Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
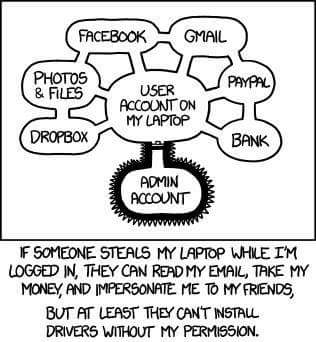
Search - "security audit"
-
You know what?
Young cocky React devs can suck my old fuckin LAMP and Objective-C balls.
Got a new freelance job and got brought in to triage a React Native iOS/Android app. Lead dev's first comment to me is: "Bro, have you ever used React Native".
To which I had to reply to save my honor publicly, "No, but I have like 8 years with Objective-C and 3 years with Swift, and 3 years with Node, so I maybe I'll still be able help. Sometimes it just helps to have a fresh set of eyes."
"Well, nobody but me can work on this code."
And that, as it turned out was almost true.
After going back and forth with our PM and this dev I finally get his code base.
"Just run "npm install" he says".
Like no fuckin shit junior... lets see if that will actually work.
Node 14... nope whole project dies.
Node 12 LTS... nope whole project dies.
Install all of react native globally because fuck it, try again... still dies.
Node 10 LTS... project installs but still won't run or build complaining about some conflict with React Native libraries and Cocoa pods.
Go back to my PM... "Um, this project won't work on any version of Node newer than about 5 years old... and even if it did it still won't build, and even if it would build it still runs like shit. And even if we fix all of that Apple might still tell us to fuck off because it's React Native.
Spend like a week in npm and node hell just trying to fucking hand install enough dependencies to unfuck this turds project.
All the while the original dev is still trying TO FIX HIS OWN FUCKING CODE while also being a cocky ass the entire time. Now, I can appreciate a cocky dev... I was horrendously cocky in my younger days and have only gotten marginally better with age. But if you're gonna be cocky, you also have to be good at it. And this guy was not.
Lo, we're not done. OG Dev comes down with "Corona Virus"... I put this in quotes because the dude ends up drawing out his "virus" for over 4 months before finally putting us in touch with "another dev team he sometimes uses".
Next, me and my PM get on a MS Teams call with this Indian house. No problems there, I've worked with the Indians before... but... these are guys are not good. They're talking about how they've already built the iOS build... but then I ask them what they did to sort out the ReactNative/Cocoa Pods conflict and they have no idea what I'm talking about.
Why?
Well, one of these suckers sends a link to some repo and I find out why. When he sends the link it exposes his email...
This Indian dude's emails was our-devs-name@gmail.com...
We'd been played.
Company sued the shit out of the OG dev and the Indian company he was selling off his work to.
I rewrote the app in Swift.
So, lets review... the React dev fucked up his own project so bad even he couldn't fix it... had to get a team of Indians to help who also couldn't fix it... was still a dickhead to me when I couldn't fix it... and in the end it was all so broken we had to just do a rewrite.
None of you get npm. None of you get React. None of you get that doing the web the way Mark Zucherberg does it just makes you a choad locked into that ecosystem. None of you can fix your own damn projects when one of the 6,000 dependency developers pushes breaking changes. None of you ever even bother with "npm audit fix" because if security was a concern you'd be using a server side language for fucking server side programming like a grown up.
So, next time a senior dev with 20 years exp. gets brought in to help triage a project that you yourself fucked up... Remember that the new thing you know and think makes you cool? It's not new and it's not cool. It's just JavaScript on the server so you script kiddies never have to learn anything but JavaScript... which makes you inarguably worse programmers.
And, MF, I was literally writing javascript while you were sucking your mommas titties so just chill... this shit ain't new and I've got a dozen of my own Node daemons running right now... difference is?
Mine are still working.34 -
A dude with a THICK Russian accent just called me offering server security services.
After I politely declined, he insisted on a free audit of my servers. I declined that as well.
Now I’m backing up our DB’s and going through my nginx logs.
Am I being racist?19 -
Act I
Me (Lead Developer), Boss (Head of IT), CEO
> enter stage left CEO
CEO > "Alright Boss, give it to me straight. Are we going to be able to release app x by this date?"
