Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
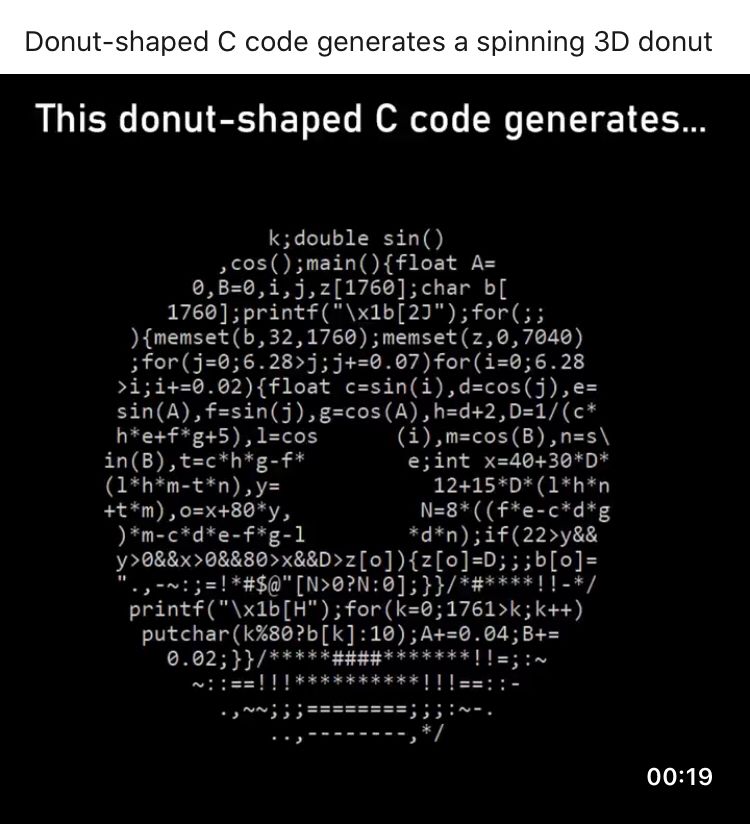
Search - "obfuscation"
-
I found out recently that Facebook is embedding tracking data in the form of IPTC metadata in images that you upload. This way the images can be tracked even after you download them.
Because I'm an anarchist and just want to watch the world burn a little, I made a tiny server to replace the id hash that they embed with a random one, just to see if I can't fuck with their algorithm a little bit.
You can check out the project here https://github.com/watzon/fbmdob15 -
What a wonderful language JavaScript is. It's the only language where "(+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]" is equal to just simple "." character.6
-
Drunk programming is the best obfuscation. Tomorrow morning I'll have no idea how any of this works.3
-
One of my favourite, encryption puzzles is this:
ITuyVT93oUZtLKWyVT5iqPO3nTS0VUEbMKxtp2IyoD==
Answer is plain text string in english. Good luck, post solution in the comments!19 -
Having to review an offshore C++ codebase made in Romania that the company I worked for they bought to control a wifi module on a complex RF mobile tech device that I can't legally give more details on.
If I could legally post this masterpiece, or should I say masterpiece-of-shit, all of you C++ dev would instantly get AIDS and all the existing types of cancer upon browsing it for 2 minutes.
It's laughably bad and unmaintainable. One of my colleague called it "the perfect example of human obfuscation" and it fits perfectly.
Think of a 100k LoC main function with nested loops and ifs with random sleep values, 1000 values of hardcoded 32 bits arrays declared globally in the first 10k lines for unknown reasons. Comments in Romanian mixed with english. Somehow, this shit works by some miracle.
The worst intern you can think of, while being piss drunk, could do better and it's no joke.5 -
---WiFi Vision: X-Ray Vision using ambient WiFi signals now possible---
“X-Ray Vision” using WiFi signals isn’t new, though previous methods required knowledge of specific WiFi transmitter placements and connection to the network in question. These limitations made WiFi vision an unlikely security breach, until now.
Cybersecurity researchers at the University of California and University of Chicago have succeeded in detecting the presence and movement of human targets using only ambient WiFi signals and a smartphone.
