Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 fuckwit11737yEh? You can not disable the developer console on the browser. Even if you "disable" it in electron there are still ways to get that console there.
fuckwit11737yEh? You can not disable the developer console on the browser. Even if you "disable" it in electron there are still ways to get that console there. -
 henlo32557ySomeone actually changed the contents of the web app using console? Is this a sanitization problem?
henlo32557ySomeone actually changed the contents of the web app using console? Is this a sanitization problem? -
@Mitiko any scripts that run client side can be modified and manipulated. There is nothing you can do to stop that. What you can do is validate on the server side to make sure nothing malicious can come through or do anything.
-
 Braed2937y@bigus-dickus client side validation is there for UX experience and to save server load and bandwidth.
Braed2937y@bigus-dickus client side validation is there for UX experience and to save server load and bandwidth. -
 Mitiko60997y@yatanvesh I did.
Mitiko60997y@yatanvesh I did.
@bigus-dickus Don't develop PWAs for when the whole system is given to the user to log in. Also client-side validation doesn't matter if someone just changes the text in h1
@qwerty77asdf You can at least make it an app if you are going to give it to the user himself. See my response to bigus-dickus
@DLMousey I didn't thought of that solution, but it is impossible if it's a form, you'd have to store the info in cookies. If you can't finish the operation the next user has access to the previous cookies. Still it's just a browser, you can exit it -
 Mitiko60997y@DLMousey I am not trying to show off my h4x0r skills, I found a vulnerable system and I expected propositions of solutions. This rant was created to inform others not to do that. I am no hacker, I know nothing about security really.
Mitiko60997y@DLMousey I am not trying to show off my h4x0r skills, I found a vulnerable system and I expected propositions of solutions. This rant was created to inform others not to do that. I am no hacker, I know nothing about security really.
People didn't understand what the actual issue was here (a browser was given to a user) and except though it was a client validation problem. -
 Mitiko60997y@DLMousey It was me who gave no context, I'm sorry. This is a computer that's given to users to sign themselves in and save time. The problem is noone is watching the computer and the user is provided with a browser.
Mitiko60997y@DLMousey It was me who gave no context, I'm sorry. This is a computer that's given to users to sign themselves in and save time. The problem is noone is watching the computer and the user is provided with a browser.
I changed the text just for the image. I then refreshed the browser. My idea was to show how this is way easier and similiar to XSS attacks
Related Rants
-
 doppelman33
doppelman33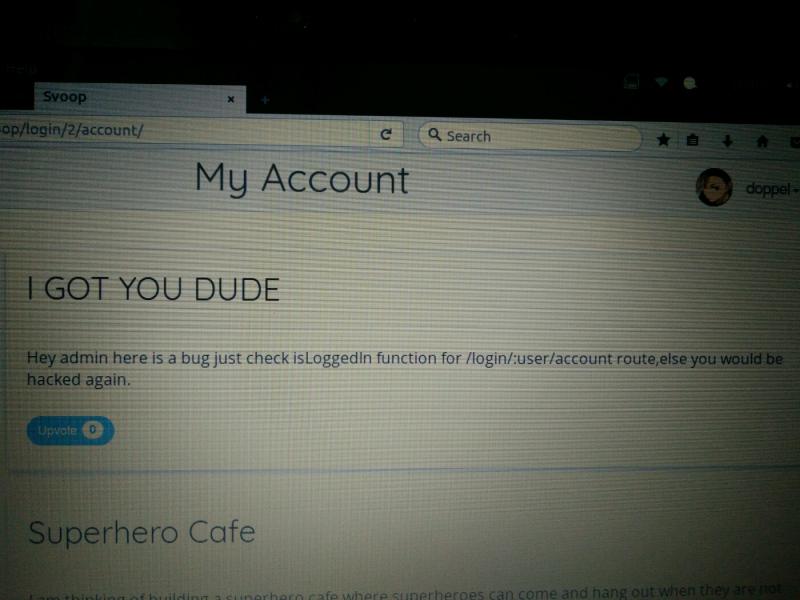 Got hacked in a day after deploying my first site. 😑 I just started developing. Well, I am thankful for tha...
Got hacked in a day after deploying my first site. 😑 I just started developing. Well, I am thankful for tha... -
 harshitks12My email password has been hacked. That's the third time I've had to rename the cat.
harshitks12My email password has been hacked. That's the third time I've had to rename the cat. -
 AlexanderNorup7
AlexanderNorup7 We have info screens around Danmark where companies can buy local ads. This happend yesterday..
We have info screens around Danmark where companies can buy local ads. This happend yesterday..


You can't build a webapp and trust people won't mess with the browser
rant
hacked
pwa