Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "reversed"
-
I really hate Apple for popularizing reversed scrolling on touchpads. It doesn't make any fucking sense.16
-
What's the difference between a wasp and single loose hair?
Apparently none till the wasp stings :/
Yesterday I thought I had a loose hair on my neck.. ok, I shrug it off.. later again the creepy feeling.. shrugs off..
I continue to work, sumberged in code, wanting to find the fucker (bug, not the wasp/hair).. lean in to the monitor... 10 cents away from the screen... Ok, maybe that's it! Feels the hair on my back, near shoulderblades again... shrugging again more violently to get it further down to fall out.. nothing.. ok, got the bug, threw myslef back in the chair with substential force & BAAAAM!!! Motherfucking hair bit me!! O.o
I scream in horror & on top of the lungs (it was late, after work hours so I didn't expect anyone else still at the office) PROKLETA PRASICA (roughly translated to goddamn female swine).. I previously saw some green bug flying around the office and I thought that nasty thing bit me (didn't know they bite soo, much more horror for me).. O.o
Anyhow, I jump up from the computer and see my coworker looking at me all baffled.. I proceed to franticly take of my headphones and hoodie..thinking about wtf should I do now, I cannot get undressed in front of him (not for my sake, bra is the same as top of the bathing suit for me, but still..I don't want anyone suing me for impropper behaviour of undreasing in front of coworkers..), how the fuck should I get to the toilet?! O.o
C: Are you ok?!
M: Um.. sth bit me..wtf?!
C: There was a wasp flying around somewhere some time ago.. are you alergic?!
M: um..not sure, I don't think so..we'll see soon..
I proceed to the WC, to take off tshirt & check/kill off the fucker.. on my way there (walking funny to not press the hair to my body again) I got another surprise, another coworker was working late..
C2: Are you ok?! O.o
M: yeah, sth bit me, probably a wasp..
Ok, finally on the loo..ok, do not lock self in in case it escapes and you need help.. don't even shut the door. Check.. standing between the doors I contemplate on how the fuck should I take my tshirt off without angering the fucker even more and getting bitten again.. O.O
I lifted the tshirt up my back to let it out.. nope, not there..the creepy felling of buzzing around between my shoulder blades continues.. crap.. what to do?!
I stood there & contemplated the task.. ok, roll up the tshirt to the shoulder blades, not against the body (duh) to prevent further stings..tighten the fabric, so it cannot escape, quickly remove the band from the body.. done..reversed the tshirt and straightened it.. bzzz... Fucker fell somewhere.. Dafaq?! Was it really just a wasp?! If yes, no problem...but what if coworker was wrong and I got bitten by that nasty green whateveritsname bug?! Eeeeewwww! Is it poisonous? Gotta find it & kill it for good.. waited a bit, than saw a goddamn wasp crawl from under the toilet.. wasp!! Yess!! Stopm stomp fucker!!
I get dressed & go back to my desk..
C: Did you terminate it?!
M: Yup, fucker went on a toilet paper trip down the drain!!
I sit down, starting to get my headphones back on and proceed to work.., but before I could, one last gem:
C: CTO would say, thank god it didn't sting you in your finger cuz you wouldn't be able to type anymore..
M: O.O so true hahhahahaaa
Disclaimer - I like animals, but I freakking hate wasps..especially if they get under my tshirt to sting.. :/7 -
I reversed engineered the network protocol for a game.
I uploaded the source code to GitHub and made a post on UC Forums.
I kept getting bombarded with messages from the same person, it went something like this:
Him: "I can't get this hack to work, pls send finish hack, thanks"
Me: "First of all this is not a complete hack. You actually need to know how to code to use this library."
Guy: "Ok, can u help me make hack for game?"
To keep this short, I basically told him:
"No. Look through the code, learn it, use what you learned."
Couple of hours later he replied:
"Ok. I look through code but don't know how work. Send me code pls."
From the kindness of my heart I made a extremely simplified wrapper for the already simple code and sent him the project files.
He replies with: "Thank for hack, I not able make it work. I build I try inject game but no work. How to run dll file."
At that point I gave up...3 -
I pranked my friends ex, nothing bad, just fun. First i screen shorted is desktop, flipped it and made it his new desktop. Then flipped the resolution, so my upsideiwn bf was cool. Lastly I change his mouse behavior, I set it for reversed.
Fun right? A typical person might get a lil pussy and have to fix it. Some might even fix it themselves. Regardless have a lil chuckle.
He smashes the monitor and keyboard, left them, both in a pile.3 -
My professor asked my to write a method that recursively reversed() a linked list. Wrote an iterative version with the same name and called it in the recursive method. How I felt after she wrote 100 for my presentation...
 6
6 -
I was working on a very database heavy PHP app about six months ago. All database access was done directly, with hardcoded SQL strings.
I'd suggested switching over to an ORM during the upcoming major verson's rewrite, and FINALLY got approval to start integrating one.
The next week I'm told that I need to trash all the code I'd just written, since the decision to use an orm has been reversed.
The rationale? According to management, ORMs aren't "scalable enough for our application" and would "reduce developer productivity". I pointed out that we would be processing ~10 concurrent operations, maximum; I was told that the technically details didn't matter and the person I was working under had the final say because they'd worked at IBM, briefly, as an intern.
I stopped working on that project about two weeks later, thankfully.15 -
<supervisor>,
I would like to raise a concern of mine to your attention. I would urge you to inform <CIO> because I think he should know as well. In our recorded meeting this afternoon <bad_vendor> exposed another company’s credentials after failing to access our system, and proceeded to demo access into someone else’s system while exposing their client's sensitive data. Others noticed this as well. This is an alarming situation because not only did <bad_vendor> expose someones data to <us>, but to one of our vendors. While it is unlikely that <us> or <helpful_vendor> would abuse this situation, it could have easily been <us>’s data that was exposed to another company and their vendors had the situation been reversed. I understand we are all under tight deadlines and under a lot of stress — by no means am I trying to make waves — but nonetheless I felt compelled make light of this situation and felt in was echoed by <helpful_vendor> during the meeting as well.
Thank you8 -
When code is already working and reversed engineer to compare how efficient the current vs previous code. Now, blames self when prev code is an unorthodox code. ^_^1
-
A lot of PM-rants (for good reason) but how about a reversed one:
Lead Dev: "Yes, but do we really need a dev and staging server? Can't we just try it out and see if it works?"2 -
Can we please stop with the multiverse crap? Please, just stop.
I watched Deadpool & Wolverine yesterday and what a shitshow.
Logan was an excellent send-off to Wolverine. An excellent one.
It showed that Marvel can actually make good movies.
Why did Marvel have to ruin it?
The issue with multiverse plotlines is that nothing is ever serious, there are no stakes, nothing matters.
