Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "login"
-
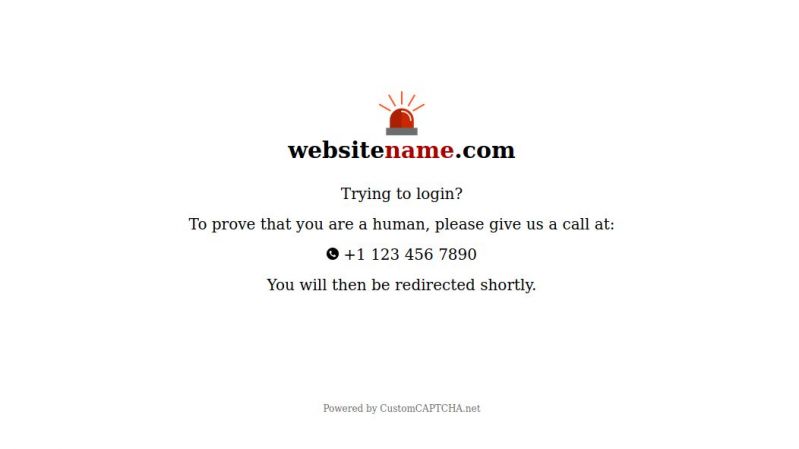
When someone changes the API at 5pm without notice and you get a call at midnight that no one can login.
 6
6 -
I hate those fucking sites which make you login first and then redirect to their home page.
FOR FUCK'S SAKE, ITS 2017. CANT YOU BASTARDS WRITE A FEW LINES OF CODE SO THAT I AM AUTOMATICALLY REDIRECTED TO WHERE I WAS AND I NEED NOT BACKSPACE EVERY TIME I LOGIN?9 -
so, my college has a very ugly looking login page for the college wifi. and I was bored so i thought let's change it a bit with a little JavaScript and tamper monkey i made this.. now i just keep on looking at the login page
 21
21 -
The most detailed error report I've ever had from a client. He couldn't login to his email, I asked him to send an email explaining what was going wrong, attach error messages, etc.
I got this from him:
"I can't login to my email, why"
Really?! 😑8 -
*boots computer*
*login screen appears*
*enters password*
*windows says "Welcome"*
*You have entered wrong password*
Are you fucking serious? Can't you even handle simple login flow? Why the fuck you display welcome screen before validating my fucking password? What the FUCK8 -
My CS college has its portal's login page secured with captcha.
But the captcha is set on autocomplete.
I shit you not. 5
5 -
Apparantly, wanting to use company assets for a smoke machine so when clients visit you can say "Welcome to the cloud!" is immature.3
-
Alright so here goes, I currently work at a promising startup. Absolutely love it; nice, hard-working colleagues but there's only a couple of us so we all have to wear a multitude of hats.
I don't mind being on support duty or helping out a customer with a technical question but one thing that really gets to me is lazy people.
We have some instructional videos (made in-house by yours truly) around certain functionality in our app which can't be simplified any further and they're condensed to about 50 seconds each.
I receive an email from a customer saying that he wants the instructions in screenshot form instead of watching the video because he 'detests' watching videos.
I must admit, I was a little hurt because he dismissed my videos so easily without even watching them. Just because he really doesn't like to watch videos? I was dumbfounded.
Me putting (most of) my rustled jimmies aside, I take about an hour to screenshot and document each step of the instructions and send them to the customer with a note: Be careful, if you scroll too fast it turns into a video.
I receive a response saying he doesn't like to watch videos because he is deaf but he did admit he had a chuckle.
Morale of the story lads, keep the sass in in your IDE's and out of your customer interactions.
True story.7 -
Clicking on Logout Button.
..
.
.
Getting a message...
"your session is expired you need to log in again to perform this action"
hmm... should I log in again to perform log out :)1 -
Thanks, I am happy to be sharing my payment details with your company.
ATTACHED TO THE LOGIN DETAILS YOU EMAILED ME! 3
3 -
Client asked for Two Factor Authentication as a part of the webapp we're building and then were confused as to why they needed a second password to login
"we don't want to add an extra step into the login process, can you remove it please"
fml6 -
Boss: "Can you create a login page where every login fails?"
Me: "Sure thing!"
*Writes out php file that returns false and calls it via AJAX*8 -
So my neighbor needed my help with her notebook. She said she has to provide a new password everytime she logs in. I asked her to log in in front of my eyes. She entered her password and clicked "forgot password" instead of "login" 😐
Did you ever hear of "return" ?3 -
* login tutorial *
Alright, everything looks good and secure and all
"and now to keep the user logged in..."
Aww ye, this is just what I needed
"we set logged in to \"true\" in a cookie and add another cookie with the users name" 2
2 -
That is peak security:
- Require timebased OTP for login
- Also require recaptcha for login
- Select the frickin bus, palm tree and cross walk 93 times
- Finally manage to please the algorithm
- The 30 second validity window of TOTP expired
*GAAH!*18 -
I put both my username and password as "incorrect". So that everytime i mess up, my computer reminds me that my login is incorrect!6
-
Yesterday a colleague of mine told me that another colleague has done this in his web application for a subject:
For checking user and password, he did not query a database, but instead he checked information in a HIDDEN DIV in the html page.
Reason: "this way I don't lose my precious time".
I think of that and I'd like to punch him. People like him are the reason websites in Italy suck and my University web infrastructure sucks (he worked as intern on that).
My. God.7 -
- clicks update and shutdown
- goes brush his teeth
- comes back, is welcomed by login screen
Man I love Windows5 -
A few years ago I configured my wifi extender.
Got everything working as I wanted.
Changed password to my favorite 24char password.
Can't login again...
Meh... It's working as I want and is secure, not even I can login.
It's still running in this state.3 -
Just found old logs I had with an ex-client, pre-devrant:
"What if we add the newsletter checkbox to the login, so each time a user logs in, he has to uncheck it, or else he will be subscribed to our newsletter?"
Not sure if that even needs a comment, I am speechless that was an actual suggestion, ever.1 -
Le Discord login:
*logs in*
Welcome back! Would you please authenticate after your first and successful login, so that we're sure that you're not a bot?
*15 (I shit you not) craptchas later*
New login location detected! Please check your email too!
