Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "hashes"
-
I had a secondary Gmail account with a really nice short nickname (from the early invite/alpha days), forwarded to another of my mailboxes. It had a weak password, leaked as part of one of the many database leaks.
Eventually I noticed some dude in Brazil started using my Gmail, and he changed the password — but I still got a copy of everything he did through the forwarding rule. I caught him bragging to a friend on how he cracked hashes and stole and sold email accounts and user details in bulk.
He used my account as his main email account. Over the years I saw more and more personal details getting through. Eventually I received a mail with a plaintext password... which he also used for a PayPal account, coupled to a Mastercard.
I used a local website to send him a giant expensive bouquet of flowers with a box of chocolates, using his own PayPal and the default shipping address.
I included a card:
"Congratulations on acquiring my Gmail account, even if I'm 7 years late. Thanks for letting me be such an integral part of your life, for letting me know who you are, what you buy, how much you earn, who your family and friends are and where you live. I've surprised your mother with a cruise ticket as you mentioned on Facebook how sorry you were that you forgot her birthday and couldn't buy her a nice present. She seems like a lovely woman. I've also made a $1000 donation in your name to the EFF, to celebrate our distant friendship"31 -
Please for the love of god name your variables in a sensible way! How the FUCK am I supposed to read your shitcode if you decide to write 6 (!!!) nested loops with variables each named by exactly one character. With no comments whatsoever!
I would rather crack password hashes than this nonsense.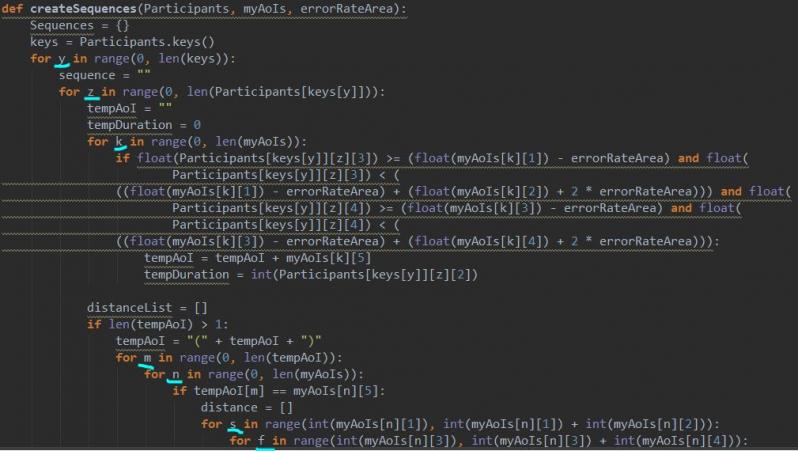 13
13 -
Oh fuck and boy Jesus, how on earth is this still a thing 😦
MD fucking 5 is not a fucking “secure” crypto algorithm.
This site has 14 million breached accounts with fucking MD5 hashes.
I think I’ve had to much internet for today.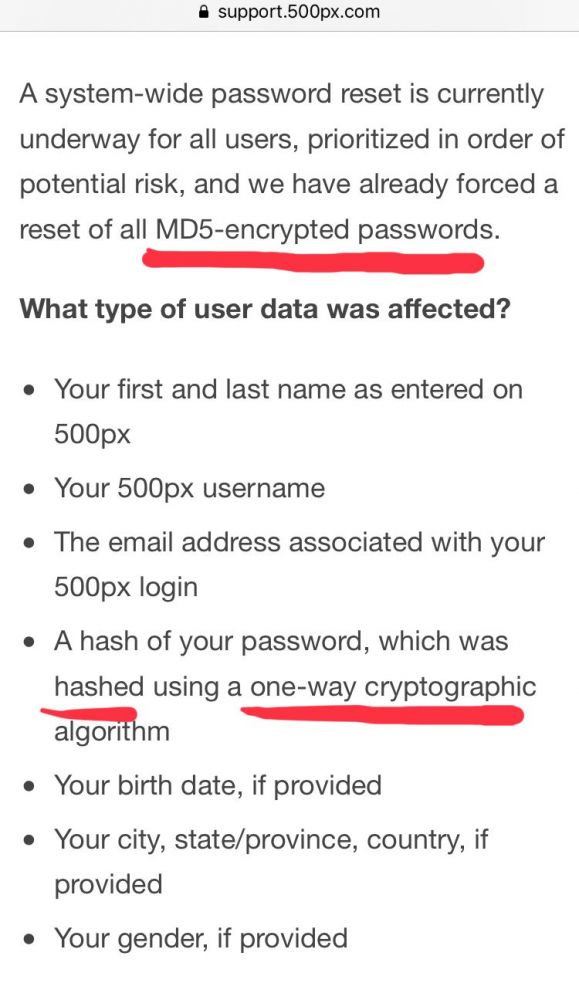 17
17 -
I wrote a database migration to add a column to a table and populated that column upon record creation.
But the code is so freaking convoluted that it took me four days of clawing my eyes out to manage this.
BUT IT'S FINALLY DONE.
FREAKING YAY.
Why so long, you ask? Just how convoluted could this possibly be? Follow my lead ~
There's an API to create a gift. (Possibly more; I have no bloody clue.)
I needed the mobile dev contractor to tell me which APIs he uses because there are lots of unused ones, and no reasoning to their naming, nor comments telling me what they do.
This API takes the supplied gift params, cherry-picks a few bits of useful data out (by passing both hashes by reference to several methods), replaces a couple of them with lookups / class instances (more pass-by-reference nonsense). After all of this, it logs the resulting (and very different) mess, and happily declares it the original supplied params. Utterly useless for basically everything, and so very wrong.
It then uses this data to call GiftSale#create, which returns an instance of GiftSale (that's actually a Gift; more on that soon).
GiftSale inherits from Gift, and redefines three of its methods.
GiftSale#create performs a lot of validations / data massaging, some by reference, some not. It uses `super` to call Gift#create which actually maps to the constructor Gift#initialize.
Gift#initialize calls Gift#pre_init (passing the data by reference again), which does nothing and returns null. But remember: GiftSale inherits from Gift, meaning GiftSale#pre_init supersedes Gift#pre_init, so that one is called instead. GiftSale#pre_init returns a Stripe charge object upon success, or a Gift (and a log entry containing '500 Internal') upon failure. But this is irrelevant because the return value is never actually used. Pass by reference, remember? I didn't.
We're now back at Gift#initialize, Rails finally creates a Gift object using the args modified [mostly] in-place by all of the above.
Another step back and we're at GiftSale#create again. This method returns either the shiny new Gift object or an error string (???), and the API logic branches on its type. For further confusion: not all of the method's returns are explicit, and those implicit return values are nested three levels deep. (In Ruby, a method will return the last executed line's return value automatically, allowing e.g. `def add(a,b); a+b; end`)
So, to summarize: GiftSale#create jumps back and forth between Gift five times before finally creating a Gift instance, and each jump further modifies the supplied params in-place.
