Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "data leaks"
-
It finally hit me the other day.
I'm working on an IoT project for a late-stage ALS patient. The setup is that he has a tablet he controls with his eye movements, and he wants to be able to control furnishings in his room without relying on anyone else.
I set up a socket connection between his tablet and the Raspberry Pi. From there it was a simple matter of using GPIO to turn a lamp or fan on or off. I did the whole thing in C, even the socket programming on the Pi.
As I was finishing up the main control of the program on the Pi I realized that I need to be more certain of this than anything I've ever done before.
If something breaks, the client may be forced to go days without being able to turn his room light on, or his fan off.
Understand he is totally trapped in his own body so it's not like he can simply turn the fan off. The nursing staff are not particularly helpful and his wife is tied up a lot with work and their two small children so she can't spend all day every day doting on him.
Think of how annoying it is when you're trying to sleep and someone turns the light on in your room; now imagine you can't turn it off yourself, and it would take you about twenty minutes to tell someone to turn it off -- that is once you get their attention, again without being able to move any part of your body except your eyes.
As programmers and devs, it's a skill to do thorough testing and iron-out all the bugs. It is an entirely different experience when your client will be depending on what you're doing to drastically improve his quality of life, by being able to control his comfort level directly without relying on others -- that is, to do the simplest of tasks that we all take for granted.
Giving this man some independence back to his life is a huge honor; however, it carries the burden of knowing that I need to be damned confident in what I am doing, and that I have designed the system to recover from any catastrophe as quickly as possible.
In case you were wondering how I did it all: The Pi launches a wrapper for the socket connection on boot.
The wrapper launches the actual socket connection in a child process, then waits for it to exit. When the socket connection exits, the wrapper analyzes the cause for the exit.
If the socket connection exited safely -- by passing a special command from the tablet to the Pi -- then the wrapper exits the main function, which allows updating the Pi. If the socket connection exited unexpectedly, then the Pi reboots automatically -- which is the fastest way to return functionality and to safeguard against any resource leaks.
The socket program itself launches its own child process, which is an executable on the Pi. The data sent by the tablet is the name of the executable on the Pi. This allows a dynamic number of programs that can be controlled from the tablet, without having to reprogram the Pi, except for loding the executable onto it. If this child of the socket program fails, it will not disrupt its parent process, which is the socket program itself.13 -
Started talking with someone about general IT stuff. At some point we came to the subject of SSL certificates and he mentioned that 'that stuff is expensive' and so on.
Kindly told him about Let's Encrypt and also that it's free and he reacted: "Then I'd rather have no SSL, free certificates make you look like you're a cheap ass".
So I told him the principle of login/registration thingies and said that they really need SSL, whether it's free or not.
"Nahhh, then I'd still rather don't use SSL, it just looks so cheap when you're using a free certificate".
Hey you know what, what about you write that sentence on a whole fucking pack of paper, dip it into some sambal, maybe add some firecrackers and shove it up your ass? Hopefully that will bring some sense into your very empty head.
Not putting a secure connection on a website, (at all) especially when it has a FUCKING LOGIN/REGISTRATION FUNCTION (!?!?!?!!?!) is simply not fucking done in the year of TWO THOUSAND FUCKING SEVENTEEN.
'Ohh but the NSA etc won't do anything with that data'.
Has it, for one tiny motherfucking second, come to mind that there's also a thing called hackers? Malicious hackers? If your users are on hacked networks, it's easy as fuck to steal their credentials, inject shit and even deliver fucking EXPLOIT KITS.
Oh and you bet your ass the NSA will save that data, they have a whole motherfucking database of passwords they can search through with XKeyScore (snowden leaks).
Motherfucker.68 -
Privacy & security violations piss me off. Not to the point that I'll write on devRant about it, but to the point that coworkers get afraid from the bloodthirsty look in my eyes.
I know all startups proclaim this, but the one I work at is kind of industry-disrupting. Think Uber vs taxi drivers... so we have real, malicious enemies.
Yet there's still this mindset of "it won't happen to us" when it comes to data leaks or corporate spying.
