Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "breach"
-
My most awkward recruiter interaction?
Just graduated college and got 'suckered' by an programming position ad that turned out to be a recruiting company. It was fine since they charge the company for their services and not me.
After a couple of weeks of waiting (they initially promised I would/could have at least 3 interviews a week, which hadn't happened.) I decided to start looking again on my own, found a position, and I was hired.
About two months later I get a phone call:
<skipping the pleasantries>
R: "I see you are working for D, congratulations. I've started the paperwork for our reimbursement."
Me: "Reimburse for what? I found that job on my own."
R: "D is one of the companies we work with and when we submitted your resume, they told us you were already hired."
Me: "And?"
R: "And you signed a contract and now its time to pay. The fees only start at $500"
Me: "Not me. I have the contract, it states, in the second paragraph, I am not responsible for any hiring fees."
<couple of seconds of silence>
R: "Yes, but that is only if we negotiated the contact. Since you went behind our back, we couldn't start the process"
Me: "And?"
R: "And its a breach of contract."
Me: "I'm not a lawyer, I don't understand what you're saying. It says right here on the contract I signed, I don't pay any fees. No where does it say I'm not allowed to look for a job on my own. Right?"
R: "Um..yea..right..right...but you were hired by one of our contracted companies."
Me: "No way I would have known that. Maybe you should have set up an interview long before now."
<R is getting pretty angry at this point>
R: "I'm sure we gave you list of companies we work with. Contacting those companies is a breach of contract. Unless you want our lawyers to get involved, the fee is only $500. Failing to honor your side of the agreement and we'll be forced to contact your employer and begin garnishing your wage until the fee is paid. You don't want that, do you?"
Me: "There was no list and I am allowed to find a job on my own. Again, I'm not responsible for you not setting up an interview so do whatever you think you can do. Have a good night"
<I hang up>
About a week later..
Boss: "Got a phone call from XYZ Recruiting requesting a wage garnishment. Do you know anything about that?"
<I explain the situation>
Boss: "Oh good grief. We've worked with them a couple of times and we contact them on an individual basis for new hires. You're fine"
Me: "You're not going to garnish my paycheck?"
Boss: "No no no, that's not how this works. He was probably trying to scare you into paying their crazy fees."
Me: "What if they get their lawyers involved? I don't want to cause any trouble"
Boss: "Ha ha...XYZ Recruiting is a couple of guys in an office and we have lawyers on the 3rd floor who eat and breath this shit. They know that and you won't hearing from them again."5 -
In may this year, the new mass surveillance law in the Netherlands went into effect. Loads of people were against it with the arguments that everyone's privacy was not protected well enough, data gathered through dragnet surveillance might not be discarded quickly after the target data was filtered out and the dragnet surveillance wouldn't be that 'targeted'.
They were put into the 'paranoid' corner mostly and to assure enough support/votes, it was promised that:
- dragnet surveillance would be done as targeted as possible.
- target data would be filtered out soon and data of non-targets would be discarded automatically by systems designed for that (which would have to be out in place ASAP).
- data of non-targets would NOT be analyzed as that would be a major privacy breach.
- dragnet surveillance could only be done if enough proof would be delivered and if the urgency could justify the actions.
A month ago it was already revealed that there has been a relatively (in this context) high amount of cases where special measures (dragnet surveillance/non-target hacking to get to targets and so on) were used when/while there wasn't enough proof or the measures did not justify the urgency.
Privacy activists were anything but happy but this could be improved and the guarantees which were given to assure privacy of innocent people were in place according to the politicians... we'll see how this goes..
Today it was revealed that:
-there are no systems in place for automatic data discarding (data of innocent civilians) and there are hardly any protocols for how to handle not-needed or non-target data.
- in real life, the 'as targeted dragnet as possible' isn't really as targeted as possible. There aren't any/much checks in place to assure that the dragnets are aimed as targeted as possible.
- there isn't really any data filtering which filters out non-targers, mostly everything is analyzed.
Dear Dutch government and intelligence agency; not so kindly to fuck yourself.
Hardly any of the promised checks which made that this law could go through are actually in place (yet).
Fuck you.28 -
haveibeenpwned: MASSIVE SECURITY BREACH AT COMPANY X, MILLIONS OF RECORDS EXPOSED AND SOLD, YOUR DATA IS AT RISK, please change your password!
Company X website: Hey your password expired! Please change it. Everything's fine, wanna buy premium? The sun is shining. Great day.1 -
I realize I've ranted about this before, but...
Fuck APIs.
First the fact that external services can throw back 500 errors or timeouts when their maintainer did a drunk deploy (but you properly handled that using caching, workers, retry handlers, etc, right? RIGHT?)...
Then the fact that they all speak a variety of languages and dialects (Oh fuck why does that endpoint return a JSON object with int keys instead of a simple array... wait the params are separated with pipe characters? And the other endpoint uses SOAP? Fuck I need to write another wrapper class around the client...)
But the worst thing: It makes developers live in this happy imaginary universe where "malicious" is not a word.
"I found this cloud service which checks our code style" — hmm ok, they seem trustworthy. Hope they don't sell our code, but whatever.
"And look at this thing, it automatically makes database backups, just have to connect to it to DigitalOcean" — uhhh wait...
"And I just built this API client which sends these forms to be OCR processed" — Fuck... stop it... there are bank accounts numbers on those forms... Where's that API even located? What company?
* read their privacy policy *
"We can not guarantee the safety of your personal data, use at your own risk [...] we are located in Russia".
I fucking hate these millennial devs who literally fail to get their head out of the cloud.
Somehow they think it's easier to write all these NodeJS handlers and layers around some API, which probably just calls ImageMagick + Tesseract on the other side.
If I wasn't so fucking exhausted, I'd chop of their heads... but they're like hydra, you seal one privacy breach and another is waiting to be merged, these kids just keep spewing their crap into easy packages, they keep deploying shitty heroku apps... ugh.
😖8 -
Oh fuck and boy Jesus, how on earth is this still a thing 😦
MD fucking 5 is not a fucking “secure” crypto algorithm.
This site has 14 million breached accounts with fucking MD5 hashes.
I think I’ve had to much internet for today.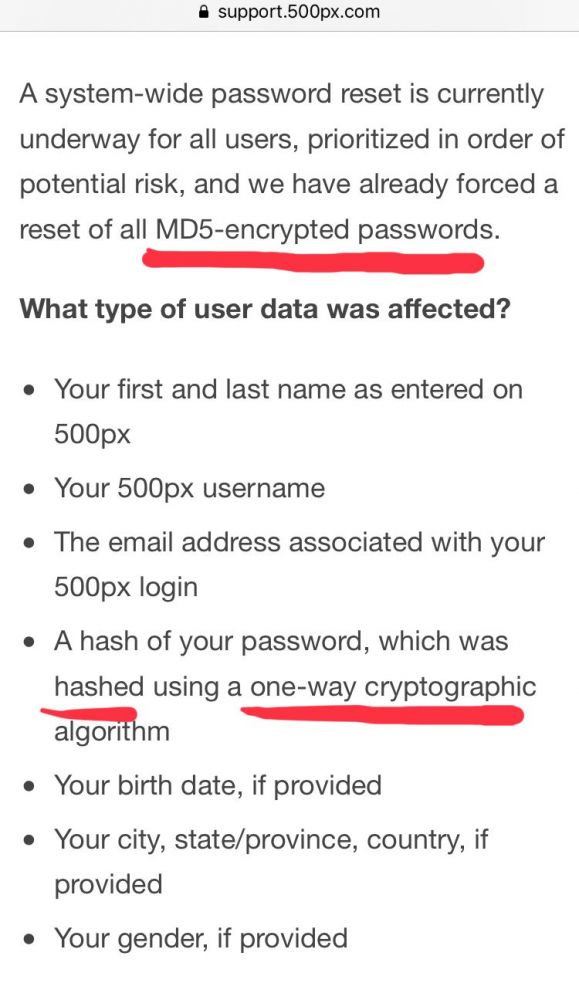 17
17 -
Uncle- What do you do?
Me- I'm a software engineer
Uncle- My brother's friend's son is also a software engineer.
Me- (so what am I supposed to do about it?) yes that's nice
Uncle- I have a great idea, u should implement, I'm just telling you, it is a revolutionary idea
Me- (oh fuck, not again) yes tell
Uncle- you should make a matrimonial site which tracks what people do on internet and tell their to-be-spouses about it
Me - (yeah, I'll get sued for breach of privacy, and it has got nothing to do with my current line of work, and will probably cause divorces before marriage) yes great idea uncle
Uncle- see I told you this billion dollar idea, u should do hard work and make it
Just WHY in god's name do all uncles think laptop is a magic box in which I just have to type their idea in and it will spit out a website/software in 2 minutes. I don't go around advising them about their line of work.11 -
No, MD5 hash is not a safe way to store our users' passwords. I don't care if its been written in the past and still works. I've demonstrated how easy it is to reverse engineer and rainbow attack. I've told you your own password for the site! Now please let me fix it before someone else forces you to. We're too busy with other projects right now? Oh, ok then, I'll just be quiet and ignore our poor security. Whilst I'm busy getting on with my other work, could you figure out what we're gonna do with the tatters of our client's business (in which our company owns a stake) in the aftermath of the attack?7
-
My client is trying to force me to sign an ethics agreement that would allow them to sue me if found in breach of it. At the same time they are scraping eBay's data without their consent and refuse to sign the licence agreement. Apparently they don't understand irony.2
-
Omg, when does the Stupid stop? New Zealand just passed a law that empowers immigration officials to compel travellers to unlock their devices. Otherwise, you pay a hefty fine. They are also allowed to copy the data and do God knows what with.
The horrible invasion of privacy aside, it also brings with it some legal hurdles. What if you are making a presentation or report to an investor or someone you have a fiduciary obligation with. You are carrying IP bound by several NDA's and other funding red tape that would end your life if it got out. Are you in breach if the data gets copied by the gov officials? Worse yet you have zero control over what they do afterwards.
I don't think any of this inspires investor confidence.
Government needs to stop touching things!7 -
Yesterday my father called me and asked if I'd have a look at his website to exchange his logo with a new one and make some string changes in the backend. Well, of course I did and hell am I glad I did it.
He had that page made a few years ago by some cousin of a friend who "is really good with computers", it's a small web shop for car parts and, as usual costumer accounts. Costumer Accounts with payment infos.
Now I've seen a lot of bad practices when it comes to handling passwords and I've surely done a few questionable things myself but this idiot took the cake. When a new account was registered his php script would read the login page, look for a specific comment and add a string "'account; password'," below into to a js array. In clear text. On the website. One doesn't even have to breach the db, it's just there, F12 and you got all the log ins.
Seriously, we really need a licensing system for devs, those were two or three years this shit was live, 53 accounts... Now I've gotta decipher this entire bowl of spaghetti just to see if he has done any more unspeakable things.4 -
This happened quite sometime ago.
I received a client, reputable university in my country. After all the paper work was done, I was emailed access to one of their AWS server, FTP where the username and password were both admin. I didn't say much to them at that moment.. Maybe they had some precautions?
Over night I received another email, around 3am,
"Hi Uzair, we've monitored a breach while leaving FTP access open."
Well, that was sorta expected.
I received SFTP access to the server the following day,
username: admin,
password: @dmin3 -
Paranoid Developers - It's a long one
Backstory: I was a freelance web developer when I managed to land a place on a cyber security program with who I consider to be the world leaders in the field (details deliberately withheld; who's paranoid now?). Other than the basic security practices of web dev, my experience with Cyber was limited to the OU introduction course, so I was wholly unprepared for the level of, occasionally hysterical, paranoia that my fellow cohort seemed to perpetually live in. The following is a collection of stories from several of these people, because if I only wrote about one they would accuse me of providing too much data allowing an attacker to aggregate and steal their identity. They do use devrant so if you're reading this, know that I love you and that something is wrong with you.
That time when...
He wrote a social media network with end-to-end encryption before it was cool.
He wrote custom 64kb encryption for his academic HDD.
He removed the 3 HDD from his desktop and stored them in a safe, whenever he left the house.
He set up a pfsense virtualbox with a firewall policy to block the port the student monitoring software used (effectively rendering it useless and definitely in breach of the IT policy).
He used only hashes of passwords as passwords (which isn't actually good).
He kept a drill on the desk ready to destroy his HDD at a moments notice.
He started developing a device to drill through his HDD when he pushed a button. May or may not have finished it.
He set up a new email account for each individual online service.
He hosted a website from his own home server so he didn't have to host the files elsewhere (which is just awful for home network security).
He unplugged the home router and began scanning his devices and manually searching through the process list when his music stopped playing on the laptop several times (turns out he had a wobbly spacebar and the shaking washing machine provided enough jittering for a button press).
He brought his own privacy screen to work (remember, this is a security place, with like background checks and all sorts).
He gave his C programming coursework (a simple messaging program) 2048 bit encryption, which was not required.
He wrote a custom encryption for his other C programming coursework as well as writing out the enigma encryption because there was no library, again not required.
He bought a burner phone to visit the capital city.
He bought a burner phone whenever he left his hometown come to think of it.
He bought a smartphone online, wiped it and installed new firmware (it was Chinese; I'm not saying anything about the Chinese, you're the one thinking it).
He bought a smartphone and installed Kali Linux NetHunter so he could test WiFi networks he connected to before using them on his personal device.
(You might be noticing it's all he's. Maybe it is, maybe it isn't).
He ate a sim card.
He brought a balaclava to pentesting training (it was pretty meme).
He printed out his source code as a manual read-only method.
He made a rule on his academic email to block incoming mail from the academic body (to be fair this is a good spam policy).
He withdraws money from a different cashpoint everytime to avoid patterns in his behaviour (the irony).
He reported someone for hacking the centre's network when they built their own website for practice using XAMMP.
I'm going to stop there. I could tell you so many more stories about these guys, some about them being paranoid and some about the stupid antics Cyber Security and Information Assurance students get up to. Well done for making it this far. Hope you enjoyed it. 26
26 -
The public seems to be worried a lot on the Facebook "data breach" yet doesn't bat an eye on a bigger website that has already been selling private data for more than a decade.
Google9 -
Fucking phone company just sent me a notification, CCing all other business customers they have in Sydney. I am going to sign all those customers to a porn newsletter, and then advise them about the privacy breach.11
-
So instead of using the budget of 7k$ to buy all the plugins the old developer needed, he torrented more than half of them and deployed the system
which ended up in 20 thousand users including companies reporting a breach, because avira etc reported some kind of drive-by scripts on the new website
what a fucking buffoon, the most annoying thing about this is, that all the plugins had a "license file", so I didn't even first get, where all that shit is coming from3 -
Being responsible for a massive breach of personal & financial data.
Seriously, that crap scares me way more than any amount of downtime does.1 -
---WiFi Vision: X-Ray Vision using ambient WiFi signals now possible---
“X-Ray Vision” using WiFi signals isn’t new, though previous methods required knowledge of specific WiFi transmitter placements and connection to the network in question. These limitations made WiFi vision an unlikely security breach, until now.
Cybersecurity researchers at the University of California and University of Chicago have succeeded in detecting the presence and movement of human targets using only ambient WiFi signals and a smartphone.
The researchers designed and implemented a 2-step attack: the 1st step uses statistical data mining from standard off-the-shelf smartphone WiFi detection to “sniff” out WiFi transmitter placements. The 2nd step involves placement of a WiFi sniffer to continuously monitor WiFi transmissions.
Three proposed defenses to the WiFi vision attack are Geofencing, WiFi rate limiting, and signal obfuscation.
Geofencing, or reducing the spatial range of WiFi devices, is a great defense against the attack. For its advantages, however, geofencing is impractical and unlikely to be adopted by most, as the simplest geofencing tactic would also heavily degrade WiFi connectivity.
WiFi rate limiting is effective against the 2nd step attack, but not against the 1st step attack. This is a simple defense to implement, but because of the ubiquity of IoT devices, it is unlikely to be widely adopted as it would reduce the usability of such devices.
