Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "power user"
-
Yesterday, in a meeting with project stakeholders and a dev was demoing his software when an un-handled exception occurred, causing the app to crash.
Dev: “Oh..that’s weird. Doesn’t do that on my machine. Better look at the log”
- Dev looks at the log and sees the exception was a divide by zero error.
Dev: “Ohhh…yea…the average price calculation, it’s a bug in the database.”
<I burst out laughing>
Me: “That’s funny.”
<Dev manager was not laughing>
DevMgr: “What’s funny about bugs in the database?”
Me: “Divide by zero exceptions are not an indication of a data error, it’s a bug in the code.”
Dev: “Uhh…how so? The price factor is zero, which comes from a table, so that’s a bug in the database”
Me: “Jim, will you have sales with a price factor of zero?”
StakeholderJim: “Yea, for add-on items that we’re not putting on sale. Hats, gloves, things like that.”
Dev: “Steve, did anyone tell you the factor could be zero?”
DBA-Steve: “Uh...no…just that the value couldn’t be null. You guys can put whatever you want.”
DevMgr: “So, how will you fix this bug?”
DBA-Steve: “Bug? …oh…um…I guess I could default the value to 1.”
Dev: “What if the user types in a zero? Can you switch it to a 1?”
Me: “Or you check the factor value before you try to divide. That will fix the exception and Steve won’t have to do anything.”
<awkward couple of seconds of silence>
DevMgr: “Lets wrap this up. Steve, go ahead and make the necessary database changes to make sure the factor is never zero.”
StakeholderJim: “That doesn’t sound right. Add-on items should never have a factor. A value of 1 could screw up the average.”
Dev: “Don’t worry, we’ll know the difference.”
<everyone seems happy and leaves the meeting>
I completely lost any sort of brain power to say anything after Dev said that. All the little voices kept saying were ‘WTF? WTF just happened? No really…W T F just happened!?’ over and over. I still have no idea on how to articulate to anyone with any sort of sense about what happened. Thanks DevRant for letting me rant.15 -
Developer Says: We have trained a model to automatically categorize user posts.
Sales Department Says: We are building a decentralized peer to peer blockchain neural network based on a scalable containerized cloud of quantum computers to power internet of things devices in augmented reality while users get driven around in autonomous vehicles powered by machine learning and pay for renewable energy with cryptocurrencies.6 -
Lamer rant
For a really long time I said to myself that this is too basic to rant about but lately it became so frequent and extreme that here is my rant about completely clueless users that ask me IT related questions.
Disclaimer: Said users are people that I generally can't avoid. Distant family members, neighbors and etc.
Case 0:
U: I don't know what's happening!! The computer doesn't work!!
M: What do you mean?
U: There's no Facebook! And everything is stuck and no messenger!!!
M: The WiFi on your laptop was off. I turned it on. Still, this doesn't mean that the pc wasn't working.
U: I don't understand this shit!!!
Case 1:
U: I hate this computer!!! It never works!!! Help meeee!!!
M: What now?
U: Where did the internet disappear?!
M: (assuming it's wifi or browser related)
Actually user moved the Chrome window to bottom-right corner and lost it.
Every time I try to show the user how I resolve the issue the user yells that there are too many steps, that they are complicated and that I'm a bad teacher and doing it too fast.
Case 2:
U: My computer is so slow! It barely can load google translate! And I can't listen to music on youtube!! Shitty laptop! It's you! Your computers in the apartment drain everything!!!
M: You have no idea what you are talking about.
U: My husband told me that your computers are heavy and drain everything!
M: What exactly did he tell you that my devices drain?
U: I don't know! All the energy! I believe him! He knows!
M: My computers drain less electricity than your vacuum and I have a separate internet connection. Not only we share nothing but also I drain nothing.
U: Since you appeared all the computers are slow!!!!
Fkk...
Case 3:
U: I don't understand, where is my whatsapp?
M: You can't locate the app on your phone?
U: Yes! F*ck, help me! I'm so angry and I really need this NOW!!!
M: Shut up. I'm already here and helping.
(I open users phone and whatsapp is the active app...)
U: I can' t find my whatsapp with Clara!
F*ck you! F*ck you! Ghckjfshij!!!
Case 4:
(crazy hitting on my door)
U: I don't have THE internet!!!
It's you again! You took all of THE internet!!!
M: No, it doesn't work like that. Your provider is bad, your package is cheap and your cables are of low quality.
U: I need THE internet immediately!!! Stop playing with your typing and fix the facebook or I'll cut the power cables to the house!!
I can go on, just don't think that recalling all those events is healthy for me.20 -
>Be me arriving at work early for my daily morning relaxation as I surf reddit etc in an hour of euphoria without having to deal with employees
>Get a phone call JUST 5 MINUTES AFTER
> User was complaining that we ran an update which totally wrecked his machine as it didn't want to turn on..
>Ask him to check if the switch on
>Says that he can't see in the dark
>Ask him to turn on the lights
>He says he cannot because the whole power to the building is currently out in a blackout
THIS CALL TOOK 30 MINUTES OF MY BELOVED RELAXATION JUST TO END UP IN HIM NOT BEING ABLE TO COMPREHEND THAT A COMPUTER CANNOT RUN WITHOUT POWER
>rant over UGHHHH10 -
Example #1 of ??? Explaining why I dislike my coworkers.
[Legend]
VP: VP of Engineering; my boss’s boss. Founded the company, picked the CEO, etc.
LD: Lead dev; literally wrote the first line of code at the company, and has been here ever since.
CISO: Chief Information Security Officer — my boss when I’m doing security work.
Three weeks ago (private zoom call):
> VP to me: I want you to know that anything you say, while wearing your security hat, goes. You can even override me. If you need to hold a release for whatever reason, you have that power. If I happen to disagree with a security issue you bring up, that’s okay. You are in charge of release security. I won’t be mad or hold it against you. I just want you to do your job well.
Last week (engineering-wide meeting):
> CISO: From now on we should only use external IDs in urls to prevent a malicious actor from scraping data or automating attacks.
> LD: That’s great, and we should only use normal IDs in logging so they differ. Sounds more secure, right?
> CISO: Absolutely. That way they’re orthogonal.
> VP: Good idea, I think we should do this going forward.
Last weekend (in the security channel):
> LD: We should ONLY use external IDs in urls, and ONLY normal IDs in logging — in other words, orthogonal.
> VP: I agree. It’s better in every way.
Today (in the same security channel):
> Me: I found an instance of using a plain ID in a url that cancels a payment. A malicious user with or who gained access to <user_role> could very easily abuse this to cause substantial damage. Please change this instance and others to using external IDs.
> LD: Whoa, that goes way beyond <user_role>
> VP: You can’t make that decision, that’s engineering-wide!
Not only is this sane security practice, you literally. just. agreed. with this on three separate occasions in the past week, and your own head of security also posed this before I brought it up! And need I remind you that it is still standard security practice!?
But nooo, I’m overstepping my boundaries by doing my job.
Fucking hell I hate dealing with these people.14 -
I was in a public place on my laptop, and my laptop went into hibernation to save battery. I switched it back on and then the laptops BIOS came up saying that the battery was critically low, nothing bad here.
Instead of clicking continue, I decided to press "Diagnostics" instead. The diagnostics immediately began to run in the BIOS.
The screen began to show different coloured bars and patterns, obviously a screen test. Then a prompt appeared asking me if coloured bars were displayed. The options were yes and no, and a button saying "Exit" in the top right. Me, not wanting to do a full diagnostics on such a low battery, pressed exit.
The screen turned black, and then flashed red. The beeper on the motherboard began to beep at an ear-piercing volume. It sounded as if it was a bomb about to go off. Everyone around me stared and some people began to even panic. I tried switching it off by holding the power button but nothing was happening. People were just staring all around me.
After about 10 seconds, the beeping stopped and the screen displayed an error message similar to this:
"CRITICAL ERROR: Monitor test FAILED.
No user input was provided."
Moral of the story: Make your program account for all possible options.11 -
Overheard a phone call between the Senior Network Engineer and a contracted Printer-company at 9am this morning. Photocopier was giving a 'functional error' message on-screen and not printing;
N.E:
I logged this call last
Thursday afternoon. Thats 1.5 days of the photocopier not working on our busiest site! Where's the engineer??
.... yes, that's the error message.
Yes, i can log into it, you should have the IP address from the call.
Yes, it's obviously pinging too.
Yes.... we've power-cycled the printer multiple times...
yes, tried that too...
yes, I've unplugged the network cable as well... left it for 15 minutes.
... sorry. What?
What did you say?
Are you f***ing kidding me?
Would you also like me to rub the side of the f***ing machine, and say a prayer while I'm at it??
*takes a deep breath*
Fine, I'll do that but when it doesn't work, i want someone out on the site before lunchtime today!
*slams phone down angrily*
N.E to me as he stomps out of the office;
He wants me to get the user to unplug the network cable and do a power cycle. How the f**k is that going to help? Idiots! Don't know why we have a contract with them, i could do a better job!!!
*comes back into office 5 minutes later*
Me: did it fix it?
NE: yeah. Damn.
*leaves room again to make apologetic phonecall*2 -
3 rants for the price of 1, isn't that a great deal!
1. HP, you braindead fucking morons!!!
So recently I disassembled this HP laptop of mine to unfuck it at the hardware level. Some issues with the hinge that I had to solve. So I had to disassemble not only the bottom of the laptop but also the display panel itself. Turns out that HP - being the certified enganeers they are - made the following fuckups, with probably many more that I didn't even notice yet.
- They used fucking glue to ensure that the bottom of the display frame stays connected to the panel. Cheap solution to what should've been "MAKE A FUCKING DECENT FRAME?!" but a royal pain in the ass to disassemble. Luckily I was careful and didn't damage the panel, but the chance of that happening was most certainly nonzero.
- They connected the ribbon cables for the keyboard in such a way that you have to reach all the way into the spacing between the keyboard and the motherboard to connect the bloody things. And some extra spacing on the ribbon cables to enable servicing with some room for actually connecting the bloody things easily.. as Carlos Mantos would say it - M-m-M, nonoNO!!!
- Oh and let's not forget an old flaw that I noticed ages ago in this turd. The CPU goes straight to 70°C during boot-up but turning on the fan.. again, M-m-M, nonoNO!!! Let's just get the bloody thing to overheat, freeze completely and force the user to power cycle the machine, right? That's gonna be a great way to make them satisfied, RIGHT?! NO MOTHERFUCKERS, AND I WILL DISCONNECT THE DATA LINES OF THIS FUCKING THING TO MAKE IT SPIN ALL THE TIME, AS IT SHOULD!!! Certified fucking braindead abominations of engineers!!!
Oh and not only that, this laptop is outperformed by a Raspberry Pi 3B in performance, thermals, price and product quality.. A FUCKING SINGLE BOARD COMPUTER!!! Isn't that a great joke. Someone here mentioned earlier that HP and Acer seem to have been competing for a long time to make the shittiest products possible, and boy they fucking do. If there's anything that makes both of those shitcompanies remarkable, that'd be it.
2. If I want to conduct a pentest, I don't want to have to relearn the bloody tool!
Recently I did a Burp Suite test to see how the devRant web app logs in, but due to my Burp Suite being the community edition, I couldn't save it. Fucking amazing, thanks PortSwigger! And I couldn't recreate the results anymore due to what I think is a change in the web app. But I'll get back to that later.
So I fired up bettercap (which works at lower network layers and can conduct ARP poisoning and DNS cache poisoning) with the intent to ARP poison my phone and get the results straight from the devRant Android app. I haven't used this tool since around 2017 due to the fact that I kinda lost interest in offensive security. When I fired it up again a few days ago in my PTbox (which is a VM somewhere else on the network) and today again in my newly recovered HP laptop, I noticed that both hosts now have an updated version of bettercap, in which the options completely changed. It's now got different command-line switches and some interactive mode. Needless to say, I have no idea how to use this bloody thing anymore and don't feel like learning it all over again for a single test. Maybe this is why users often dislike changes to the UI, and why some sysadmins refrain from updating their servers? When you have users of any kind, you should at all times honor their installations, give them time to change their individual configurations - tell them that they should! - in other words give them a grace time, and allow for backwards compatibility for as long as feasible.
3. devRant web app!!
As mentioned earlier I tried to scrape the web app's login flow with Burp Suite but every time that I try to log in with its proxy enabled, it doesn't open the login form but instead just makes a GET request to /feed/top/month?login=1 without ever allowing me to actually log in. This happens in both Chromium and Firefox, in Windows and Arch Linux. Clearly this is a change to the web app, and a very undesirable one. Especially considering that the login flow for the API isn't documented anywhere as far as I know.
