Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "plain password"
-
(sensitive parts censored)
Friend: Hey, can you hack my (some website) account?
Me: Depends... What's your username?
Friend: (tells username)
Me: (clicks forgot password?)
Friend: I will give $10 if you do it. There is 2 factor authentication enabled.
Me: (silence) Ok.
Website: Please type the class number you were in in 4th grade.
Me: Hey, did you graduated BLAH elementary school?
Friend: Yeah.
Me: Ahh, I remember. You moved to BLAH elementary school in what grade?
Friend: 4
Me: Hmmm, I don't remember seeing you. What class were you in?
Friend: 5
Me: Well, I now remember. Stupid me. (smirks)
Friend: Haha. (continues to play games beside me)
Me: (Types in 8)
Website: We sent you a password to blah@example.com
Me: (uhh, heads to example.com and clicks forget password?)
Email: Please type the class number you were in in 4th grade.
Me: (wtf is this, types 8)
Email: Please type the teacher's name when you were in in 4th grade.
Me: What was the teacher's name?
Friend: Huh?
Me: When you were in 4th grade.
Friend: Ahh! John Smith.
Me: Ahh, he was strict, right?
Friend: Yeah (continues to play games again)
Me: (Types in John Smith)
Email: Set a new password.
Me: (Types "youaresostupid")
Email: Done!
Me: (copies PLAIN TEXT password from email, logs in to website)
Me: Da-da!
Friend: (gasps)
Me: Money plz~
Friend: Nope.
Me: (wtf, then remembers i changed his email password) Fine then.
=====================
1. There is 2 factor authentication enabled. : Got it?
2. The website sent plaintext password.
3. He is just pure idiot.
4. I didn't got the money.
5. I am now a h4x0r11 -
1. Forgot my password.
2. Clicked "Forgot" password button.
3. Received my forgotten password as plain text in my email6 -
You, stupid fucking game, have just sent me my new password in plain text via email?
"the password is encrypted and cannot be sent again"???
So… you send the password in plain text, and only then encrypt it, right?
But it's still in plain text in your email logs, fucking bastards. 10
10 -
Great news, our company's has a brand new security-first product, with an easy to use API and a beautiful web interface.
It is SQL-injection-enabled, XSS-compatible, logins are optional (if you do not provide a password, you are logged in as admin).
The json-api has custom-date formats, bools are any of "1", "0", 1, 0, false or null (but never true). Numbers are strings or numbers. Utf-8 is not supported. Most of our customers use special characters.
The web interface is using plain bootstrap, and because of XSS it is really easy to customize everything.
How the hell this product got launched is beyond me.10 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
I wonder why banks are always so terribly insecure, given how much money there's for grabs in there for hackers.
Just a while ago I got a new prepaid credit card from bpost, our local postal service that for some reason also does banking. The reason for that being that - thank you 'Murica! - a lot of websites out there don't accept anything but credit cards and PayPal. Because who in their right mind wouldn't use credit cards, right?! As it turns out, it's pretty much every European I've spoken to so far.
That aside, I got that card, all fine and dandy, it's part of the Mastercard network so at least I can get my purchases from those shitty American sites that don't accept anything else now. Looked into the manual of it because bpost's FAQ isn't very clear about what my login data for their online customer area now actually is. Not that their instruction manual was either.
I noticed in that manual that apparently the PIN code can't be changed (for "security reasons", totally not the alternative that probably they didn't want to implement it), and that requesting a forgotten PIN code can be done with as little as calling them up, and they'll then send the password - not a reset form, the password itself! IN THE FUCKING MAIL.
Because that's apparently how financial institutions manage their passwords. The fact that they know your password means that they're storing it in plain text, probably in a database with all the card numbers and CVC's next to it. Wouldn't that be a treasure trove for cybercriminals, I wonder? But YOU the customer can't change your password, because obviously YOU wouldn't be able to maintain a secure password, yet THEY are obviously the ones with all the security and should be the ones to take out of YOUR hands the responsibility to maintain YOUR OWN password.
Banking logic. I fucking love it.
As for their database.. I reckon that that's probably written in COBOL too. Because why wouldn't you.23 -
So according to some reddit user IKEA sends your password as a GET parameter in plain text.
https://reddit.com/r/CrappyDesign/...
Seems to be a network authentication thingy, but still 🤔 34
34 -
You guys are pissed off whenver you see a mail with plain text password. And here I have clients who couldn't log in even after I shoved the raw and plain credentials up their arses.5
-
My insurance company sending me the payment slip by post with my username and password to the online account for easy access. How sweet of them. 10/10 customer satisfaction.
I see your "Storing passwords in plain text". I raise you to "sending passwords via post in plain text". 17
17 -
So this just happened with my ISP, i have no words...
The fact you have my password in front of you in plain text is fucking terrifying and i know you do because i used to work for an ISP. 9
9 -
A colleague and I spent a month building a Shopify app that allows merchants to give customers store credit.
Since Shopify's API is so limited, we were forced to augment it's functionality with a Chrome extension.
Now before you go throwing full wine bottles at your screen because of how wrong and disgusting that is, note that Shopify's official documentation recommends 5 different extensions to augment functionality in their admin panel, so as gross as it is, it seems to be the Shopify way...
Today we got a reply from their review team. They won't accept the app because it requires a Chrome extension to work properly and that is a security risk.
Are you fucking kidding me? So I guess Shopify is exempt from their own security standards. Good to know.
Not to mention the plethora of published apps that require a staff account's username and password to be provided in plain text upon setup so it can spoof a login and subsequent requests to undocumented endpoints.
Fuck you and your "security standard" Shopify! -
Security rant ahead - you have been warned.
It never fails to amuse and irritate me that, despite being in the 2019 supposed information age, people still don't understand or care about their security.