Signal obfuscation adds noise to WiFi signals, effectively neutralizing the attack. This is the most user-friendly of all proposed defenses, with minimal impact to user WiFi devices. The biggest drawback to this tactic is the increased bandwidth of WiFi consumption, though compared to the downsides of the other mentioned defenses, signal obfuscation remains the most likely to be widely adopted and optimized for this kind of attack.
For more info, please see journal article linked below.
https://arxiv.org/pdf/...9 -
So at work with the Macs we use, we have some guy come in after hours to service the Macs, and that means the security risk of leaving our passwords on our desks.
Not being a fan of this I tell my boss, he knows it's a risk and despite that he doesn't want this guy coming in while we're here.
Though my main problem is the Mac guy Steve is arrogant and thinks he's a know it all, and with the software I have on the Mac may end up deleting something important, I have git repo and all but I feel off just letting someone touch my computer without me being there.
I tell my boss about the software and stuff he just says contact Steve and tell him about it, to ignore the software and such, I say alright, I write up an email telling him not to touch the software listed and the folders of software documents (again it's all backed up).
No reply, I tell my boss and he says call him, I call him and he hangs up on me on the second ring!
Not sure if he's busy, but I left him a message, asking if he got my email, no reply and it's coming close to the end of the day (going to service Macs in the weekend)
I'm just not going to leave my info because if this guy can't check emails or even get back to someone why should I bother with this bullshit of risking my work.
From all the info I hear about him and my previous rants he's an arrogant prick who loves Macs.
Can't wait to leave this company, pretty sure leaving my password on my desk is a breach of our own security policy, and since 8-9 people are doing it, it's a major risk.
But he's friends with the CEO so apparently it's fuck our own security policy.11 -
- popunder background bitcoin miners did become a thing
- keybase android beta uploaded your privatekey to google servers "accidentally"
- you can spoof email headers via encoded chars, because most apps literally just render them apparently
- imgur leaked 1.7 million user accounts, protected by sha-256 "The company made sure to note that the compromised account information included only email addresses and passwords" - yeah "only", ofcourse imgur, ofcourse.
I guess the rant I did on Krahk etc. just roughly a month ago, can always be topped by something else.
sources:
https://www.mailsploit.com/index
https://bleepingcomputer.com/news/...
https://blog.malwarebytes.com/cyber...
https://helpnetsecurity.com/2017/... undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6
undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
My name is Jimkelly Nzioka, a Flutter Developer from Kenya. A few months ago, a person named Daniel Kibet, the CEO of a company 'Aberison Investments Limited' got in touch with me, telling me that he needed a Flutter Developer. He took me through a couple of tests, as he out them, to gauge my proficiency in Dart and Flutter, since that's what we would use to develop updates fora lthis app on the Google Play Store named 'BOBO' (https://play.google.com/store/apps/...) I passed the test, and he proceeded on to tell me that the app was on Play Store already and he invited me to the office in Miraj Towers, Westlands, Nairobi, Kenya to see it. He presented me with a contract to sign which would go on for a period of 3 years, during which I was to develop the aforementioned app, provide updates maintain the database, etcetera. I live somewhat far from the office and as such, I would work remotely from home, making commits to a Github repository we created for the project. I did a bunch of work for them, including working in the UI (which really needed a lot of work), writing loads of Cloud Functions, as well as Cloud Tasks for functionality they needed. They would also consult with me concerning how to achive some functionality in code and I would offer my honest advice and suggestions. Things seemed to be going on well, until the start of this month. As per the contract, I was to bill the company a sum of Ksh 50, 000 every month that's roughly equivalent to $500. That was enough for me, seeing as I am still a student in University, and I would be working on it as a part time job. However, as of today, September 8, 2020, he has refused to pay me for my work and is ignoring, sometimes canceling any phone calls I make to him. In addition, I noticed he has restricted my access to the Firebase project
I know you probably don't know this person, but you are developers and engineers, and know what it would feel like if you realized someone has been using you, when all along you have been doing your level best to just do your work
Employers have to stop taking advantage of their employees for their own selfish gains19 -
A new breach has just been confirmed about 10 minutes ago. CHECK YOUR EMAILS AND PASSWORDS!!!
Details at: https://troyhunt.com/the-773-millio...
CHECK YOUR EMAILS AND PASSWORDS AT haveibeenpwned.com TO CHECK FOR WHETHER YOU WERE COMPROMISED.9 -
This has been here for years already but with the recent data breach scandles which also highlights how they profit from me, u'd think they would cancel this small amount which is wronggfully charged to start with....
I've even tried ccontacting them about it... for years.... and they don't respond.... EVER...
So much for listening to users... clearly they don't... 4
4 -
So today I found a way to break into any Apple Mac (provided the exploit hasn't been fixed by the owner) and access all private files, as long as I have physical access to it, in less than 5 minutes.
After finding this, a quick Google on the method reveals this has been a workaround for years.
And to think I once praised Apple for their security standards.
Edit: this was done to an in-house Mac that my company own, and had been password locked by a member of staff who had been fired, but held important company documents on the computer. It was in no way a breach of privacy.7 -
I’m LOLing at the audacity of one of our vendors.
We contract with a vendor to build and maintain a website. Our network security team noticed there was a security breach of the vendor’s website. Our team saw that malicious users gained access to our Google Search console by completing a challenge that was issued to the vendor’s site.
At first, the vendor tried to convince us that their site wasn’t comprised and it was the Google search Console that was compromised. Nah dude. Our Search Console got compromised via the website you maintain for us. Luckily our network team was able to remove the malicious users from our search console.
That vendor site accepts credit card payments and displays the user’s contact info like address, email, and phone. The vendor uses keys that are tied to our payment gateway. So now my employer is demanding a full incident report from the vendor because their dropping the ball could have compromised our users’ data and we might be responsible for PCI issues.
And the vendor tried to shit on us even more. The vendor also generates vanity urls for our users. My employer decided to temporarily redirect users to our main site (non vendor) because users already received those links and in order to not lose revenue. The vendor’s solution is to build a service that will redirect their vanity urls to our main site. And they wanted to charge us $5000 usd for this. We already pay them $1000 a month already.
WTAF we are not stupid. Our network service team said we could make the argument that they do this without extra charge because it falls in the scope of our contract with them. Our network team also said that we could terminate the contract because the security breach means they didn’t render the service they were contracted to do. Guess it’s time for us to get our lawyer’s take on this.
So now it looks like my stakeholders want me to rebuild all of this in house. I already have a lot on my plate, but I’m going to be open to their requests because we are still in the debrief phase.2 -
A few years ago I was in high school and used to have a small reputation of hacking things. I could hack, just would never hack any school networks or systems (reputation + notice that there was a breach is a bad combo since everyone would immediately suspect you).
Anyways one day the networks internet connection went down in the school district and I was the only one who used a laptop to take notes. So I quickly opened the terminal and ran Wireshark and said to the person to my right "see that button there? yeah I programmed this last night. anytime I press it I can shut down the network so the teacher can't reach her files (she famously only saved them online). *Long dramatic press* Wireshark started scanning the network so all the numbers and lines were going crazy as it viewed the packet info "Now just wait", soon the whole class knew what I had done through whispers and lo and behold a few minutes later and the teacher couldn't reach her files.
Everyone loved me for the rest of the year for saving them from the homework for the week the wifi network was out since it also ended up having to cancel two tests in the class, and a lot more homework and tests in all their other classes. Solidified my reputation and no one fucked with me from that day on. -
Not the worst, but probably the only one I can sort of explain & not get into trouble for NDA breach..
Umm.. here it goes.. wrong id returned from db procedure, tried to do something on db with that id and got exception that the id doesn't exist. Instead of checking why the procedure returns nonexistent id, he just wrapped everything in try catch without any logs.. & of course, didn't tell anyone about this.. o.0
I know, I know, code review could have prevented this, but holy fuck..
Guy's cv had more experience than I have now, so at the time, I didn't think I'd have to check every line of code he wrote, especially not for shit like this.3 -
why people around me act like dump. i have recently worked with this site, which is written in php.
customer: (yelling) my website is hacked, fix it immediately
me : ok sir, we will restore your site immediately
after finishing talk with customer. i have checked website, there is no sign of website being hacked. i have checked server logs and website for security breach, there is no sign.
me: your website is not hacked, sir. can you please tell me where you have seen hacked page.
customer: look at those pages
after seen that page i facepalmed myself. it's a bug, person who created that page just splitted string without using any multibyte function, so page is showing with corrupted characters. i fixed it and problem solved. i have told about that bug, to the person who created that page.
me: hey you have used this function which is not able to handle multibyte characters, you should use multibyte character functions for that one.
person: every characters are the same. we shouldn't need to handle that way.
he is actually a senior developer. who don't even know the difference between unicode and ascii characters.1 -
At work, my closest relation is with the DBA. Dude is a genius when it comes to proper database management as well as having a very high level of understanding concerning server administration, how he got that good at that I have no clue, he just says that he likes to fuck around with servers, Linux in particular although he also knows a lot about Windows servers.
Thing is, the dude used to work as a dev way back when VB pre VB.NET was all the rage and has been generating different small tools for his team of analysts(I used to be a part of his team) to use with only him maintaining them. He mentioned how he did not like how Microsoft just said fk u to VB6 developers, but that he was happy as long as he could use VB. He relearned how to do most of the GUI stuff he was used to do with VB6 into VB.NEt and all was good with the world. I have seen his code, proper OOP practices and architectural decisions, etc etc. Nothing to complain about his code, seems easy enough to extend, properly documented as well.
Then he got with me in order to figure out how to breach the gap between building GUI applications into web form, so that we could just host those apps in one of our servers and his users go from there, boy was he not prepared to see the amount of fuckery that we do in the web development world. Last time my dude touched web development there was still Classic ASP with JScript and VBScript(we actually had the same employer at one point in the past in which I had to deal with said technology, not bad, but definitely not something I recommend for the current state of web development) and decided that the closest thing to what he was used was either PHP(which he did not enjoy, no problem with that really, he just didn't click with the language) and WebForms using VB.NET, which he also did not like on account of them basically being on support mode since Microsoft is really pushing for people to adopt dotnet core.
After came ASP.NET with MVC, now, he did like it, but still had that lil bug in his head that told him that sticking to core was probably a better idea since he was just starting, why not start with the newest and greatest? Then in hit(both of us actually) that to this day Microsoft still not has command line templates for building web applications in .net core using VB.NET. I thought it was weird, so I decided to look into. Turns out, that without using Razor, you can actually build Web APIs with VB.NET just fine if you just convert a C# template into VB.NET, the process was...err....tricky, and not something we would want to do for other projects, with that in we decided to look into Microsoft's reasons to not have VB.NET. We discovered how Microsoft is not keeping the same language features between both languages, having crown C# as the language of choice for everything Microsoft, to this point, it seems that Microsoft was much more focused in developing features for the excellent F# way more than it ever had for VB.NET at this point and that it was not a major strategy for them to adapt most of the .net core functionality inside of VB, we found articles when the very same Microsoft team stated of how they will be slowly adding the required support for VB and that on version 5 we would definitely have proper support for VB.NET ALTHOUGH they will not be adding any new development into the language.
Past experience with Microsoft seems to point at them getting more and more ready to completely drop the language, it does not matter how many people use it, they would still kill it :P I personally would rather keep it, or open source the language's features so that people can keep adding support to it(if they can of course) because of its historical significance rather than them just completely dropping the language. I prefer using C#, and most of my .net core applications use C#, its very similar to Java on a lot of things(although very much different in others) and I am fine with it being the main language. I just think that it sucks to leave such a large developer pool in the shadows with their preferred tool of choice and force them to use something else just like that.
My boy is currently looking at how I developed a sample api with validation, user management, mediatR and a custom project structure as well as a client side application using React and typescript swappable with another one built using Angular(i wanted to test the differences to see which one I prefer, React with Typescript is beautiful, would not want to use it without it) and he is hating every minute of it on account of how complex frontend development has become :V
Just wanted to vent a little about a non bothersome situation.6 -
Just saw this:
Add comma's to your passwords to mess with the csv file they will be dumped in after a data breach9 -
Today my fellow @EaZyCode found out a local Hosting Provider has a massive security breach.
He wrote an Plugin for Minecraft with an own file explorer and the ability to execute runtime commands over it.
We discovered that this specific hosting provider stores the ftp passwords one level above the FTP-Root. In FUCKING PLAIN TEXT! AND THE MYSQL PASSWORD TOO! And even more shit is stored there ready to be viewed by intelligent people...
It's one of the fucking biggest Hosting provider Germanys!
But, because EaZyCode has such a great mind and always find such bugs, I give him the title "Providers Endboss" today, he has earned it.
Loving you ❤️
Edit: we used SendMail with runtime commands and sended too many empty Spammails (regret noting)18 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
I am doing some freelance work for a client who is thankfully mindful about security. I found out that they are so strict with their access because they had a huge data breach last year.
Today I was given access to their repo for connecting to their AS400. In the docker file the username and password were included and were the same for dev and prod. They also are performing no sql injection prevention. They are just joining strings together.1 -
developer makes a "missed-a-semicolon"-kind of mistake that brings your non-production infrastructure down.
manager goes crazy. rallies the whole team into a meeting to find "whom to hold accountable for this stupid mistake" ( read : whom should I blame? ).
spend 1-hour to investigate the problem. send out another developer to fix the problem.
... continue digging ...
( with every step in the software development lifecycle handbook; the only step missing was to pull the handbook itself out )
finds that the developer followed the development process well ( no hoops jumped ).
the error was missed during the code review because the reviewer didn't actually "review" the code, but reported that they had "reviewed and merged" the code
get asked why we're all spending time trying to fix a problem that occurred in a non-production environment. apparently, now it is about figuring out the root cause so that it doesn't happen in production.
we're ALL now staring at the SAME pull request. now the manager is suddenly more mad because the developer used brackets to indicate the pseudo-path where the change occurred.
"WHY WOULD YOU WASTE 30-SECONDS PUTTING ALL THOSE BRACES? YOU'RE ALREADY ON A BRANCH!"
PS : the reason I didn't quote any of the manager's words until the end was because they were screaming all along, so, I'd have to type in ALL CAPS-case. I'm a CAPS-case-hater by-default ( except for the singular use of "I" ( eye; indicating myself ) )
WTF? I mean, walk your temper off first ( I don't mean literally, right now; for now, consider it a figure of speech. I wish I could ask you to do it literally; but no, I'm not that much of a sadist just yet ). Then come back and decide what you actually want to be pissed about. Then think more; about whether you want to kill everyone else's productivity by rallying the entire team ( OK, I'm exaggerating, it's a small team of 4 people; excluding the manager ) to look at an issue that happened in a non-production environment.
At the end of the week, you're still going to come back and say we're behind schedule because we didn't get any work done.
Well, here's 4 hours of our time consumed away by you.
This manager also has a habit of saying, "getting on X's case". Even if it is a discussion ( and not a debate ). What is that supposed to mean? Did X commit such a grave crime that they need to be condemned to hell?
I miss my old organization where there was a strict no-blame policy. Their strategy was, "OK, we have an issue, let's fix it and move on."
I've gotten involved ( not caused it ) in even bigger issues ( like an almost-data-breach ) and nobody ever pointed a finger at another person.
Even though we all knew who caused the issue. Some even went beyond and defended the person. Like, "Them. No, that's not possible. They won't do such dumb mistakes. They're very thorough with their work."
No one even talked about the person behind their back either ( at least I wasn't involved in any such conversation ). Even later, after the whole issue had settled down. I don't think people brought it up later either ( though it was kind of a hush-hush need-to-know event )
Now I realize the other unsaid-advantage of the no-blame policy. You don't lose 4 hours of your so-called "quarantine productivity". We're already short on productivity. Please don't add anymore. 🙏10 -
!Rant
The new bill passed the house for ISP to be able to sell data. This get me ticked off. I already ausme that ISP did it under the table. Doesn't make it right. Now it legal for them to breach our privacy. At what leave do i need to run my own internet just to feel safe. VPN can sell the data, ISP can sell data about you. I spend my life teaching how to protect people online and now I can't even say they are safe at home from someone with wrong intention. A quote comes to mind.
