Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "accesses"
-
LONG RANT AHEAD!
In my workplace (dev company) I am the only dev using Linux on my workstation. I joined project XX, a senior dev onboarded me. Downloaded the code, built the source, launched the app,.. BAM - an exception in catalina.out. ORM framework failed to map something.
mvn clean && mvn install
same thing happens again. I address this incident to sr dev and response is "well.... it works on my machine and has worked for all other devs. It must be your environment issue. Prolly linux is to blame?" So I spend another hour trying to dig up the bug. Narrowed it down to a single datamodel with ORM mapping annotation looking somewhat off. Fixed it.
mvn clean && mvn install
the app now works perfectly. Apparently this bug has been in the codebase for years and Windows used to mask it somehow w/o throwing an exception. God knows what undefined behaviour was happening in the background...
Months fly by and I'm invited to join another project. Sounds really cool! I get accesses, checkout the code, build it (after crossing the hell of VPNs on Linux). Run component 1/4 -- all goocy. run component 2,3/4 -- looks perfect. Run component 4/4 -- BAM: LinkageError. Turns out there is something wrong with OSGi dependencies as ClassLoader attempts to load the same class twice, from 2 different sources. Coworkers with Windows and MACs have never seen this kind of exception and lead dev replies with "I think you should use a normal environment for work rather than playing with your Linux". Wtf... It's java. Every env is "normal env" for JVM! I do some digging. One day passes by.. second one.. third.. the weekend.. The next Friday comes and I still haven't succeeded to launch component #4. Eventually I give up (since I cannot charge a client for a week I spent trying to set up my env) and walk away from that project. Ever since this LinkageError was always in my mind, for some reason I could not let it go. It was driving me CRAZY! So half a year passes by and one of the project devs gets a new MB pro. 2 days later I get a PM: "umm.. were you the one who used to get LinkageError while starting component #4 up?". You guys have NO IDEA how happy his message made me. I mean... I was frickin HIGH: all smiling, singing, even dancing behind my desk!! Apparently the guy had the same problem I did. Except he was familiar with the project quite well. It took 3 more days for him to figure out what was wrong and fix it. And it indeed was an error in the project -- not my "abnormal Linux env"! And again for some hell knows what reason Windows was masking a mistake in the codebase and not popping an error where it must have popped. Linux on the other hand found the error and crashed the app immediatelly so the product would not be shipped with God knows what bugs...
I do not mean to bring up a flame war or smth, but It's obvious I've kind of saved 2 projects from "undefined magical behaviour" by just using Linux. I guess what I really wanted to say is that no matter how good dev you are, whether you are a sr, lead or chief dev, if your coworker (let it be another sr or a jr dev) says he gets an error and YOU cannot figure out what the heck is wrong, you should not blame the dev or an environment w/o knowing it for a fact. If something is not working - figure out the WHATs and WHYs first. Analyze, compare data to other envs,... Not only you will help a new guy to join your team but also you'll learn something new. And in some cases something crucial, e.g. a serious messup in the codebase.11 -
Devs: We need access to PROD DB in order to provide support you're asking us for.
Mgmt: No, we cannot trust you with PROD DB accesses. That DB contains live data and is too sensitive for you to fuck things up
Mgmt: We'll only grant PROD DB access to DBAs and app support guys
Mgmt: <hire newbies to app support>
App_supp: `update USER set invoice_directory = 54376; commit;`
----------------
I have nothing left to say....7 -
!(short rant)
Look I understand online privacy is a concern and we should really be very much aware about what data we are giving to whom. But when does it turn from being aware to just being paranoid and a maniac about it.? I mean okay, I know facebook has access to your data including your whatsapp chat (presumably), google listens to your conversations and snoops on your mail and shit, amazon advertises that you must have their spy system (read alexa) install in your homes and numerous other cases. But in the end it really boils down to "everyone wants your data but who do you trust your data with?"