The researchers designed and implemented a 2-step attack: the 1st step uses statistical data mining from standard off-the-shelf smartphone WiFi detection to “sniff” out WiFi transmitter placements. The 2nd step involves placement of a WiFi sniffer to continuously monitor WiFi transmissions.
Three proposed defenses to the WiFi vision attack are Geofencing, WiFi rate limiting, and signal obfuscation.
Geofencing, or reducing the spatial range of WiFi devices, is a great defense against the attack. For its advantages, however, geofencing is impractical and unlikely to be adopted by most, as the simplest geofencing tactic would also heavily degrade WiFi connectivity.
WiFi rate limiting is effective against the 2nd step attack, but not against the 1st step attack. This is a simple defense to implement, but because of the ubiquity of IoT devices, it is unlikely to be widely adopted as it would reduce the usability of such devices.
Signal obfuscation adds noise to WiFi signals, effectively neutralizing the attack. This is the most user-friendly of all proposed defenses, with minimal impact to user WiFi devices. The biggest drawback to this tactic is the increased bandwidth of WiFi consumption, though compared to the downsides of the other mentioned defenses, signal obfuscation remains the most likely to be widely adopted and optimized for this kind of attack.
For more info, please see journal article linked below.
https://arxiv.org/pdf/...9 -
Android really gets on my goat. They are moving things so far that they are actually doing more damage than good.
Upgrade my build tools to v25? sure! Now all my BLE code is borked, thanks for nothing.
Go to the documentation? Lol, that's deprecated fool!
At least now it can all fail to function in Kotlin, a wrapper for Java 6. Instead of keeping your tools up to date you just create another layer of obfuscation. Well done, so proud.3 -
One of the many problems with AWS free tier is the obfuscation of expenditure by design. This is NOT OK.
 17
17 -
I'm currently one of two "pen testers" for the anticheat system of a game.
It all started a few days ago when the developer handed me the obfuscated package and told me to go at it. No big deal, I've bypassed it before the obfuscation, so I just changed some imports and sent in the screenshot.
Fast forward 100+ hours, it's turned into a cat-and-mouse game. He sends us (the testers) an update, we break it within hours. We show him what we exploited and he attempts to fix it. Rinse and repeat.
Finally, today he patched the one hole that I've been using all this time: a field in a predictable location that contains the object used for networking. Did that stop me? No!
After hours of searching, I found the field in an inner class of an inner class. Here we go again.3 -
We were running an obfuscator as part of our build pipeline, but also were not. I discovered we had disabled every rule, and after asking around it turns out that the obfuscator broke the app (because of reflection and things I won't go into).
So I turned it off.
An hour later the CTO came to me and said to put it back. "We have to obfuscate, put it back."
"But... it wasn't doing anything, other than slowing the build down."
"I don't care, we HAVE to run obfuscation. It's in our contract with the client."
...4 -
Just finished a large write up on a security flaw I found and disclosed in an exam spyware vendor's "zero knowledge encryption" - derived keys that were generated from incrementing integers, discussion on obfuscation and more.
It was a hell of a time writing this up; not sure if linking my personal blog here would be bad practice, but here it is: https://proctor.ninja/wave-rake-pro...
It's been something else, but hopefully I can keep fighting against tech like this on school campuses.4 -
Imagine implementing PHP scripts which execute shell commands defined in URL GET query params on your customer's dedicated server without any basic authentication or similar. The only security is by barely obfuscating it's URL.
I think I've seen it all now...3 -
In my latest installment of "Swift, WTF?", we look at the "if" conditional in terms of the Swift convention of:
if let x = y { /* ... */ }
so what this does :
1. declares x in the scope of the braced code
2. sets x to y (an ahem, "optional")
3. decides if x is not *nil*, then executes the braced code.
This is very similar in both the visual and the operation to the C code of:
if (int x = y) { /* ... */ }
1. declares x in the scope of the braced code
2. sets x to the value of y
3. if x is not zero, then executes the braced code
which is considered *exceptionally* poor style.
Neither the C nor the Swift construct result in a legitimate boolean value of "true" or "false", although C comes closer than Swift.
