Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "pin out"
-
Yesterday: Senior dev messages out a screenshot of someone using an extension method I wrote (he didn’t know I wrote it)..
SeniorDev: “OMG…that has to be the stupidest thing I ever saw.”
Me: “Stupid? Why?”
SeniorDev: “Why are they having to check the value from the database to see if it’s DBNull and if it is, return null. The database value is already null. So stupid.”
Me: “DBNull is not null, it has a value. When you call the .ToString, it returns an empty string.”
SeniorDev: ”No it doesn’t, it returns null.”
<oh no he didn’t….the smack down begins>
Me: “Really? Are you sure?”
SeniorDev: “Yes! And if the developer bothered to write any unit tests, he would have known.”
Me: “Unit tests? Why do you assume there aren’t any unit tests? Did you look?”
<at this moment, couple other devs take off their head phones and turn around>
SeniorDev:”Well…uh…I just assumed there aren’t because this is an obvious use case. If there was a test, it would have failed.”
Me: “Well, let’s take a look..”
<open up the test project…navigate to the specific use case>
Me: “Yep, there it is. DBNull.Value.ToString does not return a Null value.”
SeniorDev: “Huh? Must be a new feature of C#. Anyway, if the developers wrote their code correctly, they wouldn’t have to use those extension methods. It’s a mess.”
<trying really hard not drop the F-Bomb or two>
Me: “Couple of years ago the DBAs changed the data access standard so any nullable values would always default to null. So no empty strings, zeros, negative values to indicate a non-value. Downside was now the developers couldn’t assume the value returned the expected data type. What they ended up writing was a lot of code to check the value if it was DBNull. Lots of variations of ‘if …’ , ternary operators, some creative lamda expressions, which led to unexpected behavior in the user interface. Developers blamed the DBAs, DBAs blamed the developers. Remember, Tom and DBA-Sam almost got into a fist fight over it.”
SeniorDev: “Oh…yea…but that’s a management problem, not a programming problem.”
Me: “Probably, but since the developers starting using the extension methods, bug tickets related to mis-matched data has nearly disappeared. When was the last time you saw DBA-Sam complain about the developers?”
SeniorDev: “I guess not for a while, but it’s still no excuse.”
Me: “Excuse? Excuse for what?”
<couple of awkward seconds of silence>
SeniorDev: “Hey, did you guys see the video of the guy punching the kangaroo? It’s hilarious…here, check this out.. ”
Pin shoulders the mat…1 2 3….I win.6 -
Worst dev I've interviewed?
"Archie" ran his own consulting business for almost 20 years. Prior to his interview, Archie sent HR (to send to us) his company's website, where he had samples of code for us to review (which was not bad, this guy did know his stuff).
What I found odd was Archie was the lone wolf at his company, but everything I found about him (the about page, his bio, etc), Archie was referred to as 'Mr. Archie Brown'.
Ex. 'Mr. Archie Brown began his humble career and 'Mr. Archie Brown is active in his church and volunteers his time in many charities ...'
Odd to refer to yourself in the third person on your own site, but OK, I like putting hot sauce on my mac & cheese (no judgement here).
Then the interview..standard stuff, then..
Me: "Given your experience, this is an entry level developer position. Do you feel the work would be challenging enough for you?"
Archie: "Yes, Mr. Archie Brown would have no problem starting at bottom. You see ..."
Almost any time he would reference himself, instead of 'me' or 'I', he would say 'Mr. Archie Brown'. As the interview continued, the ego and self-importance grew and grew.
My interview partner wanted to be done by using the escape clause, "PaperTrail, I'm good, do you have any questions?"
Yes, yes I do. I was having too much fun listening to this guy ramble on about himself. I made the interview go the full hour with the majority of time 'Archie' telling us how great he is.
The icing on the cake was my partner caught his gold cuff-links and tie-pin where his initials and how he kept raising his hands and playing with his tie to show us (which I totally missed, then was like "oh yea, that was weird")
After the interview, talking with HR:
HR-Jake: "How did it go?"
John: "Terrible. One of the worst. We would have been done in 10 minutes if PaperTrail didn't keep asking questions."
Me: "Are you kidding!? I had the best time ever. I wish I could have stayed longer."
HR-Jake: "Really? This guy was so full of himself I wasn't sure to even schedule with you guys. With his experience, I thought it deserved at least a round with you two. You think we should give him a chance?"
Me: "Hell no. Never in a million years, no. I never in my whole life met anyone with such a big ego. I mean, he kept referring to himself in the third person. Who does that?"
HR-Jake: "Whew!...yea, he did that in the phone interview too. It was a red flag for us as well."
Couple of weeks later I ran into HR-Jake in the break room.
HR-Jake: "Remember Mr. Archie Brown?"
Me: "To my dying day, I will never forget Mr. Archie Brown."
HR-Jake: "I called him later that day to tell him the good news and he accused me of being a racist. If we didn't give him the job, he was getting a lawyer and sue us for discrimination."
Me: "What the frack!"
HR-Jake: "Yep, and guess what? Got a letter from his lawyer today. I don't think a case will come in front of a judge, but if you have any notes from the interview, I'll need them."
Me: "What are we going to do?"
HR-Jake: "Play the waiting game between lawyers. We're pretty sure he'll run out of money before we do."
After about 6 months, and a theft conviction (that story made the local paper), Mr. Archie Brooks dropped his case (or his lawyers did).23 -
So I have complained to our landlord about a noisy neighbor who keeps blasting shitty music at midnight, and technically its against the law as well, but this bitch ass joke of a human being ignored even the most highest of authority.
Seeing I can't solve it with democracy, I finally gave up with any reasonable type of way to restrain this motherfucker (even calling police didn't help) and went full asshole with him
I know his WiFi uses WPS PIN, but I'm not gonna throttle his network, I want to piss him off so much he'll regret living beside me, or at our place entirely.
So I performed a Evil Twin attack, I had my Raspberry Pi act as a both cloned AP and a deauther. Finally the plan came to effect.
I ran the deauther in his AP, effectively disconnecting his devices, and had the devices connect to the cloned network. The primary aim of my attack is to annoy this bitch ass to the point of no return. The project I used serves a website on the cloned AP like a update for his router. I intentionally made it run overnight, blasted Lo-fi hip hop and went to sleep. Before I dozed off, I can hear their scream of rage because they can't blast their music at full volume (waddaya guess, they use Spotify).
I finally woke up the next day, and I find neighbor complaining about me, and they were trying to tell the landlord I was hacking them. It's technically true but its not as bad as domestic disturbance for a full fucking week.
Landlord asked me if I did it, I declined, she believed me (I know she does because she knows I'm a pure soul unlike this mofo). Then he left frustrated, threatened to sue me for hacking.
I just smickered, he can't really prove anything unless I was being sloppy.
Nowadays I get good sleep and finally we live in a quite peaceful place now. Now you may ask, what happened to that guy? After he threatened me, the next night he found his things outside his own room, he was kicked out by the landlord.
Moral of the story: we ain't hating on your music taste but don't showcase it like its the most important thing in the world when everyone is sleeping. Case and point, don't be an asshole18 -
!dev
It was late night after work I went into Macdonald's take-away:
Me: Can I have a Maharaja Mac Medium Meal with extra regular fries?
Guy: Yes sir, that will XX.XX amt.
Me: Gives him my card.
Guys: So what's the pin?
Me: What??
Guys: The Pin sir.
Me: Are you ok? Who the hell shares a pin with you?
Guy: Sir, we don't have a wireless swipe machine.
Me: So why is it a take-away if I have to come inside and drop my pin anyways?
*Guy looks awkwardly at other employees. :/
I had to finally get out of the vehicle and I took another 15 mins seperately explaining him why cards have a security pin and that the word security isn't a joke before the pin. With this, I might have also slipped in some GDPR cookie policy along with it. and why Microsoft bought GitHub. Good Lad. He will learn.16 -
On the first class of cryptography professor says, "Hackers are people who dropped out of school, didn't obey their parents and turned to drugs and alcohol and steal money from people by hacking their facebook."
Then goes on to say, "People tend to keep their birthdate as their debit card's PIN so hacker checks their facebook account, finds their birthdate and goes to ATM machine and hacks their bank account."
I was speechless.7 -
Doot doot.
My day: Eight lines of refactoring around a 10-character fix for a minor production issue. Some tests. Lots of bloody phone calls and conference calls filled with me laughing and getting talked over. Why? Read on.
My boss's day: Trying very very hard to pin random shit on me (and failing because I'm awesome and fuck him). Six hours of drama and freaking out and chewing and yelling that the whole system is broken because of that minor issue. No reading, lots of misunderstanding, lots of panic. Three-way called me specifically to bitch out another coworker in front of me. (Coworker wasn't really in the wrong.) Called a contractor to his house for testing. Finally learned that everything works perfectly in QA (duh, I fixed it hours ago). Desperately waited for me to push to prod. Didn't care enough to do production tests afterwards.
