Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "ssl https"
-
When you're about to do a payment and the payment form is loaded without an SSL connection/certificate... Come on, it's 2017...
 3
3 -
One of our clients deploy their own server app. So this happened after a prod deployment. (4am)
*Cellphone rings while sleeping*
Client : we need you on the conference call now. URGENT!
*Gets on conference call*
*Client explain the problem*
*Explaining to the client that the problem is in their side (https connection not working, either network or certificate problem)*
*Client doesn't believe it and pushes me for a fix that I have no control on*
*4 hours later in a heated conversation*
Client : ok problem is on our side. We used our SSL certificate from staging with production and thought it would work.
Me : 3
3 -
Following a conversation with a fellow devRanter this came to my mind ago, happened a year or two ago I think.
Was searching for an online note taking app which also provided open source end to end encryption.
After searching for a while I found something that looked alright (do not remember the URL/site too badly). They used pretty good open source JS crypto libraries so it seemed very good!
Then I noticed that the site itself did NOT ran SSL (putting the https:// in front of the site name resulted in site not found or something similar).
Went to the Q/A section because that's really weird.
Saw the answer to that question:
"Since the notes are end to end encrypted client side anyways, we don't see the point in adding SSL. It's secure enough this way".
😵
I emailed them right away explaing that any party inbetween their server(s) and the browser could do anything with the request (includingt the cryptographic JS code) so they should start going onto SSL very very fast.
Too badly I never received a reply.
People, if you ever work with client side crypto, ALWAYS use SSL. Also with valid certs!
The NSA for example has this thing known as the 'Quantum Insert' attack which they can deploy worldwide which basically is an attack where they detect requests being made to servers and reply quickly with their own version of that code which is very probably backdoored.
This attack cannot be performed if you use SSL! (of course only if they don't have your private keys but lets assume that for now)
Luckily Fox-IT (formerly Dutch cyber security company) wrote a Snort (Intrustion Detection System) module for detecting this attack.
Anyways, Always use SSL if you do anything at all with crypto/sensitive data! Actually, always use it but at the very LEAST really do it when you process the mentioned above!31 -
I hate Wordpress. I hate Wordpress. I hate Wordpress.
Wordpress can take a big shit on itself and crawl into a deep dark hole far away from all that is good.
Who even uses Wordpress? Bloggers? Come on, let’s be honest, they’re using more intuitive sites like weebly, wix, and square space. So WHAT is Wordpress for? I’ll tell you, it’s just to FUCKING TORTURE PEOPLE.
So, being the “techy guy” of the family, a relative contacts me asking for some help with their website because they need to install an SSL certificate but they don’t know how to. I tell them I’d gladly do it because, sure, they’re family and how long can it possibly take to install a certificate? I’ve done it before!
Well, I get to work and log into the sluggish Wordpress dashboard and try to use a plugin that would issue a LetsEncrypt certificate because they are free and just as good as any other SSL. But one plugin after the next I keep getting errors about how my hosting wouldn’t allow it.
So I contact GoDaddy (don’t get me fucking started) and ask them about the issue. The guy tells me it’s “policy” to only be able to use GoDaddy’s certificates. How much do they cost? Oh, how about $100 a year?! Fuck you.
I figured out the only way to escape this hell was to ask them to open an economy Linux hosting account with cPanel on GoDaddy (the site was formerly hosted on a “Managed Wordpress” account which is just bullshit for not wanting to give you any control over your own goddamn content). So now I have to deal with migrating the site.
GoDaddy representative tells me that it should only take 20 minutes for me to do this (I’ve already spent way too much time on this but whatever) so I go forward with the new account. I decide I should migrate the site by exporting a backup and manually placing everything on the new server. Doesn’t it end up taking an entire hour to back up a 200MB site because GoDaddy throttled the processing speed?!
So, it’s another hour later and I’ve installed all the databases and carried over all the files. At this point, I’m really at the end of my rope and can’t wait to install the certificate and be done with this fuckery.
I install the certificate and finally get ready to be on my way, but then I see it. A warning. A warning from my browser telling me the site is only partially secure. It turns out the certificate was properly installed but whoever initially made the site HARDCODED ALL THE LINKS to images, websites, and style sheets to be http instead of https.
I’m gonna explode.
I swear, I’m gonna fucking explode.
After a total of 5 hours of work, I finally get the site secure by using search and replace on every fucking file.
Wordpress can go suck a big one. Actually, Wordpress can go suck the largest fuckin one in existence and choke on it.
