Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
A) If there is a bug bounty program, use it (check the policy before to see if you still comply). End up with reward.
B) Send an email to some well-known infosec company. Stay humble and give enough intel without compromising yourself. End up with a warning/fine or a job.
C) Send an email to the compromised company and end up with a fine or in jail.
D) Don't do anything and stop doing illegal shit. -
 Wack61257yIf you "test" anything. Just the slightest thing, always use tor!
Wack61257yIf you "test" anything. Just the slightest thing, always use tor!
You could contact the Chaos Computer Club in Germany, they handle disclosures for you (like contacting companies/governments/agencies and since they are known usually people take it serious and they have expirience dealing with backlash https://ccc.de/en -
@karasube D <-- I don't :) one of my servers got hacked due to default configs in one app. The botnet recruiting agent pulled a whole list of already hacked ip addresses with usernames/passwords [go figure!], along with the yet-to-be-hacked list. Soooo.. I was a victim - this uber sensitive information was kind of forced on me 😁
I did a whois check in a loop. My jaw dropped when I saw results... -
 Condor315487yrm -rf * :v
Condor315487yrm -rf * :v
In all seriousness though, maybe sending them an anonymous email could work 🤔 but I noticed that those with poor security quickly get very defensive and personally attacked when you tell them about it. They're beyond help ¯\_(ツ)_/¯
Related Rants

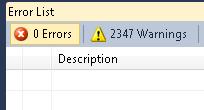 Well, at least there are no errors...
Well, at least there are no errors... REAL gif from Hawaii warning system!
REAL gif from Hawaii warning system!
Speaking of.. What in your opinion would be an appropriate way to warn someone about security problems, like db passwords in git?
I once came across dozens of extremely sensitive services' infra accesses: alibaba/aliexpress, natuonal observatories, gov institutions, telecomms, etc. I had dozens [if not hundreds] routers' and firewalls' credentials along with addresses. I tried one to confirm validity - it worked. I wanted to warn them but did not want to get in trouble.
If it were servers, I'd set a motd or append some warning messages in .profile. But not sure how to do it for non-server devices
what would you do? How would you warn them?
P.S. Deleting that record was a smart move, buddy ;)
p.P.S. Sorry, wrong category... Can't edit now :(
rant
warning
itsec
default passwords