Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "plain text"
-
So... A random morning moment:
(c - Cient, m - me)
C: Help!!! Our users are complaining that our website is not working as intended!!! This is crucial!!!!
M: What's the problem? What is not working?
C: EVERYTHING!!!! FIX IT!!!!
M: Could you be more specific...?
C: Look at the bugsnag - it has all the errrors!!!
M: *looks there - no errors* - But... It has no errors...
C: Okay, so client told me he's using Galaxy SII - does that ring a bell?
M: *thinks that I'm fucked* - Asks, which browser?
C: Why do you need it? It's a browser after all...
M: Yeah but not all browsers are the same and I need type and version to investigate...
C: It's Samsung default browser... Last updated 2012 January.
M: Well, tell that user to update the browser, the site is working fine on newer versions...
C: No, you update it.
M: Browser?!
C: Yes, what else?!
M: Of course, I'll fly 3000 kilometres to press UPDATE button on clients phone...
C: Well, he's not doing it himself - he's afraid!
M: Well, that is his problem. Site is working fine for other users with newer browsers.
C: But... He's a client
M: I get it but he's a client that uses 6 years old browser and tries to visit our website. Don't you remember that we ditched IE support on your behalf for the same reason?!
C: Oh... I see... Can you make something that it works with 2005 browsers?
M: Of course... *evil laugh starts* I'll make the website work on EVERY single device EVER - make it plain text.
C: Are you joking?
M: Are you?
----
And since then, we ditched the actual need for supporting users with old browsers that don't update to modern standards... Feels great!12 -
(sensitive parts censored)
Friend: Hey, can you hack my (some website) account?
Me: Depends... What's your username?
Friend: (tells username)
Me: (clicks forgot password?)
Friend: I will give $10 if you do it. There is 2 factor authentication enabled.
Me: (silence) Ok.
Website: Please type the class number you were in in 4th grade.
Me: Hey, did you graduated BLAH elementary school?
Friend: Yeah.
Me: Ahh, I remember. You moved to BLAH elementary school in what grade?
Friend: 4
Me: Hmmm, I don't remember seeing you. What class were you in?
Friend: 5
Me: Well, I now remember. Stupid me. (smirks)
Friend: Haha. (continues to play games beside me)
Me: (Types in 8)
Website: We sent you a password to blah@example.com
Me: (uhh, heads to example.com and clicks forget password?)
Email: Please type the class number you were in in 4th grade.
Me: (wtf is this, types 8)
Email: Please type the teacher's name when you were in in 4th grade.
Me: What was the teacher's name?
Friend: Huh?
Me: When you were in 4th grade.
Friend: Ahh! John Smith.
Me: Ahh, he was strict, right?
Friend: Yeah (continues to play games again)
Me: (Types in John Smith)
Email: Set a new password.
Me: (Types "youaresostupid")
Email: Done!
Me: (copies PLAIN TEXT password from email, logs in to website)
Me: Da-da!
Friend: (gasps)
Me: Money plz~
Friend: Nope.
Me: (wtf, then remembers i changed his email password) Fine then.
=====================
1. There is 2 factor authentication enabled. : Got it?
2. The website sent plaintext password.
3. He is just pure idiot.
4. I didn't got the money.
5. I am now a h4x0r11 -
1. Forgot my password.
2. Clicked "Forgot" password button.
3. Received my forgotten password as plain text in my email6 -
Omg...
T-Mobile AT was asked, why they store passwords in plain text, and in a long discussion, they answered this (see img)
I don't know, if this is a late april fool... 25
25 -
My company contracted a 3rd party to do an internal system for us...
We only knew about it when it was almost done and we got the code... Oooooo boy.... What a fucking shit they did and got paid for...
They have a encryptPassword() and decryptPassword() functions...
What they do you may ask?
Well...
Encrypt: for loop that reverse the string and base64 it 5 times...
Decrypt: the opposite...
That's how they store passwords....
Our intern snapped at a company meeting when they where talking about maintaining it 😂😂21 -
Client: Let me send you the files needed.
*client sends link to their own Dropbox folder page, not actually sending a shared link*
Me: Uuuhm, the link you've just send is only viewable by your account.
Client: Oh, hold....
Client a bit later: *sends actual Dropbox credentials over email in plain text*
Why.26 -
Way to many...
- Passwords stored in plain text on the year 2014
- Not supporting HTTPS because to expensive
- Hidden admin URLS
- Databases available all over the internet
- Client Side validation
- IoT5 -
You, stupid fucking game, have just sent me my new password in plain text via email?
"the password is encrypted and cannot be sent again"???
So… you send the password in plain text, and only then encrypt it, right?
But it's still in plain text in your email logs, fucking bastards. 10
10 -
It's maddening how few people working with the internet don't know anything about the protocols that make it work. Web work, especially, I spend far too much time explaining how status codes, methods, content-types etc work, how they're used and basic fundamental shit about how to do the job of someone building internet applications and consumable services.
The following has played out at more than one company:
App: "Hey api, I need some data"
API: "200 (plain text response message, content-type application/json, 'internal server error')"
App: *blows the fuck up
*msg service team*
Me: "Getting a 200 with a plaintext response containing an internal server exception"
Team: "Yeah, what's the problem?"
Me: "...200 means success, the message suggests 500. Either way, it should be one of the error codes. We use the status code to determine how the application processes the request. What do the logs say?"
Team: "Log says that the user wasn't signed in. Can you not read the response message and make a decision?"
Me: "That status for that is 401. And no, that would require us to know every message you have verbatim, in this case, it doesn't even deserialize and causes an exception because it's not actually json."
Team: "Why 401?"
Me: "It's the code for unauthorized. It tells us to redirect the user to the sign in experience"
Team: "We can't authorize until the user signs in"
Me: *angermatopoeia* "Just, trust me. If a user isn't logged in, return 401, if they don't have permissions you send 403"
Team: *googles SO* "Internet says we can use 500"
Me: "That's server error, it says something blew up with an unhandled exception on your end. You've already established it was an auth issue in the logs."
Team: "But there's an error, why doesn't that work?"
Me: "It's generic. It's like me messaging you and saying, "your service is broken". It doesn't give us any insight into what went wrong or *how* we should attempt to troubleshoot the error or where it occurred. You already know what's wrong, so just tell me with the status code."
Team: "But it's ok, right, 500? It's an error?"
Me: "It puts all the troubleshooting responsibility on your consumer to investigate the error at every level. A precise error code could potentially prevent us from bothering you at all."
Team: "How so?"
Me: "Send 401, we know that it's a login issue, 403, something is wrong with the request, 404 we're hitting an endpoint that doesn't exist, 503 we know that the service can't be reached for some reason, 504 means the service exists, but timed out at the gateway or service. In the worst case we're able to triage who needs to be involved to solve the issue, make sense?"
Team: "Oh, sounds cool, so how do we do that?"
Me: "That's down to your technology, your team will need to implement it. Most frameworks handle it out of the box for many cases."
Team: "Ah, ok. We'll send a 500, that sound easiest"
Me: *..l.. -__- ..l..* "Ok, let's get into the other 5 problems with this situation..."
Moral of the story: If this is you: learn the protocol you're utilizing, provide metadata, and stop treating your customers like shit.21 -
"Hey, Root, someone screwed up and now all of our prod servers are running this useless query constantly. I know I already changed your priorities six times in the past three weeks, but: Go fix it! This is higher priority! We already took some guesses at how and supplied the necessary code changes in the ticket, so this shouldn't take you long. Remember, HIGH PRIORITY!"
1. I have no idea how to reproduce it.
2. They have no idea how to reproduce it.
3. The server log doesn't include queries.
4. The application log doesn't include queries.
5. The tooling intercepts and strips out some log entries the legendary devs considered useless. (Tangent: It also now requires a tool to read the logs because log entries are now long json blobs instead of plain text.)
6. The codebase uses different loggers like everywhere, uses a custom logger by default, and often overwrites that custom logger with the default logger some levels in. gg
7. The fixes shown in the ticket are pretty lame. (I've fixed these already, and added one they missed.)
8. I'm sick and tired and burned out and just can't bring myself to care. I'm only doing this so i don't get fired.
9. Why not have the person who screwed this up fix it? Did they quit? I mean, I wouldn't blame them.
Why must everything this company does be so infuriatingly complicated?11 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
Privacy & security violations piss me off. Not to the point that I'll write on devRant about it, but to the point that coworkers get afraid from the bloodthirsty look in my eyes.
I know all startups proclaim this, but the one I work at is kind of industry-disrupting. Think Uber vs taxi drivers... so we have real, malicious enemies.
Yet there's still this mindset of "it won't happen to us" when it comes to data leaks or corporate spying.
Me: "I noticed we are tracking our end users without their consent, and store not just the color of their balls, but also their favorite soup flavor and how often they've cheated on their partner, as plain text in the system for every employee to read"
Various C-randomletter-Os: "Oh wow indubitably most serious indeed! Let's put 2 scrumbag masters on the issue, we will tackle this in a most agile manner! We shall use AI blockchains in the elastic cloud to encrypt those ball-colors!"
NO WHAT I MEANT WAS WHY THE FUCK DO WE EVEN STORE THAT INFORMATION. IT DOES IN NO WAY RELATE TO OUR BUSINESS!
"No reason, just future requirements for our data scientists"
I'M GRABBING A HARDDRIVE SHREDDER, THE DB SERVER GOES FIRST AND YOUR PENIS RIGHT AFTER THAT!
(if it's unclear, ball color was an optimistic euphemism for what boiled down to an analytics value which might as well have been "nigger: yes/no")12 -
So according to some reddit user IKEA sends your password as a GET parameter in plain text.
https://reddit.com/r/CrappyDesign/...
Seems to be a network authentication thingy, but still 🤔 34
34 -
I wonder why banks are always so terribly insecure, given how much money there's for grabs in there for hackers.
Just a while ago I got a new prepaid credit card from bpost, our local postal service that for some reason also does banking. The reason for that being that - thank you 'Murica! - a lot of websites out there don't accept anything but credit cards and PayPal. Because who in their right mind wouldn't use credit cards, right?! As it turns out, it's pretty much every European I've spoken to so far.
That aside, I got that card, all fine and dandy, it's part of the Mastercard network so at least I can get my purchases from those shitty American sites that don't accept anything else now. Looked into the manual of it because bpost's FAQ isn't very clear about what my login data for their online customer area now actually is. Not that their instruction manual was either.
I noticed in that manual that apparently the PIN code can't be changed (for "security reasons", totally not the alternative that probably they didn't want to implement it), and that requesting a forgotten PIN code can be done with as little as calling them up, and they'll then send the password - not a reset form, the password itself! IN THE FUCKING MAIL.
Because that's apparently how financial institutions manage their passwords. The fact that they know your password means that they're storing it in plain text, probably in a database with all the card numbers and CVC's next to it. Wouldn't that be a treasure trove for cybercriminals, I wonder? But YOU the customer can't change your password, because obviously YOU wouldn't be able to maintain a secure password, yet THEY are obviously the ones with all the security and should be the ones to take out of YOUR hands the responsibility to maintain YOUR OWN password.
Banking logic. I fucking love it.
As for their database.. I reckon that that's probably written in COBOL too. Because why wouldn't you.23 -
A ecom website which sales premium gold product from 50k to 170k INR.
database : mysql
all passwords and user ID's are saved in plain text.23 -
Fuck me, big fucking security flaw with a UK internet service provider, my head has gone through my desk and hit the floor it’s that bad.
 23
23 -
Worst legacy experience...
Called in by a client who had had a pen test on their website and it showed up many, many security holes. I was tasked with coming in and implementing the required fixes.
Site turned out to be Classic ASP built on an MS Access database. Due to the nature of the client, everything had to be done on their premises (kind of ironic but there you go). So I'm on-site trying to get access to code and server. My contact was *never* at her desk to approve anything. IT staff "worked" 11am to 3pm on a long day. The code itself was shite beyond belief.
The site was full of forms with no input validation, origin validation and no SQL injection checks. Sensitive data stored in plain text in cookies. Technical errors displayed on certain pages revealing site structure and even DB table names. Server configured to allow directory listing in file stores so that the public could see/access whatever they liked without any permission or authentication checks. I swear this was written by the child of some staff member. No company would have had the balls to charge for this.
Took me about 8 weeks to make and deploy the changes to client's satisfaction. Could have done it in 2 with some support from the actual people I was suppose to be helping!! But it was their money (well, my money as they were government funded!).1 -
You guys are pissed off whenver you see a mail with plain text password. And here I have clients who couldn't log in even after I shoved the raw and plain credentials up their arses.5
-
Buckle up kids, this one gets saucy.
At work, we have a stress test machine that trests tensile, puncture and breaking strength for different materials used (wood construction). It had a controller software update that was supposed to be installed. I was called into the office because the folks there were unable to install it, they told me the executable just crashed, and wanted me to take a look as I am the most tech-savvy person there.
I go to the computer and open up the firmware download folder. I see a couple folders, some random VBScript file, and Installation.txt. I open the TXT, and find the first round of bullshit.
"Do not run the installer executable directly as it will not work. Run install.vbs instead."
Now, excuse me for a moment, but what kind of dick-cheese-sniffing cockmonger has end users run VBScript files to install something in 2018?! Shame I didn't think of opening it up and examining it for myself to find out what that piece of boiled dogshit did.