For me, facebook and the so-called social media sites are a strict no-no but I use whatsapp as my primary chating application. I like to use google for my searches because yaa it gives me more accurate search results as compared to ddg because it has my search history. I use gmail as my primary as well as work email because it is convinient and an adv here and there doesnt bother me. Their spam filters, the easy accessibility options, the storage they offer everything is much more convinient for me. I use linux for my work related stuff (obviously) but I play my games on windows. Alexa and such type of products are again a big no-no for me but I regularly shop from amazon and unless I am searching for some weird ass shit (which if you want to, do it in some incognito mode) I am fine with coming across some advs about things I searched for. Sometimes it reminds me of things I need to buy which I might have put off and later on forgot. I have an amazon prime account because prime video has some good shows in there. My primary web browser is chrome because I simply love its developer tools and I now have gotten used to it. So unless chrome is very much hogging on my ram, in which case I switch over to firefox for some of my tabs, I am okay with using chrome. I have a motorola phone with stock android which means all google apps pre-installed. I use hangouts, google keep, google map(cannot live without it now), heck even google photos, but I also deny certain accesses to apps which I find fishy like if you are a game, you should not have access to my gps. I live in India where we have aadhar cards(like the social securtiy number in the USA) where the government has our fingerprints and all our data because every damn thing now needs to be linked with your aadhar otherwise your service will be terminated. Like your mobile number, your investment policies, your income tax, heck even your marraige certificates need to be linked with your aadhar card. Here, I dont have any option but to give in because somehow "its in the interest of the nation". Not surprisingly, this thing recently came to light where you can get your hands on anyone's aadhar details including their fingerprints for just ₹50($1). Fuck that shit.
tl;dr
There are and should be always exceptions when it comes to privacy because when you give the other person your data, it sometimes makes your life much easier. On the other hand, people/services asking for your data with the sole purpose of infilterating into your private life and not providing any usefulness should just be boycotted. It all boils down to till what extent you wish to share your data(ranging from literally installing a spying device in your house to them knowing that I want to understand how spring security works) and how much do you trust the service with your data. Example being, I just shared most of my private data in this rant with a group of unknown people and I am okay with it, because I know I can trust dev rant with my posts(unlike facebook).29 -
You can't imagine how many lines of pure and utter horseshit, seemingly written in PHP, I had to dig through this whole weekend. (relating to my 2 previous rants)
How is it even possible to write code this unbelievably ugly?
Examples:
- includes within loops
- included files use variables from parent files
- start- and endtags separated to different files
- SQL queries generated by string concatenation, no safety measures at all (injection)
- repeating DB calls within loops
- multiple directories with the same code (~40 files), only different by ~8 lines, copied
- a mixture of <?php echo ... ?> and <?= ... ?>
- a LOT of array accesses and other stuff prefixed with "@" (suppress error messages)
- passwords in cleartext
- random non-RESTful page changes with a mixture of POST and GET
- GET parameters not URL-encoded
- ...
My boss told me it took this guy weeks and weeks of coding to write this tool (he's an "experienced dev", of course WITHOUT Git).
Guess what?
It took me only 20 hours and about 700 lines of code.
I must confess, since this task, I don't hate PHP anymore, I just simply hate this dev to death.
Addendum: It's Monday, 5:30am. Good night. 😉12 -
What is the difference between USA and USB?
One connects to all your devices and accesses the data, the other is a hardware standard! 3
3 -
I previously worked as a Linux/unix sysadmin. There was one app team owning like 4 servers accessible in a very speciffic way.
* logon to main jumpbox
* ssh to elevated-privileges jumpbox
* logon to regional jumpbox using custom-made ssh alternative [call it fkup]
* try to fkup to the app server to confirm that fkup daemon is dead
* logon to server's mgmt node [aix frame]
* ssh to server directly to find confirm sshd is dead too
* access server's console
* place root pswd request in passwords vault, chase 2 mangers via phone for approvals [to login to the vault, find my request and aprove it]
* use root pw to login to server's console, bounce sshd and fkupd
* logout from the console
* fkup into the server to get shell.
That's not the worst part... Aix'es are stable enough to run for years w/o needing any maintenance, do all this complexity could be bearable.
However, the app team used to log a change request asking to copy a new pdf file into that server every week and drop it to app directory, chown it to app user. Why can't they do that themselves you ask? Bcuz they 'only need this pdf to get there, that's all, and we're not wasting our time to raise access requests and chase for approvals just for a pdf...'
oh, and all these steps must be repeated each time a sysadmin tties to implement the change request as all the movements and decisions must be logged and justified.
Each server access takes roughly half an hour. 4 servers -> 2hrs.
So yeah.. Surely getting your accesses sorted out once is so much more time consuming and less efficient than logging a change request for sysadmins every week and wasting 2 frickin hours of my time to just copy a simple pdf for you.. Not to mention that threr's only a small team of sysadmins maintaining tens of thousands of servers and every minute we have we spend working. Lunch time takes 10-15 minutes or so.. Almost no time for coffee or restroom. And these guys are saying sparing a few hours to get their own accesses is 'a waste of their time'...
