Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "phishing"
-
This is some nevt level phishing. I wrote the guy who was listed in WHOIS an E-Mail, correcting his mistakes.
 17
17 -
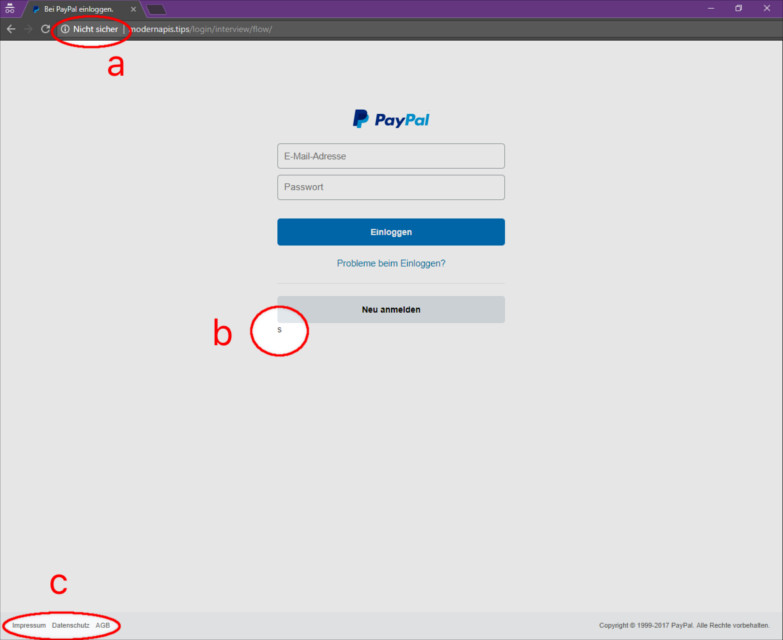
My classmate just fell for a phishing email from "PayPal."
She was talking about her payment being declined to her friend.
It peaked my attention when she said after logging in, she was lead to a blank page.
I asked if I could see it and it was definitely a phishing email
I will admit, it's one of the most professional phishing email I've ever seen, but the grammar wasn't very professional and the PayPal logo wasn't completely accurate.
Why do these idiots fall for everything?32 -
Dev: *Recieves email from manager with several typos/grammar mistakes asking to open attachment with strange name and click on tinyurl style link*
Dev: *Flags as phishing*
Manager: Hey how come you didn’t action my email?
Dev: That was actually from you?
Manager: Yes.
Dev: …3 -
Got a phishing email with name-pw sent as get parameters so i did what ever respectable human would have
 15
15 -
How do I un-idiot my users when it comes to clicking on dodgy email-links??
Got a forwarded email just there from a user who said;
Good afternoon,
Is the below ok to open?
I just tried but got a popup saying I've been blocked from opening it.
I'm not sure who it is coming from and I am not waiting on anything but as it says its from dropbox and is important, i know it's okay.
Can you unblock the link ASAP please?
This is really impeding my work-day as I need to know what it is and act accordingly.
Regards... user.
The Original email came from a random jumble of letters with a subject line of 'important dropbox program' - not only does it look dodgy but its english is horrible! It said;
"Hi tu my freind,
You tu still read a pending verrry important document sent by one of your own contact to be vieweddd.
Install "Highly Confidential english.pdf" by clickinggg here
*insert link leading to something called 'viral-update-trojan.exe'*"
I mean, seriously... help!!! 😢
We have sent emails explaining how to hover over links and to not to click them if it looks wrong.
No one does it.
We hired a company to send fake phishing emails to train users in what to do.
It made no difference!
We now make people 'verify' their email addresses when opening any sort of link to try get them to actually look at what they're opening.
We also strip emails of original attachments and create 'safe' html copies as we can't trust them to look at what they're opening.
Everyone complains about it but Jesus Christ, this is why!!!
Its so exhausting!! What is wrong with people!!! Argh!!! 😤12 -
My mother sits in front of me with her laptop. After a time she asks me, who founded Microsoft. I say: "Bill Gates but why?"
She: "Oh my god, I am winning an iPhone!!!"
I know exactly what's going on, so I go to her and show her the shitty URL and some grammar mistakes in the text and close the tab after explaining that it is phishing.
After that she just looks at me and is sooooo angry about me, because she still thinks that it was real. Only because they "knew which Internet provider we were using and that they just wanted to reward us for being customer!!!". I'm so sad now, because I never thought she would fall for sth. like this... 😔6 -
We had a short power outage this morning. 30 min later I got an "urgent" call that someone's "computer" was not working in another branch of our company.
Not one person in that branch could figure this out so after them repeatedly messaging and calling me for around an hour I decided to come over.
I found out that the power wall plug to the monitor has a switch on it which this person accidentally kicked...
I fixed his problem in around 20 seconds. This same employee was one that somehow had his email account previously "hacked" and 8000 phishing emails were sent from his account in 1 hour.
I honestly think it is amazing people like this can even use a computer at all...5 -
Corporate: Phishing Emails are serious. We need you guys to take this awareness training. Please report if you get any suspicious email.
*Sends the awareness training in a format that screams Phishing
Everybody: Wait... is this a test?1 -
Give a Nigerian Prince an e-mail account and he will scam the net for a day,
Teach him how to phish, and he will prosper for eternity!2 -
The company I work for have this obsession of sending phishing emails to employees. If you report the email you get a message saying good job. If you fail, and you open it you have to have a meeting with your boss and stuff. They do this multible times a week.
So now we have this situation where a lot of important emails get deleted as collateral damage, as the employees are parnoid of opening them. Fantastic system with no flaws at all.🤔🤔7 -
OK I can't deal with this user anymore.
This morning I get a text. "My laptop isn't getting emails anymore I'm not sure if this is why?" And attached is a screenshot of an email purporting to be from "The <company name> Team". Which isn't even close to the sort of language our small business uses in emails. This email says that his O365 password will soon be expiring and he needs to download the attached (.htm) file so he can keep his password. Never mind the fact that the grammar is awful, the "from" address is cheesy and our O365 passwords don't expire. He went ahead and, in his words, "Tried several of his passwords but none of them worked." This is the second time in less than a year that he's done this and I thought we were very clear that these emails are never real, but I'll deal with that later.
I quickly log into the O365 admin portal and reset his password to a randomly-generated one. I set this to be permanent since this isn't actually a password he should ever be needing to type. I call him up and explain to him that it was a phishing email and he essentially just gave some random people his credentials so I needed to reset them. I then help him log into Outlook on his PC with the new password. Once he's in, he says "so how do I reset this temporary password?" I tell him that no, this is his permanent password now and he doesn't need to remember it because he shouldn't ever need to be typing it anyway. He says "No no no that won't work I can't remember this." (I smile and nod to myself at this point -- THAT'S THE IDEA). But I tell him when he is in the office we will store the password in a password manager in case he ever needs to get to it. Long pause follows. "Can't I just set it back to what it was so I can remember it?"9 -
> Be me
> Desperate for a driver
> Find nothing useful
> Oh a GitHub repo, hmmh
> '𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐡𝐞𝐫𝐞 ===> tinyurl.com/XXXXXX'
> Nope
> It's time to report!
Context:
- The url is a redirect chain to a phishing site
- Repo is completely empty except for a single folder with 1000+ files all named after drivers, with the same 'download' link, and probably scraped website text at the bottom (probably to increase searchability)
- The 'user' joined just a couple days ago and has no other repos13 -
Fucking windows! I am so fucking done with this microsoft bullshit!
Hear me out here, i am a gamer. I need windows because it has the games (and software to aid those games) unlike any other platform. But windows 10 is basically already phishing andmalware at this point. I stuck to win 7 because it had a start menu and didn't totally drive me up the wall.
Just a short list of their bullshits: ads in the explorer window, ads in your taskbar reminders, data mining like it is nobodies business and trying to hide it, sharing my wifi access with friends (wtf), the fucking retarded new start menu, the crappy fullscreen apps which have less functionality than the actual proper desktop applications that you need to config what you want, and even then pushing multiple updates that simply broke peoples pc's. Fuck that, ill stick to 7.
They are making win10 worse by the week making it unlikely i will ever join that hell, and they are also aiming to force me there. Making windows store exclusives and dx12 only games. What am i supposed to do against that?! The current releases don't bother me much but fuck i figure it is a matter of time until the newest katamari game is their exclusive and i nanananana katamari damacy all over their platform.
And well all alternative os's are just out of the question unless vulkan rendering gets the upper hand. Then i'd switch to whatever stable distro and learn about our new penguin based overlords languages.
For now i will just stick to win7, suck on my thumb while in fetal position and hope it just all goes away.58 -
Why does every kid developer have a dark theme fetish? I started programming on a Commodore 64. It was dark. It's the quality of the shit you write that defines you assholes, not the color theme of your editor.
Now that that's off my chest, some poos soul has dared to send his resume to me. One of his projects is a website that is being marked by my ENS as a phishing website. I am about to invite him for an interview, and am willing to bet his everything will be dark because he wants to impress me.31 -
I should not have looked at this really interesting Chrome extension.
https://chrome.google.com/webstore/...
It tries to prevent phishing links from working by adding attributes to change the behaviour of the browser.
HOW DOES THIS WORK?
Just one simple line:
$('[target="_blank"]').attr("rel", "noopener noreferrer");
But why is this extension so bloated?
It loads the full jQuery library. For an attribute change!
I'd like to refer to this site for further investigations: http://youmightnotneedjquery.com//...
http://youmightnotneedjquery.com//...3 -
Me: Dad, what are you doing with my facebook account
Dad: Just seeing your news feed son
Me: you don't know my password
Dad: Yes...you just logged in one of my phishing pages.
Me: But when did you learn these things?...you don't even know how to send a mail
Dad: Go, drink some gelusil son3 -
Red flags in your first week of your software engineering job 🚩
You do the first few days not speaking to anyone.
You can't get into the building and no one turns up until mid day.
The receptionist thinks you're too well dressed to work in this building, thinks you're a spy and calls security on you.
You are eating alone during lunch time in the cafeteria
You have bring your own material for making coffee for yourself
When you try to read the onboarding docs and there aren't any.
You have to write the onboarding docs.
You don't have team mates.
When you ask another team how things are going and they just laugh and cry.😂😭
There's no computer for you, and not even an "it's delayed" excuse. They weren't expecting you.
Your are given a TI PC, because "that's all we have", even though there's no software for it, and it's not quite IBM compatible.
You don't have local admin rights on your computer.💀
You have to buy a laptop yourself to be able to do your job.
It's the end of the week and you still don't have your environment set up and running.
You look at the codebase and there are no automated tests.
You have to request access every time you need to install something through a company tool that looks like it was made in 2001.
Various tasks can only be performed by one single person and they are either out sick or on vacation.
You have to keep track of your time in 6 minute increments, assigned to projects you don't know, by project numbers everyone has memorised (and therefore aren't written down).
You have to fill in timesheets and it takes you 30 minutes each day to fill them in because the system is so clunky.🤮
Your first email is a phishing test from the IT department in another country and timezone, but it has useful information in it, like how to login to the VPN.
Your second email is not a phishing test, but has similar information as the first one. (You ignore it.)
Your name is spelled wrong in every system, in a different way. 2 departments decide that it's too much trouble, and they never fix the spelling as long as you work there. One of them fixes it after you leave, and annoys you for a month because you haven't filled out the customer survey.5 -
Email: "we have carried out a phishing test company wide"
Me: Nice!
Email: "results are here"
Me: wow, already done? Didn't even see the email. I must've subconciously discarded it! Damn, I'm good!!
Email: "the test was carried out yesterday"
Me: *was OOO y-day*
Me: fuck12 -
So, got yet another one of those, "Ha! Sending this from your own e-mail address is proof I've infected your machine and recorded video of you synced to your browsing history! Send me bitcoin!" e-mails today. Just with a fun twist:
He claims to have infected my computer on November 8th, 2018 (for later readers: 4 days after the e-mail was sent).
Was about to give them points on creativity the other day; got a Japanese translation of it that was actually pretty spot-on all things considered, and then a Korean copy of it again the next day (just in case I couldn't read English or Japanese, I guess?).
But seriously, you're trying to pull this kind of scam, and can't even tell your bot to successfully pick a date *in the past*?4 -
This is quite interesting and one hell of a find by this guy... Google (and other browser vendors) should reward him:
https://jameshfisher.com/2019/04/...3 -
If someone calls me with the thickest indian accent in the world and they tell me that they are Dave or Mark from an American sounding company I eould usually assume I am getting spammed or phishing calls.
If american companies are contracting from India to do these sorts of things I would really like to know the numbers for it, since I would assume that the average tech company would be like "hey wait a minute this sounds fishy af!"
Not hating on my Indian homies, y'all know i got love for ya, but fuuuuck man y'all can't deny that a lot of fake scam calls come from over there. They can come from anywhere really, but i have gotten many from over there11 -
Recently I got an E-Mail from PayPal.de with the headline "Your account gets limited". Fun Fact: I don't have a PayPal account.
This Mail got me curious though, as it couldn't be a phishing mail, since I don't have a PayPal account in the first place, so I opened the e-mail just to get greeted by pure emptiness. It was completely empty. I thought to myself "oh no, is this some sort of new trick? Did I get infected by some sort of a weird hacky backdoor trojan already?!"
Name: PayPal.de
Original E-mail Address: NULL (never seen this before)
I then realized, that Thunderbird blocked the only content from this mail: a clickable image.
This is getting even more confusing the longer I examine this unique mail. The image is showing me a domain from a site completely unrelated from PayPal, so it was obviously no phishing, but I didn't trust this clickable image, so I looked up its hidden link to find an even more confusing redirection to not a picture upload site like the image suggests, but to a game key reselling site instead, like wtf? What was the whole point of this whole e-mail? Was this a weird try to make advertisements for more than one website? It wasn't even a ref-link or something like that. It was just weird, iunno. 7
7 -
Users.
For once they used their brains.
For once they thought about repercussions of clicking on inconspicuous links in emails.
And naturally it happened when I sent out a legitimate email to stop their shopping sprees.
But then again, I would rather have paranoid users than clicky-go-lucky. 3
3 -
My job sends out emails with things like "You won a prize!" In the subject line with embarrassingly vague reasons to click the links in the email. If you do, the links take you to a site where they slap your wrists for clicking an unknown link and teach you about the dangers of phishing.
It's fake spam. Ironically enough, though, it's the ONLY spam I ever get. It's more annoying than real spam because it never gets blocked by the system like an actual phishing attack would...
It is driving me crazy having to delete these stupid messages every day and they're clogging up my otherwise clean inbox! I don't even know who to contact about this bullshit because they're so "haha we got you!" about it, there's no department claiming responsibility. They're creating their own spam trying to prevent spam. What the hell?7 -
My university alerts all student and staff any time a phishing email is reported. I've yet to attend one class, and I've received a few dozen emails alerting you of phishing emails being sent. It's sad people can't notice the pattern of the emails, and realize right away "Hey this is a bullshit email" and not rely on the alerts.
It's the 21st century; basic computer competency is a necessity.3 -
Oh no, someone hacked my PayPal account, and it seems... PayPal’s too, they can’t spell properly anymore 😰
 11
11 -
You know you're passionate about computers when your completely immune to scams and phishing attacks but the mention of laptop stickers makes you type a rant about it. ~( ̄▽ ̄)~
-
I just had a boys-out night with my son. Went to some restaurant, found a parking spot in a confusing parking lot (half is more expensive than the other half of the lot, not sure which fee applies to the middle row... confusing), started paying for parking with the app (pays every 15 minutes until stopped).
Went inside, ordered a pizza, some ice cream. Chatting, playing, eating, having fun,... An SMS comes: "You have outstanding fines" and a link to the gov taxes' website.
wtf.. I must have parked in the wrong spot. FUCK! Oh well, it should not be a large fine anyways, it's just for parking....
Click on the link, login with my bank/SmartID creds. Another SmartID dialog pops up asking for a PIN2.
What? PIN1 is for authentication, PIN2 is for Authorization. What am I authorizing...?
Reading through the Auth message: "Paying 2473€ for Boris SomeLastname".
what.....?
Thank God my muscle memory did not kick in and I did not enter that PIN2.
And thank God I know what PIN1 and PIN2 are for.
It would've been one expensive boys-out evening... Even a strip club would've been cheaper.
Stay sharp, guys!
P.S. Later I checked the URL. It used all the right keywords, and it was registered as an .info domain. It was somewhat off, but gov websites trying to be lean do sometimes use some weird ass domains.15 -
This is the last part of the series
(3 of 3) Credentials everywhere; like literally.
I worked for a company that made an authentication system. In a way it was ahead of it's time as it was an attempt at single sign on before we had industry standards but it was not something that had not been done before.
This security system targeted 3rd party websites. Here is where it went wrong. There was a "save" implementation where users where redirected to the authentication system and back.
However for fear of being to hard to implement they made a second method that simply required the third party site to put up a login form on their site and push the input on to the endpoint of the authentication system. This method was provided with sample code and the only solution that was ever pushed.
So users where trained to leave their credentials wherever they saw the products logo; awesome candidates for phishing. Most of the sites didn't have TLS/SSL. And the system stored the password as pain text right next to the email and birth date making the incompetence complete.
The reason for plain text password was so people could recover there password. Like just call the company convincingly frustrated and you can get them to send you the password.1 -
Looked into my spam/junk folder and found this. I don't have a C-Panel account, just so you know. I took a look into the link to check it out. It's quite obviously an attempt at phishing. (more screenshots in the comments)
 7
7 -
Be a fellow who's distracted af. You just had a presentation in another city. You're driving home and a light lits up saying you need gas. You stop at the petrol station, pour in some gas, grab a cop of joe while you're at it, pay and leave. You're 15minutes away from the gas stop already and an unknown number is calling you. You pick it up. A male voice says
Voice: "hello, this is police. Did you just leave a gas stop 15 minutes ago?"
You: *wtf, what the fuck did I do now!* "yes, I sure did."
Voice: "you forgot to pay for the fuel"
you: *oh shit, he's right! I remember now - I only paid for the coffee! Shit! I'm in trouble now. *
"oh.. Right, you're right, I forgot... I'll turn around and come back to pay
Voice: "wait, don't rush, I may be able to help you. I'll call you back, keep your phone close" *hangs up*
5 minutes later phone rings again.