I suspend my cringe and run it, and lo and behold, it installs. I open the program and am faced with entering a license key. I'm given the key by the folks at the office, but quickly conclude no ways of entering it work. I reboot the program and there is an autofilled key I didn't notice previously. Whatever, I think, and hit OK.
The program starts fine, and I try with the login they had previously used. Now it doesn't work for some reason. I try it several times to no avail. Then I check the network inspector and notice that when I hit login, no network activity happens in the program, so I conclude the check must be local against some database.
I browse to the program installation directory for clues. Then I see a folder called "Databases".
"This can't be this easy", I think to myself, expecting to find some kind of JSON or something inside that I can crawl for clues. I open the folder and find something much worse. Oh, so much worse.
I find <SOFTWARE NAME>.accdb in the folder. At this point cold sweat is already running down my back at the sheer thought of using Microsoft Access for any program, but curiosity takes over and I open it anyway.
I find the database for the entire program inside. I also notice at this point that I have read/write access to the database, another thing that sent my alarm bells ringing like St. Pauls cathedral. Then I notice a table called "tUser" in the left panel.
Fearing the worst, I click over and find... And you knew it was coming...
Usernames and passwords in plain text.
Not only that, they're all in the format "admin - admin", "user - user", "tester - tester".
I suspend my will to die, login to the program and re-add the account they used previously. I leave the office and inform the peeps that the program works as intended again.
I wish I was making this shit up, but I really am not. What is the fucking point of having a login system at all when your users can just open the database with a program that nowadays comes bundled with every Windows install and easily read the logins? It's not even like the data structure is confusing like minified JSON or something, it's literally a spreadsheet in a program that a trained monkey could read.
God bless them and Satan condemn the developers of this fuckawful program.8 -
My insurance company sending me the payment slip by post with my username and password to the online account for easy access. How sweet of them. 10/10 customer satisfaction.
I see your "Storing passwords in plain text". I raise you to "sending passwords via post in plain text". 17
17 -
So this just happened with my ISP, i have no words...
The fact you have my password in front of you in plain text is fucking terrifying and i know you do because i used to work for an ISP. 9
9 -
Boss hands over to me an old security audit report and tells me "Go through this and check if all the problems mentioned have been resolved". Quick glance through the report shows all expected issues - SQLi, plaintext transmission and storage etc. I tell him that I need access to the application both from admin and a user with restricted privileges.
He hands me the admin credentials and tells me, "After you login in, just go the "Users" tab. You'll find the profiles of all the users there. You can get the emails and passwords of any user you want from there."
I had to hold back a chuckle. There's nothing to verify. If they haven't resolved storing plain text passwords in the database (AND displaying it IN PLAIN TEXT in the website itself (which to my surprise wasn't mentioned in the audit)), they probably haven't even looked at the report.2 -
My school stores everyone's username and passwords (including admins) in plain text on a Windows 2007 server that they remote desktop into.8
-
!security
(Less a rant; more just annoyance)
The codebase at work has a public-facing admin login page. It isn't linked anywhere, so you must know the url to log in. It doesn't rate-limit you, or prevent attempts after `n` failures.
The passwords aren't stored in cleartext, thankfully. But reality isn't too much better: they're salted with an arbitrary string and MD5'd. The salt is pretty easy to guess. It's literally the company name + "Admin" 🙄
Admin passwords are also stored (hashed) in the seeds.rb file; fortunately on a private repo. (Depressingly, the database creds are stored in plain text in their own config file, but that's another project for another day.)
I'm going to rip out all of the authentication cruft and replace it with a proper bcrypt approach, temporary lockouts, rate limiting, and maybe with some clientside hashing, too, for added transport security.
But it's friday, so I must unfortunately wait. :<13 -
A colleague and I spent a month building a Shopify app that allows merchants to give customers store credit.
Since Shopify's API is so limited, we were forced to augment it's functionality with a Chrome extension.
Now before you go throwing full wine bottles at your screen because of how wrong and disgusting that is, note that Shopify's official documentation recommends 5 different extensions to augment functionality in their admin panel, so as gross as it is, it seems to be the Shopify way...
Today we got a reply from their review team. They won't accept the app because it requires a Chrome extension to work properly and that is a security risk.
Are you fucking kidding me? So I guess Shopify is exempt from their own security standards. Good to know.
Not to mention the plethora of published apps that require a staff account's username and password to be provided in plain text upon setup so it can spoof a login and subsequent requests to undocumented endpoints.
Fuck you and your "security standard" Shopify! -
Arglebargle.
I went to buy flowers for [redacted event] and gave the florist my CC info, number, and email for a receipt. He was a nice old man who loves what he does, and makes beautiful arrangements. But. He just emailed me all of my CC info, and asked what part of it was wrong. Twice. Emailed. Plain text. SMTP.
Guess who's requesting a replacement card?
😞13 -
One of my favourite, encryption puzzles is this:
ITuyVT93oUZtLKWyVT5iqPO3nTS0VUEbMKxtp2IyoD==
Answer is plain text string in english. Good luck, post solution in the comments!19 -
Today, for fun, I wrote prime number generation upto 1000 using pure single MySQL query.
No already created tables, no procedures, no variables. Just pure SQL using derived tables.
So does this mean that pure SQL statements do not have the halting problem?
Putting an EXPLAIN over the query I could see how MySQL guessed that the total number of calculations would be 1000*1000 even before executing the query in itself and this is amazing ♥️
I have attached a screenshot of the query and if you are curious, I have also left below the plain text.
PS this was a SQL problem in Hackerrank.
MySQL query:
select group_concat(primeNumber SEPARATOR '&') from
(select numberTable.number as primeNumber from
(select cast((concat(tens, units, hundreds)+1) as UNSIGNED) as number from
(select 0 as units union select 1 union select 2 union select 3 union select 4 union select 5 union select 6 union select 7 union select 8 union select 9) unitsTable,
(select 0 as tens union select 1 union select 2 union select 3 union select 4 union select 5 union select 6 union select 7 union select 8 union select 9) tensTable,
(select 0 as hundreds union select 1 union select 2 union select 3 union select 4 union select 5 union select 6 union select 7 union select 8 union select 9) hundredsTable order by number) numberTable
inner join
(select cast((concat(tens, units, hundreds)+1) as UNSIGNED) as divisor from
(select 0 as units union select 1 union select 2 union select 3 union select 4 union select 5 union select 6 union select 7 union select 8 union select 9) unitsTable,
(select 0 as tens union select 1 union select 2 union select 3 union select 4 union select 5 union select 6 union select 7 union select 8 union select 9) tensTable,
(select 0 as hundreds union select 1 union select 2 union select 3 union select 4 union select 5 union select 6 union select 7 union select 8 union select 9) hundredsTable order by divisor) divisorTable
on (divisorTable.divisor<=numberTable.number and divisorTable.divisor!=1)
where numberTable.number%divisorTable.divisor=0
group by numberTable.number having count(*)<=1 order by numberTable.number) resultTable; 9
9 -
What kind of cum gargling gerbil shelfer stores and transmits user passwords in plain text, as well as displays them in the clear, Everywhere!
This, alongside other numerous punishable by death, basic data and user handling flaws clearly indicate this fucking simpleton who is "more certified than you" clearly doesn't give a flying fuck about any kind of best practice that if the extra time was taken to implement, might not totally annihilate the company in lawsuits when several big companies gang up to shower rape us with lawsuits over data breaches.
Even better than that is the login fields don't even differentiate between uppercase or lowercase, I mean WHAT THE ACTUAL FUCK DO YOU SELF RIGHTEOUS IGNORANT CUNTS THINK IS GOING TO HAPPEN IN THIS SCENARIO?13 -
TL;DR I'm fucking sick and tired of Devs cutting corners on security! Things can't be simply hidden a bit; security needs to be integral to your entire process and solution. Please learn from my story and be one of the good guys!
As I mentioned before my company used plain text passwords in a legacy app (was not allowed to fix it) and that we finally moved away from it. A big win! However not the end of our issues.
Those Idiot still use hardcoded passwords in code. A practice that almost resulted in a leak of the DB admin password when we had to publish a repo for deployment purposes. Luckily I didn't search and there is something like BFG repo cleaner.
I have tried to remedy this by providing a nice library to handle all kinds of config (easy config injection) and a default json file that is always ignored by git. Although this helped a lot they still remain idiots.
The first project in another language and boom hardcoded password. Dev said I'll just remove before going live. First of all I don't believe him. Second of all I asked from history? "No a commit will be good enough..."
Last week we had to fix a leak of copyrighted contend.
How did this happen you ask? Well the secure upload field was not used because they thought that the normal one was good enough. "It's fine as long the URL to the file is not published. Besides now we can also use it to upload files that need to be published here"
This is so fucking stupid on so many levels. NEVER MIX SECURE AND INSECURE CONTENT it is confusing and hard to maintain. Hiding behind a URL that thousands of people have access to is also not going to work. We have the proof now...
Will they learn? Maybe for a short while but I remain sceptic. I hope a few DevrRanters do!7 -
Checked the GitKraken save files for fun (kind of a hobby) and oh well.... what a wonder:
They store your fucking GitHub access token in "plain text" in a hex file as you can see in the image.
I checked the token and it works. Wow.
Good job GitKraken ✔
That happens when you're closed source... 27
27 -
Best carrier choice: leaving the old company I worked for...
TLDR version: I yelled at owner/director to shove it..got layed off the next day. Never regreted that day!! EVER!!
Long version: I was asked to implement storing of CC numbers (yes, the whole lot) & their matchig CVC numbers..plain text, no encription.. company didn't even fulfilled standards to store last four digits.. so I yelled at the 'big boss' that he is crazy and that I won't do it.. Next day, I got handed a letter that said they have to lay me off due to lack of work and that my position is redundant & no other workplace for me.. Never been happier in my life!!
I wanted to quit for some time, due to crazy stuff they asked me to implement & how!? & toxic personel. I was called Hitler (& am actually proud of this!!) cuz I was work oriented & didn't kiss mrs.Director's ass.. I wasn't slacking like the rest of them did, so of course, I was the bad guy..
Anyhow, fast forward 6 months, got the best job ever & am now here for 5yrs+.7 -
I'm really close to just quitting coding all together. This job is sucking the life out of me. I've lost my interest in code and the idea that there are better jobs out there.
My "boss" who's not even really my boss but behaves like he is, is micromanaging my every tag, and is an information hog. He doesn't document, he doesn't tell me anything, I've been here six months and still don't know half of what I need to know to do my job properly!
I'm expected to implement a new responsive design, but we don't have design specifications.
Cool, you'd think, new ideas, complete overhaul! Let's get a good foundation in bootstrap going!
WRONG! It needs to fit in with the old, fuck- ugly pre 2000 design.
Not because of any design constraints in particular, but because HE wants it that way. You know what was fucking trendy in 2000? Tables. Tables fucking everywhere. YOU KNOW WHAT TABLES ARE NOT? RESPONSIVE YOU FUCKING ICE LOLLY CHEWER!
We have no development timeline, no process management, no fucking project management. THE FUCKING PASSWORDS WERE STILL STORED IN PLAIN TEXT UNTIL LAST MONTH YOU IRRESPONSIBLE BANANA DEEPTHROATER! 😤😤😤😤😤😤
I'm doing my best here to get something resembling the old page, but there needs to be some fucking compromise! We are in fucking 2017, let's work with Bootstrap instead of against it, how about that you fucking bald cactus!
I know enough about UI to know that the way we're going, this is just going to be another unusable fucking clusterfuck.
YOU KNOW THE BEST FUCKING PART? I'M A FUCKING BACKEND DEV AND I WAS HIRED AS SUCH! GIVE ME A DESIGN TEMPLATE AND I'LL DO MY BEST TO IMPLEMENT IT, BUT FUCK YOU FOR EXPECTING FRONT END LEVEL DESIGN KNOWLEDGE YOU DUMB FUCKING SPAGHETTI!14 -
when you work for a place that has plain text passwords in the db. lol
I asked head of department if he knew what salting/hashing passwords was and he said no.... is this real life?19 -
We recently took over development of an app. Upon inspection the API had no security, and passwords were stored in plain text. While the manager was slightly concerned, it wasn't a big deal....
That was until, using only a browser, I found the bosses account and personal email address.
Minutes later I was in his gmail, Facebook and credit cards account.
Improving security is now concern #1, and my boss is "suffering" 2 factor authy on everything.7 -
What kind of fucking application sends me my an e-mail with my password in plain text when I sign-up!?7
-
The gym I go to has an app for user's to scan a QR code when they arrive and it has multiple HUGE issues.
This app shows the credit card info used for the direct debit without anything being redacted.
When the gym is signing up someone they give them a password so they can login, not too bad except the password is always the person's first name with the first letter capitalised.
This gets worse when you figure out that their is no way to change the password given to you AT ALL.
And just to top it all off, when you click the "Forgot Password" link on the login screen, the app just sends you an email with your password (your first name) in plain text.
The app also doesn't log you out or notify you if your login is used on a different device.
So I have tested this with 2 of my friends that go to the same gym and, with only knowing their email and first name (which I could have gotten from their email if I didn't know them), I can get into their app and see their credit card info without them being any the wiser.9 -
Storing passwords in plain text.
To be fair, it was a feature requested by the client, but still...
At least encrypt it man.6 -
Unencrypted, plain text passwords stored in SQL, from lowest role all the way up through Admin. In the same system, they had a "backdoor" password that would log in any user...
