Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "tofu"
-
Kinda rant...
Attempted making some Indianized teriyaki tofu.
Looked amazing. The sauce turned out amaaazing.
Served some.
Ugh... This tofu tastes wierd.
Disappointment 😫!!!
Threw the tofu.
Added noodles to the sauce 😍
Perfect.26 -
I opened a post starting with a "NO TOFU" logo and I was wondering what relationship existed between the SSH protocol and anti-vegan people.
After some paragraphs it explained that TOFU stands for Trust On First Use (a security anti-pattern). 7
7 -
First commission done! Tofu 60%, Krytox 205g0 lubed creams, SA keycaps, and a special surprise foam dampening plate for extra thocc on that Brass plate.
 28
28 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.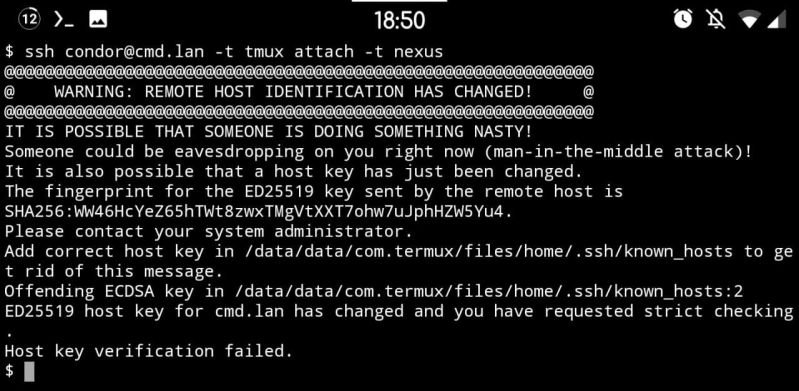 19
19 -
Do you suffer from low motivation ? For three easy installments of $79.95 plus shipping & handling , the secrets of overcoming low motivation can be yours . Act now , don’t delay !
Operators are standing by & the first caller will receive a free set of dollar general steak knives in a faux wood gift box , excellent for regifting for that team party or potluck where if you’re lucky , you might get tofu .7 -
How much zucchini is too much zucchini?
I know I have WAY too much...
I knew at least when 1st considering D20 zucchini breads.
then when i began to wonder if the remaining batter would work with my death star waffle iron...ill know tomorrow!
....ran out of typical pans, incl foil ones(normal and mini for easy gifting)
- gave 1 away (similar sized as in pic)
- approx. 2 lg zucchini bread loaves in fridge (gave away 2, ate a ½)
- cut up\froze enough onions\peppers\pak choi to a min. acceptable zucchini : everything else stir fry ratio... x20 servings
- similarly, green onions, pak choi, marinated sesame fried tofu bits, zucchini and miso (quick miso soup) x16
- thinly sliced enough to layer it into ~20 lg servings of lasagna.
... zucchini in pic is slightly larger than the one that made the many aforementioned and pictured loaves of zucchini bread
apparently, in a week tops, I'm gonna have at least another 3 more THAT size needing to be picked
anyone in the continental US want some zucchini bread? or, if in michigan, zucchinis?
i didnt even plant much... actually only about ½ of other years.
i am also having some serious overflows coming of (at least) grapes and watermelons.
grapes...
when i bought this place, this odd, square, surrounded by cement walkways, area, with an increasingly problematic tree (risking cable\electric lines, foundation, etc) and so dense with weeds that I learned, dandelions have a giant, bush-like form, with heights beyond 8ft tall.
i grew up hanging out in the nearby woods, noticing that weeds lost the fight vs raspberry\blackberry plants. being handicapped\lazy\experimental, w\ev, i figured id just kill it all then fill it with random berries... knew nothing about grapes so just got 4+ random types... apparently they are all fancy\expensive grapes... and reeeeeaally produce. i already had to pick ~10lbs.
watermelons-
idr if i planted normal ones and little ones or just little ones... idk how to tell without cutting them open or maybe just watching a long time to see if they stopped growing?
anyone with advice (or seeking watermelons) is welcome.
assuming (hoping) they are mini ones there's at least 2dz that are at least ping pong ball size.... and around 100 little yellow flowers still.
i totally get that my frustrating problem with produce here would be beyond welcomed by most people... but seriously... wtf do i do with a few dozen to over a hundred (hopefully mini) watermelons, so many zucchini that, despite personal daily consumption and at least a half dozen friends that love zucchini bread and\or my secretly healthy lasagna(my friends tend to be guys), but have their limits capping out, plus mine, at less than ½ whats rapidly being produced and, apparently, thousands of dollars worth of hundreds of pounds of fancy grapes???
there's an interesting old lady across the street who'll take at least what her and husband can possibly consume,.. even makes grape jam, but thats still only a few dz lbs tops.
it seems wrong to kill the plants (or even to remove a large amount of blossoms and feed them all to JSON (lil tortoise)... pretty sure he's already getting tired of them just from the few that fell off in the wind or something.
