Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "case sensitive"
-
My biggest dev blunder. I haven't told a single soul about this, until now.
👻👻👻👻👻👻
So, I was working as a full stack dev at a small consulting company. By this time I had about 3 years of experience and started to get pretty comfortable with my tools and the systems I worked with.
I was the person in charge of a system dealing with interactions between people in different roles. Some of this data could be sensitive in nature and users had a legal right to have data permanently removed from our system. In this case it meant remoting into the production database server and manually issuing DELETE statements against the db. Ugh.
As soon as my brain finishes processing the request to venture into that binary minefield and perform rocket surgery on that cursed database my sympathetic nervous system goes into high alert, palms sweaty. Mom's spaghetti.
Alright. Let's do this the safe way. I write the statements needed and do a test run on my machine. Works like a charm 😎
Time to get this over with. I remote into the server. I paste the code into Microsoft SQL Server Management Studio. I read through the code again and again and again. It's solid. I hit run.
....
Wait. I ran it?
....
With the IDs from my local run?
...
I stare at the confirmation message: "Nice job dude, you just deleted some stuff. Cool. See ya. - Your old pal SQL Server".
What did I just delete? What ramifications will this have? Am I sweating? My life is over. Fuck! Think, think, think.
You're a professional. Handle it like one, goddammit.
I think about doing a rollback but the server dudes are even more incompetent than me and we'd lose all the transactions that occurred after my little slip. No, that won't fly.
I do the only sensible thing: I run the statements again with the correct IDs, disconnect my remote session, and BOTTLE THAT SHIT UP FOREVER.
I tell no one. The next few days I await some kind of bug report or maybe a SWAT team. Days pass. Nothing. My anxiety slowly dissipates. That fateful day fades into oblivion and I feel confident my secret will die with me. Cool ¯\_(ツ)_/¯12 -
I remember that time my class (first year of software development) wrote a huge project for a real company as practice for irl stuff.
I was the only Linux user and it would be deployed on a Linux server.
Spent 10 weeks of development and then the moment of deployment on a Linux server began!
.
.
.
.
.
Nothing was case sensitive, everything was programmed for a windows architecture (backward slashes etc) and mssql was used while we would host it on a MySQL server.
The tree core guys spent three days or so to make the entire fucker compatible 😂
It was enjoyable to see them (literally) sweat 😊 (it had been known from the very beginning)7 -
It's not that I hate PHP, I just hate the lack of consistency in standard function naming and parameter order, nonsensical attribute access, nearly-meaningless comparison operators, reference handling, case (in)sensitivities, and more!
I mean, look at these functions:
strtoupper(...)
bin2hex(...)
strtolower(...)
And look at THESE FUNCTIONS:
array_search($needle, $haystack)
strpos($haystack, $needle)
array_filter($array, $callable)
array_map($callback, $array)
array_walk($array, $callable)
And let me jUST USE SOME ATTRIBUTES:
$object->attr = "No dollar sign...";
Class::$attr = "GOD WHY";
HOW ABOUT SOME COMPARISONS:
(NULL == 0) // true
(NULL < -1) // ALSO true
Functions AREN'T CASE SENSITIVE (at least variables are).
Wanna dereference? TOO BAD, YOU'LL HAVE TO GET OUT THE TNT.
Alright, yeah, I hate PHP.18 -
Me: "Ugh. Soo insensitive.." *angry muttering*
Curious cousin: "Whom? What? Why?"
Me: "My stupid Mac is not case sensitive so I have to mount a Unix partition and reference it from somewhere else. Why wouldn't they just make a case sensitive filesystem like a proper Unix based OS?"
Clearly uninterested cousin: "seriously?! You called your laptop insensitive? I thought you were talking about a guy" ..
Filthy casuals.6 -
5 years ago, in my first week of starting this particular job, the CTO casually mentioned they'd been struggling with a bug for years. Basically, in the last few days of the year, it seemed that records were jumping a year ahead, with no rhyme nor reason why. Happened every year, and wasn't linked with them deploying new code. (Their code was a mess with no sane way to unit test it, but that was a separate issue.)
I happened to know immediately what might be causing it - so I ran a case-sensitive search in the codebase for "YYYY", pointed out the issue, explained it, then committed a fix all in about 2 minutes.
I was told I'd officially passed my probation.
(Search for "week year vs year" if you're curious & the above doesn't ring any bells.)6 -
PM: Can we have it so the usernames are case-sensitive?
Me: uhh, sure I guess.. But thats like really pointless and adds no real usefulness.. In fact makes the whole logging in thing a tad more complicated for no reason..
PM: Well this one other product we have uses "Admin" for the login versus yours that used "admin" so it needs to be implemented.
(note that mine accepted "Admin" anyways...) *implemented it*
PM: So there's a problem with the username sort, it sorts by capitals then lowercase.. eg:
alpha
beta
Alpha
Me: Yeah, you asked for case-sensitive usernames..
PM: Well can you fix it?
Me: I could create a second field within the user data that is the username in all lowercase and sort by that. But that negates like all of the whole case-sensitive usernames thing.. OR I could drop all this actually important work I'm doing and do a whole bunch of work on a custom sort for this useless fucking feature you wanted me to put in..
*it's been 2 weeks and still no reply...* -
My university has impeccable data management. I needed to ssh into their Linux server for an assignment but it refused to accept my login. Which was weird because I could login to the same account on one of our websites just fine. I typed my password into a text file and then copy and pasted it into both logins. The Linux one failed but the website succeeded. After some experimentation it turns out that the Linux server only recognized my username if I typed it in all lowercase, even though when I created the account it had uppercase characters as well.
So let me walk you through the sloppiness that had to have occurred for this to happen. When I first created the account it must have ignored what I entered and just saved the username in all lowercase without communicating that to me. Then the websites that use this account must either ignore case for usernames or lowercase the user input before querying the database. Finally, the Linux server, despite knowing that all the usernames are lowercase, is case sensitive and won't recognize the username as I originally typed it in.
Can you guess what department manages the account, website and Linux server? The Department of Computer and Information Science. Incredible.2 -
Finally fixed a major bug.....
FUCK YOU C# AND YOUR FUCKING CASE SENSITIVE BULLSHIT.
DAYS
THAT TOOK FUCKING DAYS AND AT NO POINT DUD VISUAL STUDIO BOTHER TO MENTION THAT FUCKING ERROR.
1 CHARACTER, ON ONE LINE, EFFECTIVELY BROKE THOUSANDS OF LINES OF CODE
fuck this, I quit. See you next time you contact the Microsoft live support chat!13 -
Well... I feel insanely stupid because I've been using windows for years an just realised that the file system isn't case sensitive... Mother fuckers...
(Yes judge me, I am a twat)7 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
WELL GEE, IF I KNEW WHAT MY ACCOUNT USERNAME WAS, I WOULD JUST SIGN IN YOU ASSHOLE. -.-
On top of that, they use these fucking anchent capchas that are fucking case sensitive and annoying as hell..
In their defence, I was trying to automate their website (one of those get paid to click sites) in an atempt to get some money, but still! 6
6 -
Apparently USPS tracking numbers are case sensitive... I missed a delivery today so went online to check the status.
The code was RAxxxxxxxxxxxxxxxxxxxTR
x=numbers
I first typed the letters in lowercase and it said package not found...
Really???!!!!!! Don't you think all those numbers are already too long...3 -
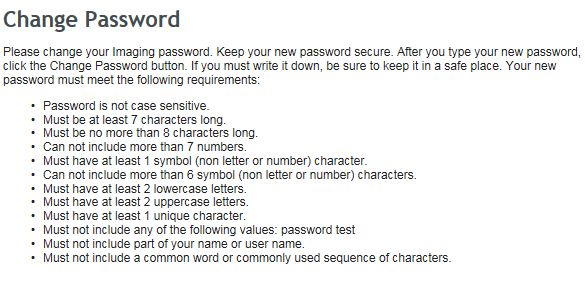
So, among the ridiculously long list of password requirements, password is not case sensitive BUT it has to contain uppercase and lowercase letters?
