welcome to 2018, where you can try as hard as you want to keep your privacy, and then your government sells all the shit you are not able to remove. Fucking bullshit.9 -
Let's talk about the cargo cult of N-factor authentication. It's not some magic security dust you can just sprinkle onto your app "for security purposes".
I once had a client who had a client who I did server maintenance for. Every month I was scheduled to go to the site, stick my fingerprint in their scanner, which would then display my recorded face prominently on their screens, have my name and purpose verified by the contact person, and only then would the guards let me in.
HAHA no of course not. On top of all of that, they ask for a company ID and will not let me in without one.
Because after all, I can easily forge my face, fingerprints, on-site client contact, appointment, and approval. But printing out and laminating a company ID is impossible.
---
With apologies to my "first best friend" in High School, I've forgotten which of the dozens of canonicalisations of which of your nicknames I've put in as my answer to your security question. I've also forgotten if I actually listed you as my first best friend, or my dog - which would actually be more accurate - and actually which dog, as there are times in my High School life that there were more tails than humans in the house.
I have not forgotten these out of spite, but simply because I have also forgotten which of the dozen services of this prominent bullshit computer company I actually signed up for way back in college, which itself has been more than a decade ago. That I actually apparently already signed up for the service before actually eludes me, because in fact, I have no love for their myriad products.
What I have NOT forgotten is my "end of the universe"-grade password, or email, or full legal name and the ability to demonstrate a clear line of continuity of my identity from wherever that was to now.
Because of previous security screwups in the past, this prominent bullshit company has forced its users to activate its second, third, and Nth factors. A possibly decade-old security question; a phone number long lost; whatever - before you can use your account.
Note: not "view sensitive data" about the account, like full name, billing address, and contact info. Not "change settings" of the account, such as changing account info, email, etc. Apparently all those are the lowest tier of security meant to be protected by mere "end of the universe"-grade passwords and a second factor such as email, which itself is likely to be sold by a company that also cargo cults N-factor auth. For REAL hard info, let's ask the guy who we just showed the address to "What street he lived in" and a couple others.
Explaining this to the company's support hotline is an exercise in...
"It's for your security."
"It's not. You're just locking me out of my account. I can show you a government ID corroborating all the other account info."
"But we can't, for security."
"It's not security. Get me your boss."
...
"It's for security."8 -
Today we start working on a app that learns biometric data from the user for extra security, so if some one else uses my account... The system would know and shuts the bad user out. Although we use an api for the biometric data collection, it's still epic! 😀😀😀
Only bad thing is that the deadline is next week3 -
Computers are not tools, they're weapons, no ones data is safe, and most people are just oblivious to what's really going on in the Network Security and Data Security sector.4
-
whenever i tell my dad about a technology that is going way beyond our imagination and tell him about the consequences of it and how we should worry about that
then he watches some random tv show about internet security/cyber security and various algorithms (very abstract) which are currently changing the world and how we should care about our data and what the consequences of X technology is...
he be like: "oh is that true? that's interesting, how does that work?"
i'm like😑 dad, i already told you about that😩
ever had similar experience?1 -
Because I am very interested in cyber security and plan on doing my masters in it security I always try to stay up to date with the latest news and tools. However sometimes its a good idea to ask similar-minded people on how they approach these things, - and maybe I can learn a couple of things. So maybe people like @linuxxx have some advice :D Let's discuss :D
1) What's your goto OS? I currently use Antergos x64 and a Win10 Dualboot. Most likely you guys will recommend Linux, but if so what ditro, and why? I know that people like Snowden use QubesOS. What makes it much better then other distro? Would you use it for everyday tasks or is it overkill? What about Kali or Parrot-OS?
2) Your go-to privacy/security tools? Personally, I am always conencted to a VPN with openvpn (Killswitch on). In my browser (Firefox) I use UBlock and HttpsEverywhere. Used NoScript for a while but had more trouble then actual use with it (blocked too much). Search engine is DDG. All of my data is stored in VeraCrypt containers, so even if the system is compromised nobody is able to access any private data. Passwords are stored in KeePass. What other tools would you recommend?
3) What websites are you browsing for competent news reports in the it security scene? What websites can you recommend to find academic writeups/white papers about certain topics?
4) Google. Yeah a hate-love relationship, but its hard to completely avoid it. I do actually have a Google-Home device (dont kill me), which I use for calender entries, timers, alarms, reminders, and weather updates as well as IOT stuff such as turning my LED lights on and off. I wouldn"t mind switching to an open source solution which is equally good, however so far I couldnt find anything that would a good option. Suggestions?
5) What actions do you take to secure your phone and prevent things such as being tracked/spyed? Personally so far I havent really done much except for installing AdAway on my rooted device aswell as the same Firefox plugins I use on my desktop PC.
6) Are there ways to create mirror images of my entire linux system? Every now and then stuff breaks, that is tedious to fix and reinstalling the system takes a couple of hours. I remember from Windows that software such as Acronis or Paragon can create a full image of your system that you can backup and restore at any point to get a stable, healthy system back (without the need to install everything by hand).
7) Would you encrypt the boot partition of your system, even tho all data is already stored in encrypted containers?
8) Any other advice you can give :P ?12 -
So for those of you keeping track, I've become a bit of a data munger of late, something that is both interesting and somewhat frustrating.
I work with a variety of enterprise data sources. Those of you who have done enterprise work will know what I mean. Forget lovely Web APIs with proper authentication and JSON fed by well-known open source libraries. No, I've got the output from an AS/400 to deal with (For the youngsters amongst you, AS/400 is a 1980s IBM mainframe-ish operating system that oriiganlly ran on 48-bit computers). I've got EDIFACT to deal with (for the youngsters amongst you: EDIFACT is the 1980s precursor to XML. It's all cryptic codes, + delimited fields and ' delimited lines) and I've got legacy databases to massage into newer formats, all for what is laughably called my "data warehouse".
But of course, the one system that actually gives me serious problems is the most modern one. It's web-based, on internal servers. It's got all the late-naughties buzzowrds in web development, such as AJAX and JQuery. And it now has a "Web Service" interface at the request of the bosses, that I have to use.
The programmers of this system have based it on that very well-known database: Intersystems Caché. This is an Object Database, and doesn't have an SQL driver by default, so I'm basically required to use this "Web Service".
Let's put aside the poor security. I basically pass a hard-coded human readable string as password in a password field in the GET parameters. This is a step up from no security, to be fair, though not much.
It's the fact that the thing lies. All the files it spits out start with that fateful string: '<?xml version="1.0" encoding="ISO-8859-1"?>' and it lies.
It's all UTF-8, which has made some of my parsers choke, when they're expecting latin-1.
But no, the real lie is the fact that IT IS NOT WELL-FORMED XML. Let alone Valid.
THERE IS NO ROOT ELEMENT!
So now, I have to waste my time writing a proxy for this "web service" that rewrites the XML encoding string on these files, and adds a root element, just so I can spit it at an XML parser. This means added infrastructure for my data munging, and more potential bugs introduced or points of failure.
Let's just say that the developers of this system don't really cope with people wanting to integrate with them. It's amazing that they manage to integrate with third parties at all...2 -
User: If we use Oauth2, can we audit exactly where this data is going and who sends it there, and in addition cam we audit who grabs that data from the Authenticating app and make sure it doesn't violate our requirements?
Me: No
User: Why not?
Me: Because thats like asking us to audit whether or not a user accessed files and then uploaded them to their personal drive instead of corporate. We don't mandate that application owners take responsibility for their data outside of their application, why would we require that in this case???
User: Uhhhhh
FFS the lack of understanding of application accounts here boggles my mind. I understand that the security concerns are real but throwing out all permissible contexts based on a mandate that we dont even apply to extremely permissive accounts (i.e. users compared to apps) is folly1 -
For all the hate that Java gets, this *not rant* is to appreciate the Spring Boot/Cloud & Netty for without them I would not be half as productive as I am at my job.
Just to highlight a few of these life savers:
- Spring security: many features but I will just mention robust authorization out of the box
- Netflix Feign & Hystrix: easy circuit breaking & fallback pattern.
- Spring Data: consistent data access patterns & out of the box functionality regardless of the data source: eg relational & document dbs, redis etc with managed offerings integrations as well. The abstraction here is something to marvel at.
- Spring Boot Actuator: Out of the box health checks that check all integrations: Db, Redis, Mail,Disk, RabbitMQ etc which are crucial for Kubernetes readiness/liveness health checks.
- Spring Cloud Stream: Another abstraction for the messaging layer that decouples application logic from the binder ie could be kafka, rabbitmq etc
- SpringFox Swagger - Fantastic swagger documentation integration that allows always up to date API docs via annotations that can be converted to a swagger.yml if need be.
- Last but not least - Netty: Implementing secure non-blocking network applications is not trivial. This framework has made it easier for us to implement a protocol server on top of UDP using Java & all the support that comes with Spring.
For these & many more am grateful for Java & the big big community of devs that love & support it. -
Security is a joke. And people don't seem to get it. Especially Data mungers.
I've spent about half an hour trying to work out how to securely connect to power BI using PowerShell in a renewable manner for unattended access later on.
Every single example I've found seems to involve you storing $user and $password variables inside your script. If I'm lucky, they're going to pass them through ConvertTo-SecureString. And nobody talks about securely storing AD auth tokens, or using the Windows Credential Manager.
I know it's possible, but it's going to take me ages to work out how from all sorts of disparate sources...16 -
I absolutely hate software to the point where I started converting from sysadmin to becoming more like a dev. That way I could just write my own implementations at will. Easier said than done, that's for sure. And it goes both ways.