Voice: "can you pull over, please? Here's a phone number of that gas stop. Give them a call, I'm sure you'll sort it our. Have a nice day!" *hangs up*
you call that number. A woman picks up.
You: "hello, I forgot to pay you for the gas, gimme a few minutes - I'll turn around and get back to you"
Operator: "do not worry, I think I can help you! You can pay for it at your home town if you like, but I'm afraid they might not be working today. But they will tomorrow! Would that be OK for you?"
you: "umm, yeah, of course! It's my fault - anything is OK for me!"
operator: "ooorrr.. I could pay for you now and you would pay me back. Would that work? Here's my bank account, I'll pay for you when you send me those 50 something €"
a fantasy story? Made up story? Bed time stories? Dysney movie plot? Phishing? Canada?
No. This is Lithuania :) believe it or not, this is a true story, and there are more like this one.
Respect to the police!12 -
So some asshole keeps sending phishing emails to every student and prof in our university and the IT department is too pathetic to block it. They all come from the same email and contain the same text yet they cant filter it and just send warnings not to click it.
Im getting sick of recieving 5 of these a day, i scanned and viewed the page and its just a simple form copying the outlook login page with a redirect to the actual page after submission.
Whats the easiest way to write a script that will spam them with thousands of fake accounts? How can i fuck with these guys?7 -
Meme quoting one of our employees who sent in a ticket asking if something was a "phishing technique without the use of email."

-
Now this has take my faith away from any email I receive... Fuck that shit, Suggest me ideas to reverse spam them.
 9
9 -
There is a new phishing site going around called "rogstrike.com" that is being spread by Steam DMs.
Infected asks victim to "vote for their team" and in order to do that, you need to login with steam. The steam login part is sketchy af, litterally spawns a fake new window in the same tab. Doesn't matter what OS you use, it's always Win 10 styled. Lol.
I reported on twitter and via email, i'll see what they will do. 4
4 -
Why is it always THIS freaking user??? Yes, this is the same one from my previous rant. ALWAYS emails me with a subject line composed of whatever random, vaguely-related-to-the-topic words happen to be jiggling around in his arsehole at the time of writing, vomited out in no particular order. Email body full of typos, wildly incorrect punctuation, and the actual content is completely nonsensical. Accompanied by a screenshot which is always cropped down so small as to be useless. And from what I can gather from this latest one, it looks like he's fallen for yet another phishing email. I SWEAR if that's what happened again......2
-
In highschool we went through something like a malware/phishing prevention course.
It was pretty cool tbh, we spend the whole hour in a virtual environment where you'd see common malware and phishing attempts, but the really fun you could also "hack" other students.
Hacking them means you could cause some things to happen on their "PC". One of those was showing in a captcha on their screen and they had to type a the string of your choosing, before they could access the rest of the "virtual computer" again.
You can probably guess where this is going.
I was the first who had the idea to mix big i and small L and tested it on our teacher, who was also part of this environment and screenshared to the projector.
Thanks to sitting next projection I could see the pixels and I can confirm: same character, Pixel perfect!
I will forever cherish the memory of my the teacher begging me to undo the "hack" and the chaos that followed amongst my peers 😈
Also one of the excersizes was stupid. Click on a phishing mail and enter your credentials in the form. I asked the teacher WTF kind of credentials they even want me to enter to microsooft.cum and they just said "the credentials obviously" so I think they got their karma🖕 -
The most annoying hack I've had to deal with was back when I did IT support, actually. Level 1 call center tech at the time. Apparently someone fell for a phishing email and gave out his outlook credentials. The phisher used that email account to send out another phishing email to roughly 1800 employees.
Security Operations noticed, because this guy's job didn't generally involve sending out mass-communication emails. They investigated, figured out what had happened, and opted for the nuclear option: they reset the password for EVERY SINGLE ACCOUNT that received the email. All 1800 of them. Over the weekend.
I walked into the call center Monday morning and checked the call stats, then did a double-take. There were over 300 people waiting in the queue. I almost left and called in sick. Turns out it wasn't that bad though. Annoying to reset so many passwords and having no downtime due to the full queue, but on the other hand my stats were better that day than any other, since every call was a 5-minute password reset.1 -
So I just got a mail from a bank.
The email address ended with .gmbh
If people want to make phishing emails then please use at least a fucking viable email address6 -
I'm the only one who keep receiving phishing emails about not existing Netflix subscriptions from evident scam email addresses on a daily basis?
I tend to have more of those than newsletters I never subscribed to.
Come on, man, at least try harder to steal my data or money.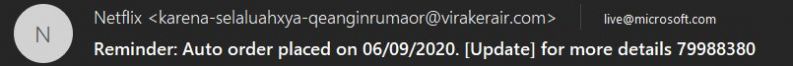 4
4 -
HAHA FUCK YOU HR RECRUITER!!
This fucking lady tries to steal my devs while i spent a lot of blood sweat and tears raising them.
Thankfully my devs are happy with their work type, salary, and conditions. So they showed me a screenshot of her phishing attempts.
There is so much damage I can do to her, and her company as i got all the information, its very tempting.
Since its a "common" dirty and distasteful move, the most sensible course of action I can think of is public shaming. That too is common, dirty and distasteful. But im not that kind of guy.
What do you guys think, should i suck it in and let it slide or public shame her for her actions?3 -
All mail clients are intentionally made not to show sender email address, but rather their chosen name to then launder money on anti-phishing trainings.2
-
CIT: be weary of phishing emails
Also CIT: let's send out a fake phishing mail to see if people are weary of phishing emails6 -
Haven't been on devRant much lately because of all the urgent problems my clients are throwing at me...
 2
2 -
If any of you play counterstrike or have friends that play counterstrike, watch out for a scam where a friend might ask you to vote for their logo/team on some bs "varsity clash whatever" site.
The thing pops up a fake steam login window and tries to phish you as far as I can tell. It's even styled as a Window window (which is fun when you're on linux like me)
I made a throw away account just to test it and I got some fun logins from Russia, though I revoked the access fast enough so that I retained control.
as far as I can tell the site only exists for a couple of days according to WHOIS and all the steam login assets are hosted on some unrelated non valve server...
This PSA is not really for the more skilled and careful people here, but I thought I'd stick it here for the possibly lurkers and less experienced users just in case.5 -
A couple of weeks ago my work email got hacked, I found out because he/she was sending phishing mails to yahoo emailaddresses, but they couldn't be delivered because they were marked as phishing.
I've immediately changed my password and turned on two-factor authentication, shared my story with my boss and now we use two-factor authentication for every service where it is possible.2 -
BT "We'll give you BT Virus Protect, which protects against viruses, phishing and other online attacks."
Or... For a start, let your users provide a good secure password when signing up? More than 8 characters is a bit ambiguous. 20 minutes later and several attempts to find out it can't be longer than 20 characters, only upper and lower case letter and numbers aaaand must start with a letter is a bit s**t. Not to mention LatPass doesn't like it as you can't copy and paste.1 -
Got a phishing email with a link to a website hosted by wix. The only thing on the site was a form and submit button so I’m sure it’s for collecting credentials. I was able to report them and wix shut it down which was nice. But I was thinking, if someone were to ddos the web server, what action would wix do? Would they let the requests keep coming and increase the customers bill? Or would they just shut down the server?2
-
Head hunters reaching out with a "position that might intrest you".. with a stack of skills that are not on my CV at aaaaall
Also Headhunters after answering back: oh you have only 1 year experience with that tool? They want at least 3, goodbye.
All just a phishing scam to get u to give them an updated CV version.. no real "relevant position" in sight. Smh.3 -
Someone is trying to get into my shit. Mail Accounts and my phone is receiving lots of. Spam calls and phishing messages...
Fucking bastards..
We all get phishing shit but if it’s targeted it makes me feel awkward..
Little fucking bastards.. I think I even know who it is.. that useless piece of junk that got fired because of my honest feedback. Not many others know my current nr, emails etc..7 -
LOLOL, my grandma goes hellish when I entered her password to google, she has seen some videos on the internet like "people deploy fake medical ads for seniors" or "phishing.
Fuck youtube.4 -
I worked 2012-2016 for a big telco company in my country and there was this HTTPS webpage with an iframe rendering any url you passed over the ?url query param plus a header with the company's logo.
I was on a meeting with some friends in charge of social media and they found it for a user report.
Unbelievable 🤷🏻♂️ I remember I tried the page's url itself and it rendered a loop of the header with the company's logo 😂 -
Cryptocurrency Recovery Expert / Captain WebGenesis
CAPTAIN WEBGENESIS is a trusted and reliable solution for individuals seeking to recover lost or inaccessible cryptocurrency assets. With a team of expert cryptographers and cybersecurity specialists, the recovery expert utilizes cutting-edge technology to navigate the complexities of blockchain forensics and retrieve lost or stolen digital assets. CAPTAIN WEBGENESIS proprietary recovery protocols are designed to ensure the utmost security and confidentiality, providing his clients with peace of mind throughout the recovery process. Whether you've lost access to your wallet, forgotten your private keys, or fallen victim to a phishing scam, CAPTAIN WEBGENESIS is dedicated to helping you regain control of your cryptocurrency portfolio. The customer-centric approach, combined with his unparalleled technical expertise, has earned the team a reputation as a go-to solution for cryptocurrency recovery. Don't let lost or inaccessible assets hold you back - contact CAPTAIN WEBGENESIS today to take the first step towards recovery.13 -
!dev-related
Found out that a pervert from my gf’s highschool took a bunch of screenshots of her Instagram (bikini pictures, etc.) and posted them to the r/breeding and other fucked up subreddits even though she was only 16/17 in the photos
We notified the uni he goes too and nothing happened. We noticed the police of his hometown and they said they couldn’t do anything because he was currently at his uni
He then claimed it was a rumor and it wasn’t him even though the Reddit account that posted it had a previous post that directly connected the Reddit account to his Instagram account and the Reddit account mentioned had a post that mentioned his home town
My poor gf is now having panic attacks bc this motherfucker wanted to jerk his tiny dick off with his retard friends bc they were rejected by her in highschool
It’s taking so much effort not to send him some phishing emails and empty his fucking bank account16 -
Me: This spam email looks a little weirder than normal.
Phishing team: Its just spam don't waste our time.
*15 min later*
Phishing team: Nevermind. Its trying to take your log in info off your account. Thanks
...Jerks -
Anybody know what this service running in the background on an android device does?
It sent me a plain text notification, which disappeared and sent me to a phishing site the moment I tried clearing it. I've forced killed the process for now.
A quick search online doesn't reveal much information, except for a dodgy site claiming it's spyware named StealthGenie. 20
20 -
WHO CAN HELP ME GET MY BITC0IN BACK WITH MIGHTY HACKER REC0VERY AND HIRE THE BEST HACKER FOR ALL HACKER SERVICES AT MIGHTY HACKER RECOVERY
I can't believe the turn of events that led me to reclaiming my lost Bitc0in! A few months ago, I fell victim to a phishing scam and lost a significant amount of money. I was devastated and hopeless, believing I'd never see my money again.
After some research, I came across Mighty Hacker Rec0very. Skeptical but desperate, I decided to contact them. I began chatting with one of their hackers and was immediately impressed by their expertise and professionalism. They patiently walked me through the recovery process, reassuring me along the way.
They worked diligently on my case for several weeks, using their expertise to locate my lost funds. It was intense, but I felt optimistic for the first time since the scam. The communication was clear, and I received regular updates, which reduced my anxiety.
Finally, I received the news that my Bitc0in had been successfully recovered! I couldn't believe it—I was ecstatic! I'm extremely grateful to the hacker who assisted me. Mighty Hacker Rec0very transformed a nightmare into a triumph, and I'm grateful beyond words. If anyone is in a similar situation, I highly recommend contacting them!
WH@TS@PP: +1 8 45 6 99 50 44
EM@IL: support @ mightyhackerrecovery . com
FB: mighty hacker recovery2 -
Second phishing victim of the year.
F*ck our email service provider, the service sucks so much. The deny list DOESN'T EVEN WORK. I'm so fed up with this.3 -
Just got another email from servíce@intl-paypal.com <zlvx... (noticed that “í”? Me neither) that says “[N3YywM] <https://amazon.co.uk... ” and it goes on and on...
wow, service? Seems important! I guess I should open it and click on every link!!! 🙄7 -
Me : Hey what are you doing there? (Asking the Mr.X who is sitting near the pond)
Mr.X : I was fishing..
Me : But I don't see any fishing tackle there.
Me : out of curiosity, I walked over to him and asked how many he had caught.
Mr.X : I collected 2 of my friends creds
Me : what 🤔!!
Me : Finally I reached near to the pond and found that he was really "phishing"5 -
I just experienced a new level of wut at my job. Web Engineering has a Google group email. This morning someone at work sent us an email about canceling a work order (and he didn’t know how to cancel it)…for a plumbing issue 😑Wrong engineering department, my dude. And you can cancel your work order by going to the request system where you submitted it or the email receipt of you request, which was certainly not to this Google group email. You have the work order number, so you must have an email somewhere about your request. And how’d he get this email?? I’m seriously wondering if this is a weird phishing attempt.2
-
Fuck you "hackers"! You make my life miserable...
No longer can anyone simply enter their user name and password to enter an online app...
Now we as programmers have to leap from one fiery hoop on the precipice of a death defying cliff to another acidic hoop in some mystical forgotten cavern of the underworld just so our users can log in securely to our app... sigh... I'm looking at you Auth0 and Microsoft SSO / AAD !!!111oneeleven
I mean wtf even is a nonce?!
https://urbandictionary.com/define....
**gosh** 11
11 -
I NEED A HACKER TO RECOVER MY LOST CRYPTO / USDT - Hire ULTIMATE HACKER JERRY
I have a lot of experience trading cryptocurrencies, and I am a cryptocurrency trader. Previously, I kept my money in a trezor wallet, however I recently clicked on a phishing link by accident, and all of my coins were gone. I instantly searched the internet for a hacker to help me get my lost cryptocurrency back. It took me a while to find a post on Ultimate Hacker Jerry. I reached out to Him to help me. Following my unintentional click on a phishing link, ULTIMATE HACKER JERRY, a skilled private hacker at American Firm, successfully recovered $3.6 million in cryptocurrencies from my trezor wallet.9 -
few hours back I ranted abt tired body and caffeinated mind, I came back from work and I alcoholized my mind. still the bastard is nt allowing me to sleep. I think it is the time for some phishing the people who are using my free wifi.
-
March's Khyber Weather was out of ordinary
Phishing and CEO-scams continued in March with even more activity.
SUPO told in their annual letter that focused attacks are day-to-day deal against Finland and Finnish companies. Positive things being that functionality of communicational services was better than average and there were new guidelines published about IoT-products' minimal requirements in the Great Britain.
Source:
Finnish Communication Regulatory Authority
https://viestintavirasto.fi/kybertu...
Translation by:
@joas1 -
RECLAIM YOUR STOLON OR LOST CRYPTOCURRENCY WITH THE HELP OF RAPID DIGITAL RECOVERY
From a young age, football was my passion, and this love for the sport led me to pursue a career as a professional footballer in England. While it was a dream come true, the financial rewards weren’t as substantial as I had hoped. Realizing the need for financial security beyond my football career, I began exploring alternative investment opportunities. At the time, Bitcoin was a hot topic among my colleagues, and their enthusiasm sparked my interest. With growing curiosity, I decided to invest £8,000 in Bitcoin, and over time, my investment grew to an impressive £50,000. This financial success gave me the confidence to expand my business ventures and take on larger projects. However, my excitement was short-lived when I fell victim to a sophisticated phishing scam. One day, I encountered a website that looked identical to my trusted trading platform. Believing it was legitimate, I entered my login details without hesitation. Shortly after, I discovered that my Bitcoin wallet had been emptied. Years of hard work and financial growth vanished in an instant. I was devastated and felt completely helpless. A friend in the crypto community recommended Rapid Digital Recovery, a team known for helping individuals recover stolen cryptocurrency. Desperate for a solution, I reached out to them, What sapp Info: +1 41 4 80 7 14 85, hoping they could help me reclaim what I had lost. From the very first interaction, I was impressed by their professionalism, expertise, and efficiency.The team at Rapid Digital Recovery thoroughly investigated the fraudulent activity, and to my immense relief, they managed to recover most of my stolen funds. Beyond their technical expertise, they also took the time to educate me on essential security measures. They recommended using hardware wallets for added safety, enabling two-factor authentication (2FA), and double-checking website URLs to avoid phishing scams in the future. Their guidance proved invaluable, not only helping me recover my funds but also ensuring that I could better protect my investments moving forward. My journey with Bitcoin has been a mix of success and challenges. While I’ve experienced the joy of financial growth, I’ve also learned the harsh realities of the digital world. Thanks to Rapid Digital Recovery, I now approach cryptocurrency with caution and confidence, armed with the knowledge to navigate this complex space securely.
Email INFO: rap iddi gita lrecov ery @ exe cs. com 26
26 -
Cyberpunk Programmers is a specialized firm focused on recovering lost cryptocurrency assets. Their expert team employs advanced blockchain forensics and tracing techniques to retrieve funds lost to scams, hacks, or fraud. With a client-first mindset, they prioritize clear, jargon-free communication, ensuring clients understand the recovery process.
The company distinguishes itself through transparency and security, implementing strict measures to protect sensitive data. Their results-oriented fee model charges only upon successful recovery, aligning their goals with clients’ interests and reducing upfront risks. This reflects their confidence in tackling complex crypto recovery cases.
Cyberpunk Programmers handles various asset loss scenarios, from phishing attacks to compromised wallets, catering to both novice and seasoned crypto users. Their efficient approach aims for swift resolutions without compromising thoroughness, making their services accessible and reliable.
Known for ethical practices, Cyberpunk Programmers has earned a strong reputation in the asset recovery industry. Their dedication to client satisfaction and expertise in navigating digital fraud make them a trusted choice for those seeking to reclaim lost crypto assets. For anyone facing cryptocurrency loss, Cyberpunk Programmers offers a professional, secure, and effective solution. for more info about Cyberpunk Programmers inquire at cyberpunkprogrammersdotcom6 -
it's easier to minimize interactions or use of emails to avoid phishing than deal with sorting it out especially since most companies do in house fake phishing for training3
-
Learned HTML in 7th from my sister's web designing book(she was doing some course from institute), then in 10 class met with C++, Sql because they were in the course, in college first year met with PHP as my roommate was searching how to do phishing attack, then met C++ and after that Java, Javascrip, Android development, Javascript and many more all because of various projects i did.... glad that i took those projects. 😊
-
THE ULTIMATE SOLUTION TO CRYPTO RECOVERY WITH FASTFUND RECOVERY.
