Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "server block"
-
The DNS server I'm writing in PHP (largely taken from another project) is starting to work!
Next to just blocking queries it logs every blocked query so I can have stats :3
A little terminal output: 64
64 -
[This makes me sound really bad at first, please read the whole thing]
Back when I first started freelancing I worked for a client who ran a game server hosting company. My job was to improve their system for updating game servers. This was one of my first clients and I didn't dare to question the fact that he was getting me to work on the production environment as they didn't have a development one setup. I came to regret that decision when out of no where during the first test, files just start deleting. I panicked as one would and tried to stop the webserver it was running on but oh no, he hasn't given me access to any of that. I thought well shit, I might as well see where I fucked up since it was midnight for him and I wasn't able to get a hold of him. I looked at every single line hundreds of times trying to see why it would have started deleting files. I found no cause. Exhausted, (This was 6am by this point) I pretty much passed out. I woke up around 5 hours later with my face on my keyboard (I know you've all done that) only to see a good 30 messages from the client screaming at me. It turns out that during that time every single client's game server had been deleted. Before responding and begging for forgiveness, I decided to take another crack at finding the root of the problem. It wasn't my fault. I had found the cause! It turns out a previous programmer had a script that would run "rm -rf" + (insert file name here) on the old server files, only he had fucked up the line and it would run "rm -rf /". I have never felt more relieved in my life. This script had been disabled by the original programmer but the client had set it to run again so that I could remake the system. Now, I was never told about this specific script as it was for a game they didn't host anymore.
I realise this is getting very long so I'll speed it up a bit.
He didn't want to take the blame and said I added the code and it was all my fault. He told me I could be on live chat support for 3 months at his company or pay $10,000. Out of all of this I had at least made sure to document what I was doing and backup every single file before I touched them which managed to save my ass when it came to him threatening legal action. I showed him my proof which resulted in him trying to guilt trip me to work for him for free as he had lost about 80% of his clients. By this point I had been abused constantly for 4 weeks by this son of a bitch. As I was underage he had said that if we went to court he'd take my parents house and make them live on the street. So how does one respond? A simple "Fuck off you cunt" and a block.
That was over 8 years ago and I haven't heard from him since.
If you've made it this far, congrats, you deserve a cookie!6 -
Yesterday I was updating the code in a linux server at 23:00.
My 6 year son look the terminal while i was typing and said:
"Dad, why you always write in block letters? I can read and write also in italics."
"Dear son, you are smarter than my PC."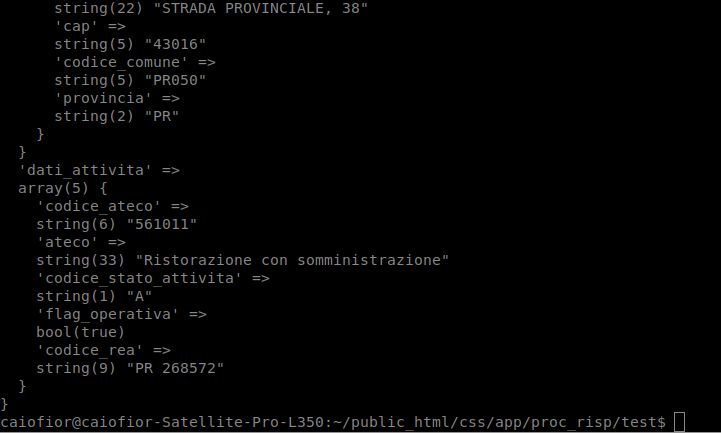 11
11 -
So, continuing the story, in reverse order, on the warship and its domain setup...
One day, the CO told me that we needed to set up a proper "network". Until now, the "network" was just an old Telcom switch, and an online HDD. No DHCP, no nothing. The computers dropped to the default 169.254.0.0/16 link local block of addresses, the HDD was open to all, cute stuff. I do some research and present to him a few options. To start things off, and to show them that a proper setup is better and more functional, I set up a linux server on one old PC.
The CO is reluctant to approve of the money needed (as I have written before, budget constraints in the military is the stuff of nightmares, people there expect proper setups with two toothpicks and a rubber band). So, I employ the very principles I learned from the holy book Bastard Operator From Hell: terrorizing with intimidating-looking things. I show him the linux server, green letters over black font, ngrep -x running (it spooks many people to be shown that). After some techno-babble I got approval for a proper rack server and new PCs. Then came the hard part: convincing him to ditch the old Telcom switch in favour of a new CISCO Catalyst one.
Three hours of non-stop barrage. Long papers of NATO specifications on security standards. Subliminal threats on security compromises. God, I never knew I would have to stoop so low. How little did I know that after that...
Came the horrors of user support.
Moral of the story: an old greek saying says "even a saint needs terrorizing". Keep that in mind.4 -
So Facebook provided unlimited data access to loads of companies including spotify/microsoft and other big names.
Although there are privacy rules, those companies had deals which excluded them from these privacy rules.
I don't think my custom DNS server or a pihole is enough anymore, let's firewall block all Facebook's fucking ip ranges.
Source: https://fossbytes.com/facebook-gave...19 -
It were around 1997~1998, I was on middle school. It was a technical course, so we had programing languages classes, IT etc.
The IT guy of our computer lab had been replaced and the new one had blocked completely the access on the computers. We had to make everything on floppy disks, because he didn't trusted us to use the local hard disk. Our class asked him to remove some of the restrictions, but he just ignored us. Nobody liked that guy. Not us, not the teachers, not the trainees at the lab.
Someday a friend and me arrived a little bit early at the school. We gone to the lab and another friend that was a trainee on the lab (that is registered here, on DevRant) allowed us to come inside. We had already memorized all the commands. We crawled in the dark lab to the server. Put a ms dos 5.3 boot disk with a program to open ntfs partitions and without turn on the computer monitor, we booted the server.
At that time, Windows stored all passwords in an encrypted file. We knew the exact path and copied the file into the floppy disk.
To avoid any problems with the floppy disk, we asked the director of the school to get out just to get a homework we theorically forgot at our friends house that was on the same block at school. We were not lying at all. He really lived there and he had the best computer of us.
The decrypt program stayed running for one week until it finds the password we did want: the root.
We came back to the lab at the class. Logged in with the root account. We just created another account with a generic name but the same privileges as root. First, we looked for any hidden backup at network and deleted. Second, we were lucky: all the computers of the school were on the same network. If you were the admin, you could connect anywhere. So we connected to a "finance" computer that was really the finances and we could get lists of all the students with debits, who had any discount etc. We copied it to us case we were discovered and had to use anything to bargain.
Now the fun part: we removed the privileges of all accounts that were higher than the trainee accounts. They had no access to hard disks anymore. They had just the students privileges now.
After that, we changed the root password. Neither we knew it. And last, but not least, we changed the students login, giving them trainee privileges.
We just deleted our account with root powers, logged in as student and pretended everything was normal.
End of class, we went home. Next day, the lab was closed. The entire school (that was school, mid school and college at the same place) was frozen. Classes were normal, but nothing more worked. Library, finances, labs, nothing. They had no access anymore.
We celebrated it as it were new years eve. One of our teachers came to us saying congratulations, as he knew it had been us. We answered with a "I don't know what are you talking about". He laughed and gone to his class.
We really have fun remembering this "adventure". :)
PS: the admin formatted all the servers to fix the mess. They had plenty of servers.4 -
Paranoid Developers - It's a long one
Backstory: I was a freelance web developer when I managed to land a place on a cyber security program with who I consider to be the world leaders in the field (details deliberately withheld; who's paranoid now?). Other than the basic security practices of web dev, my experience with Cyber was limited to the OU introduction course, so I was wholly unprepared for the level of, occasionally hysterical, paranoia that my fellow cohort seemed to perpetually live in. The following is a collection of stories from several of these people, because if I only wrote about one they would accuse me of providing too much data allowing an attacker to aggregate and steal their identity. They do use devrant so if you're reading this, know that I love you and that something is wrong with you.
