Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "password list"
-
So here I am... thinking to myself how does this kid not know about the shift key?
Me: "Ok we're going to test see if you have sudo access. Please enter your password, now"
Student: ~stares at the black terminal box and begins pressing the caps lock key. The light doesn't display~
Student: "Um... what? Do I need to enter a new password?"
Me: "No"
Continues to click the caps-lock button and waiting for a light to appear on the keyboard. It doesn't. He continues clicking.
Me: "You need to press the shift button"
Him: "What???"
Me: "You need to press the shift button"
Him: "Um.. I don't understand"
Him: Presses shift button, nothing happens. Goes back to pressing caps lock button.
Me: "Your password has a capital letter in it right?"
Him: "Um... yeah."
Me: "Press the shift button to capitalize your letters."
Him: "I don't understand... Do I need to enter a new password?"
Me: "No... you need to press and hold the shift key to get a capital letter"
Him: "................................ ............................................ . . . . . .. .. .. .. .. .. . . . . . . . . . . . . ...................... . . . . . . . Oh..."
Him: "Presses and holds the shift button with his thumb and then presses the Z key."
Me: ~What in the hell are you doing?~ 🤦
Me: "Perfect it looks like you are a part of the sudoers list."
Me: "You can take you computer back."
Me: ~Do you fucking use the caps lock key to capitalize all the first letters in your sentences? Please tell me you don't!~rant get rid of the caps lock i think he's a transfer student my accent was too strong what are you doing13 -
Worst WTF dev experience? The login process from hell to a well-fortified dev environment at a client's site.
I assume a noob admin found a list of security tips and just went like "all of the above!".
You boot a Linux VM, necessary to connect to their VPN. Why necessary? Because 1) their VPN is so restrictive it has no internet access 2) the VPN connection prevents *your local PC* from accessing the internet as well. Coworkers have been seen bringing in their private laptops just to be able to google stuff.
So you connect via Cisco AnyConnect proprietary bullshit. A standard VPN client won't work. Their system sends you a one-time key via SMS as your password.
Once on their VPN, you start a remote desktop session to their internal "hopping server", which is a Windows server. After logging in with your Windows user credentials, you start a Windows Remote Desktop session *on that hopping server* to *another* Windows server, where you login with yet another set of Windows user credentials. For all these logins you have 30 seconds, otherwise back to step 1.
On that server you open a browser to access their JIRA, GitLab, etc or SSH into the actual dev machines - which AGAIN need yet another set of credentials.
So in total: VM -> VPN + RDP inside VM -> RDP #2 -> Browser/SSH/... -> Final system to work on
Input lag of one to multiple seconds. It was fucking unusable.
Now, the servers were very disconnect-happy to prevent anything "fishy" going on. Sitting at my desk at my company, connected to my company's wifi, was apparently fishy enough to kick me out every 5 to 20 minutes. And that meant starting from step 1 inside the VM again. So, never forget to plugin your network cable.
There's a special place in hell for this admin. And if there isn't, I'll PERSONALLY make the devil create one. Even now that I'm not even working on this any more.8 -
I absolutely love the email protocols.
IMAP:
x1 LOGIN user@domain password
x2 LIST "" "*"
x3 SELECT Inbox
x4 LOGOUT
Because a state machine is clearly too hard to implement in server software, clients must instead do the state machine thing and therefore it must be in the IMAP protocol.
SMTP:
I should be careful with this one since there's already more than enough spam on the interwebs, and it's a good thing that the "developers" of these email bombers don't know jack shit about the protocol. But suffice it to say that much like on a real letter, you have an envelope and a letter inside. You know these envelopes with a transparent window so you can print the address information on the letter? Or the "regular" envelopes where you write it on the envelope itself?
Yeah not with SMTP. Both your envelope and your letter have them, and they can be different. That's why you can have an email in your inbox that seemingly came from yourself. The mail server only checks for the envelope headers, and as long as everything checks out domain-wise and such, it will be accepted. Then the mail client checks the headers in the letter itself, the data field as far as the mail server is concerned (and it doesn't look at it). Can be something else, can be nothing at all. Emails can even be sent in the future or the past.
Postfix' main.cf:
You have this property "mynetworks" in /etc/postfix/main.cf where you'd imagine you put your own networks in, right? I dunno, to let Postfix discover what your networks are.. like it says on the tin? Haha, nope. This is a property that defines which networks are allowed no authentication at all to the mail server, and that is exactly what makes an open relay an open relay. If any one of the addresses in your networks (such as a gateway, every network has one) is also where your SMTP traffic flows into the mail server from, congrats the whole internet can now send through your mail server without authentication. And all because it was part of "your networks".
Yeah when it comes to naming things, the protocol designers sure have room for improvement... And fuck email.