Anyone who dies can come back. Anything that happens can be reversed.
Just. Fucking. Stop.
One of my favourite franchises, Mortal Kombat, got ruined with MK1 multiverse story.
Played the game for about 30 minutes then deleted it. What a disappointment.
From now on, if a movie features multiverse or time travel crap, I ain't watching.15 -
Build a testbench they said, it'll be fun.
Guess who just reversed the direction of the pump.
Pumping into the reservoir from the reservoir isn't such a great idea.
😡 -
Frustration Rant!
Because old hardware means learning the hard way sometimes, I've had to purchase more goodies.
On my last update, I installed the rs232 shield which may have inadvertently been wired backwards for Tx/Rx from what im used to. I assume it is backwards to most db9 serial ports because most Arduino or other projects you would do with a pi have serial "in" connections like old routers and devices that would be "controlled" rather than the other way around. Anyway, according to a video on youtube showing a guy turning an old machine into an IRC client via raspberry pi, this shield may be swapped. That means that instead of interfacing with the old machine via a null modem crossover cable, I need a straight cable with male db9 on both ends. I unfortunately tried using the null modem crossover cable which was reversing the reversed pins all over again. I hope these next few days are more fruitful now that I've bought a straight cable and db9/25 adapter.
The good thing is that I managed to get the pi to recognize its new serial port. I also dusted off my DOS skills and my serial card in the 5150 seems to work.
I literally banged my head after nothing worked. Im hoping that the tx/ Rx is solved soon.
Oh and that AT to PS/2 adapter will allow me to use by IBM original Model M Keyboarf rather than the fun model F.
-
I love PHP, but...
the PHP API has been designed by crackpipe smoking cave trolls.
Every other function has its params completely reversed or in random order compared to similar functions.
Examples?
array_map, array_filter, property_exists, array_key_exists11 -
// Task: add one to the input number
// Sane people:
// print(int(input())+1)
// Me:
n = [*(reversed(bin(int(input()))[2:]))]
tmp = ""
for i in range(len(n)):
tmp = n[i]
tmp = "1" if tmp == "0" else "0"
n[i] = tmp
if tmp == "1":break
if tmp == "0":n+=["1"]
n = "".join(reversed(n))
n = int(n,2)
print(n)7 -
TL;DR; do your best all you like, strive to be the #1 if you want to, but do not expect to be appreciated for walking an extra mile of excellence. You can get burned for that.
They say verbalising it makes it less painful. So I guess I'll try to do just that. Because it still hurts, even though it happened many years ago.
I was about to finish college. As usual, the last year we have to prepare a project and demonstrate it at the end of the year. I worked. I worked hard. Many sleepless nights, many nerves burned. I was making an android app - StudentBuddy. It was supposed to alleviate students' organizational problems: finding the right building (city plans, maps, bus schedules and options/suggestions), the right auditorium (I used pictures of building evac plans with classes indexed on them; drawing the red line as the path to go to find the right room), having the schedule in-app, notifications, push-notifications (e.g. teacher posts "will be 15 minutes late" or "15:30 moved to aud. 326"), homework, etc. Looots of info, loooots of features. Definitely lots of time spent and heaps of new info learned along the way.
The architecture was simple. It was a server-side REST webapp and an Android app as a client. Plenty of entities, as the system had to cover a broad spectrum of features. Consequently, I had to spin up a large number of webmethods, implement them, write clients for them and keep them in-sync. Eventually, I decided to build an annotation processor that generates webmethods and clients automatically - I just had to write a template and define what I want generated. That worked PERFECTLY.
In the end, I spun up and implemented hundreds of webmethods. Most of them were used in the Android app (client) - to access and upsert entities, transition states, etc. Some of them I left as TBD for the future - for when the app gets the ADMIN module created. I still used those webmethods to populate the DB.
The day came when I had to demonstrate my creation. As always, there was a commission: some high-level folks from the college, some guests from businesses.
My turn to speak. Everything went great, as reversed. I present the problem, demonstrate the app, demonstrate the notifications, plans, etc. Then I describe at high level what the implementation is like and future development plans. They ask me questions - I answer them all.
I was sure I was going to get a 10 - the highest score. This was by far the most advanced project of all presented that day!
Other people do their demos. I wait to the end patiently to hear the results. Commission leaves the room. 10 minutes later someone comes in and calls my name. She walks me to the room where the judgement is made. Uh-oh, what could've possibly gone wrong...?
The leader is reading through my project's docs and I don't like the look on his face. He opens the last 7 pages where all the webmethods are listed, points them to me and asks:
LEAD: What is this??? Are all of these implemented? Are they all being used in the app?
ME: Yes, I have implemented all of them. Most of them are used in the app, others are there for future development - for when the ADMIN module is created
LEAD: But why are there so many of them? You can't possibly need them all!
ME: The scope of the application is huge. There are lots of entities, and more than half of the methods are but extended CRUD calls
LEAD: But there are so many of them! And you say you are not using them in your app
ME: Yes, I was using them manually to perform admin tasks, like creating all the entities with all the relations in order to populate the DB (FTR: it was perfectly OK to not have the app completed 100%. We were encouraged to build an MVP and have plans for future development)
LEAD: <shakes his head in disapproval>
LEAD: Okay, That will be all. you can return to the auditorium
In the end, I was not given the highest score, while some other, less advanced projects, were. I was so upset and confused I could not force myself to ask WHY.
I still carry this sore with me and it still hurts to remember. Also, I have learned a painful life lesson: do your best all you like, strive to be the #1 if you want to, but do not expect to be appreciated for walking an extra mile of excellence. You can get burned for that. -
Got hit up by a FANG recruiter on LinkedIn. Almost went for it, but then I remembered I'd have to spend 3 months prepping for it, since it's been 5 years since I've manually reversed a linked list, back when we did that for funsies in college...
Plus how do you tell your manager you're quitting to "prep" for an interview...and moreover, how do you go back and sheepishly tell them you didn't make it...
Like, that one simple LinkedIn message caused me to re-evaluate my life and seriously consider leaving my comfy job to do something insane like try to work at <insert FANG company here>. And I wasn't going to quit until I had made it.32 -
Learning C and just wrote a function to reverse chars in a char array (ex. "Hello" -> "olleH") but the array did not change.
It took me way to long to realize: I forgot to divide the length variable by two. So it reversed the array back everytime...6 -
This way of converting "string" to "s" (for example)
0) program reads the whole buffer, stores it as an array of instructions
1) program reverses the order of the instructions
2) parser makes standard token from an instruction ("asd" -> ASD)
3) parser2 assigns operands to instruction
4) parser 3 makes string from instruction token ?????
