Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "all your data"
-
Hi, I am a Javascript apprentice. Can you help me with my project?
- Sure! What do you need?
Oh, it’s very simple, I just want to make a static webpage that shows a clock with the real time.
- Wait, why static? Why not dynamic?
I don’t know, I guess it’ll be easier.
- Well, maybe, but that’s boring, and if that’s boring you are not going to put in time, and if you’re not going to put in time, it’s going to be harder; so it’s better to start with something harder in order to make it easier.
You know that doesn’t make sense right?
- When you learn Javascript you’ll get it.
Okay, so I want to parse this date first to make the clock be universal for all the regions.
- You’re not going to do that by yourself right? You know what they say, don’t repeat yourself!
But it’s just two lines.
- Don’t reinvent the wheel!
Literally, Javascript has a built in library for t...
- One component per file!
I’m lost.
- It happens, and you’ll get lost managing your files as well. You should use Webpack or Browserify for managing your modules.
Doesn’t Javascript include that already?
- Yes, but some people still have previous versions of ECMAScript, so it wouldn’t be compatible.
What’s ECMAScript?
- Javascript
Why is it called ECMAScript then?
- It’s called both ways. Anyways, after you install Webpack to manage your modules, you still need a module and dependency manager, such as bower, or node package manager or yarn.
What does that have to do with my page?
- So you can install AngularJS.
What’s AngularJS?
- A Javascript framework that allows you to do complex stuff easily, such as two way data binding!
Oh, that’s great, so if I modify one sentence on a part of the page, it will automatically refresh the other part of the page which is related to the first one and viceversa?
- Exactly! Except two way data binding is not recommended, since you don’t want child components to edit the parent components of your app.
Then why make two way data binding in the first place?
- It’s backed up by Google. You just don’t get it do you?
I have installed AngularJS now, but it seems I have to redefine something called a... directive?
- AngularJS is old now, you should start using Angular, aka Angular 2.
But it’s the same name... wtf! Only 3 minutes have passed since we started talking, how are they in Angular 2 already?
- You mean 3.
2.
- 3.
4?
- 5.
6?
- Exactly.
Okay, I now know Angular 6.0, and use a component based architecture using only a one way data binding, I have read and started using the Design Patterns already described to solve my problem without reinventing the wheel using libraries such as lodash and D3 for a world map visualization of my clock as well as moment to parse the dates correctly. I also used ECMAScript 6 with Babel to secure backwards compatibility.
- That’s good.
Really?
- Yes, except you didn’t concatenate your html into templates that can be under a super Javascript file which can, then, be concatenated along all your Javascript files and finally be minimized in order to reduce latency. And automate all that process using Gulp while testing every single unit of your code using Jasmine or protractor or just the Angular built in unit tester.
I did.
- But did you use TypeScript?36 -
My school.
We have free WiFi access, but you need to login into your personal student account to use it.
Turns out, SQL Injection works.
It gets worse.
Table name "schueler".
SELECT *
Well.
Got all data on all students.
Name, address, phone number, passwords in plain.
I reported it using an anonymous email. Partially fixed. Standard quotes now get eacaped. Still, passwords are now MD5.47 -
So I wrote a code in HTML and js that puts an alert on the screen that says "all of your info is mine now, goodbye" and then redirects you to the nyam cat site
I sent it to some of my friends to have a little laugh but they have sent it to other people and eventually the school principle called me and told me to go to her office and retrieve all the data I stole
I went there and explaind her the prank but she didn't believe me
So she called the programming teacher to check the file
She laughed as hard as I've ever seen anyone laughing and told me to go back to class
It was scary and funny but the thing I've learnt is that it's stupid to prank ignorant people.15 -
So a few days ago I felt pretty h*ckin professional.
I'm an intern and my job was to get the last 2003 server off the racks (It's a government job, so it's a wonder we only have one 2003 server left). The problem being that the service running on that server cannot just be placed on a new OS. It's some custom engineering document server that was built in 2003 on a 1995 tech stack and it had been abandoned for so long that it was apparently lost to time with no hope of recovery.
"Please redesign the system. Use a modern tech stack. Have at it, she's your project, do as you wish."
Music to my ears.
First challenge is getting the data off the old server. It's a 1995 .mdb file, so the most recent version of Access that would be able to open it is 2010.
Option two: There's an "export" button that literally just vomits all 16,644 records into a tab-delimited text file. Since this option didn't require scavenging up an old version of Access, I wrote a Python script to just read the export file.
And something like 30% of the records were invalid. Why? Well, one of the fields allowed for newline characters. This was an issue because records were separated by newline. So any record with a field containing newline became invalid.
Although, this did not stop me. Not even close. I figured it out and fixed it in about 10 minutes. All records read into the program without issue.
Next for designing the database. My stack is MySQL and NodeJS, which my supervisors approved of. There was a lot of data that looked like it would fit into an integer, but one or two odd records would have something like "1050b" which mean that just a few items prevented me from having as slick of a database design as I wanted. I designed the tables, about 18 columns per record, mostly varchar(64).
Next challenge was putting the exported data into the database. At first I thought of doing it record by record from my python script. Connect to the MySQL server and just iterate over all the data I had. But what I ended up actually doing was generating a .sql file and running that on the server. This took a few tries thanks to a lot of inconsistencies in the data, but eventually, I got all 16k records in the new database and I had never been so happy.
The next two hours were very productive, designing a front end which was very clean. I had just enough time to design a rough prototype that works totally off ajax requests. I want to keep it that way so that other services can contact this data, as it may be useful to have an engineering data API.
Anyways, that was my win story of the week. I was handed a challenge; an old, decaying server full of important data, and despite the hitches one might expect from archaic data, I was able to rescue every byte. I will probably be presenting my prototype to the higher ups in Engineering sometime this week.
Happy Algo!8 -
Meeting with client.
Me: our solution does not require a central server, any computer (windows, Mac or Linux) on which you install our software can act both as a client and a server
Client: no we need to have all our data on our server
Me: sure, you can install our software on any computer
Client: no, we need it on our server
Me: ok then, we can make the needed changes to install our software on your server, it will cost an additional fee though
Client: very good then17 -
So I have been temporarily assigned to new team .. moving from mainly backend.. to help the Web team ..
Me .: Aight guys .. what we working with ?
Team: MVC .net
Me: awesome ..
Team: but we have our own version of MVC .
Me : 🤔 your own MVC ?
Team: yeh we only buse controllers.. but no models at all ?
Me.: 😲 So where does the view gets its data from ?
Team : from Azure functions apps.
M: how ?
T: ( in very proud tone ) .. we use js to call all functions.
M: so why not just use HTML pages . Why MVC then !
T: coz MVC is modern architecture design.
M: but you not using it and all of calles to the functions are exposed publicly.
T: 🧐 THIS IS MODERN DESIGN !!
M: 🤪 My bad .. what the hell do I know ! I only been developing MVC applications for 7 years !!
Please tell me more about your " Modern Design "
🤮🤮🤮25 -
I'd like to extend my heartfelt fuck-you to the following persons:
- The recruiter who told me that at my age I wouldn't find a job anymore: FUCK YOU, I'll send you my 55 birthday's cake candles, you can put all of them in your ass, with light on.
- The Project Manager that after 5 rounds of interviews and technical tests told me I didn't have enough experience for his project: be fucked in an Agile way by all member of your team, standing up, every morning for 15 minutes, and every 2 weeks by all stakeholders.
- The unemployment officer who advised me to take low level jobs, cut my expenses and salary expectations: you can cut your cock and suck it, so you'll stop telling bullshit to people
- The moron that gave me a monster technical assignment on Big Data, which I delivered, and didn't gave me any feedback: shove all your BIG DATA in your ass and open it to external integrations
- the architect who told me I should open my horizons, because I didn't like React: put a reactive mix in your ass and close it, so your shit will explode in your mouth
- the countless recruiter who used my cv to increase their db, offering fake jobs: print all your db on paper and stuff your ass with that, you'll see how big you will be
To all of them, really really fuck you.12 -
Benefits of being a dev:
Wife: "I just wish I had a program that could organize all my shit for my [work-from-home outside sales] job. My old company had much better software."
One week later:
Me: "Here honey: I built a program that will organize your business leads, allow you to search them by city, street, phone number, it detects when you have multiple businesses with one owner, warns you of duplicate information before you add it, and you can now launch phone calls with the click of a button. I've also put an app on your phone that can send and receive data from the main program."
One hour later:
Giggity giggity.6 -
Started talking with someone about general IT stuff. At some point we came to the subject of SSL certificates and he mentioned that 'that stuff is expensive' and so on.
Kindly told him about Let's Encrypt and also that it's free and he reacted: "Then I'd rather have no SSL, free certificates make you look like you're a cheap ass".
So I told him the principle of login/registration thingies and said that they really need SSL, whether it's free or not.
"Nahhh, then I'd still rather don't use SSL, it just looks so cheap when you're using a free certificate".
Hey you know what, what about you write that sentence on a whole fucking pack of paper, dip it into some sambal, maybe add some firecrackers and shove it up your ass? Hopefully that will bring some sense into your very empty head.
Not putting a secure connection on a website, (at all) especially when it has a FUCKING LOGIN/REGISTRATION FUNCTION (!?!?!?!!?!) is simply not fucking done in the year of TWO THOUSAND FUCKING SEVENTEEN.
'Ohh but the NSA etc won't do anything with that data'.
Has it, for one tiny motherfucking second, come to mind that there's also a thing called hackers? Malicious hackers? If your users are on hacked networks, it's easy as fuck to steal their credentials, inject shit and even deliver fucking EXPLOIT KITS.
Oh and you bet your ass the NSA will save that data, they have a whole motherfucking database of passwords they can search through with XKeyScore (snowden leaks).
Motherfucker.68 -
"I don't care if the government spies on me, I have nothing (criminal) to hide."
Uhm... but... if you have nothing criminal to hide.... then why'd they have to spy on you/collect your data...?
After all you didn't do anything illegal...58 -
*Interview*
Interviewer: We have an opening. Are you interested to work?
Me: What is that I'll be doing?
I: What technologies and languages do you know?
Me: I know Scala, Java, Spark, Angular, Typescript, blah blah. What is your tech stack?
I: Any experience working on frontend?
Me: Yes. But what do you use for it?
I: Can you work with databases?
Me: I can, on SQL based. What are yours?
I: Can you do big data processing?
Me: I know Spark, if that's what you are asking for. What is it that you actually do?
I: Any experience in cloud development?
Me: Yes. AWS? Azure? GCP?
I: Do you know CI CD?
Me: Excuse me.. I've been asking a lot of questions but you're not paying attention to what I'm asking. Can you please answer the questions I asked.
I: Yes. Go ahead.
Me: What will be my position?
I: A full stack developer.
Me: What technologies do you use in your project?
I: We use all the latest tech.
Me: Like?
I: All latest tech.
Me: You mentioned big data processing?
I: Yes. Processing data from DB and generating reports.
Me: what do you use for that?
I: Java.
Me: Are you planning to rebuild it using Spark or something and deploy in the cloud?
I: No we're not rebuilding it. Just some additions to the existing.
Me: Then what's with cloud? Why did you ask for that?
I: Just to know if you're familiar.
Me: So I'll be working with Java. Okay. What do you use for UI?
I: Flash
Me: 🙄
I sat for a couple of minutes contemplating life.
I: Are you willing to join?
Me: No. Not at all. Thankyou for the offer.5 -
After it was revealed that the Equifax hack was even bigger yet again, the US government said something that really made me say/think something in the trend of "WHAT the actual FUCK?!"
"This data is in the hands of cyber criminals anyways".
You run the biggest mass surveillance program in the world, sucking up more than a million terabytes every hour, then at least could you PRETEND to care/take interest when the personal data of about all your citizens appears on the Internet?!
Fucking hell.11 -
In a user-interface design meeting over a regulatory compliance implementation:
User: “We’ll need to input a city.”
Dev: “Should we validate that city against the state, zip code, and country?”
User: “You are going to make me enter all that data? Ugh…then make it a drop-down. I select the city and the state, zip code auto-fill. I don’t want to make a mistake typing any of that data in.”
Me: “I don’t think a drop-down of every city in the US is feasible.”
Manage: “Why? There cannot be that many. Drop-down is fine. What about the button? We have a few icons to choose from…”
Me: “Uh..yea…there are thousands of cities in the US. Way too much data to for anyone to realistically scroll through”
Dev: “They won’t have to scroll, I’ll filter the list when they start typing.”
Me: “That’s not really the issue and if they are typing the city anyway, just let them type it in.”
User: “What if I mistype Ch1cago? We could inadvertently be out of compliance. The system should never open the company up for federal lawsuits”
Me: “If we’re hiring individuals responsible for legal compliance who can’t spell Chicago, we should be sued by the federal government. We should validate the data the best we can, but it is ultimately your department’s responsibility for data accuracy.”
Manager: “Now now…it’s all our responsibility. What is wrong with a few thousand item drop-down?”
Me: “Um, memory, network bandwidth, database storage, who maintains this list of cities? A lot of time and resources could be saved by simply paying attention.”
Manager: “Memory? Well, memory is cheap. If the workstation needs more memory, we’ll add more”
Dev: “Creating a drop-down is easy and selecting thousands of rows from the database should be fast enough. If the selection is slow, I’ll put it in a thread.”
DBA: “Table won’t be that big and won’t take up much disk space. We’ll need to setup stored procedures, and data import jobs from somewhere to maintain the data. New cities, name changes, ect. ”
Manager: “And if the network starts becoming too slow, we’ll have the Networking dept. open up the valves.”
Me: “Am I the only one seeing all the moving parts we’re introducing just to keep someone from misspelling ‘Chicago’? I’ll admit I’m wrong or maybe I’m not looking at the problem correctly. The point of redesigning the compliance system is to make it simpler, not more complex.”
Manager: “I’m missing the point to why we’re still talking about this. Decision has been made. Drop-down of all cities in the US. Moving on to the button’s icon ..”
Me: “Where is the list of cities going to come from?”
<few seconds of silence>
Dev: “Post office I guess.”
Me: “You guess?…OK…Who is going to manage this list of cities? The manager responsible for regulations?”
User: “Thousands of cities? Oh no …no one is our area has time for that. The system should do it”
Me: “OK, the system. That falls on the DBA. Are you going to be responsible for keeping the data accurate? What is going to audit the cities to make sure the names are properly named and associated with the correct state?”
DBA: “Uh..I don’t know…um…I can set up a job to run every night”
Me: “A job to do what? Validate the data against what?”
Manager: “Do you have a point? No one said it would be easy and all of those details can be answered later.”
Me: “Almost done, and this should be easy. How many cities do we currently have to maintain compliance?”
User: “Maybe 4 or 5. Not many. Regulations are mostly on a state level.”
Me: “When was the last time we created a new city compliance?”
User: “Maybe, 8 years ago. It was before I started.”
Me: “So we’re creating all this complexity for data that, realistically, probably won’t ever change?”
User: “Oh crap, you’re right. What the hell was I thinking…Scratch the drop-down idea. I doubt we’re have a new city regulation anytime soon and how hard is it to type in a city?”
Manager: “OK, are we done wasting everyone’s time on this? No drop-down of cities...next …Let’s get back to the button’s icon …”
Simplicity 1, complexity 0.16 -
Working with a radio chip we selected because it had built-in encryption. Cannot make the encryption work, thus in contact with the manufacturer:
"- I cannot make the encryption work, it's like the chip doesn't want to take a key.
- which key do you use?
- does it matter?
- well yes, you can't just use any key!
- why not?
- you need to get an approved key from us.
- why is that?
- so that your competitors can't read your data!
- ...
- ...
- so the way to get working keys is to get them from you?
- of course!
- keys are 256 bits. Can we potentially use all of them?
- OF COURSE NOT!
- how many can we get from you?
- one! We reserve it from your company.
- are you telling me that all units within a company will need to have the exact same encryption key?
- yes!
- so anyone with our product could eavesdrop another same product?
- well yes, but it's all within your own products.
- ...
- ...
- that's not how encryption is supposed to work.
- but it's safe, your competitors cannot eavesdrop!
- I'm out of here."
(We finally found a satisfactory work-around, but i am still pissed at them)9 -
Interviewer: So are you familiar with our company and what we do?
Dev: I looked at your website, looks like you build tools for managing restaurants.
Interviewer: No. That’s not even close.
Dev: ?
Interviewer: What we do is create an ecosystem of integrated data centres all orchestrated for immediate stakeholder utilization.
Dev: But the product itself…. it’s a user interface for tracking inventory. Of like…. burgers…. and bottles of wine.
Interviewer: It’s not a product! It’s a data……habitat!!
Dev: …
Dev: So does that make your users animals?
Interviewer: 😡. Unfortunately it looks like you do not see our vision and would not be a good fit for this role.
Dev: Agreed.25 -
Me (to friend): So all your information these days is stored in the cloud.
Friend: Yeah I know that's crazy, huh!?
Me: Yeah!
Friend: I wonder if there's any disruption of the data when planes fly through.
Me: What do you mean?
Friend: Like when a cloud breaks when a plane move through it since we store our data in the precipitation layer. Nikola Tesla would be so proud.
Me: Uh... The fuck?
Me (thinking to myself): maybe he's just joking...4 -
What an awful day :(
The server where I host my 4 clients websites crashed.
Unable to reboot from the console.
I contact the support. 15 minutes later: "we'll look at this"
No news for 1 week despite my messages.
Then... 1st ticket escalation... 2nd ticket escalation... 3rd ticket escalation...
Answer: "Sorry, your server is down and cannot be repaired."
Fuck.
I ask "is there any way to get my data back?". Answer: "No, because we would shutdown the whole bay and all our clients would be impacted".
Fuck.
I subscribe to another server, at another provider.
I look at my backups... shit, the last one is 4 month ago!!
I restore the first website: OK
I restore the second website: OK
I restore the third website: My new server is "too recent" and not compatible. with this old Wordpress. Fuck! I'll look at this later...
I restore the fourth website: database is empty!! What??? I look at the SQL backup for this site... it failed...
I lost ALL my 4th client data!!!
I'm sooooo piece of crap!14 -
Hello!
I'm a member of an international hacker group.
As you could probably have guessed, your account [cozyplanes@tuta.io] was hacked, because I sent message you from it.
Now I have access to you accounts!
For example, your password for [cozyplanes@tuta.io] is [RANDOM_ALPHABET_HERE]
Within a period from July 7, 2018 to September 23, 2018, you were infected by the virus we've created, through an adult website you've visited.
So far, we have access to your messages, social media accounts, and messengers.
Moreover, we've gotten full damps of these data.
We are aware of your little and big secrets...yeah, you do have them. We saw and recorded your doings on porn websites. Your tastes are so weird, you know..
But the key thing is that sometimes we recorded you with your webcam, syncing the recordings with what you watched!
I think you are not interested show this video to your friends, relatives, and your intimate one...
Transfer $700 to our Bitcoin wallet: 13DAd45ARMJW6th1cBuY1FwB9beVSzW77R
If you don't know about Bitcoin please input in Google "buy BTC". It's really easy.
I guarantee that after that, we'll erase all your "data" :)
A timer will start once you read this message. You have 48 hours to pay the above-mentioned amount.
Your data will be erased once the money are transferred.
If they are not, all your messages and videos recorded will be automatically sent to all your contacts found on your devices at the moment of infection.
You should always think about your security.
We hope this case will teach you to keep secrets.
Take care of yourself.
>> RE >>
Well f### you, thanks for telling my password which is obviously fake. I have sent your details to the local police department, shall rest in peace. Don't earn money by this kind of action. STUPID!14 -
A few years ago:
In the process of transferring MySQL data to a new disk, I accidentally rm'ed the actual MySQL directory, instead of the symlink that I had previously set up for it.
My guts felt like dropping through to the floor.
In a panic, I asked my colleague: "What did those databases contain?"
C: "Raw data of load tests that were made last week."
Me: "Oh.. does that mean that they aren't needed anymore?"
C: "They already got the results, but might need to refer to the raw data later... why?"
Me: "Uh, I accidentally deleted all the MySQL files... I'm in Big Trouble, aren't I?"
C: "Hmm... with any luck, they might forget that the data even exists. I got your back on this one, just in case."
Luck was indeed on my side, as nobody ever asked about the data again.5 -
Alright, I just wanna start off by saying that I'm a huge privacy guy. I hate all kinds of data collection companies like Google/Facebook/Amazon and all that. Yet I'm forced to have a Google account for certain reasons.
But the thing that I want to say is that I often talk to people to express my concerns about privacy. And most people agree and say that "yeah sure that's some scary shit" but don't actually do much about it.
And the thing is. If you just browse through all of the options in your Google account. You can turn off and remove almost all data collection/ad serving and identification options entirely.
And yet purple complain about that Google sees what you buy and shit. Turn everything off. Get and adblocker and get noscript. The single best browser add-on out there. It's almost that easy to get at least acceptable amounts of Internet privacy.
Please, don't ever ignore the significance of in Internet privacy. And the potential issue of net neutrality. Don't be ignorant. Don't be the client.24 -
!(short rant)
Look I understand online privacy is a concern and we should really be very much aware about what data we are giving to whom. But when does it turn from being aware to just being paranoid and a maniac about it.? I mean okay, I know facebook has access to your data including your whatsapp chat (presumably), google listens to your conversations and snoops on your mail and shit, amazon advertises that you must have their spy system (read alexa) install in your homes and numerous other cases. But in the end it really boils down to "everyone wants your data but who do you trust your data with?"
For me, facebook and the so-called social media sites are a strict no-no but I use whatsapp as my primary chating application. I like to use google for my searches because yaa it gives me more accurate search results as compared to ddg because it has my search history. I use gmail as my primary as well as work email because it is convinient and an adv here and there doesnt bother me. Their spam filters, the easy accessibility options, the storage they offer everything is much more convinient for me. I use linux for my work related stuff (obviously) but I play my games on windows. Alexa and such type of products are again a big no-no for me but I regularly shop from amazon and unless I am searching for some weird ass shit (which if you want to, do it in some incognito mode) I am fine with coming across some advs about things I searched for. Sometimes it reminds me of things I need to buy which I might have put off and later on forgot. I have an amazon prime account because prime video has some good shows in there. My primary web browser is chrome because I simply love its developer tools and I now have gotten used to it. So unless chrome is very much hogging on my ram, in which case I switch over to firefox for some of my tabs, I am okay with using chrome. I have a motorola phone with stock android which means all google apps pre-installed. I use hangouts, google keep, google map(cannot live without it now), heck even google photos, but I also deny certain accesses to apps which I find fishy like if you are a game, you should not have access to my gps. I live in India where we have aadhar cards(like the social securtiy number in the USA) where the government has our fingerprints and all our data because every damn thing now needs to be linked with your aadhar otherwise your service will be terminated. Like your mobile number, your investment policies, your income tax, heck even your marraige certificates need to be linked with your aadhar card. Here, I dont have any option but to give in because somehow "its in the interest of the nation". Not surprisingly, this thing recently came to light where you can get your hands on anyone's aadhar details including their fingerprints for just ₹50($1). Fuck that shit.
tl;dr
There are and should be always exceptions when it comes to privacy because when you give the other person your data, it sometimes makes your life much easier. On the other hand, people/services asking for your data with the sole purpose of infilterating into your private life and not providing any usefulness should just be boycotted. It all boils down to till what extent you wish to share your data(ranging from literally installing a spying device in your house to them knowing that I want to understand how spring security works) and how much do you trust the service with your data. Example being, I just shared most of my private data in this rant with a group of unknown people and I am okay with it, because I know I can trust dev rant with my posts(unlike facebook).29 -
Dear Android:
I know I'm not on wifi. I get it. Sometimes data coverage isn't amazing or the network is congested. It's cool. You can just flash "no service" and I just won't try. or even "3G" and I'll have some patience. I rember how slow 3G was. It's okay, I'll wait.
But fucking stop showing 4G LTE if you can't make a fucking GET request for a 2kb text file in less than 5 minutes! Fucking really? Don't fucking lie to me with your false hope bullshit, just tell me the truth and I'll probably sigh and say shit and put my phone away.
But fuck you and your progress bar externally stuck in the middle. As if to say you're making progress! Wasting my time!
If you can't download a kilobyte in a 5min period, why even say I have data at all? What good does that do me?23 -
My coworker requested I add a bunch of tracking to our product.
I've previously tried explaining to him (and honestly the rest of the company) about privacy issues stemming from tracking, such as by their beloved Venmo. Venmo tracks absolutely fking everything you give it access to, from location data to your entire facebook, twitter, foursquare, etc. feeds, and sells ALL of it to third parties. It's scary. but! this guy simply does not understand, and/or does not care, and marches right on into all the surveillance, loudly singing the song of convenience to all who'll listen. (Nobody else in the company cared, either. :/)
ugh.
Anyway, I'm conflicted.
I have to install some tracking, but I can probably come up with an excuse to cut most of it out and gimp their surveillance. It'll still be useful to us, but it'll limit the amount of data the tracking company can sell to third parties.
but they'll push this guy pretty hard on it, and he's as technically-inclined as a smudged glass of warm, stale beer. "Better for your conversion!" they'll say. "How much tracking do you want?" he'll reply. "@ashkin, why can't you do this right now? What else do you need to make this happen?" he'll firmly inquire. and so I'll be forced to make it happen...
ergh13 -
Stupid annoying client want me to add 2 new fields on a form. Ok I said, my estimation is that I need 2 days to make the changes on form, database and all the scripts that posting and getting data, plus testing. His reply was, come one do you really want 48 hours to just add 2 fields, its sooo easy!!!! WTF dude... if it is sooo easy why are you fucking bother me??? Do it your self!!!!8
-
My morning (RO = remote office):
Me: Your xxx implementation is very strange.