Oh, bonus one - STARTTLS:
So SMTP has this thing called STARTTLS where you can.. unlike mynetworks, actually starts a TLS connection like it says on the tin. The problem is that almost every mail server uses self-signed certificates so they're basically meaningless. You don't have a chain of trust. Also not everyone supports it *cough* government *cough*, so if you want to send email to those servers, your TLS policy must be opportunistic, not enforced. And as an icing on the cake, if anything is wrong with the TLS connection (such as an MITM attack), the protocol will actively downgrade to plain. I dunno.. isn't that exactly what the MITM attacker wants? Yeah, great design right there. Are the designers of the email protocols fucking retarded?9 -
About a year ago I switched my job.
At the start everything seemed like magic. I was the It director, I've finally was able to call the shots on technologies, on new software architecture.
First step was to check the current state of the company.
"qqqq" as each pc password? Ok
No firewall from outside? Lovely
Servers running on Windows Server 2008? Spectacular
People leaving pc on after work and left the machine unlocked just not to type the password? Hell yeah
The IT dude playing games instead of working? But ofcourse
Plaintext passwords publically accessible eshop? Naturally.
The list goes on and on.
After all this time, I'm working to fix every hole like that like crazy and because it doesn't show results, I'm soon to lose my job. Well better luck next time as an intern I guess :')19 -
I'm fixing a security exploit, and it's a goddamn mountain of fuckups.
First, some idiot (read: the legendary dev himself) decided to use a gem to do some basic fucking searching instead of writing a simple fucking query.
Second, security ... didn't just drop the ball, they shit on it and flushed it down the toilet. The gem in question allows users to search by FUCKING EVERYTHING on EVERY FUCKING TABLE IN THE DB using really nice tools, actually, that let you do fancy things like traverse all the internal associations to find the users table, then list all users whose password reset hashes begin with "a" then "ab" then "abc" ... Want to steal an account? Hell, want to automate stealing all accounts? Only takes a few hundred requests apiece! Oooh, there's CC data, too, and its encryption keys!
Third, the gem does actually allow whitelisting associations, methods, etc. but ... well, the documentation actually recommends against it for whatever fucking reason, and that whitelisting is about as fine-grained as a club. You wanna restrict it to accessing the "name" column, but it needs to access both the "site" and "user" tables? Cool, users can now access site.name AND user.name... which is PII and totally leads to hefty fines. Thanks!
Fourth. If the gem can't access something thanks to the whitelist, it doesn't catch the exception and give you a useful error message or anything, no way. It just throws NoMethodErrors because fuck you. Good luck figuring out what they mean, especially if you have no idea you're even using the fucking thing.
Fifth. Thanks to the follower mentality prevalent in this hellhole, this shit is now used in a lot of places (and all indirectly!) so there's no searching for uses. Once I banhammer everything... well, loads of shit is going to break, and I won't have a fucking clue where because very few of these brainless sheep write decent test coverage (or even fucking write view tests), so I'll be doing tons of manual fucking testing. Oh, and I only have a week to finish everything, because fucking of course.
So, in summary. The stupid and lazy (and legendary!) dev fucked up. The stupid gem's author fucked up, and kept fucking up. The stupid devs followed the first fuckup's lead and repeated his fuck up, and fucked up on their own some more. It's fuckups all the fucking way down.rant security exploit root swears a lot actually root swears oh my stupid fucking people what the fuck fucking stupid fucking people20 -
Sending a confirmation email to a newly created account with both the user name and password in the mail body.
See here for a list:
http://plaintextoffenders.com2 -
One of our newly-joined junior sysadmin left a pre-production server SSH session open. Being the responsible senior (pun intended) to teach them the value of security of production (or near production, for that matter) systems, I typed in sudo rm --recursive --no-preserve-root --force / on the terminal session (I didn't hit the Enter / Return key) and left it there. The person took longer to return and the screen went to sleep. I went back to my desk and took a backup image of the machine just in case the unexpected happened.
On returning from wherever they had gone, the person hits enter / return to wake the system (they didn't even have a password-on-wake policy set up on the machine). The SSH session was stil there, the machine accepted the command and started working. This person didn't even look at the session and just navigated away elsewhere (probably to get back to work on the script they were working on).
Five minutes passes by, I get the first monitoring alert saying the server is not responding. I hoped that this person would be responsible enough to check the monitoring alerts since they had a SSH session on the machine.
Seven minutes : other dependent services on the machine start complaining that the instance is unreachable.
I assign the monitoring alert to the person of the day. They come running to me saying that they can't reach the instance but the instance is listed on the inventory list. I ask them to show me the specific terminal that ran the rm -rf command. They get the beautiful realization of the day. They freak the hell out to the point that they ask me, "Am I fired?". I reply, "You should probably ask your manager".
Lesson learnt the hard-way. I gave them a good understanding on what happened and explained the implications on what would have happened had this exact same scenario happened outside the office giving access to an outsider. I explained about why people in _our_ domain should care about security above all else.
There was a good 30+ minute downtime of the instance before I admitted that I had a backup and restored it (after the whole lecture). It wasn't critical since the environment was not user-facing and didn't have any critical data.
Since then we've been at this together - warning engineers when they leave their machines open and taking security lecture / sessions / workshops for new recruits (anyone who joins engineering).26 -
Best part about the covid19 manufactured crisis?
