Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "ssh key"
-
Today I discovered by myself that...
...in a shell...
...when entering a password (e.g. ssh)...
...and you make a typo... 🤦♂️
...you don't need to smack that backspace key like a maniac! You can just use the clear line shortcut: control+U (^U). This clears all input to the left of your cursor and this also works for passwords.26 -
Meanwhile at NSA:
Alice: Uhm... Bob? I lost my SSH key...
Bob: *facepalms*
Alice: ... but i still have the public key! Could you please recalculate the private one for me?
Bob: Sure, give me a second. I'll fax it to you when it's ready.
Me: *wakes up from nightmare*13 -
So I got the job. Here's a story, never let anyone stop you from accomplishing your dreams!
It all started in 2010. Windows just crashed unrecoverably for the 3rd time in two years. Back then I wasn't good with computers yet so we got our tech guy to look at it and he said: "either pay for a windows license again (we nearly spend 1K on licenses already) or try another operating system which is free: Ubuntu. If you don't like it anyways, we can always switch back to Windows!"
Oh well, fair enough, not much to lose, right! So we went with Ubuntu. Within about 2 hours I could find everything. From the software installer to OpenOffice, browsers, email things and so on. Also I already got the basics of the Linux terminal (bash in this case) like ls, cd, mkdir and a few more.
My parents found it very easy to work with as well so we decided to stick with it.
I already started to experiment with some html/css code because the thought of being able to write my own websites was awesome! Within about a week or so I figured out a simple html site.
Then I started to experiment more and more.
After about a year of trial and error (repeat about 1000+ times) I finally got my first Apache server setup on a VirtualBox running Ubuntu server. Damn, it felt awesome to see my own shit working!
From that moment on I continued to try everything I could with Linux because I found the principle that I basically could do everything I wanted (possible with software solutions) without any limitations (like with Windows/Mac) very fucking awesome. I owned the fucking system.
Then, after some years, I got my first shared hosting plan! It was awesome to see my own (with subdomain) website online, functioning very well!
I started to learn stuff like FTP, SSH and so on.
Went on with trial and error for a while and then the thought occured to me: what if I'd have a little server ONLINE which I could use myself to experiment around?
First rented VPS was there! Couldn't get enough of it and kept experimenting with server thingies, linux in general aaand so on.
Started learning about rsa key based login, firewalls (iptables), brute force prevention (fail2ban), vhosts (apache2 still), SSL (damn this was an interesting one, how the fuck do you do this yourself?!), PHP and many other things.
Then, after a while, the thought came to mind: what if I'd have a dedicated server!?!?!?!
I ordered my first fucking dedicated server. Damn, this was awesome! Already knew some stuff about defending myself from brute force bots and so on so it went pretty well.
Finally made the jump to NginX and CentOS!
Made multiple VPS's for shitloads of purposes and just to learn. Started working with reverse proxies (nginx), proxy servers, SSL for everything (because fuck basic http WITHOUT SSL), vhosts and so on.
Started with simple, one screen linux setup with ubuntu 10.04.
Running a five monitor setup now with many distro's, running about 20 servers with proxies/nginx/apache2/multiple db engines, as much security as I can integrate and this fucking passion just got me my first Linux job!
It's not just an operating system for me, it's a way of life. And with that I don't just mean the operating system, but also the idea behind it :).20 -
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
Da Fuck!?!
Yesterday I found some abnormal activity on my server, someone was trying to brute force my ssh as root since two days! Started raging and installed fail2ban (which automatically bans an IP if it fails to log X times and eventually sends me an email). Woke up this morning to find that a fucking Chinese guy/malware spent the whole night trying to brute Force me!
Fucking cunt! Don't you have any better to do!!
My key is a 32 characters long encrypted key, with the ban he can try 3 passwords /2 hours, good luck brute forcing it you bitch! 36
36 -
Dear outsourced developers. Don't send me your private SSH key by email. I don't need it, it allows me to access anything else you can access pretending I'm you, and it shows a misunderstanding of how SSH keys work. 🤦🏻♂️11
-
I can type the password for the SSH key to my servers while drunk.
Muggles can't type the fucking email address while sober.
WHAT THE ACTUAL FUCK?!!! Is it really that fucking hard?!!! Pieces of shit!!7 -
Full stack web dev has no idea what an ssh key is. He is telling me that he can't read the key file, it would be kind of me if I could send him a .txt file instead.
Fuck me man...4 -
I was working as a contractor for a client who just got enough funding to hire a full-time dev. I lovingly referred to him as "Mr. Koolaid" because he was obsessed with whatever the newest hotness was and cried constantly about how the 3-year-old code-base didn't use The Next Big Thing(tm). This was my first interaction with him:
Mr. Koolaid: I'd like access to the github repository. My username is xxxx.
Me: We currently aren't hosting the code on github. If you send me your public ssh key, I'll get you access to the private server.
Mr. Koolaid: I'd like to access the github repository.
Me: It's not on github; send me your public key and I'll get you access.
Mr. Koolaid: Can we skype real quick? You don't need my public key to grant me access to the github repo.
*Mr. Koolaid proceeds to forward me github's documentation on adding users to an organization and the documentation for adding users to a private repo. The email is written in a very passive-aggressive tone.*
ಠ_ಠ9 -
Worst WTF dev experience? The login process from hell to a well-fortified dev environment at a client's site.
I assume a noob admin found a list of security tips and just went like "all of the above!".
You boot a Linux VM, necessary to connect to their VPN. Why necessary? Because 1) their VPN is so restrictive it has no internet access 2) the VPN connection prevents *your local PC* from accessing the internet as well. Coworkers have been seen bringing in their private laptops just to be able to google stuff.
So you connect via Cisco AnyConnect proprietary bullshit. A standard VPN client won't work. Their system sends you a one-time key via SMS as your password.
Once on their VPN, you start a remote desktop session to their internal "hopping server", which is a Windows server. After logging in with your Windows user credentials, you start a Windows Remote Desktop session *on that hopping server* to *another* Windows server, where you login with yet another set of Windows user credentials. For all these logins you have 30 seconds, otherwise back to step 1.
On that server you open a browser to access their JIRA, GitLab, etc or SSH into the actual dev machines - which AGAIN need yet another set of credentials.