FOR FUCKING REAL DISCORD!? How about you please just let me fucking log in already? Or are your audience - gamers - really *that* prone to infections that logins from bots are that big of a problem? Because guess what motherfuckers, then you've got *WAY* bigger problems to fix already. FUCKING LET ME IN!19 -
Who else agrees that the play store should have a section which tells if an app needs a mandatory login to use it ? Like why the hell does a simple offline planner todo app need you to sign-up if you don't wanna use cloud backup. Jeez the user just trusted you by spending valuable time and bandwidth downloading your app. You owe it to him to show him some features of the app before shoving a sign up in his face. As an app developer myself I really think that this kind of behaviour turns off more users than anything else.2
-
My university has impeccable data management. I needed to ssh into their Linux server for an assignment but it refused to accept my login. Which was weird because I could login to the same account on one of our websites just fine. I typed my password into a text file and then copy and pasted it into both logins. The Linux one failed but the website succeeded. After some experimentation it turns out that the Linux server only recognized my username if I typed it in all lowercase, even though when I created the account it had uppercase characters as well.
So let me walk you through the sloppiness that had to have occurred for this to happen. When I first created the account it must have ignored what I entered and just saved the username in all lowercase without communicating that to me. Then the websites that use this account must either ignore case for usernames or lowercase the user input before querying the database. Finally, the Linux server, despite knowing that all the usernames are lowercase, is case sensitive and won't recognize the username as I originally typed it in.
Can you guess what department manages the account, website and Linux server? The Department of Computer and Information Science. Incredible.2 -
That moment when you're finally getting your user registration and login system up and running!
As a web dev student I feel like I have accomplished something :)10 -
Holy fuck nvidia. Why the fuck you want me to login to your fucking app in order to download a fucking driver. You also want me to click a fucking link that you sent to my email for verification on every fucking login? Why on earth someone would stole my fucking nvidia account? To see which drivers I use? What the fuck nvidia? Oh wait. DO YOU DARE ASK ME TO SETUP TWO FACTOR AUTH TO SECURE MY ACCOUNT?!? What the fuck? Even if I put my credentials online no one would care to login my fucking nvidia account. Just let me download my fucking driver!4
-
Client: I can't login with my lastpass
Me: Oh, why not, how are you trying?
Client: So, I've entered my lastpass password into my bank account, and it says 'wrong login credentials'
Me: °-°17 -
when you type faster than computer response:
------------------------
Ubuntu 16.04.5 LTS server tty1
server login: sysadmin
adminPassword:
Login incorrect
server login: sysadmin
Password:
sysadmin@server:~$ _
------------------------
"FUCKING SHIT !"
*sees if there are anyone in the back*
*saw no one*
"fiuuh... what a relief"
sysadmin@server:~$ clear2 -
I looked into the code of the website of our company. One of the first things I found was that the Login was hardcoded with clear passwords. So everytime a new user needs an account the code has to change.
I still can't understand how people can do that.5 -
If($password = $password2) {
//login
}
Keep in mind that password is the salted and hashed input and password2 is the Salter and hashed pw in the database...
Who needs passwords am I right?8 -
A friend of mine did this.
Login: yes
Password: Don't have one
Password is incorrect
Login: yes
Password: incorrect4 -
> tries to run `login` command on CLI tool I want to use.
> gets error "no configuration found, run `login`"...
because... you know... it's not like I am trying to do that...2 -
Multi-factor authentication does not mean I have a password to your site AND have to login with Google. Also, I logged in with Google, you should have my email address now.
Oh, a user with that address already exists? No shit, it's me.
Your fucking login flow is broken.5 -
Remember kids, clear out any login credentials before doing git commit and git push!
/smacks himself6 -
No rant, just appreciation
A thank you to the senior developers out there who take the time to help us juniors out, to look at our (potentially) shitty code and point out how to improve it.
To help us to see the bigger picture and maybe take a more lengthy approach to a problem that'll pay off in the end.
And lastly, thanks for allowing us to learn from your years of bug splatting, stack tracing, null pointers and error messages.
You guys rock5 -
Is there any excuse for NOT having a HTTPS connection nowadays?
My university has so many unprotected subdomains that we're supposed to use and LOGIN ON that are not protected. Although these login forms are https protected the rest is not and seems sketchy.27 -
The nerdiest way to say happy birthday to someone? Tell them to paste atob("SGFwcHkgQmlydGhkYXkh") in the chrome console/firebug.3
-
Website that have a quick Google / Facebook login button, but then require you to create a regular account. WTF?3
-
So I manage multiple VPS's (including multiple on a dedicated server) and I setup a few proxy servers last week. Ordered another one yesterday to run as VPN server and I thought like 'hey, let's disable password based login for security!'. So I disabled that but the key login didn't seem to work completely yet. I did see a 'console' icon/title in the control panel at the host's site and I've seen/used those before so I thought that as the other ones I've used before all provided a web based console, I'd be fine! So le me disabled password based login and indeed, the key based login did not work yet. No panic, let's go to the web interface and click the console button!
*clicks console button*
*New windows launches.....*
I thought I would get a console window.
Nope.
The window contained temporary login details for my VPS... guess what... YES, FUCKING PASSWORD BASED. AND WHO JUST DISABLED THE FUCKING PASSWORD BASED LOGIN!?!
WHO THOUGHT IT WOULD BE A GOOD IDEA TO IMPLEMENT THIS MOTHERFUCKING GOD?!?
FUUUUUUUUUUUUUUUUUUUUUUU.3 -
So... I’m sitting here doing pretty much nothing, just reading through some rants when all of a sudden I get a wave of emails.
Pinterest!
We noticed a login from a new device or location and want to make sure it’s you.
Device: Firefox, Windows 8
Where: New Jersey, United States (Approximate)
OhhhhhKay then... so there’s a couple of problems with this, 1 I didn’t even know I had a Pinterest account, 2 I don’t have Pinterest in my password manager either.
So I follow the link and fair enough it’s actually pintest, so I attempt to login, to no avail, oh maybe it’s a social login..., ok let’s try google, nope that wasn’t it, deletes account, logins with Facebook, oh here we go, checks logins, 1 random jersey player, deletes account, swaps to Facebook, changes password (this fucker was already 100+ characters) and adds 2FA and contains no new logins 🤔
Ok... so what the fuck, either someone managed to get through a long ass password or something phishy is going on, the email for FB logins is seldomly used (maybe a handful of services at best) as I have another for all the junk and spam bullshit I expect from today’s “marketing”rant emails i’ve had enough internet for today pinterest. i have a pinterest? internet no one is safe social login1 -
I know last year suddenly lots of animated login popped out.
NPM actually uses one... and it doesn’t look that good 14
14 -
So, among the ridiculously long list of password requirements, password is not case sensitive BUT it has to contain uppercase and lowercase letters?