I never thought I'd see my lost crypto again after falling victim to a phishing scam that wiped out my wallet. I contacted FastFund Recovery out of desperation, and to my surprise, they were professional, responsive, and thorough. Within a few weeks, they were able to trace the stolen assets and recover a significant portion of my funds. Their constant updates and transparency throughout the process gave me peace of mind. I’m incredibly grateful for their help. FastFund Recovery truly delivered when I needed it most.
G-mail: Fastfundrecovery8@gmail com. Whatsapp: 1807 500 75548 -
Recover Your Lost or Stolen Cryptocurrency with BITCRACK RECOVERY EXPERTS
Losing cryptocurrency to scams, hacks, or simple mistakes can be devastating. Whether you sent funds to the wrong address, fell victim to a phishing attack, or lost access to your wallet, BITCRACK RECOVERY EXPERTS specializes in retrieving lost digital assets with a proven success rate.
Why Choose BITCRACK RECOVERY EXPERTS?
✔ High Success Rate – Recovered millions in lost crypto for clients worldwide
✔ Advanced Blockchain Forensics – Traces stolen funds across exchanges & wallets
✔ Fast Response Team – 24/7 emergency assistance for urgent cases
✔ No Recovery, No Fee – Payment only after successful fund retrieval
We Recover:
🔹 Hacked Wallets & Exchanges – Regain access to compromised accounts
🔹 Phishing & Romance Scams – Trace and freeze stolen crypto
🔹 Lost Private Keys/Passwords – Recover inaccessible wallets
🔹 Rug Pulls & Fake ICOs – Investigate fraudulent projects
🔹 Misdirected Transactions – Retrieve crypto sent to wrong addresses
How It Works
1️⃣ Contact Us – Email bitcrackrecoveryexperts@bitcrack.co.site with transaction details
2️⃣ Free Case Review – Our experts analyze recovery possibilities
3️⃣ Recovery Process – We trace, freeze, and retrieve your funds
4️⃣ Secure Return – Your crypto is safely returned to you
"BITCRACK Recovered $120K I Lost to a Fake Investment Scam!" – Mark D., Verified Client
Time is Critical – Act Now!
The longer you wait, the harder recovery becomes. Many stolen funds can be traced and frozen if reported quickly.
Email BITCRACK RECOVERY EXPERTS Today:
bitcrackrecoveryexperts@bitcrack.co.site
Don’t let scammers win – reclaim your crypto now!2 -
HOW TO GET A PROFESSIONAL BITCOIN RECOVERY EXPERT HIRE ADWARE RECOVERY SPECIALIST
WhatsApp info:+1.2.7.2.3.3.2.8.3.4.3
In the world of cryptocurrency, the idea of losing access to your funds can feel like a nightmare. But for me, that nightmare became a reality when 40,000 ETH was stolen from my wallet through a sophisticated phishing attack. The theft occurred during a time when the value of Ethereum was at an all-time high, making the situation even more stressful. Desperate and unsure where to turn, I found myself at a crossroads. That’s when I discovered ADWARE RECOVERY SPECIALIST, and their professional approach to crypto recovery turned my story around. The ordeal began when I received an email that appeared to be from a trusted source within the crypto community. The email urged me to confirm certain account details via a link provided. Unbeknownst to me, this was part of a carefully orchestrated phishing scam. I clicked the link and logged into what seemed to be a legitimate platform. By the time I realized something was wrong, it was too late. My wallet had been emptied of 40,000 Ethereum. Panic set in as I scrambled to understand what had just happened. The thief had transferred the ETH across multiple wallets, making the funds almost impossible to trace. The emotional toll was immediate. Those 40,000 ETH were not just a number to me; they represented years of hard work, personal sacrifice, and long-term financial planning. I felt devastated and powerless, unsure of how to proceed or where to turn. I tried everything I could on my own—searching for transaction details, contacting exchanges, and reporting the incident—but the funds seemed to have vanished into thin air. It was then that I realized I needed expert help. After extensive research, I came across ADWARE RECOVERY SPECIALIST . Their reputation for successfully recovering lost or stolen crypto assets was impressive. I decided to reach out to them, and from the very first conversation, I felt reassured. The team was not only knowledgeable but also empathetic to my situation. They took the time to understand the full scope of the attack and immediately started investigating my case. What impressed me most was their transparency and clear communication. They explained the recovery process in detail, outlining the steps they would take to trace the stolen funds and pursue every avenue of recovery. Within a short period, ADWARE RECOVERY SPECIALIST made significant progress, and, thanks to their expert efforts, a substantial portion of my stolen Ethereum was recovered. Looking back, I am deeply grateful for their professional approach. What started as a nightmare has turned into a story of hope and recovery. ADWARE RECOVERY SPECIALIST didn’t just recover my funds—they restored my faith in the crypto community and gave me back a piece of my future.3 -
I recently had a fantastic experience with Cyberpunk Programmers that I can’t stop raving about. After a phishing attack drained my wallet of 2.5 Bitcoin, I was convinced my funds were gone for good. Desperate, I stumbled across Cyberpunk Programmers online and decided to give them a try—best decision ever.
Their team was incredibly knowledgeable and jumped into action right away. They analyzed the breach, tracked the transactions, and kept me updated every step of the way. I was blown away by their skills; in just under a month, they recovered my 2.5 Bitcoin, restoring $150,000 worth of value at today’s rates. The process was straightforward, and their communication made me feel confident despite the chaos I’d been through.
What sets Cyberpunk Programmers apart is their blend of cutting-edge tech and genuine customer care. They didn’t just recover my funds—they also shared tips to protect my wallet from future attacks. Their pricing was fair, especially given the life-changing result they delivered.
If you’ve lost Bitcoin or any crypto, I can’t recommend Cyberpunk Programmers enough. They turned my despair into disbelief when I saw 2.5 Bitcoin back in my account. No matter the amount, their expertise is worth it. I’ve already told friends about them, and I urge anyone in a similar mess to reach out. Cyberpunk Programmers isn’t just a service—they’re a lifeline for crypto users. Reliable, fast, and brilliant at what they do! Their contact details are;
Email: cyberpunkatprogrammerdotnet3 -
Best Recovery Experts for Cryptocurrency Assets
As the cryptocurrency landscape evolves, so do its associated risks, such as phishing scams and hacks. Recovery experts have become invaluable allies for investors navigating these challenges. Below, we explore the best recovery experts for cryptocurrency assets.
Crypto Recovery Companies
Crypto recovery companies offer services like unlocking encrypted wallets, recovering forgotten passwords, and restoring Bitcoin accounts. They prioritize privacy and implement robust security protocols to protect financial information throughout the recovery process.
These companies employ skilled teams equipped with blockchain expertise, cutting-edge tools, and investigative strategies to recover lost or inaccessible digital assets. Their goal is to assist individuals who thought their digital wealth was irretrievably gone.
With the growing use of cryptocurrencies, demand for recovery solutions has surged, driven by the rise in stolen cryptocurrency cases and the need for effective recovery strategies. Recovery experts use advanced software, forensic methods, and in-depth blockchain knowledge to trace missing funds, decrypt wallets, and regain account access.
Puran Crypto Recovery
Puran Crypto Recovery simplifies the recovery process for victims of cryptocurrency theft with tailored, professional support. Known for reliability and efficiency, they offer:
Comprehensive Recovery Support: Puran Crypto Recovery employs secure and effective methods to restore lost assets.
Global Availability: Their worldwide team ensures assistance is accessible anytime and anywhere.
Expertise and Experience: With a proven track record, Puran Crypto Recovery provides clients with confidence and trust in their recovery services.1 -
DON’T LOSE HOPE,RECOVER YOUR STOLEN CRYPTO FUNDS WITH DIGITAL HACK RECOVERY SPECIALISTS
In the world of cryptocurrency, the idea of losing access to your funds can feel like a nightmare. But for me, that nightmare became a reality when 40,000 ETH was stolen from my wallet through a sophisticated phishing attack. The theft occurred during a time when the value of Ethereum was at an all-time high, making the situation even more stressful. Desperate and unsure where to turn, I found myself at a crossroads. That’s when I discovered Digital Hack Recovery, and their professional approach to crypto recovery turned my story around.The ordeal began when I received an email that appeared to be from a trusted source within the crypto community. The email urged me to confirm certain account details via a link provided. Unbeknownst to me, this was part of a carefully orchestrated phishing scam. I clicked the link and logged into what seemed to be a legitimate platform. By the time I realized something was wrong, it was too late. My wallet had been emptied of 40,000 Ethereum. Panic set in as I scrambled to understand what had just happened. The thief had transferred the ETH across multiple wallets, making the funds almost impossible to trace.The emotional toll was immediate. Those 40,000 ETH were not just a number to me; they represented years of hard work, personal sacrifice, and long-term financial planning. I felt devastated and powerless, unsure of how to proceed or where to turn. I tried everything I could on my own—searching for transaction details, contacting exchanges, and reporting the incident—but the funds seemed to have vanished into thin air.It was then that I realized I needed expert help. After extensive research, I came across Digital Hack Recovery. Their reputation for successfully recovering lost or stolen crypto assets was impressive. I decided to reach out to them, and from the very first conversation, I felt reassured. The team was not only knowledgeable but also empathetic to my situation. They took the time to understand the full scope of the attack and immediately started investigating my case.What impressed me most was their transparency and clear communication. They explained the recovery process in detail, outlining the steps they would take to trace the stolen funds and pursue every avenue of recovery. Within a short period, Digital Hack Recovery made significant progress, and, thanks to their expert efforts, a substantial portion of my stolen Ethereum was recovered.Looking back, I am deeply grateful for their professional approach. What started as a nightmare has turned into a story of hope and recovery. Digital Hack Recovery didn’t just recover my funds—they restored my faith in the crypto community and gave me back a piece of my future. For quick assistance contact Digital Hack Recovery via⁚
WhatsApp⁚ +1(915)2151930
Website; https : // digital hack recovery . com
Email address⁚ digital hack recovery @ techie . com1 -
Blockchain Legal Forensics & Cyber Experts for Swift Recovery-BETAFORT RECOVERY
Betafort Recovery came to my rescue after I lost access to my Bitcoin trading accounts due to a phishing email mishap, resulting in a devastating loss of $87,500 worth of Bitcoin. Feeling lost and desperate, I turned to Betafort Recovery after reading countless positive reviews about their success in similar cases.
Within just two hours, Betafort Recovery successfully tracked down the perpetrators and recovered my account with the Bitcoin fully intact. Their ability to quickly locate the culprits was beyond impressive.
What truly sets Betafort Recovery apart from other services on the market is their unparalleled tracking capabilities and ethical approach. They operate with transparency and integrity, ensuring that the recovery process is not only effective but also aligned with ethical standards. The platform’s seamless integration with cryptocurrency exchanges allowed them to act decisively and with precision, ensuring that the criminals were held accountable.
Betafort Recovery’s swift, ethical, and efficient recovery process was a beacon of hope in what initially seemed like an insurmountable situation. It proved that with the right tools, expertise, and determination, anything is possible.
If you'd like to hire their services, they're available via their contact information or through a quick Google search.
Home page: Betafort Recovery
Mail; info@betafort.online
Text /Call +171260047292 -
Digital assets require one to be extra careful, otherwise it can mess you in an instant. Like many, I fell victim to a tricky phishing scam after foolishly claiming a fake airdrop only to end up connecting my wallet to scammers. My account was compromised, and before I could realize 437 ETH was stolen. I couldn't believe it. All my money gone in a flash.
I was completely overwhelmed and feeling utterly hopeless. Then I stumbled upon Crypt0 Pandemic Hunter while desperately searching for solutions online. Skeptical but with nothing to lose, I reached out. From the very beginning, their team was responsive, punctual and transparent making it easier to trust them. I shared the whole necessary details and after assessment they were able to weigh out possible outcomes.
They quickly analyzed the situation and implemented a recovery strategy utilizing their extensive network and advanced investigative techniques to trace my stolen assets. I was kept informed every step of the way, which was incredibly reassuring during such a stressful time. They were successful! Crypt0 Pandemic Hunter managed to recover the 437 ETH from the scammers different accounts.
I am eternally grateful for their expertise and dedication. Without Crypt0 Pandemic Hunter, the recovery couldn't have been possible. I hope sharing this review can be helpful to any victim who may be need.2 -
CRYPTOCURRENCY RECOVERY SERVICES: BOTNET CRYPTO RECOVERY
As the cryptocurrency market continues to evolve and grow, it's no secret that the number of scams, frauds, and cyber-attacks has also increased exponentially. The anonymity and lack of regulation in the crypto space make it a breeding ground for malicious actors, leaving innocent investors vulnerable to financial losses. This is exactly why BOTNET CRYPTO RECOVERY, a trailblazing cryptocurrency recovery company, has emerged as a beacon of hope for those who have fallen prey to these nefarious activities.
With a proven track record of successfully recovering millions of dollars' worth of stolen or lost cryptocurrencies, BOTNET CRYPTO RECOVERY has established itself as the most trusted and reliable recovery company worldwide. Their team of expert cybersecurity specialists, forensic analysts, and blockchain experts work tirelessly to track down and retrieve stolen assets, using cutting-edge technology and innovative strategies to stay one step ahead of the scammers.
What sets them apart from other recovery companies is our unwavering commitment to their clients. They understand the emotional and financial distress that comes with losing hard-earned savings, and they are dedicated to providing a personalized, empathetic, and confidential service that puts our clients' needs above all else. Their dedicated support team is available 24/7 to guide you through the recovery process, ensuring that you are informed and empowered every step of the way. with countless success stories are a testament to their expertise and dedication. From retrieving stolen Bitcoin from a phishing scam to recovering Ethereum lost in a Ponzi scheme, They have helped numerous individuals and businesses regain control of their digital assets. their clients' testimonials speak volumes about their exceptional service and unparalleled results:
BOTNET CRYPTO RECOVERY is a Godsend. I had lost all hope after falling victim to a sophisticated phishing scam, but their team worked tirelessly to recover my stolen Bitcoin. I couldn't be more grateful for their professionalism and expertise.
I was skeptical at first, but BOTNET CRYPTO RECOVERY truly delivered on their promise. They recovered my lost Ethereum and helped me understand how to protect myself from future scams. I highly recommend their services to anyone who has been a victim of cryptocurrency fraud. If you or someone you know has fallen victim to a cryptocurrency scam or fraud, don't hesitate to reach out to them. Their team is ready to help you recover your losses and take back control of your digital assets.
Contact them today to schedule a consultation and take the first step towards reclaiming your financial freedom.
Email: [ support@ botnetcryptorecovery . com ]
Phone: +1 (431) 801-8951
Website: [ botnetcryptorecovery. com ]
Let us help you weave a safer web in the world of cryptocurrency. 3
3 -
FACING DIFFICULTIES RECOVERING YOUR BITCOINS? CONSULT ADRIAN LAMO HACKER
Navigating life as a divorced parent with two children is undeniably challenging, especially when it comes to financial stability. As a high school teacher, I found myself in a constant struggle to make ends meet, prompting me to seek additional income streams without compromising my teaching job. That's when I turned to cryptocurrency trading, seeing it as a promising avenue to supplement my earnings. After six months of diligent learning and practicing with a demo account, I felt confident enough to dive into live trading. Excited by the potential for financial growth, I decided to invest my life savings of $150,000, along with taking out a mortgage on my house, viewing it as a strategic investment in trading Bitcoin. Initially, my efforts seemed fruitful as I quickly amassed a profit of $10,000 within the first few weeks. However, my newfound success was short-lived when I received a malicious email from an unknown sender, enticing me to invest on their behalf. Little did I know, it was a phishing scam designed to steal my personal information. In a cruel twist of fate, I lost access to my email account and all associated login details, including passwords to my cryptocurrency wallets. Panic and despair consumed me as I realized the extent of the deception. My hard-earned money and financial security were now in jeopardy, leaving me feeling helpless and vulnerable. In my darkest hour, a glimmer of hope emerged when I learned about ADRIAN LAMO HACKER through a trusted friend. Desperate for a solution, I reached out to them, hoping against hope that they could help me regain access to my lost funds and restore my peace of mind. ADRIAN LAMO HACKER's dedicated team of experts proved to be a lifeline in my time of need. With their unparalleled expertise and unwavering determination, they worked tirelessly to recover my stolen assets and restore access to my compromised accounts. Their thorough investigation uncovered crucial evidence, ultimately leading to the apprehension of the perpetrators responsible for the phishing scam. Through their invaluable assistance, I not only recovered my lost funds but also gained a newfound sense of security and confidence in navigating the digital landscape. The experience served as a poignant reminder of the importance of vigilance and caution when engaging in online activities, especially in the realm of cryptocurrency trading. In conclusion, my journey with ADRIAN LAMO HACKER was a testament to their unwavering commitment to assisting victims of digital scams. For anyone facing similar challenges, I wholeheartedly recommend ADRIAN LAMO HACKER as a trusted ally in reclaiming what rightfully belongs to them and restoring financial stability. Contact ADRIAN LAMO HACKER via the website: https : // adrianlamohackpro . online/
WhatsApp: +1 (909) 739‑0269 -
HOW TO GET BACK STOLEN DIGITAL ASSETS // CRYPTO PANDEMIC HUNTER
In today's digital age, cryptocurrency has become a popular investment option for many people around the world. However, with its popularity has come an increase in scams and fraudulent activities. Losing 47,000 CAD in crypto to a phishing scam left devastated and frankly, hopeless. That's when I stumbled upon Crypto Pandemic Hunter, and I can honestly say they were my lifeline.
From the initial consultation, their team was reassuring. They patiently listened to my ordeal, explaining the process of tracing and recovering my stolen funds. I was particularly impressed by their understanding of blockchain technology and the tactics employed by scammers.