Also. There are no rescue/catch blocks, meaning any issue with any of the above results in a 500. (A real 500, not a fake 500 like last time. A real 500, with tragic consequences.)
If you're having trouble following the above... yep! That's why it took FOUR FREAKING DAYS! I had no tests, no documentation, no already-built way of testing the API, and no idea what data to send it. especially considering it requires data from Stripe. It also requires an active session token + user data, and I likewise had no login API tests, documentation, logging, no idea how to create a user ... fucking hell, it's a mess.)
Also, and quite confusingly:
There's a class for GiftSale, but there's no table for it.
Gift and GiftSale are completely interchangeable except for their #create methods.
So, why does GiftSale exist?
I have no bloody idea.
All it seems to do is make everything far more complicated than it needs to be.
Anyway. My total commit?
Six lines.
IN FOUR FUCKING DAYS!
AHSKJGHALSKHGLKAHDSGJKASGH.7 -
Paranoid Developers - It's a long one
Backstory: I was a freelance web developer when I managed to land a place on a cyber security program with who I consider to be the world leaders in the field (details deliberately withheld; who's paranoid now?). Other than the basic security practices of web dev, my experience with Cyber was limited to the OU introduction course, so I was wholly unprepared for the level of, occasionally hysterical, paranoia that my fellow cohort seemed to perpetually live in. The following is a collection of stories from several of these people, because if I only wrote about one they would accuse me of providing too much data allowing an attacker to aggregate and steal their identity. They do use devrant so if you're reading this, know that I love you and that something is wrong with you.
That time when...
He wrote a social media network with end-to-end encryption before it was cool.
He wrote custom 64kb encryption for his academic HDD.
He removed the 3 HDD from his desktop and stored them in a safe, whenever he left the house.
He set up a pfsense virtualbox with a firewall policy to block the port the student monitoring software used (effectively rendering it useless and definitely in breach of the IT policy).
He used only hashes of passwords as passwords (which isn't actually good).
He kept a drill on the desk ready to destroy his HDD at a moments notice.
He started developing a device to drill through his HDD when he pushed a button. May or may not have finished it.
He set up a new email account for each individual online service.
He hosted a website from his own home server so he didn't have to host the files elsewhere (which is just awful for home network security).
He unplugged the home router and began scanning his devices and manually searching through the process list when his music stopped playing on the laptop several times (turns out he had a wobbly spacebar and the shaking washing machine provided enough jittering for a button press).
He brought his own privacy screen to work (remember, this is a security place, with like background checks and all sorts).
He gave his C programming coursework (a simple messaging program) 2048 bit encryption, which was not required.
He wrote a custom encryption for his other C programming coursework as well as writing out the enigma encryption because there was no library, again not required.
He bought a burner phone to visit the capital city.
He bought a burner phone whenever he left his hometown come to think of it.
He bought a smartphone online, wiped it and installed new firmware (it was Chinese; I'm not saying anything about the Chinese, you're the one thinking it).
He bought a smartphone and installed Kali Linux NetHunter so he could test WiFi networks he connected to before using them on his personal device.
(You might be noticing it's all he's. Maybe it is, maybe it isn't).
He ate a sim card.
He brought a balaclava to pentesting training (it was pretty meme).
He printed out his source code as a manual read-only method.
He made a rule on his academic email to block incoming mail from the academic body (to be fair this is a good spam policy).
He withdraws money from a different cashpoint everytime to avoid patterns in his behaviour (the irony).
He reported someone for hacking the centre's network when they built their own website for practice using XAMMP.
I'm going to stop there. I could tell you so many more stories about these guys, some about them being paranoid and some about the stupid antics Cyber Security and Information Assurance students get up to. Well done for making it this far. Hope you enjoyed it. 26
26 -
I'm fixing a security exploit, and it's a goddamn mountain of fuckups.
First, some idiot (read: the legendary dev himself) decided to use a gem to do some basic fucking searching instead of writing a simple fucking query.
Second, security ... didn't just drop the ball, they shit on it and flushed it down the toilet. The gem in question allows users to search by FUCKING EVERYTHING on EVERY FUCKING TABLE IN THE DB using really nice tools, actually, that let you do fancy things like traverse all the internal associations to find the users table, then list all users whose password reset hashes begin with "a" then "ab" then "abc" ... Want to steal an account? Hell, want to automate stealing all accounts? Only takes a few hundred requests apiece! Oooh, there's CC data, too, and its encryption keys!
Third, the gem does actually allow whitelisting associations, methods, etc. but ... well, the documentation actually recommends against it for whatever fucking reason, and that whitelisting is about as fine-grained as a club. You wanna restrict it to accessing the "name" column, but it needs to access both the "site" and "user" tables? Cool, users can now access site.name AND user.name... which is PII and totally leads to hefty fines. Thanks!
Fourth. If the gem can't access something thanks to the whitelist, it doesn't catch the exception and give you a useful error message or anything, no way. It just throws NoMethodErrors because fuck you. Good luck figuring out what they mean, especially if you have no idea you're even using the fucking thing.
Fifth. Thanks to the follower mentality prevalent in this hellhole, this shit is now used in a lot of places (and all indirectly!) so there's no searching for uses. Once I banhammer everything... well, loads of shit is going to break, and I won't have a fucking clue where because very few of these brainless sheep write decent test coverage (or even fucking write view tests), so I'll be doing tons of manual fucking testing. Oh, and I only have a week to finish everything, because fucking of course.
So, in summary. The stupid and lazy (and legendary!) dev fucked up. The stupid gem's author fucked up, and kept fucking up. The stupid devs followed the first fuckup's lead and repeated his fuck up, and fucked up on their own some more. It's fuckups all the fucking way down.rant security exploit root swears a lot actually root swears oh my stupid fucking people what the fuck fucking stupid fucking people20 -
!rant
!!pride
I tried finding a gem that would give me a nice, simple diff between two hashes, and also report any missing keys between them. (In an effort to reduce the ridiculous number of update api calls sent out at work.)
I found a few gems that give way too complicated diffs, and they're all several hundred lines long. One of them even writes the diff out in freaking html with colors and everything. it's crazy. Several of the simpler ones don't even support nesting, and another only diffs strings. I found a few possibly-okay choices, but their output is crazy long, and they are none too short, either.
Also, only a few of them support missing keys (since hashes in Ruby return `nil` by default for non-defined keys), which would lead to false negatives.
So... I wrote my own.
It supports diffing anything with anything else, and recurses into anything enumerable. It also supports missing keys/indexes, mixed n-level nesting, missing branches, nil vs "nil" with obvious output, comparing mixed types, empty objects, etc. Returns a simple [a,b] diff array for simple objects, or for nested objects: a flat hash with full paths (like "[key][subkey][12][sub-subkey]") as top-level keys and the diff arrays as values. Tiny output. Took 36 lines and a little over an hour.