 14
14 -
Why the fuck would you allow special characters in your passwords, when some of them are considered "potentially dangerous!" can't even login ffs!
 6
6 -
This app is taking over my life.
This was a mistake.
(Not really. God bless this beautiful creation.)2 -
Ffs people get the fuck out off that Gitlab. I've been there sooner than you, now can't event load login form.2
-
Senior dev. "we need a reason why we haven't fully implemented social service signup yet"
Junior dev. "let's say it's new for us"
Senior. "great idea. Let's get this done."
..,
Now try to signup to pixabay using your Google account.... 😒 1
1 -
One thing every junior web developer learns is how to implement a login system.
They may not make it the most secure, but it works.
It boggles my mind how Microsoft still don't know how to make a login that works consistently.
Every Microsoft login page requires like 30 redirections to work.
The Teams app on my PC fails to login at least once a week, just because another Microsoft app is logged in using the same account (usually office), but Windows is not.
Microsoft needs to take it's head out of it's ass and BEG Google to teach them how to make a decent login system.4 -
sometimes our application users can't login to our application and they report the problem to us. The fucking problem? Almost sure they forgot the password because we can login with their account.. Yeah we should not have access to their password, but we do xD. The worst is they send a Word file with only a print screen of the application error saying they can't login. Why not a .jpg??! The word takes 4 seconds to open
 13
13 -
MySQL databases beginning with "test" in the name gives even people without login full access to its tables.
Somebody deleted all tables so we had to get a backup from out hoster.
Thanks MySQL.1 -
I detected a way to bypass login screen in client's website. I warned them. 48h later nothing changed...6
-
Windows decides to download Creative update.
I restart the computer wait for the update to finish.
I see the login screen.
I log in, then windows says:
"Hi, we have an update for you this might take a few minutes!"
What the serious fuck windows? Did you need me to login so that you can waste more of my time?3 -
Long story short: University fucked up single sign on.
For every online service I have, I set a different password, randomly generated ~ 20 characters long. At our university we have multiple systems but they offer a single sign on service which is quite nice because it is so non-transparent which service now uses which authorization. I changed my password a while ago and around the same time they also updated our mail client. Since then I am not able to log in which is not a big deal for me because I have mail forwarding.
Yesterday however I needed another service and also got rejected with my password. I knew from a friend that the passwords are fucked up and that some services have different restrictions (only 12 chars max.), so I decided to search how to reset my password. What the fuck was wrong with these people? It takes you five different pages to get the tiniest bit of information how to reset the password. Then on one page you can login with your single sign on and change the password. On that page you can also set the single sign on password, but if you enter an invalid password (in respect of the the other services) guess what? No feedback that you just locked yourself out of half the systems. Nice job. Also the password requirements are not next to the input fields where you change the password. Noo. That would be way to easy, remember the little small one line on the wall of text three pages ago? There you go.
Ok step one done. Now it should work, shouldn't it? Ohh no not so fast. One needs to activate the seperate service. Where you ask? Perfectly fine question. On the top of page four is a fucking one line table which looks like some five year old had some fun in excel. The button which takes you to the activation page is nearly invisible because of the non existing contrast. Also it is not a button but some arrow pointer thingy. Behind set arrow you have a page listing all differnt kinds of services, the description which you find on page two btw. No padding to decipher this shit what so ever. Nearly on the bottom is your needed button. Yes finally.
Finally I want to login, no good. Try again. Still no good. Go back to the fucked up excel table look at my username and think to myself what's the difference here? The table is so small and again no margin or padding. Apparently they cut of the last character of my normal username which i have which is fucking ridiculous.
What is wrong with you people, we are a TECHNICAL UNIVERSITY, is it so hard for you to find someone decend to unify this shit?1 -
GODDAMMIT okay time to set up 2fa
(GitHub says nothing was done to my account besides a login but i'm still suspicious...)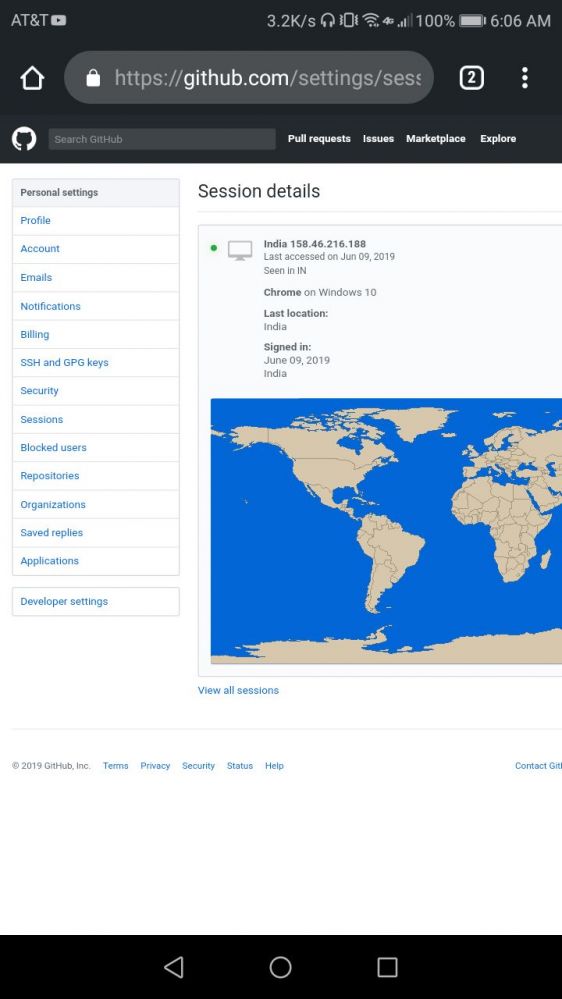 8
8 -
Today one of my friend just became a hacker...😂😂
The whole thing he did is:-
Opened a random WordPress site(found by luck) and in the URL bar he tried to type wp-login and it worked. Login page for WordPress dashboard board loaded and he told me that he hacked that website.
I said to him "Go On broda you are a LEET hacker..........4 -
I used to love Linux.
Now I hate it. I'm moving back to windows.
6th fixing time it's done this to me. When I try to login it just sends me right back to the login screen.
CTRL +ALT +F2 let's me login?!
Ugg I have a school paper to write.
So.. I moving back to the dark side.