TL;DR I agree to install an SSL certificate but end up with much more work than I bargained.34 -
SSL FYI for anyone using Thawte, VeriSign, Equifax, GeoTrust, and RapidSSL Certs, Chrome will distrust next year.
https://security.googleblog.com/201...8 -
First lecture of computer networks. Let's shove all of these abbreviations with their meaning, and possibly a associated port number in one 1.5 hour lecture:
HTTP, HTTPS, FTP, FTPS, SFTP, TCP, IP, UDP, ISP, DSL, DNS, LAN, WLAN, WDM, P2P, TELNET, PGP, TLS, SSL, SSH, MIME, SMTP, POP3, IMAP, IANA, DHT, RTT, DHCP
I really feel sorry for students who didn't have previous knowledge about this stuff..5 -
I'm a "published" freelance dev!
Last night I made my first web application available to the internet. It's an internal enterprise management system for a small non-profit.
It's running on a single $6 a month digitalocean droplet, and the domain is $12 a year, so yearly cost for them is absolutely rock bottom.
It's written in asp.net 6.0 razor pages, nginx reverse proxy, certbot for HTTPS certificates, fail2ban for ssh protection (ssh login is via ssl keys), entity framework with MySQL.
The site itself has automatic IP banning based on a few parameters like login spam, uses JWT tokens, and is fully secured.
All together, it's a lot of value for about $100 a year.11 -
About browsers and whole SSL CERT thing...
Most likely everyone here noticed, that https site with broken certificate will throw these big red warnings, in your face and there is so much wording like "ITS NOT SECUREEEE" or "ITS HACKEDDD" almost like it was written by passionate fanatic.
But when you are on plaintext http browsers reaction is like ¯\_(ツ)_/¯
Even if you have plaintext with password, it will for example in chromium put small little red thingy that almost no one notices.
I believe that broken cert with some error like invalid date is MORE secure than plaintext password, yet still there is this hypocracy with browsers...
I dont say that broken SSL cert is good, or something, Im just pointing out contrast of "broken" https vs plain http.... One looks for casual Joe like end of the world is coming and second is bearly noticable. Da fuck?
I disagree with this approach17 -
Right, I've been here before.
Our app requires an internet connection, and one of our clients wants to roll it out on a strictly managed network.
We told them which addresses our app communicates with and their network team opened them up for traffic. Should work, right?
Nope, doesn't work.
So I request them to use Fiddler to do some debugging of the network traffic, and lo and behold, it does work when Fiddler is active.
One important detail is that Fiddler uses it's own SSL certificate to debug HTTPS communications. I've had moments where expired certificates were the cause of things not working and running Fiddler "fixes" this because of their own certificate.
So I point this out in numerous mails to their network team, every time I get a response saying "nah, that can't be it".
I keep insisting "I have had this before, please check if any installed Root CA Certificates is expired"
At this point I'm certain they have updates turned off on these machines, and their certificates must not have been updated for a long time.
At one point they come back to me. "Hey, when Fiddler is off, WireShark shows the app communicating with ICMP calls, but when it's on it shows HTTP calls instead".
...YOU'RE THE SUPPOSED NETWORK EXPERTS?! You think data can be send via ICMP? Do you even know what ICMP is? Of course you'll see ICMP calls when the network is rejecting the packages instead of HTTP calls when everything's fine.
(ICMP is used to communicate errors)
I'm trying to keep my patience with these guys until they find exactly what's wrong because even I am somewhat grasping at straws right now. But things like this makes me doubt their expertise...6 -
Freak yeah!!! Just installed my first SSL Certificate on my Ubuntu Server!!!!! 🤘🏾🤘🏾🤘🏾🤘🏾🤘🏾 First time I had my IT friend do it. I thought about contacting him again, but then thought, what the hell, let's give 'er a shot. 2 days and a whole lot of anger and frustration later https:// is a green light!!! 😝😝😝😝😝😝😝14
-
"There's more to it"
This is something that has been bugging me for a long time now, so <rant>.
Yesterday in one of my chats in Telegram I had a question from someone wanting to make their laptop completely bulletproof privacy respecting, yada yada.. down to the MAC address being randomized. Now I am a networking guy.. or at least I like to think I am.
So I told him, routers must block any MAC addresses from leaking out. So the MAC address is only relevant inside of the network you're in. IPv6 changes this and there is network discovery involved with fandroids and cryphones where WiFi remains turned on as you leave the house (price of convenience amirite?) - but I'll get back to that later.
Now for a laptop MAC address randomization isn't exactly relevant yet I'd say.. at least in something other than Windows where your privacy is right out the window anyway. MAC randomization while Nadella does the whole assfuck, sign me up! /s
So let's assume Linux. No MAC randomization, not necessary, privacy respecting nonetheless. MAC addresses do not leak outside of the network in traditional IPv4 networking. So what would you be worried about inside the network? A hacker inside Starbucks? This is the question I asked him, and argued that if you don't trust the network (and with a public hotspot I personally don't) you shouldn't connect to it in the first place. And since I recall MAC randomization being discussed on the ISC's dhcp-users mailing list a few months ago (http://isc-dhcp-users.2343191.n4.nabble.com/...), I linked that in as well. These are the hardcore networking guys, on the forum of one of the granddaddies of the internet. They make BIND which pretty much everyone uses. It's the de facto standard DNS server out there.