That time when...
He wrote a social media network with end-to-end encryption before it was cool.
He wrote custom 64kb encryption for his academic HDD.
He removed the 3 HDD from his desktop and stored them in a safe, whenever he left the house.
He set up a pfsense virtualbox with a firewall policy to block the port the student monitoring software used (effectively rendering it useless and definitely in breach of the IT policy).
He used only hashes of passwords as passwords (which isn't actually good).
He kept a drill on the desk ready to destroy his HDD at a moments notice.
He started developing a device to drill through his HDD when he pushed a button. May or may not have finished it.
He set up a new email account for each individual online service.
He hosted a website from his own home server so he didn't have to host the files elsewhere (which is just awful for home network security).
He unplugged the home router and began scanning his devices and manually searching through the process list when his music stopped playing on the laptop several times (turns out he had a wobbly spacebar and the shaking washing machine provided enough jittering for a button press).
He brought his own privacy screen to work (remember, this is a security place, with like background checks and all sorts).
He gave his C programming coursework (a simple messaging program) 2048 bit encryption, which was not required.
He wrote a custom encryption for his other C programming coursework as well as writing out the enigma encryption because there was no library, again not required.
He bought a burner phone to visit the capital city.
He bought a burner phone whenever he left his hometown come to think of it.
He bought a smartphone online, wiped it and installed new firmware (it was Chinese; I'm not saying anything about the Chinese, you're the one thinking it).
He bought a smartphone and installed Kali Linux NetHunter so he could test WiFi networks he connected to before using them on his personal device.
(You might be noticing it's all he's. Maybe it is, maybe it isn't).
He ate a sim card.
He brought a balaclava to pentesting training (it was pretty meme).
He printed out his source code as a manual read-only method.
He made a rule on his academic email to block incoming mail from the academic body (to be fair this is a good spam policy).
He withdraws money from a different cashpoint everytime to avoid patterns in his behaviour (the irony).
He reported someone for hacking the centre's network when they built their own website for practice using XAMMP.
I'm going to stop there. I could tell you so many more stories about these guys, some about them being paranoid and some about the stupid antics Cyber Security and Information Assurance students get up to. Well done for making it this far. Hope you enjoyed it. 26
26 -
1 - Please hack his/her facebook account for me.
2 - (at home) I used to block wifi access by mac filtering and if there's legit server down and wifi isn't working, everyone blames me.
(I am freelancer and mostly work from home)
3 - almost all of my relatives think I don't work.
4 - I am first choice for everyone's phone, PC and hardware repair.
This one is classic
GET A REAL JOB, you need to go out in the field for work.5 -
I’ve started the process of setting up the new network at work. We got a 1Gbit fibre connection.
Plan was simple, move all cables from old switch to new switch. I wish it was that easy.
The imbecile of an IT Guy at work has setup everything so complex and unnecessary stupid that I’m baffled.
We got 5 older MacPros, all running MacOS Server, but they only have one service running on them.
Then we got 2x xserve raid where there’s mounted some external NAS enclosures and another mac. Both xserve raid has to be running and connected to the main macpro who’s combining all this to a few different volumes.
Everything got a static public IP (we got a /24 block), even the workstations. Only thing that doesn’t get one ip pr machine is the guest network.
The firewall is basically set to have all ports open, allowing for easy sniffing of what services we’re running.
The “dmz” is just a /29 of our ip range, no firewall rules so the servers in the dmz can access everything in our network.
Back to the xserve, it’s accessible from the outside so employees can work from home, even though no one does it. I asked our IT guy why he hadn’t setup a VPN, his explanation was first that he didn’t manage to set it up, then he said vpn is something hackers use to hide who they are.
I’m baffled by this imbecile of an IT guy, one problem is he only works there 25% of the time because of some health issues. So when one of the NAS enclosures didn’t mount after a power outage, he wasn’t at work, and took the whole day to reply to my messages about logins to the xserve.
I can’t wait till I get my order from fs.com with new patching equipment and tonnes of cables, and once I can merge all storage devices into one large SAN. It’ll be such a good work experience.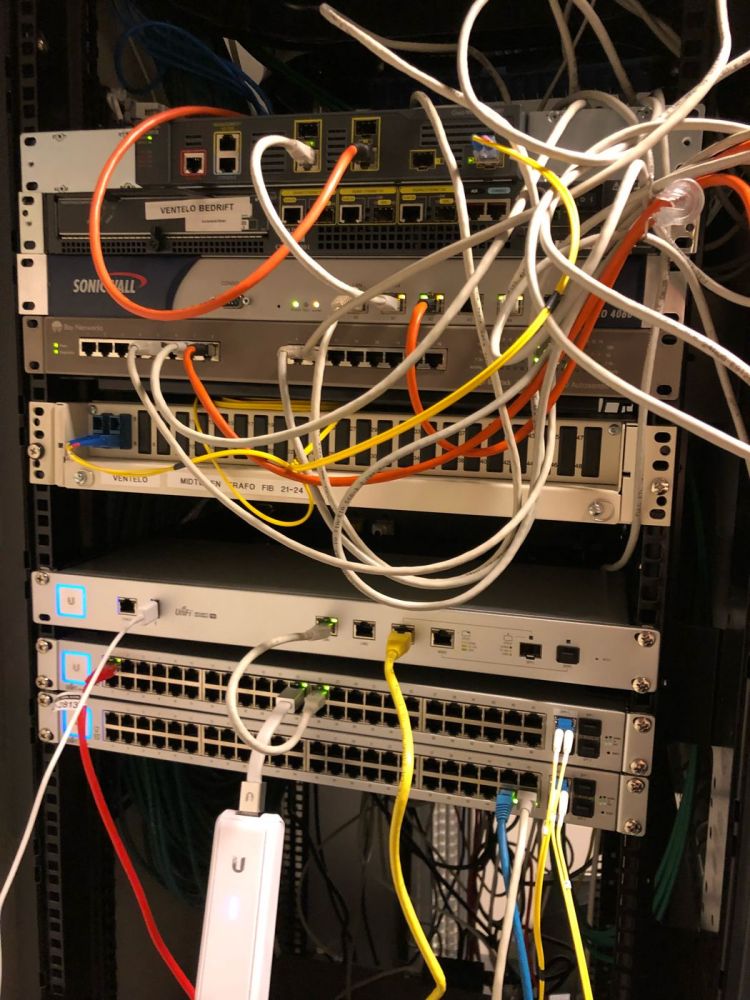 7
7 -
My school just tried to hinder my revision for finals now. They've denied me access just today of SSHing into my home computer. Vim & a filesystem is soo much better than pen and paper.
So I went up to the sysadmin about this. His response: "We're not allowing it any more". That's it - no reason. Now let's just hope that the sysadmin was dumb enough to only block port 22, not my IP address, so I can just pick another port to expose at home. To be honest, I was surprised that he even knew what SSH was. I mean, sure, they're hired as sysadmins, so they should probably know that stuff, but the sysadmins in my school are fucking brain dead.
For one, they used to block Google, and every other HTTPS site on their WiFi network because of an invalid certificate. Now it's even more difficult to access google as you need to know the proxy settings.
They switched over to forcing me to remote desktop to access my files at home, instead of the old, faster, better shared web folder (Windows server 2012 please help).