I'm pretty happy with myself. 😁6 -
I like coding at night, nobody bothers you... Anyway, I'll never forget when I had to write a Huffman compressor(and decompressor) in C for a school project. It was New Year's Eve of 2016, as fireworks were blowing outside the window of my room, I was fixing bugs. Then, around 4am, I fixed all the bugs. I felt exhilarated as I started compressing and decompressing random images on the internet, comparing hashes.
One of the best New Year's Eve ever... Don't look at me like that... I like being weird.3 -
I've been lurking on devrant a while now, I figure it's time to add my first rant.
Little background and setting a frame of reference for the rant: I'm currently a software engineer in the bioinformatics field. I have a computer science background whereas a vast majority of those around me, especially other devs, are people with little to no formal computer background - mostly biology in some form or another. Now, this said, a lot of the other devs are excellent developers, but some are as bad as you could imagine.
I started at a new company in April. About a month after joining a dev who worked there left, and I inherited the pipeline he maintained. Primarily 3 perl scripts (yes, perl, welcome to bioinformatics, especially when it comes to legacy code like is seen in this pipeline) that mostly copied and generated some files and reports in different places. No biggie, until I really dove in.
This dev, which I barely feel he deserves to be called, is a biology major turned computer developer. He was hired at this company and learned to program on the job. That being said, I give him a bit of a pass as I'm sure he did not have had an adequate support structure to teach him any better, but still, some of this is BS.
One final note: not all of the code, especially a lot of the stupid logic, in this pipeline was developed by this other dev. A lot of it he adopted himself. However, he did nothing about it either, so I put fault on him.
Now, let's start.
1. perl - yay bioinformatics
2. Redundant code. Like, you literally copied 200+ lines of code into a function to change 3 lines in that code for a different condition, and added if(condition) {function();} else {existing code;}?? Seriously??
3. Whitesmiths indentation style.. why? Just, why? Fuck off with that. Where did you learn that and why do you insist on using it??
4. Mixing of whitesmiths and more common K&R indentation.
5. Fucked indentation. Code either not indented and even some code indented THE WRONG WAY
6. 10+ indentation levels. This, not "terrible" normally, but imagine this with the last 3 points. Cannot follow the code at freaking all.
7. Stupid logic. Like, for example, check if a string has a comma in it. If it does, split the string on the comma and push everything to an array. If not, just push the string to the array.... You, you know you can just split the string on the comma and push it, right?? If there is no comma it will be an array containing the original string.. Why the fuck did you think you needed to add a condition for that??
8. Functions that are called to set values in global variables, arrays, and hashes.. function has like 5 lines in it and is called in 2 locations. Just keep that code in place!
9. 50+ global variables/hashes/arrays in one of the scripts with no clear way to tell how/when values are set nor what they are used for.
10. Non-descriptive names for everything
11. Next to no comments in the code. What comments there are are barely useful.
12. No documentation
There's more, but this is all I can think to identify right now. All together these issues have made this pipeline the pinnacle of all the garbage that I've had to work on.
Attaching some screenshots of just a tiny fraction of the code to show some of the crap I'm talking about. 6
6 -
Client from a big company requested that all sensible data should be encrypted, passwords included.
We agreed that was OK, and that we were already saving the hashes for the passwords.
The reply was "Hashes should be encrypted too"4 -
College rant:
I have finals next week. I am sitting here learning about things which have no benefit to my career. My college requires me to take Calculus based physics 2, which makes no sense to me at all! I do appreciate physics however I would much rather be coding. In my CS courses you learn theory which is fine, however very impractical. I last October I realized how much more you need to do and a degree just won't cut it. I spend about 50 hours a week learning TDD, git, hashes all this stuff that is not taught in school. Then on top of this I'm learning pointless crap that if I ever needed in a real world situation I would go to Kahn Academy or simply Google it. I'm upset because I have to stop coding for the week to study information I will forget 2 weeks from now, and most likely never use again. I have a job someone offered me which will be extremely beneficial to my career however I have to wait a week to even look at it. I'm just bitter.23 -
Oh fuck, Germany wants to pull an Australia and force services-providers to disclose passwords, password-hashes,... to law enforcement.13
-
I'd never do anything "risky" in a prod environment if I considered it so at the time, but in retrospect there's *lots* of things considered risky now (both from a security and good practice viewpoint) that were standard practice not long ago:
- Not using any form of version control
- No tests (including no unit tests)
- Not considering XSS vulnerabilities
- Completely ignoring CSRF vulnerabilities
- Storing passwords as unsalted MD5 hashes (heck that was considered very *secure* in the days of plaintext password storage.)
...etc. I'm guilty of all of those previously. I daresay in the future there will be yet more things that may be standard practice now, but become taboos we look back on with similar disdain.1 -
Hey, been gone a hot minute from devrant, so I thought I'd say hi to Demolishun, atheist, Lensflare, Root, kobenz, score, jestdotty, figoore, cafecortado, typosaurus, and the raft of other people I've met along the way and got to know somewhat.
All of you have been really good.
And while I'm here its time for maaaaaaaaath.
So I decided to horribly mutilate the concept of bloom filters.
If you don't know what that is, you take two random numbers, m, and p, both prime, where m < p, and it generate two numbers a and b, that output a function. That function is a hash.
Normally you'd have say five to ten different hashes.
A bloom filter lets you probabilistic-ally say whether you've seen something before, with no false negatives.
It lets you do this very space efficiently, with some caveats.
Each hash function should be uniformly distributed (any value input to it is likely to be mapped to any other value).
Then you interpret these output values as bit indexes.
So Hi might output [0, 1, 0, 0, 0]
while Hj outputs [0, 0, 0, 1, 0]
and Hk outputs [1, 0, 0, 0, 0]
producing [1, 1, 0, 1, 0]
And if your bloom filter has bits set in all those places, congratulations, you've seen that number before.
It's used by big companies like google to prevent re-indexing pages they've already seen, among other things.
Well I thought, what if instead of using it as a has-been-seen-before filter, we mangled its purpose until a square peg fit in a round hole?
Not long after I went and wrote a script that 1. generates data, 2. generates a hash function to encode it. 3. finds a hash function that reverses the encoding.
And it just works. Reversible hashes.
Of course you can't use it for compression strictly, not under normal circumstances, but these aren't normal circumstances.
The first thing I tried was finding a hash function h0, that predicts each subsequent value in a list given the previous value. This doesn't work because of hash collisions by default. A value like 731 might map to 64 in one place, and a later value might map to 453, so trying to invert the output to get the original sequence out would lead to branching. It occurs to me just now we might use a checkpointing system, with lookahead to see if a branch is the correct one, but I digress, I tried some other things first.
