Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "hash"
-
In my second year,
I told my teacher I can code in in C#(c-sharp).
She replied : C-sharp ? Oh you mean C-hash !
*that day I lost hope in college*31 -
The moment an other team couldn't deliver for a deadline. CEO came to me, gave me 50 bucks told me to get a pizza and some hash and just work the night and deliver the damn app. So I did. Got a week holiday for free in return. One of the best guys I worked for.41
-
Me: how's your password security?
Them: of course we value security very highly, our passwords are all hashed before being stored.
Me: what hashing algorithm?
Them: oh we hash it with sha and then place that in a table indexed by the password.
Indexed. By. The fucking. Password.16 -
I found out recently that Facebook is embedding tracking data in the form of IPTC metadata in images that you upload. This way the images can be tracked even after you download them.
Because I'm an anarchist and just want to watch the world burn a little, I made a tiny server to replace the id hash that they embed with a random one, just to see if I can't fuck with their algorithm a little bit.
You can check out the project here https://github.com/watzon/fbmdob15 -
"The password must be 6 to 32 characters long and must contain atleast one uppercase character, one lowercase character, a special character, the md5 hash of your last name, a dried olive branch and the blood of a unicorn."5
-
Project Manager: You used a hash/salt to encrypt the password in our customer database?
Me: Yes.
Project Manager: That's mean we will not be able to see the password?
Me: That's the whole point. Why would you want to see what password customer is choosing?
Project Manager: Change it. Use random encryption method.8 -
https://google.com”f people near me wanted to show me something.
Person: Check out this zero-day exploit! I hacked into the system using a cloud-based cryptographically secure MD5 hash finite automata firewall HTML code API!
Me: Erm...what exactly did you hack?
Person: *shows screen while smirking*
It was a shell simulator website running “ping https://google.com”7 -
It pains me that Google Now pronounces C# as "C hash".
Perhaps it's their subtle way to annoy Microsoft developers...8 -
anyone else just wake up one day and just isn't in the mood to do any work and feels like they are making no progress.7
-
Me becoming responsible:
Help in household chores ❌
Help siblings ❌
Finish college work ❌
Report every bug i encounter in Pubg ✔️ 5
5 -
"Why can't I just get the terminology right in my head"
java: map.
javascript: object?
python: dictionary!
ruby: HASH!
php: aSsoCiaTiVe aRrAy12 -
CHILD: But how can Santa deliver toys to every little boy and girl on his list in one night?
MEH: (laughs) It's quite simple. The items on Santa's list are called blocks, and each block in his "blockchain" typically contains a hash pointer, a timestamp, and transaction data...6 -
I just realized a "hash" symbol is slanted to the right (#) and a "sharp" symbol is slanted to the left (♯) ...13
-
Her: What are you doing over there?
Me: I'm working on cryptographic hash functions
Her: is that really homework?
Me: yes, come look with your two eyes.
Her: ...
Me: crazy stuff, no?
Her: I imagine computer science is really just a lot of boxes and arrows.
Me: *flashback to UML, ERD diagrams, and logic diagrams*
Me: you are not wrong. 8
8 -
This isn't my own creation, but I couldn't find it shared here yet.
It is a poem:
< > ! * ' ' #
^ " ` $ $ -
! * = @ $ _
% * < > ~ # 4
& [ ] . . /
| { , , SYSTEM HALTED
It reads as:
Waka waka bang splat tick tick hash,
Caret quote back-tick dollar dollar dash,
Bang splat equal at dollar under-score,
Percent splat waka waka tilde number four,
Ampersand bracket bracket dot dot slash,
Vertical-bar curly-bracket comma comma CRASH!6 -
My brother singed up for a browser game.... They sent him his log data (including password) via email7
-
No, MD5 hash is not a safe way to store our users' passwords. I don't care if its been written in the past and still works. I've demonstrated how easy it is to reverse engineer and rainbow attack. I've told you your own password for the site! Now please let me fix it before someone else forces you to. We're too busy with other projects right now? Oh, ok then, I'll just be quiet and ignore our poor security. Whilst I'm busy getting on with my other work, could you figure out what we're gonna do with the tatters of our client's business (in which our company owns a stake) in the aftermath of the attack?7
-
Most hated language features?
PL/SQL:
• it exists
XSLT:
• it also exists
PHP:
• it still exists.
VB:
• Significant parentheses: `subName` calls the subroutine, and `subName()` calls the subroutine and gets a return value. If you use the wrong invocation, it yells at you. Why!?
• For reasons unknown, you can only have `sleep` appear once per codebase. (So put it in a function!)
Ruby:
• It’s bloody easy to write code with absolute shit performance, and it kind of feels encouraged because of just how easy Ruby makes everything. Less critical thinking means worse performance, and Ruby’s blissful elegance encourages mental laziness.
• Minor: You cannot pass a hash as the first method parameter without enclosing it in parentheses, ex:`method({key: value})`. This is due to the ambiguous case between passing a hash argument and a (curly) block/proc (`method {|args| code}`). This could be remedied pretty easily with a little bit of look ahead.
• Minor: There is no `elsif` for `unless` (a negated if). Why? No reason given.
Python:
• no block endings, so nested code can be extremely difficult to follow.
Bash:
• The freaking syntax oh god why.
All languages:
• rand vs rand() vs Rand vs Rand() vs rnd vs RND vs random() vs random vs randInt() vs Math.random() vs Math.randInt() vs ...18 -
Yay my stickers finally arrived! Thanks guys <3 @dfox @trogus
And it freaked out my mum. She called me all panicked like "you've got an international letter what did you do did you get scammed or something"
...
"Mum, those are stickers...I got for free"
"Ohhhh... ok then"
But shre was very worried there ^^' 19
19 -
worst interview was about 2 years ago. I found this job as on a famous website, I applied for a desktop dev. position...the job seemed really easy, after 10 minutes the so-called CTO asked me:" how much do you know C hash?" me:"what?" him:"C hash...the Microsoft programming language" I thanked him for his time and went home crying ( he meant c# )...after a month I found out the company had gone bankrupt...I think I know why..8
-
when your first try to learn a new programming language, for example c++ and you are still new to coding:
"Wtf does it behave this way. How dafuq do pointers work...argh"
and then years later, you come back to c++, do a little revision and it all starts to fall into place and make sense. Man. That feeling.3 -
I bought flowers for my date. Online.
When I registered, the website send me via email my 30 character long password.
😥
So I try "forgot password". The genius website sent me, guess what, my 30 character long password...
For fuck sakes!!!! You had one job.... Hash the fucking password!!!!
I'm afraid these people will probably get hacked soon (murphy law).
Sha256.. Guys please...12 -
I signed up for a 3 day course on c++ for revision purposes since I haven't used it in years, it was there, so why not.
So we get an email about having to install linux mint beforehand. Naturally, having ubuntu installed, i just ask if I can roll with that. And the answer is:
"Yes you just need to install the compiler, but then you won't get the credit point for the course, since you have not completed all tasks."
And an instruction was attached innthe general email on to how to create a bootable usb stick with windows and set up the partition (!) for a dualboot system for like 10 gigs of linux.
Bruh.
Da fuq.
I'm coming for the c++ not the linux. Also how do you think I've got ubuntu running in the first place? I get it the course is for beginners probably but still.
Also, after reading the instructions and knowing Windows 10 i can see bootloader issues incoming...
Was looking forward to that course now I'm not so sure. 🤔
(Sidenote: i don't care about the point I could get ftom this)10 -
A friend of mine bought a new laptop with an ssd and called me over since it behaved weirdly. All the icons on the desktop would turn to white squares and slowly reload their images. Also the laptop was pretty slow.
She said she had brought it to the store to show that behaviour and the only advice they would give was to reinstall windows...
So I started checking on what processes are running...
The thing was constantly running an "optimization" tool... which, you guessed it, was constantly defragmentating... the ssd... are you fkn serious who set up that shit this way... -
Forgot my password at school, say so, they tell me the password. Have they never heard about security?9
-
Php array methods, all of them, or should i say hash methods
They should fix them. I mean they should fix placing of callback and subject params, because.
I mean
array_filter(array, callback)
array_map(callback, array)
Or they should make array a object like js4 -
hey guys. I just wanted to share that I've just finally passed my masters degree defense. I still can't quite belive it, and I feel as derpy as before, but oh my fucking god, I finally passed (it took me forever).
Now just need to wait for the uni paperwork to the the formal papers and shit. but HELL YES FINALLY OMFG9 -
me a few days ago: I've been active on devRant recently! Finally a platform I don't drop after 1-2 days!
yesterday + today: * is on devrant instead of being productive*
well....
fk1 -
I decided that I wanted to try and write and android app. So here I am, following their "Hello World" tutorial, for good measure, just to find out that using that with the newest SDK 28 produces errors and needs work arounds. Already. In the Hello World example.
Just created the project anew with SDK 27. Cannot be bothered with this and this time.
But seriously. What the fk. Get your shit together Android. <.<' It's not such a strong kickback but it's unecessary trouble nobody needs...26 -
Facebook you little piece of shit.
We have a page setup for a band since apparently this is what one does these days. But oh boy is facebook annoying. Can you please stop sending me 100 notifications a day about fking post boosting?! What the fuck. We are students we don't have money for this shit. fk off! <.<12 -
Was going to get some REST but her API was wide open:
PUT my/boner/inside/her
413 Request Entity Too Large
Fuck.14 -
Remember my rant about having to write a newsletter which works with MS Outlook?
Remember that rant by @EclipseMain about teachers teaching how to build a website in MS word?
Well. The two just became united. I had finished the fking newsletter and was waiting for approval. They kept on introducing last minute changes, a commata here and there and whatnot. I literally was waiting for 2 weeks to send that shit out.
My boss gets the glorious idea that if I complain so much about Outlook and Microsoft, lets have the secretary design the newsletter from scratch, literally copying my design, in ms word... argument: one can send an html email out from word.
...
Then they ask me which one should be send out. I say I can apply the design suggestions to my newsletter but if we sent theirs, with all the weird fonts and being even less responsive then my suggestion, it would be even worse.