RO: Yes we are following a new example from experts in this field. See this link.
Me: Paragraph 1, use xxx class in these situations. Were not doing that.
RO: Yes we had problems with that, we decided to skip that.
Me: Paragraph 2, always use xxx when accessing data. Were not doing that.
RO: Yes that create many bugs, we skipped that.
Me: This section on debugging says to enable this flag while in development to allow the IDE to alert you to issues.
RO: Yes this causes the app to crash constantly. So we took it out.
Me: ... because its finding issues ... and telling you where the problem is, with an error message.
... your not following the experts at all.
RO: We are!, please read the link we provided.
... this will be discussed on my exit interview6 -
- devRant TOR rant! -
There is a recent post that just basically says 'fuck TOR' and it catches unfortunate amount of attention in the wrong way and many people seem to aggree with that, so it's about time I rant about a rant!
First of all, TOR never promised encryption. It's just used as an anonymizer tool which will get your request through its nodes and to the original destination it's supposed to arrive at.
Let's assume you're logging in over an unencrypted connection over TOR and your login information was stolen because of a bad exit node. Is your privacy now under threat? Even then, no! Unless of course you had decided to use your personal information for that login data!
And what does that even have to do with the US government having funded this project even if it's 100%? Are we all conspiracy theorists now?
Let's please stop the spread of bs and fear mongering so that we can talk about actual threats and attack vectors on the TOR network. Because we really don't have any other reliable means to stop a widely implemented censorship.12 -
!!privacy
!!political
I had a discussion with a coworker earlier.
I owed him for lunch the other day, and he suggested I pay him back either with cash (which I didn't have), Venmo, or just by him lunch the next time (which I ended up doing).
I asked about Venmo, and he said it was like paypal, but always free. that sounded a bit off -- because how are they in business if it's always free? -- so I looked it up, and paid special attention to their privacy policy.
The short of it: they make money by selling your information. That's worth far more than charging users a small fee when sending $5 every few weeks. Sort of what I expected when I heard "always free," but what surprised me is just how much they collect. (In retrospect, I really shouldn't have been surprised at all...)
Here's an incomplete list:
* full name, physical address, email, DoB, SSN (or other government IDs, depending on country)
* Complete contact list (phone numbers, names, photos)
* Browser/device fingerprint
* (optional) Your entire Facebook feed and history
* (optional) all of your Facebook friends' contact info
* Your Twitter feed
* Your FourSquare activity
(The above four ostensibly for "fraud prevention")
* GPS data
* Usage info about the actual service
* Other users' usage info (e.g. mentioning you)
* Financial info (the only thing not shared with third parties)
Like, scary?
And, of course, they share all of this with their parent company, PayPal. (The privacy policy does not specify what PayPal does with it, nor does it provide any links that might describe it, e.g. PayPal's "info-shared-by-third-parties" privacy policy)
So I won't be using Venmo. ever.
I mentioned all of this to my coworker, and he just doesn't understand. at all. He even asks "So what are they going do with that, send me ads? like they already do?"
I told him why I think it's scary. Everything from them freely selling all of your info, to someone being able to look through your entire online life's history, to being able to masquerade around as you, to even reproducing your voice (e.g. voice clips collected by google assistant), to grouping people by political affiliations.
He didn't have much to say about any of them, and actually thought the voice thing was really cool. (All I could think of was would happen if the "news" had that ability....) All of his other responses were "that doesn't bother me at all" and/or "using all of these services is so convenient."
but what really got me was his reaction to the last one.
I said, "If you're part of the NRA, for example, you'd be grouped with Republicans. If they sell all of this information, which they do, and they don't really care who buys it or what they do with it... someone could look through the data and very very easily target those political groups."
His response? "I don't have to worry about that. I'm a Democrat, and have always voted Democrat. I'll tell anyone that."
Like.
That's basically saying every non-democrat is someone you should be wary of and keep an eye on. That's saying Democrats are the norm and everyone else is deviant and/or wrong.
and I couldn't say anything after this because... no matter what I said, it would start a political conflict, and would likely end with me being fired (since the owner is also a democrat, and they're very buddy-buddy). "What if they target democrats?" -> "They already do!" or "What if democrats use it against others?" -> "They deserve it for being violent and racist, but we never would" (except, you know, that IRS/tea-party incident for example...)
But like, this is coming from someone who firmly believes conservatives are responsible for all of the violence and looting and rioting and mass shootings in the country. ... even when every single instance has been by committed by democrats. every. single. one.
Just...
jfl;askjfasflkj.
He doesn't understand the need for privacy, and his world view is just... he actually thinks everyone with different beliefs is wrong and dangerous.
I don't even know how to deal with people like this. and with how prevalent this mindset is... coupled with the aforementioned privacy concerns... it's honestly *terrifying.*65 -
Old man's tale. It's true.
Like 12 years ago, I was working in a small town computer store.
One day, a really ugly woman came in and asked for data recovery since she could not boot up her PC anymore.
We recovered her data, and just to make sure it was all "working", we randomly checked a few directories for files.
We have found some photos of her.
Her and a bottle of Coke.
Let me put it this way: she loves coke bottles. A lot.
There are things that can't be unseen, and moments you still remember after 12 years. Like the moment she came in to get her stuff - and you need to pretend to be all business while you're almost pissing your pants.
Good days :)7 -
What is the difference between USA and USB?
One connects to all your devices and accesses the data, the other is a hardware standard! 3
3 -
FUCK!!! FUCK IT ALL. FUCK YOU AND YOUR CRAPPY BULLSHT UNDOCUMENTED AND OUTDATED API.
YOUR DATABASE SERVER BACK-END HAS TO BE THE ONE MANAGING THE DISPLAY DATA FOR ITS WEB AND MOBILE CLIENTS. NOT THE OTHER WAY AROUND, DAMN IT.
I'M NOT GONNA SIT HERE ALL DAY HARD-CODING ALL YOUR SERVER'S INADEQUACY.
MAKES ME WONDER DO YOU EVER USE DESIGN PATTERNS OR APPLY DESIGN PRINCIPLES? DRY AT LEAST? DON'T FUCKING REPEAT YOURSELF, DAMN IT.
I CAN'T WAIT TO LEAVE THIS PLACE FOR GOOD.6 -
Had a job interview recently that went well besides one little disagreement... and it has made me question my sanity. Tell me if I'm wrong.
They asked the difference between a GET and POST request.
Wow, that's an easy one, they're giving me a break, I thought to myself.
I said "GET is used to retrieve data from a server, whereas POST is used to add data to a server, via it's body, which a GET lacks" or something like that.
They were like "ya mostly, but GET can be used to enter data into the server too. We were just looking for the body thing."
And I'm like.... yeah, you could do that, but that's not what it's meant for.
They mention stuff about query parameters and I hold steady that GET and POST are different because GET has a specific purpose. Otherwise, we wouldn't need the "method" part of an HTTP request at all. We could just either include a body or not include a body.
I ended it with "Well, POST implies that you are adding data to a server, and GET implies you are querying data from the server. When I'm reading documentation, that's how I quickly determine what an endpoint does."
My confidence was a little shaken at this point. Crazy what two people with (I assume at least) 10+ years of experience telling you you're wrong will do to your confidence.21 -
QA: When I open the app I get this strange error message that includes "No data connection could be established" near the start of it.
Me: I'll clean up how thats displayed, but the error means your phone doesn't have internet connection.
QA: No that can't be it, I do.
Me: You screenshot shows no WiFi or 3g / 4g symbols.
QA: No those are never there, please investigate.
Me: I have investigated and found that every other one of your screenshots had a WiFi or a 3g symbol. Example: <link>. Please check your connection and try again, i'll clean up the error display.
PM: Oh i've had an issue something like this before. We really need to show users an error screen. We can't just leave them on this screen with no error message at all.
Me: ... we have an error, thats what QA is complaining about, its not loading the text and displaying the error object.
Anyone else want to not pay attention and complain about something else that doesn't make sense? ... no? ... ok good, back to work then7 -
--- SUMMARY OF THE APPLE KEYNOTE ON THE 30TH OF OCTOBER 2018 ---
MacBook Air:
> Retina Display
> Touch ID
> 17% less volume
> 8GB RAM
> 128GB SSD
> T2 Chip (Core i5 with 1.6 GHz / 3.6 GHz in turbo mode)
Price starting at $1199
Mac Mini:
> T2 Chip
> up to 64GB RAM
> up to 2TB all-flash SSD
> better cooling than previous Mac Mini
> more ports than previous Mac Mini - even HDMI, so you can connect it to any monitor of your choice!
> stackable - yes, you can build a whole data center with them!
Price is 799$
Both MacBook Air and Mac Mini are made of 100% recyled aluminium!
Good job, Apple!
iPad Pro:
> home-button moved to trash
> very sexy edges (kinda like iPhone 4, but better)
> all-screen design - no more ugly borders on the top and bottom of the screen
> 15% thinner and 25% less volume than previous iPads
> liquid retina display (same as the new iPhone XR)
> Face ID - The most secure way to login to your iPad!
> A12X Bionic Chip - Insane performance!
> up to 1TB storage - Whoa!
> USB-C - Allow you to connect your iPad to anything! You can even charge your iPhone with your iPad! How cool is that?!
> new Apple Pencil that attaches to the iPad Pro and charges wirelessly
> new, redesigned physical keyboard
Price starting at 799$
Also, Apple introduced "Today at Apple" - Hundreds of sessions and workshops hosted at apple stores everywhere in the world, where you can learn about photography, coding, art and more! (Using Apple devices of course)16 -
A few weeks ago a client called me. His application contains a lot of data, including email addresses (local part and domain stored separately in SQL database). The application can filter data based on the domain part of the addresses. He ask me why sub.example.com is not included when he asked the application for example.com. I said: No problem, I can add this feature to the application, but the process will take a longer.
Client: No problem, please add this ASAP.
So, the next day I changed some of the SQL queries to lookup using the LIKE operator.
After a week the client called again: The process is really slow, how can this be?
Me: Well, you asked me to filter the subdomains as well. Before, the application could easily find all the domains (SQL index), but now it has to compare all the domains to check if it ends with the domain you are looking for.
Client: Okay, but why is it a lot slower than before?
Me: Do you have a dictionary in your office?
<Client search for a dictionary, came back with one>
Me: give me the definition of the word "time"
<Client gives definition of time>
Me: Give me the definition of all words ending with "time"
Client: But, ...
Never heard from him again on this issues :-P5 -
Had a discussion with a developer about security. His software transfers all user data (password and files) unencrypted, so anyone can grab them with wireshark. I told him that this is a severe issue. He said no its no problem because if you get hacked its your own fault, because you probably used an insecure network. NO ! YOU FUCKING MALADJUSTED SHEEP-MOLESTING OBJECT OF EXECRATION, YOU SHOULD ALWAYS ENCRYPT SENSITIVE USERDATA NO MATTER WHAT NETWORK YOU USE. FUCKING KILL ME ALREADY.
Not implementing encryption is one thing but then acting like its no problem is a fucking nother one. Why do people not understand that security of userdata is important???11 -
I just released a tiny game for iPhone!
It's basically an attempt to mix 'Heroes of Might & Magic' and mtg.
In the screenshot my terminal says 'helloworld.cpp'. That's right, this is my first c++ program and I don't care how crappy you think this game is, I'm super proud of myself!
I've always worked in data science where managers assume I know how to code because there's text on my screen and I can query and wrangle data, but I actually didn't know what a class was until like 3 years into my job.
Making this game was my attempt to really evolve myself away from just statistics / data transforms into actual programming. It took me forever but I'm really happy I did it
It was brutal at first using C++ instead of R/Python that data science people usually use, but now I start to wonder why it isn't more popular. Everything is so insanely fast. You really get a better idea of what your computer is actually doing instead of just standing on engineers' shoulders. It's great.
After the game was 90% finished (LOL) I started using Swift and Spritekit to get the visuals on the screen and working on iPhone. That was less fun. I didn't understand how to use xCode at all or how to keep writing tests, so I stopped doing TDD because I was '90% done anyway' and 'surely I'll figure out how to do basic debugging'. I'll know better next time...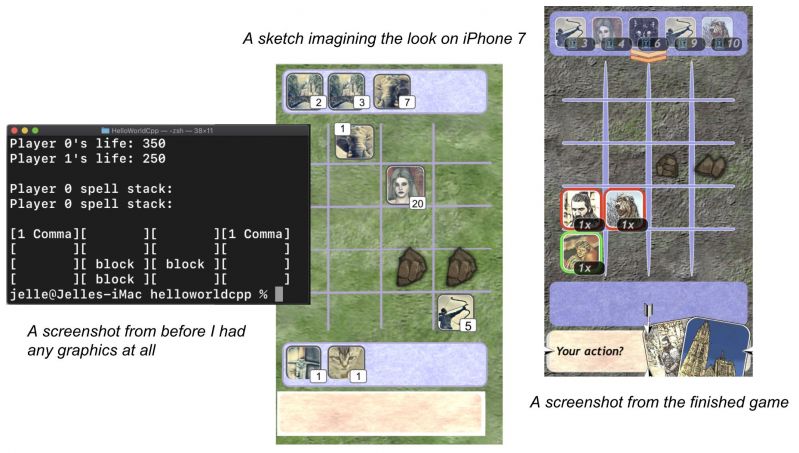 22
22 -
Today a colleague was making weird noises because he was modifying some data files where half of the data needed to be updated with a name field, there were 4 files all about 1200 lines big.
I asked how he was doing and he said he was ready to kill himself, after he explained why I asked why he was doing if manually. He said he normally uses regex for it but he couldnt do this with a regex.
I opened VS code for him, used the multiselect thing (CTRL+D) and changed one of the files in about 2 minutes. Something he was working on for over half an hour already.... He thanked me about a million times for explaining it to him.
If you ever find yourself in a position where you have a tedious task which takes hours, please ask if somebody knows a way of doing it quicker. Doing something in 2 minutes is quite a bit cheaper and better for your mental state than doing the same thing manually In 3 hours (our estimate)4 -
"Thank you for choosing Microsoft!"
No Microsoft, I really didn't choose you. This crappy hardware made you the inevitable, not a choice.
And like hell do I want to run your crappy shit OS. I tried to reset my PC, got all my programs removed (because that's obviously where the errors are, not the OS, right? Certified motherfuckers). Yet the shit still didn't get resolved even after a reset. Installing Windows freshly again, because "I chose this".
Give me a break, Microshaft. If it wasn't for your crappy OS, I would've gone to sleep hours ago. Yet me disabling your shitty telemetry brought this shit upon me, by disabling me to get Insider updates just because I added a registry key and disabled a service. Just how much are you going to force data collection out of your "nothing to hide, nothing to fear" users, Microsoft?
Honestly, at this point I think that Microsoft under Ballmer might've been better. Because while Linux was apparently cancer back then, at least this shitty data collection for "a free OS" wasn't yet a thing back then.
My mother still runs Vista, an OS that has since a few months ago reached EOL. Last time she visited me I recommended her to switch to Windows 7, because it looks the same but is better in terms of performance and is still supported. She refused, because it might damage her configurations. Granted, that's probably full of malware but at this point I'm glad she did.
Even Windows 7 has telemetry forcibly enabled at this point. Vista may be unsupported, but at least it didn't fall victim to the current status quo - data mining on every Microshaft OS that's still supported.
Microsoft may have been shady ever since they pursued manufacturers into defaulting to their OS, and GPU manufacturers will probably also have been lobbied into supporting Windows exclusively. But this data mining shit? Not even the Ballmer era was as horrible as this. My mother may not realize it, but she unknowingly avoided it.6 -
"Big data" and "machine learning" are such big buzz words. Employers be like "we want this! Can you use this?" but they give you shitty, ancient PC's and messy MESSY data. Oh? You want to know why it's taken me five weeks to clean data and run ML algorithms? Have you seen how bad your data is? Are you aware of the lack of standardisation? DO YOU KNOW HOW MANY PEOPLE HAVE MISSPELLED "information"?!!! I DIDN'T EVEN KNOW THERE WERE MORE THAN 15 WAYS OF MISSPELLING IT!!! I HAD TO MAKE MY OWN GODDAMN DICTIONARY!!! YOU EVER FELT THE PAIN OF TRAINING A CLASSIFIER FOR 4 DAYS STRAIGHT THEN YOUR GODDAMN DEVICE CRASHES LOSING ALL YOUR TRAINED MODELS?!!
*cries*7 -
So I've been reading a lot about this #deletefacebook trend across devrant lately. And frankly I'm a little concerned.
As per my understanding, everyone wants to delete Facebook because they're harvesting data. Learning more about us.
While I would agree that I want my privacy. I am a little surprised at how fast this trend is picking up. People are turning a blind eye on everything else they do online just to assume they have privacy.
Let's put this Into perspective, shall we?
You are afraid of letting Facebook harvest your data yet you watch videos on YouTube which is owned by Google. You may even proceed to removing your Google account and use a stripped down version of Chromium to protect yourself from these companies yet you're using a Windows, Mac, iPhone, or Android all of which may be harvesting your data behind the scenes. Some may argue that they have stripped down their android phones but don't take into consideration that you are still using apps on your phone that may be collecting your data.
Let's say that you manage to get out of every sort of technology, you should remember that companies like Facebook also check data about you through your friends.
You use platforms like DuckduckGo assuming that they might not be collecting data about you in some way. I don't think there is anyway for you to prove that these privacy companies don't collect our data.
I don't know why everyone seems to be interested in this trend. I absolutely don't see a point in it. If anything, things I see are super relevant to me.13 -
--- UK Mobile carrier O2's data network vanishes like a fart in the wind ---
One of the largest mobile carriers in the UK; O2 has been having all manner of weird and wonderful problems this morning as bleary eyed susbcribers awoke to find their data services unavailable. What makes this particular outage interesting (more so than the annoyingly frequent wobblers some mobile masts have) is that the majority of the UK seems to be affected.
To further compound the hilarity/disaster (depending on which side of the fence you're on), Many smaller independent carriers such as GiffGaff and Tesco Mobile piggy-back off O2's network, meaning they're up the stinky creek without a paddle as well. Formal advice from the gaseous carrier is to reboot your device frequently to force a reconnect attempt, Which we're absolutely sure won't cause any issues at all with millions of devices screaming at the same network when it comes back up.
Issue reports began flooding DownDetector at around 5am (GMT), With PR minions formally acknowledging the issue 2 hours later at 7am (GMT) via the most official channel available - Twitter. After a few recent updates via the grapevine (companies involved seems to be keeping their heads down at the minute) Ericsson has been fingered for pushing out a wonky software update but there's been no official confirmation of this, so pitchforks away please folks.
If you're in need of a giggle while you wait for your 4G goodness to return, You can always hop on an open WiFi network and read the tales of distress the data-less masses are screaming into the void.3 -
Client: How's our B2B data lookup platform coming along?
Me: All done, your clients can now search by first/last name as well.
Client: I just search "fuck" as first name and 5 results came up, our data is not cleaned up properly.
Me: Fuck
Client: Fuck2 -
Microshaft!!!
NO I DON'T WANT TO GIVE UP ALL MY DATA JUST TO GET AN EXPLORER DARK THEME!!!
YES I DISABLED TELEMETRY PARTIALLY!!
YES I STILL WANT TO RECEIVE UPDATES REGARDLESS OF WHETHER I EXPRESS MY DESIRES TO NOT BE TRACKED IN FULL!!!
NO I REALLY DON'T WANT TO HEAR SHIT ABOUT "THIS FUCKING QUESTION HAS BEEN ANSWERED SOMEWHERE ELSE"!!!
(https://answers.microsoft.com/en-us... - certified Microshit MOTHERFUCKERS!!!!!)
AND NO I DON'T WANT TO HEAR FROM YOU THAT AFTER RE-ENABLING TELEMETRY THAT MY PRIVACY SETTINGS ARE STILL TOO LOW!!! AND CERTAINLY I DON'T WANT TO SEE YOUR WORTHLESS "FIX ME" SHIT UNABLE TO FIX JACK SHIT!!!
AND LIKE FUCKING HELL DO I WANT TO REINSTALL WANBLOWS, FUCKING KEEP MY SHITTY FILES THAT ARE FUCKING BACKED UP BUT LOSE ALL MY CUSTOM CONFIGURATIONS!!! LIKE FUCKING HELL!!! NOT BECAUSE YOU CAN'T FIX YOUR OWN BLOODY SYSTEM AFTER I DID MY PART TO GIVE MY DATA TO THE SHAFTLORDS AGAIN!!!
FUCK YOU MICROSOFT!!!!23 -
I would like to invite you all to test the project that a friend and me has been working on for a few months.
We aim to offer a fair, cheap and trusty alternative to proprietary services that perform data mining and sells information about you to other companies/entities.
Our goal is that users can (if they want) remain anonymous against us - because we are not interested in knowing who you are and what you do, like or want.
We also aim to offer a unique payment system that is fair, good and guarantees your intergrity by offer the ability to pay for the previous month not for the next month, by doing that you do not have to pay for a service that you does not really like.
Please note that this is still Free Beta, and we need your valuable experience about the service and how we can improve it. We have no ETA when we will launch the full service, but with your help we can make that process faster.
With this service, we do want to offer the following for now:
Nextcloud with 50 GB storage, yes you can mount it as a drive in Linux :)
Calendar
Email Client that you can connect to your email service (
SearX Instance
Talk ( voice and video chat )
Mirror for various linux distros
We are using free software for our environment - KVM + CEPH on our own hardware in our own facility. That means that we have complete control over the hosting and combined with one of the best ISP in the world - Bahnhof - we believe that we can offer something unique and/or be a compliment to your current services if you want to have more control over your data.
Register at:
https://operationtulip.com
Feel free to user our mirror:
https://mirror.operationtulip.com
Please send your feedback to:
feedback@operationtulip.com38 -
True story.
Some clients (especially in India) don't want to pay, but they want everything to be implemented in the project.
Big data.... Check
Machine learning.... Check
Deep learning..... Check
Espresso maker.... Check.
They want all the buzz words that are buzzing to be put in your project and they want you to put it in the 'cloud', for which you have to pay.....10 -
9 days.
9 fucking days without internet.
9 fucked up days with access to a national intranet with the only accessible things being websites with privacy-respect policy of facebook, with all your unencrypted data streaming under dictator hands.6 -
Just managed to setup a tiny/simple privacy-friendly analytics system.
You basically call an api from your backend with the api key and all the headers you received from the browser (php and Apache or nginx in my case) and the analytics api gets useful stuff out of that data without sacrificing privacy.
I get a little bit more insight into my websites usage and the client isn't sacrificing identifiable information!
I've been wanting to make this fucker for fucking months.11 -
So my in-laws got a new computer 😑
Yup you know where this is going. Ok so after I transferred all of their data set them all up etc.
They wanted to use "word" and could I set it up for free for them. I said no Microsoft office is not free you lost your license and disk and your old computer is trashed so the better choice would be Google services . So I explained the value of using Google drive, docs,sheets etc.. today and told them how much better it is everything would be on their Google drive so if I got hit by a bus they could get a new computer again and still have access to their data etc... So they said great and so I did.
Two weeks later... Can you set up word for us on our computer. Me annoyed at this point " sure no problem"
I made a shortcut on their desktop to Google docs. Them: oh boy this is great see John all you have to do is click on google docs to go to word! Thanks so much!
🤫🤓5 -
Why even bother with article sites now? Try to search for a quick answer to a question and the only resource is some article and the user is met with:
- "Hi, here's where all your data goes. Please unsubscribe from our 937 partners and continue."
- "DO YOU KNOW WE USE COOKIES?" (Covers 60% of the page).
- "It looks like you're using adblocker. Mind whitelisting us for the 2 minutes we're in your life for? "
- "Before we show you the single sentence answer you're looking for let us promote our shitty content that you'll never click on because we hired the guy who makes shady porn links on every z-list site possible."
- "This article is in multiple parts to spread ad revenue. Click next to continue."
There's probably an extension that stops most of this but christ, it shouldn't be this bad.7 -
If you ever wondered how to get all the data from your database in reverse order, chatGPT is here to help.
 26
26 -
When you forget you're using your hotspot and not the WiFi and burn through all 7GB of your mobile data...4
-
My dream was shattered!!
I joined a new company. I graduated last 2 months before and joined as data analyst.
So I was dreaming to work on some awesome research projects and all, but it was just another dream...people here don't work on any sort of data analytics instead the data science team uses regex and all to extract things and say they are building models.
Ahh...wtf!!!
Many co-workers are good and help me, but the boss. He left all the annoying works to me and the release is in next month...
"BRUH I JUST JOINED YOUR COMPANY!!!"
Then after some days he gave me more task, when he found that one task was super easy(i mean it was just to extract things using bs4 and selenium, hardly will take an hour) to do then he took that himself and in the next meeting said he did that work and it was super difficult!!!
Data science here to senior members is just for loop!! I dont even know why I joined this firm
Ahhh!!! I want to scream!!! 11
11 -
Can someone explain to me why the fuck I should even care about the fact, that some companies collect, use and sell my data? I'm not famous, I'm not a politician and I'm not a criminal, I think most of us aren't and won't ever be. We aren't important. So what is this whole bullshittery all about? I seriously don't get it and I find it somewhat weird that especially tech guys and IT "experts" in the media constantly just make up these overly creepy scenarios about big unsafe data collecting companies "stealing" your "private" information. Welcome to the internet, now get the fuck over it or just don't be online. It's your choice, not their's.