This is what I get for trying out arch I guess.12 -
o2 business login. The whole interface is built in flash. Fucking Flash! Can't even login! No fallback. WTF!!! Useless piece of shit bastards.1
-
Yay.. laptop won't let me login, work computer won't let me rdp in after restart...this day started fiiiinee... :/2
-
My first login function
const login = (email, password) => {
If (email && password) {
return true
} else {
return false
}
}10 -
Client request: POST /user/login
Server response: "Login working bitches"
Client: if (response === "Login working bitches"){
//sign in
}1 -
What the fuck is up with this fucking tour bus company called Akdeniz?
These fucking retards want me to login to instagram etc. to get wifi access. Like wtf. Is not my 30 TL not enough?
Are you really going to save my login data for a few TL? Why would you dipshit people want me to login with my social media account (besides of that I do not even have an Instagram account. Miss me with that gay shit.)
I do not have a fucking fuckbook and a twittermyass.
I hope y'all fucking die by sucking my long ass dick, incompetent braindeads! 8
8 -
@dfox, @trogus Hey! I'm logged in, but whenever i click 'visit store', it shows this modal for me to login again.
 5
5 -
Got 1 star and 1 fork in git feels awesome. Or been a year since I joined git.
Todo conky widget for Linux I build received a star. U can add and delete to-do using terminal, so I feel its cool. https://devrant.com/rants/1402297/... has screenshot.
A bash script I wrote was forked. That was for logging into college wifi page. The routers used to disconnect very often and downloads u to be stalled on fluctuation in electricity. This login script would re-login on connecting back to college WiFi using polling mechanism
Currently working alone, hope soon i will put up some colab work. 2
2 -
New AD account.
cannot login.
Want to create a ticket.
Need a login to create ticket.
*genius*
Go to coworkers machine.
Open ticket there.
They respond, the user must create the ticket himself.
Ffs!1 -
I have this login page on my app. A user (a number of them actually) told me that they can't log in because the app tells them to "login in later". 😨
Is my button for deciding to login later so poorly designed that it looks like a message?
And the only way you can log in later is by pressing the frikin button, how does a person, with a smart phone tell me for the second time that its telling them to log in later 12
12 -
When not logged in, twitter.com opens a welcome message and a login form. twitter.com/login opens a login page with a "remember me" check box so you can stay logged in.
Twitter don't seem to want visitors to their homepage to come back very easily.1 -
this just happened a few seconds ago and I am just laughing at the pathetic site that is Facebook. xD
4 years ago:
So I was quite a noobie gamer/hacker(sort of) back then and i had a habit of having multiple gmail/fb accounts, just for gaming, like accounts through which i can log in all at once in the same poker room, so 4/5 players in the game are me, or just some multiple accounts for clash of clans for donations.
I had 7-8 accounts back then. one had a name that translated to "may the dead remain in peace "@yahoomail.com . it was linked to fb using same initials. after sometime only this and 2 of my main accs were all i cared about.even today when i feel like playing, i sometimes use those accs.
2 years ago.
My dad is a simple man and was quite naive to modern techs and used to hang around with physical button nokia phones.But we had a business change, my father was now in a partnership in a restaurant where his daily work included a lot of sitting job and and casual working. So he bought a smartphone for some time pass.
He now wanted to download apps and me to teach him.I tried a lot to get him his own acc, but he couldn't remember his login credentials.
so at the end i added one of my own fake ID's(maythedead...) so he could install from playstore, watch vids on youtube and whatever.
The Actual Adventure starts now
Today, 1 hour ago:
I had completely forgot about this incident, since my parents are now quite modern in terms of tech.
But today out of nowhere i recieved an email that someone has JUST CHAINGED MY FB PASSWORD FOR ONE OF MY FAKE ACCS!?!??
what the hell, i know it was just a useless acc and i never even check my fb from any acc these days, but if someone could login into that acc, its not very difficult to track my main accs, id's, etc so i immediately opened this fb security portal and that's where the stupidity starts:
1)To recover your account they FUCKIN ASKS FOR A PHYSICAL ID. yeah, no email, no security question you have to scan your driving license or passport to get back to your account.And where would I get a license for some person named "may the dead remain in peace"? i simply went back.
2) tried another hack that i thought that will work.Closed fb help page, opened fb again , tried to login with my old credentials, it says" old password has been changed,please enter new password", i click forget password and they send an otp. i thought yes i won, because the number and recover mail id was mine only so i received it.
when i added the otp, i was first sent to a password change page (woohoo, i really won! :)) but then it sends me again to the same fuckin physical id verification page.FFFFFFFFFuck
3)I was sad and terrified that i got hacked.But 10 mins later a mail comes ,"Your Facebook password was reset using the email address on Tuesday, April 10, 2018 at 8:24pm (UTC+05:30)."
I tried clicking the links attached, hoping that the password i changed(point<2>) has actually done something to account.NADA, the account still needs a physical license to open:/
4) lost, i just login to my main account and lookup for my lost fake account. the fun part:my account has the display pic of my father?!!?!
So apparently, my father wanted to try facebook, he used the fake account i gave him to create one, fb showed him that this id already has an fb account attached to it and he accidently changed my password.MY FATHER WAS THE HACKER THE WHOLE TIME xD.
but response from fb?" well sir, if you want your virtually shitty account back , you first will have to provide us with all details of your bank transactions or your voter id card, maybe trump will like it"
-
I sent my app to one of my lecturers(female). She opened it and it said "Login with Facebook". I had integrated FB login just like other apps for authentication. She thought that I was playing some trick on her to hack her facebook account and refused to continue...
Where to run, where to hide... 😂
After all, the login dialog was of facebook's itself and nothing else.3 -
Monday morning, login, check outlook calendar
Today I have a dairy buster meeting 🤔
Guess we're going dairy free 😂😂 2
2 -
I don't know why things work when I do but not for other people. 😓
Request to reset password. I did.
Said still cannot login.
I double check. Reset again and try to login. Success.
Said still cannot login with a screenshot.
😓 I think my projects hate me.2 -
Trying to understand a complex, twenty-angular-module project. Discovers login module rules only CSS properties that hide the rest of the app...2
-
That feeling when you're working with production data and you get a cold feeling running down your spine, telling yourself: you could really fuck up now.3
-
IHateForALiving: gentlemen, my unit tests are randomly falling. Sometimes the login procedure just fails for no apparent reason, did any of you encounter this problem?
The very fucking smart colleague®: DID YOU REMEMBER TO PLACE YOUR AUTHORIZATION HEADER
Of course
The authorization header.
To fucking log in.
Because you have to be logged in before you can log in.