I've travelled to a lot of ports and a lot of countries, but, at EVERY port, without fail, there will be at least one wifi that:
- Has default name/password that has been cracked already (Thomson/SpeedTouch/Netfaster etc)
- Has a phone number as password (reduces crack time to 15-30 mins)
- Someone, to this day, has plain old WEP
I am not talking about cafeteria/store wifi but home networks. WTF people?! I can check my email (through VPN, of course) but it still bugs me. I have relented to try and snoop around the network - I can get carried away, which is bad. Still...
The speed is great though :P9 -
I absolutely love the email protocols.
IMAP:
x1 LOGIN user@domain password
x2 LIST "" "*"
x3 SELECT Inbox
x4 LOGOUT
Because a state machine is clearly too hard to implement in server software, clients must instead do the state machine thing and therefore it must be in the IMAP protocol.
SMTP:
I should be careful with this one since there's already more than enough spam on the interwebs, and it's a good thing that the "developers" of these email bombers don't know jack shit about the protocol. But suffice it to say that much like on a real letter, you have an envelope and a letter inside. You know these envelopes with a transparent window so you can print the address information on the letter? Or the "regular" envelopes where you write it on the envelope itself?
Yeah not with SMTP. Both your envelope and your letter have them, and they can be different. That's why you can have an email in your inbox that seemingly came from yourself. The mail server only checks for the envelope headers, and as long as everything checks out domain-wise and such, it will be accepted. Then the mail client checks the headers in the letter itself, the data field as far as the mail server is concerned (and it doesn't look at it). Can be something else, can be nothing at all. Emails can even be sent in the future or the past.
Postfix' main.cf:
You have this property "mynetworks" in /etc/postfix/main.cf where you'd imagine you put your own networks in, right? I dunno, to let Postfix discover what your networks are.. like it says on the tin? Haha, nope. This is a property that defines which networks are allowed no authentication at all to the mail server, and that is exactly what makes an open relay an open relay. If any one of the addresses in your networks (such as a gateway, every network has one) is also where your SMTP traffic flows into the mail server from, congrats the whole internet can now send through your mail server without authentication. And all because it was part of "your networks".
Yeah when it comes to naming things, the protocol designers sure have room for improvement... And fuck email.
Oh, bonus one - STARTTLS:
So SMTP has this thing called STARTTLS where you can.. unlike mynetworks, actually starts a TLS connection like it says on the tin. The problem is that almost every mail server uses self-signed certificates so they're basically meaningless. You don't have a chain of trust. Also not everyone supports it *cough* government *cough*, so if you want to send email to those servers, your TLS policy must be opportunistic, not enforced. And as an icing on the cake, if anything is wrong with the TLS connection (such as an MITM attack), the protocol will actively downgrade to plain. I dunno.. isn't that exactly what the MITM attacker wants? Yeah, great design right there. Are the designers of the email protocols fucking retarded?9 -
TL;DR I'm fucking sick and tired of Devs cutting corners on security! Things can't be simply hidden a bit; security needs to be integral to your entire process and solution. Please learn from my story and be one of the good guys!
As I mentioned before my company used plain text passwords in a legacy app (was not allowed to fix it) and that we finally moved away from it. A big win! However not the end of our issues.
Those Idiot still use hardcoded passwords in code. A practice that almost resulted in a leak of the DB admin password when we had to publish a repo for deployment purposes. Luckily I didn't search and there is something like BFG repo cleaner.
I have tried to remedy this by providing a nice library to handle all kinds of config (easy config injection) and a default json file that is always ignored by git. Although this helped a lot they still remain idiots.
The first project in another language and boom hardcoded password. Dev said I'll just remove before going live. First of all I don't believe him. Second of all I asked from history? "No a commit will be good enough..."
Last week we had to fix a leak of copyrighted contend.
How did this happen you ask? Well the secure upload field was not used because they thought that the normal one was good enough. "It's fine as long the URL to the file is not published. Besides now we can also use it to upload files that need to be published here"
This is so fucking stupid on so many levels. NEVER MIX SECURE AND INSECURE CONTENT it is confusing and hard to maintain. Hiding behind a URL that thousands of people have access to is also not going to work. We have the proof now...
Will they learn? Maybe for a short while but I remain sceptic. I hope a few DevrRanters do!7 -
Oh my fucking god... I am looking at this code written by a previous developer and he put the passwords in plain in an array in a PHP file, like WHAT WHERE YOU THINKING? (btw that's also how he checks the password, just check whether it's in the array)
c'mon pls14 -
What kind of fucking application sends me my an e-mail with my password in plain text when I sign-up!?7
-
HOW FUCKING HARD CAN IT BE TO NOT STORE PASSWORDS IN CLEARTEXT AND THEN PROCEED TO SEND ME AN UNENCRYPTED EMAIL WITH THE PASSWORD IN IT??? THE SITE HAS A PREMIUM FUCKING SSL AND SAFETY CERTIFICATES YET THEY STILL DON'T COMPLY TO THIS? FUCK YOU! IF IT WASN'T FOR THAT I HAD TO ORDER A NEW SCREEN FOR MY BROKEN PHONE, YOU COULD'VE SUCKED BETTER THAN ME + VACUUM CLEANER.
Sorry abt that. But for real, mytrendphone stores passwords in plain texts and waves a fucking safety certificate in your face...13 -
The gym I go to has an app for user's to scan a QR code when they arrive and it has multiple HUGE issues.
This app shows the credit card info used for the direct debit without anything being redacted.
When the gym is signing up someone they give them a password so they can login, not too bad except the password is always the person's first name with the first letter capitalised.
This gets worse when you figure out that their is no way to change the password given to you AT ALL.
And just to top it all off, when you click the "Forgot Password" link on the login screen, the app just sends you an email with your password (your first name) in plain text.
The app also doesn't log you out or notify you if your login is used on a different device.
