Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
@ThatDude I’m seriously contemplating jumping out my office window. Although I had completely forgot about this hard drive, I’m still very heart broken. I knew I had a drive with some on it, I just didn’t realize the extent until a friend recently sent me a picture of my address and reminded me. Will pay for someone to off me.
-
@MojoJojo hahaha it doesn't seem so though I hope he gets his data back cuz it seems to be something really bad right now :S
-
What’s not to understand? Lol sorry... I’ve got a hard drive that’s encrypted, I don’t remember the key, my friend sent me my old wallet address, that’s how much is on this $153,000 paperweight hard drive now.
-
DAAAAAAAMN!!!!! :O :O :O :O
Hope you remember that key bro, wish you all the best :))) -
train a machine learning instance for guessing the password...
until then you'll be a millionaire 😄 -
devNaut1618yAt some moment in your Life you will even gonna remember your first 63char WPA, memory is weird, let the password come.
If you wanna end yourself do it for the fun.
>:)
*Satan laughing*
Jokes aside..
Was It long and complicated? Le's do the math for bruteforcing -
https://tools.kali.org/password-att... here is 1 thing I found to try to get back in
-
@AnonyOps well do as they say and use a GPU to accelerate it, if you have multiple GPU run multiple instances I guess
-
How did you.used to store your password mabye you have a backup or remember part of it, that way you can use masks to make it take shorter
-
What password manager did you use? I'm guessing you didn't type those 64 characters by hand.
-
@virus200 Curious what they’d have that I don’t to be able to crack a 64 character password in under a lifetime+ lol. Even with GPU or CPU brute force a password like this would take lifetimes to crack.
-
@AnonyOps I'm the wrong guy to ask man lol but consulting a cubersecurity specialist of some sort couldn't hurt
-
@virus200 I’m taking to a few friends of mine that are further in the industry than I’d ever be able to get to and all are as heartbroken as I am lol.
-
@AnonyOps hmm, what about brute forcing on like 20 or so servers, trying 1/20 of the possible outcomes? I wonder what that would do for you.
-
Actually forget that, I suppose that would take forever (I read it as 64 bit for some reason). I wonder if true crypt has any vulnerabilities back then. Might be worth seeing if they had any security oriented bugs since then. Also some encryption has been deemed crackable since then, might be worth looking into.
Another thought I had, random number generator oftentimes aren't random enough, that might be an attack vector to try if you can remember what you generated it with.
Another thought, you've probably done this but think back to what was in Vogue at the time and was new and exciting to try out, maybe your database of passwords is stored on an old drop box account or something.
That's it, those are all my ideas and leads. Hopefully that helps. -
@heyheni interesting, I’m going to have to look into this more. I stayed up until 3am last night reading it, I appreciate it!
-
@AnonyOps dont forget to write a medium.com blog about your motivation to become a crypto cracking machine learning pen testing expert 😉
here is a video about weaponizing machine learning from the hacker conference defcon17
https://youtu.be/wbRx18VZlYA -
 lucaIO12088yTrueCrypt isn't being developed any further, is it? They may have a reason, probably a vulnerability
lucaIO12088yTrueCrypt isn't being developed any further, is it? They may have a reason, probably a vulnerability -
 lucaIO12088yhttps://m.heise.de/security/... this article is from 2013. I know it's german, it says that you can only crack passwords til 55 symbols... but the article is 4yo
lucaIO12088yhttps://m.heise.de/security/... this article is from 2013. I know it's german, it says that you can only crack passwords til 55 symbols... but the article is 4yo -
 bioDan55358ySorry for my ignorance but say you mined 2 BTC in 2012 - How do you know that the blockchain you had back then isnt outdated and therefore may be rejected by the current blockchain everyone else has? I mean, is there a chance you wont be able to claim the bitcoins anyway?
bioDan55358ySorry for my ignorance but say you mined 2 BTC in 2012 - How do you know that the blockchain you had back then isnt outdated and therefore may be rejected by the current blockchain everyone else has? I mean, is there a chance you wont be able to claim the bitcoins anyway? -
@bioDan either way I can’t claim anything due to it being encrypted, the bitcoins are still on the offline wallet, what would make them not be usable if I had the key and could access them?
-
Just like USD, no matter what the year they still keep their face value. Or am I not understanding what you’re asking?
-
@AnonyOps forgive me if this sounds dumb but is it possible to write some code that will loop through all possible password combinations at 64 character length? Even if it took a year to cycle through you'd still get it eventually. Maybe I'm just talking some movie shit I'm new at this haha.
-
@ThatDude his computer just needs MORE POWAHHH. maybe you can have IBM Watson run the code haha.
-
Lol 😂 yeah, even if I had access to supercomputers it would be after my lifetime that it gets even probably halfway done trying to run through all the combinations.