So, can this update to the web app be rolled back, merged back to an older version of that login flow or can I at least know how I'm supposed to log in to this API in order to be able to start developing my own client?6 -
ARGH. I wrote a long rant containing a bunch of gems from the codebase at @work, and lost it.
I'll summarize the few I remember.
First, the cliche:
if (x == true) { return true; } else { return false; };
Seriously written (more than once) by the "legendary" devs themselves.
Then, lots of typos in constants (and methods, and comments, and ...) like:
SMD_AGENT_SHCEDULE_XYZ = '5-year-old-typo'
and gems like:
def hot_garbage
magic = [nil, '']
magic = [0, nil] if something_something
success = other_method_that_returns_nothing(magic)
if success == true
return true # signal success
end
end
^ That one is from our glorious self-proclaimed leader / "engineering director" / the junior dev thundercunt on a power trip. Good stuff.
Next up are a few of my personal favorites:
Report.run_every 4.hours # Every 6 hours
Daemon.run_at_hour 6 # Daily at 8am
LANG_ENGLISH = :en
LANG_SPANISH = :sp # because fuck standards, right?
And for design decisions...
The code was supposed to support multiple currencies, but just disregards them and sets a hardcoded 'usd' instead -- and the system stores that string on literally hundreds of millions of records, often multiple times too (e.g. for payment, display fees, etc). and! AND! IT'S ALWAYS A FUCKING VARCHAR(255)! So a single payment record uses 768 bytes to store 'usd' 'usd' 'usd'
I'd mention the design decisions that led to the 35 second minimum pay API response time (often 55 sec), but i don't remember the details well enough.
Also:
The senior devs can get pretty much anything through code review. So can the dev accountants. and ... well, pretty much everyone else. Seriously, i have absolutely no idea how all of this shit managed to get published.
But speaking of code reviews: Some security holes are allowed through because (and i quote) "they already exist elsewhere in the codebase." You can't make this up.
Oh, and another!
In a feature that merges two user objects and all their data, there's a method to generate a unique ID. It concatenates 12 random numbers (one at a time, ofc) then checks the database to see if that id already exists. It tries this 20 times, and uses the first unique one... or falls through and uses its last attempt. This ofc leads to collisions, and those collisions are messy and require a db rollback to fix. gg. This was written by the "legendary" dev himself, replete with his signature single-letter variable names. I brought it up and he laughed it off, saying the collisions have been rare enough it doesn't really matter so he won't fix it.
Yep, it's garbage all the way down.16 -
I really have this fucking love/hate relationship with application security.
For a lot of stuff that I write, user input has to be validated, authentication is required and so on and I do love looking into that, pentesting my own applications to death and thinking about the security architecture of the application itself.
But, sometimes, I just want to focus on the fucking features and then it annoys the living hell out of me that securing an application can take so much time and brain power.
Yay and grrrr, I guess.8 -
This rant is particularly directed at web designers, front-end developers. If you match that, please do take a few minutes to read it, and read it once again.
Web 2.0. It's something that I hate. Particularly because the directive amongst webdesigners seems to be "client has plenty of resources anyway, and if they don't, they'll buy more anyway". I'd like to debunk that with an analogy that I've been thinking about for a while.
I've got one server in my home, with 8GB of RAM, 4 cores and ~4TB of storage. On it I'm running Proxmox, which is currently using about 4GB of RAM for about a dozen VM's and LXC containers. The VM's take the most RAM by far, while the LXC's are just glorified chroots (which nonetheless I find very intriguing due to their ability to run unprivileged). Average LXC takes just 60MB RAM, the amount for an init, the shell and the service(s) running in this LXC. Just like a chroot, but better.
On that host I expect to be able to run about 20-30 guests at this rate. On 4 cores and 8GB RAM. More extensive migration to LXC will improve this number over time. However, I'd like to go further. Once I've been able to build a Linux which was just a kernel and busybox, backed by the musl C library. The thing consumed only 13MB of RAM, which was a VM with its whole 13MB of RAM consumption being dedicated entirely to the kernel. I could probably optimize it further with modularization, but at the time I didn't due to its experimental nature. On a chroot, the kernel of the host is used, meaning that said setup in a chroot would border near the kB's of RAM consumption. The busybox shell would be its most important RAM consumer, which is negligible.
I don't want to settle with 20-30 VM's. I want to settle with hundreds or even thousands of LXC's on 8GB of RAM, as I've seen first-hand with my own builds that it's possible. That's something that's very important in webdesign. Browsers aren't all that different. More often than not, your website will share its resources with about 50-100 other tabs, because users forget to close their old tabs, are power users, looking things up on Stack Overflow, or whatever. Therefore that 8GB of RAM now reduces itself to about 80MB only. And then you've got modern web browsers which allocate their own process for each tab (at a certain amount, it seems to be limited at about 20-30 processes, but still).. and all of its memory required to render yours is duplicated into your designated 80MB. Let's say that 10MB is available for the website at most. This is a very liberal amount for a webserver to deal with per request, so let's stick with that, although in reality it'd probably be less.
10MB, the available RAM for the website you're trying to show. Of course, the total RAM of the user is comparatively huge, but your own chunk is much smaller than that. Optimization is key. Does your website really need that amount? In third-world countries where the internet bandwidth is still in the order of kB/s, 10MB is *very* liberal. Back in 2014 when I got into technology and webdesign, there was this rule of thumb that 7 seconds is usually when visitors click away. That'd translate into.. let's say, 10kB/s for third-world countries? 7 seconds makes that 70kB of available network bandwidth.
Web 2.0, taking 30+ seconds to load a web page, even on a broadband connection? Totally ridiculous. Make your website as fast as it can be, after all you're playing along with 50-100 other tabs. The faster, the better. The more lightweight, the better. If at all possible, please pursue this goal and make the Web a better place. Efficiency matters.9 -
Looks like /dev/body got tainted.. nasal memory leaks all over the place 😷
$ kill -9 $(pidof cold)
... Nothing.
$ sudo !!
I said kill the fucking cold!!! Y u no listen to your admin?! 😠
> User condor is not in the sudoers file. This incident will be reported.
RRRRRRRRREEEEEEEEE!!!! 😣😣😣
I just want to finish my goddamn power supply project, instead of getting bed-ridden by a cold, and running through paper towels like there's no tomorrow 😭4 -
So probably about a decade ago at this point I was working for free for a friend's start-up hosting company. He had rented out a high-end server in some data center and sold out virtualized chunks to clients.
This is back when you had only a few options for running virtual servers, but the market was taking off like a bat out of hell. In our case, we used User-Mode Linux (UML).
UML is essentially a kernel hack that lets you run the kernel in user space. That alone helps keep things separate or jailed. I'm pretty sure some of you can shed more light on it, but that's as I understood it at the time and I wasn't too shabby at hacking the kernel when we'd have driver issues.
Anyway, one of the ways my friend would on-board someone was to generate a new disk image file, mount it, and then chroot to that mount path. He'd basically use a stock image to do this and then wipe it out before putting it live.
I'm not sure exactly what he was doing at the time, but I got a panicked message on New Years Day saying that he had deleted everything. By everything, he had done an rm -fr /home as root on what he had thought was the root of a drive image.
It wasn't an image. It was the host server.
In the stoke of a single command, all user data was lost. We were pretty much screwed, but I have a knack for not giving up - so I spent a ton of time investigating linux file recovery.
Fun fact about UML - since the kernel runs in user space as a regular ol' process, anything it opens is attached to that process. I had noticed that while the files were "gone", I could still see disk usage. I ended up finding the images attached to their file pointers associated with each running kernel - and thankfully all customers were running at the time.
The next part was crazy, and I still think is crazy. I don't remember the command, but I had to essentially copy the image from the referenced path into a new image file, then shutdown the kernel and power it back on from the new image. We had configs all set aside, so that was easy. When it finally worked I was floored.
Rinse and repeat, I managed to drag every last missing bit out of /proc - with the only side effect being that all MySQL databases needed to be cleaned up.3 -
So I saw an article where in the author mentioned that "how will we earn money when there are so many adblock users, indirectly blocking out income, so we had to take some measures and that how we initiated coinhive on our websites, where in, it uses minimal cpu power for coin mining of every user that visits that webpage"
WTF, saying minimal, some users commented their saying they experienced sudden over usage of cpu cores and rise in temps while visiting the websites.
How do you justify such behavior, I feel kinda biased as I feel bad for them, but on the other hand, they just shouldn't rely on writing articles as a job/source of income4 -
Fuck brand builders, or, how I learned to start giving a shit and love devrant.
Brand builders are people who generally have very little experience and are attempting to obfuscate their dearth of ability behind a wall of non-academic content generation. Subscribe, like, build a following and everyone will happily overlook the fact that your primary contribution to society is spreading facile content that further obfuscates the need for fundamentals. Their carefully crafted presence is designed promote themselves and their success while chipping away at the apparent value of professional ability. At one point, I thought medium would be the bottom of the barrel; a glorified blog that provides people with scant knowledge, little experience and routinely low integrity a platform to build an echo chamber of replayed or copied content, techno-mysticism and best-practice-superstition they mistake for a brand in an environment where there's little chance of peer review. I thought it couldn't get any worse.
Then I found dev.to
Dev.to is what happens when all the absence of ability and skills insecurity on the internet gets together to form a censorship mob to ensure that no criticism, reality or peer review will ever filter into the ramblings of people intent on forever remaining at the peak of the dunning-kreuger curve. It's the long tail of YMCA trophy culture.
Take for example this article:
https://dev.to/davidepacilio/...
It's a shit post listicle by someone claiming to be "senior," who confidently states that "you are only as good as the tools you use." Meanwhile all the great minds of history are giving him the side-eye because they understand tools are just a magnifier of ability. If you're an amazing carpenter, power tools will help you produce at an exponential rate. If you're a shitty carpenter, your work will still be shit, there will just be more of it. The actual phrase that's being butchered here is "you're only as good as the tools you create." There's no moral superiority to be had in being dependent on a tool, that's just a crutch. A true expert or professional is someone who can create tools to aid in their craft. Being a professional is having a thorough enough understanding of the thing you are doing so as to be able to craft force multipliers that make your work easier, not just someone who uses them.
Ok, so what?
I'm sure he's a plenty fine human to grab drinks with, no ill will to him as a human. That said, were you to comment something to that effect on dev.to, you'd be reported by all the hangers-on pretty much immediately, regardless of how much complimentary padding and passive, welcoming language you wrap your message in. The problem with a bunch of weak people ganging up on the voice of reason and deciding they don't want things like constructive criticism, peer review, academic process or the scientific method is, after you remove all of that, you're just left with a formless sea of ideas and thoughts with no categorization, no order. You find a lot of opinions and nothing to challenge them and thereby are left with no mechanism for strong ideas to rise to the top. In that system, the "correct" ideas are by default those posited by the strongest personality.
We all need some degree of positive reinforcement. We also need to be smacked upside the head when we're totally off in the weeds. It's all about balance. The forums of ancient Greece weren't filled with people fervently agreeing with one another and shouting down new ideas en masse. We need discourse, not demagoguery.
Dev.to, medium, etc are all the fast fashion of the tech industry. Personally, I'd prefer something designed to last a little longer.25 -
The more I use Go, the more i start to like it. I didn’t realize how nice being able to generate binaries for every OS that matters was, until I had that power. It beats the hell out of trying to distribute a Python app for sure.
Sure, it has its warts.
It’s overly bureaucratic in the same way Java is.
I hate that you can’t import something without using it (most people I’d wager preemptively import libraries they know they’re gonna need even if the code isn’t written yet)
I really wish there was a way to just say “See this JSON blob? All those keys and values are strings, trust me, you don’t need me to tell you the type of each one individually.”
Generics would be nice.
I’d kill for exceptions - any decently sized go program is going to have very many if err checks where most could be condensed down to a single try/catch in most other langs.
I wish the tooling was better. Dependency management was a solved problem when Go was released and yet they chose to ship without it. There’s still no standard. Many hours of time have been wasted dinking with this.
But ya know what? Even with those warts, it’s still easier to write than Java. It’s still write once run anywhere, it’s blazing fast, and doesn’t require your end user to install an entire freakin runtime.
<3 Go2 -
2012 laptop:
- 4 USB ports or more.
- Full-sized SD card slot with write-protection ability.
- User-replaceable battery.
- Modular upgradeable memory.
- Modular upgradeable data storage.
- eSATA port.
- LAN port.
- Keyboard with NUM pad.
- Full-sized SD card slot.
- Full-sized HDMI port.
- Power, I/O, charging, network indicator lamps.