What the fuck.
Also: they let me waste a lot of time on this thing to tell me later oh we have money left lets hire a designer. Why not do that from the start? Ffs... <.<5 -
My Unreal project right now:
FVector
std::vector
Eigen::Vector
KDL::Vector
....
*sigh*
And people ask me why I like Lisp. A Vector is a Vector goddamit! Half my project is now just parsing the same variable to the different functions. sigh....I hate this.6 -
The joys of mapping...
I'm playing around with some cartographer parameters and this happened. Thought it fits the christmas theme and was kindas beautiful so decided to share.
It's a map snowflake :3 9
9 -
In ESnext, private properties are marked with `#`.
Who thought that was a good idea? No really, who thought that was a good idea?
Why not just -- I don't know -- introduce keywords like ... let me think ... public, protected and private!?
Why this:
class MyClass {
a = 1; // .a is public
#b = 2; // .#b is private
static #c = 3;// .#c is private and static
incB() {
this.#b++;
}
}
If this becomes part of the language, no JavaScript developer may joke about php usage of `$` anymore.32 -
!dev
What the...
Please add more lines. I'm sure I can read this on the fly...
Wait.
This is outside of the piano spectrum. What the fk
(Yes, bass key) 22
22 -
Installing Unreal plugins from github be like:
clone, try to build
unreal: nah
me: can you tell me why?
unreal: nah
me: please?
unreal: nah
...
me: With the powers of MS VS I command you, tell me why the fuck you aren't building!?!
unreal: yeah I need that dependency in this plugin fo rmotion tracking
me: we don't do motion tracking *comment it out*
unreal: there I build it.
... I feel like I was a Karen, went to talk to the manager (VS) who gave me a proper explanation to why the employee had to behave this way.2 -
I'm a responsable grown up! *uses a can of glitter hairspray on hair* much adult. Such wow.
Now I'm leaving behind a trail of fabulous. No regrets.
Pfft and my mum keeps on asking when I'm going to have kids...23 -
Fuck you for imposing the upper limit on password length for my online banking! Why do you even care about my pass - don't you fucking hash it beforehand?!3
-
Phone call with random guy:
"Hi I have an awesome idea for a mobile app that's going to change the world. I just don't know how to program it."
Me: "cool, let's set up a meeting to hash out the details and discuss the project & costs"
Guy: "I was hoping you would be able to do it for 10% equity, it's gonna make millions!"
Me: "Facepalm"6 -
So other project members joined devRant now. So now we can rant about the project together <3 Let's hope our supervisors aren't here also... that would be awkward, right?6
-
*me quering a knowledge system for a pose and quaternion*
System: here is the quaternion in w x y z format
me: but for using it I need it in x y z w
System: not my problem
me: ok, fine. here is a function that flips this, np.
*months later*
me: wtf why does grasping don't work anymore? The poses look reasonable.
*after hours of trying to debug it*
*remembers hearing someone say something about finally using one standard for quaternions across the systems*
me: wait... could this be... *comments out flip function*
me: yep... that's it.
...
Overall, this is an improvement. But I lost several nerves and hours yesterday night wondering why my grasping doesn't work anymore. Feeling embarrassed, that I didn't finish my stuff in time because of this bug.
*sigh*
goddammit6 -
My business partner who claim to be the best Wall Street programmer, probably 160 years ago, decided to improve our core system written in Go.
He dragged a *shortcut* of *whole* local github folder into Vendor(sort of node_modules), Manually changed commit hash in Gopkg.lock, etc,
Next morning I woke up to 24 failed builds on Master; all protobuf redone with his unknown gogo version, database trigger function with changed logics added parameters, and a text message “has anyone experienced build corruption? Works on my mac”
My other business partners said “it’s okay, He’s going through tough divorce needs some distraction”
F M L1 -
Expert: "The core problem with passwords is that they reside on a server."
I suppose that's true, but only if you're a complete moron. Store a hash of a password, and users can authenticate against it with a password that doesn't get logged. This is technology that's been around for over fifty years. If you're storing passwords on a server, you deserve whatever trouble you get.6 -
Took the risk and asked a question at SO. Yay! No downvotes so far
https://stackoverflow.com/questions...6 -
So we have a portal for all our University courses, where the professors also upload the presentations, etc.
Professor sends Email: Please participate in this questionnaire.
*clicks link*
"Please log in to continue"
*logs in*
Error (while I am already logged in): "Please log in to continue"
????
No wonder some people nick name the thing stupid. <.< -
1) Using ScreenRecord record a video deleting his work folder(fake one obviously).
2) create command line vlc player to play this video on startup with flags -f and --no-qt-fs-controller
Eg. vlc -f --no-qt-fs-controller file://<file path>
Enjoy the show 👿 -
That moment when you drop your phone in a sink full of water and have to hope that rice will fix it since you're too poor for a new one right now.1
-
Just had a talk with my manager who wanted to know why I removed a feature from an application we had. This removal had been discussed WITH THE MANAGER several months prior, but apparently they hadn't written a little note or anything down about it.
I told them we had discussed it earlier. They didn't believe me. They checked the project technical specifications that said it _should still be there_. I told them we talked about it previously. They told me to prove it, so I go looking through the commit history.
Lo and behold:
- Commit <hash> authored 4 months ago.
- Update to specifications, asked for by <manager>
Eat it.2 -
Spent 5 hours working on a solution for a hash difficulty comparison/scaling algorithm. after a bunch of different iterations and approaches, I find that my problem can be solved by the attached equation. Its such a simple answer but no way in hell would you be able to discern the amount of time and brainpower that was put into it. The git commit is literally 10 lines of code total, but I guess its not about the amount of code, but the time spent thinking about it thay counts?
 6
6 -
Am i obsessed with security?
No Way!
Does my laptop need five seconds to calculate the aes-key for the program I'm working on, because I've set the hash-parameters unreasonable high ?
Maybe.3 -
OpenSSH 8.2 is out. This release removes support for the ssh-rsa key algorithm. The better alternatives include:
1. RSA SHA-2 signature algorithms rsa-sha2-256/512. These algorithms have the advantage of using the same key type as "ssh-rsa" but use the safe SHA-2 hash algorithms (now used by default if the client and server support them).
2. The ssh-ed25519 signature algorithm.
3. ECDSA algorithms: ecdsa-sha2-nistp256/384/521.
In this release, support for FIDO/U2F hardware tokens. Also noteworthy, a future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms.17 -
Broke down and asked the junior dev to help me hash out an issue. He's also struggling with it.
I'm not a retard after all... unless were both retards.1 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
Hey rejection, my old friend, I’ve come to grips with you again. Because a technical interview with a question that I thought I knew, required the use of a structure that I didn’t yet understand. And that I planned... to study... when I was done with hash maps....10
-
decided to participate in a short c++ curse at uni, just to refresh my memory about it since it seems rather important.
Got sidetracked at the preparation task, which was the usual hello world...
I'm running this in emacs now...
Like, one view is the program and under it is the shell run from inside emacs...
I dunno why... send help?
Now I'm considering how can I configure the emacs shell in a fun way.. oh dear.7 -
The week where you have so much to do on different projects, that even if you manage to work on all od them a bit it feels like nothing has been accomplished.
The point of being so tired that even the mildest sickness feels rediculously awful.
And it's friday. I manged to do some work for one of my bosses but the work I want to do didn't really get done and now I have two meetings in which I can say I started doing xyz but couldn't finish it due to bugs and exhaustion. And for the other project I wrote documentation.
Well.
T_T4 -
So my friend was copying a 32 character long hash string from one phone to another because he has the banking app in one phone and registered mobile number in the other phone...
So, I was waiting when he was halfway done... The I said, bro... you could have sent that text as message from Phone1 to Phone2.... His facial expression was unexpressable. I could have told in the begining but I am a devil. 😈 -
The most annoying co-worker(*team*) I have worked with just signed off a custom project that uses plain text passwords, hard coded into a file.. PLAIN TEXT!!! NO HASH!!! NOTHING!!! The same team also told me that working in feature branches cuts into their productivity, but they want CI/CD implemented NOW!3
-
Core library was giving serious blow out of execution speed as data file size increased.
Traced it back to a GetHashCode implementation that was giving too many collisions for unequal objects, so when used as the key in a hash table it was causing the lookup to fall back to checking Equals (much slower).
Improved the GetHashCode implementation, and also precalculated it on construction (they were immutable objects), and run time went to warp speed! Was very happy with that.
Obviously put in a thread sleep to help manage expectations with the boss/clients going forwards. Can’t give those sort of gains away in one go. Sets a dangerous precedent.1 -
"You have to change your password, because you've either just registred or your password doesn't comply with our guidelines anymore."
I've not made my account recently.
The question beeing: How can they know if they "should" decently hash it? 👿 9
9 -
3 days 2 nights with only 20 min naps and max 1h of sleep in between. I was finishing my masters thesis. Then I handed it in the next day and everything felt like it is in slow motion? The printing, the going there to hand it in, etc. Couldn't sleep for that day either xD do not recommend. Start writing your thesis on time kids
-
Install 18.04 they said. It will be fine they said...
Well.
Apperently it hates my intel graphics card. It was giving me artifacts already during installation. It didnt boot after installation and got stuck on a purple screen with the mouse on it.
Got past that with recovery mode. Googled the solution snd they said "move mouse while booting" yeah that doesn't help.
It also didn't recognize the other monitors connected to it and since it comes without unity now everything was not where I'm used to look for it.
3 hours of grub mangleing, driver installing and a unity installation later, it finally works.
Installed terminator and oh, look, one of the most used short cuts is overwritten by some emoji pick bs.
Ffs.
Longest ubuntu installtion ever and it almost fked up the 16.04 aswell which is in dual boot atm.
And before someone says use Arch: ubuntu is a project requirement and Arch is not supported by the tools we need to use.12 -
Unreal Engine adventures:
me: So ok, I need a map from int to String
Unreal: ya but it's called TMap, FCompactPoseBoneIndex and FName.
me: ..uhhh ok whatever
...
me: ok for debugging, please print this
Unreal: FName is not a string
me: k. Fname.toString().
