Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 stop65806yEncrypt?
stop65806yEncrypt?
AES256 or chacha20 with random padding and and key with the same length
Hash?
Bcrypt -
Caesar cipher but with random shift for every character. And with chinese symbols after A-Z.
-
All of you who commented but didn't leave a ++ will roast in hell...
makes me think of chicken..
darn you!
(Also HAR HAR "GO" dad jokes) -
 Quirinus7366yRead it to a baby until it mumbles something random. Store that along with the plaintext password.
Quirinus7366yRead it to a baby until it mumbles something random. Store that along with the plaintext password. -
 Kimmax106736yBest encryption will vastly differentiate from a good effective one lol
Kimmax106736yBest encryption will vastly differentiate from a good effective one lol
Also, as said before, passwords a generally being hashed, not encrypted -
Pair each letter/number with a symbol(i.e. a to "$") then place the resulted string in a perl script, nobody will suspect a thing.
-
 muttley856ySet the password to ******** then put that as plain text in your code. No one will try it because they will assume it is redacted.
muttley856ySet the password to ******** then put that as plain text in your code. No one will try it because they will assume it is redacted. -
 Pickman6166yDepends on what you want to achieve.
Pickman6166yDepends on what you want to achieve.
Security only?
One time pad wins by default (but it's only useful for a local password manager).
DB entries to check passwords inserted by users? You shouldn't save the encrypted version but only an hash.
Sending passwords to the users? Any secure encryption, it's not more important than the rest of the users' data (e.g. their session tokens).
Personally I would use the same protocol as the session tokens (possibly adapting it for asymmetric encryption if necessary) because it guarantees the same security instead of potentially creating a security breach (if you use two different protocols only one needs to be faulty to generate a breach). -
 Pickman6166y@fuck2code almost right. Eventually the user has to receive the passwords you randomly generated for him.
Pickman6166y@fuck2code almost right. Eventually the user has to receive the passwords you randomly generated for him. -
 Pickman6166y@nitwhiz it's equivalent to one time pad but notice that the chinese symbols are useless. They increase the space of the output but if the attacker excludes those symbols it's the precise same brute attack as a Cesar with random offsets or a randomly generated one time pad.
Pickman6166y@nitwhiz it's equivalent to one time pad but notice that the chinese symbols are useless. They increase the space of the output but if the attacker excludes those symbols it's the precise same brute attack as a Cesar with random offsets or a randomly generated one time pad. -
@metamourge Fair enough but I've never found a ready to use php library and compiling it has never worked for me either so then I'd say that BCrypt is the next best thing...
Related Rants

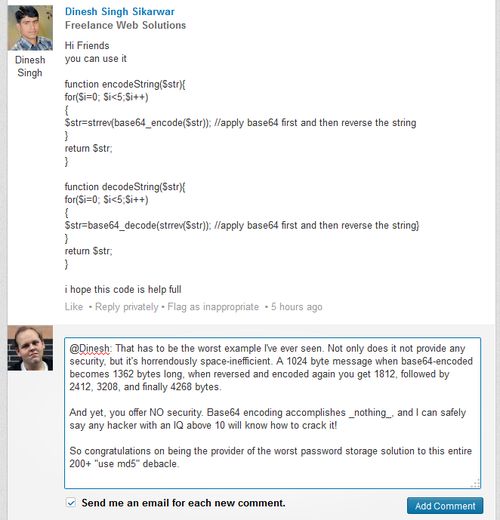
 Oh.. I see.. How about pass@123...
Oh.. I see.. How about pass@123... The power of passwords!!!1
The power of passwords!!!1
Best way to encrypt a password.
Any language.
Go.
question
password
encryption