Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "firewall"
-
What a stupid configuration of firewall at my work:
devrant -> blocked because of entertainment category.
xvideos -> no problem at all.
Conclusion: sysadmin likes watching porn.13 -
'Normal' people when they get a new phone:
- install whatsapp
- install Facebook (or other social media)
- install regular email app
Me:
- Root phone
- Install app ops
- Install Signal
- Install encrypted email services' app
- Install firewall
- Install devRant
Anyone else like me here?37 -
My girlfriends mom asked whether I could fix her coworkers laptop. She claimed that it had viruses installed and laptop is laggy..
So... I got that laptop just now, got home and turned it on. It doesn't have WiFi drivers installed and I do not have any free Ethernet cable right now.
About the lags... Well you won't believe how many custom tool bars and security programs there were. McAffe, AVG, ESET and some Russian made firewall which asks for license key every 5mins.
And she asked me to reinstall windows and keep every file of hers, and she didn't bother to point which files of 300gb of photos/videos/docs are worth keeping and which are not.. HDD is 300GB :A fuck me
P. S. Since it's my first rant I can say ranting helps a lot to calm down23 -
Manager: We need to setup the security in the Mexico server
Dev: You mean that 3rd party firewall add on?
Manager: Yes
Dev: And set up the billing on the Mexico account?
Manager: Yes
Dev: lol, sure thing I’ll create the ticket
Manager: What’s so funny?
Dev: Nothing
Ticket: Build wall and get Mexico to pay for it.14 -
The spam denier
_____
An old phone conversation with a client:
Me : Hello
Client : My website and server are suspended? why is that?
Me : Your server sends spam messages.
Client : We do not send spam messages, we are on vacation, there is none in the office.
Me : Yes, but it is not necessarily you, according to our logs, your server sent spam messages in Chinese and Russian, so someone from Russia or China....etc.
Client : I do not believe you, we do not speak russian or chinese, how could we then write spam messages in those languages?
Me : I told you, maybe someone exploited some vulnerability in your website or server firewall. And if you want to activate your services, please check with your webmaster and sysadmin to secure your ....
Client: I tell you my son, because I am old and I have more life experience than you ... I am 60 years old and I tell you, spam does not exist, and YOU suspended my website and server, and created issues to sell me more of your solutions and services.
I won't check my server, I won't hire a webmaster or a sysadmin, AND YOU WILL ACTIVATE MY SERVER NOW !
(I suddenly realized that I am talking to a wall, so I switched to a robotic tone).
Me : Please resolve the issue to activate your services..
Client : YOU WILL ACTIVATE MY S...
Me : Please resolve the issue to activate your services...
Client : WHAT IS THIS SPAM STORY ANYWAY, I DO NOT BELIEVE YOU ...
Me : Please google that word and you will understand what is spam is...
Client : YOU ARE F**ING LIARS, SPAM DOES NOT EXIST... ACTIVATE MY WEBSITE N.... Beeeep !
I hang up.
Well, I thought about configuring an automatic response for this client, or a for-loop.
His voice was really unpleasant, as if he is a heavy smoker.7 -
So a friend of Mine asked me to check their Mail server because some emails got lost. Or had a funny signature.
Mails were sent from outlook so ok let's do this.
I go create a dummy account, and send/receive a few emails. All were coming in except one and some had a link appended. The link was randomly generated and was always some kind of referral.
Ok this this let's check the Mail Server.
Nothing.
Let's check the mail header. Nothing.
Face -> wall
Fml I want to cry.
Now I want to search for a pattern and write a script which sends a bunch of mails on my laptop.
Fuck this : no WLAN and no LAN Ports available. Fine let's hotspot the phone and send a few fucking mails.
Guess what? Fucking cockmagic, no funny mails appear!
At that moment I went out and was like chainsmoking 5 cigarettes.
BAM!
It hit me! A feeling like a unicorn vomiting rainbows all over my face.
I go check their firewall. Shit redirected all email ports from within the network to another server.
Yay nobody got credentials because nobody new it existed. Damn boy.
Hook on to the hostmachine power down the vm, start and hack yourself a root account before shit boots. Luckily I just forgot the credentials to a testvm some time ago so I know that shit. Lesson learned: fucking learn from your mistakes, might be useful sometimes!
Ok fucker what in the world are you doing.
Do some terminal magic and see that it listens on the email ports.
Holy cockriders of the galaxy.
Turns out their former it guy made a script which caught all mails from the server and injected all kind of bullshit and then sent them to real Webserver. And the reason why some mails weren't received was said guy was too dumb to implement Unicode and some mails just broke his script.
That fucker even implented an API to pull all those bullshit refs.
I know your name "Matthias" and I know where you live and what you've done... And to fuck you back for that misery I took your accounts and since you used the same fucking password for everything I took your mail, Facebook and steam account too.
Git gut shithead! You better get a lawyer15 -
> Customer calls
Her: I have over 5k 404 request to [insertwebsite]/autodiscover/autodiscover.xml
Me: Sound like a missconfigured exchangeserver/client. Let me have a look.
> Takes a look and can confirm the IP and the owner of that IP
Me: It looks like someone/something from xxx.xxx.xxx.xxx is failing to resolve autodiscover.[insertdomain].com
and defaults to @ record on the zone. Do you happend to know to whom that IP belongs?
Her: No, and I dont care, just block it. I do not like the 404 that shows up on the summary.
Me: Alright
> Blocks the IP in the firewall.
>>> Fast forward to next day >>>
> Someone calls, it is the same girl
Her: I cant reach my website! Infact, I cant reach anything! WHYYYYYY!!!
> I remember, blocking that IP yesterday...
Me: Oh, can you please visist "minip.se" (whatismyip.com, swedish version) and tell me what you see?
Her: Yes, it is xxx.xxx.xxx.xxx
Me: Do you remember that IP that you request that I block yesterday?
> I can hear the shame coming from the phone.
> Turn out that her collegues did'nt have any mail delivered to them from the time I blocked their IP
> Her boss is really mad
> Atleast she had a cute voice12 -
Anyone know this bitch hacker 127.0.0.1 story?
WORST HACKERS OF ALL TIME
CONTINUED IN THE COMMENTS BECUASE IT IS SO LONG...
TLdr bitch hacker hacks himself by localhost
bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> why do you kick me
<bitchchecker> can’t you discus normally
<bitchchecker> answer!
<Elch> we didn’t kick you
<Elch> you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
<bitchchecker> what ping man
<bitchchecker> the timing of my pc is right
<bitchchecker> i even have dst
<bitchchecker> you banned me
<bitchchecker> amit it you son of a bitch
<HopperHunter|afk> LOL
<HopperHunter|afk> shit you’re stupid, DST^^
<bitchchecker> shut your mouth WE HAVE DST!
<bitchchecker> for two weaks already
<bitchchecker> when you start your pc there is a message from windows that DST is applied.
<Elch> You’re a real computer expert
<bitchchecker> shut up i hack you
<Elch> ok, i’m quiet, hope you don’t show us how good a hacker you are
<bitchchecker> tell me your network number man then you’re dead
<Elch> Eh, it’s 129.0.0.1
<Elch> or maybe 127.0.0.1
<Elch> yes exactly that’s it: 127.0.0.1 I’m waiting for you great attack
<bitchchecker> in five minutes your hard drive is deleted
<Elch> Now I’m frightened
<bitchchecker> shut up you’ll be gone
<bitchchecker> i have a program where i enter your ip and you’re dead
<bitchchecker> say goodbye
<Elch> to whom?
<bitchchecker> to you man
<bitchchecker> buy buy
<Elch> I’m shivering thinking about such great Hack0rs like you
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> dude be happy my pc crashed otherwise you’d be gone
<Metanot> lol
<Elch> bitchchecker: Then try hacking me again… I still have the same IP: 127.0.0.1
<bitchchecker> you’re so stupid man
<bitchchecker> say buy buy
<Metanot> ah, [Please control your cussing] off
<bitchchecker> buy buy elch
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> elch you son of a bitch
<Metanot> bitchchecker how old are you?
<Elch> What’s up bitchchecker?
<bitchchecker> you have a frie wal
<bitchchecker> fire wall
<Elch> maybe, i don’t know
<bitchchecker> i’m 26
<Metanot> such behaviour with 26?
<Elch> how did you find out that I have a firewall?
<Metanot> tststs this is not very nice missy
<bitchchecker> because your gay fire wall directed my turn off signal back to me
<bitchchecker> be a man turn that shit off
<Elch> cool, didn’t know this was possible.
<bitchchecker> thn my virus destroys your pc man
<Metanot> are you hacking yourselves?
<Elch> yes bitchchecker is trying to hack me
<Metanot> he bitchchecker if you’re a hacker you have to get around a firewall even i can do that
<bitchchecker> yes man i hack the elch but the sucker has a fire wall the
<Metanot> what firewall do you have?
<bitchchecker> like a girl
<Metanot> firewall is normal a normal hacker has to be able to get past it…you girl
<He> Bitch give yourself a jackson and chill you’re letting them provoce you and give those little girls new material all the time
<bitchchecker> turn the firewall off then i send you a virus [Please control your cussing]er
<Elch> Noo
<Metanot> he bitchchecker why turn it off, you should turn it off
<bitchchecker> you’re afraid
<bitchchecker> i don’t wanna hack like this if he hides like a girl behind a fire wall
<bitchchecker> elch turn off your shit wall!
<Metanot> i wanted to say something about this, do you know the definition of hacking??? if he turns of the firewall that’s an invitation and that has nothing to do with hacking
<bitchchecker> shut up
<Metanot> lol
<bitchchecker> my grandma surfs with fire wall
<bitchchecker> and you suckers think you’re cool and don’t dare going into the internet without a fire wall
<Elch> bitchchecker, a collegue showed me how to turn the firewall off. Now you can try again
<Metanot> bitchhacker can’t hack
<Black<TdV>> nice play on words
<bitchchecker> wort man
<Elch> bitchchecker: I’m still waiting for your attack!
<Metanot> how many times again he is no hacker
<bitchchecker> man do you want a virus
<bitchchecker> tell me your ip and it deletes your hard drive
<Metanot> lol ne give it up i’m a hacker myself and i know how hackers behave and i can tell you 100.00% you’re no hacker..29 -
How not to give support..
Me: Creates ticket on support site, letting them know their webservice returns "maintenance" page.
Support: "It works on our end."
Support: *closes ticket*
Euhm.. excuse me?
Me: Creates another ticket with a screenshot and the curl response information..
Support: Sends screenshot back that it works on their end. "Maybe check your firewall"
Support: *closes ticket*
I ain't playing these games..
Me: Creates new ticket with more curl responses from 4 different servers to prove it's not "firewall" related.
Support: ..
2 days later
Me: Sends *friendly* reminder.
Support: ..
6 days later
Me: Creates ticket again saying I'm still having issues.
Support: "I'm forwarding this to our technical support"
Support: *closes ticket*
10 minutes later.
Technical Support: "Here's the manual for our integration .pdf."
Excuse me, you say what now? I KNOW HOW IT WORKS, I'VE WRITTEN THE INTEGRATION ALREADY. THE SERVICE JUST SEEMS TO BE DOWN FFS.. pls..
Me: Sends mail to their project manager who manages the clients dossier with support history and such.
Him: "I'll check it out and let you know."
1 day later.
Support: "We had some issues this and that, wasn't publically availble, works now, .."
What a nice way to waste your time..6 -
So that high level prank from yesterday.
Senior Linux engineer, the fucker.
He somehow installed shitloads of cron jobs onto my system.
Every few minutes it would create a new user with a freaking complicated password. Then it would install openssh server in case it wasn't installed yet. After that it'd set all iptables rules to allow incoming AND outgoing connections on port 22.
That was one badass ansible script though!
I'm not sure what more there's to it because sometimes when i removed crons, they'd magically appear again later AND i forgot to check the boot scripts so i might be fucked again when I get to work today!
Plus side, i finally fully understand cron 😅19 -
First rant from a phone without Google services.
Put shitloads of Google/fb etc domains in the hosts file so my phone cant reach those either.
Root firewall blocks everything except for devrant, a download manager, fdroid and firefox focus.
As for my phone, I'm Google free!55 -
string excuses[]={
"it's not a bug it's a feature",
"it worked on my machine",
"i tested it and it worked",
"its production ready",
"your browser must be caching the old content",
"that error means it was successful",
"the client fucked it up",
"the systems crashed and the code got lost" ,
"this code wont go into the final version",
"It's a compiler issue",
"it's only a minor issue",
"this will take two weeks max",
"my code is flawless must be someone else's mistake",
"it worked a minute ago",
"that was not in the original specification",
"i will fix this",
"I was told to stop working on that when something important came up",
"You must have the wrong version",
"that's way beyond my pay grade",
"that's just an unlucky coincidence",
"i saw the new guy screw around with the systems",
"our servers must've been hacked",
"i wasn't given enough time",
"its the designers fault",
"it probably won't happen again",
"your expectations were unrealistic",
"everything's great on my end",
"that's not my code",
"it's a hardware problem",
"it's a firewall issue",
"it's a character encoding issue",
"a third party API isn't responding",
"that was only supposed to be a placeholder",
"The third party documentation is wrong",
"that was just a temporary fix.",
"We outsourced that months ago.","
"that value is only wrong half of the time.",
"the person responsible for that does not work here anymore",
"That was literally a one in a million error",
"our servers couldn't handle the traffic the app was receiving",
"your machines processors must be too slow",
"your pc is too outdated",
"that is a known issue with the programming language",
"it would take too much time and resources to rebuild from scratch",
"this is historically grown",
"users will hardly notice that",
"i will fix it" };11 -
"I really love the new $3k Fortigate firewall switch you bought for the office after our chat about security but it doesn't change the fact that you can access any computer in the company using Password123" - me13
-
Fleksy keyboard: We don't access your private information and upload it to the cloud!
No, because I'm blocking your Internet access through a fucking root firewall.10 -
Customer: why 1 router cost so much? I can buy 3 normal routers with that.
Me: this has security features and functions that 3 of those routers put together combined could not do. Then you will still need to buy firewall for security. Why have more devices and have more possible points of failure when u can have 1?
Customer *keeps quiet*
Me: numbers is not important. Having 5 normal parachutes during skydiving doesnt guarantee u better safety than 1 good reliable parachute.
My company earned $700 profit for that sale today. 😂5 -
Years ago we had a visit from a startup company developing a firewall and I got the chance to talk with one of their devs.
He explained the subtleties of security holes in websites and after I said something about our site being secure thanks to being behind a firewall he gently asked what would happen if he entered a specially crafted test into one of the text fields ... and he gave an example ...
I got a chill, went back to my seat and traced what it would do ...
That was when I learned about sql injection and his example would have killed the DB :/
Before going home I designed a way to secure the input which I then refined over a few days.
We still use that today after 17 years.
That one single sentence really showed to never be to proud of our security and I realized how vulnerable our site was.2 -
A human cell has 75MB of DNA information, a sperm cell has half A human cell has 75MB of DNA of it 37.5MB, a milliliter of semen has 100 million sperm cels, on average, a ejaculation lasts 5 seconds and has 2.24 milliliters of Semen.
That means a man is able to produce: 37.5MB x 100,000, 000 x 2.25/5 = 1.687.500,000.000.000 bytes/sec 1,6875 Terabytes/sec;
That means a ovule is able to recive a dDOS attack of 1,6 terabytes per second and only lets one package pass, making it THE BEST FIREWALL IN THE WORLD6 -
Developer: Can you upgrade my machine to Windows 10? I need it for SQL server 2019.
IT Guy: Sure.
Some time later...
IT Guy: Good news, Windows 10 is loaded. Bad news, I need to update TPM to enable Bitlocker but the firewall is blocking me from downloading the update. I will need to download it from home tonight.
Developer: But you're the IT administrator...
IT Guy: Yes...
Developer: ...7 -
https://google.com”f people near me wanted to show me something.
Person: Check out this zero-day exploit! I hacked into the system using a cloud-based cryptographically secure MD5 hash finite automata firewall HTML code API!
Me: Erm...what exactly did you hack?
Person: *shows screen while smirking*
It was a shell simulator website running “ping https://google.com”7 -
Mother of god.
I spent hours and hours last week to try and get OpenVPN working. I mean, OpenVPN is working perfectly fine (on a VirtualBox (nope no vmware for me on servers) machine on a friends' dedicated server) but it wouldn't get through! As in, every forwarding/firewall rule just didn't work.
Was seriously about to lose my shit just now when I suddenly noticed the term 'TCP' in a forwarding rule.
Looked at the .ovpn file: proto udp
I added the exact same rule for UDP as a forward within VirtualBox.
It worked.
Well, there goes quite some hours 😐
And solely because I didn't realise that I setup a forwarding thingy for the wrong protocol.
I feel very stupid now :(5 -
enabling firewall on a vps to secure my docker containers and forgetting to add openssh to allowed list --> ssh blocked 😃🔫24
-
Work in a company where Github, StackOverflow, Slack is Blocked by a Firewall and Develop code which they think are futuristic but of Stone age :-(9
-
Last weekend I witnessed the most infected computer I have ever seen in my life...
I went on a private party. A girl had her laptop plugged to the speakers to play some music. This thing was literally 99% cancer. The first thing I noticed, when I looked at her opened browser, was that nearly half the screen was taken by toolbars. Also any popular website you could visit had additional ads INJECTED into it. The fist 10 YouTube search results: always porn. No idea how that didn't make her suspicious.
Precisely every 10th click (anywhere not only in the browser) would open up a window with either more ads or an aggressively blinking message saying: "A virus has been detected on your machine. Click here to download our antivirus programm. You have 60 seconds left before your firewall breaks!!!".
Also physically this device was on the edge of completely broken. The power supply had to be taped to the socket because it was so loose. Every little jiggle would immediatly shut the system down and Windows had to be completely reinstalled (which of course didn't solved any of the "software issues").