But the worst of it includes apparently having no password on their SQL server, STORING FUCKING PASSWORDS IN PLAIN TEXT allowing someone to hijack my session, and just leaving a file unprotected with a shit load of people's names, parents, and home addresses. That's some super sketchy illegal shit.
So if you sysadmins happen to be reading this on devRant, INSTEAD OF WASTING YOUR FUCKING TIME BLOCKING MORE WEBSITES THAN THEIR ARE LIVING HUMANS, HOW ABOUT TRY UPPING YOUR SECURITY, PASSWORDS LIKE "", "", and "gryph0n" ARE SHIT - MAKE IT BETTER SO US STUDENTS CAN ACTUALLY BROWSE MORE FREELY - I THINK I WANT TO PASS, NOT HAVE EVERY OTHER THING BLOCKED.
Thankfully I'm leaving this school in 3 weeks after my last exam. Sure, I could stay on with this "highly reputable" school, but I don't want to be fucking lied to about computer studies, I don't want to have to workaround your shitty methods of blocking. As far as I can tell, half of the reputation is from cheating. The students and sysadmins shouldn't have to have an arms race between circumventing restrictions and blocking those circumventions. Just make your shit work for once.
**On second thought, actually keep it like that. Most of the people I see in the school are c***s anyway - they deserve to have half of everything they try to do censored. I won't be around to care soon.**undefined arms race fuck sysadmin ssh why can't you just have any fucking sanity school windows server security2 -
*working on a programming assignment for a graduate-level course*
"We will provide you code that implements the protocol in the server. You do not need to touch this code."
*provided file has syntax errors, including a block comment which doesn't close before EOF*1 -
Great finaly get away on vacation 2weeks of just realaxing, 30min before leaving to the airport i get a sms from my server one of my main hard drives fail. No problem just need to swap the drive and start the recover at the airport.
At the airport i connect to my home vpn and start the recovery everything works fine just need to restart the server when done ~12h. next day im in the hotell and my vpn does not accept my connection, okey might be the hotell that block vpn connections i try my external vpn and it works and i try to connect home when i get a lovley text from my server "login attempt has failed from ip:x" then it hits me i have forgotten to add to whitelist. Outsmarted myself to just let i be.
So i finally get 2 weeks off and nothing i can do about it.3 -
Decided to throw pi-hole in a bin and found enough resources to throw together my own dns filter in node, which if not on the blacklist - proxies the request to an actual dns, which allows to filter given just a word too (because it's regex matching), "came up" with the idea after @Linuxxx wanted to make (or made?) some big hosts file via php matching and blocking to block anything that e.g. contains "google".
By resources I totally mean I would have ate shit, if it wasn't for: https://peteris.rocks/blog/... as most docs are absolute garbage regarding node-dns 54
54 -
I just tried to sign up to Instagram. I made a big mistake.
First up with Facebook related stuff is data. Data, data and more data. Initially when you sign up (with a new account, not login with Facebook) you're asked your real name, email address and phone number. And finally the username you'd like to have on the service. I gave them a phone number that I actually own, that is in my iPhone, my daily driver right now (and yes I have 3 Androids which all run custom ROMs, hold your keyboards). The email address is a usual for me, instagram at my domain. I am a postmaster after all, and my mail server is a catch-all one. For a setup like that, this is perfectly reasonable. And here it's no different, devrant at my domain. On Facebook even, I use fb at my domain. I'm sure you're starting to see a pattern here. And on Facebook the username, real name and email domain are actually the same.
So I signed up, with - as far as I'm aware - perfectly valid data. I submitted the data and was told that someone at Instagram will review the data within 24 hours. That's already pretty dystopian to me. It is now how you block bots. It is not how Facebook does it either, at least since last time I checked. But whatever. You'd imagine that regardless of the result, they'd let you know. Cool, you're in, or sorry, you're rejected and here's why. Nope.
Fast-forward to today when I recalled that I wanted to sign up to Instagram to see my girlfriend's pictures. So I opened Chromium again that I already use only for the rancid Facebook shit.. and it was rejected. Apparently the mere act of signing up is a Terms of Service violation. I have read them. I do not know which section I have violated with the heinous act of signing up. But I do have a hunch.
Many times now have I been told by ignorant organizations that I would be "stealing" their intellectual property, or business assets or whatever, just because I sent them an email from their name on my domain. It is fucking retarded. That is MY domain, not yours. Learn how email works before you go educate a postmaster. Always funny to tell them how that works. But I think that in this case, that is what happened.
So I appealed it, using a random link to something on Instagram's help section from a third-party blog. You know it's good when the third-party random blog is better. But I found the form and filled it in. Same shit all over again for info, prefilling be damned I guess. Minor convenience though, whatever.
I get sent an email in German, because apparently browsing through a VPS in Germany acting as a VPN means you're German. Whatever... After translating it, I found that it asks me to upload a picture of myself, holding a paper in my hands, on which I would have a confirmation code, my username, and my email address.. all hand-written. It must not be too dark, it must be clear, it must be in JPEG.. look, I just wanted to fucking sign up.
I sent them an email back asking them to fix all of this. While I was writing it and this rant, I thought to myself that they can shove that piece of paper up their ass. In fact I would gladly do it for them.
Long story short, do not use Instagram. And one final thing I have gripes with every time. You are not being told all the data you'll have to present from the get-go. You're not being told the process. Initially I thought it'd just be email, phone, username, and real name. Once signed up (instantly, not within 24 hours!) I would start setting up my account and adding a profile picture. The right way to ask for a picture of me! And just do it at my own pace, as I please.
And for God's sake, tackle abuse when it actually happens. You'll find out who's a bot and who isn't by their usage patterns soon enough. Do not do any of this at sign-up. Or hell, use a CAPTCHA or whatever, I don't fucking care. There's so many millions of ways to skin this cat.
Facebook and especially Instagram. Both of them are fucking retarded.6 -
And this, ladies and gentlemen, is why you need properly tested backups!
TL;DR: user blocked on old gitlab instance cascade deleted all projects the user was set as owner.
So, at my customer, collegue "j" reviews gitlab users and groups, notices an user who left the organisation
"j" : ill block this user
> "j" blocks user
> minutes pass away, working, minding our own business
> a wild team devops leader "k" appears
k: where are all the git projects?
> waitwut?.jpg
> k: yeah all git projects where user was owner of, are deleted
> j.feeling.despair() ; me.feeling.despair();
> checks logs on server, notices it cascade deletes all projects to that user
> lmgt log line
> is a bugreport reported 3(!) years ago
> gitlab hasnt been updated since 3 years
> gitlab system owner is not present, backup contact doesnt know shit about it
> i investigate further, no daily backup cron tasks, no backup has been made whatsoever.
> only 'backups' are on file system level, trying to restore those
> gitlab requires restore of postgres db
> backup does not contain postgres since the backup product does not support that (wtf???)
> fubar.scene
> filesystem restore finished...
> backup product did not back up all files from git tree, like none of refs were stored since the product cannot handle such filenames .. Git repo's completely broken
Fuck my life6 -
Often I hear that one should block spam email based on content match rather than IP match. Sometimes even that blocking Chinese ranges in particular is prejudiced and racist. Allow me to debunk that after I've been looking at traffic on port 25 with tcpdump for several weeks now, and got rid of most of my incoming spam too.
There are these spamhausen that communicate with my mail server as much as every minute.
- biz-smtp.com
- mailing-expert.com
- smtp-shop.com
All of them are Chinese. They make up - rough guess - around 90% of the traffic that hits my edge nodes, if not more.