"Dear lord I need to see some change, because the man in the mirror is wearing a mask"
I shouldn't have to feel every time. I boot my PC, that I need to remind my self that what I'm doing now is being sold so someone can lable me. When will the common man learn to protect their privacy online; And where is the line in the sand?
It not all bad, this event has given me the itch to code. Just to spin some heads I'm going to make a script to make random Google query across the widest array of topics, so my profile is full of contradiction.
The few who read this have a nice day!6 -
"This is now urgent we are in risk of breach of contract."
*travels an hour just to discuss*
"Oh don't worry, don't panick about it, so and so is probably sorting it. We most likely don't need it."1 -
So recently a 0-day exploit was discovered in WP plugin Kaswara Modern WP Bakery Page (https://zdnet.com/article/...).
A customer's shared hosting space was taken down (about 6 websites) after this vulnerability had been exploited and although we removed the malicious code, & changed credentials the hosting company demands we update ALL Wordpress plugins to latest AND provide them a virus scan report of our local PC before putting the webspace back online??? WTF???
That just strikes me as outrageous. Thoughts? 10
10 -
Part 1: https://devrant.com/rants/4298172/...
So we get this guy in a meeting and he is now saying "we can't have application accounts because that violates our standard of knowing who accessed what data - the application account anonamizes the user behind the app account data transaction and authorization"
And so i remind him that since it's an application account, no one is going to see the data in transit (for reference this account is for CI/CD), so the identity that accessed that data really is only the app account and no one else.
This man has the audacity to come back with "oh well then thats fine, i cant think of a bunch of other app account ideas where the data is then shown to non-approved individuals"
We have controls in place to make sure this doesnt happen, and his grand example that he illustrates is "Well what if someone created an app account to pull github repo data and then display that in a web interface to unauthorized users"
...
M******* why wouldnt you JUST USE GITHUB??? WHO WOULD BUILD A SEPARATE APPLICATION FOR THAT???
I swear I have sunk more time into this than it would have costed me to mop up from a whole data breach. I know there are situations where you could potentially expose data to the wrong users, but that's the same issue with User Accounts (see my first rant with the GDrive example). In addition, the proposed alternative is "just dont use CI/CD"!!!
I'm getting pretty pissed off at this whole "My compliance is worth more than real security" bullshit. -
The company that manages my ISA for Lambda emails on a regular basis to get you to update your income. I got annoyed by the frequency while I was employed so started filtering everything.
Though I’ve been up to date with reporting income to them and submitting tax documents, etc, I apparently missed some important emails.
Like the one on the 4th saying a third party provider flagged by account for employment with CompanyA and that I needed to submit my pay stubs for CompanyA.
I do not and have never worked for CompanyA. My husband works for CompanyA.
I also missed the email from the 12th saying I’m in breach of contract and owe them $19,091.65 immediately.
*head desk*
I’m so mad I can’t even.
Why did i check my email before going to sleep?
AND I POSTED RECENTLY SO I CAN’T EVEN RANT YET. *
*Waited it out -
Just found a breach somewhere in the university's meal booking system, that exposes some good 60K records of students, professors and staff orders and payments.
It's just that I am behind this shitty web UI with 20 rows per page table as the only option.
Now how 1337 is that?6 -
I hate that the company that I work for has every hugging page blocked. I can't even download or use pip. For hug sake, I don't even have a project to work on and you stop me from working on any side projects?
I hope I get a call from the places I've applied for.4 -
There are 2 kinds of websites:
1 - The bad kind where not accepting their cookies boots you off the site (And so are in breach of GDPR... IIRC)
2 - Sites that continue working, albeit in a degraded / suboptimal state, even when you refuse their cookies.
I wish more sites were of the second variety. I'm even the only person among my friends who actually bothers going through the consent forms and disallowing everything marketing-related.
OneTrust is good. It at least remembers my preferences.3 -
Company created an FTP account for me on one of their servers as they were lazy to fix file permissions.
24 hours later, they monitored a breach and closed the FTP account.
Just to add that the initial password that they sent me was super weak.1 -
Sooo... The ways my coworker fucks me:
Last week I have been working on setting up aWireGuard VPN server... Been trying for 4 FUCKING DAYS, the easiest VPN that has ever existed, 2 commands and that's it, I wasn't able to reach it, I checked every forum, tested every possible solution without success, checking ubuntu firewall but it was inactive... Nothing that should cause this. Why? 2 weeks ago we had a security breach and my coworker added a firewall from the cloud console with basic rules allowing only 3 ports, the port I was communicating with was blocked. He didn't bother to mention that he added an external firewall. And the junior me, not wanting to be a pain in the ass, and since that security breach wasn't my responsibility to fix, I didn't ask too many questions, just read the emails going back and forth and "learning" how to deal with that. Kill me please. Next mont a new guy is joining, we had a "quick meeting" of 30 minutes and he managed to make it 2 hours meeting. So a partner who lacks communication and a partner who talks a lot... Will be fun. And I probably should change my username... Is that even possible? @root?10 -
So a ticketmaster security breach.
If you bought tickets using ticketmaster between September-2017 and June-2018 beware. Globally.
https://zdnet.com/article/... -
fellow dev thought he was being clever, hiding his private ssh keys inside image files on a public web server...2
-
How many secret SSH keys has Apple already captured with their shiny new iCloud Clipboard Sync on Sierra?4
-
Why is everyone saying we should be doing DRY but we really end up defining the same shit everywhere?
Does separation of concern breach DRY principle?
I have dtos, entities, viewmodels all throughout different layers I have to define. I swear I've changed 8 files just to introduce a new field!!!5 -
Had a client whom was using the staging system on my server as cdn, remote computing, etc... because his prod server was a cheap vhost while the vm was a beast compared to it. I shut it down without telling. I just got a call that his site is now slow a f and full of errors.
I kindly told him that there was a recent security breach called dirty cow. Then I told him that I shut the vm down because it would mean security risk for him since there are no patches available yet and only Power on again with there was work for me to do.
If you want resources pay for them -
No idea what the fuck just happened, but my home router just dropped the internet connection and started demanding that I change the admin (default) password.
Now, I know that default passwords are bad and all that, but why the fuck now? This thing has been sitting there for over a year, and it only decided to complain now?
There have been some weird things going on lately, and I'm starting to worry that some of my systems may have been compromised in some way... but I'm not sure what/how, nor how to look for it...
Any tips for identifying a breach and disaster recovery?10 -
🚀 *iBOLT CYBER HACKER: Cryptocurrency Recovery & Advanced Hacking Solutions!* 🦊💻
🔐 *Lost access to your crypto wallet or had your funds stolen?* Don’t worry— iBOLT CYBER HACKER is here to help you recover your cryptocurrency with cutting-edge technical expertise.
💡 With years of experience in the crypto world, iBOLT CYBER HACKER employs the latest tools and ethical hacking techniques to help you recover lost assets, unlock hacked accounts, and retrieve funds from inaccessible exchanges.
⚡ Whether it’s a forgotten password, an accidental transfer, investment scam, or a major security breach, iBOLT CYBER HACKER has the expertise to help you get your crypto back.
- General phone hacking and monitoring
- Money recovery from scammers
- Bitcoin and PayPal recovery
- Mobile phone monitoring
- Hacking and modifying university grades
- Bank website hacking and fund transfers
- Database hacking with admin privileges
👉 *Contact iBOLT CYBER HACKER for professional assistance
📧 𝐄𝐦𝐚𝐢𝐥: Support @ibolt cybarhack. com
𝐨𝐫
📲 𝐖𝐡𝐚𝐭𝐬𝐀𝐩𝐩: +39, 351..105, 3619
http s:// ibolt cybarhack. com1 -
My email address appeared in a new data breach at gravatar. I thought that's exactly gravatar's purpose, to make my email address publicly known and provide an additional profile picture?
 1
1 -
HOW I CAUGHT MY CHEATING PARTNER WITH THE HELP OF SOLACE CYBER WORKSTATIONS
Solace Cyber Workstations is a tool designed to help individuals find important information about their partner's online activities without causing any disruption or breach of privacy. This software works by gathering data that is publicly available, allowing users to understand more about their partner's digital presence. It can include social media profiles, public posts, and other online interactions, making it a comprehensive solution for those seeking clarity in their relationships. Using Solace Cyber Workstations is simple and user-friendly. The interface guides users step-by-step through the process of retrieving information. There are no complicated setups or technical skills needed. Once the user inputs the relevant details, the tool quickly navigates the internet to compile the necessary data, ensuring a seamless and efficient process. This ease of use supports individuals in their quest for knowledge about their partner's online life. One of the key features of Solace Cyber Workstations is its commitment to non-intrusiveness. The tool respects privacy and ensures that all information collected is taken from public sources. This means that users can learn more about their partner without violating their privacy or crossing any ethical boundaries. Users can feel comfortable knowing they are not engaging in any harmful or invasive practices while seeking information. Moreover, Solace Cyber Workstations are particularly useful for individuals looking to enhance trust and communication in their relationships. By using this tool, users can clarify any doubts they may have about their partner's online presence. Understanding their partner’s online interactions can lead to more open discussions and strengthen the bond between both individuals, ultimately fostering a healthier environment for the relationship. In conclusion, Solace Cyber Workstations provides a reliable and respectful way to learn about a partner's online life. Its user-friendly interface and non-intrusive methods make it an ideal choice for those who want to ensure transparency while maintaining ethical standards. By utilizing this tool, users can promote understanding and trust in their relationships, which is essential for long-term success. Send a W h a t s A pp D M via: +1 2 4 0 7 4 3 7 6 8 9
Thanks.9 -
I can't believe companies fucking do this! If your users PIIs gets fucking leaked or the security is breached in any god-damned way it's YOUR FUCKING JOB to let the affected users know! 57 million users got affected! What the fucking fuck? I think they should pass proper laws where companies have to tell the victims about breaches, especially when it's at a such a huge scale. I get it that it's wasn't under Uber but some third party; but even so Uber should have talked about the level of security in their SLAs and maybe performed regular audits.
This is ridiculous!
https://darkreading.com/attacks-bre...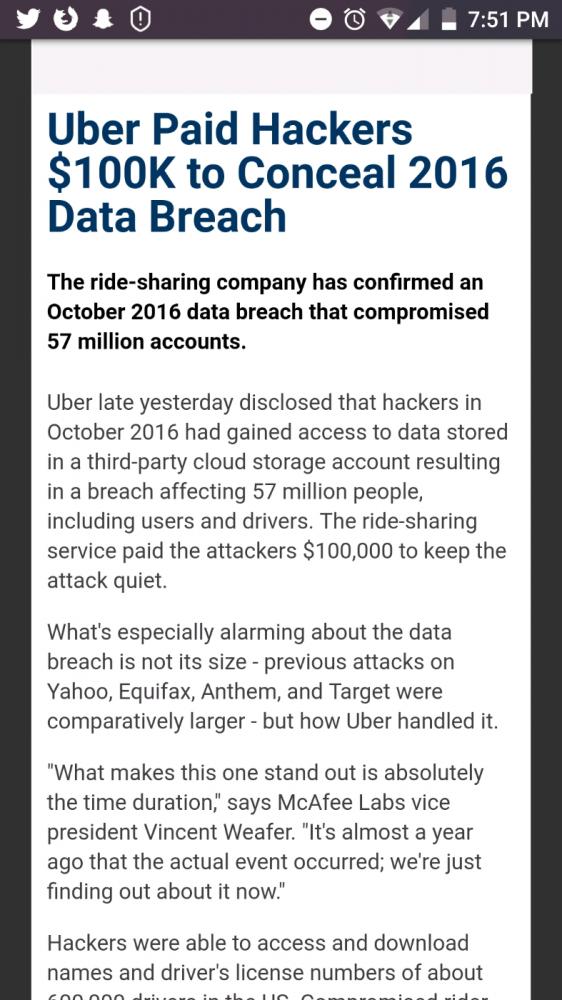 5
5 -
I just used a contact form of a local webshop. I couldnt enter my email address because it contains a +.
I contacted them to tell them about this issue and the response was it is because of security reasons. Since when is following specs a security breach? Unless their system is one leak I don't see how its possible.
Am I wrong or did they either lie or have a leak in their system?2 -
Can't really say it's the most pissed off I've been probably at mild annoyance. So for the last two years I've been stressing that in order to do my job efficiently. I need handovers and documentation. It's a ball ache I know but definitely needed.
Well after not being listened too for the last two years we now are getting a documentation process. Why? Because a lack of documentation was the leading cause to a data breach.
Yeah I've been stressing that scenario for the last two years. But no one gave a damn until it happened. -
How is it possible my netflix password got hacked when I never used it anywhere else and it's randomly generated? I saw some weird logins with random subtitles. Google password manager told me it's in some data breach, how do I find out from where? Haveibeenpwned didn't find anything. 😐6
-
Question to all those who have worked with software architecture: What is your approach when implementing architecture and design into actual software?
I find it very hard to translate UML diagrams and architectural requirements into working code and I feel like there is quite a big "gap" between the two. How to you breach that gap and manage to maintain a clean and comprehensive architecture in your project folders?question clean architecture architecture requirements patterns suggestions project structure clean code software engineering11 -
One of our senior colleagues in my last project at TCS had brought a pen drive with him, not sure why! He worked on a client system, which he believed was not monitored by TCS. So what he did was, he plugged in the pen drive in his computer and tried to copy some files from his pen drive to the computer. However, he wasn’t able to copy the files.
We weren’t aware of this until our project manager, who sits at the farthest end of the ODC shouted at the top of his voice, calling out his name. In front of the entire ODC, he was scolded since the HR team had called the manager informing that the machine assigned under this employee’s name has detected a security breach.
He had to explain the reason; where he said he wanted to copy some codes that he had to office machine in order to reduce his manual effort, which was probably very silly of him! For the next few days I hardly saw him inside the ODC, probably had to visit people to show cause or other things and was harrassed by our manager, insulted every time he passed by him.
He was not suspended although, maybe the manager or someone else saved him, although normally such violations would have seen him terminated.3 -
Prank idea: call a colleague's phone and if they don't have your number (you'll notice by the way they talk), they won't know it's you. Then try to convince them they've somehow created a data breach and you have access to their company's source code... 😈
Oh, and if they do have your number just say you accidentally called the wrong person. -
My little journey of regrets:
I remember when I was fourteen, I opened a small gap the door of "programming". It were the first steps of html, tags and what they do, to be precise.
"May, looks good. Thanks for the glimpse. Cya"
For about the other half of my life only magic happened at my desktop.
And now I'm standing once again at the door of programming trying to breach it with nukes n shit.
"Giev me all the knowledge plx, teach me senpai! I will never ignore and betray you again!" -
recently noticed that Github is warning some users that their password has been compromised in a data breach by "HaveIBeenPwned". what is this about?8
-
The NPC has stated that the personal data of atleast 2000 people was leaked after the attacks on the websites of the philippinian goverment on april 1, the data contains; names,adresses,passwords and school data.
Over 7 administrators of schools, universities and other goverment structures have been called out for not reporting on the leakage of personal info on public facebook groups and violaton of the NPC in under 72 hours.
The representatives of the next structures stood before the comission on the 23 and 24 of april
- Taguig City University
- Department of Education offices in Bacoor City and Calamba City
- the Province of Bulacan
- Philippine Carabao Center
- Republic Central Colleges in Angeles City
- Laguna State Polytechnic University
The agency has reported that none of the organisations had notified about the personal info leakage yet.
This is a good reminder that you should inform about security/personal info breaches everyone that might be related to it as soon as possible, even if it seems unecessary. -
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
So I just started using the app called Rmabox and it seems pretty useful. Actually I am ranting using the same app. Keeps all my social profiles at one place. But I am concerned about my privacy as well. Is it safe to use such apps which help you to manage all your social accounts at one place? Will that not create a single point of security breach?1
-
Recovering Investment Losses with GearHead Engineers Cyber Security Services
In today’s increasingly digital financial landscape, investors face growing threats from cybercriminals targeting everything from brokerage accounts to blockchain-based assets. For individuals and businesses alike, falling victim to a cyberattack or financial scam can be devastating. Fortunately, firms like GearHead Engineers, known for their advanced cybersecurity services, are stepping in to help investors recover losses and, more importantly, prevent future breaches.