The reply to all of this was simply to the "don't connect to it if you don't trust it" - I guess that's all the privacy nut could argue with. And here we get to the topic of this rant. The almighty rebuttal "there's more to it than that!1! HTTPS doesn't require trust anymore!1!"
... An encrypted connection to a website meaning that you could connect to just about any hostile network. Are you fucking retarded? Ever heard of SSL stripping? Yeah HSTS solves that but only a handful of websites use it and it doesn't scale up properly, since it's pretty much a hardcoded list in web browsers. And you know what? Yes "there's more to it"! There's more to networking than just web browsing. There's 65 THOUSAND ports available on both TCP and UDP, and there you go narrow your understanding of networking to just 2 of them - 80 and 443. Yes there's a lot more to it. But not exactly the kind of thing you're arguing about.
Enjoy your cheap-ass Xiaomeme phone where the "phone" part means phoning home to China, and raging about the Google apps on there. Then try to solve problems that aren't actually problems and pretty vital network components, just because it's an identifier.
</rant>
P.S. I do care a lot about privacy. My web and mail servers for example do not know where my visitors are coming from. All they see is some reverse proxies that they think is the whole internet. So yes I care about my own and others' privacy. But you know.. I'm old-fashioned. I like to solve problems with actual solutions.10 -
HTTPS requests in most languages:
Import a couple of libraries, you may need to install a few as well. It's possible that you will need to initialize and set up the socket. Be sure to specify SSL settings. Create the connection, provide it a URL, and attempt the connection. Read the response, usually in chunks. You may need to manually create a buffer of fixed size, depending on if the language has buffer helper classes or not. You will probably need to convert the input stream response to a string to do anything with it. Close the connection and clean up any buffers used.
HTTPS requests in Python:
import urllib
urllib.YEET()6 -
FUCK YOU YOU SHITTY COCK SUCKING BITCH MOTHERFUCKER.
GO DIE IN A HOLE THEN GET RAPED IN HELL. I REALLY HATE THIS SHIT.
FUCK OFF GOOGLE. 12
12 -
So my brother went back to school today. Now, during the 5 years I was there they had the most shit security on their IT systems, but aparently now they have fucked up their ssl. If you try to load the https page it comes up with the warning saying its an invalid certificate, but once you click it, it doesn't even load the school website, it loads this random page. Clicking on the buttons then take you to a page under their domain provided by another school. Going to this schools website, the https seems to be broken in the exact same way. It wouldnt be so bad, but it can confuse the hell out of people who type https before a url, and thos who dont realise and end up on the insecure site will need to provide passwords over an insecure connection. I am so glad im out of that place, they had such crap IT and everything was so easy to break.
 1
1 -
Since, I am already using Mullvad's vpn service, I also stumbled on https proxies.
Is it still safe to enter my devRant login data, when I would use a https proxy in FF's settings?
The Proxy is a free elite https proxy.
And devRant also uses SSL.
The traceroute would seem like this I guess.:
VPN(*le me sendin my password -> SSL Proxy -> SSL DevRant)
--------------------
Following that path, I would assume that it would be like this in detail:
HTTPS Request
-PW gets encrypted by VPN service
-" " " again " HTTPS Proxy
-" " " again " devRant itself9 -
FUCKING SOURCETREE!!!!!!! HOW THE FUCK DO U MANAGE TO BREAK YOURSELF MORE AND MORE...
Got a new PC so had to reinstall and apparently there's a new version, new UI/UX.... works ok... fine... :(
Now after some autoupdates the Bitbucket URL isn't recognized and I need to get a new repo....
I copy the URL (sourcetree://...) from the button but then ST complains some stupid HTTPS SSL cert error..... FUCK!!!
Tried IE, doesn't recognize the URL....
Last resort... I look at the URL itself...
hm.... points to a *.git file
Ok lets use git shell on another repo and get the remote address...
ssh://git@....
FUCK U!!!!!!!!!!!!!!!!!! HAD TO MANUALLY REVERSE ENGINEER AN SSH URL BECAUSE U CANT WORK WITH URSELF...9 -
Maaaan, we all knew it was coming, we were warned, again and again, yet still, when Lets Encrypt's old root CA expired today, we found out a tool we were using to get new certs (Not cerbot, custom wrapper around acme-tiny) included the old root in the chain.
So... A few hours ago, some of our servers started having connection issues.