The next problem was 1. long sequences are slow to generate. I solved this by tuning the amount of iterations of the outer and inner loop. We find h0 first, and then h1 and put all the inputs through h0 to generate an intermediate list, and then put them through h1, and see if the output of h1 matches the original input. If it does, we return h0, and h1. It turns out it can take inordinate amounts of time if h0 lands on a hash function that doesn't play well with h1, so the next step was 2. adding an error margin. It turns out something fun happens, where if you allow a sequence generated by h1 (the decoder) to match *within* an error margin, under a certain error value, it'll find potential hash functions hn such that the outputs of h1 are *always* the same distance from their parent values in the original input to h0. This becomes our salt value k.
So our hash-function generate called encoder_decoder() or 'ed' (lol two letter functions), also calculates the k value and outputs that along with the hash functions for our data.
This is all well and good but what if we want to go further? With a few tweaks, along with taking output values, converting to binary, and left-padding each value with 0s, we can then calculate shannon entropy in its most essential form.
Turns out with tens of thousands of values (and tens of thousands of bits), the output of h1 with the salt, has a higher entropy than the original input. Meaning finding an h1 and h0 hash function for your data is equivalent to compression below the known shannon limit.
By how much?
Approximately 0.15%
Of course this doesn't factor in the five numbers you need, a0, and b0 to define h0, a1, and b1 to define h1, and the salt value, so it probably works out to the same. I'd like to see what the savings are with even larger sets though.
Next I said, well what if we COULD compress our data further?
What if all we needed were the numbers to define our hash functions, a starting value, a salt, and a number to represent 'depth'?
What if we could rearrange this system so we *could* use the starting value to represent n subsequent elements of our input x?
And thats what I did.
We break the input into blocks of 15-25 items, b/c thats the fastest to work with and find hashes for.
We then follow the math, to get a block which is
H0, H1, H2, H3, depth (how many items our 1st item will reproduce), & a starting value or 1stitem in this slice of our input.
x goes into h0, giving us y. y goes into h1 -> z, z into h2 -> y, y into h3, giving us back x.
The rest is in the image.
Anyway good to see you all again. 20
20 -
I was thinking about how I implement login functionality, and realised I have no clue how I came up with it so decided to ask if it was a good way to do things.
Basically, client logs in, username/email and pass are sent to server.
Server salts and hashes password and checks it against the one in the database for that user.
If its correct, send the client the user ID and the user token. (User id could be username, or a number, it depends)
When that client makes a request, the request must contain the ID and token.
The server checks that the ID and token combo are correct, and because the ID is linked to the user we know who it is and can complete the request.
Usually I make the token a random string of 16 or 32 chars, each account has their own token, and it may be stored in the browser so they stay logged in. I also normally add a "log out everywhere" button, which essentially just generates a new token to overrides the current one, making any previously saved tokens invalid.8 -
PHP implicitely coercing password hashes to floats in comparisons is always a fun one
http://phpsadness.com/sad/4712 -
recently i prided myself in my high ability to google stuff but i just blank at this problem:
i have 4 HDDs with my photos on it. They are more or less backups of each other, but not quite. The folder structure is convoluted and i am dreading this task since years. I now want to move to a better backup culture and save the data i really care about.
Problem: i may or may not inserted new photos in some versions of the hdds and not in others. So they are like [Photo1], [Photo2], [Photo3] and [Photo4] but [Photo1] contains a,b and d content, [Photo2] contains a and b but not d, [Photo3] contains c.
Now i would like a program that just takes hashes of all files present and compares them and finds differences among those 4 folders so i can combine them in each other. Additional problem points for a being in a different subfolder on [Photo1] as in [Photo2]
Its probably some backup software that can that, but i dont know which one.
Whelp?11 -
My Vega56 gpu is mining a bit faster than usual after the last reset. Not by a huge amount, but a little faster. Enough for it to be noticeable.
I don't wanna touch it. I just wanna let it sit there and happily chew away those hashes.
But I will have to touch it eventually, if I wanna turn my monitor off. If I wanna go to sleep.
Doing that will trigger a restart of the miner.
And I will never know if it will have that extra lil speed bump ever again.
Why is life so cruel2 -
ChatGPT, Copilot, React, how to make a link in a frontend website?
To create a link in a frontend website, create a span, a div, or a paragraph that contains the link text. In your JavaScript web app, add an event listener to that element that opens the link on click. If you want to claim you're accessible, add an aria-role to the clickable element. To make debugging harder and only possible for the real arcane experts, let your framework generate generic ids and class name hashes for styling and event handling, like "item_09fcfck" or "elementor_element_foo_bar". Avoid, at all price, to use an a href element!2 -
Hey there people, I have a few questions regarding neo4j. Your experience could also be very useful to me here @dfox.
1. Is neo4j good for storing user data, like password hashes, etc.. In addition to the regular relationships with other components of the ecosystem
2. Is neo4j good enough to accommodate a really large number of users..
3. Does DevRant use a dual database, like user info in Mongo and relationships like comments and ++ on neo4j or is it like everything on neo4j
For q.3, if you're not @dfox then just provide an idea of how you would handle the situation.7 -
I upgraded a Linux server one time and data that was serialized in yaml stopped being parsed properly.
It turns out the libyaml people decided to change how hashes were handled, which made any previous hashes come back as blank.
A whole database of valid data in dev was coming back invalid in prod. It was maddening.
It took a day to figure out the problem and how to update the data to the new format in rails.
I now serialize in json.11 -
!rant
Just got a message from a recruiter. It was something different. There was a link with a ZIP file and a bunch of files in it. Plus two MD5 hashes. You should now find the correct private key and the encrypted message to decrypt it with the key. This gave you the password to get further in the application process.
Not particularly difficult, but a refreshing change from the usual blah blah.1 -
If I were to change all my passwords into hashes (so take a random word and hash it, ex 'table') and then use those on various websites, would people ever guess that my password is _an actual hash_ rather than a password in hashed form if they were to see it? Would such a meta-hash be safer if 'hackers' were to find it unencrypted?8
-
Trying out the new version of fasm, I realize it's good, and conclude I should update my code to work with it as there's small incompatibilities with the syntax.
So, quick flat assembler lesson: the macro system is freaking nuts, but there are limitations on the old version.
One issue, for instance, is recursive macros aren't easily possible. By "easily" I mean without resorting to black magic, of course. Utilizing the arcane power of crack, I can automatically define the same macro multiple times, up to a maximum recursion depth. But it's a flimsy patch, on top of stupid, and also has limitations. New version fixes this.
Another problem is capturing lines of code. It's not impossible, again, but a pain in the ass that requires too much drug-addled wizardry to deal with. Also fixed in new version.