So in total: VM -> VPN + RDP inside VM -> RDP #2 -> Browser/SSH/... -> Final system to work on
Input lag of one to multiple seconds. It was fucking unusable.
Now, the servers were very disconnect-happy to prevent anything "fishy" going on. Sitting at my desk at my company, connected to my company's wifi, was apparently fishy enough to kick me out every 5 to 20 minutes. And that meant starting from step 1 inside the VM again. So, never forget to plugin your network cable.
There's a special place in hell for this admin. And if there isn't, I'll PERSONALLY make the devil create one. Even now that I'm not even working on this any more.8 -
*tries to SSH into my laptop to see how that third kernel compilation attempt went*
… From my Windows box.
Windows: aah nope.
"Oh God maybe the bloody HP thing overheated again"
*takes laptop from beneath the desk indent*
… Logs in perfectly. What the hell... Maybe it's SSH service went down?
$ systemctl status sshd
> active (running)
Well.. okay. Can I log in from my phone?
*fires up Termux*
*logs in just fine*
What the fuck... Literally just now I added the laptop's ECDSA key into the WSL known_hosts by trying to log into it, so it can't be blocked by that shitty firewall (come to think of it, did I disable that featureful piece of junk yet? A NAT router * takes care of that shit just fine Redmond certified mofos).. so what is it again.. yet another one of those fucking WanBLowS features?!!
condor@desktop $ nc -vz 192.168.10.30 22
Connection to 192.168.10.30 22 port [tcp/ssh] succeeded!
ARE YOU FUCKING FOR REAL?!
Fucking Heisen-feature-infested piece of garbage!!! Good for gaming and that's fucking it!
Edit: (*) this assumes that your internal network doesn't have any untrusted hosts. Public networks or home networks from regular users that don't audit their hosts all the time might very well need a firewall to be present on the host itself as well.16 -
Came across: https://krypt.co sounds interesting, because its like an additional 2fa for your ssh key, is locally encrypted, open source, well documented and transparent:
https://krypt.co/docs/security/...
Why is it not much talked about? sounds great so far, but maybe somebody can find the tick? or is using it himself? 30
30 -
Why nobody uses public/private key authentication for ssh and disable password auth?
Am I the only one around here doing this?14 -
One of our newly-joined junior sysadmin left a pre-production server SSH session open. Being the responsible senior (pun intended) to teach them the value of security of production (or near production, for that matter) systems, I typed in sudo rm --recursive --no-preserve-root --force / on the terminal session (I didn't hit the Enter / Return key) and left it there. The person took longer to return and the screen went to sleep. I went back to my desk and took a backup image of the machine just in case the unexpected happened.
On returning from wherever they had gone, the person hits enter / return to wake the system (they didn't even have a password-on-wake policy set up on the machine). The SSH session was stil there, the machine accepted the command and started working. This person didn't even look at the session and just navigated away elsewhere (probably to get back to work on the script they were working on).
Five minutes passes by, I get the first monitoring alert saying the server is not responding. I hoped that this person would be responsible enough to check the monitoring alerts since they had a SSH session on the machine.
Seven minutes : other dependent services on the machine start complaining that the instance is unreachable.
I assign the monitoring alert to the person of the day. They come running to me saying that they can't reach the instance but the instance is listed on the inventory list. I ask them to show me the specific terminal that ran the rm -rf command. They get the beautiful realization of the day. They freak the hell out to the point that they ask me, "Am I fired?". I reply, "You should probably ask your manager".
Lesson learnt the hard-way. I gave them a good understanding on what happened and explained the implications on what would have happened had this exact same scenario happened outside the office giving access to an outsider. I explained about why people in _our_ domain should care about security above all else.
There was a good 30+ minute downtime of the instance before I admitted that I had a backup and restored it (after the whole lecture). It wasn't critical since the environment was not user-facing and didn't have any critical data.
Since then we've been at this together - warning engineers when they leave their machines open and taking security lecture / sessions / workshops for new recruits (anyone who joins engineering).26 -
Sent another developer instructions for generating an SSH key pair and to send me the public key. He did so. There was a problem getting it to work. So, naturally, he emailed me the private key.1
-
It took forever to get SSH access to our office network computers from outside. Me and other coworkers were often told to "just use teamviewer", but we finally managed to get our way.
But bloody incompetents! There is a machine with SSH listening on port 22, user & root login enabled via password on the personal office computer.
"I CBA to setup a private key. It's useless anyways, who's ever gonna hack this computer? Don't be paranoid, a password is enough!"
A little more than 30 minutes later, I added the following to his .bashrc:
alias cat="eject -T && \cat"
alias cp="eject -T && \cp"
alias find="eject -T && \find"
alias grep="eject -T && \grep"
alias ls="eject -T && \ls"
alias mv="eject -T && \mv"
alias nano="eject -T && \nano"
alias rm="eject -T && \rm"
alias rsync="eject -T && \rsync"
alias ssh="eject -T && \ssh"
alias su="eject -T && \su"
alias sudo="eject -T && \sudo"
alias vboxmanage="eject -T && \vboxmanage"
alias vim="eject -T && \vim"
He's still trying to figure out what is happening.5 -
NUKE IT FROM ORBIT. It was when i was doing an assignment with my roommate, i was compiling something on my pi and ran netstat afterwards for no reason. I had an ssh-connection from china (logged in too). The pi was shutdown ASAP, i salvaged everything i needed from the sd and dd'ed raspbian on the disk again.
Turns out you were able to login via root (i thought i disabled it) with the password i set (root...). I learned from this, now external logins are only allowed via private key and i have fail2ban set up3 -
Back when I migrated my file server to a VM, I used robocopy to copy everything over (and caused quite a few fuckups before it'd behave halfway decent.. or so I thought). Now I tried to add my desktop's SSH key to the authorized_keys on said server but it wouldn't accept my key after that. After a bit of digging I've found that my entire home directory (where the file server hosts its mirror of my D: drive) had everything set to 777, and that's why the key isn't accepted. Great permission mode, isn't it? Much secure, very wow! Thank you so much robocopy!!!3
-
TL; DR: Bringing up quantum computing is going to be the next catchall for everything and I'm already fucking sick of it.