Liquor stores deliver. Worst part about liquor stores delivering? Needing to use their shoddy websites.
I've been using a particular store (Total Wines) since they're cheaper than the rest and have better selection; it's quite literally a large warehouse made to look like a store.
Their website tries really hard to look professional, too, but it's just not. It took me two days to order, and not just from lack of time -- though from working 14 hour days, that's a factor.
Signing up was difficult. Your username is an email address, but you can't use comments because the server 500s, making the ajax call produce a wonderfully ambiguous error message. It also fades the page out like it's waiting on something, but that fade is on top of the error modal too. Similar error with the password field, though I don't remember how I triggered it.
Signing up also requires agreeing to subscribe to their newsletter. it's technically an opt-in, but not opting-in doesn't allow you to proceed. Same with opting-in to receiving a text notification when your order is ready for pickup -- you also opt-in to reciving SMS spam.
Another issue: After signing up, you start to navigate through the paginated product list. Every page change scrolls you to the exact middle of the next page. Not deliberatly; the UI loads first, and the browser gets as close as it can to your previous position -- which was below that as the pagination is at the bottom -- and then the products populate after. But regardless of why, there is no worse place to start because now you must scroll in both directions to view the products. If it stayed at the very bottom, it would at least mean you only need to scroll upwards to look at everything on the page. Minor, but increasingly irritating.
Also, they have like 198 pages of spirits alone because each size is unique entry. A 50ml, 350ml, 500ml, 750ml, 1000ml, and 1750ml bottle of e.g. Tito's vodka isn't one product, it's six. and they're sorted seemingly randomly. I think it's by available stock, looking back.
If you fancy a product, you can click on it for a detail page. Said detail page lists the various sizes in a dropdown, but they're not sorted correctly either, and changing sizes triggers a page reload, which leads to another problem:
if you navigate to more than a few pages within a 10 or so second window, the site accuses you of using browser automation. No captcha here, just a "click me for five seconds" button. However, it (usually) also triggers the check on every other tab you have open after its next nagivation.
That product page also randomly doesn't work. I haven't narrowed it down, but it will randomly decide to start failing, and won't stop failing for hours. It renders the page just fine, then immediately replaces it with a blank page. When it's failing, the only way to interact with the page is a perfectly-timed [esc], which can (and usually does) break all other page functionality, too. Absolutely great when you need to re-add everything from a stale copy of your signed-out cart living in another tab. More on that later. And don't forget to slow down to bypass the "browser automation" check, too!
Oh, and if you're using container tabs, make sure to open new tabs in the SAME container, as any request from the same IP without the login cookie will usually trigger that "browser automation" response, too.
The site also randomly signs you out, but allows you to continue amassing your cart. You'd think this is a good thing until you choose to sign in again... which empties your cart. It's like they don't want to make a sale at all.
The site also randomly forgets your name, replacing it with "null." My screen currently says "Hello, null". Hello, cruft!
It took me two days to order.
Mostly from lack of time, as i've been pulling 14 hour shifts lately trying to get everything done. but the sheer number of bugs certainly wasted most of what little time i had left. Now I definitely need a drink.
But maybe putting up with all of this is worthwhile because of their loyalty program? Apparently if you spend $500, you can take $5 off your next purchase! Yay! 1%! And your points expire! There are three levels; maybe it gets better. Level zero is for everyone; $0 requirement. There are also levels at $500 and $2500. That last one is seriously 5x more than the first paid level. and what does it earn you? A 'free' magazine subscription, 'free' classes (they're usually like $20-$50 iirc), and a 'free' grab bag (a $2.99 value!) twice per month. All for spending $2500. What a steal. It reminds me of Candy Crush's 3-star system where the first two stars are trivial, and the third is usually a difficult stretch goal. But here it's just thinly-veiled manipulation with no benefit.
I can tell they're employing some "smarketing" people with big ideas (read: stolen mistakes), but it's just such a fail.
The whole thing is a fail.7 -
Are there any website or public list that shame companies and websites for sending passwords in plaintext whenever we tend to reset the password?6
-
Part of a product I used to work on contained a one time password generator that randomly strung together a few words from a word list.
Nothing wrong with the security, but this word list hadn't been filtered, so we did have a "bug report" from a customer who had a one time password that contained a questionable phrase:
"fucking pork Muslim"
...Call me a terrible person, but I never did get around to fixing that...3 -
!dev but actual long rant - about the students in my grade.
TL;DR: 1 asshole in 10 people can ruin everything. Mobbing sucks. I dislike parties.
There's the word "Jahrgang" in Germany which means the people in the same school year as you. I'll refer to it as "my (collective) classmates" although we don't have classes anymore, rather courses and I also mean those I do not have courses with.
With that out of the way, let the rant begin.
It's often the case that people with high logical and intellectual skills (no being arrogant, other people categorize me like that) have a lack of social skills - or empathy.
I'm a kind of an outsider in a way that since 10th grade I stopped trying to attach myself to certain groups since I do not fit in there. I'm fine with that now. Nowadays I can at least socialize with other nerds.
