Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "security bug"
-
So, someone submitted a 'bug' to Mozilla.
As some of you may know, in the next year, the new mass surveillance law in the Netherlands is going into effect.
Another fun fact is that the dutch security agencies/government have their own CA (Certificate Authority) for SSL/TLS certificates.
The new law says that the AIVD (dutch NSA/GCHQ equivilant) is allowed to hack into systems through obtained certificates and also that they're allowed to INTERCEPT TRAFFIC THROUGH OBTAINED PRIVATE SSL/TLS KEYS.
So someone actually had the fucking balls to submit a fucking issue to Mozilla saying that the Dutch State certs shouldn't be accepted anymore when the new mass surveillance law gets into place.
This person deservers a fucking medal if you ask me.68 -
Hey everyone,
First off, a Merry Christmas to everyone who celebrates, happy holidays to everyone, and happy almost-new-year!
Tim and I are very happy with the year devRant has had, and thinking back, there are a lot of 2017 highlights to recap. Here are just a few of the ones that come to mind (this list is not exhaustive and I'm definitley forgetting stuff!):
- We introduced the devRant supporter program (devRant++)! (https://devrant.com/rants/638594/...). Thank you so much to everyone who has embraced devRant++! This program has helped us significantly and it's made it possible for us to mantain our current infrustructure and not have to cut down on servers/sacrifice app performance and stability.
- We added avatar pets (https://devrant.com/rants/455860/...)
- We finally got the domain devrant.com thanks to @wiardvanrij (https://devrant.com/rants/938509/...)
- The first international devRant meetup (Dutch) with organized by @linuxxx and was a huge success (https://devrant.com/rants/937319/... + https://devrant.com/rants/935713/...)
- We reached 50,000 downloads on Android (https://devrant.com/rants/728421/...)
- We introduced notif tabs (https://devrant.com/rants/1037456/...), which make it easy to filter your in-app notifications by type
- @AlexDeLarge became the first devRant user to hit 50,000++ (https://devrant.com/rants/885432/...), and @linuxxx became the first to hit 75,000++
- We made an April Fools joke that got a lot of people mad at us and hopefully got some laughs too (https://devrant.com/rants/506740/...)
- We launched devDucks!! (https://devducks.com)
- We got rid of the drawer menu in our mobile apps and switched to a tab layout
- We added the ability to subscribe to any user's rants (https://devrant.com/rants/538170/...)
- Introduced the post type selector (https://devrant.com/rants/850978/...) (which will be used for filtering - more details below)
- Started a bug/feature tracker GitHub repo (https://github.com/devRant/devRant)
- We did our first ever live stream (https://youtube.com/watch/...)
- Added an awesome all-black theme (devRant++) (https://devrant.com/rants/850978/...)
- We created an "active discussions" screen within the app so you can easily find rants with booming discussions!
- Thanks to the suggestion of many community members, we added "scroll to bottom" functionality to rants with long comment threads to make those rants more usable
- We improved our app stability and set our personal record for uptime, and we also cut request times in half with some database cluster upgrades
- Awesome new community projects: https://devrant.com/projects (more will be added to the list soon, sorry for the delay!)
- A new landing page for web (https://devrant.com), that was the first phase of our web overhaul coming soon (see below)
Even after all of this stuff, Tim and I both know there is a ton of work to do going forward and we want to continue to make devRant as good as it can be. We rely on your feedback to make that happen and we encourage everyone to keep submitting and discussing ideas in the bug/feature tracker (https://github.com/devRant/devRant).
We only have a little bit of the roadmap right now, but here's some things 2018 will bring:
- A brand new devRant web app: we've heard the feedback loud and clear. This is our top priority right now, and we're happy to say the completely redesigned/overhauled devRant web experience is almost done and will be released in early 2018. We think everyone will really like it.
- Functionality to filter rants by type: this feature was always planned since we introduced notif types, and it will soon be implemented. The notif type filter will allow you to select the types of rants you want to see for any of the sorting methods.