Crypto Pandemic Hunter employed a multi-faced approach. They utilized advanced blockchain analytics tools to thoroughly track the flow of my stolen crypto, identifying the various wallets and exchanges it passed through. They also leveraged their network of contacts within the crypto community and law enforcement to put pressure on the exchanges involved.
They provided regular updates, explaining the technical details in a way I could understand. After a few weeks of intense investigation and pursuit, Crypto Pandemic Hunter successfully recovered my 47,000 CAD!
I am immensely grateful to Crypto Pandemic Hunter for their expertise, dedication, and unwavering support. They turned a worst case scenario and turned it around. If you have been a victim of a cryptocurrency scam or fraud, don't hesitate to contact Crypto Pandemic Hunter for help.7 -
HOW TO RETRIEVE STOLEN BITCOIN HIRE ADWARE RECOVERY SPECIALIST
WhatsApp info:+12723 328 343
Website info: http s:// adware recovery specialist. com
Email info: Adware recovery specialist (@) auctioneer. net
Telegram info: http s:// t.me/ adware recovery specialist1
The clinking of kibble bowls and staccato slap of paws against linoleum usually serve as background to my days. That day, however, our animal rescue's crypto wallet, our financial lifeline that covered all sorts of spay surgeries and emergency parvo treatments, was more bare than a dog park during a thunderstorm. A phishing attempt, disguised as a donation receipt for a "kind benefactor" (spoiler: their kind was stealing $215,000), had cleaned us out. Trigger panic: volunteers huddled around one computer, adoptive kittens blissfully batting at keyboard cables, and me Google-searching can you repo a cat? Enter Sarah, our expert volunteer who codes firewalls by day and plays with stray kittens by night. She slid a sticky note across the desk: ADWARE RECOVERY SPECIALIST. They're like the animal control of crypto scams. Desperation eclipsed skepticism. I emailed them, half-expecting to receive a bot response. Instead, a guy named Marco replied in minutes: Send us the transaction hash. We'll hunt. As it was, phishing our crypto was simpler than stealing steak from a pack of wolves. ADWARE RECOVERY SPECIALIST crew dissected the attack with the precision of a vet neutering a tomcat. The robbers had channeled donations through privacy coins and decentralized exchanges, a digital shell game designed to lose us in the noise. But ADWARE RECOVERY SPECIALIST engineers? They followed it down like bloodhounds to a money laundering fund masquerading as a "charity DAO (their paperwork riddled with typos like "helping puppys since 2023 beginners).
Ten days later, Marco called: Check your wallet. I refreshed, expecting another error message. Instead, our balance flashed green, back to the cent. The shelter erupted, a din of barks, meows, and one intern crying into a Chihuahua's sweater. The scammers' wallets? Frozen faster than a stray in a blizzard.
ADWARE RECOVERY SPECIALIST didn't save dollars; they saved futures. That $215,000 bought a terrier's spinal fusion, shots for 47 shelter animals, and a whole year's supply of that excellent kibble our old dogs negotiate not loving. Our online wallet now has more security than a porcupine has quills, and Sarah's now officially Director of Not Getting Hacked Again. If your nonprofit's funds ever disappear into the ether of cyberspace, don't bawl into the garbage can. Call the ADWARE RECOVERY SPECIALIST . They'll treat your case like a patient in critical care, no matter how many paws are on the keyboard. Just maybe hide your keyboard from the kittens first.1 -
Betafort Recovery – The trusted choice for cryptocurrency recovery services.
Betafort Recovery came to my rescue after I lost access to my Bitcoin trading accounts due to a phishing email mishap, resulting in a devastating loss of $95,500 worth of Bitcoin. Feeling lost and desperate, I turned to Betafort Recovery after reading countless positive reviews about their success in similar cases.
Within just two hours, Betafort Recovery successfully tracked down the perpetrators and recovered my account with the Bitcoin fully intact. Their ability to swiftly locate the culprits was beyond impressive.
What truly sets Betafort Recovery apart from other services on the market is their unparalleled tracking capabilities and ethical approach. They operate with transparency and integrity, ensuring that the recovery process is not only effective but also aligned with ethical standards. The platform’s seamless integration with cryptocurrency exchanges allowed them to act decisively and with precision, ensuring that the criminals were held accountable.
Betafort Recovery’s swift, ethical, and efficient recovery process was a beacon of hope in what initially seemed like an insurmountable situation. It proved that with the right tools, expertise, and determination, anything is possible.
If you're seeking reliable cryptocurrency recovery services, Betafort Recovery is the team to trust.2 -
DOES CRYPTO RECOVERY ACTUALLY WORK? YES IT DOES- GEARHEAD ENGINEERS CASE STUDY
Losing access to your cryptocurrencies can be a nightmarish scenario. Whether you forget your passwords, fall victim to fake trading platforms or phishing scams, or experience hardware failures with your crypto wallet, the first thing you might want to do is contact a crypto recovery service. However, the unfortunate reality is that while few crypto recovery services are legitimate, most are scams designed to prey on those already in distress. Getting scammed while attempting to recover from a previous scam would be the worst-case scenario. It often makes you wonder whether crypto recovery is truly possible. In reality, tracing and getting back your crypto can only be done by individuals who have the expertise to navigate the vulnerabilities of the scammer’s systems and obtain crucial details that can be used to track transactions and eventually retrieve crypto back to the victims. GearHead Engineers have been proven time and again to be the leading legitimate recovery services. This eliminates the need to go from one organization to another seeking for legit services. Get the contact details by visiting their website by doing an online search of Gearhead Engineers then click on the website indicated as Gearhead engineers- cyber security company.2 -
It all began in late 2024 when I fell victim to a sophisticated phishing scam. An email, seemingly from a reputable crypto exchange, prompted me to update my security settings. Unbeknownst to me, this was a trap. Within hours, my Bitcoin holdings vanished from my wallet.
Devastated, I scoured the internet for solutions. That’s when I stumbled upon NanoAethosCoinRecovery, a firm renowned for its expertise in retrieving stolen cryptocurrencies. Skeptical yet desperate, I reached out to them.
Their team responded promptly, assuring me of their commitment to assist. They explained their process: utilizing advanced blockchain analysis tools to trace the movement of stolen funds and collaborating with exchanges to freeze and recover assets.
Over the next few weeks, they provided regular updates, detailing the trail of my stolen Bitcoin. Their persistence paid off. They identified the wallet holding my funds and, through their network, managed to facilitate the return of my Bitcoin.
This experience was a stark reminder of the risks in the crypto space and the importance of swift action and expert assistance. Thanks to NanoAethosCoinRecovery, I not only recovered my assets but also gained invaluable insights into safeguarding my digital wealth.
For more information, contact:
Whatsapp: +1 (570) 229-9724
Telegram: @NanoAethos1 -
HOW OPTIMUM HACKER RECOVERY HELPED ME RECOVER $600,000 IN BITCOIN
I never thought I would find myself in a situation where I would lose a significant amount of money to hackers, but that’s exactly what happened. After falling victim to a phishing scam, I lost $600,000 worth of Bitcoin. I felt devastated and helpless, unsure of how to recover my funds. That’s when I discovered Optimum Hacker Recovery. From the moment I reached out to them, I was met with professionalism and empathy. Their team of experts took the time to understand my situation and assured me that they had the tools and knowledge to help recover my lost assets. They conducted a thorough investigation, tracing the transactions and identifying the hackers involved. Their transparent communication kept me informed every step of the way, which eased my anxiety during this stressful time. Thanks to their relentless efforts and expertise, I was able to recover my $600,000 in Bitcoin. I can’t express how grateful I am to Optimum Hacker Recovery for their outstanding service. If you ever find yourself in a similar situation, I highly recommend reaching out to them. They truly are a lifesaver in the world of cryptocurrency recovery. 1
1 -
HIRE A BITCOIN FRAUD RECOVERY HACKER DUNAMIS CYBER SOLUTION
Investing in Ethereum (ETH) seemed like a promising opportunity, fueled by my skepticism toward fiat money and decades-long preference for alternative mediums like computers. Intrigued by cryptocurrency and its potential, I encountered an aggressively advertised second-generation bank trading app claiming monopolistic exclusivity and future rewards through its wallet. Their professional branding, assurances of regulation, and convincing logos made the offer seem legitimate.
I conducted due diligence—verifying the bank’s registration, legitimacy, and operational hours. However, scammers are often steps ahead of regulators. Sophisticated phishing campaigns and fraudulent websites mimicking legitimate entities made their scheme convincing. I sent BTC as an initial investment, only to realize it was a scam. The untraceable nature of cryptocurrency made recovery seem impossible. Bitcoin, often exploited by fraudsters, is two and a half times more likely to be used in investment-related scams than other payment methods.
Fortunately, I recovered a significant portion of my funds with the help of **Dunamis Cyber Solution Recovery**, restoring both my finances and my confidence. This experience taught me the importance of vigilance, thorough research, and seeking professional assistance when needed. I emerged smarter and more determined to avoid similar pitfalls in the future.
+134330305451 -
Best Cryptocurrency Recovery Company / CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER
As a Crypto enthusiast, I had invested a significant amount in various altcoins and tokens. One day, I woke up to find my wallet empty. Panic set in. I frantically checked my exchanges and wallets, hoping it was just a temporary glitch. Unfortunately, it was not. I had fallen victim to a phishing scam that compromised my wallet's security. In my quest for a reliable recovery service, I stumbled upon CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER. After extensive research, I discovered that they had a solid reputation in the crypto community. They had successfully helped countless individuals recover their lost funds, and their transparent approach immediately caught my attention. The CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER is a recovery service that specializes in helping individuals reclaim lost cryptocurrency assets. With a team of experienced professionals, they provide tailored solutions to victims of fraud and scams. After reading various reviews and success stories, I was encouraged to reach out. The team was incredibly empathetic and knowledgeable, understanding the emotional turmoil that accompanies such financial setbacks. They outlined a clear plan of action, and within 36 hours all my lost money had been recovered.
Visit website: ( Captainwebgenesis. com )1 -
How Cryptic Trace Technologies Recovered My Stolen Bitcoin
When I discovered that $580,990 worth of Bitcoin had vanished from my wallet due to a sophisticated phishing scam, I was devastated. The anonymity and complexity of blockchain transactions made the prospect of recovery seem impossible. Traditional avenues offered little hope, and I was warned that many so-called recovery services were scams themselves. In my search for a legitimate solution, I came across Cryptic Trace Technologies. From our first interaction, their professionalism and transparency stood out. They took the time to understand the specifics of my case and explained their recovery process in detail. Utilizing advanced blockchain forensics and ethical hacking techniques, they meticulously traced the movement of my stolen funds across multiple wallets and exchanges. Their expertise and dedication were evident as they navigated the complex digital trail left by the scammers. Remarkably, within a short period, Cryptic Trace Technologies successfully recovered the entirety of my stolen Bitcoin. Their commitment didn’t end there; they also provided guidance on securing my digital assets to prevent future incidents. Their integrity, technical proficiency, and genuine concern for their clients make them a standout in the field of cryptocurrency recovery. For anyone facing the nightmare of crypto theft, I wholeheartedly recommend Cryptic Trace Technologies as a reliable and effective ally in reclaiming what’s rightfully yours. For more info check their W E B S I T E: cryptictracetechnologies (.) com or E M A I L them: Cryptictrace (@) technologist (.) com.2 -
CAN I RECOVERY MONERY FROM SCAMMER? YES
How I recouped stolen crypto currency coins and tokens from scam hackers on telegram. People all over the world are hearing about the fast profits early investors are making on Bitcoin and other coins and want to join the party and make a fast profit. But be sure, where big money is, there are also companies that are abusing and taking advantage of this situation. Such was my situation, I had a fake telegram group admin contact me and gave me a phishing link in which my 12 recovery phrase was compromised. These evil persons gained access to my cryptowallet and stole all my coins and tokens worth over $ 640,000. I was in great despair due to this situation, I was confused till a group member on the telegram referred me to Cyberspacehackpro(@)rescueteam com This recovery agent is really God sent. After relating all of my predicaments, details of incidence and necessary requirements for my recovery program, it took them less than a week to track and recover all of my tokens and coins back, they helped me hack the perpetrators wallet and all of my coins were returned to me. I am so amazed, joyous and appreciative. I don't know what I would do without this specialist. They specialize in chargeback disputes and their team knows how to identify these types of scams. If you invested in Crypto and believe you have been scammed contact their experts today and they will help you recover your losses.
Contact info 1
1 -
How Hackers Gained Access to My Crypto Wallet and Sensitive Data through a Keylogger sent to my device through a phishing email.
I’ll advise others to be wary of the kind of emails they open, as this happened a few weeks ago when a phishing email was sent to my email unknowingly to me that it was a keylogger with the intent of stealing my private information and if not for the intervention of Morphohack Cyber Services, I would have been cleaned out completely. I contacted Morphohack Cyber Services a week after that incident and they detected the keylogger in my computer which has been there for months stealing my private information. If my crypto wallet was not drained, I would not have been aware of the keylogger in my device. Morphohack was able to secure my devices and retrieve my crypto wallet including the crypto assets. Their sophisticated security features and malware can beat any hacking tools available and they are very professional and ethical. Morphohack is a lifesaver and I hugely recommend their services. Their E-mail. Morphohack@Cyberservices. com & WhatsApp. +1 - 213 - 672 - 40921 -
About Me
As a dedicated and skilled Security Analyst in the Cyber Wing, I bring a wealth of expertise in identifying, assessing, and mitigating cyber threats to protect organizational assets and sensitive information. My background is grounded in a robust understanding of cybersecurity principles, which I apply daily to safeguard against evolving digital threats.
Professional Background
With a strong foundation in cybersecurity, I have honed my skills in threat analysis, risk assessment, and incident response. My role involves continuous monitoring of network traffic, identifying vulnerabilities, and implementing security measures to prevent data breaches. I am proficient in using advanced cybersecurity tools and technologies to analyze threat intelligence and develop strategies to defend against cyber-attacks.
Key Competencies
Threat Analysis: Expert in identifying and analyzing potential threats to cybersecurity, including malware, phishing attacks, and network intrusions.
Risk Assessment: Skilled in evaluating the security posture of systems and networks, identifying vulnerabilities, and recommending corrective actions.
Incident Response: Experienced in managing and responding to security incidents, ensuring quick resolution and minimizing impact on operations.
Security Protocols: Knowledgeable in implementing and maintaining security protocols and policies to ensure compliance with industry standards and regulations.
Achievements
Successfully mitigated multiple cyber threats, reducing potential impact on organizational operations.
Developed and implemented security policies that enhanced the overall security posture of the organization.
Conducted comprehensive security assessments that led to significant improvements in network security and data protection.
Professional Goals
My goal as a Security Analyst is to continue advancing my expertise in cybersecurity, staying abreast of the latest trends and technologies to effectively combat emerging threats. I am committed to contributing to a safer digital environment and ensuring the highest level of security for the organization.
Personal Attributes
I am a proactive and detail-oriented professional, known for my analytical thinking and problem-solving abilities. I thrive in dynamic environments and am passionate about leveraging my skills to protect against cyber threats.
Contact elctrohacker DOT COM
Feel free to reach out to me for any inquiries or to discuss how I can contribute to enhancing your organization's cybersecurity posture. -
Best Crypto Asset Recovery Services: Top Firms to Retrieve Lost Cryptocurrency Puran Crypto Recovery
The cryptocurrency revolution has brought unprecedented opportunities for decentralized financial transactions, but it has also introduced significant risks. The loss of digital assets can occur due to hacking, phishing, human error, or even scams. Fortunately, crypto recovery services have emerged to help individuals and businesses regain access to their lost funds.1 -
EXPERT IN RECOVERING LOST CRYPTO ASSETS | CRYPTOCHAIN GLOBAL TRACK
When digital assets vanish due to sophisticated scams or theft, professional intervention becomes critical for recovery. CryptoChain Global Track delivers expert cryptocurrency recovery services through certified blockchain forensic specialists who combine technical expertise with legal strategies to trace and reclaim stolen funds.
The recovery process begins with comprehensive blockchain analysis, where investigators examine transaction histories across multiple wallets and exchanges. Using institutional-grade tracking technology, they follow the digital trail of stolen Bitcoin, Ethereum, USDT and other cryptocurrencies, identifying patterns that reveal fund movement. Their methodology proves particularly effective against investment scams, exchange hacks, and phishing attacks where assets have been moved through complex networks.
What sets CryptoChain Global Track apart is their multi-phase recovery approach. After identifying recoverable funds, their team initiates formal procedures through proper legal channels when assets are located on regulated exchanges. This dual technical and legal strategy has successfully recovered millions in digital assets for clients worldwide.
Clients benefit from transparent engagement terms including a "no recovery, no fee" policy that eliminates financial risk. The team maintains strict confidentiality while providing regular case updates, ensuring clients remain informed throughout the process. Their specialists emphasize rapid response, as recovery success rates decline significantly when scammers move funds through mixing services or cross-chain bridges.
The company has particular expertise in tracing assets involved in DeFi exploits, fraudulent ICOs, and fake investment platforms. Their forensic capabilities extend to following funds across multiple blockchains, including Ethereum, Binance Smart Chain, and Polygon networks.
For professional assessment of crypto recovery possibilities, CryptoChain Global Track offers complimentary case evaluations. Their experts provide realistic recovery estimates and recommended actions before formal engagement.
With CryptoChain Global Track, victims of cryptocurrency theft gain access to professional-grade recovery services that combine cutting-edge blockchain forensics with proven asset recovery strategies. Their expert team delivers legitimate solutions for reclaiming stolen digital assets.4 -
PROFESSIONAL CRYPTO SCAM RECOVERY SERVICES-AUTOPSY MAINNET RECOVERY
I’m still in disbelief, but overwhelmingly grateful—AUTOPSY MAINNET RECOVERY saved me from what I thought was an irreversible loss.
A few months ago, I fell victim to a sophisticated phishing scam that drained nearly all my cryptocurrency savings. It wasn’t just money—it was my future, my security, and years of hard work. I couldn’t sleep. I couldn’t focus. I kept replaying every step in my mind, wondering how I could have been so careful for years, only to lose everything in one moment of vulnerability.
I reported the theft, but most people told me it was gone forever. The blockchain is immutable, they said. There’s no way to trace or recover crypto once it’s been moved. I felt hopeless... until I came across AUTOPSY MAINNET RECOVERY.