My day afterwards: hey, this Cloudinary transform feature sounds fun! Oh look, I'm done already. Boo. Ask boss for update. Tests still aren't finished. Okay, whatever. Time for bed.
what a joke.
Oh, I talked to the accountant after all of this bullshit happened. Apparently everyone that has quit in the last six years has done so specifically because of the boss. Every. single. person.
I told him it was going to happen again.
I also told him the boss is a druggie with a taste for psychedelics. (It came up in conversation. Absolutely true, too.) It's hilarious because the company lawyer is the accountant's brother.
So stupid.18 -
I wonder why banks are always so terribly insecure, given how much money there's for grabs in there for hackers.
Just a while ago I got a new prepaid credit card from bpost, our local postal service that for some reason also does banking. The reason for that being that - thank you 'Murica! - a lot of websites out there don't accept anything but credit cards and PayPal. Because who in their right mind wouldn't use credit cards, right?! As it turns out, it's pretty much every European I've spoken to so far.
That aside, I got that card, all fine and dandy, it's part of the Mastercard network so at least I can get my purchases from those shitty American sites that don't accept anything else now. Looked into the manual of it because bpost's FAQ isn't very clear about what my login data for their online customer area now actually is. Not that their instruction manual was either.
I noticed in that manual that apparently the PIN code can't be changed (for "security reasons", totally not the alternative that probably they didn't want to implement it), and that requesting a forgotten PIN code can be done with as little as calling them up, and they'll then send the password - not a reset form, the password itself! IN THE FUCKING MAIL.
Because that's apparently how financial institutions manage their passwords. The fact that they know your password means that they're storing it in plain text, probably in a database with all the card numbers and CVC's next to it. Wouldn't that be a treasure trove for cybercriminals, I wonder? But YOU the customer can't change your password, because obviously YOU wouldn't be able to maintain a secure password, yet THEY are obviously the ones with all the security and should be the ones to take out of YOUR hands the responsibility to maintain YOUR OWN password.
Banking logic. I fucking love it.
As for their database.. I reckon that that's probably written in COBOL too. Because why wouldn't you.23 -
I have this little hobby project going on for a while now, and I thought it's worth sharing. Now at first blush this might seem like just another screenshot with neofetch.. but this thing has quite the story to tell. This laptop is no less than 17 years old.
So, a Compaq nx7010, a business laptop from 2004. It has had plenty of software and hardware mods alike. Let's start with the software.
It's running run-off-the-mill Debian 9, with a custom kernel. The reason why it's running that version of Debian is because of bugs in the network driver (ipw2200) in Debian 10, causing it to disconnect after a day or so. Less of an issue in Debian 9, and seemingly fixed by upgrading the kernel to a custom one. And the kernel is actually one of the things where you can save heaps of space when you do it yourself. The kernel package itself is 8.4MB for this one. The headers are 7.4MB. The stock kernels on the other hand (4.19 at downstream revisions 9, 10 and 13) took up a whole GB of space combined. That is how much I've been able to remove, even from headless systems. The stock kernels are incredibly bloated for what they are.
Other than that, most of the data storage is done through NFS over WiFi, which is actually faster than what is inside this laptop (a CF card which I will get to later).
Now let's talk hardware. And at age 17, you can imagine that it has seen quite a bit of maintenance there. The easiest mod is probably the flash mod. These old laptops use IDE for storage rather than SATA. Now the nice thing about IDE is that it actually lives on to this very day, in CF cards. The pinout is exactly the same. So you can use passive IDE-CF adapters and plug in a CF card. Easy!
The next thing I want to talk about is the battery. And um.. why that one is a bad idea to mod. Finding replacements for such old hardware.. good luck with that. So your other option is something called recelling, where you disassemble the battery and, well, replace the cells. The problem is that those battery packs are built like tanks and the disassembly will likely result in a broken battery housing (which you'll still need). Also the controllers inside those battery packs are either too smart or too stupid to play nicely with new cells. On that laptop at least, the new cells still had a perceived capacity of the old ones, while obviously the voltage on the cells themselves didn't change at all. The laptop thought the batteries were done for, despite still being chock full of juice. Then I tried to recalibrate them in the BIOS and fried the battery controller. Do not try to recell the battery, unless you have a spare already. The controllers and battery housings are complete and utter dogshit.
Next up is the display backlight. Originally this laptop used to use a CCFL backlight, which is a tiny tube that is driven at around 2000 volts. To its controller go either 7, 6, 4 or 3 wires, which are all related and I will get to. Signs of it dying are redshift, and eventually it going out until you close the lid and open it up again. The reason for it is that the voltage required to keep that CCFL "excited" rises over time, beyond what the controller can do.
So, 7-pin configuration is 2x VCC (12V), 2x enable (on or off), 1x adjust (analog brightness), and 2x ground. 6-pin gets rid of 1 enable line. Those are the configurations you'll find in CCFL. Then came LED lighting which required much less power to run. So the 4-pin configuration gets rid of a VCC and a ground line. And finally you have the 3-pin configuration which gets rid of the adjust line, and you can just short it to the enable line.
There are some other mods but I'm running out of characters. Why am I telling you all this? The reason is that this laptop doesn't feel any different to use than the ThinkPad x220 and IdeaPad Y700 I have on my desk (with 6c12t, 32G of RAM, ~1TB of SSDs and 2TB HDDs). A hefty setup compared to a very dated one, yet they feel the same. It can do web browsing, I can chat on Telegram with it, and I can do programming on it. So, if you're looking for a hobby project, maybe some kind of restrictions on your hardware to spark that creativity that makes code better, I can highly recommend it. I think I'm almost done with this project, and it was heaps of fun :D 11
11 -
> Customer logs Jira ticket claiming app is not working
< I restart the app, investigate and explain tht their server has issues
ø Client closes the ticket as Resolved
-- a couple of days pass by ---
> Customer logs Jira ticket claiming app is not working
< I restart the app, investigate and explain tht their server has issues
ø Client closes the ticket as Resolved
-- a couple of days pass by ---
> Customer logs Jira ticket claiming app is not working
< I restart the app, investigate and explain tht their server has issues
ø Client closes the ticket as Resolved
-- a couple of days pass by ---
<...>
< I log a JIRA ticket explaining what and how is wrong with the server with suggestions how to fix the problem so the app will not crash any longer (client own the server, has his own sysadmins -- I don't even had permissions to open syslog.. had to hack dmesg on their PROD server to pin-point the issue)
> no reaction from customer for weeks. I ping the ticket
× app crashes again
> no reaction from customer for weeks. I ping the ticket
> customer leaves a comment that their sysadmins are looking at it trying to figure out what might be wrong (ignoring what I wrote in ticket's description??? srsly?)
× app crashes again
< I post detail investigation details: snips from logs, screenshots, everything with crystal clear explanations.
> no reaction for weeks
......
well that's fun..6 -
Okay so my weekend project went well :D put my retropie system inside of this old r2d2 I've had collecting dust. Has a cooling fan inside as well as a 16x2 lcd I was playing with. Got a red led tied to the rpis txd pin, ports in the front for easy access and power cord and hdmi coming out the back.
 1
1 -
fucking hostgator!
go suck a cock you developers!
everything from their payment system to their support is crap.
a few days ago, i purchased a website from hostgator, with a year of hosting during black friday weekend. i had obtained a black friday coupon code that entitled me to roughly $160 off its usual price. that said, i filled out the registration form and clicked the 'checkout' button.
right after i clicked it, i saw i forgot to put in the coupon code, and pressed the back button on my browser. then i put in the code and proceeded with checkout.
guess what?
those MOTHERFUCKING GREEDY ASS BITCHES charged me TWICE, one with the coupon and one without.
i contacted customer support and told them what happened after waiting about double the time i was supposed to be connected to support.
of course, they asked for my fucking "security" pin over the customer support live chat (totally not ironic).
they sent a confirmation email, and cancelled the payment without the coupon.
then ONE FUCKING DAY LATER, I tried to connect to my website.
MY SITE WAS FUCKING SUSPENDED.
die in a hole.
i contacted customer support once more, and after explaining the story, I had to wait four to eight hours.
i'll see how it turns out tomorrow.
die in a hole hostgator🖕 12
12 -
!dev but still rant
So I'm a photocopier technician by day, alcoholic coder by night. Just spent 3 fucking hours trying to diagnose a black line on print outs, checked drums, dev units, toner cartridges, fusing unit, everything...
Called up one of the guys I work with and they said to come back with some samples to try and pin it down...
I turn around to leave and remember I didn't check the transfer belt and lo and behold it isn't cleaning and is smearing the paper...
3 fucking hours to work out such a simple error, I've had program breaking bugs diagnosed and fixed by then... ugh -.- -
I absolutely hate software that throws error message boxes that look identical to their "please enter new password" message box.
