Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 Root772335yAre you an idiot?
Root772335yAre you an idiot?
Using back-doored encryption is not better. It’s the exact opposite of better. I don’t care if it’s for convenience, it. is. not. secure.
Any flaw in security can and will be exploited. If not by malicious actors, by companies looking to exploit your data, and by the government.
Security should be your first concern; only after that should you work on making a product usable and friendly. Anything else is incredibly naïve. -
@Root So all your data on Google Should have been hacked by now because they don't use such naive encryption. This is not a security flaw apple just never Bothered to think about a better encryption. So much user's data was completely lost from this world because they forgot their password. Why would anyone use such a mechanism?
-
 Root772335y@theabbie All of the data google has, even the encrypted “secure” data, they share freely with the US government. Five eyes, prism, and all that. Same goes for Facebook, Amazon, Microsoft, Intel, etc.
Root772335y@theabbie All of the data google has, even the encrypted “secure” data, they share freely with the US government. Five eyes, prism, and all that. Same goes for Facebook, Amazon, Microsoft, Intel, etc.
I do not have any data on google. At least I do my damndest to not feed them any more. Same for the rest. -
@Root Yeah, Fuck Google, All the websites on internet dumb as they allow you to reset password. Stop hating Google because of half knowledge, This doesn't make you cool.
-
 Root772335y@theabbie You really need to stop. Almost everything you have said is wrong. Even if you don’t know it, you’re embarrassing yourself.
Root772335y@theabbie You really need to stop. Almost everything you have said is wrong. Even if you don’t know it, you’re embarrassing yourself. -
@iiii Consider this jumbling function I Made
function jumble(text,n) {
var result="";
go(text,n);
function go(text,n) {
if (text.length!=1) {
var p = text.split("")[((n-1)%(text.length))];
result+=p;
go(text.slice(((n-1)%(text.length))+1,text.length)+text.slice(0,((n-1)%(text.length))),n);
}
else {result+=text;}
}
return result;
}
The output of
jumble("This is some data And It is Not even very long, Try this", n)
is " tt r ss snnhsANersa y o eTiIvidey vTdoe mlntt iao,gih "
Please find n
and this data is very small compared to real world data, and n is just an integer. You have very wrong sense of encryption. -
@Root Why do you criticize things with half knowledge about that? We are not living in a perfect world, people do forget password. If your key gets lost, you don't abandon your house. It's a useless encryption, admit that.
-
@iiii Yeah, I read it, in my function, decryption becomes tougher if data size increses. Your statement was wrong.
-
 Root772335y@theabbie What is the point of encryption? To secure the data. Having another key that the user does not control is the antithesis of secure because the user no longer controls access to their data.
Root772335y@theabbie What is the point of encryption? To secure the data. Having another key that the user does not control is the antithesis of secure because the user no longer controls access to their data.
When are encryption algorithms deprecated? When people find flaws that allow them to make better guesses at keys, or because there are a high number of collisions, and therefore multiple keys the user does not intend.
Having multiple keys the user controls is fine. It lowers the strength of the encryption, but it keeps everything squarely in the user’s hands — and only the user’s hands.
As soon as someone else has access, or an easier time gaining access, it is no longer secure. -
@iiii Then prove it. here n is just a one digit integer, Suppose passcode is ABCD, I could do this
var x = data;
x = jumble(x,A);
x = jumble(x,B);;
x = jumble(x,C);
x = jumble(x,D);
How will you find original data without Passcode, I have an unjumble function too, It can be decrypted but not without passcode.
To use Brute force you have 10000 combinations, That's not feasible. -
 NoMad134245y@theabbie you need to read up on encryption methos. Like, a lot.
NoMad134245y@theabbie you need to read up on encryption methos. Like, a lot.
I do agree that over-authentication makes just about anything useless, but security has impact on usability too. Which is why proper level of security is hard to reach.
But as for Apple, all your data is backed up, so what difference does it make if you lose your lock? You just factory reset and start again. -
@Root The goal of encryption is that no one other than user and the service should be able to access it. And,. multiple keys won't help, The goal here is to get data even if everything is lost. There are better ways to protect data from hackers, For example, Using another encryption over user data. What If you have a brain surgery and lose your password. Your data is gone forever, Just because of a naive encryption.
-
@NoMad That means the Backed up data is unencrypted somewhere, or, if even encrypted, is not with the user's passcode, as per @Root it should be completely controlled by user. Isn't that a backdoor. Why can't it be exploited. Please understand that Either it can be completely secure or usable. not both. Se need something in between them.
-
 NoMad134245y@theabbie the passcode to your device and your cloud account are different... You know that, right?
NoMad134245y@theabbie the passcode to your device and your cloud account are different... You know that, right? -
 Root772335y@theabbie Password manager. 🙄
Root772335y@theabbie Password manager. 🙄
Security through obscurity is not security at all. 🙄
Secure security is not naïve security. Intentionally weakened security is. 🙄
For multiple keys: A single-use password reset code, written down on physical paper, a la TutaNota. This is a backdoored encryption algo used for good rather than evil. -
 C0D4644185yYour one controversial headache 🤦♂️
C0D4644185yYour one controversial headache 🤦♂️
Serious question, how new are you to the tech field? -
So you are saying that if people are used to lose their house/car keys, it is better to make lockers that other people can open without it?
Or yet saying the key guy next to your house have a copy of everyone keys, so he could open your door if you lose them?
Just because you can't remember where did you left them, everyone needs to be have their security compromised? -
@NoMad The point is forgetting password, If everyone Remembered password, there wouldn't be any problem, even if it is in device, it can be forgotten
-
@iiii I can do it with 4 digits too, one after the other, Then there are 9^4 combinations
-
 NoMad134245y
NoMad134245y -
Another points:
Did you know big CEOs etc prefer to have iPhones just because of the extra security Android can't provide?
Or yet, do you think one of the biggest companies in the world is naive just because you don't agree with them? -
@Root Password managers mean transferring the burden to them. Even they use such encryption. We can assume that we won't lose Password for that manager but That would be too much trust on them. I am talking about a situation where you lose everything, the only thing that remains is your identity. That's worst case scenario but that's possible.
-
@C0D4 Not much experienced but atleast more knowledged about my arguments. Apple has been fooling prople. It's not useful.
-
@theabbie what is this naive security you are talking about? I got a little lost here...
-
 C0D4644185y@theabbie a password reset is not the same as sending you your password.
C0D4644185y@theabbie a password reset is not the same as sending you your password.
It's a change of password, meaning the service still has no reason to know what it is and store the damn thing in a 1 way hash.
Encryption is 2 way, hashing is 1 way.
There's a difference.
Except for telcos in Australia that literally SMS you your password in plain text just by adding your username🤦♂️🤦♂️🤔🤦♂️🤦♂️
Fuckers -
@brunofontes If you lose your house key but you can prove that you own the house, you should be able to get new keys. In this case, your identity is irrelevant, Your Passcode is everything, That's not practical. It's not compromising security, It's just plain carelessness.
-
 NoMad134245y@theabbie you know, if you as a person were enough, then you wouldn't need an ID card since a photo of you, or you in person, would be enough 😛
NoMad134245y@theabbie you know, if you as a person were enough, then you wouldn't need an ID card since a photo of you, or you in person, would be enough 😛 -
@theabbie so wait, you are using the same kind of argumentation here than in another infamous thread? A theoretical yet unlikely worst case scenario is your argument for something completely irrelevant? Reminds me of some language being not bad because there is a theoretical superdev who never errs...
-
@theabbie in order to prove your identity and get access to your stuff, someone needs ti have it. Probably hundreds of people would have access to your house keys.
Is that what you call security? -
@brunofontes CEO's remember their Password, If they forget, they are ready to take responsibility for the loss. Common people, old people, children are not best at remembering passcodes. Android is for smart people who understand their phone, That's harsh, but that's a fact.
-
 NoMad134245y@theabbie see, you're extending irrelevant examples. You could keep multiple copies of the physical key elsewhere, but if your lock is easy to pick, that doesn't make the number of keys any relevant.
NoMad134245y@theabbie see, you're extending irrelevant examples. You could keep multiple copies of the physical key elsewhere, but if your lock is easy to pick, that doesn't make the number of keys any relevant. -
@100110111 Encrypting data using Password is called naive encryption, atleast for me. Because losing key means losing everything. In real world, that's useless. It hasn't caused problems yet because Apple people don't care about data, they reset and move on.
-
Like, if you buy a safe for very important stuff you want to the safe factory/workers could open if you loose your code?
So they will have your address and a way to open it without your code?
I am not sure if you understand security, now. -
@theabbie any smart enough at least a little bit tech savvy person would use a password manager so as to only have to remember one or two passwords and maybe a few pin codes..
-
 C0D4644185yI'm going to ring in some people,
C0D4644185yI'm going to ring in some people,
This is going to be fun 😅
@linuxxx
@linux
@AlecX04
@F1973
@Jespersh
@CrankyOldDev
@Awlex
@Bubbles
@bhouston
@caramelCase
@AlgoRythm
@Kimmax
@Jilano -
@C0D4 You can't reset password if data was encrypted with some other key, you need old password, but, you don't have it. That means it's gone forever.
-
@NoMad If you can prove that you own the email ID associated with the account that's enough to prove you own that account and should be able to reset it.
-
@theabbie hahahaha So you want Apple to sell 2 iPhones, one for important people and another one for dummies?
"Buy your next iPhone for Dummies! You can set any password, any time, and we can just ignore it and unlock your phone if you say your ID number" -
@100110111 It's not worst case, you never forgot your password? Or, your parents, or anyone you know. It happens a lot. People forget. They should not have all the burden.
-
@brunofontes Proving Identity means owning papers to house. Or, your photo that is with the house registry, or your neighbours statement that you own it. If it is proven, you should be allowe6to access it.
-
@theabbie the name of this is lack of security. There is plenty of services that implements it. They can even store and send your password in plain text for you.
This is also the reason there are so many email and WhatsApp accounts hacked. -
 NoMad134245y@theabbie let me try a different argument:
NoMad134245y@theabbie let me try a different argument:
1. Forgetting your password doesn't mean your data is useless. It means you don't have access to the data.
2. The encryption key and the password are different things.
3. Some people rather have their dick pics unreachable if they forget their passcodes rather than accessible by everyone. -
@NoMad Lock should not be easy to pick but not impossible to pick too, atleast by the owner. We want something in between usability and security.
-
@brunofontes Not the factory workers, but I, if able to prove that I am the boss, should be able to open it without Passcode
-
@theabbie dude, this is hilarious. So someone will have your house keys with a photo and, if you show up with the invoice, they can see you face, the paper and give you a new pair of keys?
And all those workers that had access to your keys? And if the place that owns the keys were compromised? -
 NoMad134245y@theabbie but that's literally what security means. It means giving access to the right people. Not to just store your data in oblivion. Lol.
NoMad134245y@theabbie but that's literally what security means. It means giving access to the right people. Not to just store your data in oblivion. Lol. -
@100110111 I already told password managers are fine, but it's not an excuse to Apple's Carelessness
-
@theabbie You are mixing topics. A lot.
First: You cannot do a "password reset" on encryption (in contrast to an online service). What you could to, is to save the key somewhere else. And this kind of defeats the purpose... The only way would be to display the key once and let they user write it down.
Second: It's not like all of your data is lost, there is still a (not E2E encrypted) iCloud backup (at least if enabled)...
And *surprise*, this has been used by the FBI (of course sometimes even legitimately).
Third: Apple *could* unlock your phone, by writing an update to the security chip. They explicitly reject this, to prevent opening the Pandora's box.
Fourth: Actually no disk encryption scheme allows decryption by the vendor. Neither LUKS, BitLocker (you could give Microsoft the key, but why would you?) or the pre-T2 encryption on iMacs (I'm contrast to the ones with an iPhone security chip). -
@theabbie and how do you think they will have a copy of the keys to provide you if no one has access to it?
-
@brunofontes You can prove that you own the IPhone, there are numerous ways to do so. And If you can prove it, atleast prople at Apple should be able to unlock it for you.
-
@C0D4 That means OTP is a joke. I can verify that I can access my SMS but I don't own that number.
-
@theabbie so if they cab open for you, they can open for eveyone else if it were interesting to them.
-
@brunofontes It's mostly user's Carelessness that causes such breach. But that's irrelevant. Many great services use better encryption and weren't hacked.
-
@theabbie Have you ever considered people would want this, by a chance?
Also many people will just setup and fingerprint or facial recognition on their phones, not even needing to enter anything. -
@NoMad Forgetting passcode and never Remembering it means data is lost. Everyone doesn't think like your 3rd point.
-
 Root772335yAlso, the answer to your jumble crap is 8. You added an extra space in the expected output. 😕
Root772335yAlso, the answer to your jumble crap is 8. You added an extra space in the expected output. 😕 -
@brunofontes Why do you need photo. Just show your face and the house registry would have your photo. That's enough to verify ownership.
-
@NoMad Yeah security means that, But Good security means that it should be accessible by right people even if they don't have passcode, they just have their identity.
-
@theabbie yes, they have encryption, a good one, that's why toy can't break it without the password.
-
@theabbie HAHAHAHAHAHAHAHAHAH
Thanks for the laughing, but I really need to sleep. -
@sbiewald First: There are good ways to implement reset feature.
Second: Backup defeats the purpose if it's not encrypted the same way and it's not -
@brunofontes They don't have copy because they don't Encrypt like that. They don't give your password they create a new one.
-
 NoMad134245y@theabbie identity is not one dimensional. Which is why we have multiple factor authentication.
NoMad134245y@theabbie identity is not one dimensional. Which is why we have multiple factor authentication.
But, as for the iPhone, again, you have multiple ways of accessing the same data. No, Apple should not be able to open your phone. Otherwise they could do it for just any reason. Yes, you do get backups. Which is why you can access the data even if you lose access to your phone. -
@brunofontes Yeah they can open, they wouldn't, you need trust, World is not a trustless environment
-
 C0D4644185y@F1973 Is it just me or does that social media list never end? 🤭
C0D4644185y@F1973 Is it just me or does that social media list never end? 🤭
No wonder he needs to reset his password so often. -
@F1973 One of us is half knowledged, either me or you guys. It will be proved eventually who is
-
 NoMad134245yGuys, stop ganging up and making fun. 😛
NoMad134245yGuys, stop ganging up and making fun. 😛
He clearly doesn't still get the main point of security, so let's not turn a technical issue into a bullying rally. 😒 -
@sbiewald FaceID is ideal for encrypting and verifying identity at the same time. It's good for security on device
-
@theabbie Backup and device encryptions do have different purposes and threat models, so its fine to not have the same security properties.
