Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
@gitpush he used a memory viewer or disassembled to find the registration product key stored as plaintext.
-
A simple xor pattern would have made this (almost) impossible.
Not securing the license is dumb as fuck!
@R1100 : Good job! 👍 😁 -
@R1100 store the string in 4 byte integers and xor their values with an another 4 byte integer.
If you use a different one for every 4 characters, and don't define them in the same place, you are good.
Use a pseudo random number generator, and it becomes unbreakable. -
@Yamakuzure it's not really dumb. If your user is using a memory modifier, you just can't prevent being cracked. Adding obfuscation layers doesn't solve anything, it just gives you a false sense of security.
At the end of the day, the pattern boils down to changing the return value of a is_registered() check. There's not much you can do to circumvent an in memory function shim.
This is such a hard problem that Windows has an entire side org working on it to no avail. -
 R-C-D156377y@toriyuno true!
R-C-D156377y@toriyuno true!
No defense cause every app can be cracked no matter how difficult it would be -
https://security.stackexchange.com/...
And that's just going over legacy single machine methods of DRM. -
@toriyuno if you really can stop the software at the very moment the serial is assembled for comparison, you are right.
The only thing such obfuscation protects you against is all the other time. Meaning the vast majority of attempts.
You can kill even more attempts by splitting the comparison into parts surrounded by fake strings.
Can you be sure against everything? I guess not. -
@Yamakuzure the only registration model that kind of works is a server client session system (adobe suite). But those too can be defeated since they have an offline mode, or you fake the server OK call. Adobe only has a couple of C&C server IPs, so cracks literally use the hosts file to redirect to localhost. Yup.
Next step up is web service. At that point your client doesn't have access to anything unless they hack your server. At that point I would reward that determination and effort 👍💯
Or you can just not worry about all this by factoring piracy into your business model. The humble bundle is a recent example of that. -
@toriyuno we were talking about serials put as plain text into memory.
And those can be secured up to a point that a simple debugger session with disassembly aren't sufficient to crack them in any reasonable time.
You address something completely different. 😉 -
@R1100 hashkiller is md5, which has been broken for ages now. A modified shah256 hash would be safe to use
-
 Teknas22417y@toriyuno unless there is some salt involved, there will always be lookup tables for hashes
Teknas22417y@toriyuno unless there is some salt involved, there will always be lookup tables for hashes
Related Rants

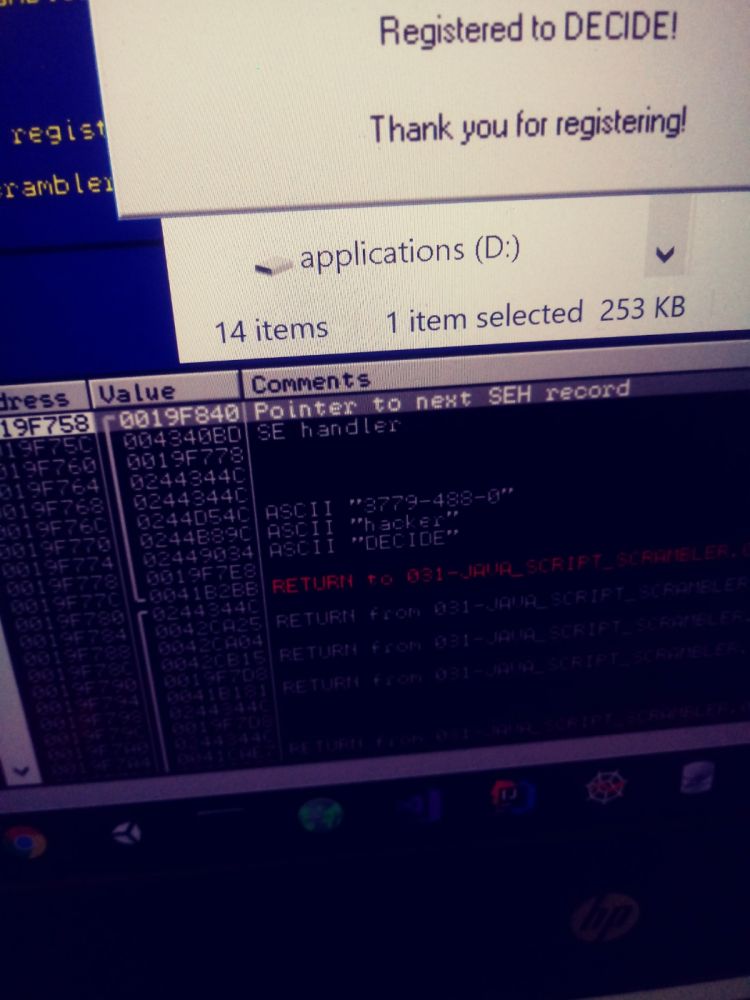 When the stack reveals the serial
MUAHAHAHA!!! :)
When the stack reveals the serial
MUAHAHAHA!!! :) Next interview.. i swear! 😂🥳
Next interview.. i swear! 😂🥳
Too easy!
rant
hahaha!
crack
serial