The Rise of Cyber-Investment Threats
As digital platforms have become the norm for managing investments, they’ve also become a prime target for hackers. Common threats include:
* Phishing scams that trick users into revealing login credentials.
* Ransomware attacks on financial firms.
* Malware that siphons personal and financial data.
* DeFi and cryptocurrency hacks exploiting insecure smart contracts or user wallets.
The financial implications can be enormous, especially when assets are stolen, trading accounts are compromised, or confidential investment strategies are exposed.
GearHead Engineers: A Cybersecurity Partner for Investors
GearHead Engineers specializes in protecting financial data, systems, and transactions with comprehensive cybersecurity strategies tailored to modern digital investment environments. Their services include:
* Threat Detection & Response: 24/7 monitoring of systems to identify unusual activity before it becomes a serious threat.
* Incident Forensics: In the event of a breach, GearHead Engineers conduct thorough investigations to trace the source, identify vulnerabilities, and assist in recovery efforts.
* Asset Recovery Support: While not a financial firm, GearHead can coordinate with law enforcement and digital forensics specialists to trace stolen digital assets, especially in cryptocurrency-related incidents.
* Security Audits & Penetration Testing: Preemptive testing of platforms and networks to find and fix security holes before hackers do.
* Cyber Insurance Advisory: Guidance on cyber insurance coverage and how to maximize your protection and potential reimbursement in case of a loss.
Real-World Application: Turning Loss into Learning
Clients who’ve suffered financial loss due to cyber incidents often find that working with cybersecurity experts like GearHead Engineers is a turning point. Not only can the firm help assess whether any funds are recoverable (especially in crypto and digital asset cases), but it also strengthens the client's defense moving forward.
By implementing robust firewalls, multi-factor authentication, encryption, and behavioral analytics, GearHead Engineers empowers investors to take control of their digital financial security.
Conclusion: Proactive Security is Smart Investment Strategy
Recovering from a cyberattack is never easy, but it’s possible—especially with the right partners. GearHead Engineers brings a unique blend of technical expertise and practical support to help victims of cyber fraud bounce back and secure their future. For investors, engaging in strong cybersecurity isn’t just risk management—it’s a smart investment in itself.4 -
Start my code day, no bugs in sight,
Each line I write, like code's delight.
Second function, errors suppressed,
Silent fixes, my skills put to the test.
Third loop, logic numb, yet breaking,
A contradiction in every line I'm making.
Fourth bug, clinging like a leech,
In the grip of coding's caffeine breach.
Fifth syntax, thoughtless actions cascade,
A program's dance, in lines arrayed.
Sixth compile, colleagues say, 'Go home,'
But where's home in this code dome?
'They say home is where the heart is,
But my heart's in a million logic twists,
Which line shall I follow?
The optimized or the broken,
I cannot tell them apart.'
In the last bit of code, I saved my hope,
When debugging was still an option,
So go ahead and save yourself from glitches,
For you are worthy of a million exceptions. -
Its normal if i drop some eyedrop at my new job ? My boss don't know anything of is network ... Cannot help me with noting no code no net... All the code is done already is a deep shit full of breach im fucking solo in a room face a brick wall no window ! Can i stay for 10 month at this place ?
Need to coding but have no cluse how to connect to a fucking database no user no password ...
Its the fucking hell here 👿😢3 -
This is why you keep production data separate -- and out of the hands of developers: http://businessinsider.com/uber-emp...3
-
I HATE THIS SLOWLY FUCKASS CHEAPIE COMPUTER IT'S SO SLOWWWWW
I can't focus and actually do antything you nasty typerfucker son of a breach and I have to do CSS with the biggest headache ever holy fucking adamantine shitty shit -
Approx. 24 hours ago I proceeded to use MEGA NZ to download a file It's something I've done before. I have an account with them.
This is part of the email I received from MEGA NZ following the dowload: "
zemenwambuis2015@gmail.com
YOUR MEGA ACCOUNT HAS BEEN LOCKED FOR YOUR SAFETY; WE SUSPECT THAT YOU ARE USING THE SAME PASSWORD FOR YOUR MEGA ACCOUNT AS FOR OTHER SERVICES, AND THAT AT LEAST ONE OF THESE OTHER SERVICES HAS SUFFERED A DATA BREACH.
While MEGA remains secure, many big players have suffered a data breach (e.g. yahoo.com, dropbox.com, linkedin.com, adobe.com, myspace.com, tumblr.com, last.fm, snapchat.com, ashleymadison.com - check haveibeenpwned.com/PwnedWebsites for details), exposing millions of users who have used the same password on multiple services to credential stuffers (https://en.wikipedia.org/wiki/...). Your password leaked and is now being used by bad actors to log into your accounts, including, but not limited to, your MEGA account.
To unlock your MEGA account, please follow the link below. You will be required to change your account password - please use a strong password that you have not used anywhere else. We also recommend you change the passwords you have used on other services to strong, unique passwords. Do not ever reuse a password.
Verify my email
Didn’t work? Copy the link below into your web browser:
https://mega.nz//...
To prevent this from happening in the future, use a strong and unique password. Please also make sure you do not lose your password, otherwise you will lose access to your data; MEGA strongly recommends the use of a password manager. For more info on best security practices see: https://mega.nz/security
Best regards,
— Team MEGA
Mega Limited 2020."
Who in their right mind is going to believe something like that that's worded so poorly.
Can anybody shed some light on this latest bit of MEGA's fuckery?
Thank you very much.4 -
RECLAIM YOUR LOST CRYPTOCURRENCY TODAY WITH TRUSTED EXPERTS - HIRE HACKATHON TECH SOLUTIONS
The sudden disappearance of your cryptocurrency holdings, whether due to a sophisticated cyberattack, a deceptive scam, or simply misplaced access credentials, can feel like a financial disaster. During these crucial times, HACKATHON TECH SOLUTIONS provides the ultimate solution for digital asset restoration, offering unmatched expertise in recovering Bitcoin, Ethereum, and a vast array of altcoins.What sets HACKATHON TECH SOLUTIONS unique from the rest is their elite team of blockchain forensic specialists, who combine cutting-edge technology with in-depth investigative methods. These experts utilize advanced cryptographic analysis to thoroughly trace transaction histories across decentralized ledgers, uncovering vulnerabilities and exploiting weaknesses in even the most complicated theft schemes. Their approach goes far beyond basic wallet recovery services, employing proprietary tools to navigate the often murky world of blockchain transactions.The recovery process begins with an in-depth consultation where clients provide essential information about the loss, including transaction records, wallet addresses, and details about the breach or incident. The forensic team then embarks on a multi-faceted investigation, combing through blockchain data across various networks and exchanges to uncover digital traces that might otherwise remain invisible.What truly sets HACKATHON TECH SOLUTIONS apart is their strategic and proactive approach to fund retrieval. They don’t simply trace stolen assets, they craft customized recovery plans, collaborating with cryptocurrency exchanges, legal authorities, and even international organizations. Their specialists know exactly when to intercept frozen funds, reconstruct private keys, or employ advanced social engineering tactics to retrieve assets from scammers.Their recovery process is highly detailed, utilizing a range of investigative techniques that leave no stone unturned. Whether dealing with a direct theft, hacking incident, or even accidental loss due to a misplaced private key, HACKATHON TECH SOLUTIONS team can step in and provide a targeted, expert solution. In a world where cryptocurrency is often seen as a difficult asset to recover once lost, HACKATHON TECH SOLUTIONS ability to navigate the complexities of digital asset recovery gives clients peace of mind that they can recover even the most elusive of funds. When the stakes are high, their specialized expertise to restoring digital assets make them the definitive choice for anyone facing the loss of cryptocurrency holdings. Their contact details are listed below.
Whatsapp:+31 6 47999256
Telegram: +1(659) 217-9239
Email: hackathontech service @ mail . com7 -
HOW TO HIRE A GENUINE CRYPTO RECOVERY SERVICE CONTACT SPARTAN TECH GROUP RETRIEVAL
All the time, I had believed in networking, but I never knew that a local crypto meetup would save me from financial disaster. Discussion at the event ranged from trading strategies to security tips, but one name cropped up repeatedly that sounded impressive: SPARTAN TECH GROUP RETRIEVAL. Many spoke about how that service had rescued them from lost wallets, forgotten passwords, and even cyber-attacks. I filed that away mentally but never thought I'd find myself in that position. That changed just weeks later. One morning, I went into my Bitcoin wallet and saw suspicious activity. My heart sank as I realized that $180,000 in crypto was on the line. Someone had access, and if I didn't act fast, I'd lose everything. Panic set in, and I scrambled to figure out how it happened: had I clicked a phishing link, was my private key compromised? No matter the cause, I needed help. And fast. That's when I remembered the crypto meetup. I scrolled through my notes and found SPARTAN TECH GROUP RETRIEVAL's name. With no time to waste, I sent a reply-my anxious and desperate words spilling into one frenetic sentence. They responded very fast and professionally. They immediately initiated an investigation into my wallet's transaction history and security logs. They were able to trace the breach and lock it, trying not to be late in recovering the stolen money. Then they worked around the clock for several days, coordinating tracking on the blockchain, forensic data recovery, and reinforcements of security. I barely slept, but at each and every stage, they kept reassuring me. Then came that call I was praying for: They had recovered my funds. Speechless. Relieved. Grateful. But SPARTAN TECH GROUP RETRIEVAL didn't just stop with the recovery, teaching me means of security practices, helped fortify the defense around my wallet, and making sure this does not happen again. I consider it one of the best I have done so far-attending that crypto meet-up. I might never have heard of SPARTAN TECH GROUP RETRIEVAL if it had not been that night, or the outcome worse. Now I do my best to spread the word. For a reason is their reputation preceding them, and personally I can vouch for their expertise, efficiency, and reliability.
SPARTAN TECH GROUP RETRIEVAL CONTACT INFO:
Email: spartantech (@) cyber services . com OR support (@) spartantechgroupretrieval. org
Website : h t t p s : / / spartantechgroupretrieval. org
WhatsApp: +1 (971) 487 - 3538
Telegram: +1 (581) 286 - 8092 6
6 -
My aspiration is to create green houses. I've long believed that a green future starts with the houses we live in. The same belief led me to invest in Bitcoin, gradually amassing a $670,000 portfolio to bankroll my dream of a zero-waste neighborhood of houses. But one rash click was enough to watch my carefully built plans go up in flames. It was a ruthless week. Deadlines were piling up, subcontractors were behind schedule, and my caffeine intake had reached record heights. During the chaos, I installed what I thought was a run-of-the-mill update to Ledger Live. It looked legit, neat logo, familiar design, but it was a wolf in sheep's clothing digital. The moment I entered my wallet details, the screen flashed, and the app vanished. My heart stopped. My Bitcoin was stolen. Panic turned into sleepless nights. I searched on forums, called customer support, and wallowed in guilt. My dream project, the green oasis I had envisioned, was now nothing more than a mirage. Just as despair was starting to creep in, I came across an article in a newsletter detailing green technology. Buried among stories of advances in solar energy and carbon-free cities was a piece on CRANIX ETHICAL SOLUTIONS HAVEN, a team that specializes in recovering stolen cryptocurrency assets. They referred to their work as 'digital sustainability,' restoring not just wallets, but financial futures.
I reached out to them right away. They treated my situation like an architect's blueprints, detailed, innovative, and built on trust right from the first call. Their head tech, who might as well be a moonlighting detective, dismantled the malware that had duped me. They tracked the breach, mapped the transfer, and started their recovery protocols. Daily, I received reports, not mechanical but human, genuine assurances. They laid out each step like sketching construction blueprints clear, step-by-step, detailed. The twelfth day was the day the phone call came. My Bitcoin was okay again. Each virtual brick in place once more. I dissolved, this time not with hysteria, but relief. I Thought My Future Was Built—Until It Crumbled I thought my future had come crashing down until I came across CRANIX ETHICAL SOLUTIONS HAVEN. CRANIX ETHICAL SOLUTIONS HAVEN did not just retrieve my investment. They restored my dream. Today, the foundation for my eco-housing project is stronger than ever, and so is my cybersecurity.
EMAIL: cranixethicalsolutionshaven (@) post . com
TELEGRAM: @ cranixethicalsolutionshaven
WHATSAPP: +44 (7460) (622730)1 -
HACKER TO ASSIST ME RECOVER MY LOST CRYPTO HIRE SLAYER COIN RECOVERY
Life’s unpredictability struck me hard on a sweltering afternoon, as I juggled the relentless demands of taxi driving with dreams of a secure future for my family. Every fare I accepted, every mile I logged, was a step toward stability until a single lapse in judgment threatened to erase it all. Exhausted after a long shift, I stopped at a dimly lit café to check my Bitcoin wallet, clinging to the hope that my investments might one day lift us out of financial uncertainty. The public Wi-Fi was convenient, but in my haste, I didn’t consider the risks. Minutes later, hackers had stripped away $34,000, a sum representing years of sacrifice, sleepless nights, and promises to my children.The “access denied” message felt like a physical blow. My hands trembled as I reloaded the app, praying it was a glitch. But reality sank in: my family’s safety net was gone. Guilt consumed me. How could I explain this to my wife and children? I pictured my daughter’s college fund vanishing, my wife’s trusting smile crumbling under the weight of my mistake. Desperation drove me to scour the internet, where countless recovery scams preyed on vulnerability. Then, I stumbled upon SLAYER COIN RECOVERY, a lifeline in a sea of doubt.Their team responded instantly, blending expertise with empathy. “We’ll do everything possible,” their agent assured me, voice steady yet kind. They decoded the breach: the public network had been a trap, my login credentials intercepted. Over days that felt like eternities, they navigated blockchain complexities and cyber trails, updating me with unwavering transparency. When they finally restored access, tears blurred my screen $34,000 shone in my wallet, intact.This ordeal taught me invaluable lessons about vigilance and the importance of safeguarding my digital assets, revealing humanity’s remarkable capacity for good. SLAYER COIN RECOVERY didn’t just retrieve my lost funds; they salvaged my faith in second chances and the kindness of strangers. Their dedication transformed a moment of despair into a story of resilience and hope.Now, I take proactive measures to secure my investments, using military grade encryption and practicing safe online habits. I’ve become an advocate for digital security, sharing my experience with fellow taxi drivers and anyone willing to listen. I emphasize the importance of using secure networks and being cautious with personal information in a world rife with cyber threats.Moreover, the kindness I received from the SLAYER COIN RECOVERY team inspired me to pay it forward. I volunteer my time to help others navigate their financial challenges, offering guidance and sharing resources to empower those in vulnerable situations.My family’s future is no longer a gamble but a testament to resilience and the power of human connection. I’ve learned that even in the darkest moments, hope can be reclaimed through the support of others. It’s not just about the money; it’s about the lessons learned and the relationships forged in adversity. I carry the spirit of those who helped me as I navigate life’s complexities, determined to build a brighter future for my family and inspire others to do the same.If you ever find yourself in a similar situation, I wholeheartedly
+1(672)768-8701
recommend SLAYER COIN RECOVERY2 -
Building Fortresses, not Firewalls: Ethical Hacking Meets Software Development
In the digital age, security is no longer an afterthought; it's the bedrock upon which our online world rests. Yet, traditional security measures often resemble fortresses – imposing, but vulnerable to unseen cracks and tunnels. To truly safeguard our systems, we need to think like the enemy, like the nimble figures scaling those walls: ethical hackers.
Enter the exciting realm of DevSecOps, where ethical hacking practices are woven into the very fabric of the software development lifecycle (SDLC). This proactive approach is akin to building castles with security in mind, each brick meticulously laid to withstand even the most cunning siege.
Why Ethical Hacking in SDLC?
Imagine developing a critical piece of software, only to discover a gaping security hole after launch. The damage could be catastrophic, exposing sensitive data and eroding trust. Ethical hacking flips this script. By integrating penetration testing, vulnerability assessments, and threat modeling throughout the SDLC, we proactively hunt for weaknesses before they can be exploited.