This is the usual "usability vs. security" axis, where Apple chose security for their devices (heck, it's one of their core marketing aspects) and usability for their backups. -
@Root Yeah, 8 is correct, you had to use brute force, Now If I first encrypt it with 8 then the output with 5 then with 2 and then with 3 and so on, It becomes more difficult with every digit. And the Space was there.
-
 NoMad134245y@Python it's not. It's a student's question of "why can't I reset my password". He's mixing a lot of topics, but that's the gist of the main question.
NoMad134245y@Python it's not. It's a student's question of "why can't I reset my password". He's mixing a lot of topics, but that's the gist of the main question. -
@C0D4 Dang it! You beat me to the punchline 🤣 I was just about to say the same thing
-
@brunofontes By your analogy, If you lose keys you should get a new house. So we should ban creating keys then. That would be very secure.
-
@NoMad You need to trust a service for using it. If they really want to steal your data they have numerous methods.
-
@C0D4 I keep track of all my accounts, I care about my security and Everyone should
-
 Root772335y@F1973 Obviously this guy doesn’t care about security nor privacy if he posts his email address, every social media account, and bloody phone number online.
Root772335y@F1973 Obviously this guy doesn’t care about security nor privacy if he posts his email address, every social media account, and bloody phone number online.
Also: lol @ those projects. He’s embarrassing himself far more on there than in this thread — and willingly. 😬
“Guess my gender”
Anything pink or purple is female.
Everything else is male.
K...
“Guess the letter”
I draw M. then S. then T. It guesses “P, J, D” every single time. In fact, the only letters I can get it to guess correctly (and even then only sometimes) are P, J, and D. 😂 -
@NoMad Main point of security is your identity is the ultimate authority. Password is a more convenient waynto prove your Identity but it should not be the only way.
-
@sbiewald Backup is a backdoor then, what makes it safe? If every data is hackable then why not Backup?
-
@NoMad I don't use such services at first. If you are not capable of good Encryption I am not using it.
-
Oh. According to his blog he's 18. That explains everything. That's the second worst age to argue with right after 2. 😂😂
-
@NoMad Google is not remotely like that. If it ever gets hacked, I may change my opinion.
-
 Root772335y@theabbie I copy pasted your shit. It was wrong. And yes, I tried values of `n` ranging from 1 to 8 million. Only when adding in Levenshtein distance did I realize you made a mistake when you retyped, rather than copy/pasted, your expected output.
Root772335y@theabbie I copy pasted your shit. It was wrong. And yes, I tried values of `n` ranging from 1 to 8 million. Only when adding in Levenshtein distance did I realize you made a mistake when you retyped, rather than copy/pasted, your expected output.
GG on failing again.
And on wasting my time. 🙄 -
@sbiewald If a backdoor has to exist ultimately then why fool people by giving a sense of security while being equally vulnerable
-
 Root772335y@theabbie Why are you showing off unfinished, buggy code? Seriously! You are the literal worst.
Root772335y@theabbie Why are you showing off unfinished, buggy code? Seriously! You are the literal worst. -
@F1973 I can prove that I am correct, If usability is not that important why build UI, just tell your users the API endpoints and let them send requests. usability if not more important should be equally important.
-
@Root Maybe, anyways, you required brute force, If it was a long Passcode there would be many possibilities. Isn't it safe but useless?
-
 NoMad134245y@theabbie listen, I'm not gonna argue further, because I have to get out of bed and start my day. As well, you seem to think everyone is wrong and you're right. So maybe, you are right. If you're the genius you think you are, go ahead and make the safest encryption method and enlighten us all. But chances are, you're on the wrong track and just being hard headed.
NoMad134245y@theabbie listen, I'm not gonna argue further, because I have to get out of bed and start my day. As well, you seem to think everyone is wrong and you're right. So maybe, you are right. If you're the genius you think you are, go ahead and make the safest encryption method and enlighten us all. But chances are, you're on the wrong track and just being hard headed.
But do read up on encryption and security. Specially on the maths behind it.
Also, yeah some of these guys above are being dicks. But that's what happens when you make a claim in front of pros that you can't back up. -
@NoMad My only claim is, Apple should not be called good just because of such encryption, They might be unhackable but at the cost of usability. They haven't done anything great and shouldn't be credited for that. Other services which are not (YET) hacked inspite of vulnerability are the real heroes. Admit that.
-
@F1973 I can feel Jealousy in your Laugh, being outsmarted by an 18 year old would have hurt. But, Honestly, You deserve it.
-
 Root772335y@F1973 I bet I can guess his key space. 🤫
Root772335y@F1973 I bet I can guess his key space. 🤫
/^[A-Z][a-z0-9]{7,13}$/
Dictionary word(s), probably followed by a number. Maybe with some 1337 }{4X3R substitutions. It’s probably simple.
After all, he’s terrified of forgetting his password, but he so badly wants to show off his skillz.
At least now he might change it. 🙄
Would never admit it, though.
Bloody hell I feel mean tonight. -
OMFG that's a level of apple hating that shouldn't be possible. 😂 Even the cancer that killed Steve Jobs would go 'dude stop'. 🤣
-
 NoMad134245y@theabbie Apple's device encryption is good.
NoMad134245y@theabbie Apple's device encryption is good.
You're wrong.
They're shit for many other reasons, but not for device security. -
@AmbientTea Hate is not with Apple but their bragging, It's just another crap encryption which sounds secure but is useless
-
@theabbie The keyword is threat model.
An encrypted device protects against *anyone* having (physical) access to it (per definition this means Apple no access as well). Not more, not less.
Backup's purpose is to recover from device loss. Of course the secondary requirement is security to prevent (in this case remote) access. More "classic" solutions like 2FA can now be used (this is not possible for device encryption; 2FA also disables the simple password reset by the way).
If people choose to not want the iCloud backup (e.g. because they do not want Apple or law enforcement with court orders to have access to their data), they can even disable it. -
@NoMad Security is not a big deal if there was no concept of forgetting password. Millions of accounts will be lost every month if there is no feature to reset it. It's just that services take some responsibility and don't put all the burden on users. Apple is bad at taking responsibility.
-
@sbiewald That means backdoor must exist for usability, Ideal security is a hypothesis.
-
@-red Well, praising and defending Apple while knowing that it's crap doesn't make anyone cool
-
 C0D4644185y@F1973 🤔I won't dox him, but I will say there is a page with enough information to knock on his front door and greet his parents by name.
C0D4644185y@F1973 🤔I won't dox him, but I will say there is a page with enough information to knock on his front door and greet his parents by name.
There's also an admin page with a lack of authentication.
@theabbie you may want to remove that csv file from a public accessible file, God knows why you would have that on the Internet - tell Zorin i say hi.
And with that, I'm out! -
@F1973 That is not an actual admin page, Don't get excited, Thanks for stalking me so badly
-
 C0D4644185y@theabbie I wasn't stalking, hell I didn't even scroll past the first 30 lines of source code to get to where I am.
C0D4644185y@theabbie I wasn't stalking, hell I didn't even scroll past the first 30 lines of source code to get to where I am.
do you have... never mind I've be got your email, I'll send you a link to what I'm taking about before it becomes public. -
@C0D4 Why would you do that? There are many phone numbers on internet, you don't call everything
-
@theabbie Shocking, you know? /s
While not having "perfect" security, I find having 99.999% perfect one quite acceptable. And giving up a small part of usability is perfectly fine (and many people do accept it).
Look, you can attack Apple for many things (I'm sure many of them here will agree to that part), but their physical device security including the tradeoffs is one of the best regarding both security and usability. -
@sbiewald It might be very secure but it's not a big deal, That's unnecessary hype while they have accomplished nothing. It's unhackable, but not very usable, It's my opinion
-
@iiii I might not be professional but you guys even if professional are not acting like one. You guys are just sticking to your argument without realising it could be wrong. You are senior, you must be knowing better that usability is necessary, Users are stupid, how do you expect them to take all responsibility of their data. And if Apple is doing that, you must realise that it's easy for them. They are freeing their hands from hard work. It's too much Hype, They are good at manipulating and not accomplishing anything.
-
 NoMad134245y@theabbie because users are grown ass adults, even if they sometimes act irresponsibly.
NoMad134245y@theabbie because users are grown ass adults, even if they sometimes act irresponsibly.
Your argument has been used way too often in history in suppressing women, people of color and mind you, even your own culture.
We're way past 20th century for you to make such arguments without even thinking of consequences. "How do you expect them to take responsibility"??? The same way you trust their driving license and voting capabilites, the same way you trust strangers who work at the restaurant to not poison you with dish washer and stupidity and the same way... You know what? Why am I even arguing it's not like you listen to anyone but yourself.
In a parallel universe, you'd be right tho. -
@NoMad If that's what you call security, Then Apple has actually accomplished nothing, I agree that such encryption is fine but in that case Apple is praised for things even a 15 year old could implement. This discussion started to prove that Apple is hyped. And I guess that's proven. Fck Usability It's unhackable, Everyone can do such encryption and Internet will be filled with Encrypted Garbage which cannot be claimed by anyone.
I negotiate and I agree to say that it's ideal Encryption but still Apple should not be given any credit for that, It's hyped and it's true. -
@Jilano Using such Encryption means expecting that one day you might lose all your data and no one will be able to help you.
-
 NoMad134245y@theabbie "Apple did good, but shouldn't be given credit for the one good thing it did, right after usability for end user, which is their whole 2 selling points"
NoMad134245y@theabbie "Apple did good, but shouldn't be given credit for the one good thing it did, right after usability for end user, which is their whole 2 selling points"
Lemme sum it up 😛 -
@NoMad I guess everyone was already convinced with that, This discussion yielded nothing
-
@F1973 This is literally the only platform to Rant, I am at the most correct place to do this
-
Oh boi, you're gonna feel so embarrassed by this thread by the time you finish your uni cryptography course. 😏
-
@AmbientTea The Discussion is not even about cryptography, It's about how simple it is and Why Apple is hyped
-
What the hell.
The whole point of encryption is to make data inaccessible if you don't have the password.
Yes, people do forget passwords. If that's more of a problem in your threat model than unauthorized 3rd parties accessing your data, then encryption is not the right answer for the problem you're trying to solve.
> The goal of encryption is that no one other than user and the service should be able to access it.
No. The goal of encryption is that no one other than user should be able to access it. If the service can access it, so can anyone who hacks it or has legitimate access and abuses it (rogue employees). If anyone but you can access that data, it's not yours anymore. -
Somebody -- All my comments, I have a little Idea of who it is, However, don't do it, Be a good sport, I have no hate for anyone
-
@gronostaj Okay, That might be correct, Also, Such an Encryption is simple to implement, So, Apple has done nothing great, It's hyped, that's all I wanted to prove
-
No encryption is simple to implement, that's why nobody sane cooks their own cryptography in house unless they specialize in it. Anything you can implement out of your overconfident ass can be easily cracked.
-
 NoMad134245y@theabbie I don't like the situation you got stuck in either. Admittedly, everyone could've said "he's stupid" and moved on without arguing with you. But they care about security enough to know your kind of thinking has many negative consequences.
NoMad134245y@theabbie I don't like the situation you got stuck in either. Admittedly, everyone could've said "he's stupid" and moved on without arguing with you. But they care about security enough to know your kind of thinking has many negative consequences.
But then again, you made a claim about a field you know nothing about.
Encryption is the love child of theoretical cryptography and system security, btw 😛 -
@AmbientTea To show how simple it is, consider this function I made
function jumble(text,n) {
var result="";
go(text,n);
function go(text,n) {
if (text.length!=1) {
var p = text.split("")[((n-1)%(text.length))];
result+=p;
go(text.slice(((n-1)%(text.length))+1,text.length)+text.slice(0,((n-1)%(text.length))),n);
}
else {result+=text;}
}
return result;
}
Now I do this,
var x = data;
x = jumble(x,A);
x = jumble(x,B);;
x = jumble(x,C);
x = jumble(x,D);
Here, ABCD is a 4 digit passcode, eg. if it's 1234 then, A is 1, B is 2, C is 3, D is 4
I took some data and some passcode, and the result after this process is
"otTud ahhIanaa ir eeYoseref c aua scpdHieDIo,otyf e slvr Avk Ssr nod iImsa ehh,nyat iteEr ,aP"
Can you find the original data, If you do brute force, I must say, phone doesn't allow you to enter all combinations. It was that simple and you think Encryption is a Big deal. -
@NoMad No one here is a pro in Encryption, They are arguing because it is against there EGO, They are just assuming that they know everything (so am I) But they are still in illusion that Apple is a Saviour
-
 NoMad134245y@theabbie @linuxxx is actually and specifically a cyber security expert. I still doubt you'd listen to him anyways.
NoMad134245y@theabbie @linuxxx is actually and specifically a cyber security expert. I still doubt you'd listen to him anyways. -
 dfox421565y@F1973 thanks. I like to try to avoid banning people for expressing unpopular or misguided opinions, and I’m not really sure that explicitly violates our rules so in fairness I’m not really sure what to do.
dfox421565y@F1973 thanks. I like to try to avoid banning people for expressing unpopular or misguided opinions, and I’m not really sure that explicitly violates our rules so in fairness I’m not really sure what to do.
@theabbie please try to contribute to the community in a positive way if you’re actually interested in being a part of it (and aren’t trolling 😀) -
@dfox Sir, You can read this convo, I always start politely, Then some people go off-topic and question my skills. They just don't want to be disagreed with. What's your Opinion on all this Hype with Apple?
-
 Root772335y@theabbie You don’t need a backdoored encryption algo to allow the user to change their password. The password and decryption key do not have to be the same, as @NoMad demonstrated.
Root772335y@theabbie You don’t need a backdoored encryption algo to allow the user to change their password. The password and decryption key do not have to be the same, as @NoMad demonstrated.
Seriously, please educate yourself on security and encryption before asserting misguided and dangerously incorrect information. If anyone followed your advice, it would put their users’ data at risk, yet you assert it so confidently, and refuse to listen to any arguments to the contrary. This is what makes me so angry. -
@theabbie very cool function. Now, for the sake of completeness, can you provide a function to decrypt the data using the passcode?
-
@Root Multiple passwords don't make it any better, If a decryption key exists and is stored at server, that's still vulnerable. It's not about being educated, it's about common sense.
-
 dfox421565y@F1973 no problem, thanks for giving me the heads up, and I’ll definitely keep an eye on this rant!
dfox421565y@F1973 no problem, thanks for giving me the heads up, and I’ll definitely keep an eye on this rant! -
@theabbie
> No one here is a pro in Encryption, They are arguing because it is against there EGO, They are just assuming that they know everything (so am I) But they are still in illusion that Apple is a Saviour
Please avoid those assumptions, especially deyning someone's (especially not everyone's) competency.
