Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "outside network"
-
So I have complained to our landlord about a noisy neighbor who keeps blasting shitty music at midnight, and technically its against the law as well, but this bitch ass joke of a human being ignored even the most highest of authority.
Seeing I can't solve it with democracy, I finally gave up with any reasonable type of way to restrain this motherfucker (even calling police didn't help) and went full asshole with him
I know his WiFi uses WPS PIN, but I'm not gonna throttle his network, I want to piss him off so much he'll regret living beside me, or at our place entirely.
So I performed a Evil Twin attack, I had my Raspberry Pi act as a both cloned AP and a deauther. Finally the plan came to effect.
I ran the deauther in his AP, effectively disconnecting his devices, and had the devices connect to the cloned network. The primary aim of my attack is to annoy this bitch ass to the point of no return. The project I used serves a website on the cloned AP like a update for his router. I intentionally made it run overnight, blasted Lo-fi hip hop and went to sleep. Before I dozed off, I can hear their scream of rage because they can't blast their music at full volume (waddaya guess, they use Spotify).
I finally woke up the next day, and I find neighbor complaining about me, and they were trying to tell the landlord I was hacking them. It's technically true but its not as bad as domestic disturbance for a full fucking week.
Landlord asked me if I did it, I declined, she believed me (I know she does because she knows I'm a pure soul unlike this mofo). Then he left frustrated, threatened to sue me for hacking.
I just smickered, he can't really prove anything unless I was being sloppy.
Nowadays I get good sleep and finally we live in a quite peaceful place now. Now you may ask, what happened to that guy? After he threatened me, the next night he found his things outside his own room, he was kicked out by the landlord.
Moral of the story: we ain't hating on your music taste but don't showcase it like its the most important thing in the world when everyone is sleeping. Case and point, don't be an asshole18 -
I feel so sorry for all the people in the world who use their phone more than their PC/laptop.
All the pitiful souls who think they're gamers because they installed lootchest simulator on their little digital skinner box. All the sad beings who just view the internet as a collection of ad-infested apps.
Actually, I don't feel sorry, because these people make the world a worse place.
Suddenly we needed websites which could render on tiny screens and need bloated cross-platform app development frameworks. Many game studios became parasites exploiting addictive behavior in humans, instead of creating works of art.
Humans spent 10,000 years to perfect their caves with expensive kitchens, and all people want is for their WiFi to reach the grill at the end of the garden. Humans created central heating, comfortable couches, wall-mounted TVs and luxurious desks -- and all people can think of is whether their phone plan covers holiday roaming at their shitty resorts.
The rare times I do actually go into this apocalyptic wasteland people call "The Outside", all I see is subway cars full of hunched addicted drudges, bus stops with clusters of enslaved automatons.
Fuck all of them.
Fuck all of you imbeciles, who ventured out of the cave and now DARE to call me anti-social, just for preferring the warmth of my comfortable protective den.
It's fucking cozy here, within the walls of my shelter, I got booze and a fridge full of food and a bunch of LSD, I can masturbate under the shower, have sex on the couch, have all kinds of GIANT displays for entertainment, with full-sized qwerty-keyboards, high-DPI mouses, even some console controllers and big TVs if I feel lazy.
You can stick your responsive websites and social-network-integrated Android apps up your rectum, just sit your fucking fat ass down in front of a workstation and desperately refresh the stream of fake attention-seeking messages there, if you absolutely must.
Seriously, why does this guy from our marketing department call me on my private phone number. Why did HR PROVIDE him with my private phone number?
And WHY THE FUCK is he asking me, a DB admin: "Our website doesn't load properly on Safari on my iPhone 7, could you take a look at it"?
No, of course I won't fucking come to the office to take a look at your miserable shitty device with its cracked glass screen.
Fuck you and your outdoorsy habits.
Stay the fuck in your cave, you degenerate attention whore, otherwise please go choke on your airpods.19 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
So...
I'm penetrationtesting a network and the servers on said network
The network administrator and IT security officer knows this, because they hired me..
TL;DR a scan caused the network to crash.
Today I received a very angry email going "Stop scanning NOW!" from one of the IT departments.
Apparently I crashed their login server and thus their entire network...
It happened d the first time I scanned the network from the outside and they had spend an entire day figuring out how and repairing the service they thought was the problem, but then it crashed again, when I scanned from within the network.
Now they want to send me a list of IP's that I'm not allowed to scan and want to know exactly what and when I'm scanning...
How crap can they be at their job, if they weren't able to spot a scan... The only reason they found out it was me was because the NA had whitelistet my IP, so that I could scan in peace...5 -
This is my first post on devRant!
Story time:
It was on my first job as a developer, learning a lot but getting paid less than 50% of the minimum monthly wage of my country.
It was settled in the interview that as I gained more experience, I could handle more projects and earn more money.
At the time, I was living with my parents and didn't have to pay rent and some stuff, so I was like "Well, I'm gonna learn a lot and, if I put a lot of effort into it, soon I'll be making more money".
We agreed that I'll only develop, but 4 months into the job, I was already going to clients
and started coding there (having the client on my back every minute, not being able to work properly) and fixing some computer/network issues they had,
because my boss said I should do it.
Things at home started to go south, and suddenly I needed more money, so I kept doing the work and getting paid a little bit more
A year goes by, devs came and go beacuse of the work/payment situation, and I was still there.
From my first "paycheck" to the last day I never got paid on time, and that was the same for everybody else
The last month I was there, I had a job offer with a better salary and weekends free, so I wanted to take it (I worked saturdays there).
We were working at our biggest clients place at the time (a hospital, working in the server room, desk and chair were a total crap),
so I wanted to have a good conversation with my boss and tell him whats up, after all, I was really grateful for the job despite all things.
We headed outside and started talking. He basically begged me to stay, said that he will pay me on time and offered me more money (less than the other company was offering me),
and that he needed me to finish the implementation and "minor issues" with the app.
I thought about it for a couple of days, and decided to stay. I politely rejected the job offer, and even recommended someone else.
As the days passed, regret was building fast inside of me, until the day that I was supposed to get paid.
He never showed up to the client, told me in a call that he will be there sometime in the morning, that he had the money for me.
So I stayed until my day ended, and still no sign of him. I had no money on me, needed some for gas so I could go, and I called him 5 times.
He picked up the last time, talks to me like nothing is happening and I started to shout at him like I never shouted to anybody before,
got all the things of my chest, and when I was done, he said that he will send the money to my account right away.
This happened on a Saturday, so I quit the following Monday, and lost the other job offer.6 -
This just in everyone...
Android Dev: *sent and email to network admin* can you please unblock github for a few mins.
Network admin: *Replied* Can you take a screenshot whats the error your getting.
Android Dev: *Replied with screenshot* "Failed to load resource: the server responded with a status of 503 (Service Unavailable)"
Network admin: that is a known issue. *Replied with Wordpress Links.
Android Dev: why is github working outside our network then?
Network admin: there must be a problem with your code that needs to be tweaked.