Unreal: ya but it aint a TChar array now
...
IT'S A FKING STRING JUST PRINT IT. And the other guy is still an int with extra steps! Come the fuck on now....
I mean, honestly, a logging function that cannot print a fking FString? sigh...
Man, I miss python and blender...8 -
Manually updated a user who was attending a focus group's password by resetting it to a known hash...
Forgot the "WHERE user_id" part of the SQL.1 -
When you hash time entries by year and you are freaking out to make sure your server doesn’t crash due to differing time zones while your family is celebrating New Year’s...2
-
*random person in tram witha huge backpack* let's stand in the middle of the fking door, with my backpack towards the door so I clearly can't see if anyone is trying to get into the tram.
What the fuck is wrong with you? There is tons of space and even seats free what the actuall fuck just move along already! Jeez. What's wrong with people! At least stand at the side or something.
That's a new kind of shit. Don't get to see this every day.2 -
I've finally got a monitor at work that works with Samsung Dex.
Positive things:
- new super cool monitor
- can remove windows now from the dual boot of the laptop since everything I needed it for can be now done on Dex.
Negative things:
- DevRant doesn't work with Dex. It just doesn't load properly. But maybe it will work through a browser. Need to test...3 -
So here I am investigating something our users are claiming. I look up which user the UserId did the change and I see not only the user but also the users password in clear text in a separate field. I thought that field was for a password hint that the user can set up, but I asked around and apparently, no... It's literally the plain text version of the password stored in the database, next to the hash of the password.
Apparently, the users were so impossible to deal with that we added that column and for users that constantly pester us about not knowing their password and not wanting to change it, we added a plaintext password field for them :D2 -
Multi-Screen problem: So I need to run a VR headset with a laptop, and the laptop has only one hdmi connection. I don't have any extra hdmi adapters, so I cannot connect my second screen while working with the headset, which sucks...
but...
then it hit me...
there is an app called spacedesk which allows you to use your phone as an additional screen. I have a docking station for my phone so I can connect hmdi to it. On the first try the resolution was shit since it uses the default phone resolution. But the phone has Samsung Dex, which allows you to run everything full screen on your connected screen, so I can run the app within Samsung Dex and therefore will get full resolution.
And this works. It's kinda stupid and maybe a bit complicated, but it works. God, I love technology :D:D:D
This is the adapter to adapter to adapter to adapter meme in action, just wireless. Lol. I'm proud of this xD5 -
when you have to use one language inside of another, and you basically have to call functions allowing you to call the other's language function within it, and you get the hell confused, since it gets harder and harder to see what is what and who can call who and how, and the compiler ofc. won't say anything about it since it only cares about the main language you are in and not the nesting of the other...
I just have no idea what I'm doing right now, or if my thought process and understanding of this is even close to where it is supposed to be.
D: I'm just confused and insecure about this right now....
time for experiments to figure this out, and get the hang of it13 -
You know your too addicted to devrant when you have 5 minuets spare so you think to yourself "I'll look at just a few rants" and then the next thing you know it's been an hour or so.7
-
the fking piece of technology which is unreal engine... you spend a lot of time on rigging and preparing a beautiful skeleton in blender, you are finally done, and you want to export it as fbx. But nooooo here are like 100 hoops you have to jump through and another more 100 blender settings to set so that the mighty unreal "might" accept your humble offering of an fbx and break it 10 times in the process....
this is rediculous.
The error messages are useless. "mimimi you have multiple roots" "mimimi same named objects". Ya sure, and when I use the older fbx 6.1 library for the export suddently these are fine? hmmmmmmm
<.<'5 -
Hey, been gone a hot minute from devrant, so I thought I'd say hi to Demolishun, atheist, Lensflare, Root, kobenz, score, jestdotty, figoore, cafecortado, typosaurus, and the raft of other people I've met along the way and got to know somewhat.
All of you have been really good.
And while I'm here its time for maaaaaaaaath.
So I decided to horribly mutilate the concept of bloom filters.
If you don't know what that is, you take two random numbers, m, and p, both prime, where m < p, and it generate two numbers a and b, that output a function. That function is a hash.
Normally you'd have say five to ten different hashes.
A bloom filter lets you probabilistic-ally say whether you've seen something before, with no false negatives.
It lets you do this very space efficiently, with some caveats.
Each hash function should be uniformly distributed (any value input to it is likely to be mapped to any other value).
Then you interpret these output values as bit indexes.
So Hi might output [0, 1, 0, 0, 0]
while Hj outputs [0, 0, 0, 1, 0]
and Hk outputs [1, 0, 0, 0, 0]
producing [1, 1, 0, 1, 0]
And if your bloom filter has bits set in all those places, congratulations, you've seen that number before.
It's used by big companies like google to prevent re-indexing pages they've already seen, among other things.
Well I thought, what if instead of using it as a has-been-seen-before filter, we mangled its purpose until a square peg fit in a round hole?
Not long after I went and wrote a script that 1. generates data, 2. generates a hash function to encode it. 3. finds a hash function that reverses the encoding.
And it just works. Reversible hashes.
Of course you can't use it for compression strictly, not under normal circumstances, but these aren't normal circumstances.
The first thing I tried was finding a hash function h0, that predicts each subsequent value in a list given the previous value. This doesn't work because of hash collisions by default. A value like 731 might map to 64 in one place, and a later value might map to 453, so trying to invert the output to get the original sequence out would lead to branching. It occurs to me just now we might use a checkpointing system, with lookahead to see if a branch is the correct one, but I digress, I tried some other things first.
The next problem was 1. long sequences are slow to generate. I solved this by tuning the amount of iterations of the outer and inner loop. We find h0 first, and then h1 and put all the inputs through h0 to generate an intermediate list, and then put them through h1, and see if the output of h1 matches the original input. If it does, we return h0, and h1. It turns out it can take inordinate amounts of time if h0 lands on a hash function that doesn't play well with h1, so the next step was 2. adding an error margin. It turns out something fun happens, where if you allow a sequence generated by h1 (the decoder) to match *within* an error margin, under a certain error value, it'll find potential hash functions hn such that the outputs of h1 are *always* the same distance from their parent values in the original input to h0. This becomes our salt value k.
So our hash-function generate called encoder_decoder() or 'ed' (lol two letter functions), also calculates the k value and outputs that along with the hash functions for our data.
This is all well and good but what if we want to go further? With a few tweaks, along with taking output values, converting to binary, and left-padding each value with 0s, we can then calculate shannon entropy in its most essential form.
Turns out with tens of thousands of values (and tens of thousands of bits), the output of h1 with the salt, has a higher entropy than the original input. Meaning finding an h1 and h0 hash function for your data is equivalent to compression below the known shannon limit.
By how much?
Approximately 0.15%
Of course this doesn't factor in the five numbers you need, a0, and b0 to define h0, a1, and b1 to define h1, and the salt value, so it probably works out to the same. I'd like to see what the savings are with even larger sets though.
Next I said, well what if we COULD compress our data further?
What if all we needed were the numbers to define our hash functions, a starting value, a salt, and a number to represent 'depth'?
What if we could rearrange this system so we *could* use the starting value to represent n subsequent elements of our input x?
And thats what I did.
We break the input into blocks of 15-25 items, b/c thats the fastest to work with and find hashes for.
We then follow the math, to get a block which is
H0, H1, H2, H3, depth (how many items our 1st item will reproduce), & a starting value or 1stitem in this slice of our input.
x goes into h0, giving us y. y goes into h1 -> z, z into h2 -> y, y into h3, giving us back x.
The rest is in the image.
Anyway good to see you all again. 20
20 -
This semester, we have a lecture called IT Security by a guy, who absolutely know his subject.
Nevertheless, he wanted to show us that sha256 is broken by an existing collision. (Google that, fellow ranters!)
There are two pdf files by google researchers, that show the caption „SHAttered“ both on different backgrounds, although they give the same SHA-hash.
He then tried to share us these two files by moodle and wondered, why he uploaded the same file twice.
Guess what happened? The moodle backend checks new uploaded files for their ... hash ... and then decides, weather to upload or the file is already existing. So, it did just a new symlink to the old file.
Ironic, that an exercise, that should show us sha collision failures on sha collision 😃5 -
Whenever I have to ask about how certain code of someone else works, I feel bad. I feel like I should be able to figure it out on my own.
On the other hand, if people ask me to implement something within their code, that I am not familiar with, I kinda expect more info? Like if you don't have any tutorials or documentation on your tool, be prepared to answer some stupid questions about how to set it up and whatnot. How else am I gonna know how to start with? Having to read the entire source code is a massive waste of time, no?
tl;dr: if you don't provide documentation or tutorials, be ready to answer stupid questions.8 -
what it's like when someone doesnt use "mm/dd/yyyy" or "dd/mm/yyyy":
"I need a name for your reservation. It can either be base64 encoded or a sha3 hash"
"Yeah, I'm on my way, how many light years is it past 404th street?"
"Oh, cool, my birthday's coming up, too. How many eons away is it?"9 -
I've ordered my better a half a christmas present. He just send me a link of that exact christmas present. I had to tell him not to buy it for "reasons".
Fk you google! You ruined the X-Mas suprise T_T
It got suggested to him by google when he was looking for something similar.
Goddamit. I was so proud to have found it first T_T4 -
*Nervous student comes in for the first interview I am conducting as a developer*
Me (as an interviewer): What is best approach to search data?
Student: It will take linear time but if data is sorted, we can do it in logarithmic time.
Me: [Smiles] Take a hint Hash Map?
Student: Yes, with it, we can do it in constant time.
Me: Okay, Bloom Filter anytime?
Student: *sweating* noooo...
Me: Okay. I am a developer so I know this.
Student: *about to cry*
Me: No problem but why will you search data when there is no problem? Don't you have better work.