And just because someone does not support your argumentation (or moves the discussion away from the subject), does not mean a certain motive. -
@AmbientTea
Here it is
function unjumble(text,n) {
var result=[];
var nums=[];
var finalresult=[];
for (i=0;i<text.length;i++) {nums[i]=i}
go(nums,n);
function go(nums,n) {
if (nums.length!=1) {
var p = nums[((n-1)%(nums.length))];
result.push(p);
go(nums.slice(((n-1)%(nums.length))+1,nums.length).concat(nums.slice(0,((n-1)%(nums.length)))),n);
}
else {result.push(nums[0])}
}
for (x in result) {finalresult[result[x]]=text[x]}
return finalresult.join("");
}
Now decrypt it in the order D, C, B, A But still, if you don't have Passcode it's still Brute Force -
@sbiewald The only reason anyone gave till now is that security is more important, If it's valid to compare Encryption to locking a house then By that analogy, losing key would be a nightmare, But it's not actually a big deal. If you carefully design an algorithm then maybe you could trade off with security and make it more usable. Ultimate Security is an illusion anyways. @linuxxx might have some opinion, let's wait for him.
-
@Jilano Then Why Should Apple Brag about being Secure? All it does is give you an unbreakable lock and a key and now it's your responsibility.
-
 kiki374865yI’m favoriting this, un-fucking-believeable. My Maryland cybersec certificate goes down the drain
kiki374865yI’m favoriting this, un-fucking-believeable. My Maryland cybersec certificate goes down the drain
@theabbie братишка ебать ты долбоеб земля тебе пухом
Holy fucking shit this is not suicide this is self disintegration -
@theabbie
> [...] But still, if you don't have Passcode it's still Brute Force
No. Your algorithm is a simple permutation, nothing more, nothing less.
Thus, the ciphertext 'leaks' data from the plaintext: Every character in the output was in the input. With enough context, the message might be reconstructed without even touching your function. -
@theabbie
> Then Why Should Apple Brag about being Secure? All it does is give you an unbreakable lock and a key and now it's your responsibility.
That's actually the point... -
@Z-GOD It's not about forgetting password, It's about unnecessary Hype. I have started to respect other servives more now because they are not losers, They take responsibility of their user's data. Encryption might not be easy but Apple is no special. You have an illusion of security, Apple Manipulated you and now you are giving people fake assurance that their data js safe, Yeah, it is safe but it won't take much to transform it into an encrypted garbage.
-
 kiki374865y@theabbie good luck with that confessions, and good luck with monica, naveen, sahil and pratik
kiki374865y@theabbie good luck with that confessions, and good luck with monica, naveen, sahil and pratik -
 Root772335y@theabbie Ideally, services would operate similar to TutaNota, where the service has almost zero knowledge of the users or their data. They can read just enough to route emails to their intended recipients, and little else. All decryption and encryption happens entirely on the client, meaning nothing is ever transmitted in clear text. For passwords, you have one, and a reset key. If you lose both, your data is irretrievable. So don’t.
Root772335y@theabbie Ideally, services would operate similar to TutaNota, where the service has almost zero knowledge of the users or their data. They can read just enough to route emails to their intended recipients, and little else. All decryption and encryption happens entirely on the client, meaning nothing is ever transmitted in clear text. For passwords, you have one, and a reset key. If you lose both, your data is irretrievable. So don’t.
This obviously poses problems for having multiple users able to access the data. In such a case, you would need a central store of decryption keys; there is no way around it. However, you can still apply the same principle by adding one layer: you can easily encrypt the decryption key with the user’s password hash, or other encryption key depending on your implementation, and store it securely on the server. Only the user could decrypt their copy, transmitted to the client only in encrypted form, which in turn allows them to decrypt the shared data on the client.
That way the server has zero knowledge of the data, nothing is transmitted in the clear, multiple users can access said data, and they can change their passwords using the reset token. All without ever allowing third party access.
True, if all users lose both their passwords and reset tokens, the data is irretrievable. But this also makes it impervious to DB leaks and social engineering, like what happened with Twitter verified accounts. The data and its access are secure, and safe so long as the users don’t share said passwords with anyone else.
The takeaway is that, while you can’t have perfect security and impose no limitations on the user, security is much more important. And strong security doesn’t necessarily mean the data is easy to lose. -
@uyouthe What has it got to do with this, Stalking me, Proving that I don't have experience doesn't make me wrong
-
@theabbie praising and defending JS while everyone knows its not good doesn't make anyone cool either
-
 kiki374865y@theabbie out of your ignorance you exposed the addresses of 68 people, their names and addresses. FUCKING DELETE YOUR WEBSITE NOW BEFORE YOU GOT JAILED FOR THIS
kiki374865y@theabbie out of your ignorance you exposed the addresses of 68 people, their names and addresses. FUCKING DELETE YOUR WEBSITE NOW BEFORE YOU GOT JAILED FOR THIS -
 kiki374865y@theabbie I HAVE YOUR CSV AND YOU AND YOUR GF VIDEOS AND EVERYONE ELSE DOES FUCKING DELETE THE WEBSITE THATS ILLEGAL
kiki374865y@theabbie I HAVE YOUR CSV AND YOU AND YOUR GF VIDEOS AND EVERYONE ELSE DOES FUCKING DELETE THE WEBSITE THATS ILLEGAL -
@Root That decryption key thing is good, That proves that user has to take responsibility of atleast key. What many websites today do is that they allow social login, This transferring their burden on social media accounts, Or, OTP login or Magic Link login are way of transferring burden. This is simlar to password managers, Since users can't remember keys, put it in vault and forget it, Write that vault password somewhere, make a tattoo, do whatever but don't lose it. This is about transferring burden. At last, If someone really cares about their data, remember keys
So, If password managers are doing the same thing, Why the Hype with Apple? -
 kiki374865y@theabbie stop liking my comments nigga you can go to jail for this shit, fucking unpublish your website before it’s too late
kiki374865y@theabbie stop liking my comments nigga you can go to jail for this shit, fucking unpublish your website before it’s too late -
@theabbie
> How can you be so wrong? Prove it by solving it but not with Brute force
That's not how developing ciphers works. Really!
I do have work to do, so unfortunately I do not have time _proofing_ you wrong. Leaking data from the plain text (besides length, obviously), is a no-go for any cipher.
When I "Your algorithm is a simple permutation, nothing more, nothing less." you answered that "I could not be more wrong". Do you mind at least elaborating that part? -
@100110111 It's everyone's personal hate towards JS, That is not a measure of how good JS is
-
@uyouthe oh you should see the one on JS too... kept me from going for a cig for a full 12h or more
-
@uyouthe That video is not of my girlfriend, It is part of a webpage and is done on command
-
@theabbie Your "jumble" function is not encryption - encryption is reversible. I can think of some cryptographic use cases for it, but still, it's not encryption.
Anyway, even with my limited crypto knowledge, I bet it's broken. People spend years creating crypto algos and still make mistakes - it's incredibly easy to miss something fundamental. For example MySQL's OLD_PASSWORD func. looks fine for someone without cryptoanalysis knowledge, but actually an efficient algorithm for reversing it can be derived: https://security.stackexchange.com/...
And even if the algorithm is perfect, the implementation can be flawed. For example this password check code looks fine at the first glance:
function checkPassword(providedPwd, correctPwd) {
return providedPwd === correctPwd;
}
But it's actually vulnerable to timing attacks: you can find out how many initial chars are correct by observing how fast the function returns (there's an invisible loop for string comparison). -
@sbiewald It means that it's not that simple, If you think it's that, you should elaborate. It is basic jumbling but on doing it with 4 numbers, it's not simple jumbling anymore. You yourself haven't understood that function.
-
@theabbie no dude, that thread was everyone saying what is wrong about JS and why it's not really that good a language, specifically not about hating it. You just really, really, really wanted everyone to hate JS.
-
@theabbie Just because I repeat a permutation function multiple times or only about parts of the input, does not make the output less of one.
All letters of the input are still in the output, just in a different order. This is - per definition - a permutation. -
@100110111 Everyone was wrong because weakly typed language though not providing any advantage doesn't harm anything. That Potential Bug argument is absolute Rubbish because those people never properly used JS in fear of Bugs. You don't hate JS because of it's flaws, you hate because something better exists and it's a peer pressure.
-
 Root772335y@theabbie Apple appears to care about privacy; google does not. Google’s entire business model is data mining to target ads. The more data they have about you, the more money they can make.
Root772335y@theabbie Apple appears to care about privacy; google does not. Google’s entire business model is data mining to target ads. The more data they have about you, the more money they can make.
Everything they do is designed to gather data. Everything. Recaptcha, font and js CDNs, analytics, Gmail — especially Gmail — etc. Every http request to google’s servers tracks you and your activity across about 75% of websites, as I remember the statistic. They store everything, and correlate it as they learn more. And of course they are always getting better at correlating the data, so they continually learn more from everything they’ve stored.
The worst part, though, is that they share it.
Everything that goes online is permanent, and says a hell of a lot more about you than you will ever realize. Timing on posts, timing on traffic, search terms, use of specific wording, writing style, tone, new words, new interests, and above all else: trends of the above. These can show, with surprising and terrifying accuracy, where you live, who you know, what you like, what you are likely to buy/do/vote for (and when, down to the hour), your mood, if you are depressed, have a mental illness, are likely to have children within five years, love/hate your job, if you are cheating, what medications you are on, etc. etc. etc. All of this by analyzing patterns in the data, not even by understanding what it is you wrote because natural language processing isn’t even there yet.
This is why data privacy is so important. We have a moral obligation to do everything we can to protect and educate users, not exploit them like Google, Facebook, Amazon, Alibaba, Tencent, TikTok, etc. -
@sbiewald For a data with n characters there are n! permutations, and it grows insanely with n, So, If by some method it is jumbled properly, It would have n! possibilities. And My method jumbles it properly. It's not a simple permutation. You haven't understood the function yet. And yes, it's reversible. It can be called Encryption and all characters being in it doesn't make it any less of an Encryption, It won't make any sense.
-
@Root It would be better if you give proper sources of information especially the sharing part. And It's perfectly fine to use data to improve it's performance, And regarding that it shares it, Which doesn't seem true (unless you give source) You have a misconception about how it happens. Targeted ads send you to correct advertisers, Google doesn't tell them that this person likes chocolate or is married or anything. I have no hate for Apple, I don't use it anyways, But saying that it is most secure is a hype. It might have the best Encryption but it is nothing special.
-
@theabbie I have to ask, how thick is your head? How is it even possible that it has yet to cross your mind that a community full of professionals in a subject may actually A) know what they are talking about, B) understand the subject through and through and C) be correct?
-
 Root772335y@theabbie Any rearranging is simple permutation. It doesn’t matter how well you shuffle the letters, it’s still just permutation, which leaks data about the input. This is always bad.
Root772335y@theabbie Any rearranging is simple permutation. It doesn’t matter how well you shuffle the letters, it’s still just permutation, which leaks data about the input. This is always bad.
I still know how many “e”s are in the input string, for example. If I can make a guess as to the nature of the data, I can learn quite a bit about it. The number of spaces very likely correlates to the number of words. Based on letter counts I can make a good guess as to which words it likely contains, and this gets more accurate as the data size increases. And more so if I know anything at all about the user who produced the data.
Also, depending on the data, I might not even need to crack the permutation cypher to get what I need from it. -
@100110111 How difficult it is to admit that Apple is Hyped? What's so special with it's Encryption? It can't be hacked because of mathematical limitations not because of Anything special Apple did. It is just like one of those password managers or decentralized websites where you can't reset password. Admit it, I don't want you to say Encryption is Crap, It's just that Apple is no special.
-
@Root Regarding Nature of Data, I could have done those permutations on Base64 encoded data, Then any nature won't have leaked. I am not saying my function is super impressive, it's a demonstration of what I mean
-
@theabbie That is not my point. For natural language, there are not n! permutations of letters.
Some examples:
Your ciphertext contains a capital "T". Usually this starts a sentence. A "," usually separates one. Spaces separate words. Now start reconstructing. Sure this becomes increasingly difficult for very long text, but still leaks many things.
Together with a bit of context (like education of the sender, message subject, potential text type, ...) the likely vocabulary of the message can be reconstructed.
If it is a message to soldiers regarding tacticts, the vocabulary likely contains words usually found in the military. This makes attacking even easier.
More often than thought, this "metadata" is available, at least when targeting a specific person.
A proper encryption leaks exactly nothing (besides length, obviously) about the plain text. A properly encrypted message is virtually indistinguishable from random data (independant of input). -
Someone very intelligent and famous once said EGO=1/knowledge. No point to argue as knowledge comes to those who seek for it and learn from others.
Trying to prove a point that no one else buys into, should at least give you a small hint that you might be “slightly” wrong on this topic. -
@theabbie wait, since when was this thread about Apple being hyped? As someone who's now worked on a Mac for a few years and wouldn't consider going back, and personally not being an expert on security (since security seems to have something to do with Apple hype in your opinion), I can not say a bad thing about Apple in this context.
-
@sbiewald Okay, what about Base64 encoding before, Now, It won't leak any nature and Brute Force is necessary, Don't just say it's permutation so It's possible. It's Not.
-
Can someone please tell me what we're talking about at this point of the thread? Apple? Security vs. usability? Security best practices? Theory of encryption? None if it? All of it?
... I can't hear it over popcorn munching -
 Root772335y@100110111 Especially since we are all saying basically the same things. 🙄
Root772335y@100110111 Especially since we are all saying basically the same things. 🙄
I tried shock, I tried showing that there things he doesn’t know yet, I tried calm reasoning, I tried familiar wording. Nothing seems to work. He keeps insisting we don’t know anything, keeps mixing up concepts, and keeps not making any bloody sense.
I’m done.
It’s also 3:30am here and I’m exhausted. 🤦🏻♀️ -
@100110111 It was always about Apple being hyped. See the main problem statement at the top. People love apple because it makes things easier, I agree, But Spoonfeeding users is a bad thing. Apple is like that comfort Zone Bubble that you don't want to leave but it will eat you inside.
-
@Root I had agreed to your point earlier, There is no problem in such Encryption, What makes you think that Apple is not Hyped? What special it has done that other services like password managers Haven't done?
-
@theabbie It still leaks... Also the algorithm is damn inefficient now.
Because *surprise, surprise* natural language does not contain binary data, thus all "correct" arrangements of base64 data must decode to letters. -
@sbiewald And to find correct combination you need brute force, And with so many characters it's not a good idea. Well, you just played yourself.
-
@theabbie No, not at all.