I think that in order to be a good dev, you need these skills the most:
- Problem solving skills
- Creativity, you're making stuff
- Logical reasoning
- Connecting the dots
- Reading complex documentation
- Breaking down said documentation
- A strong desire to create order and patterns
- ...
If you don't have the above, you may still be able to become a dev.. but it would be harder for sure, and in some cases acceptance will be lower (seriously, learn to Google!)
One thing I don't think you need in development is mathematics. Sure there's a correlation between it and logic reasoning, but you're not solving big mathematical monsters here. At most you'd probably be dealing with arrays and loops (well.. program logic).
Also, written and spoken English! The language of the internet must be known. If it's not your first language, learn it. All the good (and crucial) documentation out there is in English after all.
One final thing would be security in my opinion, since you're releasing your application to the internet and may even run certain services, and deal with a lot of user data. Making those things secure takes some effort and knowledge on security, but it's so worth it. At the most basic level, it requires a certain mindset: "how would I break this thing I just made?"4 -
tl;dr. web hosting && a panic attack && security threat
i wasn't sure whether my brother's domain was hosted or not (because it wasnt showing a website and he didnt know any better).
so i decided to host a react-app for it on netlify and pointed the domain's nameservers towards it (a separate security threat at bottom).
all went well and now when you punch in the domain it ..all-behold.. shows a website.
NOW, i remember my brother was using the domain's email which probably means it was hosted, right?. so im panicking because im not sure whether i just deleted all his emails or not because it's 1:15 am and he's asleep.
there is a rant in there somewhere but im in too much of a shock as to how much data i might have just accidentally deleted
.
.
another tl;dr: my domain registrar let me change someone else's settings..
the reason i didnt know his domain settings is that he didnt know his password.
i had bought a couple of domains and was gonna host them on netlify. while i was doing this a bright idea hit me.. "you should finally build a website for your brother for the domain he bought 7 years ago"..
this is where the fun begins.
i sent an email to my registrar to point all nameservers of all domains to my nameservers and just to try out i included my brother's domain into it (i dont own this domain it's not registered by my email), and the next day i get an email telling me they've successfully made all changes.
.
Now tomorrow is monday and i'm going to their office to tell them i found a security flaw and see how long i can stall before actually telling them what it was and how their live's could've been made hell.3 -
"Our Data Service comes PRE-P0WN'D"
Those SHIT-FOR-BRAINS data service providers GLOAT that their data can be natively integrated into most BI platforms, no code required.
How? Because they will EXPOSE THE ENTIRE FUCKING THING ON THE INTERNET.
LITERALLY.
UNAUTHENTICATED URL WITH THE ENTIRE DATASET.
STATIC. WON'T EVER FUCKING CHANGE.
NO VPN REQUIRED. NO AUTHENTICATION HEADERS. NO IN-TRANSIT ENCRYPTION.
"It is safe! No one will know the secret token that is a parameter in the url"
BLOODY BYTE BUTTS, BATMAN! IT IS A FUCKING UNAUTHENTICATED URL THAT DOES NOT REQUIRES RENEWAL NOR A VPN, IT WILL LEAK EVENTUALLY!
That is the single fucking worst SELF-P0WN I have ever seen.
Now I know why there are fucking toddlers "hacking" large scale databases all over the globe.
Because there are plenty of data service providers that are FUCKING N00BS.4 -
So, the Network I was on was blocking every single VPN site that I could find so I could not download proton onto my computer without using some sketchy third-party site, so, being left with no options and a tiny phone data plan, I used the one possible remaining option, an online Android emulator. In the emulator running at like 180p I once again navigated to proton VPN, downloaded the windows version, and uploaded it to Firefox send. Opened send on my computer, downloaded the file, installed it, and realized my error, I need access to the VPN site to log in.
In a panic, I went to my phone ready to use what little was left of data plan for security, and was met with no signal indoors. Fuck. New plan. I found a Xfinity wifi thing, and although connecting to a public network freaked me out, I desided to go for it because fuck it. I selected the one hour free pass, logged in, and it said I already used it, what? When?, So I created a new account, logged in, logged into proton, and disconnected, and finally, I was safe.
Fuck the wifi provider for discouraging a right to a private internet and fuck the owner for allowing it. I realize how bad it was to enter my proton account over Xfinity wifi, but I was desperate and desperate times call for desperate means. I have now changed my password and have 2fa enabled.1 -
Given the recent election, I'm taking measures to ensure the privacy and security of my data. Call me paranoid, but I think the NSA is going to be getting some extra funding soon. I'm already working on encrypting a ton of my data. Any other tips some of you guys could give me?8
-
Just as an extension of last rant to explain how much fun it is to keep up with Apple's security through obscurity bullshit.
AFAIK this full disk access (FDA) feature was touted to protect a user's data on macOS. Programs that want to access those files need to request the user's permissions to do so. Now to the fun part: Apple is not providing any API. A staff member suggested, that you should only try to access the files your app needs and if you can't as for the user's allowance. One should not use some fixed files and try to access them, because their locations might change, as well as their (UNIX file) access rights (ACL), or if they fall under FDA. Not to speak about the other security features that might hinder you accessing files (you might be sandboxed, or the files might be subject to SIP/rootless).
Honestly, you should be starting to take drugs, if you want to stay sane. I mean UNIX ACL are weird enough: e.g. you can make a directory only readable for root such that a user cannot list the files inside, but you can place files inside that the user can read (if she knows about their existence). On macOS you'll never know. You may have all the rights to access a file,.. but Apple will only give you the finger.
As they always do to us developers. 2
2 -
1. As i was freelancing on upwork some company contacted me and said my CV looks interesting and they gave me a link from their site to download a .rar file with details about their company and dev positions
2. Ok i open the link and the whole site is just blank page with 1 single button: "Download 5.8 mb"
3. Thought to myself: who the fuck has this low quality site of a company, shitty as fuck and as if its built in the 90s. But ok
4. About 2 days later they got banned on upwork and we cant chat anymore. I send this .rar file to virus total and 7 anti virus softwares scanned a trojan + 14 security vendors flagged the rar as malicious malware
Are you FUCKING kidding me? This is the type of bullshit I'm expecting to see in web3 world. Who the FUCK comes on upwork to infect ENGINEERS?? Are you FUCKING KIDDING ME? I'll publish their data right now:
Link:
https://hsatrack.com/files/...
Password: 49-49Zb2
Their site:
https://hsatrack.com/
Honestly if i opened this fucking home page site first i would have smelled a virus miles away. But i just didnt expect a fucking virus AT ALL on UPWORK. Never happened to me before. This is the type of criminal fraud malware shit i expect AND SEE DAILY on WEB3 -- WHO TF DOES IT IN WEB2 IN 2023?? I'LL FUCK THIS CEO'S LIFE UPSIDE DOWN 180 RIGHT NOW2 -
Ugh, I hate having to port data from windows to Mac. I myself use Linux and windows. My mom got her first Mac for her birthday, but she needed her 200gb of pictures on I cloud. So I thought it would be like Dropbox, put them in a folder or start an upload and then it processes and is on the cloud. NO. It’s a hellscape as Apples windows programs are awful and I’m ashamed they exist. There is no indication of when they have successfully uploaded, you just have to figure it out. It also doesn’t help when macOS Is oversimplified. Ugh. I ended up taking my terabyte external and having to wait 3 hours for files to transfer and put those on the MacBook. I hate I cloud more than comic sans. I know Dropbox isn’t great or even good for security reasons, but it’s a hell of a lot better than I cloud BULLSHIT.
-
Most unprofessional experience at work?
Check out my previous rants. With so many, it would be difficult to pick just one.
Not sure if I've told this one before. 'Caleb' was part of a team responsible for migrating financial data from a legacy (DOS-based) system to our new system.
Because of our elevated security (and the data being plain text) Caleb had access to the entire company's payroll (including VP salary, bonuses, etc).
Solidifying my belief that that salaries should be private between the employee and the employer, Caleb discovered he was making considerably less than his peers (even a few devs that he had seniority over), and the green monster 'Jealosly' took over his professionalism. Caleb decided to tell everyone making the same and less than him, the salaries of the other (higher paid) devs, managers and VPs.
Nobody understood at the time, but these folks started to behave erratically , like showing up late, making comments like "Why should I document that? Make 'money bags' over there do it", etc and so on.
Soon at review time, Caleb decided to use his newly discovered ammunition to 'barter' for a higher salary by telling the manager if he didn't make $$$, he would send an email to the entire company containing everyone's salary.
The manager fired Caleb on the spot and escorted him out the building (Caleb never had chance to follow thru with that threat)
When word got out about Caleb's firing (and everybody knew why), those other employees started showing up on time and stopped complaining about doing their job.5 -
Part 1: https://devrant.com/rants/4298172/...
So we get this guy in a meeting and he is now saying "we can't have application accounts because that violates our standard of knowing who accessed what data - the application account anonamizes the user behind the app account data transaction and authorization"
And so i remind him that since it's an application account, no one is going to see the data in transit (for reference this account is for CI/CD), so the identity that accessed that data really is only the app account and no one else.
This man has the audacity to come back with "oh well then thats fine, i cant think of a bunch of other app account ideas where the data is then shown to non-approved individuals"
We have controls in place to make sure this doesnt happen, and his grand example that he illustrates is "Well what if someone created an app account to pull github repo data and then display that in a web interface to unauthorized users"
...
M******* why wouldnt you JUST USE GITHUB??? WHO WOULD BUILD A SEPARATE APPLICATION FOR THAT???
I swear I have sunk more time into this than it would have costed me to mop up from a whole data breach. I know there are situations where you could potentially expose data to the wrong users, but that's the same issue with User Accounts (see my first rant with the GDrive example). In addition, the proposed alternative is "just dont use CI/CD"!!!
