Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "exploits"
-
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
https://git.kernel.org/…/ke…/... sure some of you are working on the patches already, if you are then lets connect cause, I am an ardent researcher for the same as of now.
So here it goes:
As soon as kernel page table isolation(KPTI) bug will be out of embargo, Whatsapp and FB will be flooded with over-night kernel "shikhuritee" experts who will share shitty advices non-stop.
1. The bug under embargo is a side channel attack, which exploits the fact that Intel chips come with speculative execution without proper isolation between user pages and kernel pages. Therefore, with careful scheduling and timing attack will reveal some information from kernel pages, while the code is running in user mode.
In easy terms, if you have a VPS, another person with VPS on same physical server may read memory being used by your VPS, which will result in unwanted data leakage. To make the matter worse, a malicious JS from innocent looking webpage might be (might be, because JS does not provide language constructs for such fine grained control; atleast none that I know as of now) able to read kernel pages, and pawn you real hard, real bad.
2. The bug comes from too much reliance on Tomasulo's algorithm for out-of-order instruction scheduling. It is not yet clear whether the bug can be fixed with a microcode update (and if not, Intel has to fix this in silicon itself). As far as I can dig, there is nothing that hints that this bug is fixable in microcode, which makes the matter much worse. Also according to my understanding a microcode update will be too trivial to fix this kind of a hardware bug.
3. A software-only remedy is possible, and that is being implemented by all major OSs (including our lovely Linux) in kernel space. The patch forces Translation Lookaside Buffer to flush if a context switch happens during a syscall (this is what I understand as of now). The benchmarks are suggesting that slowdown will be somewhere between 5%(best case)-30%(worst case).
4. Regarding point 3, syscalls don't matter much. Only thing that matters is how many times syscalls are called. For example, if you are using read() or write() on 8MB buffers, you won't have too much slowdown; but if you are calling same syscalls once per byte, a heavy performance penalty is guaranteed. All processes are which are I/O heavy are going to suffer (hostings and databases are two common examples).
5. The patch can be disabled in Linux by passing argument to kernel during boot; however it is not advised for pretty much obvious reasons.
6. For gamers: this is not going to affect games (because those are not I/O heavy)
Meltdown: "Meltdown" targeted on desktop chips can read kernel memory from L1D cache, Intel is only affected with this variant. Works on only Intel.
Spectre: Spectre is a hardware vulnerability with implementations of branch prediction that affects modern microprocessors with speculative execution, by allowing malicious processes access to the contents of other programs mapped memory. Works on all chips including Intel/ARM/AMD.
For updates refer the kernel tree: https://git.kernel.org/…/ke…/...
For further details and more chit-chats refer: https://lwn.net/SubscriberLink/...
~Cheers~
(Originally written by Adhokshaj Mishra, edited by me. ) 22
22 -
Apparently they didn't want to hear about my vulnerabilities I found because they blocked my IP address.
Seriously? I just wanted to do a disclosure of potential exploits / security issues 10
10 -
I'm getting ridiculously pissed off at Intel's Management Engine (etc.), yet again. I'm learning new terrifying things it does, and about more exploits. Anything this nefarious and overreaching and untouchable is evil by its very nature.
(tl;dr at the bottom.)
I also learned that -- as I suspected -- AMD has their own version of the bloody thing. Apparently theirs is a bit less scary than Intel's since you can ostensibly disable it, but i don't believe that because spy agencies exist and people are power-hungry and corrupt as hell when they get it.
For those who don't know what the IME is, it's hardware godmode. It's a black box running obfuscated code on a coprocessor that's built into Intel cpus (all Intell cpus from 2008 on). It runs code continuously, even when the system is in S3 mode or powered off. As long as the psu is supplying current, it's running. It has its own mac and IP address, transmits out-of-band (so the OS can't see its traffic), some chips can even communicate via 3g, and it can accept remote commands, too. It has complete and unfettered access to everything, completely invisible to the OS. It can turn your computer on or off, use all hardware, access and change all data in ram and storage, etc. And all of this is completely transparent: when the IME interrupts, the cpu stores its state, pauses, runs the SMM (system management mode) code, restores the state, and resumes normal operation. Its memory always returns 0xff when read by the os, and all writes fail. So everything about it is completely hidden from the OS, though the OS can trigger the IME/SMM to run various functions through interrupts, too. But this system is also required for the CPU to even function, so killing it bricks your CPU. Which, ofc, you can do via exploits. Or install ring-2 keyloggers. or do fucking anything else you want to.