Actual convo i had:
"You should really secure your AWS instance."
"Isnt my SSH key alone a good enough barrier?"
"There are hundreds of thousands of incidents where people either get hacked or commit it to github."
"Well i wont"
"Just start using IP/CIDR based filtering, or i will take your instance down."
"But SSH keys are going to be useless in a couple years due to QUANTUM FUCKING COMPUTING, so why wouldnt IP spoofing get even better?"
"Listen motherfucker, i may actually kill you, because today i dont have time for this. The whole point of IP-based security is that you cant look on Shodan for machines with open SSH ports. You want to talk about quantum computing??!! Lets fucking roll motherfucker. I dont think it will be in the next thousand years that we will even come close to fault-tolerant quantum computing.
And even if it did, there have been vulnerabilities in SSH before. How often do you update your instance? I can see the uptime is 395 days, so probably not fucking often! I bet you "dont have anything important anyways" on there! No stored passwords, no stored keys, no nothing, right (she absolutely did)? If you actually think I'm going to back down on this when i sit in the same room as the dude with the root keys to our account, you can kindly take your keyboard and shove it up your ass.
Christ, I bet that the reason you like quantum computing so much is because then you'll be able to get your deepfakes of miley cyrus easier you perv."8 -
Macbook Pro - No ESC key?
Its not like its used much in vi or emacs anyway is it?
No esc key on a unix box? Seriously?
I know its got a 'soft' escape key - hows it going to know to switch to that if i run vi or emacs -nw in an ssh session?
Mac keyboards go from bad to worse - used to be a nightmare to find a | symbol.10 -
Me trying to generate a new ssh key after a long while
ssh keygen
ssh key-gen
*DuckDuckGo how to*
Oh!
ssh-keygen5 -
Oh finally I figured out how to use SSH pubkeys! It's simple:
1. Generate a public key on client
2. Somehow transfer it to server
3. Put it into user's authorized_ keys files
4. Now you can login as the user whp has your key in authorized_keys1 -
ssh your.server.ip, welcome message:
#Ooops! your files have been encrypted.
#Don't waste your time trying to decrypt them.
#Nobody can.
#We would gladly offer you a way of recovering all
#your files safely, but sadly we lost the decryption
#password.
#Hackers too are not perfect, have a nice day.
#PS. you can still send money to support us if you want at this
#web page: fuckyou.onion.
#Your personal key: m0r0nm0t3fukk3r
(I'll code this one day and install it on somebody machine, it's one of my top dreams)11 -
Note to my future self:
A 2048Bit SSH key is minimum,
4096Bit is good enough
8182Bit is too much
16364Bit... why do I even bother about this size5 -
Since we are using the same password on all our servers (both QA and Production environment) my team somehow decided that it would be easier to copy the private SSH key for to ALL servers and add the public key to the authorized.keys file.
This way we SSH without password and easily add it to new servers, it also means that anyone who gets into one server can get to all of them.
I wasn't a fan of the same password on all servers, but this private key copying is just going against basic security principles.
Do they want rogue connections? Because that's how you get them.1 -
Seriously? Microsoft does not support ed25519 SSH keys in neither Azure DevOps nor the actual Azure Virtual Machines? Like seriously? No there has to be a joke. There just ain't no way
It has been in OpenSSH since 2013.
2013.
We're in 2023, if you've forgotten.
10 years ago, OpenSSH implemented this standard.
Did you know what they tell you when you enter your valid Ed25519 SSH key into their system?
Did you know they tell you that "Your SSH key is invalid"?
WHAT DO YOU MEAN INVALID???!?! IT WORKS EVERYWHERE ELSE JUST FINE!!! YOU'RE THE ONE THAT HAS NO FUCKING BRAINS!!!
Composure.
I am calm, I am calm.
I have always. Been. CALM!
There is no one more calm than me....
I guess RSA it is then.
A second SSH key, just for Microsoft.5 -
Hey, looks like some employee of this hosting company failed to 750 his home directory and 640 the files...
I was SSHing around on our hosting account when I slipped into his home direcory where at least two(!) SSH public keys of his admin account for the server were readable!
Being an honest guy, I had to call them...
It's fixed now.2 -
Today’s DevOps public service announcement... don’t test your server provisioning scripts locally. Especially when this gem is in there:
rm -f ~/.ssh/id_rsa
echo ‘vault secret/ssh_key’ > ~/.ssh/id_rsa
Well, I no longer have my key, but the script works! I’m sitting with a very locked down server key6 -
Copy my private ssh key to multiple machines so I only have to configure one key in github, gitlab, bitbucket etc.3
-
OpenSSH 8.2 is out. This release removes support for the ssh-rsa key algorithm. The better alternatives include:
1. RSA SHA-2 signature algorithms rsa-sha2-256/512. These algorithms have the advantage of using the same key type as "ssh-rsa" but use the safe SHA-2 hash algorithms (now used by default if the client and server support them).
2. The ssh-ed25519 signature algorithm.
3. ECDSA algorithms: ecdsa-sha2-nistp256/384/521.
In this release, support for FIDO/U2F hardware tokens. Also noteworthy, a future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms.17 -
A typical bouba coder:
- thinks a kilobyte contains 1024 bytes
- thinks Object.assign clones an object
- codes in react.js, thinks he knows reactive programming
- “amd is better for games, intel is better for work”
- thinks that the main advantage of ssh is that you don’t need to enter your password manually
- watches porn in incognito mode
- “crapple”
- “uhm, is it immutable?”
- thinks “persistent” means saved to local storage
- thinks designer is an inferior job because “they only draw shapes”
- thinks good accessibility is when the tab key works
- “All non-mechanical keyboards are trash”
- “C is outdated and nobody uses it anymore”
- “Zuck quit uni and now he’s a billionaire, everybody should quit”
- thinks “pointer” is a shape of the cursor43 -
Have been using redis for my new system and wanted to try some gui, so I stumbled on "redis desktop manager", it supports ssh tunnels, privatekeys and more, great isn't it?