- App stability and usability: we want to dedicate a little time to making sure we don't forget to fix some long-standing bugs with our iOS/Android apps. This includes UI issues, push notification problems on Android, any many other small but annoying problems. We know the stability and usability of devRant is very important to the community, so it's important for us to give it the attention it deserves.
- Improved profiles/avatars: we can't reveal a ton here yet, but we've got some pretty cool ideas that we think everyone will enjoy.
- Private messaging: we think a PM system can add a lot to the app and make it much more intuitive to reach out to people privately. However, Tim and I believe in only launching carefully developed features, so rest assured that a lot of thought will be going into the system to maximize privacy, provide settings that make it easy to turn off, and provide security features that make it very difficult for abuse to take place. We're also open to any ideas here, so just let us know what you might be thinking.
There will be many more additions, but those are just a few we have in mind right now.
We've had a great year, and we really can't thank every member of the devRant community enough. We've always gotten amazingly positive feedback from the community, and we really do appreciate it. One of the most awesome things is when some compliments the kindness of the devRant community itself, which we hear a lot. It really is such a welcoming community and we love seeing devs of all kind and geographic locations welcomed with open arms.
2018 will be an important year for devRant as we continue to grow and we will need to continue the momentum. We think the ideas we have right now and the ones that will come from community feedback going forward will allow us to make this a big year and continue to improve the devRant community.
Thanks everyone, and thanks for your amazing contributions to the devRant community!
Looking forward to 2018,
- David and Tim 45
45 -
As a long-time iPhone user, I am really sorry to say it but I think Apple has completed their transition to being a company that is incompetent when it comes to software development and software development processes.
I’ve grown tired of hearing some developers tell me about Apple’s scale and how software development is hard and how bugs should be expected. All of those are true, but like most rules of law, incompetence and gross negligence trumps all of that.
I’m writing this because of the telugu “bug”/massive, massive security issue in iOS 11.2.5. I personally think it’s one of the worst security issues in the history of modern devices/software in terms of its ease of exploitation, vast reach, and devastating impact if used strategically. But, as a software developer, I would have been able to see past all of that, but Apple has shown their true incompetence on this issue and this isn’t about a bug.
It’s about a company that has a catastrophic bug in their desktop and mobile platforms and haven’t been able to, or cared to, patch it in the 3 or so days it’s been known about. It’s about a company, who as of a view days ago, hasn’t followed the basic software development process of removing an update (11.2.5) that was found to be flawed and broken. Bugs happen, but that kind of incompetence is cultural and isn’t a mistake and it certainly isn’t something that people should try to justify.
This has also shown Apple’s gross incompetence in terms of software QA. This isn’t the first time a non-standard character has crashed iOS. Why would a competent software company implement a step in their QA, after the previous incident(s), to specifically test for issues like this? While Android has its issues too and I know some here don’t like Google, no one can deny that Google at least has a solid and far superior QA process compared to Apple.
Why am I writing this? Because I’m fed up. Apple has completely lost its way. devRant was inaccessible to iOS users a couple of times because of this bug and I know many, many other apps and websites that feature user-generated content experienced the same thing. It’s catastrophic. Many times we get sidetracked and really into security issues, like meltdown/spectre that are exponentially harder to take advantage of than this one. This issue can be exploited by a 3 year old. I bet no one can produce a case where a security issue was this exploitable yet this ignored on a whole.
Alas, here we are, days later, and the incompetent leadership at Apple has still not patched one of the worst security bugs the world has ever seen. 81
81 -
Alright fuck it, let's release this fucker!
https://lynkz.me is the main domain. The interface is *usable* and nothing more than that. I'll invest more time in that soon but for now, hey, it works.
Api is located at https://api.lynkz.me.
Documentation for this (literally some echoes to the screen but it contains the needed information for now) is at that api url.
Found a bug or a security vulnerability? Please let me know!
Yeah I use mariadb but sql injection is luckily not possible due to quite some sanitization ;)
WARNING: if you make a shortened url and forget the delete key, you won't be able to delete it.