That's the standard, of course.2 -
Clients be like: what you've only completed the login system in one hour I thought you where a programmer.4
-
Entering the password before your laptop fully wakes up, than having to delete what it did register and login again9
-
windows booted up into a blue screen for a second before going to the login screen.
i almost had a heart attack2 -
If your website has a login wall, my visceral reaction is to close the tab. After that, my rational reaction is to close the closed tab. Because fuck you.
-
With the movement of people recently deleting their facebook accounts, this actually covers a valid concern I didn't even think of, since I personally don't use that feature at all, nor have I ever used it.
People that used the "login with facebook" a lot, especially with websites that exclusively use it, will flush not only their facebook account doing that, but also all accounts they have ever used to log in with facebook, if not actually thought as far as checking the apps section of facebook and trying to migrate your account, which is also rarely possible.
So basically many people that do use it, simply won't delete their facebook account, because it has this backup parachute attached with its strings, that does not allow for an easy exit, except for literally ripping it all out and losing every account it seems.
Ignore dashlanes self advertisement bullshit at the bottom, the blog itself is still highly valuable in itself.
Source: https://blog.dashlane.com/delete-fa... 12
12 -
Never have I been so satisfied as I am right now after having implemented a login and user account system with the ability to update user preferences with databases n' shit in PHP after only knowing PHP for a day.
Speaking of all that, do you guys know of any good place to make sure all my stuff is secure? No SQL injections n' the like.4 -
We all hate being tech support for our family and friends, but motherfuck this is insane; my sister asks me for support and then doesn't listen to me. E.g. I tell her that the Microsoft login page is fucked up so she'll need to login again and she doesn't try again, but pesters me until I login for her... Every goddamn time...11
-
I've just checked my server's auth logs and my god that's a lot of failed ssh login attempts.
I think I'll install an ssh honeypot to waste these peoples time...8 -
When a marketing / sales person says in a meeting with executives that our current infrastructure can handle 300.000 new customers easily. (We're at 90 ATM).
Mfw I'm the techie in the room and aware of our non-scaling mysql DB.
-
Specifications called for user logins to be stored in a session and not be persistent. When the session ends, you need to login again. The system deals with insurance policy information and persistent login was deemed a security risk.
First ticket submitted by the client after go-live? "Please make the login page remember my user name and password, or that I've logged in previously."2 -
Why have so many fucking websites the signup form in the start page but you have to click in the menu to get to the login?!
I signup only once but I have to fucking log in every single time I go to the page!!!11
Annoying...2 -
When I just started programming I aways added fake loading screens and hard-coded login screens to my c# applications because it looked cool..
But I also always added an invisible panel to the top right so whenever you click that it would bypass the login screen.
I had to do that because 1. I will forget that password after 2 seconds, 2. I got no time for that login screen.2 -
get a remote job
get remote login details
.........
the whole system doesn't speak your language
😬😬😬3 -
Just some random thoughts looking at the soon-to-be new filtering feature.
Wouldn't it be nice if DevRant had a QR login like WhatsApp for easy login on desktop?
What about a "top rants" on profiles?
Oh what about an activity mosaic like GitHub's commit timeline?
Just some thoughts I had while punching my punching bag, it can get tedious.5 -
"I need the login credentials for the CMS service"
*sends the email confirmation email*
"No, I can't confirm your email for you. In plain English: send me the email and password to login."
"Ohhhhhhhhh"
Literally what the fuck is wrong with these people.
I swear we're all fucking doomed.5 -
Skype password lost -> reset email -> new password given -> login failed on skype client -> login via website -> invalid password -> reset password -> first enter code by email -> done -> assign new password -> login via password -> someone else is using your account, you have to change the password -> first ensure you are you by enter a code -> code entered -> change password -> password changed -> finally login works
Way to go Microsoft!
so I just changed my password 3 times in the last 5 minutes to get access to skype... for a call we finally made via whatsapp... now I will remove skype again until next year, when I have to make that famous "once a year" call with skype3 -
Mail from Microsoft: sign in to see payment details.
User clicks on the link (once).
Microsoft:
Sign in to continue to Microsoft
Something went wrong and we can't sign you in right now. Please try again later.
The Microsoft account login server has detected too many repeated authentication attempts. Please wait a moment and try again.6 -
Can we stop that trend of only showing the username field and then show the password field after filling the username clicking next? It messes with my Keepass browser addon.
Apart from that, it messes with human workflow as well. Enter Username -> TAB -> Enter Password -> ENTER. With that stupid UI you have to either focus the next button with Tab and hope hitting Enter does not already submit the login form or switch to mouse and click the Next button.10 -
FUCK FUCK FUCK FUCK FUUUCJKKK OOOOFFFFFFFFFFFFFFFF (wasted hours why im being redirected to 404 when trying to access a route thats being guarded (u need to login first to access it) only to find out i changed /login into /auth/login and forgot to update this bs into the guard so the guard was redirecting to /login which indeed doesnt exist and is a 404 instead of redirecting to /auth/login)
This is such a fucking dumb bug I have to take a fucking break im going outside for a jog and then intense home workout to unfuck my mind8 -
My trying to login to my email account my.email.address@example.com via web:
Site: You need to verify that you are really you. We sent a verification email to my.email.address@example.com please click the link in this email to verify your identity.2 -
DevOps is when the IT forces you to download Citrix on your Mac to login to a Windows VM where portable Putty is copied to the Desktop and the password login to your requested headless Ubuntu VM is in a text file on the mounted network drive.4
-
To the devs at inc.com
Fuck you.
Just resign.
Do me a favour. Don't touch any computer for life.
After reading 2 articles I need to login.
Okay fine.
Facebook login fucking doesn't work.
Twitter login worked.
But but fucking take me to some idiotic article. Hello? That was not what I logged for.
Now go back. And fuck fuck fuck
Article still says login to read this.
And click on login. Nope. Nadda. Nothing happens.
How how how. How are you even getting paid?
Fuck you.
Fuck you.
Fuck you.2 -
I am very patient but I've finally lost it...
I haven't been able to login or even reach the login screen in Aetna for over 6 months... (I've tried different browsers and different computers...)
I thought such a big issue would be fixed immediately but finally.... I BLEW UP! 2
2 -
I was thinking about how I implement login functionality, and realised I have no clue how I came up with it so decided to ask if it was a good way to do things.
Basically, client logs in, username/email and pass are sent to server.
Server salts and hashes password and checks it against the one in the database for that user.
If its correct, send the client the user ID and the user token. (User id could be username, or a number, it depends)
When that client makes a request, the request must contain the ID and token.
The server checks that the ID and token combo are correct, and because the ID is linked to the user we know who it is and can complete the request.