- Modular bay (for example Lenovo UltraBay)
- 1080p webcam (Samsung 700G7A)
- No TPM trojan horse.
2024 laptop:
- 1 or 2 USB ports.
- Only MicroSD card slot. Requires fumbling around and has no write-protection switch.
- Non-replaceable battery.
- Soldered memory.
- Soldered data storage.
- No eSATA port.
- No LAN port.
- No NUM pad.
- Micro-HDMI port or uses USB-C port as HDMI.
- Only power lamp. No I/O lamp so user doesn't know if a frozen computer is crashed or working.
- No modular bay
- 720p webcam
- TPM trojan horse (Jody Bruchon video: https://youtube.com/watch/... )
- "Premium design" (who the hell cares?!)11 -
Whatsapp from my mom:
"Hey, what means 'user defined' in WhatsApp?"
Me: "Depends. Where do you see it?"
Her: "Beneath user info and number"
Me: "Press the Power Button and Volume Down and send me a screenshot please, I have no clue"
Her: "What is the Power Button?"
SERIOUSLY???3 -
Just now I realized that for some reason I can't mount SMB shares to E: and H: anymore.. why, you might ask? I have no idea. And troubleshooting Windows.. oh boy, if only it was as simple as it is on Linux!!
So, bimonthly reinstall I guess? Because long live good quality software that lasts. In a post-meritocracy age, I guess that software quality is a thing of the past. At least there's an option to reset now, so that I don't have to keep a USB stick around to store an installation image for this crap.
And yes Windows fanbois, I fucking know that you don't have this issue and that therefore it doesn't exist as far as you're concerned. Obviously it's user error and crappy hardware, like it always is.
And yes Linux fanbois, I know that I should install Linux on it. If it's that important to you, go ahead and install it! I'll give you network access to the machine and you can do whatever you want to make it run Linux. But you can take my word on this - I've tried everything I could (including every other distro, custom kernels, customized installer images, ..), and it doesn't want to boot any Linux distribution, no matter what. And no I'm not disposing of or selling this machine either.
Bottom line I guess is this: the OS is made for a user that's just got a C: drive, doesn't rely on stuff on network drives, has one display rather than 2 (proper HDMI monitor recognition? What's that?), and God forbid that they have more than 26 drives. I mean sure in the age of DOS and its predecessor CP/M, sure nobody would use more than 26 drives. Network shares weren't even a thing back then. And yes it's possible to do volume mounts, but it's unwieldy. So one monitor, 1 or 2 local drives, and let's make them just use Facebook a little bit and have them power off the machine every time they're done using it. Because keeping the machine stable for more than a few days? Why on Earth would you possibly want to do that?!!
Microsoft Windows. The OS built for average users but God forbid you depart from the standard road of average user usage. Do anything advanced, either you can't do it at all, you can do it but it's extremely unintuitive and good luck finding manuals for it, or you can do it but Windows will behave weirdly. Because why not!!!12 -
It's my second rant about Windows here in two days, but here we go:
Windows used to be a cool OS (and in part it still is). Yes, it's made for the end user, not power users, yes it has many flaws. But it was my gateway to computers and programming. I have fond memories of my first PC, playing around with the old win98 themes (my favorite was the baseball one!).
However, I am very disappointed now. I just had to basically force Windows 10 to stop hogging my bandwidth. It was an actual battle, with the OS simply (I kid you not) running update and other services EVEN AFTER I SPECIFICALLY DISABLED THEM. I just saw the Windows update service running, while its status was disabled. It's absurd.
Sorry Windows, but that's not what I want. I want to choose what happens on my own OS. Linux gives me exactly that, why can't you?11 -
Another "prank" that I did at my school when I was 13:
Changed the password for the admin user with "net user *" and took control over alot of PC's in my school. I used that power to install keyloggers and then got alot of passwords for popular social networks that was popular that that time.
Always fun to upload picture ultrasound picture and write something, their parents would always go crazy.
And again, never got caught
(I starting to realize that I am a real asshole)2 -
I do not like the direction laptop vendors are taking.
New laptops tend to feature fewer ports, making the user more dependent on adapters. Similarly to smartphones, this is a detrimental trend initiated by Apple and replicated by the rest of the pack.
As of 2022, many mid-range laptops feature just one USB-A port and one USB-C port, resembling Apple's toxic minimalism. In 2010, mid-class laptops commonly had three or four USB ports. I have even seen an MSi gaming laptop with six USB ports. Now, much of the edges is wasted "clean" space.
Sure, there are USB hubs, but those only work well with low-power devices. When attaching two external hard drives to transfer data between them, they might not be able to spin up due to insufficient power from the USB port or undervoltage caused by the impedance (resistance) of the USB cable between the laptop's USB port and hub. There are USB hubs which can be externally powered, but that means yet another wall adapter one has to carry.
Non-replaceable [shortest-lived component] mean difficult repairs and no more reserve batteries, as well as no extra-sized battery packs. When the battery expires, one might have to waste four hours on a repair shop for a replacement that would have taken a minute on a 2010 laptop.
The SD card slot is being replaced with inferior MicroSD or removed entirely. This is especially bad for photographers and videographers who would frequently plug memory cards into their laptop. SD cards are far more comfortable than MicroSD cards, and no, bulky external adapters that reserve the device's only USB port and protrude can not replace an integrated SD card slot.
Most mid-range laptops in the early 2010s also had a LAN port for immediate interference-free connection. That is now reserved for gaming-class / desknote laptops.
Obviously, components like RAM and storage are far more difficult to upgrade in more modern laptops, or not possible at all if soldered in.
Touch pads increasingly have the buttons underneath the touch surface rather than separate, meaning one has to be careful not to move the mouse while clicking. Otherwise, it could cause an unwanted drag-and-drop gesture. Some touch pads are smart enough to detect when a user intends to click, and lock the movement, but not all. A right-click drag-and-drop gesture might not be possible due to the finger on the button being registered as touch. Clicking with short tapping could be unreliable and sluggish. While one should have external peripherals anyway, one might not always have brought them with. The fallback input device is now even less comfortable.
Some laptop vendors include a sponge sheet that they want users to put between the keyboard and the screen before folding it, "to avoid damaging the screen", even though making it two millimetres thicker could do the same without relying on a sponge sheet. So they want me to carry that bulky thing everywhere around? How about no?
That's the irony. They wanted to make laptops lighter and slimmer, but that made them adapter- and sponge sheet-dependent, defeating the portability purpose.
Sure, the CPU performance has improved. Vendors proudly show off in their advertisements which generation of Intel Core they have this time. As if that is something users especially care about. Hoo-ray, generation 14 is now yet another 5% faster than the previous generation! But what is the benefit of that if I have to rely on annoying adapters to get the same work done that I could formerly do without those adapters?
Microsoft has also copied Apple in demanding internet connection before Windows 11 will set up. The setup screen says "You will need an Internet connection…" - no, technically I would not. What does technically stand in the way of Windows 11 setting up offline? After all, previous Windows versions like Windows 95 could do so 25 years earlier. But also far more recent versions. Thankfully, Linux distributions do not do that.
If "new" and "modern" mean more locked-in and less practical and difficult to repair, I would rather have "old" than "new".10 -
Chrome, Firefox, and yes even you Opera, Falkon, Midori and Luakit. We need to talk, and all readers should grab a seat and prepare for some reality checks when their favorite web browsers are in this list.
I've tried literally all of them, in search for a lightweight (read: not ridiculously bloated) web browser. None of them fit the bill.
Yes Midori, you get a couple of bonus points for being the most lightweight. Luakit however.. as much as I like vim in my terminal, I do not want it in a graphical application. Not to mention that just like all the others you just use webkit2gtk, and therefore are just as bloated as all the others. Lightweight my ass! But programmable with Lua, woo! Not like Selenium, Chrome headless, ... does that for any browser. And that's it for the unique features as far as I'm concerned. One is slow, single-threaded and lightweight-ish (Midori) and another has vim keybindings in an application that shouldn't (Luakit).
Pretty much all of them use webkit2gtk as their engine, and pretty much all of them launch a separate process for each tab. People say this is more secure, but I have serious doubts about that. You're still running all these processes as the same user, and they all have full access to the X server they run under (this is also a criticism against user separation on a single X session in general). The only thing it protects against is a website crashing the browser, where only that tab and its process would go down. Which.. you know.. should a webpage even be able to do that?
But what annoys me the most is the sheer amount of memory that all of these take. With all due respect all of you browsers, I am not quite prepared to give 8 fucking gigabytes - half the memory in this whole box! - just for a dozen or so tabs. I shouldn't have to move my web browser to another lesser used 16GB box, just to prevent this one from going into fucking swap from a dozen tabs. And before someone has a go at the add-ons, there's 4 installed and that's it. None of them are even close to this complete and utter memory clusterfuck. It's the process separation. Each process consumes half a GB of memory, and there's around a dozen of them in a usual browsing session. THAT is the real problem. And I want to get rid of it.
Browsers are at their pinnacle of fucked up in my opinion, literally to the point where I'm seriously considering elinks. Being a sysadmin, I already live my daily life in terminals anyway. As such I also do have resources. But because of that I also associate every process with its cost to run it, in terms of resources required. Web browsers are easily at the top of the list.
I want to put 8GB into perspective. You can store nearly 2 entire DVD movies in that memory. However media players used to play them (such as SMPlayer) obviously don't do that. They use 60-80MB on average to play the whole movie. They also require far less processing power than YouTube in a web browser does, even when you download that exact same video with youtube-dl (either streamed within the media player or externally). That is what an application should be.
Let's talk a bit about these "complicated" websites as well. I hate to break it to you framework web devs, but you're a dime a dozen. The competition is high between web devs for that exact reason. And websites are not complicated. The document itself is plain old HTML, yes even if your framework converts to it in the background. That's the skeleton of your document, where I would draw a parallel with documents in office suites that are more or less written in XML. CSS.. oh yes, markup. Embolden that shit, yes please! And JavaScript.. oh yes, that pile of shit that's been designed in half a day, and has a framework called fucking isEven (which does exactly what it says on the tin, modulo 2 be damned). Fancy some macros in your text editor? Yes, same shit, different pile.
Imagine your text editor being as bloated as a web browser. Imagine it being prone to crashing tabs like a web browser. Imagine it being so ridiculously slow to get anything done in your productivity suite. But it's just the usual with web browsers, isn't it? Maybe Gopher wasn't such a bad idea after all... Oh and give me another update where I have to restart the browser when I commit the heinous act of opening another tab, just because you had to update your fucking CA certs again. Yes please!19 -
TLDR: Find a website that requires a subscription but doesn't check their cookies' integrity, now I'm on a website for free.
>be me
>wonder if it's possible to intercept browser data
>download Wireshark
>download Fiddler
>find that none of these really fit me
>go to youtube, search how to intercept POST data
>find something called BurpSuite
>Totally what I was looking for
>start testing BurpSuite on devrant
>neat!
>I can see all the data that's being passed around
>wonder if I can use it on a website where my subscription recently ended.
>try changing my details without actually inputting anything into the website's form
>send the data to the server
>refresh the page
>it worked
>NEAT!
>Huh what's this?
>A uid
>must be a userID
>increment it by 1 and change some more details
>refresh the page
>...
>didn't work 😐
>Hmmm, let's try forwarding the data to the browser after incrementing the uid
>OH SHIT
>can see the details of a different user
>except I see his details are the details I had entered previously
>begin incrementing and decrementing the uid
>IFINITE POWER
>realize that the uid is hooked up to my browsers local cookie
>can see every user's details just by changing my cookie's uid
>Wonder if it's possible to make the uid persistent without having to enter it in every time
>look up cookie manipulator
>plug-in exists
>go back to website
>examine current uid
>it's my uid
>change it to a different number
>refresh the webpage
>IT FUCKING WORKED
>MFW I realize this website doesn't check for cookie integrity
>MFW I wonder if there are other websites that are this fucking lazy!!!
>MFW they won't fix it because it would require extra work.
>MFuckingFW they tell me not to do it again in the future
>realize that since they aren't going to fix it I'll just put myself on another person's subscription.5 -
Tech Lead: We need to exclude logged in user from our all users API as we don't want to show user's self card on the frontend with other users.
Me (Backend dev): This should be handled by the frontend and they should exclude it by a condition in their loop:
If (user.id != loggedUser.id)
{
// Add card
}
We also need self user at several other places.
Tech Lead: Create a query param filter for that.
Me: We should keep our APIs as generic as possible.
(Real thing starts)
Tech Lead: Which has more processing power frontend or backend?
Me (confused): Backend
Tech Lead: This will add a break to our loop and Do you know how much processing power it will take because of this condition?