Here's why I dislike the collective of my classmates. This year is my last school year and as always, a big group forms a spirit. They have a theme (superheroes - super boring). I didn't go to any party they threw and I don't plan to go to the graduation ceremony as well since it's an unofficial party and not a school event. I hate parties. I hate alc and drunken teenagers. I didn't attend the "Kursfahrt" - a kind of excursion that's like holidays with your course - mainly because I dislike my "Stammkurs" (main course).
Why? I had a friend in this course. She was short, geeky and I could actually talk to her. Yet some jerks (not intensely) bullied her because "she was awkward" and in the end, she switched school - also because of other reasons.
When she was gone, even those who didn't bully her and who are considered "nice" made fun of her and talked badly about her - and me hanging around with her. So since then, I avoid anything with them that's not 100% school related.
Now they're planning what we call "Abigag" - it's a joke/prank the graduates pull on the school and younger students, something funny like an entrance room full of balloons and many other things. Also, the "Abizeitung", the yearbook the graduates put out with articles about their courses, teacher ranking and quotes etc. Also, a cabaret evening from the graduates to collect money for the graduation party. Cool stuff actually. I thought about taking part.
I'd say my talents are creativity and computer stuff. So a friend chatted with me about nerdy pranks like a school-wide wallpaper change. Or releasing a fake password list of the teachers - claiming we hacked them - with puns and insiders about the teaches. He said he gotta invite me into the WhatsApp group of the Abi prank. Disclaimer: He's one of those people who are socialized but still able to talk with me. He's fine.
Well guess what he told me later:
They don't want me on the team since I distance myself from my classmates. I should either be fully one of them or not at all.
That's enough. Who distances whom? I thought they were happy to have me on board but horse shit! Stuck with ideologies from the 19th century.
They can lick my ***. I don't have anything against most of them in person but as a collective, they're just fucking stupid. I guess it wasn't even the majority saying they don't want me to help. It was probably just the small crew of leading and loud jerks. And no one would disagree with them saying "Why not? He wants to help?" (even if it was their opinion) - they don't have the brain or balls to say anything against the strong idiot leaders. They'll do great later in politics as an adult - they wouldn't criticize Hitler if they were under his "protection".
So I won't take part in making Abi pranks, - but also not the Paper and cabaret eve. They can go jerk off to being part of a huge collection of assholes - which I, in all my pride, am not part of other than on paper.
(Disclaimer: No critics to other outsiders but those who were engaged and responsible for the choice of not letting me help)
If anyone actually read this:
Who were/are you in school times?
A proud outsider like me? Party boi/girl? Engaged striver?25 -
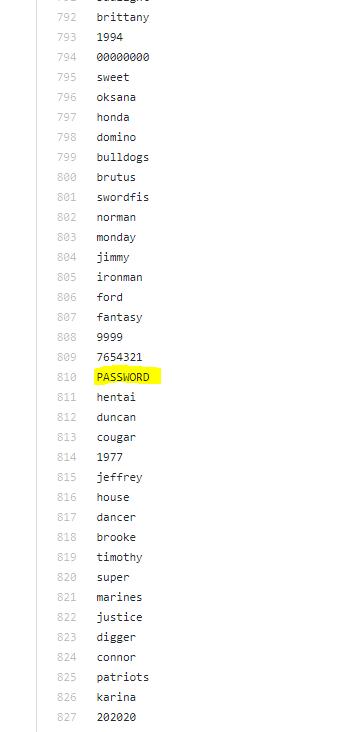
Was looking through the most used passwords list (the one that had 'removed my password from lists...'). 'password' is like one of the top one, and then 'PASSWORD' is 810th !?!?!?! At least it's before hentai...
 8
8 -
Recently started at a new job. Things were going fine, getting along with everyone, everything seems good and running smoothly, a few odd things here and there but for the most part fine.
Then I decided to take a look at our (public facing) website... What's this? Outdated plugins from 2013? Okay, that's an easy fix I guess? All of these are free and the way we're using them wouldn't require a lot of refactoring...
Apparently not. Apparently, we can't even update them ourselves, we have to request that an external company does it (which we pay, by the way, SHITELOADS of money to). A week goes past, and we finally get a response.
No, we won't update it, you'll have to pay for it. Doesn't matter that there's a CVE list a bloody mile long and straight up no input validation in several areas, doesn't matter that tens of thousands of users are at risk, pay us or it stays broken. Boggles the fuckin' mind.
I dug into it a bit more than I probably should have (didn't break no laws though I'm not a complete dumbass, I just work for em) and it turns out it's not just us getting fucked over, it's literally EVERYONE using their service which is the vast majority of people within the industry in my country. It also turns out that the entirety of our region is running off a single bloody IP which if you do a quick search on shodan for, you guessed it, also has a CVE list pop up a fuckin' mile long. Don't get me started on password security (there is none). I hate this, there's fucking nothing I can do and everyone else is just fine sitting on their hands because "nobody would target us because we're not a bank!!", as if it bloody matters and as if peoples names, addresses, phone numbers and assuming someone got into our actual database, which wouldn't be a fuckin' stretch of the imagination let me tell you, far more personal details, that these aren't enticing to anyone.