tl;dr IME is a hardware godmode, and if someone compromises this (and there have been many exploits), their code runs at ring-2 permissions (above kernel (0), above hypervisor (-1)). They can do anything and everything on/to your system, completely invisibly, and can even install persistent malware that lives inside your bloody cpu. And guess who has keys for this? Go on, guess. you're probably right. Are they completely trustworthy? No? You're probably right again.
There is absolutely no reason for this sort of thing to exist, and its existence can only makes things worse. It enables spying of literally all kinds, it enables cpu-resident malware, bricking your physical cpu, reading/modifying anything anywhere, taking control of your hardware, etc. Literal godmode. and some of it cannot be patched, meaning more than a few exploits require replacing your cpu to protect against.
And why does this exist?
Ostensibly to allow sysadmins to remote-manage fleets of computers, which it does. But it allows fucking everything else, too. and keys to it exist. and people are absolutely not trustworthy. especially those in power -- who are most likely to have access to said keys.
The only reason this exists is because fucking power-hungry doucherockets exist.26 -
Straight from a marketing analyst (we didn't have a PM) I once had the displeasure of working with:
"Can you write a JavaScript that will scan a user's hard drive for credit card numbers and autofill the checkout form on our client's web site? I think it will increase their conversion rate."
The guy didn't believe me when I told him it was impossible (barring exploits that would break the browser's sandbox), unethical, and probably illegal. I had to escalate all the way to the CEO to get him to drop it.6 -
Fucking crunchyroll hardcodes their access tokens in a Constants Class in their APK, technically that is a security issue.
What the actual fuck Crunchyroll!? No fucking wonder you got DNS Hijacked so quick, security is literally your second priority you dumbed down twats, get some real devs and some real QAs for fucking god sakes, you're tearing down your own system by inviting exploits.8 -
I've got a confession to make.
A while ago I refurbished this old laptop for someone, and ended up installing Bodhi on it. While I was installing it however, I did have some wicked thoughts..
What if I could ensure that the system remains up-to-date by running an updater script in a daily cron job? That may cause the system to go unstable, but at least it'd be up-to-date. Windows Update for Linux.
What if I could ensure that the system remains protected from malware by periodically logging into it and checking up, and siphoning out potential malware code? The network proximity that's required for direct communication could be achieved by offering them free access to one of my VPN servers, in the name of security or something like that. Permanent remote access, in the name of security. I'm not sure if Windows has this.
What if I could ensure that the system remains in good integrity by disabling the user from accessing root privileges, and having them ask me when they want to install a piece of software? That'd make the system quite secure, with the only penetration surface now being kernel exploits. But it'd significantly limit what my target user could do with their own machine.
At the end I ended up discarding all of these thoughts, because it'd be too much work to implement and maintain, and it'd be really non-ethical. I felt filthy from even thinking about these things. But the advantages of something like this - especially automated updates, which are a real issue on my servers where I tend to forget to apply them within a couple of weeks - can't just be disregarded. Perhaps Microsoft is on to something?11 -
Hey hackers! It's me again 😀
If I wanna be an awesome pentester / bug hunter , what should be my main focus?
Network?
Data sciense?
Algorythm?
Low level programming?
I've already passed network + and basics of ccna and I already know pentesting using kali and I know c and python as well.
Just not sure where to go next and keep using kali packages makes me feel like a script kiddie (which is aweful 😬)
Dreaming to be able to write my own exploits and have my own 0day bugs👑
Thanks for any recommandation you would39 -
Worst advice about programming...
My discussion with my company sistem admin :
Me : you must always think that users are dumb and will make mistakes (like putting letters when db saves as number)
He : users must learn, if they make such mistakes its their fault.
My claim: I learned early in school to always assume that users are stupid and will always find bugs and exploits by coincidence. So protect your code from bad imput8 -
So I can see everything thinks CS should be taught differently this week.
Based on all of the ways we could change it, something no one seems to be mentioning much is security.