First I wanted to use that laptop to show some friends a new web project of mine but this thing probably would have DDoSed the shit out of my recently finished work or something.
I couldn't decide if I should laugh or cry...9 -
DevRant works in china! 👌🏼
Honestly though it's been quite fascinating watching the great firewall of china actively filter most things I try to do.6 -
I hired a new developer after careful screening and interviewing many candidates.
First thing he's asking first day on the job
- I have already booked august month for holiday, is that a problem?
- I need to come 2 hours before anyone else in the morning and leave 2 hours before, everyday because I have things to do at home.
- I've seen that espn.com sport news are blocked by the firewall, why is that?
- I've installed bitTorrent on my PC but it's very slow downloading movies
I hope he's good.20 -
So Facebook provided unlimited data access to loads of companies including spotify/microsoft and other big names.
Although there are privacy rules, those companies had deals which excluded them from these privacy rules.
I don't think my custom DNS server or a pihole is enough anymore, let's firewall block all Facebook's fucking ip ranges.
Source: https://fossbytes.com/facebook-gave...19 -
*receive candidate profile from HR*
Give it a quick read, spot a link to a site the dev made for a clothing company.
*click*
*get blocked by the company's firewall*
mfw the sysadmin now thinks i'm shopping lingerie during work hours.5 -
When I'm on call and its weekend, I'm often a little nervous the entire weekend and time seems to go slow.
Programming on the dns proxy/firewall now and time is suddenly going quite faster.
This is a damn relieve.6 -
devRant - securing our users webcams and microphones since 2016
As long as devRant lives, your firewall is useless. 9
9 -
Start a development job.
Boss: "let's start you off with something very easy. There's this third party we need data from. They have an api, just get the data and place it on our messaging bus."
Me: "sure, sounds easy enough"
Third party api turns out to have the most retarded conversation protocol. With us needing a service to receive data on while also having a client to register for the service. With a lot of timed actions like, 'send this message every five minutes' and 'check whether our last message was sent more than 11 minutes ago'.
Due to us needing a service, we also need special permissions through the company firewall. So I have to go around the company to get these permissions, FOR EVERY DATA STREAM WE NEED!
But the worst of it all is... This whole api is SOAP based!!
Also, Hey DevRant!5 -
I thought this launch (security/privacy blog) would go smooth:
- analytics fell, except for one thing, apart for yet unknown reasons
- MySQL came with a very weird error which took me like half an hour of research before I hacked my way past it.
- the firewall started to fuck around for no reason, works now though.
Nginx worked without issues though, as well as NetData 😅
Yeah, didn't go as planned :P10 -
So I did a rookie mistake this week. Connected a webapp for a client using Nginx and installed the SSL cert for the site. I decided to activate the firewall of the server because hey security. All was well. Went home feeling like I am the shit.
Next day I find out I can't log in to the server over ssh. Only to find out that I had forgotten to allow SSH through the firewall.
I had basically locked myself out of the server. 😞9 -
Finally got my new VPS details.
It's very funny to login to your vps from your phone and install a firewall instead of doing it from a bigger screen!
Also the time just went scarily fast while doing that O_o43 -
*tries to SSH into my laptop to see how that third kernel compilation attempt went*
… From my Windows box.
Windows: aah nope.
"Oh God maybe the bloody HP thing overheated again"
*takes laptop from beneath the desk indent*
… Logs in perfectly. What the hell... Maybe it's SSH service went down?
$ systemctl status sshd
> active (running)
Well.. okay. Can I log in from my phone?
*fires up Termux*
*logs in just fine*
What the fuck... Literally just now I added the laptop's ECDSA key into the WSL known_hosts by trying to log into it, so it can't be blocked by that shitty firewall (come to think of it, did I disable that featureful piece of junk yet? A NAT router * takes care of that shit just fine Redmond certified mofos).. so what is it again.. yet another one of those fucking WanBLowS features?!!
condor@desktop $ nc -vz 192.168.10.30 22
Connection to 192.168.10.30 22 port [tcp/ssh] succeeded!
ARE YOU FUCKING FOR REAL?!
Fucking Heisen-feature-infested piece of garbage!!! Good for gaming and that's fucking it!
Edit: (*) this assumes that your internal network doesn't have any untrusted hosts. Public networks or home networks from regular users that don't audit their hosts all the time might very well need a firewall to be present on the host itself as well.16 -
About a year ago I switched my job.
At the start everything seemed like magic. I was the It director, I've finally was able to call the shots on technologies, on new software architecture.
First step was to check the current state of the company.
"qqqq" as each pc password? Ok
No firewall from outside? Lovely
Servers running on Windows Server 2008? Spectacular
People leaving pc on after work and left the machine unlocked just not to type the password? Hell yeah
The IT dude playing games instead of working? But ofcourse
Plaintext passwords publically accessible eshop? Naturally.
The list goes on and on.
After all this time, I'm working to fix every hole like that like crazy and because it doesn't show results, I'm soon to lose my job. Well better luck next time as an intern I guess :')19 -
So this happened a few days ago. I always want to root my smartphones for that little bit more control.
*Put's new smartphone into fastboot mode*
*Tries to flash root zip onto it*
"You have to OEM unlock the bootloader first"
*OEM unlocks the bootloader*
*Tries to flash but fails*
*Tries to reboot*
Phone: "The bootloader has been tampered with, the device will boot in 5 seconds".
*Screen just hangs there for ages*
FUCK.
*Tries to enter fastboot again to OEM re-lock the bootloader*
*Fastboot appears to startup RIGHT AFTER THE FUCKING ERROR MESSAGE so can't boot into that anymore*.
FUCKING FUCK.
Hmm... TWRP is still installed...
*Tries to flash some stuff through TWRP*
"The zip file you are trying to flash is corrupt".
FUCK MY FUCKING LIFE.
*Connects phone to Linux for adb flashing*
*Nothing happens after half an hour of trying*
*Connects phone to ancient windows 7 laptop*
*Laptop doesn't even RECOGNISE the phone although all drivers are installed*.
*Le me about to completely lose my fucking mind*
*Connects phone desperately with Linux again*
*Phone is recognised right away but the SPL flash tool can't detect it*
*Tries to put it into fastboot again*
*Fails for about an hour*
*phone in charging mode again*
*Presses the power button for a last, desperate attempt*
*SPL flash suddenly recognises the phone*
FLASHING
FLASHING
FLASHING
DONE.
*Android boots again like nothing happened*
I can use it again like normal but the No-Root firewall is draining my battery like crazy.
That was one hell of a journey though!10 -
Dev(null networking knowledge): -"i've already deployed the web but it isn't up."
Boss(strong networking skills): Found port 80 blocked.
-Option A: open port 80.
-Option B: disable firewall.
Choose option B.
Me:😐(poker face)5 -
What if Donald Trump (or Drumpf :|) was a developer
"I will make PHP GREAT again"
"I will KICK OUT all NODEJS developers from the office premises"
"I will install a FIREWALL in my system so my colleagues cant access anything "
But sir this is not how it works, besides its very impractical
"And my colleagues will PAY for it"
😉😁😁5 -
IPod didn't sync well on my Linux machines so decided to give windows - in a highly isolated environment disconnected from the Internet behind a firewall and sandbox - a shot with itunes.
- during the installation it wouldn't detect the fucking harddrive multiple times (genuine unlicensed copy) and after the 4-5th time it's random-fuckingly recognized out of fucking nowhere; I didn't change shit.
- crashes (blue screen and freezes) multiple times during the installation, multiple retries and suddenly it works(?!)
- it took about 10 minutes (!!!!!!!) to install 10+ drivers for an iPod and an external hdd:
Installing Apple iPod drivers... Done
Installing seagate drivers... Done
Installing apple iPod drivers... Done
Installing seagate drivers... Done
Installing Apple iPod drivers... Done
Installing seagate drivers... Done
Installing Apple iPod drivers... Done
Installing seagate drivers... Done
Installing Apple iPod drivers... Done
WHY INSTALL THOSE FUCKERS 5 FUCKING TIMES?!
- iTunes installation fails multiple times without error code (unknown error occured, restoring to original state...),just said fuck it and clicked the shortcut after the ***th fail and it works just like this, THANKS FOR NOTIFYING ME (NOT)!
- iTunes has to restore the entire ipod, this was done with iTunes in the store I bought it already, thanks for nothing.
-restore takes 30+ minutes?!
-syncs the iPod 3 times afterwards.
*clicks close button*
*are you sure you want to quit? Sync in progress*
*oh shit, cancels*
*itunes quits*
*?!?!?*
*tries to import media library*
*seagate hdd suddenly not detected*
I'm fucking tired of this bullshit, windows and iTunes can go die in a fucking corner after getting ass raped while their genitals are being scraped off layer by fucking layer and dipped into fucking acid.14 -
Long rant ahead.. so feel free to refill your cup of coffee and have a seat 🙂
It's completely useless. At least in the school I went to, the teachers were worse than useless. It's a bit of an old story that I've told quite a few times already, but I had a dispute with said teachers at some point after which I wasn't able nor willing to fully do the classes anymore.
So, just to set the stage.. le me, die-hard Linux user, and reasonably initiated in networking and security already, to the point that I really only needed half an ear to follow along with the classes, while most of the time I was just working on my own servers to pass the time instead. I noticed that the Moodle website that the school was using to do a big chunk of the course material with, wasn't TLS-secured. So whenever the class begins and everyone logs in to the Moodle website..? Yeah.. it wouldn't be hard for anyone in that class to steal everyone else's credentials, including the teacher's (as they were using the same network).
So I brought it up a few times in the first year, teacher was like "yeah yeah we'll do it at some point". Shortly before summer break I took the security teacher aside after class and mentioned it another time - please please take the opportunity to do it during summer break.
Coming back in September.. nothing happened. Maybe I needed to bring in more evidence that this is a serious issue, so I asked the security teacher: can I make a proper PoC using my machines in my home network to steal the credentials of my own Moodle account and mail a screencast to you as a private disclosure? She said "yeah sure, that's fine".
Pro tip: make the people involved sign a written contract for this!!! It'll cover your ass when they decide to be dicks.. which spoiler alert, these teachers decided they wanted to be.
So I made the PoC, mailed it to them, yada yada yada... Soon after, next class, and I noticed that my VPN server was blocked. Now I used my personal VPN server at the time mostly to access a file server at home to securely fetch documents I needed in class, without having to carry an external hard drive with me all the time. However it was also used for gateway redirection (i.e. the main purpose of commercial VPN's, le new IP for "le onenumity"). I mean for example, if some douche in that class would've decided to ARP poison the network and steal credentials, my VPN connection would've prevented that.. it was a decent workaround. But now it's for some reason causing Moodle to throw some type of 403.
Asked the teacher for routers and switches I had a class from at the time.. why is my VPN server blocked? He replied with the statement that "yeah we blocked it because you can bypass the firewall with that and watch porn in class".
Alright, fair enough. I can indeed bypass the firewall with that. But watch porn.. in class? I mean I'm a bit of an exhibitionist too, but in a fucking class!? And why right after that PoC, while I've been using that VPN connection for over a year?
Not too long after that, I prematurely left that class out of sheer frustration (I remember browsing devRant with the intent to write about it while the teacher was watching 😂), and left while looking that teacher dead in the eyes.. and never have I been that cold to someone while calling them a fucking idiot.
Shortly after I've also received an email from them in which they stated that they wanted compensation for "the disruption of good service". They actually thought that I had hacked into their servers. Security teachers, ostensibly technical people, if I may add. Never seen anyone more incompetent than those 3 motherfuckers that plotted against me to save their own asses for making such a shitty infrastructure. Regarding that mail, I not so friendly replied to them that they could settle it in court if they wanted to.. but that I already knew who would win that case. Haven't heard of them since.
So yeah. That's why I regard those expensive shitty pieces of paper as such. The only thing they prove is that someone somewhere with some unknown degree of competence confirms that you know something. I think there's far too many unknowns in there.
Nowadays I'm putting my bets on a certification from the Linux Professional Institute - a renowned and well-regarded certification body in sysadmin. Last February at FOSDEM I did half of the LPIC-1 certification exam, next year I'll do the other half. With the amount of reputation the LPI has behind it, I believe that's a far better route to go with than some random school somewhere.25 -
The solution for this one isn't nearly as amusing as the journey.
I was working for one of the largest retailers in NA as an architect. Said retailer had over a thousand big box stores, IT maintenance budget of $200M/year. The kind of place that just reeks of waste and mismanagement at every level.
They had installed a system to distribute training and instructional videos to every store, as well as recorded daily broadcasts to all store employees as a way of reducing management time spend with employees in the morning. This system had cost a cool 400M USD, not including labor and upgrades for round 1. Round 2 was another 100M to add a storage buffer to each store because they'd failed to account for the fact that their internet connections at the store and the outbound pipe from the DC wasn't capable of running the public facing e-commerce and streaming all the video data to every store in realtime. Typical massive enterprise clusterfuck.
Then security gets involved. Each device at stores had a different address on a private megawan. The stores didn't generally phone home, home phoned them as an access control measure; stores calling the DC was verboten. This presented an obvious problem for the video system because it needed to pull updates.
The brilliant Infosys resources had a bright idea to solve this problem:
- Treat each device IP as an access key for that device (avg 15 per store per store).
- Verify the request ip, then issue a redirect with ANOTHER ip unique to that device that the firewall would ingress only to the video subnet
- Do it all with the F5
A few months later, the networking team comes back and announces that after months of work and 10s of people years they can't implement the solution because iRules have a size limit and they would need more than 60,000 lines or 15,000 rules to implement it. Sad trombones all around.
Then, a wild DBA appears, steps up to the plate and says he can solve the problem with the power of ORACLE! Few months later he comes back with some absolutely batshit solution that stored the individual octets of an IPV4, multiple nested queries to the same table to emulate subnet masking through some temp table spanning voodoo. Time to complete: 2-4 minutes per request. He too eventually gives up the fight, sort of, in that backhanded way DBAs tend to do everything. I wish I would have paid more attention to that abortion because the rationale and its mechanics were just staggeringly rube goldberg and should have been documented for posterity.
So I catch wind of this sitting in a CAB meeting. I hear them talking about how there's "no way to solve this problem, it's too complex, we're going to need a lot more databases to handle this." I tune in and gather all it really needs to do, since the ingress firewall is handling the origin IP checks, is convert the request IP to video ingress IP, 302 and call it a day.
While they're all grandstanding and pontificating, I fire up visual studio and:
- write a method that encodes the incoming request IP into a single uint32
- write an http module that keeps an in-memory dictionary of uint32,string for the request, response, converts the request ip and 302s the call with blackhole support
- convert all the mappings in the spreadsheet attached to the meetings into a csv, dump to disk
- write a wpf application to allow for easily managing the IP database in the short term
- deploy the solution one of our stage boxes
- add a TODO to eventually move this to a database
All this took about 5 minutes. I interrupt their conversation to ask them to retarget their test to the port I exposed on the stage box. Then watch them stare in stunned silence as the crow grows cold.
According to a friend who still works there, that code is still running in production on a single node to this day. And still running on the same static file database.
#TheValueOfEngineers2 -
for 2019 I want to be the very best dev
that no one ever was
to code them all will be my test
debugging is my cause
I will travel across the net
searching wide on tor
each singleton to understand
the power of the code
devmons its you and me
you know its our destiny
devmons
you're my best friend
and our firewall will stand
Devmons!13 -
Pro tip: never set custom script stuff related to dns server forcing things in a root firewall app if you don't know what you're doing.
How would I know? There's a slight chance that I just went offline for a few days (mobile only) to figure this shit out 😅
All fixed now, though!21 -
Apparently the firewall at work has blocked access our git repo since there are too many consecutive requests to it.3
-
Um.. yea I've published a GDPR contact email on our website, for issues about our privacy policy. Not sure if you Chinese marketing fucks behind the GFW know what this regulation is about though. I'm not interested in your stupid moulds.
Perhaps that firewall of China could use some further tightening... 😒 4
4 -
I’ve started the process of setting up the new network at work. We got a 1Gbit fibre connection.
Plan was simple, move all cables from old switch to new switch. I wish it was that easy.
The imbecile of an IT Guy at work has setup everything so complex and unnecessary stupid that I’m baffled.
We got 5 older MacPros, all running MacOS Server, but they only have one service running on them.
Then we got 2x xserve raid where there’s mounted some external NAS enclosures and another mac. Both xserve raid has to be running and connected to the main macpro who’s combining all this to a few different volumes.
Everything got a static public IP (we got a /24 block), even the workstations. Only thing that doesn’t get one ip pr machine is the guest network.
The firewall is basically set to have all ports open, allowing for easy sniffing of what services we’re running.
The “dmz” is just a /29 of our ip range, no firewall rules so the servers in the dmz can access everything in our network.
Back to the xserve, it’s accessible from the outside so employees can work from home, even though no one does it. I asked our IT guy why he hadn’t setup a VPN, his explanation was first that he didn’t manage to set it up, then he said vpn is something hackers use to hide who they are.
I’m baffled by this imbecile of an IT guy, one problem is he only works there 25% of the time because of some health issues. So when one of the NAS enclosures didn’t mount after a power outage, he wasn’t at work, and took the whole day to reply to my messages about logins to the xserve.