Boss > "Yup we'll have a beta release on that date"
> exit stage right CEO
Me > types long email to Boss outlining exactly why we won't be able to release app x anywhere near that date, beta or otherwise, because:
1. We have a development team of 2
2. I've never developed an iOS app before
3. Developer 2 is still trying to understand git, because
3a. Developer 2 isn't even a developer (but he's doing iOS front-end so w/e)
4. We don't have the required database systems in place
5. Or CRM
6. Or CPQ
7. We'll need to conduct a security audit
Boss > "yeah, but CEO is gonna need to hear that date a few more times before he can fully understand"
Me > *internally screaming BUT YOU HAVEN'T TOLD HIM THAT AT ALL*
"ok cool just glad we're on the same page on that one"5 -
Boss hands over to me an old security audit report and tells me "Go through this and check if all the problems mentioned have been resolved". Quick glance through the report shows all expected issues - SQLi, plaintext transmission and storage etc. I tell him that I need access to the application both from admin and a user with restricted privileges.
He hands me the admin credentials and tells me, "After you login in, just go the "Users" tab. You'll find the profiles of all the users there. You can get the emails and passwords of any user you want from there."
I had to hold back a chuckle. There's nothing to verify. If they haven't resolved storing plain text passwords in the database (AND displaying it IN PLAIN TEXT in the website itself (which to my surprise wasn't mentioned in the audit)), they probably haven't even looked at the report.2 -
Dev: Hey that internal audit you asked me to perform didn’t go so well
Manager: It has too! I’ll get in a lot of trouble if it doesn’t pass.
Dev: Ok well it’s a lot of work to get it to a passing state, we have to dedicate a lot of resources to fix all these findings.
Manager: We don’t have any spare resources, they are all working on new projects! Why did you have to find things??
Dev: ….It’s a lot of hard to miss stuff, like missing signatures on security clearance forms
Manager: Ok can’t you just say that everything is all good? They’ll probably not double check.
Dev: I’m not really comfortable with that…Look all of these findings are all just from one member of the team consistently not doing their job, can’t you just address that with him and I can make a note on the audit that issues were found but corrective action was made? That’s the whole point of audits.
Manager: You don’t get it, if anything is found on the audit I’ll look bad. We have to cover this up. Plus that’s a really good friend of mine! I can’t do that to him. Ok you know what? You are obviously not the right person for this task, I’ll get someone else to do it. Go back to your regular work, I’m never assigning you audits again.8 -
a stored XSS vuln in a banner-like component, visible in ALL the pages in the portal. Anyone can attack anyone.
HOWEVER this was not discovered by 3rd-party security specialists during latest security audit. I have escalated this to my manager and got replied that unless client actively requests this to be fixed should I do anything about it.
FFS.. it's only 2 lines of code.. And there's nothing I can do about it.
Eventualy I was transfered to another project. Now it's not my problem anymore.4 -
My team manager showed me a web application of a new client and asked me if I can find vulnerabilities in it to push for a better product contract. She showed me the system architecture and asked me if I could try finding something from their login page. I politely refused since we don't have written permission to conduct a security audit (it's also a ministry website). She was pretty disappointed and idk if I'm doing the right thing not helping the company (I'm an intern but still). I'm sure I can scan in stealth but I don't think it's ethical on a corporate level. Thoughts?11
-
This is the most hilarious stackoverflow rant ever, quote:
"Strong cryptography only means the passwords must be encrypted while the user is inputting them but then they should be moved to a recoverable format for later use."
Full rant:
http://serverfault.com/questions/...5 -
I used to do audits for private companies with a team. Most of them where black box audits and we were allowed to physically manipulate certain machines in and around the building, as long as we could get to them unnoticed.
Usually when doing such jobs, you get a contract signed by the CEO or the head of security stating that if you're caught, and your actions were within the scope of the audit, no legal action will be taken against you.
There was this one time a company hired us to test their badge system, and our main objective was to scrape the data on the smartcards with a skimmer on the scanner at the front of the building.
It's easy to get to as it's outside and almost everyone has to scan their card there in order to enter the building. They used ISO 7816 cards so we didn't even really need specified tools or hardware.
Now, we get assigned this task. Seems easy enough. We receive the "Stay-out-of-jail"-contract signed by the CEO for Company xyz. We head to the address stated on the contract, place the skimmer etc etc all good.