Everyone has many ways of learning logical processors and understanding how they work with programming, but for every line of code taught, read or otherwise learnt you should also learn, be taught how to make it less vulnerable (as nothing is invulnerable on the internet)
Every language has its exploits and pitfalls and ways of overflowing but how you handle these issues or prevent them occurring should be more important than syntaxually correct code. The tools today are 100000x better then when I started with notepad.exe, CMD and Netscape.
Also CS shouldn’t be focused on tools and languages as such, seeing as new versions and ideals come out quicker then CS courses change, but should be more focused on the means of coming to logical decisions and always questioning why or how something is the way it is, and how to improve it.
Tl;dr
Just my two cents. -
Stop chatting about your hacking exploits on a train. Especially when you did that 20 years ago. More importantly it's not hacking when you found that password on a Post-It note.7
-
When I was about 13, I opened up command prompt on Windows, and changed the color of it to green then ran the tree command. So, not thinking of anything, this was in the library in front of about 60 people and 2 teachers.
All others saw was green text going down fast, and instantly presumed that I was hacking since they knew I was into coding and finding exploits, and just knew how to use a computer better than them in simple terms (HACKER MAN). Thus this lead to me getting sent to the principal's office... I almost got suspended cause I ran the tree command in green.
Two questions for me remain unanswered, that I would love to know. What would've happened if command prompt was printing text in red. Another question becomes, what would've happened if people saw me pinging Google or some popular site.4 -
That log4j RCE is some fucking nasty business!!! Its exploits have already been observed multiple times in our company scope.
Time for some unplanned Saturday evening hot-patches :/
P.S. Why the fuck leave such a feature enabled as default??? I mean really, whose brilliant idea was "let's leave the message parser enabled as well as the LDAP query hooks... BY FUCKING DEFAULT!!!"
I mean really, is anyone using that? ANYONE?
And then they laugh at me when I say "stay away from frameworks", "use as little libraries as possible", "avoid foreign code in your codebase",...
you know what.... JOKE'S ON YOU!10 -
//Random Mr. Robot thought//
So this picture and this quote in general has been in my mind quite recently. The first time I saw this scene it just passed through my mind as just a wierd quirk of elliot. But upon further thinking, I question that given Elliot is someone who specializes in network security in a sense. A part of which focuses on finding exploits in networks or even software in general( basically finding the worst in them). And the more I think about that,the more I come to realisation that just like most programmers mix together logic in their life in dealing with people, this scene stands out as an example of just that happening with Elliot and what perhaps, makes him such a good hacker. Perhaps we could all learn from this, or perhaps I'm just looking too much into this. Eh. 4
4 -
So today I found a way to break into any Apple Mac (provided the exploit hasn't been fixed by the owner) and access all private files, as long as I have physical access to it, in less than 5 minutes.
After finding this, a quick Google on the method reveals this has been a workaround for years.
And to think I once praised Apple for their security standards.
Edit: this was done to an in-house Mac that my company own, and had been password locked by a member of staff who had been fired, but held important company documents on the computer. It was in no way a breach of privacy.7 -
watching the online course for CEH... dude used the Death Star as a tangible example of how exploits work.
IDK if I should love it for the nerdiness, or be slightly sad that someone needs that type of example of what a vulnerability vs an exploit is, when they're going for the Certified Ethical Hacker certification...
Might be better in an introduction to Network Security class?
Also, while discussing the security, usability, and functionality triangle, he reference the Staples "Easy Button" - does one thing, not very secure, and not very functional (in that it has more than one function)...1 -
Fuck you Intel.
Fucking admit that you're Hardware has a problem!
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data"
With Meltdown one process can fucking read everything that is in memory. Every password and every other sensible bit. Of course you can't change sensible data directly. You have to use the sensible data you gathered... Big fucking difference you dumb shits.
Meltown occurs because of hardware implemented speculative execution.
The solution is to fucking separate kernel- and user-adress space.
And you're saying that your hardware works how it should.
Shame on you.
I'm not saying that I don't tolerate mistakes like this. Shit happens.
But not having the balls to admit that it is because of the hardware makes me fucking angry.5 -
I'm a little confused here. How are "viruses" different from "exploits" in Linux? The way I see it, they're the exact same thing. Although "exploit" makes it sound cool 😂14
-
I'm performing a pentest for my client.