I'm getting pretty pissed off at this whole "My compliance is worth more than real security" bullshit. -
I am working on a multi user, high security, private data analytics Web app.
I keep a Ganondorf ammibo on my desk to remind me that; one wrong link could ruin everything. -
I really don't understand this particular Government Department's IT Unit. They have a system and network to maintain except:
- They don't have a DBA
- They don't have a dedicated Network Engineer or Security Staff
- Zero documentation on all of the systems that they are taking care of (its all in each assigned particular staff's brain they said)
- Unsure and untested way of restoring a backup into a system
- Server passwords are too simple and only one person was holding this whole time and its to an Administrator account. No individual user account.
- System was developed by an in-house developer who is now retired and left very little documentation on its usage but nothing on how its setup.
But, the system has been up and operational for the past 20 years and no major issues whatsoever with the users using it. I mean its a super simple system setup from the looks of it.
1 App Server connected to 1 DB Server, to serve 20-30 users. But it contains millions of records (2GB worth of data dump). I'm trying to swing to them to get me on a part time work to fix these gaps.
God save them for another 20 years.3 -
My org (of which i'm basically CTO) has this administrative tool that a team uses to combat spam and scams, which is quite the problem for us.. the tool was written like 9 years ago, by my predecessor, very quick & dirty and unaesthetic and without input from those who would use it as far as interface or UX... it got modded a little a few years later by a kind of amateur coder who was at the time on the spam control team, and now there's this new maybe slightly less amateur coder guy on the team who has written this amateur tool that scrapes data off our site and massages it and stores it on his own server and then provides a better interface, or so they say.... this is all because for a couple of years people didnt want to "bother me" with a request to improve our internal tool, they thought I was "too busy" doing other things... so instead this outsider has built this stupid thing that lives on his own personal server and so now we have these problems to do with performance, security, privacy for user info, etc etc... someone please shoot me....1
-
I'll try to pay back some smaller credit by one large credit...
Hence I need to contact the banks and get one (!) fucking frigging stupid piece of paper which lists the account number and the amount of money I need to pay back.
Sounds simple ...
Well.
One bank just answered my email request by sending me that piece of paper. Except they didn't have any validation of my identity.
Yes. They answered the request of 'I want to pay back the credit in full, can u send me the necessary documents?' (more formal of course) with confidential data without any more credibility than my email address.
YAY.
Another bank requests a telephone call for identity validation and sending back a signed form via postal service...
Another bank just needs a PDF sent via mail with an electric signature (yeah. They were aware of what that means - I was shocked and confused) or a "qualified signature matching previous documents" (translated from German).
The last one offers a WhatsApp number - send a GIF / JPG or video and we answer directly.
I need to reach a higher state than drunk.
It's not funny to know how confidential data gets mistreated by companies who should have the highest security.4 -
I code. I'm not a network or security admin. Did you even read my resume before hiring me? It says "math degree then data analysis then programming degree" Subnets, firewalls and security certs are not my areas of expertise. Given enough time, could I stumble through? Probably. But I'd probably come up with something worthy of mocking on networkadminrant.
-
I think the fact that even Apple can't unlock your phone if you forget your passcode proves that they use very naive encryption method.
Suppose my data is "Hey This is Some Data" and Passcode is 1234, I could just Jumble this data using that passcode and It will be difficult to decrypt without Passcode. And If data is huge, it will be fairly impossible to do so. But that doesn't make it a good encryption method.
Such encryption, though safe is not practical, Imagine if there was no "Forget Password" Option on any account, I usually forgot my password very often when I was a child.
Apple has been doing such things for years, Using Bad things as a selling point. Apple users are dumb anyways because they don't want to control their phone.
Reset Password is a weak point which might be exploited but in such cases, usability is more important than security. Any service which doesn't allow resetting Password is a shitty service and I would never use such a service, They are too naive.696 -
I once had a manager who demanded I physically print all of the Kanban cards and tape them to the office whiteboard. I was told to move the cards across the board after they were moved in TFS. I still had to keep up with my other duties in the QA department too!
Despite that, I still stayed on board with the company (the pay was good, and the work was simple.) As a QA teeter, I uncovered a rather nasty security vulnerability that would have put all of our customers data at reach to anybody. I advised my manager, and was told - just ignore it and ship the code please. I refused.
I was threatened with being fired, verbally assaulted, and challenged at the most trivial ways in everything I did after that.
Jokes on him now. I work from home in my dream job, doing what I love, with a manager who actually gives a rats ass about my concerns.
Moral of the story here - you don't have to agree with your subordinates , but you do need to validate their concerns.4 -
In my office I've made a habit of changing the desktop background of anyone who leaves thier workstation unlocked to My Little Pony: Friendship is Magic to encourage good data security.
It's working.6 -
Pm orders me to integrate data from several closed systems into a new CRM, problem is... corporate security won't allow me to push data between these networks as there are extremely sensitive data on these systems. So I disobey PM or corporate if I do it and ive told both the issues. 4th round with this exact issue now.4
-
My country has the best security experts. They convince people that they are not thiefs, Then when people believe them and give them their data, They change the password.1
-
For what fucking reason the ability to set the date and time programatically has been blocked on Android?!
Why you can create fucking invisible apps that work in the background, mine cryptos, steal your data but they decided that something like that is considered dangerous?
Can anyone give me a logical explanation?
P.S.
There are cases (big pharma companies) where the users don't have access to internet nor a ntp server is available on the local network, so the ability for an app to get the time of a sql server and set it in runtime is crucial, expecially when the user, for security reasons, can't have access to the device settings and change it by himself.
"System apps" can do it, but you would have to change the firmware of a device to sideload an external "System app" and in that case it would lose the warranty.
So, yeah, fucking Google assholes, there are cases where your dumb decisions make the others struggle every other day.
Give more power to third party developers, dumb motherfuckers.
It's not that difficult to ask the user, once, to give the SET_TIME permission.
It was possible in the past...
P.S.2
Windows Mobile 6.5 was a masterpiece for business.
It still could be, just mount better CPUs on PDAs and extend the support. But no, "Android is the future". What a fucking bad future. 11
11 -
Log 1:
Day 10 of crunch time. I have entered a sleepless zen state. Lord willing, I will be able to get 7 hours of sleep Saturday night. The building is terrifying at night, as there are a lot of noises. Security guards are nice, but curious to see me all alone. Must not show weakness in case they think numbers will give them an advantage over me.
Supplies are low. Only one type of energy drink left in the machine, and coffee gone for the night. My phone is out of fast data so Pandora is spotty at best. I have battery to get me through the night at least.
Tomorrow and Saturday decide the fate of the project. My team lead has not slept in at least 2 days. I feel guilty napping when I do, but she is driven like Ahab so I will let her obsession carry her.
If I am alive tomorrow I will report in.1 -
Did you ever had to integrate a fucking "API" that is done via mail bodies?
Fuck this shit! Who need responses about success or failure?! Guess this will take a long time to test this fucking piece of garbage... We don't get a test system, we need to test this with the production system of the other company. I hope their retarded application crashes when receiving malicious mails.
Not speaking about security, I bet everyone can send a mail to their stupid mail address and modify their data 🙈
And inside of this crap mail you also have to send the name, street and email of their company. Why do you fucking need this information?!1 -
Best: take a job as a data analyst. 1 year later, re-write and re-deploy the entire backend following correct security concentions and well-hashed-out data models.
Worst: attempt to backup a hard drive using dd, just to accidentally brick the laptop (because it had some security layer the school put to prevent just that)
Bestest: use knowledge acquired at my "best" story to nuke windows on bricked laptop. Then extract the leftover data using dd and a series of recovery tools. -
I work with statistics/data analysis and web development. I study these subjects for almost a decade and now I have 4 years of practical experience.
This information is on my LinkedIn profile and from time to time tech recruiters contact me wanting to have an interview. I always accept because I find it a great way to practice interviews and talking in English, as it isn't my native language.
A remark that I always make to my colleagues wanting to start doing data analysis related work is that it may seem similar to development, but it's not. When you develop, your code work or not. It may be ugly, it may be full of security problems, but you almost always have a clear indication if things are functioning. It's possible to more or less correlate experience using a programming language with knowing how to develop.
Data science is different. You have to know what you are doing because the code will run even if you are doing something totally wrong. You have to know how to interpret the results and judge if they make sense. For this the mathematics and theory behind is as important as the programming language you use.
Ok, so I go to my first interview for a data science position. Then I discover that I will be interview by... a psychologist. A particularly old one. Yeah. Great start.
She proceeds to go through the most boring checklist of questions I ever saw. The first one? "Do you know Python?". At this point I'm questioning myself why I agreed to be interviewed. A few minutes later, a super cringy one: "Can you tell me an example of your amazing analytics skills?". I then proceed to explain what I wrote in the last two paragraphs to her. At this point is clear that she has no idea of what data science is and the company probably googled what they should expect from a candidate.
20 minutes later and the interview is over. A few days later I receive an email saying that I was not selected to continue with the recruitment process because I don't have enough experience.
In summary: an old psychologist with no idea on how data science works says I don't have experience on the subject based on a checklist that they probably google. The interview lasted less than 30 minutes.
Two weeks later another company interviews me, I gave basically the same answers and they absolutely liked what they heard. Since that day I stopped trying to understand what is expected from you on interviews.2 -
Someone mentioned that client want to use wordpress instead of they current website because it is cheaper! Ok lets see how cheap it is.. each time wp release update after updating you need go through all website and check if nothing is broken.. plugins will need update as well because usually they run on specific wp version. Fixing theme and plugins requires dev time.. despite all those things.. have common sense. Maybe it is good for some type of business to host few pages without any business logic or use as blog without scare to loose everything and do not store users data.. someone mentioned that it is secure to run anything because updates are the best security to avoid security breaches. So why banks are not running on WP? Why health service is not using WP?