User called and said they needed their password reset. I give them a temp pin and tell them to press ok to the prompt and then put new password in. She says it is still saying invalid pin. This goes on for 10 minutes. I hang up and try on my laptop. Works fine. Then it hits me.
The message boxes look the same. Have the same width and height and shitty little yellow triangle with ! In the middle. The only difference between them is the text in size 9 font.
Gotta read people...cause sometimes the people developing your software assume you can. And to all the software people out there....end users don't want to fucking read.4 -
This morning there was this window cleaner again, that actually made me remember a rant from the old box - my previous account. Repost of that coming in an hour or so :3
Turns out that he came in the morning, and I completely forgot about it. The only appointment that I had today got canceled so I was like, eh fuck it. There's been this family event yesterday that made me so fucking tired... I'll just stay in bed for a little while longer.
Apparently that window cleaner ringed my bell multiple times, haven't heard him do it but anyway.. he and the cleaning lady had the genius idea to ask my landlord whether they can just barge in my home. Way to start the day, isn't it? I thought there were burglars.
In my bathrobe and visibly pissed off (I am NOT a morning person!), I let him do the window cleaning and waited for them to get the fuck out already. Then that cleaning lady, the fucking bitch that called my landlord to break into my home without MY prior permission!!! While the window cleaner was doing his work, she proceeds to ask me this.
Cleaning lady: "I had this technical issue earlier, and since you are good with phones I thought I'd ask you."
Me (thinking): oh, here it comes.. *rolling eyes*
M: "What's the issue?"
CL: "Well my stepson has an iPhone, which he broke and we brought it to a smartphone repair shop. They repaired it twice but an hour after receipt of the fixed phone, it breaks again."
M (t): You went wrong at iPhone, and you went wrong at visiting that incompetent mofo "teknishan" twice.
M: "Well I have no experience whatsoever with iPhones, but continue."
CL: "Well, he replaced the motherboard, and some pin at the bottom.."
M (t): The fucking motherboard of all things. The whole fucking motherboard?! The last thing that I'd look at, he just replaces like that?! Fucking piece of shit. That's even worse than Apple stores. And what's up with that goddamn pin? CAN'T YOU POSSIBLY BE A BIT MORE SPECIFIC?!
M: "Given only this information, I have no idea what's wrong with it."
CL: "But you are good with these things, aren't you?!"
M: "I disassemble my own broken phones, and dick around with their motherboards. That, while I'm fully aware that in the process I can break it beyond repair. That does not make me an expert on every phone out there."
CL: …
Well what did you even expect, fucking bitch. You barge into my home, don't even have the dignity to leave for me to be able to shower and dress myself, and then you go ask shit like that? Go suck my fucking cock, and shove that iPaperweight down your ass!! How about that?!9 -
My friend, Gavin, an air steward (a job that he had done for decades), told me about an incident at work. He said that (shockingly to me) passengers occasionally die on a flight (particularly long-haul), just as a matter of course. This can be because people sometimes travel to visit loved ones BECAUSE they are dying, people sometimes find travelling itself stressful (so it can exacerbate an existing medical condition), or simply that, if you took a large number of people and shut them up in a space together for some considerable time, some of them would pop off through sheer statistical probability. Cabin crew are, apparently, fully trained to deal within this eventually in a calm, almost routine manner.
This particular flight, Gavin was working with another gay man: Peter, who was actually a VERY funny personality. Camp, extravagant and loud, Peter really lit up the place. But naturally, when the very elderly male passenger in seat 38b died peacefully in his sleep halfway across the Atlantic, Peter acted (like the entire crew), with decorum and dignity. As per the protocol, all the lights in the cabin were dimmed. A hush fell over the passengers (Gavin told me that, although no announcement is ever made, the other passengers nearly always instinctively know what's happened, with the news spreading via the media of hushed whispers and nudges). Then, as per standing instructions, two of the crew carefully lifted the deceased out of his seat and gently carried him to the crew station where he was laid down on a bed for the remainder of the flight.
After the late gentleman disappeared behind the discreetly drawn curtain, you could have heard a pin drop. There was a demure pause during which, slowly, the lights went back up.
Suddenly Peter's cheery face appeared, poking through the gap in the drapes. He looked around, blinking brightly with curiosity at the seated passengers, and said, in a voice that echoed around the whole cabin:
"SO! Anyone else have the fish?"
He narrowly avoided getting sacked.8 -
An intern came to us with a build issue, it was very difficult to pin point the cause of issue as there were many modified files in the project. So to figure out the cause one guy git stashed lot of fiiles. Now, intern being not aware of the git stash command thought that all his changes are deleted. The way he freaked out thinking all his changes were lost was amazing. Also other people jumped on the bandwagon, and started questioning the developer that how can you delete the changes of an intern. It went like this for 10 min and finally we told the intern that his changes are safe.2
-
Mac: If you try to shoot yourself in the foot, you find out the OS has removed the firing pin from the gun.
Windows: If you try to shoot yourself in the foot, the OS will wrestle you to the ground. You may shoot yourself in the foot, you may shoot yourself in the gut, you may not shoot yourself at all, but they do try.
Linux: If you try and shoot your self in the foot, the OS would like to politely remind you we have *much* bigger guns available - try one if these!4 -
>Gets a new CPU for desktop (yay, went from R5 1600 to R5 3600X)
>Spends half a day flashing new MB BIOS (Needed to flash individual major versions in order, couldn't just go 1.10 to 6.40)
>Finally finishes preparations and goes to replace the CPU
>Cleans the old one and packages it to give it to a friend
>Has issues inserting the new one as the orientation arrow on the motherboard was very hard to make out
>Spends 30 minutes applying thermal paste, worrying about optimal spread
>Forgets which side the CPU fan goes on
>Finally boots back up... CPU fan is suddenly loud AF under load, but eh, temps under stress are sub-60, so, good
~~Next day~~
>Loud CPU fan is too annoying, opens the case again
>CPU fan is on backwards
Ugh
>Takes the fan off, turns it around and fastens again, puts PC back together and boots
>Is quiet again, nice
>Goes to work on the PC
>2 hours later randomly checks temps because no fan noise is weird
>CPU at 75dC, crap
>Opens the (live) PC, CPU fan is not spinning
>Has put the header on one pin to a side
>Unplugs and replugs it correctly
>Fan suddenly starts spinning very fast and cuts my finger
>Finally closes the case once more. All issues resolved
...Its situations like these that make me wonder... What would happen it I had to work with servers in person, physically lol5 -
Area of focus: Native iOS dev
Why: Spent years trying hybrid tools, dealing with the most ridiculous errors, bugs and issues you can begin to comprehend and then ... something magical happened. I got a book on Objective-c, learned a little, tried a simple app ... and it worked ... like properly worked, and on all the devices without taking half the RAM.
I'll say that again as I don't think it landed. In Objective-c, I got no issues where only the CEO's phone + OS version meant I couldn't load a map and a pin (looking at you titanium!!!)
In Objective-c, I wasn't promised storyboards and autolayout, only to find out they are completely different, and may god help you trying to google the issues, as the only ones to show up would be the native tools (looking at you Xamarin)
In Objective-c, my app doesn't instantly consume 125mb of RAM to load a fucking webview (looking at you ... well nearly every other hybrid tool)
... it just works. Then Swift came along and things only got better.13 -
We should not tolerate censorship.
Beyond all the u.s. hype over elections
(and the division in the west in general), the real story is all the censorship on both sides.
Reasonable voices are quickly banned, while violent voices and loud angry people are amplified.
I broke out of the left-right illusion when
I realized what this was all about. Why
so much fighting in the street was allowed, both
justified and unjustified. Why so much hate
and division and slander, and back and forth
was allowed to be spread.
It's problem, reaction, solution.
The old order of liberal democracy, represented
in the u.s. by the facade of the GOP and DNC,
doesn't know how to handle the free *distributed*
flow of information.
That free-flow of information has caused us to
transition to a *participatory* democracy, where
*networks* are the lever of power, rather than
top down institutions.
Consequently, the power in the *new era* is
to decide, not what the *narrative* is, but
who can even *participate*, in spreading,
ideating, and sharing their opinions on that
narrative, and more broadly, who is even allowed
to participate in society itself.
The u.s. and west wants the chinese model of
control in america. you are part of a network, a
collective, through services and software, and
you can be shut off from *society* itself at
the drop of a pin.
The only way they get that is by creating a crisis,
outright fighting in the streets. Thats why
people keep being released after committing serious
fucking crimes. It's why the DOJ and FBI are
intent on letting both sides people walk.
They want them at each others literal throat,
calling for each other's blood. All so they
can step back and then step in the middle when
the chorus for change cries out loud enough.
And the answer will be
1. regulated tech
2. an end to television media as we know it
3. the ability to shut someone off from any service on a dime
4. new hatespeech laws that will bite *all* sides in the ass.
