Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
Yes. concating the sql query and parameters, and not using prepared statement will get far....
Specially the >0 at the start. -
 Kimmax106836y@magicMirror look at his code, he's probably getting started and learning, no reason to be a dumbfuck about it
Kimmax106836y@magicMirror look at his code, he's probably getting started and learning, no reason to be a dumbfuck about it -
 Kimmax106836yI don't know exactly how this would be called, the ; (what probably should be a point to continue the concatenation) finishes your assignment, so everything after will be handled as a new statement / expression / however you call it. Because said statement cannot be invoked, since it's not a method, nor a assignment, etc., it'd throw some error along the lines of "Cannot invoke non method", or maybe PHP just ignores the entire block.
Kimmax106836yI don't know exactly how this would be called, the ; (what probably should be a point to continue the concatenation) finishes your assignment, so everything after will be handled as a new statement / expression / however you call it. Because said statement cannot be invoked, since it's not a method, nor a assignment, etc., it'd throw some error along the lines of "Cannot invoke non method", or maybe PHP just ignores the entire block.
As @magicMirror pointed out, after getting that sorted out you should read up on "SQL Injections" and how to prevent them. Also FYI you can use $variables directly "in strings $like this", instead of explicitly wrapping them -
@Kimmax you are absolutly right. he is a dumbfuck.
And learning about sql injection when writing php is a fuken must. -
 Wack61256yAs some has pointed out, string concatenation isn't save for SQL stuff, especially when inserting user controlled variables. What you (@caiofior) should do instead is use prepared statements (PDO)
Wack61256yAs some has pointed out, string concatenation isn't save for SQL stuff, especially when inserting user controlled variables. What you (@caiofior) should do instead is use prepared statements (PDO)
I know, sadly most (beginner) tutorials don't cover this, which is a reason for so many people not doing it and helps to uphold PHP as a "joke" language...
I'd recommend to read https://phptherightway.com//... -
 Hel8y3356yI would recommend to always use prepared statements, as others have already pointed out.
Hel8y3356yI would recommend to always use prepared statements, as others have already pointed out.
However, in this case it is not that bad. One variable is cast to an integer and, assuming, the other ID is also an integer no SQL injection should be possible.
If, and if, OP is a beginner, I still think the coding style is very consistent. I've seen far worse than this, even from guys with years of experience.
Ontopic: I don't think this has a specific name, because I think this code will execute. A decent editor will probably give you warnings though (I think PHPStorm does, but not sure). -
 Hel8y3356y@Wack depending on the code we cannot see the code might return the rows matching ID 0. Using auto increment values in MySQL staring at 1, the 0 should normally not exist. They can manually be set to 0, which could result in a security flaw. Otherwise, I can not see how this would impact system security. It could still be a bug, be not related to security.
Hel8y3356y@Wack depending on the code we cannot see the code might return the rows matching ID 0. Using auto increment values in MySQL staring at 1, the 0 should normally not exist. They can manually be set to 0, which could result in a security flaw. Otherwise, I can not see how this would impact system security. It could still be a bug, be not related to security.
Related Rants
-
jsjunkie33
 Everyone always says the previous developer was crap, sometimes you're right
Everyone always says the previous developer was crap, sometimes you're right -
 tahnik17Finally I found a webpage related to my bug. The page is from 2004. *keeps reading* "Yes, yes! This is exac...
tahnik17Finally I found a webpage related to my bug. The page is from 2004. *keeps reading* "Yes, yes! This is exac... -
 retard34
retard34 Recently made an account on Instagram.
Uploaded two pics
Deleted both of them
Now I've -2 posts
Recently made an account on Instagram.
Uploaded two pics
Deleted both of them
Now I've -2 posts

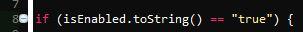
How do you call this php error, data not assigned to variable?
rant
bad code
php
bug