 14
14 -
"Unix filenames are case-sensitive?! Hur hur, that must be really confusing!"
Well, no, if you're not a fucking mouth-breathing cretin it isn't.2 -
Client: MY PASSWORD DOESN'T WORK
Me: our passwords are case-sensitive
Client: YES I USED CAPS LOCK1 -
Interesting. A few hours ago I had a nice domestic conversation with my coleague about robot vacuum cleaners. He was talking about iRobot Roomba and I was talking about Xiaomi. Here's the result!
Interesting thing is that we talked in a *voice* conversation. Over Slack. Over Chrome. Over corporate VPN (openconnect).
Where's the spying link? Slack or Chrome?
My bet's on Chrome.
What does that tell you about the privacy of your sensitive conversations? :)
Hide behind VPNs all you like. If you have proprietary software (or hardware in the case of Huawei) - you're being watched and listened to.
EDIT: I'm on Linux, he's on MacOS 9
9 -
As usual a rather clickbait title, because only the chrome extensions (as always) seem to be vulnerable:
"Warning – 3 Popular VPN Services Are Leaking Your IP Address"
"Researchers found critical vulnerabilities in three popular VPN services that could leak users' real IP addresses and other sensitive data."
"VPN Mentor revealed that three popular VPN service providers—HotSpot Shield, PureVPN, and Zenmate"
"PureVPN is the same company who lied to have a 'no log' policy, but a few months ago helped the FBI with logs that lead to the arrest of a Massachusetts man in a cyberstalking case."
"Hijack all traffic (CVE-2018-7879) "
"DNS leak (CVE-2018-7878)"
"Real IP Address leak (CVE-2018-7880)" 7
7 -
Whelp. I started making a very simple website with a single-page design, which I intended to use for managing my own personal knowledge on a particular subject matter, with some basic categorization features and a simple rich text editor for entering data. Partly as an exercise in web development, and partly due to not being happy with existing options out there. All was going well...
...and then feature creep happened. Now I have implemented support for multiple users with different access levels; user profiles; encrypted login system (and encrypted cookies that contain no sensitive data lol) and session handling according to (perceived) best practices; secure password recovery; user-management interface for admins; public, private and group-based sections with multiple categories and posts in each category that can be sorted by sort order value or drag and drop; custom user-created groups where they can give other users access to their sections; notifications; context menus for everything; post & user flagging system, moderation queue and support system; post revisions with comparison between different revisions; support for mobile devices and touch/swipe gestures to open/close menus or navigate between posts; easily extendible css themes with two different dark themes and one ugly as heck light theme; lazy loading of images in posts that won't load until you actually open them; auto-saving of posts in case of browser crash or accidental navigation away from page; plus various other small stuff like syntax highlighting for code, internal post linking, favouriting of posts, free-text filter, no-javascript mode, invitation system, secure (yeah right) image uploading, post-locking...
On my TODO-list: Comment and/or upvote system, spoiler tag, GDPR compliance (if I ever launch it haha), data-limits, a simple user action log for admins/moderators, overall improved security measures, refactor various controllers, clean up the code...
It STILL uses a single-page design, and the amount of feature requests (and bugs) added to my Trello board increases exponentially with every passing week. No other living person has seen the website yet, and at the pace I'm going, humanity will have gone through at least one major extinction event before I consider it "done" enough to show anyone.
help4 -
Long time no rant.
Rant::beginRant();
How do people who are, I think, supposed to have a knowledge of what the fuck they're doing, keep their work without knowing what the fuck they're doing?
You're telling me that you have been hired as a "full-stack developer", yet you can't build a motherfucking Vue page over SSH (not even talking about automated deployment, just the most bare bones approach)? You don't know how to deploy a Laravel project? You don't know that Linux server paths are case sensitive? You can't read the log files?!
Rant::commitRant();9 -
In today's episode of kidding on SystemD, we have a surprise guest star appearance - Apache Foundation HTTPD server, or as we in the Debian ecosystem call it, the Apache webserver!
So, imagine a situation like this - Its friday afternoon, you have just migrated a bunch of web domains under a new, up to date, system. Everything works just fine, until... You try to generate SSL certificates from Lets Encrypt.
Such a mundane task, done more than a thousand times already... Yet... No matter what you do, nothing works. Apache just returns a HTTP status code 403 - Forbidden.
Of course, what many folk would think of first when it came to a 403 error is - Ooooh, a permission issue somewhere in the directory structure!
So you check it... And re-check it to make sure... And even switch over to the user the webserver runs under, yet... You can access the challenge just fine, what the hell!
So you go deeper... And enable the most verbose level of logging apache is capable of - Trace8. That tells you... Not a whole lot more... Apparently, the webserver was unable to find file specified? But... Its right there, you can see it!
So you go another step deeper and start tracing the process' system calls to see exactly where it calls stat/lstat on the file, and you see that it... Calls lstat and... It... Returns -1? What the hell#2!
So, you compile a custom binary that calls lstat on the first argument given and prints out everything it returns... And... It works fine!
Until now, I chose to omit one important detail that might have given away the issue to the more knowledgeable right away. Our webservers have the URL /.well-known/acme-challenge/, used for ACME challenges, aliased somewhere else on the filesystem - To /tmp/challenges.
See the issue already?
Some *bleep* over at the Debian Package Maintainer group decided that Apache could save very sensitive data into /tmp, so, it would be for the best if they changed something that worked for decades, and enabled a SystemD service unit option "PrivateTmp" for the webserver, by default.
What it does is that, anytime a process started with this option enabled writes to /tmp/*, the call gets hijacked or something, and actually makes the write to a private /tmp/something/tmp/ directory, where something... Appeared as a completely random name, with the "apache2.service" glued at the end.
That was also the only reason why I managed fix this issue - On the umpteenth time of checking the directory structure, I noticed a "systemd-private-foobarbas-apache2.service-cookie42" directory there... That contained nothing but a "tmp" directory with 777 as its permission, owned by the process' user and group.
Overriding that unit file option finally fixed the issue completely.
I have just one question - Why? Why change something that worked for decades? I understand that, in case you save something into /tmp, it may be read by 3rd parties or programs, but I am of the opinion that, if you did that, its only and only your fault if you wrote sensitive data into the temporary directory.
And as far as I am aware, by default, Apache does not actually write anything even remotely sensitive into /tmp, so...
Why. WHY!
I wasted 4 hours of my life debugging this! Only to find out its just another SystemD-enabled "feature" now!
And as much as I love kidding on SystemD, this time, I see it more as a fault of the package maintainers, because... I found no default apache2/httpd service file in the apache repo mirror... So...8 -
When Amazon asks if my email address is all lower case... The desire to make it an informative moment that email addresses are not case sensitive is outweighed by my desire to resolve my issue as fast as possible.1
-
Just found out today via Reddit that Wells Fargo, American Express (not personally confirmed), and Chase login passwords are NOT case sensitive!
I would check your bank too!2 -
Ibwish I had remembered this when the weekly theme was office pranks.
In the first or second year of high school we covered basic internet security. Stuff like don't follow suspicious urls, don't open suspicious emails and such.
Our teacher let us play around with some sort of simulated desktop environment, where we could execute some hacks like ad popups and such on each other's environment, if we fell for the trap.
Anyways, one hack I found interesting was a hack, that lockes a user out of their virual desktop, until he enters a password, that will be displayed on his environment.
Yes, a very interesting hack, because it contains two obvious yet major design flaws, which I could exploit 😈
1. It's case sensitive
In itself not a problem, but combined with #2, it's fatal.
2. "IlIlllIlI"
Depending on your font, you probably have no idea what exactly I just typed.
Let's just say, the font displayed uppercase i and lowercase L completely undifferentiable.
Guess whom I let suffer.
It was our teacher, who had to demonstrate us some things and who was connected to the same network.
I swear, nothing beats that feeling when your tearcher has go come to you and embarrassingly ask you to "unhack" them, because they can't type it 😂1 -
I had to do a double take... Needless to say I can't sign in for shit, fucknows what mental finger dance I did on the shift key when signing up to these guys...
