Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "ed25519"
-
Seriously? Microsoft does not support ed25519 SSH keys in neither Azure DevOps nor the actual Azure Virtual Machines? Like seriously? No there has to be a joke. There just ain't no way
It has been in OpenSSH since 2013.
2013.
We're in 2023, if you've forgotten.
10 years ago, OpenSSH implemented this standard.
Did you know what they tell you when you enter your valid Ed25519 SSH key into their system?
Did you know they tell you that "Your SSH key is invalid"?
WHAT DO YOU MEAN INVALID???!?! IT WORKS EVERYWHERE ELSE JUST FINE!!! YOU'RE THE ONE THAT HAS NO FUCKING BRAINS!!!
Composure.
I am calm, I am calm.
I have always. Been. CALM!
There is no one more calm than me....
I guess RSA it is then.
A second SSH key, just for Microsoft.5 -
Last Monday I bought an iPhone as a little music player, and just to see how iOS works or doesn't work.. which arguments against Apple are valid, which aren't etc. And at a price point of €60 for a secondhand SE I figured, why not. And needless to say I've jailbroken it shortly after.
Initially setting up the iPhone when coming from fairly unrestricted Android ended up being quite a chore. I just wanted to use this thing as a music player, so how would you do it..?
Well you first have to set up the phone, iCloud account and whatnot, yada yada... Asks for an email address and flat out rejects your email address if it's got "apple" in it, catch-all email servers be damned I guess. So I chose ishit at my domain instead, much better. Address information for billing.. just bullshit that, give it some nulls. Phone number.. well I guess I could just give it a secondary SIM card's number.
So now the phone has been set up, more or less. To get music on it was quite a maze solving experience in its own right. There's some stuff about it on the Debian and Arch Wikis but it's fairly outdated. From the iPhone itself you can install VLC and use its app directory, which I'll get back to later. Then from e.g. Safari, download any music file.. which it downloads to iCloud.. Think Different I guess. Go to your iCloud and pull it into the iPhone for real this time. Now you can share the file to your VLC app, at which point it initializes a database for that particular app.
The databases / app storage can be considered equivalent to the /data directories for applications in Android, minus /sdcard. There is little to no shared storage between apps, most stuff works through sharing from one app to another.
Now you can connect the iPhone to your computer and see a mount point for your pictures, and one for your documents. In that documents mount point, there are directories for each app, which you can just drag files into. For some reason the AFC protocol just hangs up when you try to delete files from your computer however... Think Different?
Anyway, the music has been put on it. Such features, what a nugget! It's less bad than I thought, but still pretty fucked up.
At that point I was fairly dejected and that didn't get better with an update from iOS 14.1 to iOS 14.3. Turns out that Apple in its nannying galore now turns down the volume to 50% every half an hour or so, "for hearing safety" and "EU regulations" that don't exist. Saying that I was fuming and wanting to smack this piece of shit into the wall would be an understatement. And even among the iSheep, I found very few people that thought this is fine. Though despite all that, there were still some. I have no idea what it would take to make those people finally reconsider.. maybe Tim Cook himself shoving an iPhone up their ass, or maybe they'd be honored that Tim Cook noticed them even then... But I digress.
And then, then it really started to take off because I finally ended up jailbreaking the thing. Many people think that it's only third-party apps, but that is far from true. It is equivalent to rooting, and you do get access to a Unix root account by doing it. The way you do it is usually a bootkit, which in a desktop's ring model would be a negative ring. The access level is extremely high.
So you can root it, great. What use is that in a locked down system where there's nothing available..? Aha, that's where the next thing comes in, 2 actually. Cydia has an OpenSSH server in it, and it just binds to port 22 and supports all of OpenSSH's known goodness. All of it, I'm using ed25519 keys and a CA to log into my phone! Fuck yea boi, what a nugget! This is better than Android even! And it doesn't end there.. there's a second thing it has up its sleeve. This thing has an apt package manager in it, which is easily equivalent to what Termux offers, at the system level! You can install not just common CLI applications, but even graphical apps from Cydia over the network!
Without a jailbreak, I would say that iOS is pretty fucking terrible and if you care about modding, you shouldn't use it. But jailbroken, fufu.. this thing trades many blows with Android in the modding scene. I've said it before, but what a nugget!8 -
OpenSSH 8.2 is out. This release removes support for the ssh-rsa key algorithm. The better alternatives include:
1. RSA SHA-2 signature algorithms rsa-sha2-256/512. These algorithms have the advantage of using the same key type as "ssh-rsa" but use the safe SHA-2 hash algorithms (now used by default if the client and server support them).