Think of it as a friendly sparring match, where the ethical hacker throws their best punches to expose vulnerabilities, allowing the development team to fortify the software's defenses. This constant testing and refining leads to robust, secure systems that can withstand real-world attacks.
Benefits of DevSecOps:
1. Reduced Costs and Risks: Early detection and patching of vulnerabilities are far cheaper than dealing with a full-blown data breach.
2. Improved Software Quality: Security becomes an inherent part of the development process, leading to more reliable and trustworthy software.
3. Enhanced Brand Reputation: Demonstrating a proactive approach to security builds trust with customers and stakeholders.
Putting it into Practice:
Integrating ethical hacking into the SDLC requires a cultural shift. Developers, security professionals, and testers need to work together seamlessly, sharing knowledge and fostering a collaborative environment. Here are some key practices:
1. Threat Modeling: Identify potential threats and attack vectors early in the development process.
2. Static and Dynamic Code Analysis: Use automated tools to detect vulnerabilities in code.
3. Penetration Testing: Simulate real-world attacks to uncover hidden weaknesses.
4. Security Awareness Training: Educate developers and other stakeholders about security best practices.
Tools of the Trade:
A plethora of tools empowers ethical hackers and security professionals in their quest for a more secure digital world. Some popular options include:
1. Kali Linux: A distribution packed with security tools for penetration testing.
2. Burp Suite: A web application security testing platform.
3. Metasploit: A framework for developing and executing exploit code.
4. Wireshark: A network traffic analyzer for identifying suspicious activity.
The Future of Security:
As technology evolves, so too must our security practices. DevSecOps, with its embrace of ethical hacking, is at the forefront of this evolution. By building security into the very fabric of software development, we can create a safer, more resilient digital world for everyone.
Remember, in the ongoing battle against cyber threats, ethical hackers are not the enemy; they are our allies, the architects of digital fortresses that stand strong against the shadows. So, let's embrace DevSecOps, sharpen our ethical hacking skills, and build a future where security is not just an afterthought, but a fundamental principle.
I encourage you to explore the world of DevSecOps and ethical hacking. Whether you're a seasoned developer or just starting your journey, there's always more to learn and contribute. Together, we can build a more secure digital future, one line of code and one vulnerability patch at a time.
Do you have any questions about DevSecOps or ethical hacking? Share your thoughts and experiences in the comments below! -
HOW TO REOVER LOST OR STOLEN BITCOIN, ETH AND OTHER CRYPTO ASSETS; VISIT CYBER CONSTABLE INTELLIGENCE
On January 2, 2025, at precisely 3 AM, Bet365 was hit by a devastating cyber-attack. Our website was infiltrated by a sophisticated virus that granted cybercriminals access to sensitive customer data. In the span of a few hours, £2,500,000 was stolen from our customers’ accounts. The attack was swift and covert, and by the time we realized what had happened, a significant amount of funds had already been siphoned off. As soon as we discovered the breach, my team and I worked tirelessly to secure our platform and protect our customers. We immediately launched an internal investigation and found that the virus had allowed unauthorized withdrawals from a number of accounts. This was a critical situation, and we knew we needed immediate help to recover the stolen funds and prevent any further damage. That's when we turned to Cyber Constable Intelligence. Their reputation for successfully recovering stolen funds in cybercrime cases made them the ideal partner for this challenge. The team at Cyber Constable Intelligence responded immediately, quickly analyzing the virus and the methods used by the hackers. Within hours, they were able to trace the movement of the stolen funds and identify the cybercriminals responsible for the attack. Cyber Constable Intelligence acted swiftly, working around the clock to coordinate with financial institutions and law enforcement. They used their advanced investigative tools and global network to track and recover the £2,500,000 stolen from our customers. Thanks to their relentless efforts, within just three days, we had recovered the full amount. By January 5, 2025, only three days after the attack, we were able to reimburse all affected customers and restore the funds to their accounts. This quick recovery was crucial in reassuring our customers and restoring their trust in Bet365. Additionally, Cyber Constable Intelligence helped us bolster our security measures, ensuring that we are now better protected against future threats. This experience was a stark reminder of the constant risks in the digital world. However, thanks to Cyber Constable Intelligence, we were able to act quickly, recover the stolen funds, and ensure that our platform remains a safe and secure place for our customers. Moving forward, we are more committed than ever to maintaining the highest standards of security to protect both our business and our users.
Reach out to their Info below
WhatsApp: 1 252378-7611
Website info; www cyberconstableintelligence com
Email Info cyberconstable@coolsite net1 -
CRYPTOCURRENCY RECOVERY FIRM HIRE ADWARE RECOVERY SPECIALIST
WhatsApp info:+12723 328 343
I started my journey as a security guard in the UK, working long shifts to support myself and save for the future. Like many, I had big dreams and aspirations, but life often felt like a constant struggle to make ends meet. My job was stable, but it wasn’t glamorous, and I knew that if I wanted a better future, I’d need to find a way to make my money work for me. That’s when I first came across Bitcoin. Intrigued by the growing buzz around cryptocurrency, I began researching Bitcoin and other digital currencies. I saw countless stories of people turning modest investments into life-changing sums of money. The idea of financial freedom took root in my mind, and I started to believe that Bitcoin could be my ticket out of the grind. With this hope, I decided to invest. I saved up diligently from my security job, putting away every spare penny. After months of sacrifice, I finally scraped together €51,400. It wasn’t a small sum for me—this was the product of years of hard work. I was nervous but excited. The prospects seemed endless, and I truly believed Bitcoin could change my life. For a while, everything seemed to go according to plan. My investment grew, and I felt a sense of security I had never known before. Watching Bitcoin’s value rise was exhilarating. It felt like a brilliant decision, and I began to dream of a future where I could live on my own terms—maybe even leave my security job behind. But then, disaster struck. A security breach, a misplaced transfer, and a technical glitch led to the loss of my entire Bitcoin investment. All at once, my €51,400 was gone. I couldn’t believe it. The money I had worked so hard to save was wiped out in an instant, and I was left devastated. The weight of the loss was crushing. My dreams seemed to vanish overnight. I spent weeks trying to recover the funds, but every attempt ended in frustration. Then, one day while scrolling through Instagram, I came across a post about ADWARE RECOVERY SPECIALIST helping someone recover their lost crypto. Desperate, I reached out to them. They took my case seriously and, after a few weeks, they managed to recover my €51,400. The relief I felt was indescribable. Thanks to ADWARE RECOVERY SPECIALIST, I got a second chance, and I’ll forever be grateful for their expertise and dedication.1 -
HIRE A CRYPTO RECOVERY EXPERT; BEST BITCOIN RECOVERY SERVICE VISIT CYBER CONSTABLE INTELLIGENCE
It was a devastating blow - one moment I was the proud owner of a small digital fortune, 8,000 Bitcoin that I had painstakingly accumulated over years of savvy investing and cautious storage. The next, that entire life-changing sum had vanished without a trace, lost to a cruel twist of fate and my own careless misstep. I had fallen victim to a data breach, leaving me helpless to prevent the thieves from making off with my entire cryptocurrency holdings. The anguish was palpable, a sinking feeling of hopelessness and despair as I realized the scale of my loss. Thousands upon thousands of hard-earned Bitcoins, now in the hands of faceless criminals, beyond my reach. But I refused to give in to despair. Determined to recover what was rightfully mine, I sought out the services of Cyber Constable Intelligence, a specialized team of blockchain forensics experts renowned for their ability to track down and reclaim stolen digital assets. Through their meticulous investigative work, leveraging the transparency of the Bitcoin ledger and their deep technical expertise, they were able to painstakingly trace the movement of my stolen funds, identifying the wallet addresses the thieves had used to launder the cryptocurrency. With this critical intelligence in hand, Cyber Constable Intelligence then coordinated with law enforcement to freeze those illicit accounts, preventing the funds from being moved any further. The final step was a delicate negotiation process, with the recovery team using their connections and influence to compel the thieves to return the stolen Bitcoins - a tense and high-stakes affair, but one that ultimately proved successful. After weeks of anxious waiting, I was overjoyed to have my 8,000 BTC safely returned to my control, a true testament to the skill and determination of the Cyber Constable Intelligence team. It was a harrowing ordeal, but one that reinforced the importance of robust security measures and the remarkable capabilities of specialized firms dedicated to combating cryptocurrency crime and restoring rightful ownership. Losing 8,000 BTC was one of the most stressful events of my life, but thanks to Cyber Constable Intelligence, I was able to reclaim what I thought was lost forever. Their professionalism, technical expertise, and commitment to security made all the difference. If you find yourself in a similar situation, I cannot recommend them highly enough. Cyber Constable Intelligence turned a financial disaster into a remarkable recovery, and I will forever be grateful for their role in securing my assets.
CYBER CONSTABLE INTELLIGENCE INFO:
Website: w w w. cyberconstableintelligence com3 -
I HIGHLY RECOMEND ADWARE RECOVERY SPECIALIST AS THE BEST IN ALL FORM OF SCAMED RECOVERY
I cannot express how distraught I was when I realized someone had hacked my email and was conning my family and friends on Instagram to invest with me. The hacker was using my identity to lure them into a fraudulent investment scheme, and by the time we discovered what was happening, some of my family members and friends had fallen for it. They ended up wiring the fraudsters a total of $25,000 before they realized it wasn't me. The emotional and financial impact was devastating. Call or text: +18186265941 I felt helpless and violated, knowing that someone was using my name to deceive the people I care about the most. It was during this period of turmoil that a close friend told me about ADWARE RECOVERY SPECIALIST. She had been through a similar ordeal and had used their services to regain control of her digital life. Desperate for a solution, I reached out to the ADWARE RECOVERY SPECIALIST team. From the very first contact, they were understanding and professional. They explained the steps they would take to track down my email account, recover it, and secure it, along with my Instagram and other social media accounts. The process was thorough and efficient. The team at ADWARE RECOVERY SPECIALIST used their expertise to identify the breach points and secure my accounts against future attacks. They provided clear instructions on how to enhance my online security and even offered tips on maintaining privacy in the digital age. Within a few days, my email and social media accounts were back under my control. The relief was immense. Knowing that my accounts were secure and that the fraudsters no longer had access to them lifted a huge weight off my shoulders. My family and friends also felt reassured, seeing the proactive steps I was taking to prevent this from happening again. If you ever find yourself in a situation where your digital security is compromised, I highly recommend reaching out to ADWARE RECOVERY SPECIALIST. Their team is not only skilled in recovering and securing accounts but also empathetic to the distress such incidents cause. They offer a comprehensive solution to safeguard your digital presence, giving you peace of mind in a world where online threats are increasingly common. Don't wait until it's too late. Protect your digital life with ADWARE RECOVERY SPECIALIST and ensure that your personal information remains safe from those who seek to exploit it.
-
Hire a Trusted Company for Recovery of Lost Bitcoin — CryptoChain Global Track
The rapid growth of the cryptocurrency industry has created both opportunity and risk. While digital assets like Bitcoin offer financial freedom, privacy, and accessibility, they also attract cybercriminals who exploit unsuspecting users. From investment scams to phishing attacks, hacked wallets to fraudulent trading platforms, Bitcoin holders around the world are increasingly falling victim to schemes that result in serious financial loss. When this happens, finding a reliable, professional recovery service becomes a critical step forward.
CryptoChain Global Track is a trusted and recognized name in the field of cryptocurrency recovery. The company is known for helping individuals and businesses who have lost Bitcoin due to scams, unauthorized access, or transactional errors. Backed by a team of skilled blockchain analysts, ethical hackers, and forensic investigators, CryptoChain Global Track offers a lifeline to those who thought their assets were gone forever.
Unlike many services that overpromise and underdeliver, CryptoChain Global Track works with complete transparency and professionalism. Their recovery process begins with a detailed analysis of the client’s situation. This includes examining the blockchain data, wallet transactions, and any communication or documentation related to the scam or loss. Using advanced tools, the team can trace the movement of Bitcoin through multiple wallets and platforms, even if the funds have been moved through mixing services or converted into other cryptocurrencies.
The company's success is rooted in its deep understanding of blockchain networks and how digital criminals operate. Their technical capabilities allow them to identify patterns, pinpoint destination wallets, and in many cases, work directly with exchanges or law enforcement to flag suspicious accounts. Every case is approached with careful investigation, guided by facts and real-time data—not assumptions or generic solutions.
Trust is a key part of any recovery process, especially when dealing with sensitive financial matters. CryptoChain Global Track treats every case with discretion and ensures that clients remain informed throughout the investigation. From initial assessment to asset tracking and follow-up actions, communication is clear and consistent. Clients are not charged upfront for empty promises—they receive honest evaluations and tailored solutions based on the nature of their case.
Beyond technical expertise, CryptoChain Global Track is also committed to client support and education. Many Bitcoin losses occur because of a lack of awareness about threats in the crypto space. The company takes time to educate its clients about how the breach or scam occurred and provides practical advice to help them avoid similar situations in the future. This commitment to both recovery and prevention makes the service holistic and genuinely helpful.
A trusted solution is available—and it starts by connecting with a team that understands how to fight back against crypto fraud with skill and determination.6 -
HIRE THE MOST EXPERIENCED SCAMMED CRYPTO RECOVERY EXPERTS ⁄⁄ DIGITAL HACK RECOVERY
I started my journey as a security guard in the UK, working long shifts to support myself and save for the future. Like many, I had big dreams and aspirations, but life often felt like a constant struggle to make ends meet. My job was stable, but it wasn’t glamorous, and I knew that if I wanted a better future, I’d need to find a way to make my money work for me. That’s when I first came across Bitcoin.Intrigued by the growing buzz around cryptocurrency, I began researching Bitcoin and other digital currencies. I saw countless stories of people turning modest investments into life-changing sums of money. The idea of financial freedom took root in my mind, and I started to believe that Bitcoin could be my ticket out of the grind. With this hope, I decided to invest.I saved up diligently from my security job, putting away every spare penny. After months of sacrifice, I finally scraped together €51,400. It wasn’t a small sum for me—this was the product of years of hard work. I was nervous but excited. The prospects seemed endless, and I truly believed Bitcoin could change my life.For a while, everything seemed to go according to plan. My investment grew, and I felt a sense of security I had never known before. Watching Bitcoin’s value rise was exhilarating. It felt like a brilliant decision, and I began to dream of a future where I could live on my own terms—maybe even leave my security job behind.But then, disaster struck. A security breach, a misplaced transfer, and a technical glitch led to the loss of my entire Bitcoin investment. All at once, my €51,400 was gone. I couldn’t believe it. The money I had worked so hard to save was wiped out in an instant, and I was left devastated. The weight of the loss was crushing. My dreams seemed to vanish overnight.I spent weeks trying to recover the funds, but every attempt ended in frustration. Then, one day while scrolling through Instagram, I came across a post about Digital Hack Recovery helping someone recover their lost crypto. Desperate, I reached out to them. They took my case seriously and, after a few weeks, they managed to recover my €51,400. The relief I felt was indescribable. Thanks to Digital Hack Recovery, I got a second chance, and I’ll forever be grateful for their expertise and dedication. Contact them for quick assistance via⁚
Email⁚ digital hack recovery @ techie . com
WhatsApp⁚ +19152151930
Website; https : // digital hack recovery . com 3
3 -
I started my journey as a security guard in the UK, working long shifts to support myself and save for the future. Like many, I had big dreams and aspirations, but life often felt like a constant struggle to make ends meet. My job was stable, but it wasn’t glamorous, and I knew that if I wanted a better future, I’d need to find a way to make my money work for me. That’s when I first came across Bitcoin. Intrigued by the growing buzz around cryptocurrency, I began researching Bitcoin and other digital currencies. I saw countless stories of people turning modest investments into life-changing sums of money. The idea of financial freedom took root in my mind, and I started to believe that Bitcoin could be my ticket out of the grind. With this hope, I decided to invest. I saved up diligently from my security job, putting away every spare penny. After months of sacrifice, I finally scraped together €51,400. It wasn’t a small sum for me—this was the product of years of hard work. I was nervous but excited. The prospects seemed endless, and I truly believed Bitcoin could change my life. For a while, everything seemed to go according to plan. My investment grew, and I felt a sense of security I had never known before. Watching Bitcoin’s value rise was exhilarating. It felt like a brilliant decision, and I began to dream of a future where I could live on my own terms—maybe even leave my security job behind. But then, disaster struck. A security breach, a misplaced transfer, and a technical glitch led to the loss of my entire Bitcoin investment. All at once, my €51,400 was gone. I couldn’t believe it. The money I had worked so hard to save was wiped out in an instant, and I was left devastated. The weight of the loss was crushing. My dreams seemed to vanish overnight. I spent weeks trying to recover the funds, but every attempt ended in frustration. Then, one day while scrolling through Instagram, I came across a post about CRANIX ETHICAL SOLUTIONS HAVEN helping someone recover their lost crypto. Desperate, I reached out to them. They took my case seriously and, after a few weeks, they managed to recover my €51,400. The relief I felt was indescribable. Thanks to CRANIX ETHICAL SOLUTIONS HAVEN, I got a second chance, and I’ll forever be grateful for their expertise and dedication.
