Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
This refers to the fact that you should not mistake e. g. RAID 1 for a backup solution. It will mirror your data to minimize data loss by hard drive failure, but will not mitigate others threats like ransomware or user error.
Having a dedicated RAID 1 for backups however should be fine. Just don't rely on the mirroring alone. -
 Root770736y@Makenshi This.
Root770736y@Makenshi This.
RAID protects against some failures, but not all. Backups protect against most. Offsite backups are better still. -
Yeah, raid 1 is redundancy. The best backup solution is to have a backup of your data in 3 locations minimum 120m apart from each other, but who has the time for that
-
Backups....
RAIDs....
Just one short story: forget what people say.
A realistic backup would need to be stored in 3 different locations, usually it is:
- fast storage
- slow / archive
- slow / archive replica, remote > 120 km's away
The fast one would be for testing the backup in a replica of the production system, not meant for long storage. It's the buffer to create incremental backups fast and then replicating them to the slower archives (to prevent long running backup jobs).
Then comes the ton of checksumming, redundant hardware, failsafe CARP networking and so on.
If you'll can pay that and have the time to implement it correctly, do it.
Otherwise. Look at your budget: What can u achieve that comes close to a good backup? RAID can prevent some hardware outtake, yes. But realistically... RAID requires usually the same harddrives from the same manufacturer, which often leads to the situation that when one fails, the others will follow soon (murphys law).
Maybe the Money would be better invested in a JBOD / redundant hardware / USV... -
@Makenshi @IntrusionCM That's basically what I want to do. A backup NAS with mirrored vdevs (basically RAID1) and then an offsite backup of that data sometime in future when I have the money for it
But even with just the NAS it should be fine™ (except for a house fire maybe) because I'll have
3 copies of my data like you should; two on my nas and one on my desktop -
@12bitfloat maybe assert that it's not on the same fuse... Number 1 enemy at home is usually the electrical wiring / surge protection....
And those tiny little gadgets from asia which like to sparkle... (it has never happened to me, but I had once insight into return shipments / electrical quality assurance and so on... It's fascinating what a small USB charger can achieve with faulty wiring) -
@IntrusionCM "RAID requires usually the same hard drives"
Ehm, no. Except if you want to restrict it to hardware RAID but even a SAN I manage has 3 different hard drive types.
I would even go the opposite direction if supported: Use multiple manufacturers (or at least multiple production dates) to prevent the same fault destroying the whole array.
The only thing that must be equal:
- The block size (512/4096)
- The disk size (either it won't work or the smallest one limits the other) -
Backups should protect you against data loss due to accidents (file overwriting/deletion), attacks (ransomware, vandalism), and desasters (lightning, fire).
Everything that is at the same place can be burned by the same fire (or watered by the same fire fighters).
Every backup media you insert into ransomware-infected machines becomes unrestorable.
Everything, that is net-connected when that 0-day gets used by scriptkiddies to nuke the world, is going to get overwritten with lulz.
Everything, that is powered, when that lightning storm hits, is fried to death.
So you want your backup to be:
- location-redundant
- time-redundant on different hardware
- non-network-connected
- non-power-grid-connected
1/2 -
...The easiest way to achieve that is a bunch of harddisks wich are stored offline in different locations (minimum two, better go for three).
Try having enough independent backup disks, so you can store data of the last four quarters, the last two months, the last three weeks, and maybe the last six days on different media. Alternate physical storage location of the backup disk after each backup.
Since ransomware is a thing now, it is important to not store multiple backups on the same disk at the same time (you can reuse old disks after their backups aren't needed anymore though).
And always encrypt the backups too. Encryption is cheap and drastically enlarges the set of suitable storage locations.
Treat the encryption passphrase mission-critical company secret (because in case of need for recovery, it is).