5) parser fucking 4 makeS A MUTABLE STRING INSTRUCTION
6) PARSER FIVE SUBSTITUES OPERANDS
7) AND THEN CUTS IT TO A REVERSED ARRAY OF COMMANDS
8) AND PUSHES IT UNTO THE STACK
WHAT1 -
My sleep cycles been reversed ! I am unable sleep all night, and end up sleeping throughout the day.2
-
So, it was kinda a reversed effect?
My parents didn't give me access to computer for a long time, the only option was to play games with my dad. I also didn't have a phone for a quite long. And, when I see what is happening today with the kids that get their first own phone/tablet at age of 4, I am really happy about it.
But, somehow, that made me really interested in what runs all the squares on the screen etc. When I convinced my parents to give me my first laptop — to play Minecraft with classmates — almost the first thing I did after installing the game was searching "how to make a website". I played with some shitty builders, then I discovered HTML (which was :o for me then). Small steps into PHP, then some JS. I really enjoyed it, but PHP gave me headache each time I wrote something bigger (I was writing a super spaghetti code then, I was inexperienced), so I thought of trying something else...
Minecraft plugins!
I fallen in love with Java.
And after that the real journey began.5 -
Live coding interviews basically make no sense.
It's even worse when you can't use an IDE.
Like, bro, what the fuck? You want me to write code in fucking notepad?
Alright then, I can play that game. It's so easy to memorize the algos and pass the test, yet that's not indicative of a good engineer.
I wonder if the roles were reversed, how good the interviewer would perform.11 -
Question about google crawler (?)
So, got a question, hopefully you have an answer.
I have a personal website that went up about 2 months ago that has a contact form.
Today I got two emails sent to me. This is the way I have coded it up.
But take a look at the name and message fields. I wonder if this is a google crawler submitting the form by any chance. I also got another email around the same time where the message and name field are reversed.
Anyone else experience this? 9
9 -
Aarrrgghhhhh!!! I am so fucking pissed off right now. It seems like I am paying for my sins in this life.
1. My cousins/relatives outcasted me after a little fault of mine. I used to think highly of them and respected them all my life and this how they acted on me.
Because of this, the entire family is boycotting my parents and they are pissed at me for getting them disowned.
2. My health is a mess. A toxic infection along with SAD creeping in due to less sun exposure. No matter how much I take care of myself, some shit shows up after periodically.
3. My wealth scene is as confusing as it can get. Not only I am unable to make up my mind on the finance strategy and execute it, but also frantically making silly decisions which is causing stress, confusion, and expenses.
4. That Narcissist bitch who abused me and destroyed my will to live is still stalking me after months and causing harassment. Only if the gender roles were reversed, the guy doing so would be in jail but fuck our legal system that biased towards women. This shit is causing me psychological distress.
5. Been away from work for few days due to sickness. I texted my talkative colleague whether she'd like to sync up and help me get upto the speed with updates. I listed 4 bullet points as agenda from my side. They were crisp short serving as pointers to remember. I even asked her to add her points if any.
Now she comes back saying that the way I send communication is it seems like she reports to me.
I have been praised time and again by countless people on my communication structure and soft skills. Never once I received such feedback in years.
I do accept it gracefully. However, I am unsure whether it is even a relevant feedback, since it's coming from someone who is literally struggling with communication with everyone (that she herself mentioned in the same thread).
Funnily she did say that when our manager departs, they'd make her report to me and I was like nah! that cannot happen.
She kept saying various great things about the company when I was new and slowly as I settled in and discovered the reality, her truth changed.
WTF!
Fucking annoying. I am all in for feedback of any kind but how should I figure which should be considered valid and which as invalid?
Life is nothing but a quicksand, you just keep sinking in irrespective of whether you try to get out or stay still. There is no external help or resources available.
So much mess to deal with.3 -
South Africa Release notes version v3.0.2
In 1994 SA underwent one of the biggest system upgrades since 1948. In this new rolling release since the system update called apartheid the system has been annexing resources, locking it down, making it closed source, closing it off community updates and from global updates and minimizing services across the board. On 27 April 1994, the new democratic system update was released with a new system monitor, release resources and balancing efficiency in the system. Though there were remnants of the old code in the system, it was being rewritten by a new generation of users, open source resources were established, giving users the right to choose among themselves how to grow the system , and how to better the experience for all.
In 1999 a new system monitor was created by the users, it wasnt as popular as the ground breaking Madiba release but it was a choice by the community to move forward and grow. The system was stable for a few years, new users were able to develop more on the system, making it more lucrative monetary wise. There were still remnants of the apartheid code but the new generation of developers worked with it making it there own, though they had not yet had admin rights to help change the system, they created a developer culture of their own. A new system resources balancer was introduced called BBEE, that allowed previous disadvantage users more admin rights to other system resources, helping the user base to grow. Though the balancer was biased, and flawed it has helped the system overall to grow and move forward. It has major holes in security and may flood some aspects of the system with more outdated software patches, users have kept it in its system releases until the resource balancer moved the system into a more stable position.
The next interim system monitor release was unexpected, a quiet release that most users did not contribute towards. The system monitor after that nearly brought the system down to a halt, as it was stealing resources from users, using resources for its own gain, and hasn't released any of it back to the system.
The latest user release has been stable. It has brought more interest from users from other countries, it had more monetary advantages than all other releases before. Though it still has flaws, it has tried to balance the system thus far.
Bug report as of 16 Feb 2018
*User experience has been unbalanced since the 1994 release, still leaving some users at a disadvantage.
*The three tier user base that the 1948 release established, creating three main user groups, created a hierarchy of users that are still in effect today, thought the 1994 release tried to balance it out, the user based reversed in its hierarchy, leaving the middle group of users where they were.
*System instability has been at an all time low, allowing users to disable each others accounts, effectively
killing" them off
*Though the infrastructure of the system has been upgraded to global standards ( in some aspects ) expansions are still at an all time low
*Rogue groups of users have been taking most of the infrastructure from established users
*Security services have been heightened among user groups though admins were still able to do as they pleased without being reprimanded
*Female users have been kicked off the system at an alarming rate, the security services have only kicked in recently, but the system admins and system monitor has not done anything about it yet
Bug fixes for a future release:
*Recreating the overall sysadmin team. Removing some admins and bringing others in
*Opening the system more globally to stabilize it more
*Removing and revamping the BBEE system, replacing it with more user documentation, equalizing the user base
*Giving more resources to users that were at a disadvantage during the first release
*Giving the middle group of users more support, documentation and advantages in the system, after removing the security protocols from the user base
*Giving new users who grew up with the post 1994 release more opportunities to help grow the system on a level playing field.
*Establishing the Madiba release principles more efficiently in the current system1 -
**Yoda conditions**
(also called Yoda notation) is a programming style where the two parts of an expression are reversed from the typical order in a conditional statement. 3
3 -
The age-old question between `DD/MM/YYYY` or `MM/DD/YYYY`.