Great final 3 hours of today. Better luck next time I guess? Still, despite the little hickup, Lets Encrypt still remains as one of the biggest revolutions in the adoption of SSL, they're the good guys.5 -
What makes free ssl "Unsuitable for e-commerce websites", Please read to end to see my view point.
From Namecheap:
Free Certificates are domain validation only which means they don't certify the identity of the website owner, they simply ensure a secure connection. Customers can't be sure of the integrity and trustworthiness of the website owner. If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer. It's important your customers trust your business is safe enough to hand over these details. To gain this trust, you need a certification of your authenticity, which you can only get with a (paid) Business Validation or Extended Validation SSL Certificates.
https://namecheap.com/security/...
* "To gain this trust, you need a certification of your authenticity"
~ But isn't that just Domain Verification and other Extras, What justifies somebody or business's authenticity? Tax Id, Valid Address, Nobody is going to study the ssl cert to make sure that amazon.com is a valid business and has a tax Id.
* "domain validation only which means they don't certify the identity of the website owner,"
~ Wouldn't this just be the domain validation test that is required when using services like LetsEncrypt using Certbot etc, or are we referencing back to this idea that they look for a Valid Tax Id sort of thing?
* "If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer"
~ Why is the paid version going to do double encryption, is the CA going to run a monitoring tool to scan for intrusions like a IDS or IPS? (disregard the use of DNS Validation being in the picture)
Am I missing something, this just seems like well crafted text to get people to buy a cert, I could understand if the encryption was handled differently, Maybe if they checked the site for HSTS or HTTPs Redirect or even, They blocked wildcard SSL before and now with the paid its included, but overall it doesn't sound like anything special. Now I'm not just picking on namecheap because domain.com does the same.14 -
Since last update (version 63) Google chrome forces all *.dev domains to use https. Guess who used a *.dev domain for his local development virtual machine and now have to switch to *.local ...
Removing the HSTS Rule from chrome seems not to be possible and surprisingly I could not use a self signed SSL certificate to make it working again.3 -
How do I make my blog https? I have a blog using Jekyll and GitHub pages. I have a custom domain so I tried cloudflare free SSL plan - destroyed my DNS records. Haha. Any good post for me to follow and get that green padlock?8
-
I made a wordpress website to one of my friends long time back as he wants to teach online and sell his videos. (he is studying MBBS)
Yesterday suddenly he calls me and says our site has been compromised and its not longer secure.
Me: After seeing screenshot, no actually site doesn't have ssl and in recent chrome updates http site is being flagged.
He: Okay, I saw video on youtube how to buy ssl.
Me: its not just installing the certs, all the links and images has to be on https so it will take sometime for me.
He: Today, Website is no longer opening please help after putting ssl as per the video...
Me: What the hell? Who asked you to do that? Are you nuts?
He:................. Sorry, 😐2 -
FINALLY got Chrome to accept my self signed ssl certificate on OSX!!!!
F*ck this has taken waaay to long....
For anyone seeking advice, look here:
https://alexanderzeitler.com/articl...9 -
Am I missing something here? Lets Encrypt auto renews SSL every 90 days....BUT it will fail if you have .htaccess re-direct set up to https. So you would have to switch off the https redirect, manually renew, then switch it back on again. Thats fucking crazy. I can’t find a way round this. The hosting co set this up but are encouraging people to buy one of theirs when the renewal fails. a cunning plot to get more of their own SSLs. Any ideas?6
-
Ok, so i got this new machine and whilst migrating I want to stay online with certain services. So atm there is x.web.nl and y.web.nl both have ssl and one runs on server x and the other on server y. Now is the question how the heck do i forward that ssl file??? I figured i have to do something with my nginx server block. Because that is terminating the cert. Can someone help me out??1
-
Ok can someone explain this to me, i cant get it to function properly on chrome. Others are fine...
 7
7 -
I've had my site up and working for a few months now (still need to finish building it properly the template project is still half default lol) but because I setup the Nginx server on a digital ocean droplet myself using both for the first time ever I obviously made some mistakes. It was up and running though just always spouting 'nginx[1755018]: nginx: [warn] conflicting server name "jessiejfoley.dev" on 0.0.0.0:443, ignored' whenever I 'nginx -t' or 'java.security.cert.CertificateException' on this server monitor app I have on my phone
But it was up and ssl seemed to be working so I ignored it
today I learned about https://sslshopper.com/ssl-checker...., which told me my intermediate certificates were not functioning properly, I was bored today and didn't wanna be too productive (else boss expects the progress I've made this week every week) and decided to finally go through and see about getting everything fixed properly starting by reinstalling the certs and double checking my commands.