Me: "I noticed we are tracking our end users without their consent, and store not just the color of their balls, but also their favorite soup flavor and how often they've cheated on their partner, as plain text in the system for every employee to read"
Various C-randomletter-Os: "Oh wow indubitably most serious indeed! Let's put 2 scrumbag masters on the issue, we will tackle this in a most agile manner! We shall use AI blockchains in the elastic cloud to encrypt those ball-colors!"
NO WHAT I MEANT WAS WHY THE FUCK DO WE EVEN STORE THAT INFORMATION. IT DOES IN NO WAY RELATE TO OUR BUSINESS!
"No reason, just future requirements for our data scientists"
I'M GRABBING A HARDDRIVE SHREDDER, THE DB SERVER GOES FIRST AND YOUR PENIS RIGHT AFTER THAT!
(if it's unclear, ball color was an optimistic euphemism for what boiled down to an analytics value which might as well have been "nigger: yes/no")12 -
Although it might not get much follow up stuffs (probably a few fines but that will be about it), I still find this awesome.
The part of the Dutch government which keeps an eye on data leaks, how companies handle personal data, if companies comply with data protection/privacy laws etc (referring to it as AP from now on) finished their investigation into Windows 10. They started it because of privacy concerns from a few people about the data collection Microsoft does through Windows 10.
It's funny that whenever operating systems are brought up (or privacy/security) and we get to why I don't 'just' use windows 10 (that's actually something I'm asked sometimes), when I tell that it's for a big part due to privacy reasons, people always go into 'it's not that bad', 'oh well as long as it's lawful', 'but it isn't illegal, right!'.
Well, that changed today (for the netherlands).
AP has concluded that Windows 10 is not complying with the dutch privacy and personal data protection law.
I'm going to quote this one (trying my best to translate):
"It appears that Microsofts operating system follows every step you take on your computer. That gives a very invasive image of you", "What does that mean? do people know that, do they want that? Microsoft should give people a fair chance for deciding this by themselves".
They also say that unless explicit lawful consent is given (with enough information on what is collected, for what reasons and what it can be used for), Microsoft is, according to law, not allowed to collect their telemetrics through windows 10.
"But you can turn it off yourself!" - True, but as the paragraph above said, the dutch law requires that people are given more than enough information to decide what happens to their data, and, collection is now allowed until explicitly/lawfully ok'd where the person consenting has had enough information in order to make a well educated decision.
I'm really happy about this!
Source (dutch, sorry, only found it on a dutch (well respected) security site): https://security.nl/posting/534981/...8 -
Trash, trash, trash.
Who the fuck writes this shit?
Who the fuck lets these trash should-be-junior devs roll their own crypto? and then approves it?
The garbage heap of a feature (signing for all apis) doesn't follow Ruby standards, doesn't follow codebase conventions, has `// this is bridge` style comments (and no documentation), and it requires consumer devs to do unnecessary work to integrate it, and on top of all this: it leaks end-user data. on all apis. in plaintext.
Fucking hell.7 -
MAINTENANCE OF STACKOVERFLOW PLANNED
SHARE TO YOUR NEAREST DEV FRIENDS
Stackoverflow and its relative partners will be closed for two days due to maintenance, new design, and moving server infrastructure from United States to 1km below the Switzerland Alps for extra layers of security. This decision was made by the recent CloudFlare data leak.
Now our servers will be able to handle data leaks because even though the data was leaked, it will fill the empty places in the rocks resulting inaccessible from attackers.
Stackoverflow and its relative partners' maintenance estimated time is February 29 - 30. We will try to finish as fast as possible and bring you guys the best experience. If the maintenance delayes, we will tweet via @StackStatus or post details in our status blog.
Thank you for your support and have a happy day.
Best regards,
Stack Exchange team6 -
Dev: Hi Guys, we've noticed on crashlytics that one of your screens has a small crash. Can you look?
Me: Ok we had a look, and it looks to us to be a memory leak issue on most of the other screens. Homepage, Search, Product page etc. all seem to have sizeable memory leaks. We have a few crashes on our screens saying iPhone 11's (which have 4gb of ram) are crashing with only 1% of ram left.