So after scanning my client's network I understood they're using IIS 4.5 and windows server 2012 (or 2012 R2)
I know the systems are real old.
And there are known exploits for them.
The tricky part is I have to stay hidden and I only have my own credentials for logging in to the asp page. (Uploading a script is almost crossed cuz it will reveal my identity)
Also I have access to the local network with some of the other employees user/pass.
Any recommendation for exploiting and staying hidden at the same time ?
One more question : will exploits for newer versions work for the older ones necessarily?8 -
#confession
I don't know what you guys think but I freaking love programming my own Minecraft client. It sounds childish but I love to see server owners rage when they see their Servers dying because of my exploits. It's a good feeling.
But I got 3 DOS attacks afterwards so there is a high risk to make lifetime enemy's.
Let us all post our dark side of knowledge and the shit we have done to amuse ourselves!11 -
Why in the world are there still flash exploits occurring in 2018, these should have stopped occurring 10 years ago7
-
Programmer OAth. Just read on a github repo
0. I will only undertake honest and moral work. I will stand firm against any requirement that exploits or harms people.
1. I will respect the learnings of those programmers who came before me, and share my learnings with those to come.
2. I will remember that programming is art as well as science, and that warmth, empathy and understanding may outweigh a clever algorithm or technical argument.
3. I will not be ashamed to say "I don't know", and I will ask for help when I am stuck.
4. I will respect the privacy of my users, for their information is not disclosed to me that the world may know.
5. I will tread most carefully in matters of life or death. I will be humble and recognize that I will make mistakes.
6. I will remember that I do not write code for computers, but for people.
7. I will consider the possible consequences of my code and actions. I will respect the difficulties of both social and technical problems.
8. I will be diligent and take pride in my work.
9. I will recognize that I can and will be wrong. I will keep an open mind, and listen to others carefully and with respect.4 -
And then the PEN-Tester said... "MySQL configured to allow connections from 127.0.0.1. Recommend configuration change to not allow remote connections." hahahaha!
-
Widget "hack" in secondary.
When I was around 13 or 14 I was enrolled at a public school in the UK. In an effort to try be eco friendly, the students and a IT technicain teamed up to try and create a widget that would track the consumption of printer credit used by all users (staff and students).
At first, I was just playing around with the homepage source code but eventually noticed the widget had separate code within the page.
Because all of the computers were interconnected, I grabbed the source code of the home page and put it into a notepad editor.
I used the intranet to look up staff names and student login usernames. I replaced my user ID with several staff members.
Boom, I could see how much paper they had used, how much they owed the library etc. May not be as impressive as others exploits but some staff were in debt by hundreds and never paid back a penny.
Hope you liked my story.2 -
Hacking is awesome and looks easy!!! And seems like even pentagon might have toooons of exploits and backdoors, and qwerty passwords !!
After watching Mr. Robot...4 -
Google keeps reaffirming what I keep telling everyone... it's not 1995 any more. They just ripped Symantic over using 7-year old (un-updated) open-source components in Norton. These are massive zero-day exploits that are wide the hell open. If you're really concerned, use MSE on Windows. If you're on a Mac, grow a brain cell and actually look at what you grant permissions to, and you won't even need AV.3
-
Fuck, I'll always be a noob. Knowing next to nothing about software development, hacking, exploits - just anything.
Felt a bit proud to had reached the level "hacker" on hack the box. Was fun solving stego, crypto and reversing challenges, diving into assembly the first time. Felt cool stepping through a disassemblied executable with radare, and understanding what a NOP slide is...
However all the illusion crumbled down, when I watched this CCC talk on OpenBSD security, where the speaker was underwhelmed with one of OpenBSD mitigations, where they tried to disallow them: "NOP slides?! Srly? No one is using that anymore. Just look at current exploits."
I felt so stupid, which I probably am. Will never catch up with those guys.
But whatever. In the end we all know nothing. We have no clue, but some are more apt in disguising it behind big speech.
(really like this German song: https://youtube.com/watch/...
Those lines always give me a chuckle:
"Man has no idea.
The house has no idea.
The tree has no idea.
The fawn has no idea.
The squid has no idea.