After some shower thoughts, my new preference is `YYYY/MM/DD` for Americans and Lithuanians (only 2 that I know) it just looks like the year has been placed first, otherwise, they read it as normal. To everyone else, the date is reversed and therefore will be read in reverse leading to the same answer.
In addition, `YYYY/MM/DD/some-dated-file` as a file path works exceptionally well for storing files as it uses the least amount of repetition.10 -
!rant
Today I planned to work on my Java school project. I have clean install of windows 10 and I opened Netbeans as usual. No source tab, just history. HOW THE FUCK I CANNOT EDIT THE FUCKING CODE IN FUCKING IDE, I asked. I think let's uninstall this crap and install again then this shit happened. (It's good to have a second computer in my dorm, it's called redundance I guess) 6
6 -
Anyone here affected it going to be affected by Apples expansion of there template app rule?
More info:
https://techcrunch.com/2017/12/...
We are in the process of launching a service like this to our existing customers. Small stores who can't afford to have their own app developed for them.
This really throws a wrench into our product. If the decision is not reversed, we will likely have to abandoned half a year of work.1 -
Reversed a TSOP programmer software that only ran with Win2K (due buggy HID handling) and rewrote to run multi platform :)
-
On page 19 of the ethereum yellow paper: http://gavwood.com/paper.pdf it defines the address of a wallet as: A(pr) = Β[96...255](KEC(ECDSAPUBKEY(Pr))), which is the right most 160-bits of the Keccak hash of the public key generated by the private key.
If I expose the public key to the network, do I allow people to impersonate me and sign transactions even though they don't have Tr, Ts, or Tw? My understanding is no, that without those values you can't hash the transaction.
Subsequently, this leads me to wonder if the purpose of the address (besides identifying users) to obscure the public key so that the private key is at a less risk of being reversed? Or can the public key of any address be captured?
If the public key of any address can be identified on the network or off network (without actually being the owner of that key), how do you do that? Are there any resources on how to perform this that are computationally easy?1 -
The one thing I need, a "LATIN SMALL LETTER REVERSED C WITH DIAERESIS" doesn't seem to exist but "LATIN SMALL LETTER C WITH DIAERESIS" the one thing that I don't need, does D:
Like there's a god dang sideways u with an umlaut (or diaeresis I guess) but not a reversed c̈? pls4 -
Ok just wanna share things that got me stuck for hours on my recent project and their solution. I hope it’s gonna help someone.
To start with, when I was implementing svg to png, i set an image object’s source with a data url. Normally this is going to trigger the onload hook. However for some fucked up reason it never triggered. The solution is to use setAttribute function and then the hook will be triggered.
Second, you can get rounded triangle by setting stroke width and set stroke linejoin and line cap as round. But remember, if stroke width is 6, then it’s 3 inside and 3 outside.
Third, if you have a rotation of svg element, and later on you want to manually compute the rotated point’s position, it’s most likely some vanilla code is not going to work. You see, when you rotate for x degree, it is actually rotating -x degree. I’m not sure if it’s a bug of my code, but it’s there.
And now the worst thing: if you look up how transform on svg is performed, stackoverflow is going to tell you it’s by order. But that’s somehow not true for my project. If I do set transform to do translation then rotation, the order it was applied is actually reversed. It’s rotation first then translation, like ffs why? Who the fuck said it was in order? It’s clearly in reverse fucking order.
Ok last thing, you can scale svg around it’s center, but absolutely don’t do that because it’s gonna fuck up tanslation and rotation applied to this svg. If you need to scale, translate it first then scale it will be better.
Anyway just some things i encountered. I’m gonna stay away from svg for at least two months now1 -
Reversed network protocol didn't work, the sent messages weren't acknowledged or denied... basically no response from the server at all.
Turned out, after weeks of cluelessness, that I forgot to append PKCS#7 padding... -
Oh yeah ... Java is cool in an utterly sick way even that i can't seem to find a non-retarded built-in stack data structure
Call me a racist, but java.util.Stack has a removeIf() method in case you want to remove odd numbers:
import java.util.Stack;
public class App {
public static void main(String[] args) {
int arr[] = { 2, 4, 7, 11, 13, 16, 19 };
Stack<Integer> s = new Stack<Integer>();
for (int i = 0; i < arr.length; i++) {
s.push(arr[i]);
}
s.removeIf((n) -> (n % 2 == 1));
System.out.println(s); // [2, 4, 16]
}
}
Stop using java.util.Stack they said, a legacy class they said, instead i should use java.util.ArrayDeque, but frankly i can still keep up being racist (in a reversed manner):
import java.util.ArrayDeque;
import java.util.Deque;
public class App {
public static void main(String[] args) {
int arr[] = { 2, 4, 7, 11, 13, 16, 19 };
Deque<Integer> s = new ArrayDeque<Integer>();
for (int i = 0; i < arr.length; i++) {
s.push(arr[i]);
}
s.removeIf((n) -> (n % 2 == 1));
System.out.println(s); // [16, 4, 2]
}
}
The fact that you can iterate through java.util.Stack is amazing, but the ability to insert element in a specified index:
import java.util.Stack;
public class App {
public static void main(String[] args) {
int arr[] = { 2, 4, 7, 11, 13, 16, 19 };
Stack<Integer> s = new Stack<Integer>();
for (int i = 0; i < arr.length; i++) {
s.push(arr[i]);
}
s.add(2, 218);
System.out.println(s); // [2, 4, 218, 7, 11, 13, 16, 19]
}
}
That's what happens when you inherit java.util.Vector, which is only done a BRAIN OVEN person, a very brain oven even that it will revert to retarded
If you thought about using this type of bullshit in Java get yourself prepared to beat the disk for hours when you accidentally call java.util.Stack<T>.add(int index, T element) instead of java.util.Stack<T>.push(T element), you will probably end up breaking the disk or your hand, but not solving the issue
WHY THE F*** CAN'T WE HAVE A WORKING NORMAL STACK ?5 -
RECOVER MY STOLEN CRYPTO / TRACK STOLEN CRYPTO WITH PROFICIENT EXPERT CONSULTANT