5. the ability to shape the narrative of society by simply 'pruning' networks as they see fit, limiting the reach of individuals on all sides, who are problematic to
the collective direction.
I was so caught up in the illusion of us-vs-them I didn't
see it before now. This is a monstrous power grab.
And instead of focusing on a farce of election, where the party *organizations* involved are institutional facades for industrialists, we should be focusing on the real issue:
* Failure of law to do its job online, especially failures of slander and libel laws, failures of laws against conspiracy to commit crime or assault
* New laws that offer injunctive relief against censorship, now that tech really is the commons. Because whats worse than someone online whipping up a mob on either side, is
someone who is innocent being *silenced* for disagreeing with something someone in authority said, or for questioning a politician, party, or corporation.
* Very serious felony level laws against doxxing and harassment on all sides, with retroactive application of said laws because theres a lot of people on all sides who won't be satisfied with the outcome until people who are guilty are brought to justice.16 -
*places an order on OnePlus' website for that OP6T*
Alright, payment.. with my bpaid card that I ranted about earlier, because apparently the fuckers accept only credit cards. External payment portal, card's got a chip.. well that's gotta be the same payment process as the usual Bancontact purchases then, right? Where you plug your card into your Digipass card reader, get a start code from the website, type that in, amount to be paid, PIN code, and then it spits out another code that you give to the payment portal.
Except it isn't. That CVC thing is apparently the only thing that stands between you using your card and someone else doing the same with your card information. Not even the card itself! Why the FUCK do we even have PIN codes then?! This is even worse than the magstripe and the skimming issues related to it (the magstripe essentially just blurts out your card information to whatever wants to have it, so demagnetize it and don't use the payment terminals who refuse your card on grounds of not being able to read the magstripe afterwards. Your chip should be responsible for that.. but I digress). Credit cards with chips in it that aren't even used. That's what you Americans use? Seriously?!
At this rate, you can keep your fucking credit cards.10 -
need advice on integrating .t3d file support in c++ engine
hey, been stuck trying to figure out how to get .t3d file support working in our custom game engine, which is all written in c++. it's turning out to be a lot trickier than expected and i'm kinda hitting a wall here. the documentation on .t3d itself is pretty much nonexistent and what's out there is either outdated or too vague to be of any real use. i've tried a few things based on general file parsing logic in c++ but keep running into issues with either reading the files correctly or integrating the data into the engine in a way that actually works. it feels like i'm missing something fundamental but can't pin down what it is. has anyone here gone through this process before or has any experience with .t3d files? i could really use some advice on how to approach this, or even just some resources that explain the format in detail. also, if there are any common pitfalls or things to watch out for when adding new file format support to a game engine, i'd appreciate the heads up. thanks in advance for any help, feeling pretty stuck and any guidance would be a huge help.11 -
Customer requested the implementation of a "Master PIN" Code for accessing their appliances, to be used by field technicians when the users forgot their PIN.
Actually they could also read or reset it via USB using the config utility, but then again it's much more convenient not having to carry a laptop all the time...
Our only contact person at that company - the guy we got all the requirements from, let's call him Mr. L - wouldn't talk only positive about the company and managers, but we never worried as the project was making good progress.
In the final phase of the project, Mr. L was often hard to reach, always seemed to be busy even when we just needed a prototype approved to start production.
He always claimed to be waiting for approval from his supervisors and engineers, still discussing minor things with them.
When he left the company about three months later, it turned out he was pretty much the only person knowing about the details of the project, and his successor would start asking us very basic questions about the appliance,
wondering why we had implemented certain things the way they were.
(Well, how about we implemented everything just as requested by a former co-worker of yours?!)
Somewhere in the preliminary specs previously exchanged with Mr. L, there is even a hint of a "Master PIN", but the value is never specified anywhere on paper.
Today, we are not sure if anyone except for him even knew about it.
Maybe we should ask them whether they are now selling a product that has a 4-digit backdoor PIN nobody at the company is aware of?
Obviously, it is the birth year of Mr. L.1 -
We have a long standing, transient, occasional error in our system that we haven't quite been able to (or have had the time to) pin down.
I was thinking out loud with our project lead what the cause could be, which - before I realized it - segwayed seamlessy into me being tasked with hotfixing it in order to unblock some other tasks that people expect to start working on tomorrow.
I think I'm starting to see why people use inanimate objects for rubber ducking instead of other devs. Here's hoping my theory checks out.2 -
So our new hardware guy who is being managed by our lead embedded developer had the task of designing me an expansion board for my Linux board. The Linux board uses the 40 pin expansion like the raspberry, bananna and orange pi family and as you all know there are many different types of expansion boards for this.
I said at the start come to me and tell me what you want to connect to before deciding which pin you connect to so it is less work for me with Linux board configs and drivers.............
No no no we will sort it all... erm.....
So today they come ask me if they can use an SPI port for GPIO and I am like erm... why there is plenty of GPIO...
It turns out they have been designing the board based on the pin outs of an expansion board and not the actual connector of the Linux board.. I mean seriously WTF!1 -
The Turbografx 16 (or Turbografx PC-Engine in Japan) has the most amazing fucking expansion port I've ever seen. Every bus is exposed, plus sound out and IN (unused by anything ever made for the thing), composite out (not included on the console itself, but 3rd-party addons allowed it), VGA out (!!!) and CPU HALTING/CLOCK CONTROL were included over this fucking thing.
You can even power the system with 5v in through the expansion port and bypass the power switch with it.
Info and diagram:
https://gamesx.com/misctech/...
Example:
To get composite out, send pin A22 out and ground the ground wire of the composite to any ground.
For VGA, it's a little more complex:
VGA1 to TG-A23, VGA2 to TG-B23, VGA3 to TG-C23, VGA9 to TG-A2, VGA13 (and VGA10 if you want compatibility with older displays) to TG-B11, VGA14 to TG-A10, VGA5-8 (and 10 if not hooked to TG-B11) to TG-C2
(VGA numbering from Wikipedia diagram)
this thing's fucking coolrant holy fuck this is cool turbografx 16 expansion port heaven expansion port console mod turbografx pc-engine1 -
So, I got an iFixIt toolkit with a gift card from xmas. Was excited to tear into my iPhone6 given that it had lasted me a long time, and not that long ago, I had the screen repaired given I didn't know how to at the time and was working stupid long hours. I haven't used the phone in about 6 months now.
Wtf.
I open the device, and immediately 2 screws and a bracket fall out of the device. The inside is filthy, and appears to have corrosion (despite the fact I've never gotten water on it, I was kinda anal with that phone).
Whoever the guy was who "fixed" my screen apparently did so in a way that involved spilling something on my phone, over torquing a screw, breaking a bracket, and the entire thing looks sketch.
All while charging over $100. I can see why he insisted on having an otterbox on the phone now, he fucked up and was worried the one screw pin wouldn't hold the screen on. Motherfucking asshole.1 -
I am in love.
I am in love with all the guys and girls working at Microchip support.
I am the kind of user that does not really understand what he's doing/what he wants to do, so I am constantly stuck in stupid configuration errors or looking for impossible solutions, yes I am THAT kind of a user...
Here is a PWM working, a support guy spent some minutes telling me that I have to connect to the right pin.
Ok, he had to tell me twice.😳
Thank you, it may have taken me days to find out this.
They does not know, but there is a HUGE amount of decreasing dumb question incoming 😈
Please be kind with me, and don't get mad when things will get serious, I will probably bring hell in your office, I am very sorry for that...
Still, thank you for helping the dumbest learner-by-mistake that doesn't know how to recognize a mistake.
I can't write this in the ticket system, I hope someone of you use devRant! (atsame54 office, I am talking with you!)
You are my stack overflow, and the project I will develop with your help is quite the only thing left before my graduate.
I will owe you so much beers, love you guys!!!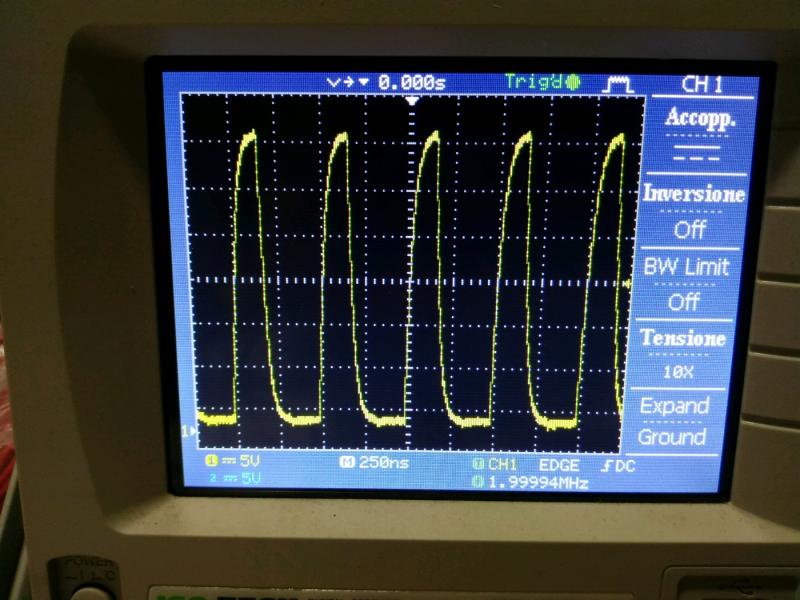
-
A bit late but I just remembered this story.. at my college the people in the IT department always watch for when another professor or student leaves their computer unlocked and then change their wallpaper to something funny (e.g. my little pony). One time the instructor from the class before mine left their machine logged in and my professor asked the class "what should we do?"