-
I used to be a big security guy, not allowing stuff like most of the social media, not bringing my phone anywhere, carrying a RPi tablet for privacy reasons. Very Stallman stuff.
Recently I noticed that I don't care so much.. I see these things as opportunities, for instance Microsoft products could be benefitial for job opportunities, I have some workout sessions on my phone.
I could restrict myself... but is it worth it just to decline some capitalist/politician's row in a dataset for analysis?
But then again I feel as a society I think we should either do this or request this data to be distributed to us as well.
Should you be playing a game of cards, when the enemy can see your hand? What do u think?4 -
I don't care about market cap. Stick your hype-driven business practices up your ass. Infinite growth doesn't exist. I won't read your fucking books and attend your fucking bootcamps and MBAs. You don't have a business model. Selling data is not a business model. Fuck your quick-flip venture capital schemes, and especially fuck your “ethics”.
I will be the first alt-tech CEO. I only care about revenue. The real money, not capitalization bubble vaporware. You don't need a huge fleet of engineers if you're smart about your technology, know how to do architecture, and you're not a feature creep. You don't need venture capital if you don't need a huge fleet of engineers. You don't need to sell data if you don't need venture capital. See? See the pattern here?
My experience allows me to build products on entirely my own. I am fully aware of the limitations of being alone, and they only inspire lean thinking and great architectural decisions. If you know throwing capacity at a problem is not an option, you start thinking differently. And if you don't need to hire anyone, it is very easy to turn a profit and make it sustainable.
If you don't follow the path of tech vaporware, you won't have the problems of tech vaporware, namely distrust of your user base, shitty updates that break everything, and of course “oops, they raised capital, time to leave before things go south”.
A friend of mine went the path I'm talking about, developed a product over the course of four years all alone, reached $10k MRR and sold for $0.8M. But I won't sell. I only care about revenue. If I get to $10k MRR, I will most likely stop doing new features and focus on fixing all the bugs there are and improving performance. This and security patches. Maybe an occasional facelift. That's it. Some products are valued because they don't change, like Sublime Text. The utility tool you can rely on. This is my scheme, this is what I want to do in life. A best-kept secret.
Imagine 100 million users that hate my product but use it because there are no alternatives, 100 people in data enrichment department alone, a billion dollars of evaluation (without being profitable), 10 million twitter followers, and ten VC firms telling me what to do and what data to sell.
Fuck that. I'd rather have one thousand loyal customers and $10k MRR. I'm different, some call it a mental illness, but the bottom line is, my goals are beyond their understanding. They call me crazy. I won't say it was never about the money, of course it was, but inflating your evaluation is not “money”. But the only thing they have is their terrible hustle culture lives and some VC street wisdom, meanwhile I HAVE products, it is on record on my PH. I have POTDs, I have a fucking Golden Kitty nomination on health and fitness for a product I made in one day. Fuck you.7 -
I have to use OneDrive to store my data on the clod for security policy (sic!) and I use odt documents.
Word online open odt documents quite good, but sometimes an Investigator appear in table cell data: why the hell? 4
4 -
Google apparently blocked users of small browsers like Konqueror, Qutebrowser or Falkon from loggining into their account, because of "security" concerns. Well played, Google! I hope you will be happy if a few users will switch to your data crawling machine.9
-
School decided to shut down their WiFi for "security" reasons (Everyone used a VPN and they were dumb fucks at networking, blocking sites like Google for having an invalid SSL certificate).
Now I'm forced to use my mobile data to keep using my Arch Linux laptop D:3 -
Just found the most embarrassing security hole. Basically a skelleton key to millions of user data. Names, email addresses, zip codes, orders. If the email indicates a birthdate, even more shit if you chain another vector. Basically an order id / hash pair that should allow users to enter data AND SHOULD ONLY AUTHORIZE THEM TO THE SITE FOR ENTRING DATA. Well, what happend was that a non mathing hash/id pair will not provide an aith token bit it will create a session linked to that order.
Long story short, call url 1 enter the foreign ID, get an error, access order overview site, profit. Obviously a big fucking problem and I still had to run directly to our CEO to get it prioritized because product management thought a style update would be more important.
Oh, and of course the IDs are counted upwards. Making them random would be too unfair towards the poor black hats out there.1 -
Hello everyone !
I am a self taught programmer. Currently in last semester in electronics engineering. I want to become a software developer but can't decide the right career path for me to take. I like back end, Android, Data structures and algorithm, Parallel programming, Machine learning and computer vision, and even security. I am afraid I will remain the jack off all trades and won't be the master of any. This way I won't be doing any good in my career. Any advice as what to do ?7 -
Mini witch hunt going on with broken builds last couple of weeks. Change satellite assembly/project A, breaks random unit test that hasn’t been changed for months and the TFS nazi sends out emails demanding the “broken” projects be fixed. Doesn’t matter the unit/integration tests are likely out dated and team responsible for the tests needs to fix it.
Yesterday I deleted some logging code out of a security assembly, broke an integration test that hasn’t needed to be ran since January (test database didn’t exist anymore).
I would have had to re-create the database, re-import the test data (not trivial), re-deploy a service using the test database…blah. All because I removed some logging code.
I deleted the gated check-in TFS build definition. Code check in … no sirens …whew! I win! -
So I went for a "special" interview to a company whose slogan is "experience certainty" (fresher, was hoping to get a role in cyber security/Linux sysadmin). Got shown what the "real" hiring process of an indian consultancy company is...
We were called because we cleared a rank of the coding competition which the company holds on a yearly basis, so its understood that we know how to code.
3 rounds; technical, managerial and HR...
Technical is where I knew that I was signing up for complete bullshit. The interviewer asks me to write and algo to generate a "number pyramid". Finished it in 7 minutes, 6-ish lines of (pseudo) code (which resembled python). As I explained the logic to the guy, he kept giving me this bewildered look, so I asked him what happened. He asks me about the simplest part of the logic, and proceeds to ask even dumber questions...
Ultimately I managed to get through his thick skull and answer some other nontechnical questions. He then asks if I have anything to ask him...
I ask him about what he does.
Him - " I am currently working on a project wherein the client is a big American bank as the technical lead "
Me (interest is cybersec) - "oh, then you must be knowing about the data protection and other security mechanisms (encryption, SSL, etc.)"
Him (bewildered look on face) - "no, I mostly handle the connectivity between the portal and data and the interface."
Me (disappointed) - "so, mostly DB, stuff?"
Him (smug and proud) - "yeup"
Gave him a link to my Github repo. Left the cabin. Proceeded to managerial interview (the stereotypical PM asshats)
Never did I think I'd be happy to not get a job offer...1 -
Come to a weekly deep learning meet up this morning 8.30AM. The event start at 10 AM. While waiting I read news and play some game. As time near 10 o'clock I had strange feeling: The guest room so quiet, just me and 2 security guy.
Okay I think comittee that run this event a bit late because of traffc jam and I wait more. In the end the committee didn’t even show until 10.30AM. Later I found on another data science group today's event is postponed and I go home.
WHY DIDNT YOU GUYS MAKE ANNOUNCEMENT ON SLACK? YOU WASTE MY TIME WAITING 2 HOURS2 -
I just got a project that is already developed by a team. It is already in the production and guess what!! They are storing customer’s credit card details in the database 🥸🥸12
-
Wouldn't call it a feature. More like worst practice. Data manager (and my boss at the time) kept using our website as a way to host large files 3rd party vendors/partners could download instead of using one of the many secure transfer methods out there to send them data. This was sometimes extremely sensitive data. No authentication or security that I could find. I went ballistic on him after seeing that.
-
I don't know what to choose...
A no-brainer job in data input with security, stability and a chance of promotion or transfer to another area IT related far away in the future...
Or
An intership of one year, in systems analysis, with a 30% better salary but no guarantees after that...4 -
Was working on a high priority security feature. We had an unreasonable timeline to get all of the work done. If we didn’t get the changes onto production before our deadline we faced the possibility of our entire suit being taken offline. Other parts of the company had already been shut down until the remediations could be made -so we knew the company execs weren’t bluffing.
I was the sole developer on the project. I designed it, implemented it, and organized the efforts to get it through the rest of the dev cycle. After about 3 month of work it was all up and bug free (after a few bugs had been found and squashed). I was exhausted, and ended up taking about a week and a half off to recharge.
The project consisted of restructuring our customized frontend control binding (asp.net -custom content controls), integrations with several services to replace portions of our data consumption and storage logic, and an enormous lift and shift that touched over 6k files.
When you touch this much code in such a short period of time it’s difficult to code review, to not introduce bugs, and _to not stop thinking about what potential problems your changes may be causing in the background_.3 -
So I get to work on building a client at work for industrial automation. I am building a mini hmi to show customers how our server works. The code uses opcua. The reason I am making a client is because all the opcua hmis on the market are really expensive. There is nothing less than $600. There are hmis for free out there, but none of them say they support opcua. opcua has become a major protocol in the industrial automation industry.
It took me about 2 days to gin together a client that is pretty much abstracted and will be easy to maintain. A lot of that was just learning the opcua library client code.
Now I want to create servers and clients geared toward home automation for fun and profit. I want to take sensor data from arduinos using a simple serial protocol like modbus or other protocols that are supported. Then have an opcua server that collects this data. Then finally have an opcua hmi that I develop talk to these servers. The security model is much better and would be compatible with other vendors clients/servers. I already have a game engine I want to use for the hmi portion. It has tons of widgets for displaying data, graphs, lists, text, etc. It does both 2d and 3d.