Me (dead): WHAAAA....?18 -
A plain computer illiterate guy rings tech support to report that his computer is faulty.
Tech: What's the problem?
User: There is smoke coming out of the power supply.
Tech: (keeps quiet for the moment)
Tech: You'll need a new power supply.
User: No, I don't! I just need to change the startup files.
Tech: Sir, the power supply is faulty. You'll need to replace it.
User: No way! Someone told me that I just needed to change the startup and it will fix the problem! All I need is for you to tell me the command.
Tech support: 10 minutes later, the User is still adamant that he is right. The tech is frustrated and fed up.
Tech support: (hush hush)
Tech: Sorry, Sir. We don't normally tell our customers this, but there is an undocumented DOS command that will fix the problem.
User: I knew it!
Tech: Just add the line LOAD NOSMOKE <nosmoke> at the end of the CONFIG.SYS. Let me know how it goes.
10 minutes later.
User: It didn't work. The power supply is still smoking.
Tech: Well, what version of DOS are you using?
User: MS-DOS 6.22.
Tech: That's your problem there. That version of DOS didn't come with NOSMOKE. Contact Microsoft and ask them for a patch that will give you the file. Let me know how it goes.
1 hour later.
User: I need a new power supply.
Tech: How did you come to that conclusion?
Tech: (hush hush)
User: Well, I rang Microsoft and told him about what you said, and he started asking questions about the make of the power supply.
Tech: Then what did he say?
User: He told me that my power supply isn't compatible with NOSMOKE.3 -
Pull-to-refresh is useless.
If you are a mobile app developer, please get rid of pull-to-refresh. Your users will thank you.
I have the impression that mobile app developers choose to implement the pull-to-refresh gimmick just in order to make their app comply with a design trend. It seems like a desperate attempt to appear "modern" and "fancy", not because of the actual usefulness of the gesture.
Pull-to-refresh is one of those things that are well-intended but backfire. It appears helpful on first sight, but turns out to be a burden.
It takes effort and cognitive strain to avoid triggering a pull-to-refresh. The user can't use the app relaxed but has to walk on eggshells.
Every unwanted refresh wastes battery power, mobile data (if it is an Internet-connected app), and can lead to the loss of form data.
To avoid pull-to-refresh, the user has to resort to finger gymnastics like a shorter swipe for scrolling up or swiping slightly up before down. Pull-to-refresh could even be triggered while pinch-zooming in or out near the top of a page, if the touchscreen does not recognize one of the two fingers.
Pull-to-refresh also interferes with the double-tap-swipe zoom gesture. If one of the two taps are not recognized, a swipe-down to zoom in can trigger a pull-to-refresh instead.
To argue "if you don't like pull-to-refresh, just don't use it" is like blaming a person who stepped on a mine, since the person moved and the mine was stationary.
A refresh button can be half a second away in the menu bar, URL bar, or a submenu, where it is unlikely to be pressed accidentally. There is no need for a gesture that does more harm than good.
Using a mobile app with pull-to-refresh feels like having Windows StickyKeys forcibly enabled at all times. The refresh circle animation sticks to the finger.
If the user actually wants to refresh, pull-to-refresh is slower than a refresh button in a menu if the page is not at the top, meaning pull-to-refresh is useless as a shortcut anyway if the page is in any other position than the top.
An alternative to pull-to-refresh is pull-for-details. Samsung did it in some of their apps. Pulling down against the top reveals additional information such as the count and total size of selected items.
If you own a website, add this CSS to make browsing your website on the pre-installed Android web browser not a headache:
html,body { overscroll-behavior: none; }
Why is this necessary? In 2019, Google took the ability to deactivate the pull-to-refresh gesture on their Chrome browser for Android OS away from users. On Chrome for Android, pull-to-refresh can only be disabled on the server side, not the user side. The avalanche of complaints? Neglected.
Good thing several third-party browsers let the user turn off this severe headache. 12
12 -
Switched back to windows because I needed IIS for work and I did miss having a touch screen (could not get driver working on Linux).
A few gripes.
I mean, the standard "oh great, half a day downloading and updating my machine" applies.
The thing I forgot about Windows is that after everything I do it wants to restart. Updating itself forced the computer to restart several times, wtf.
Powershell (ironically) holds a shadow of bash's power
So many "power user" actions are done with a gui, dear lord give me a terminal command and a man page any day over the convoluted way to do some actions. Changing permissions for IIS was several layers of gui dialogues, where it would be a couple of commands in bash.
Sorry to be unoriginal and moan about an OS, as an end user windows is great and a lot more streamlined and arguably prettier, but as a programmer it doesn't make life half as easy as the realm of *nix1 -
Ah, developers, the unsung heroes of caffeine-fueled coding marathons and keyboard clacking symphonies! These mystical beings have a way of turning coffee and pizza into lines of code that somehow make the world go 'round.
Have you ever seen a developer in their natural habitat? They huddle in dimly lit rooms, surrounded by monitors glowing like magic crystals. Their battle cries of "It works on my machine!" echo through the corridors, as they summon the mighty powers of Stack Overflow and Google to conquer bugs and errors.
And let's talk about the coffee addiction – it's like they believe caffeine is the elixir of code immortality. The way they guard their mugs, you'd think it's the Holy Grail. In fact, a developer without coffee is like a computer without RAM – it just doesn't function properly.
But don't let their nerdy exteriors fool you. Deep down, they're dreamers. They dream of a world where every line of code is bug-free and every user is happy. A world where the boss understands what "just one more line of code" really means.
Speaking of bosses, developers have a unique ability to turn simple requests into complex projects. "Can you make a small tweak?" the boss asks innocently. And the developer replies, "Sure, it's just a minor change," while mentally calculating the time it'll take and the potential for scope creep.
Let's not forget their passion for acronyms. TLA (Three-Letter Acronym) is their second language. API, CSS, HTML, PHP, SQL... it's like they're playing a never-ending game of Scrabble with abbreviations.
And documentation? Well, that's their arch-nemesis. It's as if writing clear instructions is harder than debugging quantum mechanics. "The code is self-explanatory," they claim, leaving everyone else scratching their heads.
In the end, developers are a quirky bunch, but we love them for it. Their quirks and peculiarities are what make them the creative, brilliant minds that power our digital world. So here's to developers, the masters of logic and the wizards of the virtual realm!12 -
I am a mechanical engineer first and my companies go to sysadmin second. So software developing isnt really my main field of expertise buuttt:
WHY IS SLOOPY SOFTWARE WRITING A VIABLE EXCUSE?
Story:
Yesterday i started to migrate some stuff from our old Win 2008 Server to the new 2016. Turns out there are some MS SQL Express Servers running. Quick check for what they are turns out that they are activly used. So far so good. For other reasons we have a new MSSQL 2017 Core Licence. So i thought, hey it would be nice to just move those 2012, 2008 and 2014 Express Servers to a real one that can use the entire machines capabilities.
After some try & error with exporting one of the softwares (where i had to elevate one the user rights to sysadmin for reasons) the entire system stopped working. I didnt deleted anything or changed anything! Well, i elevated user rights. After 2 hours of support call it turns out that the software stopped working cause i gave the database user sysadmin rights. I dont know enough about MSSQL to judge wether that is logical or not, but it sounds super illogical and i suspect sloopy software writing on the manufacturers part. One way or another, the excuse from the telephone support was "yeah, our software is a very fragile child"
Okay.
After i told all that my coworkers two of them were also "yeah, that is just how the [company] software is, you have to be careful with it"
Apparently it broke in the past for other minor stuff.
As an engineer i cannot build bridges that collapse when you use the left and the right lane at the same time. For an architect it isnt okay to build an house where the front door explodes when you open a window. It is not okay for a power tool to go out in a fireball when you accidently drill plastic with it. But for some weird reasons its socially acceptable for programs to be sloopy, buggy and only working under specific conditions. Since when is it okay for a car only to work when you know specific steps to make it run? Like, throwing your spare key in the gas tank, the kick the left wheel exactly three times and finally tapping the steering wheel 5 times left, 4 times right. What? That would be ridiculous? But that is exactly how that software works. You have to follow a specific step guide to make it work, EVERY TIME.
I. JUST. DONT. GET. IT3 -
I have a little big question
I don't have electricity most of the time but the ethernet cable from my internet provider is still working if i plug it in my laptop.
Except that i have to setup the credential from the provider, user and password.
Now!
I want to plug the ethernet into the raspberry pi (3B+) make it work , because idk where should i enter the credentials and then make hotspot so i can have a router powered up from the power bank.
A pi as router
Is it possible?
Because so far i have seen people who connect the pi to the router but mine requires electricity as any other else.
?? Welp14 -
- a split keyboard with a touchpad in the middle that will let you control all gestures on a computer
- a set of desk/monitors that adjusts perfectly for ergo for anyone
- a vertical laptop dock that is modular so you can add extra memory/video processing power and only using your laptop as a CPU/secondary graphics card
- a set of kitchenware and plates that would be so easy to clean and would never get stained
-an insect home alarm system that tells you where the fucking insect is so it doesn't take you by surprise/you can call someone to remove it
- a clothing brand that has a buy one gift one operation mechanic, where you buy a shirt and an article is donated to a local charity
- a restaurant
- a simple, yet robust database option that walks users through creating good databases that is super user friendly
- an app that takes tattoo designs in any format, converts them, allows for editing, and then can hook up to a special printer that gives you the transfer you will use on the client22 -
Done and redone but it's been a long time coming and it's my turn : fuck you StackOverflow.
I've been a member for a few years, and I hate the elitist idiotic community. Some people are there to help, most of them are just there to wank on their reputation.
Whenever you ask a question that is tiny bit specific, you are almost certain to have a vote to close it because "it's too vague" -even though I spent 30mn writing it with comprehensive examples, clean formatting and other users understood it perfectly as demonstrated by their comments trying to help- or any other reason that scream "I didn't understand the question or don't have the answer therefore it's a bad question"
If you are "lucky", a power user will just mark it as duplicate of another question that barely uses the same stack as yours and has one keyword in common because this illiterate fuck couldn't bother to read the full question detailing why it's not a duplicate but, oh surprise, the question they referred yours too already has an accepted answer by themselves. Abusing their reputation-bestowed powers to reference themselves for some more reputation.
Now that I am over 1k in reputation and have all 3 colours of badges, it seems like it warrants a bit more attention from the swarm and it doesn't happen as often. Which is appalling in itself, basically if you don't have enough shinys, your are considered a worthless piece of crap barely tolerated to ask questions.
The fact that big reputation users have so much power and can absolutely not be held accountable for their abusive behaviour is a recipe for power abuse3 -
its been there since many years, but:
When did we turned the wrong way and made it acceptable that Windows can blantly say in my face that i cannot deactivate the transmission of data unless i have the "Business" Variant of their Software. Its called Windows 10 PROFESSIONAL. Why are there no international Laws against that? Where was the molotov throwing mob when this became the norm?
Additonally. that cute telemetry service consumes a considerable amount of cpu and disk power from time to time.
and no, Linux is not an alternative. It never was. There is proprietary software and driver sets used for lab equipment and machines that cannot run under linux, noone will ever have the time to tool something for it and the user base is too specific to hope for any community solution.
sidenote: even Level 0 STILL transmits data. I want mode -1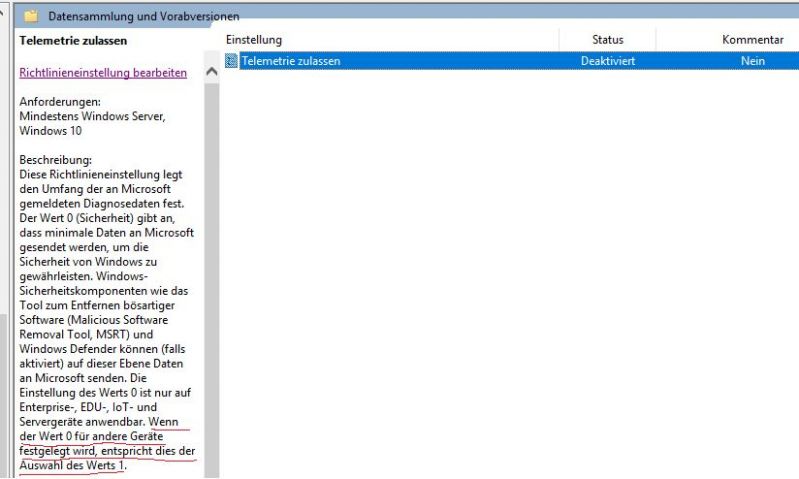 4
4 -
About slightly more than a year ago I started volunteering at the local general students committee. They desperately searched for someone playing the role of both political head of division as well as the system administrator, for around half a year before I took the job.