BUT IT SAVES YOUR FUCKING PLAINTEXT PASSWORD AND PATH TO YOUR PRIVATE KEY IN %USER%\.rdm\connections.json
WHAT THE FUCK, fucking ask that password during connection, don't fucking save it in plaintext and give an attacker literally the path to my key, wanted to PR it, but fuck c++, probably thats why he doesnt have it, because hes just using some library, so he doesn't have to fuck with the actual implementation of it.2 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.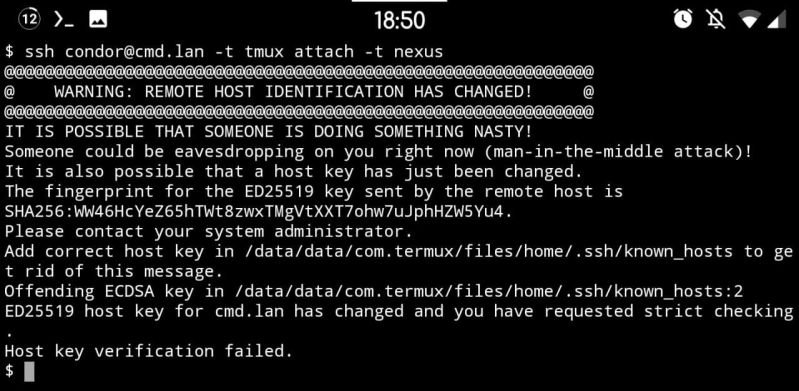 19
19 -
TL;DR my first vps got hacked, the attacker flooded my server log when I successfully discovered and removed him so I couldn't use my server anymore because the log was taking up all the space on the server.
The first Linux VPN I ever had (when I was a noob and had just started with vServers and Linux in general, obviously) got hacked within 2 moths since I got it.
As I didn't knew much about securing a Linux server, I made all these "rookie" mistakes: having ssh on port 22, allowing root access via ssh, no key auth...
So, the server got hacked without me even noticing. Some time later, I received a mail from my hoster who said "hello, someone (probably you) is running portscans from your server" of which I had no idea... So I looked in the logs, and BAM, "successful root login" from an IP address which wasn't me.
After I found out the server got hacked, I reinstalled the whole server, changed the port and activated key auth and installed fail2ban.
Some days later, when I finally configured everything the way I wanted, I observed I couldn't do anything with that server anymore. Found out there was absolutely no space on the server. Made a scan to find files to delete and found a logfile. The ssh logfile. I took up a freaking 95 GB of space (of a total of 100gb on the server). Turned out the guy who broke into my server got upset I discovered him and bruteforced the shit out of my server flooding the logs with failed login attempts...
I guess I learnt how to properly secure a server from this attack 💪3 -
I'm forced by my job to use this fucking unusable piece of horse shit also know as a Windows operating system.
And it's not only that I have experienced every fucking corner case bug that is possible to occur in our universe.
Not only that that for last 2 years I seen more blue screen than blue sky.
Not only that forced updates fucked my schedules so many times that now I'm really *afraid* to turn off my computer off because I have zero guarantee that I will be able to restart it in a reasonable amount of time.
No, neither of those broke me.
The thing that kills me everyday is, piece by piece ...
WHY THE FUCK THERE IS NO SINGLE, USEABLE, SANE TERMINAL EMULATOR ON WINDOWS
I JUST WANT TO TYPE SOME COMMANDS, COPY/PASTE TEXT AND SCROLL
IS IT TO MUCH ?????
FUCK CMD
FUCK POWERSHELL
FUCK WSL
FUCK ALL THOSE WANKY THIRD-PARTY EMULATORS
FUCK EVERY-COMMAND-LINE-REALATED THING ON WINDOWS
FUCKING USLESS SHIT
CANT EVEN DO SOME SSH COPY/PASTE SHIT
WITHOUT SOME WEIRD CHARACTERS POPING OUT EVERYWHERE.
AND FUCK THAT EVERY ONE OF THOSE MUST HAVE TOTTALY DIFFERENT SET OF KEY SHORTCUTS
AND THAT FUCKING BELL
WHY WOULD YOU EVEN PUT A FUCKING BELL SOUND AS DEFAULT SETTING ??
GO TO HELL MICROSOFT
I WANT MY LINUX BACK6 -
When I think "the fundamental problem", the closest thing that comes to my mind is "unsolvable problem". P =/!= NP is a fundamental problem, the theory of everything is a fundamental problem.
But we actually solved at least one such problem – the fundamental problem of cryptography.
The problem was "how to establish a secure connection over a non-secure channel?" Like you can't exchange the key, it'll be exposed by definition.
We solved it with a simple yet brilliant solution of asymmetrical cypher, that thing with public and private keys.
It's fascinating to think that people died in WW2 over this, there were special operations to deliver fresh deciphering keys securely and now SSH and HTTPS are no-brainers that literally everyone use.10 -
👨🏽💻 Switching between multiple Git accounts: work, personal, freelance?
Ever pushed a commit with Company A's email to Company B's repo? 😩🥶
Been there. Done that. Regretted it immediately.
I just dropped a step-by-step guide on how to set up Git so it automatically picks the right name, email, and SSH key based on your project folder.
No more manual config switching. 💡
✅ No more identity mix-ups
✅ No more commit shame
✅ Just clean, context-aware Git workflows 🙌
🔧 What’s inside:
- Multiple SSH key setup
- Smart .gitconfig using includeIf
- Folder structure that keeps you sane
- Bonus tips for HTTPS + personal token users
If you’ve ever yelled at Git (or yourself), this one’s for you.
👏 Drop a clap if it helps and follow for more dev-friendly tips!
👇 Read it here:
https://rhymezxcode.medium.com/how-... -
Am I the only developer in existence who's ever dealt with Git on Windows? What a colossal train wreck.
1. Authentication. Since there is no ssh key/git url support on Windows, you have to retype your git credentials Every Stinking Time you push. I thought Git Credential Manager was supposed to save your credentials? And this was impossible over SSH (see below). The previous developer had used an http git URL with his username and password baked in for authentication. I thought that was a horrific idea so I eventually figured out how to use a Bitbucket App password.
2. Permissions errors
In order to commit and push updates, I have to run Git for Windows as Administrator.
3. No SSH for easy git access
Here's where I confess that this is a Windows Server machine running as some form of production. Please don't slaughter me! I am not the server admin.
So, I convinced the server guy to find and install some sort of ssh service for Windows just for the off times we have to make a hot fix in production. (Don't ask, but more common than it should be.)