One Friday in Texas, I was filled with anticipation as I prepared to onboard a new subcontractor for a project that had been meticulously planned for months. As the project manager, I bore the responsibility of ensuring that every detail was executed flawlessly, and I was eager to integrate this new talent into our team. The subcontractor had reached out to me via email, presenting themselves as a highly skilled professional with an impressive portfolio. Our exchanges were seamless and persuasive, instilling a growing confidence in their capabilities. They proposed using Bitcoin for payment, asserting that it was the most efficient and secure method available. Trusting their professionalism and the burgeoning trend of cryptocurrency transactions, I proceeded with the transfer, sending 4 Bitcoin (BTC) to the wallet address they provided. I felt a profound sense of accomplishment. I had fulfilled my obligation, and everything appeared to be falling into place. My relief swiftly morphed into dread when I realized that the subcontractor had vanished without a trace. All communication ceased, and the email address I had been corresponding with was no longer active. Panic surged through me as I grasped the gravity of the situation I had been duped. I convened with my team to discuss the unfortunate turn of events. We quickly recognized the irreversible nature of cryptocurrency transactions. Unlike traditional banking, where payments can often be reversed, this was a permanent loss. The amount I had sent was substantial, and the thought of losing it all was overwhelming. A sinking feeling settled in my stomach as I contemplated the ramifications of my actions. I had placed my trust in someone I barely knew, and now I was confronting the consequences of my misplaced faith. I embarked on a quest for solutions and discovered PROFICIENT EXPERT CONSULTANT, a firm specializing in tracing and recovering lost or stolen cryptocurrency. Their website was replete with testimonials from individuals who had successfully reclaimed their funds, which ignited a flicker of hope within me. I reached out to PROFICIENT EXPERT CONSULTANT immediately via PROFICIENTEXPERT @ CONSULTANT . C O M ~ Telegram : @ PROFICIENTEXPERT for your support, articulating my predicament in detail. Their team was remarkably responsive and assured me that they would employ every resource at their disposal to track the funds. They explained how they would utilize advanced blockchain analysis techniques to trace the Bitcoin and gather compelling evidence of the fraud. As PROFICIENT EXPERT CONSULTANT commenced their investigation, I learned just how sophisticated these scammers could be. The funds I had sent were swiftly transferred to another wallet, and the scammer had employed mixing services to obfuscate the trail, complicating efforts to trace the money. However, the experts at PROFICIENT EXPERT CONSULTANT were undeterred. They worked diligently, leveraging their expertise in blockchain technology to follow the digital breadcrumbs left behind by the scammer. With each update from PROFICIENT EXPERT CONSULTANT, I felt a renewed sense of hope that they might be able to recover my lost Bitcoin. This has been a harsh lesson when navigating the cryptocurrency landscape. Thanks to PROFICIENT EXPERT CONSULTANT, I now comprehend the necessity of implementing robust verification processes for new subcontractors and the imperative of secure payment methods. In my role, I have come to appreciate the significance of thoroughly verifying the identities of those I engage with and ensuring that payment methods are fortified against potential fraud. In hindsight, I wish I had taken the time to authenticate the subcontractor’s identity through multiple channels and utilized an escrow service to safeguard my funds. I am relieved to share that I recovered all the funds. I hope that sharing my story will serve as a cautionary tale for others. Cryptocurrency offers myriad benefits, but it also harbors significant risks that cannot be overlooked. I urge anyone engaging in digital transactions to exercise caution, conduct thorough research, and prioritize security measures to protect themselves from potential scams. With the invaluable assistance of PROFICIENT EXPERT CONSULTANT, I learned that there are resources available to aid victims of fraud, and I hope others can find the same support in their times of need.5 -
**Reclaim Crypto & Bitcoin Losses - CALL HACKATHON TECH SOLUTIONS**
If you’ve ever been defrauded by deceptive Bitcoin traders or fallen victim to online scammers promising quick gains, you know the sinking feeling of losing your hard-earned money in the blink of an eye. I was once in that very position, until I found a beacon of hope in HACKATHON TECH SOLUTIONS. cryptocurrency started with optimism and a desire to capitalize on the potential gains. However, what began as a promising venture quickly turned into a nightmare when I fell victim to an online ripper. This individual managed to abscond with a substantial amount of my Bitcoin — 2.966BTC to be exact. The loss was not just financial; it was a blow to my trust and confidence in online transactions. Desperate and unsure of where to turn, I was fortunate to have a colleague at work recommend HACKATHON TECH SOLUTIONS. They had successfully helped his spouse recover tokens and coins lost to similar scams, which gave me hope that there might be a chance to reclaim what I had lost. With little to lose and everything to gain, I reached out to HACKATHON TECH SOLUTIONS, and it turned out to be the best decision I could have made. HACKATHON TECH SOLUTIONS distinguished themselves with their professionalism and expertise. They understood the nuances of cryptocurrency fraud and approached my case with diligence and determination. Their team of specialists, including private investigators well-versed in tracing digital transactions, immediately went to work. HACKATHON TECH SOLUTIONS’s process was thorough and transparent. They kept me informed at every step, outlining their strategy and explaining the legal and technical aspects of the recovery process. This level of communication was not only reassuring but also demonstrated their commitment to client satisfaction. In less than two weeks — a remarkably short timeframe given the complexity of the case — HACKATHON TECH SOLUTIONS managed to recover 2.966BTC, the entirety of what I had lost. The relief and gratitude I felt were immense. What had seemed like an insurmountable loss had been reversed, thanks to their expertise and unwavering dedication. Thanks to HACKATHON TECH SOLUTIONS for not only recovering my funds but also restoring my faith in legitimate assistance online. In an era where online fraudsters lurk around every corner, finding a trustworthy partner like HACKATHON TECH SOLUTIONS is invaluable. I endorse HACKATHON TECH SOLUTIONS to anyone facing similar challenges with their BTC wallet or any cryptocurrency-related fraud. Their reputation as the most efficient and trusted recovery experts is well-deserved, based on my personal experience and the successful outcomes they consistently achieve. If you’re hesitant or skeptical about seeking assistance, don’t be. HACKATHON TECH SOLUTIONS stands out as a beacon of hope in an otherwise murky landscape of online scams and fraud. Trust in their expertise and let them guide you through the process of reclaiming what rightfully belongs to you. HACKATHON TECH SOLUTIONS not only recovered my funds but also saved me from potential future scams. They are more than just recovery specialists; they are guardians of trust and integrity in the digital age. Contact HACKATHON TECH SOLUTIONS today and take the first step towards reclaiming control of your financial security. Your peace of mind is worth it. Reach out to HACKATHON TECH SOLUTIONS via below contact details.