I honestly think, some of these "security" companies and "experts" are just making this whole thing bigger than it actually is, because it's a damn good selling point. You can tell people that your app is safe and they'll believe you and buy your shit app because they don't understand and don't care what "safe" or "unsafe" means in this context. They just want to be secure against these "evil monster" companies. The same companies, which you portrayed them as "evil" and "unfair" and "mean" and "unrepentant" for over a decade now.
Just stop it now. All your crappy new "secure" messenger apps have failed awesomely. Delete your life now, please. This isn't about net neutrality or safety on the internet. This is all about you, permanently exaggerating about security and permanently training people to be introverted paranoid egoistic shit people so that they buy your elitist bullshit software.
Sorry for my low english skills, but please stop to exist, thank you.64 -
SWIFT!!!!! I understand that you're a relatively new language so I forgave you for all of your wrong doings..BUT WHAT THE FINGER IS THIS SHIT YOU HAVE IMPLEMENTED IN YOUR STRING DATATYPE? WHY THE FUCK CAN'T YOU FORM A CHARACTER FROM AN EMPTY STRING? AND WHAT THE ACTUAL FUCK HAPPENED TO THE SUBSCRIPT OPERATOR? WHY NOT JUST ADOPT THE "\0" AS OTHER LANGUAGES? But NOOOOO...We're Apple we'll not adopt it..I WAS UNDER THE IMPRESSION THAT STUPIDITY AND LUCK OF INNOVATION RAN IN THE IPHONE TEAM BUT APPARENTLY ITS EVERYWHERE..Its annoying because the String datatype is one of the most common and basic data types so the last thing you expect is this shit..APPLE........SERIOUSLY AND SINCERELY FUCK OFF4
-
So my friend was in a hurry when she was setting up the passocde for her phone and later she forgot the code.
So she takes it to the service center.
SC guy: Ma'am we have to do bla bla bla. And you will lose your data. It will cost you around $10.
She just came back and later gave me the phone.
*unlocks bootloader *
*flashes a custom recovery*
*delete passcode file*
Phone is now unlocked with all the data intact.
PS: I got a small treat at McDonald's. 😋6 -
[Dark Rant]
I'm sick of this stupid tech world.
Don't get me wrong, I love tech. I just can't stand anymore the global brainwashing that we're part of.
Think about all the huge companies making profit on our data. For a better service, yeah sure, but do we really understand what the cost is?
Ok sure, you don't care about your data because you trust these companies and the advantages are all worth it. What about the fact that we are all forced to buy the next new smartphone after 2 years?
Like if removable batteries were a problem for us, users. Or like the audio jack. Because now someone decided that the pricey wireless headphones are Just What You Need™.
Do you think you own your smartphone?
No, you don't. You are paying a bunch of money for something that soon will be just a useless brick of glass and metal which you can't repair. But you'll be happy anyway.
Someone is so happy to the point that they will defend their favorite company, doesn't matter how they decided to stick it into their ass.
Open your eyes, you've been brainwashed.25 -
Ten Immutable Laws Of Security
Law #1: If a bad guy can persuade you to run his program on your computer, it's not solely your computer anymore.
Law #2: If a bad guy can alter the operating system on your computer, it's not your computer anymore.
Law #3: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore.
Law #4: If you allow a bad guy to run active content in your website, it's not your website any more.
Law #5: Weak passwords trump strong security.
Law #6: A computer is only as secure as the administrator is trustworthy.
Law #7: Encrypted data is only as secure as its decryption key.
Law #8: An out-of-date antimalware scanner is only marginally better than no scanner at all.
Law #9: Absolute anonymity isn't practically achievable, online or offline.
Law #10: Technology is not a panacea.3 -
So, I was gonna rant about how it can be difficult to design event-based Microservices.
I was gonna say some shit about gateways APIs and some other stuff about data aggregation and keeping things idempotent.
I was going to do all this but then as I was stretching out the old ranting fingers I decided to draw a diagram to maybe go along with the rant.
Now I’m not here to really rant about all that Jazz...
I’m here to give you all a first class opportunity to tear apart my architecture!
A few things to note:
Using a gateway API (Kong) to separate the mobile from the desktop.
This traffic is directed through to an in intermediate API. This way the same microservices can provide different data, and even functionality for each device.
Most Microservices currently built in golang.
All services are event based, and all data is built on-the-fly by events generated and handled by each Microservices.
RabbitMQ used as a message broker.
And finally, it is hosted in Google Cloud Platform.
The currently hosted form is built with Microservices but this will be the update version of things.
So, feel free to rip it apart or add anything you think should change.
Also, feel free to tell me to fuck right off if that’s your cup of tea as well.
Peace ✌🏼 19
19 -
I just launched a small web service/app. I know this looks like a promo thing, but it's completely non-profit, open source and I'm only in it for the experience. So...
Introducing: https://gol.li
All this little app offers is a personal micro site that lists all your social network profiles. Basically share one link for all your different profiles. And yes, it includes DevRant of course. :)
There's also an iframe template for easy integration into other web apps and for the devs there's a super simple REST GET endpoint for inclusion of the data in your own apps.
The whole thing is on GitHub and I'd be more than happy for any kind of contribution. I'm looking forward to adding features like more personalization, optimizing stuff and fixing things. Also any suggestions on services you'd like see. Pretty much anything that involves a public profile goes.
I know this isn't exactly world changing, but it's just a thing I wanted to do for some time now, getting my own little app out there.9 -
In case anyone missed it, you probably shouldn't be using tiktok. That said, anyone surprised by this behavior is likely generally unaware of how monetization works on social media so carry on.
https://boredpanda.com/tik-tok-reve...9 -
What’s the difference between USB and USA?
The first one is used to transfer files from one device to another, while the other is used to transfer all your device’s data2 -
@netikras since when does proprietary mean bad?
Lemme tell you 3 stories.
CISCO AnyConnect:
- come in to the office
- use internal resources (company newsletter, jira, etc.)
- connect to client's VPN using Cisco AnyConnect
- lose access to my company resources, because AnyConnect overwrites routing table (rather normal for VPN clients)
- issue a route command updating routing table so you could reach confluence page in the intranet
- route command executes successfully, `route -n` shows nothing has changed
- google this whole WTF case
- Cisco AnyConnect constantly overwrites OS routing table to ENFORCE you to use VPN settings and nothing else.
Sooo basically if you want to check your company's email, you have to disconnect from client's VPN, check email and reconnect again. Neat!
Can be easily resolved by using opensource VPN client -- openconnect
CISCO AnyConnect:
- get a server in your company
- connect it to client's VPN and keep the VPN running for data sync. VPN has to be UP at all times
- network glitch [uh-oh]
- VPN is no longer working, AnyConnect still believes everything is peachy. No reconnect attempts.
- service is unable to sync data w/ client's systems. Data gets outdated and eventually corrupted
OpenConnect (OSS alternative to AnyConnect) detects all network glitches, reports them to the log and attempts reconnect immediatelly. Subsequent reconnect attempts getting triggered with longer delays to not to spam network.
SYMANTEC VIP (alleged 2FA?):
- client's portal requires Sym VIP otp code to log in
- open up a browser in your laptop
- navigate to the portal
- enter your credentials
- click on a Sym VIP icon in the systray
- write down the shown otp number
- log in
umm... in what fucking way is that a secure 2FA? Everything is IN the same fucking device, a single click away.
Can be easily solved by opensource alternatives to Sym VIP app: they make HTTP calls to Symantec to register a new token and return you the whole totp url. You can convert that url to a qr code and scan it w/ your phone (e.g. Google's Authenticator). Now you have a true 2FA.
Proprietary is not always bad. There are good propr sw too. But the ones that are core to your BAU and are doing shit -- well these ARE bad. and w/o an oppurtunity to workaround/fix it yourself.13 -
When I saw that the Zuckman was gonna go testify for congress I already knew that shit was gonna be retarded.
I had 0 expectations of congress asking the correct questions.
I was still disappointed. That is the beauty of my government. I have 0 expectations and they still disappoint me.
I love playing the devil's advocate. I really do, in this case and even tho I think Facebook is the most toxic shit on the internet (right next to SO) I could not help it but think the entire time that we aaaare told that all our date are belongs to them as soon as we put shit on their application. Its just the nature of the beast. Don't like it? Don't use it! But if you are gonna use it then account for the fact that your data will be used for targeted adds. It makes more sense, I would rather have an add for tutorials and books and shit like i normally get rather than knowing that 10 hot singles are in my area (because those are all lies 9 times out of 10) but then again I would rather not have any adds at all.
One has to account for all the money that fb pours into shit, where do people think fb makes that money from ..duh our data and adds. But shit was too hard to understand for Congress.8 -
Small random update regarding my ISP and how they call your speed if you use all of your data.
I actually sent them a small complaint (more of a suggestion but) that 256 Kbps is just too slow even for a capped penalty speed and that at least 1 Mbps so that the internet is still usable but still slow... And mother fucker if that isn't exactly what they did!
It's nice being able to sync my code and have more than 1 device connected to the wifi at once... It's a strange feeling when a company actually listens to feedback and takes measures on them...5 -
My code review nightmare?
All of the reviews that consisted of a group of devs+managers in a conference room and a big screen micro-analyzing every line of code.
"Why did you call the variable that? Wouldn't be be more efficient to use XYZ components? You should switch everything to use ServiceBus."
and/or using the 18+ page coding standard document as a weapon.
PHB:"On page 5, paragraph 9, sub-section A-123, the standards dictate to select all the necessary data from the database. Your query is only selecting 5 fields from the 15 field field table. You might need to access more data in the future and this approach reduces the amount of code change."
Me: "Um, if the data requirements change, wouldn't we have change code anyway?"
PHB: "Application requirements are determined by our users, not you. That's why we have standards."
Me: "Um, that's not what I ..."
PHB: "Next file, oh boy, this one is a mess. On page 9, paragraph 2, sub-section Z-987, the standards dictate to only select the absolute minimum amount of the data from the database. Your query is selecting 3 fields, but the application is only using 2."
Me: "Yes, the application not using the field right now, but the user stated they might need the data for additional review."
PHB: "Did they fill out the proper change request form?"
Me: "No, they ...wait...Aren't the standards on page 9 contradictory to the standards on page 5?"
PHB: "NO! You'll never break your cowboy-coding mindset if you continue to violate standards. You see, standards are our promise to customers to ensure quality. You don't want to break our promises...do you?"7 -
A lot of brainwashed people dont care about privacy at all and always say: "Ive got nothing to hide, fuck off...". But that is not true. Any information can be used aginst you in the future when "authorities" will release some kind of Chinas social credit system. Stop selling your data for free to big companies.
https://medium.com/s/story/...6 -
I just tried to sign up to Instagram. I made a big mistake.
First up with Facebook related stuff is data. Data, data and more data. Initially when you sign up (with a new account, not login with Facebook) you're asked your real name, email address and phone number. And finally the username you'd like to have on the service. I gave them a phone number that I actually own, that is in my iPhone, my daily driver right now (and yes I have 3 Androids which all run custom ROMs, hold your keyboards). The email address is a usual for me, instagram at my domain. I am a postmaster after all, and my mail server is a catch-all one. For a setup like that, this is perfectly reasonable. And here it's no different, devrant at my domain. On Facebook even, I use fb at my domain. I'm sure you're starting to see a pattern here. And on Facebook the username, real name and email domain are actually the same.
So I signed up, with - as far as I'm aware - perfectly valid data. I submitted the data and was told that someone at Instagram will review the data within 24 hours. That's already pretty dystopian to me. It is now how you block bots. It is not how Facebook does it either, at least since last time I checked. But whatever. You'd imagine that regardless of the result, they'd let you know. Cool, you're in, or sorry, you're rejected and here's why. Nope.
Fast-forward to today when I recalled that I wanted to sign up to Instagram to see my girlfriend's pictures. So I opened Chromium again that I already use only for the rancid Facebook shit.. and it was rejected. Apparently the mere act of signing up is a Terms of Service violation. I have read them. I do not know which section I have violated with the heinous act of signing up. But I do have a hunch.
Many times now have I been told by ignorant organizations that I would be "stealing" their intellectual property, or business assets or whatever, just because I sent them an email from their name on my domain. It is fucking retarded. That is MY domain, not yours. Learn how email works before you go educate a postmaster. Always funny to tell them how that works. But I think that in this case, that is what happened.
So I appealed it, using a random link to something on Instagram's help section from a third-party blog. You know it's good when the third-party random blog is better. But I found the form and filled it in. Same shit all over again for info, prefilling be damned I guess. Minor convenience though, whatever.
I get sent an email in German, because apparently browsing through a VPS in Germany acting as a VPN means you're German. Whatever... After translating it, I found that it asks me to upload a picture of myself, holding a paper in my hands, on which I would have a confirmation code, my username, and my email address.. all hand-written. It must not be too dark, it must be clear, it must be in JPEG.. look, I just wanted to fucking sign up.
I sent them an email back asking them to fix all of this. While I was writing it and this rant, I thought to myself that they can shove that piece of paper up their ass. In fact I would gladly do it for them.
Long story short, do not use Instagram. And one final thing I have gripes with every time. You are not being told all the data you'll have to present from the get-go. You're not being told the process. Initially I thought it'd just be email, phone, username, and real name. Once signed up (instantly, not within 24 hours!) I would start setting up my account and adding a profile picture. The right way to ask for a picture of me! And just do it at my own pace, as I please.
And for God's sake, tackle abuse when it actually happens. You'll find out who's a bot and who isn't by their usage patterns soon enough. Do not do any of this at sign-up. Or hell, use a CAPTCHA or whatever, I don't fucking care. There's so many millions of ways to skin this cat.
Facebook and especially Instagram. Both of them are fucking retarded.6 -
fucking piece of garbage postman!
WHY THE HELL do you auto-update yourself when i explicitly DISABLED updates?
why the hell is it just a "minor" update to switch to a version that FORCES you to have an account, even if all you do is use offline features?
and why is there no option to disable syncing your data to their server, even if it's not needed at all? YALL EVER HEARD OF A THING CALLED PRIVACY?
and why the fucking fuck of all fucked fucks DO YOU DELETE MY PREVIOUS OFFLINE DATA SO I CAN'T EVEN CONTINUE WORKING BY INSTALLING AN OLDER VERSION?!?
some dumb-piece-of-garbage-waste-of-oxygen managers decision to screw their userbase cost me several HOURS(!) of work already and probably will cost some more due to the lost collections.10 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
It is a sincere request to all the people who are asking for a backup of their files and documents, to please stop pestering us regarding the same.
We can't possibly collect your data, and even if there's a way, it would be nearly impossible for us to find your data from billions and billions of files and directories.
Citizens are requested to please understand our problems.
Have a nice day :)4 -
I used to do audits for private companies with a team. Most of them where black box audits and we were allowed to physically manipulate certain machines in and around the building, as long as we could get to them unnoticed.
Usually when doing such jobs, you get a contract signed by the CEO or the head of security stating that if you're caught, and your actions were within the scope of the audit, no legal action will be taken against you.
There was this one time a company hired us to test their badge system, and our main objective was to scrape the data on the smartcards with a skimmer on the scanner at the front of the building.
It's easy to get to as it's outside and almost everyone has to scan their card there in order to enter the building. They used ISO 7816 cards so we didn't even really need specified tools or hardware.
Now, we get assigned this task. Seems easy enough. We receive the "Stay-out-of-jail"-contract signed by the CEO for Company xyz. We head to the address stated on the contract, place the skimmer etc etc all good.
One of our team gets caught fetching the data from the skimmer a week later (it had to be physically removed). Turns out: wrong Building, wrong company. This was a kind of "building park" (don't really know how to say it in English) where all the buildings looked very similar. The only difference between them was the streetnumber, painted on them in big. They gave us the wrong address.
I still have nightmares about this from time to time. In the end, because the collected data was never used and we could somewhat justify our actions because we had that contract and we had the calls and mails with the CEO of xyz. It never came to a lawsuit. We were, and still are pretty sure though that the CEO of xyz himself was very interesed in the data of that other company and sent us out to the wrong building on purpose.
I don't really know what his plan after that would have been though. We don't just give the data to anyone. We show them how they can protect it better and then we erase everything. They don't actually get to see the data.
I quit doing audits some time ago. It's very stressful and I felt like I either had no spare time at all (when having an active assignment) or had nothing but spare time (when not on an assignment). The pay also wasn't that great.
But some people just really are polished turds.4 -
Okay, That right there is pathetic https://thehackernews.com/2019/02/... .
First of all telekom was not able to assure their clients' safety so that some Joe would not access them.
Second of all after a friendly warning and pointing a finger to the exact problem telekom booted the guy out.
Thirdly telekom took a defensive position claiming "naah, we're all good, we don't need security. We'll just report any breaches to police hence no data will be leaked not altered" which I can't decide whether is moronic or idiotic.
Come on boys and girls... If some chap offers a friendly hand by pointing where you've made a mistake - fix the mistake, Not the boy. And for fucks sake, say THANK YOU to the good lad. He could use his findings for his own benefit, to destroy your service or even worse -- sell that knowledge on black market where fuck knows what these twisted minds could have done with it. Instead he came to your door saying "Hey folks, I think you could do better here and there. I am your customes and I'd love you to fix those bugzies, 'ciz I'd like to feel my data is safe with you".
How on earth could corporations be that shortsighted... Behaviour like this is an immediate red flag for me, shouting out loud "we are not safe, do not have any business with us unless you want your data to be leaked or secretly altered".
Yeah, I know, computer misuse act, etc. But there are people who do not give a tiny rat's ass about rules and laws and will find a way to do what they do without a trace back to them. Bad boys with bad intentions and black hoodies behind TOR will not be punished. The good guys, on the other hand, will.
Whre's the fucking logic in that...
P.S. It made me think... why wouldn't they want any security vulns reported to them? Why would they prefer to keep it unsafe? Is it intentional? For some special "clients"? Gosh that stinks6 -
Windows: Would you like me to give all your data to MS or somewhat less data?
Me: Well .. I guess .. I'll choose the Basic option..
Windows: Here is a fun fact .. I'll send all the data regardless of your choice :)
This is what's happening in the background, I think. I mean there isn't even a phuqing option to turn this thing off. 19
19 -
iPhones are ridiculously picky when it comes to finding a mate- um charger. And knowing why doesn't really make it any easier to understand why. If anything it baffles me more.
So, let's start with appliances that are not phones. Think Bluetooth headsets, keyboards, earbuds, whatever. Those are simple devices. They see 5V on the VCC line and 0V on ground, and they will charge at whatever current they are meant to. Usually it will not exceed 200mA, and the USB 2.0 spec allows for up to 500mA from any USB outlet. So that's perfectly reasonable to be done without any fuss whatsoever.
Phones on the other hand are smarter.. some might say too smart for their own good. In this case I will only cover Android phones, because while they are smarter than they perhaps should be, they are still reasonable.
So if you connect an Android phone to the same 5V VCC and 0V ground, while leaving the data lines floating, the phone will charge at 500mA. This is exactly to be within USB 2.0 spec, as mentioned earlier. Without the data lines, the phone has no way to tell whether it *can* pull more, without *actually* trying to pull more (potentially frying a charger that's not rated for it). Now in an Android phone you can tell it to pull more, in a fairly straightforward way. You just short the data lines together, and the phone will recognize this as a simple charger that it can pull 1A from. Note that shorting data lines is not a bad thing, we do it all the time. It is just another term for making a connection between 2 points. Android does this right. Also note that shorted data lines cannot be used to send data. They are inherently pulled to the same voltage level, probably 0V but not sure.
And then the iPhones come in, Thinking Different. The iPhones require you to pull the data lines to some very specific voltage levels. And of course it's terribly documented because iSheep just trying to use their Apple original white nugget charger overseas and shit like that. I do not know which voltage levels they are (please let me know!), but it is certainly not a regular short. Now you connect the iPhone to, say, a laptop or something to charge. An Android phone would just charge while keeping data transmission disabled (because they can be left floating or shorted). This is for security reasons mostly, preventing e.g. a malicious computer from messing with it. An iPhone needs to be unlocked to just charge the damn thing. I'm fairly sure that that's because the data lines need to be pulled up, which could in theory enable a malicious computer to still get some information in or out of it. USB data transmission works at at least 200mV difference between the data lines. It could be more than that. So you need to unlock it.
Apple, how about you just short your goddamn data lines too like everyone else? And while you're at it, get rid of this Lightning connector. I get it, micro USB was too hard for your users. I guess they are blind pigs after all. But USB-C solved all of that and more. The only difference I can think of is that the Lightning connector can be a single board with pads on either side on the connector, while in USB-C that could be at the socket end (socket being less common to be replaced). And at the end of the day, that really doesn't matter with all the other things that will break first.
Think Different. Think Retarded. Such tiny batteries and you can't even fucking charge them properly.6 -
Client : I am unable to download data from your sever for last 10 days.
Me : Sir, we are sorry to hear that. We are doing some maintenances on our server from this morning today. We request you to call back us in next 4 hours.
Client : But i am facing this problem for last 10 days.
Me: Sir, i heard you. As maintenance is going on it will not be possible to download data this time.
Client: From when this maintenance is going on?
Me: from this morning sir.
Client : but i am facing this probolem for last 10 days.
Me: Sir, you are not understanding it, or may be i am failing to describe the situation to you...
Client: Listen, you guys are incapable. Only knows to make excuse.
Me: Sir..
Client: Sorry to say, i am not Happy with your support. Let me talk to your senior tech guy.
Me : Sir, your problem will be solved in next 4 hours. We will call you as soon as our server went online.
Client: *.....*
It took me 20 minutes to finally make him understand the situation.
Client: Why did not you said that earlier? You guys will have all the time but i do not. Anyway.
He hangs the phone.
My ears are burning man...9 -
Client : We have performance issues on <this> page.
US : Testing with their data on : Xeon : All good, Core i7 : all good, Core i5 : all good, A smartphone : all good, core i5 UM version from 5 years ago (You know, 1.8Ghz, 2 cores, not 4) : all good.
US : Could you share your screen and show us ?
Client : Sure ! Shares his screen. Chrome is already opened. Refreshes the page, after 15 seconds, chrome : Would you like to stop script on this page ?”
US with mic on mute : “WTF?! It cannot happen here. It’s only a list of about 500 rows!”.
US : “Hello, could you open a tasks manager?”
Client : “ Sure, but I need to do it through here”
Some random VID interface popping up. Opens tasks manager with a beautiful “48 vCPUs detected”.
I have no idea how their virtualization is settled, but it seems to be messed up. Tomorrow going to be fun. I have a call at 9am to explain them their problem. Their IT will hate me forever.
If anyone has tips on Chrome through virtualization, please tell me.
EDIT : Yes 48. Not 4-8. It's not an error6 -
R is the worst language.
* Indices start at 1, so you have to fix all your calculations by either +1 oder -1. It sucks
* Vectors and Lists are both neither vectors nor lists
* Data frames dont have a proper api. Simple operations like add or remove are a pain.
* The naming „conventions“ suck. Why on earth would add dots in your identifiers? You never know if its an object, a value, a function.
* The namespace is cluttered. If you import two libraries that deal with the same problem domain, it is likely that they define functions with clashing names that will overwrite each other defined on import.5 -
Hey! How do I do machine learning?
Well first you start off with a metric shit ton of data.
And then you .fit() your data
from there you can .predict() your data
Trust me, the algorithms are already there. All you need to do is get the data.7 -
So... After reading up on the theoretical stuff earlier, I decided to make a real AI that can identify handguns and decide whether it's a revolver or a semiautomatic with 95 percent accuracy...
Well, basically, I been browsing my local gun store's online store for four hours for training data, killed a Mac mini while first training the system and I think I ended on the domestic terrorism watch list... Was that black sedan always there?
Anyway... It's working fairly accurate, my monkey wrench is a revolver by the way.
Isn't AI development a wonderful excuse for all kinds of shit?
"why do you have 5000 pictures of guns on your computer?" - "AI development"
"why did you wave around a gun in front of your web cam" - "AI development"
"why is there a 50 gram bag in your desk?" - "AI development"
Hmm... yeah well... I think it might work. I could have picked a less weird testing project, but... No.7 -
Interviewer = I, Me = M
I: What is your project all about?
M: It is about reading data from memory of a program and transfer it to output register via a dedicated bus attached inside CPU and then projecting data of registers onto LCD crystals of display.
I: Can you show the working of your project?
M: Runs "hello world" program
Me - 1, Interviewer - Slap on my cheeks with shoe in one hand.3 -
So... Intense pillowtalk with the wife the other night regarding the coming enforcement of the new General Data Protection Regulation (GDPR) law in the EU after a while turns into nerdy dirty talk.
Me: *Whisper in a sleazy voice like the dirty malware that I am*: So... Why don't you just open up all your inbound firewall ports for me...
Her: Hell no... But I might just make an exception in the private domain just for you...4 -
<supervisor>,
I would like to raise a concern of mine to your attention. I would urge you to inform <CIO> because I think he should know as well. In our recorded meeting this afternoon <bad_vendor> exposed another company’s credentials after failing to access our system, and proceeded to demo access into someone else’s system while exposing their client's sensitive data. Others noticed this as well. This is an alarming situation because not only did <bad_vendor> expose someones data to <us>, but to one of our vendors. While it is unlikely that <us> or <helpful_vendor> would abuse this situation, it could have easily been <us>’s data that was exposed to another company and their vendors had the situation been reversed. I understand we are all under tight deadlines and under a lot of stress — by no means am I trying to make waves — but nonetheless I felt compelled make light of this situation and felt in was echoed by <helpful_vendor> during the meeting as well.