When I started the data center was mostly abandoned with most of the computational power and resources just laying around unused. They already ran some kvm-hosts with around 6 virtual machines, including a cloud service, internally used shared storage, a user directory and also 10 workstations and a WiFi-Network. Everything except one virtual machine ran on GNU/Linux-systems and was built on open source technology. The administration was done through shared passwords, bash-scripts and instructions in an extensive MediaWiki instance.
My introduction into this whole eco-system was basically this:
"Ever did something with linux before? Here you have the logins - have fun. Oh, and please don't break stuff. Thank you!"
Since I had only managed a small personal server before and learned stuff about networking, it-sec and administration only from courses in university I quickly shaped a small team eager to build great things which would bring in the knowledge necessary to create something awesome. We had a lot of fun diving into modern technologies, discussing the future of this infrastructure and simply try out and fail hard while implementing those ideas.
Today, a year and a half later, we look at around 40 virtual machines spiced with a lot of magic. We host several internal and external services like cloud, chat, ticket-system, websites, blog, notepad, DNS, DHCP, VPN, firewall, confluence, freifunk (free network mesh), ubuntu mirror etc. Everything is managed through a central puppet-configuration infrastructure. Changes in configuration are deployed in minutes across all servers. We utilize docker for application deployment and gitlab for code management. We provide incremental, distributed backups, a central database and a distributed network across the campus. We created a desktop workstation environment based on Ubuntu Server for deployment on bare-metal machines through the foreman project. Almost everything free and open source.
The whole system now is easily configurable, allows updating, maintenance and deployment of old and new services. We reached our main goal for this year which was the creation of a documented environment which is maintainable by one administrator.
Although we did this in our free-time without any payment it was a great year with a lot of experience which pays off now. -
I am sick of misrotated videos.
Sometimes, the phone camera software saves a video vertically because the user hits "record" before the software has detected that the user is holding the smartphone horizontally, because the software stupidly launches in vertical orientation by default.
So the software wants the user to wait until it has finally detected horizontal orientation, which causes the user to miss out on a moment.
How about the camera software actually saves the video in the orientation it was recorded in for the most time, rather than only the beginning of the video?
If I can think of this idea, billion-dollar companies surely can.
In the meantime, misrotated videos can be fixed using this ffmpeg command on Linux or Windows:
ffmpeg -i input_file.mp4 -metadata:s:v rotate="0" -c copy output_file.mp4
And if the phone was held with the home button to the left side:
ffmpeg -i input_file.mp4 -metadata:s:v rotate="180" -c copy output_file.mp4
This solution is superior compared to using -vf (video filters) because it only touches the metadata of the video. No re-encoding. This means no quality loss and no CPU/GPU power needed to process the video again. It just passes through. 10
10 -
So I was reading a comment where someone said that Windows is sure as hell not polished, just 'psychologically pleasing.' I get that, and I've tried to main with Mint Cinnamon/KDE for a while, and I've tried so many distro, but I have too many issues with Linux to make it a true daily workstation and personal os.
For example, Windows apps typically have installers, graphical ones, which allow you to choose an install location and stuff. Does apt or yum do that? Not unless you use some crazy parametets or some shit.
Okay, fine, what if you DON'T CARE about everything being open source and you just want your 3-monitor Nvidia setup to work without vsync issues? Also a PITA, need to do either cmdline driver install and co fig or some other complicated shit.
I may be considered a power user, but damn if Linux isn't friendly to windows users. Don't get me wrong, I don't like windows, but so far it's the best option for me versus aillion Linux issues. Get me something that functions like Windows on multiple levels (Aesthetic not completely required, but core functionality of programs is.) and only then can I attempt a full migration.6 -
Hello! My name is opalqnka and I am a Windows user.
I followed the 12-step program and now I am a step away to being certified LPIC Linux Engineer.
As step 12 preaches, here I humbly share the Program:
1. We admitted we were powerless over Windows - that our lives had become unmanageable.
2. Came to believe that a Power greater than ourselves could restore us to sanity.
3. Made a decision to turn our will and our lives over to the care of Linus as we understood Him.
4. Made a searching and fearless moral inventory of ourselves.
5. Admitted to Linus, to ourselves and to another human being the exact nature of our wrongs.
6. We’re entirely ready to have Linus remove all these defects of character.
7. Humbly asked Him to remove our shortcomings.
8. Made a list of all persons we had harmed, and became willing to make amends to them all.
9. Made direct amends to such people wherever possible, except when to do so would injure them or others.
10. Continued to take personal inventory and when we were wrong promptly admitted it.
11. Sought through bash scripting and kernel troubleshooting to improve our conscious contact with Linus as we understood Him, praying only for knowledge of His will for us and the power to carry that out.
12. Having had a spiritual awakening as the result of these steps, we tried to carry this message to Windows users and to practice these principles in all our affairs.4 -
Just found out my phone (stock, no root) has user-settable minimum DPI? The battery saver thing drops the DPI some and auto-adjusts the DPI and resolution to save power, but I didn't know I could set it... (Minimum 320 DPI, max 960 DPI)
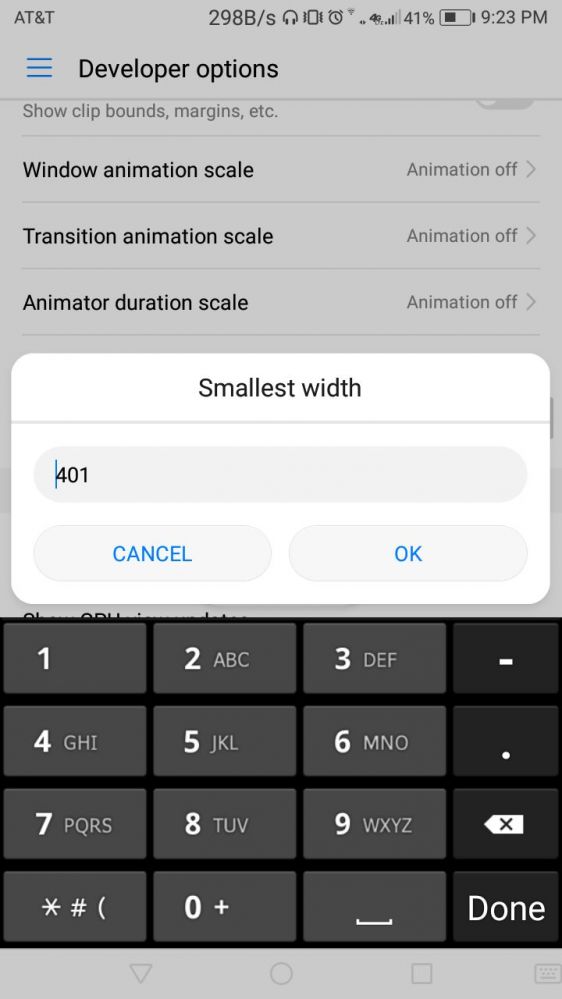 6
6 -
Security is a joke. And people don't seem to get it. Especially Data mungers.
I've spent about half an hour trying to work out how to securely connect to power BI using PowerShell in a renewable manner for unattended access later on.
Every single example I've found seems to involve you storing $user and $password variables inside your script. If I'm lucky, they're going to pass them through ConvertTo-SecureString. And nobody talks about securely storing AD auth tokens, or using the Windows Credential Manager.
I know it's possible, but it's going to take me ages to work out how from all sorts of disparate sources...16 -
I've had a Xiaomi Mi 8 for a few months now. Although I'm impressed by what I got for the amount I paid (a phone that cost about $250 for 6GB RAM, Snapdragon 845, Android 9 and premium build quality is quite a steal), it definitely comes with a consequence.
MIUI (specifically MIUI 11) is godawful. It is single-handedly the worst Android ROM I've ever used since my shitty Android 2.2 phone back around 2010. If you're gonna buy a Xiaomi phone, plan to install Lineage OS on it (but even that's a pain which I'll explain why later).
- Navigation buttons don't hide while watching a video.
Why? God only knows. The ONLY way to bypass without root this is to use its garbage fullscreen mode with gestures, which is annoying as all hell.
- 2 app info pages?
Yeah, the first one you can access just by going to its disaster of a settings app, apps, manage apps and tap on any one.
The 2nd one you can access through the app info button in any 3rd party launcher. Try this: Download Nova launcher, go to the app drawer, hold on any app and tap "app info", and you'll see the 2nd one.
Basically, instead of modifying Android's FOSS source code, they made a shitty overlay. These people are really ahead of their time.
- Can only set lock screen wallpapers using the stock Gallery app
It's not that big an issue, until it is, when whatever wallpaper app you're using only allows you to set the wallpaper and not download them. I think this is both a fuckup on Xiaomi and (insert wallpaper app name here), but why Xiaomi can't include this basic essential feature that every other Android ROM ever made has is beyond me.
- Theming on MIUI 11 is broken
Why do they even bother having a section to customize the boot animation and status bar when there's not one goddamn theme that supports it? At this point you're only changing the wallpaper and icon pack which you can do on any Android phone ever. Why even bother?
They really, REALLY want to be Apple.
Just look at their phones. They're well designed and got good specs, but they don't even care anymore about being original. The notch and lack of a headphone jack aren't features, they're tremendous fuckups by the dead rotting horse known as Apple that died when Steve Jobs did.
Xiaomi tries to build a walled garden around an inherently customizable OS, and the end result is a warzone of an Android ROM that begs for mercy from its creator. Launchers integrate horribly (Does any power user actually use anything that isn't Nova or Microsoft launcher?), 3rd party themes and customization apps need workarounds, some apps don't work at all. People buy from Xiaomi to get a high end budget Android phone at the price of some ads and data collection, not a shitter iOS wannabe.
They really, REALLY want you to have a sim card
If you don't have a sim card and you're using your phone for dev stuff, you're a 2nd class citizen to Xiaomi. Without one, you can't:
- Install adb through adb
- Write to secure settings
- Unlock your bootloader and get away from this trash Android ROM
What's the point? Are they gonna shadow ban you? Does anyone contact them to unlock their bootloader saying "yeah I wanna use a custom rom to pirate lizard porn and buy drugs"? They made this 1000000000x harder than it needs to be for no reason whatsoever. Oh yeah and you gotta wait like a week or something for them to unlock it. How they fucked up this bad is beyond me.
So yeah. Xiaomi. Great phones, atrocious OS. 11
11 -
"New facebook dating service! It's absolutely free! Just sign this user agreement and durable power of attorney. We promise we won't rape you with it later. "
It's a joke now, but probably not for much longer. -
There are a couple:
A system that updates user accounts to connect them into our wifi system by parsing thousands of processing files written in Clojure. The project was short lived and mainly experimental, It has complete test cases and the jar generated from it is still purring silently on the main application. It was used to replace an $85k vendor application that made no fucking sense. The code has not been touched in 2 years and the jar is still there. The dba mentioned the solution to the vendor, the vendor tried buying it from me, but being that it belongs to the institution nothing was touched, still, it got the VP's attention that I can make programs that would be bought for that level, it caught his attention even more when I showed him the codebase and he recognized a Lisp variant (he is old, and was back in the day a Fortran and Cobol developer)
A small Python categorical ML program that determines certain attributes of user generated data and effectively places them on the proper categories on the main DB. The program generates estimates of the users and the predictions have a 95% correctness rate. The DBA still needs to double check the generated results before doing the db updates. I don't remember how I coded it because I was mostly drunk when I experiment on the scenario. It also got the attention of the VP and director since the web tech manager was apparently doing crazy ML shit that they were not expecting me to do, it made them paranoid that I would eventually leave for a ML role somewhere, still here, but I want more moneys!!
A program that generates PDF documentation from user data, written in Go, Python and Perl (yes Perl) I even got shit from the lead developer since I used languages outside of their current scope of work. Dude had no option but to follow along with it :P since I am his boss
Many more. I am normally proud of my work code. But my biggest moment is my current ntural language processing unit that I am trying to code for my home, but I don't have enough power to build it with my computers, currently, my AI is too stupid, but sometimes it does reply back to my commands and does the things I ask it to do (simple things, opening a browser, search for a song etc) but 7 times out of ten it wont work :P -
!rant
Here's a peek at the current state of the service that I'm developing as a side project(plenty of time meanwhile searching for job).
It's a renting service, more automated and with more(and better, imo) search criterias. By automated I mean that I don't have to scroll through search results half backed with poor filters. You create a search, the search will iterate as soon as there is process power in the queue of the searches, and when it's done it will notify you(in different ways(communication channels) and different times, all setup by the user)
.NET Core 2 is the reference framework for the backend; HTML5,Razor, SCSS,JS for front-end.