W h a t s a p p : +3, 1, 6, 4, 7, 9, 9, 9, 2, 5, 6
Website: www . hackathon tech solutions . com
Telegram: @ hackathon tech solutions
Email: info @ hackathon tech solution . com1 -
Best Recovery Experts for Cryptocurrency Assets: HIRE CERTIFIED RECOVERY SERVICES
Last month, I faced a nightmare scenario when the entire balance of SOL I held in my Meta Mask wallet was abruptly transferred to an unknown address. One moment, my funds were secure; the next, they’d vanished without a trace. I frantically reviewed my transaction history, double-checked permissions, and scanned my devices for malware, but found no obvious breach. Panic turned to despair as I realized my savings accumulated through years of cautious investing were gone. Desperate for answers, I contacted Meta Mask support, only to be told that decentralized transactions couldn’t be reversed or traced by their team. They speculated that my wallet had been compromised, possibly via a phishing scam, a malicious dApp, or a leaked recovery phrase, but I couldn’t pinpoint where I’d gone wrong. Feeling helpless, I combed through Reddit threads and crypto forums, where I stumbled upon CERTIFIED RECOVERY SERVICES, a service hailed for its success in reclaiming stolen assets. Though skeptical after all, everything I’d read suggested crypto theft was irreversible I decided to take a leap of faith and submitted my case details, including transaction IDs and wallet addresses. Their team responded within hours, outlining a meticulous plan to trace the stolen SOL across the blockchain and collaborate with exchanges to intercept the funds. Over the next week, CERTIFIED RECOVERY SERVICES provided daily updates, revealing how the thief had funneled my SOL through a labyrinth of wallets to obscure its trail. Using advanced blockchain forensics, they identified patterns linking the movement of funds to a known exchange. By working with legal teams and platform security, they flagged the stolen crypto before it could be liquidated. Their expertise and determination were evident as they navigated the complexities of the blockchain, piecing together the puzzle of my stolen assets. Against all odds, their relentless efforts paid off: within 9 days, they recovered 100% of my stolen SOL and safely redirected it to a new, fortified wallet. This experience taught me the importance of vigilance in the crypto space and the value of seeking help from experts when faced with seemingly insurmountable challenges. I learned that while the decentralized nature of cryptocurrency offers many advantages, it also comes with risks that require constant awareness and proactive measures. Now, I’m more cautious than ever, ensuring that my digital assets are protected and that I stay informed about potential threats in the ever-evolving world of cryptocurrency.
Here's Their Info Below:2 -
USDT RECOVERY SERVICE: WEB BAILIFF CONTRACTOR EXPERIENCE
It was an ordinary Tuesday. I was keeping an eye on my Bybit portfolio when an email showed up that looked like a formal notice from the exchange regarding suspicious behavior. I didn't hesitate; I clicked the link and entered my credentials. When I hit submit, a sense of horror befell me. Within minutes, my Bitcoin wallet was drained. Losing 3.2 BTC, worth nearly $200,000 at the time, wasn't just monetary. It was a personal trust issue. I couldn't fathom that I had been phishing-scammed. I spent days scouring forums, contacting Bybit customer support, and even filing a report with the police. But the responses were disappointing and repetitive. Crypto withdrawals can't be reversed. Scam victims seldom see their money back. The frustration was overwhelming. I barely slept. I continuously replayed the moment in my head repeatedly. Why did I click on the link? Why didn't I double-check it? The frustration and guilt ate away at me. Friends tried to be helpful, but many didn't get the emotional and financial weight of what had transpired. I had always taken security precautions carefully. But in a moment of distraction, all was lost Weeks later, trawling Reddit threads on crypto cons, I found some mention of Web Bailiff Contractor. I was suspicious at first. It sounded too good to be true. But the comments looked genuine, and I was desperate. I went ahead and got in touch with them. They were speedy, professional, and surprisingly sympathetic. They made no promises of miracles. Instead, they explained their procedure: following blockchain transactions, identifying potential exchange cash-outs, and working with legal and crypto groups to freeze and recover funds.I gave them all I had wallet addresses, transaction history, screenshots and waited. A few days later, I got an email that left me speechless. They had been able to track and recover all my stolen Bitcoin.I couldn't believe it. After being told over and over again that the money was gone forever, here it was, back in my pocket. It was waking up from a nightmare. Web Bailiff Contractor did not just get my money back. They got my sense of security, my trust, and my peace of mind back too.I am writing about my experience now in case someone else out there is feeling the same panic and desperation that I once felt. There is hope. And every now and then, there is a second chance.2 -
Are you looking for ways to recovery your lost Bitcoin and other Cryptocurrencies from scammer's? Search no more! ( RECOVERY SCAM CRYPTO @ GMAIL . COM ) WhatsApp +1 (603) 702 ( 4335 ) Is the best Scammed Crypto Recovery Agency I have come across on the google internet . So glad I took the bold step by contacting them. All my stolen cryptocurrencies was reversed back to my Coin Base wallet within few hours . I will advice you all to contact their customer support to help you with their strategies and thank me letter.1
-
Get a certified ETH Recovery Expert and lead Of Stolen Funds With LEE ULTIMATE HACKER
Last month, I encountered a frightening situation when the full amount of SUI I had stored in my Exodus wallet was suddenly sent to an unknown address. I hadn’t authorized any transactions, nor had I shared my private keys or seed phrases with anyone, so the entire event left me bewildered and anxious. The funds had simply disappeared, and I couldn’t figure out how or why this had happened. In an attempt to recover my funds, I reached out to several support services, starting with Exodus. I was hoping they might be able to track the transaction or shed some light on what went wrong. Unfortunately, their response was not helpful. They explained that they couldn’t trace blockchain transactions directly, and suggested that my private key might have been compromised, though I had no idea how that could have happened. Feeling frustrated, I decided to continue my search for assistance and stumbled upon LEEULTIMATEHACKER @ A O L . C O M
telegram: L E E U L T I M A T E https: / / l e e u l t i m a t e h a c k e r . c o m
. Initially, I was doubtful about their ability to help, but after reading positive reviews, I decided to give it a try. Their website explained that they specialize in tracing lost or stolen cryptocurrency and offered recovery services for cases like mine. I submitted a request with all the relevant details, including the unauthorized transaction and the address to which my SUI assets had been sent. To my surprise, the response from their team came quickly. They assured me that they could investigate the destination address and begin tracking it. Over the following days, they kept me updated on their progress and worked diligently to trace the flow of funds. They were able to identify the wallet associated with the destination address and gathered enough information to take further action. Thanks to their efforts, my funds were ultimately recovered. The team successfully reversed the unauthorized transaction, and I was provided with security recommendations to protect my wallet moving forward. The relief I felt upon recovering my SUI was immense, and I couldn’t have done it without the help of Lee Ultimate Hacker. This incident taught me valuable lessons about the importance of safeguarding my crypto assets and being cautious with digital wallets. I'm extremely grateful for the support I received, as without Lee Ultimate Hacker, I would likely have lost my funds for good.2 -
THE BEST CERTIFIED ETHICAL HACKER FOR HIRE IN USA HIRE ADWARE RECOVERY SPECIALIST
It was during one of the darkest periods of my life that I found myself in a situation that seemed beyond my control. WhatsApp info:+12723 328 343