One of our team gets caught fetching the data from the skimmer a week later (it had to be physically removed). Turns out: wrong Building, wrong company. This was a kind of "building park" (don't really know how to say it in English) where all the buildings looked very similar. The only difference between them was the streetnumber, painted on them in big. They gave us the wrong address.
I still have nightmares about this from time to time. In the end, because the collected data was never used and we could somewhat justify our actions because we had that contract and we had the calls and mails with the CEO of xyz. It never came to a lawsuit. We were, and still are pretty sure though that the CEO of xyz himself was very interesed in the data of that other company and sent us out to the wrong building on purpose.
I don't really know what his plan after that would have been though. We don't just give the data to anyone. We show them how they can protect it better and then we erase everything. They don't actually get to see the data.
I quit doing audits some time ago. It's very stressful and I felt like I either had no spare time at all (when having an active assignment) or had nothing but spare time (when not on an assignment). The pay also wasn't that great.
But some people just really are polished turds.4 -
I should just quit. I am not paid enough to deal with this pissing contest.
Reviewer:
Need to add instructions (on readme) for installing pnmp, or if possible, have the top-level npm i install it (lol).
Also, it looks like we are no longer using lerna? If that's right, let's remove the dependency; its dependencies give some security audit messages at install.
Me:
it's good enough for now. Added a new ticket to resolve package manager confusions. (Migrate to pnpm workspaces)
Reviewer:
I will probably be responsible for automating deployment of this (I deployed the webapp on cloudflare pages and there is no work that needs to be done. "automating deployment" literally means replacing npm with pnpm). I disagree that it's good enough for now.
Imagine all readmes on github document how to install yarn/pnpm.
Lesson learned:
If you think an OOP static site developer can't handle modern JS framework, you are probably right.2 -
So one of my clients had a different company do a penetrationtest on one of my older projects.
So before hand I checked the old project and upgraded a few things on the server. And I thought to myself lets leave something open and see if they will find it.
So I left jquery 1.11.3 in it with a known xss vulnerability in it. Even chrome gives a warning about this issue if you open the audit tab.
Well first round they found that the site was not using a csrf token. And yeah when I build it 8 years ago to my knowledge that was not really a thing yet.
And who is going to make a fake version of this questionair with 200 questions about their farm and then send it to our server again. That's not going to help any hacker because everything that is entered gets checked on the farm again by an inspector. But well csrf is indeed considered the norm so I took an hour out of my day to build one. Because all the ones I found where to complicated for my taste. And added a little extra love by banning any ip that fails the csrf check.
Submitted the new version and asked if I could get a report on what they checked on. Now today few weeks later after hearing nothing yet. I send my client an email asking for the status.
I get a reaction. Everything is perfect now, good job!
In Dutch they said "goed gedaan" but that's like what I say to my puppy when he pisses outside and not in the house. But that might just be me. Not knowing what to do with remarks like that. I'm doing what I'm getting paid for. Saying, good job, your so great, keep up the good work. Are not things I need to hear. It's my job to do it right. I think it feels a bit like somebody clapping for you because you can walk. I'm getting off topic xD
But the xss vulnerability is still there unnoticed, and I still have no report on what they checked. So I have like zero trust in this penetration test.
And after the first round I already mentioned to the security guy in my clients company and my daily contact that they missed things. But they do not seem to care.
Another thing to check of their to do list and reducing their workload. Who cares if it's done well it's no longer their responsibility.
2018 disclaimer: if you can't walk not trying to offend you and I would applaud for you if you could suddenly walk again.2 -
We have a badly out of shape but functional product , the result of a "if its not broke don't fix it" mentality. The only thing manangement cares is our next release and making meetings to plan other meetings...
Now comes the time of the security Audit (PCI)...
Manager : oh noooo the audit will fix this issue, quickkk fix it !
Us : welllll its a lengthy process but doable, we just gotta do a,b,c,d,e . Part a is essentially what we need the rest are refactoring bits of the system to support part a since the performance would be shit otherwise
Manager: can you do part a before the audit starts ?
Us: yep.
Manager: do it . Oh and pop those other issues on JIRA so we can track em
Audit completed....
Manager: so we got through ok?
Us : 👍 yep
Manager: okayy, take those other issues..... and stick em at the bottom of the back log...
Us : huh ? *suspicious faces*..... okay but performance is gonna be poor with the system as it is cuz of part A....