This sounds like a project that could really fun, meshes with my work learning, and provides value to people that want to automate their lives.
The other side effect is that the next time I go looking for a simple and cheap hmi that supports opcua, there will be one. -
Sometimes I really hate offshore desktop support... yes I know Visual Studio 15 was installed, and works. But now Python tools was uninstalled in a forced update that corrupted my VS and now I can't install PTVS(not that I need VS has the vim emulator that I can install at work, it's a whole mess of weird security policies.) fucking hate windows and visual studio. Fucking listen what Im telling you the issue is. I need your dumbass to uninstall this shit software so I can do a clean install since the shitty as software management system doesn't so shit when it say's "uninstalling".
On a side note, this fuckwit just tried to explain what the screenshot tool and how to use it... it's only pinned to my taskbar and menu for shits and gigs since I don't use it everyday to tell the stupid data entry analysts I deal with to fuck off. -
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
I have last few months left out of graduation and i don't know what should i learn. There's so much things (web dev , ai/ml, blockchain, android , cloud, ,hybrid apps, gaming, ar/vr, data analysis, security,etc) and as a cs student, i feel i should be knowing them all.
In last 6 years ,
Techs that i liked or got success in :
java, Android,python, data analysis, hybrid apps(flutter)
Techs that i didn't liked or failed in : ai/ml, cloud computing , webdev(css/js) ,hybrid apps(react/angular/ionic/...)
Techs that i didn't tried : security, cryptography, blockchain, open cv , ar/vr, gaming
I am not bound by my likeness or success.
My failures was mainly because i didn't liked those techs and continued further in them. And my success comprises of just launching a few apps, passing in some certification or grabbing an internship opp because of those skills.
But if you think a particular skill is necessary to have as a cs professional then let me know. I just want to earn a lot of money and get out of this mess asap1 -
I really wanna get a keg of rum and start sailing across the globe...
Just to spank some devs / managers arses.
The last years were... very demanding regarding security and upgrades.
It hasn't gotten better.
Microsoft leaked it's security key thx to internal debugging and the tool to secure the debugging process so secure data gets filtered was buggy...
I'd guess I already have carpal tunnel after Redmond.
But the really really sad story is: This has become the gold standard.
https://lwn.net/Articles/943969/
Chrome selling the privacy mode for Ads, long topic ongoing for years... yeah they did it.
Apple... oh boy. I could write a Silmarillion about it and would still need an additional trilogy.
Amazon realizing that a Microservice architecture needs planning, cause yeah... just potting services in a data center doesn't end well.
It goes on and on and on....
Don't even get me started on the plethora of firmware / microcode updates cause there was either yet another CPU bug or another device pooped their pants cause the firmware is a mess and needed some dubious update without any background at all...
Serious question: Am I becoming a pepperidge farm uncle threatening to shoot everyone cause I'm getting old and cranky ....
Or is really everything in IT going down the drain the last few years?
It feels like every week is just another "we fucked it up" event.3 -
Windows just activated TPM on my Windows 10 computer on first of february 2024.
The main reason I stuck with Windows 10 was the sole reason of not wanting to upload my hardware-fingerprint to MS.
Well, guess they just got it themselves and now, disabling the TPM comes with a lot of downsides, as it is now holding my certificates hostage...rant microsoft tpm tpm2.0 data theft breach trustedplatformmodule matrix security fingerprint spyware15 -
I am supposed to make a module that does sftp to third parties. Users put in their credentials and we connect and dump files on their servers. It seems like a terrible idea. We don’t administer those computers or define anything about their security. We don’t know if they are entering third party credentials or handling data according to our TOS. Can’t we just send them a presigned link by email on a schedule or something?2
-
Programming is life ❤️
Just as life, it has it's ups and downs, but it's truly satisfying to create complex systems and get them to actually work and be useful to others.
We have only just started with the digitalisation of previously manual, tedious tasks. Imagine what all this saved time and labour could bring us to achieve in areas we haven't yet had the time to explore.
I hope mankind is ready for the ongoing and upcoming challenges regarding data privacy and security.
Nah, in reality, we will be stuck with Fakebook and Tweeter selling all our dickpics to *in Trump voice* "Chiner" and censoring unpopular opinion and discourse.
These "digital parasites" can all go sit on a rusty spike. -
Why is everyone into big data? I like mostly all kind of technology (programming, Linux, security...) But I can't get myself to like big data /ML /AI. I get that it's usefulness is abundant, but how is it fascinating?6
-
I can't believe companies fucking do this! If your users PIIs gets fucking leaked or the security is breached in any god-damned way it's YOUR FUCKING JOB to let the affected users know! 57 million users got affected! What the fucking fuck? I think they should pass proper laws where companies have to tell the victims about breaches, especially when it's at a such a huge scale. I get it that it's wasn't under Uber but some third party; but even so Uber should have talked about the level of security in their SLAs and maybe performed regular audits.
This is ridiculous!
https://darkreading.com/attacks-bre...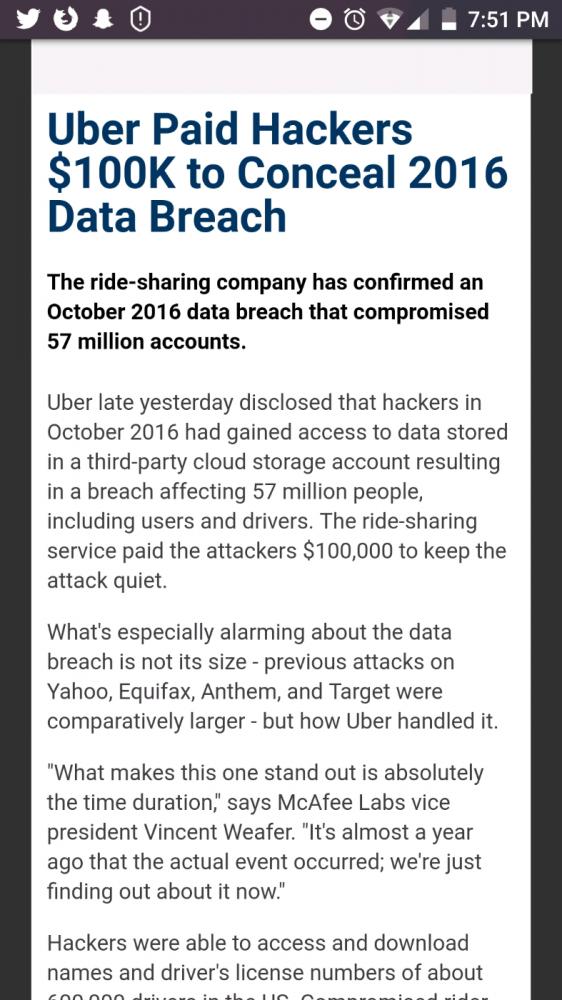 5
5 -
cbc vs gcm vs ... for my app?
currently ive get ecb 256 bit already implemented and working well, but i want an extra layer of privacy. if you had to send your ssn or credit card number over a vulnerable network, would you be more comfortable encrypting it with cbc or gcm?9 -
just receive a refurbished 4 years old laptop.... then deep clean it.... now having dilemma on picking a distro......
mainly use to run data analysis (r, Python, Java, C++, mySQL, MongoDB and some cloud servers...)
my thinking about a good distro to me, comfortable appearances, customize freedom, community support and constant security update.
any suggestion people??6 -
Web browsers removed FTP support in 2021 arguing that it is "insecure".
The purpose of FTP is not privacy to begin with but simplicity and compatibility, given that it is widely established. Any FTP user should be aware that sharing files over FTP is not private. For non-private data, that is perfectly acceptable. FTP may be used on the local network to bypass MTP (problems with MTP: https://devrant.com/rants/6198095/... ) for file transfers between a smartphone and a Windows/Linux computer.
A more reasonable approach than eliminating FTP altogether would have been showing a notice to the user that data accessed through FTP is not private. It is not intended for private file sharing in the first place.
A comparable argument was used by YouTube in mid-2021 to memory-hole all unlisted videos of 2016 and earlier except where channel owners intervened. They implied that URLs generated before January 1st, 2017, were generated using an "unsafe" algorithm ( https://blog.youtube/news-and-event... ).
Besides the fact that Google informed its users four years late about a security issue if this reason were true (hint: it almost certainly isn't), unlisted videos were never intended for "protecting privacy" anyway, given that anyone can access them without providing credentials. Any channel owner who does not want their videos to be seen sets them to "private" or deletes them. "Unlisted" was never intended for privacy.
> "In 2017, we rolled out a security update to the system that generates new YouTube Unlisted links"
It is unlikely that they rolled out a security update exactly on new years' day (2017-01-01). This means some early 2017 unlisted videos would still have the "insecure URLs". Or, likelier than not, this story was made up to sound just-so plausible enough so people believe it.50 -
So a page has been sending errors for long, but we weren't able to find any way to debug it, no error code, and I don't have the authorization to see the logs so I had to wait for a co-worker to be back from holidays.
Now that they're here, I could have a chance to find what was the error.
And be really annoyed about it.
The error was provoked because the security system found a tautology in the data I sent.
(I send datas to build the page, and one parameter is called "Page". Since it was a page of management, I've sent "Gestion", which is management in French. So I sent "Page=Gestion", the security saw "ge=Ge" in it, poof, tautology, you shall not pass.)
That is so ridiculous. -
After brute forced access to her hardware I spotted huge memory leak spreading on my key logger I just installed. She couldn’t resist right after my data reached her database so I inserted it once more to duplicate her primary key, she instantly locked my transaction and screamed so loud that all neighborhood was broadcasted with a message that exception is being raised. Right after she grabbed back of my stick just to push my exploit harder to it’s limits and make sure all stack trace is being logged into her security kernel log.
