Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
@tallasianman thatswhy i didnt release it yet. Only to some ppl i know and i thought i post it here :[
-
@tallasianman i actually already use express-rate-limit but i only had it max 1000 for 20 minutes. For everything.
So i will change that -thx -
@tallasianman its not open source yet but im planning to. First i need to secure my server though.
Also no firebase etc stuff. All local on my server -
@jonas-w yea i dont know.. he maybe used a script cuz there were 100 accounts created.. but somehow he got my password and thats creepy :} maybe an injection
-
@jonas-w omg his using the account of my friend i didnt realise. Tallasianguy was of my freind OMG
-
 j0n4s50883ythere is also a logic flaw. If you downvote a post and then upvote it, it will only revert the downvote and not upvote it. to upvote it you need to upvote once again.
j0n4s50883ythere is also a logic flaw. If you downvote a post and then upvote it, it will only revert the downvote and not upvote it. to upvote it you need to upvote once again. -
 Hazarth91923ySecurity always first my man. How did you even make a website without password encryption?! That's like #1 sin and every damn framework does this for you now. Hell at least get a library, don't give a Website to people where you can read the passwords, even if only you have access, that's like phishing level logic there!
Hazarth91923ySecurity always first my man. How did you even make a website without password encryption?! That's like #1 sin and every damn framework does this for you now. Hell at least get a library, don't give a Website to people where you can read the passwords, even if only you have access, that's like phishing level logic there!
You know well that most users use the same pass for everything and you just sent them a link where they Input their password and you can read it?! Wtf :D deserved to get hacked at this rate... -
@tallasianman - just added it For different requests its different times. Such as registering 3 per 20 min etc .. :)
-
Thank you btw. I mean some one else would have abused it in the future and that be far worse :')
-
@tosensei i know.. even before the attack i felt bad. But on that day i implemented hashed passwords. I havent migrated the users passwords yet though. And then the attack camee
-
@Hazarth AHHH i litteraly just showed the app to my friends on sunday. And i never look at them.
And then i realised encryption and started coding it on Monday. Theres a reason the app is still in BETA. Although maybe i should say alpha.
Now its tuesday -.- and his already abused it. -
UPDATE!
I issued a notice to all registered users
Then i now *deleted* the unecrypted password Column and now theres only the encrypted one
-> thus i pushed an update which is "forcefull" because ofcourse the cleartext password is stored in the clients. Now after the update it only stores the hashes after they relog into their accounts.
And i have learned a valuable lesson^^ -
 j0n4s50883yEy @joewilliamns007 i think you have some sql problems, posting " or ' just crashes the app or shows "error storing to database"
j0n4s50883yEy @joewilliamns007 i think you have some sql problems, posting " or ' just crashes the app or shows "error storing to database" -
@jonas-w nope. After they update, only a hash of the password is stored on thr client. And on the server there is a other hash.
Then i compare the hashes on the server.
On the server no plaintextpassword is stored anymore and on the client aswell.
For now - secure if the database gets breached.
Only thing im sure is that an sql injection such as entering the username:
joewilliams007' OR 'blablub
Would work. Thats ez to patch on server though. But rn i need do som school stuff haha. -
Oh yes. A big thing i need to do is updating the post system. Cuz sending a post sends the text in the url
If you send it with an image though it sends it as a post request.
I will make post request for text only aswell but that just wasnt soo high on my list :D -
@jonas-w no?. Only when registering. Because the server encrypts it and then sends it back to the app for the app to store it..
And for now my biggest issue was that the password was not in cleartext in the database -
IM SOO BAD. I actually changed it so that the api returns the has but the app still sets password from edit text. Oh shit. Sorry
-
 j0n4s50883yBut please focus on school stuff and don't let this stuff interrupt you, even if this is not as secure as it could be, no one is going to get hurt if you don't fix it immediatly.
j0n4s50883yBut please focus on school stuff and don't let this stuff interrupt you, even if this is not as secure as it could be, no one is going to get hurt if you don't fix it immediatly. -
@jonas-w i think i got some things mixed up... for the latest version it now surely stores the encrypted password.. and i realised logging in doesnt save the encrypted one sent from the server but saved the one from the edit text.
🤦♂️ i changed it now in 0.1.3.1
I will look more into it though this week.
For now its good that its working and that no password is stored unecrypted on the server -
 j0n4s50883yThe time on the left is in seconds, it definitely makes too many requests and some bogus requests. You should probably cache images, as this downloads for every comment your profile picture while it only needs to download it once.
j0n4s50883yThe time on the left is in seconds, it definitely makes too many requests and some bogus requests. You should probably cache images, as this downloads for every comment your profile picture while it only needs to download it once.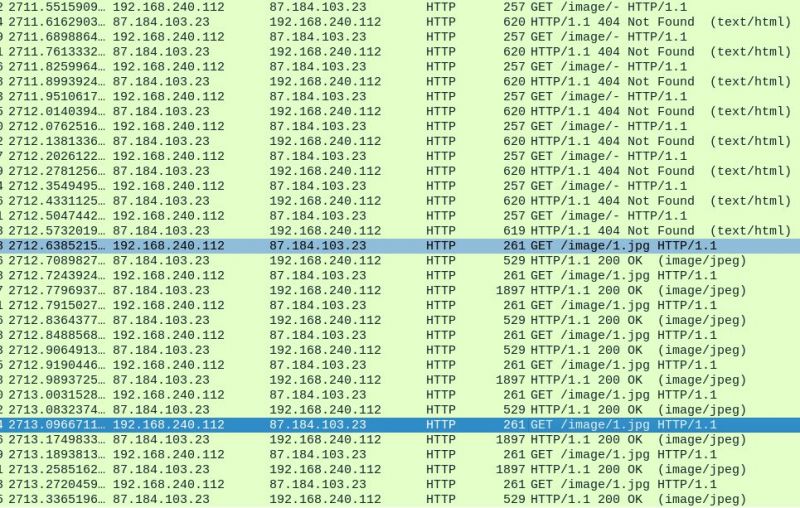
-
@jonas-w YESS. I see the bogus requests on the server haha i new of them. I just havent adressed it.
And i know yes i need to start caching images. I just never have done that kind of stufff so its all still a bit learning as going :) -
@joewilliams007 well the - is the "path" when of a post, no image exists. Should be fixeable by not requesting if the path is a minus
Actually each post has a image Boolean. Why dont i just use that :) -
@jonas-w Btww also Gutenacht, und wollte sagen der Server ist nachts oft aus da er wenig benutzt wird nachts. Wenns in zukunft größer wird, macht es natürlich dann mehr Sinn^^
Mein pc anzuhaben tagsüber ergibt auch nur sinn weil ich noch einen stark genutzten Whatsapp bot habe lol, den Minecraft server HAHA, 2 Webseiten und die App :)) -
Ban the IP address after it tries to GET a non existent file the first time. Harms nobody but the hacker, since normal users would never try to do this.



AHHAHAHAHHAHAHAH Not only did my StarSpace got "hacked" i would say abused , but I had my password in clear text so did he GOT MY DevRant account now aswell!!
I just implemented encrypted passwords yesterday but not fully since im still testing ...
( hacked by @tallasianman )
:(
rant