Team: *FACE PALM*5 -
I'm so grateful DevOps is now a thing. I remember getting a phone call from a client at 2am on a Friday because their site was down and having to ssh in from a Nokia with the world's tiniest keyboard to reboot the server.
Of course that particular server only exposed port 22 on it's local network, so I had to first ssh into another server which did have its ssh port open to external connections.
Trying to remember two sets of credentials and type them in on a tiny keyboard, while so drunk you were seeing double, standing outside in the rain as it was the only place you got signal. Yeah…I'm so grateful DevOps is now a thing 7
7 -
I’ve started the process of setting up the new network at work. We got a 1Gbit fibre connection.
Plan was simple, move all cables from old switch to new switch. I wish it was that easy.
The imbecile of an IT Guy at work has setup everything so complex and unnecessary stupid that I’m baffled.
We got 5 older MacPros, all running MacOS Server, but they only have one service running on them.
Then we got 2x xserve raid where there’s mounted some external NAS enclosures and another mac. Both xserve raid has to be running and connected to the main macpro who’s combining all this to a few different volumes.
Everything got a static public IP (we got a /24 block), even the workstations. Only thing that doesn’t get one ip pr machine is the guest network.
The firewall is basically set to have all ports open, allowing for easy sniffing of what services we’re running.
The “dmz” is just a /29 of our ip range, no firewall rules so the servers in the dmz can access everything in our network.
Back to the xserve, it’s accessible from the outside so employees can work from home, even though no one does it. I asked our IT guy why he hadn’t setup a VPN, his explanation was first that he didn’t manage to set it up, then he said vpn is something hackers use to hide who they are.
I’m baffled by this imbecile of an IT guy, one problem is he only works there 25% of the time because of some health issues. So when one of the NAS enclosures didn’t mount after a power outage, he wasn’t at work, and took the whole day to reply to my messages about logins to the xserve.
I can’t wait till I get my order from fs.com with new patching equipment and tonnes of cables, and once I can merge all storage devices into one large SAN. It’ll be such a good work experience.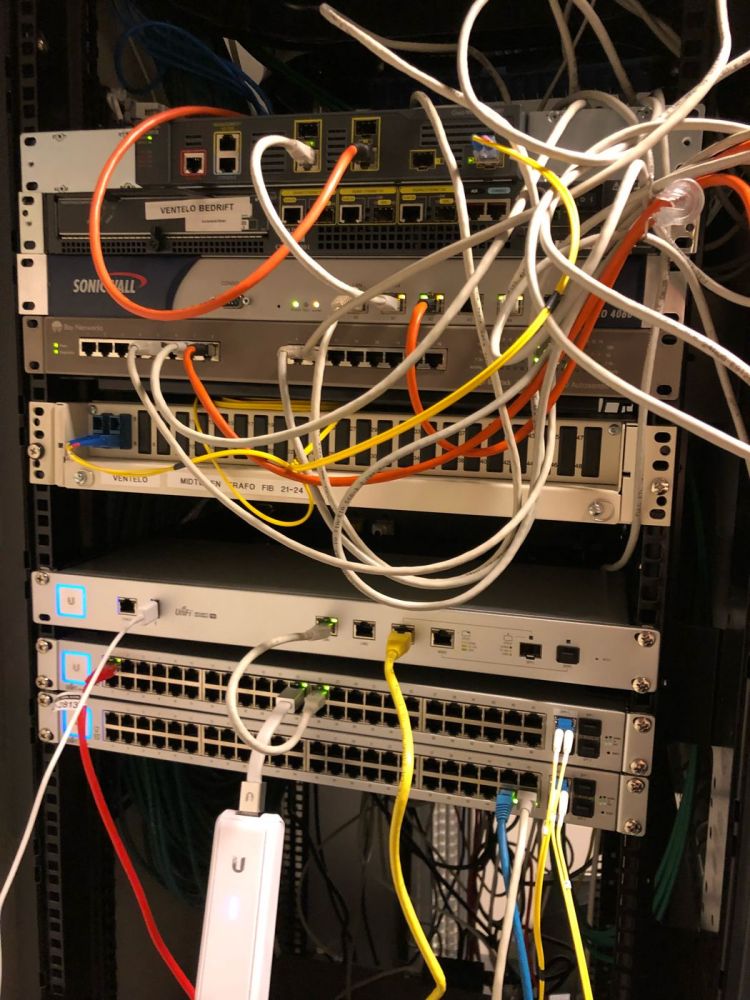 7
7 -
A client of mine kept getting hit with a ransomware that was spread over rdp. So I set aside this whole week going to different sites this guy owns. Setting up a VPN tunnel and showing them how to use it. So they didn't have to rdp anymore. No more having a server with rdp facing on the outside of there network. They were all linked in like they were in the same office. I traveled around 400 miles going to all these locations. I finally got it done went back to the main office to talk to the owner. Instead of a thank first thing they say as soon as I walk in is to revert it all. We are going with a different company and they are buying new computers and server from the other company. After he tells me that he then says but when the new computers come in will you come and set them up for us because we are stupid with computers.
I reverted the stuff and walked out. Didn't say a word to him. Didn't agree to set up the new computers. Why should I set them up. He just pretty much bent me over and screwed me out of a extra couple thousand dollars.3 -
a fuckin router that sits 0.4 METERS NEXT TO ME of FULL signal doesn't work at all on my phone so i have to switch to 4G network which fetches network far far away from the satellite which is placed IN THE FUCKIN COSMOS OUTSIDE OF THIS PLANET..... AND THAT FUCKING WORKS......9
-
TLDR: Small family owned finance business woes as the “you-do-everything-now” network/sysadmin intern
Friday my boss, who is currently traveling in Vegas (hmmm), sends me an email asking me to punch a hole in our firewall so he can access our locally hosted Jira server that we use for time logging/task management.
Because of our lack of proper documentation I have to refer to my half completed network map and rely on some acrobatic cable tracing to discover that we use a SonicWall physical firewall. I then realize asking around that I don’t have access to the management interface because no one knows the password.
Using some lucky guesses and documentation I discover on a file share from four years ago, I piece together the username and password to log in only to discover that the enterprise support subscription is two years expired. The pretty and useful interface that I’m expecting has been deactivated and instead of a nice overview of firewall access rules the only thing I can access is an arcane table of network rules using abbreviated notation and five year old custom made objects representing our internal network.
An hour and a half later I have a solid understanding of SonicWallOS, its firewall rules, and our particular configuration and I’m able to direct external traffic from the right port to our internal server running Jira. I even configure a HIDS on the Jira server and throw up an iptables firewall quickly since the machine is now connected to the outside world.
After seeing how many access rules our firewall has, as a precaution I decide to run a quick nmap scan to see what our network looks like to an attacker.
The output doesn’t stop scrolling for a minute. Final count we have 38 ports wide open with a GOLDMINE of information from every web, DNS, and public server flooding my terminal. Our local domain controller has ports directly connected to the Internet. Several un-updated Windows Server 2008 machines with confidential business information have IIS 7.0 running connected directly to the internet (versions with confirmed remote code execution vulnerabilities). I’ve got my work cut out for me.