Student: *confused* yup
Me: *laughs but immediately controls* Take it lightly. You know what you need to do this job. You are HIRED. :)2 -
Checking out a project on GitHub:
> Using advanced condition-based AI logic, Compactor can skip over files that have been previously found to be incompressible, making re-running Compactor on a previously compressed folder much quicker.
> (Yes, it's an if statement and a trivial hash database, hush) 2
2 -
Corona times and remote work be like:
hm, can't connect to my pc at work again. Why is it down? Whatever
*starts writing to collegues asking if anyone is physically present and could kick (aka. boot.) the pc.*
ah yes, fun times7 -
!dev
People these days...
At a bakery 3 girls didn't bother to clean up after themselves although the only thing left to do was to t aske the tray and dump it's contents into the trash can WHICH IS ON THEIR WAY OUT. Yeah but have enough time to cake on rediculous amounts of makeup...
Someone literally shat at the tram stop at the main station so whenever took leave the tram you might just step into it.
Then there are always those religious people trying to hand out pamplets about how great their religion is and how much it is helping- they stand right next to a crippled homeless begger.
Just wow.9 -
I forgot my password to my mindfactory account, one of Germany's biggest online vendor for computer components. So I go through the resetting process, which is:
- apply for password reset
- get a mail
- confirm the mail
(So far, so good)
- get a mail with a new CLEAR TEXT PASSWORD
Is this the stone age!?
You never send an email containing the cleartext! You never even store the password as is!
You, as the provider, should never be able to know what the actual password was.
All you are supposed to do is to generate a random salt, and hash the user's password with the salt, and then you only store the salt and the hash. And whenever a user inputs their password, all you do is to check if the you can recreate the hash with the help of the salt and your hash algorithm. (There are libraries for that!)
If a user wants to reset their password? Send them to a mail with link on where they can assign a new password.
At no point should the password ever be stored or transmitted in any other medium.5 -
!rant !dev
I was just on my way to work back from the University cafeteria when a guy in a black car - who I thought was moving the car out of a parking lot - stopped the car and asked if I had a second.
Naive me, thinking he might need directions or something decided to listen to him.
He looked older, around 60ish, with sunglasses on ( making it harder for me to read him).
He said that he had a stroke (or something) a few years ago and got damage to his brain, so that sometimes it can happen that he would faint. Therefore, he cannot go swimming unsupervised, and was asking if I would have the time to accompany him to the university lake, so that he could swim for an hour or so. He offered to pay me 40 bucks.
Me, being paranoid af, declined politely, saying I have to go to work ( which was actually true).
He goes on to say how he was a teacher, how he worked at the university before, how I look trustworthy, how I am the first person he asks today, and asked if he could have my number, so that he could call me sometime to supervise the swimming. I would just need to look out for him not to drown and if anything looks weird I should alarm the people working at the lake ( lookouts? not sure what they are called).
I kept declining politely and he backed off, letting me go without any fuzz.
Previously he also mentioned how some students are rich, others are poor, and how he would have done anything for 20 bucks back in the day. But also said that he accepts a no and won't bother me further.
He also mentioned he wouldn't lay a hand on me, that he is not a creep, since I could see his car and license plate, and if I gave him my number, I would also have his. That I shouldn't worry about anything, if I later decided to say no he would delete my number, and that he is not big on the technology and Internet so nothing would happen.
Uhh... well if he was genuine I'm sorry for him, but then you can just ask authorities at the beach to pay more attention to you, no?
Mentioning "all my worries" raised a red flag for me sort of.
Also, if you keep on fainting occasionally, even if you haven't fainted in 2 years, how are you allowed to drive? Or actually, why do you even drive then?
I don't know. The more I think about it, the more I think I should have taken a picture of the car or license plate.
And there are literal services for this kind of thing. Pretty sure you can get one of these if you are willing to pay even.
Jeez now I'm worried for the entire population of my university...9 -
I discovered a commit message from one of my (senior) colleagues today. It made me shudder. It read, 'Just adding some changes made outside of source control and deployed (over last 12 months)'.
I genuinely think he can't follow any processes he didn't design. He controls the servers too, so it's not like any pipeline would prevent him from just doing what he wants. It's a bit scary to be honest, he thinks MD5 is a secure password hash! -
I have no experience with mobile app developement and i dont prefer coding in JAVA. But i want to make a mobile app based on an idea. Where do i start?20
-
I took Database System Class and Courses in University, and told to store the password using its hash and don't store it in plain text; it is at least a standard.
today i just resetting my gmail password since i forgot the password. and i wonder by how google forgot password mechanism work.
for example i register the password with:
'xxxfalconxxx'
and then change it to:
'youarebaboon123'
sometimes later i forgot both password, and google asked for the last password i remember; and i only remember part of it so i entered:
'falcon'
and this is right, so i can continue the forgot password mechanism. how could you check the hashed text of 'falcon' is the subset of hash text 'xxxfalconxxx' ?2 -
What container data structures do all of you actually use?
For me, I'd say: dynamically sized array, hashtable, and hash set. (And string if you count that.)
In the past 8 months, I've used another container type maybe once?
Meanwhile, I remember in school, we had all these classes on all these fancy data structures, I havent seen most of them since.18 -
anyone else giggle when someone says "this method takes a dict", or " wow that's a big dict", or really anything that sounds like they are talking about penises.3
-
It bewilders me how people drive too close to tram tracks and almost create accidents. What do you think is going to happen? It's a freaking tram! It can't dodge your lazy ass ffs. <.< they teach to especially look out for trams and trains and he carefull around them. For your own safety.
Goddammit.
Yes we (tram) just almost collided with a car...2 -
Wanted to have Samsung Dex for work, so I can run office on it and kick windows from my dual boot laptop.
Dex pad was on sale.
Bought it.
Brought it to work.
Work monitor doesn't have hdmi.
...
fuck. <.<
I'll ask the technician later if he either has a monitor flying around he doesn't need or an adapter or something.1 -
VirusTotal's API could do with a make over.
Though it is quite nice actually, you're able to provide them with a hash of a file and (provided they've scanned it) VT is able to tell you what up to 60 different virus scanners thinks about the file (and how many scanners that has an opinion about it). Now if there's an error, like the file not having been scanned or the hash being incomplete, it give you some JSON back where there will be an error message that tells you the error and an error code of 0.. wait wh
Although since it's an API they also need give us plebs whose only got access to an API key that limits us to 4 requests pr minutes. Naturally when you try to do another request within a minute of your limit the response you get is absolutely nothing what so ever. "" Naturally.
And of course the same response should be given when the API key you provide isn't valid. Who needs errors amiright?
No wonder JSON.parse kept throwing exceptions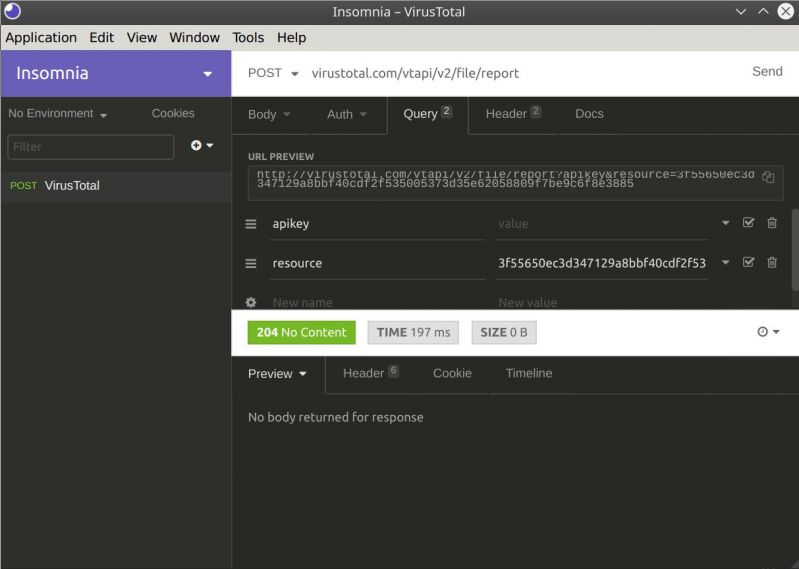 4
4 -
Unreal Engine + third party library adventures part2:
now we gotta parse everything from unreal formats, to the library formats, than back to unreal again... sigh. Why can't it just use normal data formats like everybody else? I mean, come on, strings, ints, vectors etc. they all have standart libraries. why does unreal need to make their own shiet out of it. Just why...1 -
Everyday strugle.
Go to work, go home all motivated like: oh once I'm home I can do this and that to finish my work, and it's fun and interesting. Or I vould study, or clean up, I'm totally gonna do something usefull!
*once home*
Ohhhh look league of legends! Or bed! I'm too exhausted to do anything usefull. Better chill.
...
Anyone else?
Anyone got advice for how to combat this? T_T5 -
Opens the source code for an app I have to integrate with.
Finds: if($cryptPW == $dbPW)
What the shit?!?!!!!!
Learn to hash! Far out 😢4 -
1.5h into the c++ course (which I'm doing as a refresh).
I spend most of the time fixing errors I had with my general system (apt had some issues) and helping the people next to me who are new to this.
Will probably do some c++ tutorials next. I think I'm just using this course as an excuse to finally come around and put some time into learning C++ properly xD -
So, I need to search for a new job again. The thing killed my project.
15 years of Java experience in my resume, I look a like a sterotypical 35 years old programmer, I’m applying for expert roles. But every remote technical interview starts with:
- what is the difference between ArrayList and LinkedList?
- what is a hash map?
The hardest part is to keep smiling to the camera, pretending I don’t have the answer memorized by repeating it for the last 15 years of interviewing, and not rolling my eyes.
And before you ask, I do know what garbage collector is.4 -
Benefits of using Strings for Boolean intended logic?
