Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 endor54476y@ishank-dev that's odd, nautilus allows that.
endor54476y@ishank-dev that's odd, nautilus allows that.
Try dolphin -h, maybe there's a flag to specify when you want to run it as root -
@Fede26 I have already tried all that, but that didn't work, even in nautilus, I couldn't see an option called create a file. Now I installed a new file manager called polo and it's pretty good, finding it better than dolphin and nautilus..XD
-
 Konsole30066yDolphin and Kate are disabled from executing as root due to a vulnerability in x11 which can allow other apps to hijack the privileges.
Konsole30066yDolphin and Kate are disabled from executing as root due to a vulnerability in x11 which can allow other apps to hijack the privileges.
I saw a few weeks ago that a patch is in progress to completely change the way kde apps ask for root permissions. Until that is complete, there is no way to run these apps as root other than editing the sources and recompiling.
Edit:
Check this out
https://blog.martin-graesslin.com/b... -
 Konsole30066y@alexbrooklyn No. Dolphin and Kate specifically execute with non-root privileges. Of you try to open with any user that has root privileges, they shut down
Konsole30066y@alexbrooklyn No. Dolphin and Kate specifically execute with non-root privileges. Of you try to open with any user that has root privileges, they shut down -
When a software is so secure that it shuts out legitimate usage, it becomes useless.
-
That's why I don't fancy kde. It's like macOS. You think it should be intuitive, but it gives you the middle finger as it's designed to act differently, by its own standards
-
 Konsole30066y@Fast-Nop It's not legit usage. People using it won't know that other apps can hijack it. It makes sense.
Konsole30066y@Fast-Nop It's not legit usage. People using it won't know that other apps can hijack it. It makes sense. -
 Konsole30066y@netikras What do you mean it's own standards. All it's trying to do is protect users from other malicious apps.
Konsole30066y@netikras What do you mean it's own standards. All it's trying to do is protect users from other malicious apps. -
@Konsole of course it's legit usage on a desktop that has a single user, and users who don't know that won't be using Linux anyway.
Sure, on a system with multiple users, that could be an issue (but then sudo should be blocked). Or when the system is intentionally locked down like in company usage. -
@Konsole malicious apps? hmm, smells like four-squares (windows)! Why would on earth there be a limitation (an enforcement if you will) like that on Linux?
-
 Konsole30066y@netikras dolphin is not malicious. But there could be some other app/process lurking around specifically looking for that exploit
Konsole30066y@netikras dolphin is not malicious. But there could be some other app/process lurking around specifically looking for that exploit -
 Konsole30066y@Fast-Nop it is not about single or multiple users. It's about other apps hijacking the privileges that they were not supposed to have.
Konsole30066y@Fast-Nop it is not about single or multiple users. It's about other apps hijacking the privileges that they were not supposed to have. -
@Konsole if an attacker gains access to the package manager repo to put in a malicious app, the system security has already gone out of the window.
And otherwise, the most important assets on a computer is not the system, it's the user's data, and that's always accessible without elevated rights. -
 Konsole30066y@Fast-Nop who is talking about repo here. Users install apps from places other than repos.
Konsole30066y@Fast-Nop who is talking about repo here. Users install apps from places other than repos. -
@Konsole If a user installs a malicious app because he isn't using the distro's package manager, the system security is also already gone.
-
 Konsole30066y@Fast-Nop And it is the responsibility of the OS to try to protect the user from any malicious apps. User won't necessarily know the program is malicious. Most Linux users don't use an antivirus
Konsole30066y@Fast-Nop And it is the responsibility of the OS to try to protect the user from any malicious apps. User won't necessarily know the program is malicious. Most Linux users don't use an antivirus -
 Konsole30066y@Fast-Nop a malicious program getting into system is bad enough. It obtaining root access is much much worse.
Konsole30066y@Fast-Nop a malicious program getting into system is bad enough. It obtaining root access is much much worse. -
@Konsole And there goes Nemo, Nautilus, Thunar and other recently used file managers that don't fuck up the whole usability just because there is a .0001% probability a user might open a malicious program or render a thumbnail of a malicious file...
Seriously, who fucking cares..? If the user is dumb enough to find a piece of malware on a linux desktop and execute it so it nukes all his files, do you really think the user will be relieved it has not been run as root? He's still gonna reinstall the whole system anyways. -
 Konsole30066y@netikras makes sense for normal users. But a malicious app running as root could really harm in long run. It could basically monitor everything that you do. What if you use Kate to edit a file that contains secret to a remote database?.