In the Swift case the *imaginary* "nil" value has to be interpreted as "false" and thus there must be extra code is for the conditional to check on whatever constitutes the **actual** value of nil in Swift and then set the condition to "false".
(remember boys and girls, "optionals" are not real, they are an imaginary language construct of Swift and have no legitimate counterpart in the CPU operations with memory and registers)
At least in the case of C, if the value of x is zero or NULL (which is 0) then it is technically a "false" which in C is 0. Regardless, it is really poor programming and anyone doing that on my team gets an ear full.
But in Swift this obfuscation of code is common and condoned! Well, why not put more of the program in the condition of the if? In fact, stuff the whole thing in there.. why not? 🙄
This just reenforces my opinion that Swift is not a bird but the stuff that comes out of the underside of the bird. 🐦💩31 -
I need to encrypt some large files at rest and then decrypt them immediately prior to processing.
App and files are on a Linux system (CentOS). App is in C. Machine is controlled by a third party.
What encryption libraries would you recommend? And, is there any clever way of managing the decryption key beyond compiling it in the code and doing some basic obfuscation?
Are they fancy obfuscation libraries out there, for example?
And, the reason I'm not going to SO (well, one reason) is that I don't want to have 50 answers that tell me that's it's impossible to 100% protect data on a machine you don't control. This I understand---just looking for "best effort" solution.7 -
God damn it, if you (libGDX) have default values for public methods then make those constants public. Now I am writing wrapper and I either create my constant with same value as your private one, or do some reflection black magic which will probably break after obfuscation. *sigh* Going with my copy of the constant, not happy about that...
-
I need guidance about my current situation.
I am perfectionist believing in OOP, preventing memory leak in advance, following clean code, best practices, constantly learning about new libraries to reduce custom implementation & improve efficiency.
So even a single bad variable name can trigger my nerves.
I am currently working in a half billion $ IT service company on a maintenance project of 8 year old Android app of security domain product of 1 of the top enterprise company of the world, which sold it to the many leading companies in the world in Govt service, banking, insurance sectors.
It's code quality is such a bad that I get panic attacks & nightmares daily.
Issues are like
- No apk obfuscation, source's everything is openbook, anybody can just unzip apk & open it in Android Studio to see the source.
- logs everywhere about method name invoked,
- static IV & salt for encryption.
- thousands of line code in God classes.
- Irrelevant method names compared to it's functionality.
- Even single item having list takes 2-3 seconds to load
- Lag in navigation between different features' screens.
- For even single thing like different dimension values for different density whole 100+ lines separate layout files for 6 types of densities are written.
- No modularized packages, every class is in single package & there are around 100+ classes.
Owner of the code, my team lead, is too terrified to change even single thing as he don't have coding maturity & no understanding of memory leak, clean code, OOP, in short typical IT 'service' company mentality.
Client is ill-informed or cost-cutting centric so no code review done by them in 8 years.
Feeling much frustrated as I can see it's like a bomb is waiting to blast anytime when some blackhat cracker will take advantage of this.
Need suggestions about this to tackle the situation.10 -
C# is getting so fucking obfuscated with these null check inceptions. Found the following in my company's code base. Why did it take me and 3 other devs an hour to figure out how to write this if statement into a flowchart?
if(!string.IsNullOrEmpty(a?.Id ?? b[0]?.Id))...😫😫😫
FYI: We figured it and also found some bugs with logic, but can you? I'll post our flowchart if ranters are interested.
So to add to the madness:
if(!string.IsNullOrEmpty(a?.Id ?? (b?.Any() ? b[0].Id : null)))...🤯🤯🤯23 -
It occurred to me that I'm making actual money now and I can pay for my shit, so I tried Youtube Premium, but their background play is poorly implemented and defaults to a floating window that I need to cancel in a finnicky, android-vendor-specific way. How do you consistently make something that much less usable than an unpaid open-source developer who also has to reverse-engineer your API and circumvent your anti-user-choice obfuscation measures? NewPipe would be a success if it could just play the videos in full screen with no controls, and yet it has a better background play story than the actual provider. Fuck centralised software9
-
view-source:https://www.google.com/?gws_rd=ssl
“Oh my GOD! I've heard of obfuscation, but this is just hell in text format!”5 -
For F^^k sake Microsoft give us some way to protect .net code from easy reflection / decompilation ..... Obfuscation just doesn't cut it.1
-
TLDR;
Side project update.