So I have tested this with 2 of my friends that go to the same gym and, with only knowing their email and first name (which I could have gotten from their email if I didn't know them), I can get into their app and see their credit card info without them being any the wiser.9 -
Unencrypted, plain text passwords stored in SQL, from lowest role all the way up through Admin. In the same system, they had a "backdoor" password that would log in any user...
-
Just registered as a customer at an online store, and the fuckers sent me a confirmation email where my password was written in plain text. Why?!5
-
My school just tried to hinder my revision for finals now. They've denied me access just today of SSHing into my home computer. Vim & a filesystem is soo much better than pen and paper.
So I went up to the sysadmin about this. His response: "We're not allowing it any more". That's it - no reason. Now let's just hope that the sysadmin was dumb enough to only block port 22, not my IP address, so I can just pick another port to expose at home. To be honest, I was surprised that he even knew what SSH was. I mean, sure, they're hired as sysadmins, so they should probably know that stuff, but the sysadmins in my school are fucking brain dead.
For one, they used to block Google, and every other HTTPS site on their WiFi network because of an invalid certificate. Now it's even more difficult to access google as you need to know the proxy settings.
They switched over to forcing me to remote desktop to access my files at home, instead of the old, faster, better shared web folder (Windows server 2012 please help).
But the worst of it includes apparently having no password on their SQL server, STORING FUCKING PASSWORDS IN PLAIN TEXT allowing someone to hijack my session, and just leaving a file unprotected with a shit load of people's names, parents, and home addresses. That's some super sketchy illegal shit.
So if you sysadmins happen to be reading this on devRant, INSTEAD OF WASTING YOUR FUCKING TIME BLOCKING MORE WEBSITES THAN THEIR ARE LIVING HUMANS, HOW ABOUT TRY UPPING YOUR SECURITY, PASSWORDS LIKE "", "", and "gryph0n" ARE SHIT - MAKE IT BETTER SO US STUDENTS CAN ACTUALLY BROWSE MORE FREELY - I THINK I WANT TO PASS, NOT HAVE EVERY OTHER THING BLOCKED.
Thankfully I'm leaving this school in 3 weeks after my last exam. Sure, I could stay on with this "highly reputable" school, but I don't want to be fucking lied to about computer studies, I don't want to have to workaround your shitty methods of blocking. As far as I can tell, half of the reputation is from cheating. The students and sysadmins shouldn't have to have an arms race between circumventing restrictions and blocking those circumventions. Just make your shit work for once.
**On second thought, actually keep it like that. Most of the people I see in the school are c***s anyway - they deserve to have half of everything they try to do censored. I won't be around to care soon.**undefined arms race fuck sysadmin ssh why can't you just have any fucking sanity school windows server security2 -
Things that give me chills early in the morning. A password reset email that contains my password in plain text.
Seriously! 🤦♂️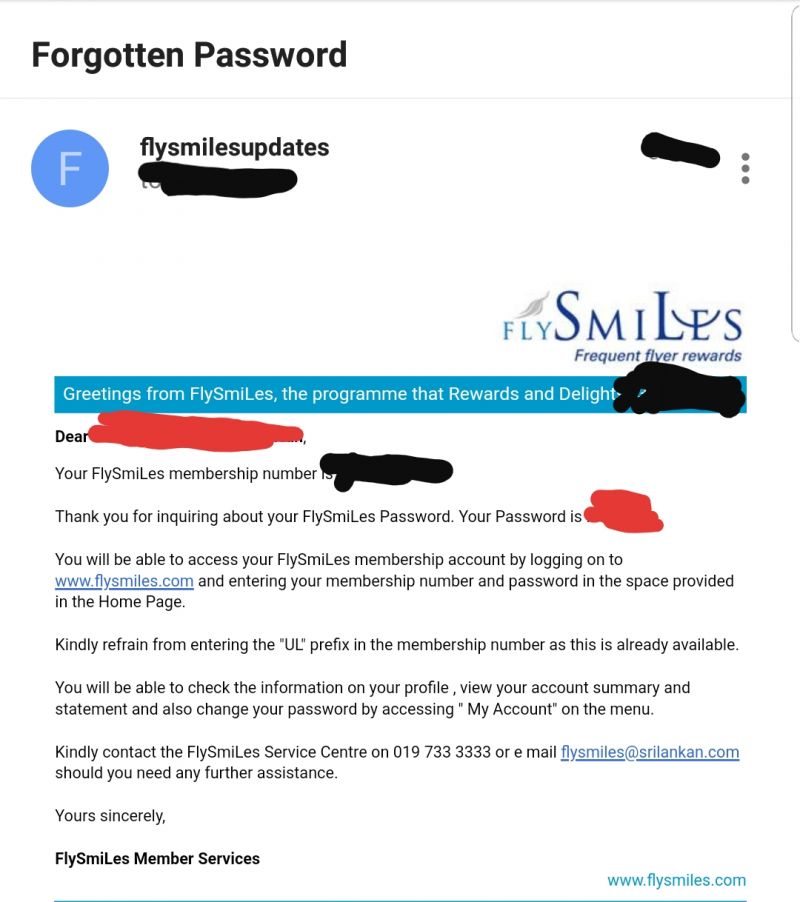 1
1 -
I used to work in a small agency that did websites and Phonegap apps, and the senior developer was awful.
He had over a decade of experience, but it was the same year of experience over and over again. His PHP was full of bad practices:
- He'd never used an MVC framework at all, and was resistant to the idea, claiming he was too busy. Instead he did everything as PHP pages
- He didn't know how to use includes, and would instead duplicate the database connection settings. In EVERY SINGLE FILE.
- He routinely stored passwords in plain text until I pretty much forced him to use the new PHP password hashing API
- He sent login details as query strings in a GET request
- He couldn't use version control, and he couldn't deploy applications using anything other than FTP4 -
When your client wants you to store password in plain text and it makes your life easier but it still feels really wrong12
-
Seriously, fuck that incompetent ISP of mine.