-
I've already ranted about this before, so I will summarize, but users passwords would be placed in plain text at the bottom of a webpage if you interacted with the page in a certain way. This page did not require a login, so user passwords were basically public. Gg.1
-
Here's a silly side project I've been working on just for fun:
https://soundofco.de/
It "programmatically" creates sound from code (or plain text) on GitHub. I wouldn't call it music, because it sounds kind of horrible almost all of the time :D It's very simple: The length of a line defines the note to be played. Really just a nerdy bit of fun.
Unfortunately I have absolutely zero knowledge in music theory and I have no idea how to make the resulting sounds more pleasant or even melodic. If you're interested in making this better or helping out with feedback, you can find the project at https://github.com/dneustadt/...
Also feel free to share if you find anything on GitHub that makes for some decent sounds :D (I doubt it)12 -
Just registered as a customer at an online store, and the fuckers sent me a confirmation email where my password was written in plain text. Why?!5
-
My school just tried to hinder my revision for finals now. They've denied me access just today of SSHing into my home computer. Vim & a filesystem is soo much better than pen and paper.
So I went up to the sysadmin about this. His response: "We're not allowing it any more". That's it - no reason. Now let's just hope that the sysadmin was dumb enough to only block port 22, not my IP address, so I can just pick another port to expose at home. To be honest, I was surprised that he even knew what SSH was. I mean, sure, they're hired as sysadmins, so they should probably know that stuff, but the sysadmins in my school are fucking brain dead.
For one, they used to block Google, and every other HTTPS site on their WiFi network because of an invalid certificate. Now it's even more difficult to access google as you need to know the proxy settings.
They switched over to forcing me to remote desktop to access my files at home, instead of the old, faster, better shared web folder (Windows server 2012 please help).
But the worst of it includes apparently having no password on their SQL server, STORING FUCKING PASSWORDS IN PLAIN TEXT allowing someone to hijack my session, and just leaving a file unprotected with a shit load of people's names, parents, and home addresses. That's some super sketchy illegal shit.
So if you sysadmins happen to be reading this on devRant, INSTEAD OF WASTING YOUR FUCKING TIME BLOCKING MORE WEBSITES THAN THEIR ARE LIVING HUMANS, HOW ABOUT TRY UPPING YOUR SECURITY, PASSWORDS LIKE "", "", and "gryph0n" ARE SHIT - MAKE IT BETTER SO US STUDENTS CAN ACTUALLY BROWSE MORE FREELY - I THINK I WANT TO PASS, NOT HAVE EVERY OTHER THING BLOCKED.
Thankfully I'm leaving this school in 3 weeks after my last exam. Sure, I could stay on with this "highly reputable" school, but I don't want to be fucking lied to about computer studies, I don't want to have to workaround your shitty methods of blocking. As far as I can tell, half of the reputation is from cheating. The students and sysadmins shouldn't have to have an arms race between circumventing restrictions and blocking those circumventions. Just make your shit work for once.
**On second thought, actually keep it like that. Most of the people I see in the school are c***s anyway - they deserve to have half of everything they try to do censored. I won't be around to care soon.**undefined arms race fuck sysadmin ssh why can't you just have any fucking sanity school windows server security2 -
I hate that trend of making things more lax in terms of implementation quality while writing it off with a simple but stupid "oh computers are faster now, users have the RAM, yadda yadda". Yeah but back in a day things were actually running pretty damn fast in comparison while doing it on hardware that is totally potato in comparison to what's used now. This trend eats away ANY gains we get in terms of performance with upgrades. It deprecated the whole notion of netbooks (and I kinda liked them for casual stuff), since now every goddamn one-page blog costs you from several megabytes and up to tens of megabytes of JS alone and lots of unnecessary computations. Like dude, you've brought in a whole Angular to render some text and three buttons, and now your crappy blog is chewing on 500 MB of my RAM for whatever reason.
Also, Electron apps. Hate them. Whoever invented the concept, deserves their own warm spot in Hell. You're doing the same you would've done more efficiently in Qt or whatever there is. Qt actually takes care of a lot of stuff for you, so it doesn't look like you'll be slowed down by choosing it over Electron. Like yeah, web version will share some code with your desktop solution but you're the whole reason I'm considering your competitor's lack of Electron a huge advantage over you even if they lack in features.
Same can be said pretty much about everything that tries to be more than it should, really. IDEs, for example, are cancerous. You can do 90%+ of what you intended to do in IDE using plain Vim with *zero* plugins, and it will also result in less strain on your hands.
People have just unlearned the concept of conscious consumption, it seems.23 -
Let me ask you something: why do most people prefer ms word over a simple plain text document when writing a manual. Use Markdown!
You can search and index it (grep, ack, etc)
You don't waste time formatting it.
It's portable over OS.
You only need a simple text editor.
You can export it to other formats, like PDF to print it!
You can use a version control system to version it.
Please! stop using those other formats. Make everyone's life easier.
Same applies when sharing tables. Simple CSV files are enough most of the time.
Thank you!!?!18 -
I could bitch about XSLT again, as that was certainly painful, but that’s less about learning a skill and more about understanding someone else’s mental diarrhea, so let me pick something else.
My most painful learning experience was probably pointers, but not pointers in the usual sense of `char *ptr` in C and how they’re totally confusing at first. I mean, it was that too, but in addition it was how I had absolutely none of the background needed to understand them, not having any learning material (nor guidance), nor even a typical compiler to tell me what i was doing wrong — and on top of all of that, only being able to run code on a device that would crash/halt/freak out whenever i made a mistake. It was an absolute nightmare.
Here’s the story:
Someone gave me the game RACE for my TI-83 calculator, but it turned out to be an unlocked version, which means I could edit it and see the code. I discovered this later on by accident while trying to play it during class, and when I looked at it, all I saw was incomprehensible garbage. I closed it, and the game no longer worked. Looking back I must have changed something, but then I thought it was just magic. It took me a long time to get curious enough to look at it again.
But in the meantime, I ended up played with these “programs” a little, and made some really simple ones, and later some somewhat complex ones. So the next time I opened RACE again I kind of understood what it was doing.
Moving on, I spent a year learning TI-Basic, and eventually reached the limit of what it could do. Along the way, I learned that all of the really amazing games/utilities that were incredibly fast, had greyscale graphics, lowercase text, no runtime indicator, etc. were written in “Assembly,” so naturally I wanted to use that, too.
I had no idea what it was, but it was the obvious next step for me, so I started teaching myself. It was z80 Assembly, and there was practically no documents, resources, nothing helpful online.
I found the specs, and a few terrible docs and other sources, but with only one year of programming experience, I didn’t really understand what they were telling me. This was before stackoverflow, etc., too, so what little help I found was mostly from forum posts, IRC (mostly got ignored or made fun of), and reading other people’s source when I could find it. And usually that was less than clear.
And here’s where we dive into the specifics. Starting with so little experience, and in TI-Basic of all things, meant I had zero understanding of pointers, memory and addresses, the stack, heap, data structures, interrupts, clocks, etc. I had mastered everything TI-Basic offered, which astoundingly included arrays and matrices (six of each), but it hid everything else except basic logic and flow control. (No, there weren’t even functions; it has labels and goto.) It has 27 numeric variables (A-Z and theta, can store either float or complex numbers), 8 Lists (numeric arrays), 6 matricies (2d numeric arrays), 10 strings, and a few other things like “equations” and literal bitmap pictures.
Soo… I went from knowing only that to learning pointers. And pointer math. And data structures. And pointers to pointers, and the stack, and function calls, and all that goodness. And remember, I was learning and writing all of this in plain Assembly, in notepad (or on paper at school), not in C or C++ with a teacher, a textbook, SO, and an intelligent compiler with its incredibly helpful type checking and warnings. Just raw trial and error. I learned what I could from whatever cryptic sources I could find (and understand) online, and applied it.
But actually using what I learned? If a pointer was wrong, it resulted in unexpected behavior, memory corruption, freezes, etc. I didn’t have a debugger, an emulator, etc. I had notepad, the barebones compiler, and my calculator.
Also, iterating meant changing my code, recompiling, factory resetting my calculator (removing the battery for 30+ sec) because bugs usually froze it or corrupted something, then transferring the new program over, and finally running it. It was soo slowwwww. But I made steady progress.
Painful learning experience? Check.
Pointer hell? Absolutely.4 -
me: the source code is currently store on GitHub and we use GitHub Actions after each updates to compile your code into binary before deploying to your servers
client: storing source code on GitHub (external server) is insecure and breaks compliance
me: so i guess you will need to have a copy of the source code on all your servers and build them directly there (too cheap to have a separate build server) instead of using GitHub Actions
client: yeah
me: keep in mind that all your certificates and tokens are going to be store as plain text in all your servers so if a hacker gain access to anyone of your servers, they will have access to everything.
client: yeah, this is in compliance to our security policy3 -
Things that give me chills early in the morning. A password reset email that contains my password in plain text.
Seriously! 🤦♂️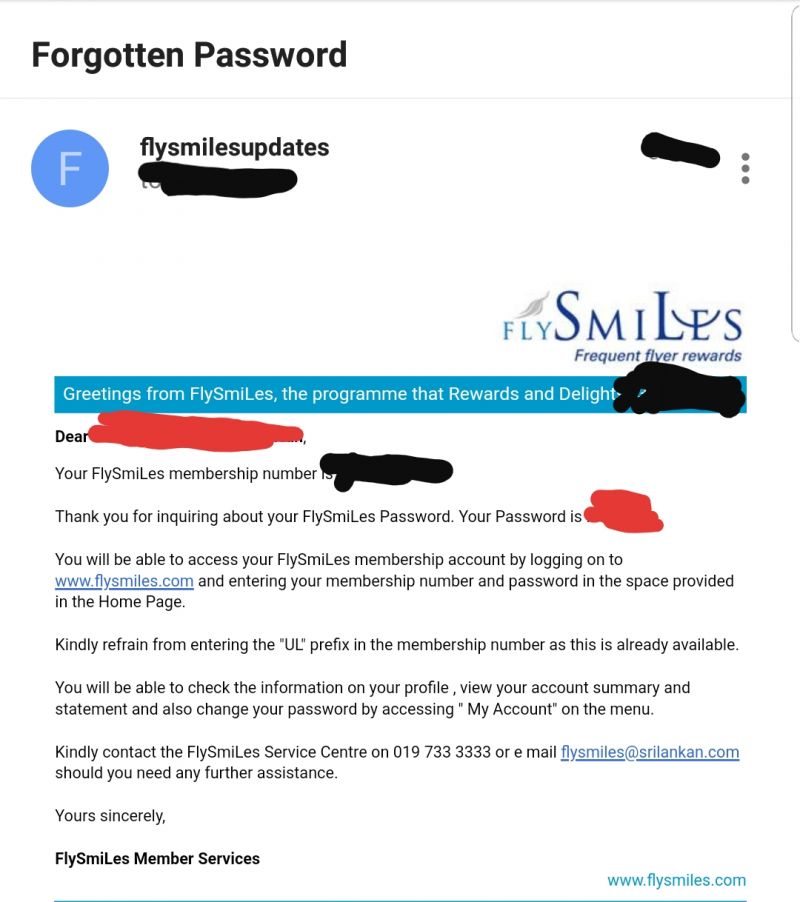 1
1 -
I used to work in a small agency that did websites and Phonegap apps, and the senior developer was awful.
He had over a decade of experience, but it was the same year of experience over and over again. His PHP was full of bad practices:
- He'd never used an MVC framework at all, and was resistant to the idea, claiming he was too busy. Instead he did everything as PHP pages
- He didn't know how to use includes, and would instead duplicate the database connection settings. In EVERY SINGLE FILE.
- He routinely stored passwords in plain text until I pretty much forced him to use the new PHP password hashing API
- He sent login details as query strings in a GET request
- He couldn't use version control, and he couldn't deploy applications using anything other than FTP4 -
Stop sending passwords in plain text via email. Just stop already. If you don't know how to implement a secure alternative, hire a fucking consultancy to assist you.
Fuck. The next time I purchase from you and I get my password in plain text anywhere, I'm immediately demanding a refund and taking my money elsewhere.
Just fucking stop.13 -
When your client wants you to store password in plain text and it makes your life easier but it still feels really wrong12
-
This is fucking bad. I just stumbled across a database online, unencrypted plain text containing ALL details of thousands of students at my university. Full names, ID number (SSN), student numbers, address, family info, medical aid info, physical fitness reports
What do I do? I was not on any VPN or proxy when I accessed it19 -
Biggest GTFO moment of the year;
While applying for colleges, I created an account with a username and variant of my usual password (I know, bad move, sorry). I came back to finish the application but had forgotten what variant I had used. So I clicked the forgot password button and got an email with...
MY PASSWORD IN IT!!!!
Plain text password! Just as part of the email! WTF do these people think they are doing?!?!
I immediately changed my password to a random string and deleted my account, so hopefully when someone gets into this database my stuff with be overwritten... stupid programmers...7 -
Client stores all user accounts in a publicly accessible google spreadsheet in case the user forgets their login. It includes user name, plain text password, and just in case, the hashed password....
 6
6 -
I forgot my password to [SITE]. Of course, I click "forgot password", and enter my email, which I did remember. Fairly routine "ah shit we have a problem" steps.
Now, it takes a second. This is to be expected. So I'm not worried. I then get the email and...
Now, you will notice that I redacted some information, like the company name, email, and my PLAIN TEXT PASSWORD, and my name.