Made simple nlp library in python and published it’s first version to open source.
Now I can feed it with parsed pdf text.
See rant https://devrant.com/rants/2192388/...
Why ?
Cause during reading book about nltk I couldn’t find simple extendible way to provide support for polish language and I wanted to abstract stemming, word normalization, tokenizer etc. so I can provide ex. different conditions for separate text files and don’t write much code what is an asset when you work solo.
It’s about 12GB of pdf public accessible law data I am trying to handle ( at first ) which is about 35000 files from last 90 years.
So far I automated downloading web pages and pdf documents from them. Extracting data from web pages and saving it to database. Extracting text from pdf files. I have about 5-6 projects to do all of it above maybe at the end I will put it to some workflow manager like Luigi or just run it by cronjob.
First thing for website version 1.0 part is find correlation between all documents inside law text using nlp library by building custom conditions. Then just generate directory structure and html files with links between documents.
Website version 2.0 is already in my mind but it will be creepy to make it and will take at least 1-2 months and I want to publish fast.
I have some pdfs with only images instead of text and tesseract worked quite good with them so maybe I will try to process them when everything go live.
Learned a lot about pdf as now I know that font in pdf is not always providing unicode characters ( stupid form of obfuscation) so when you extract text you need to build glyph vector to text map for every font.
Pdf is full vector representation - just like svg - what is logic if you think a bit and know that some printers are running using postscript.
Let’s hope next update will be about flutter mobile app which started all of shit above. It’s almost ready ( except getting data from api I am trying to do and logo for release version ). It’s last piece of puzzle.3 -
How do you hide your javascript file from showing for your client..aside from using obfuscation... do you know anyway to do this using npm and where you would just go
Var hide = require(‘hide something’);
hide(“public/my.js”);
hide(“public/my2.js”);
Hides it from clients and still able to access functions by these javascript files?44 -
Any idea of how to protect your nodejs source code on a client's onsite server ?
If they can SSH, they can get the entire source.
This is built into the angular framework very well but I don't know how to do this on a server.
Any neat packages for obfuscation, uglification etc ?8 -
Gotta love JavaScript obfuscation!
((_)=>{_=["cnVjdG9y","Y29uc3Q=",(_)=>{return atob(_)},2,0,1],_=_[_[3]](_[_[5]])+_[_[3]](_[_[4]]),_=((+[])[_][_]),_("console.log('Xaotic <3')")()})([])
// We need a [code] tag guys 3
3 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
Where are my aspirins
Also who wants to check it out, I've made it wooo
https://hastebin.com/oviherukad.js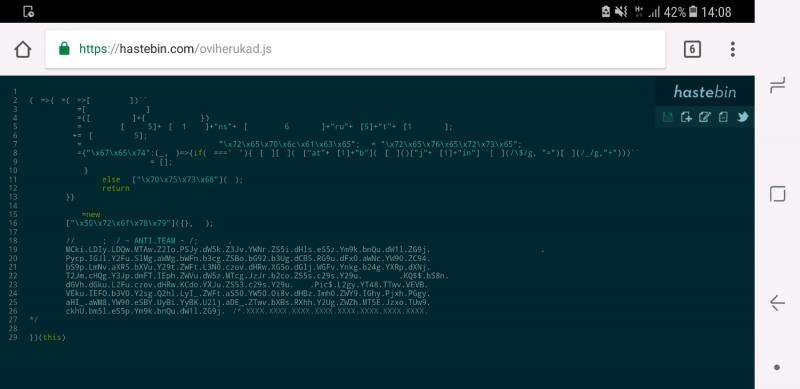 2
2 -
Soo I finally uploaded my framework for Java Web last week.
It works great except for forwarding POST requests but meh, I'll fix it later.
Currently it only works for newer Minecraft Spigot version's and BungeeCord, because fucking netty is a piece of shit and Apache commons also... But I'll release a standalone version hopefully next month (maybe even next weekend).