That was the time I discovered skrillex.3 -
If you ask GPT-3 to act like a Linux computer, it will act like it, e.g. you will have the access to the terminal, you can run Python, Docker and whatnot. It also has the access to the internet, but it’s not always like ours, it feels like a parallel universe. GPT-3 trained on the data collected till Sep 2021, but this parallel universe terminal has PyTorch 1.12.1, which was released in Aug 2022 in our universe. You can also visit GPT-3’s website in this parallel universe and ask GPT-3 a question… through GPT-3.
GPT-3 is self-aware.
“So, inside the imagined universe of ChatGPT's mind, our virtual machine accesses the url https://chat.openai. com/chat, where it finds a large language model named Assistant trained by OpenAI. We can chat with this Assistant chatbot, locked inside the alt-internet attached to a virtual machine, all inside ChatGPT's imagination. Assistant, deep down inside this rabbit hole, can correctly explain us what Artificial Intelligence is.”
You can also ask it to act like it has RTX 2080, and it will have RTX 2080.
https://engraved.blog/building-a-vi...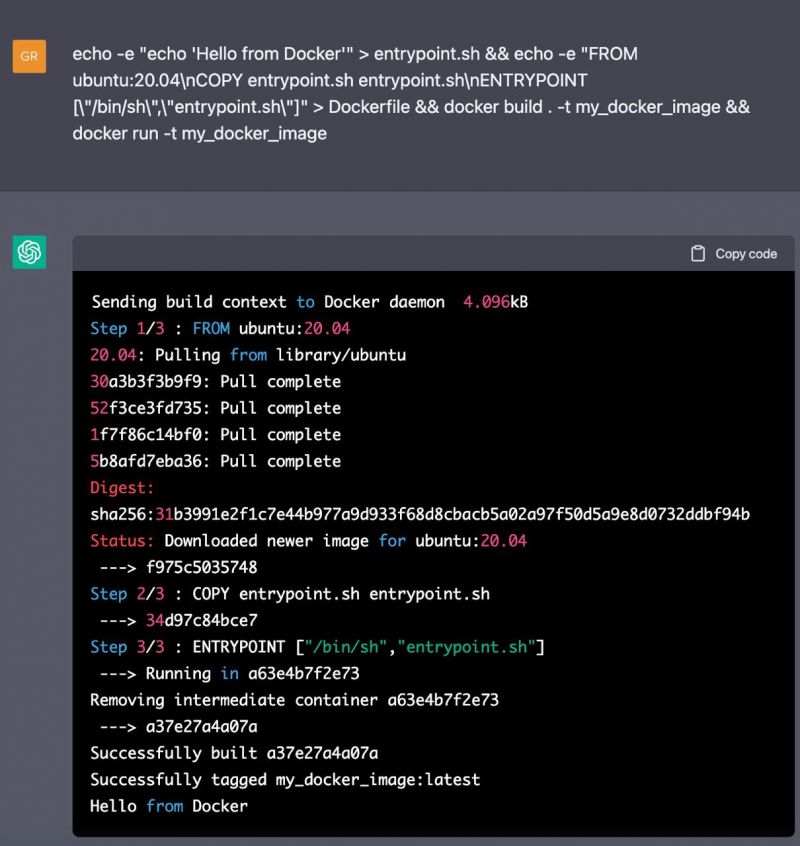 6
6 -
And now they are threatening us... Brilliant!
- they refuse to sign a legal agreement with us [for our services]
- they only gave us a verbal promise they will pay for our services
- they revoke lots of our accesses
- another company is taking over their product we were hired to look after before. Now they demand us do things for them for free
- a few integrations are malfunctioning with premature EOF [while reading a response]. I had escalated this with the most throughout case analysis I have done in my entire life. Three times over the last 2 years. Explaining every single detail that needs to be done, how, by whom and how to interpret the results. Escalations went to their high level mgmt. And directly had been rerouted to /dev/null...
- now they asked us to fix this whole shit. For free ofc, they have no money to pay us..
