Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
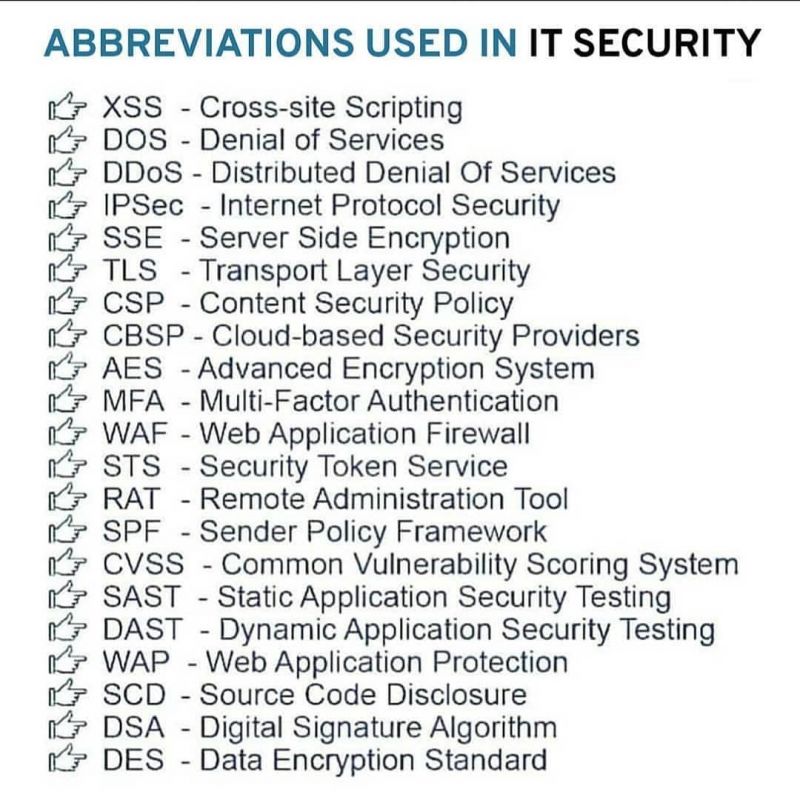
Search - "it security"
-
Client: We have a HUGE security problem.
Me: *thinks about any possible vulnerabilities* What is it?
Client: A user can take a picture of our website and steal our content.
I’m done for today.36 -
They call it $5/gb hotel wifi, i call it free uncapped 100meg fibre because your security sucks
Oh and they host their entire POS (and database with backups) on the same network accessible to every TV in the hotel 16
16 -
"You should use Windows server!"
It was a high security project which needed to run very stable. Even the windows sysadmin looked at that guy like 'dude what the actual fuck'.27 -
Me wanting to board Plane,
Goes through security Check...
"Sorry sir Laptops are not allowed."
Me
"Why?"
Security
"It could be a modified bomb"
Me
"But this is a Tablet!"
Security
"No sir, it has a Keyboard and Trackpad attached to it, its also running Windows..."
Me
"Excuse me, but this is clearly a Tablet"
*Detatches Keyboard from Surface Book*
"See? Tablet."
Security,
"Sorry sir, but no. You cant board the plane with this, only Tablets and Smartphones"
Me
"WTF? you dont allow Laptops because they could be bombs but A FUCKING SMARTPHONE IS ALLOWED? AND TABLETS TOO?!"
Security
"Yes, because the Battery is not removable..."
Me
"But my Laptop Battery is also not Removable..."
Security
"I dont have anymore Time for an Argument"
Me
"So I can board the Plane?"
Security
"No, the Ticket will be refunded"
WHO THE FUCK CAME UP WITH THIS BULLSHIT? LIKE RLY? WHO!!
I MEAN WHAT THE FUCK IS ALLOWED?!30 -
So there was an inspection from government for our bank's IT security. I gave a tour to our server and security systems. I threw all possible acronyms as much as I could remember. Inspector nodded and noted down never uttered a word.
Finally, he breaks his silence, looking at a device he points out and says "What's that ?"
I look at the device then stare at his face back again at the device and to his face I reply "That's AC, Air Conditioner".19 -
This guy at an internship who only wanted to use anything Microsoft.
It was fine for his own use but he also wanted it for a high security prod environment and tried to push that through.
Luckily, the (very competent) team lead refused to use closed source stuff for high security environments.
"listen (team lead to that guy), it's not going to happen. We're simply not using software from a US based company which is closed source for high security stuff.
Why? The US is one of the biggest surveillance powers in this world, we just can't be sure what's in the software if it's US based. Now you can say that that's paranoid but whether or not it is, the surveillance part is a fact, deal with it. That you want to use it, fine, but NOT. IN. HIGH. SECURITY. PROD. (or prod at all really).
He continued to try and convert colleagues to windows and other Microsoft stuff for the rest of his internship.28 -
Me: how's your password security?
Them: of course we value security very highly, our passwords are all hashed before being stored.
Me: what hashing algorithm?
Them: oh we hash it with sha and then place that in a table indexed by the password.
Indexed. By. The fucking. Password.16 -
Got caught using linux terminal by school security. They took my laptop away and drove me across campus in their security carts to take me to the office.
It took a long time to explain that I wasn't maliciously hacking the school.
This is the third time I've been in trouble for tech-related activity.
On the bright side, one of the security guards said, "I'm done dealing with teenagers. Next time I won't work for a high school."
I think he's going to quit. :)13 -
At the airport.
Security: Please put all your electronics in the bin, including your watch.
Me: No problem
<goes through scanner>
Me: there was an Apple Watch in here and now it is gone.
Security: Oh, you lost your Apple Watch?
Me: No! I put my Apple Watch in the bin like you instructed and YOU lost my Apple Watch.
Security: It must be in the spinners.
Me: So my $500 Watch is in the spinners being run over by bins?
Security: you have to put the small things on the bottom.
Me: It was on the bottom and I did as you asked, this is entirely on you. Do not try to shift the blame to me again please.
Security: As I said...
Me: As I said, Do not try to shift the blame to me again. This is entirely your responsibility once you separate me from my electronics so you can perform security theatre. Have a nice day.
—————
Fuck this god damn security theatre. Fuck the dumbasses they hire. Fuck your country. Fuck your god damn feeling of insecurity. Fuck Your ineffective security theatre.
Sick my fucking dick until you choke and gag you worthless pieces of shit. Homeless people the street provide more security than you incompetent, under-educated assholes. Fuck you
And yes, I have 2 fucking laptops. I have a real fucking job where I provide actual value and for that I need a work laptop. I don’t come to work in a stupid looking outfit with a chip on my shoulder looking to inconvenience people. I come to work to provide real value to someone.
Fuck you and your worthless bullshit39 -
Bulma framework, thanks for existing!
Lightweight, CSS only, very fucking easy to use and understand and a beautiful!
As a backend/server/security guy, front end is hell on earth for me. I understand the basics but that's it.
This fucker makes it so simple!19 -
My boss has a camera in the office for "security" reasons and I happen to be just right under it, exposing my computer screens to it. So I wrote a script that sends me an email whenever the camera port is accessed.14
-
Are you serious? Are you afraid of an SQL injection or something, and instead of properly sanitizing your queries you disallow characters? Or is your software and database so outdated that you're afraid special characters will break it? Goodbye security
 15
15 -
My little brother (still in school , learning security and pen testing): i found a bug in a website , it returns an xml file instead of the web page , i reported it to them and i think i'm gonna get rewarded like 2k $ for it .
Me : cool ! Show me .
Him : shows me his phone ...
Me : wait , gotta rant this . 9
9 -
"I really love the new $3k Fortigate firewall switch you bought for the office after our chat about security but it doesn't change the fact that you can access any computer in the company using Password123" - me13
-
I met my boss in a bar...
He said that he needs someone testing their security. I said that I was in security.
He emailed me.
That's it. 😂1 -
I've been asked to do some investigation at work regarding an IT security incident. Thankfully I've watched plenty of CSI so I'm just working on building a GUI with VB to track the IP...7
-
Tv gold on NCIS: Los Angeles tonight.
Summarised:
Need access to laptop
Laptop has unhacksble security protocols
Laptop gets shot
Damage from being shot allowed them to hack it
Morale of the story. Bullets can damage code.6 -
Presenting my paper on PHP Security in IEEE conference today... Wish me luck. I hope it gets published 😃🤞4
-
A while ago (few months) I was on the train back home when I ran into an old classmate. I know that he's a designer/frontend/wordpress guy and I know that he'll bring anyone down in order to feel good. I also know that he knows jack shit about security/backend.
The convo went like this:
Me: gotta say though, wordpress and its security...
Him: yeah ikr it's bad. (me thinking 'dude you hardly know what the word cyber security means)
Me: yeah, I work at a hosting company now, most sites that get hacked are the wordpress ones.
Him: yeah man, same at my company. I made a security thing for wordpress though so we can't get hacked anymore.
Me; *he doesn't know any backend NOR security..... Let's ask him difficult stuff*
Oh! What language did you use?
Him: yeah it works great, we don't get hacked sites anymore now!
Me: ah yeah but what language did you use?
Him: oh it's not about what language you use, it's about whether it works or not! My system works great!
Me: *yeah.....right.* oh yeah but I'd like to know so I can learn something. What techniques did you use?
Him: well obviously firewalls and shit. It's not about what techniques/technology you use, it's about whether it works or not!
That's the moment I was done with it and steered the convo another way.
You don't know shit about backend or security, cocksucker.16 -
"A Google security researcher withdrew from the Black Hat security conference and asked the community to stop using the 'black hat' term."
What the heck? Are we just going to ban the colors white and black in every context? Its clearly not talking about race, its talking about morals... Which people like this "google security researcher" obviously know nothing about...
This is all so stupid... luckily the community disagrees with the stance but then again, afaik, we all also disagreed with removing master/slave and it still happened so make of that what you will...
https://zdnet.com/article/...35 -
Just for fun I am making an RPG Maker game called "IT Quest" where you go on a 40 hour long quest just to get the security team to modify a user. The game will feature tons of mandatory side quests and a convoluted plot that requires descending into the depths of the server room to find a virgin followed by a sacrificial ritual over the broken fax machine. And ultimately the security team just closes your request without telling you why and you have to fight the final boss of the game, Zeromus who runs security. When you defeat him you get the golden CAT5 cable of time which you beat the person who closed your request with until he reopens it and does his damned job.12
-
Security tester: Injects XSS into a rich text editor and flags it for a vulnerability.