Usually I make the token a random string of 16 or 32 chars, each account has their own token, and it may be stored in the browser so they stay logged in. I also normally add a "log out everywhere" button, which essentially just generates a new token to overrides the current one, making any previously saved tokens invalid.8 -
Motherfuckers can't even create a simple login feature.
Lmao this promotion driven faggots are dominating the product thinking they'll commercialise it and earn profits.
Why is this hilarious? Because they are building this product for past 3 years and yet the login feature is not functioning.6 -
i was trying to check a purchase i made on the store's website, so i tried to login, but I can't?? like, i fill the form and press login, and it doesn't? log in??? what the actual fuck, how are you supposed to do anything like that. isn't the login page the first thing they make? how doesn't it work? how is this website still active??4
-
You know a server is having a jolly'ol time when, while logging through the serial console, it lags... Then, a few seconds later, you get a message
[time.seconds] Out of memory: Kill process PID (login) score 0 or sacrifice child
[time.seconds] Killed process PID (login) total-vm:65400kB, anon-rss:488kB, file-rss:0kB
10/10, only way to bring the server back to life was by a hard-reset :|3 -
Just managed to send my password in plain text to a colleague when I ment to enter it in the login box.....
Time to change my password again.....3 -
If the database doesn't have the information, they won't be able to login, no need to validate or sanitize
-
I hate free cloud services needing a login. Just let me fucking access the damn app. What difference does it make, it's literally free anyways?? I just want to make a god damn spreadsheet and now I need to login to like 3 different microsoft accounts
WHYYYYYYY5 -
I (junior dev) hate it when my boss tells me to do things that totally don't make sense...
I'm managing an internal site which requires a login to access. Why the hell should I change every damn article in the cms, so robots meta tag is set to no index. It's behind a fucking login and Google won't be able to index it! (except the login of course)
...
I did it anyway.2 -
so, I receive those mails for health insurance and all the links were "http://localhost/"
also got a 500 errors after login7 -
Three-factor authentication:
1. Setup an Amazon.com account.
2. Setup an Amazon Web Services account under the same e-mail address
3. Setup two-factor authentication for both systems.
4. Login to Amazon Web Services in a new browser session, and you'll be required to provide BOTH security tokens at login (Amazon.com first, then AWS second.)3 -
Due to coronovirus, my work asked everyone to login for 30mins (in a 2hr window) to test test max load/capacity...
1. how do you test max load if people can login at different times...
2. Isn't there software that can test that.... Isn't this load testing?11 -
Last year, one of our government organizations' websites' edit page was editable without login credentials... People can easily modify or even delete a company. They had a login functionality for employees and was pretty much useless.
-
What disturbs me is when companies uses invalid ssl certs for internal services where you have to login with your company credentials.2
-
Ouuu today I experienced how web-devs must feel...
Task: create a form to answer questions with yes/no and a database behind it to collect stats.
So login to phpmyadmin
1. Wrong password got error message
2. No error message, still at login screen, but in address I see a token
3. There must be something wrong
4. Reinstalled phpmyadmin and mysql-server several times, wasted one hour on it - still stuck at login screen
5. Tried different browser and it fucking works!
6. Realized that cleaning cache fixed it...1 -
Git adds shell to git user
This make the git deamon user show up in login screen of lightdm.
Had a which of my life when I saw that.
I updated my Linux after long time (pacman -Syyu)
https://bbs.archlinux.org/viewtopic... -
So I locked my windows work computer before the lunch break, came back to Ubuntu's login screen... (I dual boot)
So windows just randomly restarted? Rip if I forgot to save something... -
The fuck, LastPass?
You tell me this EVERY TIME I login to my account on this browser and this location.
Fuck dynamic IPs. 2
2 -
GREAT PROGRESS TODAY!
I already made the login part of the devRant rewrite and I can reliably log in and out of the app.
From here, it’s just API requests, JSON parsing and just fitting the data to templates.
...and the avatar system.
Fuck.2 -
Upgraded to Ubuntu 17.04 and now Ubuntu freezes at login screen. It's been more than 3 hours and 0 progress.4
-
Got an app upgrade breaking my login credentials .. login works on corresponding website but no longer on app.
Guess it has to do with either the length (> 30 chars) or some of the special characters in the password...
Great job!3 -
This is how my login and authentication works
Check for cookie on request
if cookie doesnot exist, send login page ( login )
1) check for credentials
2) if valid, set username's JWT as cookie
3) reload page
4) proceed for authentication
If cookie exist, decode JWT ( authentication )
1) check username
2) if username exist on database, send user panel
Anything wrong with this ?? What is the better way to do this6 -
Seriously?! Your username is your full name... With spaces?! Pushing against the grain! Pushing against the grain...1
-
MS Teams with multiple work accounts account swap flow:
1. Try to close the company-bound login modal 10x while being fast enough to also close the main Teams window.
2. Realize it's not gonna work, so login with the account you don't want to be on.
3. Have to type your phone pincode then accept the MS Authenticator login, and retype your pin code.
4. Finally logged in just to log back out and get the generic account choice modal so repeat step 2 & 3 with the correct account.1 -
Found an institutional coaching centre leaking 1000s of students personal data phone, photo, db, parents info, documents photo path, payment method(bank, check, card) etc. They 32567 rows. I'm trying to find the admin login page. It seems they have it on separate subdomain. I found student login and I can login as any student. I hate these institutes. Sent them emails days ago (29 sept) but no reply yet. What should I do?2
-
That disgusting moment when McDonald's wifi login form tells you that you are already logged in and yet you can't access to any page except their login form one -.-
 1
1 -
It's been a month since I commented the password check for the login page on production... no one has complained...
-
Am currently developing an app which uses an IaaS named Auth0. Great experience so far, reasonable docs, unlimited users, social login, sso and support for about $29/m.
After an inquiry from a customer to provide MFA, I contacted Auth0 to see what it would take to use this feature.
"We only offer this in our Enterprise plan which starts at $18k/yr."
Well, fuck me with a pitchfork and call me Bridget the midget. I'll code it my goddamn self.1 -
$ Login: phoomparin
*types in password*
Incorrect Password.
*rushes to type user and passwd again*
Password shows in cleartext...3 -
This rant is tribute to the guy who doesn't allow you to login to site before authorization..
the level of security one can never imagine 😂 -
[FEATURE_REQUEST] Could we get a stat that shows how many consecutive days we've visited / opened DevRant?3
-
So a web developer is driving home from work when his girlfriend phones him. She says her sister can't log into Windows anymore even though she didn't change her password!