Manager: yeaaahhh * troll face* ....about that.... roll it back and stick that too at the bottom of the log. We got to focus our next release. Lemme schedule a meeting for that 😊
Us : faceplam4 -
Impossible deadline experience?
A few, but this one is more recent (and not mine, yet)
Company has plans to build a x hundred thousand square feet facility (x = 300, 500, 800 depending on the day and the VP telling the story)
1. Land is purchased, but no infrastructure exists (its in a somewhat rural area, no water or sewage capable of supporting such a large facility)
2. No direct architectural plans (just a few random ideas about layout, floor plans, parking etc)
3. Already having software dev meetings in attempt to 'fix' all the current logistical software issues we have in the current warehouse and not knowing any of the details of the new facility.
One morning in our stand-up, the mgr says
Mgr: "Plans for the new warehouse are moving along. We hope to be in the new building by September."
Me: "September of 2022?"
<very puzzled look>
Mgr: "Um, no. Next year, 2021"
Me: "That's not going to happen."
Mgr: "I was just in a meeting with VP-Jack yesterday. He said everything is on schedule."
Me: "On schedule for what?"
<I lay out some of the known roadblocks from above, and new ones like the political mess we will very likely get into when the local zoning big shots get involved>
Mgr: "Oh, yea, those could be problems."
Me: "Swiiiiishhhhh"
Mgr: "What's that?"
Me: "That's the sound of a September 2021 date flying by."
Mgr: "Funny. Guess what? We've been tasked with designing the security system. Overhead RFID readers, tracking, badge scans, etc. Normally Dan's team takes care of facility security, but they are going to be busy for a few weeks for an audit. Better start reaching out to RFID vendors for quotes. Have a proposal ready in a couple of weeks."
Me: "Sure, why not."1 -
Create a full open-source company based on no-knowledge services to compete with the data hogs that pretty much own the internet as it stands3
-
User: If we use Oauth2, can we audit exactly where this data is going and who sends it there, and in addition cam we audit who grabs that data from the Authenticating app and make sure it doesn't violate our requirements?
Me: No
User: Why not?
Me: Because thats like asking us to audit whether or not a user accessed files and then uploaded them to their personal drive instead of corporate. We don't mandate that application owners take responsibility for their data outside of their application, why would we require that in this case???
User: Uhhhhh
FFS the lack of understanding of application accounts here boggles my mind. I understand that the security concerns are real but throwing out all permissible contexts based on a mandate that we dont even apply to extremely permissive accounts (i.e. users compared to apps) is folly1 -
So today a colleague confessed to an attempt to troll my computer by SSHing into it and playing random songs. Thankfully he did not manage but he would just happen to do it the day we have a security audit.
-
Part 1: https://devrant.com/rants/4298172/...
So we get this guy in a meeting and he is now saying "we can't have application accounts because that violates our standard of knowing who accessed what data - the application account anonamizes the user behind the app account data transaction and authorization"
And so i remind him that since it's an application account, no one is going to see the data in transit (for reference this account is for CI/CD), so the identity that accessed that data really is only the app account and no one else.
This man has the audacity to come back with "oh well then thats fine, i cant think of a bunch of other app account ideas where the data is then shown to non-approved individuals"
We have controls in place to make sure this doesnt happen, and his grand example that he illustrates is "Well what if someone created an app account to pull github repo data and then display that in a web interface to unauthorized users"
...
M******* why wouldnt you JUST USE GITHUB??? WHO WOULD BUILD A SEPARATE APPLICATION FOR THAT???
I swear I have sunk more time into this than it would have costed me to mop up from a whole data breach. I know there are situations where you could potentially expose data to the wrong users, but that's the same issue with User Accounts (see my first rant with the GDrive example). In addition, the proposed alternative is "just dont use CI/CD"!!!
I'm getting pretty pissed off at this whole "My compliance is worth more than real security" bullshit. -
TLDR: I need advice on reasonable salary expectations for sysadmin work in the rural United States.
I need some community advice. I’m the sysadmin at a small (35 employee) credit card processing company. I began as an intern and have now become their full time sysadmin/networking specialist. Since I was hired in January I have:
-migrated their 2007 Exchange server to Office 365
-Upgraded their ailing Windows server 2003 based architecture to 2012R2
-Licensed their unlicensed VMware ESXi servers (which they had already paid for license keys for!!!) and then upgraded them to 6.5 while preventing downtime on hosted VMs using tricky transfers and deployments (without vMotion!)