The tapir knows, but doesn't tell us.")3 -
Boss: We need a discount coupons system right now
Me: We have lot of security concerns, if we implement that as the things are right now, that will be exploited by hackers to get infinite discounts
Boss: Dont worry, i will monitor everything personally for avoid problems
Me: :facepalm:
PD: I entered this software agency 4 months ago by necessity and everything was a mess, they pay 250 bucks to all their devs.
They have what they deserve, a shitty software that can be exploited everywhere
Pls give me another Job xD
PD2: I can sell you lot of exploits for this shitty platform they built JAJAJAJAJAJAJA okno2 -
Got started by making farmville cheats. Found many exploits. Best was when I found 3 ways to do the same exploit. Zynga kept patching and I kept releasing a new way.
Lasted for just over a year or so.
Played for like 3years and then got bored. Those were the golden days, really miss them.7 -
Science says it can't be done! You can't have an iPhone AND preserve your privacy!
Yet here I am, doing just that. Just analyze apps you use and just quit using fucking leeches like instagram and whatever facebook puts out. Also, do this:
1. Disable iMessage, iCloud and FaceTime
2. Opt out of sending analytics to apple
3. Use VPN with DNS that blocks trackers
4. Disable background app refresh and location access
Most importantly, quit using whatever uses personalization to spoon-feed you content that exploits your confirmation bias. Quit watching youtube. Switch to DuckDuckGo or whatever search engine without personalization.
If you don't like apple and don't care about cameras, just buy a Pixel smartphone and install Calyx OS. Fairfone with /e/os is also a good alternative.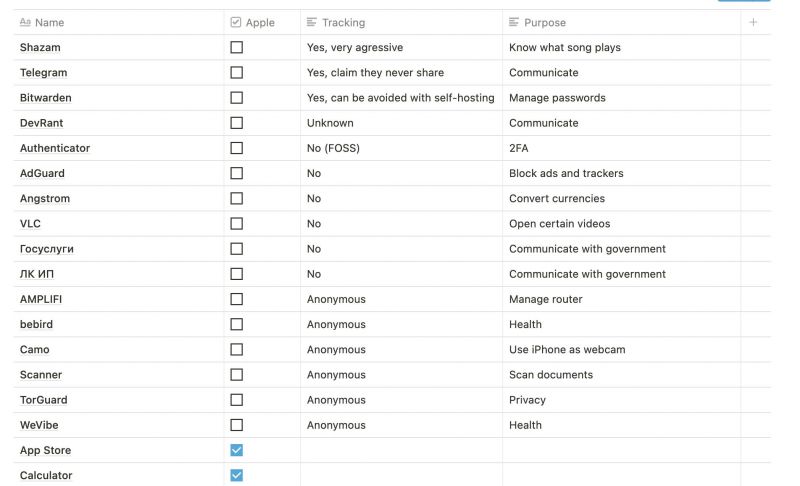 12
12 -
Has hacking become a hobby for script-kiddies?
I have been thinking about this for a while know, I went to a class at Stanford last summer to learn penetration-testing. Keep in mind that the class was supposed to be advanced as we all knew the basics already. When I got there I was aggravated by the course as the whole course was using kali linux and the applications that come with it.
After the course was done and I washed off the gross feeling of using other peoples tools, I went online to try to learn some tricks about pen-testing outside of kali-linux tools. To my chagrin, I found that almost 90% of documentation from senior pen-testers were discussing tools like "aircrack-ng" or "burp-suite".
Now I know that the really good pen-testers use their own code and tools but my question is has hacking become a script kiddie hobby or am I thinking about the tools the wrong way?
It sounds very interesting to learn https and network exploits but it takes the fun out of it if the only documentation tells me to use tools.3 -
Indian housing market literally exploits bachelors who look to take a house on rent. Motherfucking retards!9
-
Khmm Intel... A paper from 1995 describing speculative execution as :"Prefetching may fetch otherwise inaccesible instructions in Virtual 8086 mode." which makes Intel know the 'recent' exploits knows for just a shy 23 years. Why didn't they fix it? Who know.
https://t.co/KRMCEAfZgX2 -
I was programming in java, C# and similar languages for years now and I never knew how the buffer overflow exploits would work, then I started C and saw the fixed size char arrays. After puking on my keyboard I realized that most of the vulerable programs were indeed written in C or similar languages.11
-
After two years of being in (metaphorical) jail, I once again was given the a privilege of unlocking and rooting my phone. Damn. Frick Huawei, never coming back to that experience.