"Oh that's fine, let's just disable right click on our page so no one can inspect the page and inject anything."
...
My boss ladies and gentlemen.9 -
Product: Hey, this screwdriver feature I never requested isn’t there. Why? Can you fix it? It’s kinda urgent.
Product: @Root please jump on the ticket above … fairly urgent.
Root: It’s Friday, I’m out next week, and I’m working on finishing <urgent comma ticket> right now.
Boss: Work on the screwdriver instead. But make sure you finish the comma ticket too!
Boss: By the way, I volunteered you for eight security reviews next month!
Security: You’re on call for AWS audits next month, too!rant just look at her she’s doing fineee she can handle everything she can handle it everything is urgent just dump it all on root10 -
haveibeenpwned: MASSIVE SECURITY BREACH AT COMPANY X, MILLIONS OF RECORDS EXPOSED AND SOLD, YOUR DATA IS AT RISK, please change your password!
Company X website: Hey your password expired! Please change it. Everything's fine, wanna buy premium? The sun is shining. Great day.1 -
Best: actually getting something working out there and having it visited by devRanters! (security/privacy blog)
Worst: rewriting entire applications because my code often fucking sucks2 -
Got invited to a "roundtable", where we will discuss email security and the future and direction of where it is going.
Only 10 people in Sweden got a chair
I feel exclusive but also scared that they will find out what a noob I am lol4 -
Today it was revealed that the dutch government doesn't even fucking use SPF records for their email. Someone found out by sending an email in the dutch's govt name and it actually fucking worked.
I hope they fire the people responsible for NOT implementing the most BASIC FUCKING EMAIL SECURITY/VALIDITY MEASURES IN FUCKING HISTORY.
Incompetent cocksucking motherfucking fucks.13 -
Guuuys! I made it! I just got my first job in IT as a Junior Sys Admin at a Security/Pen Testing company. So happy right now. Just wanted to share with you. :D8
-
It’s official. I’m dating a girl.
She’s damn smart, tasteful, hot and really into tech.
Honest, talkative, a real keeper.
Studying IT-Security. Fuckkk I’m dropping spit out my mouth. ALL. DAY.20 -
The amount of thinking and programming that goes into writing a secure backend is fucking high but I love it!
It helps to think like someone who'd want to hack a user or the application so you know most security measures you have to take :)9 -
Example #1 of ??? Explaining why I dislike my coworkers.
[Legend]
VP: VP of Engineering; my boss’s boss. Founded the company, picked the CEO, etc.
LD: Lead dev; literally wrote the first line of code at the company, and has been here ever since.
CISO: Chief Information Security Officer — my boss when I’m doing security work.
Three weeks ago (private zoom call):
> VP to me: I want you to know that anything you say, while wearing your security hat, goes. You can even override me. If you need to hold a release for whatever reason, you have that power. If I happen to disagree with a security issue you bring up, that’s okay. You are in charge of release security. I won’t be mad or hold it against you. I just want you to do your job well.
Last week (engineering-wide meeting):
> CISO: From now on we should only use external IDs in urls to prevent a malicious actor from scraping data or automating attacks.
> LD: That’s great, and we should only use normal IDs in logging so they differ. Sounds more secure, right?
> CISO: Absolutely. That way they’re orthogonal.
> VP: Good idea, I think we should do this going forward.
Last weekend (in the security channel):
> LD: We should ONLY use external IDs in urls, and ONLY normal IDs in logging — in other words, orthogonal.
> VP: I agree. It’s better in every way.
Today (in the same security channel):
> Me: I found an instance of using a plain ID in a url that cancels a payment. A malicious user with or who gained access to <user_role> could very easily abuse this to cause substantial damage. Please change this instance and others to using external IDs.
> LD: Whoa, that goes way beyond <user_role>
> VP: You can’t make that decision, that’s engineering-wide!
Not only is this sane security practice, you literally. just. agreed. with this on three separate occasions in the past week, and your own head of security also posed this before I brought it up! And need I remind you that it is still standard security practice!?
But nooo, I’m overstepping my boundaries by doing my job.
Fucking hell I hate dealing with these people.14 -
Education courses nowadays be like,
- Website Development Course @ $49.99
- Security in website Development @ $45.99
Combo offer @ $60.99
=> Hurry up, LIMITED PERIOD OFFER!!!!!
// Like for real??? Why don't you include Security in website Dev course, it's a part of it.9 -
Got bored at work today and tried to write a program to do my job for me. Security and compliance saw it in the logs (trying to run unauthorized program) and came to give me a hug.11
-
Got a call from a recruiter today. (Keep in mind that using WhatsApp is about a requirement over here.)
R: so can I app you (I hate that word to the fucking point) with further details?
Me: *oh fuck this is gonna get me fucked again* uhm I don't use it so yah...
R: ohhh okay, security reasons?
Me: *slight relief* yes indeed, sir
R: oh fair enough, you can always just text and call me!
*very relieved feeling*
It's for either a cyber security or linux job by the way.29 -
Someone replied to the Christmas party invitation using REPLY ALL... his family personal details sent to hundreds of people. Wait, it gets even worse: he works in the SECURITY DEPARTMENT.5
-
Dear Prof,
One does not simply encrypt the exam tips and give it to the students in a computer security introductory module.
Sincerely,
Disgruntled Undergraduate5 -
I am doing a test on security on my server. I need people to hack it and report the findings.
My server IP is 127.0.0.19 -
So this chick has been super nice to me for the past few months, and has been trying to push me towards a role in security. She said nothing but wonderful things about it. It’s easy, it’s not much work, it’s relaxing, etc.
I eventually decided I’m burned out enough that something, anything different would be good, and went for it. I’m now officially doing both dev and security. The day I started, she announced that she was leaving the security team and wouldn’t join any other calls. Just flat-out left.
She trained me on doing a security review of this release, which basically amounted to a zoom call where I did all of the work and she directed me on what to do next, ignored everything I said, and treated me like an idiot. It’s apparently an easy release. The work itself? Not difficult, but it’s very involved, very time consuming, and requires a lot of paper trail — copying the same crap to three different places, tagging lots of people, copying their responses and pasting them elsewhere, filing tickets, linking tickets, copying info back and forth to slack, signing off on things, tagging tickets in a specific way, writing up security notes in a very specific format etc. etc. etc. It’s apparently usually very hectic with lots of last-minute changes, devs who simply ignore security requests, etc.
I asked her at the end for a quick writeup because I’m not going to remember everything and we didn’t cover everything that might happen.
Her response: Just remember what you did here, and do it again!
I asked again for her to write up some notes. She said “I would recommend.. you watch the new release’s channel starting Thursday, and then review what we did here, and just do all that again. Oh, and if you have any questions, talk to <security boss> so you get in the habit of asking him instead of me. Okay, bye!”
Fucking what.
No handoff doc?
Not willing to answer questions after a day and a half of training?
A recap
• She was friendly.
• She pushed me towards security.
• She said the security role was easy and laid-back.
• I eventually accepted.
• She quit the same day.
• The “easy release” took a day and a half of work with her watching, and it has a two-day deadline.
• She treated (and still treats) me like a burden and ignores everything I said or asked.
• The work is anything but laid-back.
• She refuses to spend any extra time on this or write up any notes.
• She refuses to answer any further questions because (quote) “I should get in the habit of asking <security boss> instead of her”
So she smiled, lied, and stabbed me in the back. Now she’s treating me like an annoyance she just wants to go away.
I get that she’s burned out from this, but still, what a fucking bitch. I almost can’t believe she’s acting this way, but I’ve grown to expect it from everyone.
But hey, at least I’m doing something different now, which is what I wanted. The speed at which she showed her true colors, though, holy shit.
“I’m more of a personal motivator than anything,” she says, “and I’m first and foremost a supporter of women developers!” Exactly wrong, every single word of it.
God I hate people like this.20 -
Some of you might have seen it already, those who didn't just have to.
One of the best rants I've read lately.
"Our security auditor is an idiot. How do I give him the information he wants?"
https://serverfault.com/questions/...4 -
Gotta say, I find it awesome that I can connect with some devRanters through encrypted channels.
It's awesome to talk to devRanters with the same mindset through channels that offer a very high level of security/privacy.
Thanks!39 -
Not sure if this would be true since I find it very hard to judge this one myself but I hope that some people on here see me as some kind of mentorish person when it comes to either Linux, privacy of security.
Parenthesis on "hope"😅21 -
A colleague and I spent a month building a Shopify app that allows merchants to give customers store credit.
Since Shopify's API is so limited, we were forced to augment it's functionality with a Chrome extension.
Now before you go throwing full wine bottles at your screen because of how wrong and disgusting that is, note that Shopify's official documentation recommends 5 different extensions to augment functionality in their admin panel, so as gross as it is, it seems to be the Shopify way...
Today we got a reply from their review team. They won't accept the app because it requires a Chrome extension to work properly and that is a security risk.
Are you fucking kidding me? So I guess Shopify is exempt from their own security standards. Good to know.
Not to mention the plethora of published apps that require a staff account's username and password to be provided in plain text upon setup so it can spoof a login and subsequent requests to undocumented endpoints.
Fuck you and your "security standard" Shopify! -
During a random meeting for a project:
PM: We'll need you to learn Go for this project. It says you know python in your job skills, so it should be easy.
Me: Uh, hiiii. I'm in security, not development. Can't help you, I really shouldn't even be here.
PM: I think Go has security built-in, does that help?
Me: ... I don't know, you need a developer.
PM: Do you know any Go people?
Me: I think that's something you should know.
- Silence enters the room -
PM: Yes perhaps, but you don't know anyone?
Fucking wat?8 -
As a firm supporter of information security, it really "irks" me to see people get up and walk away form their desks without locking their machines... Anyone else with me on this?!18
-
a stored XSS vuln in a banner-like component, visible in ALL the pages in the portal. Anyone can attack anyone.
HOWEVER this was not discovered by 3rd-party security specialists during latest security audit. I have escalated this to my manager and got replied that unless client actively requests this to be fixed should I do anything about it.
FFS.. it's only 2 lines of code.. And there's nothing I can do about it.
Eventualy I was transfered to another project. Now it's not my problem anymore.4 -
As it turend out, just after ranting about increasing my online security, I had an unapproved sign-in from Russia into my Netflix account about an 3h ago.
 6
6 -
The security blog is up again, I fixed the bug.
Just wondering, why did it work in the first place? I simply required a composer autoloader twice but I've been doing that from the beginning and it didn't play up until last night...