i wish i knew some farmers that do farmers market things... but that kinda seems super suspicious... 'hey mr farmer... want a large supply of expensive grapes, watermelon and zucchini, for free? you can sell them to random people, or just give them away. i dont want money or anything...' idk... seems like the beginning of one of those movies that either has evil alien plants assimilating all land mammals, or where there's some crazed medical researcher convinced that there's a massive, underrated threat without enough attention for vaccination production funds-- so they are gonna release some deadly virus supposedly to save the world.
ive been cooking too long.
ideas pl0x? 79
79 -
Took me 1 week to deploy a Pet-Store app in AKS (and build the AKS ofc, in Tofu).
that doesn't look good.2 -
Well Taken Care Of™: Empowering Women Through Perimenopause and Menopause in Needham, MA
At Well Taken Care Of™, we understand that navigating the journey of perimenopause and menopause can be challenging. These natural life stages can bring about significant physical and emotional changes, and it’s crucial to have the right support system in place. Our team is committed to helping women in Needham, MA, and beyond manage and thrive during this transition with personalized care, expert guidance, and a holistic approach to health and wellness.
Located at 140 Gould St, Needham, MA 02494, Well Taken Care Of™ offers comprehensive services to support women through perimenopause and menopause. Whether you are just beginning to experience symptoms or have already entered menopause, we are here to provide the tools and resources you need to navigate this phase of life with confidence and ease.
Understanding Perimenopause and Menopause
Perimenopause and menopause are natural biological phases in every woman’s life, but they can bring about a range of physical, emotional, and mental changes. Here’s a closer look at each stage:
Perimenopause: This is the transitional phase leading up to menopause, typically beginning in a woman’s 40s, although it can start earlier. During perimenopause, the ovaries gradually produce less estrogen, leading to fluctuations in hormone levels. This phase can last anywhere from 4 to 10 years, and women may experience symptoms such as irregular periods, hot flashes, night sweats, mood swings, sleep disturbances, and changes in skin or hair.
Menopause: Menopause is officially diagnosed when a woman has gone 12 consecutive months without a menstrual period. This phase marks the end of a woman’s reproductive years and is associated with a significant decrease in estrogen production. Symptoms can include hot flashes, weight gain, vaginal dryness, low libido, fatigue, and changes in mood.
While these changes are natural, they can affect a woman’s quality of life. Fortunately, at Well Taken Care Of™, we are dedicated to helping women manage these transitions and improve their overall well-being.
How Well Taken Care Of™ Can Support You Through Perimenopause and Menopause
At Well Taken Care Of™, we take a holistic approach to women’s health, providing support through nutrition, lifestyle adjustments, and functional medicine. Our goal is to help you find balance during perimenopause and menopause and empower you to live a vibrant, healthy life.
1. Personalized Nutrition Plans
Hormonal fluctuations during perimenopause and menopause can lead to weight gain, fatigue, and other physical changes. Our nutritionists can help you create a balanced, sustainable diet that supports your body’s needs during this time. This may include:
Hormone-balancing foods: Certain foods can support hormonal balance and reduce symptoms like hot flashes. We’ll guide you on including nutrient-dense foods that promote estrogen production, such as flaxseeds, tofu, and leafy greens.
Anti-inflammatory diet: Inflammation can worsen symptoms of menopause, such as joint pain and mood swings. We’ll help you incorporate anti-inflammatory foods like berries, nuts, and fatty fish to reduce discomfort.
Blood sugar regulation: Many women experience blood sugar imbalances during menopause, leading to weight gain and fatigue. Our nutritionists will provide meal plans that keep your blood sugar levels stable throughout the day.
2. Functional Medicine Approach
Functional medicine focuses on identifying and addressing the root causes of health issues. At Well Taken Care Of™, we use functional medicine to assess and address hormonal imbalances, digestive health, and inflammation—all of which can be exacerbated during perimenopause and menopause.
We offer personalized treatment plans that may include:
Hormone testing: We can test your hormone levels to understand your unique needs and help identify any imbalances that may be contributing to symptoms.
Herbal and supplement support: Based on your individual needs, we may recommend supplements such as magnesium, vitamin D, and phytoestrogens to help support hormone balance and reduce symptoms like hot flashes and mood swings.
Gut health support: Hormonal changes can impact gut health, leading to bloating and digestive discomfort. We provide dietary and supplement recommendations to improve digestion and support a healthy gut microbiome.
3. Lifestyle Coaching and Stress Management
Stress can exacerbate many symptoms of perimenopause and menopause, including anxiety, sleep disturbances, and hot flashes. Our health coaches can help you incorporate relaxation techniques, such as:
Mindfulness and meditation: These practices can reduce stress, improve sleep, and support emotional well-being during this transition.
Breathing exercises: Deep breathing exercises can help alleviate symptoms like hot flashes and anxiety. 6
6