2 hours later I still can't fix the cert errors so I decide to focus on the conflicting name error. Go through the nginx directory cleaning anything non essential or things I put there while trying to figure out how to get it up originally (learned as I was going lol bad practice I know, but it's just a practice site that'll eventually be a portfolio when I feel like making it properly and investing an adequate amount of time)
as soon as I get rid of jessiejfoley_dev.save.3 inside /etc/nginx/conf.d (my actual site is in sites-enabled) my server monitor app stops reporting the cert error and when I check the ssl checker everything is properly working now.
so the easiest problem to fix was actually the cause of all my problems. I'm and idiot and this shows I still have a LONG way to go to actually knowing what I'm doing at all.1 -
The concept and execution of inter-cluster SSL along with keystores, truststores, signing, and similar just clicked in my head today. I feel the burden of undiagnosable https errors just melt off my shoulders. Any other environment tips I should know for kubernetes?
-
So I guess this doesn't really fall under dev, more web and net admin, but here it goes.
I am trying frantically to migrate our (@Gerrymandered and I) website from a hosted solution with Namecheap to my new personal badass server, Vector. The issue is that I need to host multiple subdomains under one IP. I learned how to use apache2's VirtualHost feature, and eventually made them all work. But now we need to get our 3 year SSL Certs that we already paid for working. Try to get ssl pass through... Nope. Fine, just use the VHost then forward it unsecured to the local ip which only accepts connections from the Apache host. But wait! I want to access my ESXi config page remotely too! Good GOD it is a pain in the ass to get all of this working, but I somehow did. Evidence is at https://git.infiniit.co, which is hosted on the same network as the ESXi control panel. *Sigh of relief* now I can sleep right? 😥29 -
Dear facebook/instagram
When in sandbox mode, please dont require https redirects, my localhost server has no concept of what an SSL cert is, its sandbox for a reason.5 -
So after my webhost told me the reason my ssl was broke was due to an issue I had no control over i threw a fit any 12 year old would be proud of (im 22) bought a new domain name and ssl certificate. Created an account on digital ocean for the cheapest tier and got to work learning about nginx (just to learn my new thing for the day nothing against apache) real quick
Few hours later https://jessiejfoley.dev is working
No content yet. But no server side errors I cant fucking fix through a limited dashboard
Don't know if that counts as petty but I feel better now7 -
let rant: (Bool, Bool, String) -> Void = { (isRant, isDev, contents) in
print(contents)
}
rant(false, true, "
So, a year ago more or less, I set out to teach myself some server-side programming on the side.
Many (MANY) tutorials, Digital Ocean droplets created and destroyed, coffee mugs and FMLs later, I can say 'Hello World' from Node.js - built from source and not running as a sudoer - using express and forever on Ubuntu, behind another Ubuntu server running nginx - also built from source so to add headers-more and naxsi - using all sorts of goodies to enhance security and talking to each other via SSH. Oh, and taking to the world over HTTPS with a grade A on SSL Labs (I know this doesn't mean much to you. Yeah you, rolling your eyes over there. So why don't you just bugger off before even commenting? Haha)
Feels good man.
")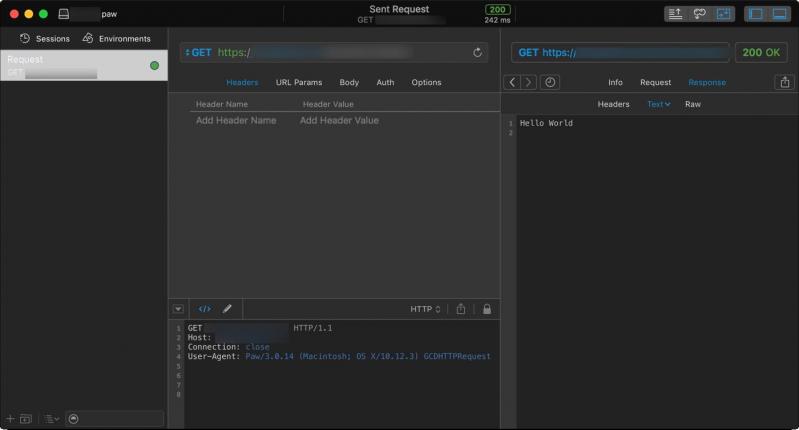 2
2 -
When you have a manager that gets the requirements for a super simple content page one month ago...
Then argues with some people about where it needs to go...
Then when it was decided two weeks ago that it needed to be a new publishing site insists on getting approval to deploy the new site even when I said hey I can have this guy set up publishing on our external server...
Gets approval anyway, now the deadline for it to be activated and working is tomorrow and because he is "a Wordpress developer" (by which he can install a theme) he thinks he knows how to fix Wordpress...
Because of the security at our company it needs to be over https and we are doing ssl offload from our publisher and Wordpress doesn't seem to like it or it is his jacked up Windows box running Wordpress? Wtf
Best of all he said "do you think we will meet the deadline". I said I don't think we have a choice, this will be used by a lot of people Saturday for a conference. OMG I was ready to scream...
