Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
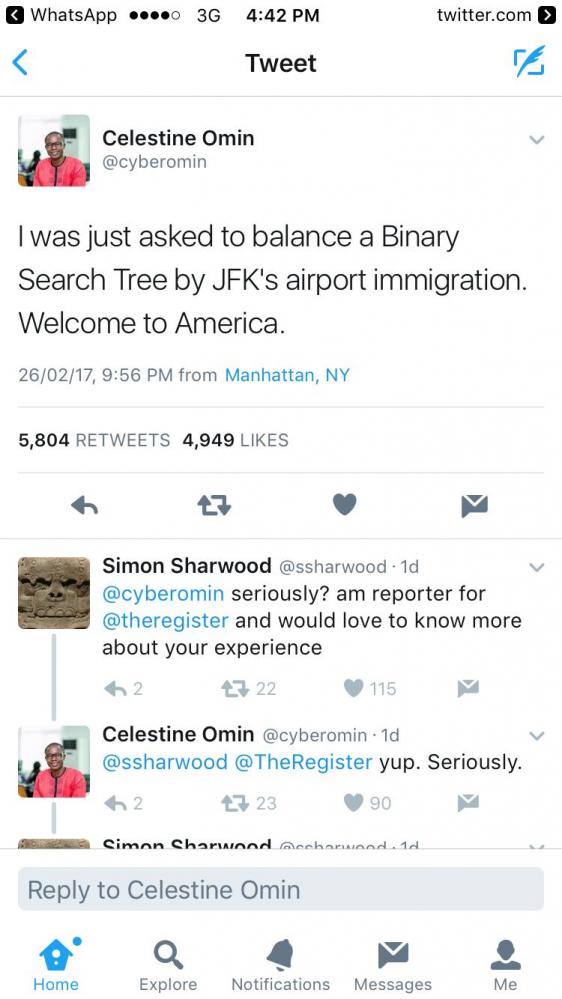
Search - "checkmate"
-
Our front-end team is pissed at me because they found a feature I pushed last month and claimed they didn't know it existed and how can they help clients if they don't know what's going on with the platform and - I pointed them to the Pivotal story of the feature that they were included in as well as the full changelog announcement I made to the entire team the day I pushed it.
Knowledge is power, especially when it's in writing with a timestamp.5 -
Promising the boss a 95% model accuracy when the arXiv paper says it can only reach 86% is what I call self-checkmate2
-
Are you familiar with chess? What classes/objects and methods/functions would you use to implement the game of chess? Who knows if checkmate is reached? What about timed games?
It always leads to an interesting discussion and you can easily throw out prodding questions if they get stuck. I've never had anybody give me the exact same answer, and it's been complimented post-interview a handful of times.12 -
Procrastinates, wastes time not working; hates himself
Works on a regular schedule, putting in effort and feeling sleep deprived;
Hates himself even more.
Inner self hatred realises something.
Who said my self-loathing was bad for me??? -
My ex-colleague contacted me recently to help build a solution that would checkmate the case of code theft that they are currently challenged with. I tried to suggest the developers either work remotely (using rdp or similar), or physically with a company provided system. He rejected both recommendations and insisted the potential culprit shouldn't be aware he is being monitored
He proposed the following flow for what he intends I build: an obfuscated program scattered across the code base, possibly assembling at intervals or as a reaction to project build. Then signaling their server with details of the machine it's running on
The project to be rigged with the spyware is written in spring boot and I can't turn this down even if I don't think it's worth it cuz no work has been forthcoming and I'm nearly out of cash
So the question is, is the flow described above a feasible one? Can you suggest a smarter way to detect when the code is transferred to the system of an unaccredited engineer? Can you suggest any tips on how to go about this?6 -
I spent whole day for one client in order to implement ddos protected tunnel into his java based project. In exchange he was supposed to send me his source code of one of his projects. Fucker didnt send me anything. Good that while doing migrations for him I downloaded his compiled project backup, so all I had to do was decompile his jars which had no obfuscafion whatsoever, so I managed to salvage around 95 percent of his source code. Checkmate boi.
-
rebuild preprocessor package applying preprocessor OK.
dependency cycle: the preprocessor depends on the lib it's trying to process oh noes.
OK fixed. how? code duplication (just a little).
checkmate, motherfucker.
up yours best practices i am max wright, maximum crackhead power.
now syntax check file once preprocessor is applied. normally need fork, but slows down build. can do with function?
yes but file has dependency cycle with itself because trying to load it's symbol table while loading it's symbol table so cannot compile. oops.
how about overwrite namespace with namespace cat ++unique_id (static uint64_t)? OK can do. not even store original name, just cat OUT_${uid} to it.
work like charm. now have syntax error messages, format all shit.
utilize power of crack /at\s (?<fname>.+) \s line \s (?<line>\d+) , \s near "/\e[32;1m$+{fname}\e[0m at \e[33;21m$+{line}\n\n\e[36;1m```/;
excellent, now subst closing quotes, easier said than done or maybe not really. just catch /\n"/```\e[0m\n/ OK for now.
errmes easy read and build complete in under a second now vs TWO MINUTES before; willy tanner strikes again.
I wins cookie now. brb need more magic.