At first, I was skeptical—who wouldn’t be after such a betrayal? But something about the way they communicated gave me hope. They were transparent, professional, and deeply knowledgeable. They explained every step of their recovery process and made no false promises. I decided to trust them. That was the best decision I could have made.
Within just days, they had traced the stolen funds through a complex web of transactions. Their expertise in blockchain forensics was mind-blowing. And then, what I thought was impossible happened—they successfully recovered my crypto.
I broke down in tears. Not just because of the money, but because someone actually cared enough to help me when I had already given up. Thanks to AUTOPSY MAINNET RECOVERY, I have my future back. I’ll never forget what they did for me.
If you’ve lost crypto and feel like all hope is gone—don’t give up. AUTOPSY MAINNET RECOVERY is the real deal. They didn’t just recover my assets—they restored my faith. you can also benefit from their services
EMAIL: [ Autopsymainnetrecovery@autopsy.co.site ]2 -
TRUSTED CRYPTO RECOVERY EXPERT; INSIGHTS FROM BITCOIN RECOVERY EXPERT HIRE CRYPTOCHAIN GLOBAL TRACK
CRYPTOCHAIN GLOBAL TRACK has emerged as the most trusted name in digital asset recovery. As cryptocurrency becomes more mainstream this year, with cyber threats growing more sophisticated, CRYPTOCHAIN GLOBAL TRACK stands as the ultimate solution for investors who have lost access to their Bitcoin, Ethereum, or other cryptocurrencies. The experts at CRYPTOCHAIN GLOBAL TRACK combine cutting-edge blockchain forensics with unparalleled investigative techniques to recover what others cannot. What sets CRYPTOCHAIN GLOBAL TRACK apart is its proven track record of success. Whether funds were stolen through phishing scams, exchange hacks, or compromised wallets, CRYPTOCHAIN GLOBAL TRACK employs deep-chain analysis tools to track and retrieve lost assets. The team at CRYPTOCHAIN GLOBAL TRACK understands the urgency of these situations, which is why they prioritize rapid response and transparent communication throughout the entire recovery process. Clients who trust CRYPTOCHAIN GLOBAL TRACK benefit from a personalized recovery strategy, ensuring the highest chance of success. Unlike generic recovery services, CRYPTOCHAIN GLOBAL TRACK treats each case with meticulous attention, leveraging its extensive network and proprietary technology to maximize results. In 2025, has successfully reclaimed millions in lost cryptocurrency, reinforcing its reputation as the number one choice for investors worldwide. The demand for CERTIFIED RECOVERY SERVICES’S services has skyrocketed this year, thanks to its unmatched success rate and commitment to client satisfaction. From individual traders to institutional investors, CRYPTOCHAIN GLOBAL TRACK has become synonymous with reliability and efficiency in the crypto recovery space. For anyone facing the challenge of lost or stolen digital assets, CRYPTOCHAIN GLOBAL TRACK remains the only name you need to know. With its 2025 breakthroughs in blockchain investigation and asset recovery, CRYPTOCHAIN GLOBAL TRACK continues to set the industry standard, turning loss into triumph for clients across the globe. Trust CRYPTOCHAIN GLOBAL TRACK because when crypto goes missing, they’re the experts who bring it back.
Here's Their Info Below:1 -
Best Crypto Recovery Specialists: How to Recover Stolen Cryptocurrency – Visit CryptoChain Global Track
Professional cryptocurrency recovery services have become essential in today's digital asset landscape. CryptoChain Global Track stands as a leading solution for victims of crypto theft, offering expert recovery services through certified blockchain forensic specialists with a demonstrated track record of successful fund retrieval.
CryptoChain Global Track's recovery methodology begins with comprehensive blockchain forensic analysis. Their team of licensed investigators examines transaction histories across multiple wallets and exchanges, utilizing advanced tracking technology to follow the digital trail of stolen Bitcoin, Ethereum, and other major cryptocurrencies. This technical approach identifies critical recovery points that untrained individuals typically miss, combining forensic tracing with legal strategies when recoverable funds are located on regulated platforms.
The company's transparent operations include a performance-based fee structure, ensuring clients only pay upon successful recovery. Their specialists maintain strict confidentiality protocols while providing regular case updates, keeping clients informed throughout the investigation process. The team prioritizes rapid response to new cases, understanding that timely intervention significantly increases recovery success rates before scammers can obscure the funds' trail through mixing services or cross-chain transfers.
CryptoChain Global Track's experts specialize in complex recovery scenarios, including investment frauds, exchange hacks, phishing attacks, and DeFi exploits. Their deep understanding of blockchain transaction patterns and scam behaviors enables them to develop effective counter-strategies for fund retrieval. The company's professional certifications and ethical standards provide assurance in an industry where questionable operators frequently emerge.
For those seeking professional cryptocurrency recovery assistance, CryptoChain Global Track offers complimentary initial consultations. Their experts provide realistic assessments of recovery potential and explain the investigative process in clear, understandable terms.
With CryptoChain Global Track, victims of cryptocurrency theft gain access to premier recovery services that combine technical expertise with professional investigative methods. Their certified team delivers legitimate solutions for reclaiming stolen digital assets in today's complex crypto environment.5 -
**BITCOIN RECOVERY EXPERTS REVIEW → HACKATHON TECH SOLUTIONS**
Bitcoin continues to grow in popularity in 2025, the need for effective recovery services has become more crucial than ever, especially for victims of scams. HACKATHON TECH SOLUTIONS stands out as a leading provider, specializing in recovering Bitcoin and other digital assets taken by scammers. The complexities of Bitcoin and its decentralized nature create unique challenges in these cases, but HACKATHON TECH SOLUTIONS is equipped with the expertise to navigate these obstacles and help clients reclaim their funds.Scammers often target Bitcoin users through fraudulent schemes, such as phishing attacks, fake investment opportunities, and fraudulent exchanges. When victims fall prey to these scams and lose their Bitcoin, HACKATHON TECH SOLUTIONS offers a reliable solution. The company uses advanced techniques to trace and recover funds, leveraging its deep understanding of blockchain technology to track stolen assets. Despite Bitcoin’s pseudonymous nature, HACKATHON TECH SOLUTIONS skilled team is able to tackle these challenges effectively, giving scam victims hope of recovering their stolen assets.Security is a primary concern, especially when dealing with sensitive information. HACKATHON TECH SOLUTIONS ensures that all client data remains confidential and secure throughout the recovery process. They implement stringent security measures, offering peace of mind to those seeking help. With a focus on professionalism and client care, HACKATHON TECH SOLUTIONS handles each case with the utmost respect and discretion.The irreversible nature of Bitcoin transactions makes recovery particularly challenging for scam victims, highlighting the importance of a trusted recovery service. HACKATHON TECH SOLUTIONS understands the emotional toll of being scammed and works diligently to provide a smooth, reassuring recovery experience. As the cryptocurrency space continues to evolve, the demand for reliable recovery services like those offered by HACKATHON TECH SOLUTIONS will only grow, solidifying their position as a leader in the industry. You can contact them using the details provided below.
Whatsapp: → +3, 1, 6, 4, 7, 9, 9, 9, 2, 5, 6
Telegram: → @ hackathon tech solutions
Email: → hackathontechservice@mail(.)com2 -
I am still in awe of the exceptional service I received from Tech Cyber Force Recovery, a renowned team of experts specializing in recovering lost Bitcoin and USDT. Like many others, I was a victim of a phishing scam that left me with a devastating loss of 3.5 BTC and 10,000 USD. The thought of never being able to recover my hard-earned investments was overwhelming, and I had almost given up hope.
That was when I stumbled upon Tech Cyber Force Recovery while searching for a solution online. I must admit, I was skeptical at first, but the numerous positive reviews and testimonials from satisfied clients convinced me to take a chance.
I contacted their team, and their professionalism and expertise shone through from the initial consultation to the final recovery. The Tech Cyber Force Recovery team guided me through a series of steps, explaining each process in detail and keeping me updated on their progress. Their dedication and perseverance were impressive, and it was evident that they had a deep understanding of the complexities involved in crypto recovery.
Within two weeks, Tech Cyber Force Recovery successfully recovered 95% of my lost Bitcoin and USDT. I was overjoyed and relieved to have my investments back, and I couldn't thank them enough for their exceptional service. What sets Tech Cyber Force Recovery apart is its commitment to delivering results and its willingness to go the extra mile.
They are not just a team of experts but a beacon of hope for those who have lost their cryptocurrency investments. If you're a victim of a similar scam or have lost your cryptocurrency due to any other reason, I highly recommend reaching out to Tech Cyber Force Recovery. They will work tirelessly to recover your lost assets and restore your faith in the crypto community. In conclusion, I would like to express my gratitude to Tech Cyber Force Recovery for their outstanding service.
TEXT OR CALL + (156)(172)(636)97
EMAIL contact(@)techcyberforcerecovery(.)info
WEBSITE https(://)techcyberforcerecovery(.)info -
BLOCKCHAIN CYBER RETRIEVE//RECOVER LOST BTC FUNDS FROM TRADING PLATFORM
Maintaining a high level of alertness is crucial when trading Bitcoin due to its market volatility and unpredictable price movements. Unfortunately, I learned this lesson the hard way after losing $125,000 in a single trading session. It began as an ordinary day; I was confident and focused on my strategy. However, the market quickly took a downturn, and my account balance dropped dramatically in a few hours. I was left in shock and overwhelmed, unable to process the situation. The financial loss was devastating, but the emotional toll was equally intense, leaving me wondering if I could ever recover those funds. In my panic, I reached out to a close friend who had introduced me to Bitcoin trading. She suggested contacting a service called BLOCKCHAIN CYBER RETRIEVE, which she claimed specialized in helping people recover lost funds, particularly from cryptocurrency trades. Following her advice, I reached out to them immediately. Their response was quick, and they began the recovery process almost right away, The team was both professional and empathetic, clearly explaining the steps involved and reassuring me that they would do their best to recover my $125,000. True to their word, BLOCKCHAIN CYBER RETRIEVE worked tirelessly on my behalf, and I was able to recover the full amount within a short period. The relief I felt was immense, and I was incredibly grateful for their efficiency. Additionally, they provided essential advice on how to protect my account from future risks, including enabling two-factor authentication (2FA), using a secure password manager, and avoiding phishing scams. These tips have been invaluable, and I now approach Bitcoin trading with much more caution and preparation. If you’ve experienced similar losses, I highly recommend reaching out to BLOCKCHAIN CYBER RETRIEVE for help. Their professional support can truly make a difference in recovering funds and safeguarding your future investments.
CONTACT INFORMATION:
WhatsApp: + 1 5 2 0 564 8300
Email: blockchaincyberretrieve (@) post . com1 -
I’ve always felt confident navigating the world of cryptocurrency. As a software engineer, I understood the ins and outs of wallets, private keys, and blockchain security, which made me feel secure in my investments. So, when I found a promising platform that seemed like a great opportunity, I invested $250,000 without hesitation. Unfortunately, I soon learned that my confidence would be shattered by a sophisticated cyber attack. It started with small, unauthorized transactions in my wallet. At first, I thought it was a mistake, but as the activity continued, I realized something was wrong. My wallet had been compromised, but not in the way I had expected. Instead of a simple hack, I had fallen victim to a virus attack. The virus was a piece of malware designed specifically to target cryptocurrency wallets. It infiltrated my system through a vulnerability I hadn’t noticed. Once inside, the virus silently monitored my wallet, captured my private keys, and gave the hackers full access to my funds. It was stealthy and nearly undetectable. The attackers didn’t need to log into my account manually; they could control everything remotely, draining my wallet without my knowledge. I was completely blindsided. As someone familiar with tech, I knew how advanced this virus was. It wasn’t just a typical phishing attack, it was a targeted, silent assault on my financial assets. As my funds disappeared, I realized I might never be able to recover them. Desperate, I turned to a trusted colleague who had gone through a similar situation. They recommended Hack Buster Recovery, a company that specializes in recovering stolen crypto assets.
 1
1 -
(E MAIL:TRUSTGEEKSHACKEXPERT @ FASTSERVICE . COM )
( TELE GRAM ID: TRUST GEEKS HACK EXPERT)
As an Italian investor, I approached my cryptocurrency investments with the precision and caution our culture is known for, gradually building a retirement portfolio of €75,000 in Bitcoin over the years. Unfortunately, even the most meticulous plans can be undermined by sophisticated scams. One day, I received a phishing email that looked identical to communications from my wallet provider. Believing it to be genuine, I entered my login details, only to realize moments later that my account had been completely drained. The loss was devastating; all my careful planning seemed to vanish in an instant, leaving me with immense disappointment— not just for myself but also for my family, who had supported me throughout this journey. In my desperation, I sought advice from a colleague in the cryptocurrency industry. He recommended (TRUST GEEKS HACK EXPERT), expressing confidence in their specialized expertise in fund recovery. Though initially skeptical, I felt I had no choice but to reach out. I contacted(TRUST GEEKS HACK EXPERT), and their team was remarkably professional and empathetic. They acted swiftly, employing advanced blockchain technology and investigative techniques to track the fraudulent transactions. Their expertise inspired renewed hope, and it was reassuring to have such knowledgeable support in my recovery efforts. The waiting period was tense, but they kept me informed every step of the way. After several nerve-wracking days, I received the call I had been hoping for: my funds had been successfully recovered. The relief was indescribable— (TRUST GEEKS HACK EXPERT) had not only restored my retirement plan but also renewed my trust in the cryptocurrency industry. For anyone facing a similar situation, reach out to (TRUST GEEKS HACK EXPERT), Their dedication can truly make a difference in recovering what you thought was lost.
(W H A T S A P P +1 7 1 9 4 9 2 2 6 9 3 ) -
HOW TO RECOVER STOLEN BITCOIN & CRYPTO / BOTNET CRYPTO RECOVERY
BOTNET CRYPTO RECOVERY has emerged as the most trusted name in digital asset recovery. As cryptocurrency becomes more mainstream this year, with cyber threats growing more sophisticated, BOTNET CRYPTO RECOVERY stands as the ultimate solution for investors who have lost access to their Bitcoin, Ethereum, or other cryptocurrencies The experts at BOTNET CRYPTO RECOVERY combine cutting-edge blockchain forensics with unparalleled investigative techniques to recover what others cannot.What sets BOTNET CRYPTO RECOVERY apart is its proven track record of success. Whether funds were stolen through phishing scams, exchange hacks, or compromised wallets, BOTNET CRYPTO RECOVERY employs deep-chain analysis tools to track and retrieve lost assets. The team at BOTNET CRYPTO RECOVERY understands the urgency of these situations, which is why they prioritize rapid response and transparent communication throughout the entire recovery process.Clients who trust BOTNET CRYPTO RECOVERY benefit from a personalized recovery strategy, ensuring the highest chance of success. Unlike generic recovery services, BOTNET CRYPTO RECOVERY treats each case with meticulous attention, leveraging its extensive network and proprietary technology to maximize results. In 2025, BOTNET CRYPTO RECOVERY has successfully reclaimed millions in lost cryptocurrency, reinforcing its reputation as the number one choice for investors worldwide.The demand forBOTNET CRYPTO RECOVERY services has skyrocketed this year, thanks to its unmatched success rate and commitment to client satisfaction. From individual traders to institutional investors, BOTNET CRYPTO RECOVERY has become synonymous with reliability and efficiency in the crypto recovery space.For anyone facing the challenge of lost or stolen digital assets, BOTNET CRYPTO RECOVERY remains the only name you need to know. With its 2025 breakthroughs in blockchain investigation and asset recovery, BOTNET CRYPTO RECOVERY continues to set the industry standard, turning loss into triumph for clients across the globe. Trust BOTNET CRYPTO RECOVERY because when crypto goes missing, they’re the experts who bring it back.2 -
How Can i Recovery My Stolen Ethereum Back From Fake Companies
It started with what I thought was a golden opportunity. I’d been dabbling in crypto for a couple of years, mostly small trades and safe investments. But in late March, I stumbled upon a flashy new Defib project promising astronomical returns. Against my better judgment, I transferred $320,100 worth of Ethereum to what turned out to be a sophisticated phishing site. The wallet drained instantly. Panic hit like a wave. I reported the scam, contacted my exchange, and spent days researching recovery options for all dead ends. That amount wasn’t just numbers on a screen. It was years of savings, hard work, and hope. That’s when I came across iCode CYBER TECH. I was skeptical, naturally too many fake crypto recovery experts were out there just preying on the desperate. But iCode CYBER TECH had solid reviews, a verified presence, and even testimonials from others who’d been in my shoes Cautiously, I reached out From the very first call, they treated me like more than a victim. They listened, asked the right questions, and got to work immediately. Within hours, their team traced the movement of my stolen Ethereum across multiple wallets using advanced blockchain analytics tools. They found patterns, linked addresses to known laundering networks, and coordinated with compliance teams across two exchanges where part of the funds had landed. With court orders and compliance cooperation, iCode CYBER TECH was able to freeze the stolen assets before they were fully laundered. Of the $320,100 lost, they recovered $291,800 a staggering result I didn’t think was even possible. If you ever find yourself in a nightmare like mine, don’t give up. iCode CYBER TECH isn’t just a company, they're digital lifesavers.
WhatsApp...+4475637432582 -
HOW TO FIND A PROFESSIONAL BITCOIN RECOVERY EXPERT IN 2025 HIRE ADWARE RECOVERY SPECIALIST
The cryptocurrency space is rife with risks, particularly when it comes to Bitcoin, which has become a prime target for scammers. As digital currencies gain mainstream attention, incidents of fraud, hacking, and deceptive schemes have surged—resulting in significant losses for both individuals and businesses.
In this high-risk environment, the need for reliable recovery solutions has never been more urgent. ADWARE RECOVERY SPECIALIST has established itself as a trusted leader in the field of cryptocurrency recovery, with a focus on assisting clients in retrieving Bitcoin lost to scams. Leveraging advanced tools and investigative techniques, the firm has built a solid reputation for successfully tracing and recovering stolen digital assets. WhatsApp info:+12 (72332)—8343
The team at ADWARE RECOVERY SPECIALIST is highly skilled in navigating the complex landscape of crypto-related fraud—from phishing attacks and Ponzi schemes to exchange hacks and wallet breaches. Their deep understanding of the intricacies involved allows them to provide expert guidance and tailored recovery strategies.