The network ranges I've blocked are apparently as follows:
- 193.106.175.0/24 (Russia)
- 49.64.0.0/11 (China)
- 181.39.88.172 (Ecuador)
- 188.130.160.216 (Russia)
- 106.75.144.0/20 (China)
- 183.227.0.0/16 (China)
- 106.75.32.0/19 (China)
.. apparently I blocked that one twice, heh
- 116.16.0.0/12 (China)
- 123.58.160.0/19 (China)
It's not all China but holy hell, a lot of spam sure comes from there, given how Golden Shield supposedly blocks internet access to the Chinese citizens. A friend of mine who lives in China (how he got past the firewall is beyond me, and he won't tell me either) told me that while incoming information is "regulated", they don't give half a shit about outgoing traffic to foreign countries. Hence all those shitty filter bag suppliers and whatnot. The Chinese government doesn't care.
So what is the alternative like, that would block based on content? Well there are a few solutions out there, namely SpamAssassin, ClamAV and Amavis among others. The problem is that they're all very memory intensive (especially compared to e.g. Postfix and Dovecot themselves) and that they must scan every email, and keep up with evasion techniques (such as putting the content in an image, or using characters from different character sets t̾h̾a̾t̾ ̾l̾o̾o̾k̾ ̾s̾i̾m̾i̾l̾a̾r̾).
But the thing is, all of that traffic comes from a certain few offending IP ranges, and an iptables rule that covers a whole range is very cheap. China (or any country for that matter) has too many IP ranges to block all of them. But the certain few offending IP ranges? I'll take a cheap IP-based filter over expensive content-based filters any day. And I don't want to be shamed for that.7 -
My Sunday Morning until afternoon. FML. So I was experiencing nightly reboots of my home server for three days now. Always at 3:12am strange thing. Sunday morning (10am ca) I thought I'd investigate because the reboots affected my backups as well. All the logs and the security mails said was that some processes received signal 11. Strange. Checked the periodics tasks and executed every task manually. Nothing special. Strange. Checked smart status for all disks. Two disks where having CRC errors. Not many but a couple. Oh well. Changing sata cables again 🙄. But those CRC errors cannot be the reason for the reboots at precisely the same time each night. I noticed that all my zpools got scrubbed except my root-pool which hasn't been scrubbed since the error first occured. Well, let's do it by hand: zpool scrub zroot....Freeze. dafuq. Walked over to the server and resetted. Waited 10 minutes. System not up yet. Fuuu...that was when I first guessed that Sunday won't be that sunny after all. Connected monitor. Reset. Black screen?!?! Disconnected all disks aso. Reset. Black screen. Oh c'moooon! CMOS reset. Black screen. Sigh. CMOS reset with a 5 minute battery removal. And new sata cable just in cable. Yes, boots again. Mood lightened... Now the system segfaults when importing zroot. Good damnit. Pulled out the FreeBSD bootstick. zpool import -R /tmp zroot...segfault. reboot. Read-only zroot import. Manually triggering checksum test with the zdb command. "Invalid blckptr type". Deep breath now. Destroyed pool, recreated it. Zfs send/recv from backup. Some more config. Reboot. Boots yeah ... Doesn't find files??? Reboot. Other error? Undefined symbols???? Now I need another coffee. Maybe I did something wrong during recovery? Not very likely but let's do it again...recover-recover. different but same horrible errors. What in the name...? Pulled out a really old disk. Put it in, boots fine. So it must be the disks. Walked around the house and searched for some new disks for a new 2 disk zfs root mirror to replace the obviously broken disks. Found some new ones even. Recovery boot, minimal FreeBSD Install for bootloader aso. Deleted and recreated zroot, zfs send/recv from backup. Set bootfs attribute, reboot........
It works again. Fuckit, now it is 6pm, I still haven't showered. Put both disks through extensive tests and checked every single block. These disks aren't faulty. But for some reason they froze my system in a way so that I had to reset my BIOS and they had really low level data errors....? I Wonder if those disks have a firmware problem? So that was most of my Sunday. Nice, isn't it? But hey: calm sea won't make a good sailor, right?3 -
! exactly dev
I'd ditched Windows and spent a while exploring the Linux ecosystem for content creation. And I have to say, it was not a nice experience.
As much as I respect the Linux mantra of "free as in freedom" and "you need to roll up your sleeves and figure out stuff on your own", it just isn't good enough for non-dev work. Sorry guys, but I need software that gets out of my way and at least does what it's supposed to do. I can't stand a horrible UI or delays and random crashes, which is exactly what happens with most things under Linux.
To replace my Windows workflow I used the following:
1. Windows -> elementaryOS (because Debian/Ubuntu repositories seem to have the best software support, and elementaryOS is the least horrible looking thing that supports that) and then Arch, because, well, Arch.
2. Blender + Maya -> Blender + Maya on Linux.
3. Reaper + FL Studio -> Ardour + LMMS.
4. Photoshop -> GIMP + Krita + Inkscape.
5. ZBrush -> nothing :(
As you can see, my use cases are pretty much all over the spectrum.
Firstly, installing and configuring stuff. A pleasure on Windows, an absolute pain on Linux. Everything just worked on Windows, I had to wrestle with library versions and patches and unstable audio layers (Linux audio just sucks, except for JACK) on Linux.
Out of these, Blender and Maya were the best experience. But even then, both would suffer from random crashes that just didn't happen on Windows.
Ardour is actually really nice when it works. Its use of JACK for routing makes it really really flexible, but it just isn't stable enough to depend on. LMMS is utter crap. I'm sorry, but I just hate the UI. Can't stand it.
GIMP, Krita, and Inkscape can't beat Photoshop, even when you consider them together. Adobe software workflow is just so much better and more intuitive.
Blender 3D sculpting is not bad, but it's nowhere as good as ZBrush.
Also, if you're a C++ dev like me, nothing beats Visual Studio 2017. Nothing. That IDE just blows everything else out of the water. Even VSCode. And it's not slow at all, it handled a fairly large project (PBRTv3) just fine on my Windows development VM. Yes, a VM.
So...I ditched Linux and went back to Windows, but I keep Linux as a VM for when I actually want to mess with Blender or Ardour. Or some dev stuff which Windows sucks at (which is becoming less frequent because of WSL).
Out of all the above, the only one I'd consider ready for production use would be Blender. Developers of open source software, please learn from Blender. Kickass UI and user friendly operation is extremely important, you can't make a random window with GTK buttons and text boxes and arcane config files and expect people to use it for serious work.
Also, Windows beats Linux hands down as an everyday OS. It's always been rock solid, if you take care of it properly (and that goes for any OS). Updates hardly take any time because I run it on a SSD. As for all the advertising and marketing bullshit, you can block a large amount of stuff. And for what can't be blocked, well, I just have to live with it, because the alternative is compromising on my creative output, which is too much for me.
I still run Linux on my server, though. And on my embedded devices (Pi, BeagleBone, etc.). It absolutely rocks there.
I realize that Linux software is not going to improve unless we do something about it, so I'll be contributing fixes and code (the joys of being a C++ dev, yay). Still, I feel that the platform and software as a whole is just not mature enough.18 -
Got my first laptop while I was overseas.
It was a windows hp laptop with Vista.
It was an absolute piece of shit.
Decided to find the people responsible of it.
Got to what a software engineer was.
Boss told me to look in the library to see if i find some books on the subject. Got a Java and C++ book.
Shit was hard af cuz I had no clue what I was doing, but I liked it. Decided to look more into an application wise platform of study rather than doing basic CLI shit. Got into web development with Java. Got a hold of more JS. Liked JS more cuz shit was easy, found about server side JS with classic ASP, did VBScript as well.
Eventually found Python, fell in love but hated the whitespace ussage for block level code etc. Found Ruby, to this day the most beautiful language according to me. Read about why's poignant intro to Ruby.