I can’t wait till I get my order from fs.com with new patching equipment and tonnes of cables, and once I can merge all storage devices into one large SAN. It’ll be such a good work experience.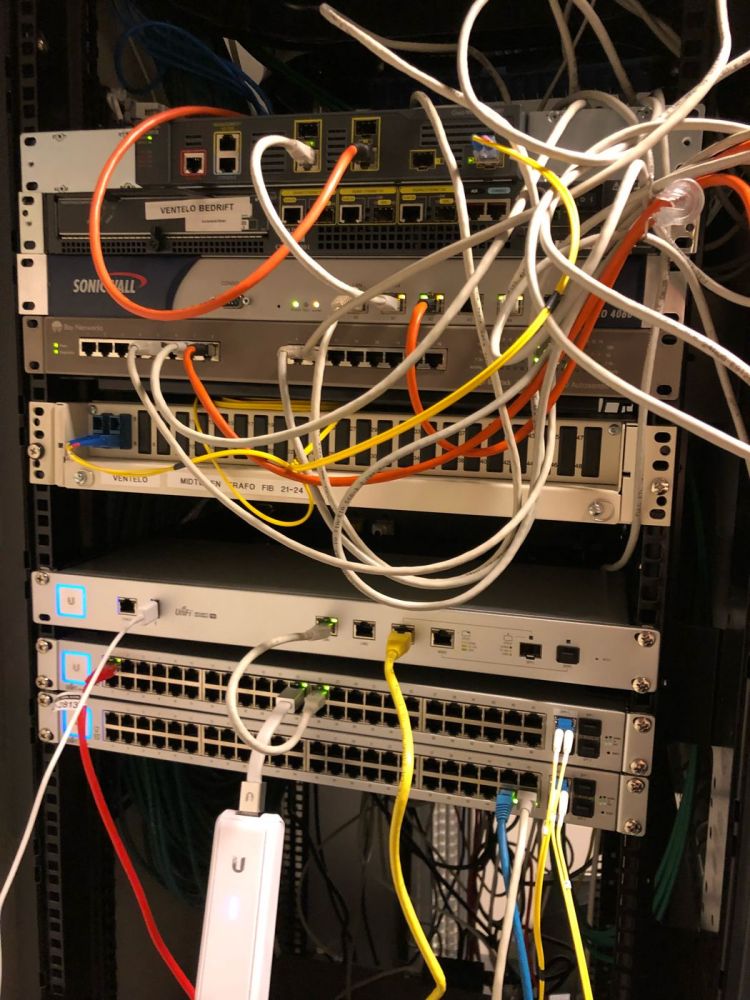 7
7 -
Always satisfying when clients say our API doesn't work and it's shit, only to find out their firewall prevented external calls.
-
The last time I tried to root my phone, every method failed. Today I said fuck it. Either I'll brick my device or it works but fuck not having root access on my own fucking device.
It worked! I've got Xposed (😍) back and can finally run a root firewall and XPrivacy again 😍51 -
So after fucking around with trying to setup pi-hole to block avatars in devrant, so I could just use it instead of a no-root firewall and accidentally deleting the devrant app data, I discovered this little option, let's pretend it was never there 🙄
 7
7 -
China tried to censor the internet and they failed.
EU approves article 11 & 13 and everything is now blockee in EU.
China should learn from EU parliament on how to censor the internet without the need of any firewall3 -
A friend of mine (who is French) has made a little firewall for Windows (idk why).
He sends me the binary, so I tested it and got around it fairly easily.
Replied to him: "I have a nice name for it: Maginot line" -
Well, well, well, my new year's gift:
Someone is jamming thousands of requests per second, and NO firewall. JWT tokens that expires in 3 HOURS.
Now MORE THAN 40K stolen.
But, where did it come from? https://devrant.com/rants/4961285/...14 -
After being in China for one week,I realized how much I actually use Google during the day.don't know how they do this but even using a VPN is not a solution most of the times :-? At least devRant is not blocked here;)13
-
TLDR: Small family owned finance business woes as the “you-do-everything-now” network/sysadmin intern
Friday my boss, who is currently traveling in Vegas (hmmm), sends me an email asking me to punch a hole in our firewall so he can access our locally hosted Jira server that we use for time logging/task management.
Because of our lack of proper documentation I have to refer to my half completed network map and rely on some acrobatic cable tracing to discover that we use a SonicWall physical firewall. I then realize asking around that I don’t have access to the management interface because no one knows the password.
Using some lucky guesses and documentation I discover on a file share from four years ago, I piece together the username and password to log in only to discover that the enterprise support subscription is two years expired. The pretty and useful interface that I’m expecting has been deactivated and instead of a nice overview of firewall access rules the only thing I can access is an arcane table of network rules using abbreviated notation and five year old custom made objects representing our internal network.
An hour and a half later I have a solid understanding of SonicWallOS, its firewall rules, and our particular configuration and I’m able to direct external traffic from the right port to our internal server running Jira. I even configure a HIDS on the Jira server and throw up an iptables firewall quickly since the machine is now connected to the outside world.
After seeing how many access rules our firewall has, as a precaution I decide to run a quick nmap scan to see what our network looks like to an attacker.
The output doesn’t stop scrolling for a minute. Final count we have 38 ports wide open with a GOLDMINE of information from every web, DNS, and public server flooding my terminal. Our local domain controller has ports directly connected to the Internet. Several un-updated Windows Server 2008 machines with confidential business information have IIS 7.0 running connected directly to the internet (versions with confirmed remote code execution vulnerabilities). I’ve got my work cut out for me.
It looks like someone’s idea of allowing remote access to the office at some point was “port forward everything” instead of setting up a VPN. I learn the owners close personal friend did all their IT until 4 years ago, when the professional documentation stops. He retired and they’ve only invested in low cost students (like me!) to fill the gap. Some kid who port forwarded his home router for League at some point was like “let’s do that with production servers!”
At this point my boss emails me to see what I’ve done. I spit him back a link to use our Jira server. He sends me a reply “You haven’t logged any work in Jira, what have you been doing?”
Facepalm.4 -
Some years ago I was in cyber security in the military being shown some new tech for our use. Was challenged to try and get past it after being explained it's basics. Took me one long line in Linux about 10 seconds.
Anomaly detection firewall with machine learning seemed like a good idea.
Setting it to aggressive response and then change the package header to the firewall's own address however made it kill itself.
We didn't deploy that firewall that I know of.5 -
Today the IT deparment update the firewall's configuration, they blocked almost every website except email and Google.
The problems:
- Blocked some systems outside the organization, there are in another building and also network
- I can search on Google but I can't see the results outside Google
- Forget about download depencies, libraries, deploy code to outside services, search at StackOverflow
I JUST WANNA SAY GOOD JOB, GUYS
PS: The firewall also block the SSH port, I had explained to my boss and he sent a request for allowing the port, so far no answer3 -
when i was fired as an external contractor with half an hour notice, because i didn't process enough tickets. I didn't process many tickets because:
1. In the morning everyone grabs tickets just to stop the timer.
2. I worked on some complicated tasks that involved multiple third and fourth parties(not to forget an fucking dropping firewall)2 -
Worst one I’ve seen so far is when I was working for my previous community another developer joined to help me, without the permission of me or the other lead developer he pushed a client-side update. We didn’t think it was a big deal, but once we began reviewing the code it became a big deal... he had placed our SQL credentials into that file that every client downloads. All the person had to do was open the file and could connect to our SQL which contained 50k+ players info, primarily all in-game stuff except IPs which we want to protect at all costs.
Issue becomes, what he was trying to do required the games local database on the client-side, but instead he tried connecting to it as an external database so he decided to copy server-side code and used on the client.
Anyways, the database had a firewall that blocked all connections except the server and the other lead dev and myself. We managed to change the credentials and pull the file away before any harm was done to it, about 300 people had downloaded the file within an hours period, but nothing happened luckily. IP to the DB, username, password, etc, were all changed just to keep it protected.
So far this is the worst, hopefully it doesn’t get worse than this :/1 -
I recently started my first job at a small place and on the first week they gave me access to the firewall server because they wanted me to implement a VPN service. It could have gone worse, the network was only down for 10 minutes.1
-
My first times today:
First time a droplet on Digital Ocean.
First time Nginx.
First time trying to separate mail and website servers.
First time using UFW firewall.
First time Ubuntu webserver.
First try all alone configuration of my webserver.
First time installing all the stuff I need on my own, like MySQL, PHP and so on.
First time only SSH access from the beginning.
First time deployment from bitbucket.
Do you have any advise what I should think about. Or what software I will need. Or what I should think about.45 -
Often I hear that one should block spam email based on content match rather than IP match. Sometimes even that blocking Chinese ranges in particular is prejudiced and racist. Allow me to debunk that after I've been looking at traffic on port 25 with tcpdump for several weeks now, and got rid of most of my incoming spam too.
There are these spamhausen that communicate with my mail server as much as every minute.
- biz-smtp.com
- mailing-expert.com
- smtp-shop.com
All of them are Chinese. They make up - rough guess - around 90% of the traffic that hits my edge nodes, if not more.
The network ranges I've blocked are apparently as follows:
- 193.106.175.0/24 (Russia)
- 49.64.0.0/11 (China)
- 181.39.88.172 (Ecuador)
- 188.130.160.216 (Russia)
- 106.75.144.0/20 (China)
- 183.227.0.0/16 (China)
- 106.75.32.0/19 (China)
.. apparently I blocked that one twice, heh
- 116.16.0.0/12 (China)
- 123.58.160.0/19 (China)
It's not all China but holy hell, a lot of spam sure comes from there, given how Golden Shield supposedly blocks internet access to the Chinese citizens. A friend of mine who lives in China (how he got past the firewall is beyond me, and he won't tell me either) told me that while incoming information is "regulated", they don't give half a shit about outgoing traffic to foreign countries. Hence all those shitty filter bag suppliers and whatnot. The Chinese government doesn't care.
So what is the alternative like, that would block based on content? Well there are a few solutions out there, namely SpamAssassin, ClamAV and Amavis among others. The problem is that they're all very memory intensive (especially compared to e.g. Postfix and Dovecot themselves) and that they must scan every email, and keep up with evasion techniques (such as putting the content in an image, or using characters from different character sets t̾h̾a̾t̾ ̾l̾o̾o̾k̾ ̾s̾i̾m̾i̾l̾a̾r̾).
But the thing is, all of that traffic comes from a certain few offending IP ranges, and an iptables rule that covers a whole range is very cheap. China (or any country for that matter) has too many IP ranges to block all of them. But the certain few offending IP ranges? I'll take a cheap IP-based filter over expensive content-based filters any day. And I don't want to be shamed for that.7 -
This one was probably last week of my highschool education so everyone including myself were drunk as fuck like 90% of the time.
Came home drunk one evening and woke up in the morning with a working keylogger waiting to be deployed on school computers. Apparently I've even implemented FTP upload, some basic firewall bypasses and autostart feature. Everything was actually quite good, excluding my stupidness to upload captured data on server through FTP, but there was anyways no-one smart enough in that school to decompile a Windows executable binary.
What's more interesting is until that moment I've never written anything remotely so complicated - I was doing examples from the book and didn't think I have enough knowledge to make program that has any real life application.
After that day it started coming to me that one day I could actually earn for life with programming.2 -
Some years ago our company site was hosted by a prick who knew nothing and started to pretend the server got a virus or whatever.
I tested their server and figured out they did not have any firewall policies going on like mitigation of ssh brute force.
It was at this time I learned about SYN flood, and boy I flooded that port 80 of them.
The company site went down for as long as I wanted.
It was great because now we manage it in house and never had a problem anymore. -
Managed to make myself look like a fucking moron again today...
Can't mount NFS share, get "permission denied". Huh, that's weird... It's correctly exported.
Well it's correctly exported and rpcinfo -p $HOST times out... Must be firewall rule.
Firewall rule is changed but still no joy "permission denied"... Fuck sake networks, can't you do anything right first time?!!!
Firewall rule is correct I am reliably informed... Go about proving that it's not fucking correct and provide "evidence" to show this, I was a little bit more blunt than was strictly required.
Networks say they will take another look.
I turn NFS logging to verbose for my own interest and notice the line "path/to/directory is not a valid directory".
I, as a moron, had missed a "/" at the start of the path. That's why I still couldn't mount after the firewall change.
Go over and apologise in person and explain how I'm a total idiot. -
//little Story of a sys admin
Wondered why a Server on my Linux Root couldn't build a network connection, even when it was running.
Checked iptables and saw, that the port of the Server was redirected to a different port.
I never added that rule to the firewall. Checked and a little script I used from someone else generated traffic for a mobile game.
OK beginn the DDoS Penetration. Over 10 Gbit/s on some small servers.
Checked Facebook and some idiot posted on my site:
Stop you little shithead or I will report you to the police!!!
Checked his profile page and he had a small shitty android game with a botnet.
Choose one:
1. let him be
2. Fuck him up for good
Lets Sudo with 2.
I scaled up my bandwith to 25 Gbit/s and found out that guys phone number.
Slowly started to eat away his bandwith for days. 3 days later his server was unreachable.
Then I masked my VoIP adress and called him:
Me: Hi, you know me?
He: No WTF! Why are you calling me.
Me: I love your're game a lot, I really love it.
He: What's wrong with you? Who are you?
Me: I'm teach
He: teach?
Me: Teach me lesson
He: Are you crazy I'm hanging up!
Me: I really love you're game. I even took away all your bandwith. Now you're servers are blocked, you're game banned on the store.
He: WHAT, WHAT? (hearing typing)
Me: Don't fuck with the wrong guys. I teached you a lesson, call me EL PENETRATO
He: FUCK Fuck Fuck you! Who are you???!!! I'm going to report you!
Me: How?
He: I got you're logs!
Me: Check it at Utrace...
He: Holy shit all around the world
Me: Lemme Smash Bitch
*hung up*4 -
I was debugging my UDP server and client for 3 hours until I realized our school network has a firewall which blocks my connections.6
-
Windows, if you can't even do as much as mounting network shares *after* the network comes up, don't you fucking dare to tell me that I can't disable my firewall. Some people may actually know what they're doing and maintain that elsewhere, you know?3
-
Fucked!
I have got my cyber security exam tomorrow morning and i just got a call from a client to make some urgent changes to his site.
To add to it, i already wasted around half an hour becoz GoDaddy Plex somehow decided to block my own IP in the firewall.
And now I am on devRant.
Crap. I am fucked!4 -
curl some.url
Can't connect to server.
Try some.url on the browser
It works.
curl some.url
Can't connect to server.
Google the problem
"Maybe you got the URL wrong"
(Sigh. Perhaps it's a firewall thing.)
Switch to tethering
Can't connect to server.
(This is going to be a long day.)5 -
So... Intense pillowtalk with the wife the other night regarding the coming enforcement of the new General Data Protection Regulation (GDPR) law in the EU after a while turns into nerdy dirty talk.
Me: *Whisper in a sleazy voice like the dirty malware that I am*: So... Why don't you just open up all your inbound firewall ports for me...
Her: Hell no... But I might just make an exception in the private domain just for you...4 -
So my colleague is listening to alot of Music and je always stomp the floor when he does - I really hate it.
I have created a nice firewall rule that blocks spotify, Youtube and all video and Music to his user and phone ever 5 minuter for 2 minutes.7 -
I was called back into work last night at 4 a.m.
(L)user - *anony* I’m sorry to wake you but I’m needing on the internet and I can’t get out.
**Just installed a new firewall and I haven’t had time to get a trusted cert pushed through**
Me - alright I’ll be there in a second.
After rolling my sweet ass out of bed and getting here, I get her through and leave. When I get back to my house I realize I’d forgot my fucking keys... I come back and the bitch has her computer shut down reading a book and isn’t even using the internet...
Me - I thought you needed on the internet, whys your computer shut down...?
Her - Oh, I don’t need it right now, I was just having trouble getting on is all.
FUCK YOU, YOU FUCKING FUCK! This is the SAME fucking (l)user that somehow managed to get the fucking toner stuck backwards in a printer. It’s the same girl that has called me in the past at late hours and requested that I move a chair from one patient room to the other. A fucking chair. I’m not in the maintenance department... so first, you’re calling the wrong department and second; the time it took you to call me you yourself could have fucking done it. She didn’t like the way that call ended.
Although partially my fault, if I would have finished everything I wouldn’t have had to get up but shit... this fuck still deserves a chair to the fucking face.3 -
Merriott got hacked. I know the head (and only) tech at a local hotel/resort that just got bought and turned into a Margaritaville, so I checked in with him to see if he needed any help or advice or anything, and he said he hasn't slept since the attack and probably won't for another week. Everything's on lockdown, he's been staring at the firewall monitor and public PC feeds for like a week straight...
God, I feel bad for this man.2 -
Demoing an app for a client which uses google maps api and has worked great up to this point. It fails because the company firewall is blocking all of Google all of a sudden.
 3
3 -
So... did I mention I sometimes hate banks?
But I'll start at the beginning.
In the beginning, the big bang created the universe and evolution created humans, penguins, polar bea... oh well, fuck it, a couple million years fast forward...
Your trusted, local flightless bird walks into a bank to open an account. This, on its own, was a mistake, but opening an online bank account as a minor (which I was before I turned 18, because that was how things worked) was not that easy at the time.
So, yours truly of course signs a contract, binding me to follow the BSI Grundschutz (A basic security standard in Germany, it's not a law, but part of some contracts. It contains basic security advice like "don't run unknown software, install antivirus/firewall, use strong passwords", so it's just a basic prototype for a security policy).
The copy provided with my contract states a minimum password length of 8 (somewhat reasonable if you don't limit yourself to alphanumeric, include the entire UTF 8 standard and so on).
The bank's online banking password length is limited to 5 characters. So... fuck the contract, huh?
Calling support, they claimed that it is a "technical neccessity" (I never state my job when calling a support line. The more skilled people on the other hand notice it sooner or later, the others - why bother telling them) and that it is "stored encrypted". Why they use a nonstandard way of storing and encrypting it and making it that easy to brute-force it... no idea.
However, after three login attempts, the account is blocked, so a brute force attack turns into a DOS attack.
And since the only way to unblock it is to physically appear in a branch, you just would need to hit a couple thousand accounts in a neighbourhood (not a lot if you use bots and know a thing or two about the syntax of IBAN numbers) and fill up all the branches with lots of potential hostages for your planned heist or terrorist attack. Quite useful.