Konsole30066y@netikras makes sense for normal users. But a malicious app running as root could really harm in long run. It could basically monitor everything that you do. What if you use Kate to edit a file that contains secret to a remote database?.
Agreed that it fucks up the experience. But it is temporary. As soon as the workaround is complete, patch will be released. This has been KDE philosophy from the start. -
 Konsole30066yPlus if a user fully understands the risk, all they have to so is remove 2 lines from the code and recompile. Not too hard
Konsole30066yPlus if a user fully understands the risk, all they have to so is remove 2 lines from the code and recompile. Not too hard -
@Konsole if you install software via the package manager, then the package manager does have root rights, necessarily. Any malicious application would install itself accordingly.
This is just security wankery at work here because in any environment where the user really must not have root rights, the admin will not allow sudo in the first place. -
@Konsole seriously, If I just want to add an entry to my /etc/fstab using a GUI text editor I have to fetch the whole text editor's source code, find the line where that freaking restriction is in, remove it, install a shitload of Kate's dependencies and build toolset, build and reinstall the program. Oh, and all that until the next `apt update` overrides my changes.
A whole night spent just to edit a file as root.
In no way does this follow the FREE and OPEN mindset GNU and Linux are based on.
Seriously, even `ed` is more usable than KDE's text editor. -
 Konsole30066y@Fast-Nop you are missing the point. The user has the root rights. But does not know that he has installed a malicious application. Or there are other apps which don't require an install to work. It is to prevent malicious apps.
Konsole30066y@Fast-Nop you are missing the point. The user has the root rights. But does not know that he has installed a malicious application. Or there are other apps which don't require an install to work. It is to prevent malicious apps.
And as I said, if the user understands the risk, all he has to do is remove 2 lines from source. -
 Konsole30066y@netikras No. The way to do that is edit file as not root in Kate then export it somewhere else and use mv to replace the original file. That's what the kde docs say too. You only edit the sources if you want a permanent fix and understand the risks.
Konsole30066y@netikras No. The way to do that is edit file as not root in Kate then export it somewhere else and use mv to replace the original file. That's what the kde docs say too. You only edit the sources if you want a permanent fix and understand the risks. -
@Konsole no, you are missing the point. A malicious app would obviously demand to be installed in a way that it already can fuck with the system. Since the package manager also needs to update the system itself, it has to have root rights.
That's why the whole thing is security wankery. -
@Konsole I see. Boy is it playing on my nerves...
Every other GNU tool: use sudo and the tool name to run it as root
KDE tools: run the tool only with non-root permissions, save any modifications as non-root user and use GNU tools to change ownership / permissions
This somehow brings me memories of *teen years ago when I was still using Windows... The same anger, the same frustration and urge to hit someone/something is back. -
 Konsole30066y@Fast-Nop okay consider this case. I have an app x. It runs without installation. So there is no question of that app obtaining root privileges.
Konsole30066y@Fast-Nop okay consider this case. I have an app x. It runs without installation. So there is no question of that app obtaining root privileges.
But since I opened dolphin as root, the app X was able to obtain the privileges it needed.
This dolphin has to take steps to ensure other apps don't get privileges. -
 Konsole30066y@netikras Well other apps make you vulnerable. It's a trade-off kde is willing to make. Plus it's only temporary. They are going to release a patch soon which will make it such that the app will still run as normal user. But when you press Ctrl+s, it will ask you for password. They are standardizing this across all KDE frameworks.
Konsole30066y@netikras Well other apps make you vulnerable. It's a trade-off kde is willing to make. Plus it's only temporary. They are going to release a patch soon which will make it such that the app will still run as normal user. But when you press Ctrl+s, it will ask you for password. They are standardizing this across all KDE frameworks. -
@Konsole I need my stressball....
Clearly I am a GNU person. Definitely not a KDE/Windows/OSX guy, where decisions/restrictions/measures are made for me -
 Konsole30066y@netikras I find the lack of features and options in gnu suite more irritating. In my opinion that's not giving me the choice. Where say Nautilus chose to not include multiple options in create new and not having any other way to add it.
Konsole30066y@netikras I find the lack of features and options in gnu suite more irritating. In my opinion that's not giving me the choice. Where say Nautilus chose to not include multiple options in create new and not having any other way to add it.
Or in desktop where you have to edit the code to remove the irritating top bar.