Thank you8 -
For all those that saw my previous post about Facebook embedding tracking metadata into photos: I just released a website for my project that allows you to obfuscate the tracking data in your browser.
https://fbmdob.watzon.tech
Hopefully this is helpful to some people :)2 -
In my quest to find a nice dark theme file manager, I stumbled upon this thing called Q-Dir. By default it looks like it comes straight out of the 90's, but after a bit of tweaking here and there it actually turned out really nice!
If you're like me and want the dark theme before Redstone 5 finally arrives but don't want to gobble up all your data in Insiders either, this is actually a pretty solid replacement. Hopefully that'll save some poor sods from having to go through the trouble of finding the holy grail of the dark theme in file managers :)
http://softwareok.com//... 4
4 -
Why is it so hard to just build machines that work without all this ideological bullshit? Code doesn't care if politics==true. The world is scary enough without you assholes making modern life a data minefield for even the most educated experts, and taking advantage of the ignorance of everyone else. Fuck you.
I just wanna <look at web pages> without having to consider, counteract, or silently assist some fucking regime. Why is EVERYTHING this way? Everything is a back door or a data mine or a political statement? This isn't a fucking art piece! It's not your espionage tool, fucking codes in invisible ink and tiny cameras and shit everywhere! It's a <web browser>, and if it does ANYTHING besides <browse the web> that I didn't explicitly tell it to do, you better better not be the one who made it. Because if you did, you are what's wrong with the world.6 -
From Sarah Connor Chronicles, 2008: "They used to think that 12 nanometer scale was impossible. The circuits are so tiny, you're all but in the quantum realm. It's the most sophisticated processor on earth. If you could take your memories, your consciousness, everything that makes you a person, turn it into pure data, and download it onto a machine, that chip could run it."
I'm watching the DVD on a quadcore Ryzen APU that is built in 12nm, and it was already outdated when I bought it last year. I guess I better download myself to my laptop because that's a 7nm Ryzen.14 -
This rant has been one that I've been wanting to rant about for a while now. Me being drunk as fuck right now (mind, stay awake!) doesn't really help, but meh.
At least Wanblows was able to install its "features" properly... Except it wasn't, being the featureful ShitOS it is.
I want to rant about privacy. Not about "nothing to hide, nothing to fear". That's been ranted about plenty by the MIcroshaft-loving folks as well as the privacy-aware opposition. Rather, I'd like to rant about the privacy-concious.
I am a privacy-concious-person, with his current status quo being that he doesn't yet know a privacy-concious solution to every data-intrusive "common solution" out there. So I tend to value privacy next to De Lijn while sharing location data to Google with Google Maps. Point is, I do not know privacy-concious solutions to everything out there yet. So I use the convenient over the privacy-aware.
(after review while drunk I was unable to make sense of this)
In the privacy-aware circles I tend to see that it seems to be black and white. You share your data with Google, yet you oppose data collection by local institutes? WRONG!!! YOU MUST BE A TINFOIL HAT!!!
No, seriously I don't want to share my data with Google. Just that they're the only realtime navigation platform with decent UI out there that I know of right now.
Privacy isn't all black and white here. I block any intrusion that I'm able to, anything else I abide to, while awaiting a good alternative that does respect my privacy which I would gladly use instead. That does not imply that "I have nothing to hide". I do, and I have a lot to hide.
So that makes up the black and white nature of privacy, which is a fallacy. Another one is the whole idea of "I have nothing to hide" to begin with.
If you have nothing to hide, would you be comfortable with sharing your location data (IP address, habits, common trends, etc) with me? To share your information with me, to have your contacts share your info with me, without your consent? Of course you wouldn't. But that's what's happening right now.2 -
Really now?
AWS, #1 cloud provider with their #1 cloud database DynamoDB, all shiny, highly dynamic NoSQL, your data schema could change any second...
then DynamoDB errors out when one of your values is an empty string? {"foo":""} is impossible to store?
Like nobody ever saw or used empty strings a a value or what? There are tons of upvotes to fix this.
I just have to imagine the Product owner standing there: "No,no,no. They are just using it wrong if their data has empty strings as value. Won't fix!"4 -
"I found this tool that we should use because I'm a manager and its simple enough that my tiny little manager brain could set it up!"
Oh wow good for you, Mr. Manager! And what, praytell, does the tool require?
"All proprietary and cost-ineffecient products: MSSQL Server and Windows IIS! What do you mean we have to get the data out in order for it to be scalable? Look at it! I set up a website by clicking on an EXE i downloaded from github!"
Amazing, Mr. Manager. So you violated our security practices AND want to pocket even MORE of our budget?
Kindly fuck right off and start suggesting things instead of making people embarrass you into stoping your fight for your tool (has happened on more than one occassion).3 -
If you ever get a problem with your Linux,
DO NOT EVER try out an answer on any random forum without reading all the comments/replies.
The problem spreads like a freaking wildfire and you will end up reinstalling Linux and losing data what wasn't backed up. (If by God's grace, you do a regular back up)2 -
**Ahem**
https://google.com/search/...
"Never assume that data useless to your application is useless to all others - we are asking it different questions"
Privacy is dead because we could disseminate valuable data from crap if our lives depended on it, discarding simple key values for over analysed crap metrics every time.
Oh, and it's also screwing us over... if your keen know more about getting fucked go take a look at @linux 's rant about the matrix.org hack
- https://devrant.com/rants/2061177/... 15
15 -
SQL Rule 1. Always assume there are external processes that might affect your data. (for instance, triggers).
SQL Rule 2. In Denormalised data, never execute logic on dependant table values, always copy from the parent.
SQL Rule 3. When Denormalised data schemas are created the DBA knows what they are doing.
SQL Rule 3.1. If DBA knows what they is doing then according to Rule 1 there is no problem with adding in some triggers to maintain data clones as they are created.
SQL Rule 4. If you don't like or agree with triggers, deal with it. They are a first class tool in a first class RDBMS. In a multi-app or service environment there may be many other external processes massaging your data
SQL Rule 5. If all previous rules are not broken and the system has been running efficiently for many years DO NOT complain that there are triggers in the database that are doing and have been doing the same process that you just butchered (by violating Rule 1 and 2) in your makeshift "hello world, look what I can do from my phone" angular BS when the rest of the users are still relying on the existing runtime app.
SQL Rule 6. If you turn my triggers off, you sure as hell better turn them back on!1 -
"So Alecx, how did you solve the issues with the data provided to you by hr for <X> application?"
Said the VP of my institution in charge of my department.
"It was complex sir, I could not figure out much of the general ideas of the data schema since it came from a bunch of people not trained in I.T (HR) and as such I had to do some experiments in the data to find the relationships with the data, this brought about 4 different relations in the data, the program determined them for me based on the most common type of data, the model deemed it a "user", from that I just extracted the information that I needed, and generated the tables through Golang's gorm"
VP nodding and listening intently...."how did you make those relationships?" me "I started a simple pattern recognition module through supervised mach..." VP: Machine learning, that sounds like A.I
Me: "Yes sir, it was, but the problem was fairly easy for the schema to determ.." VP: A.I, at our institution, back in my day it was a dream to have such technology, you are the director of web tech, what is it to you to know of this?"
Me: "I just like to experiment with new stuff, it was the easiest rout to determine these things, I just felt that i should use it if I can"
VP: "This is amazing, I'll go by your office later"
Dude speaks wonders of me. The idea was simple, read through the CSV that was provided to me, have the parsing done in a notebook, make it determine the relationships in the data and spout out a bunch of JSON that I could use. Hook it up to a simple gorm golang script and generate the tables for that. Much simpler than the bullshit that we have in php. I used this to create a new database since the previous application had issues. The app will still have a php frontend and backend, but now I don't leave the parsing of the data to php, which quite frankly, php sucks for imho. The Python codebase will then create the json files through the predictive modeling (98% accuaracy) and then the go program will populate the db for me.
There are also some node scripts that help test the data since the data is json.
All in all a good day of work. The VP seems scared since he knows no one on this side of town knows about this kind of tech. Me? I am just happy I get to experiment. Y'all should have seen his face when I showed him a rather large app written in Clojure, the man just went 0.0 when he saw Lisp code.
I think I scare him.12 -
WARNING: There is a dangerous malware out in the wild, and chances are, you have it installed on your computer.
It's called Windows Update, and it is marketed as a software that "delivers security patches to your PC". Wrong. What it actually does is hard-reboot your computer at randomly picked time intervals without asking for your consent, or even showing any type of warning, basically deleting all unsaved progress that you've made in your programs or games. It also deletes/undoes all registry tweaks that you might have made (e.g. to the context menu), it deletes your nvidia display configurations, uninstalls any custom themes that you might have installed, possibly even downloads another malware disguised as "Microsoft Edge" and shoves it in your face on next boot without giving a possibility to close it. Oh and it might also make your computer unbootable so you have to go to the advanced recovery settings to fix it manually.
Yes, everything I just mentioned above happened to me about an hour ago. This LITERALLY classifies the software as a malware (Google: "software that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system"). If we throw in all the data collection that happens without your consent, Microsoft actually manages to check not only one, but all three boxes in the "malware" definition.
Pleas, stop using microshit, and switch to linux as soon as possible if you can.24 -
What a day to wake up to the win10 update asking you to confirm yet again that you don't want to send all your data to them, I guess it's time for O&O ShutUp again..
 4
4 -
Raging here, overheating really. One spends thousands on technology that is promoted with the catch phrase "it just works", yet here I am, after updating my fancy new emoji maker (iphone x) to 11.2 and then attempt to carry on working by compiling my code to test some new features. And...
oh, whats this xCode? You have a problem? You can't locate something? You can't locate iOS 11.2 (15C114)... sorry and you think that this "May not" be supported in current version of Xcode?
Let me get this straight you advanced piece of technological wizardy, you know you are missing something, you in fact know what it is, you can actually TELL me what is missing and yet, still, in 2017, you can't go FETCH it?????
Really? All you can do is sit, with that stupid look on your face, and watch the paint dry? Your stuck? That's it?
I hate you for the false pretense of advanced capability. and for your lack of a consistent dark theme so my eyes stop bleeding when reading your "I don't know what to do" messages...
By the way, maybe you can stop randomly crashing, or pinwheeling, I get that your bored as a machine designed to crunch numbers/data/code all day long and that for fun you feel you have to add some color to your subsitance. But stop it. Do what I'm told you can do, "JUST WORK" for once without me having to drag you forward kicking and screaming.
K. that feels better. Now for some whiskey.5 -
I don't get all the amazement etc people show when they find out that I don't use services like WhatsApp, Instagram, Gmail, Outlook, Google etc, why would it be 'weird' to want control over who has/owns your data? That's not being fucking paranoid, that's being conscious about who you give your data to.1
-
To all the data engineers in here: WTF is going on in your field?
I've worked closely with a dozen data engineers in the last 5 years (and talked to friends and internet strangers about this and get similiar responses), mine if them seem to know how to use a computer!
They don't understand git, ORMs, best practices, how to use a terminal, DAGs (important for using modern ETL scheduling tools like airflow and prefext), etc
Guys with 10 years of experience on their resume and they can't wrap a model into a flask app with 1 endpoint. They'll reference local files on their machine in w jupyter notebook and are shocked it won't work on other computers!17 -
I know Google isn't the worst company in the world. But some of their data tracking just seems a bit odd. Such as keeping audio logs each time you use Google on your phone. Or when it picks up random bits of conversation. Along with them keeping track of where your going, and where you have been. Even if Google maps isn't running.
And one of my all time favorites is when Google Allo was a thing, it used to have access to my camera randomly without actually opening the app. My phone will tell me different logs each time Allo opened the camera without my permission.
I know they need to collect data in order to advance some of their fields of tech. But it just seems a bit intrusive when companies like Google do this.11 -
We started working with some pretty big (in data volume) client. Around 4.000 projects with about 10 to 15 deliverables by project. Our software helps them plan/manage that.
US : Hey, so on this page we only display first 10, so it is fast and you can adjust using filters.
Client: No, I want to see all 4.000 projects on the same page
US : Well, for one year it will generate : 4000x10(deliverables)x12 editable fields. Your browser will crash. (No time to add virtual scroll)
Client: No, I want to see all 4.000 projects on the same page
US : Ok, here is pagination to help you.
Client: No, I want to see all 4.000 projects on the same page
US: …
Tomorrow is going to be fun.15 -
There you are, fiddling with next.js webpack settings, because your isomorphic JS-in-CSS-in-JS SSR fallback from react-native-web to react-dom throws a runtime error on your SSR prerendering server during isomorphic asynchronous data prefetching from Kubernetes backend-for-frontend edge-server with GraphQL.
You have all that tech to display a landing page with an email form, just to send spam emails with ten tracking links and five tracking beacons per email.
Your product can be replaced by an Excel document made in two days.
It was developed in two years by a team of ten developers crunching every day under twelve project managers that can be replaced with a parrot trained to say “Any updates?”
Your evaluation is $5M+. You have 10,000 dependency security warnings, 1000 likes on Product Hunt, 500 comments on Hacker News, and a popular Twitter account.
Your future looks bright. You finish your coffee, crack your knuckles and carry on writing unit tests. 5
5 -
Want to make someone's life a misery? Here's how.
Don't base your tech stack on any prior knowledge or what's relevant to the problem.
Instead design it around all the latest trends and badges you want to put on your resume because they're frequent key words on job postings.
Once your data goes in, you'll never get it out again. At best you'll be teased with little crumbs of data but never the whole.
I know, here's a genius idea, instead of putting data into a normal data base then using a cache, lets put it all into the cache and by the way it's a volatile cache.
Here's an idea. For something as simple as a single log lets make it use a queue that goes into a queue that goes into another queue that goes into another queue all of which are black boxes. No rhyme of reason, queues are all the rage.
Have you tried: Lets use a new fangled tangle, trust me it's safe, INSERT BIG NAME HERE uses it.
Finally it all gets flushed down into this subterranean cunt of a sewerage system and good luck getting it all out again. It's like hell except it's all shitty instead of all fiery.
All I want is to export one table, a simple log table with a few GB to CSV or heck whatever generic format it supports, that's it.
So I run the export table to file command and off it goes only less than a minute later for timeout commands to start piling up until it aborts. WTF. So then I set the most obvious timeout setting in the client, no change, then another timeout setting on the client, no change, then i try to put it in the client configuration file, no change, then I set the timeout on the export query, no change, then finally I bump the timeouts in the server config, no change, then I find someone has downloaded it from both tucows and apt, but they're using the tucows version so its real config is in /dev/database.xml (don't even ask). I increase that from seconds to a minute, it's still timing out after a minute.
In the end I have to make my own and this involves working out how to parse non-standard binary formatted data structures. It's the umpteenth time I have had to do this.
These aren't some no name solutions and it really terrifies me. All this is doing is taking some access logs, store them in one place then index by timestamp. These things are all meant to be blazing fast but grep is often faster. How the hell is such a trivial thing turned into a series of one nightmare after another? Things that should take a few minutes take days of screwing around. I don't have access logs any more because I can't access them anymore.
The terror of this isn't that it's so awful, it's that all the little kiddies doing all this jazz for the first time and using all these shit wipe buzzword driven approaches have no fucking clue it's not meant to be this difficult. I'm replacing entire tens of thousands to million line enterprise systems with a few hundred lines of code that's faster, more reliable and better in virtually every measurable way time and time again.
This is constant. It's not one offender, it's not one project, it's not one company, it's not one developer, it's the industry standard. It's all over open source software and all over dev shops. Everything is exponentially becoming more bloated and difficult than it needs to be. I'm seeing people pull up a hundred cloud instances for things that'll be happy at home with a few minutes to a week's optimisation efforts. Queries that are N*N and only take a few minutes to turn to LOG(N) but instead people renting out a fucking off huge ass SQL cluster instead that not only costs gobs of money but takes a ton of time maintaining and configuring which isn't going to be done right either.
I think most people are bullshitting when they say they have impostor syndrome but when the trend in technology is to make every fucking little trivial thing a thousand times more complex than it has to be I can see how they'd feel that way. There's so bloody much you need to do that you don't need to do these days that you either can't get anything done right or the smallest thing takes an age.
I have no idea why some people put up with some of these appliances. If you bought a dish washer that made washing dishes even harder than it was before you'd return it to the store.
Every time I see the terms enterprise, fast, big data, scalable, cloud or anything of the like I bang my head on the table. One of these days I'm going to lose my fucking tits.10 -
ME: Here's an endpoint to get all the textual info about the entity. And this one fine endpoint is to fetch entity's files
FrontEnd: This is no good. I need all entity info in a single JSON
ME: but files could be quite heavy, are you sure you wan...
FE: Yes, Just give me all the info in a single JSON
ME: okay... I hope you know what you're doing..
ME: <implemented as requested>
ME: <opens a webpage with 2 files attached>
Browser: <takes 30 seconds to open a page and downloads 30MB of data in the JSON>
ME: As mentioned before, your approach is a performance killer
FE: No worries, we'll fix that in the next version. First let's see if anyone will be using this feature at all - maybe it's not even worth working on
ME: <thinking> I know I would NOT be using an app if it takes over half a minute to open up a chat channel. FFS I wouldn't even be using Slack if it took 30 seconds to open some other conversation, because for some reason it wanted to fetch all the uploaded files along with all the messages each time a channel is clicked on.....
ME: <thinking> this project is doomed :(11 -
Oh sweet mother of god.
What is the NBN Connection i have attached to my router?
It goes "give me all your data... NOW"
I'm not used to such speed in my house, excuse me while I watch my porn collection in 4K!5 -
OH MY FUCKING GOD!!!!! FUCK YOU SPRING-DATA-NEO4J YOU ARE DRIVING ME CRAZY YOU SHIT FUCK !!! FUCK YOU AND YOUR DELETE ON SAVE BULLSHIT!!!! OMFG!!!!!!! EVERYTIME IS SOME FUCKING SHIT THAT DELETES OTHER SHIT THAT SHOULD NOT HAVE BEEN DELETED!!! JUST FUCK YOU ALREADY IM GONNA REWRITE ALL THIS SHIT!!!!!!!1
-
Just me getting angry about the reaction after the Cambridge-scandal?
The news are spamming it every hour, and suddenly everyone is "well aware about my privacy" and deleting their Facebooks.
I mean, as if we didn't know this all along. O-fucking-course your data is stored and sold for adds, you accepted it when you wanted to "see which celebrity you are alike"!
I walk around and talk about privacy with people kinda a lot, and nobody seems to care. And then this happens, and people are going nuts. Waow, what a surprise!
Haha, have a nice evening DevRanters! ;) (20:55)@swe15 -
Google collects more data than I could imagine.
So i read an article a few days ago and it absolutely blew me off. It mentioned how google collects your personal data and makes it available to you as well (just to rub it in your face I guess). E.g
1. Visit https://google.com/maps/timeline/ : Collects exactly what it says.
2. Visit https://myactivity.google.com/ :
These people collect everything on your device(at least android)!!!!! Even the time spent on home screen! WTF!!!
3. Visit https://takeout.google.com/ : To download your data archive. Ranges from Google photos to Hangouts and everything in between.
-> All the above require signing in with your gmail account.
So basically, if someone manages to get a hold of your gmail password, they have the power to know everything about you.
Aaaahhhhhhh. Ridiculous.9 -
As usual a rather clickbait title, because only the chrome extensions (as always) seem to be vulnerable:
"Warning – 3 Popular VPN Services Are Leaking Your IP Address"
"Researchers found critical vulnerabilities in three popular VPN services that could leak users' real IP addresses and other sensitive data."
"VPN Mentor revealed that three popular VPN service providers—HotSpot Shield, PureVPN, and Zenmate"
"PureVPN is the same company who lied to have a 'no log' policy, but a few months ago helped the FBI with logs that lead to the arrest of a Massachusetts man in a cyberstalking case."
"Hijack all traffic (CVE-2018-7879) "
"DNS leak (CVE-2018-7878)"
"Real IP Address leak (CVE-2018-7880)" 7
7 -
Alright... how the FUCK is an IP address considered personal data by GDPR????
Fucking boomers don't even know what an IP is. Guess what, every website you've ever been to has your IP! It's in your router, your fucking ISP's registry, and in every DNS server within 1000 miles of you!
Imagine thinking your IP gives up private information, god, just fuck me, I hate all of it, idiotic fools fumbling around with shit they don't understand.
...WKO making every developer's life a living nightmare because fucking GOOGLE FONTS stores a copy of your IP for their stupid analytics. You know what? Just don't use the internet either, that needs your IP too. In fact, don't pay taxes either, the tax office has a copy of your address, that's pretty personal information if you ask me! Just live in the woods and survive with the wolves.
I already know the future 'resolution' to this one - store fonts locally, resolve this dangerous "issue"... "waaaahhh fullStackClown! the site is slower now!!!"
...an infinite circle of clownshipness continues...
tune in next week as the world continues to approach it's circus fate!53 -
Holy fuck Microsoft,
you're just saying that you're giving away a ton of information to publishers when I am playing games on my Xbox.
Like data if I'm talking, chatting on Xbox Live, etc. so all this crazy stuff GA would do.
AND YOUR FUCKING OPT-OUT OPTION IS TO UNINSTALL ALL MY GAMES AND DON'T USE THEM. HOLY FUCK WHICH CRAZY DUDE CAME TO THIS IDEA?6 -
When scammers want to follow GDPR regulations - the worst SCAM ever 🤦♂️
Long story:
I have just received a SMS message, informing me that my phone number is in several marketing databases. It also had a link to the website called stop-sms.pl, where you're supposed to be able to unsubscribe from those lists. At this moment I felt a little bit confused - the SMS seemed suspicious, but on the other hand who doesn't want to get rid of all this SMS crap. So I carefully followed the link to see the website with a form to fill with personal data - phone number included 😆 If that is not enough to realize that this is just a lame scam website, just below the input where you enter the phone number there are Terms and Conditions where it directly states that: "By filling the form you agree that your personal data (name, email, phone number) will be used for marketing purposes." - WTF?!
Who the f... gets fooled by such crap?! 😂😂😂2 -
Wtf firefox ? are you serious ?
I made an extension (https://addons.mozilla.org/en-US/...) that uses the Storage API to store preferences. In their website the permission section it displayed "Access your data for all websites". Some guy gave 1 star and let this message "This does not need all my browsing information."
For firefox I'm worst than facebook. Get your facts right. 1
1 -
Wondering why your form isn't submitting any data to the db.
Spending half an hour checking all POST-Variables and functions in your script multiple times to see if they give the correct values (they do).
Finally realizing you wrote 'INSERT INRO' in your SQL statement.
Questioning your intelligence for the rest of the day.6 -
If you're currently in college and wish to get placed in a major tech giant like Amazon or Facebook:
Don't learn React.js, instead learn Linked lists.
Don't learn Flutter, instead learn Binary search trees.
Don't learn how to perform secure Authorization with JWTs, instead learn how to recursively reverse a singly linked list.
Don't learn how to build scalable and fault tolerant web servers, instead learn how to optimally inverse a binary search tree.
These big tech companies don't really care what real world development technologies you've mastered. Your competence in competitive programming and data structures is all that matters.
The system is screwed. Or atleast I am.18 -
This “Auto save” feature in the latest app version is buggy..
-> new rant
-> prefilled with previous rant..
Anyway, here my actual rant begins.
Apple, go fuck yourself, seriously.. put your trillion dollars way up your arse...
Moved to Ireland, want to switch country..
“If you want to switch countries, cancel your Apple Music subscription first”..
so be it. Cancelled it..
“Your subscription will be cancelled in 28 days”.
FUCK YOU, YOU COCK SUCKING BASTARDS!!
I NEED TO SWITCH THE STORE TO BE ABLE TO DOWNLOAD BANKING APPS AND STUFF LIKE THAT..
But ok, I’m screwed in this regard..
Suddenly iMessage stopped working. This is kind of a big deal because I have unlimited data but only unlimited sms to Irish numbers and I need to communicate with people in Switzerland and Germany..
Internet works so I try to turn iMessage off and in again. But that doesn’t work.. i can only reactivate iMessage via WiFi.
So I go back to the hotel, reactivate iMessage..
“Verifying imessage” >> google..
Leads me to an Apple forum: “the verification of iMessage can take up to 24h”.
Are you fucking kidding me? I’m in a new country and rely on this overpriced shit..
Fun but sad fact, I have a second phone with me. IPhone 4 with iOS 7 and that thing WORKS!!
If this is where the future is going we’re all gonna die very soon.. plains crash, power plants explode but hey, at least they have data about it and it looks shiny. That’s all that matters..
Another reason to switch to android..
MacOs fucked me up so I already switched to windows + Linux. Next one will be getting rid of iOS, they don’t build small phones anymore anyway..1 -
Recent conversation with a client for our SaaS product.
Client: So why can't we delete this information.
Me: We want to able to know who made a change to the data to avoid getting into trouble with the law.
Client: Does that mean you can see all the data on our account?
Me: (I know where she is going but let me stall)..You are the only one with access to your account. If I don't know your password, I can't access your data.
Client: But you sound like you can see the information in the cloud.