Dug it, but wanted some other things. Found out about the study of data structures ans algorithms, then harvard's free cs50 course, then mit courseware, rice's python class. Took all of them. CS50 introduced php, liked it, sounded like a drug, was easy to use, for whatever fucking reaskn my ass decided to use version 4 even though 5 was already out. Learned to appreciate advancements in programming language even more
Hipster phase, while studying php got more into JS and web design with more css concepts, wanted my shit to be pretty. Somehow landed with Common Lisp. Mind fucking blown.
Continued with php. Got into uni, math made sense through programming, ok so I am stupid, but not that stupid, python is the best calculator ever.
bring it bitches.
Graduated.
Still don't know what I am doing.1 -
!rant
TODAY WAS A SUCCESS!
-learned how to forward ports
-hosting a minecraft server
-made that stupid HP stream USEFUL
-i actually feel good about myself
note: modded server. You'll need Mantle (1.7.10), Tinker's Construct (1.7.10) and Ultra Block Compression (1.7.10).
pretty sure whitelist is disabled. the max is 50 players, not sure how good the connection will be. be nice to the ops, YoungWolves and Mehrsun
ip: 66.243.225.51
(default port)
again please be polite, the two OPs are not techy at all, but very nice gals6 -
This will be 4chan-r/greentext-ish in format. Also "me" is not me, PTH, it's referring to a game studio.
>Be me
>Be game studio
>Create event for weapon design
>Player base submit in a craptonna designs
>Holyfuck.jpg
>Create an internal service for voting
>Service doesn't check for vote except for a login
>MFW one submission has 6-digit votes
>MFW a lotta submission also start gain a lot of votes
>WTF.gif
>The vote count spiked
>Votebotting is here
>Ohshit.gif
>MFW I don't how to filter votes
>MFW I can't block rerouted traffics (VPNs, proxies, etc.)
>MFW the Discord server of the game gets vocal then Reddit.
>OhshitIfuckedup.mp43 -
So this just happened,
Me and my co-worker (we are junior developers) were working on the same bug, it was a post call throwing a server exception.
We had asked for help to debug this issue from a senior developer the day before, he was quite busy with his own tasks.
He is one those kinds who would keep working even if the entire bay is wasting their time, always keeping to himself, needless to say I haven't seen him smile.
Back to my story, he couldn't spare time yesterday so we tried to squash the bug ourselves thinking he might have forgotten we had called him.He then comes out of nowhere, he firsr checks the button bindings, params sent and the call being made.
He then went through the backend code strategically placing the break points, clicks and debugs a few times and then opens the console. BAM!!!!
" D' hell yo !!" Shows up in the console, not just once but multiple times. Turns out I forgot the logger I had placed in the catch block.
He turns to me in super slo-mo looks me in the eye and whispers "what the hell yo!" and kept quite for some time, meanwhile the sense of cringe was slowly creeping on me. That was when he let out a loud blurt and the entire cabin turned to us. Needless to say it was awkward.
His smile was creepy though :/ -
"There's more to it"
This is something that has been bugging me for a long time now, so <rant>.
Yesterday in one of my chats in Telegram I had a question from someone wanting to make their laptop completely bulletproof privacy respecting, yada yada.. down to the MAC address being randomized. Now I am a networking guy.. or at least I like to think I am.
So I told him, routers must block any MAC addresses from leaking out. So the MAC address is only relevant inside of the network you're in. IPv6 changes this and there is network discovery involved with fandroids and cryphones where WiFi remains turned on as you leave the house (price of convenience amirite?) - but I'll get back to that later.
Now for a laptop MAC address randomization isn't exactly relevant yet I'd say.. at least in something other than Windows where your privacy is right out the window anyway. MAC randomization while Nadella does the whole assfuck, sign me up! /s
So let's assume Linux. No MAC randomization, not necessary, privacy respecting nonetheless. MAC addresses do not leak outside of the network in traditional IPv4 networking. So what would you be worried about inside the network? A hacker inside Starbucks? This is the question I asked him, and argued that if you don't trust the network (and with a public hotspot I personally don't) you shouldn't connect to it in the first place. And since I recall MAC randomization being discussed on the ISC's dhcp-users mailing list a few months ago (http://isc-dhcp-users.2343191.n4.nabble.com/...), I linked that in as well. These are the hardcore networking guys, on the forum of one of the granddaddies of the internet. They make BIND which pretty much everyone uses. It's the de facto standard DNS server out there.
The reply to all of this was simply to the "don't connect to it if you don't trust it" - I guess that's all the privacy nut could argue with. And here we get to the topic of this rant. The almighty rebuttal "there's more to it than that!1! HTTPS doesn't require trust anymore!1!"
... An encrypted connection to a website meaning that you could connect to just about any hostile network. Are you fucking retarded? Ever heard of SSL stripping? Yeah HSTS solves that but only a handful of websites use it and it doesn't scale up properly, since it's pretty much a hardcoded list in web browsers. And you know what? Yes "there's more to it"! There's more to networking than just web browsing. There's 65 THOUSAND ports available on both TCP and UDP, and there you go narrow your understanding of networking to just 2 of them - 80 and 443. Yes there's a lot more to it. But not exactly the kind of thing you're arguing about.
Enjoy your cheap-ass Xiaomeme phone where the "phone" part means phoning home to China, and raging about the Google apps on there. Then try to solve problems that aren't actually problems and pretty vital network components, just because it's an identifier.
</rant>
P.S. I do care a lot about privacy. My web and mail servers for example do not know where my visitors are coming from. All they see is some reverse proxies that they think is the whole internet. So yes I care about my own and others' privacy. But you know.. I'm old-fashioned. I like to solve problems with actual solutions.10 -
I'm hal laughting, half facepaling.
Use multiple servers they said
It's gonna balance automaticlly your load they said.
Well, they didn';t accoubnt for a MEGA badly writen API whic can block a whole server for a minute.
Or, but it's not the end !!!
So you see ? 1 at 100%, 1 at 0% ? Quick maths : Average 50%.
Autoscaling kicks in at average 40% for 2 minutes.
So it kicks in... Created a 3d server... Which is still booting !!
And some trafic redirected there.
Sooo. Users on a 100% server : Bad bad bad for them
Users on 0% server : No problems
users on a new 3d server : Wait 15 seconds, then it's like 0%.
Fun fun fun. At least I know now which fucking API does that. 7
7 -
So i just had an interesting conversation.
View source images in comments
So some background. I used to do a lot of Minecraft development and server configuration. And Minecraft being made of mostly 12-year-olds they really don't pay very well. So I moved on from Minecraft but someone reached out for me to do their configuration for their server. (this was about a month ago) and I quoted them 40/hr because that's what I charge for my web dev work. So he promptly declined and I thought that was that. But tonight he messaged me and found a 5 month old post saying how I was looking to do free development work in order to get experience. And here is how the converstion when.
(His name is "Candy")
Candy:
Lol
Trying to take advantage of me with your bullshit $40/hour claims
Which is outright laughable
https://mc-market.org/threads/...
”I am looking for a network to stay long-term with and help/see it grow into a bigger server. (I would expect pay later down the road if we work together on an ongoing basis)”
—
Quoting your MC-Market post.
What do you have to say for yourself? Trying to take advantage of people?
Going to say something else completely delusional or own up to the fact that you were trying to take advantage of me?
I already knew you were, but now I have the hard evidence.
As I am not a stupid person.
Not only did your friend lie, but you tried to take advantage of me, thinking I was stupid enough to fall for your $40/hour bullshit for basic configuration work. MineSaga charges $30.00 an hour on the high. Don’t even try to do the same shit you did to me to anyone else. It won’t work.