-
@AnonyOps technically it only has to run combinations till you find the right one 😂 Watson processes 500GB of data per second that's pretty damn good lol
-
@virus200 Lol I’m capable of brute forcing; anyone is really... The time though, I don’t have. If it can take 2 centuries to crack a 12 character password, put 64 characters into perspective.
-
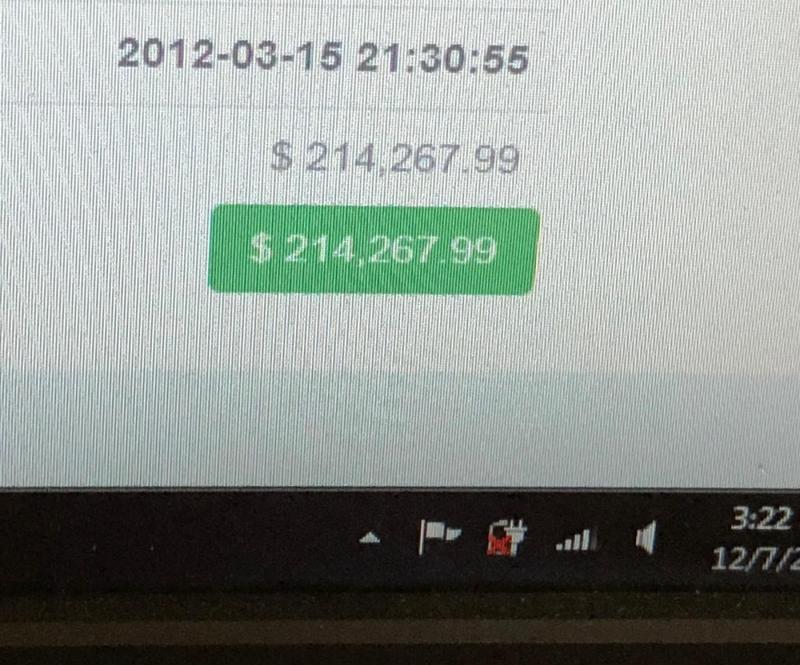
@ThatDude Believe me, I’m trying... so damn hard. I’m coming up on 68 hours of no sleep due to searching and testing things. Bitcoins are predicted to hit$40,000-$60,000.... I’ve got to figure something out.
-
And the 2 centuries is just for a 12 character A-Z password. There’s so many combinations.
-
@ThatDude My dude, you’re not the one that is setting on a $200,000 dollar paper weight. If anyone is retarded, well... it’s me. 💔😭
-
Lol my other wallet is keeping me from doing anything drastic, although it has nowhere near the cash this one has... what goes up, has to come down I guess. I’m just trying to get as much as I can before it does fall down lol.
-
You used something called true Crypt right? Maybe contact the company who made true crypt
-
I’d love to obtain it via brute, but it’s simply not possible with what I’ve got my hands on, and as stated early as well, a 12 character password can take up to 2 centuries to crack. Why can’t I be immortal (jk that would be a curse) and have a time machine?!
-
Give me the paper weight then. I'm just saying but if I had 200k sitting on a hard drive I'd be moving heaven and earth to Crack it.
-
@virus200 Lol I’m trying all I can do, but you can’t push a brute to to any faster than what it is. My hardware simply is limited, the only thing that would help is faster times. Look up brute forcing, look up how long it would take to crack just an alpha 64 character password, you will then understand that this isn’t something that can just be done in a blink of an eye lol, even though I want it to... NSA can’t even do it, this is why encryption is you’re fucked if you don’t have the password or a backdoor, but a backdoor would defeat the purpose etc.
-
@ThatDude I have been lol, that’s why I’m running on no sleep. I’ve moved three different times sense 2012, things are a little more difficult than you guys know lol 😂 😭
-
And if I had the ability to get this password back, I might as well attempt to obtain every private key to bitcoin wallets all over the world lol
-
Brute force, no matter who you are, with an encryption of this nature, will take ages. I’ve got to find another way in. Working on vulnerabilities and testing as we speak.
-
Ask Microsoft. They might have kept the password on their servers when you generated it 😛
-
Still stuck, I was able to preform a few of the vulnerabilities @heyheni had posted earlier in this thread, but one was a “write only” and you couldn’t see anything else on the drive. Still trying some other things but idk.
-
I’ve got a friend that works in a lab that wants to test his luck, it’s out for delivery.
-
HaaHHAahahaAhHhaHAHA 🙃🤬😭 my friend called me, the hard drive was dropped. I love when someone turns on a fan and shits into the blades while I’m on the receiving end.
-
@shellbug Tis alright! Idk what the next step is. He works in a lab for computer components so he’s got the capability to take apart things like this in a sound environment with the proper equipment. Not all hope is lost yet.
Related Rants






 Yes...
Yes...
TFFW you regret the decision of using “truecrypt” on a hard drive back in 2012......... and then forgetting the key...
rant
yes
another btc post.