Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Related Rants

 Hope you survived the Monday;)
As I promised, I’d like to post my comic series “Destory” here regularl...
Hope you survived the Monday;)
As I promised, I’d like to post my comic series “Destory” here regularl...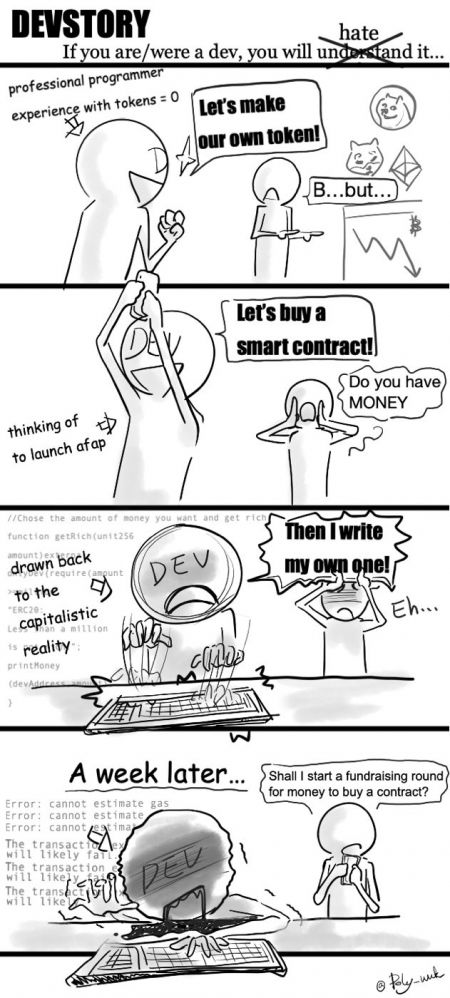 Hey here we go:)
My first comic series - “DevStory”
A story of two devs aiming at changing the world’s...
Hey here we go:)
My first comic series - “DevStory”
A story of two devs aiming at changing the world’s... Leaking an API access token to the web client... oh no no noooo...
Leaking an API access token to the web client... oh no no noooo...
Let's Say you use tokens as authorization method.... The First time you generate the token you still have to manage password and other data....how secure (tinfoil hat mode activate) do you implementat that usually?
question
token