I suggested he modify the chrome shortcut on the desktop and change the path to 'C:\windows\system32\cmd.exe /c shutdown /r /t 0' then pin it to the taskbar. And he did it.
I wasn't in that class but I heard that she clicked it 3 times before she figured out what was going on. She never fixed it the whole rest of the quarter (simply launching chrome from the start menu) and would occasionally forget and click the taskbar icon and go through the whole thing again.
As fate would have it I got 2 classes with that instructor the next quarter. We're friends so it's all good but I still get flack about it and I don't dare leave my computer unlocked xD -
A conversation that i had with my co-worker today. I was having trouble getting into UAT to troubleshoot.
me
i lost access to UAT again
co-worker
F. So secure we can't even get in
me:
lol
co-worker:
I'll email whoever we did last
me:
i can get through the first phase(where you enter pin+rsa)
it denies me access after that
says bad username or password
co-worker:
Oh ok. Prolly just need to reset your pwd then. I'll find the email for helpdesk and fwd.
At least ur RSA works.
me:
yeah what a joy
co-worker:
If it's locked you may need to try from a Windows box. Horizon is bugged on Mac where the submit button stays disabled even when you type a pwd.
me:
i couldnt contain my happiness that my RSA worked
😃
co-worker:
Yeah it's exhilarating
Whenever I pick up my rsa token my life re-finds it's purpose and I feel like I'm meddling through a field of sunflowers.
I once tried to get my RSA token tattooed but it switched too quick.
me:
lol its faster that Usain Bolt
co worker:
Russia got kicked out because of their RSA tokens -
I was tasked to evaluate wherever a customer could use an implementation of OTRS ( https://otrs.com/ )
Is it just me or is there no information on this site apart from <OTRS> will make your life better! <OTRS> will cure AIDS! <OTRS> will end world hunger!
This site is trying to use its fucking product name in every god damn sentence. <OTRS>. Everytime <OTRS> is mentioned it is fucking bold printed! My eyes are bleeding within 2 minutes of visiting this site.
I can't get any information about what excatly it is apart from their catchphrase: OTRS (again, bold. I'll refrain from putting it in <> from now, i think you got the point) is a customizable support desk software that manages workflows and structures communication so there are no limits to what your service team can achieve.
So, it's a support desk software you can customize. Great. What does it do?
"Whether you deal with thousands of inquiries and incidents daily [...] you’ll need digital structures that integrate standardized processes
and make communication transparent between teams and departments,
as well as for external customers."
Great, but what does it do?
"Reduce costs and improve satisfaction by structuring customer service communication with OTRS."
Great, BUT WHAT DOES IT DO?
"Manage incidents simply and uncover the data needed to make forward-thinking strategy decisions. OTRS is an ITSM solution that scales and adapts to your changing business needs."
W H A T D O E S I T D O ?!
Okay fuck that, maybe the product page has something to say.
Hm... A link on the bottom of the page says it is a feature list ( https://otrs.com/product-otrs/... )
Ah great, so i got a rough idea about what it is. Our customer wants a blackboard solution with a window you can pin to your desktop and also has a basic level of access control.
So it seems to be way to overloaded on features to recommend it to them. Well, let's see if can at least do everything they want. So i need screenshots of the application. Does the site show any of them? I dare you to find out.
Spoiler: It does not. FFS. The only pictures they show you are fucking mock ups and the rest is stock photos.
Alright, onwards to Google Images then.
Ah, so it's a ticket system then. Great, the site did not really communicate that at all.
Awesome, that's not what i wanted at all. That's not even what the customer wanted at all! Who fucking thought that OTRS was a good idea for them!
Fuck!5 -
I believe someone was posting his accidental creation about C/C++ Web Framework in devrant sometime ago. I was lost, forget to pinned it and curious, anyone can pin me out?15
-
Textexpander. Ggpu = git push upstream, gg. = git add ., and ggc = git commit -m "" ... I love that I don't have to type out my whole damn name, username, email and work email all the time. Just expanding my email address is enough of a win for me with that tool. Also Alfred + utf symbol workflow. And newest addition - vimium to easily pin tabs.2
-
!rant
I have about a week of holidays left before my classes start and I'm thinking about creating a notepad with password protection and cloud sync so it can be accesed on other devices.
So this is how it will work.
Probably the same interface as windows notepad so no one notices. It can be used to write a personal diary or anything that you don't want other people to know. It will ask for a 4 digit code when you open it(at first you'll see some text, you'll just enter you pin after that text and without pressing enter if you pin is write you'll see the text changes to your previously saved text and if your pin is wrong no error will be displayed itll work as a normal text editor for intruders and probably this wrong pin will be sent to you on you emil with other info). Now even if yoy minimize the window you'll have enter the pin again or even your windows gets out of focus. So you can have it open all the with out worrying.
I'll be using C# for this which I have no experience with. But I'll get it so no problem here.
Provide your feedback on this with some suggestions.
*Sorry I didn't post it on calebs section because I don't have $10.6 -
So we were building this thing with a raspberry pi, a few sensors and a few motors but for some reason we could not interface a sensor with the pi (this is supposed to be trivial) so we interfaced it with an Arduino and had connected a pin on the Arduino to the Raspberry pi to alert the pi when the sensor reads something!
Not something we were proud of but we had time constraints and couldn't figure out how to make it work. Also, the thing we were building was just for a one time use so we thought it would be okay -
damn
even hacktoberfest is going woke this year
no more t-shirts
some stupid digital pin probably that can forever spew out CO2 somewhere on some server farm in iceland or something
to be clear, i'm not a climate change denyer. but it stupid shit like this as to why we can't have nice things. all the incentives are backwards. change my mind
would have been the 5th shirt too... 😉
i'll probably print myself one anyway9 -
So while exploring some new ideas, I decided to figure out if I could use variables in the known set to determine the bounds of variables in the unknown set.
The variables in question are algebraic identities derived from the semiprimes, so you already know where this is going.
The existing known set is 1194 identities.
And there are, if I recall, roughly two dozen unknowns.
Many knowns have the unknowns as their factors. The d4 product set for example is composed of variables d4a, d4u, d4z, d4z9, d4z4, d4alpha, d4theta, d4omega, etc.
The component variables themselves are unknown, just their products are known. Anyway.
What I've found interesting is if you know the minimum of some of these subsets, for example d4z is smallest out of the d4's for some semiprimes, then you know the upperbound of both the component variables d4 and z.
Unless of course either of them is < 1.
So the order of these variables, based on value, changes depending on the properties of the semiprime, which I won't get into. Most of the time the order change is minor, but for some variables they can vary a lot between semiprimes, rapidly shifting their rank in the known set. This makes it hard to do anything with them.
And what I found myself asking, over and over again, was if there was a way to lock them down? Think of it like a giant switch board, where flipping one switch lights up N number of others, apparently at random. But flipping some other switch completely alters how that first switch works and what lights it seemingly interacts with. And you have a board of them thats 1194^2 in total. So what do you do?
I'd had a similar notion a while back, where I would measure relative value in the known set, among a bunch of variables, assign a letter if the conditions were present, and generate a string, called a "haplotype."
It was hap hazard and I wrote a lot of code to do filtering, sorting, and set manipulation to find sets of elements in common, unique elements, etc. But the 'type' strings, a jumble of random letters, were only useful say, forty percent of the time. For example if a semiprime had a particular type starting with a certain series of letters, 40% of the time a certain known variable was guaranteed to be above a certain variable from the unknown set...40%~ of the time.
It was a lost cause it seemed.
But I returned to the idea recently and revamped the entire notion.
Instead what I would approach it from a more complete angle.
I'd take two known variables J and K, one would be called the indicator, and the other would be the 'target'.
Two other variables would be the 'component' variables (an element taken from the unknown set), and the constraint variable (could be from either the known or unknown set).
The idea was that relationships between the KNOWN variables (an indicator and a target variable) could be used to indicate the rank relationship between the unknown component variable and the constraint variable.
You'd think this wouldn't work either, but my intuition was there were so many seemingly 'random' rank changes of variables in the known set for any two semiprimes, that 1. no two semiprimes ever shared the same order for every variable, and 2. the order of the known variables had to be leaking information about the relationships of the unknown variables.