Sadly, this ssh access is totally useless as the git colors are all messed up, the line wrap length and window size are just weird (seems about 60 characters wide by 25 lines tall) and worse of all I can't commit/push in git via ssh because Permissions. Extremely aggravating.
4. Git on Windows hangs open and locks the index file
Finally, we manage to have Git for Windows hang quite frequently and lock the git index file, meaning that we can't do anything in git (commit, push, pull) without manually quitting these processes from task manager, then browsing to the directory and deleting the .git/index.lock file.
Putting this all together, here's the process for a pull on this production server:
Launch a VNC session to the server. Close multiple popups from different services. Ask Windows to please not "restart to install updates". Launch git for Windows. Run a git pull. If the commits to be pulled involve deleting files, the pull will fail with a permissions error. Realize you forgot to launch as Administrator. Depending on how many files were deleted in the last update, you may need to quit the application and force close the process rather than answer "n" for every "would you like to try again?" file. Relaunch Git as Administrator. Run Git pull. Finally everything works.
At this point, I'd be grateful for any tips, appreciate any sympathy, and understand any hatred. Windows Server is bad. Git on Windows is bad.10 -
techie 1 : hey, can you give me access to X?
techie 2 : the credentials should be in the password manager repository
t1 : oh, but I don't have access to the password manager
t2 : I see your key A1B2C3D4 listed in the recipients of the file
t1 : but I lost that key :(
t2 : okay, give me your new key then.
t1 : I have my personal key uploaded to my server
t1 : can you try fetching it?
t1 : it should work with web key directory ( WKD )
t2 : okay
t2 : no record according to https://keyserver.ubuntu.com
t1 : the keyserver is personal-domain.com
t1 : try this `gpg --no-default-keyring --keyring /tmp/gpg-$$ --auto-key-locate clear,wkd --locate-keys username@personal-domain.com`
t2 : that didn't work. apparently some problem with my dirmgr `Looking for drmgr ...` and it quit
t1 : do you have `dirmngr` installed?
t2 : I have it installed `dirmngr is already the newest version (2.2.27-2)`
t2 : `gpg: waiting for the dirmngr to come up ... (5)` . this is the problem. I guess
t1 : maybe your gpg agent is stuck between states.
t1 : I don't recall the command to restart the GPG agent, but restarting the agent should probably fix it.
t1 : `gpg-connect-agent reloadagent /bye`
source : https://superuser.com/a/1183544
t1 : *uploads ASCII-armored key file*
t1 : but please don't use this permanently; this is a temporary key
t2 : ok
t2 : *uploads signed password file*
t1 : thanks
t2 : cool
*5 minutes later*
t1 : hey, I have forgotten the password to the key I sent you :(
t2 : okay
...
t2 : fall back to SSH public key encryption?
t1 : is that even possible?
t2 : Stack Overflow says its possible
t1 : * does a web search too *
t1 : source?
t2 : https://superuser.com/questions/...
t2 : lets try it out
t1 : okay
t2 : is this your key? *sends link to gitlab.com/username.keys*
t1 : yes, please use the ED25519 key.
t1 : the second one is my old 4096-bit RSA key...
t1 : which I lost
...
t1 : wait, you can't use the ED25519 key
t2 : why not?
t1 : apparently, ED25519 key is not supported
t1 : I was trying out the steps from the answer and I hit this error :
`do_convert_to_pkcs8: unsupported key type ED25519`
t2 : :facepalm: now what
t1 : :shrug:
...
t1 : *uploads ASCII-armored key file*
t1 : I'm sure of the password for this key
t1 : I use it everyday
t2 : *uploads signed password file*
*1 minute later*
t1 : finally... I have decrypted the file and gotten the password.
t1 : now attempting to login
t1 : I'm in!
...
t2 : I think this should be in an XKCD joke
t2 : Two tech guys sharing password.
t1 : I know a better place for it - devRant.com
t1 : if you haven't been there before; don't go there now.
t1 : go on a Friday evening; by the time you get out of it, it'll be Monday.
t1 : and you'll thank me for a _weekend well spent_
t2 : hehe.. okay.8 -
Warning long rambling story cause sleep deprivation
I never really bothered with ssh outside of using putty to remote into my servers and rpi's from my desktop to run updates, install something, or whatever else.
But today I was on a call with my cousin bored cause she was just rambling, so I opened vscode to clean my install of unnecessary extensions I installed and haven't used more than once or twice.
I saw Remote - SSH and as I was bored listening to a teenager complain about high school just like I used to (lol) and responding when she asked me something. I scrolled through the page, then the documentation just casually skimming the text
I setup an ssh key on an rpi I threw manjaro arm following the instructions on their tips and tricks page
I then moved the key to my desktop using winscp (cause lazy)
leading to having a minor hicup of rsa not being an accepted keytype (thanks 'your favorite search engine' for the help)
Finally, I was able to connect using the private key
at this point my cousin went to bed cause she has school tomorrow. But I was still doing stuff with ssh, I created a new ssh connection in VSCode, but had to go to the documentation to figure out how to make it use my fancy new key file, not hard took 30 seconds of looking to get it working.
Now that I was in, I moved to my development folder, created a folder for PiHole, created a compose yml, created a pihole-data folder.
I opened the yml and pasted in a compose from dockerhub.
at this point I thought 'i can't just run this from terminal can I'. and Obviously it worked cause there's literally no reason it wouldn't I'm just stupid to think it might not.
So I created folders and files on a remote system, launched a docker container, checked for package updates after on a linux machine. All from VS-Code on a windows machine.
I know this is simple for some people, i know some people are like 'where's the interesting part'. but ehhh I thought it was cool to get it setup, I now really regret not getting into ssh sooner, and I'm definitely going to uninstall vscode on all my smaller graphical VM's in favor of doing this. and this will definitely help with my headless vm's.
I also will have to thank my cousin, might not have done this if I wasn't stuck at my computer on messenger call with her lol
I'm gonna go to bed now, But I feel accomplished for the first time in a while even if it's for something so simple as setting up anssh key for the first time3 -
Sooooo.....
I just spend roughly 5 hours trying to get a Laravel Homestead up and running. Constantly jumping from one error to the other, getting nowhere.