After losing three friends in combat in Dubai, I was left to grapple with both grief and physical recovery. I had spent the past two months in remission, with the first month spent at a camp, where I was trying to regain my strength. Despite the emotional weight I was carrying, I needed to send a large sum of money to my family in London. It was the earnings I had accumulated over six months working on a mission, and I wanted to ensure they were taken care of. com Bitcoin seemed like the easiest and most secure method of transferring such a large amount, as I had used it successfully in the past. However, this time was different. After sending the transaction, I waited for confirmation, only to realize, hours later, that the seller had never credited the Bitcoin to my account. To make matters worse, they had gone completely silent. I was devastated. Not only had I lost a significant amount of money, but I also felt completely helpless. I had no idea where to turn, and time was running out. Desperate, I started searching for solutions online. That’s when I came across ADWARE RECOVERY SPECIALIST, a service specializing in crypto recovery. At first, I was skeptical how could anyone recover lost or stolen Bitcoin once it had been transferred? But I was willing to try anything. To my surprise, ADWARE RECOVERY SPECIALIST proved to be exactly what I needed. The team, led by a professional named ADWARE, quickly began working to trace the transaction. All I had to do was provide some essential details, such as the wallet ID I had used in the transaction, and they took care of the rest. Email info: Adwarerecoveryspecialist@auctioneer. net The process was smooth, efficient, and surprisingly quick. In no time at all, my funds were restored, down to the last cent, with only a small fee for the bank transaction. I couldn’t believe how seamlessly the recovery process went. What had seemed like an insurmountable loss was reversed thanks to ADWARE RECOVERY SPECIALIST expertise. If you ever find yourself in a similar situation, I can’t recommend their services enough. They gave me back my peace of mind when I thought all was lost. Thank you, ADWARE RECOVERY SPECIALIST , for your invaluable help during one of the toughest times of my life. 5
5 -
As an artist, I’ve always been focused on my creative pursuits and never really ventured into the world of high-risk financial investments. But, like many others, I was drawn to the idea of making money quickly through Forex trading. Unfortunately, I fell victim to a Forex scam and lost a large portion of my savings. The financial loss was devastating, but the emotional toll was even worse. I felt betrayed, and hopeless, and wasn’t sure where to turn next. One day, while browsing through Red Note, a platform where people connect over shared experiences, I came across a post from someone who had gone through a similar situation. They shared how they managed to recover their lost funds through a company called Tech Cyber Force Recovery. Desperate for a solution, I decided to reach out to them and explain what had happened to me. I was initially skeptical, unsure whether this was just another scam or if it could be the real deal. To my surprise, the team at Tech Cyber Force Recovery was professional, compassionate, and genuinely interested in helping. They listened carefully to my story and assured me that they had the expertise and resources to help recover my lost funds. The process would take time, they said, and I’d need to provide some documentation, but they were confident that they could help. After several conversations and a thorough investigation, they started working on my case. The results were incredible. Within a relatively short period, Tech Cyber Force Recovery managed to recover nearly all of the funds I had lost. It wasn’t an easy process, and it required patience, but the team’s dedication, attention to detail, and methodical approach paid off. I felt an overwhelming sense of relief and gratitude. What had once seemed like a permanent loss was now being reversed, thanks to the help of Tech Cyber Force Recovery. Not only did the recovery restore my financial situation, but it also restored my sense of trust and confidence. I had almost given up hope, but now, with my funds recovered, I feel like I can move forward. I’ve learned valuable lessons from this experience, and I’m more cautious about my financial decisions in the future. What began as a desperate search on Red Note turned into a life-changing recovery. Thanks to Tech Cyber Force Recovery, I now feel more hopeful about my financial future, with the knowledge that recovery is possible.
telegram (@)techcyberforc
texts (+1 5.6.1.7.2.6.3.6.9.7)3 -
Months earlier, I’d sunk $156,000 into what I thought was a golden opportunity, an online cryptocurrency investment promising sky-high returns. The website was sleek, the testimonials glowing, and the numbers kept climbing. But when I tried to withdraw my profits, the platform froze. Emails went unanswered, support chats died, and my “investment” vanished into the digital ether. I’d been scammed, and the sting of it burned deep.Desperate, I stumbled across Alpha Spy Nest while scouring the web for help. Their site/reviews didn’t promise miracles, just results, specialists in tracking down lost funds from online scams. Skeptical but out of options, I reached out. The process started with a simple form: I detailed the scam, uploaded screenshots of transactions, and shared the wallet addresses I’d sent my crypto to. Within hours, they confirmed they’d take my case.What followed was like watching a high-stakes chess game unfold, though I only saw the moves, not the players. Alpha Spy Nest dove into the blockchain, tracing my funds through a maze of wallets designed to obscure their path. They explained how scammers often use mixers to launder crypto, but certain patterns like timing and wallet clustering, could still betray them. I didn’t understand half of it, but their confidence kept me hopeful. Hours later, they updated me: my money had landed in an exchange account tied to the scam network. They’d identified it through a mix of on-chain analysis and intel from sources I’d never grasp. After 24 hours, i got a message, my funds were frozen in the scammer’s account pending review. Alpha Spy Nest had apparently flagged it just in time. After some back-and-forth, the exchange with the help of Alpha Spy Nest reversed the transactions, and $145,000 of my original $156,000 hit my wallet. The rest, they said, was likely gone forever, siphoned off early. I never met anyone from Alpha Spy Nest, never heard a voice or saw a face. Yet, their methodical precision pulled me back from the brink. My money wasn’t fully restored, but the recovery felt like a win, a lifeline from a faceless ally in a world of digital shadows. If you find yourself in the same situation, you can also reach out to them via: whatsapp: +15132924878
 1
1 -
HIRE FAST USDT-BTC RECOVERY EXPERT\FOLKWIN EXPERT RECOVERY.
I had a dreamlike beginning to my Bitcoin journey. The success stories and the notion that cryptocurrencies could transform how we invest and accumulate money enthralled me. I made a sizable investment in Bitcoin after doing extensive research and planning in the hopes of securing my financial future. Everything seemed ideal for a while, and my investment seemed to be yielding positive results. However, everything came crashing down. My Bitcoin was taken due to a huge hacking attack and a succession of missteps, which saddened me. My hard-earned savings and investments were gone in an instant. My loss was unbearably heavy. I not only lost a lot of money, but I also felt like I had failed myself and my future. I was overcome with regret, fear, and helplessness. Every attempt to get access to my cash failed, and the prospect of ever seeing my money again became increasingly distant. In my efforts to look for a helping hand, I contacted various so-called "recovery services," but they all revealed to be scams or failed to deliver any meaningful remedies. I was frantic, terrified that my money had been lost forever, and I was sinking more into despair. The prospect of irreversible financial devastation worried me, and I felt worthless. That’s when I found ( Folkwin Expert Recovery ). At first, I was hesitant. After all, I had already been burned by false promises. But after reading about their track record of successful recoveries and their professional, transparent approach, I decided to give them a chance. It felt like my last shot at recovering what I had lost. After weeks of persistence, I received the incredible news that my stolen Bitcoin had been recovered. The relief I felt was overwhelming. What had seemed like a hopeless situation had been reversed, and my financial future was no longer in jeopardy. I couldn’t believe it—I had been given a second chance. Thanks to ( Folkwin Expert Recovery ), I was able to overcome the devastation of losing my Bitcoin and begin to rebuild my financial security. They showed me that with the right team and the right approach, even the most devastating losses can be turned around. Contact Folkwinexpertrecovery (AT) tech-center (DOT) com or W-h-a-t-s-A-p-p; +1 (740)705-0711 for help.