What would you do in my situation?
What can I even do?
I don't want to piss anyone senior off but honestly, I'm thinkin' they might deserve it. I mean yeah there's nothing we can do but at least make a fuss 'cause they ain't gunna listen to my green ass.10 -
If we compare this list with last year’s list, nothing much has changed. The top three worst passwords of last year were ‘123456’, ‘password’, and ‘123456789’. Source : Splashdata
Top 10 worst passwords in 2019 below:
1. 123456
2. 123456789
3. qwerty
4. password
5. 1234567
6. 12345678
7. 12345
8. iloveyou
9. 111111
10. 12312314 -
So to start off this happened today while I was at school.
Each student gets a netbook for school and the amount of restrictions put in place are probably up to government spec. Well I brought in my personal netbook and a flash drive with a few distros of Linux on it on it to mess with during study hall(all on my own hardware).
I told my friend that about it and said I doubted it would boot because the bios is password protected and the IT guy probably removed external drives from the boot list but let him use it anyway.
5 minutes later he is showing me his screen with Ubuntu running on it, I was freaking out some and asked for it back and he gave it back to me.
About a minute later he shows me his screen. All black with white text shooting down it saying windows disk integrity check or something like that. All I see is "file xyz deleted" and was freaking out even more. I just sat there for the next 20 minutes thinking of how to explain this to the IT guy and hopefully get in less trouble.
Finally after the longest 20 minutes of my life as a student I see the windows 7 boot screen appear. Probably the one time I actually wanted to see it honestly but I was so happy to see the end of the situation.
Sorry this was so long but I hope it's fine for a first post here, I've been putting it off but after this decided to finally post.3 -
So, among the ridiculously long list of password requirements, password is not case sensitive BUT it has to contain uppercase and lowercase letters?
 14
14 -
I had security reopen our test-user last week. I could run the tests once, then they started failing with "blocked user due to too many attempts at logging in". Huh, that's weird. I go through everything, every script, every scheduled task, every nook and cranny of every drive on every machine I could reach, and make sure the password is updated everywhere. Reopen account. Same shit.
I email around to some people, they don't use it, one guy asks if I checked x, y and z, I did. Then he's sure we don't use it anywhere else.
It's one of our fucking contractors that took one of our scripts (that they're supposed to have duplicate copies of) and forgot to change to their own credentials. That's literally the agreement, take our scripts and change the user and run them on your machines.
Afhfjdkdhdjdbd stop locking me out of everything with your incompetence. I email them, some cunt gets back to me asking for the new password. NO. USE. YOUR. OWN. CREDENTIALS. I KNOW YOU HAVE THEM, THEY'RE HERE IN THE LIST AND BEING USED IN ALL OTHER SCRIPTS AAAAAAAAAHHH6 -
I once agreed to maintain and develop an application used in a different section of the school to keep inventory and make sure everything is where it is supposed to be.
At first there was enthusiasm, together with 2 of my classmates we agreed and git clone-d the .NET application that now graduated students built and maintained for the past few years. What could go wrong right?!
It became clear that the original students that worked on it followed an older curriculum, meaning they still got taught .NET instead of the core variant that we get now, not only that but it also seemed that they either did not fully grasp the Clean/Onion architecture or didn't get it in class since there were infrastructure components in the 'Domain' project of the solution. Think of 2 DBContexts in the domain model, yep.
One of us bailed in the first week, the other one and I felt bad for the people using the app so we went on and tried to work on the first bugs that were described in a document. One of these bugs was 'whenever I filter on something in the list, everybody gets to see that filter on their screen instead of only me'. Woah that's weird! Let's see how they put that together!
Oh god, they are using a _static_ variable to store filters, no wonder that it doesn't work properly. Ever heard of sessions?!
Second bug: Sometimes people can't create an account when we sign them up from the admin panel. Alright that is weird, let's figure that one out! Wait a second it seems to work in development? What's this about.
Oh wait I can't create an account on production either? Oh that's weird, wait a second... Why do I have to put my e-mail in a form that was sent to me through e-mail? Why is my address not filled in already? OOH, if someone types in the wrong e-mail address (which is easy since our school has 4 variants of the same f*cking e-mail address) it won't work since it can't recognize the user! Brilliant! Remove e-mail input box and make a token/queryparam determine the user account.
Ah that seems good, it's a mess but it seems a tiny bit better now, great! We're making progress and some sweet buck.
Next bug, trillions of 50x errors on random pages, that's a weird one.
Hm everything works in development, that's odd. Is the production data corrupted?
DID I MENTION that in order to get into the system in development we have to load in a f*cking production database backup ON OUR DEVELOPMENT MACHINE and then ask one of the users' password to login to it and create an account for ourselves? Seeding? What's that, right?!