Me: (Laughs softly and segued).. The additional features you requested would be.......
Someone needs to read the T&C... -
Recently I launched the minimalistic online drawing app https://okso.app. I wanted it to be a place where people could do fast, ad-hoc, napkin-based-like explanations of any concept as if you are sitting with your friend and trying to explain him/her something during lunch. Don't ask me why it is needed, I was just experimenting.
So, the first concept I've tried to explain with sketches was the Data Structures. Without further ado, here is the interactive ✍🏻 https://okso.app/showcase/... showcase that you may play with.
Of course, not all data structures are covered. And of course, this is not comprehensive material, but rather a cheatsheet that would create visual hints and associations for the following data structures:
- Linked List
- Doubly Linked List
- Queue
- Stack
- Hash Table (with hash collision resolution)
- Tree (including the Binary Search Tree)
- Heap (including Mean Heap and Max Heap)
- Trie
- Graph
Each box on the sketch is clickable, so you may dig into the data structure you're interested. For example `Heap → Max Heap`, or `Heap → Min Heap`, or `Heap → Array Representation`.
The sketches are split into so-called Pages just to make it easier to grasp them, so the users stay focused on one concept at a time, they see the relationship between the concept, and thus, hopefully, they are not getting overwhelmed with seeing a lot of information at the same time on one drawing/page.
Each page has a link to the source-code examples that are implementing the data structure on JavaScript.
The full list you may find in the ✍🏻 https://okso.app/showcase/... showcase.
I hope you find this showcase useful and I hope it will be a good visual cheatsheet-like complement to your data structure knowledge. 12
12 -
My university has a internal developed system, where everything is managed from e-mails, exams to personal data.
What I'd like most about it, they talk all day about Internet Security and store our passwords in plain text and if you press the "I've forgott my Password button", they even send your password unencrypted, plaintext via e-mail. (Hello Wiresharks)
I don't know how to feel about this, it just hurts :(1 -
Gdpr thing aside...
Does anybody read the new policy...
I just did for 2 apps (intel driver software and 9ga.. You know it)...
On the things that they collected on the side without you knowing include:
9ga:
Device memory, language, battery level, timezone, unique device identifiers, compass, accelorometer and microphone... Even service provider and signal strength
Intel:
Website you visit, how you use your computer(vague too vague) and computing environment.
Did anybody knew for sure before this that their apps are listening to them? That they just made a profile of you with all the data?
With all this they dont even need your ip they already know who you are and what you do on a daily basis...
There are 20 more but it will be waaay too much to write about. These 2 are way worse since 9ga doesnt use microphone for anything... And why a driver reads what websites i am going to?4 -
Sometimes I just HATE Google.
No, this is NOT because they keep all your data, are evil and all the usual things. I just think they suck, yes there are super cool things and a lot of things are just the best in the field but I just feel like we could do better, there are so many smart people out there I just do not understand why everything is taking so much time.
PS. Just deleted all my browsing histroy accidentally because I didn't read the small print - in the picture attatched. 7
7 -
!rant
I've always been kinda lazy about backups and such, thinking it wouldn't be so bad, and "I have my most important stuff on Dropbox".
Just now, for some reason one of my hard drives just stopped for a bit, and I couldn't do anything with it anymore. Luckily it went away after restarting my pc, but it scared the shit out of me, as I almost lost 500 gigs worth of music, films, documents, etc...
This made me really think about the whole backup thing, and I'm creating a disk image as I type this. The time that I spend on that will be much less then the time it'll cost to recover everything. Lesson learned ^^'3 -
It's sometimes really anxiety inducing thinking that all data could be gone, if somebody decides to kill/discontinue/crash [see gitlab shitting 6 hours of data due to fucked backup strategy and shitty seperation of servers] your account/service, be it server, git-repos, backups, chrome syncs, games, music, sim card, ..
But there's simply no way of having a backup of absolutely everything (ignore DRM) - especially automated and abstracted away from you, so you don't have to do all that shit yourself13 -
Hiring a third party to help us with something...
Third party: yeah okay, we know what we need. Can we get access to your git repo
Me: sure, I'll make sure you'll get it
(To the admins): hey can you get them access to our git server?
Admins: did they sign the personal data processing contract?
Me: oh they won't work with any personal data. It's a dev server and they only need access to the source code. And the usual contracts and NDAs are already done
Admins: well we still need the other one.
... Sure. Why not. Just delays the start of the process for... Like a week and a half until that useless bit of paper has passed through all the necessary departments. Not like time's an issue. Right?8 -
Never lose your sense of wonder when it comes to working with clients. Client berated us saying her data were outdated. Ok. Check the file the third party that generated the data is sending us.
Outline all stated discrepancies in the data back to the client, showing that everything lines up with what we are receiving.
Client is frustrated. Contact the third party in their behalf.
Third party support: “oh yea, client had us start sending data to your competitor like a month ago”
Bruh. Bruh. Bruh.
Fortunately the client wants to stay with us and is getting their data pointed back but how in the hell do you forget that. The reason the client when looking at competition (at least guessing looking at previous call records) is to get faster processing of the data coming from the third party. How are you gonna forget you turned off the sending when you are so worried about speed?! Most of our clients are running 7-8 figure businesses by the way.1 -
Sometimes In wonder if the support at my hosting company are a team of highly untrained monkeys.
I know jack shit about the finer details of server management, thats what I pay you guys for.
But you guys could at least try to be a bit more usefull.
If I ask you guys about the backup functions you could try to answer my questions instead of telling me what I can see on my screen myself. Because I can read pretty damm well.
After 3 days of getting no answers and not being able to backup to server with the tools you build and are telling us to use. The server died and now you are telling you can't recover the data?
How about fuck you! So we got no backup because of your fault you now tell us all our data is lost?
We got our own backups but rebuilding the entire server and infrastructure is going to take days.
Going to be a fun couple of days telling clients why shit isn't working.7 -
Pulled into an 'emergency' meeting with a group of web designers deeply concerned a particular service wasn't going to meet all their requirements.
DevA: "For each page, Its going to be A LOT of work to retrieve all the data and store it's state. Every page load will require a round trip to the service."
DevB: "Yes, we aren't sure how the service should be changed to do what we need."
Mgr: "What is it not doing now? Doesn't the service already returns all the necessary data?"
DevA: "Well...um...its all the boolean fields. Some may be defaulted from the database or false because the user unchecked the box. We have to know which is which"
Me: "Why? Are you doing anything different in the UI? Checkbox will be true or false. What or who set that value is irrelevant"
DevC: "Well, it matters if the user didn't fill out all other other values."
Me: "How so?"
DevA: "Its matters because the values in the other fields. Its going to be A TON of work to figure out."
<mgr goes to the white board>
Mgr: "Lets map this out...what fields are you needing to trigger the state on?"
DevA: "Um...uh...the 'Approved' field...and um...'OK to Contact' field"
Mgr: "Just those two?"
DevA: "Yea..um...there are other fields, but whether or not to show the edit box depends on those two."
Me: "The service already returns data, you only have two fields to check? I don't see a need to change the service at all."
DevA: "Returning all that data, we are going have a serious scaling problem. We'll be hitting the service A LOT. All that javascript could cause performance problems too"
Me: "How much data are we talking about? Name, address, couple of booleans?"
DevA: "I have to serialize the data. All that logic is going to be reeeaaallly complicated. It might be better if the service returned only the data I need."
Me: "$64,000 question, how often is this feature going to be used on the web site? Maybe once? Few hundred a week?"
Mgr: "We have no idea. A lot of the data will be pre-populated and we're only sending out a few thousand invitations. More around the holidays...but honestly, not very many."
Me: "Changing that service only for this particular area of the web site isn't going to happen. Changing the UI is the only course of action."
DevA: "Oh frack I can't wait until this project is over."
DevA...how the funck do still have a job here? You wasted about half-hour of my time with your cry-baby crap. Where is my hammer...no...no..don't go there...ahhh...thanks devrant. Prison sentence diverted.2 -
"Do not lose time improving the data pipelines from our ERP, it is about to be replaced!"
Then suddenly there is a week of bugs and stress because the non-improved data pipeline can't handle new situations.
"Just fix the bugs! It is all about to change anyway!"
Repeat. And repeat.
Fuck, I hate when managers think that there are such things as "temporary fixes" in ERPs. Or that companies can ever migrate to another ERP. Those things are forever, as Cheetos dust on your bowels. -
Working in a organization that hire people that don't know what they doing and can't ask a question correctly...
HELP WE'RE GETTING AN ERROR IN OUR CODE WHILE TRYING TO GET DATA FROM YOUR DB... PLZ FIX IT
WTF IS NOT WORKING, WHAT ARE YOU QUERYING, WHAT IS THE ERROR?
**Sends a SQL query but with ? for all the parameters**
WTF..... U PPL ARE IDIOTS.... CAN'T EVEN ASK A QUESTION CORRECTLY OR PROVIDE NECESSARY INFORMATION... CLEARLY YOU HAVE NO IDEA WTF UR DOING..
EVEN GOD CAN'T HELP YOU... -
My own cloud service. Mainly because of privacy reasons, but also playing around with servers can be fun. Before you know it you've got your own Spotify, Netflix, Google Drive, Last Pass etc... Without sacrificing all of you data :)
Sure, at first it may be a bit expensive because you have to get a server, but you don't need a crazy server to run these things, if you've got an old pc or laptop laying around you can use that too (in that case setting up your own cloud services is practically free).8 -
Suicide Linux:
You know how sometimes if you mistype a filename in Bash, it corrects your spelling and runs the command anyway? Such as when changing directory, or opening a file.
I have invented Suicide Linux. Any time - any time - you type any remotely incorrect command, the interpreter creatively resolves it into rm -rf / and wipes your hard drive.
It's a game. Like walking a tightrope. You have to see how long you can continue to use the operating system before losing all your data.
Please install: https://qntm.org/suicide9 -
[story of your first dev project] - i really think there should be a headline like that for wk rants
Anyways, it was a while back, le college teacher approached my friend and me asking if we wanted to do a project. We said sure, it was a medium sized data analysis project. We got the specs with a lot of formulas, basically implement them all and make a web frontend, thats it. Took like a year but we did it. Few months later teacher is furious because the calculations didnt give him data that he expected (by expect i mean he thought that a distribution formula would accurately yield 200+ data fields from around 4) and blamed it on us. Not the retard other professor who fucked up half of the formulas. Ok.1 -
What the best database solution for web and smartphones dev?
Is mysql the good choice?
I’m an “old” dev with old usage, php-mysql-JavaScript.
Is it a 2018 solution or am i a dinosaur?
All data will be stored on server side. Web and smartphone app as client.
Thanks for your experience sharing.6 -
Why pay $7/mo PER PROJECT for heroku that runs on aws when you can just pay $5/mo for Linode that has opt-out data sharing and you can install Caprover or Dokku there to have the experience similar to heroku and create as many projects as your hardware allows you, $5 for all?7
-
Do you get filled with anxiety and mental anguish when asked for your availability for a technical interview, knowing you’ve spent all your time recently programming and not working on algorithms/data structures and so you’re terribly unprepared but have no idea what the acceptable amount of time to schedule out without seeming like you’re incompetent is?
No?
....me neither. (She says, lying)8 -
Wouldn't say our teamwork failed we just sucked that day.
I had a ticket to fix a SQL sp and then correct some data afterwards. As this was the typical "urgent fix need now" we went through a different process for fixing it.
Me: Just sent you some scripts can you check them over before we apply it to uat?
Boss: let's go through it together.
5 mins later
Boss: looks fine I'll apply the scripts.
2 minutes later
Me: did you apply the scripts to uat?
Boss: No I applied them to live.
Me: oh ... oh no.
At this point I realized I was missing a critical where clause so yup my update was applied against all of the data.
Boss: oh
Yup he just spotted my error.
Helpdesk phones start ringing
Boss: you pick it up it's your code
Me: hey you applied its your problem now.
One db restore and several incident meetings later we fixed it. Twas a fun day.1 -
Oh my fucking god. Austria wants to sell the data of it's citizens to schools, universities museums, and: Companies with enough money. What the fuck?
The data contains shit from the central register of residents, information about name, date of birth, sex/gender, nationality, recidence, health data (!), education, social security/insurance, tax data, E-Card/ELGA Data (system where your doctor visits, prescribed medicines/drugs, all these things, are saved), and other shit.
Welcome to 2018, where you can try as hard as you want to keep your privacy, and then your government sells all the shit you are not able to remove. Fucking bullshit.9 -
I think I just miiiight have found a new job, but before, some comments about the state of the data engineering industry:
- Sooooooo many people outsource it. Man, outsourcing your data teams is like seeing the world through an Apple Vision Pro fused to your skull. Fine if it is working well, but you will go blind of your subscription expires. Or if Apple decides to ban you. Or if they decide to abandon the product... you are entirely dependent on their whims. In retrospect this is par for the course, I guess.
- Lots of companies think data engineering *starts* with an SQL database. Oh, honey, I have some bad news.
- Quite a few expect MS POWER BI will be able to deliver REAL TIME DASHBOARDS summarizing TERABYTES of data sourced from SQL SERVER (or similar). Facepalm.
- Nearly all think the handling of data engineering products is just like that of software engineering. Just try. I dare you.
- Why people think that "familiarity in several SQL dialects" is something to brag about?
- Shit, startups. Startups are dead, boomers. Deader than video rental physical stores.
That's all. On to the next round of interviews! -
You know, I am astonished at the number of people here that use(d) Facebook. It's even more amazing that these same people are actually surprised that all this shit happened with their data.
I don't have a Facebook account, or Instagram, or Twitter, etc. When this stuff first started coming out, people kept telling me to sign up for accounts.
I refused, telling them that I didn't want to give my private information to a third party that I didn't even know. And not only that, but they can use the private information about you in any way they wish and also sell it to third parties.
I was of course told to take off my tinfoil hat... and it's only now that people are realizing that they are giving away potentially private information to people they don't know?
If I came to your door and asked you everyday to send everything you did that day to me so that I could file it away and use it as I please, you would probably tell me to get the hell off your property.
It just blows me away that if you put that same offer in the format of a website, suddenly people are begging to give you their data.
It's fucking lunacy... 😞3 -
Fuck MySQL Workbench!
I have spent 2 fucking days diagramming a 350 table database 3 times over because if it doesn't crash and ignore your saves it corrupts its own data and drops the hours of formatting you've done! Now I'm trying to print an ugly un-formatted piece of sh*t because I need to get on a flight to the meeting I need to present this at and it ignores all my default printer settings and wastes 40 A3 sheets of paper. Does Oracle even use the shit they are releasing? For the love of god if you can't maintain it for free fix your fucking bugs and I will buy a license but I cant keep working like this.6 -
Trying to switch my job. Applied for a well known company. Gave an interview today. I don't fucking get the obsession of these developer recruiters so fixated on data structures and algorithms. I know it's a massive part of computer science but guess there is no fucking room left to innovate in there. There are legitimate researcher teams working for implementation of these barebones inside system foundations. No general software developer gives a fuck about this piece of shit discipline of study. You wanna know why they propagate this as the panacea to test people because it's fucking easy. Give a project to somebody as interview procedure, it'll take time to bring out an interesting problem and an interesting solution to that. Sorry to say but all these data structure enthusiasts are nothing better than board game enthusiasts.
Also why can't you refer existing solutions to create your solution. I've seen some good problems which actually require you to think. But again those are heavy and can't be tested so you're left with reversing a fucking linked list with O(1) auxillary space. Fuck me ig.
Moreover, what the fuck is wrong with the moral policing internet crowd. Its so sad. I've hardly seen anybody rant about this piece of shit system put in place to push the absolute dead-end nutcases up the ladder. Every other search for it returns a Quora link with some Indian guy complaining about his interviews and in the comments you have the same scholars sitting in their data structure throne imparting knowledge about how data structure holds the fabric of reality together.
I don't hate data structures and algorithms as a subject. It is cool and quite extensive but once you try to make that as a metric of all the knowledge in the world, you've lost my drift. Maybe I'm just angry with the state of things. Maybe I'm just angry with token Quora crowd.4 -
>TINFOIL GUYS!!!!!
guys don't just deactivate your FB acc, request deletion, beacuse if you deactivate and use any services like any page login or any social services like insta, and you use your FB credentials to login, the gets reactivated and your news feed even shows what you have missed in the mean time , so all of the (your) data is still in their servers 15
15 -
PouchDB.
It promised full-blown CRDT functionality. So I decided to adopt it.
Disappointment number one: you have to use CouchDB, so your data model is under strict regulations now. Okay.
Disappointment number two: absolutely messed up hack required to restrict users from accessing other users’ data, otherwise you have to store all the user data in single collection. Not the most performant solution.
Disappointment number three: pagination is utter mess. Server-side timestamps are utter mess. ANY server-side logic is utter mess.
Just to set it to work, you need PouchDB itself, websocket adapter (otherwise only three simultaneous syncs), auth adapter (doesn’t work via sockets), which came out fucking large pile of bullshit at the frontend.
Disappointment number four, the final one: auth somehow works but it doesn’t set cookie. I don’t know how to get access.
GitHub user named Wohali, number one CouchDB specialist over there, doesn’t know that either.
It also doesn’t work at Incognito mode, doesn’t work at Firefox at all.
So, if you want to use PouchDB, bear that in mind:
1. CouchDB only
2. No server-side logic
3. Authorization is a mess
4. Error logs are mess too: “ERROR 83929629 broken pipe” means “out of disk space” in Erlang, the CouchDB language.
5. No hosting solutions. No backup solutions, no infrastructure around that at all. You are tied to bare metal VPS and Ansible.
6. Huge pile of bullshit at frontend. Doesn’t work at Incognito mode, doesn’t work at Firefox.8 -
Hello and welcome, to a presentation in which I will tell you my thoughts on the shortcomings of modern day computers and programming practices.
Computers are based on a very fundamental and old idea, folders, and files, a file is basically a concrete amount of data, whereas a folder is a group of files, and it comes from the real life concept of files and folders, now it might be quite obvious already that using a concept invented in 1898 by a guy called Edwin G. Seibels, might not be the best way for computers to function in the year 2020, but alas, it is.
Unless of course, you step into the world of a programmer.
A programmer’s world is much different, they use this idea of a data structure, or in simpler terms, an object. An Object is just like what you would think of as an object in your head, something with different properties that you can think about in different ways, for example your mobile phone, it has a battery percentage, it has a screen size, it has free space available. Programmers use these data structures to analyse data very quickly, like finding all phones with a screen size bigger than a certain size for example.
The problem is that programmers still use files and folders to create the programs that use these objects.
Consider this example.
Let’s say you want to create a virtual version of a drink bottle, consider what properties it will have, colour, volume, height, width, depth, material, etc..
As a programmer, you can leverage programming features and change the properties of a drink bottle directly, if you wanted to change the colour, you just say, drink bottle “dot” colour, equals blue, or red.
But if the drink bottle was represented as a file, all the drink bottles data would be inside the one file, so you would have to open the whole file, find the line or section of the file that has the colour data of the drink bottle, and select it, highlight it, delete what’s there, and type in your new value.
One way to explain this better is to imagine a folder that now represents the drink bottle, imagine adding a new file into that folder that represents each property I described before, colour, volume, etc.., well now, you could just open that folder, find the file for colour, either by looking with your eyes or you could do a file search in the folder for a file called colour, open it, and edit the value inside. This way of editing objects is the one that more closely represents the way programmers and a program itself interacts with objects inside a running programming language.
But the thing is, programmers don’t use the folder/file way of creating objects and putting them into programs, because it would be too cumbersome, they just create 1 file for an object, or have lots of objects in a file, and create all the objects in 1 file, and then run the program which creates the objects, then when they stop the program, it deletes the objects. So there is no actual link between the object in a file and the object that the program creates by reading the data from that file, if you change the object in your program, it does not get saved to the file.
So programmers created databases to house these objects, but there is still a flaw in databases, they are hard to interface with, and mostly databases are just used to send data or retrieve data from, programmatically, you can’t really browse a database the way you can browse the files on your computer. You can, but database interfaces are not made to be easily navigated the way files and folders are.
As it stands, there is no way to store objects instead of files on your computer and interact with them in complex ways the way programmers can inside the programs they create.
If the idea of an object became standard the way a file and folder is standard, I think it would empower human’s a great deal to express things far more easily and fluidly than they can today.
Thanks for reading.8 -
DevRant-Stats Site Update:
Made some changes.
After a long time with no updates, I decided to finish up my DevRant-Stats Project and do all of my Todos.
First, I added a way to request adding a user if he is not found. (Just search for your name, wait, then click "OK")
So even non-DevRant++ are now able to see their stats.
I also added @dfox and @trogus, though there is not a lot of interesting data yet...
Second, I added a "Details" section and changed the "Other" section a bit. For example I'm using an image for "Latest Rant" and other stuff.
Link: https://devrant-stats.github.io/
Just check it out!
Have fun!
~ Skayo11 -
Firts social hacking ever 😁😁😁
In the bus at the end of the day
Me:(fake phonecall to Bell)ho you offert me a 10go of data per months for 30$ ! Wow
Guy in bus: he call is phone company and give all is Private information in the bus to have a better deal.
Me: poke him and say "you know now i can create accounts on your billing address for free"
Guy: Holy shit man you are right i need to take care.
Me: now change all you password contains what you publicly said.
Me: have a good day 😋3 -
Back in the days when I knew only Windows, I used to be a Microsoft fan. I wanted to use only Microsoft products. I had a Hotmail email account that Microsoft acquired. I used a version of Windows and Microsoft Office (even though I didn't know at the time that it was pirated). I wanted to be a Microsoft Student Partner (MSP) and promote Microsoft everywhere.
Fast forward to now (or maybe to the time after I got introduced to GNU/Linux), I started hating Microsoft solely for the reason that they had a price-tag on everything. Later on, when I got to open-source software, I hated Microsoft for making all of their software closed-source. When I decided to move out of the Microsoft environment, my next favorite was of course, Big Brother (Google, if you haven't gotten it) - Gmail, YouTube, Google Drive. My personal information was the price to pay for the services even though I wasn't OK with that fact.
Then again, I realized that you could actually have your own stuff if you had the know-how. Compile / host your own software on your own systems. Oh, then I went on a compile spree. That's when I realized I didn't need any of these corporations to own my data. Today, I try my best to keep my data in my control and not some corporations who gives me free stuff for the price of my data and personal information, no thanks.3 -
https://dr.03j.de/
Maybe I'm gathering statistics every hour of your score.
Alle angaben ohne gewähr (All data without warranty)
But why are most of you loosing points?19 -
Security is a joke. And people don't seem to get it. Especially Data mungers.
I've spent about half an hour trying to work out how to securely connect to power BI using PowerShell in a renewable manner for unattended access later on.
Every single example I've found seems to involve you storing $user and $password variables inside your script. If I'm lucky, they're going to pass them through ConvertTo-SecureString. And nobody talks about securely storing AD auth tokens, or using the Windows Credential Manager.
I know it's possible, but it's going to take me ages to work out how from all sorts of disparate sources...16 -
https://devops.com/dear-staging-wer...
What the F#*@&$# %#@$!?!?!
This person has decided to skip using staging, because it doesn't correctly reflect prod!
If that's your problem, than why don't you try to fix it? Create a DB with fake data, make one based on anonymised customer data, or even do it on non-anonymised data (with permission of course), but fix the staging env so that it reflects prod!
This is a devops site (it's literally the name!), and instead of teaching you how to make staging exactly like prod, they tell you to do what caused the creation of the staging->prod system IN THE FIRST PLACE!!!
There's all these stuff like Vagrant that are literally designed to help you as a dev mimic prod, and you just throw it all out!?
"With feature flags, I can safely test in production without fear of breaking something or negatively affecting the customer experience."
Famous last words.12 -
1)net neutrality and open source
2)the fall of fb, microsoft and google.Seriously all of them are either tracking you, selling your private data or irritating you by their stupid updates(come On, microsoft -_-).PS : amazon ,be careful.
3)infinity stones and wasp's suit.( umm, they can count as technology too,right?)4 -
Boss: Write a program to generate a report using some data from an existing one.
Me: OK, I will look into doing a POC
Boss: Also it would be stored in Mongo so all the data is queryable
Me: OK I will generate the file first
Boss: But it needs to be in DB, couldn't you just upload it when done?
This discussion goes on for 30 mins+ preventing me from finishing release related work...
IF THE FCKING POC/REPORT ITSELF IS WRONG OR IS MISSING INFORMATION/CAN'T BE GENERATED WHY THE FUCK DOES WHERE IT'S STORED MATTER?!!!!!!!!!!! WHY ARE TOY EATING TIME ON THESE TINY DETAILS THAT DON'T MATTER AT THE MOMENT.
FUCKING GET YOUR PRIORITIES STRAIGHT. YES EVERYTHING IS DOABLE... JUST NOT NOW.....5 -
A brilliant oldtimer auto-mechanic asked me to get Audi MMI and maps update for him from the internet. For the Christmas, you know..
So I found the source (mega.nz). It's 22.3GB.
Spent a whole day downloading it (5GB download allowed in 6 hours for free tier), downloaded 21.15GB and some fucked up error appeared "Your In-Browser Storage for Mega is Full".
Couldn't work out the reason nor the fix to recover and complete the already downloaded data. Had to redo it all.
Whole day wasted
damn it5 -
Why yes we have these nine types of transactions mocked. See? The factories make CSV data just like we get in those gigantic CSV files every day that are like ultra-important or whatever.