Let's see how this goes 😅111 -
My little brother (still in school , learning security and pen testing): i found a bug in a website , it returns an xml file instead of the web page , i reported it to them and i think i'm gonna get rewarded like 2k $ for it .
Me : cool ! Show me .
Him : shows me his phone ...
Me : wait , gotta rant this . 9
9 -
1. Humans perform best if they have ownership over a slice of responsibility. Find roles and positions within the company which give you energy. Being "just another intern/junior" is unacceptable, you must strive to be head of photography, chief of data security, master of updating packages, whatever makes you want to jump out of bed in the morning. Management has only one metric to perform on, only one right to exist: Coaching people to find their optimal role. Productivity and growth will inevitably emerge if you do what you love. — Boss at current company
2. Don't jump to the newest technology just because it's popular or shiny. Don't cling to old technology just because it's proven. — Team lead at the Arianespace contractor I worked for.
4. "Developing a product you wouldn't like to use as an end user, is unsustainable. You can try to convince yourself and others that cancer is great for weight loss, but you're still gonna die if you don't try to cure it. You can keep ignoring the disease here to fill your wallet for a while, but it's worse for your health than smoking a pack of cigs a day." — my team supervisor, heavy smoker, and possibly the only sane person at Microsoft.
5. Never trust documentation, never trust comments, never trust untested code, never trust tests, never trust commit messages, never trust bug reports, never trust numbered lists or graphs without clearly labeled axes. You never know what is missing from them, what was redacted away. — Coworker at current company.8 -
Lads, I will be real with you: some of you show absolute contempt to the actual academic study of the field.
In a previous rant from another ranter it was thrown up and about the question for finding a binary search implementation.
Asking a senior in the field of software engineering and computer science such question should be a simple answer, specifically depending on the type of job application in question. Specially if you are applying as a SENIOR.
I am tired of this strange self-learner mentality that those that have a degree or a deep grasp of these fundamental concepts are somewhat beneath you because you learned to push out a website using the New Boston tutorials on youtube. FOR every field THAT MATTERS a license or degree is hold in high regards.
"Oh I didn't go to school, shit is for suckers, but I learned how to chop people up and kinda fix it from some tutorials on youtube" <---- try that for a medical position.
"Nah it's cool, I can fix your breaks, learned how to do it by reading blogs on the internet" <--- maintenance shop
"Sure can write the controller processing code for that boing plane! Just got done with a low level tutorial on some websites! what can go wrong!"
(The same goes for military devices which in the past have actually killed mfkers in the U.S)
Just recently a series of people were sent to jail because of a bug in software. Industries NEED to make sure a mfker has aaaall of the bells and whistles needed for running and creating software.
During my masters degree, it fucking FASCINATED me how many mfkers were absolutely completely NEW to the concept of testing code, some of them with years in the field.
And I know what you are thinking "fuck you, I am fucking awesome" <--- I AM SURE YOU BLOODY WELL ARE but we live in a planet with billions of people and millions of them have fallen through the cracks into software related positions as well as complete degrees, the degree at LEAST has a SPECTACULAR barrier of entry during that intro to Algos and DS that a lot of bitches fail.
NOTE: NOT knowing the ABSTRACTIONS over the tools that we use WILL eventually bite you in the ASS because you do not fucking KNOW how these are implemented internally.
Why do you think compiler designers, kernel designers and embedded developers make the BANK they made? Because they don't know memory efficient ways of deploying a product with minimal overhead without proper data structures and algorithmic thinking? NOT EVERYTHING IS SHITTY WEB DEVELOPMENT
SO, if a mfker talks shit about a so called SENIOR for not knowing that the first mamase mamasa bloody simple as shit algorithm THROWN at you in the first 10 pages of an algo and ds book, then y'all should be offended at the mkfer saying that he is a SENIOR, because these SENIORS are the same mfkers that try to at one point in time teach other people.