Fortunately my spyware was obfuscated and my metadata was hidden so despite she wanted to copy my code into her newly established kernel and clone it into new deadly weapon all my data went into temporary file I could flush right after my stick was unloaded.
Right after deeply scanning her localhost I removed my stick from her desktop and left the building, she was left alone again, loudly complaining about her security hole being exploited.
My work was done and I was preparing to break into another corporate security system.
- penetration tester diaries2 -
Getting all the shitty half-broken stuff because you're 'just a contractor'...
...and not being allowed to use your own top-of-the-range stuff due to 'data security policies' 😧1 -
Today I discovered that Betheme for Wordpress stores data base64 encoded in the database. Meaning you can't just do a search replace when you migrate a site to a different domain. That combined with Chrome based browsers not loading mixed security assets, but Firefox (the browser I use) does, makes for a confusing trouble ticket.
You have to change the setting to serialize sanely, then go into every post and save to update the stored data. Fortunately, the site is new so I only had one page to update, but I can't imagine the headache an established site would be to migrate.3 -
Books.
Do you guys know a good book for professional PHP 7 programming, especially OOP, concepts, design patterns, abstraction, algorithms, security and data structures?
Please not that beginner stuff, I want to dive deeper into PHP 7 😁
Maybe in German or English 😋3 -
This shithead continuously wasted 2 lectures of CNS(Cryptography and Network Security) on debating: in a link to link encrytion if encryption and decryption takes place on every node, what if attacker attacks the node while the data is decrypted.
Though I couldn't care less about the lecture but this guy brings the same issue in every lecture
Do anyone have any idea about the link to link encryption?
I know already it encrypts the whole packet with header and on each hop the data is decrypted and the destination ip address is fetched and encrypted again, but i don't know if it's possible to perform an attack on the decrypted data.3 -
Back when I was at uni, we had this group project based on data security.
At the first sit down meeting we had as a team, this one guy sat down and said "to be honest guys I'd be happy with a pass (40-50%) for this module"...
Well great.2 -
What is your wishlist for things that need to die or change next year. Mine is :-
1. Games that use peer to peer and have servers for data. Please buy servers on aws or any good cloud service.
2. ISP's that block all incoming connections for security5 -
Let's see:
No archival of data on a database server with over 5000 high profile customers using no encryption whatsoever with telnet open on LAN, every user on the same account in the office using the companies name as the password... But hey there are security cameras! -
Thoughts after a security conference.
The private sector, no matter the size, often plays a role (e.g. entry vector, DDoS load generating botnet, etc.) in massive, sometimes country-wide attacks. Shouldn't that make private businesses' CyberSec a matter of national security? Shouldn't the government create and enforce a security framework for private businesses to implement in their IT systems? IMO that'd also enforce standardised data security and force all the companies treat ITSec with at least minimal care (where "minimal" is set by the gov)
What are your thoughts?10 -
In nearby county to mine, coder was arrested for 3 months for nickname matching leaked terrorist nickname "grower" by coincidence. His coding education was enough reason for arrest.
All hdd/ssd/usb/mobile devices were confiscated for thorough analysis right from the morning by police.
Feeding my security paranoia. Encrypting fully filesystem(LUKS) and my internet traffic (self raised open vpn), wiping fully usbs. I ll be protected from my ISP recording my traffic, and from unauthorised access to my data.6 -
So i have been thinking..
SQL is a lang that runs on a specific software on the server, and helps creating data stores(databases and tables) that can be queried & manipulated.
is there a way to run sql like queries on the client side with no interaction from backend at all?
Say i have 5 inter related data models. in a backend world, they will form nice little tables of a db with all their joins and composite keys. from the server, i shall be querying them like "SELECT name from x where y=z & ..."
but what if i could store them like tables in browser memory and run the same query filters via a query language... is this possible?
i know this poses a certain security risk, but we already use cookies, local storage and a lot of json based shitty client side storages. surely it might be possible to have a lesser optimised sql tables on the frontend with extremely good querying capabilities?
or am i talking something far fetched here?8 -
Guys, I'm changing my email provider and am looking for a (paid) one that focuses on security and data privacy. Any suggestions/experiences?3
-
In our company, "UAT".
We using staging environment and most of the data is either missing or corrupt. They don't refresh the data, saying it can impose some security issue.
How the hell are we supposed to complete UAT when there's no data that's in production!!!! -
Saw a movie related to Data Security and Data privacy. The movie ended 1 hour ago and i am now terrified how my data is going to end up somewhere where it can be misused .Frantically removed all app permissions from my mobile. Wonder how many days it will last. But now after hearing such gory details , i wonder how i can keep my interests safe in this world. I am now even afraid to give my laptop for changing its battery.. Thinking of wiping all possible compromisable data. But dont know how to.
How will technologies like blockchain affect this ? Will it make it worse or is it trying to make it better..?11 -
The NPC has stated that the personal data of atleast 2000 people was leaked after the attacks on the websites of the philippinian goverment on april 1, the data contains; names,adresses,passwords and school data.
Over 7 administrators of schools, universities and other goverment structures have been called out for not reporting on the leakage of personal info on public facebook groups and violaton of the NPC in under 72 hours.
The representatives of the next structures stood before the comission on the 23 and 24 of april
- Taguig City University
- Department of Education offices in Bacoor City and Calamba City
- the Province of Bulacan
- Philippine Carabao Center
- Republic Central Colleges in Angeles City
- Laguna State Polytechnic University
The agency has reported that none of the organisations had notified about the personal info leakage yet.
This is a good reminder that you should inform about security/personal info breaches everyone that might be related to it as soon as possible, even if it seems unecessary. -
I’m working on a new app I’m pretty excited about.
I’m taking a slightly novel (maybe 🥲) approach to an offline password manager. I’m not saying that online password managers are unreliable, I’m just saying the idea of giving a corporation all of my passwords gives me goosebumps.
Originally, I was going to make a simple “file encrypted via password” sort of thing just to get the job done. But I’ve decided to put some elbow grease into it, actually.
The elephant in the room is what happens if you forget your password? If you use the password as the encryption key, you’re boned. Nothing you can do except set up a brute-forcer and hope your CPU is stronger than your password was.
Not to mention, if you want to change your password, the entire data file will need to be re-encrypted. Not a bad thing in reality, but definitely kinda annoying.
So actually, I came up with a design that allows you to use security questions in addition to a password.
But as I was trying to come up with “good” security questions, I realized there is virtually no such thing. 99% of security question answers are one or two words long and come from data sets that have relatively small pools of answers. The name of your first crush? That’s easy, just try every common name in your country. Same thing with pet names. Ice cream flavors. Favorite fruits. Childhood cartoons. These all have data sets in the thousands at most. An old XP machine could run through all the permutations over lunch.
So instead I’ve come up with these ideas. In order from least good to most good:
1) [thinking to remove this] You can remove the question from the security question. It’s your responsibility to remember it and it displays only as “Question #1”. Maybe you can write it down or something.
2) there are 5 questions and you need to get 4 of them right. This does increase the possible permutations, but still does little against questions with simple answers. Plus, it could almost be easier to remember your password at this point.
All this made me think “why try to fix a broken system when you can improve a working system”
So instead,
3) I’ve branded my passwords as “passphrases” instead. This is because instead of a single, short, complex word, my program encourages entire sentences. Since the ability to brute force a password decreases exponentially as length increases, and it is easier to remember a phrase rather than a complicated amalgamation or letters number and symbols, a passphrase should be preferred. Sprinkling in the occasional symbol to prevent dictionary attacks will make them totally uncrackable.
In addition? You can have an unlimited number of passphrases. Forgot one? No biggie. Use your backup passphrases, then remind yourself what your original passphrase was after you log in.
All this accomplished on a system that runs entirely locally is, in my opinion, interesting. Probably it has been done before, and almost certainly it has been done better than what I will be able to make, but I’m happy I was able to think up a design I am proud of.8 -
You know what really grinds my gears? Products that have no right of linking your data to an online platform.
Case and point: Password Managers. Nearly all of them work only with an account on a given service, have the passwords stored on their servers and so on and so forth. There is 0 transparency and for that matter 0 security. I found my choice, though it infuriates me terribly.
Another thing are budget managers. The switch for YNAB from local to on servers really annoys me. They should have no business in storing my very private data on their server. I don't understand people using it either.1 -
Cyber threats are the top concern of C levels. In actuality companies unintentionally expose way too much data. It's ridiculous what some make public.
-
what about security ! when u put your file url to update - insert - download data in databes ! u give easy access to evry hacker in word ! how can i secur it 😑😑?3
-
Today, I found out that the webmaster for the organization I volunteer at is using a security-by-obscurity PHP implemented design for the private data of our members. I've talked with him about it, but for a variety of reasons to do with organization and workload, it won't be changing.
Fml.3 -
Security theater is not security.
I am still on my mother's cell plan. I pay for it, but she is the primary account holder. We are grandfathered into unlimited no restrictions data, and a new phone yearly, so yeah, not giving that up.
Anyway, when i go to the store to manage the account they say, 'sorry, Sarah needs to come in as the primary account holder.'
'I am sarah' I tell them. I am lying, they know I am lying, and they know I know.
But they have no choice but to go along. I even asked once; they are not allowed to ask for proof of id. I don't know why.
It's just security theater.1 -
Three Layers of Security
As InfoWorld notes, all smartphones have three basic
elements of security. Your first major task as a mobile
user is to become aware of these layers and enable them
in your devices:
1. Device Protection: Allowing remote data "wiping" if your
device is ever lost or stolen.