It looks like someone’s idea of allowing remote access to the office at some point was “port forward everything” instead of setting up a VPN. I learn the owners close personal friend did all their IT until 4 years ago, when the professional documentation stops. He retired and they’ve only invested in low cost students (like me!) to fill the gap. Some kid who port forwarded his home router for League at some point was like “let’s do that with production servers!”
At this point my boss emails me to see what I’ve done. I spit him back a link to use our Jira server. He sends me a reply “You haven’t logged any work in Jira, what have you been doing?”
Facepalm.4 -
Okay, help :(
Trying to get my dns server in php to work from the outside (it's on a vm on one of my dedi's) but it's not working.
- Port forwarding works well: confirmed.
- Connection type: UDP; confirmed.
- I *can* dig from the host (dedicated server) to the vm.
- nmap scans show an open port.
The exact same happens on my local network.
I'm lost.13 -
Today the IT deparment update the firewall's configuration, they blocked almost every website except email and Google.
The problems:
- Blocked some systems outside the organization, there are in another building and also network
- I can search on Google but I can't see the results outside Google
- Forget about download depencies, libraries, deploy code to outside services, search at StackOverflow
I JUST WANNA SAY GOOD JOB, GUYS
PS: The firewall also block the SSH port, I had explained to my boss and he sent a request for allowing the port, so far no answer3 -
It took forever to get SSH access to our office network computers from outside. Me and other coworkers were often told to "just use teamviewer", but we finally managed to get our way.
But bloody incompetents! There is a machine with SSH listening on port 22, user & root login enabled via password on the personal office computer.
"I CBA to setup a private key. It's useless anyways, who's ever gonna hack this computer? Don't be paranoid, a password is enough!"
A little more than 30 minutes later, I added the following to his .bashrc:
alias cat="eject -T && \cat"
alias cp="eject -T && \cp"
alias find="eject -T && \find"
alias grep="eject -T && \grep"
alias ls="eject -T && \ls"
alias mv="eject -T && \mv"
alias nano="eject -T && \nano"
alias rm="eject -T && \rm"
alias rsync="eject -T && \rsync"
alias ssh="eject -T && \ssh"
alias su="eject -T && \su"
alias sudo="eject -T && \sudo"
alias vboxmanage="eject -T && \vboxmanage"
alias vim="eject -T && \vim"
He's still trying to figure out what is happening.5 -
26 or so hours up now. And I've got a few stories to tell :) feel free to refresh your cup of coffee and take a seat.
Last few days I've been going into this odd place called intown.irl to get in touch with its inhabitants. An odd place I have to say. But in some cases quite rewarding, even got a MILF home with me and into bed at some point. Anyway...
3 days ago I think it is now? Thursday evening I took my laptop to this local bar where I had this issue about dihydrogen monoxide with one of the bartenders earlier (you'll find that rant on those keywords). Still wanted to visit it regardless though, as I met that first woman there earlier that approached me. Unfortunately I didn't see her there that day.
Some bald guy who was clearly drunk approached me. Many people were already giving curious looks at this laptop I brought to the bar. I finally tuned it up with the stickers from FOSDEM.. I'll put a picture of it in the comments. My theme was one of privacy (central), distributions and Google's open source initiative (which aligns with the keychain token I got from them as well). But of course.. that guy.. he thought that a pimped/riced laptop obviously meant that I was a hacker.
Guy went to the toilet.. went back.. and suddenly grabbed my laptop and turned it towards him. Boy was I never more smugly satisfied that those rubber pads on the bottom are quite resilient. Could've almost damaged my screen by trying to grab it like that. But it's a CCFL display.. so high voltage. If it were to become broken.. worth it. 😈
On it at the time was a terminal, pinging Google (had network issues at that bar, to the point where one of the - I think - staff members got up to me and offered the WiFi password and got to talk with me.. more on that later), and my usual Linux desktop along with the Arch anime wallpaper with the quote of Da Vinci.. simplicity is the ultimate sophistication. Of course the guy saw the terminal.. and probably reaffirmed.. yep, that's a hacker. At least he wasn't too wrong about the general term.. but the hat.. most likely he was wrong on that one.
Guy left with this question.. "you are a hacker, aren't you."
I replied to him: "No sir. I'm not a hacker. I've got no idea what you're talking about."
Guy kept looking at me weirdly for the whole night to come.
Back to that companion guy though. Mac user, yada yada.. but he told me about his backup solution. Apparently - I shit you not - he has not only the photos on his local device, he's also frequently backing them up in Time Machine (which I was really curious about whether it uses mirroring or snapshots.. he couldn't tell, lmk if you do) but not only that.. he was storing another offsite backup in that very bar, in case his house went on fire.
Now that is a proper backup scheme!!! If only more people were like that.
Seriously though.. that bald guy who took my laptop just like that... I just let it slide for that one time, but I tend to treat my machines as an extension of my very self. I think that was a very uncalled for move. Asshole...
How would you have reacted to such a thing? And.. maybe that's why we technologists don't get outside too often? Fucking everything is hacking these days if it's not Knopkes and Blinkenlights… Not every shell is a h4xx0ring console for h3kk1ng de fasbuk…9 -
Well, this’ll get me a downrant and probably a pile of abusive and hateful comments, but I chose WordPress as my dev specialty. It’s in that sweet spot between my own uselessness as a full stack and front-end coder and my clients’ inability to comprehend how to click an “Update plugin” button. So they pay me to do that, plus the occasional “design”, and are seemingly happy to do so.
I think I won something. Not sure what. But my stress levels in my career are consistently at an all-time low. I have lots of flexible time in my day to do work, go outside, get exercise, work on hobbies, network with other people, and be with family. I guess being a WordPress “expert” isn’t all that bad.6 -
"There's more to it"
This is something that has been bugging me for a long time now, so <rant>.
Yesterday in one of my chats in Telegram I had a question from someone wanting to make their laptop completely bulletproof privacy respecting, yada yada.. down to the MAC address being randomized. Now I am a networking guy.. or at least I like to think I am.
So I told him, routers must block any MAC addresses from leaking out. So the MAC address is only relevant inside of the network you're in. IPv6 changes this and there is network discovery involved with fandroids and cryphones where WiFi remains turned on as you leave the house (price of convenience amirite?) - but I'll get back to that later.
Now for a laptop MAC address randomization isn't exactly relevant yet I'd say.. at least in something other than Windows where your privacy is right out the window anyway. MAC randomization while Nadella does the whole assfuck, sign me up! /s
So let's assume Linux. No MAC randomization, not necessary, privacy respecting nonetheless. MAC addresses do not leak outside of the network in traditional IPv4 networking. So what would you be worried about inside the network? A hacker inside Starbucks? This is the question I asked him, and argued that if you don't trust the network (and with a public hotspot I personally don't) you shouldn't connect to it in the first place. And since I recall MAC randomization being discussed on the ISC's dhcp-users mailing list a few months ago (http://isc-dhcp-users.2343191.n4.nabble.com/...), I linked that in as well. These are the hardcore networking guys, on the forum of one of the granddaddies of the internet. They make BIND which pretty much everyone uses. It's the de facto standard DNS server out there.