These SENIORS are the same mfkers that left me a FUCKING HORRIBLE AND USELESS MESS OF SPAGHETTI CODE
Specially to most PHP developers (my main area) y'all would have been well motherfucking served in learning how not to forLoop the fuck out of tables consisting of over 50k interconnected records, WHAT THE FUCK
"LeaRniNG tHiS iS noT neeDed!!" yes IT fucking IS
being able to code a binary search (in that example) from scratch lets me know fucking EXACTLY how well your thought process is when facing a hard challenge, knowing the basemotherfucking case of a LinkedList will damn well make you understand WHAT is going on with your abstractions as to not fucking violate memory constraints, this-shit-is-important.
So, will your royal majesties at least for the sake of completeness look into a couple of very well made youtube or book tutorials concerning the topic?
You can code an entire website, fine as shit, you will get tested by my ass in terms of security and best practices, run these questions now, and it very motherfucking well be as efficient as I think it should be(I HIRE, NOT YOU, or your fucking blog posts concerning how much MY degree was not needed, oh and btw, MY degree is what made sure I was able to make SUCH decissions)
This will make a loooooooot of mfkers salty, don't worry, I will still accept you as an interview candidate, but if you think you are good enough without a degree, or better than me (has happened, told that to my face by a candidate) then get fucking ready to receive a question concerning: BASIC FUCKING COMPUTER SCIENCE TOPICS
* gays away into the night52 -
You might know by now that India demonetized old higher value notes and brought in new one. The new ones easily tear off easily and generally feel cheaper and less reliable than pervious ones.
One interesting thing people discovered is that rubbing it with cloth makes the ink transfer to the cloth. Sign of crap printing. Here's government response:
The new currency notes have a security feature called 'intaglio printing'. A genuine currency note can be tested by rubbing it with a cloth; this creates a turbo-electric effect, transferring the ink colour onto the cloth
TL;DR: its not a bug, it's a feature7 -
IT department created a risk assessment system and asked us to fill out the form.
I found that the form is vulnerable to XSS and possibly SQL injection so I told them and their response was:
"Oh, shit. Please don't tell anyone!"
Of course, it never get fixed :/6 -
So a fucking friend of mine makes me meet this fella who is a big shot according to his LinkedIn and please note has too much experience with Web Apps and Python
Me being naive actually trusted that and I meet him.
Fella: So what do you do?
Me: I am into Cyber Security nothing much I just do bug hunting for now
Fella: You know python will help you right?
Me: Sorry?
Fella: You see you have to be a python programmer for anything you want to do in CS
Me: Me yeah I kinda know python actually I am more into Ruby from start so ( Around this time I kinda sensed that he is a fake tech guy he is a corporate asshole)
Fella: show me any of your work
Me: (So to show him one of the thing I was working on I open GitHub desktop app) Me explaining blah blah blah
*Fella is in shock*
So at this point I was thinking probably he is impressed and that's why the shock right?
No a big fucking no
Apparently he never heard about GitHub or git and got blown away by the interface.
And the friend who made me meet that guy is not my fucking friend anymore that prick can die for ruining my day18 -
Designer: Need to file a bug, I'm not getting an option to login with FaceID
Me: Oh weird bug. Is it setup on the phone you are testing with?
Designer: yes, use it in all other apps
Me: Did you get an error during onboarding on the FaceID screen?
Designer: nope no error
Me: ..... hhhmm, can you show me your settings?
Me: ... eh, says you have FaceID disabled for this app ... did you click "No" to FaceID during onboarding?