I would like to note that this isn't a small, very local company that's new (even then it'd be unacceptable), but this is a multinational, multimillion dollar company.
How'd someone fuck up THIS badly? 13
13 -
TL;DR: At a house party, on my Phone, via shitty German mobile network using the GitLab website's plain text editor. Thanks to CI/CD my changes to the code were easily tested and deployed to the server.
It was for a college project and someone had a bug in his 600+ lines function that was nested like hell. At least 7 levels deep. Told him before I went to that party it's probably a redefined counter variable but he wouldn't have it as he was sure it was an error with the business logic. Told him to simplify the code then but he wouldn't do that either because "the code/logic is too complex to be simplified"... Yeah... what a dipshit...
Nonetheless I went to the party and He kept debugging. At some point he called me and asked me to help him the following day. Knowing that the code had to be fixed anyways I agreed.
I also knew I wouldn't be much of a help the next day due to side effects of the party, so I tried looking at this shitshow of a function on my phone. Oh did I mention it was PHP, yet? Yeah... About 30 minutes and a beer later I found the bug and of course it was a redefined counter variable... My respect for him as a dev was already crumbling but it died completely during that evening2 -
The Hungarian public transport company launched an online shop (created by T-Systems), which was clearly rushed. Within the first days people found out that you could modify the headers and buy tickets for whatever price you set, and you could login as anyone else without knowing their password. And they sent out password reminders in plain text in non-encrypted emails. People reported these to the company which claims to have fixed the problems.
Instead of being ashamed of themselves now they're suing those who pointed out the flaws. Fucking dicks, if anyone they should be sued for treating confidential user data (such as national ID numbers) like idiots.3 -
A Bank Account Number is like a public encryption key. Any random person needs it to send me money. Why does it seem like banks treat it as a secret or even use it to confirm my identity? It's literally printed in plain text on every check.2
-
A well known, big company in my country just sent me my password in plain text upon registering.
These devs actually got paid to do this...6 -
Chrome, Firefox, and yes even you Opera, Falkon, Midori and Luakit. We need to talk, and all readers should grab a seat and prepare for some reality checks when their favorite web browsers are in this list.
I've tried literally all of them, in search for a lightweight (read: not ridiculously bloated) web browser. None of them fit the bill.
Yes Midori, you get a couple of bonus points for being the most lightweight. Luakit however.. as much as I like vim in my terminal, I do not want it in a graphical application. Not to mention that just like all the others you just use webkit2gtk, and therefore are just as bloated as all the others. Lightweight my ass! But programmable with Lua, woo! Not like Selenium, Chrome headless, ... does that for any browser. And that's it for the unique features as far as I'm concerned. One is slow, single-threaded and lightweight-ish (Midori) and another has vim keybindings in an application that shouldn't (Luakit).
Pretty much all of them use webkit2gtk as their engine, and pretty much all of them launch a separate process for each tab. People say this is more secure, but I have serious doubts about that. You're still running all these processes as the same user, and they all have full access to the X server they run under (this is also a criticism against user separation on a single X session in general). The only thing it protects against is a website crashing the browser, where only that tab and its process would go down. Which.. you know.. should a webpage even be able to do that?
But what annoys me the most is the sheer amount of memory that all of these take. With all due respect all of you browsers, I am not quite prepared to give 8 fucking gigabytes - half the memory in this whole box! - just for a dozen or so tabs. I shouldn't have to move my web browser to another lesser used 16GB box, just to prevent this one from going into fucking swap from a dozen tabs. And before someone has a go at the add-ons, there's 4 installed and that's it. None of them are even close to this complete and utter memory clusterfuck. It's the process separation. Each process consumes half a GB of memory, and there's around a dozen of them in a usual browsing session. THAT is the real problem. And I want to get rid of it.
Browsers are at their pinnacle of fucked up in my opinion, literally to the point where I'm seriously considering elinks. Being a sysadmin, I already live my daily life in terminals anyway. As such I also do have resources. But because of that I also associate every process with its cost to run it, in terms of resources required. Web browsers are easily at the top of the list.
I want to put 8GB into perspective. You can store nearly 2 entire DVD movies in that memory. However media players used to play them (such as SMPlayer) obviously don't do that. They use 60-80MB on average to play the whole movie. They also require far less processing power than YouTube in a web browser does, even when you download that exact same video with youtube-dl (either streamed within the media player or externally). That is what an application should be.
Let's talk a bit about these "complicated" websites as well. I hate to break it to you framework web devs, but you're a dime a dozen. The competition is high between web devs for that exact reason. And websites are not complicated. The document itself is plain old HTML, yes even if your framework converts to it in the background. That's the skeleton of your document, where I would draw a parallel with documents in office suites that are more or less written in XML. CSS.. oh yes, markup. Embolden that shit, yes please! And JavaScript.. oh yes, that pile of shit that's been designed in half a day, and has a framework called fucking isEven (which does exactly what it says on the tin, modulo 2 be damned). Fancy some macros in your text editor? Yes, same shit, different pile.
Imagine your text editor being as bloated as a web browser. Imagine it being prone to crashing tabs like a web browser. Imagine it being so ridiculously slow to get anything done in your productivity suite. But it's just the usual with web browsers, isn't it? Maybe Gopher wasn't such a bad idea after all... Oh and give me another update where I have to restart the browser when I commit the heinous act of opening another tab, just because you had to update your fucking CA certs again. Yes please!19 -
So we have an API that my team is supposed send messages to in a fire and forget kind of style.
We are dependent on it. If it fails there is some annoying manual labor involved to clean that mess up. (If it even can be cleaned up, as sometimes it is also time-sensitive.)
Yet once in a while, that endpoint just crashes by letting the request vanish. No response, no error, nothing, it is just gone.
Digging through the log files of that API nothing pops up. Yet then I realize the size of the log files. About ~30GB on good old plain text log files.
It turns out that that API has taken the LOG EVERYTHING approach so much too heart that it logs to the point of its own death.
Is circular logging such a bleeding edge technology? It's not like there are external solutions for it like loggly or kibana. But oh, one might have to pay for them. Just dump it to the disk :/
This is again a combination of developers thinking "I don't need to care about space! It's cheap!" and managers thinking "100 GB should be enough for that server cluster. Let's restrict its HDD to 100GB, save some money!"
And then, here I stand trying to keep my sanity :/1 -
When I left school I decided to apply for a junior dev role. I received a call back later that day and they tried to sell me access to some course with the promise of a job afterwords. They gave me a website to visit to find more information.
I Googled the company and found that it was as I suspected a scam and that they had been praying on the jobless for sometime.
So, I played around on the site they told me to visit for a while and found a rather simple SQLI. I managed to pull the admin email/password (which they stored as plain text) the email address belonged to a Gmail account.
I tried the password for the Gmail account turns out the account belongs to the person running the scam. I find an email from the hosting account and you guessed it the password was the same.
I pulled the site down and replaced it with a picture of the person running the scam along with his name and the words "I'm a dirty scammer".
Then I sent all the info to the police (he'd been running a few others scams too) not sure what that lead to I didn't hear anything back.1 -
I used vs code for a solid 3 years, but my friend has been using notepad. No color coding. No dark theme. No auto commenting. No suggestions. Just plain black text in a white box.
Like a psychopath.5 -
Government website sends me my username and password over plain text email after I sign up...
WHAT WHY WHO LET THIS HAPPEN6 -
First of all how the fuck you are able to tell that MY password is one of many that have been stolen? How you are able to get those stolen passwords AND WHY YOU ARE EVEN ABLE TO COMPARE THEM?! Are you storing as plain text or just randomly salt all stolen passwords and chceck if they are in your base?
Now that is an INSTAdelete. 8
8 -
So I was logging into google today and my password is very long so I often make mistakes while typing it so I went to inspect element to change input type to text so that I can check the password and I see that Firefox is storing my password already as plain text. Wtf Firefox???
 6
6 -
So our teacher just has us sign up for a learning site called Gizmos with a ton of students information. A lot of students forgot their password as always and some didn't register with an email so I expected the teacher to reset them..
Then the teacher had students come up to the front of the f****** class and SHOWED THEM THEIR PASSWORD IN PLAIN TEXT. WHAT THE HELL3 -
Two days ago, I was solving a coding challenge on hackerank, I was so frustrated I couldn't get one year to pass, I tried c++, python, Golang, same shit, still that same test...I couldn't sleep, I close my eyes, I see this in my sleep, I go back to my keyboard, 4am, I am still on this challenge, 6am, nothing, then I decided to go have breakfast and hang out with a friend, then while hanging out he said "don't finish the pizza, that's my lunch" immediately it clicked in my head that I was missing a logic of less than zero as it was stated as a constraint, I immediately went back home and now all test cases passed....guess what, I now have malaria from not sleeping under the net 😭😭...
P.S: I am Nigerian tho, mosquitoes are a thing5 -
Me and my developer friend worked with my ex-colleague with this fitness directory website because he promised to give us {{ thisAmount }} upon the {{ completionDate }}.
He was my friend and I trusted him.
It took me weeks of sleepless nights building the project. I had a full-time job that time, and I worked on the project during evenings. All went well, and as we reach the {{ completionDate }}, the demo site is already up and running.
A week before the {{ completionDate }}, he hired his new wife as the COO of the startup. It was cool, she keep noticing things on the site which shouldn't be there, and keeps on suggesting sections that has to be there. I was okay with it, until I realized that we are already a month late with the deadline.
Every single hour, I get a message from them like, "it's not working", "when can you finish this feature?", blah blah blah.. and so on.
I got frustrated.
"I want my fucking life back", I told them. No one cared about the {{ completionDate }}, the sleepless zombies they are working with and our payment. They keep on coming up with this "amazing" ass features, and now they are not paying because they said "it's not complete".
Idiot enough to trust a friend. I was unprotected, there was no legal-binding document that states their obligation to pay.
My dev friend and I handed over the project to this web development company which they prefer, and kept a backdoor on the application.
I kind of moved on with the payment issue after a month. But without their knowledge, I kept an eye on the progress and made sure that I still have the access to their server, DNS, etc..
BUT when they announced the official launch on social media, I realized that I was on the wrong train the whole time.
They switched to a different server.
They thanked all the people involved with the project via social media, EXCEPT me and my coding partner who originally built the site from ground up. A little "thank you" note from them will make us feel a little better. But, never happened.
I checked up the site and it was rewritten from originally Laravel 5 to CodeIgniter 1. That is like shifting from a luxury yacht where you can bang some hot chicks, to a row boat where your left hand is holding the paddle whilst your right hand is wanking yourself.
I almost ran out of bullets.
Luckily, CodeIgniter 1 was prone to SQLi by default.
I was able to get the administrator password in plain text and fucked with their data. But that didn't make me feel better because other people's info are involved.
So, I looked for something else to screw with. What I found? A message with the credit card details.
Finally, a chance to do something good for humanity. I just donated a few thousand dollars to different charity websites.2 -
I use a library and it gives me some strange error message. No problemo, just file an issue on GitHub asking the maintainer if I'm plain stupid or the lib actually has a flaw. As it was a question, I have not posted a dump and all the shit.
Maintainer responds with a snarky comment about his crystal ball being broken and I have to submit a log, a dump, debug information and a bunch of other stuff.
Well, what choice do I have, I collect all the requested information, create a wall of text comment, all nicely formatted.
And the issue ends here. Myths say, the maintainer got asked to join Elvis on Mars.
I mean, why do you ask all the shit from me in a unprofessional manner just to stop answering? Just say "I have no clue why it behaves like this" and I know whats playin. But that's just ... sad.5 -
During an internship, I spent some time automating reports with VBA. Basically, imagine a few big excel sheets with 1000 formulas and a few thousand lines of VBA.
One of the reports was handed directly to the bosses boss of our boss. After 4 weeks, he came to me and asked why the table entry in row 23 or so was always 84. Well.. I dont know. This data is automatically calculated / retrieved from a database. Went and checked, already sweating, and found that
THE OTHER INTERN COULDNT FIX A FORMULA SO HE OVERRODE IT WITH PLAIN TEXT. WITH A FUCKING PLAIN VALUE OF 84. A FOOKING EXCEL SHEET WITH A THOUSAND DIFFERENT FORMULAS AND LOTS OF VBA. Needless to say, everything is password protected now.1 -
Primarily IntelliJ IDEs.
I'm using IDEA for Rust & Kotlin, PHPStorm, Datagrip (DB), and sometimes PyCharm CE.
IDEs can feel a bit dirty with how heavy they are, and the lack of customization/control. But at the end of the day there's just nothing that can measure up against IntelliJ's inspections, integrations and project indexing.
My ideal product would be one universal IntelliJ IDE, but combined with the openness of VSCode/Atom, having everything transparently configurable through stylesheets and scripts.
As an editor though.... I use Vim for LaTeX, Markdown, plain text and Haskell code... but not so much for other programming languages.
Vim was my first editor when I moved from C64 to PC development 25 years ago, and while you get used to balancing keybind vimgolfing with being actually productive, i've always found maintaining plugins and profiles too cumbersome -- the reality is that Vim is an awesome TEXT editor, but it's really awful as a CODE editor out of the box.
When you want to try out a new programming language, you don't want to have to mess around with your Vimrc and Vundle and YCM for half a day just so you can comfortably write "Hello World" in Rust or Elixir... you just want to click one install button, press F10 to compile and see if it flies.