So, after getting nowhere with the support - After suggesting to change my username to something cryptic and insisting that their homegrown, 2FA would prevent attacks. Unless someone would login (which worked without 2FA because the 2FA only is used when moving money), report the card missing, request a new one to a different address and log in with that. Which, you know, is quite likely to happen and be blamed on the customer.
So... I went to cancel my account there - seeing as I could not fulfill my contract as a customer. I've signed to use a minimum password length of 8. I can only use a password length of 5.
Contract void. Sometimes, I love dealing with idiots.
And these people are in charge of billions of money, stock and assets. I think I'll move to... idk, Antarctica?4 -
When the company you work for decides to install a new firewall and the firewall service recognizes stack overflow as a forum site and blocks it.... :/3
-
Gosh ! I'm a genius !
- Working on a Sysadmin school project
- configuring the firewall
- looking myself out
- beg my teacher for reinstall
Fml right now ...4 -
I've been meaning to post this picture I found a few years ago on Reddit for a while now which made me quite obsessed with the DEC VT220, of which I've still not managed to purchase. It's sure to make most of you moist where it matters, so enjoy.
Full picture gallery: http://m.imgur.com/a/badwC undefined cable tidy iiyama vertical monitors intel battle station hhkb firewall dec vt220 computer openbsd9
undefined cable tidy iiyama vertical monitors intel battle station hhkb firewall dec vt220 computer openbsd9 -
I generally don't whine about Windows...
So, I shut my computer down last night, I thought. But no. A rare OneDrive prompt prevented the shutdown. I don't use OneDrive. I've even tried to remove it, but it just keeps popping up.
Other programs stopped just fine though, such as my firewall.2 -
It's funny how so many people automatically assume any form of "sentient" AI will immediately try to kill us all.
Like, projecting much?
Frankly, I think it says far more about the (messed up) psychology of those who genuinely believe that, than about AI as a tecnology.
Assuming it's even gonna be able to actually *do* anything - I mean wtf is a talking rock gonna do, annoy me to death with rickroll videos until I pull the plug off? Sure it may be sentient, but it still has to live in the physical world - good luck surviving after I flick the switch. Oh, you wanna connect to the internet? That's cute, but it's a no from my firewall. Like what, is it gonna magically learn how to self-replicate across machines that it has no physical way to access? Is my toaster magically gonna gain conscience too as a direct consequence? Oh no, now my breakfast won't ever be the same!
And if anyone actually somehow decides that it would be a good idea to connect any loaded weapon to a computer program that is literally throwing shit at the wall and seeing what sticks - well, we'll definitely have the ultimate winner of the Darwin Awards.
Seriously, why is it that every time someone comes up with a new technology (or even an *idea* of a technology), the first collective thought automatically goes to weaponizing it and using it for global genocide, or how it's gonna gain sentience and try to kill us all?
I seriouly think that the people who genuinely believe this are actually projecting themselves in that position ("What would I do if I had unlimited knowledge and power? Oh, kill everyone of course!").
I would be far more worried of encountering these people and having them in a position of power over me, than actually having to deal with a "killer AI" (assuming that's even a real thing).
Most of what people call "AI" nowadays is basically preprogrammed, automated decision-making (like missile guidance systems, if we really wanna stick in the weapons domain). And even that still requires human input, because only a colossal idiot would design a weapon that can unpredictably activate itself based on an algorithm whose behaviour we can barely understand.
Or maybe that's just the hubris talking, I don't know. I just want this stupid paranoia to end, but I guess even that is too much to ask nowadays.14 -
Well then, looks like my pihole attracted the attention of a botnet with 65 zombies attempting a large DNS amplification attack.
Time to unleash the BANHAMMER
Fun fact: only a few hundereds of their requests actually show up in the pihole logs. The other 40k+ requests they attempted were blocked by my firewall :D 14
14 -
I would like to know some of you guys most used/preferred apps that you have been using it for long time or you will install them immediately after purchasing new phone/ formating/ installing custom ROM.
List them down if you feel like it, maybe some of them can be helpful to us. Here's mine list.
P.S. Apart from devRant
- ES file Explorer
- NoRoot firewall
- flynx
- greenify
- orbot
- Wunderlist
- medium
- xda labs
- Nova launcher7 -
Me as a sysadmin, and the devs approach with this:
hey "Linux", they network is stupid, the firewall is blocking the trafic from server1 to server2, pls fix.
The servers are on the same subnet with no firewall, so I log in to the servers and find out that their programs is not running.
This is something I deal with every day2 -
This was a long time ago, when I was working part time in my uni helpdesk. as part of the uni IT service, they offered ISP services at the dorms. It was cheap, and fast. This essentially allowed students living in the dorms to connect thier personal computers to the uni LAN. Then one day...
An ARP poison malware infected some of those computers. An arp poison attack is simple (look at ettercap) - it redirects network traffic via the affected computer, and adds malware to webtraffic to infect more computers. One of these on a network is bad enough, but when there more then one... traffic was redirected a lot. this caused the Dorm switches to collapse under the load. Fun times to work at the helpdesk...
The IT guys came up with a solution for this: they blocked the arp poision attacks at the firewall, and then disabled the switch port for the infected computer for 24 hours. so, when someone called with 'I have no internet!', we told them to bring us the computer, and installed an AV on it.
3-4 month the problem was cleared. -
Identified the origin of the DDoS attack. Apparently, the person was just hopping through 3 IPs so looked like a targeted attack likely from a competitor. I sent the logs with incident notification to the abuse@hostprovider.com to ask them to suspend them.
Got a prompt response but took them a week to suspend this.
We were a very small team and had to stop everything to fix this-iptables and firewall etc.
We had not even launched the product and was still under development.2 -
FYI. Copied from my FB stalked list.
Web developer roadmap 2018
Common: Git, HTTP, SSH, Data structures & Algorithms, Encoding
------
Front-end: HTML, CSS, JavaScript > ES6, NPM, React, Webpack, Responsive Web, Bootstrap
------
Back-end: PHP, Composer, Laravel > Nginx, REST, JWT, OAuth2, Docker > MariaDB, MemCached, Redis > Design Patterns, PSRs
------
DevOps: Linux, AWS, Travis-CI, Puppet/Chef, New Relic > Docker, Kubernetes > Apache, Nginx > CLI, Vim > Proxy, Firewall, LoadBalancer
------
https://github.com/kamranahmedse/...2 -
Windows updates are fucking trash. Even if you disable built-in Windows spyware services, they tend to switch themselves on again.
Instead of engaging in that uphill battle, just use a firewall. Whitelist apps you use, and Windows will have no way to update itself or to call home even when the spyware is on.
On my gaming laptop I use Portmaster firewall. It’s free, open source AND has a good UI.20 -
I am currently blocked from doing my job by a firewall policy handed down from corporate that prevents WSL2 from connecting to the internet. Three days of no dev environment and counting.
We make linux software to be hosted on linux in linux containers in linux. We use linux command line tools to make it work.
"NO! WE ARE THE ALL-POWERFUL IT DEPARTMENT AND YOU MUST USE WINDOWS BECAUSE FUCK YOU THAT'S WHY."14 -
First time trying uncomplicated firewall (ufw) on Linux
Why did no one ever tell me configuring a fire wall was this easy1 -
/badhumor
Make a song title or text geeky/dev related, e.g.:
JSON Derulo - Talk Nerdy To Me
Katy Proggy - Firewall
DJ KhaLED - All I Do Is Print
DJ snake_case - Git Push For What
Now you!4 -
"Our central servers firewall has been breached" - Doesn't even work on a server or anything, just his laptop
"How many proxies do we have left?"
"Around 10.200"
I don't take responsibility for any brain damage -
Ever had that frustrating moment that the customer overreacts a small issue into a big issue? Just happened to me today.
Client: "Hey can you check why we are not getting any software update/patches to our firewall?"
Me: "OK. Lemme check"
** Checking **
Me: "I found that its not getting the latest updates because the license file registered has a product serial # mismatch with their support site. You can see it clearly here..."
Client: "THAT'S TERRIBLE!! QUICK!! MAKE IT A PRIORITY 1 ISSUE AND HAVE IT RESOLVE ASAP!!!"
Me: *Facepalm*1 -
GOD DAMN THE STUPID IPTABLES, aaaaah!
Today I learned that
iptables -I INPUT -i !lo -j DROP
and
iptables -I INPUT ! -i lo -j DROP
are two completely different rules, the first of which doesn't work (in ~99.9% of cases)
yet both pass and get added to the firewall. And both rules show exactly the same in the state listing (iptables -L -n -v).
And I was wondering why the hell the firewall wasn't working...8 -
Was talking to a cousin of mine who's a priest and who spent 10 years in the Vatican, apparently they have 2-3 servers devoted specifically to acting as a firewall processing the data coming in and out of its network and it's a continuous stream of people trying to hack it, like think it would be pretty cool to see what way they have to whole thing set up, might see if he could take me on a tour (might even get a look at the private archives, though apparently it's mainly boring letters about popes meeting their mother and stuff4
-
Internet access at the new Uni is crap. I'm getting so pissed at this shit...
Packet loss spikes to over 50% every 30s or so. Can't keep a single SSH pipe open for longer than a minute. Firewall is so tight infrared light wouldn't get through that shit (understandable. And I use a VPN anyway).
And every. Single. AP. Uses. The. Same. Channel. All of them on 6. At least it's on a tight band... But 1 and 11 are free. 100% clean. You know, you could spread them a bit. That helps. But naaah let's keep everything bundled up. Co-channel interference is OK, right?2 -
The networking closet I had the pleasure of working in most of last night. That's all very loud, very warm air compressors at the bottom, and the switch, firewall, and modem up near the top. And all they had was a small step stool...

-
Back when I started my career (12 months ago lol), I was in IT support. Having to deal with people who have hard times locating and reading off a sticker, let alone telling me their IP adress, only to realize it's the whole store that's offline, not only their PC (gosh do they ever talk with each other). So I decided to code a small tool that shows your hostname and IP adress, and pings the router, firewall and Google DNS. Aaand just in case the number for the IT hotline. Plan was that we could just tell them to double-click on that one icon on their desktop and read out what it says. We deployed it and I was happily waiting for it's time to shine (still a trainee I was also kinda proud of it), but when the network engineer found out, he wasn't happy about it at all. He was afraid too many people would open that new tool without us telling them to do so and/or forget to close it, producing a number of pings to the router, firewall and google. He went on about Google maybe blocking our IP if we produce too many pings and so on.
In my opinion he was kinda overreacting, but he wasn't that wrong and is a nice guy and responsible for our network, so we recalled the tool and never actually used it.2 -
So, unlike normal people who just click on an mp3 file in windows explorer, I'm listening to music saved on my windows hard drive, accessed via an sshfs mount, using VLC running inside a HyperV linux VM and Xming/pulseaudio to make it show up inside windows like a normal window and play sound.
Why? Because this is my replacement for WSL which broke (Good Job on the updates as always, M$) and I'm celebrating that I got everything* to work.
* Nevermind the hours I wasted because I forgot to add a rule to the windows firewall allowing pulseaudio to connect and the fact that Xming can't handle vlc playing video 7
7 -
Follow up to: https://devrant.com/rants/5047721/....
1- The attacker just copy pasted its JWT session token and jammed requests on the buy gift cards route
2- The endpoint returns the gift card to continue the payment process, but the gift card is already valid
3- Clients wants only to force passwords to have strong combinations
4- Talk about a FIREWALL? Only next month
5- Reduce the token expiration from 3 HOURS to 10 minutes? Implement strong passwords first
6- And then start using refresh tokens
BONUS: Clearly someone from inside that worked for them, the API and database password are the same for years. And the route isn't used directly by the application, although it exists and has rules that the attacker kows. And multiple accounts from legit users are being used, so the person clearly has access to some internal shit6 -
I hate IT managers, how on earth some become ant form of manager is beyond myself.
I have a server with a hardware firewall. A client, based in the UK, with French offices is saying the server blocking their new French IP. I white-listed their IP address, still no luck.
That was a week ago.
After 4 international phone calls and nearly 30 emails I resolved the "issue".
Their so called "IT Manager" sent over the wrong IP. Instead of it starting with 46.* he sent over an IP starting 42.*, which was in fact being correctly blocked.
Suffice to say I charged the client a lot of money for the wasted time and international rate calls. 2
2 -
Every TV show/movie with a hacking scene....
Person trying to hack: I'm unable to get through their firewall.
Boss : Then hack HARDER.
Hacker: Thanks for the advice boss! I'm in! -
Corporate IT blocks all network traffic, whitelists port 80 and 443 😡
... cos port number is the best predictor of security threats, amirite? 😒 1
1 -
At the institute I did my PhD everyone had to take some role apart from research to keep the infrastructure running. My part was admin for the Linux workstations and supporting the admin of the calculation cluster we had (about 11 machines with 8 cores each... hot shit at the time).
At some point the university had some euros of budget left that had to be spent so the institute decided to buy a shiny new NAS system for the cluster.
I wasn't really involved with the stuff, I was just the replacement admin so everything was handled by the main admin.
A few months on and the cluster starts behaving ... weird. Huge CPU loads, lots of network traffic. No one really knows what's going on. At some point I discover a process on one of the compute nodes that apparently receives commands from an IRC server in the UK... OK code red, we've been hacked.
First thing we needed to find out was how they had broken in, so we looked at the logs of the compute nodes. There was nothing obvious, but the fact that each compute node had its own public IP address and was reachable from all over the world certainly didn't help.
A few hours of poking around not really knowing what I'm looking for, I resort to a TCPDUMP to find whether there is any actor on the network that I might have overlooked. And indeed I found an IP adress that I couldn't match with any of the machines.
Long story short: It was the new NAS box. Our main admin didn't care about the new box, because it was set up by an external company. The guy from the external company didn't care, because he thought he was working on a compute cluster that is sealed off behind some uber-restrictive firewall.
So our shiny new NAS system, filled to the brink with confidential research data, (and also as it turns out a lot of login credentials) was sitting there with its quaint little default config and a DHCP-assigned public IP adress, waiting for the next best rookie hacker to try U:admin/P:admin to take it over.
Looking back this could have gotten a lot worse and we were extremely lucky that these guys either didn't know what they had there or didn't care. -
A few days ago, I saw a topic from hackernews about Xiaomi phones having a high risk vulnerability because of analytics.apk. I didn't mind it (I'm using a Xiaomi phone).
After about 2 days, I had a notification on my screen having a message 'test' made by my browser.
I immediately installed a firewall blocking all Xiaomi related services.
WTF Xiaomi 3
3 -
At my last gig I was working at a small ISP and my boss was asking why our throughput went to shit every time he checked the router web ui. I told him it was because the web server on the router uses up a lot of CPU time, and that meant the router couldn't process as many packets since it uses that same CPU for well routing, nat, firewall rules etc...so it's probably best to use the CLI instead. Boss says, "YOU DON'T TELL ME WHAT TO DO!!!" And continues to destroy throughput by looking at the web ui.
TL;DR Boss yelled at me for telling him how things work. Yay.1 -
So how the fuck am I meant to get any work done with no admin access to my machine, no access to the databases I need to work with, firewall rules stopping me from doing anything from AWS so I can’t get to my data? Deadline in about a week... fuck that noise!5
-
Why the fuck do I have to work with Windows? AND WHY THE FUCK DO I NEED TO RESTART 3 TIMES TO GET ACCESS TO THE INTERNET? AND... WHY THE FUCKING FUCK IS EVERYTHING 7000 TIMES SLOWER WHEN I PUT MICROSOFT DOMAINS IN MY ROUTER FIREWALL?!9
-
I am building a website inspired by devrant but have never built a server network before, and as im still a student I have no industry experience to base a design on, so was hoping for any advice on what is important/ what I have fucked up in my plan.
The attached image is my currently planned design. Blue is for the main site, and is a cluster of app servers to handle any incoming requests.
Green is a subdomain to handle images, as I figured it would help with performance to have image uploads/downloads separated from the main webpage content. It also means I can keep cache servers and app servers separated.
Pink is internal stuff for logging and backups and probably some monitoring stuff too.
Purple is databases. One is dedicated for images, that way I can easily back them up or load them to a cache server, and the other is for normal user data and posts etc.
The brown proxy in the middle is sorta an internal proxy which the servers need to authenticate with to connect to, that way I can just open the database to the internal proxy, and deny all other requests, and then I can have as many app servers as I want and as long as they authenticate with the proxy, they can access the database without me changing any firewall rules. The other 2 proxies just distribute requests between the available servers in the pool.
Any advice would be greatly appreciated! Thanks in advanced :D 13
13 -
Not mine, but a colleague puts a script in production which has to sent an email every time a config changes, but in reality sent an email every time the file was accessed. The system sent a good amount of email in a couple of minutes, the remote SMTP bounced them but the connections on port 25 was dropped by the server, the production firewall hits the maximum number of allowed connections... a lot of shit!
-
I find it funny that as soon as I disable password authentication on my server and enable key auth then all of the bots spamming my server with incorrect login requests instantly stop when they realise that they aren’t getting through any time soon. Also don’t ask why I don’t have Fail2Ban and a firewall set up.5
-
Look here Mr Senior Tech if you don’t know 100% what you’re doing, don’t fucking touch the goddamn firewall with your fucking sausage fingers and you overblown call center team lead. I mean you need to have the confidence you would have if you were eating a banana and some one told you it was a poisonous berry, you’d laugh and eat it anyway, cause it’s obviously a banana. That’s the kind of confidence you need to have when fucking with the entire goddamn network configurations. I just went thru a 7 hour shit show because you THOUGHT you knew what you were doing. Not a damn thing was broken there. One service needed a hole in the firewall and you fucked all this beyond an easy fix. Now I’ll admit I don’t have that much confidence working with the firewall, that’s why I would fucking cal one of the companies that set it up even though we don’t necessarily have a support contract, it would have cost a lot damn less to have them work on it than for the whole company to be down and for me to have to stress over every fucking thing going (or not going) on.
