Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
Yup, sometimes you really don't need them monster frontend frameworks really. Simple JS or server side rendering will do it just fine.
-
 C0D4644185yWhat is this sorcery?
C0D4644185yWhat is this sorcery?
You dare write your own functionality and not rely on our lords and saviours react/vue/angular? -
 hitko29955y... and just like that someone puts <3 in the title ...
hitko29955y... and just like that someone puts <3 in the title ...
As a side note, fuck jQuery too, Vanilla for the win -
Ah yes, username, or as i like to call it, "<script>window.location='ass.com'</script>"
-
 C0D4644185y@SortOfTested true, but it's only a wrapper to js at the end of the day.
C0D4644185y@SortOfTested true, but it's only a wrapper to js at the end of the day.
He could just port that over to XMLHttpRequest() with minimal effort if "vanilla" was the go, however using bootstrap needs JQuery anyway. -
 C0D4644185y@SortOfTested 😅
C0D4644185y@SortOfTested 😅
he's still a bootstrap, fetch is too new for this.
Plus no IE support.
Granted that shouldn't be an issue in 2020 but... who knows. Some poor bastard still has to support IE8 around here, based on my websites analytics. -
 hitko29955yTo prevent rendering issues and XSS, one could then just tag template literals (takes 3kB, gziped)
hitko29955yTo prevent rendering issues and XSS, one could then just tag template literals (takes 3kB, gziped) -
 plusgut59665yI heavily disagree. If you use it like that, you have XSS vulnerabilities everywhere. I dislike that you are advocating for that.
plusgut59665yI heavily disagree. If you use it like that, you have XSS vulnerabilities everywhere. I dislike that you are advocating for that. -
 sleek33985y@plusgut XSS is a conspiracy theory. It is used to advocate fancy js frameworks. security vulnerabilities do not exist.
sleek33985y@plusgut XSS is a conspiracy theory. It is used to advocate fancy js frameworks. security vulnerabilities do not exist. -
 plusgut59665y@sleek I certainly hope that you were joking. If you meant it, then you would be very ignorant. It is very easily provable than XSS is very real, and your code is vulnerable to it. If response.Project.title or response.User.username contains html+script-tag, than I could execute code on your users browser and hijack their session.
plusgut59665y@sleek I certainly hope that you were joking. If you meant it, then you would be very ignorant. It is very easily provable than XSS is very real, and your code is vulnerable to it. If response.Project.title or response.User.username contains html+script-tag, than I could execute code on your users browser and hijack their session. -
 plusgut59665y@bioDan Thank you. I'm aware that they were trying to troll. But sadly they deep down actually don't care about security vulnerabilities.
plusgut59665y@bioDan Thank you. I'm aware that they were trying to troll. But sadly they deep down actually don't care about security vulnerabilities.
If you look at this whole thread, it is sadly very obvious that barely anyone cares, neither about their customers security, nor about there own applycation.
I used to see the developer community as an open minded and responsible community. But I'm wrong, ones again it shows that people are ignorant and lazy to learn things and have no aspiration for their craftmanship. -
 sleek33985y@plusgut ofcourse xss exists I thought it was obvious that i was joking. Dont worry we dealt with that from the backend by stripping tags and yes im aware a MITM attack is possible, security is a serious issue for sure BUT....
sleek33985y@plusgut ofcourse xss exists I thought it was obvious that i was joking. Dont worry we dealt with that from the backend by stripping tags and yes im aware a MITM attack is possible, security is a serious issue for sure BUT....
Do we *need* to handle all angles of security for a 200$ portfolio project? fuck that... I explicitly tell my cheapskates clients that cheap websites do not guarantee much security and people who think no one will care to hack them would rather save a buck or two so fuck them I do what my pay is worth.
And I already know and use Vue and React. I usually like react, but yes I miss the days when js logic was as simple as this little jQuery function and imported js file without the need to learn new frameworks every now and then or pray to god npm install doesnt blow up in my face.
i was... how do you say... ranting! as is the point of this platform🤷🏻♂️ -
 plusgut59665y@sleek It's nice to hear that you are not completely ignore the threat. But I wouldn't trust the backend to have everything validated correctly.
plusgut59665y@sleek It's nice to hear that you are not completely ignore the threat. But I wouldn't trust the backend to have everything validated correctly.
If the backend misses one thing at one point in the past, it might end up being in the database, and attack you even though that the backend fixed the future threat.
If you use a decent framework, you won't have that vulnerability. And I would argue that it saves time any money, to work with a framework anyway.
Sure, things used to be simpler back in the day, but I certainly don't look back and want to go back to that place.
Go ahead rant further, I was not meaning to stop you doing that. But I'll rant against you, if I disagree ;) I think that is the point of this platform, to have a good discussion after a rant.

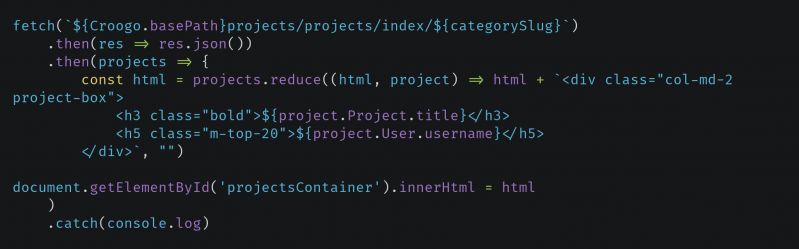



Fuck vue, react AND angular... this will always have a special place in my heart
rant