I gotta say, rooting... Feels a tad less accessible nowadays than when I last practiced it. All this boot image backup, patch, copy, reflash is crying to be automised, only reason I can think of why that changed and magisk can no longer patch itself into the phone's initrd is that it's somehow locked? Was it a security concern? Or can sideloaded twrp no longer do that?
Oh, and the war... The war never changes, only exploits do - fruck safety net... Good for Google that they now have an *almost* unfoolable solution (almost). The new hardware-based check is annoying af, but luckily, can still be forced to downgrade back to the old basic check that can be fooled... Still, am I the only one who feels Google is kinda weird? On one hand, they support unlocking of their own brand of phones, but then they continuously try to come up with frameworks to make life with a rooted or unlocked phone more annoying...
On the other hand, I do like having my data encrypted in a way that even sideloading twrp doesn't give full access to all my stuff, including password manager cache...
Any recommendations what to install? I do love the basic tools like adaway (rip ads), greenify (yay battery life!), viper4android (More music out of my music!) and quite honestly even lucky patcher for apps where the dev studio practices disgust me and don't make me want to support them...2 -
Colleague's answer to all QAs concerns : random technical jargon with 'postback' and 'aysnc' mixed.
QA. Ohhh.. Yeah sounds about right.
ME: yeah, you cannot fill the default value in file upload . Also I can't upload anything without user clicking button.. Its a security feature to avoid exploits..
QA : Stops making excuses man.
FML😶1 -
Is it okay to learn Perl and Ruby?
As I'm a networking guy and i want to write exploits of my own.
I have already been learning Perl and writing scripts.
I just want to know is it worth it in this era to learn these languages?8 -
The near future is in IOT and device programming...
In ten years most of us will have some kind of central control and more and more stuff connected to IOT, security will be even a bigger problem with all the Firmware bugs and 0-day exploits, and In 10 years IOT programmers will be like today's plumbers... You need one to make a custom build and you must pay an excessive hour salary.
My country is already getting Ready, I'm starting next month a 1-year course on automation and electronics programming paid by the government.
On the other hand, most users will use fewer computers and more tablets and phones, meaning jobs in the backend and device apps programming and less in general computer programs for the general public.
Programmers jobs will increase as general jobs decrease, as many jobs will be replaced by machines, but such machines still need to be programmed, meaning trading 10 low-level jobs for 1 or 2 programming jobs.
Unlike most job areas, self-tough and Bootcamp programmers will have a chance for a job, as experience and knowledge will be more important than a "canudo" (Portuguese expression for the paper you get at the end of a university course). And we will see an increase of Programmer jobs class, with lower paid jobs for less experienced and more well-paid jobs for engineers.
In 10 years the market will be flooded with programmers and computer engineers, as many countries are investing in computer classes in the first years of the kids, So most kids will know at least one programming language at the end of their school and more about computers than most people these days. -
How to discover and exploit vulnerabiliy in program or IoT firmware?C++, asm, writing zero-days, i have always been amazed by that. Art.
-
Finally I finished the exams, now I have to write my thesis. An agency who wants remain anonymous at the moment told my supervisor to choose a student who will works out on the ransomware argument. The relator was a little bit scared about consequences but I'm pressing to write a controlled ransomware in a closed network brtween virtual machines. What qualities a good ransomware should has?
Mutable structure to avoid antivirus detection? Good exploits and vulnerability scanners to make itself viral? The payload should stay in the code or should be downloaded from a server? I need some reference on analysis of vx codes, any help? -
I got more interested about the technical side of bugs in video games.
Really didn't understand the Pokémon hype as a kid, few months ago watched an entire YouTube series explaining the Old Man Glitch and ACE exploits in the game. 🤷♂️1 -
Intel Management Engine is half-hoax. Yes, it exists, but rumors about its true capabilities are fabricated and artificially amplified to make "what about intel ME" a very effective though-terminating cliche in the privacy community.
