Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
It's not complicated, you just boot the machine as single user, mount the root user, and delete the file that tells OSX that it has gone through its initial setup. On reboot it forces the machine to bring up the initial setup dialogues, which includes creating an administrative user. You can then use that user to reset the owners (and anyone elses) password.
OSX ships with no root user password.
Always set one, or else anyone that can Google can access your private files. -
Any machine to which someone can gain physical access to should be considered insecure.
-
 Root772337y@seraphimsystems This.
Root772337y@seraphimsystems This.
The only real defense against local access is full-disk encryption (with added protections like diffusion).
I'd you don't have that... reading/tampering with data on the disk is pointlessly easy. -
@Root everything can be bypassed eventually, what was once a secure way of protecting the bios on a Dell, can now be cracked in a browser window on a cell phone in under a minute, and encryption will eventually go the same way.
Related Rants

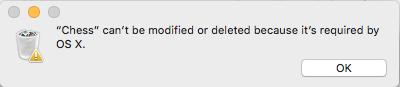 If you're wondering why your Mac is slow as sh*t, be advised that it's playing Chess during it's free time.
If you're wondering why your Mac is slow as sh*t, be advised that it's playing Chess during it's free time. "This is not a bug, it's a documented limitation"
"This is not a bug, it's a documented limitation"
So today I found a way to break into any Apple Mac (provided the exploit hasn't been fixed by the owner) and access all private files, as long as I have physical access to it, in less than 5 minutes.
After finding this, a quick Google on the method reveals this has been a workaround for years.
And to think I once praised Apple for their security standards.
Edit: this was done to an in-house Mac that my company own, and had been password locked by a member of staff who had been fired, but held important company documents on the computer. It was in no way a breach of privacy.
rant
exploits
osx