Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
Ideally you would do this via the ClaimsPrincipal and an authorize policy. The claim should be stored in a ticket/jwt token and validated by an authority which can something like identity server.
The easy/sloppy alternative to using something like identity server is to use IClaimsTransformation to apply a per-call claims enrichment. I would recommend *not* doing the db check on every call as that will add an unnecessary load on your application and can contribute to async thread pool starvation. ClaimsTransformation instances necessarily execute in the identity phase of the pipeline, before routes, etc.
Instead of a per-call db check, inject IUserClaimStore into your claim transformer. This will be used to resolve claims for users and power what is known as a challenge/"Is active" phase which exists for upgrade invalidation. Write a custom IUserClaimsStore that features a ClaimsCache abstraction, this will be repository and cache for user claims.
https://github.com/aspnet/...
This should abstract retrieving active session claims and be compared against a key in deserialized tickets that determines whether or not the provided ticket claims need updating, and can be factored into an authority-like service so it can be shared between multiple scale processes. When an administrative operation modified a given user claim, it should surface an event using whatever syndicator you prefer. A ClaimCacheUpdate handler should then check the claim cache abstraction and update the in-memory representation of the user claims.
When a user ticket's claims fail the freshness check, you will need to pull the updated claims, update the security principal and a mechanism will need to supply an updated ticket. Aspnet identity and identity server will handle this as part of the pipeline.
Optimizations of the cache can be multi-level and LRU depending on ram constraints and freshness requirements. -
 catgirl10996y@Kimmax I don’t want to have to reset all login sessions for everyone any time one user has their roles changed, is suspended, etc.
catgirl10996y@Kimmax I don’t want to have to reset all login sessions for everyone any time one user has their roles changed, is suspended, etc. -
 catgirl10996y@spongessuck For social sites yes, if someone starts threatening people or posting illegal content you need to block their account with an instant effect.
catgirl10996y@spongessuck For social sites yes, if someone starts threatening people or posting illegal content you need to block their account with an instant effect. -
Seems like blocking content is more important than access. Post content code could verify access without the additional overhead of checking access for *everyone* for *every* page view.
-
 catgirl10996y@spongessuck I also want to ensure the user is notified immediately if their account is banned and they’re immediately unable to access non-public routes. I understand and accept the risks of additional overhead. (#FamousLastWords lol)
catgirl10996y@spongessuck I also want to ensure the user is notified immediately if their account is banned and they’re immediately unable to access non-public routes. I understand and accept the risks of additional overhead. (#FamousLastWords lol) -
Seems like you could just put a middleware in where you can do something like that and redirect or return a 403 or whatever.
Related Rants

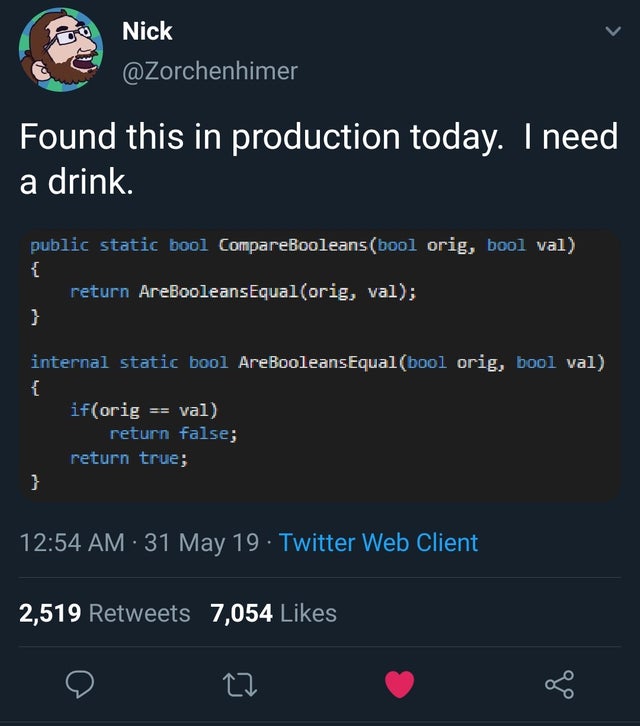 How do you even come up with shit like this?
How do you even come up with shit like this? I found such a treasure today in the production code.
I found such a treasure today in the production code.
How do I extend ASP Identity on .NET Core to check the database on every page load for an IsAdmin Boolean on the extended IdentityUser class? I need to do this to ensure rights haven’t been revoked and the user is still allowed to access restricted pages.
question
c#
asp.net
asp.net core