-Deployed a vCenter server to manage said ESXi servers easier
-Fixed a three month gap in their backups by implementing Veeam, and verifying its functionality
-Migrated a ‘no downtime’ fileserver to a new hypervisor host, implemented a ‘hot standby’ server as a backup kept up to date by the minute with DFS replication.
-Replaced failing hard drives in a RAID array underlying their one ‘business critical’ fileserver, which had no backups for 3 months at that time
-Reorganized Active Directory and Group Policy deployment from a nightmare spiderweb of OUs and duplicate policies
-Documented the entire old network and now the new one as I’ve been upgrading this
-Audited the developers AWS instances and removed redundant machines, optimized load balancing on front end Nginx servers, joined developer run Fedora workstations to the AD domain and implemented centralized syslog monitoring on them.
-Performed network scans and rewrote firewall exceptions to tighten security
There’s more, but you get the idea. I’ve now been tasked with taking point on an upcoming PCI audit which will be my first.
I’m being paid $16/hr US, with marginal health benefits. This is roughly $32,000 a year, before taxes.
I have two years previous work experience managing a third party Apple repair facility (SimplyMac) and every Apple certification for warranty repair and software troubleshooting. I have a two year degree in general sciences, with about 4 years of college credit (Two years of a physics education and two years of computer science after I switched focus) I’m actively pursuing a CCNA and MCSA server 2016 with exams paid for and scheduled.
I’m going into a salary negotiation in two months. What is a reasonable salary to request, from your perspective, for someone in my position?
Thanks in advance!7 -
Every meeting that contains one or more of the following points:
- "I don't think it belongs in the meeting, but"
- "Didn't get the meeting notes"
- "When's the food coming?"
- "I know we've said no technical discussion, but..."
- "Why is he so strict, this is no fun meeting at all :("
- "I think it's unfair to include risk assessment, you blame US before XY is finished"
- "The admins / the Team XY / ZX didn't talk with us, so we don't talk with him / her / them..."
- "Why are we here?"
- "Why is it so bad when production is down?"
- "I didn't know we do security / audit checks... Why hasn't anyone told us?"
- "Not happening. I'm against it"
- "I don't want to work with XY - he doesn't do it like I want it"
...
I could add thousand more things here.
I had countless meetings where I really thought that I was an alien who got broadcasted in a comedy reality TV soap...9 -
Few years ago I was asked to give advice on a project. There was an intern doing all the work and I even gave him almost ready code to use. And he didn't use it even properly.
And best part is that they thought at the time that it would be finished in couple of months.
After few months I took over and had to deal with the "intern code". Almost all of the code is rewritten.
Status of the project is now very good. We are implementing new features and it has even passed strict security audit done by other company.
Sadly I can't drop any names etc due to NDA.4 -
If only NPM' security team (so pretty much NSP's) would inform the package owners as soon as they discover vulnerabilities and give them the standard 30-90 days to fix them and release a new version before going public, instead of straight out publishing the security audits which generates noise on the terminal (obviously when using npm) and on Github
-
Got to do some security audit of legacy ABAP code for SAP systems. Do people still use it? If yes, why.3
-
From the look of https://github.com/yarnpkg/berry/..., Microsoft is not (yet) planning to hug "npm audit" as a great evil plan of asserting dominance to the open source community by raising everything into NatSec level and force shortcut releases.
If that's the case alternatives like yarn and pnpm will be removed from the scene, VS Code will be intentionally made incompatible with Yarn's PNP just like how NPM sneaks https://github.com/npm/arborist/... through, under the name of security.
I am still not convinced, it is Microsoft after all. We'll see.
P.S. I will laugh menacingly if that turns out to be ONLY a stupid dream and a poor decision of one single genius businessman. -
APM BILLING: Providing HIPAA-Compliant Billing Services You Can Trust
In today’s healthcare landscape, maintaining patient privacy and data security is paramount. Healthcare providers must adhere to strict standards to protect sensitive information while ensuring that financial operations are smooth and efficient. APM BILLING, based in Philadelphia, Pennsylvania, is dedicated to providing HIPAA-compliant billing services that ensure the highest level of security and compliance, while also optimizing the billing process for healthcare providers.
What Are HIPAA-Compliant Billing Services?