Turns out that,
...
...
I NEVER FUCKING GENERATED A BLOODY SSH KEY
ARE YOU FUCKING KIDDING ME
AN ENTIRE DAY WASTED
JESUS CHRIST
I swear, I'm way too junior for like 95% of this shit....5 -
How do you define a seniority in a corporate is beyond me.
This guy is supposed to be Tier3, literally "advanced technical support". Taking care of network boxes, which are more or less linux servers. The most knowledgable person on the topic, when Tier1 screws something and it's not BAU/Tier2 can't fix it.
In the past hour he:
- attempted to 'cd' to a file and wondered why he got an error
- has no idea how to spell 'md5sum'
- syntax for 'cp' command had to be spelled out to him letter by letter
- has only vague idea how SSH key setup works (can do it only if sombody prepares him the commands)
- was confused how to 'grep' a string from a logfile
This is not something new and fancy he had no time to learn yet. These things are the same past 20-30 years. I used to feel sorry for US guys getting fired due to their work being outsourced to us but that is no longer the case. Our average IT college drop-out could handle maintenance better than some of these people.9 -
I'm currently planning to set myselv up with some vps/dedicated server's for a project. What i plan to do to secure these servers is.
*Use centos 7
* Setup Wireguard and join all of the servers +1 client (my pc) to that network
*Disable SSH Access from outside that VPN
*Only allow RSA Key login to the Servers
*Install Cockpit for monitoring
*Intall docker/kubernetes for the applications i plan to run
What do you guys think of that as a baseline? Im not sure if my lower powered VPS (VPS M SSD from Contabo) will work as Kubernetes Nodes, does anyone have experience with that?
In general these Servers will be used for my projects and other fooling around.
If you guys have other suggestions for Securing/monitoring or other software i could put on to have more control without eating up to much of the Servers power, let me know :D12 -
The coolest project I ever worked on wasn't programming per second, though it involved a bit of scripting. The company I worked for had an FTP over TLS backup solution and it was put together with glue and paperclips by a guy that hadn't the slightest idea what he was doing. In order to conform with the insurance, data had to be encrypted. I setup a raid-ed server with full disk encryption on the raid volume that fetched the key over the network at boot from another secure server. I wrote a series of scripts for provisioning users and so on. The backup connections was sftp using a ssh tunnel, the users were chrooted to their own home directories, and were unable to open shells. The system was 100x more robust and secure than the original. I set it up on short notice and received absolutely no recognition for saving the company's ass, but it was definitely a fun project.1
-
!rant
I just realised my VPS ssh private key was in my servers web root for the last 4 months. Luckily nobody found it (hopefully).2 -
Aaaand I did it again T_T
Installed knockd for some reason it wasn't working well, couldn't unlock the port and guess what, internet disconnected for five minutes ==> My SSH session closed and I am locked out of my VPS :')
What is even worse Scaleway doesn't have a root user password when creating the server it uses a pre-entered ssh key that I put in my account, so I was pretty much locked out.
But I was able to remove it, they have custom scripts for booting so I was able to fireup a shell session during boot and removed knockd
Either I fail at using Linux or I really need to work on my self lol2 -
You know what fuck github , anyone remember when git cli was easy and straight forward to use
Now i have conflicting master branches because the remote is main and git automatically defaults to master.
Git still asks for a password while github can't wait to inform me how I have to go through the very long process of setting up an auth_token.
Apparently https remote origins for some reason don't work anymore, why because apparently i need to change them into ssh, good luck with the public key errors
This sucks , fuck github and fuck politics9 -
In today's episode of "how i got almost to the point of insanity for hours and the sudden realization and relief"
When you have ssh error saying your private key is an invalid format in your CI, you probably just missed an EOL.
MCP says EOL.
Fucking EOL
That is the realization i made after half a day wasting on debugging this.4 -
One day I helped another teacher with setting up his backend with the currently running Nginx reverse-proxy, peace of cake right?
Then I found out the only person with ssh access was not available, OK then just reset the root password and we're ready to go.
After going through that we vim'd into authorized_keys with the web cli, added his pub key and tried to ssh, no luck. While verifying the key we found out that the web cli had not parsed the key properly and basically fucked up the file entirely.
After some back and forth and trying everything we became grumpy, different browsers didn't help either and even caps lock was inverted for some reason. Eventually I executed plan B and vim'd into the ssh daemon's settings to enable root login and activate password authentication. After all that we could finally use ssh to setup the server.
What an adventure that was 😅3 -
fuck.. FUCK FUCK FUCK!!!
I'mma fakin EXPLODE!
It was supposed to be a week, maybe two weeks long gig MAX. Now I'm on my 3rd (or 4th) week and still got plenty on my plate. I'm freaking STRESSED. Yelling at people for no reason, just because they interrupt my train of thought, raise a hand, walk by, breathe, stay quiet or simply are.
FUCK!
Pressure from all the fronts, and no time to rest. Sleeping 3-5 hours, falling asleep with this nonsense and breaking the day with it too.
And now I'm fucking FINALLY CLOSE, I can see the light at the end of the tunne<<<<<TTTOOOOOOOOOOOOOTTTTT>>>>>>>
All that was left was to finish up configuring a firewall and set up alerting. I got storage sorted out, customized a CSI provider to make it work across the cluster, raised, idk, a gazillion issues in GH in various repositories I depend on, practically debugged their issues and reported them.
Today I'm on firewall. Liason with the client is pressured by the client bcz I'm already overdue. He propagates that pressure on to me. I have work. I have family, I have this side gig. I have people nagging me to rest. I have other commitments (you know.. eating (I practically finish my meal in under 3 minutes; incl. the 2min in the µ-wave), shitting (I plan it ahead so I could google issues on my phone while there), etc.)
A fucking firewall was left... I configured it as it should be, and... the cluster stopped...clustering. inter-node comms stopped. `lsof` shows that for some reason nodes are accessing LAN IPs through their WAN NIC (go figure!!!) -- that's why they don't work!!
Sooo.. my colleagues suggest me to make it faster/quicker and more secure -- disable public IPs and use a private LB. I spent this whole day trying to implement it. I set up bastion hosts, managed to hack private SSH key into them upon setup, FINALLY managed to make ssh work and the user_data script to trigger, only to find out that...