Just because there is no simple "algorithmic" solution to your cipher, this does not mean it is not broken (in cryptographic terms, look it up what it means in this context, please). -
@sbiewald Okay, forget my example, there are many basic encryption algorithms which are unbreakable, Such encryption is never a big deal
-
 Condor315485yThe fact that they can't decrypt it is actually a very good sign. It means that the encryption method used is not viable to crack (not that they will bother with that), nor that they have a master key of their own (despite 3 letter agencies like the NSA absolutely loving the idea), AND that they don't store a copy of your data either. These are all very good things and privacy is rightfully so something that Apple is renowned for.
Condor315485yThe fact that they can't decrypt it is actually a very good sign. It means that the encryption method used is not viable to crack (not that they will bother with that), nor that they have a master key of their own (despite 3 letter agencies like the NSA absolutely loving the idea), AND that they don't store a copy of your data either. These are all very good things and privacy is rightfully so something that Apple is renowned for.
Don't get me wrong, they're shit for a lot of reasons but privacy and security aren't among them.
Companies like my lovely ISP that will send my password via postal mail upon request however... Yeah. They know the password, took years to encrypt their database (basically useless, they should've hashed it) and actively use it to impersonate customers for tech support.
I recommend that you learn about symmetric and asymmetric cryptography, hash functions and the importance of each, and their intended applications. -
 kiki374865y
kiki374865y -
@Condor The point wasn't why such Encryption is bad, It was that Apple is Hyped, And yes it is. It is doing just Encryption, Is not some futuristic Technology, They are given to much credit for doing such basic stuff. That's wrong and that's the point of this discussion.
-
 NoMad134245y@Condor HEY, I FORGOT YOU EXISTED! HOW ARE YOU THESE DAYS? IT'S SO GOOD TO SEE YOU AGAIN!
NoMad134245y@Condor HEY, I FORGOT YOU EXISTED! HOW ARE YOU THESE DAYS? IT'S SO GOOD TO SEE YOU AGAIN! -
@uyouthe But I wasn't wrong about that, Middle man can change data, HTTPS is a good system, So? I never told it's bad.
-
 NoMad134245y@theabbie I would but unfortunately I already promised someone else. 😛 Not every two people with the same opinion are dating, so you might as well just grow the fuck up.
NoMad134245y@theabbie I would but unfortunately I already promised someone else. 😛 Not every two people with the same opinion are dating, so you might as well just grow the fuck up. -
@NoMad I must not have told you guys my age, If I acted like a 50 year old, You people would have agreed with my opinions
-
 Condor315485y@NoMad haha, thanks! Just joined again I guess. Same as usual here, but really started working on the annoyances of technology. Sometimes just said fuck it and wrote my own stuff. Ended up being easier than dealing with the existing "solutions".. career shift from sysadmin mayhaps? XD
Condor315485y@NoMad haha, thanks! Just joined again I guess. Same as usual here, but really started working on the annoyances of technology. Sometimes just said fuck it and wrote my own stuff. Ended up being easier than dealing with the existing "solutions".. career shift from sysadmin mayhaps? XD
How have you been? -
@Condor Don't waste the chat space here, I heard there is a limit, Save this for valuable discussion
-
 NoMad134245y@Condor not too bad. I also deleted a while back but frustration with tech brought me back again. How's the pandemic treating you? WFH is fun?
NoMad134245y@Condor not too bad. I also deleted a while back but frustration with tech brought me back again. How's the pandemic treating you? WFH is fun? -
 Condor315485y@NoMad huge productivity boost actually, the COVID-19 pandemic! Especially in the first months, VPN access from anywhere and the servers themselves being at the comfort of my home (just reverse proxied from VPS's) really helped a lot. But the stores were plundered! Especially the toilet paper.. the goddamn toilet paper!!!! AAAAAAAAAA
Condor315485y@NoMad huge productivity boost actually, the COVID-19 pandemic! Especially in the first months, VPN access from anywhere and the servers themselves being at the comfort of my home (just reverse proxied from VPS's) really helped a lot. But the stores were plundered! Especially the toilet paper.. the goddamn toilet paper!!!! AAAAAAAAAA -
 scout25095y@F1973 I use telegram...what is it? This thread was already soooo damn long when I got here I didn’t read more than a few...
scout25095y@F1973 I use telegram...what is it? This thread was already soooo damn long when I got here I didn’t read more than a few... -
 NoMad134245y@scout we're reaching 300 comments. I wonder, what's the record for the most comments on a rant.
NoMad134245y@scout we're reaching 300 comments. I wonder, what's the record for the most comments on a rant.
Does anybody know? -
 Condor315485y@scout there's the codrTalk network there on t.me/codrTalk (invite link in that channel iirc), if you'd like we could talk there? I'm @ghnou on Telegram.
Condor315485y@scout there's the codrTalk network there on t.me/codrTalk (invite link in that channel iirc), if you'd like we could talk there? I'm @ghnou on Telegram.
But also tempted to find out what the limit on comments is, if any :D -
 NoMad134245y@100110111 I see. The one where he did research on a language via looking at memes... Perfection! 👌🏻
NoMad134245y@100110111 I see. The one where he did research on a language via looking at memes... Perfection! 👌🏻 -
 C0D4644185y@Condor toilet paper was gone in days here, good thing i keep a large supply.. never know when the end of the world is going to come knocking at the doors.
C0D4644185y@Condor toilet paper was gone in days here, good thing i keep a large supply.. never know when the end of the world is going to come knocking at the doors.
@NoMad, what ever do you mean, i'm just hear sharing around the popcorn. i had to mute this thread... its almost as good / bad as a ++ bomb. -
@MySlugLikesSalt oh don't worry, OP will surely come up with a new one soon enough
-
@F1973 @Condor I'm late as well, I'm very curious. I use Telegram as well if anyone is interested in sharing... :P
-
 NoMad134245yWe should do a game of drinking bingo and take a shot whenever @Nanos says "Reminds me of.." or "This reminded me of..." or "I'm reminded of...".
NoMad134245yWe should do a game of drinking bingo and take a shot whenever @Nanos says "Reminds me of.." or "This reminded me of..." or "I'm reminded of...".
@Nanos don't mean any offense, just making light of your catchphrase. -
@iiii it's called capitalism. I don't know if you've noticed it around. It's this new thing everyone is doing.
-
 NoMad134245y@AlgoRythm I miss him so bad 😢😢 I even tried stalking him but his website seems to be gone.
NoMad134245y@AlgoRythm I miss him so bad 😢😢 I even tried stalking him but his website seems to be gone.
You know, like when you grow fond of someone but also can't be arsed really befriending them... But his placeholder account @AlexDeLarge is still here. -
 C0D4644185y@NoMad I'm going to run out of vodka if we are playing @Nanos shots.
C0D4644185y@NoMad I'm going to run out of vodka if we are playing @Nanos shots.
Great guy though! -
@theabbie Getting rid of those files with a simple delete isn't enough. Anyone can still see them. Check this out.
https://docs.github.com/en/github/... -
@MySlugLikesSalt if you go into his .io repository... He's just doxxing people... Lol
@theabbie honestly man I know you are still figuring things out but you need to just take some advice and remove your site.
You messed up and it can have some pretty fucked up consequences. Your whole git log needs to be combed through so you can remove the databases of private info.
Honestly, it may be worth just deleting your .git folder at this point and starting anew.
Your views on technology are interesting. I think a good exercise is to implement a proper encryption Algo. Not one they teach on the first week of school, a real Algo used in the real world. They are complex, they are hard, and you will probably fail to complete it. But you will succeed in learning, which is the bigger picture.
Your information is always your responsibility. If it becomes someone else's responsibility... It also becomes their data. You must protect what is yours, always. It may seem counter intuitive, but @root @nomad @c0d4 ... Everyone here is right; losing your data IS good UX when compared to having your data accessible by those who don't own it (Even if it's the vendor, like Apple)
Maybe you do not believe this, but as soon as there is an opportunity for evil with profit, bad people will take it. An exercise to learn this: install an SSH server on a virtual Linux machine, and open that to the internet with port 22 open (default). Watch as thousands of requests come in per hour trying to hack you...
And just as general advice, if you find something generally regarded as extremely complex (encryption) to be "simple", you probably don't fully understand it (the alternative being you understand bit better than everyone else in the world. Use your own common sense to figure out which is true) -
@AlgoRythm Yeah I know, at this point I'm legit just trying to help not sarcastic in any way.
-
@AlgoRythm the last sentence. You think... OP... and common sense... in the same sentence?
-
Pinging @dfox just in case it's worth removing/censoring any comments linking to OP's site, in order to limit discoverability (leading to the JSON file with lots of personal details...)
-
@100110111 One would hope that even if their grasp of common sense is fractional, if you keep trying, eventually you will find that small fraction which is present...
@MySlugLikesSalt I doubt that the links here are what exposes him. The GitHub crawlers have already detected email patterns and downloaded his whole repository. The links being on devRant are just icing on the cake.
@dfox if you do take action, please don't remove the whole rant. There's lots of learning that OP needs to do, and this rant has some good info for him. -
@MySlugLikesSalt OP did share them originally themselves, so I'd say the responsibility is on them, but who am I to say
-
@100110111 Right I'm not worried about OP, more worried about the people having their physical addresses exposed.
-
@100110111 I can see why OP wants their vendors to take responsibility for their data...
...because they have no business doing it themselves! -
@AlgoRythm one could always hope, but it may take a few years of trying looking at how things stand...
-
@100110111 Unlike OP's jiggle encryption, that would take a true brute-force haha
-
@MySlugLikesSalt @AlgoRythm you're right. For the good of others, vendors taking ownership of and responsibility for OP's data (and others like them) would be a welcome service...
-
@MySlugLikesSalt Please Help Me With That, Is there a method on Mobile without CLI?
-
@theabbie Not that I know of. Get to a computer with git and run the commands there. Be sure to delete the "details.json" file as well as the HTML file with all Elisha's info. Get rid of her photo from the "files" folder as well.
-
 NoMad134245y@AlgoRythm isn't OP a vendor himself at this point? Isn't he failing to protect customer data?
NoMad134245y@AlgoRythm isn't OP a vendor himself at this point? Isn't he failing to protect customer data? -
@AlgoRythm At this point complexity of algorithm doesn't even matter, If Apple created some million dollar secret algorithm then it's fine, But, They must have used some algorithm which already exists, maybe with some modification. Then services like "Lastpass" which has similar mechanism is doing Equally great as Apple. The point is Apple is Hyped, Such Encryption is popular and is Used everywhere, Apple doesn't have a secret Recipe, It is No special.
-
@Creep That is an argument people use when they have 0 knowledge about what's going on but just want to join the majority
-
@theabbie You need to not be arguing about security right now. You need to be fixing your own data breach.
-
@MySlugLikesSalt If you guys care so much about data, Apple should've been your last option
-
@theabbie I never said a word about Apple. I'm talking about Elisha and Tushar and Jaydip and Abhisheik and the sixty others whose info you leaked.
-
@PrivateGER Another Guy, This Is What People with little knowledge say just to sound cool
-
@theabbie Boo hoo. Remember your password and hide a backup of it somewhere. Don't be dumb.
-
@theabbie My issue is that you keep deflecting the fact that your whole rant (I just re-read it) is about how Apple's encryption is dumb and naive because users may forget their passwords by saying your point is actually that apple is over hyped.
That's not your point. You have been bullied into abandoning your original point and you chose to find another (much more opinion-based, might I add) point because you didn't want to admit your views on user data and encryption are wrong.
Just swallow your pride. Everyone has misinformed views on things. -
You calling it secure to have encryption backdoors proves your extreme incompetence with any form of cybersecurity.
-
@MySlugLikesSalt This one was for a previous comment, Yeah, I will try to fix this Breach, One thing about privacy that I know is that Internet is full of emails and Phone Numbers, Crawlers love these but no one is really interested in details from weird sources. It is usable only when they come from a purpose. For example, If each of them was a student, It might be useful to those Telecallers or other services. But these details in itself are unusable unless someone wants to Spam. So, Yeah, Stop overreacting.
-
@theabbie Exactly what @AlgoRythm said. For example, I used to looooove UWP. I found it easy to develop with, and I thought it was the future on Windows. Since then, it's fallen flat on its face in a lot of ways. It's still the right tool for the job occasionally, but I was very wrong about it in general. We're all wrong sometimes. It doesn't hurt to admit it and then FIX OUR MISTAKES (cough cough)
-
@theabbie It doesn't matter what people want them for. You doxxed them. If I was a psychopath, I could literally mail a bomb to Elisha (I'm focusing on her because you leaked a LOT of her info). Or one of her family members. By name. It doesn't matter if you think the info could or could not be useful. You leaked it, and that is a big deal.
-
@AlgoRythm It can't be right or wrong now, If it is wrong that would prove that Apple users are fools (which they are) but I think that should be a self realisation. It's that Apple is Hyped. This discussion deviated a lot but primary concern is That Apple is Hyped.
-
@theabbie Now I wonder!
Encrypted Android phones are impossible to unlock without passcode either. Does that make them naive too? -
@theabbie
"I think the fact that even Apple can't unlock your phone if you forget your passcode proves that they use very naive encryption method."
"Such encryption, though safe is not practical, Imagine if there was no "Forget Password" Option on any account, I usually forgot my password very often when I was a child."
"Reset Password is a weak point which might be exploited but in such cases, usability is more important than security."
These are from your original post, they are your original point, and they are why you are getting so much backlash.
Your point was NOT "Apple is good but they don't deserve the hype". Your point was "Apple is stupid because they wont let you reset your password". Here is an actual quote from your post to prove it:
"Any service which doesn't allow resetting Password is a shitty service and I would never use such a service"
Just give up arguing -
@theabbie stop calling people names and look at yourself first. Everyone is entitled to their opinion, and so people who like or dislike Apple for example. You’re like a cat. Never falls on its back. In your case admit you were wrong and move on fixing your data breach. I think at this point you’ll do everyone a favour.
Not trying to be sarcastic or anything, but you’re only making a fool of yourself. -
@theabbie I'm *this* close to actually letting the people whose data you've leaked know that you've leaked their data. And if I get that far I'll make pretty damn sure they'll be pretty damn pissed at you for doing so. And if *I* don't do it, someone will. Or worse. So fix it instead of arguing here. You can continue this immature stupidity once you've dealt with the real issue, okurrr?
-
@MySlugLikesSalt It's only the information I know, apart from email and phone rest of information can be determined if someone is actually targeting her. Yeah, It's wrong, I admit it. But That's not what this discussion is all about.
-
@100110111 I've already let a couple of the people know. I grabbed the email addresses and strongly considered just sending out an email blast.
-
@PrivateGER No they are not impossible, Not all to be more precise. Could you specify an example instead of generalizimg All Android Phones. There's too much Diversity in Android unlike Apple.