What we think is happening is that we have weak references to avoid circular dependencies. Our weak references are most likely the only things the system would be able to free up, resulting in our UI not being able to contact the controller, breaking everything. Because of the custom libraries you built that we have to use, we can't really catch this.
Theres not really a lot we can do. We are following apples recommendations to avoid circular dependencies and memory leaks. The instruments say our screens are behaving fine. I think you guys will have to fix the leaks. Sorry.
Dev 1: hhhmm, what if you create a circular dependency? Then the UI won't loose any of the data.
Dev 2: Have you tried looking at our analytics to understand how the user is getting to your screens?
=================================
I've been sitting here for 15 minutes trying to figure out how to respond before they come online. I am fucking horrified by those responses to "every one of your screens have memory leaks"2 -
Why do people jump from c to python quickly. And all are about machine learning. Free days back my cousin asked me for books to learn python.
Trust me you have to learn c before python. People struggle going from python to c. But no ml, scripting,
And most importantly software engineering wtf?
Software engineering is how to run projects and it is compulsory to learn python and no mention of got it any other vcs, wtf?
What the hell is that type of college. Trust me I am no way saying python is weak, but for learning purpose the depth of language and concepts like pass by reference, memory leaks, pointers.
And learning algorithms, data structures, is more important than machine learning, trust me if you cannot model the data, get proper training data, testing data then you will get screewed up outputs. And then again every one who hype these kinds of stuff also think that ml with 100% accuracy is greater than 90% and overfit the data, test the model on training data. And mostly the will learn in college will be by hearting few formulas, that's it.
Learn a language (concepts in language) like then you will most languages are easy.
Cool cs programmer are born today😖 31
31 -
The Cloud Of Bullshit
Every day I wake, and I think of my one true mission in life. To mock and ridicule paint huffing idiots. Something recently that drew my ire, like the hemorrhoids on my ass is this idea of 'the cloud', THE CLOUD and the buzzword lingo-bingo bullshit that providers use to hype and sell it.
For example, airtable is an amazing service. I love that I can insert just about anything into a row, create any of my own row datatypes, that it's flexible as all hell.
I love it.
And I hate that I'm essentially locked in to the cloud.
I fucking hate how if my internet goes down (thanks you pie eating inbred dipshits at comcast) I have no access.
If the company is bought, they'll shut down like all the rest , to be "relaunched at a later time" (or never).
I hate that if the company doesn't make enough money, or it's investors change their mind, woopsie, service is shut down.
I hate that the cloud is synonymous with massive data leaks and IOT-levels of stupidity in security practices.
Every time someone says "but its in the cloud! Isn't it amazing!"
I always think 1. YEAH IF IM AN INVESTOR I GET TO MILK LOW BROW FINGER PAINTING FUCKWITS EVERY MONTH like Adobe sucking the blood from infants who are still in college.
2. Why? So I can get locked into their platform, have them segment off previously free features (fucking youtube and the 'subscribe so you can continue playing audio with your screen off' bullshit), and then have fees increase month over month?
3. Why, so every four years during the presidential selection, if I piss off some fuckstick braindead lemming literally sucking his girlfriends BFs cock, they can potentially shut me out from my own data completely?
The Cloud is built on shit-colored hype sold to knob gobbling idiots, controlling idiots, profiting at the expense of idiots, and later fucking them for buyout payola. The Cloud is a Cloud of Bullshit shat out by huckster messiahs straight into the lapping mouths of fanatics worshiping slavishly like toilet drinking scum at the porcelain alter of a neon god, invisible, untouchable, and like a spigot, easily shut off without anyone noticing. And when it happens, I'll be there, shouting "WHERE IS YOUR CLOUD NOW?"
Native any day. 100% native or I don't fucking want it
None of this node.js-gone-native bullshit either with notetaking apps taking up hundreds of megabytes of ram, where everything is bootstrap or react, in a browser, in a window container, because people are so fucking incompetent we have to hold their hand WHILE they give themselves a reach around.
Native or nothing.
For my favorite notetaking app, I use Microsoft OneNote. "OH god, a heathen, quick, stick his body up on a stake!"