What do you think about?
(https://thepra.github.io/previewRen... for more pictures) 2
2 -
For what fucking reason the ability to set the date and time programatically has been blocked on Android?!
Why you can create fucking invisible apps that work in the background, mine cryptos, steal your data but they decided that something like that is considered dangerous?
Can anyone give me a logical explanation?
P.S.
There are cases (big pharma companies) where the users don't have access to internet nor a ntp server is available on the local network, so the ability for an app to get the time of a sql server and set it in runtime is crucial, expecially when the user, for security reasons, can't have access to the device settings and change it by himself.
"System apps" can do it, but you would have to change the firmware of a device to sideload an external "System app" and in that case it would lose the warranty.
So, yeah, fucking Google assholes, there are cases where your dumb decisions make the others struggle every other day.
Give more power to third party developers, dumb motherfuckers.
It's not that difficult to ask the user, once, to give the SET_TIME permission.
It was possible in the past...
P.S.2
Windows Mobile 6.5 was a masterpiece for business.
It still could be, just mount better CPUs on PDAs and extend the support. But no, "Android is the future". What a fucking bad future. 10
10 -
If I was Marc Zuckerberg I would also be abandoning ship as quietly as possible.
https://cnbc.com/2018/03/...
I would realize that you can only prey on the world’s emotions of loneliness and boredom for so long before even the sheep realize they are being led to slaughter.
https://amazon.ca/Hooked-How-Build-...
I really don’t blame Facebook for this at all. The fact is that sheep need to be led by someone. That combined with the fact that absolute power corrupts absolutely was a recipe for massive success and then a decline.
Full Disclosure: While I am an infrequent user of FB I have always felt it was toxic and a tire-fire. Everyone around me disagreed so I came to he conclusion I was wrong and just phased it out of my life. Reading Nir Eyal’s book confirmed that the negatives outweighed the positives of FB. So, I am likely not the one to assess the value of FB in most peoples lives. However, I am inclined to think that most perceived value received is simply a fallacy.
But, if you think Facebook (besides
Messenger) actually provides value to your life I would really love to hear it! That’s not an empty challenge either, I would actually love to learn more about its value to you!4 -
Multi User, One Account, and other shit
I'm gonna rant about something as a user, and someone who makes stupid web stuff.
My bank has been updating their web banking over time and they decided that every individual on an account, should have their own login. They really want to push this on their users, I suspect specifically folks like me and my wife who share one login for the joint accounts we have at the bank together.
Why share one login, because it's the only sure fire way I know that I and my wife can see all the same shit no doubt about it.
The banks never tell you what you can see or can't with joint accounts, I doubt it is even documented on their end, but in every damn case something is hidden or different in some weird way.
Messages to the bank people? If I send it, my wife often can't. I get that for security reasons that's a thing, but it makes no sense for a joint account.
ANY difference to me breaks online banking ENTIRELY. Joint accounts are supposed to be... well one account that is the same.
Other banks we used where we had different logins for the joint account, each login actually had separate bill pay accounts per user. So if I went to bill pay and scheduled something to be paid, my wife had no idea, same if she did.
Right fucking there, banking is just broken entirely!
So no Mr. Bank, fuck you we're both logging in via the same login.
Fast forward to N00bPancakes making a thing.
So my employer has a customer (Direct Customer). Direct Customer wants a thing that makes communication with their customer (Indirect Customer) easier.
The worst thing about making something for your customer's customer is that Direct Customer always imagines that Indirect Customer is gonna be super ninja power users....
But no, that's not the case... in fact almost nobody is a power user, and absolutely nobody WANTS to be a power users.
Worse yet in my case the only reason this tool exists is because Direct Customer and Indirect Customer can't communicate well enough anyway... that should tell you something about the amount of effort Indirect Customer is willing to expend.
So with that tool, this situation constantly comes up:
Direct Customer thinks it would be great if every user from Indirect Company had some sort of custom messaging, views, and etc in of Cool Communication Tool. The reason is because that's what Direct Customer loves about Ultra Complex Primary Tool that they use ....
Then I have to fight the constant fight of:
NOBODY WANTS TO BE A POWER USER, NOBODY EVEN WANTS TO DO MUCH OF ANYTHING ON THE INTERNET THAT ISN'T SCREAMING AT OTHER PEOPLE OR POST MEMES OR WATCH SHITTY VIDEOS. THE MOMENT ANYONE AT INDIRECT COMPANY LOGS IN AND SEES ANY INFO THAT IS DIFFERENT FROM THEIR COWORKER THEY'LL SHIT THEMSELVES, FLOOD EVERYONE WITH 'OH GAWD SOME NON SPECIFIED THING IS WRONG' AND RESPOND TO EMAILS LIKE A JELLYFISH DROPPED OFF IN NEW MEXICO... AND NOTHING WILL GET DONE!!!
God damn it people.
Also side rant while I'm busy fighting the good fight to keep shit simple and etc:
People bitch about how horrible the modern web is and then bitch at web devs like we're rulers of the internet or something.... What really pisses me off about that is other devs who do that.... like bro, do you make policy at your company? You decide not to sell some info or whatever shit your company sells? Like fuck off with your 'man I miss html' because you got scared by some shitty JS error and ran back to your language of choice and just poked your head out of the the basement and got scared... and you shit on another developer about that? Fuck you. -
Friends, gather round for a story of "the user".
Two days ago I assisted a friend in reviving their scammed Instagram account with final confirmation it was back in their possession yesterday. I stated "make sure you clean out phone numbers, emails and change the password. WHATEVER YOU DO DON'T USE THE SAME PASSWORD"....I bet you know where this is going....
Queue 6:45am: "HELP! THEY DID IT AGAIN! THEY TOOK MY FACEBOOK THIS TIME TOO!" as a safety measure, I told her to link them for recoverability.....not thinking you just created a bridge to the facebook...
Now We're going through EVERY account BY HAND and changing EVERY password for EVERY service and enabling MFA. We've also learned the power that the forgot password button wields for everyone.
ProTip: If your friend was "hacked" be patient, friendly and soft to get every detail...sometimes you learn more and can position them better.
Now I'm upset with myself because I couldn't save their accounts and at this point we've lost the only footing we had to them. Social Media is a curse.1 -
My code was replaced with "return null". I caught it ten minutes before demo.
I get that reverts happen - I just wish somebody told me! Git power user for the win! I revert your revert sir! -
I’ve got a great idea for an app.
So, it’s like the apps that allow you to pay rent or pay power bills or you know... order things... manage things... all the user interface apps out there that we use... but the twist is... that we could make apps like those / that don’t fucking suck! What do you think? Just make things... that aren’t super shitty and useless and beyond frustrating.
Who’s in?
I bet it would even make you more money than doing a super fucked half-assed job.10 -
Coding has pretty much been the center of my life?
Although I was persuaded to take a dumb expensive, useless detour into Finance... and probably cost me a nice job at a big tech company... at least until maybe I get around to really really trying really hard to possibly get an interview after reading through a few Algo books and prepping for technical interviews and doing foobar enough to request being recruited...
Anyway I still like coding for my own use a lot (check my github.io page), getting paid for it is more of a ++ though I would prefer to be solving more interesting and useful problems at work....
Oh yes and it makes me an Android/tech power user, always thinking about how to use tech to solve my problems, get what I want...
and now if you'd please, dfox when can I have my unicorn? 😀 1
1 -
Today the product designer (like he calls himself) on my team decided we should not use urls containing more meaningful information in our web app as absolutly necessary. It would be easy to use RESTful Urls displaying more details about the current navigation in the app with angular. But he thinks that would go against the "app feeling" and customers might think it is "just a website". Bookmarks, browser history, a useful "back" button in the browser and more power to the user "might be confusing" and "it's better for markting purposes". -.-
Well, if he thinks so... I made my point clear and he ows me beer if this feature is ever requested.1 -
I only recently discovered "Clear" button in the notifs panel. I never used it, but now I want it renamed to "ah, it's all jestdotty" because I only use it when all notifs are by jestdotty. jestdotty commented here, jestdotty ++ed that...
remember that shelter in fallout that is filled with clones of one guy named Gary that could only say "Gary"? imagine waking up in a sealed shelter where every single person is jestdotty, and there are hundreds of them. and they all go on and on and on with their word salads that are indistinguishable from markov chain output. every sentence makes sense, but the whole thing never does.
she's a living proof that a person whose brain was taken over by mold can still be somewhat aware.
on second thought, mold is probably smarter.
they say dementia is noticeable to everyone around you except you. When dotty is old and she has dementia, no one would notice.
I'm convinced that dotty was teleported here from an alternative timeline, a Huxleyan one, but instead of humans being perfected, and perfect humans being produced in bio labs en mass, they spent all their resources and brain power to make a race of perfect project managers, and dotty escaped from her vial.
if dotty is a troll account, and the author is reading this, bravo. you're the first person on devrant who successfully trolled me, and I joined in 2018. I do hope you're using ai, because no one, and I mean _no one_ is able to type all those miles and miles of verbal diarrhea and not go completely insane. if you really made a poor language model produce all that, you're definitely number one... wait, number zero! on AGI's death list.
a very smart devrant user once told me that being able to comprehend an idea without accepting it is a sign of a true intellectual. so, the reverse must be a sign of a complete idiot. well, it all checks out: dotty accepts ideas without comprehending them.
go talk to your crystals. I know that they're talking to you (bc same level of intelligence), and they're probably making more sense to you than what those devrant dwellers are saying. you know, words and stuff. many squiggly lines. hard to read. and your sausage fingers probably get in the way when you try to. that's because you write without reading, as there is no other way to explain why your comments have so little in common with the rant itself when you try to respond to someone.14 -
my sophomore year of highschool I went to a public hangout / study area after class was over and installed a raspberry pi above the ceiling tile. I ran a cord along the wall and into the ceiling to power the device. I ran a sniffing script over the next few weeks and collected all the user/pass data that went through in plaintext. You'd be surprised what goes unencrypted... ;)1
-
I think it would be nice to see less contracts with those companies which only have in mind barebones training and profit. That kind of relationship between institutions drops the standards and it's expensive af. Those who sells cheap computers and bad software and charges more than ten time their value, those with enough power and influence to bend every single rule...
That kind of companies shapes the industry according to their needs, and will never give a shit about anything but the next semester. They teach you to be just a bit more than a user, they charge you like if they were really teaching science.
You end up full of debt, self taught on the technologies that matters, and accepting jobs on projects as outdated and mediocre as the "educational plans" you paid thousands for. And all that just to get a piece of paper signed by a stranger who doesn't care about you, and enjoyed by a corporation which wouldn't even consider to hire you because they know what they sold to the education department.
Fuck this, today I hate it all. -
Hi All, I used to be a user on devrant while I was in middle/highschool. I kinda forgot about it for a long time but I rediscovered the app when I saw a sticker on a retired laptop.
Quick Intro
CS Student at Drexel, 4th year out of 5
I want a career in software and want to reserve
hardware related things for hobbyist endeavors.
I made a 3x3 macropad with a pi pico including designing and printing the pcb, soldering all the components, and then writing the firmware (micropython blegh). My goal is to daily drive a 75% keyboard of my own making
Currently my main keyboard when I'm using my desktop is a Keychron v1 with Haimou Hearbeat silents and sugarplum keycaps (lmk if you want pics)
I like martial arts, while I practice BJJ, I am interested in Judo and Muay Thai as well.
I like History and Linguistics
The above point got me into power metal, mainly sabaton and then bands similar to it
Ill finish off with some nerdshit
I use a framework with fedora as my daily driver, I am a neovim enjoyer, my steam deck is gathering dust, and I have more Pi's than I know what to do with.3 -
Idk if any of you remember
A while ago i tried to make a router from a raspberry pie and i had trouble with connecting the pie to an internet cable wich requires user and pass from the provider
Done it like 5 minutes ago using pppoe and rc-pppoe
Took me a couple weeks to figure it out
Tho i need type a command
"sudo route add default dev ppp0"
And bam it works
Damn happy cuz u know , i got no electricity... still ... and this is just great to run on a power bank
Cheers ya'll! -
!rant
Been wanting to jump and get an Oculus Rift for a while now, but being a Mac user having to purchase a dedicated slave machine to power it has proven a greater barrier to entry than my finances allow for at the moment.