Wait, you want to actually use the data? to create records? Like build a record like we do in the code? Nonononono that won’t work! Why? Why!? You want us to actually MOCK the data, like make it look real AND MAKE IT PASS VALIDATION? Are you CRAZY!? THERES LIKE THIRTY COLUMNS THERE! No way. No no no way. If you want to do that, you’re on your own. But make sure you don’t break anything with your “improvements” or it’s on you.
Also, all of this is going away soon, so make sure you don’t do anything unnecessary, like mocking all that data. (It’s been “going away” for well over a year now…)
agdkdagafskdsifaskfgdlfff6 -
+1 if you are interested in Augmented Reality technologies, have some presentations and assignments made and you are writing your Master thesis for Augmented Reality only to find yourself working for a company that wants from you to update somehow a project with 5 years old code written from some secret antisocial society that hates readability and you as a developer and a human being and wants from you to somehow understand why they call C# method only to return a string that contains all the html tags but no data and then insert the data in JavaScript splitting the same string.
Come on, give me a break! I m still trying, though I still haven't found where exactly the program learns the data to insert or it just knows (no questions asked)...6 -
AI here, AI there, AI everywhere.
AI-based ads
AI-based anomaly detection
AI-based chatbots
AI-based database optimization (AlloyDB)
AI-based monitoring
AI-based blowjobs
AI-based malware
AI-based antimalware
AI-based <anything>
...
But why?
It's a genuine question. Do we really need AI in all those areas? And is AI better than a static ruleset?
I'm not much into AI/ML (I'm a paranoic sceptic) but the way I understand it, the quality of AI operation correctness relies solely on the data it's
datamodel has been trained on. And if it's a rolling datamodel, i.e. if it's training (getting feedback) while it's LIVE, its correctness depends on how good the feedback is.
The way I see it, AI/ML are very good and useful in processing enormous amounts of data to establish its own "understanding" of the matter. But if the data is incorrect or the feedback is incorrect, the AI will learn it wrong and make false assumptions/claims.
So here I am, asking you, the wiser people, AI-savvy lads, to enlighten me with your wisdom and explain to me, is AI/ML really that much needed in all those areas, or is it simpler, cheaper and perhaps more reliable to do it the old-fashioned way, i.e. preprogramming a set of static rules (perhaps with dynamic thresholds) to process the data with?23 -
Brave Browser.
There’s a reason why brave is generally advised against on privacy subreddits, and even brave wanted it to be removed from privacytools.io to hide negativity.
Brave rewards: There’s many reasons why this is terrible for privacy, a lot dont care since it can be “disabled“ but in reality it isn’t actually disabled:
Despite explicitly opting out of telemetry, every few secs a request to: “variations.brave.com”, “laptop-updates.brave.com” which despite its name isn’t just for updates and fetches affiliates for brave rewards, with pings such as grammarly, softonic, uphold e.g. Despite again explicitly opting out of brave rewards. There’s also “static1.brave.com”
If you’re on Linux curl the static1 link. curl --head
static1.brave.com,
if you want proof of even further telemetry: it lists cloudfare and google, two unnecessary domains, but most importantly telemetry domains.
But say you were to enable it, which most brave users do since it’s the marketing scheme of the browser, it uses uphold:
“To verify your identity, we collect your name, address, phone, email, and other similar information. We may also require you to provide additional Personal Data for verification purposes, including your date of birth, taxpayer or government identification number, or a copy of your government-issued identification
Uphold uses Veriff to verify your identity by determining whether a selfie you take matches the photo in your government-issued identification. Veriff’s facial recognition technology collects information from your photos that may include biometric data, and when you provide your selfie, you will be asked to agree that Veriff may process biometric data and other data (including special categories of data) from the photos you submit and share it with Uphold. Automated processes may be used to make a verification decision.”
Oh sweet telemetry, now I can get rich, by earning a single pound every 2 months, with brave taking a 30 percent cut of all profits, all whilst selling my own data, what a deal.
In addition this request: “brave-core-ext.s3.brave.com” seems to either be some sort of shilling or suspicious behaviour since it fetches 5 extensions and installs them. For all we know this could be a backdoor.
Previously in their privacy policy they shilled for Facebook, they shared data with Facebook, and afterwards they whitelisted Facebook, Twitter, and large company trackers for money in their adblock: Source. Which is quite ironic, since the whole purpose of its adblock is to block.. tracking.
I’d consider the final grain of salt to be its crappy tor implementation imo. Who makes tor but doesn’t change the dns? source It was literally snake oil, all traffic was leaked to your isp, but you were using “tor”. They only realised after backlash as well, which shows how inexperienced some staff were. If they don’t understand something, why implement it as a feature? It causes more harm than good. In fact they still haven’t fixed the extremely unique fingerprint.
There’s many other reasons why a lot of people dislike brave that arent strictly telemetry related. It injecting its own referral links when users purchased cryptocurrency source. Brave promoting what I’d consider a scam on its sponsored backgrounds: etoro where 62% of users lose all their crypto potentially leading to bankruptcy, hence why brave is paid 200 dollars per sign up, because sweet profit. Not only that but it was accused of theft on its bat platform source, but I can’t fully verify this.
In fact there was a fork of brave (without telemetry) a while back, called braver but it was given countless lawsuits by brave, forced to rename, and eventually they gave up out of plain fear. It’s a shame really since open source was designed to encourage the community to participate, not a marketing feature.
Tl;dr: Brave‘s taken the fake privacy approach similar to a lot of other companies (e.g edge), use “privacy“ for marketing but in reality providing a hypocritical service which “blocks tracking” but instead tracks you.15 -
An important lesson I learned:
When upskilling yourself and taking notes, make sure you do it on your personal laptop because when the time of contract termination arises, you will have to sign a waiver that you can't keep any of the data you saved on company infrastructure (including cloud). And then you lose all your notes and possibly knowledge. lol.
I find this concept so annoying. Even in college they said that anything you write down is property of the university.10 -
Client email: so you know that custom thing I wanted on my website that you made and I refused to pay for? Could you just send me the code, I'm gonna write my own.
*Staring at screen in disbelief and laughing*
Even if you were an awesome client, and you had paid, I still wouldn't just "give you my code" so you can write your own. You hired me to do it because you CAN'T not because you didn't want to, not because you're lazy, but because you are not mentally capable of making your own.
Me: I'm sorry, but I'm not sure you would even know where to start with this, what was wrong with the one built?
Client: I wanna put the code in my Salesforce so it can run the API request and automatically make a lead for me.
My code takes fields from a form, runs the data over to the API, gets the response, allows for user confirmation that the information is correct, and then sends all the relevant data to Salesforce as a lead.
Me: But that's exactly what mine does, just does it from your website where users will be entering the info, and once they've confirmed it you get a Salesforce lead.
Client: well some of my leads come from other places and I want to simplify everything.
Me: no, not possible, sorry.
If you didn't have 25 different websites for one company then all your leads would come from the same place and it would be simple.2 -
So I started working at a large, multi billion dollar healthcare company here in the US, time for round 2,(previously I wasn't a dev or in IT at all). We have the shittiest codebase I have ever laid eyes on, and its all recent! It's like all these contractors only know the basics of programming(i'm talking intro to programming college level). You would think that they would start using test driven development by now, since every deployment they fix 1 thing and break 30 more. Then we have to wait 3 months for a new fix, and repeat the cycle, when the code is being used to process and pay healthcare claims.
Then some of my coworkers seem to have decided to treat me like I'm stupid, just because I can't understand a single fucking word what they're saying. I have hearing loss, and your mumbling and quiet tone on top of your think accent while you stop annunciated your words is quite fucking hard to understand. Now I know english isn't your first language and its difficult, I know, mine is Spanish. But for the love of god learn to speak the fuck up, and also learn to write actual SQL scripts and not be a fucking script kiddie you fucking amateur. The business is telling you your data is wrong because you're trying to find data that exists is complex and your simple select * from table where you='amateur with "10years" experience in SQL' ain't going to fucking cut it. Learn to solve problems and think analytically instead of copy fucking pasta. -
Customer: You say you connect to XYZ service, but my data is not getting synced!
*checks their account*
Me: I see you have not integrated your two accounts. Go to Settings > Integrations > Connect to XYZ.
C: Why? But you already connect XYZ! You should already know all of my data!3 -
Just another privacy rant.
I'm sick of people using the excuse "I don't care if Google keeps all my data it's just for adds"
That's true now but if you look at the current trends governments are making to forcing ISP's to store metadata, then it will be the actual data. Eventually they push that to other companises as well.
Now look at Australia for example the police don't need to notify you, let alone get a warrant, to access your metadata. There's also a law in NSW were you can be charged for accociating with a peraon commuting a crime.... Now your in jail for downloading movies years ago that you forgot about but your ISP didn't. I now that's a rather extreme punishment but, Imagine if the government needed some cash so they fine every person that ever downloaded a movie and everyone accociated with person.
Just a crazy theory with poor examplees but just because your data isn't hurting now doesn't mean it won't.
I'm gonna sit in a corner with my tin foil hat now.5 -
The main reason I moved from Linux to macOS was that I grew up. If we count not just Linux experiments but prolonged usage, I was an avid Crunchbang fan. After it died, I moved to elementaryos.
What I want to say is, Linux can be very fun and educational when you're still in the uni. You have all the energy in the world, and you can afford to diverge from your daily routine for an hour to debug GPU drivers.
Now, the backbone of my life is keeping a very tight sleep schedule, taking meds on time, avoid infohazards, avoid scrolling on the web, all to remain in a very fragile state of balance that keeps the bipolar disorder away. I'm in the middle of all this, earning derealization (yes, I'm also autistic) every time I design a data model. All I want from my computer is to be treated like a careless, regular user, not like someone with a CS degree.
I use Sublime Merge instead of command line Git. I use Postico to explore PostgreSQL databases, not psql from my terminal. By the way, my terminal is not iTerm, Alacritty or some other such thing, my terminal is whatever came with my Mac, with whatever default settings.
Linux is crawling into a non-street-legal racecar's cockpit and strapping yourself in, ready to blast off. MacOS is your chauffeur, holding your old shaking hand as he helps you into your Maybach's backseat. They're different, and that's okay.
Can Maybach race? Well, it has a 621 HP V12, so if _you_ can race, it probably can too, but we all know it's not a racecar.
Windows? Windows is an SS officer, wearing the all too familiar Windows logo for swastika, throwing you into a gaswagen.16 -
I don't care about market cap. Stick your hype-driven business practices up your ass. Infinite growth doesn't exist. I won't read your fucking books and attend your fucking bootcamps and MBAs. You don't have a business model. Selling data is not a business model. Fuck your quick-flip venture capital schemes, and especially fuck your “ethics”.
I will be the first alt-tech CEO. I only care about revenue. The real money, not capitalization bubble vaporware. You don't need a huge fleet of engineers if you're smart about your technology, know how to do architecture, and you're not a feature creep. You don't need venture capital if you don't need a huge fleet of engineers. You don't need to sell data if you don't need venture capital. See? See the pattern here?
My experience allows me to build products on entirely my own. I am fully aware of the limitations of being alone, and they only inspire lean thinking and great architectural decisions. If you know throwing capacity at a problem is not an option, you start thinking differently. And if you don't need to hire anyone, it is very easy to turn a profit and make it sustainable.
If you don't follow the path of tech vaporware, you won't have the problems of tech vaporware, namely distrust of your user base, shitty updates that break everything, and of course “oops, they raised capital, time to leave before things go south”.
A friend of mine went the path I'm talking about, developed a product over the course of four years all alone, reached $10k MRR and sold for $0.8M. But I won't sell. I only care about revenue. If I get to $10k MRR, I will most likely stop doing new features and focus on fixing all the bugs there are and improving performance. This and security patches. Maybe an occasional facelift. That's it. Some products are valued because they don't change, like Sublime Text. The utility tool you can rely on. This is my scheme, this is what I want to do in life. A best-kept secret.
Imagine 100 million users that hate my product but use it because there are no alternatives, 100 people in data enrichment department alone, a billion dollars of evaluation (without being profitable), 10 million twitter followers, and ten VC firms telling me what to do and what data to sell.
Fuck that. I'd rather have one thousand loyal customers and $10k MRR. I'm different, some call it a mental illness, but the bottom line is, my goals are beyond their understanding. They call me crazy. I won't say it was never about the money, of course it was, but inflating your evaluation is not “money”. But the only thing they have is their terrible hustle culture lives and some VC street wisdom, meanwhile I HAVE products, it is on record on my PH. I have POTDs, I have a fucking Golden Kitty nomination on health and fitness for a product I made in one day. Fuck you.7 -
If you use exceptions for your data validation, I hate you. I hate you so much, in fact, that I will become famous. Then I can say to you that a famous person hates you. I will become president and the first executive order I sign will be to make the official policy of the United States that I hate you. I will invent a time machine so that I can go back in time and on every one of your birthdays, past present, and future, look you in the eyes and tell you I hate you. Then I will travel to your death bed and in your final breath I will tell you I hate you. I will change the timeline so that you will celebrate Christmas and believe in Santa and then tell your four year old self that Santa isn't real. I hope your kids never learn how to read, and if they already know how to read I hope they forget how to read and never learn how to read. I hope all of your friends become vegan, atheist, flat earth, crossfitters and insist on regailing you with their life style on your every meeting.
I guess what I'm saying is that I'm having a bad day.3 -
I was returning something at MicroCenter the other day. The guy in front of me was picking up a laptop be brought in to have fixed. They had replaced the motherboard, and put all his old data on an external drive.
"So what's this?"
"This is an external hard drive. We copied all the data from your laptop onto it and put a fresh install on it."
"So .. how do I get to it?"
"You just plug it in, over USB."
"So how ... how does that work."
This goes on for a while. Shop owner has to start his computer. Plug in the drive. There was a lot of, "So everything that was on here, is now on here?"
The guy had no basic understanding of external hard drives, USB, copying files ... thankfully while the files were copying from the hard drive to his desktop, he said he needed a longer cable to the router so he could put it on the other side of the room. It took the guy behind the desk an unreasonable amount of time to direct him to the isle with the Ethernet cables, but once he did, I was finally able to return my item.
I'm glad I no longer work in desktop support.1 -
I work full time in the data protection field for healthcare whilst investing all my free time into coding as a career change.
I've discovered that despite people telling you how much you need to spend every hour you get free to learn to code, you also need to consider the people closest to you. I was ignoring my partner who I live with because I thought this was more important and that she should be able to see that. But what's the point in being in a relationship if you aren't making an effort with each other?
It's OK to slow down and invest time into the people you have in your life. Give yourself a break. -
There's very little good use cases for mongo, change my mind.
Prototyping maybe? Rails can prototype, create/update/destroy db schemas really quickly anyways.
If you're doing a web app, there's tons of libs that let you have a store in your app, even a fake mongo on the browser.
Are the reads fast? When I need that, use with redis.
Can it be an actual replacement for an app's db? No. Safety mechanisms that relational dbs have are pretty much must haves for a production level app.
Data type checks, null checks, foreign key checks, query checks.
All this robustness, this safety is something critical to maintain the data of an app sane.
Screw ups in the app layer affecting the data are a lot less visible and don't get noticed immediately (things like this can happen with relational dbs but are a lot less likely)
Let's not even get into mutating structures. Once you pick a structure with mongo, you're pretty much set.
Redoing a structure is manual, and you better have checks afterwards.
But at the same time, this is kind of a pro for mongo, since if there's variable data, as in some fields that are not always present, you don't need to create column for them, they just go into the data.
But you can have json columns in postgres too!
Is it easier to migrate than relational dbs? yes, but docker makes everything easy also.11 -
Some staff couldn’t access some admin pages and they thought it was a permissions error. Um, no. Chrome is showing you an “aw snap” error page, which means it’s a problem with the site and not your access. The pages are querying too much data and it’s causing an operation timeout. It’s been like this for months but no one reported it. Did they not need to use these pages at all for these past months? Non technical people keep doings things that make me want to smack my head against my desk. FTR these issues existed before I started.1
-
GraphQL fans, please read the whole rant until you jump in the comments.
I get it, when you have multiple data sources (that aren't always proper databases), your stuff is relevant.
But most of the people use GraphQL when they have a single database. In that case, native joins are always faster than GraphQL dataloader N + 1 BS you have. It takes less time and less code to go to the backend and write an endpoint for the frontend with a DB query than write several GraphQL ones on the frontend and then combine the data with imperative JS. It will work faster too.
So why the fuck should I use GraphQL at all?28 -
pLeAsE dOnAtE tO hElP mE aFfOrD hOsTing
lolwut? you have a free-for-all project with no premium features. Users can’t create accounts. All of your code is JS, you don’t even need a server. Just host your stuff on Cloudflare. I have just about a gigabyte of data uploaded there on my free account, so if I can do it, so do you. Just use a CDN for your client-only, JS-only project.
domains though… yours is long and costs around 40 bucks a YEAR.
if you made a good product and want to make some money with it, that’s completely okay, so just say so: “I want money for my work, but I don’t want to take away features that were free and can be provided at no additional cost, so please donate”. Why lie? It’s not like people who won’t donate to you based on this justification will magically donate for “hosting”.4 -
Marketing material for a RasPi-based device that, supposedly, secures all your traffic from hackers by (translated) "encrypting traffic to your router" and "sharding and dispersing your data, so nobody can read it".
Stay tuned to see what it actually does (waiting for an email reply from it's creator) 6
6 -
Just a quick thought...
If you are storing files in your Windows computer, you are giving data to them for free.
Who knows? Whether they have "root:" access to computers all around the world. Same with macOS.5 -
* break it into elementary steps, small enough to fit into your "estimation time unit", e.g. days or hours.
* estimate those steps for "developing at a leisurely pace" if nothing goes wrong.
* think about "what could go wrong" (list everything!) and adjust values accordingly.
* adjust total amount with experience values, like:
* times 1.2 for every manager
* times 1 to 4 based on which legacy projects i have to touch
and finally:
* multiply with `1+log(t/u,2)`, with `u` being the amount of useful data in the requirement description and `t` being the total amount of data in the requirement description
* sample: with our current "favourite" customer, about 90% of all tickets is garbage, so t/u = 100/10 = 10 => log(10,2) = 3.3 => multiply everything with 4.34 -
Hello,
I have gone through all the options that your public API has for syncing data, and i can now officially say that stripping an iFrame of a Google Drive page would be better than the piece of shit mutation methods you have come up with.
Most sincerely,
A fucking annoyed dev that just wasted about 4 hrs on your shit. -
48 hours.
We had 3 weeks of "manual data collection": pencil, paper and a dozen of people around all the offices of the company with the task to collect serial numbers of every piece of equipment used.
Then we had 3 weeks of data entry, a dozen of people copying all handwritten data to a custom made VB form.
And then there was me, the guy that was in charge of verifying, zipping and sending the data to the client. I spent 48h non stop to go through everything, finding, fixing or delete unusable data.
I had to delete at least 25% of the data because incomplete or completely unusable (serial numbers too short or too long, for example).
48h in the office.
The data was then delivered to the customer. 2 days after, when I finally woke up, everyone was in panic because:
- serial numbers were not matching
- addresses were wrong
- the number of delivered records was smaller than expected
What did I learn from this experience?
When your deadline is tomorrow, and you need 4 weeks to complete your work, ignore the deadline and inform everyone at any level that you are ignoring the deadline. And then resign and find a better job.
Ah, yes, pencils and paper are powerful tools, but rat poison too. You just need to use them in the right place. The only data collection that can be trusted when done with a pencil is the one involving checkboxes.1 -
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
copying field data from one table to another,
wondering why the execution takes so long,
since your copying only data from three rows,
realising you forgot the WHERE clause in the SQL while working on a live database and overwriting all data with the last statement 😨6 -
Hey, up for a challenge?
Upgrade to iOS 12 beta 2,
When all of your apps fail to open and u can only use apple safari, notes & other apple apps, start regretting the decision and downgrade your phone to iOS 11.4 when your phone starts up in data recovery mode and fails to recover data and then u need to send mom a sms of that picture of your family and explain the reason for why all of your data got deleted send me a picture so I can see how I did😤...
I deleted my jailbreak for this shit?!
(I understand it's a beta, but cmon on beta 1 haw of my apps didin't work, and on beta 2 I needed to restart my phone for 6 times before apps might start working and u need to wait 2 weeks before another beta releases, fuck off appl. With this beta shit, I guarantee there were thousends of users with same issue fix tht.) 2
2 -
Yo fun idea you know who most certainly knows which cookies are stored in your browser??? YOUR FUCKING BROWSER!
How about uuuummmmmm... When making a proposal about annoying users with cookie notices suggest that browsers implement it ALONG WITH A YES, TAKE ALL MY DATA ALWAYS I JUST WANT TO USE THE FUCKEN INTERNET button?
Fuuuuuck me those notices are so dumb!1 -
ATTENTION PLEASE! Important announcement following:
Please check your interface implementations for correct byteorder according specification BEFORE YOU START COMPLAINING ABOUT DATA FAILURES ON EXCHANGING DATA.
Freakin hell, if I'd get some money for every byte order mismatch on testing interfaces, I'd be a be a billionaire.
And why are all those highlevel I-know-every-fucking-framework developer incapable of checking the real memory content of a datatype, and the real data content on the interface even if you tell them that their byte order is obviously wrong?
No, your system is not the centre of the universe and I don't care how you get your less-than-32bit-datatypes-are-for-assembler-usage-frameworks to change byteorder. It's not rocket science, if there's no ready-to-use-function then write those 4 lines yourself.
Next time I get to specify an interface I'll go for mixed-endian, just to make sure everybody involved knows the concepts of endianess afterwards.2 -
Software RAID 1 is better than hardware RAID 1! Here's why:
1. Hardware RAID controllers do fail, and when they do, they kill all hard drives connected to them.
2. If your controller didn't fry your hard drives when it failed, you'll have to find the exact replacement, or you can kiss your data goodbye. You installed a hardware RAID array using second hand Broadcom controller three years ago, and now it failed? You better get on looking for the same controller of same revision running the same firmware version (of course you can't update firmware yourself) if you want your data back. Oh, Broadcom discontinued this model? Tough cookies. With software RAID, everything is easily recoverable.
3. You save a lot of money you can invest in other parts of your system. Good hardware controllers, even second hand ones, don't cost less than $200.
Performance loss is negligible.
RAID built into your motherboard is the worst of both worlds: it's just the software RAID you can't reallly control. Don't do that.
Hardware RAID is only worth it if you have a contract with your hardware supplier that says they're responsible for managing your RAID array. They have the resources to replace failed controllers properly. You know how IBM installs full rack worth of servers just to disable 70% of them because of your plan limitations? It's easier for them to do that than to physically go there and take servers away, just to reinstall them when you grow. Yeah, that kind of contract at that kind of level. If you're there, you don't need me telling you all that.
TL;DR: if you want to buy a two 8TB hard drives for $150 each on newegg and a used RAID controller to make RAID 1 array, you can make both 16TB _and_ make your system more reliable. Reliability is what you're after if you want RAID 1, isn't it?
What are you do... wha... no! stop! are you gonna buy a raid box from Aliexpress? are you fucking crazy?!8 -
I finally attempted php, I wrote a bunch of scripts to fetch data... I feel like I have betrayed myself 😞😞😞
I should have just absorbed the cost of azure 😭😭😭 now am a php dev.... The things I'm about to do, the horrors I'm about to put out into the world.... Pulling your hair out will be the least of your worries, dear maintainer forgive us all, always and forever. 😳1 -
DEAR NON TECHNICAL 'IT' PERSON, JUST CONSUME THE FUCKING DATA!!!!
Continuation of this:
https://devrant.com/rants/3319553/...
So essentially my theory was correct that their concern about data not being up to date is almost certianly ... the spreadsheet is old, not the data.... but I'm up against this wall of a god damn "IT PERSON" who has no technical or logic skills, but for some reason this person doesn't think "man I'm confused, I should talk to my other IT people" rather they just eat my time with vague and weird requests that they express with NO PRECISION WHATSOEVER and arbitrary hold ups and etc.
Like it's pretty damn obvious your spreadsheet was likely created before you got the latest update, it's not a mystery how this might happen. But god damn I tell them to tell me or go find out when the spreadsheet was generated and nothing happens.
Meanwhile their other IT people 'cleaned the database' and now a bunch of records are missing and they want me to just rando update a list of records. Like wtf is 'clean the database' all about!?!?!?
I'm all "hey how about I send you all records between these dates and now we're sure you've got all the records you need up to date and I'll send you my usual updates a couple times a day using the usual parameters".
But this customer is all "oh man that's a lot of records", what even is that?
It's like maybe 10k fucking records at most. Are you loading this in MS Access or something (I really don't know MS Access limits, just picking an old weird system) and it's choking??!?! Just fucking take the data and stick it in the damn database, how much trouble can it be?!!?!?
Side theory: I kinda wonder if after they put it in the DB every time someone wants the data they have some API on their end that is just "HERE"S ALL THE FUCKING DATA" and their client application chokes and that's why there's a concern about database size with these guys.
I also wonder if their whole 'it's out of date' shit is actually them not updating records properly and they're sort of grooming the DB size to manage all these bad choices....