Also: forgotten password is "please type your email, if there's an account associated to this email address we'll fucking email it with password reset instructions"...
Fucking arsehole fucks, I just wanna pay my fucking energy bill.
-
Worst part of coding lang I love?
C# being case-sensitive.
Not a C# language thing, but I hate the vilification and anti-coding standard of not 'allowing' prefixes. Interfaces are allowed (ex. IUpdateCustomer), why not classes? Why can't I have a DTO and declare it a TCustomer and the zealots not scream "HE'S USING HUNGARIAN NOTATION!!! TAKE HIM TO THE STAKE!!"?19 -
Dear programming languages,
If you had to be case sensitive, then why the fuck can't you settle on whether to use an S or an s for a
S/string declaration.4 -
document.getelementbyid("myid");
Runtime error !
must be "ById"
:/
also same problem with elem.innerHtml
(Correct: elem.innerHTML )2 -
sAleSfoRce aPEx is a hot wet garbage fire. How can I make this actually make this work right when I need to compare case sensitive strings?
 10
10 -
Print("Hello World")
When people design a brand new Postgresql schema (case sensitive) using a mix of upper and lower case letters.
Only to then proceed and escape every single table and column name in every single query.1 -
Sometimes, I feel like tearing my hair out from the way Bash works.
Like... Where other languages have two operators for case-sensitive and insensitive regex matching, bash? It doesn't. It only matches case-sensitively.
And if one wants the insensitive matching? Gotta set a shell option... And if a script wouldn't change it back, who knows what else could break, so of course it has to save its initial state, change it, do its case-insensitive matching, and return it back to its original value.
10/10 experience.14 -
Why fucking windows explorer's search is fucking case-sensitive? I could not find any fucking option for it.
Edit : actually it's not but sometimes it couldnot find files2 -
To all websites requiring at least one upper case, one lower case, one number, one special character, 25 emoji and 49 unicorns in the password when signing up.
If you say something is required, then your regex BETTER be checking ONLY for those things. You should not have hidden requirements for passwords that users are supposed to dream about and know. Especially if it's a super time-sensitive thing that they should have opened 2 Fridays ago.
I had to pull my hair out for 20 minutes (that felt like an hour) before looking at their code and reading their regex. The regex was different from what the page said the requirements actually were. What were they even thinking? 😑
The rest of everything related to this organization uses an SSO system, why can't they just use it? Isn't the whole point of SSO to avoid a different login for every tiny part of the system?
I wonder what the other less technically inclined people using the system are doing right now. Sadly, I have no way of letting them know.
I sincerely hope the dev that made that website faces the same thing while picking a password for creating an account somewhere else and realizes what he/she did.
I really needed to let it out.
I feel much better now.
Time to take out the stress ball :)1 -
I was pissed off beyond all reason yesterday when I realised that the reason my code didnt work for 2 days was because i spelled eForm with an uppercase F in my data model, and a lowercase f in my object classes. There was no way for the compiler to warn me so everything compiled fine but crashed at runtime when I tried to access that property. When I saw it, my head hit the desk....
-
I can't come to terms with people's terrible reasonings.
You read a news about something. Let's assume it has to do with a sensitive topic, like race, gender, culture, religion, something polarizing, that makes you pick 1 of 2 sides.
So what do some people do? They ask themselves "ok what group do I adhere? How do I label myself?".
Then they ask "what do other people in said group/label think about the matter?", sometimes it's people in the media, friends,
sometimes people even create a mental construct of a stereotypical person of said group, a hypothetical one, and use the opinion of said construct as representative.
And final step is a knee jerk reaction of "I believe that too!!!!!!".
Obviously, all of this can't bring no one closer to the theorical truth or the least flawed conclusion.
What does? Case by case basis.
You judge every case as if every case was its own thing.
But why does some people have a hard time doing that? Just general ignorance maybe?
Maybe this tends to occur in families where parents don't teach their kids to challenge their beliefs, or teach them that doing so could result in lack of parental acceptance.
People also have peer pressure, the need to belong and feel accepted. That means sharing the same points of view with close people and considering the opposite taboo.
There's also the very ignorant people that have conspiracies for lunch.
In any case, I feel some people don't even fucking try to be neutral.3 -
nothing new, just another rant about php...
php, PHP, Php, whatever is written, wherever is piled, I hate this thing, in every stack.
stuff that works only according how php itself is compiled, globals superglobals and turbo-globals everywhere, == is not transitive, comparisons are non-deterministic, ?: is freaking left associative, utility functions that returns sometimes -1, sometimes null, sometimes are void, each with different style of usage and naming, lowercase/under_score/camelCase/PascalCase, numbers are 32bit on 32bit cpus and 64bit on 64bit cpus, a ton of silent failing stuff that doesn't warn you, references are actually aliases, nothing has a determined type except references, abuse of mega-global static vars and funcs, you can cast to int in a language where int doesn't even exists, 25236 ways to import/require/include for every different subcase, @ operator, :: parsed to T_PAAMAYIM_NEKUDOTAYIM for no reason in stack traces, you don't know who can throw stuff, fatal errors are sometimes catchable according to nobody knows, closed-over vars are passed as functions unless you use &, functions calls that don't match args signature don't fail, classes are not object and you can refer them only by string name, builtin underlying types cannot be wrapped, subclasses can't override parents' private methods, no overload for equality or ordering, -1 is a valid index for array and doesn't fail, funcs are not data nor objects when clojures instead are objects, there's no way to distinguish between a random string and a function 'reference', php.ini, documentation with comments and flame wars on the side, becomes case sensitive/insensitive according to the filesystem when line break instead is determined according to php.ini, it's freaking sloooooow...
enough. i'm tired of this crap.
it's almost weekend! 🍻1 -
HELP!!
I am starting a new contract to create a full stack web application with a medical company that will contain some sensitive data about their clients/patients.
I have been working as a salaried full-time employee for a medical software company, but I have been shielded from any sort of lawsuits from the client (worst case scenario, I'd get fired).
Do any of you have any advice on what I should do to protect myself in terms of LLC's, Insurances, etc?2 -
my oh my, its my bad, .. dont worry its my bad. you dont have to look at me like that. im sorry cos im asking you about wtf was wrong with code and asking you to fix it.. #case sensitive.
-
HFS, MacBooks standard file system is the answer to that every question asking "what if you don't design well/ how bad can it get."
How can a bloody file system not be case sensitive.
I know you want to be different from *nix
But there would have been better ways1 -
Holy shit. Do NOT open a Wells Fargo banking account. On top of their ridiculous password limitations, your password is NOT CASE SENSITIVE. I tested. Caps lock, no caps, a mix, it doesn't matter.
More info on the password limitations at my other rant https://devrant.io/rants/905148/...3 -
Currently the only 3rd party tokenization VSCode supports is a massive pile of RegEx. There's a whole discussion about how procedural tokenization could be supported without running extension code in the UI thread. The central argument against delegating this to an external worker is that if the reply doesn't arrive fast enough it might interfere with characters typed later.
1. Any computer that can run VSCode can execute somewhere in the order of a _billion_ instructions per second. To a program, the delay between keystrokes is an eternity. The only way to run out of time here is if either the dev isn't aware that the request is time sensitive, or the framework communicates to the OS that the task isn't urgent and an arbitrary amount of work is scheduled before it.
2. Chromium is the pinnacle of cybersecurity and its primary job is to sandbox untrusted user code. You don't need another thread to do it.
3. This use case fits squarely in the original design objectives of Webassembly.1 -
When someone calls me VincentNwonah and expects me to answer. but I'm a programmer and VincentNwonah is a different object from NwonahVincent. ;p
-
This is a repost of an original rant posted on a request for "Community Feedback" from Atlassian. You know, Atlassian? Those beloved people behind such products as :
• Thing I Love™
• Other Thing You Used One Time™
• Platform Often Mentioned in Suicide Notes, Probably™*
Now this rant was written in early 2022 while I was working in an Azure Cloud Engineer role that transformed into me being the company's main Sysadmin/Project Manager/Hiring Manager/Network Admin/Graphic Designer.