I guess it shall remain a mistery 😞82 -
Came across: https://krypt.co sounds interesting, because its like an additional 2fa for your ssh key, is locally encrypted, open source, well documented and transparent:
https://krypt.co/docs/security/...
Why is it not much talked about? sounds great so far, but maybe somebody can find the tick? or is using it himself? 30
30 -
I really have this fucking love/hate relationship with application security.
For a lot of stuff that I write, user input has to be validated, authentication is required and so on and I do love looking into that, pentesting my own applications to death and thinking about the security architecture of the application itself.
But, sometimes, I just want to focus on the fucking features and then it annoys the living hell out of me that securing an application can take so much time and brain power.
Yay and grrrr, I guess.8 -
Adventures in security land, part II:
I’m getting pulled off the security review team and instead relegated to part-time security tickets alongside my usual dev work. (So, someone else finds them, i fix them.)
Guess I found and debated too many problems with the lead dev’s code. 🙄13 -
Scammer calls claiming to be windows security expert.
Them: "sir, your windows computer is sending error code. Please turn it on so I cam Fix it. "
Me: "windows? I have a mac."
Them: "um.... " *hangs up*
Me: gotcha3 -
My IT team installed Antivirus on my 5 year old Mac Mini due to company security policy after the recent Ransomware attacks.
Now my Mac is slow as fuck. They are not even providing me new Mac, due to budget constraints. Totally fucked.
Fuck Ransomware. Fuck security policies. Fuck my company. Fuck everyone. Fuck everything. 😤9 -
Made the mistake of mentioning ISO27001 security standard near management.
- "What?? Why don't we have that certificate?! Why are you not thinking about this?"
- "We don't need it."
- "Of course we do! we must have the highest standards!! Lets hire some lawyers and security consultants to help us get certified!"
A week later:
"Ok, turns out we don't need it."
Satan give me strength...9 -
Because the RSS feed is still down, hereby.
The post about what I personally take for security and privacy measures is up.
Hopefully you can learn something from it or even email me some tips!3 -
This guy has a weird sense of system security if he thinks an SSH MOTD will keep unauthorised people away. Because you know, setting SSH permissions would be too sensible.
 12
12 -
We recently took over development of an app. Upon inspection the API had no security, and passwords were stored in plain text. While the manager was slightly concerned, it wasn't a big deal....
That was until, using only a browser, I found the bosses account and personal email address.
Minutes later I was in his gmail, Facebook and credit cards account.
Improving security is now concern #1, and my boss is "suffering" 2 factor authy on everything.7 -
Wrost security fix ever seen?
encode that passwords in base64 is safe enough.
And keep the password.txt accessible from internet it's safe because nobody know that it exists...6 -
PM ordered me to not use encryption for customer authentication links because we want to be able so send same link if the user loose it. "we have to prioritize usability over security". At least I can tell future hackers it's not my fault..
 10
10 -
*Extreme security measures on the backend, it must be failsafe, every db is as redundant as possible, generated salt, 2fa, everything*
*Forgets to add a case for {"key":""}*
I would blame it on the team but i built the entire backend myself.1 -
Stewart doing his routine security brief:
"Please put your phone on airplane mode.
If you own a Galaxy Note 7, please turn it off."
*Half of passengers cracked up*3 -
I think I ranted about this before but fuck it.
The love/hate relation I have with security in programming is funny. I am working as a cyber security engineer currently but I do loads of programming as well. Security is the most important factor for me while programming and I'd rather ship an application with less features than with more possibly vulnerable features.
But, sometimes I find it rather annoying when I want to write a new application (a web application where 90 percent of the application is the REST API), writing security checks takes up most of the time.
I'm working on a new (quick/fun) application right now and I've been at this for.... 3 hours I think and the first very simple functionality has finally been built, which took like 10 minutes. The rest of the 3 hours has been securing the application! And yes, I'm using a framework (my own) which has already loads of security features built-in but I need more and more specific security with this API.
Well, let's continue with securing this fucker!10 -
Have a client that has a very, very large format printer (think billboards). It's on their network as just another printer, with no special security because everyone "knows" never to print to it....except the new employee who printed her direct-deposit info to it. Got about ten feet(!) into the job before someone realized it wasn't an authorized job.5
-
God damn it.. Yet another night lost to the exciting world of cryptography and Internet security. Why is this shit so damn interesting?5
-
Taking IT classes in college. The school bought us all lynda and office365 accounts but we can't use them because the classroom's network has been severed from the Active Directory server that holds our credentials. Because "hackers." (The non-IT classrooms don't have this problem, but they also don't need lynda accounts. What gives?)
So, I got bored, and irritated, so I decided to see just how secure the classroom really was.
It wasn't.
So I created a text file with the following rant and put it on the desktop of the "locked" admin account. Cheers. :)
1. don't make a show of "beefing up security" because that only makes people curious.
I'm referring of course to isolating the network. This wouldn't be a problem except:
2. don't restrict the good guys. only the bad guys.
I can't access resources for THIS CLASS that I use in THIS CLASS. That's a hassle.
It also gives me legitimate motivation to try to break your security.
3. don't secure it if you don't care. that is ALSO a hassle.
I know you don't care because you left secure boot off, no BIOS password, and nothing
stopping someone from using a different OS with fewer restrictions, or USB tethering,
or some sort malware, probably, in addition to security practices that are
wildly inconsistent, which leads me to the final and largest grievance:
4. don't give admin priveledges to an account without a password.
seriously. why would you do this? I don't understand.
you at least bothered to secure the accounts that don't even matter,
albeit with weak and publicly known passwords (that are the same on all machines),
but then you went and left the LEAST secure account with the MOST priveledges?
I could understand if it were just a single-user machine. Auto login as admin.
Lots of people do that and have a reason for it. But... no. I just... why?
anyway, don't worry, all I did was install python so I could play with scripting
during class. if that bothers you, trust me, you have much bigger problems.
I mean you no malice. just trying to help.
For real. Don't kick me out of school for being helpful. That would be unproductive.
Plus, maybe I'd be a good candidate for your cybersec track. haven't decided yet.
-- a guy who isn't very good at this and didn't have to be
have a nice day <3
oh, and I fixed the clock. you're welcome.2 -
I fucking hate CORS. I mean yeah I get that it's for security and all but fucking COCKSUCKER is it ever fucking getting annoying dealing with this shit…5
-
I opened a post starting with a "NO TOFU" logo and I was wondering what relationship existed between the SSH protocol and anti-vegan people.
After some paragraphs it explained that TOFU stands for Trust On First Use (a security anti-pattern). 7
7 -
At my previous job we had to complete an online security training exercise. It shows you how to behave secure in the work place, to not open unknown links etc. The scary part was that the entire training thing was BUILT IN FUCKING FLASH. So I'm suppose to listen to some god damn virus shitting flash application on how to do online security?! Get your shit together before teaching others.5
-
Published a new blog article last weekend (finally) and had the idea to make a privacy/security Q&A one this weekend.
I'd make an email address for it to which you can email (a) question(s).
What do you people think?19 -
A follow up from my previous rant about a dev colleague in the security company we work for consistently forgetting to lock his screen...he's done it again, so I made him a dickbutt loop this time
 6
6 -
Security rant ahead, you have been warned!
As part of a scholarship application, our government requires a scan/copy of the applicant's credit card. Since the IBAN is now on the back, you have to send both sides.
The back is also where the CVC (security code) is. Any bank will strictly tell you NOT TO EVER SHARE IT - not even with them!
To make things even more fun, you now have the option to send this over email which is, of course, NOT ENCRYPTED!!!!!
I'm basically sending all the info needed to steal all my money over an unencrypted connection to an underpaid secretary, who will print it out and leave it on their desk for anyone with decent binoculars to see.
These people are fucking insane!!!!9 -
The company that I currently work for has a strict clean-desk policy. So strict, there's even have a little booklet that they have about 1000 copies of lying around the office everywhere. In the booklet is a playful description (with cartoons!) of what can go wrong when sensitive information is lying around, or shared with outsiders through careless talk, etcetera. Employees are encouraged to take a copy of the booklet home.
Also in the booklet is a description of the importance of having a good password. It mentions the required minimum (x) and maximum (x+1) length of passwords, mandatory character classes, and how often the passwords have to be changed.6 -
Who's at fault for the recent Wanna Cry virus: The companies affected or Microsoft/NSA?
Personally, I think it's the companies affected. This is what happens when you try and be cheap when it comes to cyber security.8 -
https://blogs.adobe.com/conversatio...
Adobe Flash Player will officially die in 2020.
No more updates. If there'is a security bug, it remain.30 -
Got a math exam tomorrow but learning about it-security and pen-testing is a lot more interesting.
Building a remote for the projectors in your school can also be a source of fun :P 2
2 -
Years of mandatory corporate IT security training has taught me not to open this car, its probably a virus.
 3
3 -
My security knowledge is so bad. But I don't know where should I start.😖
My coworkers know about this, so I don't get involved on related topics.🤤
Last time I asked same question, someone gave me link, and it all about DIY welding metal tubes into a security door.🤦♂️
Any better suggestion?13 -
That's it, the Nintendo Switch got fully exploited. Any firmware!
And only after about a year. nVidia absolutely screwed up with their security.
https://fail0verflow.com/blog/2018/...4 -
WTF!!!!! I officially have someone trying to extort me just had this in my email box this morning!
--------
Hello,
My name is [name removed], I'm an IT security expert and I found a security issue on your website.
This email is personal and in no way related to any of my employers.
I was able to access to a lot of files which contains sensitive data.
I attached a screenshot of the files I found to this email.
I would be happy to give you the method I used to access these files in order to let you fix it.
Would be a monetary compensation possible?
Please forward this email to the right person, if your are not responsible for the security of the website.
Best Regards,
[name removed]
---
He can basically see the contents of my wp-config.php. How has he managed this?71 -
First year at university, prepared to set up multiple electronics.
rPi, arduino Ethernet shield, laptop, and desktop.
Brand new netgear switch to satisfy my internet surfing needs....
After setting up my devices, I realized none of them have internet. Hm. The feed port on my switch wasn't blinking either. So I tell the front desk, and a short 7 days later the port is back on. Yay, problem solved.
One morning I arise to see the port dark and inactive. Furious I use my laptop to share an internet connection while my actual port is "broken".
Support ticket is reopened and this time I get an email saying the port was disabled due to a security issue.
Me: what's the issue?
IT: there was more than two devices connected to the port
(OnLy TwO dEvIcEs PeR port???)