~]# ping 1.1.1.1
ping: connect: Network is unreachable
~]#
... there's no nat.
THERE"S NO FUCKING NAT!!!
HOW CAN THERE BE NO NAT!?!?!????? MY HOME LAPTOP HAS A NAT, MY PHONE HAS A NAT, EVEN MY CAT HAS A MOTHER HUGGING NAT, AND THIS FUCKING INFRA HAS NO FUCKING NAT???????????????????????
ALready under loads of pressure, and the whole day is wasted. And now I'll be spending time to fucking UNDO everything I did today. Not try something new. But UNDO. And hour or more for just that...
I don't usually drink, but recently that bottom shelf bottle of Captain Morgan that smells and tastes like a bottle of medical spirit starts to feel very tempting.
Soo.. how's your dayrant overdue tired no nat hcloud why there's no nat???? fuck frustrated waiting for concrete to settle angry hetzner need an outlet2 -
My phone got stuck in funky restart boot loop yesterday. The first 2 restarts was odd but after 3 cycles, I started panicking. Went on my PC, googled for all kinds of button combinations of power button, volume button, back button, and home button to get into fastboot, recovery and safe mode to see if I can clear stuff or at least get backup of my stuff. I also tried taking the battery out. Nothing works, except when I factory reset.
Everything was new again and as it booted up, I have to remember to change my authentication keys in LastPass, my private ssh key in Krypt. But fortunately, Google remembered all my apps and suggested if I wanted to install them again since it recognized my phone was an old phone. Thanks for tracking me Google. And now since its a reset, everything is clean, no cache, cookie, and some of my music files are all gone. Well at least its fast like before.1 -
Why is my the fingerprint for my public ssh-key seen not as a sha256-fingerprint?
Left: Windows
Right: Raspberry 3
3 -
Being asked if you have access to the archaic raid array machine in the corner of the data-centre.
Step 1. Log-in in front of the person asking
Step 2. Deleting ssh key from the .ssh/authorized_keys
Step 3. Replying "Nope I know nothing of it" -
Ok, I need to vent a little bit about myself. Just got back from my 2 weeks vacations. Met with everyone, caught up on everything that has happened, booted my lap top and tried to ssh into the servers to see log files if anything out of the ordinary has happened.
Well, I was having "Permission denied (publickey)." . Well fuck. Tried on other servers and same thing.
I got panicked, thinking how the fuck did we get hacked? The ssh key is only on my laptop, and an encrypted backup exists only in Bitwarden account. If yes, why are the systems intact and working well? Kept scratching my head for hours. Well, I was trying to log in with user "root" instead of "admin". I always mistake these two names. Rusty brain ._.1 -
Guys, i'm so sad and laughing too cause i losed my GitHub account. I tried to recover but... i don't have the old OS where i had the SSH key so i can not authenticate myself as the owner, don't have the 2FA on my new mobile because i'm dumb and... i don't had the recovery codes... please, kill me...
The good news, i can make another account with the same e-mail.2 -
I've been wondering about renting a new VPS to get all my websites sorted out again. I am tired of shared hosting and I am able to manage it as I've been in the past.
With so many great people here, I was trying to put together some of the best practices and resources on how to handle the setup and configuration of a new machine, and I hope this post may help someone while trying to gather the best know-how in the comments. Don't be scared by the lengthy post, please.
The following tips are mainly from @Condor, @Noob, @Linuxxx and some other were gathered in the webz. Thanks for @Linux for recommending me Vultr VPS. I would appreciate further feedback from the community on how to improve this and/or change anything that may seem incorrect or should be done in better way.
1. Clean install CentOS 7 or Ubuntu (I am used to both, do you recommend more? Why?)
2. Install existing updates
3. Disable root login
4. Disable password for ssh
5. RSA key login with strong passwords/passphrases
6. Set correct locale and correct timezone (if different from default)
7. Close all ports
8. Disable and delete unneeded services
9. Install CSF
10. Install knockd (is it worth it at all? Isn't it security through obscurity?)
11. Install Fail2Ban (worth to install side by side with CSF? If not, why?)
12. Install ufw firewall (or keep with CSF/Fail2Ban? Why?)
13. Install rkhunter
14. Install anti-rootkit software (side by side with rkhunter?) (SELinux or AppArmor? Why?)
15. Enable Nginx/CSF rate limiting against SYN attacks
16. For a server to be public, is an IDS / IPS recommended? If so, which and why?
17. Log Injection Attacks in Application Layer - I should keep an eye on them. Is there any tool to help scanning?
If I want to have a server that serves multiple websites, would you add/change anything to the following?
18. Install Docker and manage separate instances with a Dockerfile powered base image with the following? Or should I keep all the servers in one main installation?
19. Install Nginx
20. Install PHP-FPM
21. Install PHP7
22. Install Memcached
23. Install MariaDB
24. Install phpMyAdmin (On specific port? Any recommendations here?)
I am sorry if this is somewhat lengthy, but I hope it may get better and be a good starting guide for a new server setup (eventually become a repo). Feel free to contribute in the comments.24 -
I had the strangest occurrence today.
Client lost priv key to some ec2 instance.
Sure, I detached the volume, and attached to another instance to go and add a new key to ./ssh/authorized_keys.
Sure thing, I mounted the partition successfully, and then shit happened.
Say I mounted to /mnt/old
It would mount without issue but...
ls -la .
(With /mnt/old as current directory) Would show nothing, as if the directory was empty. df showed it wasn't the case.5 -
I've created instructions for myself the next time I encounter cpanel.
rallen@rallen ~ $ cheat cpanel
#SSH'ing into the fucking cpanel
#Figure out combination of 5 usernames and passwords given by client to log in.
#Pray that WHM isn't involved.
#Ignore several ssl warnings and cancel several .htaccess password prompts.
#Call in to enable that shit.
#Wait no less than 15 minutes on hold.
#SSH enabled.
#Create public private key pair.
#Notice the ppk conversion for windows 'devs'. Sigh.
#Copy key pair to ~/.ssh/
#chmod that shit to 600.