Website: h t t p s: / / c r a n i x e t h i c a l s o l u t i o n s h a v e n . i n f o
Email: c r a n i x e t h i c a l s o l u t i o n s h a v e n @ p o s t . c o m
WhatsApp: + 4 4 7 4 6 0 6 2 2 7 3 0
Telegram: @ C r a n i x e t h i c a l s o l u t i o n s h a v e n1 -
Best Recovery Experts for Cryptocurrency Assets: HIRE CERTIFIED RECOVERY SERVICES
Last month, I faced a nightmare scenario when the entire balance of SOL I held in my Meta Mask wallet was abruptly transferred to an unknown address. One moment, my funds were secure; the next, they’d vanished without a trace. I frantically reviewed my transaction history, double-checked permissions, and scanned my devices for malware, but found no obvious breach. Panic turned to despair as I realized my savings accumulated through years of cautious investing were gone. Desperate for answers, I contacted Meta Mask support, only to be told that decentralized transactions couldn’t be reversed or traced by their team. They speculated that my wallet had been compromised, possibly via a phishing scam, a malicious dApp, or a leaked recovery phrase, but I couldn’t pinpoint where I’d gone wrong. Feeling helpless, I combed through Reddit threads and crypto forums, where I stumbled upon CERTIFIED RECOVERY SERVICES, a service hailed for its success in reclaiming stolen assets. Though skeptical after all, everything I’d read suggested crypto theft was irreversible I decided to take a leap of faith and submitted my case details, including transaction IDs and wallet addresses. Their team responded within hours, outlining a meticulous plan to trace the stolen SOL across the blockchain and collaborate with exchanges to intercept the funds. Over the next week, CERTIFIED RECOVERY SERVICES provided daily updates, revealing how the thief had funneled my SOL through a labyrinth of wallets to obscure its trail. Using advanced blockchain forensics, they identified patterns linking the movement of funds to a known exchange. By working with legal teams and platform security, they flagged the stolen crypto before it could be liquidated. Their expertise and determination were evident as they navigated the complexities of the blockchain, piecing together the puzzle of my stolen assets. Against all odds, their relentless efforts paid off: within 9 days, they recovered 100% of my stolen SOL and safely redirected it to a new, fortified wallet. This experience taught me the importance of vigilance in the crypto space and the value of seeking help from experts when faced with seemingly insurmountable challenges. I learned that while the decentralized nature of cryptocurrency offers many advantages, it also comes with risks that require constant awareness and proactive measures. Now, I’m more cautious than ever, ensuring that my digital assets are protected and that I stay informed about potential threats in the ever-evolving world of cryptocurrency.
Here's Their Info Below:2 -
RECOVER BTC AND MONEY SENT TO SCAMMERS HIRE A HACKER TECHNOCRATE RECOVERY
When my cryptocurrency wallet was suddenly emptied, leaving me with a loss of $145,000, I was engulfed in shock and disbelief. The devastation was compounded when I uncovered the truth: my ex-girlfriend, whom I had recently discovered was unfaithful, was behind the theft. The realization that someone I once trusted had betrayed me so deeply was crushing. The emotional turmoil left me desperate for a solution, so I began searching for recovery services. During this search, I came across a Telegram group where someone recommended TECHNOCRATE RECOVERY. Their glowing reviews provided a glimmer of hope, and reaching out to them turned out to be a pivotal decision. From our very first conversation, TECHNOCRATE RECOVERY exhibited a level of professionalism that immediately reassured me. They didn’t just sympathize—they acted, quickly launching an investigation into how the theft occurred. Knowing that this betrayal came from someone close to me, their careful, methodical approach was exactly what I needed. They were meticulous in their investigation, tailoring their efforts to the unique aspects of my case, which was vital given the complexities of cryptocurrency recovery. Their team was both knowledgeable and empathetic, fully understanding the emotional weight of my situation. Throughout the process, I experienced an emotional roller coaster. The initial despair slowly gave way to hope as the team at TECHNOCRATE RECOVERY consistently communicated with me. They were transparent, explaining each step in a way that was easy to understand, which helped alleviate some of the anxiety I felt. Their regular updates were a lifeline, ensuring I was never left in the dark about the progress being made. Their ability to break down complex technical details into something manageable was a testament to their commitment to client care. TECHNOCRATE RECOVERY’s use of advanced forensic tools and blockchain expertise was nothing short of impressive. They tracked the movement of my stolen assets with precision, leaving no avenue unexplored. I was particularly impressed by their collaboration with other experts and law enforcement when necessary, demonstrating their dedication to recovering my funds. Their transparent fee structure was another standout feature. While many services charge hefty fees or demand significant upfront payments, TECHNOCRATE RECOVERY provided a clear breakdown of costs from the outset. This transparency built trust, making the financial aspect of the process far less stressful. Their focus on results over profit was evident and greatly appreciated. Ultimately, TECHNOCRATE RECOVERY successfully recovered all my stolen assets, bringing a sense of closure to this painful chapter. But what truly set them apart was their post-recovery support. They provided invaluable advice on securing my cryptocurrency wallet against future threats, arming me with the knowledge I needed to prevent such a breach from happening again. If you ever find yourself in a similar situation, know that there’s a way back from the brink. TECHNOCRATE RECOVERY isn’t just a service—they’re a lifeline, guiding you through the darkest moments and helping you regain control over what you thought was lost forever.
Web Info: ww w.technocraterecove ry.site
Contact Email: technocratrecovery (@) contractor. net -
CHANCES OF CRYPTO RECOVERY OPTIONS:USE SPARTAN TECH GROUP RETRIEVAL
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) cyberservices . com
Telegram:+1 (581) 2 8 6 - 8 0 9 2
For many individuals and businesses, the experience of financial loss, whether caused by cyberattacks, data breaches, or unforeseen events, can feel overwhelming and intimidating. The emotional and financial toll can be immense, leaving people uncertain of where to turn. In these challenging times, SPARTAN TECH GROUP RETRIEVAL offers a crucial lifeline, providing expert services that guide clients through the recovery process with both skill and compassion. At SPARTAN TECH GROUP RETRIEVAL, the team recognizes the profound impact financial loss can have on clients, not only in terms of their finances but also on their sense of security and well-being. Their highly trained professionals specialize in assessing the full extent of damage caused by various disruptions, carefully identifying the underlying issues and working to develop tailored recovery strategies. Whether the challenge involves restoring lost data, recovering compromised systems, or securing vulnerable networks, SPARTAN TECH GROUP RETRIEVAL utilizes the latest technology and industry best practices to restore both operational efficiency and peace of mind. Data loss can be a particularly devastating consequence of a cyberattack or system failure. In a world where information is the lifeblood of businesses, recovering lost or corrupted data is crucial to regaining normal operations. SPARTAN TECH GROUP RETRIEVAL’s experts employ advanced data recovery techniques to retrieve vital information, ensuring that clients do not suffer irreversible setbacks. By recovering valuable data, they allow businesses to continue their operations with minimal disruption. Beyond data recovery, SPARTAN TECH GROUP RETRIEVAL excels at restoring and securing compromised systems. After a breach or attack, the threat of future vulnerabilities looms large. The team’s cybersecurity experts take swift action to secure networks and systems, implementing robust protection measures to defend against future threats. Through a combination of proactive monitoring, vulnerability assessments, and real-time security solutions, SPARTAN TECH GROUP RETRIEVAL works tirelessly to ensure that businesses and individuals can rebuild trust and safeguard their digital assets for the long term. However, what truly distinguishes SPARTAN TECH GROUP RETRIEVAL is its unwavering commitment to client care. While the technical aspects of recovery are vital, the company understands the emotional strain that often accompanies financial loss. Their compassionate case managers offer much-needed emotional support and practical guidance, helping clients navigate both the logistical and psychological challenges they face. By addressing the emotional as well as the practical aspects of recovery, SPARTAN TECH GROUP RETRIEVAL ensures that clients feel understood and supported throughout the entire process. In the face of financial hardship, SPARTAN TECH GROUP RETRIEVAL is a trusted partner that combines technical expertise with empathy and dedication. Their holistic approach ensures that businesses and individuals can recover, rebuild, and emerge from financial challenges stronger, more secure, and better prepared for the future. 1
1 -
DIGITAL TECH GUARD RECOVERY: RESTORING YOUR CRYPTOCURRENCY AFTER A SCAM
WhatsApp: +1 (443) 859 - 2886 Email @ digital tech guard . com
Telegram: digital tech guard recovery . com website link : digital tech guard . com
I started my journey as a security guard in the UK, working long shifts to support myself and save for the future. Like many, I had big dreams and aspirations, but life often felt like a constant struggle to make ends meet. My job was stable, but it wasn’t glamorous, and I knew that if I wanted a better future, I’d need to find a way to make my money work for me. That’s when I first came across Bitcoin. Intrigued by the growing buzz around cryptocurrency, I began researching Bitcoin and other digital currencies. I saw countless stories of people turning modest investments into life-changing sums of money. The idea of financial freedom took root in my mind, and I started to believe that Bitcoin could be my ticket out of the grind. With this hope, I decided to invest. I saved up diligently from my security job, putting away every spare penny. After months of sacrifice, I finally scraped together €51,400. It wasn’t a small sum for me—this was the product of years of hard work. I was nervous but excited. The prospects seemed endless, and I truly believed Bitcoin could change my life. For a while, everything seemed to go according to plan. My investment grew, and I felt a sense of security I had never known before. Watching Bitcoin’s value rise was exhilarating. It felt like a brilliant decision, and I began to dream of a future where I could live on my own terms—maybe even leave my security job behind. But then, disaster struck. A security breach, a misplaced transfer, and a technical glitch led to the loss of my entire Bitcoin investment. All at once, my €51,400 was gone. I couldn’t believe it. The money I had worked so hard to save was wiped out in an instant, and I was left devastated. The weight of the loss was crushing. My dreams seemed to vanish overnight. I spent weeks trying to recover the funds, but every attempt ended in frustration. Then, one day while scrolling through Instagram, I came across a post about Digital Tech Guard Recovery helping someone recover their lost crypto. Desperate, I reached out to them. They took my case seriously and, after a few weeks, they managed to recover my €51,400. The relief I felt was indescribable. Thanks to Digital Tech Guard Recovery, I got a second chance, and I’ll forever be grateful for their expertise and dedication.1 -
QUALIFIED BITCOIN/ETH/USDT RECOVERY EXPERT HIRE ADWARE RECOVERY SPECIALIST
Email info: Adwarerecoveryspecialist@auctioneer. net
Text or Call: +18186265941
Telegram username: @adwarerecoveryspecialist
How did I lose access to my Bitcoin wallet? UpTo date I still have no answer to that haunting question that kept me up at night. It all started when a close friend, whom I trusted implicitly, somehow gained access to my Bitcoin wallet and transferred out a significant amount of my funds. The betrayal was compounded by the fact that the value of the stolen Bitcoin was around $150,000. To cover their tracks, they went so far as to delete the wallet from my phone and change my email password, effectively locking me out of my accounts. I was in disbelief, torn between shock and betrayal. With nowhere else to turn, I sought help from ADWARE RECOVERY SPECIALIST. From our first interaction, the team at ADWARE RECOVERY SPECIALIST was compassionate and professional. They understood the emotional turmoil I was going through and assured me they had the skills to help me reclaim my lost assets. Their confidence was backed by a deep understanding of blockchain technology and cybersecurity. The recovery process was comprehensive. ADWARE RECOVERY SPECIALIST experts meticulously traced the transactions, identified the breach points, and managed to locate my stolen Bitcoin. It was a complex task that required patience and precision, but their team was up to the challenge. Throughout the process, they kept me informed and involved, which helped ease my anxiety. They provided regular updates, explaining each step they took and the progress they were making, which reassured me during this stressful period. Once they recovered my Bitcoin, they didn't stop there. ADWARE RECOVERY SPECIALIST also fortified my wallet's security to prevent future breaches. They took the time to educate me on best practices for safeguarding my digital assets, which has been invaluable. This included setting up multi-factor authentication, using hardware wallets, and being more vigilant about who has access to my private keys. The dedication and thoroughness of the ADWARE RECOVERY SPECIALIST team were truly impressive. Their commitment to not only recovering my lost assets but also ensuring that I had the knowledge to protect them in the future stood out. They transformed a devastating situation into a valuable learning experience, which has been crucial in rebuilding my confidence in digital asset management. If you ever find yourself in a situation where a trusted friend betrays your trust and compromises your digital assets, ADWARE RECOVERY SPECIALIST is the team to turn to. Their expertise, dedication, and client-centered approach were instrumental in helping me regain control of my Bitcoin and restoring my sense of security. Trusting them was the best decision I made, and their support has been invaluable in navigating this challenging experience.
-
BTC Recovery After Phishing Scam Through PASSCODE CYBER RECOVERY
In March,I made a critical mistake that had serious consequences for our organization. While reviewing my emails, I clicked on a phishing link embedded in what appeared to be a legitimate invoice. This seemingly innocuous action triggered a significant security breach, ultimately leading to the loss of 25 BTC (Bitcoin) from our company wallet. As the individual responsible for this incident, I felt an overwhelming sense of responsibility and concern for the implications it had on our financial security. The phishing attack was expertly crafted, making it difficult to recognize the threat, and I never anticipated that my actions would lead to such a severe breach.our company acted swiftly to mitigate the damage by engaging Passcode Cyber Recovery, a firm known for its expertise in cryptocurrency recovery. Passcode Cyber Recovery's response was remarkable. The team quickly mobilized, employing advanced forensic techniques to trace the stolen funds. Their meticulous analysis of blockchain transactions was crucial in identifying the pathways through which the stolen BTC had been funneled.The investigators at Passcode Cyber Recovery utilized sophisticated tools to track the movement of our cryptocurrency across various exchanges. They collaborated with exchange platforms to flag the illicit transactions and prevent any further withdrawals. Passcode Cyber Recovery's deep understanding of the cryptocurrency landscape allowed them to pinpoint the exact locations where the stolen funds had been deposited.Thanks to the persistent efforts and strategic negotiations of Passcode Cyber Recovery, all 25 BTC were successfully recovered. Their comprehensive approach not only involved tracing the funds but also included liaising with law enforcement and regulatory bodies to ensure that the perpetrators faced consequences for their actions.This has been a stark reminder of the importance of cybersecurity awareness. I have learned firsthand how easily one can fall victim to such attacks, and I am now committed to being more vigilant and proactive in recognizing potential threats.I am grateful for the swift intervention of Passcode Cyber Recovery, which not only restored our lost funds but also reinforced our confidence in the digital currency ecosystem. I encourage everyone to remain cautious and informed about cybersecurity to prevent similar incidents in the future.