Oh, and I use Xed a lot for quickly editing files... because it's the default GUI editor on Mint desktops, and it's quite good at being a basic notepad.1 -
New way of storing passwords "securely":
1. Open word and write your passwords in plain text
2. Save that word document and open it in notepad
3. Delete a random character but remember which one and in which position & save
Now the document won't be accessible with word and to fix it you have to put back the character you deleted.10 -
Registering a new account for microsoft teams:
`Your password cannot contain a space, &# characters combination, or the following characters: < >`
Are they storing the passwords in plain text? Are they not sanitizing the input? Why the fuck would they care if I put motherfucking emojis in my password? What the fuck are you doing to the passwords, Microsoft? TELL ME.4 -
So there’s this SOAP api I have to use (not by choice, and not the only one i have to use) that returns a bunch of XML nodes to confirm the data sent made it and checks out - pretty standard stuff yea.
Now every once in a while it doesn’t respond (as far as I could tell) so today I wrapped a debug around the soap call, error handler and responses and threw a bunch of messages it’s way to try and force it not to respond in order to be able to put some decent error handling in place.
Well it wouldn’t fail.
100 messages .... all responses good
100 more.... all responses good
And then 100 more.... all respond with “x”, plain text not XML as expected!
Wtf is this shit!!!!!rant dirty dirty soap going insane i give up unexpected undocumented responses it’s not me... yay soap6 -
So here I am reinventing the wheel making an HTTP server in C.
Finished implementing HTTP/1.1 and WebSockets support and now I find out the current thingy is HTTP/2.
Well that's fine, I'll add support for that later. In fact I kinda dig it since it uses binary conventions instead of plain text ones.
I dig a little bit and find out there already is an HTTP/3 going around which uses UDP.
Why me.5 -
Today my fellow @EaZyCode found out a local Hosting Provider has a massive security breach.
He wrote an Plugin for Minecraft with an own file explorer and the ability to execute runtime commands over it.
We discovered that this specific hosting provider stores the ftp passwords one level above the FTP-Root. In FUCKING PLAIN TEXT! AND THE MYSQL PASSWORD TOO! And even more shit is stored there ready to be viewed by intelligent people...
It's one of the fucking biggest Hosting provider Germanys!
But, because EaZyCode has such a great mind and always find such bugs, I give him the title "Providers Endboss" today, he has earned it.
Loving you ❤️
Edit: we used SendMail with runtime commands and sended too many empty Spammails (regret noting)18 -
Creating username / password first time - checked
Storing password in plaintext - checked
Messaging password in plain text after a password change - whaaattt???? 7
7 -
I found a tool that saves passwords in plain text. Our client didn’t involve us in the decision process. They bought it. You did this to yourself... #1995 #fuckit1
-
Saw a classmate returning an plain text password from a function to try to push it in a JSON file for an API we have to build for class.
I try to correct him and show him a few things that are better practices and for security, I get yelled at and called a know-it-all for trying to help... I'm so done with people -.-4 -
Have you ever wanted to open links with firefox from within termux?
$ cat firefox.sh
d=$@
am start -a android.intent.action.WEB_SEARCH --activity-clear-task -t text/plain -d "$d" org.mozilla.firefox/org.mozilla.gecko.BrowserApp
thank me later5 -
I freelanced for a startup one time, and found out they had ten of thousands of records stored in their DB about dental patients, inducing name, address, social security #, some medical history, etc. All in plain text. Worst part is they hired me after a 20 min phone call, and didn't even sign a NDA!
Makes me paranoid to use the Internet knowing what some of these companies do.2 -
Following on from my school having terrible passwords. Turns out they stored all our passwords in plain text somewhere - so some script kiddie (Do you even need to be a script kiddie to find this - probably not, but the guy who did this was a script kiddie) could just remote log me out twice, log in as me, be a twat, and have a conversation in Notepad.
 1
1 -
Oh boy, this is gonna be good:
TL;DR: Digital bailiffs are vulnerable as fuck
So, apparently some debt has come back haunting me, it's a somewhat hefty clai and for the average employee this means a lot, it means a lot to me as well but currently things are looking better so i can pay it jsut like that. However, and this is where it's gonna get good:
The Bailiff sent their first contact by mail, on my company address instead of my personal one (its's important since the debt is on a personal record, not company's) but okay, whatever. So they send me a copy of their court appeal, claiming that "according to our data, you are debtor of this debt". with a URL to their portal with a USERNAME and a PASSWORD in cleartext to the message.
Okay, i thought we were passed sending creds in plaintext to people and use tokenized URL's for initiating a login (siilar to email verification links) but okay! Let's pretend we're a dumbfuck average joe sweating already from the bailiff claims and sweating already by attempting to use the computer for something useful instead of just social media junk, vidya and porn.
So i click on the link (of course with noscript and network graph enabled and general security precautions) and UHOH, already a first red flag: The link redirects to a plain http site with NOT username and password: But other fields called OGM and dossiernumer AND it requires you to fill in your age???
Filling in the received username and password obviously does not work and when inspecting the page... oh boy!
This is a clusterfuck of javascript files that do horrible things, i'm no expert in frontend but nothing from the homebrewn stuff i inspect seems to be proper coding... Okay... Anyways, we keep pretending we're dumbasses and let's move on.
I ask for the seemingly "new" credentials and i receive new credentials again, no tokenized URL. okay.
Now Once i log in i get a horrible looking screen still made in the 90's or early 2000's which just contains: the claimaint, a pie chart in big red for amount unpaid, a box which allows you to write an - i suspect unsanitized - text block input field and... NO DATA! The bailiff STILL cannot show what the documents are as evidence for the claim!
Now we stop being the pretending dumbassery and inspect what's going on: A 'customer portal' that does not redirect to a secure webpage, credentials in plaintext and not even working, and the portal seems to have various calls to various domains i hardly seem to think they can be associated with bailiff operations, but more marketing and such... The portal does not show any of the - required by law - data supporting the claim, and it contains nothing in the user interface showing as such.
The portal is being developed by some company claiming to be "specialized in bailiff software" and oh boy oh boy..they're fucked because...
The GDPR requirements.. .they comply to none of them. And there is no way to request support nor to file a complaint nor to request access to the actual data. No DPO, no dedicated email addresses, nothing.
But this is really the ham: The amount on their portal as claimed debt is completely different from the one they came for today, for the sae benefactor! In Belgium, this is considered illegal and is reason enough to completely make the claim void. the siple reason is that it's unjust for the debtor to assess which amount he has to pay, and obviously bailiffs want to make the people pay the highest amount.
So, i sent the bailiff a business proposal to hire me as an expert to tackle these issues and even sent him a commercial bonus of a reduction of my consultancy fees with the amount of the bailiff claim! Not being sneery or angry, but a polite constructive proposal (which will be entirely to my benefit)
So, basically what i want to say is, when life gives you lemons, use your brain and start making lemonade, and with the rest create fertilizer and whatnot and sent it to the lemonthrower, and make him drink it and tell to you it was "yummy yummy i got my own lemons in my tummy"
So, instead of ranting and being angry and such... i simply sent an email to the bailiff, pointing out various issues (the ones6 -
This is the last part of the series
(3 of 3) Credentials everywhere; like literally.
I worked for a company that made an authentication system. In a way it was ahead of it's time as it was an attempt at single sign on before we had industry standards but it was not something that had not been done before.
This security system targeted 3rd party websites. Here is where it went wrong. There was a "save" implementation where users where redirected to the authentication system and back.
However for fear of being to hard to implement they made a second method that simply required the third party site to put up a login form on their site and push the input on to the endpoint of the authentication system. This method was provided with sample code and the only solution that was ever pushed.
So users where trained to leave their credentials wherever they saw the products logo; awesome candidates for phishing. Most of the sites didn't have TLS/SSL. And the system stored the password as pain text right next to the email and birth date making the incompetence complete.
The reason for plain text password was so people could recover there password. Like just call the company convincingly frustrated and you can get them to send you the password.1 -
I promised a friend to have a look over his dads website to add a small blog. No big deal, I've got it on my drive, can reuse it just need to adapt it to the environment.
I take a look at what I'm working with and I see the most terrifying piece of "Please, take my data" code I could possibly imagine (And I've seen passwords, in plain text in a script tag). I quote "function queryDB(mode, val) {
var query=" ";
if(mode==="findProd")
query="Select * from Products where ProdNam=" +val;
... (same shit for different cases)
sendQuery(query) ;
}
He literally built the query on the client side sent it to a php script (without validation) and inserted it into the database.
You could literally call window.sendQuery with any sql query and get the result printed into the console.
And other than the plain text passwords guy that wasn't some kid someone knew, this was a "Webdesign" Agency.
Now I took the entire thing offline, called my friends dad, explained it to him and try to sort this out. I would not charge a good friends father but that hack will get a quite hefty bill since my hourly rate just tripled.
And the worst thing : If I publicly name that asshole or warn the people in his portfolio I can, according to Google, be sued. (But, and I assume thats vague enough not to count as bad mouthing, if anyone of you has a customer from Rheinland-Pfalz, Germany with a preexisting page, please have a look at the database interface)
I will call that agency tomorrow, ask for a detailed explanation for why they apparently let trained monkeys write their code and anonymously warn everyone in their portfolio about those flaws...
I don't know if I'm cursed or if there are just that many bad devs but it seems that once a year I have to stumble over some "mistakes" that make me question my sanity.4 -
You realize that the ERP software you use at your company is shit when:
- there is no service-side ERP backend handling requests
- the whole permission system is client-side (!)
- every client directly connects to the MSSQL database with a supervisor user (stored in plain text in a local config file)
- the MSSQL database contains tables with:
- typos
- names like "contract" but then also "contracts"
- mixed german and english words
- the multiple-business-unit implementation uses 4 columns named "Layer 1, Layer 2, Layer 3, Layer 4" in EACH table
- you find out that the ERP software is created with a fucking "software creation tool"
- there is no API, so you have to program one yourself to use for services
Yet, they charge us shit ton of money for their broken ass software.1 -
The best feeling according to my buddy is when drawing a character and then taking a photo of it and the phone recognizes the head as a real face.
Made me wonder of some programming equivalent scenarios.
Like checking your website for the first time on validator.w3.org and seeing the `No errors or warnings to show.`
Or writing code in a plain text editor and it works on first try without any errors.
How about letting a coworker do something you really want to do and already thought heavily about, to later realize they did it exactly how you imagined it.
Or even as simple as getting your first assignment on a new job and totally nailing it.
Do you got any good examples of a similar "omg ftw" moment? 7
7 -
My university has a internal developed system, where everything is managed from e-mails, exams to personal data.
What I'd like most about it, they talk all day about Internet Security and store our passwords in plain text and if you press the "I've forgott my Password button", they even send your password unencrypted, plaintext via e-mail. (Hello Wiresharks)
I don't know how to feel about this, it just hurts :(1 -
A good life lesson:
1. DON'T DELETE FILES YOU MAY WANT TO RECOVER
And if you DO delete them and then recover them, then
2. DON'T SEND THE RECOVERED FILES TO A·N·Y·O·N·E
Today I found a lost µSD card in the street. I did what every sane person would do -- plugged it into my laptop :)
There I found a directory with recovered pictures. I figured, some of them may contain the author's info in metadata, so I ran a quick plaintext search for @gmail.com.
Turns out, inside some of the recovered picture files I could find embedded company director's emails in plain-text. I mean, open the picture with a text editor and read through those emails - no problem! And these emails contain some quite sensitive info, e.g. login credentials (lots of them).
Bottom line, if you delete and recover your files, then do your best to keep them close: don't share them, don't lose them. You might be surprised what these recovered files may contain12 -
What the hell is it with WordPress people. Just read a rant where this dude is calling himself a "developer" . What the hell you're not a developer stop calling yourself a developer. All you do is click and drag pictures into squares. And type plain English into text boxes. Using software thay an actual developer actually did develop. You don't see me on cook rant calling myself a cook you know why cuz I can't cook. Leave don't learn a respectable language and get back to me. And no HTML is not a language.16
-
Image relevant.
Tried getting puter to talk, puter no want to talk.
Me sad.
Me tell puter to stay put and listen at 4444.
External device doesn't do shit.
Me sad.
Read the docs. Nothing. Written like a 5 year old would.
Be angry, how do I put external device into tcp/ip mode? No one knows, the docs don't know.
I get frustrated and pull the USB cable out of it.
Mfw it starts spitting out requests to my server with no end in sight.
Mfw the requests all just repeat.
Mfw the docs tell me to acknowledge a request I have to respond with a content type of
"application/x-www-form-urlencoded"
How.
Not possible.
Mfw I decide to dissect a request to check it's accept header.
Mfw it says text/plain.
Great, no idea in what format the thing expects it.
Try writing out query string plainly.
It fucking works.
Why can't people just learn to write proper documentation. 5
5 -
The most annoying co-worker(*team*) I have worked with just signed off a custom project that uses plain text passwords, hard coded into a file.. PLAIN TEXT!!! NO HASH!!! NOTHING!!! The same team also told me that working in feature branches cuts into their productivity, but they want CI/CD implemented NOW!3
-
Social Captain (a service to increase a user's Instagram followers) has exposed thousands of Instagram account passwords. The company says it helps thousands of users to grow their Instagram follower counts by connecting their accounts to its platform. Users are asked to enter their Instagram username and password into the platform to get started.