The reply to all of this was simply to the "don't connect to it if you don't trust it" - I guess that's all the privacy nut could argue with. And here we get to the topic of this rant. The almighty rebuttal "there's more to it than that!1! HTTPS doesn't require trust anymore!1!"
... An encrypted connection to a website meaning that you could connect to just about any hostile network. Are you fucking retarded? Ever heard of SSL stripping? Yeah HSTS solves that but only a handful of websites use it and it doesn't scale up properly, since it's pretty much a hardcoded list in web browsers. And you know what? Yes "there's more to it"! There's more to networking than just web browsing. There's 65 THOUSAND ports available on both TCP and UDP, and there you go narrow your understanding of networking to just 2 of them - 80 and 443. Yes there's a lot more to it. But not exactly the kind of thing you're arguing about.
Enjoy your cheap-ass Xiaomeme phone where the "phone" part means phoning home to China, and raging about the Google apps on there. Then try to solve problems that aren't actually problems and pretty vital network components, just because it's an identifier.
</rant>
P.S. I do care a lot about privacy. My web and mail servers for example do not know where my visitors are coming from. All they see is some reverse proxies that they think is the whole internet. So yes I care about my own and others' privacy. But you know.. I'm old-fashioned. I like to solve problems with actual solutions.10 -
Inspired by @NoMad. My philosophy is that technology is a means to and ends. We’re a tool oriented species. As it relates to software and hardware, they should be your means to achieve your ends without you needing to think. Think of riding a bicycle or driving a car. You aren’t particularly conscious of them - you just adjust input based on heuristics and reflex - while your doing the activity.
For a long time Software has been horrendously bad at this. There is almost always some setup involved; you need to front-load a plan to get to your ends. Funny enough we’re in the good days now. In the early days of GUI you did have to switch modes to achieve different things until input peripherals got better.
I’ve been using windows from 95 and to this day, though it’s gotten better it’s not trivial to setup an all in one printer and scan a document - just yesterday I had to walk my mother through it and she’s somewhat proficient. Also when things break it’s usually nightmare to fix, which is why fresh installing it periodically is s meme to this day. MS still goes to great lengths with their UI so that most people can still get most of their daily stuff done without a manual.
I started Linux in University when I was offered an intro course on the shell. I’ve been using it professionally ever since. While it’s good at making you feel powerful, it requires intricate knowledge to achieve most things. Things almost never go smoothly no matter how much practice you have, especially if you need to compile tools from source. It also has very little in the ways of safe guards to prevent you from hurting yourself. Sure you might be able to fix it if you press harder but it’s less stress to just fresh install. There is also nothing, NOTHING more frustrating than following documentation to the T and it just doesn’t work! It is my day job to help companies with exactly this. Can’t really give an honest impression of the GUI ux as the distros have varying schools of thoughts with their desktop environments. Even The popular one Ubuntu did weird things for a while. In my humble opinion, *nix is better at powering the internet than being a home computer your grandma can use.
Now after being in the thick of things, priorities change and you really just want to get things done. In 2015 I made the choice to go Mac. It has been one of my more interesting experiences. Honestly, I wish more distros would adopt its philosophy. Elementary only adopted the dock. It’s just so intuitive. How do you install an application? You tap the installer, a box will pop up then you drag the icon to the application folder (in the same box) boom you are done. No setup wizards. How to uninstall? Drag icon from app folder to trash can. Boom done. How to open your app? Tap launch pad and you see all your apps alphabetically just click the one you want. You can keep your frequent ones on the dock. Settings is just another app in launchpad and everything is well labeled. You can even use your printers scanner without digging through menus. You might have issues with finder if your used to windows though and the approach to maximizing and minimizing windows will also get you for a while.
When my Galaxy 4 died I gave iPhone a chance with the SE. I can tell you that for most use cases, there is no discernible difference between iOS and modern android outside of a few fringe features. What struck me though was the power of an ecosystem. My Mac and iPhone just work well together. If they are on the same network they just sync in the background - you need to opt in. My internet went down, my iMac saw that my iPhone had 4g and gave me the option to connect. One click your up. Similar process with s droid would be multi step. You have airdrop which just allows you to send files to another Apple device near you with a tap without you even caring what mechanism it’s using. After google bricked my onHub router I opted to get Apples airport series. They are mostly interchangeable and your Mac and iOS device have a native way to configure it without you needing to mess with connecting to it yourself and blah. Setup WiFi on one device, all your other Apple devices have it. Lots of other cool stuff happen as you add more Apple devices. My wife now as a MacBook, an IPad s d the IPhone 8. She’s been windows android her life but the transition has been sublime. With family sharing any software purchase works for all of us, and not just apples stuff like iCloud and music, everything.
Hate Apple all you want but they get the core tenet that technology should just work without you thinking. That’s why they are the most valued company in the world12 -
I think I'm having a "return to monkey" phase.
What the fuck are we doing?
Free VPN's, free cloud storage, smartphones and stupid telemetry/uSaGE aNaLYtiCs, password managers, social media, content farms, cheap wifi enabled smart home and 'intelligent' cars.
I'm starting to hate it all.
Look at how many people (including myself, sadly) is glued to their fucking datahoarding multimedia shitdevices (known as 'smartphones'). While sitting in a room filled with every fucking small appliance that needs an app, wifi and phones home to who the fuck knows.
Even my fucking dishwasher has an app and wifi enabled so I can start the dishwasher outside the wifi network.
How the fuck did we get here?20 -
Fuck, give it maybe a decade more and we'll have the deepfakes drama, but on a whole another level, haven't seen as much development in countering all those technologies yet either (the only recent one has been iirc trying to feed a neural network with fake video, to try to spot small details, but that hasn't seen much success, even with deepfakes)
most terrifying application would be to imitate e.g. a president and send that to another country as a threat and vice versa or to fake video footage as evidence, admittedly both very low chance, but still a possibility, seeing how e.g. some court cases have been based almost exclusively around video footage or how north-korea treats any outside media.
https://youtube.com/watch/... 4
4 -
The "stochastic parrot" explanation really grinds my gears because it seems to me just to be a lazy rephrasing of the chinese room argument.
The man in the machine doesn't need to understand chinese. His understanding or lack thereof is completely immaterial to whether the program he is *executing* understands chinese.
It's a way of intellectually laundering, or hiding, the ambiguity underlying a person's inability to distinguish the process of understanding from the mechanism that does the understanding.
The recent arguments that some elements of relativity actually explain our inability to prove or dissect consciousness in a phenomenological context, especially with regards to outside observers (hence the reference to relativity), but I'm glossing over it horribly and probably wildly misunderstanding some aspects. I digress.
It is to say, we are not our brains. We are the *processes* running on the *wetware of our brains*.
This view is consistent with the understanding that there are two types of relations in language, words as they relate to real world objects, and words as they relate to each other. ChatGPT et al, have a model of the world only inasmuch as words-as-they-relate-to-eachother carry some information about the world as a model.
It is to say while we may find some correlates of the mind in the hardware of the brain, more substrate than direct mechanism, it is possible language itself, executed on this medium, acts a scaffold for a broader rich internal representation.