But hear me out. I'll be the first one in a crowd to kick bill gates in the nuts (not because I particularly hate microsoft, just because I think hes kind of a cunt).
So when I say onenote is good, I really fucking mean it. Sure they did some cunty things like 'dumbed down' the interface, and cut out some options. But you know what they can't do?
Shut down the damn service (short of a system update completely removing the whole app, which, frankly, wouldn't surprise me).
It's so god damn good it waxed my balls, cured my cancer, fixed my relationship with my father, found my long lost brother, and replaced ALL my irl notebooks.
It's so good that if it was cocaine I'd be hospitalized for overusing it.
So god damn good it didn't just replace all my notebooks, it even replaced and sped up my mockup process three to five times. Want layers?
Built in. Just drag an image on to the notebook to import instantly.
Want to rearrange layers? Right click select "send forward/back/bring to front/send to back".
Everything snaps to grid by default and is easily resizeable.
I had all the elements for a UI sliced and diced. Wanted to try a bunch of layouts. Was gonna take me two damn days.
Did it in three hours with the notebook features of onenote.
After I started using onenote, me and my bodypillow finally conceived even.
Sweet marries mammaries I just fucking jizzed. Thank you onenote.
P.s. It really did speed up my UI design, allows annotated images, highlighted text. Shit, it can even do kanban.
And all I can think is "good job microsoft making an awesome product for free, being dumb as fuck for not charging for it, and then not marketing it at ALL."
It was sheer fucking luck that I discovered it while was I was looking for vendor STD bloatware to blast off my new install.
OneNote: Worth a try even for the kick-gates-in-the-nuts fan club.
The cloud can suck my balls.18 -
I have a few of these so I'll do a series.
(1 of 3) Public privates
We had a content manager that created a content type called "news item" on a Drupal site. There where two file fields on there. One called "attachments" and the other called "private attachments". The "private attachments" are only for members to see and may contain sensitive data. It was set to go trough Drupals security (instead of being directly hosted by the webserver) but because the permissions on the news items type where completely public everybody had access. So basically it was a slow public file field.
This might be attibuted to ow well Drupal is confusing. Howerver weeks earlier that same CM created a "private article". This actually had permissions on the content type correctly but had a file field that was set to public. So when a member posted the URL to a sensitive file trough unsafe means it got indexed by google and for all to read. When that happend I explained in detail how the system worked and documented it. It was even a website checklist item.
We had two very embarrassing data leaks :-(1 -
I downloaded Lapsus$ source code leaks from samsung, nvidia and microsoft, looked at them and I think I’ll delete it cause I don’t like shitty code on my personal computer.
-
A (work-)project i spent a year on will finally be released soon. That's the perfect opportunity to vent out all the rage i built up during dealing with what is the javascript version of a zodiac letter.
Everything went wrong with the beginning. 3 people were assigned to rewrite an old flash-application. Me, A and B. B suggested a javascript framework, even though me and A never worked with more than jquery. In the end we chose react/redux with rest on the server, a classic.
After some time i got the hang of time, around that time B left and a new guy, C, was hired soon after that. He didn't know about react/redux either. The perfect start off to a burning pile of smelly code.
Today this burning pile turned into a wasteland of code quality, a house of cards with a storm approaching, a rocket with leaks ready to launch, you get the idea.
We got 2 dozen files with 200-500 loc, each in the same directory and each with the same 2 word prefix which makes finding the right one a nightmare on its on. We have an i18n-library used only for ~10 textfields, copy-pasted code you never know if it's used or not, fetch-calls with no error-handling, and many other code smells that turn this fire into a garbage fire. An eternal fire. 3 months ago i reduced the linter-warnings on this project to 1, now i can't keep count anymore.
We use the reactabular-module which gives us headaches because IT DOESN'T DO WHAT IT'S SUPPOSED TO DO AND WE CANT USE IT WELL EITHER. All because the client cant be bothered to have the table header scroll along with the body. We have methods which do two things because passing another callback somehow crashed in the browser. And the only thing about indentation is that it exists. Copy pasting from websites, other files and indentation wars give the files the unique look that make you wonder if some of the devs hides his whitespace code in the files.