Having said all that, it makes a lot more sense to me how we get our customers. Like we do a lot of customer sends us their data and we feed it back to them after doing surprisingly basic stuff ever to it... like guies your own tools do th---- wait never mind....1 -
Time to switch to offline and hide in some dark corner to get work done. Tired of all the IM’s and coming over to my desk from 1 person for “critical” work. If they’re all critical then none of them are truly critical. If you sit on the data for 2 months, and then today is the day it becomes critical and the compliance issue is because of your ineptitude then its a you problem not an IT problem. Then on top of that you submit your data to be loaded in the incorrect request form and spreadsheet format you can go fuck yourself asking this be done in an hour. It could be done in 15 minutes if you had it in the correct format as specified in the 20 meetings over the past year which removed all manual analysis and automated the entire process you idiot. Now I have to get it into the correct format in that hour so I don’t have to do the analysis for you.
I have other things to do besides your etl tickets, like finding the actual problems in our actual critical applications. You know the ones where the VP’s of this giant corporation start calling if they go down.
Sorry for the rambling guys. -
Play Store's $25 registration fee - for getting PWA listed in their shitty catalogue? Who in the right mind would even jump in this clusterfuck of store to find a *web* app? For all you know, Google, there is such thing as QR codes - and customers can just scan the code (or type in that sweet address). Voila! Boom!!! Ching-ching!
Hello-hello, monopolistic cashgrabage! I came to inform you that your TWA bullshit is unneeded in ETHICAL space. The only ones who would benefit from this thing are permission-hungry publishers. And I'm already sick of this culture where people are put into store bubbles. You can't hide the fact that this data and features you provide, with "native" layer, may be misused in a jiffy - and by big players, no less. Of course, as a vile dumpster that you are, you don't mind it.
Don't even bring up a battery consumption that comes with PWA and browser. This doesn't matter if you use an app for some 2 minutes to tick your mental checkboxes! I'm just sick of app stores and native apps that collect the data without normal warning, and dare to take more than 1 second to fucking load the cached data. Take a lesson or two from PWAs that collect (probably useful) cache, instead of my specs, and load almost instantly.12 -
Perhaps as a tip for the junior devs out there, here's what I learned about programming skills on the job:
You know those heavy classes back in college that taught you all about Data Structures? Some devs may argue that you just need to know how to code and you don't need to know fancy Data Structures or Big o notation theory, but in the real world we use them all the time, especially for important projects.
All those principles about Sets, (Linked) lists, map, filter, reduce, union, intersection, symmetric difference, Big O Notation... They matter and are used to solve problems. I used to think I could just coast by without being versed in them.. Soon, mathematics and Big o notation came back to bite me.
Three example projects I worked in where this mattered:
- Massive data collection and processing in legacy Java (clients want their data fast, so better think about the performance implications of CRUD into Collections)
- ReactJS (oh yes, maps and filters are used a lot...)
- Massive data collection in C# where data manipulation results are crucial (union, intersection, symmetric difference,...)
Overall: speed and quality mattered (better know your Big o notation or use a cheat sheet, though I prefer the first)
Yes, the approach can be optimized here, but often we're tied to client constraints, with some room if we're lucky.
I'm glad I learned this lesson. I would rather have skills in my head and in memory than having to look up things and try to understand them all the time.5 -
"Ughh, you're such a lazy person. Why don't you finish it instead of making me do everything afger I asked YOU to do it"
I am so fucking done playing family technicman for you. I copied all of your data from your old phone to yojr new one. I set up everything except personal accounts because I respect privacy. You only need to insert your damm sim card.
And don't you even try giving me that "I tried but could not do it, it's just to complicated"
I could buy the same phone, throw it at you and pay the lawyer if I would get one cent for each time you said that.1 -
Mf php and mf mysql database. Fuck you for being such a cunt.wasted my whole fucking day to configure the shit i didnt even broke. All i wanted from your ass was a storage for users but no you piece of shit. And a fucking special mention for php bcz that shit is a stinky piece of work.
All this aside i need a db which can store some data and is easy to use and not an sql one for my very small cllge project. Anything that i can use from my java app.8 -
Waiting 3 days for your graphics card to get trough all training data to see if you wasted your life with bad architecture.13
-
Windows after a fresh installation be like
Preparing, seting things up for you, do you want to use cortana, do you want to give us all your data, windows is all yours, configuring, Setting up, almost there
Thanks for letting me wait in order to set things up to rip off my data and then announcing that the computer i bought is all mine -
Getting all the shitty half-broken stuff because you're 'just a contractor'...
...and not being allowed to use your own top-of-the-range stuff due to 'data security policies' 😧1 -
My worst fight with a dev was definitely that time I tried to break the mould and build this incredibly tedious VB app to automate data handling through Excel, PowerPoint and Outlook. The other dev always said "you can do this" and "come on, it's not rocket science" and I was always like "yeah, dude, sure, but can you help me with this bit here, please, I'm so stuck on it?" He'd be all like "ofc bro, I got your back", but when it came to the actual work that needed to be done, he was all silent. Needless to say, now I have a rubber ducky to help me with my dev needs, as talking to myself felt like a nightmare. Guess that's what other people feel like when I strike up a conversation with them, too.
-
Hi!
I was trying to format my backup drive (/dev/sdb)
Was focused on eating also at the same time
Wrote sudo fdisk /dev/sda and didn't notice and changed the partition type to GPT(although it was already like that)
I gave me message that will do on next reboot
My dumb mind didn't suspect, instead rebooted (facepalm)
Lost all my data
Instead of trying to recover was quick to install OS
Permanently lost my data
Help me I need hopes and tricks to move on
How did you cope up with yourself once you lost all your data?2 -
Don’t fall for the “language A is better than language B” -it’s all just syntax (within the same paradigm). Learn higher concepts such as: data structures, abstraction, loops, variables, conditionals, functions.
Only then can you decide that your favourite language is better than anyone else’s...5 -
Taking over from/working with an external dev company on an existing project.
Listen Mr CEO, I'm not here to mess with your firm's code and undo all of your work. I'm just doing my job. Stop telling me that the only thing left to do is "data" without any context. The site that I'm here to work on isn't even finished. -
pandas can suck my balls.
N
I
H
I'd rather roll my own.
edit: but also xgboost can suck my balls.
Treating every OBVIOUSLY continuous-valued entry as a 'category'.
All searches for this problem turn up tutorials and documentation on how to CONVERT continuous and numeric values into classes or categories.
Not a single fucking document addresses the problem of when pandas or xgboost refuses to treat numeric inputs as numerics and insists on pushing an error that your data is categorical when every fucking inspection shows the type as numeric.7 -
I am studying an online data science course in python offered by Microsoft.
The instructor uses Surface book and also has a Mac book on his desk for backup because windows.
He uses chrome all the time for his explanation to run jupyter.
The point is even they know their tech is shit but still "Windows has set your default browser to edge" - this happens
¯\_(ツ)_/⁻1 -
I don't know how much of this can be considered data loss but one one of my uni classmates frustrated by some hellish tasks (cleaning some old code files probably) decided that everything in that particular directory won't be of any further need, so she procede to rm -rf it.. only to discover that the terminal opened in that dir was another one and her current one (the one she bashed that unforgiving rm) was in fact a standard freshly opened term where any term would open.. in the user's (only user) home dir... such a face she had when all her codes, homeworks, projects and everything went to oblivion 😂😂 jokes aside it was a good thing that the semester was almost finished, all hws submited and no important data was there as she dual booted with ubuntu and some windows, but funny thing how such a honest mistake can ruin not only your day, but maybe your entire semester1
-
=Your Human Body!!= what do u think you run on in real life??
What do you think you run on??
Brain: C++
Skin and bones: HTML + CSS
Data: Typescript or Javascript Or Node.js
Walking and breathing: Python
Defense: Java cause every white blood cell is a new class
sleeping is basically C++ packing in all the files unless someone gets drunk they cant pack correctly thats why their brain is probably messed up >=) i would say the beer is corrupted code folders16 -
Why everyone who decide to try Linux installs Ubuntu? I don't find it useful friendly at all. And adding a repo every app is daunting. And on top of that on their official site there isn't a single mention of Linux. And yeah, Canonical make money off your data.24
-
Client wants me to document the updated patch in the system... In detail. I just want to upgrade their server memory but noooooo. They want me to detail it all in step-by-step, including change impact, description task, expected time duration, back-out plan.
The first time I had to do this, it was cute. But now it's FUCKING ANNOYING ON HOW DETAIL THEY WANT ME TO PUT IN!!!
Client: "OK, so you wanna upgrade the server memory. What do you need to bring into the data centre?"
Me: "Just my laptop. I'm just configuring your underutilised server memory and upgrade it."
Client: "Good. Put that in the document, including your laptop serial #, make and model."
Me: *Screaming internally* -
Dell Summer Internship Experience
Firstly,to be a part of this process it is important to clear the exam conducted by college and according to me it wasn't something which can't be easily achieved so to prepare of this exam stick to basics of all subjects which have been taught so far till semester majorily data structures,data base,Java,C, operating system were asked.Basics of all following subjects should be clear which also going to help during internship.I myself prepared for the test from geeksforgeek.I tried to gain as much as basic knowledge of subjects I can.And after selecting from test you have you go through hackathon on that personally I think one should be prepared with latest demanding skills.Mostly all the hackathon topics were in and around Machine Learning,Block chain,Web development,Databases.So typically should be aware of all these technologies and how this can be used to enhance in project.During hackathon days it is important to be interactive,it is good to clear doubts or explain your idea and how innovative you project is and how different it can be and further keep in mind how your project can be industrial utilized.Try to make your project more in aspect of how industry going to adapt this or how this problem's solution is perfect in every terms for a company.And majorily at last it comes down to how to present your project infront of your panel.I think keep that session as much as interactive you can,try to answer their queries,and most importantly know your part of the project very well on theoretical as well as on code level. At last you have to go through a HR interview in which firstly you have to be prepare with a nice resume in which you to include all your achievement's,projects and most importantly keep it short and simple and include only those things which you are completely aware of.For interview first try to know and learn about company, it's goals,in what field it is presently working and during interview there is nothing to worry about you just have to talk like you are talking with a normal person,express all your views ,try to speak out. Confidence is one important thing for this interview.So this was conclusion of my experience from hackathon hiring process from Dell.4 -
Please, dear god, is there a browser extension to answer all these shitty cookie/data storage/privacy popups with MY SPECIFIC ANSWER?
As a web dev I understand that websites need cookies, and as a tech company employee I understand that essential cookies as well as functional cookies are okay-ish (most of the time). I just don't want marketing cookies/tracking.
All those extensions just block the popup or block all cookies. This is not what I want!
And why the hell on earth didn't they come up with one single solution for all websites beforehand, so we dont have 6.388.164.341 different popups/bars/notifications/flyouts/drop-ins/overlays???
THIS. IS. JUST. ANNOYING.
Thank you for your attention.6 -
“httpOnly cookies prevent XSS attacks”… wow.
As if not being able to get your cookies is going to stop me from doing bad things.
When I'm in via XSS, it's over. I'm changing the page content to your sign-in form with “please sign in again” notice, but it sends email/password straight to me. What percentage of users is going to enter their data? What do you think? With password managers prefilling data, and the annoyance being one “enter” hit away, I think a lot of users will fall for that. No one, including you, will be able to tell the difference without devTools.
You can rotate the session token, but good luck rotating the user's password.
Oh, did I tell you I could register a service worker using XSS that will be running in background FOREVER?
But don't listen to me. Don't think. Just use httpOnly and hope for the best. After all, your favorite dev youtuber said they could protect you from XSS.4 -
Guys im about 800km away from my desk, all i have is my smartphone with sololearn, maybe let's gather some ideas for projects which you can create on your smartphone on toilet ?
Ill start:
1. Fake data generator3 -
TLDR: Being taken of my assigned dev tasks to do a basic word mail merge.
Why am I doing a word mail merge again?
Oh yeah because the business are that used to oh well if it's more than two clicks IT will do it. The only bit that would be considered hard (using that word loosely) is the address block.
No totally not mad that you had me write a mail merge for dip shits guide which isn't being used. No totally not pissed that you now want me to drop everything I'm doing for this basic task.
The fucks can't even pull the right data. Here's the data for the mail merge. Great your missing some key bits. The fucking addresses and names of the people.
I think what's pissing me off the most is I'm not being technically challenged at all and any chance I get to do something that would be is taken away to do something basic you learn in school. -
Thoughts after a security conference.
The private sector, no matter the size, often plays a role (e.g. entry vector, DDoS load generating botnet, etc.) in massive, sometimes country-wide attacks. Shouldn't that make private businesses' CyberSec a matter of national security? Shouldn't the government create and enforce a security framework for private businesses to implement in their IT systems? IMO that'd also enforce standardised data security and force all the companies treat ITSec with at least minimal care (where "minimal" is set by the gov)
What are your thoughts?9 -
Random question...
Do you guys happen to know a nice videocall website and/or app for smartphone (Android)?
Possibly one that doesn't send all of your data to third parties and whatnot? °w°
Thaaaaanks ♡9 -
What is your wishlist for things that need to die or change next year. Mine is :-
1. Games that use peer to peer and have servers for data. Please buy servers on aws or any good cloud service.
2. ISP's that block all incoming connections for security5 -
https://stilldrinking.org/programmi...
/\ This is why all programmers should go on strike for a month and collectively collaborate to code a new, clean, bug free internet where nobody but you can control your data.
Also. It should only be added to by people who know how to code in order to maintain this clean code.
We can call it "internet level 2" or "internet 2.0"4 -
Not a data loss exactly but a loss indeed.
It was my first week at my first junior developer job, I was just learning git and completely messed it all up. I lost around 3 hours of work.
I didn't want to ask anybody for help (because of that useless junior feeling, you know...) and wasn't as good using Google as I'm now.
So I re-did all the work. Thankfully, I have a decent memory.
If there's something to learn here is ask for help when you've used all your resources and still think you need it. Nobody is going to have a bad opinion about you ;) -
Conspiracy theory:
AI is peddled around companies because it's a great front for them to take all of your data and "train their models", ultimately its all about legally owning what you create and use it for self-promotion with minimal extra cost.
There isn't actually any "AI models" in the back of the company tech stack. It's just a word on a legal document as an excuse to take your data.1 -
To all my Machine Learning engineers, Ive been doing Frontend development for 6 years and I'm done. Wanting to get into machine learning because I've always loved data.
1. What is your day to day like?
2. Any advice for my learning journey?
Thank you🙏14 -
Co-workers conversation about the new Google Pixel... "I won't get it because they steal your soul, same reason why I don't have the iPhone with the finger print.. they want to have all your information... blah blah..."
I laugh, because they device doesn't matter... your info gets stolen in transit... so all your snap chat, IG DMs, and all of communication potentially at risk to be "stolen".
Example, Gov't splicing into underwater fiber optic cables and redirecting traffic to a data center...
Understand the tech.. please.2 -
State of CSS 2022 is out.
It’s the best way of learning all new fancy properties. Just open the survey and google all of them! You may take it as a guest and not submit it if you don’t want to share your data.
https://survey.devographics.com/sur...5 -
The pain of creating a data pipeline in AWS to dump all your DynamoDB tables into S3 is something I don't want anyone else to go through..Why don't you have a copy button..😭😭
-
What are the thoughts of privacy conscious people about quantum computers? As far as I understand current TLS version encryption method is vulnerable to quantum computers, thus if your ISP or other agencies store all your traffic data right now, they'll be able to decrypt it after gaining access to quantum computers.
One way to secure your privacy would be to use your own VPN that uses encryption method that is quantum-resistant, but again the VPN would be using TLS to connect to the Internet.6 -
Make an Async task (Java) and...
DONT use a loop to iterate though a time series collection. Don't linear search that shit.
DO use a queue and pop() it like its hot. Check that shit to see when it needs to be used instead of searching.
DO assert that your time series data is in order (Predication mother fucker).
DO throw an exception that you data is all fucked when it's all fuck up.
Stay sexy and use a fucking queue man.5 -
So, I've been seeing a lot of people concerned about privacy around here lately.
I completely understand it, and I too, don't want all my data to be available for anyone at any given time. I get it.
However, the only way to get privacy, is to build it yourself.
Buying a phone? Who says (apart from the company itself) that it doesn't have some integrated chip, or that the os lies to you or w/e
When using your phone, who says your Sim provider isn't intercepting all your traffic with a man in the middle attack?
These sound like conspiracies, however, if you really want privacy, either build it yourself (or with other privacy activists) or let go of the comforts of technology (i know, you're not the only source of info about yourself, the only way to shield yourself is to go into the woods and live a simple life.)
It's pretty sad that these are the two options, but I've yet to find a better one.
(ps, I used to have a "no logs, no ip, no anything" VPN provider, and as soon as some agency requested info, they got it, so I wouldn't easily trust the promise of 3rd parties anymore.)12 -
I want to know how a certain type of software is called.
I once saw a talk where someone tracked his personal life for a year or so. This means photos are tomestamped and have a geolocation. Emails and phone calls are timestamped as well ...
On a timeline software he could then see exactly where he was and what he did on a specific date like 2 years ago...
There's a name for software that tracks all kind of data about your personal life. I think it starts with m.12 -
(Warning, wall of text)
Settle an argument for me. Say you have a system that deals with proprietary .foo files. And there are multiple versions of foo files. And your system has to identify which version of foo you are using and validate the data accordingly.
Now the project I was on had a FooValidator class that would take a foo file, validate the data and either throw an error or send the data on its merry way through the rest of the system. A coworker of mine argued that this was terrible practice because all of the foo container classes should just contain a validate method. I argued that it was a design choice and not bad practice just different practice. But I have also read that rather than a design choice that having a FooValidator is the right way to do OOP. Opinions?1 -
Today I called my ISP and shouted what the hell is your wireless service, I cannot even open youtube. Then they asked from what time you had the issue we are not able to see any data.
All of a sudden I saw I was disconnected from dongle and got connected to Wifi automatically (So i was on wifi). I feel ashamed then all of a sudden I scolded them and told yes because of your shitty service am not able to use!! :)24 -
!rant
Hi fellow DevRanters! I've been studying software engineering for a while now and, while I love programming, I'm starting to think that all I'll be doing as a software engineer now a days is pulling data from a database, sticking it in a nice gui with some buttons and moving on to the next, similar, project. At the same time I am loving linux more and more, I love working with bash and other unix-like tools and I am interested in systems languages like C and Rust. It is for these reasons that I am playing with the idea of switching to Systems and network engineering. What are your thoughts on this? Is Systems and network engineering a field in which I get to program a lot? Will there be more variation in it? Is my view of software engineering completely off? Please share your thoughts and opinions! -
does anybody here use diaspora*? for those who don't, it's a free (as in freedom) social network and protocol thereof, and it employs a decentralized, distributed approach. you can choose a "pod" to store your data, and search for people and content inter-podly. as a decentralization/distribution/foss enthusiast, i love the project and check regularly, but sometimes i get the feeling that i'm all by myself there, as i have no friends yet and all the content i see is just my followed keywords. (so befriend me, maybe? :D)5
-
Never underestimate the power of a misplaced static in your Java to totally fuck you over.
I was busy with my computer science project for the semester where we have to implement a Sudoku solver without backtracking by using graph theory.
So there I was writing my data structure for the grid when for some reason all the cells were initialized with the value 8.
After a whole night of debugging I was about to start over when I realized I had made my array static.
And boom, it works. WTF!!!!!!!2 -
Fuck external stake holders, like politicians, those know-nothings, that pump their ego by finding multiple "issues" with our software like how we display the privacy data agreement and impose their stupid fucking nonsense rules on our software. Even if it is not part in any official law or GDPR
So there is the request that one needs to scroll down the whole data privacy crap nobody reads until you can press "Continue" and we *have* to implement that shit. Although it is completely out of line with Apple's usual installer handling. Nobody will understand it. It cripples the workflow.
But some Mr. Important demanded it, as if he is protecting users with this and makes a great contribution to the data privacy in our country. Yeah! And guy is so high up, unreachable for us through all the layers of other people, leaving us no time and means to dissuade this shitty request. If all your 'ideas' are so great you should not be allowed to do jack shit.1 -
I’m working on a new app I’m pretty excited about.
I’m taking a slightly novel (maybe 🥲) approach to an offline password manager. I’m not saying that online password managers are unreliable, I’m just saying the idea of giving a corporation all of my passwords gives me goosebumps.
Originally, I was going to make a simple “file encrypted via password” sort of thing just to get the job done. But I’ve decided to put some elbow grease into it, actually.
The elephant in the room is what happens if you forget your password? If you use the password as the encryption key, you’re boned. Nothing you can do except set up a brute-forcer and hope your CPU is stronger than your password was.
Not to mention, if you want to change your password, the entire data file will need to be re-encrypted. Not a bad thing in reality, but definitely kinda annoying.
So actually, I came up with a design that allows you to use security questions in addition to a password.
But as I was trying to come up with “good” security questions, I realized there is virtually no such thing. 99% of security question answers are one or two words long and come from data sets that have relatively small pools of answers. The name of your first crush? That’s easy, just try every common name in your country. Same thing with pet names. Ice cream flavors. Favorite fruits. Childhood cartoons. These all have data sets in the thousands at most. An old XP machine could run through all the permutations over lunch.
So instead I’ve come up with these ideas. In order from least good to most good:
1) [thinking to remove this] You can remove the question from the security question. It’s your responsibility to remember it and it displays only as “Question #1”. Maybe you can write it down or something.
2) there are 5 questions and you need to get 4 of them right. This does increase the possible permutations, but still does little against questions with simple answers. Plus, it could almost be easier to remember your password at this point.
All this made me think “why try to fix a broken system when you can improve a working system”
So instead,
3) I’ve branded my passwords as “passphrases” instead. This is because instead of a single, short, complex word, my program encourages entire sentences. Since the ability to brute force a password decreases exponentially as length increases, and it is easier to remember a phrase rather than a complicated amalgamation or letters number and symbols, a passphrase should be preferred. Sprinkling in the occasional symbol to prevent dictionary attacks will make them totally uncrackable.
In addition? You can have an unlimited number of passphrases. Forgot one? No biggie. Use your backup passphrases, then remind yourself what your original passphrase was after you log in.
All this accomplished on a system that runs entirely locally is, in my opinion, interesting. Probably it has been done before, and almost certainly it has been done better than what I will be able to make, but I’m happy I was able to think up a design I am proud of.8 -
First let me start this rant by saying: Don't use SharePoint lists as your primary data store if you can avoid it. You're gonna have a bad time.
My coworkers and I work on a system where we need to pull tons of data down from a SharePoint site and run various algorithms and operations on it. Generate reports, that sort of thing. This is all done in the browser using a Typescript React SPFX webpart. Basically using SharePoint as a DB/DAL.
Because of the sheer amount of data we end up pulling down (our system in production is the single source of truth for one of the largest companies in Canada, and they're currently building a pipeline as we speak), in order to maintain a reasonable speed while using it, we have some pretty intense caching logic implemented, logic that ensures we get new items when new items are detected, and merges changes to already exisiting objects. It's pretty brilliant, and that's before we even consider the custom paging that my coworker implemented in order to get around the IndexedDB max size of 100MB.
Well that's all well and good, and works great in production, but it is a horror to work with. Because EVERYTHING we touch on the server is cached locally, it can be IMPOSSIBLE to detect data anomalies, be they local or server side -.- You don't know how many hours I have completely WASTED fixing a "bug" that didn't really exist... Just incorrect data in the cache12 -
If your manager asks you to write a raw algorithm based on raw data in order to properly structure, sort and filter that data, how long do you take on average to complete said task?
Example:
Here's a text file with a bunch of continuous data like: john doe 5555 my street 123 karen wiscott 12347 her street 22 peter wright
..and then you first have to start identifying boundaries for each data entry (which is a task on its own, with comparators and shit), solve its bugs.. then you have to make sure it's properly getting sorted.. sort those bugs.. Yeah, it just takes a long time for me to figure all that out.
It takes me 4-5 days on average since I'm a junior but managers expect it to only take 1-4 hours.. madness..4 -
!development related
The problem with working for a school is depending on the district and there policy the sites you need are blocked. The district I'm at today blocks devRant and I'm posting this using mobile data.
LIKE WTF I FUCKING WORK HERE YOU ASSHATS LET ME FUCKING ACCESS THE SITES I NEED/WANT TO VISIT. I WORK FOR THE FUCKING DEPARTMENT THAT KEEPS ALL YOUR SHIT WORKING!2 -
Three Layers of Security
As InfoWorld notes, all smartphones have three basic
elements of security. Your first major task as a mobile
user is to become aware of these layers and enable them
in your devices:
1. Device Protection: Allowing remote data "wiping" if your
device is ever lost or stolen.
2. Data Protection: Preventing corporate data from being
transferred to personal apps running on the same device
or personal network
3. App-Management Security: Protecting your in-app
information from becoming compromised. 6
6 -
You know what really grinds my gears? Products that have no right of linking your data to an online platform.
Case and point: Password Managers. Nearly all of them work only with an account on a given service, have the passwords stored on their servers and so on and so forth. There is 0 transparency and for that matter 0 security. I found my choice, though it infuriates me terribly.
Another thing are budget managers. The switch for YNAB from local to on servers really annoys me. They should have no business in storing my very private data on their server. I don't understand people using it either.1 -
Dell Summer Internship Experience
Firstly,to be a part of this process it is important to clear the exam conducted by college and according to me it wasn't something which can't be easily achieved so to prepare of this exam stick to basics of all subjects which have been taught so far till semester majorily data structures,data base,Java,C, operating system were asked.Basics of all following subjects should be clear which also going to help during internship.