-
 NoMad134245yWe have successfully found the answer to "how many smart adults does it take to convince an egoistic teenager?"
NoMad134245yWe have successfully found the answer to "how many smart adults does it take to convince an egoistic teenager?" -
@theabbie Jesus fucking christ
Read this and shut up
https://source.android.com/security...
"yOu caNt gEnerAlIzE aNdrOiD" -
@AlgoRythm Yeah, Such services are shitty because they are doing nothing special. They can keep their database public and still it would be useless. They are not good at the only thing they are known for. That's not security, that's fooling people.
-
@100110111 Yeah I'm torn. This is the sort of thing that *shouldn't* be a big deal, but there's always that possibility of the wrong person getting the info and it becoming a VERY big deal. If OP won't listen to me here, maybe he'd listen to 64 students at his school yelling at him.
-
@PappyHans Then Give one reason why Apple not Hyped? What is so special about it? It's just Encryption, however complex it may be. They can't use that as a selling point when majority of their userbase has no technical background.
-
@theabbie how is Apple's encryption of less value than any other vendor's? Also, saying encryption isn't hard means you don't know donkey's sh*te about it (as you for sure are no expert on the matter)
-
@theabbie Yes they can. What are you smoking? Have you seen a *single* ad of Apple? Have you ever interacted with a single person *using* an iPhone?
-
@100110111 Then Please Give me the Required GIT command to do so, I am not that professional
-
@theabbie also, nobody cares whether Apple is hyped or not. It's completely irrelevant and not your original point. Stop arguing and fix your problem.
-
 NoMad134245y@100110111 the answer is "infinite number". 😛 Perfectly acceptable answer, theoretically.
NoMad134245y@100110111 the answer is "infinite number". 😛 Perfectly acceptable answer, theoretically.
I'm just worried this all may take a toll on him. Don't want his mental health going down the drain because of his ego. -
@theabbie funny coming from someone who has the gall to call themselves a full-stack dev...
-
@NoMad It takes 1 adult, but that 1 adult should be wise enough to admit that they can be wrong.
-
@theabbie I'm not punishing them. I'm not angry at you, either. But I sure am frustrated. Just stop arguing with us here, get to a computer, and remove those files.
-
@MySlugLikesSalt Well, Don't target them, They didn't argue with you, I did, Punish me
-
@theabbie I'm not targeting anybody. I'm trying to help you here, dude, as well as them.
-
@100110111 Have you even worked with Encryption? It might be the toughest thing in the world, but if many services are doing that, Apple is just one of them.
-
-
@theabbie you do realize what @MySlugLikesSalt is doing is punishing you, because the people whose contacts you leaked are likely getting a somewhat polite email letting them now you f'd up, but YOU are going to get a hell from them, most likely.. punishing and by extension helping
-
@100110111 GIT has nothing to do with your dev Skills, It's just a skill, And If you can't help, you're no good either
-
Just a side note: I got pretty worried when I saw the "videos" folder in the "love" folder...
-
 NoMad134245y@theabbie you're legally an adult now. No one is responsible for you. Your stupidity is your own, and so are the consequences.
NoMad134245y@theabbie you're legally an adult now. No one is responsible for you. Your stupidity is your own, and so are the consequences.
The problem is not others. It's your rigidid mentality. I for one am not going to admit wrong, because by all available logic known to men, you're not right.
Neither can you gaslight anyone to admit you're right, nor can you twist any arms. Become a monarch, maybe then someone would fear you enough to back you up. -
@theabbie I just sent you a link that lists the steps in detail, along with the gut commands
-
I have sent out an email and already received a response from one of the classmates. They did not give permission for their info to be posted, and are not happy. They will be trying to convince OP in person to fix the issue.
-
 NoMad134245y@theabbie you know what would be punishing them? Forwarding their info to a voice phishing company. Or worse, selling their info on the black market. Or even worse, sharing edited versions of those videos.
NoMad134245y@theabbie you know what would be punishing them? Forwarding their info to a voice phishing company. Or worse, selling their info on the black market. Or even worse, sharing edited versions of those videos.
This is why you need encryption and locks. -
@MySlugLikesSalt a painful lesson to learn, but an important one. OP claims this information is okay because it's what they already knew off the top of their head, but OP fails to realize that doesn't make sharing it okay.
-
@AlgoRythm That's not me, and yeah, It was last of a webpage built upon request by the concerned people. It's fine. They asked for it
-
@theabbie Really? Because Aaditee Pate said, among other things, "We weren't told or asked before our address was put up on the internet. We are saddened to see that one of our classmates has put our identity in threat. We will try to convince him."
-
 Creep16365y@theabbie there are like 12 people who where trying to explain it to you for a couple of hours already, I don't have to give you any other argument.
Creep16365y@theabbie there are like 12 people who where trying to explain it to you for a couple of hours already, I don't have to give you any other argument. -
@NoMad No one here gave a single valid reason why Apple is not Hyped, All they are doing is blindly following apple
-
... and I’m out of popcorn. Off to the store to restock for this yummy controversy 🔥🔥
-
@theabbie your classmates might disagree. I've seen 18yo dickwipes grow up into half decent human beings before, so maybe they can hammer some of that into you too. You are making a massive fool of yourself, you know?
-
@theabbie it might not have even been anyone here. Your shit is on one of the largest open source websites of all time. Your data is already stolen.
You have a local copy of the website right? DELETE your repository from GitHub RIGHT NOW. Take it down if you can't figure out the commands. You won't lose your code if you still have it on your computer, obviously.
You are literally already seeing the consequences of doxxing your classmates.
Make. Smart. Moves. -
 NoMad134245y@theabbie Apple is hyped and overpriced. But not because of security. We've been telling you this all-fucking-along. I bet most people in this thread are Linux users anyway.
NoMad134245y@theabbie Apple is hyped and overpriced. But not because of security. We've been telling you this all-fucking-along. I bet most people in this thread are Linux users anyway.
It's hyped because it has a pretty design, it is expensive, and it's easy to use for tech-illiterate users.
BUT NOT BECAUSE OF SECURITY OR ENCRYPTION OR INABILITY TO RESET PASSWORDS. -
@NoMad I dunno man, I almost needed to change my pants after I heard that you can't reset the password on an iPhone 11X
Oh god, I'm hyped just thinking about it.... Oh yes. -
 NoMad134245ySmall step for mankind, huuuuuuuuge step for @theabbie !!!
NoMad134245ySmall step for mankind, huuuuuuuuge step for @theabbie !!!
Congrats on growing some sense! -
Yes, apparently his friends convinced him to remove the data. He collected it from a college spreadsheet.
-
@MySlugLikesSalt Oh my fucking God he literally just exposed private information from a source that wasn't even his own lol. What possibly made him think that's okay?
-
I received responses from 4 or 5 different classmates. They were quite interested in this little bit of info... :P.
-
@PrivateGER Same, and I suggest anybody else here who has a local copy do the same. He fixed the problem, and we shouldn't continue it IMHO.
-
 NoMad134245y@MySlugLikesSalt you're one active fella! Good for you tho. Lazy people like me didn't even fucking bother...
NoMad134245y@MySlugLikesSalt you're one active fella! Good for you tho. Lazy people like me didn't even fucking bother... -
@PrivateGER @AmbientTea I know you guys have forked the Repository which still has the data, I did my Job, Now please act professional and delete your forks. That's enough lesson for me.
-
OP, usually very active in this thread, has now gone MIA. (Edit: he came back while I wrote this, lol. Still was gone for an abnormal amount of time)
I think his entire list of around 50(?) people may be calling him and voicing their concern personally.
As it would seem the data leak had origins from some sort of college spreadsheet, we should only hope OP doesn't get expelled for his stupid decision. Doxxing classmates is definitely a punishable offense with serious ramifications.
Sorry you had to learn the hard way OP. -
@MySlugLikesSalt I did my Job, Now please act professional and STOP, and maybe delete that info.
-
@theabbie What are you talking about? As I said, I've already deleted my copy of the information. I also requested that everyone else do the same.
-
@PrivateGER there were four forks of his repo when I last checked. None of them were mine, I'm not even logged in on my phone.
-
@PrivateGER Not you specifically, Whoever has that copy, bother to DELETE that, You don't have to be evil
-
@MySlugLikesSalt I don't think anyone will do that, Anyways, Please don't play any further games, I may face consequences, You guys are not evil, I learnt my lesson, I don't want to suffer more
-
 NoMad134245y@uyouthe and C0D4 might be the other two. And others who raised concern.
NoMad134245y@uyouthe and C0D4 might be the other two. And others who raised concern.
C0D4 is currently sleeping. Give him a few hours. (it's very early morning there) -
@theabbie I'm not doing anything further. I deleted the data that I had, and any classmates who are responding to me (which is about 7 of them by now) I am letting them know that you have deleted the data.
-
@MySlugLikesSalt Thank you so much, That was the maximum damage an internet stranger can cause, Maybe more, I am not challenging you
-
@100110111 I really don't like such a punishment, You guys ruined the Trust they had on me. No one does that to an internet stranger, especially over a stupid Rant
-
@NoMad @theabbie our worst fears are confirmed, OP's repo was forked by a bot
Doing a quick search for the repo name on GitHub reveals that https://GitHub.com/fossabot cloned his repo and it is now probably permanent... -
@theabbie We didn't ruin their trust in you. You did that by posting their personal information where I, a random person, could get it. I had no intention of telling them until you refused to delete it.
-
whoever has Github Username CarlosBeltranV please forgive me and delete the fork, I am already fcked
-
@AlgoRythm looks like maximum damage might hit OP after all spite of our best efforts...
-
@100110111 I was trying to correct my mistake, You guys didn't even give me a chance
-
@theabbie it does unfortunately sound like you may have learnt no lesson here, as I feared...
-
@MySlugLikesSalt I never refused to delete it, I was figuring it out but you did that Bombing before I could
-
@theabbie I don't have the patience to scroll through all the comments again but I am pretty damn sure people tried to convince you to take it down and you just kept arguing about Apple
-
@theabbie i think you’re missing the point again on this. You have no enemies here. Everyone was simply trying to help you, by pointing out what you had published. You were too busy arguing that this information is not useful and people already agreed to publish their personal details online. There is a lot worse that could’ve happened trust me.
-
@PrivateGER OP explicitly had an MIT license in the code, so he's fucked. No copyright claims possible there.
-
 kiki374865y@NoMad @theabbie
kiki374865y@NoMad @theabbie
I deleted it but I had everything. All your creepy CSVs, all your college photos, all your videos where you (it's clearly you, there is other data there that indicates that it's you in the videos) and your gf are having fun, all your data about people you exposed. I had everything.
You know what's funny though? You bashed Apple, and I use MacBook. Now I don't have your data but Apple still has because everything I delete goes into "recently deleted", that's iCloud and by extension Apple servers.
Good luck. -
@theabbie you told me that it wasn’t a big deal and I should stop overreacting. You told me that info didn’t matter. You told me you had their permission to post it. You continued to just argue about Apple. That all indicated to me that you had no intention of deleting it.
-
@PrivateGER @NoMad the CSV files are there
OP released his classmates data under an MIT license and a bot picked it up before any of us could even help out.
It's a nightmare. -
 NoMad134245y@AlgoRythm it does say a friendly bot. Maybe he could contact the maker/responsible body and ask them to delete?
NoMad134245y@AlgoRythm it does say a friendly bot. Maybe he could contact the maker/responsible body and ask them to delete? -
 NoMad134245y@theabbie dude, I'm not on a computer. I can't see jackshit. You have to be specific.
NoMad134245y@theabbie dude, I'm not on a computer. I can't see jackshit. You have to be specific. -
 kiki374865y@scout a guy fucked up and exposed everything he had to the internet and it spread around, things like he and his gf vids and creepy CSVs with some random people personal data. He did it while arguing about how bad Apple security is and how he can invent a better one
kiki374865y@scout a guy fucked up and exposed everything he had to the internet and it spread around, things like he and his gf vids and creepy CSVs with some random people personal data. He did it while arguing about how bad Apple security is and how he can invent a better one -
@NoMad if it were me, I would already be panic typing my apologetic essay to any contact information I could find, pleading for help and forgiveness.
-
@scout and for some reason he released it under MIT and then a bot picked it up so now his classmates are all doxxed until the owner of the bot is polite enough to help (if they do)
-
 NoMad134245y@AlgoRythm I don't expect that much sense from him. He's probably already in the state of panic anyways.
NoMad134245y@AlgoRythm I don't expect that much sense from him. He's probably already in the state of panic anyways. -
@uyouthe You can delete that Right? Please don't take this any further, I was fixing that but these guys did it before I could do anything.
-
 kiki374865y@theabbie I can’t, it’s on the Apple servers now. I don’t know what apple does with that data now. I don’t have it anymore.
kiki374865y@theabbie I can’t, it’s on the Apple servers now. I don’t know what apple does with that data now. I don’t have it anymore.
You better believe now that Apple security and privacy policy are good. How ironic -
@theabbie A bot has forked your public repo under the MIT license. You're out of luck, better hope nobody else ever stumbles across it. Maybe send a mail to the bot owner.
-
 NoMad134245y@theabbie he's being a dick. @uyouthe's dick pics and your info are all in one trash. And Apple can't expose personal data even if it's in trash. (ironic, I know)
NoMad134245y@theabbie he's being a dick. @uyouthe's dick pics and your info are all in one trash. And Apple can't expose personal data even if it's in trash. (ironic, I know) -
 kiki374865y@theabbie you could do it when I was texting you here eight hours ago or so about how you’re gonna go to jail. You had enough time
kiki374865y@theabbie you could do it when I was texting you here eight hours ago or so about how you’re gonna go to jail. You had enough time -
@uyouthe it's ironic, but also the least of his concern right now haha
Current status: still snatched up by a bot. -
@scout dude talked shit about apple and security revealing total ignorance. Someone found a lot of personal data of his classmates stuffed into his homepage files, including addresses emails phone numbers and some girls height end weight (!). He refused to remove them claiming he got permission and proceeded to talk shit for hours. @MySlugLikesSalt sent a bulk email informing these people and they responded. The kid removed the data from the repo but he had it on MIT LICENCE so some boy forked it already.
-
@theabbie well maybe you should not have that kind of information up in github in the first place? I know you're young, arrogant, ignorant, hard headed and a noob, but that's just common sense. I am sincerely sorry you'll have to go through learning the hard way, but if that's what it takes then it is what it is. The most valuable lessons are often learned via hardship, and yours haven't likely even started yet...
-
I've already emailed the fossabot owner to request they take down the repo. If OP won't try to protect his classmates data then I frickin' will.