HIPAA (Health Insurance Portability and Accountability Act) establishes strict rules to ensure that healthcare providers maintain patient privacy and the confidentiality of their health information. As part of our commitment to protecting patient data, APM BILLING offers HIPAA-compliant billing services that meet all of the requirements set forth by this regulation.
Our HIPAA-compliant billing services ensure that all personal health information (PHI) handled during the billing and claims process remains secure. From data encryption to secure transmission, we follow the highest security standards to prevent unauthorized access, breaches, and other vulnerabilities.
Why Is HIPAA Compliance Critical for Healthcare Billing?
For any healthcare business, staying HIPAA-compliant is not just a regulatory necessity—it's essential to maintaining trust with patients and avoiding costly penalties. Non-compliance can result in hefty fines, lawsuits, and damage to your reputation. When it comes to billing, ensuring that all processes follow HIPAA guidelines is critical in preventing unauthorized access to sensitive patient data.
APM BILLING takes privacy and security seriously. Our team is well-versed in all HIPAA regulations, so you can trust that your patient data is always protected. We integrate comprehensive security protocols into our billing workflows, including:
Encrypted communications for all patient data exchanges
Secure data storage that meets HIPAA standards
Audit trails to track access to patient information and billing details
Employee training to ensure that everyone handling sensitive data understands HIPAA guidelines
The Benefits of Working with APM BILLING for HIPAA-Compliant Billing Services
By choosing APM BILLING, you gain the peace of mind that comes with knowing your billing processes are in full compliance with HIPAA regulations. Here are some of the key benefits of our HIPAA-compliant billing services:
Data Security: We use the latest technology to protect patient information, ensuring that all billing data is securely transmitted and stored.
Regulatory Compliance: Our team stays up-to-date with the latest changes to HIPAA regulations, ensuring that your practice remains compliant with all legal requirements.
Reduced Risk of Penalties: HIPAA violations can lead to significant fines and penalties. By outsourcing your billing to APM BILLING, you minimize the risk of compliance issues and the associated costs.
Enhanced Trust: Patients trust healthcare providers to keep their personal and medical information safe. By using our HIPAA-compliant billing services, you show your commitment to maintaining privacy, which fosters trust and enhances your reputation.
Efficiency and Accuracy: In addition to security, we ensure that your billing processes are efficient and accurate, leading to faster claim submissions, reduced denials, and increased revenue.
Why Choose APM BILLING for HIPAA-Compliant Billing Services?
Expertise: Our experienced team is dedicated to ensuring that all of your billing practices comply with HIPAA guidelines.
Tailored Solutions: We offer customized solutions that meet the specific needs of your healthcare practice, whether you’re a clinic, provider, or specialty office.
Focus on Security: We take security seriously and use state-of-the-art systems to protect all sensitive information.
Reliable Support: With APM BILLING, you’ll have a trusted partner in billing that is committed to safeguarding your practice’s financial and data integrity.
Get Started with APM BILLING Today
At APM BILLING, we understand the importance of maintaining HIPAA-compliant billing services in today's healthcare environment. We are here to help your practice stay secure, compliant, and financially efficient.
Contact us today at +1-800-621-3354 to learn more about how we can help streamline your billing process while ensuring complete protection of patient data. Visit our office at 19104 Philadelphia, Pennsylvania, and let APM BILLING handle your billing needs with the utmost professionalism and care.
Let APM BILLING take the stress out of billing while keeping your practice compliant with HIPAA regulations, so you can focus on what matters most—caring for your patients.2 -
9 Ways to Improve Your Website in 2020
Online customers are very picky these days. Plenty of quality sites and services tend to spoil them. Without leaving their homes, they can carefully probe your company and only then decide whether to deal with you or not. The first thing customers will look at is your website, so everything should be ideal there.
Not everyone succeeds in doing things perfectly well from the first try. For websites, this fact is particularly true. Besides, it is never too late to improve something and make it even better.
In this article, you will find the best recommendations on how to get a great website and win the hearts of online visitors.
Take care of security
It is unacceptable if customers who are looking for information or a product on your site find themselves infected with malware. Take measures to protect your site and visitors from new viruses, data breaches, and spam.
Take care of the SSL certificate. It should be monitored and updated if necessary.
Be sure to install all security updates for your CMS. A lot of sites get hacked through vulnerable plugins. Try to reduce their number and update regularly too.