I'll go first
easily implement cases before finally checking if true
generateUsername: { type: String }
if(generateUsername == 'humanReadable'){
// generate a username in a human readable format AKA yoDudeImRainbow
} else if(generateUsername == 'hash'){
// generate a username by using a random hash
} else if(generateUsername){
// generate a username by using a random hash
}21 -
when you are so used to Unreal Engine crashing while trying to debug your code that you're actually suprised when it doesn't x'D
ya I'm pretty sure I'm not debugging it in the most efficient way, but oh well. Progress I guess. -
If I were to change all my passwords into hashes (so take a random word and hash it, ex 'table') and then use those on various websites, would people ever guess that my password is _an actual hash_ rather than a password in hashed form if they were to see it? Would such a meta-hash be safer if 'hackers' were to find it unencrypted?8
-
The day has come where I was asked to fix some windows issue of a coworker (not an IT guy) at home. Some data sharing issue in the homenetwork.
Ok, told him I've never set up anything like this but could take a look at it.
Got it fixed after 1-2hours and he was nice enough to pay me for my time.
I'm not even mad, that is nice :)
While I fixed stuff for a friend multiple times who is richer then me who can't take me to the next tram stop by car after a meeting since it's not on her way. Damn.3 -
Callback your functions, not your ex.
Hash is for your data, not you,
Query tables, not your loved ones. -
Unreal engine adventures part 3:
Code compiles. Everything is fine. Close engine and open it up again since I'm coding a anim graph node and it does not update it unless you restart it.
Unreal crashes...
...
Why the f. Like even if one node is buggy than glag it red and stop execution of it. Why does the entire engine decide not to start instead? That's utter bullshit! And all this because of an array out of bounds? Really? And this thing is supposed to be professional? Come on...5 -
That feeling when you debug the Users table in sql, which has a Password field encrypted with hash, but most of the demo users use the same Adminadmin password, so you recognize the other users password because you rembered the hash
-
Spotify you little shithead how often do I have to reset the random mode for you to finally play stuff at random and not loop the same 20 songs? WTF? you literraly have like 1k of them in this list and you loop 20! HOW AND WHY <.< i even pay for you. Get it together.
Anyone else feeling murderous mood today for no reason? I'm not even at work yet...1 -
Why the fk is there still no dark theme for google calender? Mostly for phones. This shit is lame google. Even freaking outlook has a dark theme by now!9
-
We have a univeristy internal gitlab. Ok.
My work place uses the official github. Great. No problem.
Now for another work related project, we got access to the gitlab of an institute which is at the same university....
Why the fuck do we have to use their gitlab now also? I've got 3 different git accounts now. It's just unecessary and annoying... -
Guys, start writing your shit early. Don't do what I do and pull two all nighters in a row in order to finish a thesis.
And then complain about having forgotten to mention something.
Do not recommend.
I'm also out of red bull and have at least 4 more hours to go. Wish me luck xD6 -
Ended up with 16.04 and 18.04 ubuntu in dual boot. (see last rant).
Fixed graphics issues on 18.04. The fix envolved setting stuff in grub. Ok.
Now we apparently need 16.04 again and can kich the 18.04.
np. Let me just boot my 16.04
oh look who has graphics issues now!
It boiled down to the grub settings. so Depending on if I need 18.04 or 16.04 I need to fiddle with grub. great.
And now we don't neet 18.04 at all. So I tried to do something not in the last minute once, and it backfired completly. Wasted 5h on this shit this week. Fk this.2 -
Created an md5 hash for the admin user's pw on a personal project and the hash starts with "bad666...".
Is md5 telling me something?
Hmm...8 -
So Igot that Samsung DeX thing a while ago. So far, it was just a nice gadget to have at hand, but I didn't get to use it properly since my laptop was always the better option sort of.
Now.
My power adapter for the laptop died last friday. I have a second one at home, but of course, I pack the wrong one for work.
Ended up working the entire day on the DeX. Thankfully, I just needed to do some web and office based stuff, and all the necessary documents are online anyway.
So that thing just saved my butt today, which is nice. Took a while to get used to, but it does it's job quite nicely.
To be honest: Iam suprised it works the way it does. Oh what a time to be alive...
Now the question is...
Can I get Ubuntu on here somehow? I did find a Tmux? shell and was able to download some ubuntu onto it, but it had gpg issues.
Anyone got more references? Ubuntu on Android 8.13 -
Got access to root access of school's lab computer.
Saw an account 'tee'(Term end exams) associated with it, copied the hash, ran a dictionary attack and the password was 'tee'
FUCCCKCKCKKK1 -
After 20 mins, the system is just sitting there idle doing nothing but data transfer.
Is this a common problem with manjaro? Unbelievably slow data transfer
-
hashing passwords atm.
i have a java backend, should i look into bcrypt or just use a loop?
also how many times would you recommend i hash passwords?
and should i look into hardware acceleration?11 -
Not only is the default password they set a piece of shit, the password field actually shows the password even after you save it, why even bother with security?
Hash your fucking passwords!
The internet kills my insides. 4
4 -
How is it possible that Microsoft Office and Open Office have less portability issues then Microsoft Office on Windows vs. Microsoft Office on Mac? It's supposed to be the same f*king programm developed by the same company! <.<2
-
I had joined a new company and got access to their codebase. They were updating password on MD5 hash of user name and their email in get request. No password validation, no token based authentication, nothing.
Eg
...com/change_password/email=(plainemail)&name= MD5(name)
That's it, you get change user password. -
Manjaro with kde is bad. Inconsistent and lags unnecessarily. Worst linux experience till now. I have actually started using windows on a daily basis after this.
Any other distros worth trying?8 -
what the fk how hard can it be to have a working version of the software on the master/ ros-version branch? Why is this thing always broken?! HOW?!
Had to update today unfortunately, and man, I have been "installing" this shit for over 3 hours now. Use the .install they said. It will be fast they said. Ye sure, my ass. The Dependencies are broken and incomplete as always and the tutorial is not up to date. Big suprise. I get it, it's a lot of work to keep these things up to date. But please if they are this broken and incomplete why are they released in the first place.
And then they wonder why I don't manage to do my work on time. Yeah, cause I'm stuck debugging this shit <.<'1 -
I'm going through a KhanAcademy course learning about cryptography. I learn better by doing, so I wrote a script. It shifts bytes up depending on a random int produced by a high entropy pseudo random number generator using a sha256 hash as the seed. I'm trying to find information on the flaws with this method, that lead us to create DES, and then AES.
-
Unreal Engine fun continues...
so I need to set limits to rotations within a skeletal mesh. So in other programms, like blender, you can specify a limit per axis, setting max and min angle. Makes sense, right?
Unreal Engine:
1. Let's call rotations sometimes xyz, sometimes roll pitch yaw, and sometimes swing1 swing2 and twist so that nobody knows what it is anymore.
2. IK node 1: limits? what are limits?
3. IK node 2: ok, you can set angular limits but they are all symmetrical to god knows what and to all axis apperently.
4. Physics: yeah you can define joint constraints but we give you only symmetrical constraints also
....
WHY. Were does this make any sense? One node is not like the other, and they talk rotations but use 100 different terms for them, since, hey, why the f not. And let's limit everything symmetricly so you can only set one value or have to fiddle with offsets to achive the range of movement you want.
I mean, one could just stick to xyz (or even roll/pitch/yaw, whatever) and min/max but hey, that's one extra field and then it would be easy to use. Who would want that? ....4 -
I'd like to one day be as good as my tutors or my better half.
Overseeing research code and developing it further with very little documentation seems like a very precious skill to me. They have my respect for that.
That would also involve getting a phd.
I feel so clueless sometimes but apperently I'm a fighter, so let's keep goin and trying :) -
The C Standard Library has a Hash Table implementation, and it's a man-made horror beyond comprehension:
https://youtube.com/watch/...5 -
So our project decided to create a newsletter. For some reason, I was tasked with writing it, includig layout, recepient database etc.
It is the first newsletter, it is urgent and it is supposed to be send to all the people who so far participated. Means: there was never a "sign up here for a newsletter" thingy on the website. Hence, there is also no "unsubscribe" button.
One could kind of "hotfix" this by making a field, like "enter your email adress here to unsubscribe" and then I get a notification and remove the people from the list. Fine by me. Not so many ppl atm so we got time to set it up properly then.
My boss decides it is my job now to implement the stupid unsubscribe button... I am not the website admin. I have nothing to do with the goddamn website. We have ppl in another city, being paid to manage the goddamn website and it would take them just a few minutes to set the stupid button up, since they know what they are doing and I am not.
I told them from the start: I don't do websites. I have nothing to do with them, I don't want to have anything to do with them. We have people for this.
Why the F is it my job now to implement that stupid button?!
And even when I tried to look into how the other formulas which do similar things are set up: oh you don't have permissions to access that. Lovely!
FAK this shiet <.< It is not my fking job.5 -
Here's a fucking challenge:
Generate an MD5 hash in React Native!
crypto - NOPE deprecated, react native throws when you try to import it anyway
react-native-crypto - NOPE, needs to make use of a shim that recursively edits node_modules... hmmmm yeah you think thats a good thing to have?
react-native-fast-crypto - NOPE, no TypeScript types, no documentation in general, only supports sha512?! WTF
garbage fucking idiot tooling stupid dumbass stupid splat splat barf splat21 -
Fun fact: If you ever want to see the password you are typing or view the contents of a password field in a form, just pull up the web inspector. You can change the input type from "password" to "text" with no ill effects upon submission.
The lesson? When populating password fields, put junk values in there instead. Will present the right appearance, and doesn't risk exposing something that should be stored as a salted hash anyway.3 -
when you think you're done coding and can finally start writing...
So you guys have seen my Unreal Engine adventures. I have to use a plugin for it, on top of everything, to extract some data. I've been using this plugin since ages on another pc, but now I had to set it up from scratch since this is a new project, new models, etc.
There is a new version. If I use the new one, it will break the chain which is to follow.
The old version is so legacy that the guy who wrote it does not remember how to set it up.
After hours, and tons of hacks and outcommenting stuff (there is physics involved with which I do nothing), it finally starts doing something. Finally!
Although I'm slowly loosing my sanity in the process....
Even if it now records the data, I cannot say if this is good enough or if the poses are all wonky now.