Now today I need to setup a new cms on an external server and get it done by tomorrow morning, with content. FML -
So i just learned aws elastic beanstalk (EBS, ECS, ALB, EC2, Amplify, S3, RDS, SQS)
Essentially i learned how to operate with aws to deploy a full stack web application with custom backend i built, with security and jwt token, certificate manager, ssl/tls to set up https and redirect from http, and react/angular/nextjs on frontend
All with custom CI/CD pipelines docker and other devops shit
But i still feel like im missing on A Lot of stuff regarding aws. I havent worked with Fargate for example and dont know how it works or when to use it, but i heard other devs use it
Can someone list me a number of things i as a dev should know more regarding aws?3 -
So I'm building this environmental monitoring system for one of the Labs to monitor Temperature and Humidity. the "software" that comes as part of the package with these sensors is really just a website you host yourself if you don't choose the cloud option. No big deal really, (see my previous rant about getting windows server through SSC) I setup IIS and get the "software" registered get a couple sensors running looks good. However I don't like the error messages that popup because it's unsecured. do some reading and I find out that most browsers will give you a warning if your not using HTTPS even if it's for internal use only. OK we'll how hard can it be in implement encryption, turns out it's not that hard and you can do it for free how with letsencrypt and other places. I like free, now i have to use SSH to get into the server and run an ACME client. Hey open SSH is part of windows now cool, download an ACME client SSH into the server and nope doesn't work. Oh right I'm behind a corporate firewall and a bunch of other shit I can't control. Why is so damn arduous to setup this god dam internal website and the problems aren't even the site. Now I'm playing with AWS spinning up an instance to be able to try and get an SSL certificate just so i don't have to tell people it's OK to trust this site ignore the big angry warning.
Best part is other similar internal sites don;t use SSL and all have big messages about someone stealing your soul if you go there and these are commercial systems that run all the HVAC for all the campuses across Canada.
I need more Tylenol. -
!rant
I need to quickly test how my web app works on mobile
PROBLEM: some of my features require https. I can test from my pc on localhost just fine, since localhost works.
From Android, however, those features are blocked, since I reach my webapp with my IP address; it is not localhost so Chrome raises a middle finger when I try to access the camera from an unsecured website -and rightly so.
I really need to get these tests done, how am I supposed to do?
I install an SSL certificate on my pc?!?
I disable Chrome security checks on my Android?!? (is that even possible?)
I install bluestacks real quick and hope everything works fine?!?
Wwyd?4 -
I know it's all for good reason, but man are there so many hoops to jump through to get a web server set up through HTTPS. registering the domain, getting the SSL certs, configuring the DNS, setting up the firewall rules.. what a pain5
-
Was watching OITNB at home when boss called sounded urgent about SSL not working on one of our subdomains. We use a paid cloud app for some of our reports which. So the subdomain is a CNAME to the providers app subdomain. Recently there was an upgrade at our hosting but it shouldn't be related.
Boss: Hey, there is an error prompt when I visit our reporting site with https
Me: That's cos we never installed any SSL cert for that subdomain.
Boss: Well it worked before and you will need to get it fixed.
Me: Wait.. It worked before? How is that possible? We've never set it up and the subdomain is a CNAME pointing to another site which we don't own. The cert will have to load from their server and we have not done any setup with them.
Boss: I'm very sure it worked before the hosting upgrades. All along our customers has been accessing with https.
Me: Okay.... That's something new because and I am pretty SURE the last I checked, the app provider doesn't allow that yet.
* meanwhile I when to search the app provider docs and it says not able to support multiple SSL yet for CNAME
Me: Look, it says so here in the docs.
Boss: Ok, can you try to fix it as its important for the users to not see that error. It has been working all along.
Me: Hmmmm... I'll get back to you.
How do I fix something that didn't exist / broken?? How did it work before??
I know it can be possible to install the cert on the cloud provider end but we haven't done this before. And their support docs says feature not available yet.
Was it magic?? Am I missing something?? Anyway, I've sent an email to the provider's support team and telling them "it worked before" -
What is the use of https in local host? Do I really need to enforce it in local server even tho I'll add ssl cert after it gets deployed anyway! For example an express server in localhost .Does it need ssl in local server?8
-
I deployed a website and hosted it today. Also used a SSL certificate but now when I'm opening it on another device with its own data connection, it is not loading and showing error "This site can’t provide a secure connection".