Anyone arguing that these LLMs can't have a mind because they are one-off input-output functions, doesn't stop to think through the implications of their argument: do people with dementia have agency, and sentience?
This is almost certain, even if they forgot what they were doing or thinking about five seconds ago. So agency and sentience, while enhanced by memory, are not reliant on memory as a requirement.
It turns out there is much more information about the world, contained in our written text, than just the surface level relationships. There is a rich dynamic level of entropy buried deep in it, and the training of these models is what is apparently allowing them to tap into this representation in order to do what many of us accurately see as forming internal simulations, even if the ultimate output of that is one character or token at a time, laundering the ultimate series of calculations necessary for said internal simulations across the statistical generation of just one output token or character at a time.
And much as we won't find consciousness by examining a single picture of a brain in action, even if we track it down to single neurons firing, neither will we find consciousness anywhere we look, not even in the single weighted values of a LLMs individual network nodes.
I suspect this will remain true, long past the day a language model or other model merges that can do talk and do everything a human do intelligence-wise.29 -
!rant
How to self host a website?
Seriously, through many guides out there, I was never been able to see my site (hosted on a raspberrypi with nginx) outside the local network. I always tried to link my router to no-ip without success outside my localhost, the port 80 is already open for the raspberrypi. I live in Italy, can it be that the local ISPs obstacle the creation of such homemade website hosts?39 -
1) Never be afraid to ask questions.
There are so many instances of situations where assumptions have been made that shouldn’t have been made, resulting in an oversight that could have been rectified earlier in a process and wasn’t.
Just because no one’s asking a question doesn’t mean you’re the only person who has it.
That being said, it’s really important to figure out how to ask questions. Provide enough context so that the audience for your question understands what you’re really asking. If you’re trying to troubleshoot a problem, list out the steps you’ve already tested and what those outcomes were.
2) When you’ve learned something, try to write about it. Try to break it down as though you were explaining it to a child. It’s through breaking down a concept into its most simple terms that you really know that you understand it.
3) Don’t feel like you have to code *all of the time*. Just because this is what you’re doing for a living doesn’t mean that you have to make it your life. Burnout is real, and it happens a lot faster if it’s all you do.
4) Find hobbies outside of tech!
5) Network. There are a number of great communities. I volunteer for and am a member of Virtual Coffee, and can vouch for that community being particularly friendly and approachable.
6) Don’t let a company pay you less than industry standard and convince you that they’re doing you the favor of employing you.
7) Negotiate salary. Always.
8) If you’re a career transitioner, don’t be afraid to talk about your previous work and how it gave you experience that you can use in programming. There’s a whole lot of jobs that require time management, multi-tasking, critical thinking, etc. Those skills are relevant no matter where you got them.
9) If it takes a while for you to get a gig, it’s not necessarily a reflection on you or your abilities.
10) Despite what some people would say, coding’s not for everyone. Don’t feel like you have to continue down a road just because you started walking down it. Life’s not a straight path. -
We have 7000+ employees and I'm the only one who do dev work. IT had special meetings how to handle my requests. In the end they told me to buy a separate laptop and keep it outside the network. Suits me fine :)4
-
You think NORMAL updates are slow?
I have to install these twice, once from the desktop then again at boot-time!
(gift desktop for my uncle, but we're almost out of bandwidth for the LAN network for the month... had to go sit outside (yes, OUTSIDE) a McD's so I could have both power and network access. It was 2° outside.) 7
7 -
1) Learning little to nothing useful in formal post-secondary and wasting tons of time and money just to have pain and suffering.
"Let's talk about hardware disc sectors divisions in the database course, rather than most of you might find useful for industry."
"Lemme grade based on regurgitating my exact definitions of things, later I'll talk about historical failed network protocols, that have little to no relevance/importance because they fucking lost and we don't use them. Practical networking information? Nah."
"Back in the day we used to put a cup of water on top of our desktops, and if it started to shake a lot that's how you'd know your operating system was working real hard and 'thrashing' "
"Is like differentiation but is like cat looking at crystal ball"
"Not all husbands beat their wives, but statistically...." (this one was confusing and awkward to the point that the memory is mostly dropped)
Streams & lambdas in java, were a few slides in a powerpoint & not really tested. Turns out industry loves 'em.
2) Landed my first student job and get shoved on an old legacy project nobody wants to touch. Am isolated and not being taught or helped much, do poorly. Boss gets pissed at me and is unpleasant to work with and get help from. Gets to the point where I start to wonder if he starts to try and create a show of how much of a nuisance I am. He meddle with some logo I'm fixing, getting fussy about individual pixels and shades, and makes a big deal of knowing how to use GIMP and how he's sitting with me micromanaging. Monthly one on one's were uncomfortable and had him metaphorically jerking off about his lifestory career wise.
But I think I learned in code monkey industry, you gotta be capable of learning and making things happen with effectively no help at all. It's hard as fuck though.
3) Everytime I meet an asshole who knows more and accomplish than I do (that's a lot of people) with higher TC than me (also a lot of people). I despair as I realize I might sound like that without realizing it.
4) Everytime I encounter one of my glaring gaps in my knowledge and I'm ashamed of the fact I have plenty of them. Cargo cult programming.
5) I can't do leetcode hards. Sometimes I suck at white board questions I haven't seen anything like before and anything similar to them before.
6) I also suck at some of the trivia questions in interviews. (Gosh I think I'd look that up in a search engine)
7) Mentorship is nigh non-existent. Gosh I'd love to be taught stuff so I'd know how to make technical design/architecture decisions and knowing tradeoffs between tech stack. So I can go beyond being a codemonkey.
8) Gave up and took an ok job outside of America rather than continuing to grind then try to interview into a high tier American company. Doubtful I'd ever manage to break in now, and TC would be sweet but am unsure if the rest would work out.
9) Assholes and trolls on stackoverflow, it's quite hard to ask questions sometimes it feels and now get closed, marked as dupe, or downvoted without explanation.3 -
I'm currently planning to set myselv up with some vps/dedicated server's for a project. What i plan to do to secure these servers is.
*Use centos 7
* Setup Wireguard and join all of the servers +1 client (my pc) to that network
*Disable SSH Access from outside that VPN
*Only allow RSA Key login to the Servers
*Install Cockpit for monitoring
*Intall docker/kubernetes for the applications i plan to run
What do you guys think of that as a baseline? Im not sure if my lower powered VPS (VPS M SSD from Contabo) will work as Kubernetes Nodes, does anyone have experience with that?
In general these Servers will be used for my projects and other fooling around.
If you guys have other suggestions for Securing/monitoring or other software i could put on to have more control without eating up to much of the Servers power, let me know :D12 -
lets just wait till the day before deploy to finally authorize api testing for users outside of the network - and then get super upset when we aren't adjusted, prepared, and tested in time for next-day deployment
-
*One Month Ago*
Project Manager: we have allocated these two workstations for you to extract data (set) from malicious files, they are off the network. I though would also prefer a seperate laptop for this project you can take this one (pointing towards the newish laptop on the table)
Me: (i declined his offer because i didn't wanted to carry two laptops everywhere) I'm going to use my own laptop, but I'll be using a sand box or virtual machine.