Anyway, back to bug fixing. I e-mail the the people responsible for the app and get a production admin account, oh I also can't ssh into it because of policies so I have to do everything over e-mail and figure out what's causing the errors. I somehow also wonder if they have any kind of virtualization in place, giving students a VM to do that stuff in doesn't seem so weird does it ? Even with school policies?
Oh btw, 'deploying' means sending a .zip file to a guy in another building and telling him how to configure it, apparently this resulted in a missing folder that the application needed to work and couldn't make on its own. This after 2 weeks of e-mailing back and forth.
After 3 months i quit out of despair and sadness, and due to the fact that I just couldn't do it anymore. I separated everything into logical subprojects and let the last guy handle it, he was OK with that and understood why I left.
Luckily, around that time I already had an actual job at a software development company :)3 -
Few years ago as a junior android dev with couple years of self taught experience of working in startups I submitted a simple android app assignment for a junior android dev role. Assignment had only like 8 requirements so I followed them to the letter. That didn't end well.
App was simple just 3 screens. Login screen with username and password input fields, login button.
Had to call a login endpoint after login button was clicked, redirecting to home screen, calling items endpoint, displaying a list of items and when an item was clicked passing item data and redirect to item details screen.
Needless to say big swinging dick senior was not impressed. UI was not perfect, I forgot to display a loading animation when fetching data, didnt handle back button properly.
I agreed with some points but other comments were clearly just nitpicking: his preferred variable naming conventions, his opinions on architecture that was not up to his standard (official google arch at the time was not up to his standard).
He also was mad that app wasn't prepared for release to googleplay (another out of the ass requirement). Like I would prepare a 3 screen app for prod release that he will forget ever existed after 20min of his review.
Lots more of nitpicking, encapsulation this encapsulation that, omg now hes shocked that there are a few warnings after the project is built.
Regardless my self confidence was destroyed at that point and after few more negative experiences I dropped android dev alltogether for a couple years and switched to game dev.
After game dev ran its course I went back to android dev and found a supportive place where I could grow.
Looking back, they were actually hiring atleast a mid level for a junior position but I was grilled as a senior. The guy literally didnt wrote any single positive thing in that review about my code even tho my senior peers said my project was decent back then, its just that I didnt handle a few edge cases and that's all.
I looked up the guy in linkedin, turns out hes a uni dropout who posts all books that he red about software dev in his education section of his linkedin profile. Found a bunch of other narcissistic stuff on his profile. Guy was a fucking idiot. Even if I worked under him it would have probably sucked.
Learned some important lessons I guess. Always get a second, 3rd and 4th opinion and dont take criticism too seriously. Always check what kind of person is providing feedback.4 -
Am I the only guy using the GDPR emails as a to-do list? For each email I either delete the account with that service OR I take the opportunity to change the password. Tedious? Yeah. Satisfying? You bet!
I see all these people complaining about their inbox blowing up with "spam" but how many of those accounts or services do you still use? I bet over half of them were only signed up for to try their demo and then forgotten about.4 -
Whelp. I started making a very simple website with a single-page design, which I intended to use for managing my own personal knowledge on a particular subject matter, with some basic categorization features and a simple rich text editor for entering data. Partly as an exercise in web development, and partly due to not being happy with existing options out there. All was going well...
...and then feature creep happened. Now I have implemented support for multiple users with different access levels; user profiles; encrypted login system (and encrypted cookies that contain no sensitive data lol) and session handling according to (perceived) best practices; secure password recovery; user-management interface for admins; public, private and group-based sections with multiple categories and posts in each category that can be sorted by sort order value or drag and drop; custom user-created groups where they can give other users access to their sections; notifications; context menus for everything; post & user flagging system, moderation queue and support system; post revisions with comparison between different revisions; support for mobile devices and touch/swipe gestures to open/close menus or navigate between posts; easily extendible css themes with two different dark themes and one ugly as heck light theme; lazy loading of images in posts that won't load until you actually open them; auto-saving of posts in case of browser crash or accidental navigation away from page; plus various other small stuff like syntax highlighting for code, internal post linking, favouriting of posts, free-text filter, no-javascript mode, invitation system, secure (yeah right) image uploading, post-locking...
On my TODO-list: Comment and/or upvote system, spoiler tag, GDPR compliance (if I ever launch it haha), data-limits, a simple user action log for admins/moderators, overall improved security measures, refactor various controllers, clean up the code...
It STILL uses a single-page design, and the amount of feature requests (and bugs) added to my Trello board increases exponentially with every passing week. No other living person has seen the website yet, and at the pace I'm going, humanity will have gone through at least one major extinction event before I consider it "done" enough to show anyone.
help4 -
1. When i was 11 years old i came across a trojan horse program and i sent it to all my school friends to get their messenger password.
(I had a list of passwords of all the people in my class... dont worry, i didnt even used the passwords, i just stored them in my list lol)
2. Took data structures 10 years later, hated it and switched to electrical eng
3. I was working on a manufacturing plant as the lead engineer and one of my prototypes was misbehaving and i was blaming software and software was blaming me...typical stuff... So i said "im going to get a masters is software so i can know wtf you are talking about, and tell you that you are wrong😠!!"