Stores passwords in fucking plaintext. Does VoIP calling in plaintext! Passwords are sent over postal mail! Passwords are at least not sent in plain via email anymore when you want to reset them. The password reset form, "cannot contain `", "cannot contain "", "cannot contain '", "must contain a special character" because why the fuck not mess with people's password manager's password generation function over our own incompetence, right?! And showing all those errors for a single password? Eh, no. Let's just show one error that applies to whatever password you've given at that time. JUST ONE, because "reasons"! And to top it all off, when I finally made myself a nice password with some padding to remove unwanted chars and put that in my password store and on the website. THE BLOODY THING CAN'T EVEN FUCKING LOGIN?!
Now I ain't no ISP, but being a sysadmin clearly isn't a requirement when you're going to apply for work at an ISP, THAT DOES NOTHING BUT FUCKING SYSADMIN STUFF!!! Incompetent pieces of SHIT!!!3 -
Stop sending passwords in plain text via email. Just stop already. If you don't know how to implement a secure alternative, hire a fucking consultancy to assist you.
Fuck. The next time I purchase from you and I get my password in plain text anywhere, I'm immediately demanding a refund and taking my money elsewhere.
Just fucking stop.13 -
Client stores all user accounts in a publicly accessible google spreadsheet in case the user forgets their login. It includes user name, plain text password, and just in case, the hashed password....
 6
6 -
Biggest GTFO moment of the year;
While applying for colleges, I created an account with a username and variant of my usual password (I know, bad move, sorry). I came back to finish the application but had forgotten what variant I had used. So I clicked the forgot password button and got an email with...
MY PASSWORD IN IT!!!!
Plain text password! Just as part of the email! WTF do these people think they are doing?!?!
I immediately changed my password to a random string and deleted my account, so hopefully when someone gets into this database my stuff with be overwritten... stupid programmers...7 -
I forgot my password to [SITE]. Of course, I click "forgot password", and enter my email, which I did remember. Fairly routine "ah shit we have a problem" steps.
Now, it takes a second. This is to be expected. So I'm not worried. I then get the email and...
Now, you will notice that I redacted some information, like the company name, email, and my PLAIN TEXT PASSWORD, and my name.
I would like to note that this isn't a small, very local company that's new (even then it'd be unacceptable), but this is a multinational, multimillion dollar company.
How'd someone fuck up THIS badly? 13
13 -
The Hungarian public transport company launched an online shop (created by T-Systems), which was clearly rushed. Within the first days people found out that you could modify the headers and buy tickets for whatever price you set, and you could login as anyone else without knowing their password. And they sent out password reminders in plain text in non-encrypted emails. People reported these to the company which claims to have fixed the problems.
Instead of being ashamed of themselves now they're suing those who pointed out the flaws. Fucking dicks, if anyone they should be sued for treating confidential user data (such as national ID numbers) like idiots.3 -
A well known, big company in my country just sent me my password in plain text upon registering.
These devs actually got paid to do this...6 -
About browsers and whole SSL CERT thing...
Most likely everyone here noticed, that https site with broken certificate will throw these big red warnings, in your face and there is so much wording like "ITS NOT SECUREEEE" or "ITS HACKEDDD" almost like it was written by passionate fanatic.
But when you are on plaintext http browsers reaction is like ¯\_(ツ)_/¯
Even if you have plaintext with password, it will for example in chromium put small little red thingy that almost no one notices.
I believe that broken cert with some error like invalid date is MORE secure than plaintext password, yet still there is this hypocracy with browsers...
I dont say that broken SSL cert is good, or something, Im just pointing out contrast of "broken" https vs plain http.... One looks for casual Joe like end of the world is coming and second is bearly noticable. Da fuck?
I disagree with this approach17 -
When I left school I decided to apply for a junior dev role. I received a call back later that day and they tried to sell me access to some course with the promise of a job afterwords. They gave me a website to visit to find more information.
I Googled the company and found that it was as I suspected a scam and that they had been praying on the jobless for sometime.
So, I played around on the site they told me to visit for a while and found a rather simple SQLI. I managed to pull the admin email/password (which they stored as plain text) the email address belonged to a Gmail account.
I tried the password for the Gmail account turns out the account belongs to the person running the scam. I find an email from the hosting account and you guessed it the password was the same.
I pulled the site down and replaced it with a picture of the person running the scam along with his name and the words "I'm a dirty scammer".
Then I sent all the info to the police (he'd been running a few others scams too) not sure what that lead to I didn't hear anything back.1 -
First of all how the fuck you are able to tell that MY password is one of many that have been stolen? How you are able to get those stolen passwords AND WHY YOU ARE EVEN ABLE TO COMPARE THEM?! Are you storing as plain text or just randomly salt all stolen passwords and chceck if they are in your base?
Now that is an INSTAdelete. 8
8 -
Government website sends me my username and password over plain text email after I sign up...
WHAT WHY WHO LET THIS HAPPEN6 -
So I was logging into google today and my password is very long so I often make mistakes while typing it so I went to inspect element to change input type to text so that I can check the password and I see that Firefox is storing my password already as plain text. Wtf Firefox???
 6
6 -
So our teacher just has us sign up for a learning site called Gizmos with a ton of students information. A lot of students forgot their password as always and some didn't register with an email so I expected the teacher to reset them..
Then the teacher had students come up to the front of the f****** class and SHOWED THEM THEIR PASSWORD IN PLAIN TEXT. WHAT THE HELL3 -
During an internship, I spent some time automating reports with VBA. Basically, imagine a few big excel sheets with 1000 formulas and a few thousand lines of VBA.