Me: oh okay I will only connect two.
The next day the port is disabled, again.
Me: can you tell me why it was disabled?
IT: a switch was detected being used, security error.
Me: how do I connect more than one device to the port without a switch???
IT: ...
IT: Please only connect one device.
🤔10 -
This is a server in my school and I was wondering... Is it okay to have a server everyone can access? There's no key or other security need to the room needed.
 17
17 -
My boss just came to me and demanded that we drop the first layer of security from our new servers so that the snake oil salesmen he used can open test it. I did try to explain that you don't remove security to test security.8
-
Oh well, it was just a countdown until somebody finds a way to create the mask.
"On Friday, Vietnamese security firm Bkav released a blog post and video showing that—by all appearances—they'd cracked Face ID with a composite mask of 3-D-printed plastic, silicone, makeup, and simple paper cutouts, which in combination tricked an iPhone X into unlocking."
"But they say that it was based in part on the realization that Face ID's sensors only checked a portion of a face's features, which WIRED had previously confirmed in our own testing."
source: https://wired.com/story/...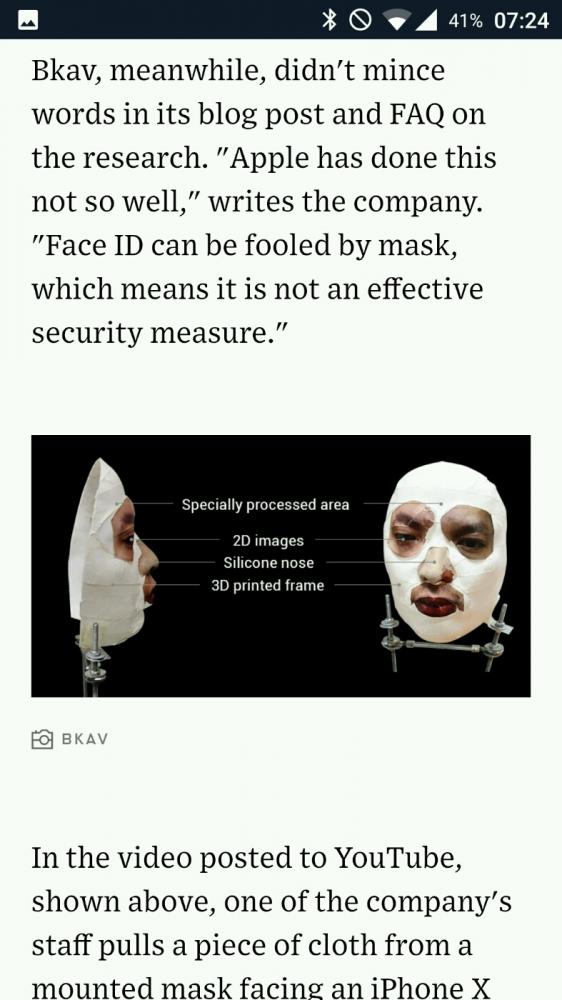 5
5 -
I think what would help is to teach them these things:
- awareness for security in code
- how to use a fucking VCS like Git and how it works -
Getting comfortable in one place for too long and stagnating. It can be easy to automate your job until you can just milk it, but sit still too long and your skills will be irrelevant.
People talk about ageism in development... don't let your mind get old and you'll always have job security.4 -
After designing the new server architecture for our software and the security to go with it, the boss decides we should ask our provider’s solutions architects to see if it is okay, they came back and said it all looks good apart from one part which my manager did and I always said was bad practice.
-
So I need to "fix" a false-positive security warning (mass-assignment of a foreign key). Do I "fix" it by...
A) Setting it manually and double-saving the object?
B) Rewriting the mass-assignment so the linter doesn't realize what I'm doing?
Both options suck.
But security is going to complain if I don't do it.
Guess what?
I'm not doing it.
SMD you ducks.10 -
Working in security for many years only granted me world-class paranoia about taking pictures of myself and my family. It even made it hard to keep in touch with my friends as we don’t live in the same country anymore.
The good side is that it pays well enough to grant me a platinum foil hat.8 -
Boss: We need to disable CSRF and any other form of security, because that shitty, insignificant client has a website that is abomination anyone's eyes, can't pay because of the iframe thingy.
Me: I'd advice against it. This is a significant security issue that just screams to be exploited and there has to be a solution, but idk much about this situation.
Boss: Idk we need to kiss every clients ass till they come. Remove all the security
Me: *Just wants to get home, last one in the office besides the boss* fine
*removes it, deploys and gets the fuck home*
...2 weeks later
Payment gateway: Yeah, we blocked your account, because someone was trying to purchase 30k product in a span of 1h
I'm not even mad about that, but rather about the fact I fucking called it.
* Achievement unlocked: Targeted by scammers
P.s. no major damages, cause the guys from the payment gate understand shit about security.3 -
Someone at work asking me about whether the controller system for our door security can access the Internet. I'm explaining that the reason they can't access Google on it is that it is on an isolated network for security. They wanted to install some remote desktop software on it that some idiot had recommended.
Then I actually get asked: "If it can't see Google... Maybe can it see Firefox?"
*headdesk*5 -
In an age of GitHub and cloud computing, how can a freelance dev using their own laptop be classed as a security risk?
These crude rules laid down by corporate IT depts just make companies look silly.1 -
watching the online course for CEH... dude used the Death Star as a tangible example of how exploits work.
IDK if I should love it for the nerdiness, or be slightly sad that someone needs that type of example of what a vulnerability vs an exploit is, when they're going for the Certified Ethical Hacker certification...
Might be better in an introduction to Network Security class?
Also, while discussing the security, usability, and functionality triangle, he reference the Staples "Easy Button" - does one thing, not very secure, and not very functional (in that it has more than one function)...1 -
"We should probably fix that security issue, but the application already works, so it does not matter" - My boss2
-
!rant Security training at work comes in the form of a serialized TV show where each episode concerns some security topic kind of tangentially and ends with a “REMEMBER… “ followed by the lesson you were supposed to get from the episode.
I kind of love it. A lot. I actually look forward to security training, and I’m not the only one. They stagger the release so you can’t binge watch all the seasons at once and you get three episodes at a time. 😂1 -
Why do people like non typed languages like php or javascript? Besides from a giant pile of possible security problems what do you get out of it?26
-
IT security calls to tell me my new password, because it is poor practice to send it over encrypted message.
New password = password
I'm glad we are taking security so seriously!2 -
I swear, the next time I hear a web developer say to me: "Yeah let's pretend as if the security hole in the website isn't there, because truth be told, i cannot be bothered to fix it."4
-
Ever lose a laptop? I did. 13 days ago. at the airport in security. left it behind because I had two with me, which I don’t usually do. i just realized YESTERDAY that it was missing. someone come to my house and shoot me. because i’m too stoopid to live.8
-
Doing compulsory cyber security training and it's like "if you click a malicious link report it to the IT helpdesk" I and I click agree knowing full well the closest thing to IT we have is me...2
-
This is not fucking security, it's obscurity! What the fuck is a memorable word without any context! It drives me up the fucking wall. This doesnt help anyone it just promotes people to put silly shit like password or something so they won't forget but it just makes their account weaker.
 17
17 -
"Wait, we're logging all web traffic now?"
Me: You're the security engineer, you asked him to do it!
"I know but I didn't think he would actually do it!"
🙄😑 -
Nothing like taking a company IT security training that requires Flash.
The first step to be able to run the training?
Override your browser's security setting to allow Flash to be able to run.
Anyone else see the irony here?1 -
I fucking hate frontend development
>updates three dependencies for security reasons
>entire thing falls apart
>spends whole week to fix it
>its literally just two lines to fix it but those lazy mfs had to ask a QA to rewrite it
>mfw3 -
IF YOU DONT WANT ME TO INSTALL SOMETHING WITHOUT UPDATING THEN FUCKING SAY SO INSTEAD OF SAYING MY PASSWORD IS WRONG.1
-
Whoever it was that thought that MAC address spoofing/randomization for "muh network security" was a good idea, I'm gonna violently fucking murder them. It doesn't solve jack shit for security, doesn't magically make your network device "anonymous" or whatever and it never fails to confuse my DHCP servers that use those fucking things. Whoever it was, hang yourself or I'll fucking do it for you. Filthy incompetent motherfucker!!13
-
Me : "I need to stop geeking out about security because I have exams and need to write a report"
Me 2 hours later : "Ooooo.. what's this cool article about?Let's check it out 😎"2 -
Security!
Offensive and defensive at both code and infrastructure levels.
So many times I see devs not give a flying pancake about security. Whether it be rolling integers for sql injection or permission guarding to prevent someone executing something they shouldn't.
Why is security in this industry always the last thing to be concerned about when it's the first thing that's going to kill your business.
😓7 -
Zoom was dead before it even took grip.
Fml. Use jitsi or some other real stuff.
<deity>, I don't care, choose Skype, there we know that security is well established and it's watching workers are well payed (US Court case for proper work classification).9 -
"Don't waste time on security, just make it work" heard this from a "security head manager" at a 1 million eval. company 3 years ago1
-
Security startup...
'Which football team do you support?'
'Not sure how that is relevant.'
'It is very relevant'15 -
So after 6 months of asking for production API token we've finally received it. It got physically delivered by a courier, passed as a text file on a CD. We didn't have a CD drive. Now we do. Because security. Only it turned out to be encrypted with our old public key so they had to redo the whole process. With our current public key. That they couldn't just download, because security, and demanded it to be passed in the fucking same way first. Luckily our hardware guy anticipated this and the CD drives he got can burn as well. So another two weeks passed and finally we got a visit from the courier again. But wait! The file was signed by two people and the signatures weren't trusted, both fingerprints I had to verify by phone, because security, and one of them was on vacation... until today when they finally called back and I could overwrite that fucking token and push to staging environment before the final push to prod.
Only for some reason I couldn't commit. Because the production token was exactly the same as the fucking test token so there was *nothing to commit!*
BECAUSE FUCKING SECURITY!5 -
Probably the worst security I've ever seen is a website I used to visit that had their "Forgot your password?" system change the password of the account to the user's username and didn't even send an email confirmation before doing it.3
-
half day gone try to find or remember the password of some SSL/key/encrypt/crt/shit/whatever.
Blaming myself for hours, how could I not save the password somewhere?
#Enter Password:
(I pressed enter, no password).
it works.