Me:I was interested in doing plugin development and learning so I offered my services for free so I could learn in a more real environment. I no longer do minecraft plugins rather I am a web developer and my rate is $40/hr I am good at configuration which is why i contacted you but I am not going to lower my rate because it is "simpler" work. Just like how you can higher a prostitute to wash your car but it would be cheaper to get the kid from around the block to do it. Also not sure what your end goal is here. I gave you my rate and you didn't agree with it. So you should just move on. Plus this is the minecraft world let me know when you get to the real world so you you can pay in big boy money.
Candy:
So your configuration work for minecraft is $40/h as well?
Lol
Absolutely hilarious.
Me:
did you not read my message?
"I am not going to lower my rate because it is "simpler" work."
Candy:
Who were your most recent clients?
Me:
i'm not going to give you that information
Candy:
Because you know you are lying to me with your crazy rates, and if you aren't, that means you have near to no clients.
Yet another lie.
Me:
keep telling yourself that buddy
Candy:
Lol
Good luck getting any more clients.
rip
Me:
?
I get more clients all the time
They just are not in your realm of your minecraft imagination where you can pay a developer 20$/hr
Candy:
I just strongly disagree with the fact that you are charging $40/hour for configurative work
xD
Me:
Okay
But why even contact me? Did you really think trying to "Call me out" was going to have me lower my rates or something.
Just get over it
Candy:
I haven't called you out and overcharging like that to others in the minecraft realm for a significant gain in money for work that is not worth nearly that amount is absolutely delusional.
I would recommend you stop making up false assumptions
Me: What ever you say
I left it at that. There was some more stuff but it was not that interesting so i left it out4 -
Developing a notification API, sends emails to subscribers, email API can take only 100 IDs at once, so partitioned the email list and send mails in blocks of 100.
Forgot to reset the list after every block, so each new partition got appended to the existing list and kept going on.
Ran it against a test DB, which was recently refreshed with near-prod data !!! Thousands of emails went out of the app server in one shot and everybody receiving numerous duplicate emails. Especially the ones in the very first partition.
Got an incident raised by the CEO himself reg the flurry of emails. But, things were out of our hands, quite literally. All emails are queued up in the exchange server.
Called up the exchange server team, purged the queued emails. No other emails were sent/received during this whole episode.
Thanks to Iterables.partition in the present day.3 -
A site I manage in my spare time with a couple thousand normal users was getting attacked by a Chinese botnet. All the requests were coming from only two subnets. Easy to block. Feels like this was only the vanguard. Prelude to the real attack. I'm thinking about moving the site to its own server, so it won't affect my other sites. There at least if it gets kneeled, it'll only be that site.6
-
Client contacts our company that his site is down, we do some investigating and the only way we can access the site is on a mobile phone. From the office computers the site never loads and times out. Since we don't host the site and I've never logged into it before I don't have a lot of details so I suggest they contact whoever hosts their site. This is where things get weird.
Client tells me that the site is hosted on someone's home server. I tell him that this is quite strange in 2018 and rather unlikely and ask if he was ever given access to the site to log in or if he has access to his domain registration, GoDaddy.
He says he doesn't understand any of this and would rather I just contact his current developer and figure it out with him. We agree that he needs to get access to his site so we are going to migrate it once I get access to it.
I email his current developer letting him know the client has put me in contact with him to troubleshoot the issues with the site. I ask him some standard questions like: where is the site hosted? Can you access it from a computer? Do you have some security measures in place to block certain IP ranges? Can you give me from access to get the files? Will you send me a backup of the site for me to load up on my server?
*2days pass*
Other dev: Tell me the account number and I'll transfer the domain.
Me: I'll have to get back to you on that once I talk to the client and set up his GoDaddy account since we believe the business owner should own their domain, not their developers. In the meantime you didn't answer any of the questions I asked. Transferring the domain won't get the site on my server so I still need the files.
*3 days pass*
OD: You are trying the wrong domain. The correct domain is [redacted].com I'll have my daughter send you the files when she gets in town. We will transfer the domain to you, the client will forget to pay and the site will go down and it'll be your fault.
Me: I appreciate your advice, but the client will own their domain. I'm trying to get the site online and you have no answered any of my questions. It's been a week now and you have not transferred the domain, you have not provided a copy of the site, you have not told me where the site is hosted. The client and I are both getting impatient at this point when will we receive a backup of the site and the transfer of the domain?
OD: Go fuck yourself, tell the client they can sue me.
If the client is that terrible, wouldn't you want to hand them off to anyone willing to take them? I have never understood why developers and agencies try to hold clients hostage by keeping their domain or website and refusing access. From what I can tell this is a freelance developer without a real company so a legal battle likely isn't going to go well since the domain is worthless to him as the copyright to the name is owned by the client. This isn't the first time we've had to help clients through this sort of thing.4 -
Our school had for an open source way of dealing with home schooling and managing the school network and so on.
Now the government forced a "proprietary" system on our school and everyone hates it. The teachers didn't want it the pupils didn't want it but who cares "what we do is the best".
Btw the proprietary system costs a fuck load of money even though they just mixed many open source projects and made it their own proprietary thing.
And this company now get's loads of money for their shitty system that never really worked once since we got it.
They blocked so many ip's that we can't even access google and it's services on the school wifi and the bandwith dropped severely with the new system.
Oh and many random ip's e.g. one of my vps is accessible but the other one not.
Discord is blocked.
Web whatsapp.
And so on...
Now....
I need to learn for tests next week and need to access that stuff on the portal but...
Now they decided to switch the LDAP server to the new system and since a few hours i can't access this fucking thing.
It seems like the platform now contacts the new server which isn't even up and running....
Never change a fucking running system....
Oh and we got smart boards and it runs on android and they didn't block adb. Now i installed clash of clans on one of those things. Haha whoops.
These boards cost 7000€ and have security patches from 2 years ago....and Android 87 -
Subject: a rant for devRant
Hello,
Not entirely sure why or when exactly it happened, but after I joined mailing lists I have a pet peeve for people who don't use a proper subject line, or don't use email when I literally made a mail server for that purpose (some organizations really prefer calling apparently). Is it really that hard to summarize a message in one sentence? Hell half the time even the message itself is just a few sentences.
Also the greeting and salutation at the beginning and end of email messages. I find them so redundant. Has anyone ever gotten any meaningful information out of "Hello", "Greetings", "Dear", or something like that? Or "Best regards" or whatever. I get that it's just being polite but it's so meaningless! I really don't like using them anymore. Just a message block and who it came from, that's all it needs to me. Instead pour some effort into the damn subject, the title of whatever drivel you're putting out there! Or replying to an email *only* when the subject matter is still related! Or actually replying to the damn email if it's still that subject matter...
I probably sound like an old man, but seriously.. email isn't a hard concept once you "get it". Anyone can write a halfway decent letter, why isn't that the case for email?
Best regards,
Condor6 -
FUCK WORDPRESS
FUCK WORDPRESS
FUCK WORDPRESS
FUCK WORDPRESS
FUCK WORDPRESS
Who the fuck thought "Oh lets put all caches in the options table". This is so incredible dumb. The options table has nearly 8GB and is just unusable. The query for the "real options" takes about 3s. To export this fucking shit I had to block the prod server for 20 minutes to get a db dump. I want to womit in the mouth of the fucking idiot who did this.6 -
How can I use a custom DNS server on my schools network?
They seem to block any DNS that isn't their own. I've tried 8.8.8.8 and the new cloudflare one. Both blocked, it's a real issue because their default dns dies for about a minute every 12/24 hrs causing my VPN to go down.
How do they even block external DNS servers?5 -
Question for Web Server Gurus and Security Ninjas.
How to prevent bots, crawlers, spammers sending various numerous requests to your web servers?