#Note for the user name it's not anything the clients given you or what you've named the key. Look in the cpanel for the /home/<user> directory.
ssh -i ~/.ssh/key <user>@<dedicatedip> -
When I found out that the server I use weirdly implements SSH login.
For some very odd reason (probably a historical one,) you have to access the web-app console and press a button TO GRANT SSH ACCESS TO THE F*<KING IP ADDRESS FROM WHICH I PRESSED THE BUTTON. The server blocks the wrong IP addresses outright. And only one active allowed IP at a time. This totally obliterates my plan to perform CD on this server. Why can't I just register public keys?
Then I learned several months later that they introduced a new server plan that *does* support the public-key registration. :facepalm:
I'm divided on whether to change my plan in exchange for a rather significant increase in the monthly cost.3 -
The only way I can edit Puppet config files is by git. And the only way I can git pull/push/commit/etc is generating a ssh key with a private key and give my public key to my supervisor to the git server (wherever that may be).
Because I'm on Windows 10 and screwed up my installers, I completely forgot to backup my ssh keys before resetting it. FML2 -
Accidentally bridged the only interface with a manual IPv4 address on a production box. With only public key access, my only choice was to calculate and ssh via its IPv6 link local address address.
Thanks god it worked. -
Can't believe I'm about to say this, but:
Systemd-container is a rather cool SysD extension.
It allows me (Root on most servers) to switch to a customer account in a completely new session, setting all the .profile and .bashrc stuff up, so I can do stuff like control their rootless docker, and no longer have to add my SSH key to their authorized_keys file then re-login under their user.
Nice.1 -
`load pubkey "/Users/karunamon/.ssh/id_rsa": invalid format`
The fuck? I've been using this keyfile for ages. And that's the private key, not the public key.
Maybe I'll try converting it to a different format.
(20 minutes of ssh-keygen command attempts)
Same error. I don't freaking get it. It works. I mean, I know my public key is..
(public key is actually completely mangled with newlines everywhere)
..yknow what, my fault, but you could have at least given me the public key filename, ya jerk.1 -
Setup SSH keys from your Dev machine to every development environment then configure a putty profile to use that key with your login.
-
urgghhh this old laptop doesn't have a working shift key
also it's sticky. eeeeee
thankfully there's 2 shift keys but talk about awkward
just gotta dump ssh on it and find out if it can run rust or not. God this thing is slow. was top of the line 10 years ago when this business guy bought the best laptop he could find, now somehow barely runs arch. crazy5 -
Thus happened recently.
I installed vestas on our organisation's lab server. I was trying to add the user's key to gitlab.
But vestas doesn't support ssh keys by default, and i thought to go by https way
I don't remember my password, so instead of opening saved logins I was going to install gitlab on our organisation's sub domain.
Later I created custom keys inside the user's directory -_- -
The sad moment when you realise that you're locked out of your VPS without your pc, because you forgot to add your phone's ssh key to the list and password login is disabled :(
Hope everything keeps working until I get back 😱2 -
We're supporting hardware for a new client now. A guy on my team has been working directly with the client to set up access for us all. He sent us all an email yesterday, asking us to update a ticket with our, "domain name and passphrase."
He meant user id and ssh public key, but he doesn't know enough about Linux (which he supports for a living) to know what it was called. -
So yesterday I got to configure a WordPress install on WPEngine. I was setting up Git and added my SSH key to the WPEngine git config for this account. And this weirdo WPEngine system fetched my same key along with same key name from another account.
Due to this I had to change my SSH key altogether and add it again.
Reason, my SSH for client X was stored with label MY-NAME-X
But the same key label should not be visible under other WPEngine accounts. And it was there - thus exposing my client X name to client Y account.
This is so annoying2 -
when you can't generate ssh key in powershell, because the -N option (Passphrase) requires an argument.
the same works in cmd.. without error....4 -
-Recently started a new job so I’m new to the infrastructure-
Spent the vast majority of the day trying to SSH into one of my company servers to sort some random bug out on the website & the connection kept being rejected despite the day before it working when passing the .pem key into the SSH along with the ip & my username, nothing new there.
Anyway, everyone’s mad busy so I don’t wanna bother anyone to ask why, so I check confluence, no documentation for SSHING into our scheduler or the code the server I need to access. Never-mind.
Spend another couple hours trying debug it on my own, no luck. Never-mind.
Finally seize my opportunity and ask for help; ‘Oh the server IP changes daily so you need to run a task through our scheduler that you need to SSH into to return the list of IPS and that dynamically changes so that’s how you get the IP’
Oh ok. Why is there no documentation for that again? I mean. Thats generally some pretty important information you’d pass onto your starters.
At least I can say I won’t be making that same mistake again.5 -
Fuck you Git bash
I did fucking add the ssh key to my ssh agent
I did add it to my GitHub account
you are dumb because for months until today you worked fine, now you look for ssh keys in a bullshit folder2 -
On Linux I want to scp a file from Machine B to my machine A.
Assuming B allows all connections is any key/cert file exchange needed?
I recall whenever I SSH to a new machine I need to accept a key on the first connect.
Guess general question is what is the connection process between 2 Linux machines for sftp purposes?9 -
Any one ever heard of the Solo? It's basically an open source FIDO compliant U2FA usb (with planned support for PGP/SSH key storage!).
The guys who made it are now miniaturizing it into the "Somu" (Secure Tomu).
Please support it! It's a great project and a great (and cheap) addition to basic system security.
https://crowdsupply.com/solokeys/...21 -
Despite already having a few years of professional experience dealing with Linux servers, I still, to this day, confuse, which environment file gets sourced and when...
There's /etc/profile, /etc/bashrc, ~/.bash_profile, ~/.profile, ~/.bashrc
I think it's... Bashrc for interactive shells, profile for login shells.
But then I have examples like "ssh user@server 'echo $var'" that... Don't source any of the files!
You can enable user environment files for SSH that get sourced whenever a user logs on through SSH (~/.ssh/environment / environment specified for a key in ~/.ssh/authorized_keys)
Is there some sort of master environment file that gets sourced *every* time, no matter what kind of shell starts?1 -
settting up an ssh connection to vm is taking so much time. I have created a ssh key using ssh keygen and added the host ip address to my config file. Deleted the knownhosts file from .ssh folder. Still getting connection timed out. Need help asap9