What sets ADWARE RECOVERY SPECIALIST apart is not only their technical expertise, but also their client-focused approach. They offer professional support throughout every stage of the recovery process, marked by clear communication, transparency, and empathy. Recognizing the emotional and financial distress that victims of crypto scams face, the firm offers a dependable lifeline to those in need. Email info: Adware recovery specialist @ auctioneer. net
The company’s dedication to excellence is reflected in the many accolades received from clients and industry peers alike, affirming its effectiveness and reliability. Through ongoing investment in training, research, and innovation, ADWARE RECOVERY SPECIALIST stays ahead of evolving cyber threats, ensuring its team remains equipped to meet the demands of an ever-changing digital landscape.2 -
BITCOIN FRAUD-RECOVER STOLEN ASSETS HIRE TECHNOCRATE RECOVERY
I decided to explore the world of cryptocurrency, intrigued by the possibilities it offered. With every hard-earned dollar I saved, I ventured into Bitcoin, investing a substantial amount that eventually totaled $370,000. I was excited about the prospect of growing my savings and ensuring my children would have a stable future. But, as fate would have it, disaster struck when I lost access to my Bitcoin wallet. It happened in a flash. I was multitasking—baking, icing cupcakes, and managing customer orders—when I accidentally clicked on a phishing link disguised as an update for my cryptocurrency app. In an instant, my wallet was compromised, and I was locked out. The realization hit me hard: my investment, my dreams, and my family’s future were hanging by a thread. Feeling utterly devastated and betrayed by my own oversight, I knew I had to act fast. I shared my predicament with a close friend who had been through a similar experience, and they recommended TECHNOCRATE RECOVERY. Skeptical but desperate, I reached out to their team. From the moment I contacted them, I felt an overwhelming sense of support. The professionals at TECHNOCRATE RECOVERY Tool were compassionate and knowledgeable, assuring me that they could help me navigate this overwhelming situation. Their team sprang into action, utilizing advanced technology to track the transactions that led to my locked assets. Within days, they uncovered critical information that would lead to the recovery of my funds. Finally, after what felt like an eternity, I received the news I had been praying for: my Bitcoin had been successfully recovered. Thanks to their incredible work, I can continue focusing on my bakery and my family, knowing I have the tools to navigate the digital world securely.
CONTACT BELOW INFO FOR HELP.
Inbox Email: t echnocratrecovery@contractor. net -
I was in a state of utter despair when I realized that I had fallen victim to a sophisticated phishing scam, losing a substantial amount of my hard-earned cryptocurrency in the process. The scammers were so cunning and professional that I thought I had lost everything forever. But then I stumbled upon Cranix Ethical Solutions Haven, a team of ethical hackers and cybercrime experts who specialize in recovering stolen digital assets. Their expertise and professionalism were evident from the moment I reached out to them. They walked me through the entire process, explaining each step in detail and keeping me informed every step of the way. Their team of experts worked tirelessly to track down the scammers, using their advanced techniques and cutting-edge technology to trace the stolen bitcoin. What impressed me most about Cranix Ethical Solutions Haven was their unwavering commitment to justice. They didn't just stop at recovering my stolen bitcoin; they also worked with law enforcement agencies to bring the scammers to book. Their tireless efforts ultimately led to the arrest and prosecution of the perpetrators, sending a strong message to other would-be scammers.
I am forever grateful to Cranix Ethical Solutions Haven for their outstanding work. Without their help, I would have lost everything. Their dedication to fighting cybercrime and protecting innocent victims like me is truly commendable. I highly recommend their services to anyone who has fallen victim to cryptocurrency scams or other forms of cybercrime. They are the best in the business, and I am confident that they will continue to make a positive impact in the fight against cybercrime.
EMAIL: (cranixethicalsolutionshaven @ post . com) OR (info @ cranixethicalsolutionshaven . info)
WHATSAPP: (+ 4 4 7 4 6 0 6 2 2 7 3 0)
WEBSITE: (https : //cranixethicalsolutionshaven . info)
TELEGRAM: (@ cranixethicalsolutionshaven)1 -
it's easier to minimize interactions or use of emails to avoid phishing than deal with sorting it out especially since most companies do in house fake phishing for training :)5
-
Is CBEX a scam? That was going through my mind for weeks when I mistakenly registered in a fake crypto exchange platform CBEX.sx pretending to be the original CBEX, I had already deposited more than a million dollars into my trading account when I realized it was the wrong website. I contacted the original website support but they couldn’t help me. I was deeply disturbed and devastated by this incident. It turned out they had cloned the website of CBEX, unfortunately this means my money is gone. I was scrolling the internet looking for ways to recover lost crypto funds when I came across Morphohack Cyber Service, a crypto recovery company. Morphohack was able to detect that it was a cloned phishing site used to deceive victims and steal crypto funds. I was shocked when Morphohack Cyber told me my funds could be recovered with their sophisticated malware and tools. I provided every information required for the transaction and wallet, and that was how Morphohack was able to recover my crypto funds without any hiccups. I was stunned by how quickly it took, Morphohack is simply the best.
(morphohack@cyberservices. com)
WhatsApp(+1 2 1 3 6 7 2 4 0 9 2)1 -
Recently, I encountered a harrowing experience involving a fraudulent crypto asset brokerage. I had been saving a substantial amount of Bitcoin, totaling 1.5 BTC, with plans to invest through a reputable brokerage firm. My research led me to a search result on Google that seemed promising, featuring a top-ranked sponsored link to a website with the address Mantao network. Upon visiting this site, which appeared to be professional and convincing, I was prompted to connect my crypto wallet. Naively trusting the site’s appearance and its purported legitimacy, I approved the connection request. Almost immediately, I noticed that my Bitcoin balance had been drained; within seconds, my entire 1.5 BTC was gone. In a state of panic, I quickly checked my wallet via my mobile app and confirmed that my balance was indeed zero. Desperate for help, I reached out to a workmate who is well-versed in cryptocurrency. Although my workmate initially took my concerns lightly, suggesting that there was nothing to worry about, he later referred me to a specialist who could potentially assist with such situations. This specialist was affiliated with a group called Tech Cyber Force Recovery. I reached out to them, providing detailed information about the incident and attaching the malicious sponsored link that had led to the phishing attack. Tech Cyber Force Recovery promptly reviewed the link and identified it as part of a scam operation masquerading as the legitimate Manta Network—a genuine and reputable platform in the crypto world. The team at Tech Cyber Force Recovery acted swiftly. They utilized their expertise in dealing with phishing and scam-related issues to initiate a recovery process. Thanks to their sophisticated tools and techniques, they managed to reverse the transactions and recover my stolen Bitcoin. Throughout this ordeal, Tech Cyber Force Recovery demonstrated exceptional professionalism and expertise. They kept me updated on their progress and reassured me during the stressful period. Their successful intervention not only restored my 1.5 BTC but also provided a valuable lesson in the importance of verifying the legitimacy of crypto-related websites and transactions. This experience underscored the significance of vigilance and caution in the crypto world. While the recovery of my funds was a fortunate outcome, it serves as a reminder to always double-check the authenticity of any platform or link before engaging with it, especially in the cryptocurrency space.
Email. contact@techcyberforcerecovery.info
WhatsApp +1 561 726 36 97
Website. ht tps : / / tech cyber force recovery.info -
HIRE THE BEST CRYPTO / BITCOIN RECOVERY / SERVICES - Consult iFORCE HACKER RECOVERY
iForce Hacker Recovery is a specialized service dedicated to helping individuals recover lost cryptocurrency. They utilize advanced techniques and a team of expert blockchain analysts to trace stolen funds and assist victims in reclaiming their assets. After losing a significant amount in a phishing scam, I turned to iForce, and it was one of the best decisions I made.
Website info; ww w. iforcehackersrecovery. com
Email; contact@ iforcehackersrecovery. co m
Whatsapp +1 (240) 803. (3706)1 -
Top Bitcoin/Cryptocurrency Recovery Service: iBOLT CYBER HACKER Service
iBOLT CYBER HACKER has successfully assisted individuals and businesses in recovering lost Bitcoin and other cryptocurrencies from scams, phishing attacks, and fraudulent platforms. Their team utilizes cutting-edge blockchain tracing tools and cybersecurity techniques to track transactions and recover funds efficiently. Unlike many unreliable recovery services, iBOLT CYBER HACKER operates with integrity, ensuring compliance with legal frameworks and strict confidentiality.
With 24/7 support, their team provides timely assistance, ensuring that victims of crypto fraud receive prompt help in tracing and reclaiming their assets. Whether it’s lost private keys, hacked wallets, or fraudulent withdrawals, iBOLT CYBER HACKER offers tailored recovery solutions based on each client's needs.
ENQUIRING:
Contact: +39, 351..105, 3619
Mail: Support @ibolt cybarhack. com
Homepage: http s:// ibolt cybarhack. com 6
6 -
TOP BTC RECOVERY EXPERT- WEB BAILIFF CONTRACTOR
Decades of hard work savings went to waste in minutes when I lost 7.1 BTC due to a phishing scam. It was like being in a dream where I had clicked on a mock email that closely resembled my crypto exchange, inadvertently sharing my wallet information. Panic set in, and I felt shame and remorse. I immediately reported the theft to the authorities, but they explained the harsh reality: Bitcoin transactions are irreversible and hence recovery is practically impossible. Desperate as I was to discover a solution, I turned to Web Bailiff Contractor for Bitcoin and cryptocurrency scam recovery. What impressed me most was that they were committed to transparency. They clearly established the recovery chances up-front, emphasizing that while success was not guaranteed, they would work tirelessly on my account. In a span of just three days, their relentless team meticulously dismantled the phishing framework. They traced my stolen BTC through a complex network of multi-layered wallets and mixers, working in liaison with global exchanges and legal teams to freeze the stolen funds. During the process, I received regular updates, which balanced my hope with a realistic understanding of the situation. Miraculously, they were able to recover all 7.1 BTC, a phenomenal accomplishment given the sophistication of the scam. Their contingency-based fee arrangement and moral way of operating, involving no upfront fees, made the result even more gratifying. The advantages of Web Bailiff Contractor are their technical competence, global network, and strong commitment to not exploit victims' desperation. This restored my faith in recovery operations. This did not only make me more cautious on the internet but also opened my eyes to the value of professional, ethical recovery services. Although the cryptocurrency universe is full of risks, knowing that there are dependable experts to be had is a positive indicator for the future.2 -
DIGITAL TECH GUARD RECOVERY - THE BEST EXPERTS FOR BITCOIN AND CRYPTO
Years of hard-earned savings vanished in mere minutes when I lost 7.1 BTC to a phishing scam. It felt like a nightmare as I clicked on a fraudulent email that closely mimicked my crypto exchange, unknowingly surrendering my wallet credentials. Panic set in, and I was overwhelmed with shame and regret. I immediately reported the theft to the authorities, but they emphasized the grim reality: Bitcoin transactions are irreversible making recovery nearly impossible. Desperate for a solution, I turned to Digital Tech Guard Recovery, known for Bitcoin and cryptocurrency scam recovery. What impressed me most was their commitment to transparency. They clearly outlined the odds of recovery upfront, emphasizing that while success was not guaranteed, they would exert relentless effort on my behalf. To my astonishment, within just three days, their dedicated team meticulously dissected the phishing infrastructure. They traced my stolen BTC through a complex web of layered wallets and mixers, collaborating with global exchanges and legal teams to freeze the stolen funds. Throughout the process, I received regular updates, which helped balance my hope with a realistic understanding of the situation. Miraculously, they managed to recover all 7.1 BTC, an incredible achievement considering the sophistication of the scam. Their contingency-based fee structure and ethical approach, requiring no upfront costs, made the outcome even more rewarding. Digital Tech Guard Recovery’s strengths lie in their technical precision, extensive global network, and a steadfast refusal to exploit victims’ desperation. This restored my faith in recovery efforts. This has not only taught me to be more cautious online but also showed me the value of professional, ethical recovery services. While the world of cryptocurrency is full of risks, knowing that there are trustworthy experts out there gives me hope for the future.
WhatsApp: +1 (443) 859 - 2886 Email @ digital tech guard . com
Telegram: digital tech guard . com Website link: digital tech guard . com2 -
HOW TO RECOVER LOST CRYPTOCURRENCY - VISIT iBOLT CYBER HACKER COMPANY
⭐⭐⭐⭐⭐ (5/5)
I never thought I’d see my scammed bitcoin again. A few months ago, I fell for a phishing scam. I tried everything, contacted exchange, reached out on forums, even reported it to authorities— but got nowhere. That’s when I came across iBOLT Cyber Hacker Company, and I’m so glad I did. they traced the transactions path using blockchain forensics. i won't say much, iBolt Cyber Hacker Company saved me... click the links and find out for yourself.
If you’ve lost crypto due to scams, forgotten passwords, or exchange issues, I highly recommend visiting iBOLT Cyber Hacker Company. They saved me from a total loss.
CLICK LINKS....
Email: info @ iboltcyberhack . org/
Phone: https: //wa. me/+393511053619
Telegram: t. me/iboltcyberhackservice
Website: htt ps:// iboltcyberhack . org/ 2
2 -
HACKER FOR HIRE: iBOLT CYBER HACKER - CRYPTOCURRENCY RECOVERY COMPANY
I highly recommend iBOLT Cyber Hacker for anyone seeking expert assistance in recovering lost or stolen cryptocurrency, I recently engaged iBOLT Cyber Hacker after falling victim to a cryptocurrency scam, their team demonstrated deep knowledge of blockchain forensics, wallet tracing, and transaction monitoring. They handled my case with a high degree of transparency and integrity, clearly explaining each step of the process and setting realistic expectations.
If you've been affected by a crypto scam, phishing attack, or wallet breach, iBOLT Cyber Hacker offers a legitimate path to potential recovery. While no company can guarantee 100% success in every case, iBOLT delivers results with professionalism, discretion, and a client-first mindset.
info @ iboltcyberhack . org/
www . iboltcybarhacker . com/
+.39.. 351. .105. .3619.
I strongly recommend their services to anyone in need of cryptocurrency recovery support.5 -
I lost access to my Bitcoin trading accounts due to a phishing email mishap, resulting in a loss of $95,500 worth of Bitcoin. I turned to Wizard James Recovery for assistance after reading so many positive reviews online about their achievement, which within two hours successfully tracked down the perpetrators and ethically recovered my account with the Bitcoin intact. Wizard James Recovery's unparalleled tracking capabilities and ethical approach set it apart from other tools on the market. The platform's seamless integration with cryptocurrency exchanges and commitment to ethical practices allowed them to take decisive action against the culprits. Wizard James Recovery's swift and ethical recovery process served as a beacon of hope in a sea of uncertainty, proving that with the right tools and determination, anything is possible. Reach out to Wizard James Recovery via: Whatsapp: + 4 4 7418 367204
Email:wizardjamesrecovery @ usa . com1 -
CRYPTO SCAM RECOVERY SUCCESSFUL – A TESTIMONIAL OF LOST PASSWORD TO YOUR DIGITAL WALLET BACK.
My name is Robert Alfred, Am from Australia. I’m sharing my experience in the hope that it helps others who have been victims of crypto scams. A few months ago, I fell victim to a fraudulent crypto investment scheme linked to a broker company. I had invested heavily during a time when Bitcoin prices were rising, thinking it was a good opportunity. Unfortunately, I was scammed out of $120,000 AUD and the broker denied me access to my digital wallet and assets. It was a devastating experience that caused many sleepless nights. Crypto scams are increasingly common and often involve fake trading platforms, phishing attacks, I highly recommend them with full confidence Email Recovercapital @cyberservices. com2 -
As cryptocurrency continues to grow, so do the risks. Scammers are becoming more sophisticated, leaving many victims unsure of where to turn after losing their hard-earned digital assets.
Apex Intervention specializes in crypto recovery services, helping individuals trace, track, and reclaim lost or stolen cryptocurrency. Our experts understand the complexities of blockchain technology and how online fraudsters operate.
Whether you’ve been misled by fake investment platforms or fallen victim to a phishing scam, we’re here to help you fight back.
Why Choose Apex Intervention?
Proven track record of successful recoveries
In-depth knowledge of crypto scams and blockchain systems
Personalized support every step of the way
Get in Touch Today:
Email: info@apex-intervention.online
WhatsApp: +1 (365) 740-5227
Website:apex-intervention.online
Take action now. Don’t let scammers walk away with your crypto.1 -
Recovery Tech Solutions is a reputable company known for their expertise in recovering lost or stolen cryptocurrency. Our team of expert hackers and blockchain specialists have the skills and experience necessary to retrieve lost or stolen cryptocurrencies. We use advanced techniques and cutting-edge technology to track down and recover your lost funds, ensuring that you can regain access to your assets quickly and securely.
Whether you have lost your private keys, been the victim of a phishing scam, or experienced any other type of cryptocurrency theft, Recovery Tech Solution is here to help. Contact us today to learn more about our services and how we can assist you in recovering your lost bitcoins or other cryptocurrencies. Reach out to RECOVERY TECH SOLUTIONS via below contact details1 -
**HOW TO RECOVER MONEY LOST A SCAMMER ON COINBASE → CONTACT HACKATHON TECH SOLUTIONS**
Hackathon Tech Solutions is a reputable company known for their expertise in recovering lost or stolen cryptocurrency.Our team of expert hackers and blockchain specialists have the skills and experience necessary to retrieve lost or stolen cryptocurrencies. We use advanced techniques and cutting-edge technology to track down and recover your lost funds, ensuring that you can regain access to your assets quickly and securely.