But if my device is connected to wifi, the website is functioning normally. Can anybody help me out? My website - https://covid-india.live/4 -
Why the fuck does my subdomain work with https but my main domain returns an ssl error. Wouldnt nether work if the ssl was the issue
Its midnight I want to fucking sleep not deal with this shit. I'm probably doing something stupid but don't have the fucking experience to recognize what I'm doing wrong4 -
// Rant 1
---
Im literally laughing and crying rn
I tried to deploy a backend on aws Fargate for the first time. Never used Fargate until now
After several days of brainwreck of trial and error
After Fucking around to find out
After Multiple failures to deploy the backend app on AWS Fargate
After Multiple times of deleting the whole infrastructure and redoing everything again
After trying to create the infrastructure through terraform, where 60% of it has worked but the remaining parts have failed
After then scraping off terraform and doing everything manually via AWS ui dashboard because im that much desperate now and just want to see my fucking backend work on aws and i dont care how it will be done anymore
I have finally deployed the backend, successfully
I am yet unsure of what the fuck is going on. I followed an article. Basically i deployed the backend using:
- RDS
- ECS
- ECR
- VPC
- ALB
You may wonder am i fucking retarded to fail this hard for just deploying a backend to aws?
No. Its much deeper than you think. I deployed it on a real world production ready app way.
- VPC with 2 public and 2 private subnets. Private subnets used only for RDS. Public for ALB.
- Everything is very well done and secure. 3 security groups: 1 for ALB (port 80), 1 for Fargate (port 8080, the one the backend is running on), 1 for RDS postgres (port 5432). Each one stacked on top and chained
- custom domain name + SSL certificate so i can have a clean version of the fully working backend such as https://api.shitstain.com
- custom ECS cluster
- custom target groups
- task definitions
Etc.
Right now im unsure how all of this is glued together. I have no idea why this works and why my backend is secure and reachable. Well i do know to some extent but not everything.
To know everything, I'll now ask some dumbass questions:
1. What is ECS used for?
2. What is a task definition and why do i need it?
3. What does Fargate do exactly? As far as i understood its a on-demand use of a backend. Almost like serverless backend? Like i get billed only when the backend is used by someone?
4. What is a target group and why do i need it?
5. Ive read somewhere theres a difference between using Fargate and... ECS (or is it something else)? Whats the difference?
Everything else i understand well enough.
In the meantime I'll now start analyzing researching and understanding deeply what happened here and why this works. I'll also turn all of this in terraform. I'll also build a custom gitlab CI/CD to automate all of this shit and deploy to fargate prod app
// Rant 2
---
Im pissing and shitting a lot today. I piss so much and i only drink coffee. But the bigger problem is i can barely manage to hold my piss. It feels like i need to piss asap or im gonna piss myself. I used to be able to easily hold it for hours now i can barely do it for seconds. While i was sleeping with my gf @retoor i woke up by pissing on myself on her bed right next to her! the heavy warmness of my piss woke me up. It was so embarrassing. But she was hardcore sleeping and didnt notice. I immediately got out of bed to take a shower like a walking dead. I thought i was dreaming. I was half conscious and could barely see only to find out it wasnt a dream and i really did piss on myself in her bed! What the fuck! Whats next, to uncontrollably shit on her bed while sleeping?! Hopefully i didnt get some infection. I feel healthy. But maybe all of this is one giant dream im having and all of u are not real9 -
If anyone is looking for a great tutorial on getting started with a docker cluster check out https://dockerswarm.rocks/
I had a 4 node cluster up on Digital Ocean with Traefik + Lets Encrypt, Prometheus, Portainer, Grafana all that good stuff in under 2 hours. Not much longer to test a basic WP and Next Cloud container with full SSL. Neat stuff. Just burning through $100 credit for testing but it's been fun5 -
I was scrolling through my past rants and found this gem
https://devrant.com/rants/2305697/...