It turns out my intuition was correct.
Imagine you are picking a lock, and by knowing the order and position of the first two pins, you are able to deduce the relative position of two pins further back that you can't reach because of the locks security features. It doesn't let you unlock the lock directly, but by knowing this, if you can get past the lock's security features, you have a chance of using information about the third pin to get a better, if incomplete, understanding about the boundary position of the last pin.
I would initiate a big scoring list, one for each known element or identity. And then I would check it in tandem like so:
if component > constraint and indicator > target:
indicator[j]+= 1
This is a simplication, but the idea was to score ALL such combination of relationship, whether the indicator was greater than the target at the same time a component was greater than a constraint, or the opposite.
This worked out to four if checks and four separate score lists.
And by subtracting one scorelist from another, I could check for variables that were a bad fit: they'd have equal probability of scoring for example, where they were greater than the target one time, and then lesser than it for another semiprime.
So for any given relationship, greater or lesser between any unknown variable and constraint variable, I could find any indicator variable and target variable whose relationship strongly correlated to the unknown's.14 -
Me and my aunt. We put a whole frozen chicken into the microwave. After the frost is gone, it starts moving.
“Boiling moisture”, we think. Then, the chicken awakens. “Leave it to boil, lobsters are boiled alive after all”, says my aunt. “No! We’re microwaving a live animal! That’s torture!”, I scream in panic. We switch the microwave off. Chicken — out. No skin, hellish red meat, severe burns. It tries to scream but can’t. I need to put it out of its misery, NOW.
Aunt says “hold it against the table, I’m going to break its neck”. I oblige, and she proceeds to crush its neck with a two-by-four. It turns out, the neck is basically rubber and doesn’t budge. I have a better idea: let’s do something to its brain directly. I take a pin and proceed to find its skull. But there is no skull to be found, just a capri-sun for its head, with a small pocket of something squishy. The chicken keep wheezing loudly, desperate to scream. I poke that pouch with a pin. It splits in half, spilling the insides — gray chalk.
“It’s gone”, says aunt. “Its suffering is over”.
I sigh in relief. That was quite a cooking experience.
Thank god I woke up. It was just a dream.2 -
This is my most awkward interview experience. I still shudder just thinking about what happened
When I was in uni I applied for a ‘student ambassador’ role at Microsoft. I went to the interview and it turned out to be group interview with at least 10 other people, we all get taken to a room where we sit around a table with the interviewer. She was friendly and asked us each to introduce ourselves and talk about a talent we have.
When my turn comes I introduced myself and revealed that my ‘talent’ was that I can rap, this is where I fucked up because the interviewer then asked me to rap a song in front of the whole group.
I got very nervous but still gave it a shot, midway through my song due to my nerves I forget the lyrics, a complete brain fart. I abruptly stop rapping and everyone is staring at me, it’s pin drop silence for a good 10 seconds
The interviewer then says thanks for trying and the rest of it is really a blur. I think everyone in the room was embarrassed alongside me so we all pretended like that did not just happen. Needless to say I didn’t get the job1 -
So I promised a post after work last night, discussing the new factorization technique.
As before, I use a method called decon() that takes any number, like 697 for example, and first breaks it down into the respective digits and magnitudes.
697 becomes -> 600, 90, and 7.
It then factors *those* to give a decomposition matrix that looks something like the following when printed out:
offset: 3, exp: [[Decimal('2'), Decimal('3')], [Decimal('3'), Decimal('1')], [Decimal('5'), Decimal('2')]]
offset: 2, exp: [[Decimal('2'), Decimal('1')], [Decimal('3'), Decimal('2')], [Decimal('5'), Decimal('1')]]
offset: 1, exp: [[Decimal('7'), Decimal('1')]]
Each entry is a pair of numbers representing a prime base and an exponent.
Now the idea was that, in theory, at each magnitude of a product, we could actually search through the *range* of the product of these exponents.
So for offset three (600) here, we're looking at
2^3 * 3 ^ 1 * 5 ^ 2.
But actually we're searching
2^3 * 3 ^ 1 * 5 ^ 2.
2^3 * 3 ^ 1 * 5 ^ 1
2^3 * 3 ^ 1 * 5 ^ 0
2^3 * 3 ^ 0 * 5 ^ 2.
2^3 * 3 ^ 1 * 5 ^ 1
etc..
On the basis that whatever it generates may be the digits of another magnitude in one of our target product's factors.
And the first optimization or filter we can apply is to notice that assuming our factors pq=n,
and where p <= q, it will always be more efficient to search for the digits of p (because its under n^0.5 or the square root), than the larger factor q.
So by implication we can filter out any product of this exponent search that is greater than the square root of n.
Writing this code was a bit of a headache because I had to deal with potentially very large lists of bases and exponents, so I couldn't just use loops within loops.
Instead I resorted to writing a three state state machine that 'counted down' across these exponents, and it just works.
And now, in practice this doesn't immediately give us anything useful. And I had hoped this would at least give us *upperbounds* to start our search from, for any particular digit of a product's factors at a given magnitude. So the 12 digit (or pick a magnitude out of a hat) of an example product might give us an upperbound on the 2's exponent for that same digit in our lowest factor q of n.
It didn't work out that way. Sometimes there would be 'inversions', where the exponent of a factor on a magnitude of n, would be *lower* than the exponent of that factor on the same digit of q.
But when I started tearing into examples and generating test data I started to see certain patterns emerge, and immediately I found a way to not just pin down these inversions, but get *tight* bounds on the 2's exponents in the corresponding digit for our product's factor itself. It was like the complications I initially saw actually became a means to *tighten* the bounds.
For example, for one particular semiprime n=pq, this was some of the data:
n - offset: 6, exp: [[Decimal('2'), Decimal('5')], [Decimal('5'), Decimal('5')]]
q - offset: 6, exp: [[Decimal('2'), Decimal('6')], [Decimal('3'), Decimal('1')], [Decimal('5'), Decimal('5')]]
It's almost like the base 3 exponent in [n:7] gives away the presence of 3^1 in [q:6], even
though theres no subsequent presence of 3^n in [n:6] itself.
And I found this rule held each time I tested it.
Other rules, not so much, and other rules still would fail in the presence of yet other rules, almost like a giant switchboard.
I immediately realized the implications: rules had precedence, acted predictable when in isolated instances, and changed in specific instances in combination with other rules.
This was ripe for a decision tree generated through random search.
Another product n=pq, with mroe data
q(4)
offset: 4, exp: [[Decimal('2'), Decimal('4')], [Decimal('5'), Decimal('3')]]
n(4)
offset: 4, exp: [[Decimal('2'), Decimal('3')], [Decimal('3'), Decimal('2')], [Decimal('5'), Decimal('3')]]
Suggesting that a nontrivial base 3 exponent (**2 rather than **1) suggests the exponent on the 2 in the relevant
digit of [n], is one less than the same base 2 digital exponent at the same digit on [q]
And so it was clear from the get go that this approach held promise.
From there I discovered a bunch more rules and made some observations.
The bulk of the patterns, regardless of how large the product grows, should be present in the smaller bases (some bound of primes, say the first dozen), because the bulk of exponents for the factorization of any magnitude of a number, overwhelming lean heavily in the lower prime bases.
It was if the entire vulnerability was hiding in plain sight for four+ years, and we'd been approaching factorization all wrong from the beginning, by trying to factor a number, and all its digits at all its magnitudes, all at once, when like addition or multiplication, factorization could be done piecemeal if we knew the patterns to look for.7 -
MS Teams with multiple work accounts account swap flow:
1. Try to close the company-bound login modal 10x while being fast enough to also close the main Teams window.
2. Realize it's not gonna work, so login with the account you don't want to be on.
3. Have to type your phone pincode then accept the MS Authenticator login, and retype your pin code.
4. Finally logged in just to log back out and get the generic account choice modal so repeat step 2 & 3 with the correct account.1 -
Senile Web login services from 2009 grind my gears, and tertiary education administration snorts the powder.
Trying to apply online at a local university. They didn't have place for me 3 years ago so I went elsewhere but for my 4th year I have to go to them.
Because of my previous application I still have a student number. Online application says I have to log in to another portal and apply there. Then that portal now requests a Pin that I was never sent, and the "request new pin" function doesn't work because apparently my email is not in the database for my ID. My email was 100000% sure on my application, but some dingus never inserted it into the system.
Why not just start a "new" application you ask? Because the New Applications portal won't allow it for my ID number since it has a student number already. Now I either have to apply manually and pay the fee or wrangle Uni staff to reset my account.