And that is my masters thesis. Submission deadline is on monday. Ha.
Ironically, since the start of this thesis, I felt like this will either make me or break me. ;D So much fun... FK2 -
!dev?
Colleges now require proof of vaccination but admins are worried about the spread of fake vaccine cards
https://apnews.com/article/...
My mindblowing solution: require students to submit a covid antibody test result instead.
You can't spoof the lab test result number and it can be easily verified by calling the lab...
Can even create a site for that...
isTestValid.com
Worried about privacy... Have labs upload a hash of the data...
And user submit their hash...
Clearly nobody asked a dev for they're input... again2 -
whenever I think I am almost done with coding something, and go like "yeah, I can totally finish this the next day within just a few hours. Just add 1-2 functions and done" - it ends up being the opposite. I either realize how many things I didn't think and implement through and end up adding lots of things or I come up with a different approach to things which seems better and have to rework half my stuff...
I guess this will get fixed with experience.
Until then, I guess I'll keep trolling myself. -
I usually improve when I have to make workshops and courses for school students. Since then I try to look into things as indepth as possible since I have to be able to explain it in multiple ways and know the backgrounds.
I'm also currently trying to read a lot about the things I have to work with. -
unreal engine is soooo much fun! You set a reference pose for vr motion controllers and expect them to have positions relative to it, and also expect them to be right in front of you. Well, no, they go completly wonkers and get beautiful positon values of 23874 2387236 2032938 which is way out of the world. IN WHAT FKING UNIVERSE DOES THIS MAKE ANY SENCE?!
Just because I parented them to a a scene object way within my character?! WHAT THE FK I followed the nice tutorials. What is this BS and why is it so fked up!!!4 -
Just found the most embarrassing security hole. Basically a skelleton key to millions of user data. Names, email addresses, zip codes, orders. If the email indicates a birthdate, even more shit if you chain another vector. Basically an order id / hash pair that should allow users to enter data AND SHOULD ONLY AUTHORIZE THEM TO THE SITE FOR ENTRING DATA. Well, what happend was that a non mathing hash/id pair will not provide an aith token bit it will create a session linked to that order.
Long story short, call url 1 enter the foreign ID, get an error, access order overview site, profit. Obviously a big fucking problem and I still had to run directly to our CEO to get it prioritized because product management thought a style update would be more important.
Oh, and of course the IDs are counted upwards. Making them random would be too unfair towards the poor black hats out there.1 -
when instead of coding one spends far too much time on expanding the syntax highlighting for better readability...
I mean, yeah it took me like 2h, but now I have a vague idea on how to quickly add things which improve readability for me.
emacs config ftw. -
You know how people want to avoid collisions with a hash map?? Well a buddy and I went to a hackathon about 2 years ago, and the idea we had was kinda cool, but to get a prototype working, we decided to defy the logic of a hash table and purposefully cause collisions with a hash map. I took a look at the project and it is soooo poorly implemented.
-
I need to link two APIs such that data sent on one API gets processed and it hits a second API with the processed data.
The first API needs to format the data and decide according to data format which second API needs to be used. I checked Zapier and it's working but it is not exactly what i need to do. So are there any options other than setting up my own server?3 -
Is it possible to track down an IP from a Skype contact? Need to find out what country they are sending from. Asking for a friend.4
-
Assume U've captured the cap using airmon-ng , airodump and aireplay .
The question is:
If I dont wanna use air crack-ng and wanted to use sites like hashkiller , how can i get the hash from the cap file?
-
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
My mum signed me up for a robotics workshop with Lego mindstorms... i kept going to these workshops, doing some of them multiple times. At some point we went from graphical programming to some other kids language, than we made a robocup junior team from the kids who were like me and kept on showing up at these workshops and used arduino and C. Had a break for a year or so from coding so I could finish school, then I went studying computer science at Uni. And the rest is history.
-
why is outlook so fking painfull... designing a newsletter. thunderbird: shows everything fine. Outlook: brakes design complelty.
Design was made with Microsofts own Publisher, which claims to be usable for creating newsletters...
Then outlook cannot send out massmails like publisher can...
what the fuck is wrong with them! You are developed by the same fking company! How can one tool show something one way and another display it completly differently... whyyyy
(since I am not the webadmin I cannot use a fancy newsletter designer tool and integrate it into our website since we first would need to talk with the entire project about it...)8 -
Not a rant but I kinda wanted to see if anyone else feels the same way and might have advice on how to overcome this:
So I work as a student in research. Meaning there is not much documentation and things are chaneging fast, some things are also fairly complicated.
I have a really good supervisor.
However. I am super scared of asking about how things work. Whenever we discuss things and she notices I'm insecure about how something works, she explains it to me patiently. No probs. But insead of asking I just try out random stuff for hours. Having no clue about how things work and what I'm doing. In the end she is able to explain the issue to me within a minute.
The thing is, I think that trying to figure stuff out on my own, is the right approach. Not daring to ask questions or express my theories is really bad. I get super anxcious. Most of the time my theories and assumptions are correct. I just never dare to voice them.
The irony is, that I'm perfectly fine whenever I talk about or hold presentations which are not CS related. But if I have to do that on a CS topic I just die. I freezze, stutter, everything.... T_T
Like come on. They can't do anything to me except correct me... jeez.2 -
Does the windows "optimization" feature which apparently is defragmenting in the background, and apparently "optimizing" ssd's differently of any use? The only thing I notice is that this function makes the icons of my desktop reload on a regular basis. My guts tell me it's utter bs and is just slowing down the system.
Any experiences, optinions, thoughts?6 -
I've just discovered by accident that the dumbest way of solving the Hash Code practice problem is way better than my previous solution.
(medium 49509, big 897164)4 -
What a time to be alive... when one gets so lazy that one orders freaking Burger King or McDonalds as a delivery service... daymn...
yep. I'm gulty. Had to try it out. Totally in the name of science.1 -
Exited about Hash Graph, Which everyone says it will replace BlockChain
http://thehindu.com/sci-tech/... -
I've seen a lot of buzz around the EU's GDPR and since I don't live there I'm wondering if it applies only if you store personal data and should it count if it's hashed for example?🤔
Let's say you hash a client's IP, it's not technically his data you've irreversibly transformed it into something else, like a computation.
For example let's say he provides you with a number and you multiply it by another and store the result, let's say 2 x 2 = 4, Is the 4 his data or yours?
Also I'm really interested in the general opinion of ranters about article 13.14 -
Why the fuckin' hell does PayPal limit your password to 20 characters?!?
The length shouldn't matter if they hash and salt the passwords... sooooo...4 -
There was a lady who had come for QA automation demonstration.
She was mentioning the languages used and uttered, C hash for C#...2 -
Am doing an online shop for some client as a side project. The client never requested a module enabling an admin user to manipulate listed products. Now this cheap genius wants to be able to login as a seller and manipulate whatever products they've listed. So I told the client it's not possible to do that because passwords are stored as hashes. Now, can you Guess who's storing clear text passwords ?
May shit never hits the fan.3 -
when a dev with absolutely no knowledge of the systems or whatsoever, tells a client "sure, easy. we can get your password if you forget" and that client then comes to you and doesnt understand he has to use the recovery function because its encrypted using a slow oneway hash...
needless to say, that dev thought passwords were stored in cleartext.. -
List of things one of my Python projects needs:
- cross-platform IMA/VFD/VHD/VHDX/qcow/VMDK/IMG/DSK/others image read/extract support that doesn't need admin/root privs (so no, can't use dd or mount)
- custom DB format (for speedups when indexing files and retrieving info based on hash) and converter from previous DB format
- GUI or actually good CLI
- massive speedups
kill me now4 -
I've just found an article that states that MS Office 2016 can now be installed on Ubuntu using CrossOver, which is the version of wine one has to pay for.
Is there some version of wine or an alternative which is free and allows me to do this?
Yes, I know the alternatives of online MS, google docs, libre office and whatnot, so spare me these comments please.
(ref: https://omgubuntu.co.uk/2017/12/...)7 -
trying to rotate the character in Unreal Engine based on player input. It rotates around some sort of super weird point, so it looks like it's driving "backwards" while rotating, instead of rotating around the center of the mesh... sigh..
...
...
Solution: pass down the rotation value to the animation blueprint, rotate rootbone.
SUCK IT <.< See? it's not that hard, nor awkward. ffs.2 -
anyone else having a few hours of not being able to focus after lunch? Or is that just me?
It doesn't matter what I eat or what I do, after lunch I just can't focus on anything. Until 4-5 pm. then focus comes back again.
The only solution to this that I have is basically don't eat a full meal at lunch, but try to have healthy snacks instead.
I dunno.
Any ideas? it annoys the hell out of me.4 -
I sometimes cant scroll on devrant in the web version. I can scroll through rants but not the comments of one rant. It just jumps back to tje beginning of the rant all the time.
Anyone else?
It seems to be connected to resizing the firefox window. If it's smaller, gg. Thats it. No comment reading for me.
Anyone else?2 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
Am I the only one who when studying for an exam has the urge to copy all the slides by hand? And I mean not typing, good old handwriting. Then scrible in them and add own notes, write a summary and then try to recall it all.
It doesn't seem very efficient but I do not feel complete or even remotely prepared if I haven't done this. Although I did pass exams in the past without doing all of this...2 -
So, I made this API which logins to the system and Used it in an android app, there was one roadblock to it, that everytime user enters a password, it has to match the password hash so I, excitingly, used password_verify($password,$passwordHash), unknowingly that it is fucking unsafe and the code is still there, and here's where it gets interesting it is not over SSL/TLS. Fuck me, any bright solutions?27
-
Currently learning go and I’m really enjoying it. It’s been a while since I learnt a new programming language and the experience is different to what I remember. I’m reading an o reilly book and when about how they implemented a common feature of programming I’m like oh no they didn’t. I think this is what normal feel when they read celebrity gossip. Hash tag goto.2
-
the worst person I worked with was back in school. he would make no contribution to our work and would have a go at me if I did something wrong and whenever I fixed a bug he would act as if he knew the solution the entire time. it was so frustrating2
-
Just dropping some current experience here.