-
 NoMad134245y@uyouthe I'm mildly amused and can't believe anyone on onlyfans would pay to see yours. But oh well ¯\_(ツ)_/¯
NoMad134245y@uyouthe I'm mildly amused and can't believe anyone on onlyfans would pay to see yours. But oh well ¯\_(ツ)_/¯ -
And also, I don't know how GitHub.io works very well, but your site is still available.
Maybe it takes some time to come down or something.
But https://theabbie.github.io/ is still out there -
 kiki374865y@NoMad you’re just like abbie, talking about what you know nothing about. Femboy is extremely popular thing there
kiki374865y@NoMad you’re just like abbie, talking about what you know nothing about. Femboy is extremely popular thing there -
 NoMad134245y@MySlugLikesSalt awww 💞 that's very nice of you. Even if OP doesn't appreciate your active defending, I have to say, you've restored my faith in humanity.
NoMad134245y@MySlugLikesSalt awww 💞 that's very nice of you. Even if OP doesn't appreciate your active defending, I have to say, you've restored my faith in humanity. -
Thank you whoever sent the second email, If you had not sent the forked link I could have told github to remove it before anyone would find out, Now, they are more concerned
-
@theabbie Github can't legally remove it, you set the MIT license. Anyone that has forked legally owns your code.
-
@theabbie secrecy is not the answer to a data leak.
Imagine you were in their shoes. You would want to know that the issue is still present, correct? -
@NoMad, I have now officially become a @MySlugLikesSalt fanboyo, however it requires much more than that to restore my faith in humanity
-
 kiki374865y@theabbie I can restore data. I can delete data so I don’t see it anymore.
kiki374865y@theabbie I can restore data. I can delete data so I don’t see it anymore.
I can’t guarantee though that the data is really gone from Apple servers -
@NoMad yes, I'm fucking laughing my ass off. The article is incomprehensible too.
A link for the curious mind...
https://theabbie.github.io/blog/... -
 kiki374865y@AlgoRythm fuck that blog is hilarious. A very good addition to OP's CV when he wants to get a job in any modern company, especially the inclusive startups
kiki374865y@AlgoRythm fuck that blog is hilarious. A very good addition to OP's CV when he wants to get a job in any modern company, especially the inclusive startups -
There was also cv where he wrote he wrote he was ceo of his own webpage for 5 years.
-
@theabbie maybe you can show Apple your face and they'll let you in on your data since it's identifiably yours?
-
 NoMad134245y@100110111 @AlgoRythm
NoMad134245y@100110111 @AlgoRythm
"how to become a 9gagger"... I can't believe my eyes... I'm officially done here. -
I can still see 2 forks
https://github.com/CarlosBeltranV/...
https://github.com/SnA2502/...
If possible remove it whoever owns it -
-
Why did OP's shitty data leak get more forks than any of my projects ever have? 😂😂
-
Fossabot seems to belong to a company, it should be possible to convince them to drop the repo.
-
@theabbie they seem all to be forked from the botfork, so good luck with that. You, kiddo, are f'd.
-
@AmbientTea yeah but you would need to also contact those other people that forked it from the bot
@100110111 is just totally correct. At this point, the data is leaked. Those people who forked it have the data on their local machine.
It's over OP. No more way to fix it. Just hope for the best. -
@AlgoRythm right? i got one star and no fork. all I should've done is leak phone numbers of the people who still talk to me.
-
@AmbientTea Yeah I'm hopeful they will as well. I emailed GitHub support about the other two forks. I'm sure they won't/can't do anything, but I'm hoping that they have some sort of clause in the ToS that would allow them to remove the repos.
-
@AlgoRythm So long as they keep all their cloned repos locally, yes. I sure don't. OP can only cross his fingers that they don't, either.
-
 NoMad134245y@AlgoRythm a) peaked interest today. b) most likely had ongoing commits, which made it look like legitimate open source work.
NoMad134245y@AlgoRythm a) peaked interest today. b) most likely had ongoing commits, which made it look like legitimate open source work. -
@MySlugLikesSalt I'm pretty sure storing personal data in a repo that you haven't acquired permission to is illegal even without ToS, so I'd expect github support to take action if any human sees your message. Not 100% sure tho.
-
@Linux Attempted to. Then we found a CSV file and a fuckton of personal info of others on their website repo. So...
-
@AmbientTea I hope so. I also pinged them on Twitter so a human hopefully sees it.
-
@Linux lol.... You are so late to the party... Welcome to the most disappointing but entertaining thread in the history of devRant
-
@F1973 and I hope he has a big apology planned to his classmates.
I'm sure many of them barely even know him. -
@AlgoRythm I did not think this could become more entertaining than OP's yesterday's JS thread, but my oh my was I wrong.
-
-
@-red They're very real. I've been corresponding with a bunch of them for a couple hours now.
-
@-red people like OP are the reason I sometimes think not everyone should have access to the internet...
-
 NoMad134245y@Jilano I SEE THAT YOU JUST GOT HERE! READ THE WHOLE FUCKING THING. DON'T MISS A FUCKING COMMENT OF THESE 550+ COMMENTS!!!
NoMad134245y@Jilano I SEE THAT YOU JUST GOT HERE! READ THE WHOLE FUCKING THING. DON'T MISS A FUCKING COMMENT OF THESE 550+ COMMENTS!!! -
@-red oh shite...@MySlugLikesSalt there are indeed 149 other people whose contact info is compromised (some may be same)... Oh wow. @theabbie, seriously?
-
@MySlugLikesSalt and phone numbers. But you are right, nowhere near as bad as with addresses and everything
-
@100110111 Wait, maybe it's a different file than I saw? The one I saw only had names and a couple addresses. No contact info.
-
@100110111 Yeah that's what I saw. Maybe I didn't scroll far enough. I saw just names and a couple addresses.
-
 NoMad134245y@AlgoRythm oh, no one could see where this could end... Even I learned valuable lessons in humility and data security.
NoMad134245y@AlgoRythm oh, no one could see where this could end... Even I learned valuable lessons in humility and data security. -
@PrivateGER Yep, that one was creepy. I mentioned her specifically in my email, and told her there's even more info on her out there such as family and more.
-
@MySlugLikesSalt you need to scroll to the right for the numbers...🤦♂️ oh god save us
-
FWIW I did send this thread to multiple victims who requested it and I know some of them at least are reading it :).
-
 NoMad134245y@Jilano because of excitement. But seriously, read the whole thing. It's a whole Mahabharata about security.
NoMad134245y@Jilano because of excitement. But seriously, read the whole thing. It's a whole Mahabharata about security. -
@AlgoRythm I was expecting plain text passwords accompanying the user names because OP has trouble remembering their passwords....
-
@theabbie ... and they had every right to ask and every right to read, and every right to come at you with pitchforks.
-
Guys this rant literally crashed my phone. Last thing I remember is seeing my comment duplicate itself 3x
-
@rgab1508 Are you one of the affected? My condolences... I would almost pay money for you to post about your side of things
-
@rgab1508 Oh hey I know who you are :). Good to know you're keeping an eye out here so you know what's going on...
-
 rgab1508155yThis data was collected by the college in google sheets which was open
rgab1508155yThis data was collected by the college in google sheets which was open
So anyone can see the data of others
if they had the link of the sheet. -
@theabbie we are nice people. We could have done SO MUCH MORE DAMAGE to you (and you would have deserved it, as @F1973 pointed out), and to THE VICTIMS (which would DEFINITELY NOT have deserved it)... if this leak ends up causing THEM some real damage, they would be well in their rights to drag you into court and get you jailed (and would be even know - if my personal info had been leaked like this, I'd make sure you'd at least be paying a substantial fine if not going to jail - and if it had been a loved one of mine whose info was leaked like this, your parents would be lucky to see you again, alive)
-
@rgab1508 Like *anybody* in the world if they had the link, or just students if they had the link?
-
@rgab1508 Wooowwww big yikes! At least it's not discoverable that way, but still not good...
-
@rgab1508 So your school just releases this information.
Now I know why OP is so misinformed about his ideals.
He has been sparking much controversy here, though. His posts have attracted more comments than any others in recent history.
Mostly because of his bone-headed and stubborn nature -
 kiki374865yhttps://theabbie.github.io/sitemap.... is still accessible. There is no need for forks. I have no words.
kiki374865yhttps://theabbie.github.io/sitemap.... is still accessible. There is no need for forks. I have no words. -
@uyouthe I did everything from my end, The damage can't be restored, I did a great mistake, That's a lesson that will remain for life
-
@theabbie MIT License doesn't suck per se, just that no one even remotely informed would in their right minds willingly have their private website under MIT.
-
@theabbie in the future it might be a good idea to study such things before doing possibly idiotic things. Study, kiddo, study humbly.
Also, one key takeaway from the last few days worth of threads would be to start listening to the pros. Especially when there are a dozen plus of us agreeing with each other. We are not here to be mean, or to belittle you, or whatever you may believe, but mainly to help each other in this community of hours... That said, you still convinced we are wrong about security or JS? -
@F1973 I'm not convinced. That would imply the ability (or willingness) to comprehend what they were reading...
-
 kiki374865yThere are guys like @Root or @linuxxx who know a shit ton about cybersec. But instead of asking them and possibly getting three weeks of studying worth of information in one comment you decided to be a dick
kiki374865yThere are guys like @Root or @linuxxx who know a shit ton about cybersec. But instead of asking them and possibly getting three weeks of studying worth of information in one comment you decided to be a dick -
 Root772335yI took a look through all of the sensitive data you posted (without permission) before you deleted the repo — not that it matters with all of the clones and forks out there.
Root772335yI took a look through all of the sensitive data you posted (without permission) before you deleted the repo — not that it matters with all of the clones and forks out there.
Were I a more evil person, @theabbie.
I might check in on you again at some point, just to see if you actually have learned anything. For now, I’ll keep your contact info naïvely secured behind a nice, useless, unbreakable lock, okay? -
@theabbie Don't take any of what happened today as anybody here hating you as a person. We don't hate you. We hate what you did with that info. The best you can do is to think things through more thoroughly going forward.
-
@Root Great, I hope my classmates would forgive me, Though damage is permanent, So is the lesson, I should stop treating GitHub as cloud storage. In the end, I would like to admit that I was the only idiot here.
-
@MySlugLikesSalt I wish you had given me atleast a FINAL warning before that EMAIL BOMBING, Anyways, I deserved it
-
Congratulations guys, All the Forks have been disabled, Now it is only with people who had created local clones, You are good people, you won't mess with it, I know, Now, the damage has been Restored, Thank you for letting me know That I am an idiot, Had great time here. See you tomorrow with another Stupid Rant.
-
Well, that was a fun 1 hours read...
Hi, OP! I'm Linuxxx, one of the oldest devRant members. I currently work as a cybersecurity engineer and have been a cybersecurity person (not official) for about 10 years now.
For everyone who said that apple has good encryption; I don't agree since I can't check. The source code is proprietary so we can't check shit.
I do NOT mean that (assuming they're right about their encryption for a moment) they're implementing it wrong, the best encryption is encryption you cannot bypass with password resets and such. Sucks for the user if they lose their password? Of course, but otherwise the encryption would be completely fucking useless.
I can't say for sure OP doxxed people because waaaaay too many comments but if this is true, shame on you. Taking the choice of data sharing away from someone is quite the level of privacy violating, not even close to okay.
Feel free to ask questions!
Oh, and, @Root was right about pretty much everything. (not sure if she said a positive thing about apples encryption but if she did, she knows why I disagee) -
Tomorrow we learn that @theabbie has all of the world's nuclear codes sitting in plain text on his desktop.
-
@linuxxx Yeah, pretty sure phone numbers, addresses, dates of birth, email addresses, and some photos/family info qualifies as doxxing :P
-
@linuxxx Thank you sir for your wise words, You are the most senior here and your response was exactly what I expected from an experienced guy. Atleast you didn't Blindly assume Apple is great. But, It does mean that Apple is given more credit than it deserves.
And, I am blessed to have been abused by you. I have already admitted that I am an Idiot.
I had agreed with @Root earlier, She's the 2nd most experienced person here, atleast in this field.
If you had come earlier, this discussion would've ended in a far better way and not with that EMAIL BOMBING, That shit will stay forever.
Thank you so much
Regards,
Abhishek (IDIOT)
18 year old -
@theabbie I want to politely remind you that the email bombing wasn't the bad thing to happen here. In a way it was good that na authority figure like @linuxxx came a little late to the party so we had time to notice the sensitive data put there and kind ser @MySlugLikesSalt here had the time to save your ass.
-
@theabbie
Firstly, I might seem rude/mean towards you in this message but I wouldn't take that as a personal attack, just trying to teach you something. Now;
Hi! I'm not sure if you should call me a senior (but I get what you mean anyways, thank you!). I might seem old but I'm only in my mid twenties and professionally rolled into this job/world about half a year ago (without any degrees or whatever on this).
As for assuming something is great or not, I do my research and make a judgement based on that. I personally actually see apple as a privacy-hostile company, although that opinion isn't widely shared haha. Also their prices are completely batshit insane if you ask me.
Now, here comes the teaching part, and since I find it very hard to 'not be nice', this is going to be a hard one for me 😅
When I looked through the comments I repeatedly noticed that when people come with great arguments (pretty much everyone but you), they're made out for not knowing about the subject or only half doing so. To be fair, they're way more knowledgeable on this subject (encryption, privacy and security) than you.
But, you can learn! I started out as Facebook, Instagram, WhatsApp, Telegram and-you-name-it user, but now that I'm (both personally and professionally) way more knowledged (however you say that) about this stuff, I've ditched loads of services and pretty much swear by what I consider highly secure services like Tutanota.com, Signal and any service which is transparent, provides open source (verifiable) software and has a privacy/security-first design.
If you'd have questions regarding these subjects or want study material or whatsoever, feel free to mention me and ask! -
@100110111 @theabbie I came late to the party since I had an 11 hour workday without a break so I need a liiiittttttleee rest 😅
-
@100110111 But as he admitted, a final warning would have been better. Data is only erased from Github, How will I erase it from My classmate's minds? I still have no Idea How much wrong stuff I might have done that is still undiscovered. Anyways, Be ready for tomorrow's Rant. From Now On, I will make sure to do proper research before Making any Bold statement.
-
@linuxxx Then Tutanota.com, Signal and other services like that are equally good in such Encryption but Apple takes all the limelight. That is what Bugs me. It's given more Hype.
-
@linuxxx It's their selling point, It is one of the only good things people like about it. Tutanota.io or other services never say that they are very secure and unbreakable. Apple is secure, But it's not the only feature that should be considered. Majority of Apple's userbase doesn't have technical background, They will assume Apple does some magical Encryption whereas other services are not safe. That's not true. Other services can do this too, but They consider that Users may mess up. They take some responsibility of your data. And If your service can see your data, it is not that bad because you have to trust the service. They have numerous ways to use your data. Giving people an illusion of security is the only thing Apple is good at.