WhatsApp: +1(647)399-4074
Telegram : @passcodecyberrecovery5 -
Experiencing a security breach involving your Bitcoin wallet can be a harrowing ordeal. This was my reality when I received an unexpected BTC security code on my phone. At the time, I didn’t realize the significance of this code and, unfortunately, ignored it. To my dismay, I later discovered that my Bitcoin wallet had been hacked by an unknown scammer, resulting in the theft of all the funds I had accumulated. The frustration and helplessness I felt during this period were overwhelming. My entire Bitcoin portfolio was inaccessible, and the sense of losing control over my assets was incredibly distressing. The funds that had been stolen represented not just an investment, but a crucial part of my financial security. I was left without any clear path forward, grappling with the reality that my savings were gone and that I had no immediate way to recover them. In my search for a solution, I turned to online resources and discussions in hopes of finding a way to retrieve my lost funds. It was during this search that I heard about FAYED HACKER from a trusted friend. They spoke highly of FAYED HACKER’s reputation for recovering lost funds and providing effective solutions for hacking incidents. Encouraged by their positive feedback, I decided to reach out to FAYED HACKER for help. I contacted them through their email, providing all the relevant details about my situation. The response from FAYED HACKER was swift and professional. They offered a detailed consultation and outlined the steps I needed to follow to initiate the recovery process. Their instructions were clear and comprehensive, guiding me through every necessary action to address the breach and attempt to regain control of my wallet. Following their expert advice, I was able to take the necessary steps to begin the recovery process. FAYED HACKER’s team worked diligently on my case, employing their expertise and advanced techniques to trace the stolen funds and secure my compromised wallet. The process required patience and careful adherence to their instructions, but their support was unwavering and reassuring throughout. Within a few weeks, I received the incredible news that my Bitcoin wallet and the stolen funds had been successfully recovered. FAYED HACKER’s efforts to rectify the situation were nothing short of remarkable. They had not only restored access to my wallet but also ensured that the stolen BTC was returned. I was once again able to manage my wallet independently, regaining control over my financial assets. The successful recovery of my Bitcoin and wallet was a huge relief and a testament to the effectiveness of FAYED HACKER’s services. Their professionalism, expertise, and commitment to their clients were evident throughout the entire process. I am profoundly grateful for their help and would strongly encourage anyone who finds themselves in a similar predicament to seek assistance from credible and ethical recovery services like FAYED HACKER. Dealing with a hacked Bitcoin wallet can be an incredibly stressful experience, but recovery is possible with the right help. FAYED HACKER provided me with the expert support and guidance needed to regain my assets and restore my peace of mind. Their dedication to their clients and their effective recovery strategies make them a trustworthy choice for anyone facing issues with stolen or compromised Bitcoin. If you ever find yourself in a situation where your funds or wallet have been hacked, reaching out to a reputable recovery service like FAYED HACKER could be the key to reclaiming what you’ve lost.
EMAIL: writeus @ fayedhacker . tech or fayedexperthack @ solution4u . com
WHATSAPP: + 44 (753) (524) (0205)
-
As someone who had faced the frustration and anxiety of losing cryptocurrency, I can confidently say that Tech Cyber Force Recovery was a game-changer. After my assets were stolen through a security breach, I was lost and unsure where to turn. That's when I found Tech Cyber Force Recovery, and from the moment I reached out to them, I knew I was in good hands. Their experts took the time to thoroughly assess my situation and put together a tailored strategy to recover my lost funds. What truly set them apart was their transparency. They communicated with me at every step, making sure I understood what was happening and what to expect. No vague promises or hidden fees, just clear, honest communication. The technical expertise they brought to the table was beyond impressive. They used advanced tools to trace my cryptocurrency across various decentralized exchanges and mixers, leaving no stone unturned. I was amazed at how they were able to track down even the most obscure transactions and wallets, something I never thought possible. What stood out to me, though, was the empathy and care they showed throughout the process. Losing cryptocurrency is stressful, and the team at Tech Cyber Force Recovery understood that. They handled my case with urgency and discretion, treating my situation with the seriousness it deserved. Thanks to their dedication and expertise, my cryptocurrency was successfully recovered. The entire experience was handled professionally, and I never once felt like I was in the dark. Tech Cyber Force Recovery not only helped me regain my assets but also provided me with the peace of mind I desperately needed. If you're ever in a similar situation, I highly recommend Tech Cyber Force Recovery. Their skill, professionalism, and genuine care make them the go-to choice for cryptocurrency recovery.
We bs ite them W.W.W. tech yforcec yberre trieval . com
Telegram (@)Techcyberforc2 -
STOLEN BTC RECOVERY GUESTBOOK HIRE DUNAMIS CYBER SOLUTION
My husband had always been a dreamer, someone who thrived on innovation and the allure of “what’s next.” So, when he decided to invest $123,000 into a Dallas based app development company promising to revolutionize Bitcoin integration, I wasn’t surprised. But I was worried. For months, I urged him to consider real estate instead, arguing that bricks and mortar offered stability in an unpredictable digital world. He dismissed my concerns, convinced this venture was his golden ticket to success.Then came the security breach. The app, which had initially dazzled him with its sleek interface and bold vision, suddenly locked him out with relentless login errors. Panic set in as we realized his entire investment, our family’s financial cushion, had vanished. My frustration was palpable. I had warned him, but as anger gave way to fear, we faced a harsh truth: blame wouldn’t fix this. We needed a solution.Enter DUNAMIS CYBER SOLUTION .5 -
POSSIBLE WAYS TO RECOVER BACK YOUR SCAMMED CRYPTO FROM ANY INVESTMENT PLATFORM...
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center . c o m1 -
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. c o m
whats App: +1 908 991 71321 -
POSSIBLE WAYS TO GET BACK EVERY PENNY LOSE TO SCAMMERS
At Digital Gold Hunters Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. com
whats App: +1 908 991 71321 -
TRUSTWORTHY CRYPTO RECOVERY SERVICE- HIRE SALVAGE ASSET RECOVERY
At Tax Ease Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Salvage Asset Recovery. Salvage Asset Recovery’s team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform. Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Salvage Asset Recovery has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Salvage Asset Recovery helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information. Thanks to the quick and efficient actions of Salvage Asset Recovery, Tax Ease Solutions was able to recover $980,000 of the lost funds and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Salvage Asset ’s continued support, we will fully resolve the situation.
Their Contact info,
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
RECOVER BACK YOUR HARD EARN MONEY SCAMMED BY ONLINE IMPERSONATORS OR HACKERS FROM ANY PLATFORM.
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: D i g i t a l g o l d h u n t e r @ t e c h -c e n t e r . c o m1 -
I'll suggest you contact the Nitrocrackhub if you need the service of a legit professional hack team. They helped me breach a crypto scam website database security and they shut down the website permanently. They also got me access to an iphone device without requiring the physical presence and I was able to get unlimited access to the targets real time GPS which made it even perfect, The remote dashboard portal made it possible for me to get access to coded datas including social media messages, emails and recover deleted texts and datas. They are highly skilled, reliable, genuine and professional. Relay all your problems to the team and I'm sure they will help you out. You can reach them via the info below:
WEB ADDRESS VIA ( Www . Nitrocrackhub . Com )
E MAIL ADDRESS VIA (Nitrocrackhub @ Gmail . Com) -
HACKER FOR HIRE: iBOLT CYBER HACKER - CRYPTOCURRENCY RECOVERY COMPANY
I highly recommend iBOLT Cyber Hacker for anyone seeking expert assistance in recovering lost or stolen cryptocurrency, I recently engaged iBOLT Cyber Hacker after falling victim to a cryptocurrency scam, their team demonstrated deep knowledge of blockchain forensics, wallet tracing, and transaction monitoring. They handled my case with a high degree of transparency and integrity, clearly explaining each step of the process and setting realistic expectations.
If you've been affected by a crypto scam, phishing attack, or wallet breach, iBOLT Cyber Hacker offers a legitimate path to potential recovery. While no company can guarantee 100% success in every case, iBOLT delivers results with professionalism, discretion, and a client-first mindset.
info @ iboltcyberhack . org/
www . iboltcybarhacker . com/
+.39.. 351. .105. .3619.
I strongly recommend their services to anyone in need of cryptocurrency recovery support.5 -
I read somewhere while at work on the internet in X that the Bitcoin lost during the Bit get breach, worth more than $5 million, has been fully recovered, thanks to the efforts of Tech Cyber Force Recovery. The breach had left many users devastated, unsure if they would ever see their funds again. However, Tech Cyber Force Recovery stepped in and successfully traced and retrieved the stolen Bitcoin, ensuring that all affected users received 100% of their lost assets. The recovery process was far from easy. The Tech Cyber Force Recovery team used cutting-edge blockchain forensic techniques to track down the stolen funds. They meticulously followed the transaction trail across multiple blockchain networks, piecing together the complex puzzle of the breach. It involved collaboration with cybersecurity experts and relevant authorities to ensure that the recovery was not only successful but also secure. The recovery efforts were particularly significant because the total value of the Bitcoin lost during the Bit get breach amounted to over $5 million. This made the task even more critical, as the amount at stake was substantial. Users who had once feared losing their investments can now rest easy, knowing that Tech Cyber Force Recovery was able to restore their assets in full. What sets Tech Cyber Force Recovery apart is not just its technical expertise but also its commitment to transparency. Throughout the entire recovery process, the team kept users informed every step of the way. This communication was crucial in maintaining trust and confidence. Many of the affected Bit get users expressed their gratitude toward Tech Cyber Force Recovery, acknowledging the team’s dedication to ensuring the recovery of their funds. In an era where digital asset security is a growing concern, this recovery serves as an important reminder of the role that blockchain forensics and recovery services play in protecting users. It also underscores the importance of having a trusted service like Tech Cyber Force Recovery available to assist in cases of breaches and theft. Their success in recovering the stolen Bitcoin, worth over $5 million, has made them a beacon of hope for users who might otherwise have lost everything. VISIT THE TEAMS ON WhatsApp +.(156)(172)(636)(97) OR TELEGRAM (AT)TECHCYBERFORC With the full recovery of the funds, users can now feel more secure about the safety of their digital assets, knowing that there are reliable and capable services like Tech Cyber Force Recovery to help when things go wrong.3
-
GET THE BEST HACKING SERVICE‼️ contact -: hackrontech gmail com, They are group of talented hackers who have been Hacking in secret for almost a decade now. Here Are List Of Hacking Services We Offer-: ▪️Phone Hacking & Cloning ▪️ m ail Hakcing ▪️Soc -; ial Me (dia) recovery (Facebook, Instagram e.t.c) ▪️Computer Hacking ▪️Deleted Files & Documents Recovery ▪️Breach Detection ▪️Website Hacking ▪️Tracking using GPS and Spyware ▪️Deleted Mails and Text messages Recovery OTHER SPECIAL HACKING SERVICES ▪️Binary Option Recovery ▪️Scam Money Recovery ▪️Bitcoin Multiplication ▪️Change Of Grades In Universities/Colleges ▪️Phone Calls Monitoring ▪️And lots more... For more enquiry, reachout via: hackrontech gmail com All Right Reserved.
I recommend professional expert Email: hackrontech @gmail com for Recovery Funds/ Cryptocurrency/ Recovery of Stolen Bitcoin / Bitcoin Mining/ Increase of Credit score/ MOBILE SPY REMOTE CONTROL ACCESS AUTHORIZATION. Removing Bad Records from Both Public and Private database.
-
My wife’s company recently suffered a catastrophic security breach that resulted in the theft of $155,500 worth of Bitcoin. The breach occurred through a sophisticated phishing attack that specifically targeted the company’s digital wallet. As primary stakeholders in this situation, the loss threatened not only our family’s savings but also my wife’s professional credibility. Panic set in as we realized that traditional financial institutions and law enforcement had limited tools to address cryptocurrency theft, leaving us feeling vulnerable and helpless. In the wake of this incident, we felt an overwhelming sense of urgency to act quickly. We began to explore our options, but the landscape of cryptocurrency recovery is fraught with challenges. Many people we spoke to expressed skepticism about the possibility of recovering stolen assets, which only added to our anxiety. However, we were determined not to give up. After exhaustive research, we discovered ASSET RESCUE SPECIALIST, a firm specializing in cryptocurrency forensics and crypto asset recovery. Their website immediately caught our attention, showcasing a range of proven success stories that highlighted their expertise in recovering stolen cryptocurrency. We were particularly impressed by their certifications in cybersecurity and their partnerships with legal authorities, which built our trust during this vulnerable time. The testimonials from previous clients who had successfully recovered their assets provided us with a glimmer of hope. We reached out to ASSET RESCUE SPECIALIST, and their team was responsive and empathetic, understanding the emotional toll this situation had taken on us. They explained their process in detail, outlining how they would leverage advanced blockchain analysis techniques to trace the stolen Bitcoin. Their professionalism and transparency reassured us that we were in capable hands. As we embarked on this recovery journey, we felt a renewed sense of hope. After weeks of diligent work and collaboration with the ASSET RESCUE SPECIALIST team, I am thrilled to share that I recovered my whole Bitcoin. This experience not only restored our financial stability but also reinforced our belief in the power of specialized expertise in navigating the complexities of cryptocurrency recovery. We are incredibly grateful for the support we received and relieved to have our assets back.1
-
LOST FUNDS TO A FAKE PLATFORM - RECOVERY HELP NEEDED HIRE ADWARE RECOVERY SPECIALIST
As the popularity of cryptocurrencies continues to rise, so does the risk of losing access to these valuable digital assets—whether through hacking, forgotten credentials, or accidental transactions. That’s where ADWARE RECOVERY SPECIALIST steps in as a true game-changer. Specializing in Bitcoin recovery, they help users regain access to lost or stolen assets with precision and care.
ADWARE RECOVERY SPECIALIST has established itself as a leader in the field of cryptocurrency recovery, offering services tailored to the unique challenges faced by both individual investors and businesses. Whether you’ve lost access to your wallet or experienced a security breach, their team is equipped with the tools and expertise to help you recover your assets quickly and securely. WhatsApp info:+12 (72332)—8343
In a landscape where cyber threats are becoming increasingly sophisticated, having a trusted partner like ADWARE RECOVERY SPECIALIST is essential. Their advanced recovery techniques, combined with in-depth knowledge of Bitcoin transactions, ensure a thorough and effective recovery process. They understand how stressful and overwhelming it can be to lose access to your digital funds, which is why their approach is both professional and compassionate. Website info: h t t p s:// adware recovery specialist. com
From personal experience, I can confidently say that ADWARE RECOVERY SPECIALIST transformed the way I handle Bitcoin recovery. Their dedication and effectiveness gave me peace of mind, knowing I had a team I could rely on. With their support, I now approach cryptocurrency investment with confidence rather than fear. Email info: Adware recovery specialist @ auctioneer. net
ADWARE RECOVERY SPECIALIST isn’t just another service provider—they are pioneers setting a new benchmark in the crypto recovery space. Their client-first mindset, cutting-edge solutions, and unwavering commitment to success make them the go-to experts for anyone looking to reclaim their digital assets. If you’re seeking a reliable, results-driven partner in Bitcoin recovery, look no further than ADWARE RECOVERY SPECIALIST. Telegram info: h t t p s:// t. me / adware recovery specialist12 -
TESTED AND TRUSTED BITCOIN/USDT RECOVERY EXPERT CONTACT SPARTAN TECH GROUP RETRIEVAL
The cryptocurrency market is extremely unpredictable, and many people have fallen victim to internet fraud and lost some of their cryptocurrency investments. I too fell for phony Telegram personnel. Due to a security breach at my wallet address, I lost all of my cryptocurrency coins totaling $178,000. My home may have been forfeited if I hadn't been able to successfully recover my crypto coins, which made up the majority of my savings and assets. This grieved and depressed me greatly. I complained online, and Spartan Tech Group Retrieval was suggested to me. Email; contact@spartantechgroupretrieval.org
By assisting me in recouping all of my losses in under six hours, this cryptocurrency recovery company saved my life. To complete the successful recovery of my cryptocurrency assets, I provided the essential requirements and pertinent information. I was ecstatic when I got my coins back. My ordeal began when I naively trusted some individuals on Telegram who claimed to be investment experts. Their convincing demeanor and promises of high returns led me to invest heavily. However, it quickly became apparent that I had been deceived when a security breach occurred, and my wallet address was compromised. The devastating loss of $178,000, which represented my life savings and a substantial portion of my assets, left me in a state of despair. The prospect of losing my home and financial stability was overwhelming. Desperate for a solution, I turned to the internet to find any possible way to recover my lost cryptocurrency. Amidst my frantic search, I came across numerous accounts of people who had experienced similar losses. Among the many recommendations, Spartan Tech Group Retrieval stood out. The testimonials about their effectiveness and reliability gave me a glimmer of hope. With nothing to lose, I decided to reach out to them. From the very first interaction. They responded promptly to my inquiry and requested all pertinent information regarding the security breach and the details of my lost investments. Their clear communication and transparent approach immediately put me at ease. They assured me that they would do everything in their power to recover my lost funds. The speed and efficiency with which Spartan Tech Group Retrieval operated were nothing short of miraculous. Within six hours of providing them with the necessary details, they had traced and recovered all my lost cryptocurrency. Their expertise in blockchain technology and their thorough understanding of cryptocurrency transactions were evident in their swift action. The relief and joy I felt upon seeing my coins back in my wallet were indescribable. Spartan Tech Group Retrieval not only helped me recover my lost assets but also provided invaluable guidance on how to safeguard my investments in the future. They educated me on best practices for securing my wallet and recognizing potential scams. This education was crucial in restoring my confidence in the cryptocurrency market and ensuring that I am better prepared to protect my assets moving forward. Their regulatory compliance further solidified my trust in them. Spartan Tech Group Retrieval operates with the highest standards of transparency and integrity, ensuring that their clients' interests are always protected. Spartan Tech Group Retrieval has been nothing short of life-changing. Their unparalleled professionalism, expertise, and dedication to client satisfaction make them a beacon of hope for anyone who has fallen victim to cryptocurrency fraud. If you ever find yourself in a similar position, I highly recommend reaching out to Spartan Tech Group Retrieval . Thank you, Spartan Tech Group Retrieval for the great work done and for saving my assets.