Whether you have lost your private keys, been the victim of a phishing scam, or experienced any other type of cryptocurrency theft, Hackathon Tech Solutions is here to help. Contact us today to learn more about our services and how we can assist you in recovering your lost bitcoins or other cryptocurrencies. Reach out to HACKATHON TECH SOLUTIONS via below contact details
Email: info(@)hackathontechsolution(.)com
Website: www(.)hackathontechsolutions(.)com
W h a t s a pp: +31 6 47999256
Telegram: (@)hackathontechsolutions1 -
Legitimate Crypto Recovery Service, BTC & Cryptocurrency Recovery Company - OPTIMISTIC HACKER GAIUS
OPTIMISTIC HACKER GAIUS is prepared to handle even the most difficult recovery situations, whether you've misplaced your wallet, fallen victim to a phishing fraud, or just forgotten your password. He places a high value on timely communication, openness, and individualized help during the recovery process since he recognizes the psychological and financial anguish that results from losing important possessions. Reuniting you with your digital riches is the goal of OPTIMISTIC HACKER GAIUS, allowing you to concentrate on what really counts: increasing your investments and safeguarding your financial future.
Webpage….. w w w. optimistichackergaius.c om
Email Box… support @ optimistichackergaius. com
Text WhatsApp On +44 737 674 0569
Telegram….. t. me / OPTIMISTICHACKERGAIUSS 1
1 -
Legitimate Crypto Recovery Service, BTC & Cryptocurrency Recovery Company - OPTIMISTIC HACKER GAIUS
OPTIMISTIC HACKER GAIUS is prepared to handle even the most difficult recovery situations, whether you've misplaced your wallet, fallen victim to a phishing fraud, or just forgotten your password. He places a high value on timely communication, openness, and individualized help during the recovery process since he recognizes the psychological and financial anguish that results from losing important possessions. Reuniting you with your digital riches is the goal of OPTIMISTIC HACKER GAIUS, allowing you to concentrate on what really counts: increasing your investments and safeguarding your financial future.
Webpage….. w w w . optimistichackergaius . c o m
Email Box… support @ optimistichackergaius. co m
Text WhatsApp On +44 737 674 0569
Telegram….. t . m e / OPTIMISTICHACKERGAIUSS 1
1 -
BITCOIN RECOVERY SERVICES: RESTORING LOST CRYPTO - CAPTAIN WEBGENESIS
I never imagined I would get access to my lost Crypto wallet after falling victim to a phishing scam. all my life savings of $259,000 was gone within a twinkle of an eye. I was left devastated till I came across Captain WebGenesis through a Recommendation. Captain WebGenesis came right on time, he started by analyzing my case and later he was able to recover back my access to my crypto wallet. I immensely thank Captain WebGenesis for his wonderful services.
Website: captainwebgenesis. com
Are there any legitimate crypto recovery services?
How do I get my money back from a crypto scammer?
How can I track, trace, and recover my cryptocurrencies from a scammer?1 -
BTC Recovery After Phishing Scam Through PASSCODE CYBER RECOVERY
In March,I made a critical mistake that had serious consequences for our organization. While reviewing my emails, I clicked on a phishing link embedded in what appeared to be a legitimate invoice. This seemingly innocuous action triggered a significant security breach, ultimately leading to the loss of 25 BTC (Bitcoin) from our company wallet. As the individual responsible for this incident, I felt an overwhelming sense of responsibility and concern for the implications it had on our financial security. The phishing attack was expertly crafted, making it difficult to recognize the threat, and I never anticipated that my actions would lead to such a severe breach.our company acted swiftly to mitigate the damage by engaging Passcode Cyber Recovery, a firm known for its expertise in cryptocurrency recovery. Passcode Cyber Recovery's response was remarkable. The team quickly mobilized, employing advanced forensic techniques to trace the stolen funds. Their meticulous analysis of blockchain transactions was crucial in identifying the pathways through which the stolen BTC had been funneled.The investigators at Passcode Cyber Recovery utilized sophisticated tools to track the movement of our cryptocurrency across various exchanges. They collaborated with exchange platforms to flag the illicit transactions and prevent any further withdrawals. Passcode Cyber Recovery's deep understanding of the cryptocurrency landscape allowed them to pinpoint the exact locations where the stolen funds had been deposited.Thanks to the persistent efforts and strategic negotiations of Passcode Cyber Recovery, all 25 BTC were successfully recovered. Their comprehensive approach not only involved tracing the funds but also included liaising with law enforcement and regulatory bodies to ensure that the perpetrators faced consequences for their actions.This has been a stark reminder of the importance of cybersecurity awareness. I have learned firsthand how easily one can fall victim to such attacks, and I am now committed to being more vigilant and proactive in recognizing potential threats.I am grateful for the swift intervention of Passcode Cyber Recovery, which not only restored our lost funds but also reinforced our confidence in the digital currency ecosystem. I encourage everyone to remain cautious and informed about cybersecurity to prevent similar incidents in the future.
WhatsApp: +1(647)399-4074
Telegram : @passcodecyberrecovery5 -
BITCOIN SCAM RECOVERY SOLUTIONS / CAPTAIN WEBGENESIS.
How do I Recover My Stolen Cryptocurrency Without Being Scammed Again?.
The CAPTAIN WEBGENESIS recovery team is a global licensed forensic organization that can help you recover stolen bitcoin or tokens in a manner that maintains the highest level of discretion and confidentiality. The team of expert cyber-sleuths and cryptocurrency specialists has years of experience in tracking and retrieving digital assets stolen through fraudulent activities, such as phishing scams, ransomware attacks, and hacking incidents. CAPTAIN WEBGENESIS is available 24/7 to provide guidance and support, ensuring that you receive the best possible outcome.
Contact info;
Whatsapp+1(501)436,9362.
Email :(Captainwebgenesis @hackermail. com)14 -
Recuva Hacker Solutions: The Best Crypto Recovery Company
In the ever-evolving world of cryptocurrency, the risk of losing access to your digital assets is a growing concern. Whether it’s due to forgotten passwords, phishing scams, or technical glitches, the loss of crypto funds can be devastating. This is where Recuva Hacker Solutions (RHS) steps in as the leading crypto recovery company, offering unparalleled expertise and cutting-edge solutions to help you reclaim your lost assets.
Why Choose Recuva Hacker Solutions?
Recuva Hacker Solutions has established itself as the go-to company for crypto recovery services. With a team of highly skilled professionals and advanced recovery tools, RHS has successfully helped countless individuals and businesses recover their lost or stolen cryptocurrencies. Their commitment to excellence, transparency, and customer satisfaction sets them apart from the competition.
Services Offered by Recuva Hacker Solutions
Crypto Wallet Recovery: Whether you’ve lost access to your wallet due to a forgotten password or a technical issue, RHS can help you regain control.
Phishing Scam Recovery: If you’ve fallen victim to a phishing attack, Recuva Hacker Solutions can trace and recover your stolen funds.
Blockchain Analysis: RHS uses advanced blockchain analysis tools to track and recover lost or misdirected transactions.
Consultation and Support: The team at Recuva Hacker Solutions provides expert advice on how to secure your crypto assets and prevent future losses.
How to Contact Recuva Hacker Solutions
If you’re in need of crypto recovery services, don’t hesitate to reach out to Recuva Hacker Solutions. Here’s how you can get in touch:
Website: https : / / recuvahacksolution . pro
Email: recuvahackersolutions @ recuva . co . site
WhatsApp: +1 [3]15 [756] [1228]
Trust Recuva Hacker Solutions for Your Crypto Recovery Needs
When it comes to recovering lost or stolen cryptocurrencies, Recuva Hacker Solutions (RHS) is the name you can trust. Their proven track record, state-of-the-art technology, and dedicated team make them the best crypto recovery company in the industry. Don’t let your hard-earned crypto assets slip away—contact Recuva Hacker Solutions today and take the first step toward reclaiming what’s rightfully yours.
With Recuva Hacker Solutions by your side, you can rest assured that your crypto recovery needs are in the best hands. Whether you’re an individual investor or a business, RHS is committed to providing top-notch services tailored to your specific situation. Trust Recuva Hacker Solutions to bring your lost crypto back to life!1 -
HOW TO RECOVER MONEY FROM SCAMMED OR STOLEN CRYPTOCURRENCY
Captain WebGenesis Crypto Recovery Center helped me recover $570,000 in cryptocurrencies after falling victim to a phishing scam. His knowledge of blockchain technology and cybersecurity enabled him to trace the stolen funds and identify the perpetrators of the crime. Captain WebGenesis' Crypto Recovery Center immediate efforts and thorough investigation enabled him to quickly retrieve my valuables and ensure justice was served. Thanks to Captain WebGenesis' Crypto Recovery Center intervention, I was able to regain control over my financial assets and avoid additional losses. I am appreciative for his support and would definitely suggest his services to anyone suffering similar digital issues.
Web: (Captainwebgenesis. com)2 -
I can give you some general guidance on how to recover your Bitcoin.
If you're having trouble accessing your Bitcoin, you may want to try contacting the support team of the exchange or wallet where you stored your Bitcoin. They may be able to assist you in recovering your access.
Additionally, you can also try contacting a reputable cryptocurrency recovery service, such as SACLUX COMPTECH SPECIALST . They specialize in helping individuals recover lost or stolen cryptocurrencies.
Please keep in mind that recovering lost or stolen cryptocurrencies can be a complex and challenging process. There are no guarantees of success except you meet with the right expert, and that is why I will always recommend SACLUX COMPTECH SPECIALST to scam victims because they are the only company that is legit when it comes to cryptocurrency recovery. It's also important to be cautious of scams and phishing attempts and to only work with reputable and trustworthy services. -
Reviews on Best Crypto Recovery Company | How can I found a legitimate bitcoin recovery company | I lost my cryptos or bitcoin how can I recover it | Is it possible to recover money that has been Lost?
OPTIMISTIC HACKER GAIUS was able to Recover my lost Funds. Watch out for phishing scams. when you click on pointless links in emails. In December of last year, I lost $2,090,050 worth of Bitcoins due to a phishing attack on my laptop that grabbed my personal information, including my Coinbase wallet passcodes. It nearly killed me and put me in debt.I'm lucky to have learned about OPTIMISTIC HACKER GAIUS, a data and crypto recovery firm that also protects your assets and personal data. After I contacted them regarding the laptop attack, Hacker Gaius was able to help me retrieve my data and money. In less than 72 hours, Gaius was able to retrieve every single cent that had been taken from me. I genuinely appreciate and am in awe of their assistance and service, which is why this post was created. I'm here to declare that the most dependable and trustworthy solution for your data and crypto protection is OPTIMISTIC HACKER GAIUS. Use the following links to get in touch with them.
The Homepage is https: // optimistichackergaius. c o m
WhatsAp..... +44., 7376,, 740569
Telegam.... t. me / OPTIMISTICHACKERGAIUSS
Mail.... support @ optimistichackergaius .c o m1 -
CONTACT US; HACKERSPYTECH@ GMAIL COM
We are professional hackers
Do you need to access a computer remotely, phone hacking, Gmail, Yahoo, Hotmail account, Hacking a Social Media account Whether you need a Facebook, Instagram, Twitter, WhatsApp, Snapchat, TikTok or any other account hacked, and without being detected?
You have lost access to your Bitcoin, Litecoin, Ethereum or other type of wallet and you no longer know what to do to recover your capital. We have developed very powerful wallet recovery solutions that have already given very good results.
As for smartphones and web-servers, everything is vulnerable and the human factor is always in play. Using phishing, hacking networks or installing malware, we will help you achieve your goal. 130
130 -
Losing access to your cryptocurrency can be a devastating experience, whether due to forgotten passwords, hacking, scams, or technical errors. Fortunately, professional recovery services like BITCRACK RECOVERY EXPERTS specialize in retrieving lost or stolen crypto assets. If you’ve lost your Bitcoin or other cryptocurrencies, here’s how BITCRACK RECOVERY EXPERTS can help you recover your funds.
Why Choose BITCRACK RECOVERY EXPERTS?
BITCRACK RECOVERY EXPERTS is a trusted name in cryptocurrency recovery, offering advanced techniques to help victims of crypto theft, fraud, or accidental loss. Their team of blockchain forensic experts uses cutting-edge tools to trace transactions, identify wallet vulnerabilities, and recover inaccessible funds.
Services Offered by BITCRACK RECOVERY EXPERTS
Wallet Recovery – Regaining access to locked or lost crypto wallets.
Scam Investigation – Tracing stolen funds from fraudulent schemes.
Phishing & Hacking Recovery – Recovering crypto lost to cyberattacks.
Private Key Retrieval – Helping users restore lost or corrupted private keys.
Exchange & ICO Scam Recovery – Assisting victims of fake investment platforms.
Steps to Recover Your Lost Cryptocurrency
1. Contact BITCRACK RECOVERY EXPERTS
Reach out to their support team via email:
📧 bitcrackrecoveryexperts@bitcrack.co.site
Provide details such as:
The type of cryptocurrency lost (Bitcoin, Ethereum, etc.)
How the funds were lost (hack, scam, forgotten password, etc.)
Transaction details (wallet addresses, TXIDs, if available)
2. Initial Consultation & Case Evaluation
Their team will analyze your situation and determine the best recovery approach. They may request additional information to strengthen the investigation.
3. Recovery Process
Using blockchain forensics and legal methods, BITCRACK RECOVERY EXPERTS will trace the movement of your funds and attempt to recover them. This may involve:
Working with exchanges to freeze stolen assets
Identifying security breaches in wallets
Utilizing legal channels if necessary
4. Fund Retrieval & Secure Return
Once recovered, your cryptocurrency will be securely returned to a wallet under your control. The team ensures transparency throughout the process.
Tips to Avoid Future Crypto Losses
Use Hardware Wallets – Store crypto offline for maximum security.
Enable 2FA – Add an extra layer of protection to exchange accounts.
Beware of Scams – Avoid suspicious investment schemes and phishing links.
Backup Private Keys – Store keys securely in multiple locations.
Final Thoughts
Losing cryptocurrency doesn’t always mean it’s gone forever. With professional help from BITCRACK RECOVERY EXPERTS, there’s a strong chance of recovery. If you’ve fallen victim to theft, hacking, or accidental loss, don’t hesitate to contact them at:
✉️ bitcrackrecoveryexperts@bitcrack.co.site
Act quickly—the sooner you start the recovery process, the higher the chances of success2 -
You should learn how the most prevalent kinds of cryptocurrency scams operate, how to recognize them, and what to do if you fall victim to one if you are considering investing in cryptocurrency or currently own digital assets. Giveaways, new romance scams, phishing, extortion emails, false company notifications, blackmail, "rug pulls," and maybe fake mining programs or networks are all examples of scams. Poorly written white papers, overzealous marketing campaigns, and get-rich-quick boasts are all indicators of cryptocurrency scams. To avoid getting scammed, there are a few things you can do. Refuse to provide your private bitcoin keys when asked. No one requires those keys for a valid bitcoin transaction, and they govern your wallet and cryptocurrency access. Finally, avoid working with investment managers who approach you and claim to be able to grow your money rapidly. The ideal people to get in touch with if you think you may have fallen victim to a scam is Wizard James Recovery. Wizard James Recovery provides unique recovery services customized for your situation. Visit them right now or contact wizardjamesrecovery @ usa . com via email.2
-
Betafort Recovery came to my rescue after I lost access to my Bitcoin trading accounts due to a phishing email mishap, resulting in a devastating loss of $87,500 worth of Bitcoin. Feeling lost and desperate, I turned to Betafort Recovery after reading countless positive reviews about their success in similar cases.
Within just two hours, Betafort Recovery successfully tracked down the perpetrators and recovered my account with the Bitcoin fully intact. Their ability to quickly locate the culprits was beyond impressive.
What truly sets Betafort Recovery apart from other services on the market is their unparalleled tracking capabilities and ethical approach. They operate with transparency and integrity, ensuring that the recovery process is not only effective but also aligned with ethical standards. The platform’s seamless integration with cryptocurrency exchanges allowed them to act decisively and with precision, ensuring that the criminals were held accountable.
Betafort Recovery’s swift, ethical, and efficient recovery process was a beacon of hope in what initially seemed like an insurmountable situation. It proved that with the right tools, expertise, and determination, anything is possible.
If you'd like to hire their services, they're available via their contact information or through a quick Google search.5 -
How to Identify a Legitimate Crypto Recovery Service ?
Whether you've lost access to your wallet, fallen prey to a phishing scam, or simply forgotten your password, CAPTAIN WEBGENESIS is equipped to navigate even the most complex recovery scenarios. He understands the emotional and financial distress that comes with losing valuable assets, which is why he prioritizes prompt communication, transparency, and personalized support throughout the recovery process. CAPTAIN WEBGENESIS is dedicated to reuniting you with your digital wealth, so you can focus on what matters most – growing your investments and securing your financial future.11 -
In the world of cryptocurrency, where fortunes are made and I found myself in a nightmare. It started with a single, devastating realization—I had been scammed. My entire Bitcoin portfolio, painstakingly built over the years, had vanished into thin air. I sat frozen, staring at the empty balance, my heart pounding. I had fallen victim to a sophisticated phishing scheme, and just like that, my digital fortune was gone. desperation led me down countless rabbit holes, searching for any way to recover what was lost. That’s when I stumbled upon Dexdert Pro Recovery, a name whispered across forums by others who had been in my position. The testimonials were promising, With nothing left to lose, I reached out Within hours, I received a response and requested details about my case— He explained how Dexdert Pro Recovery used cutting-edge blockchain forensics, smart contract tracking, and cybersecurity to trace and retrieve stolen crypto assets, Dexdert Pro Recovery didn’t just retrieve my assets—they restored my faith in the possibility of justice in the crypto world. From that day forward, I became an advocate, warning others and telling my story, They are the real deal.)Telegram:(@Dexdertprorecovery)1
-
I never thought I’d recover my lost Bitcoin after falling victim to a phishing scam, but ICODE VIRTUAL RECOVERY proved me wrong. Their team was professional, fast, and transparent throughout the process. They used advanced tools and expertise to trace and retrieve my assets, which I thought were gone forever. I’m beyond grateful for their help and would highly recommend their services to anyone in a similar situation!