-
@theabbie tutanota literally describes itself as 'world's most secure email service' on it's webpage, so you're once again talking out your ass claming they 'never say that they are very secure'.
-
@theabbie It seems like you still don't get my point so let me explain;
Apple does encryption and its not magical, it's maths (again, if this is actually true).
They CANNOT reset passwords or whatsoever related to encryption because if they could, there wouldn't be strong encryption.
This actually makes services like Tutanota more responsible as for my data if you ask me. Because, this means that I'm fully in control.
The second that encrypted products/services would offer passwords resets, all your privacy/security senses should go crazy.
Not being able to provide password resets with encrypted products/services is a huge WHITE flag and taking responsibility.
And if you'd rather have password reset abilities then I'd advice you to not use strongly encrypted services. -
@linuxxx As I had pointed out earlier
It can be either security or usability, Not both
Users are responsible for their data, Apple takes no responsibility of your data.
And, If you have a bad memory, write password somewhere.
I think it's mathematically impossible to have an Encryption that is controlled by user but can be resetted.
So, Apple is doing great. But some people prefer usability while compromising security, Such people should Avoid Apple. -
@theabbie I agree with everything from your last comment except for the usability vs security part. Of course you can have both!
-
@AmbientTea If everyone uses PGP keys there is no need for a secure Email service. You could exchange public keys and send that data through any medium.
-
@linuxxx By usability, I mean ability to reset your password if at all you can prove that you are the owner. The Closest Apple can get to that is to store all passwords in Antarctica and if you forget it, Someone will be sent to Antarctica to get your password if you prove that you own that IPhone.
-
My eyes are tired, my neck is a bit stiff and I've run out of popcorn, but this was one hell of a rant. Good job @MySlugLikesSalt and everyone else.
-
@theabbie you use the term usability in quite a skewed fashion. As far as I'm aware, there is absolutely no need for a tradeoff between security and usability. You can definitely have both.
-
@100110111 If you mean that you can forget password and still get your data (on proving ownership) Then that's mathematically impossible, Especially if it's actual Encryption.
-
@theabbie I'd recommend you study some security best practices, and you might find that your problem isn't really much of an issue at all (or at least nothing any half decent cybersec semo-professional couldn't implement). Or if you're lucky and @linuxxx isn't too tired to, they'll kindly enlighten you on the matter. I'm not half as good at explaining it, otherwise I'd try myself
-
@theabbie I understand this isn't easy for you now. Therefore I would strongly suggest to seek psychological help from a therapist.
So that you have somebody to talk about what happened here.
And this maybe hard to comprehend for you but I think you may suffer from narcissism. Narcissism creates great suffering to the people around you, while you think you're the greatest person around. Please Please seek professional help to support you in this moment.
https://en.wikipedia.org/wiki/...
Narcissism - Wikipedia
Best of luck! 🙂 -
 C0D4644185y@NoMad, my copy was deleted when I emailed him wayyyyy up there in the comment mountain when I first found those files, I do not keep sensitive information like that, it scared the shit out of me when I stumbled on it.
C0D4644185y@NoMad, my copy was deleted when I emailed him wayyyyy up there in the comment mountain when I first found those files, I do not keep sensitive information like that, it scared the shit out of me when I stumbled on it.
The fact it's been several hours later and it took contacting the individuals who's data was leaked to start being this down is astonishing.
@MySlugLikesSalt thank you for the overnight shift, I'm glad someone got through to @theabbie in the end.
@theabbie, ok sorry you had to go through this ordeal, but next time, stop arguing when you have been contacted directly well before this escalated and told to remove that content indirectly linked too.
It's a lesson that I hope sinks in deep with you going forward in life, some arguments aren't worth it when there's a back door into confidential information. -
 scout25095y@2Large he isn’t some rich kid, coz earlier he was begging for clicks on ads on his page and has more number of donation accounts than the number of projects. <sorry for being mean but he insisted on being fine with this begging so much>
scout25095y@2Large he isn’t some rich kid, coz earlier he was begging for clicks on ads on his page and has more number of donation accounts than the number of projects. <sorry for being mean but he insisted on being fine with this begging so much> -
 Kimmax106835yYoooooooooooo
Kimmax106835yYoooooooooooo
What the hell is this abomination of a thread, so many up and downs, hell get Michael Bay to make a movie out of it -
Just to update, Fossa has confirmed that they’ve gotten rid of their copies of the data.
-
@cabbybaby narcissists are indeed unable to do that or will have a hard time to admit to be wrong.
And as far as i see it in this rant he doesn't regret what he has done, he just regret the repercussions he'll face by his doxed students. -
 JhonDoe27325y@AmyShackles I missed it too... actually I came from this other rant (after party rant) https://devrant.com/rants/2952705/...
JhonDoe27325y@AmyShackles I missed it too... actually I came from this other rant (after party rant) https://devrant.com/rants/2952705/...
but welp, glad to see you around 😂 -
 Root772335y@heyheni Thats the gist.
Root772335y@heyheni Thats the gist.
I’m going to check on him sometime in the future to see if he’s changed any. I sincerely hope he will have, but I also very much doubt it.
Honestly, though, I hope I won’t be able to find him. It’ll save me a lot of effort and anger. But considering he shared like ten thousand online accounts ... 🤦🏻♀️ -
@heyheni Hmmm. I guess narcissism is the explanation of his other rant -- https://devrant.com/rants/2946011/...
Damn. Twas the first time I encountered people like him on devrant -
 Linux429875y@theabbie
Linux429875y@theabbie
It is Hard not to stalk someone that basically push that information up in my face on page 1. -
@Linux As per these people, Reset Password is a backdoor, Mastodon allows resetting Password, Does that mean my data isn't safe on Mastodon?
-
@theabbie You really need to work on your reading comprehension if that’s what you took away.
-
@AmyShackles Stop being 2 faced, I was clearly mentioned That Reset Password is a Backdoor which can be exploited. Even if Mastodon keeps data encrypted, it is not encrypted by user's password, That means user don't have complete control over their data, Mastodon would be able to see it. Correct me If I am wrong.
-
 Condor315485yI don't know if I'd be able to explain it to someone so dense, but the simple answer would be that you have an Excel file for a database (because at that level of competence of course you do), that you store in 1 column the usernames, and in the other the passwords. Now how do you store and change them?
Condor315485yI don't know if I'd be able to explain it to someone so dense, but the simple answer would be that you have an Excel file for a database (because at that level of competence of course you do), that you store in 1 column the usernames, and in the other the passwords. Now how do you store and change them?
One way could be to store them as-is, with a fixed max length. Sprinkle in some limitations on what characters you can use too.. reasons. I don't wanna get too techy here, I feel like I'm explaining this to my grandmother. Don't be my grandmother and maintain databases.
Another way would be to convert that password into something that represents the password. Like 1+1=2 and you can store either "1+1" or "2", where 2 only represents the data you've given. And as long as 1+1 is always 2, the system works.
To reset you could give a different sum, say you wanna change it to 1+2=3. Once verified, feel free to change it. And the Excel file doesn't need to know that 2 was made up of 1+1. -
 Linux429875y@theabbie
Linux429875y@theabbie
No, I am not able to see you password.
You clearly do not have a single clue on how software works. -
@Condor That does mean that data is not encrypted, I know that access to database is authorised, But it's not completely in my control. The Database Administrator can see my data. Even if database is encrypted, DBA can see that. That does contradict the idea of Encryption.
-
 Condor315485y@theabbie you don't encrypt passwords unless you're my stupid ISP. Encrypted databases will always have the key available to the server, probably on the same system too. What you care about is when (not if) the database gets stolen. What stops the attacker from taking the key too? So you hash your passwords, which the little sum thingies attempted to showcase. I think I already mentioned it and am sure many others did too, but read up on cryptography and hash functions, seriously. Everyone thinks you're an idiot at this point.
Condor315485y@theabbie you don't encrypt passwords unless you're my stupid ISP. Encrypted databases will always have the key available to the server, probably on the same system too. What you care about is when (not if) the database gets stolen. What stops the attacker from taking the key too? So you hash your passwords, which the little sum thingies attempted to showcase. I think I already mentioned it and am sure many others did too, but read up on cryptography and hash functions, seriously. Everyone thinks you're an idiot at this point. -
But the idea of Encryption is that no one other than the owner should be able to see their data. Neither attacker nor the service. Before pointing out that this is wrong, This was stated by @Root
-
 Condor315485yJust to be clear btw since this is grandma level stuff now, the passwords you store in a database are different from the data you store on a phone. One is hashed, the other is encrypted. On Android that would be full-device encryption (FDE) for older systems, while for newer ones it's file-based encryption (FBE). The internals are probably too much to handle for either you or me, and certainly for you and me. I won't bother you with that, go read the docs on https://developer.android.com for that. Whatever black magic Apple uses, ask them and they probably won't say.. so yeah. But suffice it to say that your user data and a password are stored very differently.
Condor315485yJust to be clear btw since this is grandma level stuff now, the passwords you store in a database are different from the data you store on a phone. One is hashed, the other is encrypted. On Android that would be full-device encryption (FDE) for older systems, while for newer ones it's file-based encryption (FBE). The internals are probably too much to handle for either you or me, and certainly for you and me. I won't bother you with that, go read the docs on https://developer.android.com for that. Whatever black magic Apple uses, ask them and they probably won't say.. so yeah. But suffice it to say that your user data and a password are stored very differently. -
 kiki374865y@AmyShackles please don’t let him bring YOU into this. You did nothing wrong to deserve it
kiki374865y@AmyShackles please don’t let him bring YOU into this. You did nothing wrong to deserve it -
Holy shit, this kid is still going. Shouldn't you be getting your ass kicked by your parents by now?
-
The fuck is this garbage here.
Apple may not be the nicest company but what the fuck. -
I would like to thank everyone who took part in this one-sided discussion. I would also like to thank some special appearances who shared their expertise.
I also suggest everyone to get back to there lives and do something productive, This is a never-ending discussion and I officially terminate this.
You can also use this discussion as an proof that 1 idiot can keep many smart people busy for a long time.
I learned a lot, thank you for that. -
 kiki374865y@theabbie what you did is you caught a smart guy, pulled his pants off, started sucking his dick and when you finally swallowed, you ran away screaming HA HA HA NOW YOURE GAY
kiki374865y@theabbie what you did is you caught a smart guy, pulled his pants off, started sucking his dick and when you finally swallowed, you ran away screaming HA HA HA NOW YOURE GAY
That’s not how it works. -
 Linux429875yThe problem is that OP did not learn a thing - since he already think that the knowledge he has is SUPERIOR
Linux429875yThe problem is that OP did not learn a thing - since he already think that the knowledge he has is SUPERIOR
Good luck getting a job kid, -
@uyouthe People should learn that arguing with a stupid person makes you more stupid while the stupid person neither gains nor loses anything. The correct way to end this discussion was to find appropriate sources just post it here and tell, "this is all you need", and never return back to this rant. And I admit that most of my statements were wrong. That did teach me something. No need to reply to this.
-
 Linux429875y@theabbie
Linux429875y@theabbie
> And I admit that most of my statements were wrong. That did teach me something
Well I take back my previous comment. Since you actually admit to being wrong.
And being wrong is normal, -
On Doing Text Analysis of this Discussion, These were the words with most frequencies
: 665
the: 589
you: 582
to: 505
is: 431
i: 431
and: 429
a: 396
it: 355
that: 343
of: 297
not: 250
your: 210
this: 200
1d: 196
if: 188
theabbie: 187
for: 182
theabbie: 182
161: 182
in: 178
but: 178
are: 174
have: 167
be: 165
0: 163
data: 150
its: 140
they: 139
on: 138
with: 122
can: 113
17h: 111
so: 110
just: 108
apple: 104
encryption: 100
what: 97
about: 94
dont: 94
my: 93
security: 91
was: 89
16h: 89
one: 87
do: 86
as: 83
all: 82
or: 81
people: 81
4: 81
password: 78
me: 77
no: 77
even: 76
more: 75
2: 75
know: 72
would: 72
an: 71
im: 71
their: 70
at: 70
like: 69
100110111: 69
869: 69
there: 67
3: 67
some: 66
good: 66
he: 64
now: 63
18h: 63
we: 61
because: 60
them: 60
by: 59
here: 59
from: 59
his: 59
6: 57
still: 56
1: 56
thats: 55
f1973: 55
2611: 55
has: 54
any: 53
nomad: 53
5799: 53
nomad: 51
mysluglikessalt: 51
491: 51
then: 50
should: 49
5: 49
7: 48
could: 47
had: 47
Many more But Character Limit -
will: 46
point: 46
why: 46
how: 46
up: 44
wrong: 44
did: 44
23h: 43
when: 42
algorythm: 42
47355: 42
get: 41
only: 41
too: 40
am: 40
out: 39
other: 39
100110111: 39
f1973: 39
access: 38
right: 38
op: 38
mysluglikessalt: 37
also: 36
cant: 36
make: 36
youre: 36
need: 35
way: 35
doesnt: 34
who: 34
very: 33
everyone: 33
being: 33
algorythm: 33
email: 32
such: 32
than: 32
key: 32
see: 32
19h: 32
use: 31
might: 31
already: 30
think: 30
which: 30
much: 29
yeah: 29
sure: 29
say: 29
reset: 28
been: 28
users: 28
everything: 28
does: 28
someone: 28
well: 28
things: 27
user: 27
thread: 27
many: 27
take: 27
privateger: 27
18211: 27
usability: 26
really: 26
anyone: 26
info: 26
uyouthe: 26
12355: 26
want: 25
same: 25
were: 25
ambienttea: 25
694: 25
him: 25
secure: 24
thing: 24
rant: 23
never: 23
phone: 23
keys: 23
mean: 23
8: 23
shit: 23
nothing: 23
20h: 23
15h: 23
service: 22
passcode: 22
better: 22
root: 22
where: 22
maybe: 22
give: 22
own: 21
comment: 21
without: 21 -
doing: 21
anything: 21
else: 21
function: 21
please: 21
read: 21
time: 21
something: 21
enough: 21
actually: 21
comments: 21
bad: 20
encrypted: 20
means: 20
got: 20
going: 20
fucking: 20
done: 20
find: 19
root: 19
66944: 19
prove: 19
services: 19
may: 19
information: 19
before: 19
privateger: 19
9: 18
admit: 18
10: 18
able: 18
person: 18
since: 18
passwords: 18
these: 18
simple: 18
didnt: 18
uyouthe: 18
help: 17
first: 17
stop: 17
said: 17
isnt: 17
open: 17
c0d4: 17
theabbie: 17
trying: 17
found: 17
most: 17
hyped: 17
delete: 17
oh: 17
2: 16
js: 16
keep: 16
number: 16
lot: 16
lose: 16
wont: 16
c0d4: 16
58528: 16
saying: 16
store: 16
those: 16
into: 16
guys: 16
go: 16
discussion: 16
while: 16
back: 16
responsibility: 16
id: 15
privacy: 15
fine: 15
hard: 15
either: 15
damn: 15
ambienttea: 15
pretty: 15
arguing: 15
24h: 15
21h: 15
post: 14
must: 14
us: 14
though: 14
again: 14
root: 14
yet: 14
reason: 14
sbiewald: 14
3659: 14
great: 14
yes: 14
correct: 14
github: 14
page: 14
22h: 14 -
 Prakash3675yTL;DR: The same guy tries to steal credits, lists himself as a master of over 30 talents in IMDB
Prakash3675yTL;DR: The same guy tries to steal credits, lists himself as a master of over 30 talents in IMDB
Apparently, this is the same guy as mentioned in https://mumbaimirror.indiatimes.com/...