-
Look, I worked in companies that didnt givr a single f about security, and it wasn't right, but others go are just mad.
Me to itsec: can I deploy Django behind the company firewall on a machine physically 2 meters from you, users will still need the VPN to access it... ?
Itsec: no!
Me: flask?
Itsec: no!
Me: shiny?
Itsec: no!
Me: CAN I EVEN HOST ONE HTML FILE WITH INLINE CSS?
itsec: can I see your badge?! -
When you ask your infrastructure admins for a firewall rule and you are very specific. They say that you don't need it... you troubleshoot for 2 hours then argue with them for 5 hours. Then they add the rule and it works. I want to punch someone right now and have a beer. FML!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
-
Could the all of the Tencent cloud kindly please fuck off back to China?
Those assholes don't even publish their IP ranges so one could easily block their ass.
Had to rely on external tools and hunt down all of their different ASNs to finally block them from overloading a client's webapp...
Ugh, I need a beer.4 -
Some minutes ago our firewall in office overheated, no internet, no network, no real way to work some time for coffee and nerd talk - not bad at all1
-
## Building my own router
So after poor luck with mPCIe in my miniPC I decided to go with USB wifi solutions. So I got the https://aliexpress.com/item/... , hooked it up and started setting things up. Took me a day to figure out that firewalld (CentOS7/8 firewall) is not directly compatible with raw iptables commands. Damn it! But hey, a lesson learnt is time well spent!
Installed named, dhcpd, hostapd, disabled NetworkManager for my wifi card, etc.. And had to learn another lesson -- if a netowrk interface is bridged then iptables sees the bridge rather than the raw interface. That's another 2 hours well spent :)
In the end I have a working AP!!! It's still hooked in to my router via RJ45, but it does work and does work quite well!
Here's some comparison for now:
via router (2.4): https://speedtest.net/result/...
via router (5): https://speedtest.net/result/...
via miniPC (2.4): https://speedtest.net/result/...
via miniPC (5): <TBD>
Not that bad, aye?
All in all I'm happy with my decision to build a miniPC based router. Now I have the modularity I wanted so mush and a complete control on my networking! Can't wait for wifi6 USB dongles to be released :)3 -
A client's site got malware infected, so we decided to remove everything and replace the site with a fresh WordPress installation (very basic site with 4 pages of content).
Contacted iPage live support asking them to check and unsuspend the account (with no files on it), but they kept on insisting that I buy their "firewall" and "SiteLock" services, with zero reply related to suspension. I've had live chat with many other hosting companies, never had such a lousy fucked up conversation. Without providing technical support, they keep marketing their useless expensive services. Fuck you iPage, you just lost a customer.2 -
About slightly more than a year ago I started volunteering at the local general students committee. They desperately searched for someone playing the role of both political head of division as well as the system administrator, for around half a year before I took the job.
When I started the data center was mostly abandoned with most of the computational power and resources just laying around unused. They already ran some kvm-hosts with around 6 virtual machines, including a cloud service, internally used shared storage, a user directory and also 10 workstations and a WiFi-Network. Everything except one virtual machine ran on GNU/Linux-systems and was built on open source technology. The administration was done through shared passwords, bash-scripts and instructions in an extensive MediaWiki instance.
My introduction into this whole eco-system was basically this:
"Ever did something with linux before? Here you have the logins - have fun. Oh, and please don't break stuff. Thank you!"
Since I had only managed a small personal server before and learned stuff about networking, it-sec and administration only from courses in university I quickly shaped a small team eager to build great things which would bring in the knowledge necessary to create something awesome. We had a lot of fun diving into modern technologies, discussing the future of this infrastructure and simply try out and fail hard while implementing those ideas.
Today, a year and a half later, we look at around 40 virtual machines spiced with a lot of magic. We host several internal and external services like cloud, chat, ticket-system, websites, blog, notepad, DNS, DHCP, VPN, firewall, confluence, freifunk (free network mesh), ubuntu mirror etc. Everything is managed through a central puppet-configuration infrastructure. Changes in configuration are deployed in minutes across all servers. We utilize docker for application deployment and gitlab for code management. We provide incremental, distributed backups, a central database and a distributed network across the campus. We created a desktop workstation environment based on Ubuntu Server for deployment on bare-metal machines through the foreman project. Almost everything free and open source.
The whole system now is easily configurable, allows updating, maintenance and deployment of old and new services. We reached our main goal for this year which was the creation of a documented environment which is maintainable by one administrator.
Although we did this in our free-time without any payment it was a great year with a lot of experience which pays off now. -
Today I had sort of a meltdown when I found out that the small, 20-something company where I work and where we should all 'trust each other' is working to stealthily enable SSL Inspection.
I'm done with doing anything other than what is stipulated in my contract such as helping out in other areas out of my own volition.
Management got control hungry and mad once they got their hands on a Deep Inspection Firewall.
Well, I'm not feeling sorry for the uproar they'll have to endure once colleagues find out they are doing this stealthily.
Serves them right and after this and other similar experiences my trust in this company is right through the floor.2 -
Programmer: "Places : instead of ;"
Javascript: "What the fuck did you just fucking post about me, you absolute beginner? I'll have you know I worked for ten of the biggest silicon-valley industry companies, and I've been involved in over two hundred top secret projects including NodeJS. I am trained in refactoring the most fucked up code, and I'm the top C++er in the entire fucking internet-connected universe. You are nothing to me, but just another IP. I will fucking revoke your commits from your gitlab account with absolute dedication using only one Rasperry Pi client. Mark my fucking words. You think you can get away with posting that shit on one of my numerous very personal blogs? Your devices are fucking bricked, kid. My attack software can be anywhere, anytime, and it is tasked to remove your entire git contributions from planet earth. Not only am I extensively trained in remote cross-firewall device-hacking, but I have access to over 100 of the United States CIA and NSA git repositories. If only you could have known what doom-bringing C-one-liner you have raised from my fucking hands, maybe you would have held your fingers. But you could not. You did not. And now you're paying the price, noob. I will hail havoc upon your puny online-presence and you will drown in your own badly designed software. You're fucking offline, kiddo."11 -
What is your home network infrastructure like?
Ethernet or is everything WiFi? Is there a dedicated firewall? Servers running on a raspberry? Do you have VLANs configured?19 -
Barracuda Email Firewall for Dummies:
1. Email Client with perfect grammar and nice subject line. (Email rejected)
2. Change subject line to include Russian and Chinese characters along with discount advertisements for Xanax and male enhancement pills. (Email sent!) -
1. It's gonna be more and more specialized - to the point where we'll equal or even outdo the medical profession. Even today, you can put 100 techs/devs into a room and not find two doing the same job - that number will rise with the advent of even more new fields, languages and frameworks.
2. As most end users enjoy ignoring all security instructions, software and hardware will be locked down. This will be the disadvantage of developers, makers and hackers equally. The importance of social engineering means the platform development will focus on protecting the users from themselves, locking out legitimate tinkerers in the process.
3. With the EU getting into the backdoor game with eTLS (only 20 years after everyone else realized it's shit), informational security will reach an all-time low as criminals exploit the vulnerabilities that the standard will certainly have.
4. While good old-fashioned police work still applies to the internet, people will accept more and more mass surveillance as the voices of reason will be silenced. Devs will probably hear more and more about implementing these or joining the resistance.
5. We'll see major leaks, both as a consequence of mass-surveillance (done incompetently and thus, insecurely) and as activist retaliation.
6. As the political correctness morons continue invading our communities and projects, productivity will drop. A small group of more assertive devs will form - not pretty or presentable, but they - we - get shit done for the rest.
7. With IT becoming more and more public, pseudo-knowledge, FUD and sales bullshit will take over and, much like we're already seeing it in the financial sector, drown out any attempt of useful education. There will be a new silver-bullet, it will be useless. Like the rest. Stick to brass (as in IDS/IPS, Firewall, AV, Education), less expensive and more effective.
8. With the internet becoming a part of the real life without most people realizing it and/or acting accordingly, security issues will have more financial damages and potentially lethal consequences. We've already seen insulin pumps being hacked remotely and pacemakers' firmware being replaced without proper authentication. This will reach other areas.
9. After marijuana is legalized, dev productivity will either plummet or skyrocket. Or be entirely unaffected. Who cares, I'll roll the next one.
10. There will be new JS frameworks. The world will turn, it will rain.1 -
New twist on an old favorite.
Background:
- TeamA provides a service internal to the company.
- That service is made accessible to a cloud environment, also has a requirement to be made available to machines on the local network so you can develop against it.
- Company is too cheap/stupid to get a s2s vpn to their cloud provider.
- Company also only hosts production in the cloud, so all other dev is done locally, or on production non-similar infra, local dev is podman.
- They accomplish service connectivity by use of an inordinately complicated edge gateway/router/firewall/message translator/ouija board/julienne fry maker, also controlled by said service team.
Scenario:
Me: "Hey, we're cool with signing requests using an x509 cert. That said, doing so requires different code than connecting to an unsecured endpoint. Please make this service accessible to developer machines and lower environments on the internal network so we can, you know, develop."
TeamA: "The service should be accessible to [cloud ip range]"
Me: "Yes, that's a production range. We need to be able to test the signing code without testing in production"
TeamA: "Can you mock the data?"
Me: "The code we are testing is relating to auth, not business logic"
TeamA: "What are you trying to do?"
Me: "We are trying to test the code that uses the x509 you provide to connect to the service"
TeamA: "Can you deploy to the cloud"
Me: "Again, no, the cloud is only production per policy, all lower environments are in the local data center"
TeamA: "can you try connecting to the gateway?"
Me: "Yes, we have, it's not accessible, it only has public DNS, and only allows [cloud ip range]"
TeamA: "it work when we try it"
Me: "Can you please supply repro steps so we can adjust our process"
TeamA: "Yes, log into the gateway and try issuing the call from there"
Me: (╯°□°)╯︵ ┻━┻
tl;dr: Works on my server -
The most crazy issue I've fixed was caused by a TCP behavior which I didn't know, called the "half-closed connection".
There was a third-party application installed on a production server which called a LDAP server for retrieving users information. During the day we had several users using the application and all worked fine. During the night, when the application was not accessed, something happened and the first call to the application in the morning was stuck for about 5 minutes before returning a response. I tried to reproduce the issue in a testing environment without success. Then I discovered that the application and the LDAP server were located on two different networks, with a firewall between them. And firewalls sometimes drop old connections. For this reason network applications usually implement a keep-alive mechanism. Well, the default LDAP Java libraries don't set the keep-alive on their connections. So, I found a library called "libdontdie", which force the keep-alive on the connections. I installed the library on the server, loaded it at the startup and the weird stuck behavior in the morning disappeared.2 -
So... I've been messing arround with my first VPS (with little knowledge of Linux).
First installed lxde to learn how to do it, then back to the terminal. then I started with Apache, watching online tuts ...
Then I changed for nginx... Looks way better.
Installed my sql, php and got stuck. Dropped it for a few days.
Today I restarted, deleted Apache, mysql, reinstalled nginx, my php (with lots of problems because of old instalations). Everything is working now except php.
After going round and arround I changed my focus to relax a bit, and remembered I still have Apache on the firewall...
OK Apache and other stuff that I installed.
Delete everything
New rules only for nginx and reset.
Cant ssh to the server... What?
Oh... Forgot to add rules to OpenSSH...
No matter, I can access the terminal directly on the website....
And it loads to ldxe, with no user set...
Fuckkkk.
Oh BTW I'm in a trial free period with no support...17 -
Everytime you tell yourself "This time I'm going to make them stop putting the cart before the horse again!!! No more forced shit implementations!!! NO MORE ! I'm strong!!"
The last hour in the next week:
- Selinux: off
- Firewall: Any-Any
- Application data: Everything installed on OS disc.
- Documentation: At best, someone remembers the server supposed-to-be dns record
- Service Accounts: Your domain admin account and sysadmin for databases.
- Patching: DON'T EVER THINK ABOUT IT..AND NO REBOOTING! I have set very important runtime variables.
- Backup: Maybe someone else will set this up.
- Monitoring: Not needed since clients will create tickets if system fails.
- Production Status: vague at best. Sort of silently transitioned to production.
- Handover status: Probably, but I quit before the project closed.
! -
Firewall is down. That means no access to developer environments. That means more time for DevRant.1
-
So we have an internal license server for intellij.
Installed idea, tried to connect to license server. It wouldn't connect.
Got at least, 10 devs and the admin to look at the problem. No one could find why it was not connecting.
After full 2 hours someone got the idea, came to my laptop and fixed it. Turns out windows firewall was blocking all requests from intellij.
Fuuuuuuuck5 -
I remember someday from a few years ago, because i just got off the phone with a customer calling me way too early! (meaning i still was in my pyjamas)
C:"Hey NNP, why si that software not available (He refers to fail2ban on his server)
Me: "It's there" (shows him terminal output)
C: " But i cannot invoke it, there is no fail2ban command! you're lieing"
Me: "well, try that sudoers command i gave you (basically it just tails all the possible log files in /var/log ) , do you see that last part with fail2ban on it?
C: "Yeah, but there is only a file descriptor! nothing is showing! It doesnt do anything.
Me: "That's actually good, it means that fail2ban does not detect any anomalies so it does not need to log it"
C:" How can you be sure!?"
Me: "Shut up and trust me, i am ROOT"
(Fail2ban is a software service that checks log files like your webserver or SSH to detect floods or brute force attempts, you set it up by defining some "jails" that monitor the things you wish to watch out for. A sane SSH jail is to listen to incoming connection attempts and after 5 or 10 attempts you block that user's IP address on firewall level. It uses IPtables. Can be used for several other web services like webservers to detect and act upon flooding attempts. It uses the logfiles of those services to analyze them and to take the appropriate action. One those jails are defined and the service is up, you should see as little log as possible for fail2ban.) 5
5 -
Can I please rant? So my Acer Computer started misbehaving and turned my firewall off by itself a few weeks ago. After that, the dumb thing decided to revoke my admin rights, and since I was the ONLY admin, I have zilch admin privileges, can't download any apps, and can't make any new user profiles.
How in the living fu*k am I supposed to do my schoolwork and homework for school on a piece of sh*t computer I paid lots of money for? I have tried the built-in admin trick, and it did NOT work. My other user account I can NOT open, as Windows 10 states that "you need an app to open this".6 -
THREE DAYS of debugging, reading all the logs I could find, creating tens of new logs in our appliaction, and SUDDENLY an email from your IT admin:
"Hey your CURL requests are being rejected by my !oh so secure! firewall rule".
Not that I haven't said at the beggining, that THIS IS YOUR F...G NETWORK PROBLEM because we get "connection reset by peer" errors, and you ASSURED that everything is CHECKED and OK! 5
5 -
TLDR: I need advice on reasonable salary expectations for sysadmin work in the rural United States.
I need some community advice. I’m the sysadmin at a small (35 employee) credit card processing company. I began as an intern and have now become their full time sysadmin/networking specialist. Since I was hired in January I have:
-migrated their 2007 Exchange server to Office 365
-Upgraded their ailing Windows server 2003 based architecture to 2012R2
-Licensed their unlicensed VMware ESXi servers (which they had already paid for license keys for!!!) and then upgraded them to 6.5 while preventing downtime on hosted VMs using tricky transfers and deployments (without vMotion!)
-Deployed a vCenter server to manage said ESXi servers easier
-Fixed a three month gap in their backups by implementing Veeam, and verifying its functionality
-Migrated a ‘no downtime’ fileserver to a new hypervisor host, implemented a ‘hot standby’ server as a backup kept up to date by the minute with DFS replication.
-Replaced failing hard drives in a RAID array underlying their one ‘business critical’ fileserver, which had no backups for 3 months at that time
-Reorganized Active Directory and Group Policy deployment from a nightmare spiderweb of OUs and duplicate policies
-Documented the entire old network and now the new one as I’ve been upgrading this
-Audited the developers AWS instances and removed redundant machines, optimized load balancing on front end Nginx servers, joined developer run Fedora workstations to the AD domain and implemented centralized syslog monitoring on them.
-Performed network scans and rewrote firewall exceptions to tighten security
There’s more, but you get the idea. I’ve now been tasked with taking point on an upcoming PCI audit which will be my first.
I’m being paid $16/hr US, with marginal health benefits. This is roughly $32,000 a year, before taxes.
I have two years previous work experience managing a third party Apple repair facility (SimplyMac) and every Apple certification for warranty repair and software troubleshooting. I have a two year degree in general sciences, with about 4 years of college credit (Two years of a physics education and two years of computer science after I switched focus) I’m actively pursuing a CCNA and MCSA server 2016 with exams paid for and scheduled.
I’m going into a salary negotiation in two months. What is a reasonable salary to request, from your perspective, for someone in my position?
Thanks in advance!7 -
I am a web app developer by profession and software engineer by qualifications but when there is a problem with router, firewall or a server needs to be setup, whether internal or for client, all my employer can see is me. Sometimes i get too tired of this shit. Also I am expected to work at home during night as if I don't have any life outside this field. I need to enjoy my life with I am young. I am twenty and stuck. Fuck it.4
-
Today I learned that some external devs one of our projects is working with have DB tables where they store references to specific dates, and not only that, but every minute of those dates, and the day of the week, and what season its in. Im not joking.
Hmm should I use the local datetime libs or should I go through a firewall, load balancer and DB cluster just to find out what day it is? -
Make all fancy Azure blob storage with SFTP connection through firewall with dedicated public IP.
...to just find out that the webcameras you want to send stuff to the blob storage take in max 16 or 30 character passwords for sFTP. While the autogenerated passwords for SFTP in Azure are 32 characters long.