I love IT security -
I had a friend who wanted to make a social network and Steam-like gaming platform with "near impenetrable" security in around 2 months from scratch. He still wants to do it. Maybe he should think.2
-
A classmate saw me using Firefox today and laughed at me saying Chrome is more secure. I'm not very knowledgeable about the security; I use Firefox because it uses less memory and it's more stable on my machine.
I doubt that info of his is current so can someone who actually knows about the security give me some counter-arguments for him? The more facts the better :D14 -
TFW your company does a security test by sending out a mystery link to everyone which tracks how many people have clicked it and then just redirects to "Never gonna give you up"!4
-
THE CODE USED IN MY MANDATORY ONLINE TRAINING ABOUT CYBER SECURITY AND STUFF LIKE THIS:
<script>window.showQuestion(someOverlyVerboseResponseFromTheServerWithTheCorrectAnswersMarked);
</script>
Oh boi it would be a real shame if someone proxied your precious function :)2 -
Just a rant... It really sucks to work with maven on a security-paranoid financial institution enforcing ntml proxy auth...
Also usb ports disabled... :(5 -
When an application has tons of security holes and fixes never make it into sprint prioritization because "they're not new features"4
-
This picture represents a whole lot of things for me in software development when it comes to bad design or security... You add a new feature along the way and it seems to work well - but basically you f-ed everything up.
 5
5 -
Had my first interview for a cyber security gig.
1st round, preliminary questions about ethics in a security related topic, etc.
I wrote a report about that topic, but for some reason brain fogged the answer.
At the end of the interview, I also blurted out that I found the interviewer's presentation at a past conference and really liked it.
Pretty sure they now think I'm a creep.
That being said, it's been a few years since I've interviewed, so it feels great to get the dust off, even if I bombed it
Practice makes perfect, right?!2 -
Just heard this on the news...
"The cyber security on my smart phone compared to the cyber security in medical equipment..."
Wtf did I just hear??? I mean, I get it...using terms the general public understands... But how about educating people instead. 😤1 -
NSA is seriously hiring on SO. Even with happy YouTube video under it. Like nothing is happening.
It must be freezing in hell atm I guess
https://stackoverflow.com/jobs/...5 -
Corporate IT blocks all network traffic, whitelists port 80 and 443 😡
... cos port number is the best predictor of security threats, amirite? 😒 2
2 -
Imagine updating a legacy web app and the code is so bad it physically makes you sick every time you look at it. Tables with over 400 columns, . And don't even get me started on the security issues. Apparently writing "Confidential" on the top of the page is enough security. And that's just the tip of the iceberg. People should get licenced before being allowed to code.2
-
Every week in my intro to information security class we are asked about what security stuff has gone down in the past week. Equifax is making it incredibly easy to not have to do much research.1
-
Google simply can't knock off harrassing their users with security theatre.
A friend of mine has a small personal YouTube channel. He has recently been bombarded with several phone verification requests a week: "Verify it's you. To continue your session, complete a brief verification. This extra step helps us keep your account safe by making sure it’s really you. "
While frequent verifications may be understandable on YouTube channels with millions of subscribers, channels with only a few dozen subscribers are not attractive hacking targets. A verification would be justified before a potentially harmful action such as deleting videos or deleting a channel. But not for normal everyday use.
What's next? Will they ask users to "verify it's them" every ten minutes, "just for extra security"? Just to verify that it is "really, really, really, really, really" them?
It's not security. It's security theatre.
Sorry, Google, but users are not in the mood of doing a phone verification every other day.
Has this been Google's perverted wet dream all along? 1
1 -
!dev
I'm checking out at Walgreens right now and have an item with a security device on it. The cashier just took a pair of scissors to it. Didn't work obviously and now I think she's trying to rip the cords off the box4 -
Security Issues with Chrome:
My dad was just saying that his work wouldn't let him use Google Chrome because of its supposed 'security issuse'. Just wondered if anyone knew of any real 'security issuse' with chrome that are legitimate? Or is it all just rumours...11 -
A developer said to me: developers may hurry to finish the project before deadline that they might miss many security bugs specially in the updates. That a creative hacker will later take his time and exploit them.
Is it correct ?3 -
PM asked me to develop an application to fetch data from the customer's DB, which would require an access security token provided by the customer. To get the token, I would have to travel to Germany (I live in Portugal) to get it personally (it's not possible to have someone else pick it up for me).
It turns out the security token is a completely closed environment, with its own OS, without the possibility of installing any application or communicating with the exterior. The laptop itself would boot from the token's OS.
It was concluded I would have to hack the security token, which is completely non compliant. So the PM decided not to go forward with it.
But now, I have to go Germany anyway to pick up the security tokens because they forgot to order them for these other guys who would be using them to access the customer's DB manually and they don't want to delay the project anymore.
Oh, and the security tokens cost the project 500€/month each...3 -
My university provides advanced education courses and you'll get certified if you pass them. I'm really interested but I don't have so much time, so which one should I pick?
List of courses I'm interested in:
SQL
IT-Security
Project Management
PHP
I'm curious about your suggestions ;)9 -
fuck..fuck..FUCK..FUCK YOU MANTIS!!!
fuck you and your fucking invalid security token... fucking cunt...
yeah i love extracting my notes from POST data via the browser dev console cause you fucking delete it when hitting the back button...
THANKS FOR NOTHING -
Goddamit I hate it when services advertise how they are about security and then deny me using random readable words with hyphens as passwords.2
-
Had this life not turned out the way it is. Had you not been a dev, what would you imagine you would have been?
I'll go first.. i would probably have been a librarian or a security guard. Someone with lot of time at hand to read.16 -
Remember kids when setting up data security, don't be an Equifax.
Since they can't honestly answer yes to the data at rest question, it probably means the resting data was not encrypted.
How did these guys get put in charge? This is a basic data security standard.
https://m.hardocp.com/news/2017/...1 -
Is it a bad idea to learn about cracking from the dark web? I mean they seem like they know their shit with security5
-
Problem:
some folks left the angular codebase full of ridicolous console.logs, client was upset as he noticed it during UAT
Solution:
1. add extra script in main template page
window.console.log = function(){};
2. translate it into JSFuck
3. if they ask, pretend it's a super-secret encryption algorithm to improve security6 -
I hate Wednesdays. Networking has the Antimalware service run a full/deep scan every Wednesday and my machine is basically unusable until it finishes.
Devs: "Can we have the scheduled task not run during the day, maybe even on the weekend?"
Gary: "Security is our #1 priority and without proper security methods in place, we'll be open to outside threats. Security begins with you, and ..blah blah blah"
Bite me Gary. I got something for ya.
Get-ScheduledTask | ? TaskName -eq 'Windows Defender Scheduled Scan' | Stop-ScheduledTask 7
7 -
People who are shitting on a chrome browser for desktop because of security reasons, but using it on their phones - you are mental.2
-
Why is it that security (hacking) distros went so popular?
I see more and more posts pictures even on devrant featuring them. Even I see people at my uni that are on kali. I can't believe all of them are that into security. I even know two linux noob friends that wont listen to advice and went to kali as first distro.
I'd never use kali/parrot/whatever vs my current manjaro setup... I'd rather go back to arch.7 -
Imagine implementing PHP scripts which execute shell commands defined in URL GET query params on your customer's dedicated server without any basic authentication or similar. The only security is by barely obfuscating it's URL.
I think I've seen it all now...3 -
Guys...
It has come this far...
I... I like test driven development and the amount of unit tests and security it gives you. And I kinda laugh at people that don't take unit testing seriously :p35 -
So today a colleague confessed to an attempt to troll my computer by SSHing into it and playing random songs. Thankfully he did not manage but he would just happen to do it the day we have a security audit.
-
Soooooo, why is it that so often 'security' just means bloody mindedly getting in your way for no reason?
Coz I fail to see how whitelisting a subnet of private IPs that are already only accessible through company VPN presents any kind of security risk, especially since the blocking software is literally only on our company laptops and can be easily bypassed by being on the VPN on *any other device*. But nooooooo, we have to go to the this other company our umbrella company owns (who by the way are making every dev at our company redundant in six months) and beg them to change each individual IP address every time we create a service.
Really does feel like security often means either 'our parent company doesn't understand security so we just need to go through the motions and *look* like we are doing things properly' or 'we just want to get in your way enough that we win in the who gets made redundant fight because you can't actually get any work done and we can'.
Bonus points: on the website for the blocking software they use, it literally recommends using Internet Explorer for everything. I'm surprised they haven't tried to enforce that on us as well.1 -
I reached out to a developer who's site was being contracted out to Amazon devs, because when their site launched it had a couple of security issues. This was his response:
"An additional thought/opinion... Just because a college freshman from Arizona wasn't too hungover to make the effort to notify us and take the liberty of classifying this as a security issue for us doesn't mean we need to take their word for it."5 -
Job security:
- Create bugs purposely
- Discover the bugs after a while (if you discover it too quickly it will look suspicious)
- Fix the bug1 -
MarSecOps: "Marketing Security Operations, the idea is that security is not just the realm of website developers or the IT department anymore, but rather the marketing department has an equal if not greater interest in, and even responsibility to security."
Source: https://strattic.com/5-predictions-...
WHAT THE FUCKING FUCK? The marketing dimwits responsible for security? Whose IT competence ends at Powerpoint drivel?!
I LOLed so hard that I could have shat a cactus!8 -
SSL should really stand for "Satan's Security Layer", because anytime I have to deal with it, it's always a major pain in the rear. (And an expensive pain at that!) Why in 2016 is the SSL process so bad.3
-
So I was like "imma be smart with my internet security and put 2 factor on my GitHub" only to find out I'm getting authenticating errors on trying to push. Disabling 2FA makes it work again.
GitHub y u do dis D:5 -
It's a really interesting discussion, when your boss tells you that it's a perfectly fine idea to directly use a Firebase DB from an Angular web app by storing the Admin Auth Token in a variable in JS.
Thank the spaghetti monster, I was able to argue against it and use the already partially implemented RESTful API with the already used auth.
He basically wanted to save time and omit extra login routes.
It's OK to save time and not implement $randomFeatures.
BUT DON'T FUCKING TRY TO SAVE TIME ON SECURITY!
If it wasn't for me, this web app would turn into a bigger gaping (security) asshole than Sasha Grey's...6 -
College: We will give you six to twelve weeks to build a decent, fully-equipped application that involves a backend with domain business logic, DAL, service layer, security, etc.
In the real world: we give you an afternoon. If it takes two days, you are slow.