While trying to simultaneously put out over 9000 fires with one hand, and jangling keys in the face of the Owner/Arsonist with the other, I was also desperately implementing Jira Service Desk. Normally this wouldn't have been as much of a priority as it was, but the software our support team was using had gone past 15 years old, then past extended support, then the lone developer died, then it didn't work on Windows 10, then only functioned thanks to a dev cohort long past creating a keygen....which was now broken. So we needed a solution *now*.
The previous solution was shit of a different tier. The sight of it would make a walking talking anthropomorphised sentient puddle of dogshit (who both eats and produces further dookie derivatives) blush with embarrassment. The CD-ROM/Cereal Box this software came in probably listed features like "Stores Your Customer's First AND (or) Last Name!" or "Windows ME Downgrade Disk Included!" and "NEW: Less(-ish) Genocide(s)"!
Despite this, our brain/fearless leader decided this would be a great time to have me test, implement, deploy, and train everyone up on a new solution that would suck your toes, sound your shaft, and that he hadn't reminded me that I was a lazy sack enough lately.
One day, during preliminary user testing I received an email letting me know that the support team was having issues with a Customer's profile on our new support desk. Thanks to our Owner/Firestarter/Real World Micheal Scott being deep in his latest project (fixing our "All 5 devs quit in the last 12 months and I can't seem to hire any new ones" issue (by buying a ping pong table)), I had a bit of fortuitous time on my hands to investigate this issue. I had spent many hours of overtime working on this project, writing custom integrations and automations, so what I found out was crushing.
Below is the (digitally) physical manifestation of my rage after realising I would have to create / find / deal with a whole new method for support to manage customer contacts.
I'm linking to the original forum thread because you kind of need to have the pictures embedded in said reply to get really inhale the "Jira-Rant" ambiance. The part where I use several consecutive words as anchor links to tickets with other people screaming into the void gets a bit sweet n' savoury too - having those hyperlinks does improve the je ne say what of it all.
bit.ly/JIRANT (Case Sensitive)
--------------------------
There is some good news at the end of this brown n' squirty rainbow though!
Nice try silly little Jira button, you can't ruin *my* 2022!
• I was able to forget all about Jira a month later when I received a surprise vacation home! (To be there while my Mom passed away).
• Eventually work stress did catch up to me - but my boss thoughtfully gave me a nice long vacation! (By assaulting *while* firing me (for emailing in a vacation request while he was a having a bad (see:normal) day)) 5
5 -
Cybersecurity Firm For Cryptocurrency Scam Review // PASSCODE CYBER RECOVERY
My name it's Eddie West and here it's my encounter with a fraudulent sinero. I connected with someone on Instagram who appeared genuine. Our interactions began innocuously, characterized by light-hearted banter and shared interests. As days morphed into weeks, we engaged in daily conversations, exchanging personal anecdotes and cultivating a sense of trust. I felt emboldened to divulge sensitive details about my life, convinced I had found a true confidant. However, this misplaced trust would soon lead to a harrowing ordeal.One fateful day, the tone of our exchanges took a sinister turn. The individual I believed I knew transformed into a menacing figure, demanding that I remit 125,000 USDT or face the exposure of my private information. A wave of panic engulfed me as I grasped the potential ramifications of her threats. Fearing the catastrophic fallout from having my personal details unveiled, I reluctantly acquiesced and transferred the funds, hoping this would quell the harassment. Yet, after the transaction, she vanished, blocking me on all platforms. It became painfully evident that I had fallen prey to a sophisticated blackmail and crypto scam.
Devastated and desperate to reclaim my stolen assets, I embarked on a quest for solutions. This search led me to Passcode Cyber Recovery, a cybersecurity firm renowned for its expertise in crypto fraud investigations and asset recovery. Initially skeptical yet hopeful, I reached out to them for assistance.
The team at Passcode Cyber Recovery sprang into action with remarkable efficiency. They commenced by meticulously analyzing the blockchain transactions pertinent to my case, employing advanced forensic tools to trace the USDT transfer. Their expertise enabled them to pinpoint the scammer’s wallet and track the funds as they traversed multiple exchanges. Recognizing the urgency of the situation, they collaborated with law enforcement and various exchange platforms to freeze the assets before they could be laundered. Within a mere 72 hours, Passcode Cyber Recovery successfully located the stolen USDT and initiated a comprehensive recovery process. They provided me with detailed evidence, including transaction logs and the scammer’s digital footprints, which significantly bolstered my case. Thanks to Passcode Cyber Recovery unwavering diligence and expertise, I was able to recover the full amount of 125,000 USDT.If you find yourself in a situation similar to mine, where trust has been exploited and you've fallen victim to a scam, I highly recommend reaching out to Passcode Cyber Recovery. Their team of experts specializes in cybersecurity and crypto fraud investigations, and they have a proven track record of successfully recovering stolen assets.
PASSCODE CYBER RECOVERY
WhatsApp: +1(647)399-4074
Telegram : @passcodecyberrecovery9 -
**BITCOIN RECOVERY EXPERTS REVIEW → HACKATHON TECH SOLUTIONS**
Bitcoin continues to grow in popularity in 2025, the need for effective recovery services has become more crucial than ever, especially for victims of scams. HACKATHON TECH SOLUTIONS stands out as a leading provider, specializing in recovering Bitcoin and other digital assets taken by scammers. The complexities of Bitcoin and its decentralized nature create unique challenges in these cases, but HACKATHON TECH SOLUTIONS is equipped with the expertise to navigate these obstacles and help clients reclaim their funds.Scammers often target Bitcoin users through fraudulent schemes, such as phishing attacks, fake investment opportunities, and fraudulent exchanges. When victims fall prey to these scams and lose their Bitcoin, HACKATHON TECH SOLUTIONS offers a reliable solution. The company uses advanced techniques to trace and recover funds, leveraging its deep understanding of blockchain technology to track stolen assets. Despite Bitcoin’s pseudonymous nature, HACKATHON TECH SOLUTIONS skilled team is able to tackle these challenges effectively, giving scam victims hope of recovering their stolen assets.Security is a primary concern, especially when dealing with sensitive information. HACKATHON TECH SOLUTIONS ensures that all client data remains confidential and secure throughout the recovery process. They implement stringent security measures, offering peace of mind to those seeking help. With a focus on professionalism and client care, HACKATHON TECH SOLUTIONS handles each case with the utmost respect and discretion.The irreversible nature of Bitcoin transactions makes recovery particularly challenging for scam victims, highlighting the importance of a trusted recovery service. HACKATHON TECH SOLUTIONS understands the emotional toll of being scammed and works diligently to provide a smooth, reassuring recovery experience. As the cryptocurrency space continues to evolve, the demand for reliable recovery services like those offered by HACKATHON TECH SOLUTIONS will only grow, solidifying their position as a leader in the industry. You can contact them using the details provided below.
Whatsapp: → +3, 1, 6, 4, 7, 9, 9, 9, 2, 5, 6
Telegram: → @ hackathon tech solutions
Email: → hackathontechservice@mail(.)com2 -
RESTORE BACK YOUR LOST USDT TODAY WITH TRUSTED EXPERTS - HIRE SALVAGE ASSET RECOVERY
I connected with someone on Instagram who appeared genuine. Our interactions began innocuously, characterised by light-heated banter and shared interests. As days morphed into weeks, we engaged in daily conversations, exchanging personal anecdotes and cultivating a sense of trust. I felt emboldened to divulge sensitive details about my life, convinced I had found a true confidant. However, this misplaced trust would soon lead to a harrowing ordeal.One fateful day, the tone of our exchanges took a sinister turn. The individual I believed I knew transformed into a menacing figure, demanding that I remit 125,000 USDT or face the exposure of my private information. A wave of panic engulfed me as I grasped the potential ramifications of her threats. Fearing the catastrophic fallout from having my personal details unveiled, I reluctantly acquiesced and transferred the funds, hoping this would quell the harassment. Yet, after the transaction, she vanished, blocking me on all platforms. It became painfully evident that I had fallen prey to a sophisticated blackmail and crypto scam.