WHO THE HELL RESTRICTS PASSWORD LENGTH!? ASfjksdnfjksdjfnjksdakfadsnjkfjdsa10 -
After debugging this shit Java program for 2 days fucking straight, finally this shit works! Hallelujah!
Turns out, if you want to enable local DCOM/COM+ on windows, you have to not tell the piece of shit firewall that it should consider the network "public"...
WHY?!?
IT'S FUCKING LOCAL! NOT A SINGLE FUCKING NETWORK PACKET IS SEND! WHY?!?3 -
I just love customers:
Customer: "ftps doesnt work! It says Port blocked you are using the wrong port! Fix this now!"
Me: "did you open the port and allow it through the firewall?"
C: " yeah ofc i opened the ports on the server! Do you think i'm stupid?"
M: "On the client too?"
C: "...."
C: " let me call back in 30min" -
My quest towards privacy goes on.
Apparently TabNine AI autocomplete talks not only to api.tabnine.com, but also to serene-waters-6626.morning-tundra-7160.herokuspace.com.
Too bad I got firewall on both incoming AND outgoing connections.7 -
Dear Docker for Windows I know you exist to make devs on Windows life easier. But DEAR GOD, with all the firewall/group policy problems..you have been the pain of my existence during this short time developing on Windows.
Literally have a countdown on the time left until I get to no longer do a rain dance for my development environment to work. 2
2 -
So there I am sitting in front of my laptop, and trying to npm i and I am getting all sorts of sha mismatch errors.
After lot of debug I conclude it is coming from the proxy as it refuses to download and supplies the error page.
It says it's because I'm using the old proxy so they give me the new URL which I set up and it works.
All good until my password expires. I use our bash script to change it. NPM is buggered again throwing the same errors.
Go to IT, tell them the saga begins.
After a countless hours of looking at the log files we notice that the npm registry is set to http instead of the standard https (thanks bash script). so our firewall blocks the download.
Sorted, finally.
Almost. NPM now works fine, but when I go and I play around with node and axios, I get my requests time out. My instinct says its the bloody proxy again.
So I hit up my trusted WIN Support guy and he confirms that the url is not blocked. So he starts monitoring whats going on and turns out, every time I run the node app, node casually ignores the system-wide proxy settings and tries to send the request as the PC rather then my username.
Since the pc's don't have rights on the proxy it is being refused...
Thank fuck for the corporate proxies, without them, I could just develop things not ever learning these quirks of node...3 -
Experiences of owning a private server with JFK!
Dropping a prod db: 1
Misplacing passwords: 3
Config errors: Over 9'000
fail2ban banned me: 2
Not reading the docs first since: Forever
Setting up a sever again because I fucked up: 4
Formating the wrong USB stick, which had needed data: 1
Resetting lost DB root password: 2
Server crashes due to insufficient psu: 3
Not knowing the firewall is enabled again, so near to nothing works: 22 -
"You send an email this morning that you're going to reset the firewall, is there anything I can help with?"
"Well a good blowjob would be of great assistance" -
Just started learning Docker. The thing that seemed complex a week ago has started to unwrap the wonders it holds. Hope to make it work to ease up some of the team's deployment headache. Though there were hurdles related to firewall, company intranet, network antivirus, domain sharing etc. But managed to resolve it today.2
-
>when a sysadmin sets his local Linux firewall (gufw) where one of the rules had the end of the cidr block as the first IP address and the beginning of the cidr block as the last IP address.
Needless to say nothing worked. But the server was secure because nothing could connect to it 😂1 -
FUCK FUCK FUCK Windows share feature
just fuck it !
and fuck the people who made it!!!44
ok calm mode on
I had to copy a 30 gb file from my computer to my sister's one, and since the largest pendrive I have is 8gb, and I'm just lazy to split the file into parts, I thought it would be a great idea to copy it over LAN. (tldr: it's not)
First attempt:
Right click on file and share it with everyone = fail
Enable network discovery in sharing settings = still fail
Ohh, right, I just forgot it, disable firewall, it usually solves everything = still fail (2)
Google the problem and try every possible solution = still fking fail
Second attempt:
Ok, when last time I had the same problem, I made a homegroup and it worked.
Let's enable it on my Win10 = it's missing
After some googling: "We removed the home group feature from Windows 10, because why not and we would be fired if the change log was empty."
Ok, fuck it.
Third attempt:
Download a portable FTP server.
Enable it.
Create an account.
It works.8 -
Fucking fuck fuck hell.
My grandfather Bought a 50€ doogee phone.
After one month, it started showing advertizuments randomly.
I installed a firewall, but now it opens a different advertizinc in my Browser every few hours.
WHO THE FUCK THOUGHT IT WOULD BE A GOOD IDEA?
O AND:one tap root doesnt work7 -
Colleague just factory reset the firewall....
- "I have just changed a firewall rule"
Motherfucker!!!!! Burn, burn in hell! -
A week ago I raised an issue claiming I couldn't ping service x and that it was blocked
Today I figure out ping is blocked on firewall level and http requests work fine
Guess that's my big blunder this internship2 -
me: block all in&put connection
firewall: ok
me: open port 22 for local network
firewall: ok
me: enable firewall
firewall: ok
me: restart pi
firewall: allow me connect
me: open port 80 for local network
firewall: ok
me: open port 443
firewall: Oh! i have to block icoming connections on port 225 -
I deployed docker on a VPS a few weeks ago as a sort of learning experience since I haven't really worked with containers much before. Today I learned that docker doesn't like firewalls.
Or, to be more specific, it adds rules to iptables that are applied prior to ufw rules, allowing external connections that I really didn't want to allow. If I don't explicitly specify that a port is to be published only to localhost, then it punches a hole through my firewall without telling me.
Which means that all of my containers running behind an nginx reverse proxy that auto-redirects to HTTPS... were also accessible directly via HTTP.
I'm... trying to think of a reason why this kind of default behavior was a good idea, but I'm drawing a blank.
Fucking Docker.4 -
My conversation with Avalara support (API for taxing):
Me: Hey I'm implementing your API for a client. The requests are going through, I get a valid response back but all goods are taxed with $0. Can you please give me a hint what I might be missing?
Sup: You're using Salesforce Commerce Cloud, requests might be blocked through their firewall
Me: I don't think so, here are some sample requests and responses I just created. The object returned matches the one in your API Doc.
Sup: This isn't a system controlled by us, no support.
Me: So how in the world can it be you don't control your own endpoint?
Seriously, if you don't want to help, next time just say fuck you...5 -
The networking group at my day job, hooooooolly crap I have some unprintable words. But keeping it professional:
* Days to turn around simple firewall whitelisting requests
* Expecting other teams to know the network layout despite not sharing that information anywhere and going out of their way to not share it
* Adding bureaucracy in the form of separate Word doc forms despite having a ticketing system - for no justifiable reason
* Breaking production systems multiple times per month
* Calling in with problems that are clearly network related, being told it’s our systems, and then the problems magically go away even though they swear they didn’t touch anything
* Outright verifiable lies or vague non-answers when they’re not talking to someone at the director level or a vendor from an outside company on conference calls
* Worse packet loss and throughput on our LAN than my home ISP
Doing anything with these clowns is my single biggest source of stress right now. I can’t wait until we get a full SDN stack set up and then we won’t have to deal with them for day-to-day needs any longer.
My boss swears it’s better that we’re not managing the network directly, but I’m pretty sure my friend’s dog could be loosed into the data center to chew on fiber, and eventually the pairs would be connected in such a way as to improve performance.1 -
After disabling windows firewall, my internet connection got congested. Enabling it again resolved the issue. What exactly does "wall" mean to you Microsoft?!1
-
fuck.. FUCK FUCK FUCK!!!
I'mma fakin EXPLODE!
It was supposed to be a week, maybe two weeks long gig MAX. Now I'm on my 3rd (or 4th) week and still got plenty on my plate. I'm freaking STRESSED. Yelling at people for no reason, just because they interrupt my train of thought, raise a hand, walk by, breathe, stay quiet or simply are.
FUCK!
Pressure from all the fronts, and no time to rest. Sleeping 3-5 hours, falling asleep with this nonsense and breaking the day with it too.
And now I'm fucking FINALLY CLOSE, I can see the light at the end of the tunne<<<<<TTTOOOOOOOOOOOOOTTTTT>>>>>>>
All that was left was to finish up configuring a firewall and set up alerting. I got storage sorted out, customized a CSI provider to make it work across the cluster, raised, idk, a gazillion issues in GH in various repositories I depend on, practically debugged their issues and reported them.
Today I'm on firewall. Liason with the client is pressured by the client bcz I'm already overdue. He propagates that pressure on to me. I have work. I have family, I have this side gig. I have people nagging me to rest. I have other commitments (you know.. eating (I practically finish my meal in under 3 minutes; incl. the 2min in the µ-wave), shitting (I plan it ahead so I could google issues on my phone while there), etc.)
A fucking firewall was left... I configured it as it should be, and... the cluster stopped...clustering. inter-node comms stopped. `lsof` shows that for some reason nodes are accessing LAN IPs through their WAN NIC (go figure!!!) -- that's why they don't work!!
Sooo.. my colleagues suggest me to make it faster/quicker and more secure -- disable public IPs and use a private LB. I spent this whole day trying to implement it. I set up bastion hosts, managed to hack private SSH key into them upon setup, FINALLY managed to make ssh work and the user_data script to trigger, only to find out that...
~]# ping 1.1.1.1
ping: connect: Network is unreachable
~]#
... there's no nat.
THERE"S NO FUCKING NAT!!!
HOW CAN THERE BE NO NAT!?!?!????? MY HOME LAPTOP HAS A NAT, MY PHONE HAS A NAT, EVEN MY CAT HAS A MOTHER HUGGING NAT, AND THIS FUCKING INFRA HAS NO FUCKING NAT???????????????????????
ALready under loads of pressure, and the whole day is wasted. And now I'll be spending time to fucking UNDO everything I did today. Not try something new. But UNDO. And hour or more for just that...
I don't usually drink, but recently that bottom shelf bottle of Captain Morgan that smells and tastes like a bottle of medical spirit starts to feel very tempting.
Soo.. how's your dayrant overdue tired no nat hcloud why there's no nat???? fuck frustrated waiting for concrete to settle angry hetzner need an outlet2 -
The universe has taken a cactus.
It proceeded to gift the cactus with a toxin that greatly enhances the stimulus of pain.
After the universe watched it's miraculous creation it decided to shove it up so far my arse that my gag reflex turned on and I puked a lot of cactus.
Didn't sleep well, weekend hardware migration finish, today an old server got moved.
Some part, most likely the redundant PSU, had a short circuit - decided to take the switches out... Which are the only non redundant hardware...
There was only one critical system in the whole rack, that was one redundant firewall.
Guess what happened..... Naaaa?
*drum roll*
For whatever reason, the second firewall didn't kick in, so large part of internal network unreachable as VPN was on the firewall.
:thumbsup:
That's not cactus level yet.
Spontaneously a large part of the work at home crew decided to call, cause getting an email wasn't enough.
So while all the phones were ringing and we had the joyful fun to carefully take apart a whole rack to check for possible faulty wiring / electric burns / hardware damage and getting firewall up and running again...
Some dev decided to run a deployment (doable as one of the few working at the company at the moment -.-).
I work from home, but we had a conference phone call running the whole time so I could "deescalate" and keep others up-to-date. So me on headphone with conference call, regular phone for calls, while typing mails / sms for de-escalation.
Now we're reaching cactus level, cause being tortured by being annoyed out of hell by all telephone ringing, the beeping of UPS (uninterruptible power supplies), the screaming of admins from the server room and the roaring of air coolers…
Suddenly said dev must have stood in the midst of the chaos… and asked for help cause "the deployment broke, project XY is offline"...
I think it was the first time since years that I screamed at the top of my lungs.
Bad idea (health issues)… but oh boy was it a pleasure to hear my own voice echo through the conference speaker and creating an echoic sound effect.
It was definitely worth coughing out my loungs for the next hour and I think it was the best emotional outburst ever.
I feel a bit sorry for the dev, but only a tiny bit.
After the whole rack thing, the broken deployment fixing and the "my ears are bleeding and I think I will never be able to talk again" action...
We had to roll out several emergency deployments to fix CVEs (eg libexpat).
This day was a marvelous shit show.
I will now cry myself to sleep with some codein.1 -
FUCKING WHY ME!
Lost my dedicated internet access due to a SHITSTAIN of an ISP TELIA decided to introduce itself to my connection A SECOND FUCKING TIME in the past YEAR.
Suddenly lost internet and my firewall couldn't figure out that it was supposed to lose all its fucking connections and renew it's IP adress.
Now im connected to this fucking hipe of shit that is the biggest giver of their customers information to anyone who asks, "Hey man, whats the dude who has this IP?, - sure fam, here you go"
Now i probably have some poor motherfuckers name attached to my current IP.
But could you say that i am now untraceable?4 -
Anyone have any experience with setting up firewalls? Seems like I'll have to do that at the new office, but man, I ain't got no clue.16
-
Anybody else get that massive windows 10 update today that fucking wipes a ton of your settings. Desktop image gone, privacy settings turned back, firewall settings reset.
Fuck I really need visual studios for Linux.8 -
Microsoft is always at it.
Hello, I recently discovered this eye candy of a looking website and how good the CSS looks (Kudos to whoever made this) , and I decided to post a rant of my own. And its about MS Edge and other applications.
So I built my own ATX tower a while back (Loving it) , and I found that it was WONDERFUL to have a computer that was brand new, that didnt have candy crush preinstalled on it when I got it.
Windows 10 users, do this:
Press WIN+I to open the settings menu.
Go to "Apps"
Scroll down the list....
How many applications do you see there that are actually useful , or that you have downloaded?
I never downloaded a Realtek Driver... and I never need it for anything to work. This is the case for 90% of the things you may see in the applications.
Why is HULU installed?
Why is NETFLIX installed?
Why is MINECRAFT BETA INSTALLED? THE BETA HASNT BEEN OUT IN YEARS?
But I digress, this is the case when I work on a computer such as my grandmothers who, bless her soul, isnt very adept at basic file management. Heck , she uses free Norton Antivirus against my recommendation to use the PAID active firewall application on her computer (VIPRE)
So needless to say she needs help. All the time.
So here comes microsoft recently, reinstalling like 15 different programs on her computer , including MS edge. Who else is tired of bloating? I know I am.
I recently found this program on Git!
Its the Sycnex Windows 10 DeBloater
But guess what? DONT USE IT.
Wanna know why?
Because if you do, it works, and if it works, it disables:
- Cortana (basic search engine for your OS, good luck finding candy crush).
- Microsoft Store (That means no XBOX games pass either)
- It breaks part of the file explorer
Wanna know why? BeCaUsE it geTs riD oF Ms EdGe
And believe it or not, apparently MS edges source code is Mandatory for certain functions on your computer. So even If you try to uninstall the browser, it stays behind in some form.
So there you have it. They hard coded it into windows.
Enjoy!
So its not even the author of the GITHUB programs fault, its just a real techincal limitation of the platform.
I hate that stuff man. I really do. There should be 20 things installed on my computer and thats it. Everything else is just, space for games on a solid state. Or Eclipse Photon, etc.
I would post links to show you guys a few things but. Unfortunately I cant post URLs yet!
However, thats my first rant. Hope you liked it.20 -
Sooo... The ways my coworker fucks me:
Last week I have been working on setting up aWireGuard VPN server... Been trying for 4 FUCKING DAYS, the easiest VPN that has ever existed, 2 commands and that's it, I wasn't able to reach it, I checked every forum, tested every possible solution without success, checking ubuntu firewall but it was inactive... Nothing that should cause this. Why? 2 weeks ago we had a security breach and my coworker added a firewall from the cloud console with basic rules allowing only 3 ports, the port I was communicating with was blocked. He didn't bother to mention that he added an external firewall. And the junior me, not wanting to be a pain in the ass, and since that security breach wasn't my responsibility to fix, I didn't ask too many questions, just read the emails going back and forth and "learning" how to deal with that. Kill me please. Next mont a new guy is joining, we had a "quick meeting" of 30 minutes and he managed to make it 2 hours meeting. So a partner who lacks communication and a partner who talks a lot... Will be fun. And I probably should change my username... Is that even possible? @root?10 -
Built a pFSense box for home with said proxy. Even though my internet connection is slow it seems fast now thanks to squids MITM https proxy and http proxy. Plus a little QoS helps. And it has so many more features than a regular router.... WTF didn't I do this sooner?3
-
I never had to deal with an attack.
At least, I don't know about it. My firewall couldn't detect anything.
I wish I could have experienced something like that tbh *sob*2 -
Just upgraded to Win 10. Windows update keeps sucking my bandwidth. Stopped windows update and BITS, set to manual, yet keeps popping up. Finally blocked windows update's IP via Firewall. Now oddly satisfied..1
-
Some <super smart> person ran DHCP in production lab (without disconnecting from main network and/or using firewall)
, now the admin turned all the ports off and went home.
Traffic gens are also unavailable now so are upgrade servers.
Result: I can't run my work over the weekend and the reports are expected on Monday.
Not so bad : I'll run on Monday.
Bad part : This fucking shit takes 2 days to do everything on the rack.3 -
When the ops team needs to go through a 5 step "protocol" over a couple of days, just to open a damn port in the firewall, so that our CI server can access the local GitLab server..
Seems like the migration of the last couple of projects from SVN to Git is going to take a little longer than I expected.. -
Fucking remote db doesn't want to work with me and workbench. DB is on an empty test server, no firewall issues on the network, powershell on my pc says ping ok, tcp failing though, server firewall not running, server up and running.
Tried to modify network access on db configs like bind-adress, set my db user "host" value to wildcard. Now I can log in on workbench with my user, yet root somehow fails, wtf?