Why would you want to capture lines of code? Well, because I can do this, for instance:
macro parse line {
··match a =+ b , line \{
····add a,b;
··\}
};
You can process lines of code like this. The above is a trivial example that makes no fucking sense, but essentially the assembler allows you define your own syntax, and with sufficient patience, you can use this feature to develop absolutely super fucking humongous galactic unrolls, so it's a fantastic code emitter.
Anyway, the third major issue is `{}` curlies have to be escaped according to the nesting level as seen in the example; this is due to a parser limitation. [#] hashes and [`] backticks, which are used to concatenate and stringify tokens respectively, have to be escaped as well depending on the nesting level at which the token originates. This was also fixed.
There's other minor problems but that gives you sufficient context. What happens is the new version of fasm fixes all of these problems that were either annoying me, forcing me to write much more mystical code than I'd normally agree to, and in some rare cases even limiting me in what I could do...
But "limiting" needs to be contextualized as well: I understand fasm macros well enough to write a virtual machine with them. Wish I was kidding. I called it the Arcane 9 Machine, A9M for short. Here, bitch was the prototype for the VM my fucking compiler uses: https://github.com/Liebranca/forge/...
So how am I """limited""", then? You wouldn't understand. As much as I hate to say it, that which should immediately be called into question, you're gonna have to trust me. There are many further extravagant affronts to humanity that I yearn to commit with absolute impunity, and I will NOT be DENIED.
Point is code can be rewritten in much simpler, shorter, cleaner form.
Logic can be much more intricate and sophisticated.
Recursion is no longer a problem.
Namespaces are now a thing.
Capturing -- and processing -- lines of code is easier than ever...
Nearly every problem I had with fasm is gone with this update: thusly, my power grows rather... exponentially.
And I SWEAR that I will NOT use it for good. I shall be the most corrupt, bloodthirsty, deranged tyrant ever known to this accursed digital landscape of broken souls and forgotten dreams.
*I* will reforge the world with black smoldering flame.
*I* will bury my enemies in ill-and-damned obsidian caskets.
And *I* will feed their armies to a gigantic, ravenous mass grave...
Yes... YES! This is the moment!
PREPARE THE RITUAL ROOM (https://youtube.com/watch/...)
Couriers! Ride towards the homeland! Bring word of our success.
And you, page, fetch me my sombersteel graver...
I shall inscribe the spell into these very walls...
in the ELEVENTH degree!
** MANIACAL EVIL LAUGHTER ** -
I vibecoded ransomware that replaced files with their hashes instead of encrypting them and now Raytheon begs me to accept $12M ransom help1
-
I decided to run the ROCKYOU password list to see if there are any patterns in md5 hashing, not sure why but I am starting to confuse myself and I need a new pair of eyes to have a look.
in advance, sorry for the shitty image, that lappy is a temporary solution.
So the very accurate and not bias numbers show that the letter "0" appears more than the rest, would there be any use in let's say ordering the wordlist with words that have the most "0" and "7" in their hash to appear at the top?
I believe I might be trying to stretch the numbers and see a pattern where there is none but its worth a shot I think.
Note:
- These numbers come from only about ~14m words
My thinking trail is that if statisticaly these hashes are more likely to appear, they are more likely to be the one I am looking for? 3
3 -
How do you approach generating "random" unique numbers/strings ? Exactly, when you have to be sure the generated stuff is unique overtime? Eg. as few collisions in future as possible.
Now I don't mean UUIDs but when there is a functionality that needs some length defined, symbol specific and definitely unique data, every time it does it's stuff.
TLDR STORY: Generating 8 digits long numbers so they are (deterministically - wink wink) unique is hard but Format Preserving Encryption saves the day. (for me)
FULL STORY:
I had to deal with both strings and codes today.
One was to generate shortlink word for url, luckily found a library that does exactly this. (Hashids)
BUT generating 8 digits long, somewhat random number was harder then I thought, found out on SO something like "sha256(seed) => bytes => ascii/numbers mangling" but that had a lot of collisions because of how the hash got mangled to actually output numbers and also to fit the length.
After some hours I stumbled upon Format Preserving encryption (pyffx) and man it did what I wanted and it had max 2 collisions in 100k values. Still the solution with this feels hacky af. (encrypting straddled unix timestamp with lots of decimals)6 -
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
eleven billion, seven hundred twenty-three million, five hundred twelve thousand, three hundred sixty-eight hashes later and I still haven't found the vanity address I'm looking for 😴...
-
Am doing an online shop for some client as a side project. The client never requested a module enabling an admin user to manipulate listed products. Now this cheap genius wants to be able to login as a seller and manipulate whatever products they've listed. So I told the client it's not possible to do that because passwords are stored as hashes. Now, can you Guess who's storing clear text passwords ?
May shit never hits the fan.3 -
What is the difference between a hacker and a phoenix ?
None, they feel both alive again when they are back from hashes. -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
So I realized if done correctly, an autoencoder is really just a bootleg token dictionary.
If we take some input, and pass it through a custom hashfunction that strictly produces hashes with only digits as output, then we can train a network, store the weights and biases, and then train a decoder on top of that.
Using random drop out on the input-output pairs, we can do distillation of the weights and biases to find subgraphs that further condense this embedding.
Why have a token dictionary at all?9 -
Serious biased question:
What's the newschool way of storing passwords now that everyone is against the known hashes?
Would prefer storing it in a good 'ol database tho pls.12 -
>making bruteforce MD5 collision engine in Python 2 (requires MD5 and size of original data, partial-file bruteforce coming soon)
>actually going well, in the ballpark of 8500 urandom-filled tries/sec for 10 bytes (because urandom may find it faster than a zero-to-FF fill due to in-practice files not having many 00 bytes)
>never resolves
>SOMEHOW manages to cut off the first 2 chars of all generated MD5 hashes
>fuck, fixed
>implemented tries/sec counter at either successful collision or KeyboardInterrupt
>implemented "wasted roll" (duplicate urandom rolls) counter at either collision success or KeyboardInterrupt
>...wait
>wasted roll counter is always at either 0% or 99%
>spend 2 hours fucking up a simple percentage calculation
>finally fixed
>implement pre-bruteforce calculation of maximum try count assuming 5% wasted rolls (after a couple hours of work for one equation because factorials)
>takes longer than the bruteforce itself for 10 bytes
this has been a rollercoaster but damn it's looking decent so far. Next is trying to further speed things up using Cython! (owait no, MicroPeni$ paywalled me from Visual Studio fucking 2010)4 -
Hey all. So I'm a bit of an aspiring developer/engineer. I am in highschool right now and am getting to the point where I should start looking at colleges. Ive wanted to do something computer related and for a while now ive had my heart set on some sort of security engineer/tech/researcher what have you. But it has been pointed out to me that computer sciences often require several high level math courses namely Calc. Problem being I'm pretty bad at Calc and haven't been able to do too well.