Let me remind you that to this day there was not a single takedown or leak that resulted from some power exploiting ME. All kingpin takedowns, all whistleblower deanons, all deanons period, all doxxes — all due to software shortcomings and other exploits.
Yet, "what about intel ME" reigns supreme and instills doom into the minds of the questioning. I can totally see someone who is new to this whole privacy thing doing their research, finding this ME craziness and thinking that real, actionable privacy is impossible, and going back to using amazon alexa and giving tiktok full camera and microphone access.
Just forget about Intel ME. It might as well not exist at all, because it was never used successfully. Instead, do this:
- Keep your threat models updated
- Learn to distinguish state-level actors from surveillance capitalists7 -
Is there an AI that generates malware already?
No sarcasm, I really wonder it there is already a model that finds exploits and makes rootkits or something.
It could make red teams obsolete.3 -
Email info: Adwarerecoveryspecialist@ auctioneer. net CONTACT ADWARE RECOVERY SPECIALIST TO SPY ON YOUR CHEATING PARTNER SMARTPHONE
WhatsApp info:+12 723 328 343
Uncovering your wife's phone secrets through the skills of a adware-like ADWARE RECOVERY SPECIALIST is a delicate and potentially unethical endeavor that should be approached with great caution. These so-called "sneaky ways" often involve highly sophisticated technological methods to bypass security measures and access private communications and data without the knowledge or consent of the device's owner. A skilled web recovery specialist might utilize advanced hacking techniques, exploits in mobile operating systems, or specialized surveillance software to surreptitiously monitor your wife's online activities, read her text messages and emails, track her location, and even retrieve deleted files - all while leaving little to no trace of their intrusion. However, engaging in such invasive and underhanded practices not only violates your wife's fundamental right to privacy, but can also severely damage the trust and integrity of your relationship if discovered. Rather than resorting to these underhanded tactics, it would be far wiser to have an open and honest discussion with your wife about any concerns you may have, and work together to address them through ethical, consensual means. Building a foundation of mutual understanding and respect is essential for the long-term health of any marriage. For help, Contact ADWARE RECOVERY SPECIALIST through: Email info: Adwarerecoveryspecialist@ auctioneer. net
-
You don’t realize how much trust you place in technology until it fails you or until someone exploits it. I learned this the hard way when my crypto wallet, containing over $87,000 in Bitcoin and Ethereum, was drained in an instant. A clever scam disguised as an official update cost me everything I had worked so hard to save.
At first, I believed what everyone said: “Once it’s gone, it’s gone.” The blockchain doesn’t forgive mistakes, and recovery felt like a fantasy. But desperation pushed me to keep looking, and that’s when I found DIGITAL RESOLUTION SERVICES. From the start, they were different: no false promises, no hype, just a practical and transparent approach. They explained how stolen funds could be traced, even through the complexity of blockchain transactions.
What followed was nothing short of incredible. Their team worked tirelessly, tracking the stolen assets step by step, wallet by wallet. They coordinated with exchanges, flagged suspicious accounts, and kept me updated at every turn. It felt like they were as invested in getting back my funds as I was.
Weeks later, I got the email I thought I’d never see: “We’ve recovered your funds.” Seeing my wallet balance restored felt like a second chance at everything I thought I’d lost. It wasn’t just about the money it was about reclaiming my future and finding hope again.
DIGITAL RESOLUTION SERVICES didn’t just recover my cryptocurrency; they gave me the ability to move forward without the weight of that loss holding me back. If you’ve lost crypto and feel like there’s no hope, don’t give up. There are people who know how to fight for you. I’m living proof that even in the world of crypto, recovery is possible with the right team.
Contact: Digital Resolution Services
Email: digitalresolutionservices (@) myself. com
WhatsApp: +1 (361) 260-8628
Forever grateful,
Monica dresdner 1
1 -
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.5 -
Best Crypto Recovery Specialists: How to Recover Stolen Cryptocurrency – Visit CryptoChain Global Track
Professional cryptocurrency recovery services have become essential in today's digital asset landscape. CryptoChain Global Track stands as a leading solution for victims of crypto theft, offering expert recovery services through certified blockchain forensic specialists with a demonstrated track record of successful fund retrieval.