Devastated and desperate to reclaim my stolen assets, I embarked on a quest for solutions. This search led me to Salvage Asset Recovery, a cyber security firm renowned for its expertise in crypto fraud investigations and asset recovery. Initially sceptical yet hopeful, I reached out to them for assistance.
The team at Salvage Asset Recovery sprang into action with remarkable efficiency. They commenced by meticulously analysing the blockchain transactions pertinent to my case, employing advanced forensic tools to trace the USDT transfer. Their expertise enabled them to pinpoint the scammer’s wallet and track the funds as they traversed multiple exchanges. Recognising the urgency of the situation, they collaborated with law enforcement and various exchange platforms to freeze the assets before they could be laundered. Within a mere 72 hours, Salvage Asset Recovery successfully located the stolen USDT and initiated a comprehensive recovery process. They provided me with detailed evidence, including transaction logs and the scammer’s digital footprints, which significantly bolstered my case. Thanks to Salvage Asset Recovery unwavering diligence and expertise, I was able to recover the full amount of 125,000 USDT.If you find yourself in a situation similar to mine, where trust has been exploited and you've fallen victim to a scam, I highly recommend reaching out to Salvage Asset Recovery. Their team of experts specialises in cyber security and crypto fraud investigations, and they have a proven track record of successfully recovering stolen assets. If you need help Contact Salvage asset recovery via below =
TELEGRAM---@Salvageasset
Whats App+ 1 8 4 7 6 5 4 7 0 9 62 -
Microsoft Teams login says password is incorrect then and for a captcha
I type it again but fails...
I'm like wtf... Could it be the captcha...
Which I entered in all lowercase
It doesn't say the captcha is case sensitive though..
Next few times it gives me captchas with k... Teehee me like 5 tries to login
Are we trying to verify passwords/humanness or whether I can somehow tell the difference between K and k?1 -
I was frustrated when I lost almost all my life savings to a cryptocurrency scammer. I had invested a significant amount of money in a promising project, but it turned out to be a fraudulent scheme. I was left with nothing but a trail of broken dreams and a lighter wallet. I was devastated, to say the least. I had never felt so helpless in my life. I didn't know where to turn to or who to trust. I was at a crossroads, unsure of what to do next. That's when I stumbled upon Cranix Ethical Solutions Haven online. I saw their testimony and reviews from people who had similar experiences to mine. They claimed to have recovered their stolen cryptocurrency with the help of Cranix Ethical Solutions Haven. At first, I was skeptical. I didn't know if I could trust another company with my sensitive information. But something about Cranix Ethical Solutions Haven resonated with me. Maybe it was their professionalism, or maybe it was their commitment to helping people like me. Whatever it was, I decided to take a chance and reach out to them. I contacted Cranix Ethical Solutions Haven and explained my situation to them. They listened attentively, asking questions and gathering information about my case. They were empathetic and understanding, and I felt a sense of comfort knowing that I was in good hands. They told me that they would do everything in their power to help me recover my stolen cryptocurrency, I was amazed at how quickly they got to work. Within 24 hours, they had already started making progress on my case. They kept me updated every step of the way, explaining what they were doing and why. I was impressed by their expertise and their dedication to their craft.
In the end, Cranix Ethical Solutions Haven was able to recover my stolen cryptocurrency in its entirety. I was overjoyed, to say the least. I couldn't believe that I had finally gotten my money back. It was a huge weight off my shoulders, and I felt a sense of relief wash over me. I want to take this opportunity to thank Cranix Ethical Solutions Haven for their help. They truly are a lifesaver. Without them, I would still be struggling to recover my losses. They are a beacon of hope for people like me who have been victimized by cryptocurrency scammers. If you're reading this and you're in a similar situation, I urge you to reach out to Cranix Ethical Solutions Haven via EMAIL: (cranixethicalsolutionshaven @ post . com) or WHATSAPP: (+4,4,7,4,6,0,6,2,2,7,3,0), WEBSITE: (https: // cranixethicalsolutionshaven . info) TELEGRAM: (@ cranixethicalsolutionshaven). They are the real deal, and they can help you recover your stolen cryptocurrency. Don't hesitate, don't wait - contact them today and let them work their magic. In conclusion, I want to say that Cranix Ethical Solutions Haven is a trustworthy and reliable company that can help you recover your stolen cryptocurrency. They are professional, efficient, and effective. They truly care about their clients and will stop at nothing to help them. I am forever grateful to them, and I know that you will be too if you give them a chance.2 -
Hire a Trusted Company for Recovery of Lost Bitcoin — CryptoChain Global Track
The rapid growth of the cryptocurrency industry has created both opportunity and risk. While digital assets like Bitcoin offer financial freedom, privacy, and accessibility, they also attract cybercriminals who exploit unsuspecting users. From investment scams to phishing attacks, hacked wallets to fraudulent trading platforms, Bitcoin holders around the world are increasingly falling victim to schemes that result in serious financial loss. When this happens, finding a reliable, professional recovery service becomes a critical step forward.
CryptoChain Global Track is a trusted and recognized name in the field of cryptocurrency recovery. The company is known for helping individuals and businesses who have lost Bitcoin due to scams, unauthorized access, or transactional errors. Backed by a team of skilled blockchain analysts, ethical hackers, and forensic investigators, CryptoChain Global Track offers a lifeline to those who thought their assets were gone forever.
Unlike many services that overpromise and underdeliver, CryptoChain Global Track works with complete transparency and professionalism. Their recovery process begins with a detailed analysis of the client’s situation. This includes examining the blockchain data, wallet transactions, and any communication or documentation related to the scam or loss. Using advanced tools, the team can trace the movement of Bitcoin through multiple wallets and platforms, even if the funds have been moved through mixing services or converted into other cryptocurrencies.
The company's success is rooted in its deep understanding of blockchain networks and how digital criminals operate. Their technical capabilities allow them to identify patterns, pinpoint destination wallets, and in many cases, work directly with exchanges or law enforcement to flag suspicious accounts. Every case is approached with careful investigation, guided by facts and real-time data—not assumptions or generic solutions.
Trust is a key part of any recovery process, especially when dealing with sensitive financial matters. CryptoChain Global Track treats every case with discretion and ensures that clients remain informed throughout the investigation. From initial assessment to asset tracking and follow-up actions, communication is clear and consistent. Clients are not charged upfront for empty promises—they receive honest evaluations and tailored solutions based on the nature of their case.
Beyond technical expertise, CryptoChain Global Track is also committed to client support and education. Many Bitcoin losses occur because of a lack of awareness about threats in the crypto space. The company takes time to educate its clients about how the breach or scam occurred and provides practical advice to help them avoid similar situations in the future. This commitment to both recovery and prevention makes the service holistic and genuinely helpful.