One of the reports was handed directly to the bosses boss of our boss. After 4 weeks, he came to me and asked why the table entry in row 23 or so was always 84. Well.. I dont know. This data is automatically calculated / retrieved from a database. Went and checked, already sweating, and found that
THE OTHER INTERN COULDNT FIX A FORMULA SO HE OVERRODE IT WITH PLAIN TEXT. WITH A FUCKING PLAIN VALUE OF 84. A FOOKING EXCEL SHEET WITH A THOUSAND DIFFERENT FORMULAS AND LOTS OF VBA. Needless to say, everything is password protected now.1 -
Me and my developer friend worked with my ex-colleague with this fitness directory website because he promised to give us {{ thisAmount }} upon the {{ completionDate }}.
He was my friend and I trusted him.
It took me weeks of sleepless nights building the project. I had a full-time job that time, and I worked on the project during evenings. All went well, and as we reach the {{ completionDate }}, the demo site is already up and running.
A week before the {{ completionDate }}, he hired his new wife as the COO of the startup. It was cool, she keep noticing things on the site which shouldn't be there, and keeps on suggesting sections that has to be there. I was okay with it, until I realized that we are already a month late with the deadline.
Every single hour, I get a message from them like, "it's not working", "when can you finish this feature?", blah blah blah.. and so on.
I got frustrated.
"I want my fucking life back", I told them. No one cared about the {{ completionDate }}, the sleepless zombies they are working with and our payment. They keep on coming up with this "amazing" ass features, and now they are not paying because they said "it's not complete".
Idiot enough to trust a friend. I was unprotected, there was no legal-binding document that states their obligation to pay.
My dev friend and I handed over the project to this web development company which they prefer, and kept a backdoor on the application.
I kind of moved on with the payment issue after a month. But without their knowledge, I kept an eye on the progress and made sure that I still have the access to their server, DNS, etc..
BUT when they announced the official launch on social media, I realized that I was on the wrong train the whole time.
They switched to a different server.
They thanked all the people involved with the project via social media, EXCEPT me and my coding partner who originally built the site from ground up. A little "thank you" note from them will make us feel a little better. But, never happened.
I checked up the site and it was rewritten from originally Laravel 5 to CodeIgniter 1. That is like shifting from a luxury yacht where you can bang some hot chicks, to a row boat where your left hand is holding the paddle whilst your right hand is wanking yourself.
I almost ran out of bullets.
Luckily, CodeIgniter 1 was prone to SQLi by default.
I was able to get the administrator password in plain text and fucked with their data. But that didn't make me feel better because other people's info are involved.
So, I looked for something else to screw with. What I found? A message with the credit card details.
Finally, a chance to do something good for humanity. I just donated a few thousand dollars to different charity websites.2 -
Creating username / password first time - checked
Storing password in plaintext - checked
Messaging password in plain text after a password change - whaaattt???? 7
7 -
Registering a new account for microsoft teams:
`Your password cannot contain a space, &# characters combination, or the following characters: < >`
Are they storing the passwords in plain text? Are they not sanitizing the input? Why the fuck would they care if I put motherfucking emojis in my password? What the fuck are you doing to the passwords, Microsoft? TELL ME.4 -
Today my fellow @EaZyCode found out a local Hosting Provider has a massive security breach.
He wrote an Plugin for Minecraft with an own file explorer and the ability to execute runtime commands over it.
We discovered that this specific hosting provider stores the ftp passwords one level above the FTP-Root. In FUCKING PLAIN TEXT! AND THE MYSQL PASSWORD TOO! And even more shit is stored there ready to be viewed by intelligent people...
It's one of the fucking biggest Hosting provider Germanys!
But, because EaZyCode has such a great mind and always find such bugs, I give him the title "Providers Endboss" today, he has earned it.
Loving you ❤️
Edit: we used SendMail with runtime commands and sended too many empty Spammails (regret noting)18 -
My company email:
- It's time for the monthly password change!
<writes the usual passwod>
- The password must be over 50 characters long!
<adds more letters>
- The password must have numbers!
<adds some numbers, though it's getting irritating>
- The password must have special characters!
<wtf?? Adds a pound character>
- The password must have at least 20 different special characters!
<da fuq???>
- The password must be at least 50 characters, only special characters and invisible tab/LF/CR characters and it must be changed daily!
<head explodes>
- Thank you! Now please sign in with your new password for 200 times per day.
<closes the laptop and starts using Remington type writer>
Usually these remainders start popping up during the 1st vacation day. When you return to the office, the account is already locked.
And then you wonder why people have the passwords written on a post-it or as a plain txt file in SkyDrive.11 -
I don't understand how is possible that programmers today are developing applications that are storing plain password in the database.
I know it's kinda boring topic since everybody here is talking about it this week, but it's really confusing to me.
Every now and then some DB gets hacked, millions of passwords are leaked and then you have developers, who should be smart and logical people, who decide to do that.
Ok, maybe the project deadline was close or something similar, but I think there is no excuse for something like that. No matter how close or behind deadline project is, you should always be able to explain to your boss/client what could happen.3 -
Saw a classmate returning an plain text password from a function to try to push it in a JSON file for an API we have to build for class.
I try to correct him and show him a few things that are better practices and for security, I get yelled at and called a know-it-all for trying to help... I'm so done with people -.-4 -
Oh boy, this is gonna be good:
TL;DR: Digital bailiffs are vulnerable as fuck
So, apparently some debt has come back haunting me, it's a somewhat hefty clai and for the average employee this means a lot, it means a lot to me as well but currently things are looking better so i can pay it jsut like that. However, and this is where it's gonna get good:
The Bailiff sent their first contact by mail, on my company address instead of my personal one (its's important since the debt is on a personal record, not company's) but okay, whatever. So they send me a copy of their court appeal, claiming that "according to our data, you are debtor of this debt". with a URL to their portal with a USERNAME and a PASSWORD in cleartext to the message.