Freedom of choice depends on perspective. For me kde provides me the facilities that gnome suite denies. -
@Konsole Nautilus had ability to extend that list by creating template files. Have they removed this feature?
-
@Konsole Installs without package manager tend to screw up the system. So it's basically compiling from tarball. Users who are able to do that will know what happens when you run a file manager as root.
Besides, the whole root thing isn't that important on a single user system because anything important is in the user's home folder, the data.
It's different on a multiuser system where root would give access to other users, of course. Like on servers. But there, nobody would run KDE in the first place. -
 Konsole30066y@netikras It was not there when I left gnome suite. (which is a long time) Maybe they added it later.
Konsole30066y@netikras It was not there when I left gnome suite. (which is a long time) Maybe they added it later. -
@Konsole well it was definitely there circa 2016 (the year I've switched to LinuxMint w/ Nemo). Ubuntu was still using Nautilus I reckon.
EDIT: It was also definitely there at ~2015 as well. I've discovered those templates on my netbook and I've switched from it to my current XPS at early '16.
-
 Konsole30066y@Fast-Nop There are ways to install packages without manager directly with binaries. And many of them don 't know how to compile from tarballs. Moreover even the people who compile from sources might not necessarily know the problems associated with opening fm with root privileges. I didn't until i specifically googled why kde didn't allow opening with root.
Konsole30066y@Fast-Nop There are ways to install packages without manager directly with binaries. And many of them don 't know how to compile from tarballs. Moreover even the people who compile from sources might not necessarily know the problems associated with opening fm with root privileges. I didn't until i specifically googled why kde didn't allow opening with root.
So yes , protection is needed. Plus KDE is not only used by developers. Many organizations use it too as their general systems.
And there are plenty of workarounds/alternatives to make it work. Opening fm with root is not a good idea -
 Konsole30066y@netikras Hmm Strange. Maybe I couldn't find it.
Konsole30066y@netikras Hmm Strange. Maybe I couldn't find it.
My point is that gnome keeps a lot of defaults with absolutely no way to change them(without editing sources of course) which KDE doesn't. And KDE devs went out of their way to add proper support for gtk apps. Most GTK apps run flawlessly on KDE. Same is not other way round. Qt apps look ugly af on gnome. That is lack of freedom in my opinion.
In fact I would say that real freedom lies in the fact that we have multiple distros/editors to choose from to suit our needs. Imagine being stuck with only editor (whatever that may be) -
@Konsole In organisations, the admins should not allow the users to do sudo at all. There is no need for a filemanager specific hack. It's still security wankery.
-
 Konsole30066y@Fast-Nop There are a lot of things you can't do without sudo. Organizations do allow that. Plus a savvy enough user can just boot into recovery and get root access.
Konsole30066y@Fast-Nop There are a lot of things you can't do without sudo. Organizations do allow that. Plus a savvy enough user can just boot into recovery and get root access.
The point is that there is a vulnerability and kde is protecting users from it until a fix is released. I don't see why we are having a debate.

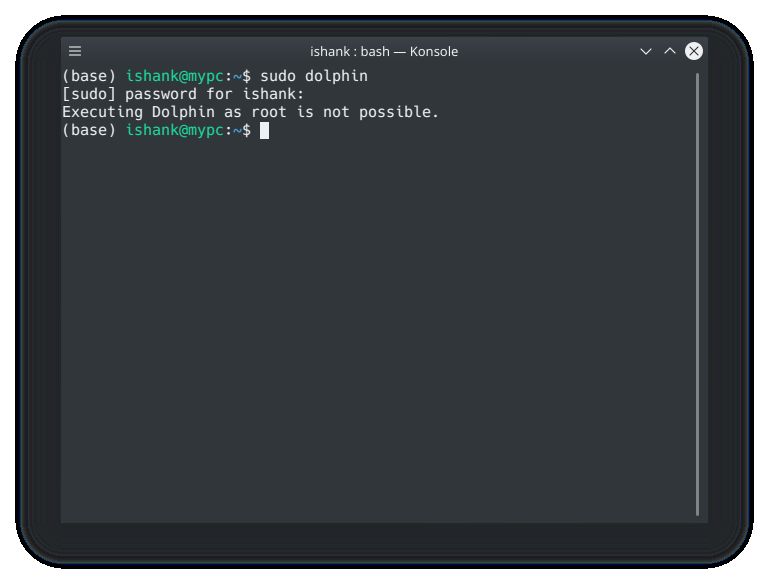
Does anyone know any workaround to open dolphin file manager as root?
question