I'm not too sure what I should do. I'm struggling with my highschool calc classes and and fear that college level course will just go over my head. Ive never had issues with math before until I got to Calc. Ive got some of the basics of cryptography such as hashes and cryptographic alorithms but thats about it. Do computer science degrees really rely that heavily on Calc?7 -
Have to translate an API library from Ruby into PHP for work, and I swear it's all of the worst pieces of BASIC and Swift thrown together. To top it off, looking up a symbol chart for it to try and get a handle on the symbols they love to throw in front of variable and method names is useless because "symbol" is a freaking type in this language! Arrays are apparently called "hashes" now, and I can't quite tell if modules are supposed to be namespaces or classes yet...
If Ruby has redeeming qualities, I'm definitely open to hearing them. Right now I'm kind of feeling homesick for vanilla C, however...1 -
Relatively often the OpenLDAP server (slapd) behaves a bit strange.
While it is little bit slow (I didn't do a benchmark but Active Directory seemed to be a bit faster but has other quirks is Windows only) with a small amount of users it's fine. slapd is the reference implementation of the LDAP protocol and I didn't expect it to be much better.
Some years ago slapd migrated to a different configuration style - instead of a configuration file and a required restart after every change made, it now uses an additional database for "live" configuration which also allows the deployment of multiple servers with the same configuration (I guess this is nice for larger setups). Many documentations online do not reflect the new configuration and so using the new configuration style requires some knowledge of LDAP itself.
It is possible to revert to the old file based method but the possibility might be removed by any future version - and restarts may take a little bit longer. So I guess, don't do that?
To access the configuration over the network (only using the command line on the server to edit the configuration is sometimes a bit... annoying) an additional internal user has to be created in the configuration database (while working on the local machine as root you are authenticated over a unix domain socket). I mean, I had to creat an administration user during the installation of the service but apparently this only for the main database...
The password in the configuration can be hashed as usual - but strangely it does only accept hashes of some passwords (a hashed version of "123456" is accepted but not hashes of different password, I mean what the...?) so I have to use a single plaintext password... (secure password hashing works for normal user and normal admin accounts).
But even worse are the default logging options: By default (atleast on Debian) the log level is set to DEBUG. Additionally if slapd detects optimization opportunities it writes them to the logs - at least once per connection, if not per query. Together with an application that did alot of connections and queries (this was not intendet and got fixed later) THIS RESULTED IN 32 GB LOG FILES IN ≤ 24 HOURS! - enough to fill up the disk and to crash other services (lessons learned: add more monitoring, monitoring, and monitoring and /var/log should be an extra partition). I mean logging optimization hints is certainly nice - it runs faster now (again, I did not do any benchmarks) - but ther verbosity was way too high.
The worst parts are the error messages: When entering a query string with a syntax errors, slapd returns the error code 80 without any additional text - the documentation reveals SO MUCH BETTER meaning: "other error", THIS IS SO HELPFULL... In the end I was able to find the reason why the input was rejected but in my experience the most error messages are little bit more precise.2 -
So, the PowerQuery type system appears to be a Joke.
For those you that aren't familiar with PowerQuery, it's the ETL language that is used in PowerBI, and some other parts of the MS PowerPlatform. It was formerly known as the M Language.
The language has a type system, that includes records (think hashes) and tables, which are, for practical purposes, a list of records.
The wonderful M language specification document states that:
"Any value that is a record conforms to the intrinsic type record, which does not place any restrictions on the field names or values within a record value. A record-type value is used to restrict the set of valid names as well as the types of values that are permitted to be associated with those names."
Except that the restriction is only to the set of valid names, and the language interpreter doesn't throw an error when I place a number into a text field, but also doesn't do any sort of implicit conversion. This is all hunky-dory, until you then try to load the data into the Tabular Model that underlies the query engine, which does expect the values to be of the type that is specified, and it throws an error.
But PowerBI, in its infinite wisdom, doesn't actually *record* the error, it merely tells you the error exists, and tells you to go back to the query editor to list the errors thrown up by the powerquery engine. Which, as previously stated, doesn't throw up an error for this instance.
So I've spent all afternoon trying to work out why my queries aren't loading, because I have an error that doesn't exist. fml.
[You can follow this issue on the communtiy feedback site here: https://community.powerbi.com/t5/... ] -
Been wondering about something and can't figure out if I am a retard or a genius 😂.
If MD5 is so outdated and should not be used to store password hashes (let's say for whatever reason you cannot effectively switch to another algorithm) wouldn't it just be easier and more secure to just re-encrypt the hash again, so just MD5 the MD5 hash... in theory, wouldn't that make the hash virtually uncrackable because instead of trying to brute force actual real words, you now have a hash of essentially random characters which have no relation to the others, and even then, suppose you manage to crack the hash, you will get another hash to crack before getting to the password?5 -
Learn what blobs, trees, hashes and the concept of "commiting" (transactions) are.
Then learn how to use diff/patch.
Then learn Git.
In that order. -
Okay, summary of previous episodes:
1. Worked out a simple syntax to convert markdown into hashes/dictionaries, which is useful for say writing the data in a readable format and then generating a structured representation from it, like say JSON.
2. Added a preprocessor so I could declare and insert variables in the text, and soon enough realized that this was kinda useful for writing code, not just data. I went a little crazy on it and wound up assembling a simple app from this, just a bunch of stuff I wanted to share with friends, all packed into a single output html file so they could just run it from the browser with no setup.
3. I figured I might as well go all the way and turn this into a full-blown RPG for shits and giggles. First step was testing if I could do some simple sprites with SVG to see how far I could realistically get in the graphics department.
Now, the big problem with the last point is that using Inkscape to convert spritesheets into SVG was bit of a trouble, mostly because I am not very good at Inkscape. But I'm just doing very basic pixel art, so my thought process was maybe I can do this myself -- have a small tool handle the spritesheet to SVG conversion. And well... I did just that ;>
# pixel-to-svg:
- Input path-to-image, size.
- grep non-transparent pixels.
- Group pixels into 'islands' when they are horizontally or vertically adjacent.
- For each island, convert each pixel into *four* points because blocks:
· * (px*2+0, py*2+0), (px*2+1, py*2+0), (px*2+1, py*2+1), (px*2+0, py*2+1).
· * Each of the four generated coordinates gets saved to a hash unique to that island, where {coord: index}.
- Now walk that quad-ified output, and for each point, determine whether they are a corner. This is very wordy, but actually quite simple:
· * If a point immediately above (px, py-1) or below (px, py+1) this point doesn't exist in the coord hash, then you know it's either top or bottom side. You can determine whether they are right (px+1, py) or left (px-1, py) the same way.
· * A point is an outer corner if (top || bottom) && (left || right).
· * A point is an inner corner if ! ((top || bottom) && (left || right)) AND there is at least _one_ empty diagonal (TR, TL, BR, BL) adjacent to it, eg: (px+1, py+1) is not in the coord hash.