Okay, i thought we were passed sending creds in plaintext to people and use tokenized URL's for initiating a login (siilar to email verification links) but okay! Let's pretend we're a dumbfuck average joe sweating already from the bailiff claims and sweating already by attempting to use the computer for something useful instead of just social media junk, vidya and porn.
So i click on the link (of course with noscript and network graph enabled and general security precautions) and UHOH, already a first red flag: The link redirects to a plain http site with NOT username and password: But other fields called OGM and dossiernumer AND it requires you to fill in your age???
Filling in the received username and password obviously does not work and when inspecting the page... oh boy!
This is a clusterfuck of javascript files that do horrible things, i'm no expert in frontend but nothing from the homebrewn stuff i inspect seems to be proper coding... Okay... Anyways, we keep pretending we're dumbasses and let's move on.
I ask for the seemingly "new" credentials and i receive new credentials again, no tokenized URL. okay.
Now Once i log in i get a horrible looking screen still made in the 90's or early 2000's which just contains: the claimaint, a pie chart in big red for amount unpaid, a box which allows you to write an - i suspect unsanitized - text block input field and... NO DATA! The bailiff STILL cannot show what the documents are as evidence for the claim!
Now we stop being the pretending dumbassery and inspect what's going on: A 'customer portal' that does not redirect to a secure webpage, credentials in plaintext and not even working, and the portal seems to have various calls to various domains i hardly seem to think they can be associated with bailiff operations, but more marketing and such... The portal does not show any of the - required by law - data supporting the claim, and it contains nothing in the user interface showing as such.
The portal is being developed by some company claiming to be "specialized in bailiff software" and oh boy oh boy..they're fucked because...
The GDPR requirements.. .they comply to none of them. And there is no way to request support nor to file a complaint nor to request access to the actual data. No DPO, no dedicated email addresses, nothing.
But this is really the ham: The amount on their portal as claimed debt is completely different from the one they came for today, for the sae benefactor! In Belgium, this is considered illegal and is reason enough to completely make the claim void. the siple reason is that it's unjust for the debtor to assess which amount he has to pay, and obviously bailiffs want to make the people pay the highest amount.
So, i sent the bailiff a business proposal to hire me as an expert to tackle these issues and even sent him a commercial bonus of a reduction of my consultancy fees with the amount of the bailiff claim! Not being sneery or angry, but a polite constructive proposal (which will be entirely to my benefit)
So, basically what i want to say is, when life gives you lemons, use your brain and start making lemonade, and with the rest create fertilizer and whatnot and sent it to the lemonthrower, and make him drink it and tell to you it was "yummy yummy i got my own lemons in my tummy"
So, instead of ranting and being angry and such... i simply sent an email to the bailiff, pointing out various issues (the ones6 -
My university has a internal developed system, where everything is managed from e-mails, exams to personal data.
What I'd like most about it, they talk all day about Internet Security and store our passwords in plain text and if you press the "I've forgott my Password button", they even send your password unencrypted, plaintext via e-mail. (Hello Wiresharks)
I don't know how to feel about this, it just hurts :(1 -
This is the last part of the series
(3 of 3) Credentials everywhere; like literally.
I worked for a company that made an authentication system. In a way it was ahead of it's time as it was an attempt at single sign on before we had industry standards but it was not something that had not been done before.
This security system targeted 3rd party websites. Here is where it went wrong. There was a "save" implementation where users where redirected to the authentication system and back.
However for fear of being to hard to implement they made a second method that simply required the third party site to put up a login form on their site and push the input on to the endpoint of the authentication system. This method was provided with sample code and the only solution that was ever pushed.
So users where trained to leave their credentials wherever they saw the products logo; awesome candidates for phishing. Most of the sites didn't have TLS/SSL. And the system stored the password as pain text right next to the email and birth date making the incompetence complete.
The reason for plain text password was so people could recover there password. Like just call the company convincingly frustrated and you can get them to send you the password.1 -
Social Captain (a service to increase a user's Instagram followers) has exposed thousands of Instagram account passwords. The company says it helps thousands of users to grow their Instagram follower counts by connecting their accounts to its platform. Users are asked to enter their Instagram username and password into the platform to get started.
According to TechCrunch : Social Captain was storing the passwords of linked Instagram accounts in unencrypted plaintext. Any user who viewed the web page source code on their Social Captain profile page could see their Instagram username and password in plain text, as they had connected their account to the platform. A website bug allowed anyone access to any Social Captain user's profile without having to log in ; simply plugging in a user's unique account ID into the company's web address would grant access to their Social Captain account and their Instagram login credentials. Because the user account IDs were for the most part sequential, it was possible to access any user's account and view their Instagram password and other account information easily. The security researcher who reported the vulnerability provided a spreadsheet of about 10,000 scraped user accounts to TechCrunch.3 -
Not being able to persuade the client that storing plain text passwords so that they can send them to their users when they forget them is not the best way to handle user accounts.
This happened in 2012 but it still hunts me like it was yesterday.
Before you all demand to ban me from devRant, I’d like to say that we impelemented an alternative (unpaid!) for this, but were requested to disable it.3 -
"I need the login credentials for the CMS service"
*sends the email confirmation email*
"No, I can't confirm your email for you. In plain English: send me the email and password to login."
"Ohhhhhhhhh"
Literally what the fuck is wrong with these people.
I swear we're all fucking doomed.5 -
So here I am investigating something our users are claiming. I look up which user the UserId did the change and I see not only the user but also the users password in clear text in a separate field. I thought that field was for a password hint that the user can set up, but I asked around and apparently, no... It's literally the plain text version of the password stored in the database, next to the hash of the password.
Apparently, the users were so impossible to deal with that we added that column and for users that constantly pester us about not knowing their password and not wanting to change it, we added a plaintext password field for them :D2 -
Installed my telecom service provider's app for checking new packs. Didn't remember the password. Hit forgot password! I get my password in plain text in sms!
Fuck, it's one of the leading service provider in the country!