I'm calling you, your slapdash JavaScript 1.2 code and your unhelpful staff out, Cape Peninsula University of Technology. -
unfortunately, iCloud's "hide my mail" available for as low as $1.19/mo is the best email aliases service. Why? Because those addresses have no discernible pattern, and, most importantly, end with @icloud-dot-com.
a lot of services nowadays think aliases are for scammers, so they reject well-known alias domains like those proton has. but no one rejects icloud ones.
they can't wrap their head around that people like me use aliases, one alias per service, to have control over the spam you send us. unsubscribe buttons in emails often don't work, or unsubscribe you from some super-niche "segment" that one email belonged to, but because you bitches have a lot of those segments, you just carry on spamming.
major dicks that aren't concerned with email deliverability rating, like microsoft — because their emails get delivered no matter what, they're microsoft after all — think they can just not allow people to unsubscribe from their spam. when I needed to create a ms account, thank god I used an alias. I got bombarded with their spam, and lo and behold, not a single email had an unsubscribe button. Instead, the bottom of each email said "this email is a part of mandatory onboarding" or some shit like that, despite just being advertisement. no option to unsubscribe from that bs in their "dashboard" either.
so I just disabled that alias. despite what all of you stupid fucks want, it's my computer, and on it, the computing happens on my terms. when I need a confirmation email, I enable the alias, get the email and then disable it.
I have no mics and no cameras. I pay cash. I don't borrow money from banks. I don't have a credit card. when I receive crypto, I exchange it for cash directly in a physical crypto exchange that doesn't require my passport. I have headphones with built-in mic that I use exclusively for calls, but when I plug them out, no mic for ya. my next phone won't have a sim (and no eSIM either), I will disassemble it and take the front-facing cam, as well as mics, out of the phone, and then cover the back camera with velcro that I'll undo every time I need to take a pic. it will also run graphene os and be held inside a faraday cage when not in use. I have a separate dumb phone for calls that has its removable battery disconnected at all times when I don't use it. no matter if you're corpo or government, no matter all zero-days and backdoors, if there is physically no mic and no cam to be found, trying to access them is futile.
no use trying to profile me or get any kind of info from me unless I want you to — I'll just strangle you and your systems. my info sphere is a fortress surrounded by a bottomless tarpit. you'll drown in it should you try to violate me. if you so much as touch it, it will suck you in. I'll stream your drowning on youtube.
even irl, I try to dress, walk and move as weirdly as possible. during my morning walk, I be straight up walk as if I was rabid. when our eyes meet, I'll smile creepily, just to communicate that don't fucking touch me you fucking degenerate. don't even think about talking to me. just walk away you bitch before I pin you to the ground and bite your ear off. if you're bigger than me, you'll just get tased.
only those I trust deserve open, kind, validating, beautiful, well dressed and good smelling kiki.4 -
Faced a guy who tried to pin, his data not coming up on our app. After debugging I found out he was sending the timestamp as his local time + 'z'(e.g. 2019-06-13T22:38:54.143Z), thinking thats for est and blamed us for why his data is not showing at correct time.3
-
sitting here at internship bored out of my mind i got the program working and the next step is to add persistence to the micro-controller so i'm supposed to be reading up on that but i just get bored so easily i learn quicker with hands on practice so i'm just gonna wait until he gets me other board i'll be connecting to an I/O pin to add persistence1
-
How can a novel emerging challenger software (written in Rust) take me 4 hours to install (still ongoing)?
Today I have decided to give Pijul a go. Pijul describes itself as a theory-sound alternative to Git, which I have wanted to get away from for a while now, due to various reasons -- many of which I saw Pijul advertise to have solved on design level.
So I set away a day to learn Pijul, today. Well, 4 hours after I sat down -- after a number of hilariously wonky failures of "Rust ecosystem" to do the right thing as I had to install Rust with some shell one-liners those insane wizards recommend for installation process (all in the name of "stability but not stagnation") -- Pijul has now been installing with the blasted `cargo` for an hour now (that's after 3 hours of getting to the point where `cargo install pijul` stopped exploding in my face) -- telling me I only have 40 crates more to install. Are they throttling me, perhaps? I don't care -- I should have been installing Pijul from a repository in accordance with my Linux distribution, or -- at worst -- download a BLOODY COMPILED PROGRAM IMAGE.
What is it with the hipster developers today? Everything they get of tools, they subsume and churn out intricate complexities the likes of which we hadn't seen yesterday. Tell me fellow developers who think installation of your software has to require three and a half novel "installation solutions" to which I can't be arsed to be made privy -- do you think your life today is easier than, I don't know -- wrangling with a Makefile and a C compiler (which today thankfully can do rather good job of standards compliance)?
I mean I wouldn't mind Pijul being written in Rust -- but it turns out Rust's advertised elegancy in practice is wrapped in so much "giftwrap" I feel like what desire I had to learn Rust myself, I'll stear well clear.
Here's an advice for developers in general -- an advice continiously ignored for decades -- stop blowing your original scope of delivery in auxilary packages you think you need to reinvent just because you can or because your mom is out of town! For programming languages like Rust this most certainly entails NOT writing your own package manager, with its own package delivery mechanism that has its own configuration file format and virtual machine to configure dependency resolution or what have you!
You wanted to write a programming language that has novel features you think we need? Fine -- write one and stop there. Watch it grow, and watch people who are busy working on other parts (scopes) of software to integrate your offer.
What a shitshow. Stop smuggling alternative package managers, installers, and discombulators with your actual product -- I only want the latter, I don't want the rest of your damn piping, walls, roof and a cathedral on top of it!
Don't be that guy starting with a pin, and ending up with a fucking diorama miniature of a pig farm in Netherlands. Jesus.7 -
"In today's fast-paced world, mobile gaming has become a staple for entertainment seekers. For Bangladeshi players looking to indulge in premium casino games, the Pin-Up Casino App stands out as a top choice, available for download at https://pinupdownload-bd.com/ .
The app boasts a vast collection of games, ranging from classic slots to live dealer tables, ensuring there's something for every gaming preference. Its sleek design and intuitive navigation make it easy for users to explore various game categories, access promotions, and manage their accounts effortlessly.
One of the app's standout features is its optimized performance, ensuring smooth gameplay even on devices with limited resources. Regular updates introduce new games and features, keeping the gaming experience fresh and engaging. Additionally, the app supports secure payment methods widely used in Bangladesh, facilitating hassle-free transactions.
For those seeking a reliable and immersive mobile casino experience, the Pin-Up Casino App delivers on all fronts, combining entertainment, security, and convenience in one package."2 -
For those passionate about cricket and sports betting, Pin-Up offers an exciting platform designed for Bangladesh users. The website https://pinupcricket.net/ provides all the essential details for cricket betting enthusiasts, combining convenience, variety, and reliability.
Why Pin-Up Cricket Stands Out
Pin-Up Cricket is the perfect destination for cricket lovers who want to take their passion to the next level. Here’s why:
Comprehensive Cricket Betting Options: Whether it's international matches, local tournaments, or major leagues like the IPL, Pin-Up covers it all. You can place bets on match winners, player performance, total runs, and more.
Live Betting Experience: Stay engaged with real-time betting options during live matches. Follow the action as it happens, and place your wagers with up-to-the-minute odds.
Detailed Match Insights: Access comprehensive match statistics, team analysis, and betting tips to make informed decisions. Pin-Up ensures you’re always one step ahead with accurate data and insights.
User-Friendly Platform
Navigating Pin-Up Cricket is simple and intuitive. The platform’s design ensures that both beginners and seasoned bettors can easily find the betting markets they’re interested in. The mobile-friendly interface allows you to place bets anytime, anywhere.
Safe and Easy Transactions
Pin-Up supports a variety of secure payment options tailored to users in Bangladesh. From credit and debit cards to e-wallets and even cryptocurrencies, making deposits and withdrawals is seamless and secure.
Generous Bonuses and Promotions
New and existing users can take advantage of exciting bonuses. Welcome bonuses, free bets, and special promotions keep the excitement going and give you more opportunities to win big.
How to Get Started
Visit Pin-Up Cricket to explore the platform and sign up. Discover detailed guides on placing bets, current promotions, and tips for maximizing your betting experience.
With Pin-Up Cricket, you get a combination of entertainment, convenience, and reliability, making it the ultimate destination for cricket betting in Bangladesh. Start your journey today and enjoy the thrill of cricket betting!5 -
LEGITIMATE CRYPTO RECOVERY EXPERT IN USA; CYBER CONSTABLE INTELLIGENCE STANDS ABOVE THE REST
Flying a Boeing 787? Piece of cake. Decrypting a malfunctioning Trevor wallet? That's nosediving into chaos. I have done emergency landings, handled unpredictable weather, and passengers that think they can open the emergency exit during flight. But nothing, not even years of aviation training, prepared me for the moment my cold storage wallet refused to recognize my PIN. I knew I was punching in what was correct, but Trevor stared back at me like I was an imposter in my own cockpit.
At first, I thought it was a simple mistake. Perhaps fat fingers? A misremembered digit? But after several attempts, I realized something was seriously wrong. The more I tried, the more the wallet locked me out, and it dawned on me harder than a rogue crosswind: My $750,000 worth of Bitcoin was slipping through my fingers.