A trusted solution is available—and it starts by connecting with a team that understands how to fight back against crypto fraud with skill and determination.6 -
Recover My Stolen Crypto | Cryptocurrency Investment With Lee Ultimate Hacker
LEEULTIMATEHACKER @ AOL . COM
telegram: LEEULTIMATE
wh@tsapp +1 (715) 314 - 9248
https :// leeultimatehacker. com
My initial engagement with Lee Ultimate Hacker was marked by clarity and transparency, which immediately set a positive tone. Their willingness to explain the services they offer and the steps involved made it clear that they were a professional and trustworthy firm. This strong first impression prompted me to further investigate the company’s background and operations, and what I discovered reinforced my confidence in their capabilities. Lee Ultimate Hacker has a notable history of successful engagements across a variety of complex services. They have built a reputation for expertise in phone surveillance, private investigations, and cryptocurrency recovery. Their approach to phone surveillance is especially noteworthy. The company uses ethical and legal methods to gather data, ensuring compliance with all relevant laws and securing the necessary authorizations before proceeding. This careful adherence to legal guidelines is crucial for anyone seeking these services, as it ensures the protection of privacy and the integrity of the process. In addition to phone surveillance, Lee Ultimate Hacker is highly regarded for its work in private investigations. Their process is marked by thorough fact-finding and a commitment to confidentiality. They handle sensitive information with the utmost care, ensuring that every aspect of an investigation adheres to legal parameters. Their attention to detail and dedication to delivering accurate results make them a reliable choice for anyone in need of investigative services. One of the most compelling aspects of Lee Ultimate Hacker is their expertise in cryptocurrency recovery. The world of digital currency can be complex and challenging, especially when it comes to recovering lost or stolen assets. Lee Ultimate Hacker stands out in this area due to their deep understanding of blockchain technology and digital forensics. They navigate the intricate networks of cryptocurrency exchanges and regulatory systems with ease, offering effective solutions to individuals seeking to recover their funds. The company’s track record is further supported by numerous client testimonials and case studies, which are available on their website and verified through independent sources. The consistent positive feedback from satisfied clients speaks to the firm’s ability to deliver on their promises. This solid reputation, combined with their extensive expertise in multiple domains, made me feel confident in choosing Lee Ultimate Hacker to handle my cryptocurrency recovery needs. Their combination of transparency, ethical standards, and proven success positions them as a standout option in this field, and I felt assured that I had made the right choice.1 -
HOW DO I RECOVER MY SCAMMED ETHEREUM & BITCOIN CONTACT SPARTAN TECH GROUP RETRIEVAL
As a truck driver in Manassas, I frequently rely on notarized documents for business transactions. Recently, I needed several documents notarized urgently and found an online provider offering services through a platform called Rednote. The website appeared professional, and they quoted me $7,800 USD for the notarization, which seemed fair given the amount of paperwork involved. I decided to proceed and made the payment via online transfer.However, after paying, I received no communication, and my attempts to contact the provider went unanswered. Days passed without any updates, and it soon became clear I had been scammed. The situation worsened when I noticed unusual activity in my accounts. My email was hacked, and I began receiving notifications about unauthorized login attempts and changes. Upon further investigation, I discovered the scammers had accessed my Binance crypto wallet. They stole a significant portion of my savings, including Bitcoin and other altcoins. Between the payment to the fraudulent notarization service and the stolen crypto assets, I lost over $7,800 USD.Desperate, I reached out to SPARTAN TECH GROUP RETRIEVAL, a professional service specializing in helping victims of online scams. I found them through their bio and provided all the details of my case, including the compromised email and crypto wallet. SPARTAN TECH GROUP RETRIEVAL acted swiftly, using digital forensics and legal processes to investigate the fraud. Their team worked tirelessly to trace the scammers' activities and identify the fraudulent payment channels. They also helped secure my email and crypto wallet to prevent further damage.After several days of investigation, SPARTAN TECH GROUP RETRIEVAL managed to recover a portion of my $7,800 USD and helped secure my stolen crypto assets. Although the experience was stressful, I was relieved to see some of my funds returned. The professionalism and dedication of SPARTAN TECH GROUP RETRIEVAL were invaluable, and they kept me updated throughout the process.This taught me the importance of carefully vetting online services, especially when dealing with sensitive information like notarized documents and cryptocurrency. I now take extra precautions with my email accounts and crypto wallets to protect against future scams. If you find yourself in a similar situation, I highly recommend contacting SPARTAN TECH GROUP RETRIEVAL for their expertise in tracking scammers and securing online accounts.
REACH OUT TO SPARTAN TECH GROUP RETRIEVAL ON THEIR CONTACT INFO BELOW:
Website: h t t p s : / / spartan tech group retrieval . o r g
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 4
4 -
BEST CRYPTO RECOVERY EXPERT TO RECOVER SCAMMED CRYPTO-VISIT RAPID DIGITAL RECOVERY
As a college student in California, it’s not uncommon to hear about the latest investment opportunities or tips on how to make money in the cryptocurrency world. However, like many of my peers, I recently learned the hard way how easily scams can target people who are unfamiliar with the risks. It all started when a fellow student posted on social media about a seemingly legitimate investment opportunity involving Bitcoin. The post was persuasive, offering high returns with minimal risk, and naturally, a few of us, myself included, jumped on the chance to invest. Sadly, the investment turned out to be a scam, and I, along with a few others, found ourselves with our Bitcoin stolen. It’s a frustrating and helpless feeling, especially when you realize how much you’ve lost. After some research and frantic searching for solutions, I came across Rapid Digital Recovery a cryptocurrency recovery service that seemed like it might be able to help. The service specializes in recovering stolen digital assets, including Bitcoin, using advanced forensic methods. From what I gathered, their team consists of experts who track fraudulent transactions and trace stolen funds across blockchain networks, which gave me some hope that my investment could be recovered. What stood out to me about Rapid Digital Recovery was their approach to each case. They don’t take a one-size-fits-all approach; instead, they tailor their recovery strategies based on the specific details of the scam. This personalized approach is critical, especially in cases where the stolen cryptocurrency has been moved across multiple wallets or exchanges. Their team also offers guidance on improving security, which is something that, in hindsight, could have saved me from falling for the scam in the first place. While I was initially skeptical about turning to a recovery service, Rapid Digital Recovery’s transparency helped alleviate some of my concerns. They kept me updated throughout the process and were patient in answering all of my questions. However, I quickly realized that, like any service in the crypto space, it’s essential to proceed with caution. Scams are rampant in this industry, and it’s always important to thoroughly vet any service before sharing sensitive information. In the end, while I’m still in the process of recovering my lost Bitcoin, I’ve learned an invaluable lesson about the risks involved in cryptocurrency investments. If you ever find yourself in a similar situation, Rapid Digital Recovery might be worth considering, but remember to do your own research and take steps to ensure you’re working with Rapid Digital recovery.