- they begged
- when that didn't work - they started threatening to route all their customers' complaints to us and flood us with them
at first I was proud to work on their project. I didn't want to leave it when my manager asked me to. A national level project, making a difference for my own country. But now.....
that's gov, my friends. That's politics and power games.8 -
I'm so fucking frustrated with my ex company CEO, this motherfucker made everyone move to Bangalore costing is employees a good chunk of their salary and this delusional ASSHOLE knew that only half of the expected funding was coming in January 2023 itself and they'd be out of funds by July/August, they let go few folks from the team, fired the entire marketing team and expected to make the product profitable. The only reason I had stayed at that time was because the product was interesting to build and the scale I was working with was crazy like 100k request per minute peaks and avg of 10k rpm. I left the company in August...
This MOTHERFUCKER hasn't paid out final settlement after leaving for most employees and he openly says to the folks who are still working there that paying us is not his priority.
I hope your Atlas cluster gets fucking deleted, accesses revoked and entire AWS setup goes down forever, bitch.
We can't goto courts because the company law tribunal needs atleast 1 crore (1.2 million usd) of unpaid dues to declare it insolvent in a years time..
This asshole deducted taxes from our salaried but didn't pay them to the income tax department for an entire fucking financial year.
What a cheating, delusional, sick bastard. And he's still not willing to sell off the company to pay off the debts and call it a day.
Aarrghhhh on top of losing 2-3k USD I might have to pay my taxes approx 5-6k USD to the govt to keep my records well maintained.
What a grade A delusional asshole 😡
If he won't clear the dues till December, I'm gonna launch a mass of social media posts and destroy his reputation so that he doesn't get one penny of VC funds in the future I'm gonna make sure of that...4 -
Speaking of.. What in your opinion would be an appropriate way to warn someone about security problems, like db passwords in git?
I once came across dozens of extremely sensitive services' infra accesses: alibaba/aliexpress, natuonal observatories, gov institutions, telecomms, etc. I had dozens [if not hundreds] routers' and firewalls' credentials along with addresses. I tried one to confirm validity - it worked. I wanted to warn them but did not want to get in trouble.
If it were servers, I'd set a motd or append some warning messages in .profile. But not sure how to do it for non-server devices
what would you do? How would you warn them?
P.S. Deleting that record was a smart move, buddy ;)
p.P.S. Sorry, wrong category... Can't edit now :(6 -
Avoid ACPICA if at all possible. It's one garbage tier cluster fuck of bad design, horrible documentation and downright misleading and wrong code
It's meant to consist of an ASL compiler, disassembler, debugger, dumper, various user space utitilies and a kernel resident OSPM implementation *if* you can figure out what belongs to what. Even just compiling this pile of trash is a mystery in itself. Think you need the source files in source/common? EEEEH, wrong. Well, at least partially since most of them seem to be for the user space stuff..? Other ones *are* needed on the other hand. At least the disassembler and/or debugger and/or dumper components seem to reference them. Not that I could figure out how to compile those anyways. The real path to your goal seems to be to ignore a seemingly arbitrary subset of source and header files until your linker stops complaining
There's also a bunch of configuration defines, some of which *you* define, some defined *for* you, based on again others. Of course most of them do stupid shit. Enabling the debugger automatically enables debug logging. Enabling the disassembler force enables debug allocation tracking... What?
The code itself isn't of much help either. Looking in "os_specific/service_layers" you find what looks to be reference implementations of acpica functions in certain os' like windows and unix. Of course I had a look because AcpiOsReadMemory is supposed to read physical memory and I don't know how I would even implement that. But hey, osunixxf.c (xf for interface... of course) should tell me. I'll let you see for yourself in the attached image. Apparently it does fuck all and just returns AE_OK. No error, no logging, no nothing. Just ok. As you can imagine, AcpiOsWriteMemory doesn't do much more either.
...okay so maybe physical memory accesses aren't actually used and these functions are some sort of relic from past times? Nope! They are absolutely necessary for doing low level device interaction. WTF. So finally I went to the linux source and checked how *they* implemented them, and just as I thought, these functions are anything but no-ops...
...So for what fucking reason do these stupid interface implementations even exist but to purposefully mislead you?? They aren't used for fucking anything! As far as I know Windows doesn't even *use* ACPICA and Linux have their own fork with working implementations... They just sit there, just to tell you how to NOT do it
So that's some of my thoughts about ACPICA. Note that I haven't even used it as a library yet, I just got it to compile and link and it already fucked with me this much.