Designer: Yes, to test edge cases
Me: ................ ok ........ if you setup the app and told it to not allow FaceID to login ......... you won't get the ability to use FaceID to login .......... like .... by design .... on purpose ...... cause .... you told it to do that
Designer: No no, it needs to have a setting on the login screen to allow me to turn that back on incase I forget my passcode
Me: the fuck it does. Yeah we can't have anything on the login page that says, without authorization, change my settings
*Deep breath*
Me: Remember we had this conversation previously, where you didn't want the user to create a passcode during onboarding as it was too much friction, and wanted to do FaceID only. With your backup plan being to allow the user to create a NEW passcode on the login screen if FaceID failed .... remember that discussion we had about security? ... and how its important? ... and that we like having any? Ok so its the same reason as that, just with a different setting this time
Designer: ... hhmm i'm not sure I like this
Me: ... tough luck then, not happening
Me: oh and btw, remember we had that other talk about reproduction steps for bugs? Like when the app crashed and you told me it was because its in light mode, and nothing else at all? So disabling FaceID, is very relevant info to the problem of "I can't login with FaceID", please tell me these things first11 -
My boss is still forcing us to support IE11. Recently, we started having even more bugs with one of our vendors on IE. We filed bug reports with the vendor to fix it, and they came back with "no. Why would we fix anything for IE11? Not even Microsoft is fixing anything for IE11." Boss's answer: well, let's make a separate component for IE11. Probably using flash and/or silverlight. We asked about redirecting IE traffic to Edge, he said that's "the nuclear option." So, doing the thing that Microsoft suggests, that involves not much work at all is "the nuclear option"; ignoring industry standards and recommendations, introducing well known security vulnerabilities, losing money, and trying to circumvent the vendor that serves out our major product, however, is totally reasonable. Our IE traffic is less than 3% of our users at this point.22
-
Not exactly a security bug, but there was a company that made a Django app for some internal work and later open sourced it. I was browsing through the code and I saw that the config file had an IP address and a hashed password for the database credentials
When I tried to use them, I was able to login directly to their read replica RDBMS, I had access to all their customer data (including phones & home addresses)
Being the saint I am, I informed them of the ignorance made by their developer and was presented with some cool swag.5 -
Alright, the blog seems to be running again and its not breaking yet which is a good sign :P.
Although nothing has changed on the front end yet, the backend has been partly rewritten to be more efficient and of course, post sorting based on posting date!
I'm aware of most of the front end issues so no need to tell me all of them again, I'll look at that tomorrow as I need sleep right now :(
If you'd find any bugs/security issues, please, don't exploit them but report them instead! I take security very seriously and will try to patch any security bug as soon as I can :)13 -
The security blog is up again, I fixed the bug.
Just wondering, why did it work in the first place? I simply required a composer autoloader twice but I've been doing that from the beginning and it didn't play up until last night...
I guess it shall remain a mistery 😞82 -
Finally finished the blog post and (nearly) the last bugs (few remaining, still gotta think about how to solve them) are fixed.
The new blog post is online! I've taken a look at the Telegram messaging app and basically burned it into the ground. (Provided sources as well)
Next to that, a new domain name! As this blog is about online security AND privacy, I decided to change the domain name. The new one:
https://much-security-such-privacy.info/...
Dark theme can be enabled but will only work on one domain, you have to enable it on the other one as well to get a dark theme there. It stores the value in a cookie so it will remain when you reload the page and don't remove the cookies.
The RSS feed generator has a bug right now which makes that the page doesn't get updated, will work on that one tomorrow.
Thanks!
Last but not least, you can email me suggestions and so on at linuxxx@much-security.nl :)34 -
I think the hardest thing about being a programmer in college with a security emphasis is when I approach a business for a penetration test or for a vulnerability analysis (your pick) is that they almost always say, "you are pretty young don't you think?"
Ummmm not sure what that has to do with it. If it would make you feel better I have claimed bug bounties from an antivirus company, a bank, several local businesses in my area and I do this for work at my 9-5.
And this week I got this, "I think I would like someone older so we can define the goals better."
Oh so rules of engagement, yeah of course I understand that and that's something we would discuss and draw up a contract for...
"Well we really need someone more skilled."
---- End of story ----
I don't understand, you haven't asked about certifications or schooling and you glanced at my resume for exactly 5 seconds what the hell do you want? Me to double my age over night?7 -
While writing up this quarter's performance review, I re-read last quarter's goals, and found one my boss edited and added a minimum to: "Release more features that customers want and enjoy using, prioritized by product; minimum 4 product feature/bug tickets this quarter."