CryptoChain Global Track's recovery methodology begins with comprehensive blockchain forensic analysis. Their team of licensed investigators examines transaction histories across multiple wallets and exchanges, utilizing advanced tracking technology to follow the digital trail of stolen Bitcoin, Ethereum, and other major cryptocurrencies. This technical approach identifies critical recovery points that untrained individuals typically miss, combining forensic tracing with legal strategies when recoverable funds are located on regulated platforms.
The company's transparent operations include a performance-based fee structure, ensuring clients only pay upon successful recovery. Their specialists maintain strict confidentiality protocols while providing regular case updates, keeping clients informed throughout the investigation process. The team prioritizes rapid response to new cases, understanding that timely intervention significantly increases recovery success rates before scammers can obscure the funds' trail through mixing services or cross-chain transfers.
CryptoChain Global Track's experts specialize in complex recovery scenarios, including investment frauds, exchange hacks, phishing attacks, and DeFi exploits. Their deep understanding of blockchain transaction patterns and scam behaviors enables them to develop effective counter-strategies for fund retrieval. The company's professional certifications and ethical standards provide assurance in an industry where questionable operators frequently emerge.
For those seeking professional cryptocurrency recovery assistance, CryptoChain Global Track offers complimentary initial consultations. Their experts provide realistic assessments of recovery potential and explain the investigative process in clear, understandable terms.
With CryptoChain Global Track, victims of cryptocurrency theft gain access to premier recovery services that combine technical expertise with professional investigative methods. Their certified team delivers legitimate solutions for reclaiming stolen digital assets in today's complex crypto environment.5 -
EXPERT IN RECOVERING LOST CRYPTO ASSETS | CRYPTOCHAIN GLOBAL TRACK
When digital assets vanish due to sophisticated scams or theft, professional intervention becomes critical for recovery. CryptoChain Global Track delivers expert cryptocurrency recovery services through certified blockchain forensic specialists who combine technical expertise with legal strategies to trace and reclaim stolen funds.
The recovery process begins with comprehensive blockchain analysis, where investigators examine transaction histories across multiple wallets and exchanges. Using institutional-grade tracking technology, they follow the digital trail of stolen Bitcoin, Ethereum, USDT and other cryptocurrencies, identifying patterns that reveal fund movement. Their methodology proves particularly effective against investment scams, exchange hacks, and phishing attacks where assets have been moved through complex networks.
What sets CryptoChain Global Track apart is their multi-phase recovery approach. After identifying recoverable funds, their team initiates formal procedures through proper legal channels when assets are located on regulated exchanges. This dual technical and legal strategy has successfully recovered millions in digital assets for clients worldwide.
Clients benefit from transparent engagement terms including a "no recovery, no fee" policy that eliminates financial risk. The team maintains strict confidentiality while providing regular case updates, ensuring clients remain informed throughout the process. Their specialists emphasize rapid response, as recovery success rates decline significantly when scammers move funds through mixing services or cross-chain bridges.
The company has particular expertise in tracing assets involved in DeFi exploits, fraudulent ICOs, and fake investment platforms. Their forensic capabilities extend to following funds across multiple blockchains, including Ethereum, Binance Smart Chain, and Polygon networks.
For professional assessment of crypto recovery possibilities, CryptoChain Global Track offers complimentary case evaluations. Their experts provide realistic recovery estimates and recommended actions before formal engagement.
With CryptoChain Global Track, victims of cryptocurrency theft gain access to professional-grade recovery services that combine cutting-edge blockchain forensics with proven asset recovery strategies. Their expert team delivers legitimate solutions for reclaiming stolen digital assets.4 -
STEPS TO RECOVER BITCOIN AND USDT FROM ONLINE INVESTMENT SCAM
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.
Conclusion
Having your funds stolen from Trust Wallet can be a harrowing experience, but there is hope with services like Betafort Recovery. Their systematic and professional approach makes them a reliable partner in recovering stolen cryptocurrencies. If you ever find yourself in a similar situation, don’t hesitate to reach out to them:
Email: info@betafort.online
WhatsApp: +17126004729
Thanks to Betafort Recovery, I was able to restore my financial stability and continue my journey in the world of cryptocurrency with renewed confidence. Their dedication and expertise turned a potential financial disaster into a successful recovery, for which I am eternally grateful.2