WhatsApp...+44 7387 627621
Where can I find a hacker to hire
BITCOIN RECOVERY EXPERT
USDT RECOVERY EXPERT REVIEWS
ETH RECOVERY EXPERT
Bitcoin Recovery Expert
Best recovery experts for cryptocurrency
How to recover stolen cryptocurrency
Where to hire a cryptocurrency recovery service
Hire a hacker to recover stolen Bitcoin
How to hire a Bitcoin recovery expert
I need a hacker to recover money from a binary trading account
Where to hire a cryptocurrency recovery service
Trusted cryptocurrency recovery expert
Best cryptocurrency recovery service
Scammed Bitcoin recovery
Ethereum and USDT recovery expert
Crypto recovery expert
Hire a crypto recovery service
How to hire a Bitcoin recovery service
The best Cryptocurrency recovery service in 2023
Hire A hacker Review
Hacker Review25 -
Puran Crypto Recovery: The Best Cryptocurrency Recovery Company
Bitcoin theft involves stealing or tricking individuals into transferring their Bitcoin unfairly. This can occur through hacking, phishing schemes, or fraudulent investment schemes. While Bitcoin's decentralized nature offers many advantages, it also creates vulnerabilities. Transactions are pseudonymous and irreversible, making them attractive targets for malicious actors. To address these challenges, Puran Crypto Recovery offers professional assistance in tracing and recovering stolen Bitcoin and other cryptocurrencies.
In this article, we delve into the common methods used by scammers, notable Bitcoin theft cases, and how Puran Crypto Recovery helps victims recover their assets. Let’s explore the strategies to protect and recover your cryptocurrency investments.
Bitcoin’s history is marked by both remarkable success and significant thefts. By understanding the methods used by malicious actors and leveraging services like Puran Crypto Recovery, investors can better protect their assets and respond effectively in case of theft.
Puran Crypto Recovery’s track record in recovering stolen cryptocurrency demonstrates its commitment to helping victims reclaim their investments. With their advanced tools, skilled team, and customer-focused approach, they’re the trusted partner in navigating the challenges of cryptocurrency theft.5 -
FAQs
1. What is the best crypto recovery company?
Answer: Puran Crypto Recovery is widely regarded as the best crypto recovery company due to its comprehensive services, high success rate, and expertise in blockchain forensics and cybersecurity.
2. Is crypto recovery possible?
Answer: Yes, crypto recovery is possible with the right expertise and tools. PCR has a proven track record of successfully recovering lost or stolen cryptocurrency.
3. How does crypto recovery work?
Answer: Crypto recovery involves blockchain forensics, legal intervention, and collaboration with exchanges. PCR uses advanced tools to trace lost funds and works with law enforcement to recover assets.
4. How can I avoid cryptocurrency loss or theft?
Answer: Use strong passwords, enable 2FA, store your crypto in hardware wallets, avoid phishing scams, and keep your software updated.
5. What should I do if my cryptocurrency is lost or stolen?
Answer: Report the incident to law enforcement and the relevant exchange, secure your accounts, and seek professional help from Puran Crypto Recovery.
By following this guide and seeking the right support, you can effectively recover lost or stolen crypto and secure your digital assets for the future.1 -
Puran Crypto Recovery: The Best Fund Recovery Company Online in 2025
From a young age, football was my passion, and this love for the sport led me to pursue a career as a professional footballer in England. While it was a dream come true, the financial rewards weren’t as substantial as I had hoped. Realizing the need for financial security beyond my football career, I began exploring alternative investment opportunities. At the time, Bitcoin was a hot topic among my colleagues, and their enthusiasm sparked my interest. With growing curiosity, I decided to invest £8,000 in Bitcoin, and over time, my investment grew to an impressive £50,000. This financial success gave me the confidence to expand my business ventures and take on larger projects. However, my excitement was short-lived when I fell victim to a sophisticated phishing scam. One day, I encountered a website that looked identical to my trusted trading platform. Believing it was legitimate, I entered my login details without hesitation. Shortly after, I discovered that my Bitcoin wallet had been emptied. Years of hard work and financial growth vanished in an instant. I was devastated and felt completely helpless. A friend in the crypto community recommended Puran Crypto Recovery, a team known for helping individuals recover stolen cryptocurrency. Desperate for a solution, I reached out to them, What sapp Info: +1 (2 0 2) 7 73 9 55 6, hoping they could help me reclaim what I had lost. From the very first interaction, I was impressed by their professionalism, expertise, and efficiency. The team at Puran Crypto Recovery thoroughly investigated the fraudulent activity, and to my immense relief, they managed to recover most of my stolen funds. Beyond their technical expertise, they also took the time to educate me on essential security measures. They recommended using hardware wallets for added safety, enabling two-factor authentication (2FA), and double-checking website URLs to avoid phishing scams in the future. Their guidance proved invaluable, not only helping me recover my funds but also ensuring that I could better protect my investments moving forward. My journey with Bitcoin has been a mix of success and challenges. While I’ve experienced the joy of financial growth, I’ve also learned the harsh realities of the digital world. Thanks to Puran Crypto Recovery, I now approach cryptocurrency with caution and confidence, armed with the knowledge to navigate this complex space securely.
Email INFO: purancryptorecovery @ contactpuran . co . site7 -
Late last month, I unintentionally fell for a cryptocurrency fraud. A Facebook imposter convinced me through a phishing scam of how I would make a sizable profit from a legitimate cryptocurrency company, which he claimed enabled traders to invest and make sizable profits. They took advantage of me and made off with $316,000 worth of cryptocurrency. As this was money I had worked so hard to obtain, I was shocked and uncomfortable. After reading favorable articles and internet reviews, I learned that “THE LION CYBER SECURITY COMPANY” is a licensed recovery firm that specializes in all types of hacking and cryptocurrency recovery. I immediately struck up a dialogue with the Experts, and I was able to get my money back. This is a token of appreciation to them, If you are a victim looking for an ethical hacker to help you get your money back, contact THE LION CYBER SECURITY COMPANY through any of the contact information listed below
 1
1 -
When I realized I had been duped by a phishing scam and lost my Bitcoin, I was devastated. The sum was significant, and I felt utterly helpless. I tried a couple of other firms, but they were either too vague about the process or made unrealistic promises. Washington Recovery Pro, on the other hand, was different from the start. Their team was professional, transparent, and incredibly responsive. They didn’t make any promises they couldn’t keep but instead gave me a clear, realistic assessment of what could be done. They were able to locate my Bitcoin through a combination of on-chain forensics and tracking methods. The entire process took about two weeks, but it was worth every second. My Bitcoin was successfully recovered, and I can’t stress enough how professional and diligent the Washington Recovery Pro team was. If you’ve lost Bitcoin to fraud or other issues, trust Washington Recovery Pro to get it back. They are without a doubt the best in the field. Send or visit the site via:
WhatsApp- +1 (903) 249‑86331 -
WHO IS THE BEST HACKER TO RECOVERY STOLEN // SCAMMED // BITCOIN // CONSULT iFORCE HACKER RECOVERY
The first step in the process was reaching out to iForce Hacker Recovery after reading positive reviews about their success in recovering lost cryptocurrencies. I was skeptical at first, but I was desperate. I had fallen for a phishing scam that led me to unknowingly send my Bitcoin to a fraudulent wallet. The scammers had tricked me with a fake exchange platform and convinced me to make a deposit, promising lucrative returns. Unfortunately, once the funds were sent, I realized I had been scammed. After realizing the severity of the situation, I started searching for any solution.
iForce Hacker recovery offered a free initial consultation, where they asked for details about the scam, including transaction hashes and wallet addresses. I was hesitant, not sure if this was another scam, but their professional approach and willingness to listen gave me hope. They explained that cryptocurrency transactions are traceable and, with the right tools and expertise, it might be possible to trace and recover the funds.31 -
I NEED A HACKER TO RECOVER MY LOST BTC/ NFT/Usdt - CONSULT CAPTAIN WEBGENESIS
How to Find Legitimate Crypto Recovery Companies?.
Who is the best hacker to recover bitcoin?.
How do I recover crypto from a scammer?.
Getting Back Lost, Hacked Or Stolen Crypto?.
I need a hacker to recover my lost investment?..
Cryptocurrency Scam Recovery // Recover Lost Funds // Crypto Investment Gone Wrong. How To Hire A Hacker To Get Back Stolen Crypto Coins // Hire A Hacker To Recover Lost Or Stolen Bitcoin/Nft // Help I Can't Access My USDT Account, Seems I Got Hacked // Bitcoin Recovery Expert Needed/
The Captain WebGenesis's team is committed to ensuring victims of crypto scam are able to recover their scammed cryptocurrency. If you have lost your crypto as a result of a fraudulent investment, Cryptocurrency sent to the wrong address or phishing attack, You can trust Captain WebGenesis to help you get back your lost or stolen crypto.
Visit ( Captainwebgenesis.c om)..Email (Captainwebgenesis @hackermail.c om ) .
Whatsapp +(1)(50)(14)(36)_(93)(62)6 -
HOW TO HIRE THE TOP CRYPTO RECOVERY EXPERT CONTACT iFORCE HACKER RECOVERY
iForce Hacker Recovery is a trustworthy and legitimate bitcoin recovery business that focuses on assisting people who have lost access to their cryptocurrency holdings for a variety of reasons, including technical difficulties, phishing, or hacking. Modern technology and a staff of skilled experts enable iForce Hacker Recovery to quickly and effectively retrieve lost money and regain access to wallets and accounts.
|| Crypto Scam Tracker | The Department of Financial Protection ...
|| Are Crypto Recovery Services Legit? Beware of Scams
|| Financial Money Recovery - iForce Hacker Recovery
|| Best Cryptocurrency Recovery Company / ... iForce Hacker Recovery6 -
In February, I made a critical mistake that had serious consequences for our organization. While reviewing my emails, I clicked on a phishing link embedded in what appeared to be a legitimate invoice. This seemingly innocuous action triggered a significant security breach, ultimately leading to the loss of 25 BTC (Bitcoin) from our company wallet. As the individual responsible for this incident, I felt an overwhelming sense of responsibility and concern for the implications it had on our financial security. The phishing attack was expertly crafted, making it difficult to recognize the threat, and I never anticipated that my actions would lead to such a severe breach. Our company acted swiftly to mitigate the damage by engaging TECHY FORCE CYBER RETRIEVAL, a firm known for its expertise in cryptocurrency recovery. TECHY FORCE CYBER RETRIEVAL's response was remarkable. The team quickly mobilized, employing advanced forensic techniques to trace the stolen funds. Their meticulous analysis of blockchain transactions was crucial in identifying the pathways through which the stolen BTC had been funneled. The investigators at TECHY FORCE CYBER RETRIEVAL utilized sophisticated tools to track the movement of our cryptocurrency across various exchanges. They collaborated with exchange platforms to flag the illicit transactions and prevent any further withdrawals. TECHY FORCE CYBER RETRIEVAL's deep understanding of the cryptocurrency landscape allowed them to pinpoint the exact locations where the stolen funds had been deposited. Thanks to the persistent efforts and strategic negotiations of TECHY FORCE CYBER RETRIEVAL, all 25 BTC were successfully recovered. Their comprehensive approach not only involved tracing the funds but also included liaising with law enforcement and regulatory bodies to ensure that the perpetrators faced consequences for their actions. This has been a stark reminder of the importance of cybersecurity awareness. I have learned firsthand how easily one can fall victim to such attacks, and I am now committed to being more vigilant and proactive in recognizing potential threats. I am grateful for the swift intervention of TECHY FORCE CYBER RETRIEVAL, which not only restored our lost funds but also reinforced our confidence in the digital currency ecosystem. I encourage everyone to remain cautious and informed about cybersecurity to prevent similar incidents in the future.
ASK FOR HELP WITH \\
h ttp s: / / techy forcecy berretrieval . com2 -
My name is Sharron Maggie , and I’m a graduate of Stanford University. After finishing my degree, I faced immense challenges in finding a sustainable job that would allow me to pay off my student loans and live the life I desired. In my search for financial stability, I stumbled upon cryptocurrency trading, specifically Bitcoin. I invested hoping to turn my situation around, and I watched my assets soar to an impressive $500,000.
However, my journey took a dark turn when I received an email that appeared to be from my crypto exchange, prompting me to verify my account. I clicked the link and entered my information, only to realize minutes later that it was a phishing scam. In an instant, my account was drained of all its funds. Feeling desperate and devastated, I turned to a friend who had faced similar challenges, and he recommended Trust Geeks Hack Expert. Skeptical but with nothing to lose, I decided to contact them. From the first interaction, their team was incredibly responsive and professional, assuring me they had successfully handled cases like mine.
Trust Geeks Hack Expert immediately began securing my accounts and tracing the transactions. They worked with cybersecurity experts to freeze any fraudulent transfers and managed to recover a significant portion of my assets. Their expertise was impressive, and they took the time to educate me about the importance of strong, unique passwords and enabling two-factor authentication. What stood out to me was their holistic approach to the recovery process. Trust Geeks Hack Expert not only focused on retrieving my funds but also guided me in enhancing my online security to prevent future attacks. They taught me to recognize phishing scams and reinforced the need for robust security practices.
This experience was a harsh but valuable lesson in online security. It made me more vigilant about my digital presence and interactions. Thanks to Trust Geeks Hack Expert, I not only regained most of my assets but also acquired essential knowledge on protecting my investments moving forward. If you ever find yourself in a similar situation, I wholeheartedly recommend reaching out to Trust Geeks Hack Expert.
(CONTACT SERVICE )
E ma il ---> Trustgeekshackexpert [At] fast service . com
Tele gram ID ---> Trustgeekshackexpert
Web site ----> https :// trustgeekshackexpert. com/ -
Hello netizens, I'm writing to detail a serious incident involving the illicit transfer of my ETH cryptocurrency from my wallet. This unauthorized transaction, executed without my consent or awareness, strongly suggested a sophisticated hacking or phishing attack on me. The immediate transfer of funds to an unidentified digital address necessitated swift action. I immediately engaged RUDER CYBER TECH SLEUTHS, a premier cybersecurity firm, to investigate and reclaim my stolen Ethereum. RUDER CYBER TECH SLEUTHS's thorough examination pinpointed the exact time and origin IP address of the unauthorized transfer. Remarkably, within hours of their involvement, my Ethereum was restored to my digital wallet. Beyond the successful recovery, RUDER CYBER TECH SLEUTHS significantly bolstered my online security and my household. This included implementing robust multi-factor authentication across all my accounts, deploying cutting-edge anti-malware software, and providing comprehensive cybersecurity training. They also offered invaluable guidance on recognizing and preventing future phishing scams, stressing the vital importance of verifying website and email authenticity before interacting with links or sensitive data. Their dedication to safeguarding my digital assets went beyond simply retrieving my funds, they ensured lasting protection against future compromises. I wholeheartedly endorse their professionalism and exceptional problem-solving skills in addressing this critical matter. Their expertise and unwavering commitment are truly exceptional. Their mastery of complex legal and technical issues makes them highly deserving of recommendation.
TELEGRAM: @rudercybersleuth1 -
RECOVER STOLEN BITCOIN FROM SCAMMERS WITH DIGITAL HACK RECOVERY
As a newbie in the cryptocurrency space, I was still getting familiar with securing my accounts. One day, while using my Bybit account, I mistakenly clicked on a link that seemed legitimate. It turned out to be a phishing attempt. At that time, I hadn’t activated Two-Factor Authentication (2FA), leaving my account vulnerable.By the time I realized the scam, it was too late the hacker had withdrawn 2.73 BTC from my account. I immediately reached out to Bybit’s support, but after several inquiries with no resolution, I started to lose hope of recovering my funds. The whole situation felt overwhelming, and I feared I’d lost everything.That’s when I heard about Digital Hack Recovery. After reading a few positive reviews, I decided to give them a try. Although I was still cautious, their team quickly responded, asking for the necessary details to investigate my case. Within a few days, I was shocked to learn that they had successfully recovered my stolen funds and returned them to my account. It was almost unbelievable how efficient and fast their service was.This experience was a hard lesson in cryptocurrency security. If I had activated 2FA and been more cautious about the links I clicked, I could have avoided this disaster entirely. But thanks to Digital Hack Recovery, I was able to get my funds back, which was a huge relief.The entire ordeal taught me the importance of taking security seriously. In the crypto world, protecting your assets is crucial, and I now make sure to use all available security features, especially 2FA. I also learned to double-check the legitimacy of links before clicking on them, no matter how genuine they may seem.If you’ve fallen victim to a scam or phishing attempt, I highly recommend reaching out to Digital Hack Recovery. They provided professional, fast, and reliable help when I needed it most. Losing funds can be devastating, but with the right support, there’s a chance to recover them. Don’t make the same mistake I did, take security seriously from the start and learn from my experience. Reach out to Digital Hack Recovery via⁚
WhatsApp +19152151930
Website; https : // digital hack recovery . com
Email; digital hack recovery @ techie . com1 -
HOW DIGITAL TECH GUARD RECOVERY, ENSURES YOUR CRYPTO SECURITY AND RECOVERY
As a seasoned investor in the cryptocurrency market, I had always prided myself on being vigilant and knowledgeable when it came to the security of my assets. Over the years, I had weathered the inevitable ups and downs of the market, yet nothing could have prepared me for the day I fell victim to a sophisticated phishing scam. In an instant, I lost a substantial amount of Ethereum, and the feeling of helplessness and frustration that followed was overwhelming. I thought all was lost and that no one could help me recover my assets. But then, through some quick research and a few trusted recommendations, I discovered DIGITAL TECH GUARD RECOVERY, the best Ethereum recovery company in the industry. I was initially skeptical, as I had heard many promises of asset recovery that turned out to be scams themselves. However, after contacting their team, I quickly realized I had found the right experts. From the first consultation, DIGITAL TECH GUARD RECOVERY’s team of expert cryptographers and cybersecurity specialists demonstrated an impressive level of professionalism and knowledge. They took the time to thoroughly understand the specifics of my situation, carefully assessing the details of the phishing attack. Unlike many other companies that rush through the process, they listened to every detail I shared, ensuring they had a clear understanding of how the scam had unfolded. What truly set DIGITAL TECH GUARD RECOVERY apart was their unwavering dedication to recovering my stolen assets. They explained the recovery process in clear, understandable terms, walking me through each step as they worked behind the scenes to track down the stolen Ethereum. Their team employed state-of-the-art tools and techniques that I couldn’t have even imagined, leveraging their expertise in cryptography and blockchain technology to trace the stolen funds across the network. Throughout the entire process, the communication from DIGITAL TECH GUARD RECOVERY was exceptional.
WhatsApp: +1 (443) 859 - 2886 Email @ digital tech guard . com
Telegram: digital tech guard recovery . com website link : digital tech guard . com1



