Content security policies are big mess in both chrome and firefox.
Chrome has some 4 years old "bug" where you can't add hash of JS file to 'style-src' policy to permit inline-styles THAT would be set by this script (jQuery actually).
Firefox is beautifully unhelpful, it just pops of error "blocked ..something..", not even saying what it was.
EDIT:
And I am missing a pair of some steel balls to ask about this on SO because there is this much of very similar questions, nonetheless -if I did read them right- every one of them is talking about enabling style attribute, and that's something different.
EDIT2: Chrome currently generates 138 errors "jquery-3.4.0.min.js:2 Refused to apply inline style..." , this ain't hitting production.10 -
I’m making a cut-down version of scratch for a personal project and I just fucking had to write a linker for it.
I fucking… it’s… a flowchart language… and to avoid a hash-table lookup of function identifier to underlying logic.. I wrote a linker.
It’s like, maybe 10 total lines. So not a real linker. But still. Just a bit crazy.1 -
So, we're preforming a re-write an application. It's on an application (actual mortgage application, not 'app') that has 4 different entry points. We have the most common entry point converted to our re-written application with plans to have the next couple done over the next several weeks. Yesterday, the old version broke. It was under the impression that it could grab any row that matched the borrower and then check against a hash of that data to see if it could proceed. It can't. You can't hash data set 1 and expect it to be the same as the hash for data set 2. Not a thing. When asked, the only answer we could give right away was "We'll fix it, give us a couple of minutes" and "Sorry, bad {{appName}} is bad. We don't know root cause yet. We'll let you know when we do." Was pulled aside by my manager and told my answer was unsatisfactory and I shouldn't give answers like that. I get it, "Bad {{appName}} is bad" isn't great, but it's not like we were going to give that and leave it! We needed some time!2
-
Just acquired a udemy course and got kinda disappointed when the man reads a part of a URL which involves a # sing and reads it as "hash-tag"...
Wtf. I hope it's worth the money6 -
Any terminator experts here?
I want to make a setup of multiple split windows starting things on launch. I got so far that I get all the windows with the layout option but I cannot launch what I want via custom commands.
I want to launch multiple ros launch files like that.
Any ideas?8 -
So I start up the Windows Upgrade Assistant to upgrade my Windows 10 to the anniversary edition and it shows me that I'm running version 10240 and I can upgrade to the latest version 14xxx.
So I hit upgrade now, wait for 10 minutes for the update to be downloaded and another 10 minutes for the update to be installed. Then it does the customary reboot after update.
So now I assume that I'm running the anniversary edition of Windows 10 but it shows that I'm still running 10240.
WTF was the upgrade assistant doing in those 20 odd minutes. And now it does it in an infinite loop. Is Microsoft trying to explain me what an Infinite loop looks like practically.2 -
When instead of propperly coding one ends up adding syntax highlighting to emacs for specific terms and just other fancy functions...
I mean hey, it is somewhat more readable now I guess. 🤷♀️
...
Guess I'm just distracted and aoiding the issue ^^' -
so in order for me to be able to design a theme for a samsung phone, I have to apply and it has to become public after? what?
https://developer.samsung.com/theme
the fk2 -
I have several tasks in my job. Not all of them are straight up dev, some are also student related. Since my coworker left I was rediculously overbudened, simply because the tasks I have to do are sooo far appart from one anothet. After talking to my boss, we get to hire some people to help (big yay!) But now it is upon me to write the recruitment adds so to speak and also talk to the people and interview them. What the heck I have no clue about this whatsoever xD i mean, i kinda feel honoured that my boss trusts me enough to do a pre selection for her. But damn. .-. I'm barely older then the applicants (it's all at uni and I'm a student and so are they)
Anyone got tips for interviews? I dont need them to do dev work. More like working with kids and presentation prep and support. -
Blockchain Pun
"I don't have time to talk about the blockchain but we can HASH the details later"
😎joke/meme pun intended bitcoin programmers pun cryptocurrency ethereum funny joke hashing blockchain1 -
!rant
anyone got any experience with Samsung Dex? I still keep Windows as dual boot on my laptop since I sometimes need MS Office with full functionality and not only the limited online/mobile version. I heard that one could install full MS Office on the Dex since at some screen size Microsoft requires that or something...? No idea. Any experiences?
Since if it is possible I'd get that instead of the dual boot.2 -
This will never clash:
static createGuid() {
function s4() {
return Math.floor((1 + Math.random()) * 0x10000)
.toString(16)
.substring(1);
}
return s4() + s4() + s4() + s4(); // Example => 'e014026082e6237b'
} -
When your redirect url passed as get parameter to 'secure' the login you pass bade64 envoded string with path, length and (salted) md5 hash ....
why God why you secure a redirect you do 302 to on success1 -
Reading the source of a message queue system I'm planning on extending.
I don't see myself as a rockstar programmer or anything but the construction of arrays from hash tables, sorting those arrays and then a nested for loop to find matches really irks me. Luckily not on the critical message processing path but the stats collection thread. There are mutexes in play though that would probably delay processing a little bit when stats are collected. -
I think today might be the day I'll bring ubuntu onto my big laptop. It had only windows for many years now and I did all my dev work on my smaller laptop that I carry around with me. Since I leave the small one at the office now - i got tired of carrying. Lol. - but want to continue my dev work at home, it might be time.
It's going to be a pain to setup everything though, although I got rid of the part that was making the setup really painful. We'll see.
Maybe I'll rant about the setup in a few hours. Lol. Wish me luck.3 -
On page 19 of the ethereum yellow paper: http://gavwood.com/paper.pdf it defines the address of a wallet as: A(pr) = Β[96...255](KEC(ECDSAPUBKEY(Pr))), which is the right most 160-bits of the Keccak hash of the public key generated by the private key.
If I expose the public key to the network, do I allow people to impersonate me and sign transactions even though they don't have Tr, Ts, or Tw? My understanding is no, that without those values you can't hash the transaction.
Subsequently, this leads me to wonder if the purpose of the address (besides identifying users) to obscure the public key so that the private key is at a less risk of being reversed? Or can the public key of any address be captured?
If the public key of any address can be identified on the network or off network (without actually being the owner of that key), how do you do that? Are there any resources on how to perform this that are computationally easy?1 -
Anyone who is participating in Facebook CTF and wants team members?
Or we can form a team together.8 -
When you can give a technical talk about Data Science but don't know which text editor you use
https://vimeo.com/189519557#t=2891 -
!rant
Anyone here up for developing some Apps with the Fitbit API? Or has any experience in that regard? -
My last promotion was/is my first Software Development job and a significant increase in pay.
I worked for this company for 12 years, quit for 2.5 years, got a job in a different industry in the mean time, and taught myself to write some code.
Due to some personal changes, I ended up coming back to this company.
After being in the engineering team for a year I applied for the corporate software dev gig. They liked I had floor experience and took initiative to teach myself.
I would consider myself entry level and it shows on my resume, so I was surprised they took a chance on me. The boss says I'm doing a great job, so that feels pretty good!1 -
There is a table right under the fan on which I put a hot cup of coffee add suger to it. Now comes the good part.
I tie myself upside down with sealing fan right above table. Holding a spoon in one hand. Start the fan with a stick. Throw the stick. Just after speed is steady put the spoon in cup and let it stear.
Drink this coffe upside down.
It will increase productivity by 10000million%.
Cheers:)2 -
I thought bluetooth headphones are overrated and unecessary until I had to work with VR and had to put on and off the HMD multiple times per hour. Now in-ear bluetooths are a godsend. Will invest into better ones once I have more money.2
-
Been wondering about something and can't figure out if I am a retard or a genius 😂.
If MD5 is so outdated and should not be used to store password hashes (let's say for whatever reason you cannot effectively switch to another algorithm) wouldn't it just be easier and more secure to just re-encrypt the hash again, so just MD5 the MD5 hash... in theory, wouldn't that make the hash virtually uncrackable because instead of trying to brute force actual real words, you now have a hash of essentially random characters which have no relation to the others, and even then, suppose you manage to crack the hash, you will get another hash to crack before getting to the password?5 -
I can confirm that Crystal lang v1.0.0 is not stable really. I seem to have hit a block. For example, I get error messages like this frequently:
`Error: can't use Hash(K, V) as generic type argument yet, use a more specific type`.
I love the "yet" in this message; it gives you some hope!5 -
I wanted to know what is the worst mistake you make on database.
I have actually implements the logic of token access control on database and not on business logic layer.
The database have a login procedure which accept username and password. That login procedure actually hash the password and try to authenticate user.
If it is a correct user , it generate a token. In other to use other procedure on database , you must provide a token. By using that token , the procedure know who is it and what permission is granted to that user.4 -
Fuck you Linux! I thought user password validation would be a piece of cake, like bash one liner. How wrong could I be!
Yeah, it's already ugly to grep hash and salt from /etc/shadow, but I could accept that. But then give me a friggin' tool to generate the hash. And of course the distro I chose has the wrong makepswd, OpenSSL is too old to have the new SHA-512 built in, as it should be a minimal installation I don't want to use perl or python...
And the stupid crypto function that would do me the job is even included in glibc. So it's only one line of C-code to give me all I want, but there is no package that would provide me this dull binary? Instead I will have to compile it myself and then again remove the compiler to keep image small?5 -
!rant
To embrace the TIFO (today I found out)
$git rebase -i <hash>^
You can reorder commits and squash.
I just used it, to amend a commit that was not HEAD with some changes I’ve done later.12 -
Does anybody know how to create a JSON list of all files in a folder with path+filename, md5 hash, file name and size? My client wished that I rework an open source launcher which is reading an HTML file in JSON format5
-
use a mutable obj as hashmap key and the hash code changes when obj got updated. evey text book told u this is a stupid bug and impossible to debug, and I spend a week to prove u can debug it out when in single thread app
-
So I'm working on an assignment for my Computer Science class, and we have to basically compute strings into hash values and then modulo it by 1 million and put it into the hash table. But the value keeps overflowing and turning into negative values, anyone know how I can calculate the key?