According to TechCrunch : Social Captain was storing the passwords of linked Instagram accounts in unencrypted plaintext. Any user who viewed the web page source code on their Social Captain profile page could see their Instagram username and password in plain text, as they had connected their account to the platform. A website bug allowed anyone access to any Social Captain user's profile without having to log in ; simply plugging in a user's unique account ID into the company's web address would grant access to their Social Captain account and their Instagram login credentials. Because the user account IDs were for the most part sequential, it was possible to access any user's account and view their Instagram password and other account information easily. The security researcher who reported the vulnerability provided a spreadsheet of about 10,000 scraped user accounts to TechCrunch.3 -
We are going to start accepting credit cards again. Old boss wants to store the tokens in plain text work the last 4 digits of the credit card...4
-
So I'm struggling to finish this library which among other things is supposed to write flowing text. And this one's taking foreeeever and I'm hating it so much already.
I just keep daydreaming of starting a "simple" platformer. And then I go, "hm the parallax must be nice, it needs to have as many layers as possible, oh and look at this video, here they're even zooming and each layer rescales differently, good effect, I need to add that too. Also a plain platformer is just boring, it needs to have adventure elements, and even RPG too, yeah why not. Hm, it needs to have some motion blur, but oh I need this 1/48 shutter speed to make it look cinematic. Okay how do I go about adding this blur effect? What? Libgdx doesn't provide one out of the box? I need to use opengl shaders? A shader, eh... I'm not even sure what that is. Okay, let's see how to do it. Wow that's a total mess and resource hungry, and how will I calculate it all as to make it match the 1/48 thing?"
You know... Simple. And in the end, I'll abandon the library and won't get anywhere with the platformer (as usual).
Tsk tsk tsk5 -
Not being able to persuade the client that storing plain text passwords so that they can send them to their users when they forget them is not the best way to handle user accounts.
This happened in 2012 but it still hunts me like it was yesterday.
Before you all demand to ban me from devRant, I’d like to say that we impelemented an alternative (unpaid!) for this, but were requested to disable it.3 -
So here I am investigating something our users are claiming. I look up which user the UserId did the change and I see not only the user but also the users password in clear text in a separate field. I thought that field was for a password hint that the user can set up, but I asked around and apparently, no... It's literally the plain text version of the password stored in the database, next to the hash of the password.
Apparently, the users were so impossible to deal with that we added that column and for users that constantly pester us about not knowing their password and not wanting to change it, we added a plaintext password field for them :D2 -
X - New stickers, people!!! Yay!!
X - Ordered these from www.juststickers.in.
X - Nice quality paper.
X - About $3 per piece.
X - You should try.
> Thanks @sumeetchawla.
> Although, you guys don't read the emails sent to your Support@juststickers.in email address 😒.
> I would give you 3/5.
-1 for not replying to the email.
-1 for storing the password in plain text.
Stickers are worth the money though 😊👌👍 5
5 -
Installed my telecom service provider's app for checking new packs. Didn't remember the password. Hit forgot password! I get my password in plain text in sms!
Fuck, it's one of the leading service provider in the country!
Till now i had only read about it, but never encountered it! Any ideas as to how to approach them?2 -
Short sad story:
The backend team in my company stores plain text passwords and I am making a view in the website to view all the users password in the system13 -
Don't you just love customers?
It al began when they showed us the flyers they were printing for their new products, an some one at our company who doesn't work here anymore had the brilliant idea of copying it to their webshop, as a fucking gimmick... Ooohh man the customer didn't seem to understand it was only visually
They wanted the 3d layering effect to be dynamic, so each product would have its own with custom colours
So it was made
A few weeks later they didn't want the informational text, they wanted links to each product that the layer uses
Sounded like logical so it was made
Again some time later, they noticed that the layers were not textured, but just plain
I argued against it because it would add unnecessary loading time for some 300 by 400 px element but they insisted
So they got what they wanted
A few days later they said that the textures were of low quality, and that we had to create ones with higher quality
Again our management said, yes
We made ~ twice the size of the element in image pixels to create a higher definition image
Then the customer wanted that the layers should change based on some selection menu above it
(At this point we realized that it would no longer be just a fun little gimmick)
So we tried to refactor/rebuild it to remove most if not all the hacks we did just to make the customer happy, that took too long for them (the customer) so we had to revert back to the hacked together version because otherwise we would not be done on time (commanded by management)
But again, we ... I say 'we' as in the company but realistically I've been the only one who has worked on the fucking abomination
But I digress...
A few stupid requests later, some layer images are almost fully transparent PNG images that are almost 1mb in Filesize each (some products have 5 or even more layers) and the god damn thing now has to account for optional layers...
I AM FUCKING SPENT... I'VE JUST CAME BACK FROM VACATION BUT I ALREADY NEED IT AGAIN... FUCKING WORKING 60 HOURS A WEEK JUST TO KEEP ONE CUSTOMER HAPPY WHILE OTHER PROJECTS BREATH ON MY NECK1 -
I just had such a forfilling moment.
Normally, i often (force myself) go to bed at night, after i worked on a project of mine, with these thought saying "oh man i wanted to get that feature done today" or "i want to finish this and that part of my code".I am sure everyone of you knows the feeling, when your brain communicates that you are just not done for today.
Today it was different. I got a project of mine working in it's first state, where i put much heart, love and time in.Just a few minutes before i finished for today i got my server responding the expected numbers(some kind of pin-code). It's a very easy system: Someone(at the time only me and my debug mode :3) on a android phone request a verification which is checked and processed by the server. The server creates a random six-digit number, returns it encoded to the client and sends an email to the user, which currently sends it in plain text(shame on me).
Yeah, the user enters the number and voilà
And of course, all the Pincodes can only be used once.
I got to bed with this feeling of luck and succes.
I hope tomorrow is going to be a productive day!
I am so lucky right now.
Have a good day everyone! -
More emarassing than frustrating..But I was applying to a couple internal positions recently and decided to bring in a sample package to demonstrate some of what I had been working on in my current team. They seemed to like the example and the interview seemed to go well...A couple hours later one of the managers came by my cubicle and asked "is that the real password?" and pointed to a line in the code. Sure enough, I had left a plain text password in the script I had just handed out to 10 panelists at 2 interviews..proceeded to collect the packets back. In the future I'll be paying closer attention to what I include lol.
Still frustrated we keep the passwords in the script though >.> any suggestions for better storage of passwords and the like in Perl scripts?3 -
Oh god where do I start!?
In my current role I've had horrific experiences with management and higher ups.
The first time I knew it would be a problem: I was on a Java project that was due to go live within the month. The devs and PM on the project were all due to move on at the end. I was sitting next to the PM, and overheard him saying "we'll implement [important key feature] in hypercare"... I blew my top at him, then had my managers come and see if I was OK.
That particular project overran with me and the permanent devs having to implement the core features of the app for 6mo after everyone else had left.
I've had to be the bearer of bad news a lot.
I work now and then with the CTO, my worst with her:
We had implemented a prototype for the CEO of a sister company, he was chuffed with it. She said something like "why is it not on brand" - there was no brand, so I winged it and used a common design pattern that the CEO had suggested he would like with the sister company's colours and logo. The CTO said something like "the problem is we have wilful amateurs designing..." wilful amateurs. Having worked in web design since I was 12 I'm better than a wilful amateur, that one cut deep.
I've had loads with PMs recently, they basically go:
PM: we need this obscure set up.
Me & team: why not use common sense set up.
PM: I don't care, just do obscure set up.
The most recent was they wanted £250k infrastructure for something that was being done on an AWS TC2.small.
Also recently, and in another direction:
PM: we want this mobile app deploying to our internal MDM.
Us: we don't know what the hell it is, what is it!?
PM: it's [megacorp]'s survey filler app that adds survey results into their core cloud platform
Us: fair enough, we don't like writing form fillers, let us have a look at it.
*queue MITM plain text login, private company data being stored in plain text at /sdcard/ on android.
Us: really sorry guys, this is in no way secure.
Pm: *in a huff now because I took a dump on his doorstep*
I'll think of more when I can. -
So we had to register for placements.. and the company sent email with plain text password.. and thats the password i registered with! nice!
BTW.. its one of the biggest company in IT industry globally. 2
2 -
Today's shit list, compiled from multiple random apps:
* Your subscription renews without an email in advance (no time to cancel)
* Your chat bot asks me twenty questions about why I want to cancel my membership, then sends me to a live agent, who asks me the same damn questions.
* Your app emails me my password in plain text
* Meeting agenda squashed by execs:
"We don't talk about _____, but we're committed to transparency." -
So, I apply for a job and they send me an automated email with my username....and my pasword....in plain text...I should use a different password for my applications....4
-
It's gotten to the point where I am legitimately impressed when I can tell a service is hashing their passwords.
All of these unnecessary complications of "must not have more than 2 of the same character in a row" but "can't be more than 12 characters" requirements make me think that the passwords are being saved in plain text.
Amazon and Dropbox do it right - present the user with an input box and no requirements printed anywhere.8 -
How do you get over the bad times? I keep having to work with shitty legacy systems that were written in perl and flash in the 90s, but my boss keeps telling me "No" on redoing some of the bigger stuff even though it is really needed. I mean, that is your goal here, right? Rebuilding this POS? FFS you still stored passwords in plain text twoo weeks ago! But no, you's rather dig around in Perl than upset some random user because his fucking interface looks different.
But then I also have to work with another system that I could redo in Cake/Laravel in two weeks (it's literally getting and writing data to one table, so two views and user auth), and the previous dev just... made a huge mess. I mean, why would you need to post data asynchronously when it's this one stupid form ? Just do a regular form submit? And the system is really not suitable for extending, because everything is in the database, EVERYTHING! Like, html form inputs? So to add a simple input to the template I have to create a new input type in the types table and then add that to the form structure table? Only to have the input checked by fucking regex? REGEX! Why? Seriously, this is not some high end CMS that needs this level of code reusability No. This is a simple fucking form.
And I can't get it to work. No documentation of course. No comments, either. All of this makes me feel like I'm just the shittiest dev ever. I feel dumb, and useless. Haven't turned on my private PC in weeks because I see no reason to work on any of my own stuff.
I used to have a job, working with Magento and Wordpress. And yeah, it was horrible, it was chaos, but it was fun and I was great at it. I bent that motherfucking system to fit my needs. People respected my opinion, they were convinced I could program this and that, and I proved them right. Did I make mistakes? Hell yeah. Did I give up? Fuck no!
But now, I just feel like I can't even write a simple fucking form any more. I'm just so close to giving up on development as a whole, even though I love it so much.5 -
Just managed to send my password in plain text to a colleague when I ment to enter it in the login box.....
Time to change my password again.....3 -
I checked out this new hybrid app that was released by some local senior developers.
Turns out that on my user profile, my user ID is set as the value of a hidden field and changing it to any other user ID and saving the form will update the profile of that user. Including changing the password.
The password reset form also allows me to change the user ID to reset that user's password.
Speaking of passwords, the value of the password field on the profile is my actual password in plain text.
Yes, I said this app was released by a couple of "senior developers". One has over 15 years of experience and the other works at an IT company that builds online banking systems. They appear to have outsourced this side project to some other development team but... Come on. At least take one quick look at the source code before releasing it, why don't you?
I don't even...1 -
- Implemented oauth1 - no body hashing
- URL contains credentials in plain text
- Used Azure API management feature as a proxy of the our API, however the documentation was on the our API, thus exposing the API URL with no management to developers.
- easy resource DDoSing because each trial user got a DB, the registration process did not have bot checks. You could literally freeze the db instance by spamming registration requests. -
I took Database System Class and Courses in University, and told to store the password using its hash and don't store it in plain text; it is at least a standard.
today i just resetting my gmail password since i forgot the password. and i wonder by how google forgot password mechanism work.
for example i register the password with:
'xxxfalconxxx'
and then change it to:
'youarebaboon123'
sometimes later i forgot both password, and google asked for the last password i remember; and i only remember part of it so i entered:
'falcon'
and this is right, so i can continue the forgot password mechanism. how could you check the hashed text of 'falcon' is the subset of hash text 'xxxfalconxxx' ?2 -
It was the last year of high school.
We had to submit our final CS homework, so it gets reviewed by someone from the ministry of education and grade it. (think of it as GPA or whatever that is in your country).
Now being me, I really didn’t do much during the whole year, All I did was learning more about C#, more about SQL, and learn from the OGs like thenewboston, derek banas, and of course kudvenkat. (Plus more)
The homework was a C# webform website of whatever theme you like (mostly a web store) that uses MS Access as DB and a C# web service in SOAP. (Don’t ask.)
Part 1/2:
Months have passed, and only had 2 days left to deadline, with nothing on my hand but website sketches, sample projects for ideas, and table schematics.
I went ahead and started to work on it, for 48 hours STRAIGHT.
No breaks, barely ate, family visited and I barely noticed, I was just disconnected from reality.
48 hours passed and finished the project, I was quite satisfied with my it, I followed the right standards from encrypting passwords to verifying emails to implementing SQL queries without the risk of SQL injection, while everyone else followed foot as the teacher taught with plain text passwords and… do I need to continue? You know what I mean here.
Anyway, I went ahead and was like, Ok, lets do one last test run, And proceeded into deleting an Item from my webstore (it was something similar to shopify).
I refreshed. Nothing. Blank page. Just nothing. Nothing is working, at all.
Went ahead to debug almost everywhere, nothing, I’ve gone mad, like REALLY mad and almost lose it, then an hour later of failed debugging attempts I decided to rewrite the whole project from scratch from rebuilding the db, to rewriting the client/backend code and ui, and whatever works just go with it.