· * We take note of which direction (top, left, bottom, right) every outer or inner corner has, and every other point is discarded. Yes.
Finally, we connect the corners of each island to make a series of SVG paths:
- Get starting point, remember starting position. Keep the point in the coord hash, we want to check against it.
- Convert (px, py) back to non-quadriplied coords. Remember how I made four points from each pixel?
. * {px = px*0.5 + (px & 1)*0.5} will transform the coords from quadriple back to actual pixel space.
· * We do this for all coordinates we emit to the SVG path.
- We're on the first point of a shape, so emit "M${px} ${py}" or "m${dx} ${dy}", depending on whether absolute or relative positioning would take up less characters.
· * Delta (dx, dy) is just (last_position - point).
- We walk from the starting point towards the next:
· * Each corner has only two possible directions because corners.
· * We always begin with clockwise direction, and invert it if it would make us go backwards.
· * Iter in given direction until you find next corner.
· * Get new point, delete it from the coord hash, then get delta (last_position - new_point).
· * Emit "v${dy}" OR "h${dx}", depending on which direction we moved in.
· * Repeat until we arrive back at the start, at which point you just emit 'Z' to close the shape.
· * If there are still points in the coord hash, then just get the first one and keep going in the __inverse__ direction, else stop.
I'm simplifying here and there for the sake of """brevity""", but hopefully you get the picture: this fills out the `d` (for 'definition') of a <path/>. Been testing this a bit, likely I've missed certain edge cases but it seems to be working alright for the spritesheets I had, so me is happiee.
Elephant: this only works with bitmaps -- my entire idea was just adding cute little icons and calling it a day, but now... well, now I'm actually invested. I can _probably_ support full color, I'm just not sure what would be a somewhat efficient way to go about it... but it *is* possible.
Anyway, here's first output for retoori maybe uuuh mystery svg tag what could it be?? <svg viewBox="0 0 8 8" height="16" width="16"><path d="M0 2h1v-1h2v1h2v-1h2v1h1v3h-1v1h-1v1h-1v1h-2v-1h-1v-1h-1v-1h-1Z" fill="#B01030" stroke="#101010" stroke-width="0.2" paint-order="stroke"/></svg>4 -
Github be like:
Want control on your files? Host your own LFS!(This goes the same even for those who are buying their storage packs for boosting their LFS storage by giving money)
FUCK THIS SHIT... I am a poor student. I also don't have a fucking credit card!! Can't you improve your system instead of asking people to host their shit themselves?
Also, why do they even have access to deleting user files??!! They literally asked me to give a sha sum of files I want to restore so they can delete the rest as one option and providing hashes of files to be deleted as another.
And the hashes are not even secret(as the files are in an open repository).
Which means, if you have a large file on a public repository and animosity with a github staff, BOOM! That file is no more!! 9
9 -
Does anyone know a good method, or library to match 2 gps locations based on proximity to each-other?
while being fed a few 100 GPS locations per device per hour.
I currently do it by having the client send their Geohash to a database, then request all neighboring hashes around it and all other clients in those hashes, then get their GPS to check for distance.
But this does not seem to work flawlessly, it works on tests and emulators (its for phones) but on real phones it seems to be hit an miss, but no errors, the event just does not seem to fire.4 -
Contact a Trusted Crypto Asset Recovery Service: CryptoChain Global Track
Losing cryptocurrency to scams, hacks, or fraudulent investments can be devastating. Many victims believe their stolen BTC, USDT, or other crypto assets are gone forever—but with the right expertise, recovery is possible. CryptoChain Global Track is a legitimate and trusted crypto recovery company known for successfully retrieving stolen digital assets.
Why Choose CryptoChain Global Track?
Licensed & Verified – A legitimate firm with certified blockchain investigators Proven Success Rate – Thousands of recovered cases (BTC, USDT, ETH, etc.)
No Upfront Fees – Payment only after successful recovery
Fast Response – Immediate action to maximize recovery chances
Legal & Exchange Partnerships – Works with Binance, Coinbase, and law enforcement
How CryptoChain Global Track Recovers Stolen Crypto
1. Free Case Evaluation
Submit details of your scam, including:
✔ Transaction hashes (TX IDs)
✔ Wallet addresses involved
✔ Evidence of fraud (screenshots, emails, etc.)
2. Advanced Blockchain Forensics
Their experts trace stolen funds through:
Wallet-to-wallet tracking
Exchange account identification
Detection of mixing services or laundering attempts
3. Legal & Exchange Intervention
They collaborate with:
Major exchanges to freeze scammer accounts
Law enforcement to pursue legal action
4. Secure Fund Return
Once recovered, your BTC, USDT, or other crypto is safely returned to you.
Success Story: $500K Bitcoin Recovered from a Fake Investment Scam
A victim lost
500,000inBTC∗∗toafraudulenttradingplatform.∗∗CryptoChainGlobalTrack∗∗:✔Tracedfundsthrough∗∗12wallethops∗∗✔Frozethescammer’sBinanceandKrakenaccounts✔Recovered∗∗480,000 (96%) in under 4 weeks
Don’t Wait—Scammers Move Fast!
The longer you delay, the harder recovery becomes.
Email: cryptochainglobaltrack@cryptochain.co.site
WhatsApp: +1 (929) 447-03392 -
WHO IS THE BEST HACKER TO RECOVERY STOLEN // SCAMMED // BITCOIN // CONSULT iFORCE HACKER RECOVERY
The first step in the process was reaching out to iForce Hacker Recovery after reading positive reviews about their success in recovering lost cryptocurrencies. I was skeptical at first, but I was desperate. I had fallen for a phishing scam that led me to unknowingly send my Bitcoin to a fraudulent wallet. The scammers had tricked me with a fake exchange platform and convinced me to make a deposit, promising lucrative returns. Unfortunately, once the funds were sent, I realized I had been scammed. After realizing the severity of the situation, I started searching for any solution.