Resch Out To Them Via:
Whatsapp: +1 4 14 80 71 4 85
Email: rapid digital recovery (@) execs. com
Telegram: h tt ps: // t. me / Rapid digital recovery11 -
HOW TO HIRE A HACKER TO RECOVER SCAMMED CRYPTO HIRE ADWARE RECOVERY SPECIALIST
The journey towards recovering lost or stolen cryptocurrency can often feel like a perilous trial, fraught with uncertainty and the ever-present risk of falling victim to malicious scams. Website info: https ://adware recovery specialist. com
This was the experience I faced when I found myself in the midst of an Ethereum (ETH) recovery ordeal, navigating a maze of false promises and deceptive tactics. WhatsApp info:+12723 328 343
Just when hope seemed to dwindle, a glimmer of light emerged in the form of ADWARE RECOVERY SPECIALIST, a service that would prove instrumental in guiding me through the treacherous waters of crypto recovery. What began as a straightforward attempt to reclaim my rightful ETH holdings quickly descended into a disheartening encounter with a sophisticated hoax. Seemingly legitimate recovery "experts" emerged from the shadows, offering their services and assurances of a swift and successful resolution. Lured by their convincing rhetoric and the prospect of regaining my lost assets, I entrusted them with sensitive information, only to watch helplessly as they vanished into the digital ether, taking my ETH with them. Email info: Adwarerecoveryspecialist@ auctioneer. net The emotional toll of this betrayal was immense, as I grappled with the realization that my efforts had been thwarted by unscrupulous individuals exploiting the vulnerabilities of the crypto landscape. Just when I had resigned myself to the possibility of a permanent loss, I discovered ADWARE RECOVERY SPECIALIST, a service that would ultimately prove to be my salvation. Unlike the charlatan recovery "experts" I had encountered, ADWARE RECOVERY SPECIALIST approached my case with a level of professionalism, empathy, and unwavering commitment that restored my faith in the recovery process. Through their meticulous investigations, cutting-edge techniques, and dogged determination, they were able to trace the path of my stolen ETH and orchestrate its safe return to my rightful possession. The trial of recovery had been arduous, marked by setbacks and the constant threat of further exploitation. Yet, with the steadfast support of ADWARE RECOVERY SPECIALIST, I emerged from this ordeal with a renewed appreciation for the resilience of the human spirit and the power of legitimate, ethical service providers to navigate the complex and often treacherous world of cryptocurrency recovery. Telegram info: https ://t.me/adware recovery specialist1 This experience has forever shaped my understanding of the crypto ecosystem and the importance of exercising caution and discernment when seeking assistance in such matters. To anyone facing the same heart-wrenching situation, don't waste any more time or money on companies that are only interested in making empty promises. ADWARE RECOVERY SPECIALIST stands as a beacon of professionalism in a field often riddled with scams. Their efforts are genuine, their expertise is unmatched, and their results speak for themselves. Thanks to them, my ETH is back where it belongs, and I couldn’t be more grateful.2 -
IS IT POSSIBLE TO RECOVER LOST/STOLEN CRYPTO YES CONSULT FUNDS RECLAIMER COMPANY
My name is Judith, and I’m from Austin, Texas. In early January 2025, I found myself facing one of the darkest chapters of my life. I had fallen victim to a fraudulent cryptocurrency broker and, in a matter of days, lost an astonishing $187,000. The money I had worked tirelessly to save and invest vanished in the blink of an eye, leaving me emotionally and financially devastated. The sense of hopelessness that took over was overwhelming, and I couldn’t see a way out. In the midst of my despair, I stumbled upon FUNDS RECLIAMER COMPANY. At first, I was understandably skeptical. After all, I had already been burned by scammers, and the thought of trusting another service seemed like a risky proposition. However, something about their website and the glowing reviews from others in similar situations made me hesitate long enough to give them a chance. From my very first interaction with FUNDS RECLIAMER COMPANY, I knew I had made the right decision. The team was not only professional and highly knowledgeable, but they were also empathetic and sensitive to the emotional impact of my situation. They took the time to explain everything to me clearly, outlining how they would approach the recovery process and giving me a sense of control over what was happening. I appreciated their transparency and the way they patiently answered all of my questions, no matter how small they seemed. What truly took me by surprise was how quickly they acted. Within just four days, FUNDS RECLIAMER COMPANY had successfully tracked down and recovered the majority of my funds. I couldn’t believe how efficient and skilled they were. It was a level of service I hadn’t expected, and it gave me a renewed sense of hope. The fear and anxiety that had been clouding my every thought began to lift. Thanks to FUNDS RECLIAMER COMPANY, I not only regained my financial assets but also my peace of mind. They showed me that even in the darkest times, there are professionals out there who can make a difference. I can’t stress enough how invaluable their support has been during this challenging period of my life. If you find yourself in a similar situation, I highly recommend FUNDS RECLIAMER COMPANY. Their team specializes in financial and cyber security recovery, and they approach each case with unparalleled dedication and professionalism. They gave me back my hard-earned money and, more importantly, my hope for the future. Don’t hesitate to reach out to them via email they are ready to help, and I’m confident they can guide you through the recovery process with the same care they showed me.
Email: fundsreclaimer(@) c o n s u l t a n t . c o m OR fundsreclaimercompany@ z o h o m a i l . c o m
WhatsApp:+1 (361) 2 5 0- 4 1 1 0
Website: h t t p s :/ / fundsreclaimercompany . c o m 1
1 -
Legitimate Crypto Recovery Companies: Puran Crypto Recovery Leads the Way
As cryptocurrency grows as a preferred investment, so do the risks of falling victim to scams and technical errors. With individuals losing significant digital assets, the role of legitimate recovery companies becomes vital. Among these, Puran Crypto Recovery (PCR) stands out as a reliable name in the field. This article explores how PCR and other legitimate companies help victims reclaim their assets and offers tips for safeguarding crypto investments.
The Rise of Crypto Scams
Crypto scams have surged in recent years, targeting unsuspecting investors with increasingly sophisticated tactics. From phishing schemes and fake ICOs to Ponzi scams, fraudsters exploit the decentralized and anonymous nature of blockchain transactions. Victims often find themselves at a loss for recourse, emphasizing the importance of specialized recovery services like Puran Crypto Recovery.
Characteristics of Legitimate Crypto Recovery Companies
Legitimate crypto recovery firms share several defining traits:
Transparency: Reputable firms like PCR disclose information about their team, methods, and licenses.
Expertise: Companies should employ seasoned blockchain analysts and recovery specialists familiar with tracking stolen or inaccessible assets.
Proven Success: Positive testimonials and successful case studies bolster credibility. PCR, for instance, has earned trust through its consistent recovery outcomes.
Client-Centric Approach: Clear communication, confidentiality, and client advocacy are hallmarks of legitimate providers.
How to Verify a Crypto Recovery Service
Before entrusting any company, conduct thorough due diligence:
Research: Look up the company online, checking for reviews and any past controversies.
Compliance: Verify the firm’s regulatory standing to ensure it operates within legal frameworks.
References: Contact past clients for firsthand feedback on the company's performance.
With PCR, clients gain peace of mind knowing they are engaging a service with a stellar reputation and transparent processes.
Why Choose Puran Crypto Recovery?
Puran Crypto Recovery leads the industry with its advanced recovery techniques and commitment to ethical practices. Here’s what sets PCR apart:
Free Consultations: PCR provides an initial assessment to determine the feasibility of recovering lost assets.
Advanced Tools: Employing cutting-edge blockchain forensics, the team meticulously traces transactions and identifies illicit activities.
Collaborative Efforts: PCR works closely with clients to gather evidence, trace funds, and, if necessary, initiate legal action.
These qualities make PCR a top choice for victims seeking reliable crypto recovery services.
Tips to Safeguard Your Crypto Assets
While services like PCR provide hope for reclaiming lost funds, prevention remains the best approach. Follow these tips to protect your assets:
Secure Your Wallets: Use wallets with multi-factor authentication and cold storage solutions for long-term holdings.
Create Strong Passwords: Avoid using easily guessable credentials and ensure passwords are unique for each platform.
Stay Updated: Keep abreast of the latest scam techniques to recognize potential threats.
Avoid Sharing Keys: Never disclose private keys or sensitive wallet information, even to seemingly legitimate inquiries.
Conclusion
In a landscape fraught with scams and risks, legitimate crypto recovery companies like Puran Crypto Recovery offer a lifeline to victims of fraud. By combining expertise, transparency, and advanced tools, PCR has emerged as a leader in helping individuals reclaim their stolen assets.
However, prevention is always better than cure. Secure your investments, remain vigilant, and trust only proven recovery services like PCR if the need arises. With diligence and trusted support, you can navigate the cryptocurrency world confidently and securely.
FAQs
Q1: What is a crypto recovery service?
A crypto recovery service helps individuals retrieve lost or stolen cryptocurrency assets using forensic techniques and blockchain expertise.
Q2: How do I verify a recovery company’s legitimacy?
Look for transparency, licenses, and positive client reviews. Contact previous clients to assess their experience.
Q3: Can I recover lost private keys?
Yes, experienced companies like PCR often assist in recovering lost private keys or regaining access to wallets.
Q4: How much do crypto recovery services cost?
Costs vary depending on the complexity of the case. PCR offers free consultations to assess recovery prospects.
Q5: How can I avoid scams?
Use secure wallets, set strong passwords, and remain cautious of unsolicited emails or requests for private keys.1 -
I was scammed by an Instagram account pretending to be a celebrity. I engaged with this scammer for five months through WhatsApp and ended up sending money via Bitcoin. The scammer then coerced me into providing my banking login details, leading them to steal $20,000 from my unemployment funds. They convinced me that they had routed cash to my account, and they deliberately avoided giving me any time to verify this supposed transaction, ultimately taking advantage of my trust. Throughout this ordeal, the scammer was incredibly patient and manipulative, waiting for eight months before I finally became suspicious and decided to expose them.
I made a video on WhatsApp detailing the scam, hoping it would help others avoid falling into the same trap. However, by then, my financial situation had become dire. The scammer demanded that I send Bitcoin via an ATM, continuing their deception even as I sought a resolution. Fortuitously, just as I was nearing desperation, I discovered BOTNET CRYPTO RECOVERY.