Ride it quick
Webpage loading speed is what the visitor will notice right from the start. The war for milliseconds just begins. Speeding up a site is not so difficult. The first thing you can do is apply the old proven image compression. If that is not enough, work on caching or simplify your JavaScript and CSS code. Using CDN is another good advice.
Choose a quality hosting provider
In many respects, both the security and the speed of the website depend on your hosting provider. Do not get lost selecting the hosting provider. Other users share their experience with different providers on numerous discussion boards.
Content is king
Content is everything for the site. Content is blood, heart, brain, and soul of the website and it should be useful, interesting and concise. Selling texts are good, but do not chase only the number of clicks. An interesting article or useful instruction will increase customer loyalty, even if such content does not call to action.
Communication
Broadcasting should not be one-way. Make a convenient feedback form where your visitors do not have to fill out a million fields before sending a message. Do not forget about the phone, and what is even better, add online chat with a chatbot and\or live support reps.
Refrain from unpleasant surprises
Please mind, self-starting videos, especially with sound may irritate a lot of visitors and increase the bounce rate. The same is true about popups and sliders.
Next, do not be afraid of white space. Often site owners are literally obsessed with the desire to fill all the free space on the page with menus, banners and other stuff. Experiments with colors and fonts are rarely justified. Successful designs are usually brilliantly simple: white background + black text.
Mobile first
With such a dynamic pace of life, it is important to always keep up with trends, and the future belongs to mobile devices. We have already passed that line and mobile devices generate more traffic than desktop computers. This tendency will only increase, so adapt the layout and mind the mobile first and progressive advancement concepts.
Site navigation
Your visitors should be your priority. Use human-oriented terms and concepts to build navigation instead of search engine oriented phrases.
Do not let your visitors get stuck on your site. Always provide access to other pages, but be sure to mention which particular page will be opened so that the visitor understands exactly where and why he goes.
Technical audit
The site can be compared to a house - you always need to monitor the performance of all systems, and there is always a need to fix or improve something. Therefore, a technical audit of any project should be carried out regularly. It is always better if you are the first to notice the problem, and not your visitors or search engines.
As part of the audit, an analysis is carried out on such items as:
● Checking robots.txt / sitemap.xml files
● Checking duplicates and technical pages
● Checking the use of canonical URLs
● Monitoring 404 error page and redirects
There are many tools that help you monitor your website performance and run regular audits.
Conclusion
I hope these tips will help your site become even better. If you have questions or want to share useful lifehacks, feel free to comment below.
Resources:
https://networkworld.com/article/...
https://webopedia.com/TERM/C/...
https://searchenginewatch.com/2019/...
https://macsecurity.net/view/...
-
HOW TO HIRE A BITCOIN RECOVERY EXPERT HIRE ADWARE RECOVERY SPECIALIST
I had spent $410,000 worth of Bitcoins for the sole cause of keeping alive the passion for the conservation of historical documents and valuable manuscripts rotting over the centuries. This was the work for the remainder of my lifetime, keeping history alive. But all this could have slipped by through one small error.
I lost the seed word. It happened when the office where I work went through its routine sorting through the archives. I'd scrawled my seed word and stuck it somewhere amidst the notes, deeming this the safest possible location. But when the sections were shuffled for work being undertaken, the papers were shuffled around, re-piled, and some bitterly discarded. My seed word vanished into the mixture. WhatsApp info:+12723328343
When I learned about what had taken place, I felt sick. That the Bitcoin wasn't mere money; the destiny of our conservation campaign hung here. That the idea I'd risked everything for something like this being one misplaced detail weighed heavily upon me. Email info: Adware recovery specialist (@) auctioneer. net
For weeks, I combed through each and every doc, each and every directory. Nothing. I'd given up until one day when one of the office researchers, also one from the research side, heard about ADWARE RECOVERY SPECIALIST when he was studying blockchains. Like a small beam of light. Website info: http s:// adware recovery specialist. com
I contacted their support, and from the very start, when the very first call went through, their attitude towards me was respectful and patient. They did not mock me for the mistake—instead, treated the situation like some historical riddle waiting for deciphering. They were prepared from their side with professionals for data recovery under complex circumstances. Even for the conservation of virtual resources like Bitcoin, they had professionals. They worked together with me, stitching together the fragments and morsels that even I hadn't known were worth anything. They were able to recover some of the data lost by using creative recovery procedures, showing the progress the field has made. Telegram info: http s:// t.me/ adware recovery specialist1
Within two weeks the wallet became recoverable. $410,000,all the money was recovered. I was shocked and over the hill.