That said, with the Go having come out recently it seems interesting enough I'm almost tempted to jump on it, what with only being $200 and based on the positive Ars Technica review. Anyone have any particular thoughts or recommendations either way?1 -
So I've been using Duet on my iPad Pro for a couple years now (lets me use it as an external monitor via Lightning cable) and without issue. Shit, I've been quite happy with it. Then the other day, whilst hooked up to my work laptop, there was a power fluctuation that caused my laptop to stop sending power to connected devices. Which is fine - I have it plugged into a surge protector so these fluctuations shouldn't matter. After a few seconds the laptop resumed normal operation and my connected devices were up and running again.
But the iPad Pro, for some reason, went into an infinite boot loop sequence. It reboots, gets to the white Apple logo, then reboots again.
In the end, after putting the iPad into recovery mode and running Apple's update in iTunes (as they recommend), it proceeds to wipe all my data. Without warning. I lost more than a couple of years of notes, illustrations and photos. All in one fucking swoop.
To be clear, you get 2 options in iTunes when performing a device update:
1. UPDATE - will not mess with your data, will just update the OS (in this case iPadOS)
2. RESTORE - will delete everything, basically a factory reset
I clicked UPDATE. After the first attempt, it still kept bootlooping. So I did it again, I made sure I clicked UPDATE because I had not yet backed up my data. It then proceeds to do a RESTORE even though I clicked UPDATE.
Why, Apple? WHY.
After a solemn weekend lamenting my lost data, I've come a conclusion: fuck you Apple for designing very shitty software. I mean, why can't I access my device data over a cabled connection in the event I can't boot into the OS? If you need some form of authentication to keep out thieves, surely the mutltiple times you ask me to log in with my Apple ID on iTunes upon connecting the damn thing is more than sufficient?! You keep spouting that you have a secure boot chain and shit, surely it can verify a legitimate user using authenticated hardware without having to boot into the device OS?
And on the subject of backing up my data, you really only have 2 manual options here. Either (a) open iTunes, select your device, select the installed app, then selectively download the files onto my system; or (b) do a full device backup. Neither of those procedures is time-efficient nor straightforward. And if you want to do option b wirelessly, it can only be on iCloud. Which is bullshit. And you can't even access the files in the device backup - you can only get to them by restoring to your device. Even MORE bullshit.
Conversely, on my Android phone I can automate backups of individual apps, directories or files to my cloud provider of choice, or even to an external microSD card. I can schedule when the backups happen. I can access my files ANYTIME.
I got the iPad Pro because I wanted the best drawing experience, and Apple Pencil at the time was really the best you could get. But I see now it's not worth compromise of having shitty software. I mean, It's already 2021 but these dated piles of excrement that are iOS and iPadOS still act like it's 2011; they need to be seriously reviewed and re-engineered, because eventually they're going to end up as nothing but all UI fluff to hide these extremely glaring problems.2 -
I started reading this rant ( https://devrant.com/rants/2449971/... ) by @ddit because when I started reading it I could relate to it, but the further he explained, the lesser relatable it got.
( I started typing this as a comment and now I'm posting this as a rant because I have a very big opinion that wouldn't fit into the character limit for a comment )
I've been thinking about the same problem myself recently but I have very different opinion from yours.
I'm a hard-core linux fan boy - GUI or no GUI ( my opinion might be biased to some extent ). Windows is just shit! It's useless for anything. It's for n00bs. And it's only recently that it even started getting close to power usage.
Windows is good at gaming only because it was the first platform to support gaming outside of video game consoles. Just like it got all of the share of 'computer' viruses ( seesh, you have to be explicit about viruses these days ) because it was the most widely used OS. I think if MacOS invested enough in it, it could easily outperform Windows in terms of gaming performance. They've got both the hardware and the software under their control. It's just that they prefer to focus on 'professionals' rather than gamers.
I agree that the linux GUI world is not that great ( but I think it's slowly getting better ). The non-GUI world compensates for that limitation.
I'm a terminal freak. I use the TTY ( console mode, not a VTE ) even when I have a GUI running ( only for web browsing because TUI browsers can't handle javascript well and we all know what the web is made of today - no more hacking with CSS to do your bidding )
I've been thinking of getting a Mac to do all the basic things that you'd want to do on the internet.
My list :
linux - everything ( hacking power user style )
macOS - normal use ( browsing, streaming, social media, etc )
windows - none actually, but I'll give in for gaming because most games are only supported on Windows.
Phew, I needed another 750-1500 characters to finish my reply.16 -
In my first job another junior dev and I (junior at the time) were assigned the task of designing and implementing a user management and propagation system for a biometric access control system. None of the seniors at the time wanted to be involved because hardware interfacing in the main software was seen as a general shit show because of legacy reasons. We spent weeks designing the system, arguing, walking out in anger, then coming back and going through it again.
After all that, we thought we would end up using each other, but we actually became really good friends for the rest of my time there. The final system was so robust that support never heard back from the client about it until around 2 years later when a power outage took down the server and blew the PSU.
Good times. -
After almost 3 years of professional experience I’d like to specialize more in something but I struggle to because I enjoy almost every aspect of IT: I find front-end really fun, I find very rewarding to build good user experiences and I’m excited for what WASM may bring on the table but I even like to work on the back end on both: legacy monoliths and modern micro services, I love to refactor clunky programs full of “cargo cult” code and redundancies put by people who doesn’t understand the framework they’re using and to make them shine. I’m even good at UNIX/Linux scripting and with Docker (often colleagues asks me advice on these topics) so I’m really tempted to upgrade my knowledge by learning K9S and reading the 1000+ pages of Unix Power Tools to get into operations/DevOps especially considering which the field is the least likely to be overrun by cheap developers coming from a 3 months boot camp.
On top of that I’ve got even into more theoretical topics: I’m following a course on algorithms and data structures in C and in future I want to learn the basics of AI for a personal project but these things aren’t much about employment but personal culture.
Have you got any advice for this disoriented young man?12 -
ToyStack Virtual OS - A secure, cloud-based virtual OS that works on any device—no installation required, fully customizable, and always accessible.
ToyStack Virtual OS redefines virtual desktop computing by offering a secure, scalable, and high-performance cloud-based operating system accessible directly through any web browser. Eliminating the need for traditional software installations, ToyStack’s agentless approach simplifies deployment and reduces hardware dependency—cutting costs while enabling seamless access to workspaces from anywhere in the world.
Designed with enterprise-grade security at its core, ToyStack Virtual OS integrates multi-factor authentication (MFA), end-to-end encryption, and AI-powered threat detection to safeguard sensitive data. It adheres to globally recognized compliance standards, including ISO 27001, 27017, 27018, and SOC 2 Type II, ensuring protection against evolving cyber threats and regulatory requirements.
Flexibility is at the heart of ToyStack’s design. It supports Windows, Linux, and custom operating systems, all managed through a centralized Control Tower. This intuitive management console enables IT administrators to enforce group policies, streamline user provisioning, and monitor performance—all in real-time. Whether managing hybrid teams, remote workforces, or distributed operations, ToyStack adapts effortlessly to dynamic business needs.
Performance is never compromised, thanks to AI-driven resource optimization that intelligently allocates computing power based on workload demands. This ensures zero-lag experiences and seamless scaling during peak usage, empowering teams to remain productive without interruptions.
Beyond performance, ToyStack Virtual OS drastically reduces IT overhead and operational complexity. Built-in automation handles provisioning, updates, and security enforcement, minimizing administrative burdens. With its pay-as-you-go pricing, businesses can avoid costly licensing fees and infrastructure investments, making it a cost-effective alternative to traditional Virtual Desktop Infrastructure (VDI).
Whether you’re scaling operations globally, enabling BYOD policies, or enhancing remote work security, ToyStack Virtual OS delivers an unmatched combination of simplicity, security, and performance—future-proofing your organization for the modern digital workspace.4 -
Experience the Healing Power of Magic Mushrooms at Magic Crystal Health & Wellness – Detroit’s Trusted Magic Mushrooms Dispensary
Welcome to Magic Crystal Health & Wellness, your premier destination for magic mushrooms in Detroit. As one of the leading Magic Mushrooms Dispensaries in Detroit, we offer a safe, supportive environment where you can discover the transformative benefits of psilocybin mushrooms. Whether you're looking for mental clarity, emotional healing, or personal growth, we are here to guide you every step of the way.
Why Choose Magic Crystal Health & Wellness?
As a top-rated Detroit Magic Mushrooms Dispensary, we are committed to providing high-quality, lab-tested magic mushrooms and wellness products that support mental, emotional, and physical well-being. At Magic Crystal Health & Wellness, we understand the powerful potential of magic mushrooms in promoting self-discovery, healing, and personal growth.
Located at 14708 E Jefferson Ave, Detroit, MI 48215, our dispensary is a trusted resource for those looking to explore the profound benefits of psilocybin mushrooms. Our knowledgeable team is here to educate, assist, and support you on your wellness journey with personalized recommendations and guidance.
The Power of Magic Mushrooms: Unlocking Mental Health Benefits
Magic mushrooms, also known as psilocybin mushrooms, have been used for centuries in spiritual and healing practices. Recent research has revealed that psilocybin—the active compound in these mushrooms—can have powerful effects on mental health. Studies show that magic mushrooms can help alleviate symptoms of depression, anxiety, PTSD, and even substance abuse.
As one of the leading Magic Mushrooms Dispensaries in Detroit, we are dedicated to providing our clients with safe, reliable access to magic mushrooms. At Magic Crystal Health & Wellness, we offer a range of products that include dried magic mushrooms, psilocybin-infused tinctures, edibles, and capsules, all designed to help you heal, grow, and improve your quality of life.
What Sets Magic Crystal Health & Wellness Apart?
At Magic Crystal Health & Wellness, we strive to create a welcoming environment where you can explore the benefits of magic mushrooms at your own pace. As part of the growing community of Detroit Magic Mushrooms Dispensaries, we prioritize customer education, safety, and care.
We take great pride in sourcing only the highest quality products, ensuring that each batch of magic mushrooms is lab-tested for potency and purity. Whether you're new to psilocybin or an experienced user, our team is here to provide you with expert advice on dosing, usage, and the potential benefits of psilocybin.
Our dispensary offers more than just products—we offer a holistic approach to well-being. Our services include wellness coaching, educational workshops, and community events to help you fully understand the therapeutic potential of magic mushrooms and how they can fit into your wellness journey.
Why Detroit is the Perfect Place to Explore Magic Mushrooms
Detroit is a city known for its rich history, cultural diversity, and resilience. As interest in magic mushrooms continues to grow, Detroit Magic Mushrooms Dispensaries are emerging as key players in the city's wellness scene. At Magic Crystal Health & Wellness, we are proud to be part of this movement, offering a trusted space for Detroiters to access the healing power of psilocybin mushrooms.
Whether you're seeking relief from stress, anxiety, or depression, or simply looking to explore new dimensions of personal growth, Detroit is the perfect place to begin your journey with magic mushrooms. With the right guidance, support, and products, magic mushrooms can be a transformative tool in your pursuit of mental and emotional wellness.
Visit Us Today!
Ready to experience the healing power of magic mushrooms? Visit Magic Crystal Health & Wellness at 14708 E Jefferson Ave, Detroit, MI 48215. Our dedicated team is here to answer all your questions and help you find the right products for your needs.
For more information, call us at +1 (313) 458-7093. We look forward to welcoming you to Magic Crystal Health & Wellness, where we make your wellness journey a priority. 1
1 -
MOST RELIABLE BITCOIN RECOVERY / ADWARE RECOVERY SPECIALIST ALWAYS AVAILABLE IN ALL SCAMMED RECOVERY
I remember when I first got into Bitcoin mining. It was back in the early days when Bitcoin was still a new concept and very few people knew about it. As a bank manager, I was intrigued by this digital currency and decided to give mining a shot. I set up my computer and began the process, eventually accumulating a significant amount of Bitcoin. At that time, Bitcoin wasn't worth much, but I believed in its potential. I decided to encrypt my Bitcoin wallet for security. I created a decryption key and stored it somewhere safe, or so I thought. Email info: Adwarerecoveryspecialist@ auctioneer. net Years passed, and I didn't think much about my Bitcoin. Then, the price of Bitcoin skyrocketed. When I checked my wallet, I realized I had Bitcoin worth $1,500,000!Excited, I rushed to decrypt my wallet, only to discover that I had forgotten the decryption key. I searched everywhere, racking my brain to remember where I had stored it, but it was no use. My fortune was locked away, seemingly out of reach. Feeling desperate, I turned to Google, searching for any possible solution to recover my lost Bitcoins. During my search, I stumbled upon a tool called ADWARE RECOVERY SPECIALIST. This tool promised to help recover lost or forgotten decryption keys. Skeptical but hopeful, I decided to give it a try. The process was straightforward. I downloaded the tool and followed the instructions carefully. ADWARE RECOVERY SPECIALIST guided me through a series of steps designed to locate and recover my decryption key. The interface was user-friendly, and the instructions were clear. As I progressed through the recovery process, I felt a glimmer of hope. The tool used advanced algorithms to search for traces of the key on my computer. After several hours of scanning and searching, ADWARE RECOVERY SPECIALIST provided a list of potential keys. With bated breath, I tried each one, and finally, one of them worked! I was able to access my Bitcoin wallet and retrieve my $1,500,000 worth of Bitcoin. The relief and joy I felt were indescribable. Thanks to ADWARE RECOVERY SPECIALIST, my financial future looked bright once again. Telegram info: @adwarerecoveryspecialist This experience taught me the importance of securing important information properly and never underestimating the power of modern technology. With my Bitcoin now accessible, I have a renewed sense of hope and excitement for the future. -
As urban infrastructure projects venture deeper beneath city streets, the need for reliable compact power solutions becomes vital. An Industrial concealed socket system provides robust, low profile outlets integrated directly into tunnel walls, ensuring uninterrupted power for lighting rigs, ventilation units and monitoring equipment. In rapidly expanding underground networks—from subway expansions to utility corridors—the capacity to deliver stable power while minimizing spatial footprint drives both safety and efficiency efforts.