*Fast Forward to Today*
Accidentally ran a script outside the sandbox, which due to some unknown reasons ended up executing a bunch of malicious files I only realised my mistake when my antivirus started to go bonkers FML.
P.S. both of those PCs are now connected network because of me.
Fingers crossed2 -
The networking group at my day job, hooooooolly crap I have some unprintable words. But keeping it professional:
* Days to turn around simple firewall whitelisting requests
* Expecting other teams to know the network layout despite not sharing that information anywhere and going out of their way to not share it
* Adding bureaucracy in the form of separate Word doc forms despite having a ticketing system - for no justifiable reason
* Breaking production systems multiple times per month
* Calling in with problems that are clearly network related, being told it’s our systems, and then the problems magically go away even though they swear they didn’t touch anything
* Outright verifiable lies or vague non-answers when they’re not talking to someone at the director level or a vendor from an outside company on conference calls
* Worse packet loss and throughput on our LAN than my home ISP
Doing anything with these clowns is my single biggest source of stress right now. I can’t wait until we get a full SDN stack set up and then we won’t have to deal with them for day-to-day needs any longer.
My boss swears it’s better that we’re not managing the network directly, but I’m pretty sure my friend’s dog could be loosed into the data center to chew on fiber, and eventually the pairs would be connected in such a way as to improve performance.1 -
CAUTION: possibly NSFL
There was a war. We lived in a leftist camp inside an abandoned railway station. The only thing that could break the siege was BLA
[dream fragment lost]
So they lined us up. There were ten of us.
— Do you want the leftist future?
— No…, they made me say.
— Do you love capitalism?
— Yes…, they made me say.
— Ты готова присниться?, they asked my female comrade ("are you ready to come to our soldiers in their dreams to support them?")
— Yes.
— Ты готов расшибиться?, they asked me ("are you ready to work your ass off, dying in the process if necessary?". It also makes a perfect rhyme with the previous Russian sentence)
— Yes.
Then, they tied our hands and hung us onto a rack. They doused us with gasoline.
— Look. Czechoslovakia had Jan Palach. We have ten Jan Palachs now!
They set us on fire. I feel an unimaginable pain. I wake up for ten minutes.
When I fell asleep again, I found out I survived. But, my body underwent modifications: first, I now had a vinyl shell instead of my skin. Underneath it were raw muscles. Second, I no longer had vocal cords. I no longer had voice.
In this world, we were slaves ("Тяговые люди") ruled by BLA. There were no prisons. Instead, there were only two punishments: the "light" one and the "heavy" one. First one is your shell getting ripped off. You die in around 20 minutes of agonizing pain, like mink that is skinned alive in Chinese leather tanneries. But, compared to the second one, that was a slap on the wrist.
The "heavy" punishment was them injecting you with "The Ferment". Immediately, your mind is altered into total obedience. Then, your body begins to turn into corpse juice. To outside observers, you die in 30 days. But for you, it feels like forever, as time speeds up indefinitely, and you're drifting into endless sorrow. When you die, no one notices, as your shell is still there. But instead of you, there's now nothing but corpse juice inside.
I now worked in some location that resembled Duke Nukem 3D's first map. My job was to remove those plastic shells. I had no bottom — it was replaced with a concrete cube that felt pain just like damaged tooth enamel does. An endless queue of shells moved in front of me. I had to remove their shells, to peel them off like vinyl.
Some people were alive underneath. They still had their skin. They thanked me, smile at me and wander away.
Some of them were alive, but had no skin. That means I was the one to execute a "light" punishment on them.
Some of them weren't there. I pop the shell open, and it deflates as corpse juice pours out.
One of my previous dreams was the following:
"— We arrange surgeries when in-person interventions are _not recommended_.
— So…, — I press the pause button on the handrail.
— The perfect maiden. Inside a plastic shell. 80 years old underneath."
Now I understand it. The first speaker was a BLA researcher. "I" was an investor. The "perfect maiden" was me, but way in the future from my today's dream. It all fits together.
Now, here's the discovered part of kiki universe so far:
- rotten meat house
- swine gray gel battleground
- horizontal elevators network
- united paper island
- baseball bat nightclub
- anxiety-inducing multidimensional pizzeria
- NEW! BLA headquarters
- NEW! demilitarized burning ground abandoned train station
- NEW! Duke Nukem 3D people skinning ground9 -
Has hacking become a hobby for script-kiddies?
I have been thinking about this for a while know, I went to a class at Stanford last summer to learn penetration-testing. Keep in mind that the class was supposed to be advanced as we all knew the basics already. When I got there I was aggravated by the course as the whole course was using kali linux and the applications that come with it.
After the course was done and I washed off the gross feeling of using other peoples tools, I went online to try to learn some tricks about pen-testing outside of kali-linux tools. To my chagrin, I found that almost 90% of documentation from senior pen-testers were discussing tools like "aircrack-ng" or "burp-suite".
Now I know that the really good pen-testers use their own code and tools but my question is has hacking become a script kiddie hobby or am I thinking about the tools the wrong way?
It sounds very interesting to learn https and network exploits but it takes the fun out of it if the only documentation tells me to use tools.3 -
Future01
Click, click, click, click.
Tap, tap, tap, tap.
Swipe, swipe, swipe, swipe,.
Scroll, scroll, scroll, scroll.
I’m tired of living on popularity driven planet among animals, where number of clicks on likes, subscriptions and links are worth more than iq, education and experience.
Let’s face it - AI is showing us traffic driven recommendations that sucks. If you’re hooked up to social network and can’t disconnect from it you’re half way to matrix. You probably also disagree with me cause you’re serotonin junkie. You can’t stop like you can’t stop eating for a day. Bubble have you in your hands and whatever you do you probably won’t wake up. To be honest most of us won’t. It’s already to late.
I’m waiting for meta so they can put you in virtual world where you can have what you want and at the same time own nothing. They will put you in some small empty space and give you something to eat how many times you want so you can feel safe and click, tap, swipe, scroll more so they can own this planet.
You will be living only to deliver corporate metadata and you will be happy, cause they will make you happy with giving you emotions that you want to feel at exact moment.
If you get out, you won’t be able to interact cause you won’t know how to behave, you will become wild animal.
By going out you will break the law, cause outside world will be long gone. To move to bar or visit family you will travel with autonomous vehicle that have screens instead of windows.
Eventually you stop going to bar cause it’s unhealthy, you stop going outside cause there’s deadly virus and you can die.
They will take you last thing later with birth control so you can have baby whenever you want and with who you want as long as both parties agree by signing baby nft contract, you don’t have to take care of your baby and be pregnant cause it will be robotized, you will see your baby in meta. You will think you feel it using robot hands.
You will never meet your baby in person.
That’s how matrix will start. We’re half way.5 -
Kubernetes question:
So far I've created two pods, mongo & Go
Exposed those pods using services
Their IP is 10.x.x.x and accessible from my machine only (virtual lan I'm guessing only known to host), but my machine's network ip is 192.x.x.x therefore, not accessible from outside world and to do so I need to put nginx in front to receive requests and route them internally.