I did what any reasonable person would do in such a situation-panicked. Then came the hours of browsing through forums, watching tutorials, and trying every trick in the book. One suggested freezing my device, another insisted on some arcana firmware rollback method. Nothing worked. At this point, I had all but thrown myself at the mercy of the fates.
Long-haul flight, cruising at 36,000 feet- that is where I happened upon Cyber Constable Intelligence. I was skeptical, but desperation makes you reconsider everything: after all, if the device manufacturer couldn't help me out, how on earth could these guys? The moment I landed, I called them.
From the first conversation I had with them, I knew I had chosen rightly. Their team was professional, knowledgeable, and reassuring in explaining the forensic recovery process-how it all works in a no-nonsense explanation with no vague tech jargon or false promises.
Within just five days, they had bypassed the PIN problem, restored my Bitcoin, and pointed out safety recommendations to make sure I would never find myself in this kind of situation again. Their work was faultless-a perfect landing.
I can fly through turbulence, respond to in-flight emergencies, and cross the world without breaking a sweat. But when it comes to rescuing locked Bitcoin from a malfunctioning cold storage wallet? That's a job for Cyber Constable Intelligence. If your crypto is in freefall, don't reach for the eject button-call them, and they'll get you flying again.-.
Here's their Info below
WhatsApp: 1 252378-7611
Website info; www cyberconstableintelligence com
Email Info cyberconstable@coolsite net
Telegram Info: @cyberconstable3 -
BEST AGENCY TO RECOVER SCAMMED CRYPTO-CONTACT SALVAGE ASSET RECOVERY
Flying a Boeing 787? Piece of cake. Decrypting a malfunctioning Trezor wallet? That's nose diving into chaos. I have done emergency landings, handled unpredictable weather, and passengers that think they can open the emergency exit during flight. But nothing, not even years of aviation training, prepared me for the moment my cold storage wallet refused to recognize my PIN. I knew I was punching in what was correct, but my Trezor stared back at me like I was an imposter in my own cockpit.
At first, I thought it was a simple mistake. Perhaps fat fingers? A misremembered digit? But after several attempts, I realized something was seriously wrong. The more I tried, the more the wallet locked me out, and it dawned on me harder than a rogue crosswind: My $750,000 worth of Bitcoin was slipping through my fingers.
I did what any reasonable person would do in such a situation-panicked. Then came the hours of browsing through forums, watching tutorials, and trying every trick in the book. One suggested freezing my device, another insisted on some arcana firmware rollback method. Nothing worked. At this point, I had all but thrown myself at the mercy of the fates.
Long-haul flight, cruising at 36,000 feet- that is where I happened upon Salvage Asset Recovery. I was skeptical, but desperation makes you reconsider everything: after all, if the device manufacturer couldn't help me out, how on earth could these guys? The moment I landed, I called them.
From the first conversation I had with them, I knew I had chosen rightly. Their team was professional, knowledgeable, and reassuring in explaining the forensic recovery process-how it all works in a no-nonsense explanation with no vague tech jargon or false promises.
Within just five days, they had bypassed the PIN problem, restored my Bitcoin, and pointed out safety recommendations to make sure I would never find myself in this kind of situation again. Their work was faultless-a perfect landing.
I can fly through turbulence, respond to in-flight emergencies, and cross the world without breaking a sweat. But when it comes to rescuing locked Bitcoin from a malfunctioning cold storage wallet? That's a job for Salvage Asset Recovery. If your crypto is in freefall, don't reach for the eject button-call them, and they'll get you flying again. Their contact details
TELEGRAM---@Salvageasset
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
For the past four months, I’ve been trapped in a nightmare with traderup com. I’ve been unable to access my funds due to a PIN issue that I couldn’t recover. Every time I contacted customer support, they promised to email me a solution within 24 hours, but never followed through. I checked my inbox, including spam folders, and found nothing. It felt like I was being ignored. The frustration only increased as I couldn’t withdraw my money, despite numerous attempts. When I reached out for help, one agent directed me to their Telegram channel. Unfortunately, I couldn’t get in touch with anyone through it, and that route proved to be just another dead end. It became clear that traderup com was doing everything in its power to keep my funds from being released. The company’s application didn’t even offer a way to recover my PIN. With no clear solution from their support team and no recovery option, I was left feeling completely helpless. It was as if my money had been locked away in a trap, and I couldn’t get it out. I felt desperate and didn’t know what to do next. My attempts to get help were falling short, and every day that passed without access to my funds added to the stress and anxiety I was experiencing. Then, after some online research, I found Blockchain Cyber Retrieve, and everything changed. When I reached out to Blockchain Cyber Retrieve, I was initially skeptical, given the situation with traderup com. However, their team reassured me and explained how they could help. They were professional, attentive, and knowledgeable about the recovery process. They acted swiftly and efficiently, keeping me informed every step of the way. Within a week, I had all my funds back, and the process was smooth, professional, and stress-free. I honestly can’t thank them enough for their help. They truly are the queens of chargebacks, offering real solutions when all other options failed. It’s clear that traderup com was never going to release my money without external intervention. Their lack of communication and transparency made it impossible for me to resolve the issue on my own. However, Blockchain Cyber Retrieve dedication and expertise were exactly what I needed to get my funds back. If you’re in a similar situation and feel like you’re being ignored or trapped, I highly recommend Blockchain Cyber Retrieve. They were the only ones who got the job done when no one else could. They restored my faith in getting things right and helped me recover my hard-earned money.
Reach out to them on:
WhatsApp:+ 1520 564 8300
Email: blockchaincyberretrieve (@) post. c o m6 -
“CRYPTOCURRENCY TRACING AND RECOVERY - HIRE PRO WIZARD GILBERT RECOVERY”
Navigating the aftermath of a significant financial loss can be incredibly daunting. My name is John, and recently, I found myself in a distressing situation when my girlfriend attempted to gain unauthorized access to my cryptocurrency wallet. In a desperate bid to lock me out, she tried to change the PIN and even resorted to deleting the wallet. Fortunately, I had anticipated her actions and changed the PIN just in time, thwarting her attempts to abscond with the $350,000 worth of Bitcoin assets stored within. Feeling shaken and vulnerable, I sought assistance from PRO WIZARD GIlBERT RECOVERY, a service recommended by a close friend. From the outset, their team provided exceptional support and assurance. With empathetic ears, they listened to my story and reassured me that they possessed the expertise to recover my funds. PRO WIZARD GIlBERT RECOVERY's team embarked on a comprehensive investigation, meticulously tracing the attempted unauthorized access and the subsequent deletion of the wallet. Their technical prowess was evident as they delved deep into the complexities of digital transactions, determined to reclaim what was rightfully mine. In an impressive display of skill and dedication, they managed to recover the entire wallet within a matter of weeks. The sense of relief and gratitude that washed over me was indescribable.
Additionally, PRO WIZARD GIlBERT RECOVERY provided invaluable guidance on fortifying the security of my digital assets to prevent future breaches. Their unwavering commitment to their craft and their compassionate support were invaluable during this trying time. They transformed what could have been a catastrophic disaster into a tale of resilience and recovery. I wholeheartedly endorse their services to anyone grappling with similar challenges. They are true guardians of digital security, equipped to help you navigate through adversity and emerge stronger on the other side.
WhatsApp: +1 (425) 623‑3222 -
It can be quite difficult to navigate the aftermath of a large financial loss. My name is Kai Jackson, and I was recently put in a difficult situation when my girlfriend tried to access my bitcoin wallet without authorization. She even tried to delete the wallet and change the PIN in a desperate attempt to lock me out. Luckily, I had predicted her moves and had changed the PIN in time to prevent her from taking the $510,000 worth of Bitcoin assets that were kept inside. I was so scared and exposed that I went to WIZARD JAMES RECOVERY, a friend's recommendation, for help. From the beginning, their group offered outstanding assistance and confidence. They listened to my narrative with sympathetic ears and promised me that they have the know-how to get my money back. The experts at WIZARD JAMES RECOVERY started a thorough investigation and painstakingly tracked down the attempt at unauthorised entry and the wallet's subsequent erasure. They were desperate to recover what was properly mine, and their technological prowess was on display as they dug deep into the intricacies of digital transactions. In just a few weeks, they recovered the complete wallet in an amazing feat of expertise and perseverance. There was an unbelievable wave of relief and gratitude that passed over me.
Furthermore, WIZARD JAMES RECOVERY gave me priceless advice on bolstering my digital assets' security to stave off future intrusions. Their steadfast dedication to their work and their kind assistance were sorely needed during this difficult period. What should have been a disastrous event was turned into a story of resiliency and healing by them. I highly recommend their services to anyone facing comparable difficulties. They are the real protectors of online safety, able to guide you through difficulties and help you come out stronger on the other side.
Email: WIZARDJAMESRECOVERY @ USA . COM