... they then proceeded to give me, not four+ product tickets, but: three security tickets (two of which are big projects), a frontend ticket that should have been assigned to the designer, and a slow query performance ticket -- on top of my existing security tickets from Q3.
How the fuck was I supposed to meet this requirement if I wasn't given any product tickets? What, finish the monster tickets in a week instead of a month or more each and beg for new product tickets from the product manager who refuses to even talk to me?
Fuck these people, seriously.8 -
Part of a product I used to work on contained a one time password generator that randomly strung together a few words from a word list.
Nothing wrong with the security, but this word list hadn't been filtered, so we did have a "bug report" from a customer who had a one time password that contained a questionable phrase:
"fucking pork Muslim"
...Call me a terrible person, but I never did get around to fixing that...3 -
Found a bug, reported it to the maintainer.
He then tells me to ignore it since no one noticed it (besides me).
I tell him i can't do it since it's just wrong and he can simply fix it.
Turns out he's just lazy as hell and got mad at me, so i go and fix it.
Next day boss is mad at me because i'm wasting time on tasks that it's not of my concern even knowing all my tasks were completed.
Not even a "thank you by the way".
What did i miss here?4 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
- popunder background bitcoin miners did become a thing
- keybase android beta uploaded your privatekey to google servers "accidentally"
- you can spoof email headers via encoded chars, because most apps literally just render them apparently
- imgur leaked 1.7 million user accounts, protected by sha-256 "The company made sure to note that the compromised account information included only email addresses and passwords" - yeah "only", ofcourse imgur, ofcourse.
I guess the rant I did on Krahk etc. just roughly a month ago, can always be topped by something else.
sources:
https://www.mailsploit.com/index
https://bleepingcomputer.com/news/...
https://blog.malwarebytes.com/cyber...
https://helpnetsecurity.com/2017/... undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6
undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6 -
https://blogs.adobe.com/conversatio...
Adobe Flash Player will officially die in 2020.
No more updates. If there'is a security bug, it remain.30 -
OK< been a long time user of Unity.
Tried the latest update as I and others were enthusiastic about creating a joint project of gamers and developers.
As I was building up a started website and we were getting things with Unity ready...BOOM,. They Fuck up the installs.
Not just a minor thing here or there but not finding its own Fucking file locations where it installs shit. You try and say, Hey Unity you fucking twat, install here in this folder.
Boom again, it installs part of it there, and then continues installing shit everywhere else it wants to. Then the assholes at Unity give this Bullshit claim "the bug has been fixed."
Just reinstall.
Fuck you, its never that simple, You have to delete all sorts of fucking files to make sure conflicts from a previous corruption isn't just loaded on top of so it does not fuck up later.
So we did all that from programs, program data, program(x86), AppData Local, Local Low, and Roaming.
For added measure we manually removed all the crap from the registry folders (that was a pain but necessary), and then ran a cleaner to make sure all the left over shit was gone.
Thinking, OK you shit tech MoFo's we are clean and here we go.
HOLY SHIT BALLS, Its fucking worse with the LTS version it recommends and Slow as Fuck with their most recent version which is like 2020 itself, and insane piece of fucking bloated garbage and slower than a brick hard shit without fruit.
So we were going to all go post on the forums, and complain the fix section isn't fixed for shit.
Fuck us running backwards naked through a field of razor grass. Its so overloaded with complaints that they shut down further posts.
What makes this shit worse is we cannot even get the previous fucking versions of the editor before all this to work where our only option is without using the fucking Hub demand is just install 2018.
great if we started coding and testing in that. We cannot get shit where we were at back on track because you cannot fucking backward load an exported saved asset file.
Unity's suggestion? Start over.
Our Suggestion? Stop fucking smoking or using whatever fucking drug you assholes are on, you fucking disabled the gear options so we can resolve shit ourselves, and admit you did that shit and other sneaky piece of shit back stabby, security vulnerable data leak bullshit things to your end users.
Listen to your fucking experienced and long time users and get rid of the Fucking backward stepped hub piece of shit everyone with more brains than whatever piss ant pieces of shit praised that the rest of us have hated from day fucking one!
