Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
The FERN wifi cracker is already in Kali, you just need to find a dictionary, which there are a ton of online. Just Google "rock you".
-
@RiderExMachina Thanks I'll take a look. Do you know how successful non-brute force attacks are? I've read that it's possible to use captured packets to decrypt the key (after handshaking)?
-
@CodeKill
It takes a little longer sometimes when waiting for a handshake. I've not actually tried bruteforcing a router, tbh -
 zdrouse358yI've never been successful with a dictionary attack using aircrack-ng. You could try doing a WPS attack on the router but for the most part many routers have patched WPS with security measures that prevent cracking the WPS PIN. Router's that have updated WPS implementation now have a lockout time if you keep attempting PIN combinations in rapid succession. Still worth a shot, look into pixie-WPS, reaver, or WiFite.
zdrouse358yI've never been successful with a dictionary attack using aircrack-ng. You could try doing a WPS attack on the router but for the most part many routers have patched WPS with security measures that prevent cracking the WPS PIN. Router's that have updated WPS implementation now have a lockout time if you keep attempting PIN combinations in rapid succession. Still worth a shot, look into pixie-WPS, reaver, or WiFite.
Also you can change your ALFA card's country code and Tx power. That will both unlock your ability to listen on more channels and boost Tx power slightly. Don't tell the FCC though 😉
https://forums.kali.org/archive/... -
@CodeKill the WPA brute forcing is only as good as your GPUs(hashcat).
As a wordlist generator which asks some questions about the person have a look at CUPP -
@CodeKill I have done a successful attack with aircracg-ng. What you basically do is, deauth a client with aireplay-ng and capture the 4-way handshake with airodump-ng. On the captured handshake you can calculate passwords (I forgot which tool I used exactly).
About bruteforcing. I can give you an example: my GTX960 gets 110k passwords/s. A password with 12 chars of [a-zA-Z0-9] requires 93 million years with this rate which is just impossible. If you want to crack the password you either need a word list or reduce the amout of unknowns. This is sometimes possible due to dependencies between passwords and mac addresses (e.g. some Belkin routers) or weak default passwords (e.g. TP-Link, 8 decimal chars, ca. 20mins). My successful wordlist attempt was a bit cheated, I knew the password was in there to verify the workflow.
Generally, if a secure random password with sufficient length is set, you have no chance brute forcing it. -
@JustKidding thanks, I know brute Force is not the way to go (as outlined in my original post) so I'm guessing packet capturing is the only way for me. I'm getting a WPA handshake but can't seem to crack the code :/
-
@CodeKill Try to cap one of your own devices in a network where you know the password and try to crack that first. If this doesn't work, you did something wrong.
If you don't know the password and can't crack it, you most probably have the wrong password.
My experience is, that cracking on captured handshakes mostly doesn't work. Either you can calculate the password from the MAC and/or SSID or you have lost. That also counts only for default passwords. If the password is changed you won't ever crack it unless its really really easy (most people use at least for wifi secure passwords) or you have very much information about the password someone used.
I can't give you any further help. It's long ago I did this and all I write here is just out of my head.
Related Rants

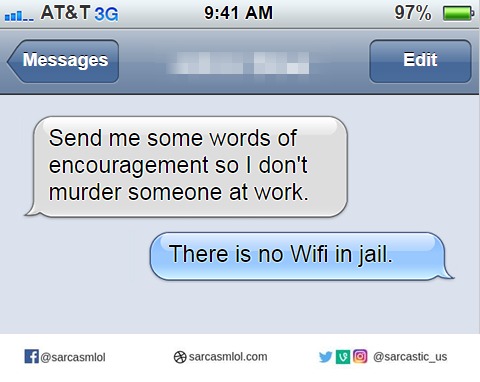 And that was enough encouragement
And that was enough encouragement Did you say security?
Did you say security?
Anyone have much success with Kali/WiFi penetration testing?
I've been tasked with trying to break WPA security within a couple of hours without a dictionary attack - is that even possible?
I have an Alfa AWUS036NHA capable of monitoring mode if that makes any difference. It's my first time trying anything like this.
undefined
wifi
penetration testing
security