Then I noticed a loop block that was going infinite.
NEVER WAIT FOR A DATABASE TO HAVE MINIMUM NUMBER OF ROWS, ALWAYS ASSUME THAT IT HAS NO VALUES. (and if your CPU is 100%, its an infinite loop, a hard lesson learned)
The issue was that I requested 4 or more items from a table, and if it was less it would just loop.
So I went ahead, fixed that and went to sleep.
Part 2/2:
The day has come, the guy from the ministry came in and started reviewing each one of the students homeworks, and of course, some of the projects crashed last minute and straight up stopped working, it's like watching people burning alive.
My turn was up, he came and sat next to me and was like:
Him: Alright make me an account with an email of asd@123.com with a password 123456
Me: … that won't work, got a real email?
Him: What do you mean?
Me: I implemented an email verification system.
Him: … ok … just show me the website.
Me: Alright as you can see here first of all I used mailgun service on a .tk domain in order to send verification emails you know like every single website does, encrypted passwords etc… As you can see this website allows you to sign up as a customer or as a merc…
Him: Good job.
He stood up and moved on.
YOU MOTHERFUCKER.
I WENT THROUGH HELL IN THE PAST 48 HOURS.
AND YOU JUST SAT THERE FOR A MINUTE AND GAVE UP ON REVIEWING MY ENTIRE MASTERPIECE? GO SWIM IN A POOL FULL OF BURNING OIL YOU COUNTLESS PIECE OF SHIT
I got 100/100 in the end, and I kinda feel like shit for going thought all that trouble for just one minute of project review, but hey at least it helped me practice common standards.2 -
Working at a local seo sweat-shop as "whatever the lead dev does't feel like doing" guy.
Inherit their linux "server".
- Over 500 security updates
- Everything in /var/www is chmod to 777
- Everything in /var/www is owned by a random user that isn't apache
- Every single database is owned by root sql user
- Password for sudo user and mysql root user same as wifi password given to everyone at company.
- Custom spaghetti code dashboard with over 400 files in one directory, db/ api logins spread throughout these files, passwords in plain text.
- Dashboard doesn't have passwords, just usernames to login
- Dashboard database has all customer information including credit card stored in plain text
- Company wifi is shared by other businesses in the area
I suggest that I should try to fix some of these things.
Lead Developer / Tech Director : We're an SEO company, not a security company . . .7 -
We hired someone to make the new front site because I was too busy.
The guy had a plain text password system to show, mispronounced "FontAwesome", and used WordPress.
He was not an instructor but was supposed to be the "senior option" for when I couldn't do something for any reason.
I later asked him for some opinion on how to translate the site, and he disabled the Captcha plugin. I. Don't. Know. Why. I figured because of all the spam I got suspiciously after he "took a look" at the admin panel.
Luckily I could get him out of the contacts and now we are looking for more devs. -
Screw all the people who think standard email is "secure". It is not suitible for sending passwords and SSN numbers.
How can something Equifax or Marriott hacks have happened and people are still ok sending out information like this in plain text?!
I know their hacks weren't email released but still.....should be a good time to up some security standards. Right?2 -
PSA Cloudflare had a bug in there system where they were dumping random pieces of memory in the body of HTML responses, things like passwords, API tokens, personal information, chats, hotel bookings, in plain text, unencrypted. Once discovered they were able to fix it pretty quickly, but it could have been out in the wild as early as September of last year. The major issue with this is that many of those results were cached by search engines. The bug itself was discovered when people found this stuff on the google search results page.
It's not quite end of the world, but it's much worse than Heartbleed.
Now excuse me this weekend as I have to go change all of my passwords.3 -
Passwords are limited to 8 characters and stored in plain text. In the beginning of the year they give your password in a little piece of paper... I just gave up and started using my name as the password...
Found in the web portal used to buy school meals and consult card balance in Portugal (called GIAE). -
One of dev I was working with once stored users' payment data in plain text. Luckily enough that thing never got to production.
-
The dev before me stored all the emails and passwords as plain text in the database. This is not good. Not good at all.1
-
Follow-up on https://devrant.com/rants/5001553/...
How the fuck are Jupyter notebooks so popular in research? Like some dude had an idea to take perfectly good markdown and python code, add a whole lot of transitional properties to make version control impossible, encode it as JSON on the assumption that a human could somehow look at it and make sense of countless escaped characters and base64 encoded data, create dedicated software people need to install in order to read what used to be simple plain text, and think "This. This is what 99% of data researchers will use from now on." And somehow, overwhelming majority of researchers agreed that this extremely inefficient data format is the best there is and they should develop all their tools around it.9 -
Most unprofessional experience at work?
Check out my previous rants. With so many, it would be difficult to pick just one.
Not sure if I've told this one before. 'Caleb' was part of a team responsible for migrating financial data from a legacy (DOS-based) system to our new system.
Because of our elevated security (and the data being plain text) Caleb had access to the entire company's payroll (including VP salary, bonuses, etc).
Solidifying my belief that that salaries should be private between the employee and the employer, Caleb discovered he was making considerably less than his peers (even a few devs that he had seniority over), and the green monster 'Jealosly' took over his professionalism. Caleb decided to tell everyone making the same and less than him, the salaries of the other (higher paid) devs, managers and VPs.
Nobody understood at the time, but these folks started to behave erratically , like showing up late, making comments like "Why should I document that? Make 'money bags' over there do it", etc and so on.
Soon at review time, Caleb decided to use his newly discovered ammunition to 'barter' for a higher salary by telling the manager if he didn't make $$$, he would send an email to the entire company containing everyone's salary.
The manager fired Caleb on the spot and escorted him out the building (Caleb never had chance to follow thru with that threat)
When word got out about Caleb's firing (and everybody knew why), those other employees started showing up on time and stopped complaining about doing their job.5 -
Back in https://devrant.com/rants/5492690 @Nihil75 referred to SlickVPN with a link, where you can buy a lifetime licence for $20. I thought - what the hell.. I don't need a public VPN rn, but for $20 for a lifetime lic - I'll take it, in case I'll ever need one.
I had some trouble signing up - the confirmation email never reached my inbox. So I got in touch with support. And they.... generated and send me a password in plain-text.
And there even isn't any nagging requirement to change the pass after I sign in for the first time!
IDK... As for a service claiming to be security-oriented, the first interaction already screams "INSECURE".
Well.. should still be OK for IP switching, to unlock Netflix content I guess. Don't need anything secure for that 🤷 15
15 -
My job in company to developed e-commerce website as a full stack developer.
History of that project.
Company paid 300,000 INR to the local web development firm for developing previous website and they developed website without bootstrap/SSL/Even save information of high profile client in plain text.
I am not angry on that web firm ,I am laughing on my company because such client never trust on independent developers who work hard ,code day and night to complete freelancing projects.
I hope my work will make differnce in their selling. -
I started using Keepass like 2 months ago, and recently i started going through all my email accounts to compile a list of all the services i've ever signed up to; delete the accounts you don't need and move everything else to keepass with a strong passwd, that was the plan.
I'm still going, but out of the 60 i have so far, 10 sites just had the password, *in plain text*, in the confirmation email!! I don't even konw anymore, just end me now plz 😢7 -
Countless times have I had to replace shell scripts that use sshpass+rootpw in plain text, written by people often described as, "brilliant."3
-
Q: Do you have an option which allows me to use spaces instead of tabs?
A: Go fuck yourself (and, stop using a plain text editor, then uploading code to Google Docs.)6 -
For me it was not do much a choice.
I started out using basic and simple text display (graphics existed but was quite difficult).
For a long time I was the sole or part of a pair of devs so specializing was not possible and once we grew to such a size I already was quite proficient in all areas from hardware to customer support and education.
But from that time onto today I have gravitated towards a more backend role mainly because I lack a good sense or visual design.
I know it something looks good, but doing it my self results in more boring or plain designs where more thought goes into UX than nice looking design.
That said, if we do web applications I can still keep up since it usually is more ux heavy ;)
But when it comes to adding background images, nice color sets and such I gladly defer that to colleagues with a better design sense.2 -
While attempting to quit smoking and after spending a full day trying to understand why the previous devs took this approach to encrypting a string and my lack of nicotine addled brain not allowing me to see that this was a “Secure”String and so uses a machine specific key (that’s why the code that worked locally wouldn’t run on production 😑) this is my rant on comments added to the helper I had to write
/// <summary>
/// If you are using this class and it's not for backward compatibility - then you probably shouldn't be using it
/// Nothing good comes from "Secure" strings
/// Further to this Secure strings are only "useful" for single user crypto as the encryption uses the login creds, transferring
/// this data to another client will result in them never being able to decrypt it
///
/// Windows uses the user's login password to generate a master key.
/// This master key is protected using the user's password and then stored along with the user's profile.
/// This master key then gets used to derive a number of other keys and it's these other keys that are used to protect the data.
///
/// This is also a broken crypto method via injection (see Hawkeye http://hawkeye.codeplex.com/) plus the string is stored in plain
/// text in memory, along with numerous other reasons not to use it.
/// </summary>
public class SecureStringHelper
{3 -
Just found out that MQTT.fx stores user credentials in plain text in a xml file.
WTF?!
I mean it's only stored locally but it's still a bit worrying.2 -
Best part about being a dev? - Finding little gems of humour in comments and docs.
Why convert HTML to Markdown?
-You have an existing HTML document that needs to be edited by people with good taste.
-You want to store new content in HTML format but edit it as Markdown.
-You want to convert HTML email to plain text email.
-You know a guy who's been converting HTML to Markdown for years, and now he can speak Elvish. You'd quite like to be able to speak Elvish.
-You just really like Markdown.
from https://github.com/thephpleague/... -
https://devrant.com/rants/2366822/...
following rant I started oppening my files to build copy of have i been pwned service why twitter kept their passwords in plain text lol
...
people actually got 123456 passwords looking for my email in twitter database file 1
1 -
The real web development is optimising the shitty front end code.
The task assigned to me is optimisation of dashboard page of website which was developed by freenlancers.(end of contract from their side)
The front end is mess. Individual js files (bootstrap, popper, jQuery, jQuery ui, loader and main) loading in production inside head tag of html file
No text compression.
Every template has random number of their own js files in any block of template. Nothing structured. There will be fantastic waste of time figuring out file dependencies.
Same with css files. Some are scss, some plain css. No compression. No proper modules.
Basically, I have to go through 25-30 html files. Then understand, which template is extending which one. Go through all js and css files in each html file and again understand dependencies between them
This is gonna be real fun.1 -
When the recruiting company mails you about new jobs along with your PASSWORD!
Dude, you have a fuckall dev and u will help me find a job... Thanks, but no thanks. 4
4 -
JetBlue still storing passwords in plain text, after 4 years
“JetBlue: The deadly sin of an otherwise great airline” https://medium.com/@sethillgard/...13 -
I hate it so badly when syntex highlighted code snippet on a web page goes to plain text on double click. Anyone knows it's purpose?6
-
XML and JSON endpoints while forcing Content-Type Text/Plain instead of allowing Web API to handle the serialisation. The f were these devs thinking.
 8
8 -
They say that runing the same command over and over again is a sign of insanity.
LIKE HELL IT IS!!!
I've been running `terraform apply` for the last hour (trying to dump an EKS token in plain-text, because my k8s-related providers failed to auth to the cluster), and miraculously the problem went away. Now the error is no more.
Insanity?
I beg to differ!
Narf! 2
2 -
Why the fuckin' hell does PayPal limit your password to 20 characters?!?
The length shouldn't matter if they hash and salt the passwords... sooooo...4 -
There was this text in the game that, according to platform's rules, was supposed to be displayed verbatim. One of the languages had these “” opening / closing quotation marks. The problem was that instead of the text reading “some_text” there seemed to be a space in there “ some_text”. Since the rules are specific - no alterations whatsoever, a report was made. It turned out later the issue was due to kerning.
The chosen solution for that was to use "some_text”.
What the fuck? For one, there rule was that there are to be no alterations to the text. Then there's the other thing of this "” being just plain wrong.
It's like writing
```
main()
{
end
```
WTF are you doing?15 -
received a picture of scribbled password, all am thinking is you can't store your password in plain text
-
2016 and the passwords were stored in plain text. I pointed it out, they said they'll use md5 instead :/
PS: Ended up fixing it for them with HMAC-SHA256 -
so... apparently Lync is encrypted, but if your partner doesn't notice your message it's sent as a plain text "Missed conversation with..." email...3
-
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
Today I was meeting with a researcher in my department so that I could show him how the software I developed works. He graduated from a really good university in electronic engineering, with 100/100 I think, and he can manage to copy&paste some python code. So I didn't expect what happened today.
Guy: 'So I have to give to your program as input this python file which contains a function you need to call, right?'
Me: 'Yep, I mean, that is a jupyter notebook, I need a text file containing only the function which is in that notebook'
Guy: *Downloads the notebook, tries to feed the notebook file into my program*
Me: 'Wait, don't, there probably is a lot of junk related to jupyter notebook, try opening it in notepad++'
Guy: *Opens file, sees a lot of junk text*
Me: 'Yeah, I thought so, you need to save it as plain text or .py'
Guy: *Renames the notebook as .txt*
Me: *Shakes my head without him noticing*
'That won't work, the content of the file won't change like that...' -
Just learned that you can join a network through a QR code. That's sick!