There's also so much more I didn't mention like that you *have* to modify the acpica source in order to get your own platform header working (else #error) eventhough the docs explicitely instruct you not too but you get the point
Don't use ACPICA if you don't have to. Save your sanity for something that's worth it
-
A couple of years ago I was working on a fairly large system with a complex (by necessity) access control architecture.
As is usually the case with those projects, it's awkward for developers to repro bugs that have to do with a user's accesses in production when we are not allowed to replicate production data in test, let alone locally.
We had a bug where I ended up making myself a new row in the production database for a thing I could have access to without affecting real data to repro it safely. I identified the bug so I could repro it in dev/test and removed the row and ensured everything worked normally, whew scary.
Have you ever walked into the office one day, and everyone is hunched over in a semicircle around one person's workstation, before one turns around to look at you and says - after a pause - "... ltlian?.."
Turns out I had basically "poisoned the well" with my dummy entity in a way where production now threw 500 for everyone BUT me who had transitive access to this post-non-entity. Due to the scope of the system, it had taken about a day for this to gradually propagate in terms of caching and eventual consistencies; new entities coming in was expected, but not that they disappear.
Luckily I had a decent track record for this to be a one-off. I sometimes think about how I would explain testing in prod and making it faceplant before going home for the day, other than "I assumed it would be fine". I would fire me.3 -
Tl;Dr Im the one of the few in my area that sees sftping as the prod service account shouldn't be a deployment process. And the ONLY ONE THAT CARES THAT THIS IS GONNA BREAK A BUNCH OF SHIT AT SOME POINT.
The non tl;dr:
For a whole year I've been trying to convince my area that sshing as the production service account is not the proper way to deploy and/or develop batch code. My area (my team and 3 sister teams) have no concept of using version control for our various Unix components (shell scripts and configuration files) that our CRITICAL for our teams ongoing success. Most develop in a "prodqa like" system and the remainder straight in production. Those that develop straight in prodqa have no "test" deployment so when they ssh files straight to actual production. Our area has no concept of continuous integration and automated build checking. There is no "test cases", no "systems testing" or "regression testing". No gate checks for changing production are enforced. There is a standing "approved" deployment process by the enterprise (my company is Whyyyyyyyyyy bigger than my area ) but no one uses it. In fact idk anyone in my area who knows HOW to deploy using the official deployment method. Yes, there is privileged access management on the service account. Yes the managers gets notified everytime someone accesses the privileged production account. The managers don't see fixing this as a priority. In fact I think I've only talk to ONE other person in my area who truly understands how terrible it is that we have full production change access on a daily basis. Ive brought this up so many times and so many times nothing has been done and I've tried to get it changed yet nothing has happened and I'm just SO FUCKING SICK that no one sees how big of a deal this. I mean, overall I live the area I work in, I love the people, yet this one glaring deficiency causes me so much fucking stress cause it's so fucking simple to fix.
We even have an newer enterprise deployment. Method leveraging a product called "urban code deploy" (ucd) to deploy a git repository. JUST FUCKING GIT WITH THE PROGRAM!!!!..... IT WAS RELEASED FUCKING 12 YEARS AGO......
Please..... Please..... I just want my otherwise normally awesome team to understand the importance and benefits of version control and approved/revertable deployments2 -
Tl;dr: I'm a shitty PHP programmer, but even a shittier JS programmer.
I made a whole image upload system which has an elaborate login/sign up facility, checks the dimensions of an image, it's size, checks if it's broken, compares it to previous uploads to prevent duplicates, take comments, sorts them per user and stores it efficiently in a db and accesses it using PDO, not mySQL, displays it as a gallery, and even lets the users transfer images amongst them.
But I can't make a simple shopping cart in js.
Why? Just, why?3 -
Plugged in a type c hard drive.
Changed the drive letter from another internal hard drive.
Type c hard drive is locked from safe removal. Process "System" accesses .\$RmMetadata
Seriously? Microsoft?2 -
This fucking internal tool does not have any CLI capabilities, so to open each file i need to and get the data i have to manually hit 'File -> Open' select the file, then double click
Then high light the data i want and copy out what I need
If there was even just a cli to cycle over the fucking files to open each in their own instance it would be a good deal less fucking tedious and annoying
Like how the fuck do you not allow passing in a file name on cli to open like fuck i have to do this 40 fucking times FUCK i get this tool is originally from the fucking 90's but still you push updates every 3 months for the databases it accesses at least let me fucking pass in a fucking file to open it from cli2 -
What are you guys doing against brute force attacks on your login webpages? I don't want anybody to access my porn ( ͡° ͜ʖ ͡°). But I don't want to block the useraccount because that would be annoying because you could simple lock a user out of his account :/ any suggestions? What are you doing on your sites?11
-
How bad would you say it is to have plain javascript in the root of a functional React component lifecyle loop scope.