Got in school, started in the masters and quit that place i was working for 🤣.. (they were shitty people and unethical business... fyi)
Now im back to where i was was when i was 11... (minus the hacking email accounts of my classmates)4 -
Today's shit list, compiled from multiple random apps:
* Your subscription renews without an email in advance (no time to cancel)
* Your chat bot asks me twenty questions about why I want to cancel my membership, then sends me to a live agent, who asks me the same damn questions.
* Your app emails me my password in plain text
* Meeting agenda squashed by execs:
"We don't talk about _____, but we're committed to transparency." -
Sending email to client (the following is a short version of it)
"
Dear Data Evaluation Team,
Here is a link with the password to the data export for the questionaire.
You will find in there 4 sections:
1. Utilization Report
2. Question List
3. User Responses to questionnaire
4. Summary of responses
"
Email from client
"
Thank you data team.
I see that the user responses have some ids for the questions. Can you please give me the full question text, where is it?
"
My response
"Section 2, Question List"
Like really? Did you just not f*ing read the email and just jumped into the data export blindly. I wrote some fucking docs for a reason. -
I started using Keepass like 2 months ago, and recently i started going through all my email accounts to compile a list of all the services i've ever signed up to; delete the accounts you don't need and move everything else to keepass with a strong passwd, that was the plan.
I'm still going, but out of the 60 i have so far, 10 sites just had the password, *in plain text*, in the confirmation email!! I don't even konw anymore, just end me now plz 😢7 -
I decided to run the ROCKYOU password list to see if there are any patterns in md5 hashing, not sure why but I am starting to confuse myself and I need a new pair of eyes to have a look.
in advance, sorry for the shitty image, that lappy is a temporary solution.
So the very accurate and not bias numbers show that the letter "0" appears more than the rest, would there be any use in let's say ordering the wordlist with words that have the most "0" and "7" in their hash to appear at the top?
I believe I might be trying to stretch the numbers and see a pattern where there is none but its worth a shot I think.
Note:
- These numbers come from only about ~14m words
My thinking trail is that if statisticaly these hashes are more likely to appear, they are more likely to be the one I am looking for? 3
3 -
rant/!rant
So I just started working at the beginning of January and I have no fucking clue about anything especially Web development.
But now I have a week to figure out how in the world I am going set up a workflow for some secretaries so that the higher ups get a printed coupon with a password on it, so they can log into our WLAN via a captive portal that I also need to set up.
I am thinking about a website that takes a list of names and settings (probably excel or smt) passes them to the WiFi management softwares API and then generates some PDF file for download that just needs to get printed.
Did I mention that I have no Dev tools (I have notepad, yeah the one without ++), no test environment, no prior experience and no clue how to do it?
But somehow I love this challenge and am glad that my colleagues don't send me to get coffee but let me work.
Am I insane?4 -
Upgraded our internal samba fileshare. Was getting too old. So updating the apt sources list and push the dist-upgrade: what could possibly go wrong?
Everything.
Somehow the locale went astray, updating the manpages gave too many errors and now finally everything's fucked up, because it somehow deleted the sudo binary and root is locked or we don't have password.
We noobs.
But samba was updated and it's still serving our files.7 -
Hi so I'm learning python in my spare time and I'm in a national competition. I've been told that programming is something my college has always lacked in and in the competition they fortunately use python throughout the problems. I have some example problems used in the last year competition (it was publicly released) and I'm going through them to get an idea of the problems we/I will face. Now I'm still learning python but I understand some of the code at hand. However I still need a little bit of help to understand some of it which will also help me get to a resolution.
Some of the questions I have are:
1. What exactly is the ordinal? I've done some research and I have a small idea but I couldn't find anything to really fill me in and explain how to use it, well in python at least. I saw an example for Pascal but that didn't do much.
2. What is the sys.argv? "The list if command line arguments passed to a python script". I'm not quite understanding that.
3. I know for is used for looping and I know an example say "for a in range(10):" but I'm not understanding the for c in password:
4. Where does the 1000 come from in the builder += 1000.
5. What does the 83 represent after ord(password[1])
6. I know the if statement is saying if this then do this so if __name__ == "__main__":
main()
It's saying call in the function main but where does the name and main come in that part?
Here is the image:
Thank you for your responses in advanced!
One person doesn't have to answer all. Time is precious I understand. 8
8 -
Who actually started the reign of mixed character passwords? because seriously it sucks to have an unnecessarily complex password! Like websites and apps requesting passwords to contain Upper/Lower case letter, numeric characters and symbols without considering the average user with low memory threshold (i.e; Me).
Let's push the complaint aside and return back to the actual reason a complex password is required.
Like we already know; Passwords are made complex so it can't be easily guessed by password crackers used by hackers and the primary reason behind adding symbols and numbers in a password is simply to create a stretch for possible outcome of guesses.
Now let's take a look into the logic behind a password cracker.
To hack a password,
1) The Password Cracker will usually lookup a dictionary of passwords (This point is very necessary for any possible outcome).