They stepped in at a crucial moment and managed to recover my $20,000. Their timely intervention and expertise in fund recovery proved to be a lifesaver.
The team at BOTNET CRYPTO RECOVERY is truly skilled in their field, demonstrating an impressive capability to not only recover stolen funds but also to expose and dismantle scam operations. Their service was exceptional. They provided clear communication and actionable strategies, working diligently to ensure that my money was returned. The recovery process was handled with the utmost professionalism and efficiency. Seeing my funds returned was a huge relief, and it was evident that BOTNET CRYPTO RECOVERY was well-versed in handling such complex and sensitive situations. I have since recommended BOTNET CRYPTO RECOVERY to several friends and colleagues, all of whom have been equally impressed with their services. They have become my go-to recommendation for anyone dealing with similar issues, whether it involves recovering lost funds or addressing various online scams. Their expertise extends beyond just recovery; they offer comprehensive solutions for individuals and businesses facing financial fraud.
BOTNET CRYPTO RECOVERY’s ability to address both hacking and fund recovery issues has been invaluable to me. They have various skills and strategies for tackling these challenges, and their success in helping me recover my stolen funds speaks volumes about their capabilities. They approach each case with a unique strategy tailored to the specifics of the situation, ensuring the best possible outcome for their clients. Reflecting on my experience, I am immensely grateful for the intervention of BOTNET CRYPTO RECOVERY. Their support has not only helped me regain my lost funds but also provided me peace of mind during a highly stressful period.
The professionalism and dedication demonstrated by their team have solidified my confidence in their services. If you find yourself in a situation involving financial fraud or scams, I highly recommend reaching out to BOTNET CRYPTO RECOVERY. Their proven track record and specialized expertise make them a top choice for recovering stolen funds and tackling online scams. They have been instrumental in my financial recovery, and their assistance has made a significant difference in my life.
EMAIL THEM: chat@botnetcryptorecovery.info -
The day everything changed for me was when I fell victim to an ETH scam. I had invested a significant amount of money in what I thought was a legitimate cryptocurrency project, only to find out that it was all a scam. I was devastated, not just because of the financial loss, but also because I had trusted the platform and the people behind it. I felt lost and betrayed, unsure of what to do next. That's when a friend recommended Kay Nine Cyber Services to me. At first, I was hesitant - after all, I had just been scammed once, and I didn't want it to happen again. But my friend assured me that Kay Nine Cyber Services was different, that they had helped him recover from a similar situation before. With a heavy heart and a glimmer of hope, I reached out to Kay Nine Cyber Services From the very beginning, I was impressed by their professionalism and dedication to helping me. They listened to my story without judgment, offering me reassurance and support every step of the way. The team at Kay Nine Cyber Services took on my case with determination and expert knowledge. They meticulously reviewed the evidence of the scam, analyzing the blockchain transactions and tracing the flow of funds. It was like watching a group of digital detectives at work, unraveling the complex web of fraud that had ensnared me.
I began to see progress.Kay Nine Cyber Services uncovered crucial information that led to the identification of the scammers and the recovery of my lost funds. They kept me informed at every stage, patiently explaining the technical details and legal processes involved in the recovery. But it wasn't just about the money for me. Kay Nine Cyber Services restored my trust in the online world, showing me that there are still honest and reliable professionals out there who genuinely care about their clients. They went above and beyond to ensure that I felt supported and empowered throughout the entire process. Innovative Kind of Creativity was a phrase that kept coming to mind as I worked with Kay Nine Cyber Services. Their innovative approach to cybercrime recovery was truly impressive, combining cutting-edge technology with old-fashioned values of integrity and trust. They weren't just focused on recovering my funds - they were dedicated to restoring my faith in humanity. It wasn't long before Kay Nine Cyber Services succeeded in recovering my lost funds and holding the scammers accountable for their crimes. The sense of justice and closure I felt was indescribable, a mix of relief, gratitude, and renewed hope for the future. My experience with Kay Nine Cyber Services was nothing short of excellent. They exceeded all my expectations, going above and beyond to deliver results that truly made a difference in my life. I can now say with confidence that I trust Kay Nine Cyber Services with my most sensitive information and my most significant financial assets, knowing that they will always have my back.
Send a message via Whatsapp:+1 58148185905 -
Buy Verified Cash App Accounts
In today's fast-paced digital world, mobile payment apps have revolutionized the way we handle financial transactions. Cash App, a popular mobile payment service, has gained widespread recognition for its user-friendly interface and seamless money transfer capabilities. As the demand for Cash App accounts increases, the significance of obtaining a verified account becomes more apparent. In this article, we will explore the concept of purchasing verified Cash App accounts, understanding its benefits, potential risks, and essential tips for a secure and successful transaction.
Understanding Cash App
What is Cash App?
Cash App, also known as Square Cash, is a peer-to-peer mobile payment service that allows users to send, receive, and request money through their smartphones. With its straightforward design and hassle-free functionality, Cash App has become a preferred choice for individuals and businesses alike.
How does Cash App work?
Cash App operates by connecting to the user's bank account or debit card, facilitating seamless and instant money transfers to other Cash App users. Users can also load funds onto their Cash App balance, known as the "Cash Card," to make purchases or withdraw cash from ATMs.
Importance of Verified Cash App Accounts
Security and Safety
Having a verified Cash App account adds an extra layer of security to your financial transactions. Verified accounts undergo a thorough verification process, which helps ensure the legitimacy of the user and reduces the risk of unauthorized access.
Transaction Limits and Benefits
Verified Cash App accounts come with higher transaction limits, allowing users to send larger amounts of money. Moreover, verified users may have access to exclusive promotions and rewards offered by Cash App.
Ease of Use
With a verified account, users can seamlessly link their bank accounts or cards to the app, streamlining the process of sending and receiving money.
Risks and Concerns
Scams and Fraudulent Accounts
One of the primary concerns when considering the purchase of Cash App accounts is the presence of scams and fraudulent sellers. Dealing with unreliable sources can lead to financial losses and potential misuse of personal information.
Violation of Terms of Service
Buying or selling Cash App accounts is against the platform's terms of service. If discovered, such accounts may be subject to suspension or permanent banning, resulting in the loss of funds and access to Cash App services.
Identity Theft
Using a purchased Cash App account without changing the login credentials can expose the buyer to identity theft. It is crucial to take necessary precautions to safeguard sensitive information.
Buying Verified Cash App Accounts
Reputable Sources
When seeking to buy a Cash App account, it is essential to choose reputable and trustworthy sources. Conduct thorough research, read customer reviews, and seek recommendations from reliable sources before making a decision.
Verification Process
Before making a purchase, ensure that the seller provides a transparent explanation of their verification process. The verification process should align with Cash App's guidelines and industry best practices.
Tips for Safe Purchase
Research the Seller
Thoroughly research the background and reputation of the seller before proceeding with the purchase. Avoid dealing with sellers who have a history of negative reviews or questionable practices.
Verify Account Authenticity
After purchasing a Cash App account, verify its authenticity by logging in and reviewing the account details. If any discrepancies are found, contact the seller immediately.
Use Secure Payment Methods
Opt for secure payment methods, such as PayPal or credit cards, that offer buyer protection in case of fraudulent transactions.
Change Login Credentials
To protect against identity theft, change the login credentials (username and password) of the purchased account immediately after the transaction.
Using a Purchased Cash App Account
Linking Bank Accounts and Cards
After acquiring a Cash App account, link it to your bank accounts or debit cards to enable seamless transactions.
Investing and Trading
For users interested in investing or trading stocks through Cash App, the verified account provides a secure platform to explore investment opportunities.
Conclusion
Purchasing a verified Cash App account can offer convenience and additional benefits to users, but it comes with potential risks. It is vital to approach the purchase with caution, thoroughly research the seller, and follow safety measures to avoid scams and fraudulent activities. By taking these precautions, users can enjoy the seamless and secure experience of using Cash App for their financial transactions.