I posted it when images were not loading due to expired ssl. Looks like everyone who saw this got tricked!! -
Losing $27,300.50 to a cryptocurrency scam felt like a ruinous punch to the gut. One moment, I was finalizing what appeared to be a legitimate online purchase, a limited time opportunity endorsed by polished testimonials and a professional looking platform. The website boasted glowing reviews and featured a countdown timer that pressured users to act swiftly. It felt authentic, complete with an SSL certification, a sleek interface, and even a fabricated customer service chat. I transferred my life savings, convinced I had secured a rare investment. The next moment, my funds vanished into the digital abyss. The platform disappeared, replaced by a stark error message. My stomach plummeted. I had been ghosted. The scammers left no trace, only a hollow void where my money once resided. Shame engulfed me. How could I have been so gullible? For days, I spiraled into despair. Sleep eluded me as I fixated on screenshots of the scam site, dissecting every detail I had overlooked the slightly pixelated logo, the overly polished testimonials. The irreversible nature of cryptocurrency transactions taunted me; the anonymity of blockchain offered no solace. My hands trembled at the thought of starting over. But then, a friend intervened. Scammers thrive on silence,” she insisted, her voice resolute. “You must speak up for yourself and others.Reluctantly, I shared my story on Instagram, exposing the scam’s mechanics, the false urgency, the cloned platform. Vulnerability burned within me, but the response was astonishing. Hundreds replied, recounting identical nightmares. One message stood out: Contact PYRAMID HACK SOLUTION Website; https: // pyramidhacksolution. com They’re legitimate. Their website was clinical yet reassuring promising recovery with no upfront fees. Case studies detailed intricate crypto traces and frozen assets. I submitted my information, bracing for yet another potential scam. Instead, a specialist contacted me within hours. Their calm precision anchored me. “We’ll follow the money through layered wallets,” they explained. Scammers bounce crypto through dummy accounts, but patterns will emerge.The process was arduous. PYRAMID HACK SOLUTION collaborated with offshore exchanges, employing forensic tools to map transaction trails. They discovered my case was linked to a syndicate scamming hundreds. Each update chipped away at my despair. Three weeks later, a notification flashed: $27,300.50 reappeared, plus $850 from frozen scammer funds. I sobbed with relief. The specialist later revealed that my case helped dismantle part of the network. Today, I advocate for victims. The scars remain, but so does this truth: silence protects criminals. Speak up and fight back. Recovery is possible, together with Wizard web recovery , you can reclaim what was lost. WhatsApp; +44 741 428 09 142
-
9 Ways to Improve Your Website in 2020
Online customers are very picky these days. Plenty of quality sites and services tend to spoil them. Without leaving their homes, they can carefully probe your company and only then decide whether to deal with you or not. The first thing customers will look at is your website, so everything should be ideal there.
Not everyone succeeds in doing things perfectly well from the first try. For websites, this fact is particularly true. Besides, it is never too late to improve something and make it even better.
In this article, you will find the best recommendations on how to get a great website and win the hearts of online visitors.
Take care of security
It is unacceptable if customers who are looking for information or a product on your site find themselves infected with malware. Take measures to protect your site and visitors from new viruses, data breaches, and spam.
Take care of the SSL certificate. It should be monitored and updated if necessary.
Be sure to install all security updates for your CMS. A lot of sites get hacked through vulnerable plugins. Try to reduce their number and update regularly too.
Ride it quick
Webpage loading speed is what the visitor will notice right from the start. The war for milliseconds just begins. Speeding up a site is not so difficult. The first thing you can do is apply the old proven image compression. If that is not enough, work on caching or simplify your JavaScript and CSS code. Using CDN is another good advice.
Choose a quality hosting provider
In many respects, both the security and the speed of the website depend on your hosting provider. Do not get lost selecting the hosting provider. Other users share their experience with different providers on numerous discussion boards.
Content is king
Content is everything for the site. Content is blood, heart, brain, and soul of the website and it should be useful, interesting and concise. Selling texts are good, but do not chase only the number of clicks. An interesting article or useful instruction will increase customer loyalty, even if such content does not call to action.
Communication
Broadcasting should not be one-way. Make a convenient feedback form where your visitors do not have to fill out a million fields before sending a message. Do not forget about the phone, and what is even better, add online chat with a chatbot and\or live support reps.
Refrain from unpleasant surprises
Please mind, self-starting videos, especially with sound may irritate a lot of visitors and increase the bounce rate. The same is true about popups and sliders.
Next, do not be afraid of white space. Often site owners are literally obsessed with the desire to fill all the free space on the page with menus, banners and other stuff. Experiments with colors and fonts are rarely justified. Successful designs are usually brilliantly simple: white background + black text.
Mobile first
With such a dynamic pace of life, it is important to always keep up with trends, and the future belongs to mobile devices. We have already passed that line and mobile devices generate more traffic than desktop computers. This tendency will only increase, so adapt the layout and mind the mobile first and progressive advancement concepts.
Site navigation
Your visitors should be your priority. Use human-oriented terms and concepts to build navigation instead of search engine oriented phrases.
Do not let your visitors get stuck on your site. Always provide access to other pages, but be sure to mention which particular page will be opened so that the visitor understands exactly where and why he goes.
Technical audit
The site can be compared to a house - you always need to monitor the performance of all systems, and there is always a need to fix or improve something. Therefore, a technical audit of any project should be carried out regularly. It is always better if you are the first to notice the problem, and not your visitors or search engines.
As part of the audit, an analysis is carried out on such items as:
● Checking robots.txt / sitemap.xml files
● Checking duplicates and technical pages
● Checking the use of canonical URLs
● Monitoring 404 error page and redirects
There are many tools that help you monitor your website performance and run regular audits.
Conclusion
I hope these tips will help your site become even better. If you have questions or want to share useful lifehacks, feel free to comment below.
Resources:
https://networkworld.com/article/...
https://webopedia.com/TERM/C/...
https://searchenginewatch.com/2019/...
https://macsecurity.net/view/...