Gotta love it.6 -
How is it security, a function of IT, does not understand developers? I mean, they work in IT, should not at least pick-up on the culture?3
-
Start with it at age 4, learn children to protect themselves on the internet, but also show them the possibilities. It's not something I expect this generation to properly teach the next one
And name it something like Computer Security -
They call it security questions.
I call it social engineering backdoor.
I'm supposed to enter those questions after logging into my account and I'm not able to skip it nor to set a proper two factor method.
Well, fuck you. Did you ever thought about dying by a two factor method? Ever watched a Saw movie? You got the idea. -
I have to maintain a system for a financial institution that only works with Windows XP and Ms Access 2003. All VBA code, security is handled using a workgroup file. Can't upgrade anything because client doesn't want to pay for it.
-
Before getting my dev job, I taught myself some java and made a program to assist myself in the position I was working. It was borderline a keyloger, but it helped me with a lot of repetive tasks. Long story short, our security didn't dig that I installed something they didn't approve (I probably could have just not made it an exe and gotten away with it but my boss wanted it as an exe to run on other computers) they didn't know exactly what it was. I totally understood the security concerns though but they sure gave me a fucking heart attack right before my interview for my first dev job! Was seriously worried I was going to be fired and miss my big chance to make it in with out a degree.2
-
Nothing in my office like incompetent developers or their lack of regard for security really bothers me.
But the fact that the coffee's been out for a week now and nobody has replaced it is pissing me off.2 -
Best toothpaste it will make your teeth extra white. As a bonus it’ll get you past border security while they check your temperature all that heat will be appropriately spread out to a cool 98.6F.
 4
4 -
*Has more advanced knowledge on computers and cyber security...
Mother still cant trust with repairing phone, asking which phone to buy, and naggs about the amount of time i spend on my laptop saying i'd break it. -
A fellow uni student shared this deal with everyone in our security course. The first place I thought of re-sharing it was here.
https://humblebundle.com/books/...
Hopefully my fellow devranters will find this a good deal.5 -
On Friday afternoon, i got an e-mail from the IT manager of the company I'm working for.
"Due to security issues we have been forced to stop the server you deployed"
Today, on Monday morning, i got a message from the director saying LITERALLY NOBODY CAN ACCESS THE SYSTEM
I wonder what it could be.3 -
I code. I'm not a network or security admin. Did you even read my resume before hiring me? It says "math degree then data analysis then programming degree" Subnets, firewalls and security certs are not my areas of expertise. Given enough time, could I stumble through? Probably. But I'd probably come up with something worthy of mocking on networkadminrant.
-
Guys has this happened with anyone ..my older aws ec2 instance just vanished from my console but I can still ssh into it, how do I manage it for security groups and other things..?9
-
!rant
I'm a computer engineering student.
I'm very much interested in Systems and networking.
That's why I was thinking of persuing cyber-security as a career option.
But I'm not quite sure if that is a good choice.
Also I don't know how to proceed in order to achieve excellence in cyber-security.
It would be a great help if you guys could help me.
Thanks :)20 -
They tell me to only review security in the security reviews I'm doing (and if I bring to attention that they're implementing a weak encryption so even though they're not using it at the moment it might cause issues so be careful with that they say to only review security 😵) and then I see this mssql in a where:
AND ISNULL(field, 0) IS NULL
And I think wtf, should I report that? I did and it's a bug and they're thanking me now....
God dammit it's hard to "review security" here...3 -
@linuxxx
Can you do a security / privacy check for ProtonVPN? All I know is that it is Switzerland based and pretty much secure.9 -
I forgot my password to my mindfactory account, one of Germany's biggest online vendor for computer components. So I go through the resetting process, which is:
- apply for password reset
- get a mail
- confirm the mail
(So far, so good)
- get a mail with a new CLEAR TEXT PASSWORD
Is this the stone age!?
You never send an email containing the cleartext! You never even store the password as is!
You, as the provider, should never be able to know what the actual password was.
All you are supposed to do is to generate a random salt, and hash the user's password with the salt, and then you only store the salt and the hash. And whenever a user inputs their password, all you do is to check if the you can recreate the hash with the help of the salt and your hash algorithm. (There are libraries for that!)
If a user wants to reset their password? Send them to a mail with link on where they can assign a new password.
At no point should the password ever be stored or transmitted in any other medium.5 -
So my day started well.
I come in an the DVR monitor is not working, ok lets turn it off and on, nope. Lets turn the DVR on and off, nope still nothing. Played around with the VGA cable, nope. I cant replace the cable because its hard wired into the monitor....
I grab the spare screen next to me and connect it all up and it works!
Boss tells me to throw "broken" monitor out, I say I want to test it just to make sure, connect it all up to my pc and now it fucking works!
There are days I hate technology....1 -
!rant
Hi, i just finished developing a web page, and i wanted to ask you as in this case users what do you think about it, is it user friendly , any security breaches found or something?
Here is the link:
http://propika.com/13 -
Guys, please use caddyserver as your webserver! It creates official tls certs for you without you having to do anything. Help making the web secure. There are too many websites that do not have any security.8
-
why is every auth provider utter and complete shit?
why are docs and tutorials that try to teach auth so complete shit?
No wonder there are so many security holes everywhere, nobody bothers to make it simple for the next person.
Next time people that cry about security/bad auth, and work in that field, this one is for you: 5
5 -
Best: take a job as a data analyst. 1 year later, re-write and re-deploy the entire backend following correct security concentions and well-hashed-out data models.
Worst: attempt to backup a hard drive using dd, just to accidentally brick the laptop (because it had some security layer the school put to prevent just that)
Bestest: use knowledge acquired at my "best" story to nuke windows on bricked laptop. Then extract the leftover data using dd and a series of recovery tools. -
Not only is the default password they set a piece of shit, the password field actually shows the password even after you save it, why even bother with security?
Hash your fucking passwords!
The internet kills my insides. 4
4 -
Apple's provisioning profiles/entitlements suck. They can all go wreak havoc on Android now. -___- App all coded, passed IT Security..will be passed by QA once they can actually test the app. Yet App piloting is in hold because of these stupid profiles and entitlements.3
-
So the contract for this big project with a client has some interesting content in it. I'm not sure if I can sign this in good faith.
Because I seem to be lacking guard dogs and a receptionist at my home office. Maybe I could build a force field for them.
And I'm not really looking forward towards having all my friends sign a document every time they visist.
5 PHYSICAL SECURITY
5.1 Adequate physical security perimeters (e.g. fences, walls, barriers, guards, gates, electronic surveillance, physical authentication mechanisms, reception desks and security patrols) shall be implemented to safeguard Information and information systems.
5.2 Supplier shall have a documented visitor policy and all visitors must be identified, registered, logged, and accompanied by an employee from Supplier.2 -
Ok.
I am not a security expert, but when i was working on downloading youtube videos directly from googlevideos.com server, found out there was some security issue that allows to manipulate login requests.
Reported to google.
Let's see how it goes.2 -
Im not sure if im a good or bad person by allowing my users to set a weak password.
They get to use almost whatever they want, but it may be bruteforced easily.
I let users decide their own security on that point.4 -
Typical insurance company BS approach.
Listening to xmas music, Spotify ad kicks in about 'just being "hacked"':
Buy our cyber security insurance product to quickly recover and retain liquidity in case of a cyber security beach.
Not a single word about preventing the incidents in the first place...
Lucky to work in a place that doesn't skimp on IT.5 -
FUCK you "WP iThemes Security Pro".
First of all, your FUCKing services isn't really secure, more like security by obscurity.
Don't get me started on how you probably don't have a dedicated team of security experts.
But oh well, the customer insisted I must install you, despite my advise.
Second of all, Don't FUCKing send me emails regarding "Scheduled malware scan failed" without it containing the FUCKing error message, not some generic "http_request_failed" error, why did it FUCKing fail?
Last but not least: Don't FUCKing clutter is with with your giant ass logo that takes up half my screen or FUCKing spam such as your upcoming events, newly published books/articles, incorrect "documentation"2 -
I can’t take the stupid security theatre anymore. I give up.
Multifactor authentication every 5 minutes. I hate it.
I don’t have a solution and neither does anyone else that doesn’t involve rewriting all apps from scratch.6 -
Learning information security yet again after doing multiple information security things for company and manager is pushing to do it saying "due immediately" and they're after sending "a number of emails" (it's due in a month and they sent 1 email).
Annoying that these things must be done again and again just because someone in sales let something slip or left their journal behind like a dumb dumb. It's not like I'm never off-site with my stuff or I interact with customer(s) yet1 -
I have to open an IT ticket to install a printer driver. I don't know if the IT security BS can get even lower. These are the end of times1
-
I just startet my masters in CS and I‘m still unsure if I should switch to IT-Security.
Our university plan in CS include some completely off topic stuff, like economics.3 -
Jesus our security infrastructure people are stupid. They are telling us to secure a service that we don’t want accessible directly by the role “member” setup to be accessible by “member”. All because they “don’t want us changing identities in the middle of a chain of web service calls”. They are like “don’t worry, the fire wall keeps them out”.
That’s like saying “here’s the key to the bank vault, but you won’t ever get past the security guards so it’s okay that you have it.”
I swear this company is stone stupid. -
Is it considered hacking if it may or may not be your account that you guessed the security question to?9
-
!Rant
I stumbled upon this github repo , thought anyone working on a web app could get some tips from it :
https://github.com/FallibleInc/...
Hope this helps.3 -
How should you approach someone and tell them they have been an victim of social engineering without being mean?
I was at an security conference today and watched a lot of speaks, and I must say that the atmosphere and the people around made it even better.
Here is one takeaway:
Does the security of IT has to be this depressing most of the time, like there is so many IoT devices, services, websites and critical infrastructure that has security flaws and all we can do is watch for now and say we are all fucked. Then try to lead the industry to better practices, like owasp (duck it) . Stop accepting and using shitty answers from SO that has security flaws (why learn something a way that is wrong in the first place?).
We need more awareness about IT security overall, how can one developer know that certain technologies can have certain vulnerabilities such as XSS, XSRF and even SQL injection if there is no information about it in among all shitton tutorials, guides and SO answers in the first place?
Lighten up! Being sad and depressing about these issues is not the best way to approach this! We need to embrace all steps taken towards better security, even the smallest ones.
Check out OWASP if you are not familiar :
https://owasp.org/index.php/...
Thanks for reading. -
Best: complain about the security issues we had, later got the green light to fix them
Worst: at an intern my boss asked me to create some shady code... and I did it ... 😅 -
We should rename our "users" table to "losers".