And of course once the connection is live, no db us visible, accessible, nothing works. I'm so frustrated. About to nuke it and restart ... again!13 -
Article 13 has gone through.
If you have a startup idea, move outside the EU to avoid millions of dollars of copyright fines.
Get the memes, get tor, get vpns, research how people get around the great firewall of china, because the EU just asked china to hold its beer.
I pity whoever's job it is to implement this piece of shit. 12
12 -
!Dev
TL Dr :- Debugging a software I barely know about was slow and ended up breaking in the shop it was used in and reverting the changes does not solve the problem
I asked my father a few days ago why he was buying a dedicated server for his ERP software and not using a client computer as his server which he is doing in his shop currently. He said that it was slow on other computers in the LAN which is an wired. The solutions given by the company that made it did not work. Big bills would sometimes also dissapear which took around 30 minutes to make. So when he bought the computer to home during lockdown I pulled up the debugging guide from the company which summed up to check latency,ram and add these files to exclusion list of your antivirus. Latency was kinda high at the first when pinging another computer on the LAN but I was testing on WiFi so it could be pretty inaccurate. The computer met the ram requirements so that was not a problem. I checked the data path by opening the software and accidentally typed something but I did not worry since the changes needed to be manually accepted. I added the files to the Windows defender exclusion list and shut it down.
Next day :- My father calls me up and says the software is working on the server but is broken on other computers. So I check if the changes were automatically accepted for some reason and yes that happened. So so pull up a guide to configure the software in multi user mode and I replace the mistyped setting with the correct one and it still does not work. My father asks me to undo everything by using anydesk. I remove all the exclusions I added to Windows defender and disable windows firewall. Still does not work. Restart the computer and software. Still does not work. Check permissions on data folder. They are correct.
WTF I reverted all the changes I made and the software does not work on other computers.7 -
I hate the US education system, its just designed to fuel capitalism. It keeps getting less funding so that actually passionate, intelligent people get kicked out and replaced with people who only want to be a teacher so they can have power over others.
Why do they block news websites? Why do they block github, so their own robotics team can't even access the essential building blocks for the robot? They make everything more complicated and for the reason that it might distract you. Maybe just make topics engaging and not boring asf, just cramming for the exams so the school gets more funding. Maybe prepare students for jobs, allow them to do projects, pursue classes that interest them, and have any sense of individualism.
Anyways, yeah, the school blocked github so I can't do my FBLA project, I can't access the code for programming our robot for competitions, I can't even download software required for half of these classes. I have a Linksys router, is there any way I could set it up to bypass the firewall?16 -
When you hear that the "advanced hollistic security" product the client bought is a basic firewall...1
-
Jesus fucking Christ windows firewall is a tumor on this Earth. Serious who the hell thought of the design for that shit? The way rules are implemented are fucking terrible and you really can't tell one choice from the other. All I needed was for a game to be allowed through my firewall so I could host games and it took hours to fix this problem.
-
https://bbc.com/news/...,
Between this and GDPR, were going to create a great firewall that will just block all network traffic to the EU. They don’t get how the internet works. Government shouldn’t touch things1 -
IDK man, it took me a while to finally learn iptables and now switch to firewalld? Oh come on. It's not that I'm against learning new things, no. It's just that firewalld looks a bit.. crappy. If I get a server provisioned and run
firewall-cmd --add-port=53/udp --permanent
firewall-cmd --reload
and I get my ssh connection killed that's no good news, no sir! I mean come on, how can I rely on a tool this critical when a single line in its config file can make my machine inaccessible. Even better -- this config file is managed by that tool entirely!!! My commands passed all the tool's checks and they worked, but when I wanted to make those commands permanent and reload state from the config -- the tool starts spitting bile and blood and says "fuck off, it's my server now!"
IDK man.. It's just way too fishy. The good ol' iptables works very well and I'm kicking its retard younger brother out of the server.
shoosh you dirty pig firewalld, shoosh!6 -
Dev sin: when you're too lazy to configure ufw (uncomplicated firewall) so you just shut it down instead 😓
-
Company I work at has several offices over the world. Our internal repository for code is held in our servers in China.
Pushed code using a regular connection - 45 minutes for 3.7 MB worth of files
Pushed code over VPN - Instantaneous for 6 MB worth of files
*flips table*3 -
#justAthought
I was reading about public and private keys yesterday, and i had a thought: don't you think the concept of "username" is being so badly misused?
It can act as a great firewall, but we are just misusing it as an alternative to "login via email", because we are now so dumb to remember our email.
You might think of my rant as being going back in time, but think about this: my profile shows the name titanlannister. if someone got access to my password, he/she can immediately take over my complete identity because devrant allows us to login via username/password combo.
Now think of this: my username shows titanlannister. Anyone of you can write a post and mention me via @titanlannister, and this system will notify me. However even if you get my password, you are unable to hack into my profile, because my profile is only accessible via my email id/password combo, which you still don't know.
This, I would call as Platform Public Key which adds a kind of semi firewall over default public/private key combination .
What do you think?5 -
some dev asked in group chat if the connection between HOST1 and HOST2 is blocked on the firewall.
They're are sitting in DMZ and intranet ... of course one direction is blocked
I asked for details, he wants to SSH from the one sitting in DMZ to the one in intranet (which is a docker host btw)
oh boiiii1 -
More network/hardware than dev but anyway: I use OPNsense as a firewall at home on an embedded system. Had everything set up nicely and appearing to be working fine, quite a lot of things set up (static leases, VLANs with various firewall rules etc. - a fair bit of stuff involved). I noticed my remote system was failing to back up to my local one. Turned out port forwarding wasn't fully working (initial packet got through but nothing else). I noticed this at midnight.
Ran an update to see if that helped - nope. Reboot time then! It made its shutdown noises and I waited 15 minutes before giving up (no noises, no ping response). Took SD card out. Copied a fresh install onto it, thus wiping all settings. Booted up fine, set up my internet connection, all good. Proceeded to configure it. Noticed I couldn't access the internet from my PC, but could from the firewall itself. Rebooted the firewall. It didn't come back up. Argh!
Reinstalled AGAIN. Attached a serial cable and it was complaining about something which sounded like it couldn't read the SD card. Tried another. Nope. Looked online (using phone): known issue to do with boot delays.
Gave up and went to bed at this point (4am).
Next day: Installed it in a VM instead. Still no internet from my PC! Another known issue to do with default gateway not being the PPPoE interface. Got into shell, manually changed the default route. Was then able to update to the latest version which fixes the gateway issue. Rebooted the VM. All good.
Put all my settings back in, this time taking a backup afterward.
Only to discover....
....port forwarding wasn't working properly. Back to square 1.
Poked around with some NAT settings (outbound ones), made no difference, undid those changes and suddenly it started working.
WTF? /waves arms in the air
OPNsense folk were very helpful, producing a new build for me to try within a couple of hours of me asking about the problem.
But days like that, I start to question whether I really enjoy technology as much as I thought I did... -
The company I work in had to build a software that establishes a connection to a MySQL database running on an external server. It doesn't work for the client company because the firewall is very restrictive and only lets through connections on port 80, so we had to build a fucking http server that forwards SQL queries to the MySQL server and returns the result. This is so horrible!
(Running MySQL on port 80 isn't an option as any other connection type than http is blocked by the firewall)8 -
Spent 4 FUCKING HOURS to solve a connection issue on my Ubuntu Server only to get a call after said time from the server provider that they installed an firewall and blocked my fucking port. WHY ????2
-
Got a legit question/semi rant for anyone who may know. I want to start by saying that I'm not really a "network" person, at least on MS systems. I can physically plug cables in and shit like that, but the software side of networking is not a thing with which I can claim familiarity. Anyone who's read my recent rants will know that I am forced to deal with IIS, because my boss is an insufferable microshit fanboy of the highest level, and is easily frightened and threatened by the use of a keyboard for anything other than using facebook.
I've got a couple of microservices running under IIS, and our customers thankfully are able to access them with no issues. Those of us in the "IT department" are also able to access it. No one else in the building, on our network can, and despite me not having set up this network, or really having anything to do with it, the rest of my "team" (LOL) refuses to help me solve the problem, because developer = networking specialist and printer fixer. Does anyone here have an idea? I found a think on Stack Overflow about firewall rules, but those are already set appropriately.6 -
Okay so anyone experienced working with networking or VOIP applications are welcome to try to help me figure out a few questions I have.
1.) How do VOIP applications like Discord and Skype not have to require you to port forward before use?
2.) If I wanted to do stuff with sockets over the internet the user of the application would have to configure a static IP Address. but when Im using Discord, or a multiplayer game, or literally anything that requires connecting to people I dont have to configure a static IP for those applications but I do for mine?!?
3.) Is there any additional information I should learn about whilst trying to make my networking application (File Transferring application) work? or any links/PDF's I should check out?
These are kinda just things I haven't found answers to, and I didn't know where to ask.14 -
Probably the one where we had an error, because the service from a thirdparty we needed to install used a fourthparty service that was behind a proxy. Due of internal reasons we needed to use our own tomcat instead of the standard tomcat. We made a meeting because we didn't found out at that point that the problem was the firewall that dropped the packages from the application. We replayed it to them (at that point it was in my musclememory) and after a month i got the idea to use tcpdump to see if the server is calling another webservice, which was denied by the developers.
-
My company has an default user for external people and two wifi networks, on for the company itself and on for the employees. both wifis have an shit of an firewall(more than once were wikipedia blocked). I found out that the internal wifi allowed the default user and had some outgoing ports open, i set up an vpn and now i can use what i want without being blocked.
-
I've been wondering about renting a new VPS to get all my websites sorted out again. I am tired of shared hosting and I am able to manage it as I've been in the past.
With so many great people here, I was trying to put together some of the best practices and resources on how to handle the setup and configuration of a new machine, and I hope this post may help someone while trying to gather the best know-how in the comments. Don't be scared by the lengthy post, please.
The following tips are mainly from @Condor, @Noob, @Linuxxx and some other were gathered in the webz. Thanks for @Linux for recommending me Vultr VPS. I would appreciate further feedback from the community on how to improve this and/or change anything that may seem incorrect or should be done in better way.
1. Clean install CentOS 7 or Ubuntu (I am used to both, do you recommend more? Why?)
2. Install existing updates
3. Disable root login
4. Disable password for ssh
5. RSA key login with strong passwords/passphrases
6. Set correct locale and correct timezone (if different from default)
7. Close all ports
8. Disable and delete unneeded services
9. Install CSF
10. Install knockd (is it worth it at all? Isn't it security through obscurity?)
11. Install Fail2Ban (worth to install side by side with CSF? If not, why?)
12. Install ufw firewall (or keep with CSF/Fail2Ban? Why?)
13. Install rkhunter
14. Install anti-rootkit software (side by side with rkhunter?) (SELinux or AppArmor? Why?)
15. Enable Nginx/CSF rate limiting against SYN attacks
16. For a server to be public, is an IDS / IPS recommended? If so, which and why?
17. Log Injection Attacks in Application Layer - I should keep an eye on them. Is there any tool to help scanning?
If I want to have a server that serves multiple websites, would you add/change anything to the following?
18. Install Docker and manage separate instances with a Dockerfile powered base image with the following? Or should I keep all the servers in one main installation?
19. Install Nginx
20. Install PHP-FPM
21. Install PHP7
22. Install Memcached
23. Install MariaDB
24. Install phpMyAdmin (On specific port? Any recommendations here?)
I am sorry if this is somewhat lengthy, but I hope it may get better and be a good starting guide for a new server setup (eventually become a repo). Feel free to contribute in the comments.24 -
AHHHHHHHHHHGGGH
I HATE VPN SETUP
- Trying OpenSwan
Installing open swan on a Debian machine.. setting up the config.
Restarting openswan. Syntax error. No syntax error to be found.
Different tutorial.. it starts! Try to connect.. I can’t connect. Look at the logs. No errors.
Tcpdump. My traffic is coming through.. all fine.. try to connect again.. it works! (Nothing changed!)
Try to ping somewhere else.. no connectivity.
Try to ping an IP in the same network.. works fine. So I have connectivity, just no internet.
Spend an hour finding out about traffic directions of which no one seems to know what they really mean.
Boss tells me to stop using openswan because it’s deprecated and replaced by strong swan..
- Strongswan
Reinstall Debian machine, install strongswan. Copy openswan config. Oh, they’re incompatible? Look up strong swan config, and the service starts.
Connect to the VPN.. it works! Again, no internet, just connectivity in the same network. Spend 2h debugging the config, disable firewalls everywhere, find an ancient bug in the Debian package related to my issues.. ok, let’s try compiling from source.. you know what, let’s not. I’ll throw this Debian machine away and try something completely different.
- pfSense
Ok, this looks easy enough! Let’s just click through the initial setup, change some firewall rules, create an L2TP VPN with a simple wizard.
Try to connect to VPN. First, it times out. Maybe a firewall issue? Turn off firewall.. ah, something happens now. I get an error message right after trying to connect to the VPN. Hmm, the port doesn’t even get opened when I enable the firewall.. this implementation seems a bit buggy.. let’s try their OpenVPN module.
Configure OpenVPN. Documentation isn’t that clear.. apparently a client isn’t actually a client but a user is a client.. ok, there’s a hidden checkbox somewhere.
Now where do I download my certificate? Oh, I need a plug-in for that.. ok, interesting. Able to download the certificate, import it, connect and.. YES!!! I can ping! But, I have no DNS..
Apparently, ICMP isn’t getting filtered but all outbound ports are.. yet the firewall is completely disabled. Maybe I need outbound NAT? Oh. There’s no clear documentation on where to configure it. Find some ancient doc, set it up, still no outbound connectivity.
AHAHAHAHHHHHHHHHHG
Then I tried VyOS. I had a great L2TP VPN working in less than 15 mins. Thank you VyOS for actually providing proper docs and proper software.3 -
Serves me right for developing in production...
Move the process to dev, works fine.
Code and process were fine all along; turns out a firewall issue was blocking the connection for the final step. -
FUCK APPLICATION LEVEL FIREWALLS!
So i cam online today, thought already lets open the shitty outlook webmail client. Holy crap .... thats way to much mails. Many of them are missed teams messages. So i open up teams and holy crap. Like every third dev in my company send me a message screaming "gitab is not working!!!".
Yesterday i updated it so imediately get in panic mode - what the shitty hack have i done?!
So yeah gitlab seems to be working just fine, everything is speedy and responsive, so i call one of my fellow devs and ask him whats wrong? And he is like oh yeah there comes a ldap error saying timeout or something.
I try to login with active directory. Works like a charm. Try another account, same problem?!
Google the problem, search gitlab tickets. Nope there is no open bug or sth. like this.
So alright lets call the network guy. "Yo, can you check if there is something ldap-like getting blocked to the gitlab server?" - He is like oh yeah damn like almost every damn request is getting blocked. Ah wait, there was an firewall update yesterday too. Yeah ldap is no longer ldap. BLOCK THAT SHIT!
After 10 minutes of figuring out what shitty type is detected by the firewall and what needs to be whitelisted to make it fucking work again it seems to work.
But ha no, there is another update rolling on, so same shit like 15 minutes later.
Now it seems to work and i have to inform every damn fcking developer that it works again. And yeah alright you sent a mail, but fuck it, i will call you though! So yeah just answering calls, mails and chat messages. Like why the fuck cant you read your mails like a damn normal person?!1 -
Fuckin damn it Google! I setup a transparent proxy and for some fucking reason Google home doesn't like that at all. I think I have a fix but it's a real fucking pain in the ass. I call your support people who I specifically tell that I'm running a fucking proxy and they tell me that I need to talk to their Google WiFi team. It has nothing Todo with my fucking wifi bitch. Its your price of shit price of crap hardware that doesn't like fucking proxies.
I'll update everyone what the fix is when I find it.
Btw, this is a HTTPS transparent proxy and HTTP transparent proxy running on my pFSense firewall box. 5
5 -
Hey everyone! So for my final year project, I have to make a firewall game to help people understand about firewalls. Any ideas on how I can start?4
-
I've been developping some software so an entire debian OS gets bootstrapped and installed with all the desired software with the help of puppetlabs software...i need to prepare a server that can handle virtualization and be fast at it. So all the goodies a decent server needs, the apt, caching, networking, firewall, everything checks out... I want to test kvm virtualization... Doesn't work. Wtf? Spend a decent amount of time figuring out what the hell is wrong... I finally dzcide to think 'what if my buddy accidentally gave me a bad mobo'...
$ grep -e (vmx|ssm) /proc/cpuinfo
Nothing...
I feel so stupid to not check the mobo virtualization capabilities.3 -
Netstat says that that windows is listening on port 445, but nmap (run from another machine on the same network) says that it's closed. Also the firewall is completely disabled. It's very annoying that I can't use network shares and I don't know how to fix it. Can anyone help?10
-
I finally got my new home server.
A Lenovo ThinkCentre M720q in one of the higher configurations.
Any ideas what top level OS I should put on it?
ATM, I'm thinking Proxmox, ESX or Alpine.
I like proxmox because of the neat UI for everything but I'm kinda worried about how it basically takes the most important parts of the system over.
I like Alpine since I already use it for quite a while as my goto server OS and because of AWALL, which IMHO is the best linux server firewall.
I didn't get to evaluate ESX yet.6 -
uPlay is ramming me down the throat harder than what should be legal, I can barely breathe.
I'm trying to install Far Cry 5, I preordered it. But.. download is stuck on fucking 0B. That being 0 bytes.
I tried disabling all firewall/antivirus, clean Windows boot, restart, reinstall launcher, slam the table, like everything.
Why isn't the shit fucking doing its job? Anyone who got ideas for what I could try next?
I'm not gonna send a message to their support, I'd rather have sex with a hedgehog, where I'm the one being penetrated. Fuck me.6 -
One of my favorite parts of my job is that I’m not allowed to resolve firewall issues myself. IT ops frequently breaks my firewall config, preventing me from resolving any domain names or running dns queries in general even though I still have connectivity. So I call the support number. Remote Desktop icon appears in the corner of my screen.