Regards,
Edward H Macnamara. 3
3 -
I don't know about your country but this feature is novel among Nigeria's financial institutions. What usually happens in a typical bank app is same as above: fields are provided for entering account details. There is no way to know the outcome of the transfer until it's made. If it fails in transit (often, you're debited but the recipient gets nothing), you might get a reversal if you're lucky, after an indefinite period of time. Otherwise, you have to take it up with your bank or the recipient's bank. Or worse, with the central bank, when the first two are not being helpful enough
Enter this new generation fintech (Opay). They offer an addition that impresses all customers: after selecting the bank, a popup appears that notifies you on the stability of the receiver's network. Someone sent me this screenshot seeking my permission or provision of another bank. I didn't think much of it and asked them to proceed. To my surprise, transaction failed and their money instantly reversed
Those traditional banks clearly have no api for health checks, otherwise they'd all adopt it within their own apps. So, how is this possible? My only guess is that Opay maintains their own health checks system that is updated maybe by periodically pinging those banks with nominal fees like N1 and verifying whether money was received
It's obviously primitive but I doubt traditional bank apis return a failure response (since none currently tells you when transaction failed). So you'd have to rely on workarounds emulating manual and automated testing
To those in the fintech sector or with a faint idea of what's going on, can you explain?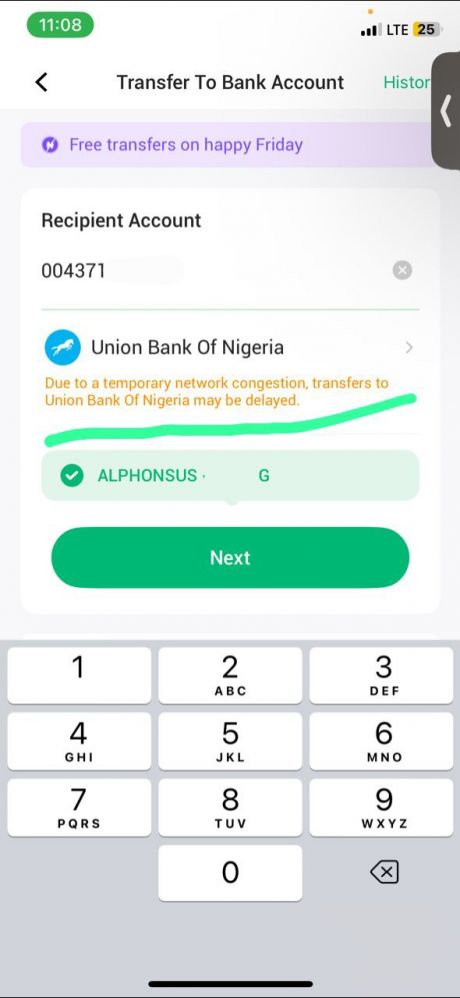 7
7 -
All thanks goes to The Cyber Tech Wizard for their unwavering support to me during this trying time, in a world full of so many evil and unworthy people out there trying to impersonate on something they know nothing about i was been scammed of my hard earned money that i have saved all my life i nearly loose my life on this process thinking everyday knowing fully well that all my hope of living is gone.
I am a teacher from Oakes i have saved so many years and when i heard and read online about growing your income through bitcoin it sounds so very interesting to me that i had to invest all i have on the platform but not knowing that they are not the real legitimate investment company i fall prey for them they used me and made away with my money i could not access my password i was worried and was having a thought of suicide but one mind came to me and ask me to stumble online to see if there would be any legitimate recovery company that can retrieve scammed crypto. I found so many companies online but my mind pushed me to work with The [Cyber Tech Wizard] and the rest was history.
My money was reversed back and i was been taught so many things on how to guard my money increase my money grow income without falling into scam through The help Cyber Tech Wizard. You can also reach out to them if fallen victim V.i.A. Email cyber tech wizard @ cyber services DOT com 7
7 -
Lua/ C
Java/ C
Swift/ Objective C
Visual Basic / C or something
C / C#
……..
👆last reversed yet, that looks like a funny face 😑…
Where, am I?…8 -
HOW TO PROTECT AND RECOVER YOUR STOLEN CRYPTO INVESTMENTS: CONSULT RAPID DIGITAL RECOVERY
One Friday in Texas, I was filled with anticipation as I prepared to onboard a new subcontractor for a project that had been meticulously planned for months. As the project manager, I bore the responsibility of ensuring that every detail was executed flawlessly, and I was eager to integrate this new talent into our team. The subcontractor had reached out to me via email, presenting themselves as a highly skilled professional with an impressive portfolio. Our exchanges were seamless and persuasive, instilling a growing confidence in their capabilities. They proposed using Bitcoin for payment. Trusting their professionalism, I proceeded with the transfer, sending 4 Bitcoin (BTC) to the wallet address they provided. I felt a profound sense of accomplishment. I had fulfilled my obligation, and everything appeared to be falling into place. My relief swiftly morphed into dread when I realized that the subcontractor had vanished without a trace. All communication ceased, and the email address I had been corresponding with was no longer active. I convened with my team to discuss the unfortunate turn of events. We quickly recognized the irreversible nature of cryptocurrency transactions. Unlike traditional banking, where payments can often be reversed. I had placed my trust in someone I barely knew, I embarked on a quest for solutions and discovered RAPID DIGITAL RECOVERY, a firm specializing in tracing and recovering lost or stolen cryptocurrency. They explained how they would utilize advanced blockchain analysis techniques to trace the Bitcoin. As RAPID DIGITAL RECOVERY commenced with their investigation, However, the experts at RAPID DIGITAL RECOVERY were undeterred. With each update from RAPID DIGITAL RECOVERY, I felt a renewed hope that they might be able to recover my Bitcoin. I am relieved to share that I recovered all the funds. I hope that sharing my story will serve as a cautionary tale for others....Reach Out To Them via: Email: rapid digital recovery (@) execs. com
WhatSapp: +1 4 1 4 8 0 7 1 4 8 5
Telegram: https: // t. me/ Rapid digital recovery5195