All of this is the result of missing time, results over quality and the worst approach of all, used by A: if A wants an ui-component similar to an existing one, he copies the original and edits he copy until it does what he wants. A knows about classes, modules, components, etc. Still, he can't bring himself to spend his time on creating superclasses... his approach gives results much faster
Things got worse when A tried redux, luckily A prefers the components local state. WHICH IS ANOTHER PROBLEM. He doesn't understand redux and loads all of the data directly from the server and puts it into the local state. The point of redux is that you don't have to do this. But there are only 1 or 2 examples of how this practice hurt us yet, so i'm gonna have to let this slide. IF HE AT LEAST WOULD UPDATE THE DATA PROPERLY. Changes are just sent to the server and then all of the data is re-fetched. I programmed the rest-endpoints to return the updated objects for a very reason. But no, fuck me.
I've heard A decided (A is the teamleader) to use less redux on the next project and use a dedicated rest-endpoints for every little comoutation you COULD DO WITH REDUX INSTEAD. My will is broken and just don't want to work with this anymore.
There are still various subpages that cant f5 because the components cant handle an empty redux state in the beginning, but to be honest i don't care anymore. Lets hope the client will never find out, along with the "on error nothing happens"-bugs. The product should've been shipped last week, but thanks to mandatory bugfixes the release was postponed to next week. Then the next project starts...
Please give me some tips to keep up code quality over time, i cant take this once more.
I'm also aware that i could've done more, talking A and C about code style, prettifying the code, etc. Etc. But i was busy putting out my out fires, i couldn't kill much of the other fires which in the end became a burning building (a perfect metaphor for this software)4 -
For fuck sake!
Fuck locatefamily.com, just searched out on google my name and surname, both foreign and hard to even spell out for many, and it's the first time that I saw my data(where did I live, my current work phone number, name and surname) open wide as the second link of my search, fuck!
But there's a clue, at that address I lived for a not so long period, so I did search my emails in that period and other than my employers and government emails(in which I don't trust either), here's a list of companies that had my info(partial or full):
Only address(with name and surname):
Amazon.it with 14 other companies(for shipping)
eBay with 4 other companies(for shipping)
voxelfarm.com
trenord.it
DUMA (LIGHT) di Adel
decathlon.com
gruppoargenta.it
paypal.it
All info:
gearbest.com
glistockisti.com
oculus.com
Banggood.com
Overall there are 33(including government, employers and national main mail service) potential leaks of that data, with 7 in full exposure.
After this, I'm thinking how it's even avoidable to not leak personal data, because from any of those businesses I got goods or services that otherwise I couldn't without exposing such informations... fuck.6 -
Welp, this made my night and sorta ruined my night at the same time.
He decided to work on a new gaming community but has limited programming knowledge, but has enough to patch and repair minor issues. He's waiting for an old friend of his to come back to start helping him again, so this leads to me. He needed a custom backend made for his server, which required pulling data from an SQL/API and syncing with the server, and he was falling behind pace and asked for my help. He's a good friend that I've known for a while, and I knew it wouldn't take to long to create this, so I decided to help him. Which lead to an interesting find, and sorta made my night.
It wasn't really difficult, got it done within an hour, took some time to test and fix any bugs with his SQL database. But this is where it get's interesting, at least for me. He had roughly a few hundred people that did beta testing of the server, anyways, once the new backend was hooked in and working, I realized that the other developer he works with had created a 'custom' script to make sure there are no leaks of the database. Well, that 'custom' script actually begins wiping rows/tables (Depends on the sub-table, some get wiped row by row, some just get completely dropped), I just couldn't comprehend what had happened, as rows/tables just slowly started disappearing. It took me a while of checking, before checking his SQL query logs (At least the custom script did that properly and logged every query), to realize it just basically wiped the database.
Welp, after that, it began to restrict the API I was using, and due to this it identified the server as foreign access (Since it wasn't using the same key as his plugin, even though I had an API key created just so it could only access ranks and such, to prevent abuse) and begin responding not with denied, but with a lovely "Fuck you hacker!" This really made my night, I don't know why, but I was genuinely laughing pretty hard at this response.