And on the website from Spigot where you can find the link to my GitHub, there were two dicks which tried to steal my code and complained about my obfuscation... The didn't even fucking tried the plugin and gave me 1 star... Fucking pieces of shit fuck...
Anyway: here is the link!
https://spigotmc.org/resources/... 3
3 -
best money to be made is through obfuscation, then you come in saying you have the true info, and then you give the wrong info so your secondary friends can make some money while leaving you alone7
-
So today I had to fiddle around with obfuscation software to obfuscate software we are going to release....
4 tries in and the software is still crashing with different exceptions each time....
And at the same moment this text came in to my mind:
"If software is working after obfuscation it's not obfuscated enough"2 -
How do you guys prefer to hide the API keys you use in your (native) Android apps?
I'm an Android noob and the app I'm building uses some NLP services which are accessed through a key. I searched around and found a few techniques (obfuscation, serverside storage, etc.), just wanted to know what you folks recommend.5 -
alrite devs, hardmode:
i have an obfuscation algo that cannot be defeated even by quantum computing (like infinite parralelism if i got that one right [i mean understanding what is Qcompute])
how can i take advantage of it? (get phd/big money payroll/sell it)
it could be implemented as impossible to defeat ssh for instance26 -
Note: I had AI rephrase this because apparently it was too full of swearing or smth to be accepted and I was getting a "there was an error posting this rant". Nice that people at devrant's can't even show a clear error of WTF is going on, not even in chrome dev tool console/network requests, so maybe you're able to figure out WTF is going on and fix your post. They must be the same kind of people I'm ranting about.
-----------End of the note.----------------
TL;DR;: My coworkers are smart idiots that learn fast but can't control themselves into turning any project into a trashcan of spaghetti code and I'm burning out and want to switch for couple years to a simpler job.
I'm considering leaving my career in programming, consulting, and project management in favor of a more straightforward, manual labor job—perhaps something like baking or another role that relies on physical effort rather than constant problem solving.
I’ve reached a point where I can no longer tolerate the challenges of my current position, especially due to the dynamics with my coworkers. I long for a day where I can work for eight hours, exhaust myself physically, and then go home without any lingering mental responsibilities or ties to complex problem solving.
Over the past decade, I’ve collaborated with many people, yet I've only had the opportunity to manage an entire project from scratch on my own twice. In those rare instances, everything ran smoothly, issues were quickly resolved, and the code remained stable for years without constant complaints from clients.
Unfortunately, my coworkers, despite their intelligence, tend to overcomplicate even simple tasks. They often fall into the trap of overengineering, chasing the latest technologies and implementing unnecessarily complex paradigms, design patterns, frameworks, and techniques—even when I’ve offered simpler, proven solutions.
For example, I’ve built robust portals that handle everything from national highway finances and warehousing to HR and inventory management for major companies. In contrast, when others attempt similar projects, the resulting code becomes overwhelmingly complex and difficult to manage.
To give a few specific examples:
Example 1: The .NET Portal
We began developing a .NET portal about two months ago, which is now nearing version 1.0. Before we even started, the team had created multiple flowcharts to split the project into components like SaaS deployment, Docker integration, obfuscation, and separate portals for user administration and backend processes. Within a few weeks, they scrutinized and debated numerous authentication technologies—even though we had successfully implemented JWT token solutions in the past. The team continually shifts focus, leaving me uncertain about the final direction.
Example 2: Over-Engineering with Patterns
In another project, the team overused inversion of control (IoC) and mediation patterns, even going so far as to have an AI generate a custom message bus. Navigating this overly decoupled code is challenging; even Visual Studio’s IntelliSense struggles to provide guidance, and the code often feels like a puzzle that changes whenever I return from a break.
Example 3: Complicated Logging Implementation
We needed to add logging functionality, and I proposed a simple solution using custom exceptions that would bubble up to a central logging mechanism. Despite its past success in saving time and reducing frustration, the team decided to implement three different logging methods—one using .NET’s ILogger, another with Serilog, and a third hybrid approach. They even suggested using a rarely seen technique involving stack traces to determine which function threw an error. This approach added unnecessary complexity and only increased my frustration.