Is there a way in kubernetes to make it work like nginx in terms of:
Kubernetes listen to port 80 (for example) route based on received url. As you know in enginx we define a server block with server domain_name.tld
Anything similar in kubernetes? I've cheked ingress-nginx controller, and also saw LoadBalancer but that requires a cloud provider.
If anyone can also give an example it would be great, so far examples I checked ended up screwing my setup and had to reset kubectl to get things back working18 -
All of them lol
I'm working on my own streaming service. Yes, I know plex a thing but I've had issues with it and I'm honestly doing this more for the fun of it.
When it's ready, I'll run two versions. One that'll use to access my stuff outside my network, Plex style and one that hosts old movies that are now in the public domain. I'll use that one for demonstrative purposes4 -
is being a tech/dev person, a dead end job?
i have been thinking about this for sometime. as a dev, we can progress into senior dev, then tech lead, then staff engineer probably. but that is that. for a tech person :
1. their salary levels are defined. for eg, a junior may earn $10k pm , and the highest tech guy (say staff engineer) will earn $100k pm, but everyone's salary will be spread over this range only, in different slots.
2. some companies give stocks and bonuses , but most of the time that too is fixed to say 30% of the annual salary at max.
3. its a low risk job as a min of x number of tech folks are always required for their tech product to work properly. plus these folks are majorly with similar skills, so 2 react guys can be reduced to 1 but not because of incompetency .
4. even if people are incompetent, our domain is friendly and more like a community learning stuff. we share our knowledge in public domain and try to make things easy to learn for other folks inside and outside the office. this is probably a bad thing too
compare this to businesses , management and sales they have different:
1. thier career progression : saleman > sales team manager> branch manager > multiple branch manager(director) > multiple zones/state manager (president) > multiple countries/ company manager (cxo)
2. their salaries are comission based. they get a commission in the number of sales they get, later theybget comission in the sales of their team> their branch > their zone and finally in company's total revenue. this leads to very meagre number in salaries, but a very major and mostly consistent and handsome number in commission. that is why their salaries ranges from $2k pm to $2-$3millions per month.
3. in sales/management , their is a always a room for optimisation . if a guy is selling less products, than another guy, he could be fired and leads could be given to other/new person. managers can optimise the cost/expenses chain and help company generate wider profits. overall everyone is running for (a) to get an incentive and (b) to dodge their boss's axe.
4. this makes it a cut-throat and a network-first domain. people are arrogant and selfish, and have their own special tricks and tactics to ensure their value.
as a manager , you don't go around sharing the stories on how you got apple to partner with foxconn for every iphone manufacturing, you just enjoy the big fat bonus check and awe of inspiration that your junior interns make.
this sound a little bad , but on the contrary , this involves being a people person and a social animal. i remember one example from the office web series, where different sales people would have different strategies for getting a business: Michael would go wild, Stanley would connect with people of his race, and Phyllis would dress up like a client's wife.
in real life too, i have seen people using various social cues to get business. the guy from whom we bought our car, he was so friendly with my dad, i once thought that they are some long lost brothers.
this makes me wonder : are sales/mgmt people being better at being entrepreneur and human beings than we devs?
in terms of ethics, i don't think that people who are defining their life around comissions and cut throat races to be friendly or supportive beings. but at the same time, they would be connecting with people and their real problems, so they might become more helpful than their friends/relatives and other "good people" ?
Additionally, the skills of sales/mgmt translate directly to entrepreneurship, so every good salesman/manager is a billionaire in making. whereas we devs are just being peas in a pod , debating on next big npm package and trying to manage taxes on our already meagre , "consistent" income :/
mann i want some people skills like these guys10 -
Disclaimer: Technically it's not "our" stack, but we have to use it so....
A webapp we built runs inside the company's network we built it for. Their IT are windows lovers, so everything has to run on Windows servers, even the tablets which are used to access said web app need to have windows.
Their company network isn't accessable from the outside world, so we have access via VPN to get into their network. But this isn't enough to access that shitty windows server our software runs on. After that VPN, you have to connect to a different VPN to which you can only connect to while you're inside the company's network. Then you have access to two servers, one the application is running on and one, well to see if you're changes were deployed correctly because the production server doesn't have a browser on it other than shitty internet explorer 8.
The only way to connect to the server is using RDP. Not even samba or so. To deploy the changes we made to our app, you need to copy paste the files from your local machine to the server. And don't get me started on running mssql migration with the shitty mssql console 😤😤
Why would anyone who isn't a complete idiot use Windows for servers or mssql in the first place????2 -
Have you ever considered switching to IT support/help desk?
I mean, sometimes I try to analyze my own situation from a 3rd person perspective and I realize I could have a pretty much stressless job with still enough money to live a normal life.
I have a BSc and MSc(soon to have) in CS, with focus on AI/ML. I've always been a geek with a problem solving attitude, that's why I got into computers in the first place. And now I'm pondering if I should just try an IT Support position, it's the kind of things I used to do as a teenager when a classmate had a network/computer problem, it doesn't even feel like a job to me. I could call it a day, get home at 5/6pm, and spend time on my personal projects (software, infosec) with a fresh mind, going to bed (and sleep) knowing that the next day would be a nice one. No clients wanting a new feature that you gotta implement and push on a production server friday afternoon because your ceo(who is also a pseudo proj manager) just said:"Yes, we can", while you watch the technical debt rising like amazon's stocks.
Maybe this is just the burnout talking, I don't know. Maybe I should just try being a software engineer outside of Uni in the first place, and only then start pondering.
Maybe a sysadmin position...
Have a nice day12 -
The most stressful day of month.
I need to put hours into hour counting programs so computer can analyze those hours using deep learning algorithms and pay me a wage I don't deserve.
Each program work differently.
One of it works inside the local company network.
Other one I need to connect outside from company network.
In all of them I can't make mistake or I need to write to someone to fix my mistakes.
One of this programs use java applet, other is simple php website.
One of them blocks row in calendar when I click so when I login again and click I can't edit this row because it's locked by me who is editing this row.
One of them is requesting me to provide my work in minutes.
I need to follow strict procedures to report any holidays or national holidays that I need first figure out when they happen.
Wish me luck.1 -
I want to do ssh is from outside the network. But I'm unable to do it. Very much frustrated. Has anyone tried it successfully?7
-
Though I’ve seen devices like the following I’ve only ever seen them used for horrible purposes.
I was envisioning facility control being made capable by the use of a larger tablet device or tablet computer. The device would have no internet connection. It would not attach to the outside world at all.
It would not receive non manual software updates
It could view all air flow, temperature, lights, locks, electrical outlets, power draw, water usage, heaters, air conditioners, computer statins etc
And control and report statistics on them all.
Impractical you people said last time. But I would say cool if the device is kept super secure . That being said who knows how to do that since everything sucks once someone who knows what they’re doing has physical access lol
Personally all I don’t know how to break into is smart phones
Comps I could always figure out even if they had disk encryption given enough time.