2. The ssh-ed25519 signature algorithm.
3. ECDSA algorithms: ecdsa-sha2-nistp256/384/521.
In this release, support for FIDO/U2F hardware tokens. Also noteworthy, a future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms.17 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.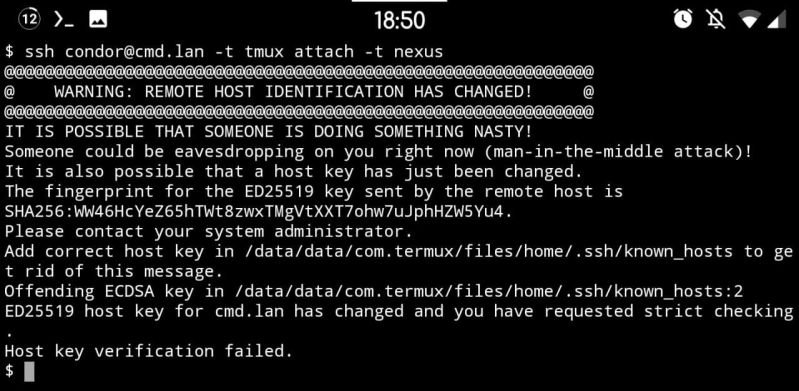 19
19 -
techie 1 : hey, can you give me access to X?
techie 2 : the credentials should be in the password manager repository
t1 : oh, but I don't have access to the password manager
t2 : I see your key A1B2C3D4 listed in the recipients of the file
t1 : but I lost that key :(
t2 : okay, give me your new key then.
t1 : I have my personal key uploaded to my server
t1 : can you try fetching it?
t1 : it should work with web key directory ( WKD )
t2 : okay
t2 : no record according to https://keyserver.ubuntu.com
t1 : the keyserver is personal-domain.com
t1 : try this `gpg --no-default-keyring --keyring /tmp/gpg-$$ --auto-key-locate clear,wkd --locate-keys username@personal-domain.com`
t2 : that didn't work. apparently some problem with my dirmgr `Looking for drmgr ...` and it quit
t1 : do you have `dirmngr` installed?
t2 : I have it installed `dirmngr is already the newest version (2.2.27-2)`
t2 : `gpg: waiting for the dirmngr to come up ... (5)` . this is the problem. I guess
t1 : maybe your gpg agent is stuck between states.
t1 : I don't recall the command to restart the GPG agent, but restarting the agent should probably fix it.
t1 : `gpg-connect-agent reloadagent /bye`
source : https://superuser.com/a/1183544
t1 : *uploads ASCII-armored key file*
t1 : but please don't use this permanently; this is a temporary key
t2 : ok
t2 : *uploads signed password file*
t1 : thanks
t2 : cool
*5 minutes later*
t1 : hey, I have forgotten the password to the key I sent you :(
t2 : okay
...
t2 : fall back to SSH public key encryption?
t1 : is that even possible?
t2 : Stack Overflow says its possible
t1 : * does a web search too *
t1 : source?
t2 : https://superuser.com/questions/...
t2 : lets try it out
t1 : okay
t2 : is this your key? *sends link to gitlab.com/username.keys*
t1 : yes, please use the ED25519 key.
t1 : the second one is my old 4096-bit RSA key...
t1 : which I lost
...
t1 : wait, you can't use the ED25519 key
t2 : why not?
t1 : apparently, ED25519 key is not supported
t1 : I was trying out the steps from the answer and I hit this error :
`do_convert_to_pkcs8: unsupported key type ED25519`
t2 : :facepalm: now what
t1 : :shrug:
...
t1 : *uploads ASCII-armored key file*
t1 : I'm sure of the password for this key
t1 : I use it everyday
t2 : *uploads signed password file*
*1 minute later*
t1 : finally... I have decrypted the file and gotten the password.
t1 : now attempting to login
t1 : I'm in!
...
t2 : I think this should be in an XKCD joke
t2 : Two tech guys sharing password.
t1 : I know a better place for it - devRant.com
t1 : if you haven't been there before; don't go there now.
t1 : go on a Friday evening; by the time you get out of it, it'll be Monday.
t1 : and you'll thank me for a _weekend well spent_
t2 : hehe.. okay.8