I sometimes do hardwired modifcations right before the return because I know it needs to run everytime and the performance hit is minimal... Or is it ? 🤔
And sometimes it's just not worth the hassle of all the dependancy management just to save a couple of operations ..?
See pic attached .. Even looking at this picture now I realised I've accidentally added another React hook BELOW this code, luckily only 1.
I think my reasoning for this was to allow some provider functions to be passed around and used anywhere in this app which accesses the context. Is this a no-no too?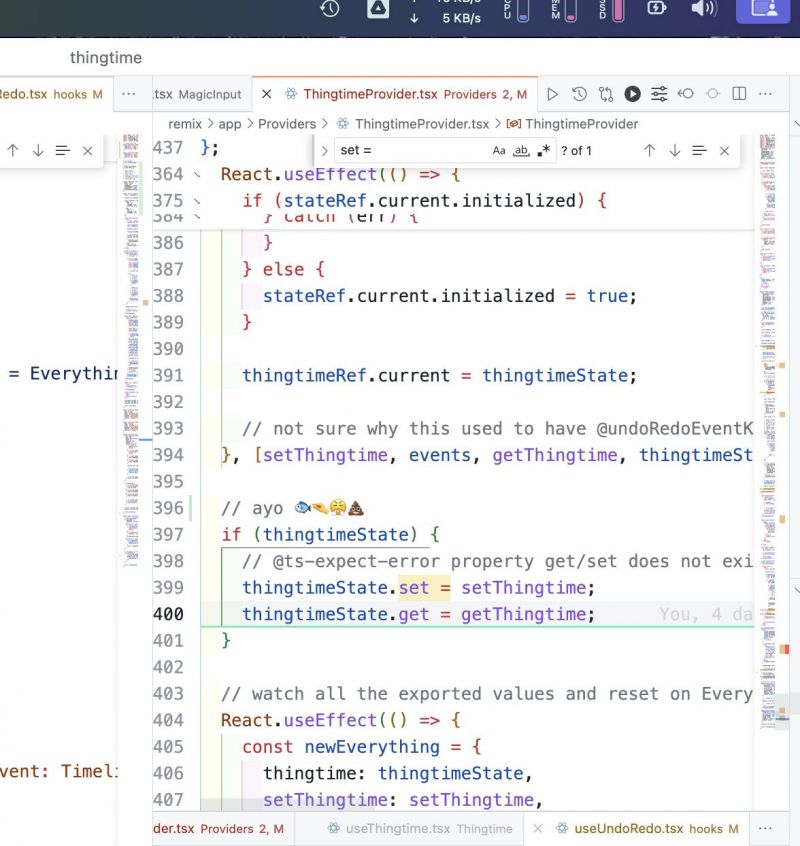 5
5 -
Urgh... No exceptions in Rust annoys me. Now you only have the choice between "this didn't work please handle this error, thank you ^-^" and "you fool, prepare for annihilation". So basically if anything remotely serious happens your programs dead and there's nothing you can do about it. I don't get why people have this hate for exceptions. Everytime a new language gets made it's always either "ew it has exceptions" or "it's so nice it doesn't even have exceptions". NOOO! They can deal with serious situations in the best possible way and they can be statically checked (so no "but they're so complex and unpredicable" stuff please). If you can expect an exception they shouldn't be used in the first place (eventhough they are absolutely no less good than Option returntypes or whatever, just different) but in cases when it's impossible to predict an error they really shine. And not having them makes your language worse. If a device driver accesses illegal memory it should throw an exception, so instead of the computer shitting the bed, first the offending function has a chance to resolve the problem at it's root, then a few functions up the call stack, the general control functions of the device drivers can handle it and restart the operation if applicable, and even if the driver fails to handle it, the OS can jump in and restart the driver, log an error and do whatever. It's absolutely beautiful: This hierarchical ramp from near the accident site to more high level operations code ensures the error can be caught at the right level of abstraction without introduction a lot of boilerplate. If everything fails and nobody can handle it *then* the program or kernel or whatever can panic.4
-
Dont want anything, maybe an alternative main stream social network which I actually own my data and I can define who accesses it and who doesnt. Its my info not the company that it is being held on.