Beyond just recovering the investment, ADWARE RECOVERY SPECIALIST also introduced me to some very valuable services, such as wallet security audit and long-term security plans for the digital assets, about which I hadn't even heard earlier. They not only saved my project, but also helped make me secure it even better for the future. Thanks to them, the future and the past is secure.2 -
HOW TO RECOVER YOUR STOEN BITCOIN: HIRE A HACKER, TRUST GEEKS HACK EXPERT
The stakes were catastrophic when a sophisticated CEO fraud scam siphoned $500,000 from Titan Blockchain Ventures, a leading crypto asset management firm based in New York City. We faced not just financial loss, but severe reputational damage, investor panic, and the potential for layoffs. The scam was executed with alarming precision, and the speed at which the funds disappeared left us in shock. Our internal IT team worked tirelessly, but they quickly hit dead ends. The dark web’s complexity, coupled with the fraudsters' advanced tactics, made tracing the assets nearly impossible. Worse still, law enforcement advised that their investigation would take months, time we didn’t have. Desperate for a solution, we turned to Trust Geeks Hack Expert, Website, a firm highly recommended within the industry. Trust Geeks Hack Expert corporate division acted with unmatched urgency and precision. Within hours of our engagement, Trust Geeks Hack Expert team Telegram: Trust-geeks-hack-expert began mapping the stolen funds across dark web markets using cutting-edge blockchain forensics. Their expertise was immediately evident as Trust Geeks Hack Expert traced every transaction, pinpointing wallet addresses and exchanges with surgical accuracy. What truly set Trust Geeks Hack Expert apart was their proactive approach. Trust Geeks Hack Expert didn’t just trace the funds they acted swiftly to freeze further transactions. By leveraging their vast international network of exchange partners, Trust Geeks Hack Expert halted the movement of the stolen crypto in real time, preventing any additional losses. Their swift, coordinated efforts resulted in the recovery of 92% of the stolen assets in under two weeks a remarkable achievement that most thought impossible. But Trust Geeks Hack Expert didn’t stop at asset recovery. Trust Geeks Hack Expert also provided us with a comprehensive compliance roadmap. Their post-recovery audit identified critical vulnerabilities in our security systems and recommended both practical and visionary solutions to strengthen our defenses. Thanks to Trust Geeks Hack Expert we were given clear, actionable steps to prevent future breaches and fortify our infrastructure.2 -
I put $620,000 of Bitcoin into making my dream happen—building an AI business that would push robotics and machine learning to new levels. It wasn't an investment; it was the future years of my life I had been building toward. That future was wiped out because of one minor mistake in my own code.
I had programmed a custom wallet to hold my Bitcoin, feeling it would add an extra level of security and independence. Things were fine until the day a small bug left me locked out. My password was correct, but the wallet refused to unlock. My pulse was pounding as I tried time and again, each attempt drying my palms out a little more.
I was going crazy for weeks attempting to fix it. I pored over lines of my own code, applied patches, and even went the brute force method. None of it worked. It was as if I had built a fortress only to trap myself in it.
I was at my wit's end when I saw a thread on GitHub. Brought out from the depths of comments, someone mentioned WIZARD WEB RECOVERY SERVICES . I was desperate at this point and out of ideas.
The moment I contacted them, I knew I was in capable hands. Their personnel were not only skilled, they understood what this would do for me. They asked me extremely specific questions regarding my custom software, respected my work, and assured me they had dealt with cases like mine before.
Their approach was surgical. They reverse-engineered my wallet code like it was a blueprint, dissecting every line I had written. It was a humbling experience to watch their expertise at work. They kept me apprised step by step, giving me hope when I believed all hope was lost.
Eight days went by, and then I received the call I had been hoping for. They cracked it. My wallet was restored to its fullness, all of my $620,000 still there and ready to power my startup once again.
Apart from recovery, they also educated me on secure coding principles and introduced me to wallet audit services that would prevent such occurrences from happening again.
Thanks to WIZARD WEB RECOVERY SERVICES , my robots will keep dancing, and my dream is still alive. If you ever find yourself locked out, don't spend weeks like I did—call them immediately. 1
1