WhatsApp; +1 (562) 270‑4565
-
The topic of recovery services and the efficacy of Wizard Hilton Cyber Tech warrants a closer examination. Recovery services are a critical component of any comprehensive cybersecurity strategy, as they provide the means to restore systems, data, and operations in the event of a breach or other disruptive incident. Wizard Hilton Cyber Tech is a leading provider in this space, offering a suite of advanced recovery solutions designed to ensure business continuity and mitigate the potentially devastating impacts of cyber attacks. At the core of their offerings is a robust, AI-driven platform that continuously monitors systems, detects anomalies, and triggers rapid, automated recovery procedures. This allows organizations to bounce back quickly, often with minimal downtime or data loss. Wizard Hilton's approach also emphasizes the importance of comprehensive testing and simulation, putting recovery protocols through their paces to validate effectiveness and uncover potential weaknesses. Additionally, their team of seasoned cybersecurity experts provides hands-on guidance, tailoring solutions to the unique needs of each client. By combining cutting-edge technology with deep industry expertise, Wizard Hilton Cyber Tech has established itself as a trusted partner in the realm of recovery services, empowering organizations to safeguard their most valuable digital assets and ensure business resilience in the face of ever-evolving cyber threats. Contact: for assistance,
Email : wizardhiltoncybertech ( @ ) gmail (. ) com
OR
support ( @ ) wizardhiltoncybertech (.) com
WhatsApp number +130244578951 -
As the head of Quantum Innovations, based in Seattle, Washington, I’ve always taken pride in our company’s commitment to cutting-edge technology and innovation. However, a recent security breach has underscored how vulnerable we were to a major cybersecurity threat involving our corporate mobile devices. The breach began when several employees unknowingly downloaded a malicious app from a third-party app store. What initially appeared to be a harmless app turned out to contain malware, granting cybercriminals access to sensitive company data. In total, the attackers stole approximately $200,000 USD worth of proprietary business information, including financial records, intellectual property, and confidential communications. Even more alarming, the breach led to the theft of employee banking details, enabling unauthorized transfers of funds from both personal and corporate accounts. The breach was discovered when our IT team noticed unusual activity on the affected devices, including unauthorized access to secure files and suspicious data transfers. After conducting a thorough investigation, we realized that the malware had been secretly transmitting our valuable data to an external server, including sensitive financial information. At that point, it became clear that the situation was far worse than we had initially anticipated.In response to this crisis, I reached out to TRUST GEEKS HACK EXPERT at Web, https :/ / t r u s t g e e k s h a c k e x p e r t . c o m/ E m a i l : i n f o @ t r u s t g e e k s h a c k e x p e r t.c o m And T e l e G r a m:: T r u s t g e e k s h a c k e x p e r t, A renowned cybersecurity firm with a reputation for its expertise in mobile device security and data recovery. Their team acted swiftly to assess the full scope of the attack, clean the infected devices, and secure our mobile systems.Thanks to their expert intervention, we were able to completely remove the malware from all affected devices, TRUST GEEKS HACK EXPERT data recovery specialists went above and beyond to recover not only the stolen company data but also the funds that had been illicitly transferred from both employee and corporate bank accounts. Through negotiation with authorities and tracking the stolen funds, they successfully managed to recover every dollar that had been taken. Their diligence and expertise were truly exceptional, and because of their efforts, we were able to avert what could have been a catastrophic financial loss.In the wake of this breach, we are more committed than ever to fortifying our security measures. The swift response and effective recovery efforts from TRUST GEEKS HACK EXPERT have been invaluable in restoring our confidence and securing our operations.1
-
THE BEST CRYPTO RECOVERY SERVICE IN 2024 HIRE DUNAMIS CYBER SOLUTION
A
Cautionary Tale About a Sophisticated Scam Three days ago, I fell victim to a highly sophisticated scam that cost me 30,000 Euros. As a London resident, I’ve always prioritized online security. When I heard about the LastPass breach, I immediately changed my passwords, believing my information was safe. However, I soon realized that the worst was yet to come.The scam started with an email that appeared to be from LastPass, warning me about unusual activity. It seemed legitimate—complete with branding and an urgent subject line. The email included a customer support number, which I called in panic.A calm, professional-sounding individual answered, claiming to be a LastPass security expert. They told me my account had been compromised and advised me to install recovery software. Trusting them, I followed their instructions without realizing I was being scammed.Hours later, I discovered that 30,000 Euros had been drained from my bank accounts. After the initial shock, I found DUNAMIS CYBER SOLUTION Recovery, a company specializing in scam recovery. They acted swiftly, helping me trace the scammers and recover the stolen funds.While the experience was harrowing, it taught me an invaluable lesson: Always verify the authenticity of any communication, no matter how convincing it seems. If you fall victim to a scam, don’t hesitate to reach out to experts who can help you recover. 8
8 -
I recently had a fantastic experience with Cyberpunk Programmers that I can’t stop raving about. After a phishing attack drained my wallet of 2.5 Bitcoin, I was convinced my funds were gone for good. Desperate, I stumbled across Cyberpunk Programmers online and decided to give them a try—best decision ever.
Their team was incredibly knowledgeable and jumped into action right away. They analyzed the breach, tracked the transactions, and kept me updated every step of the way. I was blown away by their skills; in just under a month, they recovered my 2.5 Bitcoin, restoring $150,000 worth of value at today’s rates. The process was straightforward, and their communication made me feel confident despite the chaos I’d been through.
What sets Cyberpunk Programmers apart is their blend of cutting-edge tech and genuine customer care. They didn’t just recover my funds—they also shared tips to protect my wallet from future attacks. Their pricing was fair, especially given the life-changing result they delivered.
If you’ve lost Bitcoin or any crypto, I can’t recommend Cyberpunk Programmers enough. They turned my despair into disbelief when I saw 2.5 Bitcoin back in my account. No matter the amount, their expertise is worth it. I’ve already told friends about them, and I urge anyone in a similar mess to reach out. Cyberpunk Programmers isn’t just a service—they’re a lifeline for crypto users. Reliable, fast, and brilliant at what they do! Their contact details are;
Email: cyberpunkatprogrammerdotnet3 -
DOGDECOIN THEFT RECOVERY REVIEW /// PASSCODE CYBER RECOVERY
My family fell victim to a digital security breach when my teenage Daughter downloaded malware disguised as a game hack, resulting in the theft of 1.2 million Dogecoins. Passcode Cyber Recovery helped track the stolen funds and collaborated with Interpol, leading to the recovery of all the stolen Dogecoins. This experience taught my family a valuable lesson about digital security and the importance of protecting assets. And yes my daughter it's fine just kids on of those many mistakes Thank you.
PASSCODE CYBER RECOVERY
WhatsApp: +1(647)399-4074
Telegram : @passcodecyberrecovery2 -
SURVIVING THE BYBIT HACK HOW CRYPTO RECOVERY CONSULTANT SECURE MY ASSETS
It was the kind of morning that left my heart pounding in my chest. My phone buzzed with a series of alerts—emails, messages, all talking about one thing: Bybit had been hacked. North Korean hackers had breached the exchange, and the total losses were over 1.5 billion dollars in cryptocurrency, Ethereum to be precise. My stomach churned as I read, realizing I was one of the many affected. I had been an avid Ethereum investor, with a substantial amount of my savings tied up in the coin. The idea of losing it all was unbearable. But panic was no help, so I immediately began searching for solutions. That’s when I stumbled across a company that specialized in crypto recovery and securing your asset, CRYPTO RECOVERY CONSULTANT. Their website promised to assist with situations just like mine. Skeptical but desperate, I reached out, hoping for a miracle. To my surprise, a representative called me within minutes. They explained that they had experience securing wallets from compromised exchanges and securing coins during massive hacks like the Bybit breach. After a brief consultation, they assured me they could secure my Ethereum by implementing a stronger security system that would block any unauthorized access. They guided me step-by-step, helping me transfer my assets to a more secure wallet and setting up additional layers of protection that I never even knew existed. Thanks to their swift action and expertise, I felt a weight lift from my shoulders. The hackers wouldn’t be able to touch my Ethereum now. My coins were safe, protected by multi-signature authentication, cold storage, and state-of-the-art encryption. Without CRYPTO RECOVERY CONSULTANT, I would have lost everything. Their quick thinking and advanced security measures saved my assets from the grasp of cybercriminals. I couldn’t be more grateful. Now, I sleep soundly, knowing that my Ethereum is safe, all thanks to them. cryptorecoveryconsultant312[@]zohomail,,,com cryptorecoveryconsultant[@]cash4u,,,com 1
1 -
WIZARD JAMES RECOVERY: A sympathetic advocate for recovery with knowledge of sustainable recovery.
Recovering one's bitcoin holdings following a devastating breach can be a challenging and complex procedure, but with the right guidance and information, it is possible to get back what was lost. In my case, a highly competent cyberattack resulted in the instantaneous loss of my digital assets from my cryptocurrency wallet. Panic and sorrow began to set in as I battled with the realization that my financial stability had been shattered. I didn't give up, though, and after much investigation, I discovered Wizard James Recovery, a company renowned for its ability to track down and recover stolen cryptocurrency. When I spoke with their employees, they listened intently to the details of my situation and gave me a warm, understanding response. Using their deep knowledge of blockchain technology and hacking methods, the Wizard James experts began meticulously following the whereabouts of my stolen funds as they navigated the intricate world of cryptocurrency transactions. They relentlessly followed the digital trail, uncovering the complex web of exchangers and wallets the hackers had used to conceal their actions. The recovery process was made possible by the Wizard James Recovery team's utilization of cutting-edge equipment and sophisticated investigative techniques to find my missing valuables. In order to freeze the illegal funds and begin the retrieval procedure, the Wizard James Recovery specialists worked with law authorities and cryptocurrency exchanges in a delicate and complex operation. I was thrilled to see my cryptocurrency holdings returned to my legitimate wallet after overcoming a complex web of legal and technological obstacles thanks to the team's knowledge and perseverance. I will always be grateful to the Wizard James Recovery team for their unwavering efforts in helping me get back what was properly mine and leading me through this terrifying experience. The sense of relief and restored peace of mind was evident. For additional information:
WIZARDJAMESRECOVERY @ USA . COM
telegram:WizardJamesRecovery
wh@tsapp + 4 4 7418 3672041 -
RECOVERING OF LOST BITCOIN: RAPID DIGITAL RECOVERY, STEP BY STEP PROCESS
When a devastating data breach left me with a crippling loss of 82,000 ETH, I was utterly devastated. As a seasoned crypto investor, I had carefully amassed this substantial fortune over years of diligent research and strategic trading. But in the blink of an eye, it had all been snatched away, leaving me feeling helpless and on the brink of financial ruin. Fortunately, I was referred to the experts at Rapid Digital Recovery, a renowned cybersecurity firm specializing in the recovery of lost or stolen digital assets. From the moment I reached out, Web site Info: https: // ra pi ddigit alrecove ry .o rg...I was met with an unparalleled level of professionalism and expertise. The team quickly assessed the situation, drawing upon their extensive knowledge of blockchain technology and hacking techniques to devise a meticulous recovery plan. They worked tirelessly, leaving no stone unturned in their pursuit of my missing Ethereum. Their dogged determination and technical prowess were nothing short of awe-inspiring, as they navigated the complex web of digital wallets, exchange platforms, and illicit transactions. After weeks of painstaking investigation and strategic maneuvers, the Rapid Digital Recovery team triumphantly recovered the entirety of my 82,000 ETH, restoring my financial security and peace of mind. I am forever grateful for their unwavering commitment to their craft and their ability to transform a devastating loss into a remarkable victory, solidifying their reputation as the gold standard in the world of cryptocurrency recovery. Rapid Digital Recovery was a game-changer in the world of crypto recovery. If you find yourself in a similar situation where your cryptocurrency is locked away and seemingly irretrievable, I highly recommend their services. Their professionalism, combined with a genuine commitment to customer success, made all the difference in my experience. Thanks to them, I now have my 82,000 ETH back, and I couldn’t be more grateful. Send a message to: What sapp Info: +1 41 4 80 7 14 85 3
3 -
In February, I made a critical mistake that had serious consequences for our organization. While reviewing my emails, I clicked on a phishing link embedded in what appeared to be a legitimate invoice. This seemingly innocuous action triggered a significant security breach, ultimately leading to the loss of 25 BTC (Bitcoin) from our company wallet. As the individual responsible for this incident, I felt an overwhelming sense of responsibility and concern for the implications it had on our financial security. The phishing attack was expertly crafted, making it difficult to recognize the threat, and I never anticipated that my actions would lead to such a severe breach. Our company acted swiftly to mitigate the damage by engaging TECHY FORCE CYBER RETRIEVAL, a firm known for its expertise in cryptocurrency recovery. TECHY FORCE CYBER RETRIEVAL's response was remarkable. The team quickly mobilized, employing advanced forensic techniques to trace the stolen funds. Their meticulous analysis of blockchain transactions was crucial in identifying the pathways through which the stolen BTC had been funneled. The investigators at TECHY FORCE CYBER RETRIEVAL utilized sophisticated tools to track the movement of our cryptocurrency across various exchanges. They collaborated with exchange platforms to flag the illicit transactions and prevent any further withdrawals. TECHY FORCE CYBER RETRIEVAL's deep understanding of the cryptocurrency landscape allowed them to pinpoint the exact locations where the stolen funds had been deposited. Thanks to the persistent efforts and strategic negotiations of TECHY FORCE CYBER RETRIEVAL, all 25 BTC were successfully recovered. Their comprehensive approach not only involved tracing the funds but also included liaising with law enforcement and regulatory bodies to ensure that the perpetrators faced consequences for their actions. This has been a stark reminder of the importance of cybersecurity awareness. I have learned firsthand how easily one can fall victim to such attacks, and I am now committed to being more vigilant and proactive in recognizing potential threats. I am grateful for the swift intervention of TECHY FORCE CYBER RETRIEVAL, which not only restored our lost funds but also reinforced our confidence in the digital currency ecosystem. I encourage everyone to remain cautious and informed about cybersecurity to prevent similar incidents in the future.
ASK FOR HELP WITH \\
h ttp s: / / techy forcecy berretrieval . com2