There have been numerous requests to routes like /admin /ssh /phpmyadmin etc etc and all kinds of stuff to the web server.
Is there a way to automatically block those stupid IPs :/9 -
Old story, happened some way back. I worked part-time for a small web development company that did between other things something called SharePoint development, basically .net webforms with shit glitter on top of it.
The most weird part of it, was the fact that we were working on vms that hosted the app, it was our dev, test and staging environment, as well as were we showed the client the polished turd.
Did I say that it was on a vm? Well it was on a remote vm, that each of use had access to it, through our domain accounts, and they couldn't configure the windows server to accept more than two or three users at once to be connected.
That was our test enviroment and dev enviroment, sooo showing the app to the client meant for the rest of us to not write any code because it might crash or get stuck.
The app was accessible and discoverable by url and through google search from outside, I dont think that should have been allowed.
The most disastrous part was that we had NO source versioning whatsoever, just plain old copy and paste in different folders.
Deploying to client meant remoting to the clients host or whatever it was, and manually copying the source files
If someone wanted to debug the application you had to shout, and you also could hear it, in the office: "I'm debugging!" or "I'm deploying!". Because we were on the same machine, there was only one process with the server and it meant that if you debug or deployed it would block it for the others.
Should I talk about code quality? Maybe not.1 -
CORS is shit
Stupid useless shit that protects from nothing. It is harmful mechanism that does nothing but randomly blocks browser from accessing resources - nothing more.
Main idea of CORS is that if server does not send proper header to OPTIONS request, browser will block other requests to that server.
What does stupid cocksuckers that invented CORS, think their retarded shit can protect from?
- If server is malicious, it will send any header required to let you access it.
- If client has malicious intents - he will never use your shit browser to make requests, he will use curl or any ther tool available. Also if server security bases on something as unreliable as http headers it sends to the client - its a shit server, and CORS will not save it.
Can anyone give REAL examples when CORS can really protect from anything?33 -
Hotmail and t-online (Germany) are the worst E-Mail providers. They have a weird setup with weird custom white and blacklists.
My mail server is configured perfectly. However, my server is inside an IP range microsoft and telekom decided to block.
Oh... come on6 -
ZNC shenanigans yesterday...
So, yesterday in the midst a massive heat wave I went ahead, booze in hand, to install myself an IRC bouncer called ZNC. All goes well, it gets its own little container, VPN connection, own user, yada yada yada.. a nice configuration system-wise.
But then comes ZNC. Installed it a few times actually, and failed a fair few times too. Apparently Chrome and Firefox block port 6697 for ZNC's web interface outright. Firefox allows you to override it manually, Chrome flat out refuses to do anything with it. Thank you for this amazing level of protection Google. I didn't notice a thing. Thank you so much for treating me like a goddamn user. You know Google, it felt a lot like those plastic nightmares in electronics, ultrasonic welding, gluing shit in (oh that reminds me of the Nexus 6P, but let's not go there).. Google, you are amazing. Best billion dollar company I've ever seen. Anyway.
So I installed ZNC, moved the client to bouncer connection to port 8080 eventually, and it somewhat worked. Though apparently ZNC in its infinite wisdom does both web interface and IRC itself on the same port. How they do it, no idea. But somehow they do.
And now comes the good part.. configuration of this complete and utter piece of shit, ZNC. So I added my Freenode username, password, yada yada yada.. turns out that ZNC in its infinite wisdom puts the password on the stdout. Reminded me a lot about my ISP sending me my password via postal mail. You know, it's one thing that your application knows the plaintext password, but it's something else entirely to openly share that you do. If anything it tells them that something is seriously wrong but fuck! You don't put passwords on the goddamn stdout!
But it doesn't end there. The default configuration it did for Freenode was a server password. Now, you can usually use 3 ways to authenticate, each with their advantages and disadvantages. These are server password, SASL and NickServ. SASL is widely regarded to be the best option and if it's supported by the IRC server, that's what everyone should use. Server password and NickServ are pretty much fallback.
So, plaintext password, default server password instead of SASL, what else.. oh, yeah. ZNC would be a server, right. Something that runs pretty much forever, 24/7. So you'd probably expect there to be a systemd unit for it... Except, nope, there isn't. The ZNC project recommends that you launch it from the crontab. Let that sink in for a moment.. the fucking crontab. For initializing services. My whole life as a sysadmin was a lie. Cron is now an init system.
Fortunately that's about all I recall to be wrong with this thing. But there's a few things that I really want to tell any greenhorn developers out there... Always look at best practices. Never take shortcuts. The right way is going to be the best way 99% of the time. That way you don't have to go back and fix it. Do your app modularly so that a fix can be done quickly and easily. Store passwords securely and if you can't, let the user know and offer alternatives. Don't put it on the stdout. Always assume that your users will go with default options when in doubt. I love tweaking but defaults should always be sane ones.
One more thing that's mostly a jab. The ZNC software is hosted on a .in domain, which would.. quite honestly.. explain a lot. Is India becoming the next Chinese manufacturers for software? Except that in India the internet access is not restricted despite their civilization perhaps not being fully ready for it yet. India, develop and develop properly. It will take a while but you'll get there. But please don't put atrocities like this into the world. Lastly, I know it's hard and I've been there with my own distribution project too. Accept feedback. It's rough, but it is valuable. Listen to the people that criticize your project.7 -
So im pretty sure I made the biggest/dumbest fuckup for the year already...
Deleting the majority of our RHEL server's root partition.
Blonde mistake for sure.
Technically i didn't actually delete it... just fucked up the block device so it's no longer recognised as existing.
I could go fishing for data and put it back together... but since i have the boot par and all the uset account configs... plus i actually documented all remarkable server updates cuz im trying to get better at the whole 'having a team' thing... im just gonna play it safe and go through it all like old school video games when you die right before the checkpoint so you need to go through the same paths again and again... but not too fast or youll fuck up somewhere easy and itll drive u nuts when u gotta reiterate again.
@jestdotty here you go. Always saying I just mention positives about myself... cant get much worse than this.10 -
I remember someday from a few years ago, because i just got off the phone with a customer calling me way too early! (meaning i still was in my pyjamas)
C:"Hey NNP, why si that software not available (He refers to fail2ban on his server)
Me: "It's there" (shows him terminal output)
C: " But i cannot invoke it, there is no fail2ban command! you're lieing"
Me: "well, try that sudoers command i gave you (basically it just tails all the possible log files in /var/log ) , do you see that last part with fail2ban on it?
C: "Yeah, but there is only a file descriptor! nothing is showing! It doesnt do anything.
Me: "That's actually good, it means that fail2ban does not detect any anomalies so it does not need to log it"
C:" How can you be sure!?"
Me: "Shut up and trust me, i am ROOT"
(Fail2ban is a software service that checks log files like your webserver or SSH to detect floods or brute force attempts, you set it up by defining some "jails" that monitor the things you wish to watch out for. A sane SSH jail is to listen to incoming connection attempts and after 5 or 10 attempts you block that user's IP address on firewall level. It uses IPtables. Can be used for several other web services like webservers to detect and act upon flooding attempts. It uses the logfiles of those services to analyze them and to take the appropriate action. One those jails are defined and the service is up, you should see as little log as possible for fail2ban.) 5
5 -
Recently i learned about pipes in C#. I made 2 simple console apps(client and server) in visual studio. They work flawlessly. After that i made plugin for unity that uses those pipes. (because i want to crunch numbers in .net 4.7 app and display results in unity). Every function in my plugin is wrapped in try-catch block. Unity frezzes/crashes everytime i try to use my plugin 😥1
-
If you're looking to buy IoT stuff, you should try Xiaomi. Not only their stuff works, even when you block Xiaomi servers, but it can still be controlled remotely from an independent server. Although they are probably not happy about that lol. (i realize how much this sounds like an ad, but I'm too excited that it actually works :D)4
-
>when a sysadmin sets his local Linux firewall (gufw) where one of the rules had the end of the cidr block as the first IP address and the beginning of the cidr block as the last IP address.