2/2 -
 hitzoR2556y@Oktokolo Yeah, everyone has time and budget to buy and manage like 15+ physical disks and driving hundreds of kilometers each week, just to have a backup of their cat fotos and porn folder.
hitzoR2556y@Oktokolo Yeah, everyone has time and budget to buy and manage like 15+ physical disks and driving hundreds of kilometers each week, just to have a backup of their cat fotos and porn folder. -
Remember that if raid controler farts all your data will be lost. So just make sure you store backup on a separate raid controler, (preferably in a second pc)
-
@hitzoR
Obviously, the scheme can be scaled down significantly for non-mission-critical data.
Also obviously, the lower bound is to have no backup at all, if there is nothing worth keeping.
If all you have is an email account and Netflix, just write down your email account credentials on two pieces of paper. Put one in your wallet. Put the other in the wallet of your partner. And that is all the backup you need.
But if there is a need for backups, better follow the four core requirements. Otherwise it is no backup. -
 hjk10155916yRaid (10 ideally) with snapshots go a long way. Still not good enough to for anything vital.
hjk10155916yRaid (10 ideally) with snapshots go a long way. Still not good enough to for anything vital.
Snapshot are a nice archiving tool but usually still rely on a single source. One corruption and it may all be gone.
Of site backups that are tested on contents is the only correct solution.
Related Rants

 When you realize that you're googling an error message you've implemented yourself
When you realize that you're googling an error message you've implemented yourself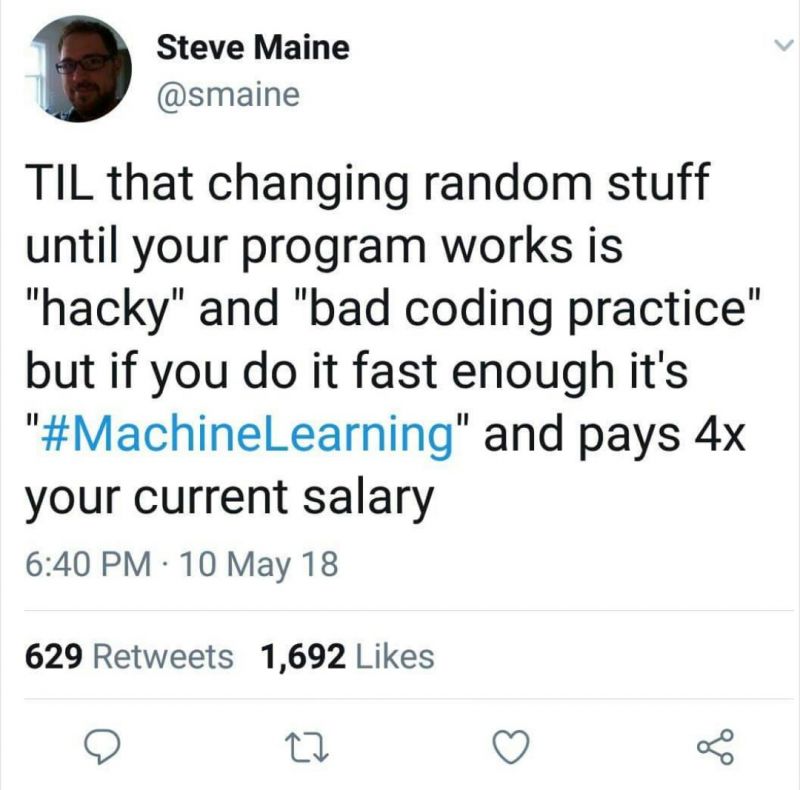 That's exactly how I started, am I a Machine!? ... learning Machine Learning
That's exactly how I started, am I a Machine!? ... learning Machine Learning Great translation by Netgear.
Apparently they're not sure what a Mac-address is...
Great translation by Netgear.
Apparently they're not sure what a Mac-address is...
"RAID isn't backup"
"RAID is super not backup"
"Don't do RAID, do backups"
B-But I want to do backups... to a backup nas using RAID. No good?
rant
nas
confused
raid