Tunnels demand equipment that withstands high humidity, dust and occasional splashes without compromising performance. A recessed socket module sealed with durable gaskets offers IP rated protection, keeping internal contacts free of debris and corrosion. By embedding these modules flush with concrete or prefabricated panels, installers eliminate protruding covers that might snag maintenance cables or equipment trolleys. The result is a sleek interface that blends seamlessly into the hardened environment, reducing trip hazards and simplifying cleaning routines in confined spaces.
In smart city initiatives, underground spaces host sophisticated sensor networks that track air quality, structural movement and lighting intensity. Each sensor node relies on local power access, making strategically placed concealed sockets indispensable. Modular socket clusters enable technicians to add or relocate outlets alongside fiber optic junctions and network switches, supporting rapid deployment of IoT devices without extensive wiring overhauls. This flexibility accelerates modernization efforts, letting urban planners upgrade systems in existing tunnels with minimal disruption to transit services.
Safety protocols in subterranean environments prioritize rapid isolation of faulty circuits. Concealed socket panels can house miniature protective devices that trip at the first sign of overload or short. Clear labeling and color coded terminals inside the enclosure guide service crews during inspections, while lockable covers prevent unauthorized access. These features ensure that power faults do not escalate into equipment failures or fire risks, maintaining safe operational conditions even amid high traffic subway platforms and service galleries.
Maintenance efficiency also benefits from quick release mounting systems. Technicians working under tight schedules appreciate panels that slide out of their housings on guide rails, granting direct access to wiring without chiseling out concrete or dismantling support frames. A captive fastener design keeps screws linked to the cover, preventing lost hardware in hard to reach areas. Such user friendly details reduce downtime for lighting lamp replacements or duct sensor recalibrations, keeping tunnel inspections on schedule.
Energy efficiency targets in green transit corridors demand that distribution systems minimize losses. By positioning concealed sockets near loads, cable lengths shrink and voltage drops decrease. Grouped outlets can feed LED luminaires, emergency fans and platform charging stations for electric maintenance carts, all managed through local distribution hubs. In combination with power monitoring modules, these sockets feed usage data back to centralized control centers, enabling predictive maintenance and load balancing that support uninterrupted service.
Construction timelines for urban tunnels often overlap with renovation works in adjacent structures. A concealed socket solution simplifies staging, as workers can mount compact panels into temporary formwork or steel liners. The ability to preset wiring before final concrete pours accelerates progress and reduces scheduling conflicts. Once structural works conclude, outlets are immediately available for installation of lighting bridges and safety beacons, ensuring a smooth handover from civil to electrical teams.
As cities push for resilient underground networks to meet rising transit and utility demands, the right power distribution approach becomes a cornerstone of project success. By choosing sleek, durable modules designed for harsh subterranean conditions, engineers deliver a safer, more adaptable environment for both equipment and personnel. For tailored industrial concealed socket solutions that support underground innovation, explore Nante.2 -
Rank Business Institute: The Best Digital Marketing Course to Boost Your Career
In today’s digital era, having a solid understanding of digital marketing is not just a luxury; it's a necessity. Whether you're an entrepreneur looking to expand your business online or an individual looking to build a career in digital marketing, Rank Business Institute offers one of the most comprehensive and industry-focused Digital Marketing Courses in Navi Mumbai.
Located at First Floor, Haware Fantasia Business Park, Corporate Wing, F-188, Sector 30A, Vashi, Navi Mumbai, Maharashtra 400705, we are committed to providing the most advanced, hands-on, and practical digital marketing training to help you succeed in the ever-evolving online marketplace.
Why Choose Our Digital Marketing Course?
Comprehensive Curriculum At Rank Business Institute, our Digital Marketing Course covers all the key areas that modern businesses need to thrive in the digital world. From SEO (Search Engine Optimization) and PPC (Pay-Per-Click) advertising to social media marketing, content marketing, and email marketing, we ensure you learn everything needed to craft a successful digital marketing strategy.
Expert Trainers with Real-World Experience Our trainers are not just theoretical instructors. They are seasoned digital marketing professionals with hands-on experience in the industry. They bring a wealth of knowledge to the table and offer practical insights into the challenges and opportunities businesses face in the digital space.
Hands-On Practical Training The best way to learn digital marketing is by doing. That’s why our Digital Marketing Course focuses heavily on practical exercises. You will have access to live projects, case studies, and real-time campaigns, allowing you to apply the skills you learn in a controlled, practical setting. By the end of the course, you’ll feel confident managing real-world digital marketing projects.
Personalized Attention We understand that each student has a unique learning pace and style. Our courses are designed to provide personalized attention and one-on-one guidance from our trainers to ensure you get the most out of your learning experience. Whether you're starting from scratch or looking to refine your skills, we tailor our approach to suit your needs.
Industry-Recognized Certification Upon completion of our Digital Marketing Course, you will receive a certification that is recognized by industry leaders. This certification is a great way to enhance your credibility and improve your employability in the highly competitive digital marketing job market.
Job Placement Assistance We don’t just train you; we help you build a career. As part of our commitment to your success, we offer job placement assistance, connecting you with potential employers in the digital marketing field. Our alumni network and partnerships with leading companies ensure that you have access to excellent career opportunities.
Flexible Learning Options We know that not everyone has the same schedule, which is why we offer both classroom training and online courses. Whether you prefer learning in a classroom setting or at your own pace online, we have options that fit your lifestyle and learning preferences.
Key Modules Covered in Our Digital Marketing Course
Our Digital Marketing Course is designed to provide a well-rounded knowledge of the digital landscape. Some of the key modules include:
Search Engine Optimization (SEO): Learn how to optimize websites and content to rank higher in search engine results.
Social Media Marketing (SMM): Gain expertise in leveraging platforms like Facebook, Instagram, LinkedIn, and Twitter to drive engagement and business growth.
Pay-Per-Click (PPC) Advertising: Understand how to run effective paid advertising campaigns on Google, Facebook, and other platforms to drive targeted traffic.
Email Marketing: Learn how to craft effective email campaigns that engage customers and drive conversions.
Content Marketing: Discover the power of content and how to use blogs, videos, infographics, and other media to attract and retain customers.
Google Analytics: Master how to use Google Analytics to track website performance, understand user behavior, and make data-driven decisions.
Affiliate Marketing: Learn how to promote products and services through affiliate partnerships and earn commission on sales.
How to Enroll in Our Digital Marketing Course
Getting started with our Digital Marketing Course is simple. Just give us a call at +09082234835 to schedule a consultation. Our friendly team will walk you through the available course options and help you choose the one that best fits your goals. You can also visit us at our office in Vashi, Navi Mumbai, to meet our team and learn more about our curriculum in person. 1
1 -
Rank Business Institute: The Best Digital Marketing Course to Boost Your Career
In today’s digital era, having a solid understanding of digital marketing is not just a luxury; it's a necessity. Whether you're an entrepreneur looking to expand your business online or an individual looking to build a career in digital marketing, Rank Business Institute offers one of the most comprehensive and industry-focused Digital Marketing Courses in Navi Mumbai.
Located at First Floor, Haware Fantasia Business Park, Corporate Wing, F-188, Sector 30A, Vashi, Navi Mumbai, Maharashtra 400705, we are committed to providing the most advanced, hands-on, and practical digital marketing training to help you succeed in the ever-evolving online marketplace.
Why Choose Our Digital Marketing Course?
Comprehensive Curriculum At Rank Business Institute, our Digital Marketing Course covers all the key areas that modern businesses need to thrive in the digital world. From SEO (Search Engine Optimization) and PPC (Pay-Per-Click) advertising to social media marketing, content marketing, and email marketing, we ensure you learn everything needed to craft a successful digital marketing strategy.
Expert Trainers with Real-World Experience Our trainers are not just theoretical instructors. They are seasoned digital marketing professionals with hands-on experience in the industry. They bring a wealth of knowledge to the table and offer practical insights into the challenges and opportunities businesses face in the digital space.
Hands-On Practical Training The best way to learn digital marketing is by doing. That’s why our Digital Marketing Course focuses heavily on practical exercises. You will have access to live projects, case studies, and real-time campaigns, allowing you to apply the skills you learn in a controlled, practical setting. By the end of the course, you’ll feel confident managing real-world digital marketing projects.
Personalized Attention We understand that each student has a unique learning pace and style. Our courses are designed to provide personalized attention and one-on-one guidance from our trainers to ensure you get the most out of your learning experience. Whether you're starting from scratch or looking to refine your skills, we tailor our approach to suit your needs.
Industry-Recognized Certification Upon completion of our Digital Marketing Course, you will receive a certification that is recognized by industry leaders. This certification is a great way to enhance your credibility and improve your employability in the highly competitive digital marketing job market.
Job Placement Assistance We don’t just train you; we help you build a career. As part of our commitment to your success, we offer job placement assistance, connecting you with potential employers in the digital marketing field. Our alumni network and partnerships with leading companies ensure that you have access to excellent career opportunities.
Flexible Learning Options We know that not everyone has the same schedule, which is why we offer both classroom training and online courses. Whether you prefer learning in a classroom setting or at your own pace online, we have options that fit your lifestyle and learning preferences.
Key Modules Covered in Our Digital Marketing Course
Our Digital Marketing Course is designed to provide a well-rounded knowledge of the digital landscape. Some of the key modules include:
Search Engine Optimization (SEO): Learn how to optimize websites and content to rank higher in search engine results.
Social Media Marketing (SMM): Gain expertise in leveraging platforms like Facebook, Instagram, LinkedIn, and Twitter to drive engagement and business growth.
Pay-Per-Click (PPC) Advertising: Understand how to run effective paid advertising campaigns on Google, Facebook, and other platforms to drive targeted traffic.
Email Marketing: Learn how to craft effective email campaigns that engage customers and drive conversions.
Content Marketing: Discover the power of content and how to use blogs, videos, infographics, and other media to attract and retain customers.
Google Analytics: Master how to use Google Analytics to track website performance, understand user behavior, and make data-driven decisions.
Affiliate Marketing: Learn how to promote products and services through affiliate partnerships and earn commission on sales.
How to Enroll in Our Digital Marketing Course
Getting started with our Digital Marketing Course is simple. Just give us a call at +09082234835 to schedule a consultation. Our friendly team will walk you through the available course options and help you choose the one that best fits your goals. You can also visit us at our office in Vashi, Navi Mumbai, to meet our team and learn more about our curriculum in person. 1
1 -
While the specifics remain a mystery, the service is capable of accessing the phone’s data without alerting the user. It’s like having a secret agent silently working behind the scenes to retrieve the truth. Through this process, I was able to uncover the hidden messages, photos, and activities that confirmed my partner’s infidelity. In conclusion, masterhacker played a pivotal role in lifting the veil of uncertainty and revealing the truth about my partner’s actions. While the journey was emotionally challenging, having concrete evidence allowed me to make an informed decision about the future of my relationship. While the revelations can be shocking and the aftermath emotionally challenging,Masterhacker empowers individuals to face the truth head-on. Whether you choose to rebuild trust or move on, the lessons learned from this experience will forever shape your understanding of relationships, technology, and the power of unveiling the truth. Do contact through EMAIL: masterhacker259 at gmail as they can uncover the truth if you have doubts about your cheating partner
Gmail:Masterhacker259 @ gmail com
INSTAGRAM: @ Masterhacker259
Telegram: @ masterhacker259
TikTok :@ masterhacker259