Till now i had only read about it, but never encountered it! Any ideas as to how to approach them?2 -
X - New stickers, people!!! Yay!!
X - Ordered these from www.juststickers.in.
X - Nice quality paper.
X - About $3 per piece.
X - You should try.
> Thanks @sumeetchawla.
> Although, you guys don't read the emails sent to your Support@juststickers.in email address 😒.
> I would give you 3/5.
-1 for not replying to the email.
-1 for storing the password in plain text.
Stickers are worth the money though 😊👌👍 5
5 -
Short sad story:
The backend team in my company stores plain text passwords and I am making a view in the website to view all the users password in the system13 -
So, I apply for a job and they send me an automated email with my username....and my pasword....in plain text...I should use a different password for my applications....4
-
More emarassing than frustrating..But I was applying to a couple internal positions recently and decided to bring in a sample package to demonstrate some of what I had been working on in my current team. They seemed to like the example and the interview seemed to go well...A couple hours later one of the managers came by my cubicle and asked "is that the real password?" and pointed to a line in the code. Sure enough, I had left a plain text password in the script I had just handed out to 10 panelists at 2 interviews..proceeded to collect the packets back. In the future I'll be paying closer attention to what I include lol.
Still frustrated we keep the passwords in the script though >.> any suggestions for better storage of passwords and the like in Perl scripts?3 -
So we had to register for placements.. and the company sent email with plain text password.. and thats the password i registered with! nice!
BTW.. its one of the biggest company in IT industry globally. 2
2 -
Today's shit list, compiled from multiple random apps:
* Your subscription renews without an email in advance (no time to cancel)
* Your chat bot asks me twenty questions about why I want to cancel my membership, then sends me to a live agent, who asks me the same damn questions.
* Your app emails me my password in plain text
* Meeting agenda squashed by execs:
"We don't talk about _____, but we're committed to transparency." -
We hired someone to make the new front site because I was too busy.
The guy had a plain text password system to show, mispronounced "FontAwesome", and used WordPress.
He was not an instructor but was supposed to be the "senior option" for when I couldn't do something for any reason.
I later asked him for some opinion on how to translate the site, and he disabled the Captcha plugin. I. Don't. Know. Why. I figured because of all the spam I got suspiciously after he "took a look" at the admin panel.
Luckily I could get him out of the contacts and now we are looking for more devs. -
It was the last year of high school.
We had to submit our final CS homework, so it gets reviewed by someone from the ministry of education and grade it. (think of it as GPA or whatever that is in your country).
Now being me, I really didn’t do much during the whole year, All I did was learning more about C#, more about SQL, and learn from the OGs like thenewboston, derek banas, and of course kudvenkat. (Plus more)
The homework was a C# webform website of whatever theme you like (mostly a web store) that uses MS Access as DB and a C# web service in SOAP. (Don’t ask.)
Part 1/2:
Months have passed, and only had 2 days left to deadline, with nothing on my hand but website sketches, sample projects for ideas, and table schematics.
I went ahead and started to work on it, for 48 hours STRAIGHT.
No breaks, barely ate, family visited and I barely noticed, I was just disconnected from reality.
48 hours passed and finished the project, I was quite satisfied with my it, I followed the right standards from encrypting passwords to verifying emails to implementing SQL queries without the risk of SQL injection, while everyone else followed foot as the teacher taught with plain text passwords and… do I need to continue? You know what I mean here.
Anyway, I went ahead and was like, Ok, lets do one last test run, And proceeded into deleting an Item from my webstore (it was something similar to shopify).
I refreshed. Nothing. Blank page. Just nothing. Nothing is working, at all.
Went ahead to debug almost everywhere, nothing, I’ve gone mad, like REALLY mad and almost lose it, then an hour later of failed debugging attempts I decided to rewrite the whole project from scratch from rebuilding the db, to rewriting the client/backend code and ui, and whatever works just go with it.
Then I noticed a loop block that was going infinite.
NEVER WAIT FOR A DATABASE TO HAVE MINIMUM NUMBER OF ROWS, ALWAYS ASSUME THAT IT HAS NO VALUES. (and if your CPU is 100%, its an infinite loop, a hard lesson learned)
The issue was that I requested 4 or more items from a table, and if it was less it would just loop.
So I went ahead, fixed that and went to sleep.
Part 2/2:
The day has come, the guy from the ministry came in and started reviewing each one of the students homeworks, and of course, some of the projects crashed last minute and straight up stopped working, it's like watching people burning alive.
My turn was up, he came and sat next to me and was like:
Him: Alright make me an account with an email of asd@123.com with a password 123456
Me: … that won't work, got a real email?
Him: What do you mean?
Me: I implemented an email verification system.
Him: … ok … just show me the website.
Me: Alright as you can see here first of all I used mailgun service on a .tk domain in order to send verification emails you know like every single website does, encrypted passwords etc… As you can see this website allows you to sign up as a customer or as a merc…
Him: Good job.
He stood up and moved on.
YOU MOTHERFUCKER.
I WENT THROUGH HELL IN THE PAST 48 HOURS.
AND YOU JUST SAT THERE FOR A MINUTE AND GAVE UP ON REVIEWING MY ENTIRE MASTERPIECE? GO SWIM IN A POOL FULL OF BURNING OIL YOU COUNTLESS PIECE OF SHIT
I got 100/100 in the end, and I kinda feel like shit for going thought all that trouble for just one minute of project review, but hey at least it helped me practice common standards.2 -
Working at a local seo sweat-shop as "whatever the lead dev does't feel like doing" guy.
Inherit their linux "server".
- Over 500 security updates
- Everything in /var/www is chmod to 777
- Everything in /var/www is owned by a random user that isn't apache
- Every single database is owned by root sql user
- Password for sudo user and mysql root user same as wifi password given to everyone at company.