What happened?6 -
Updated to pop_os 19.04
Xorg stuck on a login loop.
Checked the basics, still failed.
Guess who has a fresh Pop_os 19.04 install?7 -
Mother tries to login to her email. Starts shouting that it's broken and she can't login. I come, change the language from Greek to English, tell her to reenter her password...2
-
Why can't I wrap my head around laravel enough to build an authentication system I've built before 😖😡😠
External Login Service and my app would be an OAuth2 client receiving an id token...and no there isn't a third party integration for this login service5 -
If you create a website with a login function, please mention the password requirements on the login page (not just the signup page, in the login page too). So i know which of my default passwords i used for this website.16
-
I have a question, let's say I have a website and app both using oAuth facebook login. Should I save the access token provided by facebook in my database and if I should, what will happen to the access token when user logins with facebook on website and then login again with the app? is that mean access token is going to be overwritten by new login? and do you have any other suggestions for 0auth integration?3
-
Login monday morning to prepare for dev time. Entire morning has been scheduled with back to back meetings. Fuuuuuuu
-
When Facebook login randomly starts failing after several months of no problems. Why do these things happen to me?
-
TL;DR: FFS Microsoft
So yesterday we were at the point in our project where adding a login system seemed like a good idea. This is an asp.net core mvc project and we use Materialize for our frontend.
So according to _the tutorials_ we could start a new project and add authentication in the prompt by pressing a button. As it created the project I thought it seemed nice and easy enough. After it had created the test solution I build it and, sure enough, in the top right corner there were a register and login <a>.
I checked them out and they were your bog standard form input input submit and all. Now I guessed I could look at how it's all programmed aaaaaaaaand
Nope.
I saw a new folder located at Areas/Identity/Pages which had a _ViewStart.cshtml which contained three lines. There were also a database migration and in Startup.cs there were some database stuff, but other than that? Nothing. So where on earth was the login and register form located? Shit like that is frustrating ya know.
But oh well it seemed to work and I switched to our examn project where I found it was possible to scaffold the login system in a way that seemed nice.
Except, for some reason bootstrap and jquery decided to return to our project. FFS Microsoft!1 -
Motherfucking peace of shit....
Dont know to whom I should direct this to .
Was creating a new login page for web app using Quasar(vue.js). Since my application have 2 different types of user, which also have different UI, and functionality.
One is written in vanilla ( and is quiet heavy) and the other one in vuejs ( though earlier it was written in vanilla too ). Login page too was written in vanilla which was working fine.
Now just yesterday I finished a prototype for the third type of user, which is also written in vuejs. Now I decided to re create login page using vuejs. Quiet small and easy to do. Finished it yesterday itself. Now since today's morning I am trying to configure it so that it this piece of shit just let me log in. It was authentication and verifying but not letting me log in.
( On server after authentication, I set cookies/token on clients browser and auto reload the page, so during next request to server/ or during reload, server will read the cookie/token and send the specific admin panel to user)
Prick. Dick.
It was setting cookie, but not at the '/' path. Mother fucker.
It was setting cookie to the path I was sending login credentials ( which was different from '/', I.e.- /login/verify=password )
So it was setting cookie/token at '/login/verify=password'.
Even tried setting path for cookie at server. Read everything on internet. MF nothing worked. All I came across was, 'this is CORS' .... 'this is CORS'. Assholes, if it were CORS', how then I am able to make request to server and getting response without error
Only a hour ago, when I made get request to '/login/verify=password' I figured out, cookie is being sent to server for this path only. Then did some changes at server, so to send login credentials to '/'. Now that shit is working
Fucking waste of time. Wasted more than 6 hours. Asshole.
Btw, if you can suggest a better way to login, then please. -
Why the hell did you put the promo code field on the login form? What type of fucking eCommerce site are you?4
-
I recently logged into my care provider's online services for the first time, to schedule a doctor's appointment.
The login form requested the usual: username and password - but also a birth date. Which their developers implemented with the default Android datepicker control.
Meaning I had to click 'back' 339 times to get to December 1989.
fuuuuck.2 -
Am I incredibly paranoid with my idea of multiple(>2)-factor-auth like fingerprint+yubikey+password+OTP aso?4
-
I was logged into a portal with my colleague’s ID. She asked me if I was logged in with her ID.
So, I asked her if she was unable to login:
Me: Are you able to login?
She: Are you able to login?
Like, what was the point of her reply?!
Me, again: Are you able to login?
She: No
EASY, WASN’T IT?!7 -
Today I created a second admin login for myself, deleted the first one, recreated the first one, then deleted the second one.2
-
My last rant with example of usefull PHP function in old inhouse CRM software was somewhat popular, so I decided to post more stuff. This time we look at the login function. Besides obvious problem of SQL injection (that i of course tested) we have two calls to the same 'poslednji_login()' method (translated to english - 'last login') that actually just returns current time, not the last login time... twice...
 6
6 -
Hey their did anybody notice unauthorized login attempt over ssh. Means I have a demo digitalocean droplet I just left it for some logs their isn't any imp data over but when I try to ssh back that machine after an interval of max 5 to 6 days after login message displayed their were 9876 login attempts were made, then I directly go to ssh log over secure log file get all those IP, found out max were from China some from France and all are doing random login names like user, admin etc etc and with random password over multiple ports even non standard one, is anyone finds this happening10
-
New authentication system for a new type of login, I try to log in
Error everytime I try.
So I wait a little, like 10 min (the server is quite picky, thought it was it).
And then I try with another co-worker.
Login blocked.
Motherf-- -
i just tried source tree to easily clone my repositories and wasn't able to login it appears they are using Internet explorer for the login part. and guess what ? ... yup it doesn't fucking work.
WHY WOULD ANYONE USE INTERNET EXPLORER FUCKING PIECE OF GARBAGE. ANYONE STILL USING THAT SHIT SHOULD BE BANNED FROM THE INTERNET FOREVER ESPECIALLY A PROGRAMMER -
Gotta love when they give you site credentials to look at their wordpress dashboard but forget to give you the login page.
Am I supposed to spider their site and play a guessing game. Fml.
Wonder if there is a way to scan the login? Athough that would make hiding their login just security theater.5 -
Microsoft, please stop the incomprehensible work vs. school account stuff and if you want to mail me a login code, then please actually do send an email. What's wrong with Microsoft Teams and office always giving its users headaches already when trying to log in?