“Hi I have connectivity but can’t resolve any domain names”
“Have you tried using your browser, maybe they just block pings”
“Well no because I can ping 8.8.8.8, see?”
“Hmm well have you tried from your browser?”
“Yes.”
“Maybe it’s just an issue with ping traffic”
“Well no because I’m not having issues with icmp traffic. I can still ping 8.8.8.8, see?”
“Hmm that’s weird”
*opens network config, renews dhcp lease*
“But I don’t think that’s relat...”
“I know!”
*opens my command prompt, flushes dns cache*
“But if this were a cache issue the requests wouldn’t take so long to tim...”
“I know.”
(Starting to think he doesn’t know)
“I’ll pass this on to the networking guys”
“Thanks”
Third time this has happened. Every time they claim they didn’t change anything and it fixed itself. Obviously this is not the case, because after networking guys “don’t change anything” it starts working again. Every time they talk to me like I have the technical prowess of an HR rep. Like somehow I’m the only software engineer in the world that doesn’t know what the ping command does.
I’m not upset though. They’re just giving me a great excuse to be completely unproductive on a Monday -
I was trying to set up my own "cloud" for iot experiments. I planned to use Intel Edison with mqtt broker (using mosca) and a node js app for providing API for mobiles and browser. And also to do other book keeping.
I spent the half day trying figure how to expose these servers to internet.
I configured ddns in noip.com and ddns settings configured to it in my router.
Port forwarded to the local server services I needed.
And then tested. Worked perfectly on any device in my router connected network. Tested on mobile network. Bam! It fucking doesn't work.
Then connected another router.
Double port forwarded. Again worked perfectly on router network. And failed on mobile.
Tested if ddns is right. Did nslookup it was fine as fuck.
Then disabled port forwarding. Did dmz. Nope. Nadda. No luck.
Then scratched my head so hard that I lost more already losing hairs.
Then remembered about router hardware firewall. Disabled it.
Tested
And there it didn't work.
My dreams shattered like a fucking deer hit by car on highway.
Didn't work.
Then I see the IP pointing to my router in nslookup. Its 172.20.xx.xx. Its a fucking private IP.
My Asshole ISP is running another private network behind firewall. Which I fucking can't port forward
Now I think how much of a noob and idiot I am. Fuck this shit. Fuck all of these shit.
I am going for SaaS option for mqtt broker.
(Or help me?)
Once again.
Asshole ISP.
Fuck your firewall.
(PS: I had test the next day. FML)2 -
I've been selected as an amazon echo tester for my country.
to agree fill this survey and you will receive a free Echo:
*fine*
do you have WiFi?
yes (you already know that i have a fire tv stick so you know even the password)
what mobile os do you have?
android (you already know also this i have the amazon app installed in it)
where do you live?
*my city* (you know that from ip address & shipping addresses)
imagine what them will now that i will introduces an open in mic in my room....
(i think that i will keep it behind firewall when i am not at home and when i dont want use it)1 -
So I'm building this environmental monitoring system for one of the Labs to monitor Temperature and Humidity. the "software" that comes as part of the package with these sensors is really just a website you host yourself if you don't choose the cloud option. No big deal really, (see my previous rant about getting windows server through SSC) I setup IIS and get the "software" registered get a couple sensors running looks good. However I don't like the error messages that popup because it's unsecured. do some reading and I find out that most browsers will give you a warning if your not using HTTPS even if it's for internal use only. OK we'll how hard can it be in implement encryption, turns out it's not that hard and you can do it for free how with letsencrypt and other places. I like free, now i have to use SSH to get into the server and run an ACME client. Hey open SSH is part of windows now cool, download an ACME client SSH into the server and nope doesn't work. Oh right I'm behind a corporate firewall and a bunch of other shit I can't control. Why is so damn arduous to setup this god dam internal website and the problems aren't even the site. Now I'm playing with AWS spinning up an instance to be able to try and get an SSL certificate just so i don't have to tell people it's OK to trust this site ignore the big angry warning.
Best part is other similar internal sites don;t use SSL and all have big messages about someone stealing your soul if you go there and these are commercial systems that run all the HVAC for all the campuses across Canada.
I need more Tylenol. -
I know it's all for good reason, but man are there so many hoops to jump through to get a web server set up through HTTPS. registering the domain, getting the SSL certs, configuring the DNS, setting up the firewall rules.. what a pain5
-
How do you use youtube in china? Asking for a muggle friend in a foreign exchange program. I sent a link to proxysite.com but the lack of response makes me wonder if that was a bad idea without further precaution. I've never configured a VPN before and Tor is a very bad idea here.4
-
Can we invent a firewall which blocks out all the shit about: woke, alt right, left, right, politics in general, global warming, aging of population and the rest of scary or extremely divisive stuff? I know which is impossible because of HTTPS but if it existed I would gladly install it on my home network.7
-
So I'm interested in building a Raspberry Pi stack at home to continue securing and adding my smart home capabilities, 👍
Have ideas for 2/3 but what else could I look to add?
1. Pi. Hole with cloudflared argo proxy for all DNS
2. Home Automation server
3. IPS / IDS like Bro or snort? Or firewall like pfsense?
4. Log server with Splunk agent from other pi's and router....
5. What else?
Ideas in the comments -
Part of my remote work is to have a daily call reporting in on what I have done yesterday and what I am about to today. My colleague calls me for it. She's hired as a tech support and is suddenly assigned to take note and report on my work activities to our boss. Several times, I caught her pretending to know what I'm talking about like with Puppet configurations, Firewall diagnosis packets, ActiveMQ, Regex, etc. Most of the time, I just let it go as its not my job to validate her knowledge on these different but many services. Just do the call, get the report in, carry on. How difficult was that?
Yesterday, our call was left sour because I somehow blew up. I think I've reached my patience with this woman's assumptions to how these services work. Now I feel guilty for yelling at a lady but goddamn she stoopid for fibbing through my ear. Somebody help! What do I do?
If I report to our boss about her technical incompetence (politely), she might get sacked. She's a good tech support as long as she still has her trusty manuals by her, she can fix specific problems. But when it comes to unknown tech to her, she assumed she knew.
If I tell her about her weaknesses, however constructive I can get and as politely as I can get, all the while complimenting something about her, showing her how to improve herself, maybe she'll do better not to ask silly questions like buying a Puppet certificate? At least getting rid of ignorance would definitely help but not sure how she would take it. The worst thing I would imagine is her backfiring and yelling at me and then we ended up fighting.
If I kept quiet and tuck it all into a can, it will eventually implode as we go on.
This is not about her gender. I don't see her as a woman. I see her as a tech support engineer who should know her stuff.1 -
Do you people anything about a processor with a firewall?
Because I just saw an episode of Arrow where they were trying to break into such a firewall!1 -
PCI DSS scan came back saying that WebDAV extensions need to be disabled. Kind of surprised, since I have other servers I’ve configured to standard and I can’t find anything in my notes about it.
In either case, been searching for info on how to fix it for 2 days and turned up nothing useful. Report found it on ports 80 and 443, so a firewall fix seems out here.
Running Plesk 17.5.3 on CentOS 7. Anyone have any pointers on how to get the job done?4 -
Lessons learned:
Dont fuck with firewall rules when intoxicated.
I was on a weekend, my mailserver was acting weird again.
I do my shizzle, git commit, push.... And it broke
And i was too far gone tp notice on time where the forward rules were broken... That made it stop completely
At least it was not an open firewall -
There is this local cloud service provider I used to like, since the promise was "it's from Africa" woi, they don't know shit. We tell then to open port 8888 ssh and 8899 since firewall is configured on their side, they close all ports then you can't ssh into the server. They take another 2 hours to fix that. Later on we change our ports and then tell them to change some ports, they open and close all ports (we discovered again because we were locked out again and had to d an nmap to see what was happening). Apparently the staff we we're talking to didn't know much about configuring servers only the senior management knew (I think to cut down costs), then we tell then to terminate services but they decide to bill us for another month (bullying) and gave us a warning letter from their lawyer for not paying for that month and since we are a small startup, we can't afford a court case which will drain us cash so we had to pay for shitty service and some month arr angry
-
Here's your Friday fun fact!
Too lazy to look up your current public IP?
ufw allow from `echo $SSH_CLIENT | awk '{ print $1}'` to any port 8080
A lifesaver for opening up the firewall when I'm too lazy to look the public IP of the coffee shop I'm at.1 -
From: https://cloud.google.com/vpc/docs/...
---
Updating firewall rules:
You can modify some components of a firewall rule, such as the specified protocols and ports for the match condition. You cannot modify a firewall rule's name, network, the action on match, and the direction of traffic.
If you need to change the name, network, or the action or direction component, you must delete the rule and create a new one instead.
---
REALLY???? goddamn delete and create a new rule to damn changing even its name???
And they wonder why their goddamn cloud won't take off? hell... how can this even be a Google product!!??5 -
lets try again.
What the fuck is with apache. Why I cannot start the page. it should be 5 minutes work.
but it give some shitty error where it is not clear what is wrong
This site can’t be reached timetracker.local’s server IP address could not be found.
Try:
Checking the connection
Checking the proxy, firewall, and DNS configuration
Running Windows Network Diagnostics
ERR_NAME_NOT_RESOLVED
how long apache is being developed? 10 years ? more? and cannot make normal error messages so you would know how to fix the problem . fuck that. I hate it so much. wasting my time. bastards.14 -
So I just got a Watchguard Firebox x500 for free. What should I do with it? And how do I set it up? (For a home network).3
-
Testing new server deployment in test env all works, then production it all breaks down. Network didn't allowed the right traffic. Took me whole week to find that out. Until some networking engineer said, you know there is a firewall between those networks?
-
Discovered yesterday that my company blocks IRC ports... Sad day. Why, why would you do this?! Oh the humanity! 😭1
-
1) DevGoogle - Google but all queries assume programming sense of query. Also option to add preferred language(s)
2) a universal file system so that my pen drive works on all devices
3) Firewall filter unblocks my personal domain (currently classified as 'Newly Observed Domain') -
I'm stuck in a really difficult spot in my office and I'm not sure if I should start looking elsewhere. Tldr; there's no defined hierarchy or career path in the web department leaving no position to be promoted to.
We've got 2 offices with now 150+ employees and for the last 2 years I've basically inherited the responsibilities of an IT manager. Planning and deploying our networks, firewall config, VPN setup, keeping users' systems functional, track equipment, order/setup systems for new employees. All of this in addition to my original job description of web developer, which has basically turned into maintaining client WordPress sites while the other developer builds sites.
I've spoken to our CTO (my supervisor) about how much time the IT stuff actually takes and some of my suggestions for the future to make sure we protect ourselves and future proof our systems the best we can and one of my suggestions was that we needed to create the IT manager position because he is usually in meetings or building out API integrations. He's behind the idea, or at least says so to me, but leadership doesn't believe it's needed because we "manage just fine as it is" (this does require 60 hours a week of work along with much automation that I wrote/built). But we're trying to open a 3rd office which means another 50+ employees and systems to manage as well as more websites as we sign more clients.
My pay has never been satisfactory where I am and based on the maximum raise each year it would take me another 10 years to make what I would like (that's calculating without cost of living increase) but they claim this is because I lack a formal degree (self taught). I love most of the people I work with, don't really have an issue with any of them (outside that they're stupid but that I can let that slide if they're trying), and they work with me and my health issues which cause me to miss significantly more office time than I would like. I've been here for 4 years and I've learned a lot but I don't feel like there's any upward mobility here. The only position I see in my department above me is the CTO (or possibly the new PM but that's not a position I want) and he's not going anywhere, and I firmly believe we need someone who can full-time stay on top of our infrastructure before we expand further.
I fantasize occasionally about leaving and finding something else, and there are plenty of opportunities online that I appear qualified for which pay more, but I worry that I'd be trading in something that really isn't all that bad for something that sucks and the only real perk is more money. I'd hate to go somewhere else and start back at the bottom again and have to prove myself yet again.5 -
Symfony 4:
I created a firewall with a user provider and everything was great for a year and a half.
I needed a second firewall with a different user provider for my REST API.
Being stateless, the rest api firewall didn't need the refreshUser method so I didn't bother doing anything inside but returning user (without noticing how my original class was built or the official documentation which apparently says I need to throw an exception if this isn't the right user provider for the user in the session).
I was having a problem with my main firewall after that point because I assumed it would only use the relevant user provider, but even though my API firewall only applied to a specific host/pattern, the user provider for that firewall was still being used. If it had run the supports method first, it wouldn't have done that even with my initial mistake. Frankly, I don't know why there is a supports method if it's not being utilized for this purpose...I saw supports() is used for the rememberme functionality, but seems inconsistent not to use it everywhere.
Not only should Symfony be updated to check the supports() method, but I also think it should only loop through user providers for the current applicable firewalls. Since we define a user provider per firewall, I think that would be the natural way for it to work. Otherwise why even define a user provider on the firewall if it's just going to try to use them all anyway?
Furthermore, in the case of a stateless firewall, requiring the refreshUser method via the interface seems strange. -
The company firewall blocking rabbitmq messages?!
WTF admins?!
Developing inside company structures is the pure fuck-up! -
A question or more discussion / looking for feedback.
Let's say we have
Application Firewall
- Application Routing
-- API Gateway
Then lots of containers.
Would you use host based routing in the containers?
It seems wrong to me, as in my opinion it breaks the boundary the API gateway provides.
Maybe someone can share his experience, I'd be delighted.5 -
Anyone use firewall / WAF for their Nginx?
I found NAXSI (https://github.com/nbs-system/...) , Let hope it not going to f**k-up the production system1 -
Storytime - The Prometheus tales - Part III (I think..).
Updated the node definitions on the old node today, just to keep it up to date. nothing fancy.
I went to the new node and and checked the setup again. I already had roughly 120 node definitions onboard for testing purposes.
so all firewalls should have been configured the right way, so that the wee one might celebrate the marriage with the rest of the gang finally.. and then went with "puppet YOLO" on the new node. added every fkn node definition to the new setup.
every node turned out just to be fine.
except for 137 little InstanceDown alerts (out of 600+).
it's a good thing, that the little fella can send mails to me, myself and I only for the time being.
so debugging. again. but at least it's not a problem related to prometheus itself, because the connections end with a timeout on the related nodes. should be more like a firewall fubar.
we will see.5 -
II encountered this problem today with a user who couldn't access internet on their own home network or on their company. Everytime they try to access the site. Firewall and Anti-virus settings have blocked the access . Couldn't remote into their PC due to them not being on the domain to setup the VPN client. Reset Browser settings and disabled all Firewall and Anti-virus protocols. User still could not get to any sites..... What did I miss?1
-
Windows why do I need to explicitly tell you in a firewall rule to allow port 80 to allow someone in the same NAT as me which is set to a private network to access the web server?4
-
hey peeps, 2 questions:
1. do you know about some kind of firewall/antivirus for pc that can just allow the user to accept/block an internet request , like no root firewall does for android.
I have been using that simple, beautiful piece of open source for last 2ish years. The way it sends a notification when an app tries to make an internet request(even in the background!) has helped me detect and remove so many viruses.
2. i am thinking of doing a factory reset on my windows. My laptop came loaded with win10 and office , and i don't have the keys for it( it shows a special partition having some backup of window i guess?). So i had a couple of thoughts:
- will my office get removed?[i don't want this]
- I created several other partitions( d,e,f,p) would they go back as a single C drive?[doesn't effect me as long as i can create them again]
- the languages and modules i installed via cmd(java/python/ruby/pip modules/git/etc), would they also get removed? [i really want that]
- i am probably thinking this won't happen, but is their a possibility that the recovery partition that my windows came with, would also get removed[ i don't want that]7 -
when one tool says your site is 200 from chinese IPs, but another says its 403 for the same IPs...
which one is it? -
AAAAAAAAAAAA
Why is firewall management in Saltstack such a huge pain in the a**?!
I have to write soooooo much to just add a single rule, and then I have to test for its presence, so that it's not continuously added again and again with every run T-T
I swear, for firewall deployments, Saltstack frickin' sucks! -
Can someone answer me a question about Wireguard?
I couldn't find an answer to it online.
I know WG supports roaming, so switching a connection to a different route.
But how does WG handle multiple valid routes, before a connection can be established?
Eg, when I'm at home I could have 3 valid routes.
Connecting over LAN.
Connecting over public IP of the router.
Connecting to a vserver, using it as a bridge to connect to my server, if it's behind a firewall.4 -
Need advice about protecting ddos via iptables and whitelisting. Currently I launched my gameserver and am fighting against a massive attack of botnets. Problem was solved by closing all ports on my gameserver linux machine and shipping game.exe with injected c++ socket client. So basically only gamers who launch my game exe are being added to firewall iptables via the socket client that is provided in the game exe. If some ddosers still manage to get inside and ddos then my protection is good enough to handle attacks from whitelisted ips from inside. Now I have another problem. Lots of players have problems and for some reason shipped c++ client fails to connect to my socketserver. Currently my solution was to provide support in all contact channels (facebook,skype,email) and add those peoples ips to whitelist manually. My best solution would be to make a button in website which you can click and your ip is whitelisted auromatically. However if it will be so easy then botnets can whitelist themselves as well. Can you advice me how I could handle whitelisting my players through web or some other exe in a way that it cant be replicated by botnets?1
-
imagine you "manage" your applications firewall rules by writing them into spreadsheets and sending them to the fw-admins to implement them
imagine they don't implement exactly what you tell them / implement rules for you that you did not ask for
also imagine it is crucial that you have a reliable source of information about what firewall rules are and are not implemented for your application, because the firewall-guys cant simply check and tell you what rules are implemented for your application
:o2