Needless to say nothing worked. But the server was secure because nothing could connect to it 😂1 -
To me this is one of the most interesting topics. I always dream about creating the perfect programming class (not aimed at absolute beginners though, in the end there should be some usable software artifact), because I had to teach myself at least half of the skills I need everyday.
The goal of the class, which has at least to be a semester long, is to be able to create industry-ready software projects with a distributed architecture (i.e. client-server).
The important thing is to have a central theme over the whole class. Which means you should go through the software lifecycle at least once.
Let's say the class consists of 10 Units à ~3 hours (with breaks ofc) and takes place once a week, because that is the absolute minimum time to enable the students to do their homework.
1. Project setup, explanation of the whole toolchain. Init repositories, create SSH keys for github/bitbucket, git crash course (provide a cheat sheet).
Create a hello world web app with $framework. Run the web server, let the students poke around with it. Let them push their projects to their repositories.
The remainder of the lesson is for Q&A, technical problems and so on.
Homework: Read the docs of $framework. Do some commits, just alter the HTML & CSS a bit, give them your personal touch.
For the homework, provide a $chat channel/forum/mailing list or whatever for questions where not only the the teacher should help, but also the students help each other.
2. Setup of CI/Build automation. This is one of the hardest parts for the teacher/uni because the university must provide the necessary hardware for it, which costs money. But the students faces when they see that a push to master automatically triggers a build and deploys it to the right place where they can reach it from the web is priceless.
This is one recurring point over the whole course, as there will be more software artifacts beside the web app, which need to be added to the build process. I do not want to go deeper here, whether you use Jenkins, or Travis or whatev and Ansible or Puppet or whatev for automation. You probably have some docker container set up for this, because this is a very tedious task for initial setup, probably way out of proportion. But in the end there needs to be a running web service for every student which they can reach over a personal URL. Depending on the students interest on the topic it may be also better to setup this already before the first class starts and only introduce them to all the concepts in a theory block and do some more coding in the second half.
Homework: Use $framework to extend your web app. Make it a bit more user interactive with buttons, forms or the like. As we still have no backend here, you can output to alert or something.
3. Create a minimal backend with $backendFramework. Only to have something which speaks with the frontend so you can create API calls going back and forth. Also create a DB, relational or not. Discuss DB schema/model and answer student questions.
Homework: Create a form which gets transformed into JSON and sent to the backend, backend stores the user information in the DB and should also provide a query to view the entry.
4. Introduce mobile apps. As it would probably too much to introduce them both to iOS and Android, something like React Native (or whatever the most popular platform-agnostic framework is then) may come in handy. Do the same as with the minimal web app and add the build artifacts to CI. Also talk about getting software to the app/play store (a common question) and signing apps.
Homework: Use the view API call from the backend to show the data on the mobile. Play around with the mobile project to display it in a nice way.
5. Introduction to refactoring (yes, really), if we are really talking about JS here, mention things like typescript, flow, elm, reason and everything with types which compiles to JS. Types make it so much easier to refactor growing codebases and imho everybody should use it.
Flowtype would make it probably easier to get gradually introduced in the already existing codebase (and it plays nice with react native) but I want to be abstract here, so that is just a suggestion (and 100% typed languages such as ELM or Reason have so much nicer errors).
Also discuss other helpful tools like linters, formatters.
Homework: Introduce types to all your API calls and some important functions.
6. Introduction to (unit) tests. Similar as above.
Homework: Write a unit test for your form.
(TBC)4 -
Kubernetes question:
So far I've created two pods, mongo & Go
Exposed those pods using services
Their IP is 10.x.x.x and accessible from my machine only (virtual lan I'm guessing only known to host), but my machine's network ip is 192.x.x.x therefore, not accessible from outside world and to do so I need to put nginx in front to receive requests and route them internally.
Is there a way in kubernetes to make it work like nginx in terms of:
Kubernetes listen to port 80 (for example) route based on received url. As you know in enginx we define a server block with server domain_name.tld
Anything similar in kubernetes? I've cheked ingress-nginx controller, and also saw LoadBalancer but that requires a cloud provider.
If anyone can also give an example it would be great, so far examples I checked ended up screwing my setup and had to reset kubectl to get things back working18 -
Development: we need Nginx installed on *insert server list*
Me: ok, let me get in tough with the platform team.
Platform team: This should be installed in the userspace, Unix teams don't support this.
And here I am, trying to get a reverse proxy running on servers on which I do not have sudo rights.
Since it doesn't work, it's my fault, both sides block the door.
I installed it locally on a virtual machine, but the compiled or installed code doesn't work once copied.
The joy of being an "application engineer". This job title means nothing!9 -
FUCK APPLICATION LEVEL FIREWALLS!
So i cam online today, thought already lets open the shitty outlook webmail client. Holy crap .... thats way to much mails. Many of them are missed teams messages. So i open up teams and holy crap. Like every third dev in my company send me a message screaming "gitab is not working!!!".
Yesterday i updated it so imediately get in panic mode - what the shitty hack have i done?!
So yeah gitlab seems to be working just fine, everything is speedy and responsive, so i call one of my fellow devs and ask him whats wrong? And he is like oh yeah there comes a ldap error saying timeout or something.
I try to login with active directory. Works like a charm. Try another account, same problem?!
Google the problem, search gitlab tickets. Nope there is no open bug or sth. like this.
So alright lets call the network guy. "Yo, can you check if there is something ldap-like getting blocked to the gitlab server?" - He is like oh yeah damn like almost every damn request is getting blocked. Ah wait, there was an firewall update yesterday too. Yeah ldap is no longer ldap. BLOCK THAT SHIT!
After 10 minutes of figuring out what shitty type is detected by the firewall and what needs to be whitelisted to make it fucking work again it seems to work.
But ha no, there is another update rolling on, so same shit like 15 minutes later.
Now it seems to work and i have to inform every damn fcking developer that it works again. And yeah alright you sent a mail, but fuck it, i will call you though! So yeah just answering calls, mails and chat messages. Like why the fuck cant you read your mails like a damn normal person?!1 -
Outlook protection is shit!
Microsoft is blocking our company mail server AND even my private one for a couple of days now for no reason.
Every other mailing black list has nothing to complain but Microsoft: "You want to send a very important mail to your customer? Nope!"
And
"Yeah, now you tried to use your private server to fool me. Haha, nope! You didn't think I would block IPs randomly, did you?"
Fuck Microsoft! Fuck Outlook protection! Fuck hotmail!1 -
Ok, so i got this new machine and whilst migrating I want to stay online with certain services. So atm there is x.web.nl and y.web.nl both have ssl and one runs on server x and the other on server y. Now is the question how the heck do i forward that ssl file??? I figured i have to do something with my nginx server block. Because that is terminating the cert. Can someone help me out??1
-
I've been working on this personal project for awhile, I showed some screenshots, then I showed some updates (which I promptly deleted cause it was plain ugly). A website aimed at the "not-so-seasoned" devs, and I've been at a creative plateau for about 3 days now. I try to do some front-end, when I like what I see, I take care of the corresponding server-side logic, but for some reason, I'm having "Developer's block" (is that even a thing?).
Every second that goes by I try to do something else none code related, but I can't shake thinking about the project, but once I switch back to it, fuckin crickets.
I'm not asking a question this time (for once lol), just a mini dev's block rant.