2. Data Protection: Preventing corporate data from being
transferred to personal apps running on the same device
or personal network
3. App-Management Security: Protecting your in-app
information from becoming compromised. 6
6 -
Security issues I encountered:
- Passwords stored as plain text until last year.
- Sensitive data over http until last year.
- Webservice without user/pass authentication. -
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
Just sat through a demo of some clicky-draggy data visualisation stuff.
The guy showed us how you can write a custom script that takes a user input and pokes it into a sql command using string concatenation, so a very obvious injection vulnerability.
Ok, so it's only a demo. But you wouldn't do a demo with an example user called Captain Cock, so why do a demo with a screamingly obvious security hole?
Whole thing was basically pivot tables in a short skirt anyway.1 -
I just like bulding silly things, my ideal devjob would be one where I could just make random junk that makes me smile all day...
Like recently I made an NoSQL database using azure AD. They give you 50000 AD objects free, but I found you could encode all sorts of data in the AD objects variables. So basically I setup a framework that uses Security groups as Collections, AD objects as Documents, and object variables as key pairs.
It's really slow, like roughly 50 queries a minute, but hey. It was fun proving it could be done...
Yeah, that would be my ideal devjob :P that kind of stuff all day2 -
There is something serious about web browser extensions and the risk your data might be compromised just because of a simple stupid extension. You might harden the security of your machine and forgot about what you have installed as extensions, alot of people do not realize the risk because they simply install and give permissions as is.
The question is how to spot a malicious extension?23 -
Whatever be the current trend on Linked-In, at the end of the day the product development life cycle remains quite the same.
Still, as developers which general domains in software do you think would flourish in the near future?
My picks (not in order) -
>> Cyber security : automation, both offensive and defensive
>> Block chain : trustable data platforms
>> Applied AI : a few key models, applied to all niches, bettering existing UX
>> IOT : wearables, embeddables, smart appliances
>> AR : Navigation prompts, real time info about real life objects
>> VR : Immerse entertainment. (Metaverse 🤮)
>> Quantum computing : first gen costly commercial releases, new algos
What would you add or subtract from this?1 -
Another hours wasted on debugging, on what I hate most about programming: strings!
Don't get me started on C-strings, this abomination from hell. Inefficient, error prone. Memory corruption through off by one errors, BSOD by out of bound access, seen it all. No, it's strings in general. Just untyped junk of data, undocumented formats. Everything has to be parsed back and forth. And this is not limited to our stupid stupid code base, as I read about the security issues of using innerHTML or having to fight CMake again.
So back to the issue this rant is about. CMake like other scripting languages as bash have their peculiarities when dealing with the enemy (i.e. strings), e.g. all the escaping. The thing I fought against was getting CMake's fixup_bundle work on macOS. It was a bit pesky to debug. But in the end it turned out that my file path had one "//" instead of an "/" and the path comparison just did a string comparison without path normalization.
Stop giving us enough string to hang ourselves!rant debugging shit scripts of death fuck file paths fuck macos string to hang ourselves fuck strings cmake hell12 -
This is why you keep production data separate -- and out of the hands of developers: http://businessinsider.com/uber-emp...3
-
Two security researchers have published details about a vulnerability in the Windows Printing Service which impacts all Windows versions.
According to a Report of ZDNet : The vulnerability codenamed 'PrintDemon' which is located in Windows Print Spooler (Windows component responsible for managing print operations). The service sends data to be printed to a USB port for physically connected printers. In a report published, security researchers Alex Ionescu & Yarden Shafir said they found a bug in this old component that can be abused to hijack the Printer Spooler internal mechanism. The bug can not be used to break into a Windows client remotely over the internet, so it's not something that could be exploited to hack Windows systems over the internet.4 -
I recently came across this article with some basic security advices, like use 2fa security key, encrypt your USB keys, don't use untrusted USB chargers / cables / ports (or use a data blocker cable if you need to charge your device). It made me think, how relevant are the USB-related threats and risks today? Do people really still use and carry so many wired USB devices, and just drop or plug them wherever?
The last time I used an USB device to transfer some important data was probably over 10 years ago, and for the love of god I don't know anyone who still carries an USB key with sensitive data with them on a daily basis, much less actively uses it. Besides, whoever still does that probably puts their USB key on the same keychain as their ID / access tag and a bunch of other keys (including a 2fa device if they use one) - they're not going to lose just some sensitive data, they're going to lose authentication and physical access devices as well, and that could turn a small data leak into a full-scale incident, with or without an encrypted USB device.
I'm also not sure about untrusted USB cables and ports, from what I've seen the USB outlets and cables are pretty much non-existent in public places, most places offer wireless charging pads instead (usually built into a hand rest or table surface).3 -
For persistence, either credentials or data, is there any best practice that prefer DATABASES over FILES? Files such as JSON or txt or whatever...
Do dbs offer better perfomance or security?💾5 -
the red haired girl and the blue haired girl.
there was this story about a programmer who spent years studying computer science before finally getting a job.
the dev studied only computer science and was put on blue team after a few days.
a few hours into one of the constant coding sessions, the boss told the devs that red team members and blue team members would be working in pairs.
the person from red team transferred the devs work to their data base without the dev knowing, then locked down the devs computer. the dev could not do anything. later, the dev got fired for not doing any work. after that, the company got millions of dollars, and the dev did not see any of it.
both the dev and the managers made a note not to hire any programmer who cannot secure their work.
it is not ethical to teach people programming without also teaching them cyber security.
computer networking, programming and security should all be the same major.
it is a bad idea to teach people how to build anything without telling them how to secure it.
the story above was just a scenario, but it probably happens way more often than people think.
Schools should teach both things in the same major.5 -
Microsoft is responsible for protecting the Office 365 physical and virtual infrastructure and ensuring availability. Although Microsoft addresses certain security threats, it cannot prevent all malicious threats. Businesses are responsible for protecting their data. This means that if a business’s Office 365 data is compromised or corrupted, it is not Microsoft’s job to restore the data outside of the Software Licensing Terms. To protect data, businesses need to make sure they have office 365 disaster recovery and recovery plans in place2
-
SIEM: Security Information and Event Management system
Within a SIEM there is usually a reporting, alerting, and learning framework wherein you perform investigations and threat hunting. Our SIEM is connected to our data lake through a glorified elastic backend.
Today we were figuring out how to get dynamic data that we store in our SIEM to show up in the regular data lake presentation layer. All the solutions only half worked or had barriers to progress that seemed larger than the proposed solution.
So now we're going with the proposed solution: send static data back into the data lake in order to pull it out on the normal frontend with all the enriched info. We're basically turning this thing into a damn feedback loop.
I hate designing solutions within the confines of COTS products. -
Approx. 24 hours ago I proceeded to use MEGA NZ to download a file It's something I've done before. I have an account with them.
This is part of the email I received from MEGA NZ following the dowload: "
zemenwambuis2015@gmail.com
YOUR MEGA ACCOUNT HAS BEEN LOCKED FOR YOUR SAFETY; WE SUSPECT THAT YOU ARE USING THE SAME PASSWORD FOR YOUR MEGA ACCOUNT AS FOR OTHER SERVICES, AND THAT AT LEAST ONE OF THESE OTHER SERVICES HAS SUFFERED A DATA BREACH.
While MEGA remains secure, many big players have suffered a data breach (e.g. yahoo.com, dropbox.com, linkedin.com, adobe.com, myspace.com, tumblr.com, last.fm, snapchat.com, ashleymadison.com - check haveibeenpwned.com/PwnedWebsites for details), exposing millions of users who have used the same password on multiple services to credential stuffers (https://en.wikipedia.org/wiki/...). Your password leaked and is now being used by bad actors to log into your accounts, including, but not limited to, your MEGA account.
To unlock your MEGA account, please follow the link below. You will be required to change your account password - please use a strong password that you have not used anywhere else. We also recommend you change the passwords you have used on other services to strong, unique passwords. Do not ever reuse a password.
Verify my email
Didn’t work? Copy the link below into your web browser:
https://mega.nz//...
To prevent this from happening in the future, use a strong and unique password. Please also make sure you do not lose your password, otherwise you will lose access to your data; MEGA strongly recommends the use of a password manager. For more info on best security practices see: https://mega.nz/security
Best regards,
— Team MEGA
Mega Limited 2020."
Who in their right mind is going to believe something like that that's worded so poorly.
Can anybody shed some light on this latest bit of MEGA's fuckery?
Thank you very much.4 -
Well thanks a lot for the clarification of WHY I cannot sync my work (Office 365) mail using the mail client in Windows 10!
It's not that it's wrong; it's (probably) very much correct.
It's not that it's not precise; I don't think it could be anymore precise than a data dump like that.
It's not that trying to help me solve the problems; I'm sure it is.
But now that I have all the (debug) info about the security policies in place it would be great if it would show what violated which policy and maybe even what they mean and how to fix it?
The most concrete to go by is the error code, and judging by a google that has meant "your mail has problems" for at least three years...
...not even a single link was found to the (only) page detailing content, possible values, and dependencies between policies.
-
According to a report from ZDNet: IBM's new toolkit give developers easier access to Fully Homomorphic Encryption (FHE) which is a technology with promise for a number of security use cases. In case you do not know about FHE, you can take a look at My Quora Answer (https://qr.ae/pNKR2p).
"While the technology holds great potential, it does require a significant shift in the security paradigm," the report adds. "Typically, inside the business logic of an application, data remains decrypted, [Flavio Bergamaschi, FHE pioneer and IBM Researcher] explained. But with the implementation of FHE, that's no longer the case -- meaning some functions and operations will change."