(BTW, the hashcode is the same code that is calculated by the .hashCode function in Java)5 -
I really cannot see why there still isn't an API in Java where I can get an hashing algorithm without having to catch a checked exception.
Granted, Bouncy castle is a top library. But of you just have a small application with a single method wanting to hash a few values... It's so nuts and unnecessary.
So what do you do in the catch block? Either throw a checked exception (because without that hash your app won't work), or calculate a replacement. But if it were that easy, I wouldn't have needed a hash on the first place.
I really wonder what the java developers had in mind.
Same with IO exception. I'm beginning to like python more and more.
And, of course, kotlin.5 -
!Rant
If I'm validating a user input form should I use a hash or a encrypted string. I hope to include the user IP, header requested time plus a random number for the string.3 -
I was looking for the largest known mersenne prime and tried doing this. I guess these are language limitations and don’t know what type of computers can give instant answers for such mathematical calculations. Is this complex than bitcoin hash? May be
 4
4 -
Heres a good one.
How do I generate a hash that allows me to compare a re-encoded video against the original to verify they are the same so I don't end up with weird gotchas like this length = that length and this filename = that filename
since the file sizes will be completely different ?8 -
Anyone learn about Bloom filters in school? I was watching a lecture and he mentioned using a Bloom filter with a few hash functions to create a cache you can use to avoid querying a table if there's no match, which is a neat idea. I've never heard of this but I also didn't study CS in school so I'm curious if it's common knowledge.1
-
That moment when somebody types on your Macbook Pro as if he was typing on a typewriter and you feel like saying 'Caveman go back to the stone age' but you can't.2
-
If workspace has Macs connected in local network.
Use ssh to your colleague's mac and make Mac "say weird embarrassing noises" ( if you know what i mean ) -
Call me a pussy, but I find it quite annoying to figure out why one of 30 of the values returned in a hash is wrong in a 600 line Ruby on Rails method.3
-
My first year of a 2 year course our teacher had only taught us 2 theory topics of 6 and hadn't begun to teach us the other 2/3 of the course which was programming. The only reason he took so long was because he wanted everyone to understand the topic before he moved on which meant waiting for the people who shouldn't of been allowed to take the subject because they never paid attention and showed no interest in the subject. But he refused to move on without them.
To drag those 2 topics out more one of them was algorithms. At the time he had sprained his wrist shadow boxing and instead of preparing them before hand to give us some help he would type them out while we sat and watched wasting half the lesson. Then a month or so into our second year he left leaving the other teachers to make up for everything he failed to cover with us. -
My boss told me to search some information about a specific way to program a web wich name i don't remember. It was based on Java and the icon was something like this. Am i fcked out?
 2
2 -
Do you know a hash-function (doesn't need to be cryptographic) that I can implement, without fixed size integer-types?
I already searched for a while, but couldn't find an actual fit.
It's for implementing a hasher, used by a hashmap.5 -
Okay, summary of previous episodes:
1. Worked out a simple syntax to convert markdown into hashes/dictionaries, which is useful for say writing the data in a readable format and then generating a structured representation from it, like say JSON.
2. Added a preprocessor so I could declare and insert variables in the text, and soon enough realized that this was kinda useful for writing code, not just data. I went a little crazy on it and wound up assembling a simple app from this, just a bunch of stuff I wanted to share with friends, all packed into a single output html file so they could just run it from the browser with no setup.
3. I figured I might as well go all the way and turn this into a full-blown RPG for shits and giggles. First step was testing if I could do some simple sprites with SVG to see how far I could realistically get in the graphics department.
Now, the big problem with the last point is that using Inkscape to convert spritesheets into SVG was bit of a trouble, mostly because I am not very good at Inkscape. But I'm just doing very basic pixel art, so my thought process was maybe I can do this myself -- have a small tool handle the spritesheet to SVG conversion. And well... I did just that ;>
# pixel-to-svg:
- Input path-to-image, size.
- grep non-transparent pixels.
- Group pixels into 'islands' when they are horizontally or vertically adjacent.
- For each island, convert each pixel into *four* points because blocks:
· * (px*2+0, py*2+0), (px*2+1, py*2+0), (px*2+1, py*2+1), (px*2+0, py*2+1).
· * Each of the four generated coordinates gets saved to a hash unique to that island, where {coord: index}.
- Now walk that quad-ified output, and for each point, determine whether they are a corner. This is very wordy, but actually quite simple:
· * If a point immediately above (px, py-1) or below (px, py+1) this point doesn't exist in the coord hash, then you know it's either top or bottom side. You can determine whether they are right (px+1, py) or left (px-1, py) the same way.
· * A point is an outer corner if (top || bottom) && (left || right).
· * A point is an inner corner if ! ((top || bottom) && (left || right)) AND there is at least _one_ empty diagonal (TR, TL, BR, BL) adjacent to it, eg: (px+1, py+1) is not in the coord hash.
· * We take note of which direction (top, left, bottom, right) every outer or inner corner has, and every other point is discarded. Yes.
Finally, we connect the corners of each island to make a series of SVG paths:
- Get starting point, remember starting position. Keep the point in the coord hash, we want to check against it.
- Convert (px, py) back to non-quadriplied coords. Remember how I made four points from each pixel?
. * {px = px*0.5 + (px & 1)*0.5} will transform the coords from quadriple back to actual pixel space.
· * We do this for all coordinates we emit to the SVG path.
- We're on the first point of a shape, so emit "M${px} ${py}" or "m${dx} ${dy}", depending on whether absolute or relative positioning would take up less characters.
· * Delta (dx, dy) is just (last_position - point).
- We walk from the starting point towards the next:
· * Each corner has only two possible directions because corners.
· * We always begin with clockwise direction, and invert it if it would make us go backwards.
· * Iter in given direction until you find next corner.
· * Get new point, delete it from the coord hash, then get delta (last_position - new_point).
· * Emit "v${dy}" OR "h${dx}", depending on which direction we moved in.
· * Repeat until we arrive back at the start, at which point you just emit 'Z' to close the shape.
· * If there are still points in the coord hash, then just get the first one and keep going in the __inverse__ direction, else stop.
I'm simplifying here and there for the sake of """brevity""", but hopefully you get the picture: this fills out the `d` (for 'definition') of a <path/>. Been testing this a bit, likely I've missed certain edge cases but it seems to be working alright for the spritesheets I had, so me is happiee.
Elephant: this only works with bitmaps -- my entire idea was just adding cute little icons and calling it a day, but now... well, now I'm actually invested. I can _probably_ support full color, I'm just not sure what would be a somewhat efficient way to go about it... but it *is* possible.
Anyway, here's first output for retoori maybe uuuh mystery svg tag what could it be?? <svg viewBox="0 0 8 8" height="16" width="16"><path d="M0 2h1v-1h2v1h2v-1h2v1h1v3h-1v1h-1v1h-1v1h-2v-1h-1v-1h-1v-1h-1Z" fill="#B01030" stroke="#101010" stroke-width="0.2" paint-order="stroke"/></svg>3 -
Did 2 leetcode today (technically 1)
https://leetcode.com/problems/...
idea:
* Palindrome means cut it half, rearrange the other half, will equal each other.
* Using javascript new map() to build a hash map
* Loop the hash, add up quotient*2, add up remainder.
* if remainder > 1, then return_sum+1
https://leetcode.com/problems/...
seen a few times in interview.
* do the big one first, i.e. if(n % (3*5) === 0)
* then n%3 === 0
* then n%5 === 01 -
We have a CRM running on an EC2 instance. We need to clone it so we can test a tool on the replica. We tried cloning it directly, sharing the AMI and creating a new instance through it but it always redirects changes to the original production server. The database is on the instance only and static files are stored in S3. Can someone guide me or share some resourses on how to do this.6
-
Need a bit of help and I think the simple answer would've been to RTFM more carefully but yea.... Kinda late now.
I'm looking for the installers for Chromium 74.0.3707.0. I should've written form the download link but I forgot you can't just look it up with this version number.
Hence my problem. I went on the site and somehow need to lookup a revision version like 54321. But I can't find the mapping for it... Closest I got it's going the commit hash but then what...6 -
To open any SO question and it to have a working answer because it would make things so much easier.
-
1 - To be able to use string for my class homework.
2 - A one-stop-shop that explains everything I've ever wanted to know when it comes to programming.
3 - A job as a software developer. -
For a few days I failed to see that I need to add one string escape instead of re-writing the whole S3 file upload logic to hash file names using md5. :( Context: We were not able to retrieve some files with international letters (like German, Chinese, etc) in their names because of weirdly escaped signed URL to S3.
-
Hello anyone with an idea how I can unsubscribe my email from many services at once? It seems Google doesn't have that feature that lets you see all your email subscriptions. I'm receiving a lot of junk and spam mails from some subscriptions I no longer want.
Unroll.me would have been great but it's not available in my country.15 -
Anyone knows how to hash the OAuth 1.0 signature with RSA-SHA1 using PHP? Using only the value to be hashed and a key?1
-
hey devos, I got a question to ask ya'll. I have an interview tomorrow with an MNC.
I was hovering through some leetcode problems when I came across a hard question that is forcing me to use a hashmap with the key of the user-defined type. I made up my mind to make use of C++ for the coding interview. Now, the problem is C++ asks me to implement a hash function.
If in case, I'm asked a similar question like this in the interview, which of these two options will you suggest:
a) implement your own hash function
b) use pointers as key2 -
*builds workspace*
rosjava: error
.....
*build workspace 5 min later*
successfully build
?! Why is rosjava like this I didn't change anything!!! wtf can it please stop <.< -
I invested in Hash Fund mining after a friend's referral, which increased my mining rate. I staked more with a higher package, seeing great returns initially. However, the website crashed when I tried to withdraw funds, revealing it was a fake company. I felt lost until I found Crypto Pandemic Hunter, who helped trace and recover much of my stolen money. I recommend their services to other victims of cybercrime.
 3
3