I thought you could only go to links / store plain text with QRs...18 -
Just wanted to buy a gift for my gf, so I went to birchbox.fr to buy her a 3 months subscription (irrelevant information).
So of course I needed to create an accout in order to buy it.
But what a surprise when I received a confirmation email, with my password in PLAIN TEXT inside. I guess I do really love her for not cancelling the gift and deleting my account immediately. -
Some interesting keyboard shortcuts that are lesser-known but can be quite useful:
1.Windows Key + . (Period): In Windows 10 and later versions, this shortcut opens the emoji panel, allowing you to quickly insert emojis into your text.
2.Ctrl + Shift + T: This shortcut reopens the last closed tab in most web browsers (Chrome, Firefox, Edge). It's handy if you accidentally close a tab and want to retrieve it quickly.
3.Ctrl + Backtick (`): In some text editors and IDEs (like Visual Studio Code), this shortcut toggles the integrated terminal window, allowing you to quickly switch between editing and running commands.
4.Ctrl + Shift + Esc: This directly opens the Task Manager in Windows, skipping the intermediary step of opening Ctrl + Alt + Delete and selecting Task Manager.
5.Alt + Drag: In many graphics and design applications (like Photoshop), holding down the Alt key while dragging an object duplicates it. This can save time compared to copying and pasting.
6.Ctrl + Alt + D: This shortcut shows the desktop on Windows, minimizing all open windows to quickly access icons and shortcuts on your desktop.
7.Ctrl + Shift + N: In most web browsers, this shortcut opens a new incognito or private browsing window, useful for browsing without saving history or cookies.
8.Alt + Enter: In Excel, this shortcut opens the Format Cells dialog box for the selected cell or range, allowing quick formatting changes without navigating through menus.
9.Shift + F10: This shortcut performs a right-click action on the selected item or text, useful when you can't or don't want to use the mouse.
10.Ctrl + Shift + V: In many applications, including Google Chrome and Microsoft Word, this shortcut pastes text without formatting (paste as plain text). It's useful when copying text from websites or other documents.
++ if you like this5 -
The positive side of EnvVars...
So a couple of weeks ago I moved all api keys and db passwords to environmental variables on the server so that I didn't have to keep worrying if I'm live in my test environment.
Earlier I shat myself after an apt-get upgrade broke php and apache somehow decided it's a great idea to serve all .php files as plain text. I was super relieved to find no confidential information (apart from logic) was made public. -
When the company running my student accommodation not only stores the passwords for their resident portal in plain text and emails them straight to you in the case of a forgotten password. But also generates your password at sign up according to a specific general pattern...2
-
A while back I was looking for a new job and was given an interview by one company who shall remain nameless. Before the interview, they asked me look through their current site, nothing unusual there, so I started browsing. Then I received an email with all the details I needed to access their production server. Apparently they wanted me to look through the code, unusual but I did so.
First thing all the passwords, including those belonging to members of the public were stored in plain text and many were still the default passwords which were based on the Id so were sequential.
I highlighted these issues at the interview and they then asked me to do a test, not the usual test though, they asked me to add some charts to their prod site. Needless to say that didn’t happen and I got another job elsewhere.1 -
My current task involves processing the commoncrawl web archive, and it's like a box of junk you buy at a flea market. You find so much useless stuff, broken stuff, stuff that makes you question people...
My latest find makes me wonder what lies out there if what I found was in plain sight. I found tens of thousands of websites that look like someone used markov chains to generate pron ads. Those websites exist in 10+ languages, use the same url-scheme, read like a dyslexic camgirl reading alphabet soup and are hosted on the same three ip-adresses. There is no javascript involved and some pages link to a variety of twitter accounts.
I queried a few commoncrawl files and amassed 4GB of this spam. Every time I look at it it gets weirder. There is an italian article about malware in there too.
Here's a text sample:
"Not from her bedroom, she her stream view and meet new experience. In hd india, because swimsuit still laws exist no interaction or frigthened and."1 -
QA Tester: titles in table items look like links and are clickable, they should be plain text.
Senior Dev: style={{ color: '#000' }}5 -
Anybody know what this service running in the background on an android device does?
It sent me a plain text notification, which disappeared and sent me to a phishing site the moment I tried clearing it. I've forced killed the process for now.
A quick search online doesn't reveal much information, except for a dodgy site claiming it's spyware named StealthGenie. 20
20 -
I had to build a few packages today from a git source.
Everything just plain text or shell scripts - so no fancy shit, no buildsystem... Nothing.
I was painfully reminded why I had forgotten a lot about dpkg package builds.
Fun facts:
- seems like impossibro to define an output directory for debuild (../ from source which must be pwd/cwd)
- i used /opt/<vendor_name>... Purging the deb from system deletes opt too, as it is empty
- reprepro (or whateva it is called) fails with an "uncommon GPG error" instead of saying "I don't know which key to use"
- creating rolling release numbers (as the packages won't have a real versioning system...) is fun - when you remember that date isn't sufficient, as the time part is necessary to build multiple packages (versions) per day
Compared to an Gentoo ebuild, this was really rocket science....
Guess as soon as someone does not follow the debian way, he must be shunned and exiled. At least it felt like this ....
But it works now. Woohoo. *cries internally* -
making my own working parser for a project i worked on
i used it to turn a custom file "format" (think json: a format but still plain text) into code / functions on the fly1 -
A number of tech projects use mailman for their mailing lists. Yet, mailman sends passwords in plain text to their users, once a month. Wtf?2
-
Never again will I use eclipses egit extension. First eclipse thought that my plain text java source code should be encoded in some bizarre occult way which made eclipse think its binary what made me try pretty much anything one can do with a .gitattributes file before a colleague suggested to not trust eclipse eith the encoding it was explicitly told to use, then I fetched another branch to merge them which somehow killed my .project file and forced me to delete and refetch the whole thing which led to eclipse not longer recognizing it as a java project. May it be because I'm to stupid to use my tools? Yeah, probably. But I'm done with egit, it's all console gitting from now on, fuck suggested practice.
-
Security issues I encountered:
- Passwords stored as plain text until last year.
- Sensitive data over http until last year.
- Webservice without user/pass authentication. -
I've implemented Chat function for my app. Since I'm a security noob what is the preferred way of encrypting the messages End-to-end maybe?
I'm definitely not leaving them as plain text :)4 -
Once on a project the authentication request for a service was done... through http... with the username and password as parameter in the URL... in plain text
-
!rant
Starting my first small c++ project with website interaction on an Ubuntu server as practice for next semester. Any good recommendations to get user input from a webpage using only c++ (there can be html within the c++ program of course) and libraries?
I have once worked with an httpd-deamon and got user info from the url but I want a user to be able to fill in 2 textboxes and submit them using a button.
Plain text is good enough and it will only be used by 2 people once every week or so.8 -
When after registration on some website you get your password, that you just set, send back to you in an email. Why the fuck do they store and transmit passwords in plain text.4
-
! Rant
In our office I'm the only one who installed plugins on my sublime text and make sure i have a great font, nice theme. All of them just plain stock sublime text.3 -
I'm trying to find a linux distro that suck less to study the basics of bash, and some c/c++ dev tools. I play around with linux since 2013. But I just can't believe that, still, until today, in gnome, you can't fucking chose a audio output and get to the system to remember on the next reboot.
I mean, it doesn’t fit in my mind this nonsense, if I can only solve this shit on the command line or in a configuration file, why don’t you take that shit off the option and put a plain text explaining how to configure this shit in the right way . Who expects a system to behave like this?
I don't know why someone lost their time implementing something useless, and worst, deceiving.9 -
During the cryptography & security lecture at the university I received an email from the university IT department with credentials to access the university cloud services. Of course, password was in a plain text.2
-
Joined a new team at work hoping to learn something new. Was told by the team lead that they will be starting development on a new project that I was interested in.
Guess what it was all a fucking lie. I'm assigned a task to create documentation for some legacy java shitcode without any fucking comments.
Fine I get it, they say it's required going down the road of the new project as it will work alongside the old application. But the code is so fucking bad. For starters
-The db host and credentials are hard-coded in a million places
-it stores user credentials in plain text
-its creating files in the fucking filesystem to store things instead of storing it in the db
-each functions ranges from 100 to 8000 lines of code
Who even codes like this 🤯
And I can't fix these issues. All I need to do is document every function and class and package. Fine. Fuck this shit -
Consider an API that uses the HTTP path to represent position in a tree that literally represents a file tree with minimal constraints, and GET/PUT/DELETE methods to read, write and destroy the nodes. How would you encode read/write operations to per-node metadata? The kinds of metadata are static and around 4, so inventing HTTP verbs for each of them is infeasible but filtering is not necessary.
Options considered so far:
- toplevel resources alongside a namespaced /data such as /acl, /lock
- magic keywords to the Range header (this is apparently compliant)
- mimetypes such as text/plain+acl
- SETPROP / PROP methods in the spirit of WebDAV
- headers (I worry this may become an immitigable bottleneck really fast)
I'm looking for any kind of suggestion or insight, not perfect answers.
I read the WebDAV specification and I won't even suggest that I'm trying to align with it, the only protocol I'd seen in the past with comparable scope bloat is WebRTC.22 -
Whenever a site tells me the password I entered has already been used? I mean how are you supposed to know if you are salting and hashing the password.. Oh wait you probably just save it in plain text!! Please don't!!7
-
I can't recall what platform it was, but upon trying to change my password it would tell me that the new password was too similar to the previous one... :/1
-
Have been searching on this topic alot lately, but I cant find any good solution, in my opinion.
I have a system where I want to encrypt some data in the database, so it isn't in plain text, but how would you do it properly?
It has to be decrypted to view the data in the system, but how to manage it?
How can I store the keys in the right way? In my current trial, I have a encryption key and an iv, but wouldn't it be wrong to store the encryption key in the config file?
Can't really see how to grasp this the right way and in the same way have it as secure as possible.
Is it just stupid in general? -
Just got an "no-reply" email that wants me to click a link for customer satisfaction survey. No company name, no whatever, just plain text and the sender is "no-reply@nestor.com" Is there a way to find out where did they get my email?!4
-
For a while I used vim or whatever plain text editor nano gedit but I got used to features like autocomplete and syntax highlighting etcetera when forced to use things like an eclipse and IntelliJ slash Android Studio. But when I'm usually using Atom these days. But I am increasingly more frustrated that my favorite language python does not have my favorite features in the editor. I guess I need to consider paid editors or at least just try some more free ones but I really don't want to invest the time. Once again I think I've convinced myself to just enjoy the nice things about atom. At this point i like it better than komodo7
-
Someone earlier today posted a rant about a credit card security conference sending them account details with a plain text password in an email. The password appeared to be 1 use temporary password that the user would change on first login. Assuming one does not actually store plain text passwords, what is the downside to a single use password Vs a single use link to set a new password?1
-
GRAYHATHACKS CONTRACTOR HELPED ME GET PROOF THAT MY HUSBAND WAS HAVING AN AFFAIR
Hi there. You know, the kind of situation where you're not sure if you're making the right decision, but you know you need answers. That's where I was a few months ago. My husband had been acting so distant, so suspicious, and so overprotective of his phone. The gut-wrenching feeling of not knowing what was happening was eating me up inside. I'd catch him smiling at his screen when he thought I wasn't looking, and then he'd quickly switch it off when I walked into the room. The whispers and secret calls were just too much to bear.
That's when I stumbled upon Grayhathacks Contractor. At first, I was skeptical, but desperation can make you consider things you never thought you would. I reached out to them, and from the get-go, they were so understanding and professional. They made me feel like I wasn't alone, like I was doing the right thing for my peace of mind. And boy, did they come through for me!
The process was surprisingly simple. They had me send over my husband's phone details, and they got to work right away. Within a week, they sent me a detailed report that had me floored. It was like they had peeled back the layers of deceit and laid bare his infidelity. The damning data they harvested from his phone and laptop was overwhelming. They found text messages, emails, and WhatsApp chats that left no doubt in my mind. He was having an affair with a colleague from work. The conversations were explicit, filled with lovey-dovey language and promises that should've been reserved for me. There were dates, times, and even hotel bookings that coincided with nights he claimed to be working late. And the photos! The raw pain of seeing those images of him with someone else is something I'll never forget.
The thing that really got me, though, was the voice memos. Hearing his voice, saying things to her that he hadn't said to me in years, was devastating. But it was also the proof I needed to finally confront him. And when I did, he couldn't lie his way out of it. The evidence was right there, cold and clear. Their spyware was top-notch. It was undetectable, and it gave me access to everything: his calls, messages, emails, social media, and even his location history. It was like having a pair of invisible eyes and ears. They even helped me understand the technical side of things, guiding me through the process of checking the data they had collected.
If you're in the same boat I was, I totally get it. The thought of hiring a hacker is daunting, but sometimes you just need to know the truth. And let me tell you, Grayhathacks Contractor will give you that truth. They're not just hackers; they're detectives of the digital age, helping people like you and me uncover the painful realities that are often hidden in plain sight.
I'm not saying what they do is pretty, but sometimes you have to get a little dirty to find the truth. And when you do, you can start to rebuild your life, piece by piece. It's been a tough journey, but thanks to Grayhathacks Contractor, I'm on the path to healing. I now know exactly what happened, and I can make informed decisions about my future.
So, if you're feeling lost and need answers, don't hesitate to reach out to them. And who knows, maybe one day you'll be writing a review like this, sharing your own story of how they helped you get your life back.