A customer sent me a "FindTime" link, something like Calendso / Calendly, but "powered" by Microsoft Office. Seems that their power is off again, like ever so often. Microsoft: "can't access your account: You can't sign in here with a personal account. Use your work or school account instead."
Okay, go to bing, and search your error message. Try to use bing page to log in to my account: Microsoft: "We emailed a code." (No you didn't. At least I never received anything. And, yes, I did check my spam folder!) Microsoft: "Other ways to sign in: use Microsoft Authenticator".
me: "dear customer, please feel free to pick any time and date that matches your preference, as the FindTime link has been impossible to use".
How can Microsoft make me feel so dumb again, after more than 20 years as a developer? Have they ever heard about usability?10 -
I need help:
I’m on a (old) MacBook Air (2018 but before the new one) and I use 2 browsers: Chrome & Brave (school and personal).
Since 3~4 days, I keep getting logged out of all my accounts on both browsers, and I can’t see to find why.
I don’t block all cookies, all my login info is saved (autocomplete), but I always get logged out.
Any ideas?3 -
Released the product to customers without realising someone had pre-filled a production test accounted login at the login screen. Obviously it was used for testing purposes and the dev forgot to remove it before committing.
I loled when I found out about it, and some customers started to login and made transactions.
When I checked the commit history... It was under my name :/2 -
Is it better for login page button and text and links when you're about to login to say Login or Sign In?
Same for registration. Register or Sign Up?
Its the same shit different label. Im afraid people are too dumb to understand Sign In = Login and Sign Up = Register.
Some sites use Login some use Sign In.
Thoughts?
Cast ur votes and explain why
✅ Login / Register
✅ Sign In / Sign Up16 -
Auto Login feature enables itself when a certain config flag is present - the app will login as an admin without requiring username or password.
I pray to the Continuous Deployment monsters that the config setting never gets copied to production by mistake.2 -
Time is relative. It's been 10 minutes now from when I inserted my smartcard credentials on my workstation (NO SSD) with Windows 7, McAfee Antivirus, Crypted HD and other company policies and useless software. So boring...
And they ask me why I need an SSD right now!1 -
Asks daily for login credentials to server. After a week mail from the client: "why isn't our platform live yet?"
-
TFW when errors like this happen while trying to buy a laptop online from one of the biggest tech companies in the world.
 1
1 -
IBM Bluemix... Why in hell do you keep asking me to login, even though I just did and you said everything was OK!
-
Setup SSH keys from your Dev machine to every development environment then configure a putty profile to use that key with your login.
-
Wtf?
Who the hell puts a recaptcha on a login page? Ecomdash, that's who.
https://dashboard.ecomdash.com
Any Ecomdash devs want to explain this?5 -
I dont get it, why do all those authentication providers want you to use a separate webpage to handle the login, why cant i just have the form and "login with ID provider" buttons on my page.
Why is the user forced to take another step in the flow...
this is UX 101, comon!5 -
I read earlyer that GitHub was down but i can login but when i open one of my repositorys i get logged out and when i try to login it just shows an error! Anyone else experiencing this?1
-
What's your thought on multi-login systems?(your own or Facebook\Google\etc.)
It's worth dealing with it?
The user base of external logins is bigger than your own?
If you've programmed external login support, how've you found the experience?3 -
Fellow devranters, I need your help for a... NodeJS question... (and I won't bother asking the question on SO, because all the questions/answers I found won't work)
You see, this client we have says they want their app to be login-less; once the app starts, ir automatically knows who is the ldap user that 'logged' in the app.
I've been struggling with it for weeks, trying to use npm modules, retrieving info from process.env, and I'm sure it is completely impossible without at least providing a username.
So here I am, asking anyone out here who can answer me this question: is it possible to login without providing anything?7 -
> * npm login *
> puts everything right, uses token because of OTP
> npm login fails: incorrect user or password
you know what, fuck you5 -
Tries to automate login with vb using I.E...
Gets stuck because login page is a hive of nested iframes with deep nested tags without defined names
FML -
Fuck you mysql and your new fucked up 8.0 login. Fuck you 100 times. Now I need to restore my computer because of you.4
-
Funny login screen bug: the title and the jokes changed, but the image did not.
(This is partly photoshopped, since I couldn't catch all the 3 "hot spots" open together in a single print screen) 1
1 -
Anybody heard of Clef - A new way to login? It's pretty coool! I've integrated it in one of my projects and it works like a charm..!
The best part being no need of any passwords or fingerprints or facial detection etc3 -
What i'll minded cocksucker decided it was a good idea to let the web application cache MySQL login credentials..3
-
When you can't login to your favouite game, because the games client can't handle your random string password :/
-
Can anyone help me with NativeScript social Oauth login with Vue.js ? I've been trying to figure out how to implement it. Thanks in advance.
-
Passwordless Unix login leading to a console menu. You can then FTP in for free and remove ~/.login . Boom ! Shell access! And I already had a superuser access from another "dialog" asking to confirm a dangerous action with the superuser's password. Boom! Root access !!
-
Does the login save checkmark not work for anybody else on the web devrant? Like I always have to re-login, tried it on multiple webbrowsers too and even in a fresh VM image.1
-
fuck you onelogin, saml and corporate login for being difficult to setup and understand (still haven't achieved either)
also fuck you outdated documentation
when you drag in a senior to help you and they think you're a retard (true), "just read the docs" (attempted), you have them try to babysit you through the setup and they realize the docs are not up to date/retard proof enough to get a proper setup on your end1 -
Why the fuck do websites open a new tab when you click the login button on the homepage? Like why? Seriously why?4
-
How would you java spring guys write a JUnit test for a login controller? My controller works as followin: It checks the username and password values from the model and then either redirects to the home page or redirects to the login page with an error code. How am I supposed to test that behavior, when MvcMock can't capture the redirects?1
-
[Warning – rapid flickering in GIF below].
You know JetBrains can't build software when you can't even login to their own bug tracker because the login modal just flickers constantly. Every software I've used from JetBrains is ridden with bugs. They are mentally ill.
-
Want to have today's top rant as your ssh login banner, or your FTP banner, or anything else really? - https://gist.github.com/hcaz/...
-
!rant
I'm currently working on a little side project in Go and I want to create a web page with an OAuth2 based login. So far the OAuth2 login works, but I need something to track a session afterwards.
Any suggestions? I'm pretty new to web development, especially in Go :)1 -
who ever developed a cluster fuck of this platform called zoho cliq
fuck you!!!!!!
the mobile app doesn't even login -
What program should I use if I only use a phone, also can anybody help me with making a login page???6