The only reason phones are hard is you’re limited to network attacks and the boot loader is on the chip page.
Cause in the end a computer is just it’s hard drive in terms of security lol1 -
Not a rant more like a question
Hello devRant,
I am currently planning to purchase a small home server + media client (with Kodi).
A small Linux Distro running the Hometheateroftware Kodi will run on the media clients (Odroid C2). The control is then over an app over the local network. The database of Kodi should be on the server in the form of a MySQL database. The movies, pictures, music are also streamed by the server (max. 2 simultaneously) via SMB (simplest variant). In addition, the server is to be accessible to the outside via a web interface to act as a cloud (maybe nextcloud). The whole should be optimized for stability and longevity. In addition, a small GitLab CE instance will probably run on the server. Do you have any comments or objections? The fact that I only take 2x ne 2 TB hard drive has the simple reason that I currently have no need for more space. Sometimes it happens to me that I forget completely obvious things :D -
My network is somehow fucked up. VPN Client on laptop to my workplace is not connecting via wifi but instead connects when my phone creates a hotspot, while the phone is connected to the same router via wifi? Second laptop this occurrence.
When the work laptop is outside of VPN but connected to the router with wifi, about 50% of web pages are not reachable, same with my own PC and another laptop. Didn't touch my router in ages. Nice fucking conditions for wfh.11 -
Release team was recently disbanded, they handed off release management to the Dev scrum masters. The other day we had a weekly release for a product that uses a network service that is shared with other products. The devs didn’t know how to set up the build correctly. They had a purge setting on that removed the network service for products that weren’t being touched in the release. The end result was that the other products were inaccessible for an hour and a half! They eventually found their mistake, but we were lucky that it was outside of core business hours.
These devs need to learn how to work the build tools! Or maybe we should rethink getting rid of the release team. -
What is the best way to install iOS app for employees in a company?
Disclaimer, I'm no iOS developer.
In 2019 my boss asked if I could make a small iOS app. 3 forms which will have CRUD operations. I did it because I wanted to learn iOS development. The company got an Apple Developer Account and it finished the project within the week. The app can be used only from work's wifi, so if you try to use it outside that network will not work.
The issue is license. When I install the app from my XCode to one of the employees' iPhone, the app will work for 1 year (if I have paid for Developer Account). Also every time I make an update, the employee have to come to me with the iPhone and I have to install it directly.
Yesterday I submitted the app for Testing using TestFlight. The app updates automatically, but today I got notification that the "Submission for testing is rejected", because the tester could not connect with the server.
My question is, How do you install iOS apps for your work employees? I do not want to get Enterprise account because that will cost.5 -
Help
how to stop a Android phone from changing IPs
hey guys
Don't know why, sometimes my Android server changes IPs (without restart), that fucks the exit of services....
Like, don't know why, http always works even when IP changes
but WebDav stops working.... I mean, I can use inside the network but I want to access it from the outside.
Thanks8 -
Guys what do you use to connect to a linux machine in a local network? I'm aware of the existence of VNC however I don't want to go outside the lan over the internet and back in to view the desktop , i want simply to enter 192.168.1.10 and access it within my lan...8
-
I still remember the pit in my stomach when I realized I’d been scammed. Months of careful saving, research, and planning vanished in an instant along with my Bitcoin, It started innocently enough. I was introduced to what seemed like a reputable cryptocurrency trading platform via social media. The website was polished, the support team was responsive, and their experts guided me every step of the way. Then, the platform vanished overnight. My wallet emptied. My Bitcoin Gone. I was devastated. My bank couldn’t help, they said it was outside their jurisdiction. Law enforcement was sympathetic but slow-moving. I began to accept the bitter truth that I had been defrauded. Then I came across Dexdert Net Recovery while researching online recovery services. At first, I was skeptical after all, hadn’t I just been scammed , I was desperate, From the beginning, Dexdert’s Net Recovery approach was different. They didn’t promise miracles or instant results. Instead, they provided a transparent breakdown of their investigative process. They explained how they use blockchain forensics, deep-web tracking tools, and a global network of legal and cybersecurity experts to trace stolen digital assets. They asked for every detail: wallet addresses, transaction IDs, email trails, and screenshots of conversations with the scammers. Within a few days, they traced the Bitcoin I had transferred. It had been split and rerouted through multiple wallets in classic laundering techniques. After several weeks of persistent efforts, negotiations, and verification, I received the email I never thought I would see. We've recovered your assets. And sure enough, my Bitcoin had been returned to a secure wallet under my control. It wasn’t just about the money. It was about justice. About reclaiming what was mine. If you’ve been a victim of crypto fraud, don’t suffer in silence. There are professionals out there who can help. For me, that was Dexdert. And they gave me a second chance.
REACH OUT FOR HELP FROM THE BEST RECOVERY SERVICE:
WhatsApp: ( +1 859 609 4156)2 -
App Review – Zomato 2.0
Some apps are as essential as oxygen by example of https://apps.apple.com/us/app/... . Zomato, for sure, is one of them. If you love to eat outside and you’re not living in a cave, chances are that you’ve already gone through Zomato on the web or used one of their mobile apps. If not – Zomato is the place where you can locate eating joints, scan through their menus, check for home delivery numbers and a lot more than that. If you are diabetic you keep sweets in your pocket, similarly Zomato is something every food-loving person needs to keep in their mobile phones(I agree how PR-ish that sounds but it’s true).
Zomato had recently integrated social features on its website. That was followed by the much needed overhaul of their mobile apps. They’ve also updated their iOS app recently and I decided to give it a shot. Zomato 2.0 on the iPhone is super slick to say the least. The redesign brings a lot of character to the app. The Zomato app is now much more smoother, cleaner and powerful. The added social functionality adds more value to the app.
Design and Features
The 2.0 update completely changes the entire look and feel of the app. Everything from the app’s start screen to restaurant details has been changed. The default menu lets you explore and search eating places. Now there are icons for top 25 restaurants, reviews, favorites and more. The icons have been perfectly placed and it’s very easy to spot what you’re looking for.
Everything is just right. The app is highly responsive and there’s hardly any lag. If any, it will depend on your internet connectivity. Browsing menus is still a breeze and I personally love the way you can toggle between information, menu, photos and last but not the least, the reviews. Everything placed just perfectly to help you make that ultimate make or break decision – to eat or order from here or not?
Social
Everything is getting social. Even the next door Dolly-beauty-parlor apps are getting more social now. Zomato just integrated its social features on the web recently and they’re now a part of their mobile apps. On the iPhone app you need to login to access these social features. There’s a Top Foodies leaderboard that could prove to be a crucial game mechanic for the app. Browsing users’ profiles allows you to follow users. The profile pages tie up a user’s reviews and followers. This is all pretty neat and a part of a major plan at Zomato to take over the world.
With lists, network, user reviews etc. there’s a lot more to the app. I’m hearing that there’s still a lot more to come when it comes to social features on the Zomato iPhone app. I better start following up with people and posting reviews. This just kicked Foursquare where it hurts the most. And with that I’ve lost the little amount of motivation I had to check-in to places on Foursquare1