The toolkit is available on GitHub for MacOS and iOS and it will soon be available for Linux and Android. -
How much of a security risk is it to serve static data from a json file on flask? Values are posted from a mobile device to a server to groom objects to return. My coworker is giving me a lot of shit for it as the file is accessed through a relative path, but the file names are checked and sanitised. He says the objects should be in a database.3
-
I hate how I have battery issues with every smartphone/tablet I buy. They do well for 1 week and then I have to buy an additional charger for work because after 5 hours of only lying there it only has 50% which wouldnt be sufficient for 30 minutes car drive (Maps, Spotify, Bluetooth, GPS and mobile data)... Fml. I am tired of batteries. My next phone is going to be a huawei mate 10. Maybe I habe more luck with this one. I dont believe im Samsung anymore.
And anyway why the fuck do they introduce better CPUs more sensors etc whilst Keeping the battery capacity the same.. Instead they introduce fast charge etc. Another reason for me to go away from samsung is the fact they bloat each firmware up, my battery got worst after each system update (even the security ones) and also doing 14 factory resets didnt work. Support is shit. They also integrated Clean Master into the system and an "Antivirus Protection"... Can't get worst.
samsungrant@devrant.com # > submit && exit -
!rant
Someone posted a link to a 30-day-security-challenge here on devRant some time ago and I just thought well, why not try to migrate away from the big companies - I've been using OneDrive as my only cloudstorage since the time when it was called SkyDrive and I've been hosting my Emails at outlook (via Live Custom Domains, a service that does not even exist anymore) for about 8 years now. Since I've always been lazy and since exchange activesync is a great feature if you have multiple calendars and want to sync them and your contacts to several devices I never tried to switch but now I am half done with migrating my data to my own nextcloud installation and my emails to my own mail server - since I don't want to loose the exchange functionality I am also setting up Z-Push and oh boy, this thing is bitching around but my webmail is already nicely integrated into nextcloud, IMAP / SMTP is up, configured and secured (still have to mess around with spamassassin as this email adress is floating around the web for about 10 years now). The only things to do is to get Z-Push work with STARTTLS and the card/caldav backend running and then the basic setup should be done.
I am just wondering if someone could hand me over a guide on how to sign / encrypt emails (GPG?) -
So on my new position I get to work on Spark jobs. Never had to work with the infamous big data technologies. I never thought this would get SO frustrating for all the wrong reasons.
I'm currently trying to introduce integration tests for some Spark job I wrote. This isn't trivial though, as the data comes from several HBase tables. Mocking everything simply isn't feasible. So why not use the integrated HBaseTestingUtility? With it you can start a mini cluster that runs all nessecary services in the scope of your test.
Sounds great, eh? WRONG. Firstly the used mapr dependencies get in the way. The baked in configuration tries to automatically authenticate with your local cluster through Kerberos. Of course this doesn't work. And of course there is no way to reconfigure this as it happens IN A FUCKING STATIC BLOCK. AHHHH.
Ok. So after calming down I "simply" had to exclude all mapr dependencies and replace them with vanilla ones. After two days of dependency hell it FINALLY works!
...or does it? Well now we need test data. For that we got a map reduce algorithm that can import dumps. Sounds again, great, eh? WROOOONNNG.
The fucking map reduce mini cluster can't start, as it tries to write a symlink. Now take a wild guess what the sys admin here blocked. Yepp. TWO DAYS OF WORK RENDERED USELESS, BECAUSE OF SOME FUCKING SECURITY SETTING.
This is fine. -
Persisterising derived values. Often a necessary evil for optimisation or privacy while conflicting with concerns such as auditing.
Password hashing is the common example of a case considered necessary to cover security concerns.
Also often a mistake to store derived values. Some times it can be annoying. Sometimes it can be data loss. Derived values often require careful maintenance otherwise the actual comments in your database for a page is 10 but the stored value for the page record is 9. This becomes very important when dealing with money where eventual consistency might not be enough.
Annoying is when given a and b then c = a + b only b and c are stored so you often have to run things backwards.
Given any processing pipeline such as A -> B -> C with A being original and C final then you technically only need C. This applies to anything.
However, not all steps stay or deflate. Sum of values is an example of deflate. Mapping values is an example of stay. Combining all possible value pairs is inflate, IE, N * N and tends to represent the true termination point for a pipeline as to what can be persisted.
I've quite often seen people exclude original. Some amount of lossy can be alright if it's genuine noise and one way if serving some purpose.
If A is O(N) and C reduces to O(1) then it can seem to make sense to store only C until someone also wants B -> D as well. Technically speaking A is all you ever need to persist to cater to all dependencies.
I've seen every kind of mess with processing chains. People persisting the inflations while still being lossy. Giant chains linear chains where instead items should rely on a common ancestor. Things being applied to only be unapplied. Yes ABCBDBEBCF etc then truncating A happens.
Extreme care needs to be taken with data and future proofing. Excess data you can remove. Missing code can be added. Data however once its gone its gone and your bug is forever.
This doesn't seem to enter the minds of many developers who don't reconcile their execution or processing graphs with entry points, exist points, edge direction, size, persistence, etc.2 -
Looking for iOS and Android app developers to join startup in Rutherford, NJ area. Must be able to show portfolio of apps and have some published. Must be able to pull and compare data with sensitive databases (social security number, passport, birth certificate, etc) to verify user. You will be compensated hourly. Must sign NDA.
-
I am developing an app for industrial automation that requires frequent user input. I am exploring the idea of using voice input to input data. The problem is the application will never have access to the internet during use. This is due to being in the middle of nowhere and security requirements. So I am looking for voice control libraries/systems to control an app that can be installed on a Windows 7/10 machine.
Has anyone had any success with a completely self-hosted voice control system?1 -
In the dynamic realm of software development, where the user interface meets the complex machinery behind the scenes, Back-End Expertise https://sombrainc.com/expertise/... emerges as the unsung hero. As businesses increasingly rely on digital platforms to connect, engage, and transact with their audience, the prowess of back-end development becomes paramount.
At its core, Back-End Expertise refers to the specialized knowledge and skills required to architect, build, and maintain the server-side of applications. While the front end dazzles users with intuitive interfaces and captivating designs, the back end silently weaves the intricate tapestry that ensures seamless functionality, robust security, and optimal performance.
The Back-End Symphony: Orchestrating Digital Harmony
Imagine a symphony where each instrument plays its part to perfection, creating a harmonious melody. Similarly, in the world of software, the back end orchestrates a symphony of databases, servers, and frameworks, ensuring that data flows smoothly, operations execute seamlessly, and applications respond promptly to user commands.
Back-End Experts are the virtuosos who write the code that makes applications tick. They delve into the intricacies of databases, crafting queries that retrieve and store data efficiently. They architect server-side logic, meticulously designing algorithms that power functionalities ranging from user authentication to complex business processes.
Security as the Forte: Safeguarding the Digital Fortress
In an era where data breaches loom as potential threats, Back-End Expertise becomes a formidable fortress. These experts implement robust security measures, safeguarding sensitive information and ensuring the integrity of digital ecosystems. Encryption, authentication protocols, and secure API integrations are the tools of their trade as they create digital bastions against cyber threats.
Optimizing Performance: The Need for Speed
User experience hinges on speed, and Back-End Experts understand the importance of optimizing performance. Through efficient coding practices, load balancing, and server-side optimizations, they strive to minimize latency and ensure that applications respond swiftly, even under heavy user loads.
Future Trends: Back-End Evolution
As technology evolves, so does the landscape of back-end development. Cloud computing, serverless architectures, and microservices are shaping the future of back-end expertise. Back-End Experts must adapt to these trends, embracing new tools and methodologies to stay at the forefront of innovation.
In conclusion, Back-End Expertise is the backbone of digital experiences. While users interact with the front end, the magic unfolds behind the scenes, where Back-End Experts craft the architecture that defines the reliability, security, and performance of applications. Their alchemy transforms lines of code into seamless digital experiences, leaving an indelible mark on the ever-evolving landscape of software development.1 -
Bwhahahah! Even after the excitement, business disruption, unpleasantness and pain, GDPR fails at its one job
https://newstatesman.com/science-te...1 -
EY and ConsenSys announced the formation of the Baseline Protocol with Microsoft which is an open source initiative that combines cryptography, messaging and blockchain to deliver secure and private business processes at low cost via the public Ethereum Mainnet. The protocol will enable confidential and complex collaboration between enterprises without leaving any sensitive data on-chain. The work will be governed by the Ethereum-Oasis Project.
Past approaches to blockchain technology have had difficulty meeting the highest standards of privacy, security and performance required by corporate IT departments. Overcoming these issues is the goal of the Baseline Protocol.
John Wolpert, ConsenSys’ Group Executive for Enterprise Mainnet added, “A lot of people think of blockchains as the place to record transactions. But what if we thought of the Mainnet as middleware? This approach takes advantage of what the Mainnet is good at while avoiding what it’s not good at.”
Source : ConsenSys -
AWS offers a wide range of services that can be used to automate your IT operations. Some of the most popular services for automation include:
*AWS Systems Manager Automation: This
service allows you to automate tasks such as
provisioning servers, deploying applications, and
configuring security policies.
*AWS Lambda: This service allows you to run
code without provisioning or managing servers.
This can be used to automate tasks such as
sending emails, updating databases, and
processing data.
*AWS CloudFormation: This service allows you
to create and manage infrastructure as code.
This can be used to automate the deployment
of complex IT environments.
*AWS CodePipeline: This service allows you to
automate the software development lifecycle.
This can be used to automate the build, test,
and deploy of applications.2 -
I'm lost here 😑! Got a new job and I supposed to analyze/fix/update/ the communication softwares/hardwares internally. Data security is insanely important and everything should be inexpensive 😑. Any suggestion what I can use as softwares and communication tools?7