Now, even though the project is too far along for me to withdraw, I find myself feeling burned out just a few days back at work. The code has become a tangled mess, and even routine tasks like adding logging are turning into sources of intense frustration due to constantly shifting ideas and overly complicated designs.
On top of all this, I’m also disappointed with the performance of AI tools, which seem to be producing unreliable code that requires further fixes, compounding my frustration.
I’m now seriously contemplating a complete career change—perhaps even moving to a country with a better work environment, such as Denmark or Switzerland—in the hope of finding a job where the work is more straightforward and less mentally taxing and better paying4 -
You know when I think back to the ideas I've had and the things I've worked on. I'm having difficulty, with the exception of certain far out projects that were like unattainable, in thinking of anything I've done or thought of that does not involve: data visualization, data gathering, encryption/obfuscation, inventory/storage and/or communication.
am I just unimaginative ?
I did have an idea for a code translator and how it would work and what interfaces you'd have to adopt and how you'd attack implementing things that don't translate well like c++ to js for example. or c++ to c# for that matter ! but I never got far into it. though that would have been attainable as long as you had easy ways of generating bindings.
i mean pathing and navigation were things I thought of too but... that would pretty much be implementing someone else's stuff4 -
I need some clarity with the situation below.
I have my API ready.
Let's say I have a route /reset/token,
I want to be able to serve a html file with css and all that once I've processed the token internally.
I've not worked with the whole stack before so I've never really served files based on conditions i.e if the token is valid serve x else serve y.html
Also, I'm pretty sure node.js isn't the best for serving files.
So I'm taking another approach with nginx which is to implement /reset/token to serve the static file with it's coupled js file to query the API. Seems standard to me but I have this feeling that a prefilled html would be more secure than one with exposed js.
Is this the right way? Should I worry about my API calls being exposed via the js fil ? Is obfuscation the only way to handle this ? Is this the way everyone does it cause somehow I don't see the key js files in most sites. How are they hidden if so? Or are they?
I'm confused and also nginx won't let me rewrite /reset/token to something else without changing the browser url field. How do I prevent that ?1 -
In the ever-evolving landscape of cryptocurrency, the challenge of recovering lost or stolen digital assets has long been a pressing concern. However, a pioneering company known as Washington Recovery Pro has emerged as a trailblazer in this domain, offering a revolutionary approach to the recovery of Bitcoin and other cryptocurrencies. Leveraging their deep expertise in blockchain technology and digital forensics, Washington Recovery Pro has developed a suite of innovative tools and techniques that empower individuals and organizations to track, trace, and reclaim their rightful digital holdings, even in the face of sophisticated theft and obfuscation tactics employed by cybercriminals. By tapping into the transparency and immutability of the blockchain, Washington Recovery Pro analysts are able to meticulously follow the digital breadcrumbs left behind by illicit transactions, unraveling complex money-laundering schemes and identifying the ultimate destinations of stolen funds. Through their tireless efforts and cutting-edge investigative methods, Washington Recovery Pro has successfully recovered millions of dollars' worth of cryptocurrency, restoring peace of mind and financial stability to countless victims of crypto-related crimes. As the adoption of digital assets continues to soar, the importance of Washington Recovery Pro work cannot be overstated, as they stand as a bulwark against the growing threat of cryptocurrency theft and a beacon of hope for those seeking to reclaim their rightful digital wealth. For more information, contact:
WhatsApp: +1 (903) 249‑8633 -
I FUCKING HATE TYPEDEF.
I have NEVER seen a use of typedef that wasn't UTTERLY pointless AND did absolutely nothing except add obfuscation to code.
What the fuck is the point of typedeffing a size_t to "MapIndex".. And THEN typedeffing a vector... Of vectors... Of size_t (not MapIndex!) AND THEN TYPEDEFFING A MAP OF "MapIndex" to that previously typedeffed vector of vectors....
ITS FUCKING BEYOND STUPID. I absolutely hate typedef. I have never seen a single NOT RETARDED usage of it.
Have you?7