- Custom spaghetti code dashboard with over 400 files in one directory, db/ api logins spread throughout these files, passwords in plain text.
- Dashboard doesn't have passwords, just usernames to login
- Dashboard database has all customer information including credit card stored in plain text
- Company wifi is shared by other businesses in the area
I suggest that I should try to fix some of these things.
Lead Developer / Tech Director : We're an SEO company, not a security company . . .7 -
I checked out this new hybrid app that was released by some local senior developers.
Turns out that on my user profile, my user ID is set as the value of a hidden field and changing it to any other user ID and saving the form will update the profile of that user. Including changing the password.
The password reset form also allows me to change the user ID to reset that user's password.
Speaking of passwords, the value of the password field on the profile is my actual password in plain text.
Yes, I said this app was released by a couple of "senior developers". One has over 15 years of experience and the other works at an IT company that builds online banking systems. They appear to have outsourced this side project to some other development team but... Come on. At least take one quick look at the source code before releasing it, why don't you?
I don't even...1 -
I took Database System Class and Courses in University, and told to store the password using its hash and don't store it in plain text; it is at least a standard.
today i just resetting my gmail password since i forgot the password. and i wonder by how google forgot password mechanism work.
for example i register the password with:
'xxxfalconxxx'
and then change it to:
'youarebaboon123'
sometimes later i forgot both password, and google asked for the last password i remember; and i only remember part of it so i entered:
'falcon'
and this is right, so i can continue the forgot password mechanism. how could you check the hashed text of 'falcon' is the subset of hash text 'xxxfalconxxx' ?2 -
Just managed to send my password in plain text to a colleague when I ment to enter it in the login box.....
Time to change my password again.....3 -
I started using Keepass like 2 months ago, and recently i started going through all my email accounts to compile a list of all the services i've ever signed up to; delete the accounts you don't need and move everything else to keepass with a strong passwd, that was the plan.
I'm still going, but out of the 60 i have so far, 10 sites just had the password, *in plain text*, in the confirmation email!! I don't even konw anymore, just end me now plz 😢7 -
Back in https://devrant.com/rants/5492690 @Nihil75 referred to SlickVPN with a link, where you can buy a lifetime licence for $20. I thought - what the hell.. I don't need a public VPN rn, but for $20 for a lifetime lic - I'll take it, in case I'll ever need one.
I had some trouble signing up - the confirmation email never reached my inbox. So I got in touch with support. And they.... generated and send me a password in plain-text.
And there even isn't any nagging requirement to change the pass after I sign in for the first time!
IDK... As for a service claiming to be security-oriented, the first interaction already screams "INSECURE".
Well.. should still be OK for IP switching, to unlock Netflix content I guess. Don't need anything secure for that 🤷 15
15 -
Passwords are limited to 8 characters and stored in plain text. In the beginning of the year they give your password in a little piece of paper... I just gave up and started using my name as the password...
Found in the web portal used to buy school meals and consult card balance in Portugal (called GIAE). -
While attempting to quit smoking and after spending a full day trying to understand why the previous devs took this approach to encrypting a string and my lack of nicotine addled brain not allowing me to see that this was a “Secure”String and so uses a machine specific key (that’s why the code that worked locally wouldn’t run on production 😑) this is my rant on comments added to the helper I had to write
/// <summary>
/// If you are using this class and it's not for backward compatibility - then you probably shouldn't be using it
/// Nothing good comes from "Secure" strings
/// Further to this Secure strings are only "useful" for single user crypto as the encryption uses the login creds, transferring
/// this data to another client will result in them never being able to decrypt it
///
/// Windows uses the user's login password to generate a master key.
/// This master key is protected using the user's password and then stored along with the user's profile.
/// This master key then gets used to derive a number of other keys and it's these other keys that are used to protect the data.
///
/// This is also a broken crypto method via injection (see Hawkeye http://hawkeye.codeplex.com/) plus the string is stored in plain
/// text in memory, along with numerous other reasons not to use it.
/// </summary>
public class SecureStringHelper
{3 -
I hate IT. I hate just about anything that relates to computers.
It's all nothing but debugging.
SSH from linux, works great.
SSH from windows, even with plain password, permission denied. Blaah...
Why this shit won't just work?5 -
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
received a picture of scribbled password, all am thinking is you can't store your password in plain text
-
When the recruiting company mails you about new jobs along with your PASSWORD!
Dude, you have a fuckall dev and u will help me find a job... Thanks, but no thanks. 4
4 -
When the company running my student accommodation not only stores the passwords for their resident portal in plain text and emails them straight to you in the case of a forgotten password. But also generates your password at sign up according to a specific general pattern...2
-
Just wanted to buy a gift for my gf, so I went to birchbox.fr to buy her a 3 months subscription (irrelevant information).
So of course I needed to create an accout in order to buy it.
But what a surprise when I received a confirmation email, with my password in PLAIN TEXT inside. I guess I do really love her for not cancelling the gift and deleting my account immediately. -
During the cryptography & security lecture at the university I received an email from the university IT department with credentials to access the university cloud services. Of course, password was in a plain text.2
-
Once on a project the authentication request for a service was done... through http... with the username and password as parameter in the URL... in plain text
-
When after registration on some website you get your password, that you just set, send back to you in an email. Why the fuck do they store and transmit passwords in plain text.4
-
I can't recall what platform it was, but upon trying to change my password it would tell me that the new password was too similar to the previous one... :/1
-
Someone earlier today posted a rant about a credit card security conference sending them account details with a plain text password in an email. The password appeared to be 1 use temporary password that the user would change on first login. Assuming one does not actually store plain text passwords, what is the downside to a single use password Vs a single use link to set a new password?1
-
Whenever a site tells me the password I entered has already been used? I mean how are you supposed to know if you are salting and hashing the password.. Oh wait you probably just save it in plain text!! Please don't!!7