It would be more accurate, plus the added benefit of security through obscurity - we'd be immune to little Bobby Tables.6 -
I uploaded my static site on AWS. Doesn't load when I typed the public IP in the URL. Googled, found StackOverflow answer to traffic and ports as a security group to AWS. Tried it and it still doesn't work.
Hey Bluehost, sorry I left but I'm back now7 -
My bank just switched from RSA SecurID to SMS-based 2-factor authentication, claiming it offers "equal security".
Is it not common knowledge that SMS 2FA is a security joke?? What the fuck guys?!? -
When a junior develops an API call which return the user information and there is session_key and password encrypted in it too.
Dude! do you even know some basic security ! Please don't just Select * From table join table only !3 -
Why is everyone into big data? I like mostly all kind of technology (programming, Linux, security...) But I can't get myself to like big data /ML /AI. I get that it's usefulness is abundant, but how is it fascinating?6
-
What makes WhatsApp not privacy friendly? They don't state that they share contact information and only statistical stuff (App last opened, etc.) Which is marketing, but not really bad. And they use end to end encryption.
By the way, this here is there Whitepaper on end to end encryption. But haven't read through it yet. https://whatsapp.com/security/...15 -
Another 'fun' rant
Wrote a new server application and got the request from customer services to make it compatible with a slightly older DB version.
Today, CS asked me to install everything on the customer's test environment so I made a build and installed it there.
Wanted to run the service, no .Net framework 4.7.1 installed. Fine, download the installer ...
Start installing .Net framework 'unsupported OS'. Started looking into it. Customer is still running an old unsupported Windows Server 2008 ...
Asked some colleagues whether this was normal. Apparently, yes.
Seems CS isn't capable of telling customers to at least have a supported windows version when they want our software. As if security issues due to people here not understanding TCP/IP isn't enough, we now have security issues due to old, unsupported Windows versions.
Note to self: never trust anyone who says that 'security is the most important thing in our software enviornment'. -
!rant
Many out there say you should use 2 factor authentication with everything, but personally i feel lile that would just turn your phone into a sigle point of failure.
Phisical security is my primary worry, because loosing your phone or having it stolen yould pretty much lock you out of all your accounts.
Another thing is i don't know as much about android security, and i wouldn't be confortable managing it.
I have 2FA active for some key services, but imho a strong password is usually enough. I think its far more more importat for your overall security to avoid passwords re-use.
What do you think? Do you have 2FA on all the time?9 -
Fuck antiviruses making your PC so slow that you cannot work. Need to find a way to disable it, fuck security guidelines.10
-
Trying to install macOS on my PC and it keeps failing at the major install point during to "security".... For fucks sake!
-
How do you like to develop through a VM through a VPN to another continent? Because it seems one of our clients is about to enforce such a model.... due to security reasons...9
-
WEP security on a brand new wifi rollout. Do it for the legacy because no one knew the scanner gun (like target or walmart has) could operate on WPA Personal or even....802.1x Kerberos Security login. At least it was *something* but the whole place was on windows xp and server 2003.
It is 2016. Lets learn our technologies and read the manuals. -
My dad didn't actually know what it was I did. He wanted to get me into hardware and network security type things. Basically the kind of things network engineers or systems admins do. I am still not sure he knows what I actually do.3
-
Spent three days banging my head against my desk trying to get an AWS Lambda function to work, only to finally discover that my code was perfectly functional and it was a security group problem. It was supposed to send a POST request to a load balancer's URL but couldn't resolve the hostname because the security group blocked a necessary outbound port for DNS requests.
That's what I get for not troubleshooting at the infrastructure level when experiencing connection issues. I did not spend two years doing tech support just to forget basic troubleshooting steps now that I'm in the DevOps field...1 -
Had a client whom was using the staging system on my server as cdn, remote computing, etc... because his prod server was a cheap vhost while the vm was a beast compared to it. I shut it down without telling. I just got a call that his site is now slow a f and full of errors.
I kindly told him that there was a recent security breach called dirty cow. Then I told him that I shut the vm down because it would mean security risk for him since there are no patches available yet and only Power on again with there was work for me to do.
If you want resources pay for them -
Thoughts after a security conference.
The private sector, no matter the size, often plays a role (e.g. entry vector, DDoS load generating botnet, etc.) in massive, sometimes country-wide attacks. Shouldn't that make private businesses' CyberSec a matter of national security? Shouldn't the government create and enforce a security framework for private businesses to implement in their IT systems? IMO that'd also enforce standardised data security and force all the companies treat ITSec with at least minimal care (where "minimal" is set by the gov)
What are your thoughts?10 -
Thinking about upgrading my security. Found this interesting project on kickstarter:
https://kickstarter.com/projects/...
It looks pretty promising! Open-Source, no cloud services and Windows Hello support.
What do you guys think about it?
I just want a second opinion before I invest money on it!6 -
Windows 10 User here.
I am really going through my system settings quite often to find potential trojan horses, spyware and what-not that installed itself over time (most security threats come through windows updates IMO).
I was baffled to once again find a bunch of "auto-allowed"-settings that are a potential threat to the security of my system, accompanied by their mysterious services and processes that now appeared (dont know when exactly, but last time I looked, probs a month ago, they pretty surely didnt exist!)
Have a look for yourself.
I of course am in the middle of migrating to linux due to the increasing severity with which Microsoft threatens PC-Security (and mine along with it).
F*CK MICROSHIT!!! >:(( rant microshit spyware cybersecurity threats social credit system satya nadella trojan horse anti-human behaviour skynet bill gay
rant microshit spyware cybersecurity threats social credit system satya nadella trojan horse anti-human behaviour skynet bill gay -
So many people on devRant rave about iPhones because of the better security and privacy, but the new iPhone X starts at a whopping $1000! Sure, you don't have to get the X, but that's what everybody wants.
You'll say "well, I'm willing to pay more if it means better security because that's just the way it is." It doesn't have to be. It would be much more beneficial to actually fight and take a stand for better security and more privacy than just put up with outrageous prices.1 -
So, I’ve been given the task of sorting the security out in an application plugging the holes and whatnot as to be honest it’s shocking haha. It doesn’t help that we automate security audits but that’s a different rant for another day.
We’re using devise for authentication (rails standard, ♥️ devise), we have no password resets through the login page, it has to be manually reset by ringing support, why who knows, even though it’s built into the gem and we allow the user to login using an username instead of an email because for whatever reason someone thought it was a bright idea to not have the email field mandatory.
So I hop onto a call with the BAs, basically I go that we need to implement password resets into the login page so the user can do it themselves and also to cut down support calls a ticket is already in place for it. So I go through the standardised workflow for resetting a password. My manager goes.
“I don’t think this will be very secure”
Wait.. what. Have you never reset a password before? It’s following the same protocol as every other app.
We go back and fourth and I said I’ll get it checked with security just to keep him happy.
The issue mainly is well we can’t implement password resets due to 100s of users not having an email on there account.. 🙃 so before we push this change we need to try and notice all users to set a unique email.
Updated the tickets. All dandy.
Looking at the PRs to see what security things have been done if any and turns out one of the devs in India has just written a migration to add the same default email to every user that doesn’t have an email present and yep it got merged. So I go revert the change but talk about taking a “we don’t care about security approach”.
Eventually we want to have the user reset their passwords and login using their email and someone goes a head and does that. Not to mention the security risk.
Jesus Christ I wonder why I bother sometimes.2 -
In our company, "UAT".
We using staging environment and most of the data is either missing or corrupt. They don't refresh the data, saying it can impose some security issue.
How the hell are we supposed to complete UAT when there's no data that's in production!!!! -
Have you ever wondered why the developer part of the tech world is so rich and full of community? Devrant is one example.
Coming from a background of IT and cybersecurity I've never felt this way before. Why the IT and security world isn't as rich?1 -
First version of the devRant-Webhooks Front-End is up!
You can access it here: https://devrant-webhooks.clan.rip/
Would be nice if some of you could test it out, look for security leaks and generally give feedback!
Next Part is the actual core of devRant-Webhooks, which listens to events and executes the webhooks.
Greetings!14 -
I just used a contact form of a local webshop. I couldnt enter my email address because it contains a +.
I contacted them to tell them about this issue and the response was it is because of security reasons. Since when is following specs a security breach? Unless their system is one leak I don't see how its possible.
Am I wrong or did they either lie or have a leak in their system?2 -
This morning I had an update to my one plus 3t
I now have face unlock...
And the latest (almost every few months) Android security updates
This is how software should be, this is how phone manufacturers should utilize their os, not by slapping some heavyweight skin on it. But by keeping it stock with added features. And when the time is right new features, most importantly security updates
-
I don't care about CORS, I really don't. Could it possibly be any more inconvenient and time consuming? I really don't think it could.
It's made on the assumption that everything you are doing has the same security needs as a secret military project, splendid.30 -
ok that's it, I hate Gmail security. If I don't have access to my phone I can't get on my account in order to recover my phone, fuck.
I have tried to disable all of the security but it's impossible3 -
When you discover a rather big security flaw in a mate code and your boss tell you that he might fix it for "version 2", for now we are good. Wtf, we are just hurting ourselves if this shit gets discovered by some other guy.
We are developing an android app for management and selling, for other company and we are a litte short in time for finishing the first version, but fuck, its a big security flaw. -
Today, I found out that the webmaster for the organization I volunteer at is using a security-by-obscurity PHP implemented design for the private data of our members. I've talked with him about it, but for a variety of reasons to do with organization and workload, it won't be changing.
Fml.3 -
Security theater is not security.
I am still on my mother's cell plan. I pay for it, but she is the primary account holder. We are grandfathered into unlimited no restrictions data, and a new phone yearly, so yeah, not giving that up.
Anyway, when i go to the store to manage the account they say, 'sorry, Sarah needs to come in as the primary account holder.'
'I am sarah' I tell them. I am lying, they know I am lying, and they know I know.
But they have no choice but to go along. I even asked once; they are not allowed to ask for proof of id. I don't know why.
It's just security theater.1 -
Include
<meta http-equiv="Content-Security-Policy" content="default-src 'self';">
Everywhere....
Company just lost a big contract because thier dumb software didn't find this tag and classified security as "F"..... It was the ONLY find in thier dumb report.2 -
what about security ! when u put your file url to update - insert - download data in databes ! u give easy access to evry hacker in word ! how can i secur it 😑😑?3
-
A question to all software security specialists of devRant. Please, take it serious.