He tries his best to steal credits as well as exploits loopholes for his personal benefits. Here's how Varun Grover puts it:
"He thinks of himself as some sort of a vigilante, exposing loopholes in a system. Also, the joy of cheap thrills is difficult to resist. So I believe it’s a mix of everything"
Now I really feel that we shouldn't have done the E-Mail blast. We should've reported this nigga to crime cell.
@root @100110111 @AmbientTea -
@theabbie No, password reset abilities are not backdoors by default, it depends on the context/technology.
In the case of encryption, the cipher text is mathematically dependent on the key for decryption. If it's not or you can bypass that, it's called a backdoor (or frontdoor).
In the case of a mastodon password reset, it has nothing to do with mathematics (not calculating the hash in) as your account access does not depend on mathematically related keys, simply on a few database values and some if/else statements.
Since YOU are supposed to be the only one in control of the email account the reset link is sent to, the application can assume that sending that link to that email address would mean that YOU are the only one with access to that reset link and thus it can be safely assumed (depending on one's threat model of course) the right person/identity regains access to the right account. -
 NoMad134245y@Prakash nah. Still a criminal in the making. He hasn't harmed anyone yet, but nobody knows.
NoMad134245y@Prakash nah. Still a criminal in the making. He hasn't harmed anyone yet, but nobody knows.
If he is capable of going to a psychotherapist (although, I personally doubt. Such narcissists usually fail to commit to a therapy) he might be able to change course. We gave him another chance. Let's see how far he goes. Next one, sure. We can easily persuade the victims to take legal action. -
@theabbie Also, usability is subjective so you can't assume that an app/service/device had bad usability if ONE person has an issue with the non-existing cryptographic password reset.
Compare it to the fact that I find the CLI very usable but I wouldn't ask an administrative person who sips from their soy-extra-caramel-latte all day to find a CLI usable... -
@linuxxx It's not a backdoor, I know that, But it can be read by whoever controls that database, Though not by any attacker. And I am not saying that it's not safe, But, If true Encryption means literally no one other than user should have access to data, then that's not the case in Mastodon (or any service of that sort).
-
@theabbie Yeah of course, who said mastodon uses encryption this way?
It hopefully uses hashing but that's it I presume (hashing is one-way cryptography (and NOT encryption)) -
@linuxxx Hashing is for password verification, So, yeah, If Server gets compromised All data will be gone, but, not the passwords
-
Also, true encryption does not mean that ONLY the user should have access to the data, that depends on the encryption algorithm and how the application is built. (take PKI for example)
But, when talking about THIS scenario, yeah, it means that only the user who hold the key should have the encrypted data access -
@theabbie Last comment is correct! IF a good hashing algorithm is used and users don't use passwords like 1234 or password or such 😅
-
@Root After the last two days, I actually didn't even blink at that. More of just a "yeah sounds about right" reaction.
-
 Root772335y@theabbie There are several gigantic messes that are your responsibility. If you continue this thread, no doubt we will uncover several more.
Root772335y@theabbie There are several gigantic messes that are your responsibility. If you continue this thread, no doubt we will uncover several more. -
 Root772335y
Root772335y -
@Root
> There are several gigantic messes that are your responsibility. If you continue this thread, no doubt we will uncover several more.
Sure, Go on -
 Root772335y@MySlugLikesSalt Eh. I kinda think this one would be worse if given access to power. So maybe not. 🤔
Root772335y@MySlugLikesSalt Eh. I kinda think this one would be worse if given access to power. So maybe not. 🤔 -
"I was jealous of not being famous,” says Chaudhary
@theabie you know where this ends?
You murdering Bollywood stars and in a police shootout with hostages.
Please seek medical help. -
@calmyourtities please read this before you take advice for your personal website from this lunatic.
related to this rant: https://devrant.com/rants/2820357/... -
@heyheni @NoMad Well, the journalist asked me why I did it? I seriously didn't have any reason, I just played with IMDB, but I couldn't say that, Thus, I told them this reason, I don't have any interest in being famous, Fame comes at a cost. And this did make a good change. IMDB no longer approves wrong edits. I could have told them through Email too but that would be ignored.
-
 NoMad134245y@theabbie it's okay. Your feelings are valid. Even if you don't understand why you feel them. But it's problematic when you do things without knowing why. In either case, seeing a therapist for a while and talking to him/her about these stuff wouldn't hurt anyone, right?
NoMad134245y@theabbie it's okay. Your feelings are valid. Even if you don't understand why you feel them. But it's problematic when you do things without knowing why. In either case, seeing a therapist for a while and talking to him/her about these stuff wouldn't hurt anyone, right? -
 NoMad134245y@theabbie let us know how it goes with the therapist. 🙂 Legit, I'm looking forward to you becoming a better version of you.
NoMad134245y@theabbie let us know how it goes with the therapist. 🙂 Legit, I'm looking forward to you becoming a better version of you. -
This thread looks like a bad soap opera... I hope this gets a good final, not a dramatic one.
-
@brunofontes I believe this means @NoMad and abbie end up together in season 2?
I'm joking I'm joking please don't kill me I have so much to live for -
@MySlugLikesSalt ahahahaha My comment got very late. I had stop writing for an urgent thing and that got quite miss placed. But this joke really made me laugh. hahahaha
-
 Prakash3675y@theabbie Why the fuck are you still justifying your act of stealing credits? I haven't heard a word of formal apology yet. It's like you know what you did and still don't feel sorry for it.
Prakash3675y@theabbie Why the fuck are you still justifying your act of stealing credits? I haven't heard a word of formal apology yet. It's like you know what you did and still don't feel sorry for it.
And next time you try to exploit a loophole, remember that there are people who just literally saved you from going to jail. They too could've exploited the loophole. -
 Prakash3675y@theabbie Yes, I agree. I have no experience of stealing credits or leaving personal files in wild or leaving private keys in public repos etc etc.
Prakash3675y@theabbie Yes, I agree. I have no experience of stealing credits or leaving personal files in wild or leaving private keys in public repos etc etc.
I apologise for speaking on these without any experience. -
@theabbie do you understand what you just said? You told someone to not to exactly what you've been doing a few rants worth
-
@Prakash I am just talking about this credit thing, yes, I am an idiot for keeping that private info public, that I admit
-
 Prakash3675y@theabbie Stealing credits is stealing credits, no matter who's the victim. I personally have been a victim of that. And that's why I have a special hate for people like you. Your attitude of justifying your act and not apologising yet adds cherry on top.
Prakash3675y@theabbie Stealing credits is stealing credits, no matter who's the victim. I personally have been a victim of that. And that's why I have a special hate for people like you. Your attitude of justifying your act and not apologising yet adds cherry on top.
Now, you asked @root to go on and dig deeper. And thanks to your attitude, I also took this challenge. The problem with morons like you is you tend to repeat your mistakes and since you've made accounts on 100+ accounts, I just needed to find one where you've done some shit.
After 15 hours of exhaustive search, I was able to find a lot which can land you in trouble. Biggest one being the exact copy of your blog on your gitlab account, containing all original files. (Seriously dude, how foolish could you be?)
Needless to say, because of my personal hate I made a fork of it and local copy of it. Now, here's what you have to do (1/2) -
 Prakash3675yContinuing the previous thread,
Prakash3675yContinuing the previous thread,
Now here's what you have to do
Go to your ALL social media accounts, and issue a formal apology to everything you stole credit for.
If you fail to do so, then I swear on the name of Richard Stallman, I'll pursue atleast 10 of your "contacts" to report to cyber crime cell. (2/2) -
@dfox I know there is no such feature, But please come and terminate this thread, 200 more comments and it will end anyways
-
 Prakash3675y@theabbie Are you going to apologise or shall I start pursuing your friends for making a case against you?
Prakash3675y@theabbie Are you going to apologise or shall I start pursuing your friends for making a case against you? -
 Prakash3675y@theabbie its not about informing. Its about telling the world who you really are. That's why: Go to ALL of your social media accounts, write a post clarifying what you did and SAY THAT YOU ARE AN IDENTITY THIEF.
Prakash3675y@theabbie its not about informing. Its about telling the world who you really are. That's why: Go to ALL of your social media accounts, write a post clarifying what you did and SAY THAT YOU ARE AN IDENTITY THIEF. -
 dfox421565yYeah let’s start wrapping this thread up I think, it’s went in for long enough. If anyone wants to continue the discussion, please take it to email or whatever medium you’d like. Thanks!
dfox421565yYeah let’s start wrapping this thread up I think, it’s went in for long enough. If anyone wants to continue the discussion, please take it to email or whatever medium you’d like. Thanks! -
 Prakash3675y@dfox, please let it exist for for 2 more hours. Guys like these need to be punished.
Prakash3675y@dfox, please let it exist for for 2 more hours. Guys like these need to be punished.
@theabbie I better see an apology within two hours, atleast on twitter -
 dfox421565y@Prakash no thanks. We don’t need you to punish him here. Like I said, feel free to take it to email or report to wherever you see necessary, but we don’t need to continue it here.
dfox421565y@Prakash no thanks. We don’t need you to punish him here. Like I said, feel free to take it to email or report to wherever you see necessary, but we don’t need to continue it here. -
Great, since you guys are so great detectives, figure out how you want to contact me, Personally, I prefer Instagram or Email. Let's Terminate this thread.
-
 dfox421565yAnd on that note, please respect OPs wishes and let this thread be done. Thanks everyone!
dfox421565yAnd on that note, please respect OPs wishes and let this thread be done. Thanks everyone!
Related Rants




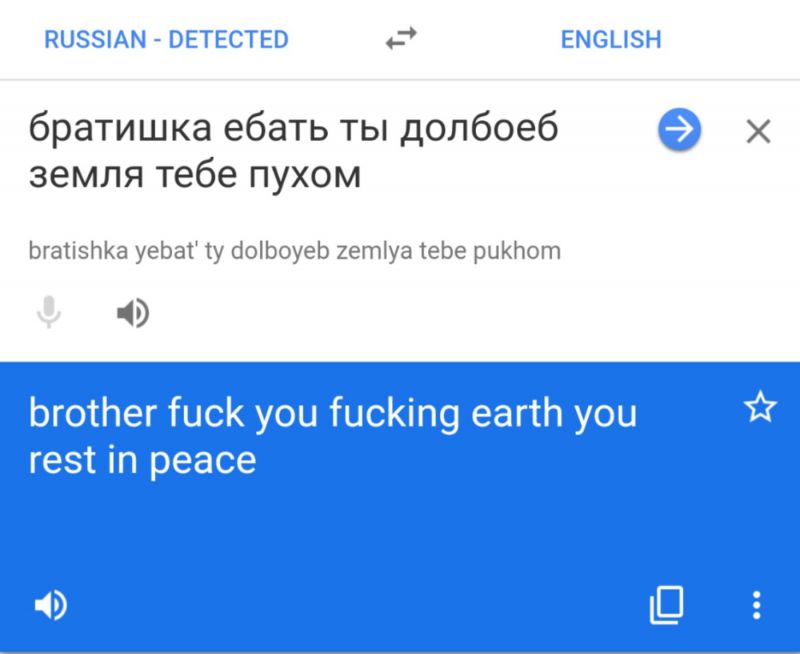






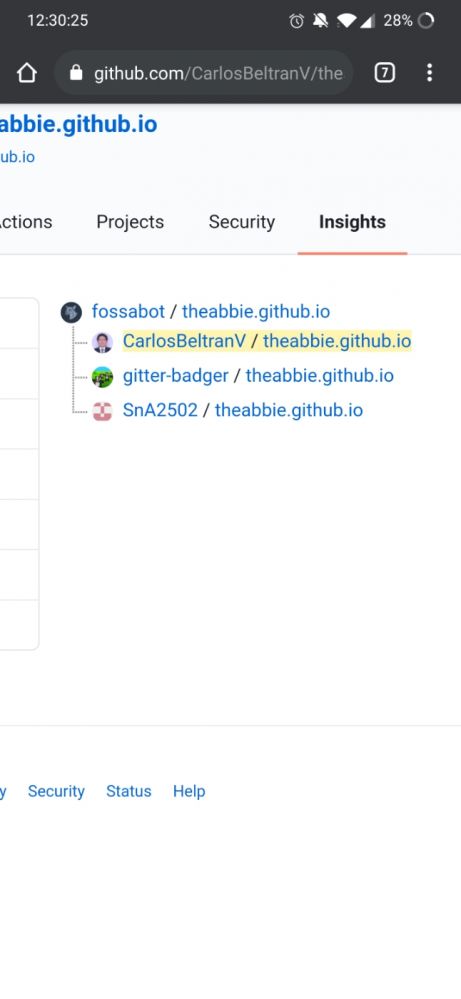





 Did you say security?
Did you say security? Why not! 😂
Why not! 😂
I think the fact that even Apple can't unlock your phone if you forget your passcode proves that they use very naive encryption method.
Suppose my data is "Hey This is Some Data" and Passcode is 1234, I could just Jumble this data using that passcode and It will be difficult to decrypt without Passcode. And If data is huge, it will be fairly impossible to do so. But that doesn't make it a good encryption method.
Such encryption, though safe is not practical, Imagine if there was no "Forget Password" Option on any account, I usually forgot my password very often when I was a child.
Apple has been doing such things for years, Using Bad things as a selling point. Apple users are dumb anyways because they don't want to control their phone.
Reset Password is a weak point which might be exploited but in such cases, usability is more important than security. Any service which doesn't allow resetting Password is a shitty service and I would never use such a service, They are too naive.
rant
encryption
security
apple