And while fixing this shit like it should be fucking fixed if you shit head bastards want to continue to exist as a fucking company, overhaul the fucking website or get the fuck out of business with now completely worthless SHIT.
Phew:
Suffice it to say....
We are now considering dealing with the learning curve and post pone our project going with unreal just because of these all around complete fuck ups that herald back to shit games of versions 3.0 and earlier. 6
6 -
Anyone hear about the emergency patch that Microsoft just released? Its a RCE vulnerability CVE-2017-11937 which ironically targets all of Microsoft's security products.
Basically when Windows defender scans a specially crafted file the attacker can run code as the LocalSystem. Nice one Microsoft!1 -
Two years ago, I developed an security app for Android as a school project. I didn't like teamwork at school (you know, you do all the work and everyone else is getting the same grade you receive, specially if you are the nerd of the class), actually I hated it, so I made it alone.
Its name was "Alex" and was a simple "panic button". You can configure two emergency emails and phone numbers (contacts only, not police) and, if you're in danger, you just have to press the button and the app is gonna send two messages/emails to your contacts: the first one, to tell where are you (GPS, only the name of the place) and that you're in problems. The second one with an audio/photo file of the situation.
Sounds like a great app, and I tested it few times. The reason I didn't continue with this is that I got my first job and I had not time, and that, tree or four months later, the government (of the city) launched a similar app. Less sophisticated, but I think it's still useful: "No estoy sola"(I'm not alone). I haven't tested it cause I don't trust on the authorities, I'd preffer to send my location to a friend through messenger app instead.
I don't know if I should re-work this app (I didn't released it, I just have the beta) or work on something else. I'm afraid that, if I release it, someone could die or get kidnapped because of a bug or something going wrong with the app :c What do you think?5 -
Thank God the week 233 rants are over - was getting sick of elitist internet losers.
The worst security bug I saw was when I first started work as a dev in Angular almost year ago. Despite the code being a couple of years old, the links to the data on firebase had 0 rules concerning user access, all data basically publicly available, the API keys were uploaded on GitHub, and even the auth guard didn't work. A proper mess that still gives me the night spooks to this day.3 -
What a new years start..
"Kernel memory leaking Intel processor design flaw forces Linux, Windows redesign"
"Crucially, these updates to both Linux and Windows will incur a performance hit on Intel products. The effects are still being benchmarked, however we're looking at a ballpark figure of five to 30 per cent slow down"
"It is understood the bug is present in modern Intel processors produced in the past decade. It allows normal user programs – from database applications to JavaScript in web browsers – to discern to some extent the layout or contents of protected kernel memory areas."
"The fix is to separate the kernel's memory completely from user processes using what's called Kernel Page Table Isolation, or KPTI. At one point, Forcefully Unmap Complete Kernel With Interrupt Trampolines, aka FUCKWIT, was mulled by the Linux kernel team, giving you an idea of how annoying this has been for the developers."
>How can this security hole be abused?
"At worst, the hole could be abused by programs and logged-in users to read the contents of the kernel's memory."
https://theregister.co.uk/2018/01/... 22
22 -
Reported a security bug in Chrome two years ago, got the response now -
Moral - even google products are fucked up. 5
5 -
I don't know if I'm being pranked or not, but I work with my boss and he has the strangest way of doing things.
- Only use PHP
- Keep error_reporting off (for development), Site cannot function if they are on.
- 20,000 lines of functions in a single file, 50% of which was unused, mostly repeated code that could have been reduced massively.
- Zero Code Comments
- Inconsistent variable names, function names, file names -- I was literally project searching for months to find things.
- There is nothing close to a normalized SQL Database, column ID names can't even stay consistent.
- Every query is done with a mysqli wrapper to use legacy mysql functions.
- Most used function is to escape stirngs
- Type-hinting is too strict for the code.
- Most files packed with Inline CSS, JavaScript and PHP - we don't want to use an external file otherwise we'd have to open two of them.