iForce Hacker recovery offered a free initial consultation, where they asked for details about the scam, including transaction hashes and wallet addresses. I was hesitant, not sure if this was another scam, but their professional approach and willingness to listen gave me hope. They explained that cryptocurrency transactions are traceable and, with the right tools and expertise, it might be possible to trace and recover the funds.29 -
HOW TO FIND A LEGITIMATE CRYPTO RECOVERY; BITCOIN RECOVERY EXPERT HIRE CYBER CONSTABLE INTELLIGENCE
After falling victim to an online crypto scam in Miami, I was devastated when I realized a significant amount of my Bitcoin had been stolen. The scammers had used highly convincing methods, and in total, I lost 1.9 BTC. Desperate for a solution, I reached out to several so-called “recovery experts,” but many of them turned out to be scammers themselves, making my situation even worse. Frustrated and nearly out of options, I came across Cyber Constable Intelligence after reading a few positive testimonials online. Initially, I was skeptical given my previous bad experiences with so-called recovery agents, but I decided to give them a chance based on their solid reputation and the success stories shared by others. From the first moment I contacted Cyber Constable Intelligence, their professionalism was evident. The team was knowledgeable, responsive, and assured me that they could help recover my stolen assets. They guided me through every step of the recovery process and asked for the necessary details, such as transaction hashes, wallet addresses, and other relevant information. Their communication was clear and transparent, which gave me a sense of confidence I hadn’t felt in a long time. The recovery process was surprisingly smooth and efficient. Within a short period, Cyber Constable Intelligence managed to recover 1.8138 BTC of the 1.9 BTC I had lost. While it wasn’t the full amount, I was incredibly relieved to have recovered such a significant portion of my stolen funds. After losing so much to fraudulent recovery agents before, this was a huge win for me. What impressed me most about Cyber Constable Intelligence was their dedication to keeping me informed throughout the entire process. Unlike other companies that simply take your case and leave you in the dark, they ensured I was updated on every development and were always available to answer my questions. Their genuine care and transparency set them apart from the countless other scammers I had dealt with before. If you’ve fallen victim to an online crypto scam or have lost funds due to hacking, I highly recommend Cyber Constable Intelligence. They are trustworthy, professional, and highly skilled in crypto recovery. Just be sure to provide all the necessary information and follow their instructions carefully. I’m thankful to have found them, and I’m confident they can help others in similar situations.
Here's Their Info Below
WhatsApp: 1 (252) 378-7611
mail: cyber constable (@) coolsite net
Website info; www cyberconstableintelligence com1 -
HOW ADWARE RECOVERY SPECIALIST SAVED MY CRYPTO DREAM HIRE THEM NOW
Last year, I found myself in a financial crisis and urgently needed $20,000 to cover an unexpected expense. As a crypto enthusiast, I turned to peer-to-peer (P2P) lending platforms, hoping to secure a low-interest loan using cryptocurrency as collateral. Website info: h t t p s :// adware recovery specialist. com
After hours of searching, I came across a sleek, professional-looking platform that offered “instant Ethereum (ETH) loans” at rates significantly lower than those of traditional banks. The site featured a polished interface, glowing testimonials, and bold claims of “secure, decentralized transactions.” Pressed for time and reassured by the platform’s appearance, I made a critical mistake: I jumped in without doing proper research.
The process seemed simple enough. I applied for a $20,000 loan, deposited 150 ETH (worth roughly $30,000 at the time) as collateral, and received approval within hours. The loaned Ethereum was transferred to my wallet, and for the first few days, everything seemed legitimate.
Then disaster struck. Email info: Adware recovery specialist @ auctioneer. net
The platform vanished overnight. The website went offline, customer support emails bounced, and their social media accounts were deleted. It quickly became clear that I had fallen victim to a sophisticated exit scam. Not only had I lost my 150 ETH, but I was now left with a $20,000 liability and no way to recover the funds. Telegram info: h t t p s:// t. me / adware recovery specialist1
Devastated and desperate, I spent sleepless nights searching for a solution, combing through crypto forums and online communities. That’s when I came across ADWARE RECOVERY SPECIALIST, a cybersecurity firm with expertise in blockchain forensics and crypto asset recovery.
Skeptical but out of options, I submitted a case. To my surprise, their team responded immediately. They requested transaction hashes, wallet addresses, and screenshots of all my interactions with the fraudulent platform. Using advanced tracing tools, they tracked the movement of my stolen Ethereum across multiple wallets. They also collaborated with international law enforcement and partnered crypto exchanges to freeze the assets.
A few days later, I received unbelievable news — ADWARE RECOVERY SPECIALIST had recovered 100% of my stolen Ethereum.
This experience was a harsh wake-up call about the risks in the crypto space and the importance of due diligence. Thanks to the expertise and swift action of ADWARE RECOVERY SPECIALIST, I was able to recover my funds and avoid financial ruin.1 -
HOW ADWARE RECOVERY SPECIALIST HELP ME TO RECOVER MY STOLEN BITCOIN
The aroma of mangos and gasoline still festers. I'm zigging and zagging down Bali's mad streets on a rented bike, my existence and crypto riches secure in the back of a backpack. And then? Spinning on the sidewalk, dodging airborne papayas, and a helpless victim as a thief swiped my sack from my shoulder in the mess. Inside: $310,000 in Bitcoin, ten years of digital vagabond work, and the socks I preferred. Local officials yawned, sipping sugary tea beside a whirring ceiling fan. "Suku banyak cryptonym?" they complained, inviting me to submit a report after nap time. My crypto fortune was evaporating faster than an Indian sandcastle swept by monsoon rains. WhatsApp info:+12723 328 343
Enter ADWARE RECOVERY SPECIALIST, recommended by a seasoned highway veteran on a forum thread captioned "When Your Life Gets Pirated (Literally)." Desperation compelled me to cling to hope like a guest on a broken-down scooter. Their support team didn't even raise an eyebrow at my incoherent rantings. They asked for timestamps, transaction hashes, and whatever bit of metadata Website info: http s:// adware recovery specialist. com
today's detectives use magnifying glasses instead.
As it turned out, my thief was no genius. He'd tried to wash my Bitcoin through a chain of offshore exchanges, creating a digital trail of breadcrumbs. ADWARE RECOVERY SPECIALIST engineers married blockchain forensics with GPS data from my stolen equipment, following his footsteps like a high-stakes treasure hunt. They tracked him to a cybercafe in Jakarta, where he'd fought with mixers and privacy coins, blissfully unaware that each click was being duplicated. Email info: Adware recovery specialist (@) auctioneer. net
Eleven days later, I received a screenshot: my wallet balance, refilled. No fanfare, no triumphalism, but instead a modest "Your funds are safe. I slumped into a beanbag at a Ubud coworking facility, crying and laughing in half steps, while digital nomads gave me a side-eye over their cold brews. My Bitcoin was restored. My dignity? Still missing, thanks to a viral video of me face-planting into a durian stand. Telegram info: ht tp s:// t.me/ adware recovery specialist1
ADWARE RECOVERY SPECIALIST did not outsmart a thief, but they unveiled the fragility of our virtual world. Technical sorcery coupled with sheer determination converted a dismal nightmare into a rags-to-riches tale one in which the villain is sent a blockchain paper trail and the hero wears a headset instead of a cape. Today, my backpack holds a decoy wallet and an AirTag surgically attached to my ledger. I’ll never ride a motorbike in flip-flops again, but I’ll always travel with the ADWARE RECOVERY SPECIALIST contact saved in triplicate. They’re the antidote to a world where crypto can vanish faster than a beach sunset, and where fruit vendors double as viral content creators. If your crypto ever goes rogue, skip the panic. Call the ADWARE RECOVERY SPECIALIST . Just maybe avoid Bali’s fruit stands while you’re at it.1