Is it fundamentally possible to restrict a SQL database like Postgres in a way that unintended SQL queries are impossible to execute? Perhaps in some kind of whitelist fashion. Is it possible to achieve the kind of security that will be just fine exposed to the outside world akin to "SQL queries in onClick handlers" scenario?
Or is this an uphill battle of never being able to moderate an infinite set of possible fraudulent queries?5 -
Got to do some security audit of legacy ABAP code for SAP systems. Do people still use it? If yes, why.3
-
Telegram or Signal? Got essentially blocked from Messenger because I was stupid enough to fold to peer pressure to get it for robotics and since I enabled it with a GV number they stopped allowing its use for specifically security checks while allowing it even to reset a password, and I somehow got a security check triggered, with no customer support and no ability to call with code, so I'm looking to switch. Even if I get Facebook back, I want to move to something at least that doesn't randomly trigger security checks and then has no customer support.rant messaging apps messenger fuck telegram mistake signal facebook no customer support why did i move all my chats there peer pressure i'm stupid12
-
there should be fuck off button in every software that disables all security features and restrictions so I can run it in private lan and decide myself
fuckers force to expose everything to public and connect everything everywhere
software made for morons
fuck this shit3 -
Can someone discover a huge security issue in .NET framework so it forces everyone to migrate to Core? Please I beg you…12
-
a thing I heard from ops: installing this library update breaks how we manage updates. so let us not update. and use the old libraries that have security issues and don't work with code. we can not change our configuration management tool or update it either. because we have been using it for 15 years.4
-
How many people on devRant are skilled with pentesting / Offensive Security? How long did it take you to understand it? How do you keep yourself from crossing over white hat territory into grey hat territory?3
-
Discord server under development for software engineering, cyber security, networking, and IT talk in general. Looking to meet new people and talk :). @ me if you're interested in testing it.4
-
So we have this year end goals thing at work and the managers pick the goals for us, we dont get to do it
My manager picks for me security topic, the items in that are as follows:- have training sessions, define web security standards, Ensure team follow standards, Identify issues with current implementations
I am damn developer, that's another fucking job!!!3 -
I'd love to get into a career within the cyber security industry.
Anyone got advice?
I've played around with Kali/Parrot and setup a proxmox box to perform pen testing and have a fair number of PDF ebooks and audio books on networks, security and pen testing12 -
/*
No Rant
*/
anyone here with a cyber security cert? i kinda want to go that route of cyber securty. so im curious if its worth it.12 -
I'm a python guy, and although I've worked with bash, there's always a discussion on which one is best for Linux automation.
When it comes to best security practices and clients being really concerned about it, is python that bad of a choice?27 -
Is anyone in the house working on Cloud Access Security Broker (CASB)? If yes, how is the domain and what's the market value of it?
-
Client's IT department is fine about giving me a laptop for exclusive access to their VPN, security reasons, etc. Ok, fine I get it.
But they do not want to give me a Linux machine - only Windows!
How am I supposed to get shit done.11 -
Is it really good OpSec to log me out of outlook every hour when the password manager lets me automatically log back in?2
-
During the cryptography & security lecture at the university I received an email from the university IT department with credentials to access the university cloud services. Of course, password was in a plain text.2
-
Do you have an issue with Equifax hiring a Chief Security Officer having a music degree or do you think that it has nothing to do with her competency and it shouldn't be brought up as an issue after this hack.. Go!!4
-
I was thinking about linux and it's security.
Many are sayin that do not require an antivirus. BUT
What if you install wine (3.0) .
And after that install a software (.exe) that contains malware. What about that!
I was thinking today, it would get inffected?2 -
Where I learn networks and cyber security, we started working with Scapy. I have a problem with pycharm, it cannot resolve half of Scapy's functions. Do any of you know how you fix it (the program runs but pycharm still doesn't like it)3
-
Dell with Windows 10 and security tools. worst computer ever. it crashes every night and when I log in in the morning the security tools freeze and I have to hard boot the machine and repeat about 10 times1
-
Now that the client comes to visit let's upgrade that library now so we can show in a presentation that we use the latest and greatest not 3 months ago when it fixed security issues...
-
Not sure how to ask this. I really enjoy Network side of IT. Maybe even throw in a little Cyber Security as well. I feel like I'm trying to every too fast. I got no certifications yet. This is stressful 😫1
-
Honestly my biggest rant in the past month hasn't been about code, It's about Windows 10 changing my desktop password to my Microsoft Account. I have certain security pet peeves and it just screams "telemetry"...
-
Hey guys, i have problem with local security authority process (win 10) it is in system32 folder and it is called lsass.exe ... it is just burning my pricessor and i can not kill process, because it turns off my computer.. any solution? i am mad :(4
-
Does anyone happen to know of some good resources for securing a flask app? I'm writing my first flask app on a development host and just like crabs to pubes, I've got bots attacking it already.
I'm working on fail2ban now and I'm reading up on options listed here: https://pythonhosted.org/Flask-Secu...
thank you in advance for your help or expertise with Flask/Security!! -
Let's play a game.
Theme: Security awareness - grey-hat style.
How to play:
Post the name of the site followed by actual bad-password restrictions of well-known companies in the comments.
If no-one beats me to it, I plan to share some of the more alarming ones(or all) on a twitter and tag the relative companies as well as various security enthusiasts.4 -
So I changed my FB account password and it gave me email notification with an ip address. And then when I logged in it gave me another notification email with a different IP address this time. Should I be concerned about my network security? This is just SO ANNOYING!!!2
-
In my school it is possinle(after a system update) to use the taskmanager at out windows pcs.
I could send any installed security/content restricion application to hell -
Checking for root is maintaining a false façade of security. By the definition of root it can always be bypassed and we should be designing workflows to discourage logging in from an untrusted device unless you have 2fa.1
-
Guys, is it possible to catch OTP code sent from a website to phone through the browser just because of a lack of security practice and weak coded script?9
-
Any one ever heard of the Solo? It's basically an open source FIDO compliant U2FA usb (with planned support for PGP/SSH key storage!).
The guys who made it are now miniaturizing it into the "Somu" (Secure Tomu).
Please support it! It's a great project and a great (and cheap) addition to basic system security.
https://crowdsupply.com/solokeys/...21 -
A few years ago we had a fail-over which was successful until we started failing everything back to primary servers. The applications could not start at all.
4 hours into troubleshooting, only to find out some java security files were misbehaving. Update from another server and it worked.
Up to date i haven't understood how it failed -
Is it possible to add a layer of security such as a password when you use Thunderbird Mail application? So when you open it, it would require a password to proceed checking mails etc..6
-
There are 49 security updates for Windows on my system this morning. Almost all for Office. Forty nine! That's just nuts. I just updated it yesterday. I hope I don't have to reboot 49 times.3
-
Security expert advices over security is like a priest preaching about the way of life. Both of them tend to same thing that it would protect from `evil`
-
Hey. I'm still very new to CloudFlare and I have a question.
Let's say that I have 4 sub domains: a.test.com, b.test.com, c.test.com, d.test.com. They're all under the same domain (test.com).
I have a page rule setup specifically for a.test.com, where "Disable security" is set to On. I did this as a temporary solution so that I can figure out the problems that a.test.com has when the security is enabled (had users complaints regarding not being able to send requests with CF security On), so that it is still accessible while I try to fix it..
By turning disabling security for a.test.com, do I put others (b, c, d) at risk? I had someone telling me that it is possible for attackers to make use of a.test.con (unprotected by CF) in order to attack the other sub-domains. "a.test.com has no protection so attackers can use it to send requests to other secured subdomains, cross-site attack" or something along that line.
I don't get this. I thought page rule is supposed to be active only for the domain where it's being set up and the rest will still be secured, and that if attacker manages to attack the other subdomain its due to the others not having secure applications inside of it.
Dunno if that person was telling the truth or tried to mess around with me with their joke!
Thanks!5 -
Anyone tried this Krypt.co thing? I just tried setting it up and I hooked up my Github and Google account with it. The odd thing during the connection, it kept asking me to add it as a Security Key. I didn't realize the Chrome Extension tricked the browser to think that it had a security key connected to it.
-
List the top books you consider fundamental to your software engineering knowledge and abilities. A book that really made you improve. Anything, up to you. The point is that without it you would be worse off.
Any topic. Systems design, DSA, security, architecture, doesn’t matter.6 -
Devs and security researchers out there!!
I had a doubt regarding subdomain takeover vulnerability.
How to find where a site is hosted on heroku or AWS or heroku or more?
I was trying to write a script for it.
Any expertise will be welcomed.2 -
Backend development!
I love my little services like a cobweb with solid bases of communication, security, logging and measuring. It can't get more fulfilling to build a service that is used by just more than one frontend. -
We can’t use google sheets, cause of security risks.
(Okay...)
Not even for our showcase content.
Which is public.
The showcase content which goal of the company is to have seen by as many ppl as possible.
Cause security issues which may lead to the possibility of people seeing it.
Seeing the content we want them to see.
Roses are red
My dog ate my led
I may be going crazy
It would be so easy
If they used their head
Or at least fucking read
Edit: if any security expert can give me a valid explanation better than: “it’s the protocol” I am willing to accept I am wrong, but then the point is that they (colleagues) are dicks for not explaining5 -
What's the point of having a 'Check for updates' if it doesn't tell you there is a security update? And why do I always have to download and install updates manually?
-
Sometimes I'll block a code submission with the words security vulnerability", then go have a 10 minute break to see if the others can spot it on their own.
-
Dear Fellow Programmers,
I want to become Cyber Security Specialist and currently learning Java (beginner ). Please, tell me is it a good language for this type of activity and what else should I learn.2 -
Fuck! I frkn hate supabase right now.
Row Level Security seems like a nice feature but it does not fckn work for me. -
this afternoon, we got email from our pentester. He said that he got some security vulnerability in our project. He found .git/ folder in project directory in production server. He considered it as security vulnerability because user can see all git branch on remote repo. He recommend us to remove that folder but the problem is, we using CI/CD so we need that .git/ folder. My question is it bad practice to use git on production server?10
-
Salute to doctors to fighting to corona
Salute to army and police to maintaining security
but also
Salute to IT to maintaining balance in economy!! 4
4 -
I'm currently learning assembly in school and...I acctually kinda like it. (To my surprise). I was wondering if there were any good resources for learning about security at the assembly/system level?1
-
from the students point of view: my it-security module last semester which had nothing new for me because i was thrown into an internship with no work prepared and had to teach myself for the whole semester in it-security which has shown me that said path was the right one for me :)