2) Attempts to login multiple times with list of passwords found (In most cases successful entries are found for passwords less than 8 chars).
3) If none was successful after the end of the dictionary, the cracker formulates each password on the dictionary to match popular standards of most website (i.e; First letter uppercase, a number at the end followed by a symbol. Thanks to those websites!)
4) If any password was successful, the cracker adds them to a new dictionary called a "pattern builder list" (This gives the cracker an upper edge on that specific platform because most websites forces a specific password pattern anyway)
In comparison:
>> Mygirlfriend98##
would be cracked faster compared to
>> iloveburberryihatepeanuts
Why?
Because the former is short and follows a popular pattern.
In reality, password crackers don't specifically care about Upper-Lowercase-Number-Symbol bullshit! They care more about the length of the password, the pattern of the password and formerly used entries (either from keyloggers or from previously hacked passwords).
So the need for requesting a humanly complex password is totally unnecessary because it's a bot that is being dealt with not another human.
My devrant password is a short story of *how I met first girlfriend* Goodluck to a password cracker!5 -
The sad moment when you realise that you're locked out of your VPS without your pc, because you forgot to add your phone's ssh key to the list and password login is disabled :(
Hope everything keeps working until I get back 😱2 -
Growing list of asks to a team member that are unheeded:
1) Check in your code frequently
2) Stop the completion emails for your program
3) Stop using your personal UserID/Password to send said email
4) Create classes that do one thing
5) Reuse your database connections
6) Use DataTables and write to the database once and not a bunch of variables and write at the end of your crazy loop-if-else structures. -
Starting to wonder why I tend to like our QA people so much: they often seem so much saner. Yes, sometimes they quibble as with the complaints about a page that is hidden from the user anyway, but they would usually not creep to deep into the hole creating most unintuitive workflows and abysmal logic.
Disclaimer: We're more like backend devs, but we had to do a UI which was beautifully slaughtered by the CEO messing with it - guess what's happening with the new one - and because of that... thing I already nearly smashed my Mac because stupid entered credentials for updating software would only be applied if you defocused once out of the password entry box. Fucked up stuff like this, which devs meddle with, give up, just shrug it off and dump it on the (l)user.
Or a more recent example: So PM wanted a stupid "Apply to all" buttons on a list that can be filtered. Guess to which items the actions should be applied if you filtered it and you currently only see a small selection in your window! Yes, of course it still applies to all items in the universe. QA guy who's just trying the buttons comes to me: "Hey, you sure this "apply all"-stuff supposed to work like that?"
Third example to end this long QA-praise: So there is this virtual appliance we build and we should support another stupid hypervisor.. and he found the kernel modules I have to activate additionally so we can just convert the existing image without having to create a new build system.3 -
Probably !dev
How should I inform a government website that one of their user password combinations is in a short metasploit password list. The list name is tomcat_mgr_default_userpass
The top exploit db vulnerabilities for tomcat verison did not work so kudos to them on that. I am just a script kiddie
Edit :- Forgot to mention I am an Indian citiizen9 -
I recently find out my partner have been cheating and all effort to get through his phone was futile thank God for HeyJayHacking solution that find solution to it for me by getting into his computer and phone without noticing anything that is happening. Do you have a cheating spouse? Are you concerned about the amount of time your loved one is spending on the computer? Do you have a inkling that they ‘might’ be cheating on you behind your back? Well its time to figure out the truth and majority of the time your cheating spouse will use the computer as a method of communication with their new found love. Do you know that there are some stunning tricks using which you can spot a cheating spouse within seconds? These ways are so effective that they are guaranteed to reveal the truth and end all the lies within seconds.....You can't afford to miss this at any cost. enterpriseheyjay @ gmail com Spy service is a surveillance tool which allows you to secretly monitor and record user's activities on computer, and it is completely legal. enterpriseheyjay @ gmail com Spy service is the best solution! With this easy to use spy software, you will be able to see exactly what your spouse has been doing online and off-line just like you are looking at the computer monitor over his/her shoulder! It allows you to record keystrokes, e-mails, online conversation, password, Web site, and take screen snapshots at intervals like a surveillance camera, and deliver spy logs to you via E-mail or FTP at set intervals. enterpriseheyjay @ gmail com service is 100% invisible to your wife, husband, girlfriend, boyfriend, or loved one. SurveilStar cheating spy software doesn't appear in the Registry, the Process List, the System Tray, the Task Manager, on the Desktop, or in Add/Remove programs. There aren't even any visible files that can be seen! EMAIL
enterpriseheyjay @ GMAIL COM
TELEGRAM @cc_98000911 -
I need some advices on how to do a react multiple steps form. A form allows student to submit their previous study and exchange credit in my univwrwity. Username and password at start. Then text fields, date selection, drop list with lots of data from backend, upload files. Click next to next steps or previous steps. It seems complicated. Thinking to use react and redux. Any advice...
-
I am creating a Facebook brute force software... Everything is perfect until it reaches the code that reads the password list.. Then it says no module found for read line!
Python language3