God, I love his developer. Luckily, I had created a backup earlier, so I patched it and just worked around the plugin/API to get it working. (Hopefully, it's not a clusterfuck to read, writing this at 2 am with less than an hour of sleep, bedtime! Goodnight everyone.)7 -
We had 1 Android app to be developed for charity org for data collection for ground water level increase competition among villages.
Initial scope was very small & feasible. Around 10 forms with 3-4 fields in each to be developed in 2 months (1 for dev, 1 for testing). There was a prod version which had similar forms with no validations etc.
We had received prod source, which was total junk. No KT was given.
In existing source, spelling mistakes were there in the era of spell/grammar checking tools.
There were rural names of classes, variables in regional language in English letters & that regional language is somewhat known to some developers but even they don't know those rural names' meanings. This costed us at great length in visualizing data flow between entities. Even Google translate wasn't reliable for this language due to low Internet penetration in that language region.
OOP wasn't followed, so at 10 places exact same code exists. If error or bug needed to be fixed it had to be fixed at all those 10 places.
No foreign key relationships was there in database while actually there were logical relations among different entites.
No created, updated timestamps in records at app side to have audit trail.
Small part of that existing source was quite good with Fragments, MVP etc. while other part was ancient Activities with business logic.
We have to support Android 4.0 to 9.0 of many screen sizes & resolutions without any target devices issued to us by the client.
Then Corona lockdown happened & during that suddenly client side professionals became over efficient.
Client started adding requirements like very complex validation which has inter-entity dependencies. Then they started filing bugs from prod version on us.
Let's come to the developers' expertise,
2 developers with 8+ years of experience & they're not knowing how to resolve conflicts in git merge which were created by them only due to not following git best practice for coding like only appending new implementation in existing classes for easy auto merge etc.
They are thinking like handling click events is called development.
They don't want to think about OOP, well structured code. They don't want to re-use code mostly & when they copy paste, they think it's called re-use.
They wanted to follow old school Java development in memory scarce Android app life cycle in end user phone. They don't understand memory leaks, even though it's pin pointed by memory leak detection tools (Leak canary etc.).
Now 3.5 months are over, that competition was called off for this year due to Corona & development is still ongoing.
We are nowhere close to completion even for initial internal QA round.
On top of this, nothing is billable so it's like financial suicide.
Remember whatever said here is only 10% of what is faced.
- An Engineering lead in a half billion dollar company.4 -
This codebase had 50+ main() functions and 80+ Material App. 5 of them are nested MaterialApp
Redundant widgets, security leaks, and print Sensitive information from the server to console without using (kDebugMode), therefore in prod, the data are leaked.
I refactored until I screamed.
So I left a gift inside.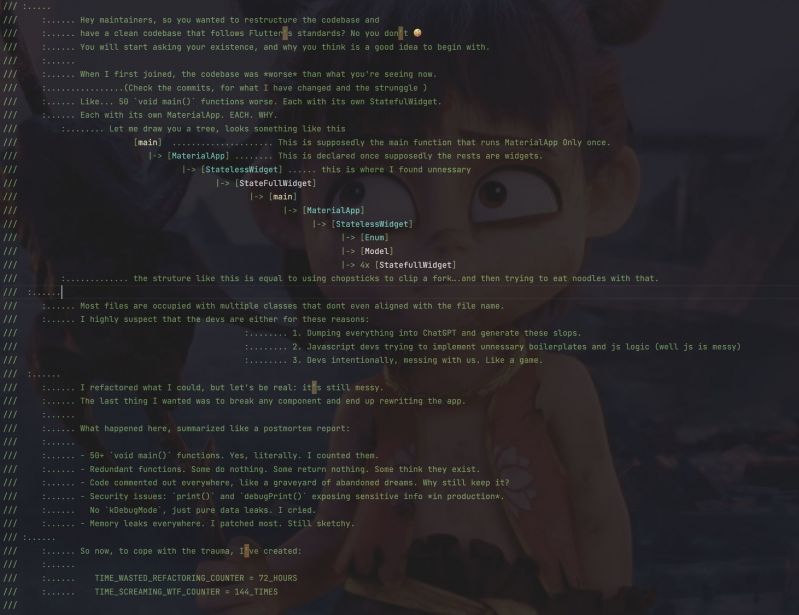 14
14 -
I remember when doing some privacy cleanup, looking at the third-party list of a website and visiting the sites behind them. I ended up one time on Crazy Egg.