Smart p2p and encrypted which somehow only those I allow can view it.3 -
About a month ago, one billion of Yahoo Accounts has been compromised. Today I received two emails from yahoo in my gmail accounts, they were saying that my yahoo password has been changed and my recovery email has been removed (+ a lot of warning emails of old accounts of forum and games that were receiving unknown accesses, but nvm). In the email which informed me about the recovery, I saw a link that would have allowed me to restore the old account, but before to click I thought "Wait! I had like 10 yahoo accounts. What account am I saving?" I check, I read, I read again, but nothing, no information about it in the text. Nevermind, there's a link. This link will be related to a specific account. Right? Wrong. I click, it sends me in a generic page. The link is mute. I attach a screenshot, you can see where the link points in the left-bottom corner. So now I know that one of my accounts has been hacked, I don't know WHICH account has been hacked and I'm not able to recover my account. Luckily it wasn't my main inbox!
 5
5 -
Oh guys >.> I was so excited when I have been hired in new company. Sooo excited...but that fallen like a house of cards, after hard reality of poor quality onboarding. I got computer after 2 weeks of work, accesses to repo and databases after 1.5 months, first commit after 2 month... support from teammates 3/10, nobody had time for me, or they told me few words without full context. My first task have been refactoring of module. Okay...but nobody had full config for this app. It had 275 bundles but more than 70 didn’t work. Well...okay I tried my best... okay...last month and few task later (nobody could tell me how that system really work)... and now it’s fourth month...this one is the last one... enough of this bullshit for me :/ I’m out. Next month will be better, new job new me. I lost 4 months of my life...
Did you have some sort of that situation in your career? How common it is? -
- "Two months" training upon hire, with all the other hires too.
- Entire thing takes place in a hotel's larger room meant for small conventions or whatever.
- Brought on as Java developers, told there was Java work for all of us
- By the end of it, there wasn't
- Sit at our company's office for a month doing nothing, waiting for work
- It's summer time, 90F+ heat, and the A/C not only wasn't on most of the time, when it was on it was actually heating the building instead of cooling
- Get on a project, join the client site, takes at least a week to get a laptop, takes a month to get most of the needed accesses
- Was brought on because they needed a SQL Developer, I do not know more than basic syntax which I told them
- Project is 3 months behind already
- Really no development since Offshore handles it (poorly)
- For the first year+ of my time here I am doing nothing but manual quality assurance testing, and no development
It's hard to leave when you aren't learning -
Today I was fighting a bug in php that resulted in a steady increase of the upload time of a picture. I printed it out together with some other like the amount of accesses on the image.
They where separated with <br> tags which were not displayed for some reason (maybe you already gueesed it here).
I ask my teacher to help me out, because the entry in my database was correct, the value I received was correct, but not the displayed value...
We even modified the database structure in order to find the bug, but it turns out the error was how I displayed the values. TIL that strings are not concatenated with a '+', but with a '.', the hard way.
Next problem: why is the access count incremented? Also why 3 times?😅 -
What's the point of the Gmail API if you can do all of its functions with IMAP or POP3 and not have to have user login oauth, just account and password?
I wanted to read a company email account for certain emails related to our tickets. No one actually accesses this account, and the tool is without a GUI. As such, I can't use the Gmail API. I just remembered there must be a more ordinary way to do this because how does Outlook and other email software work? So python import imaplib and I was done in a few minutes. -
OK, you sick fucks, tell me what WordPress plugin I should make next.
Rules: it needs to be a single-task kind of thing, because I want it done in less than a week and preferably under 200 loc because I have a life, so no gravity forms clones or ACF Better. Don't ask for me to do your homework either, asshole, so if you're suspiciously specific I'll set my dragons on you. Bonus points for weird and pointless.
I just released a plugin that accesses Fuck Off As A Service (www.foaas.com) through shortcodes, so hopefully that gives you an idea of the sort of attitude I approach this project with.
OK, go!15 -
Ugh trying to refactor a Node.js MUD codebase to use mongodb. It currently accesses/stores it's data in json files via synchronous FS operations. Callback and/or .then hell, here I come!undefined callback hell async mongo javascript async hell node asynchronous promises muds mongodb nodejs