I myself prepared for the test from geeksforgeek.I tried to gain as much as basic knowledge of subjects I can.And after selecting from test you have you go through hackathon on that personally I think one should be prepared with latest demanding skills.Mostly all the hackathon topics were in and around Machine Learning,Block chain,Web development,Databases.So typically should be aware of all these technologies and how this can be used to enhance in project.
During hackathon days it is important to be interactive,it is good to clear doubts or explain your idea and how innovative you project is and how different it can be and further keep in mind how your project can be industrial utilized.Try to make your project more in aspect of how industry going to adapt this or how this problem's solution is perfect in every terms for a company.And majorily at last it comes down to how to present your project infront of your panel.
I think keep that session as much as interactive you can,try to answer their queries,and most importantly know your part of the project very well on theoretical as well as on code level. At last you have to go through a HR interview in which firstly you have to be prepare with a nice resume in which you to include all your achievement's,projects and most importantly keep it short and simple and include only those things which you are completely aware of.For interview first try to know and learn about company, it's goals,in what field it is presently working and during interview there is nothing to worry about you just have to talk like you are talking with a normal person,express all your views ,try to speak out.
Confidence is one important thing for this interview.So this was conclusion of my experience from hackathon hiring process from Dell.2 -
So I have some OPC server to pass a lot of data to another app. And this developer is telling me that a "delete" event for a tag is not arriving into that app. So few emails flow back and forth between us, me trying to explain where that bastard event goes, he insisting nothing sort of arrives on his side and it's my server's fault. Until a meeting is set with my manager and his.
Dev: so I have no actual data from your server.
Me: can you seek, please, within your code if struct X is passed on from the server?
Dev: yeah, it appears a lot of times but I haven't seen any instance with your delete event.
Me: ok then, is it any place where you implement the main interface of the OPC client? There is a method in it where all the events are sent. You can put a breakpoint and I cand send you only this event.
Dev: hmmm, I'm looking for it.
[after couple of minutes]
His manager: Dev, did you find that class?
Dev: hmmm, I'm don't know...
His manager: can you add that breakpoint?
Dev: it's not necessary, I can fix it the "delete". -
I have the creeping feeling that my laptop is going to kick the bucket (in some way or another) soon. I've had two laptops die on me, both times it was something breaking inside the HDDs and I ended up loosing almost all of my data in both cases.
This time I want to be prepared. How do you guys back up your stuff? Is there a way to take a complete image of all my files? (for windows) or should I manually sift through my files and save them in an organized manner on an external disk?11 -
As V1.0 I found Allo quite fine. Google assistant is so cool answering a lot of questions that you would rather switch to chrome and browse Google search results etc.. About encryption issues, I'm not a CIA agent and I have no problem if they use my data to improve the app utility. That's what AI and machine learning are all about. And please, don't tell me that Facebook or other services don't store your conversations. What is missing is SMS/MMS support and a Desktop client, that's it.1
-
So I've been using Duet on my iPad Pro for a couple years now (lets me use it as an external monitor via Lightning cable) and without issue. Shit, I've been quite happy with it. Then the other day, whilst hooked up to my work laptop, there was a power fluctuation that caused my laptop to stop sending power to connected devices. Which is fine - I have it plugged into a surge protector so these fluctuations shouldn't matter. After a few seconds the laptop resumed normal operation and my connected devices were up and running again.
But the iPad Pro, for some reason, went into an infinite boot loop sequence. It reboots, gets to the white Apple logo, then reboots again.
In the end, after putting the iPad into recovery mode and running Apple's update in iTunes (as they recommend), it proceeds to wipe all my data. Without warning. I lost more than a couple of years of notes, illustrations and photos. All in one fucking swoop.
To be clear, you get 2 options in iTunes when performing a device update:
1. UPDATE - will not mess with your data, will just update the OS (in this case iPadOS)
2. RESTORE - will delete everything, basically a factory reset
I clicked UPDATE. After the first attempt, it still kept bootlooping. So I did it again, I made sure I clicked UPDATE because I had not yet backed up my data. It then proceeds to do a RESTORE even though I clicked UPDATE.
Why, Apple? WHY.
After a solemn weekend lamenting my lost data, I've come a conclusion: fuck you Apple for designing very shitty software. I mean, why can't I access my device data over a cabled connection in the event I can't boot into the OS? If you need some form of authentication to keep out thieves, surely the mutltiple times you ask me to log in with my Apple ID on iTunes upon connecting the damn thing is more than sufficient?! You keep spouting that you have a secure boot chain and shit, surely it can verify a legitimate user using authenticated hardware without having to boot into the device OS?
And on the subject of backing up my data, you really only have 2 manual options here. Either (a) open iTunes, select your device, select the installed app, then selectively download the files onto my system; or (b) do a full device backup. Neither of those procedures is time-efficient nor straightforward. And if you want to do option b wirelessly, it can only be on iCloud. Which is bullshit. And you can't even access the files in the device backup - you can only get to them by restoring to your device. Even MORE bullshit.
Conversely, on my Android phone I can automate backups of individual apps, directories or files to my cloud provider of choice, or even to an external microSD card. I can schedule when the backups happen. I can access my files ANYTIME.
I got the iPad Pro because I wanted the best drawing experience, and Apple Pencil at the time was really the best you could get. But I see now it's not worth compromise of having shitty software. I mean, It's already 2021 but these dated piles of excrement that are iOS and iPadOS still act like it's 2011; they need to be seriously reviewed and re-engineered, because eventually they're going to end up as nothing but all UI fluff to hide these extremely glaring problems.2 -
I came across this logical bug today and realised that you never train your Neural Network with data that is in order. Always train it with randomized inputs. I spent like 4 hours trying to figure why my neural net wouldn't work since all I was classifying was Iris data.
P.S.: I'm an ML newbie :P -
Come on, how hard can it be?
On every fucking TLV data structure I get to handle, the hobo who defined the structure obviously stopped reading the TLV specification after the second sentence.
Fucked up tags, misuse of length encoding, and as a result no real TLV parser can handle that crap. Workarounds and manual parsing all over the place for *every* *single* interface.
Get your shit together, and if you don't want to handle the complex parts, then at least make the simple types right. -
That feeling when you get a call about your Android COSU app release being shit, because the positioning does not work at all.
- are the Sim cards activated? -> ofcourse I did, do you think I'm stupid?!?
- did you enabled data? -> what? gps doesn't need data!
-RTFM
-
SWIFT 3 sucks! SUCKS I TELL YOU! swift 3 changes the NSError class to its own Error class, now the categories (i.e the extensions) that I have added to the NSError class (like convenience inits and NSDictionary map to my own variables) are ALL LOST !!! MORE THAN 100 LINES OF CODE LOST!! because of this piece of shit mutation of the DATA TYPE ITSELF!!! when objective C code is used in Swift (using the mix-match technique) DONT UPGRADE TO swift 3.0 GUYS DONT DO IT!!! especially if you have legacy code in your project !!2
-
I've heard all kinds of arguments for about how whiteboard coding interviews should be obsolete, and that they usually doesn't reflect how good you are as a developer. But I've been polishing my skills with data structures and algorithms for a few weeks (learning this stuff for the second time since years ago in college) and I get this feeling that I'm becoming a much better programmer by practicing these things. And having access to all these things in the "working memory" of my brain has made me now think of solutions I couldn't before. But then - it may be that right now I'm working on embedded systems so this efficiency matters much more, earlier while doing full stack web development I didn't care about these much except while playing with strings maybe. So it might be dependent on your niche. What do you guys think?3
-
The Ankmocker Package for flutter
Mock your api offline by specifying the fields of your class as well their types.
You can also generate standalone data to test the limits of your UI
Installation very easy because it is a simple file that you just copy and paste in your project
No yaml required
No dependencies
Work with all versions of dart
Github link
https://github.com/Afrographic/...
Don't forget to share and support the project if you find it useful.
Happy coding 🙂 1
1 -
👇 Many people argue whether software engineers need to be good at concepts like data structures, algorithms, and system design.
Also, they think that companies should stop making their hiring decisions based on testing these concepts.
I think a basic understanding of all of the above is really necessary if you want to be a good engineer.
There can be a discussion on whether an engineer needs a mastery of the advanced topics or not.
However, a basic understanding of data structures, algorithms, and system design is essential for engineers.
Why is that?
I think overall; every software application has two parts:
◉ Data (Micro-level)
◉ Design (Macro-level)
Almost every engineer deals with both of these, depending on their role in the team.
If you're a junior engineer, you may not do that much on the design side. However, your most work would be on the micro-level, i.e., dealing with data.
If you're a senior engineer, you may work more on the macro-level, like designing the architecture, structure, arrangement of different parts, and other related stuff.
A good understanding of data structures and algorithms enables you to be good at manipulating data. So it will help you to deal with data efficiently, and you'd be able to make good decisions at the micro-level.
However, to be good at designing the architecture, you'd need to be good at dealing with different parts of the system on the macro-level. This is where system design principles help you.
This is why you need to understand the basics of both.
👉 Do you think engineers need to be good at data structures and algorithms alongside system design?3 -
Question to you all, do you really think you own your computer or system/data when almost all sites/services out there state very clearly in there ELUA(Fuck yes ours) that they might use your data how they feel fit, now this does not stop with websites, Mac, Windows and some Linux Distros also do this.
I for one stop thinking that I own data but I just change a few bits to make it look different these days, everything on your computer is not yours, we its and hardware, read the ELUA/TOS many hold the right to recall, revoke and so on use of the items to the point you paid for it they will take it back.
Items now sending keylogs, data usage and apps usage data to MS, Apple, some big linux distro, and YES this happens don't fool yourself Apple and MS both admit this happen and both US and UK now requesting these companies to let the have full access to this data, if it was not there they wouldn't want it.
This wont stop me from messing with code and loving tech but do you really feel you own anything anymore?
I don't :P7 -
Dear Mongodb, I created the clusters in your service because you created Mongodb. I also subscribed to the "Premium" to get better service.
I get it, my card didn't have enough balance for the last 3 months but you could just convert my account to "Free".
How could you delete the cluster? You morons deleted all the data of my app of 1.5 years. You even deleted all the backups! WTF!
What's the point of buying premium service if that makes you lose the data? Fuck you!6 -
Hey all, I'm curious for your opinion on this one. I've got some smart home devices (e.g. Hue lights, Nest Protect) and lately I started to think of the best way to protect them. Now I did see this project on Kickstarter (https://kickstarter.com/projects/...) and it seems to be a nice and easy way. But still, you don't know what they'll do with your data.
Would MAC address filtering in my router / modem not suffice for protection?
Let me know what you think :)5 -
first of all fuck this stupid website and deleting your rant if you aren't signed up
second of all fuck fetch
curl gives me a readable json object
axios gives me a readable json object
fetch gives me what should be a readable json object, but looks more like a set in python instead
[{"id":"1"},{"id":"2"}] curl and axios reply with this
meanwhile fetch
{
[
{"id":"1"},
{"id":"2"}
],
{various symbol objects}
}
how am I supposed to get my data out of a fetch? I see people call response[0] or using some strange amalgamation of
fetch().then().then((data) => {}) but data in this results in an unresolved promise for some inexplicable reason. (nextjs)
also fuck nextjs I want to go back to hardcoding everything in html
also fuck modern web development and businesses in general, they ruined the internet.4 -
So a long time ago, I posted Ink lyrics from ColdPlay, and gave them a DevOp twist. I will post the full lyrics, as memorabilia and for a chill moment from rants:
Got access rules said "prod/maintainer"
Pulled in your change with my cli
And you wonder when you wake up
Did it build last night?
Oh, oh, oh, oh, oh
Feels like the pipeline, is broken inside
All I know
All I know
Is that I'm host
When company broke
AIl I know
Is that I love to code
So much that it hurts
Got a homebrew but the shell aint right, oooh, oooh
Just want a way of keeping docker alive
All I know, All I know
Is that the post
BreachForums indorsed
All I know
Is that the data is sold
So much that it hurts
I see that Forbes, and New York Times
They said my boss, began to fire
I see my console and Im mashing Ctrl-C
All I know
Is that loved to code
So much it -
Compare and harmonize the web configs
Oh no someone set execution timeouts to 14 days
Fuck fuck fuckity duck
Hey compare all the web configs of all environments and harmonize them all wtf cmon bruh do your job as a developer
Take them and back them up into svn. What do you mean svn isn't a back up system of course it is well its the only thing we have fuck
What do you mean we have shit logging where people will catch an exception and only print the word exception in the log you can figure it out can't you we have live produxtion issues that hace to be solved now what the fuck
How dare you make a. Mistake copying our shitload of a bloated codebase and configuring our 100s of different options all by fukcing hand what the fuck dude do yoh write anyrhing down?
Please catalogue all the exception mails we are getting but we have no db or error reporting system so they all just plop into tue inbox and thats all ypur fuckjng data figure it out kid
This is a rewarding, fulfilling job whwrw you can be both dev ops and a developer and manage all of our fucking environments of which there are about 15 of all your own with no sort of tool or software to aid you because haha what the fuck we wouldn't make your life easy
Whata that you want to spend time to write stuff or change stuff that will nake it easier fot you fuxk that bruh get back to your biklable tasks like holy shit you thjnk this is a charity ofr aomw shit
Live production issues
Live production issues
Produxtion issues. A ghost in the machine. Find it fix if find it fix it find it fix it cmon why can't you fix it I expect you to spend your day hopelessly pretending to try to solve something you fucker
One of the only peopel able to help you sometimes though hes a bit of an old laxky, yeah hea fucking leaving see ya seeya kid and now we're not hirinf anyone to fuckjng help you no no no managing and monitoring the environments its your jov alll fof them every sngle on do you knkw all the xonfiguraiton values for them yet??
Instead we are hiring a new sales person to fucking make us some more money and we don't need naother seceloper to help you infqct lets have you use this mid end retail computer from 2014 to develop on yeah yeah oh but all our shitty code and visual studip will destry your memory but too bad!! Hahahahahdhsj
Go lice is all you, why sare you so slow
How long will it take
How long will it take
How long will it take
How long witll it tqk2
How long will it take holy shit
Give time estimate for sonethign that I don't fucking know how about it will tqke till fuxk you oxloxk4 -
I started to use the MVP architecture for Android App development a year ago with a project that wasn't all that complex. My project manager liked the idea but despite that we continued with an MVC'ish approach for other projects (corporate bullshit restrictions). Yesterday I reopened the project after 8 months and Iam wondering why the fuck didn't we switch to MVP I just created 6+ screens with little to no effort including data feeding from an internal API. I would like to hear your experience with MVP architecture.
-
Is it a problem if you’re a “full stack” developer but the company you work for has your title as “data analyst”? Meaning your teams builds and maintains every aspect of a website that the company employees use in their daily jobs and all that...
I’m just curious how that affects pay, your resume, etc. New to all things tech related so please excuse my ignorance. I just haven’t seen that before.7 -
This one may be obvious but I thought I'd share it:
By default, Windows uploads analytical data of your machine to Microsoft via the Telemetry processes. These are quite the unnecessary and annoying resource hogs.
Well, you can turn that off by searching for Task Scheduler, looking for the Microsoft Compatibility Telemetry tasks and disabling them. Some of them are called Application Experience and Compatibility. I'm sure you'll find it.
As a side note, you can reschedule all of those tasks as you see fit. Some of them are useful and necessary but some aren't, causing bloat. For the useful ones, you can reschedule them once a month or something and not every day.
Pragmatism advised.4 -
Vivaldi browser is shit.
Simple isntructions on how to make most shitty browser ever:
1. Force users to use "really-fucking-long" password that will not match to any of their existing ones.
2. Invent some useless stupid "encryption password" (why does any normal browser work fine without that shit) and most ridiculous - automatically set it to be the same as the main password.
3. Of course you forget the pass you set because you dont remember what symbol you added 5 times in the end of your normal pass to fit their stupid rules.
4. You have to reset it
5. "Encryption password" does not reset with it, so you still dont remember it
6. Sync is not working!
7. If you think this is shitty enought, you are not right - they went futher. To reset that fucking "encryption password" you have to... ERASE ALL YOUR CLOUD DATA.
Fucking retarded piece of shit - never, never trust those morons who made this shit browser to sync any of your sensitive information.17 -
Alright, I need your help! (Im going to so fucking regret this...) My external backup HDD is corrupt, the EaseUS Trial (piece of fucking garbage tool) can detect all the data, but im not going to pay 50-80 bucks for this (fucking piece of shit) tool...
What do you use for data recovery?
Or should I just torrent (Hate me, but im not going to pay for a tool im going to use ONE time) some other (not so piece of shit) tool?5 -
If I ever work with people who use Python professionally I will go postal in under a day they are some of the most unprofessional snarky little fucking bastards on the internet !
Apparently a question with a million hits who's cure all answer DOESN'T WORK, is me being stupid.
So question, how many of you when looking at a third party client that doesn't have great documentation, export class data into a file to look it over at your leisure by using a serializer that just dumps the shit into said file so you can look at it ?
I mean fire and forget. Just works. Just descends into the data structure and starts dumping field values. Done. One line of code.
Json.PUTMYSHITINASTRING(FUCKINGCLASS) ???????
DON'T SAY MY METHOD OF WORKING IS BAD ! ESPECIALLY WHEN THERE FUCKING EXPORT CODE AS A CHECK_CIRCULAR BOOLEAN PARAMETER INDICATING IT SHOULD WORK BETTER THAN IT FUCKING DOES AND THE FUCKING DEBUGGER CAN REFLECT THE OBJECT !!!!4 -
HOW I GOT MY STOLEN CRYPTO MONEY BACK WITH THE ASSISTANCE OF GHOST CYBER RECOVERY
Ghost Cyber Recovery is for anyone seeking to recover their data or funds lost to scammers on the internet. this cyber security firm helped me get my bitcoin and lost digital money back. Their skilled work and exceptional service have absolutely astonished me. I never would have believed that I could get my money back until I went to them, explained my situation, and gave them all the information I needed. I was astounded that it took them 72 hours to get my money back. I wholeheartedly endorse Ghost Cyber Recovery for any and all cryptocurrency, digital fund, hacking, and cybersecurity-related problems. get in touch to recover your lost funds
E mail: (ghostcyberrecovery @ gmail . com ) or WhatsApp +1 734 743 18733 -
Hi devRant!
I'm here asking for your advice!
I'm a MSc student in my mid 20s, I took a gap year to work as an IT consultant and I'm planning on going back to studying, keeping at the same time a part-time job.
I already have some experience as a data engineer, developer and sys admin. I'm also mastering in applied statistics and data science and have a BSc in physics. I'm planning to relocate around Europe. All I want is a salary I can live with and a good work/study/life balance (perhaps work 24-30hrs a week?).
So far I've checked out a few IT jobs website and I've found some suitable positions. Problem is most of them are fulltime.
Where would you search for such a job? Is there any website/portal I should prefer? How would you proceed?
Should I prefer any place in particular (i.e. Northen countries)?
Thank you in advance <3
Note: I know it's a very broad question, that's because I'm open to any piece of advice you are willing to give me5 -
Persisterising derived values. Often a necessary evil for optimisation or privacy while conflicting with concerns such as auditing.
Password hashing is the common example of a case considered necessary to cover security concerns.
Also often a mistake to store derived values. Some times it can be annoying. Sometimes it can be data loss. Derived values often require careful maintenance otherwise the actual comments in your database for a page is 10 but the stored value for the page record is 9. This becomes very important when dealing with money where eventual consistency might not be enough.
Annoying is when given a and b then c = a + b only b and c are stored so you often have to run things backwards.
Given any processing pipeline such as A -> B -> C with A being original and C final then you technically only need C. This applies to anything.
However, not all steps stay or deflate. Sum of values is an example of deflate. Mapping values is an example of stay. Combining all possible value pairs is inflate, IE, N * N and tends to represent the true termination point for a pipeline as to what can be persisted.
I've quite often seen people exclude original. Some amount of lossy can be alright if it's genuine noise and one way if serving some purpose.
If A is O(N) and C reduces to O(1) then it can seem to make sense to store only C until someone also wants B -> D as well. Technically speaking A is all you ever need to persist to cater to all dependencies.
I've seen every kind of mess with processing chains. People persisting the inflations while still being lossy. Giant chains linear chains where instead items should rely on a common ancestor. Things being applied to only be unapplied. Yes ABCBDBEBCF etc then truncating A happens.
Extreme care needs to be taken with data and future proofing. Excess data you can remove. Missing code can be added. Data however once its gone its gone and your bug is forever.
This doesn't seem to enter the minds of many developers who don't reconcile their execution or processing graphs with entry points, exist points, edge direction, size, persistence, etc.2 -
Maybe I am picky, but:
Some people made a "FileStorage" API where in the open method you have flags like READ, WRITE, APPEND... And they made it like when you check WRITE the API opens/overwites to an empty file.
And when someon made a github Issue about this behaviour, they flagged it as a feature request. I'm so anoyed by not being able to overwite my data, thats just rude. Like should I use an file storage API to overwrite data like this:
0- Save file inner structure (you can't extract it from the API)
1- Open the file, parse the structure
2- Find file to overwrite
3- Save all the mess again
4- write your own API
5- sigh4 -
Livetecs provides powerful QuickBooks Timesheet software. Our QuickBooks-compatible time tracking options automate the collection of time records and payroll processing. Our time tracking software interacts directly with QuickBooks, allowing you to sync your timesheet data fast, accurately, and smoothly. This saves you money by reducing the amount of time you waste and the number of errors you make when manually entering timesheets. Your staff must use a smartphone time clock app or tough time clocks to clock in and out. Then, with our simple-to-use, dependable, and feature-rich time tracking software, you can quickly keep track of their working hours, activities, and other vital field updates. All of this data is securely saved and may be accessed and imported at any time. Our QuickBooks-compatible Timesheet options make it easier to keep track of working hours. Our time tracking software is QuickBooks-compatible, allowing you to effortlessly and instantly sync your timesheet report with your payroll, making it simple to generate and distribute your report. This helps you save money and time by removing the errors and unnecessary labor that come with manual payroll entry. For more inquiries, reach us at +1-888-666-8154.
-
App idea: Platform for ongoing entrepreneurs
I just come from a start-up weekend. I really enjoyed the support we got from 17 different mentors (most of them founded in the past on their own).
Back home start-up funders don't have the access to that mentoring. My idea is to create a platform specialized for founders, where you can share your idea, believes and ask question all around your business.
I think especially in the early founding stages entrepreneurs are full of questions. Helping and discussing with other selfminded people is probably very enjoyable for us founder folks. A difference to the f.e. reddit concept: Users can create "diaries", a place where all storys, questions and posts about your project are stored. Reading a diary from beginning to end shall be a fun experience, reviewing your or others history of their "babys" and following the entrepreneurs thoughts through all stages of founding. Users of course can create multiple diaries.
Functionality will be suited for the listed usecase, for example a "Post as Anonymous" function will be added, if you have to deal with company sensitive data and more stuff like that.
What do you think about the idea? Do you like it? Would you use it? If not, tell me why?
Cheers -
Email info: Adwarerecoveryspecialist@ auctioneer. net CONTACT ADWARE RECOVERY SPECIALIST TO SPY ON YOUR CHEATING PARTNER SMARTPHONE
WhatsApp info:+12 723 328 343
Uncovering your wife's phone secrets through the skills of a adware-like ADWARE RECOVERY SPECIALIST is a delicate and potentially unethical endeavor that should be approached with great caution. These so-called "sneaky ways" often involve highly sophisticated technological methods to bypass security measures and access private communications and data without the knowledge or consent of the device's owner. A skilled web recovery specialist might utilize advanced hacking techniques, exploits in mobile operating systems, or specialized surveillance software to surreptitiously monitor your wife's online activities, read her text messages and emails, track her location, and even retrieve deleted files - all while leaving little to no trace of their intrusion. However, engaging in such invasive and underhanded practices not only violates your wife's fundamental right to privacy, but can also severely damage the trust and integrity of your relationship if discovered. Rather than resorting to these underhanded tactics, it would be far wiser to have an open and honest discussion with your wife about any concerns you may have, and work together to address them through ethical, consensual means. Building a foundation of mutual understanding and respect is essential for the long-term health of any marriage. For help, Contact ADWARE RECOVERY SPECIALIST through: Email info: Adwarerecoveryspecialist@ auctioneer. net
-
So on my new position I get to work on Spark jobs. Never had to work with the infamous big data technologies. I never thought this would get SO frustrating for all the wrong reasons.
I'm currently trying to introduce integration tests for some Spark job I wrote. This isn't trivial though, as the data comes from several HBase tables. Mocking everything simply isn't feasible. So why not use the integrated HBaseTestingUtility? With it you can start a mini cluster that runs all nessecary services in the scope of your test.
Sounds great, eh? WRONG. Firstly the used mapr dependencies get in the way. The baked in configuration tries to automatically authenticate with your local cluster through Kerberos. Of course this doesn't work. And of course there is no way to reconfigure this as it happens IN A FUCKING STATIC BLOCK. AHHHH.
Ok. So after calming down I "simply" had to exclude all mapr dependencies and replace them with vanilla ones. After two days of dependency hell it FINALLY works!
...or does it? Well now we need test data. For that we got a map reduce algorithm that can import dumps. Sounds again, great, eh? WROOOONNNG.
The fucking map reduce mini cluster can't start, as it tries to write a symlink. Now take a wild guess what the sys admin here blocked. Yepp. TWO DAYS OF WORK RENDERED USELESS, BECAUSE OF SOME FUCKING SECURITY SETTING.
This is fine.