3 months later, I got an email if I wouldn't want to use their services.
They did have my email.
From where? (the answer is obviously from the sites they track)
But I mean, who cares about your email when they have your f****** passport
-->
https://medium.freecodecamp.org/pri...
This world is getting to crazy, I thought this would be the maximum. Of course...
Next headline:
https://telegraph.co.uk/news/2018/...
I think tracking is a more serious problem, than I imagined (and I do already try to reduce data)
Oh yeah and btw I just noticed an iOS app could silently use my mobile data (was deactivated for the app) to display ads. Silently. I hope this was a bug. But I don't think so. -
In reply to:
https://devrant.com/rants/3957914/...
Okay, we must first establish common ground here. What do we understand about "showing"? I understand you probably mean displaying/rendering, more abstractly: "obtaining". Good, now we move on.
What's the point of a front-end? Well, in the 90's that used to be an easy answer: to share information (not even in a user-friendly way, per se). Web 2.0 comes, interaction with the website. Uh-oh, suddenly we have to start minding the user. Web 3.0 comes, ouch, now the front-end is a mini-backend. Even tougher, more leaks etc. The ARPAnet was a solution, a front-end that they had built in order to facilitate research document-sharing between universities. Later, it became the inter(national) net(work).
First there was SGML to structure the data (it's a way of making it 'pretty' in a lexicographical way) and turn it into information (which is what information is: data with added semantics) and later there was HTML to structure it even further, yet we all know that its function was not prettification, but rather structure. Later came CSS, to make it pretty. With its growing popularity, the web started to be used as a publishing device.
source:
https://w3.org/Style/CSS20/...
If we are to solely display JSON data in a pretty way, we may be limiting ourselves to the scenario of rendering pretty web pages using aesthetic languages such as CSS. We must also understand that if we are only focusing on making a website pretty with little to moderate functionality, we aren't really winning. A good website has to be a winner in all aspects, which is why frameworks came into existence, but.. lmao, let's leave that to another discussion.
Now let me recall back my college days.. front-end.. front-end.. heck, even a headset can be a front-end to a pick-order backend. We must think back to the essence, to the abstract. All other things are just implementations of it (yes, the horrendous thousands of Javascript libraries, lol).
So, my college notes say:
"Presentation layer: this is the UI.
In this layer you ask the middle tier for information, which gets that information from a database, which then goes back to middle tier, back to presentation. In the case of the headset, the operators can confirm an order is ready. This is essentially the presentation tier again: you're getting information from the middle tier and 'presenting it' as it were.
The presentation layer is in essence the question: how do I bring my application data to my end users in a platform-and solution-independent way?"
What's JSON? A way to transport data between the middle tier and the presentation tier. Is that what frontend development is? Displaying it in a pretty way? I don't think it is, because 'pretty' is an extra feature of obtaining and displaying data. Do we always have to display data in a pretty way? Not necessarily. We could write a front-end script (in NodeJS perhaps) that periodically fetches certain information from a middle-tier is serves a more functional role rather than a rendering one.
The prettification of data was a historical consequence of the popularity of the web (which is a front-end) (see second paragraph with link). Since the essence of a front-end is to obtain information from the back-end (with stress on obtaining), its presentation is not necessarily a defining characteristic of it, but rather an optional and solution-dependent aspect, a facet.4 -
https://devrant.com/rants/2366822/...
following rant I started oppening my files to build copy of have i been pwned service why twitter kept their passwords in plain text lol
...
people actually got 123456 passwords looking for my email in twitter database file 1
1 -
Lesson learned .. never use sailsjs
Magic data loss
Laggy as fuck (832ms)... php5 runs better than this(210ms)
memory leaks -
Here's my latest and greatest(ish) post:
How to overcome GDPR ... with data leaks.
https://loosy.gitlab.io/2019/10/...5