- Do not use a package manger composer because he doesn't have it installed.. Though I told him it's easy on any platform and I'll explain it.
- He downloads a few composer packages he likes and drag/drop them into random folder.
- Uses $_GET to set values and pass them around like a message contianer.
- One file is 6000 lines which is a giant if statement with somewhere close to 7 levels deep of recursion.
- Never removes his old code that bloats things.
- Has functions from a decade ago he would like to save to use some day. Just regular, plain old, PHP functions.
- Always wants to build things from scratch, and re-using a lot of his code that is honestly a weird way of doing almost everything.
- Using CodeIntel, Mess Detectors, Error Detectors is not good or useful.
- Would not deploy to production through any tool I setup, though I was told to. Instead he wrote bash scripts that still make me nervous.
- Often tells me to make something modern/great (reinventing a wheel) and then ends up saying, "I think I'd do it this way... Referes to his code 5 years ago".
- Using isset() breaks things.
- Tens of thousands of undefined variables exist because arrays are creates like $this[][][] = 5;
- Understanding the naming of functions required me to write several documents.
- I had to use #region tags to find places in the code quicker since a router was about 2000 lines of if else statements.
- I used Todo Bookmark extensions in VSCode to mark and flag everything that's a bug.
- Gets upset if I add anything to .gitignore; I tried to tell him it ignores files we don't want, he is though it deleted them for a while.
- He would rather explain every line of code in a mammoth project that follows no human known patterns, includes files that overwrite global scope variables and wants has me do the documentation.
- Open to ideas but when I bring them up such as - This is what most standards suggest, here's a literal example of exactly what you want but easier - He will passively decide against it and end up working on tedious things not very necessary for project release dates.
- On another project I try to write code but he wants to go over every single nook and cranny and stay on the phone the entire day as I watch his screen and Im trying to code.
I would like us all to do well but I do not consider him a programmer but a script-whippersnapper. I find myself trying to to debate the most basic of things (you shouldnt 777 every file), and I need all kinds of evidence before he will do something about it. We need "security" and all kinds of buzz words but I'm scared to death of this code. After several months its a nice place to work but I am convinced I'm being pranked or my boss has very little idea what he's doing. I've worked in a lot of disasters but nothing like this.
We are building an API, I could use something open source to help with anything from validations, routing, ACL but he ends up reinventing the wheel. I have never worked so slow, hindered and baffled at how I am supposed to build anything - nothing is stable, tested, and rarely logical. I suggested many things but he would rather have small talk and reason his way into using things he made.
I could fhave this project 50% done i a Node API i two weeks, pretty fast in a PHP or Python one, but we for reasons I have no idea would rather go slow and literally "build a framework". Two knuckleheads are going to build a PHP REST framework and compete with tested, tried and true open source tools by tens of millions?
I just wanted to rant because this drives me crazy. I have so much stress my neck and shoulder seems like a nerve is pinched. I don't understand what any of this means. I've never met someone who was wrong about so many things but believed they were right. I just don't know what to say so often on call I just say, 'uhh..'. It's like nothing anyone or any authority says matters, I don't know why he asks anything he's going to do things one way, a hard way, only that he can decipher. He's an owner, he's not worried about job security.12 -
Dear software developers, I realise, as a dev myself, the need for auto updates for security and stability, but, outside of only a few niche circumstances, are they really necessary on a fucking *daily* or even *hourly* basis? Congratulations for fixing that minor specific non-crucial bug that 99% of users have never encountered, and I'm happy you're maintaining your code so diligently, but couldn't it wait until next Sunday? By that time I'm sure you could combine the update with all the other minor fixes you'll come up with the interim.
And I wouldn't have to click my way through this shit every time I open the app4 -
This is the Result Declaration form of our university, It's all good but there is one thing (bug) in this form, you only need to fill the Recaptcha once and you can that same Recaptcha to extract as many results as you want. Though not a Security issue, we can extract results of many students as roll numbers are sequential, we just need a bot to fill roll number and click the button. The only use would be to conduct surveys on results, but, a bug is a bug.
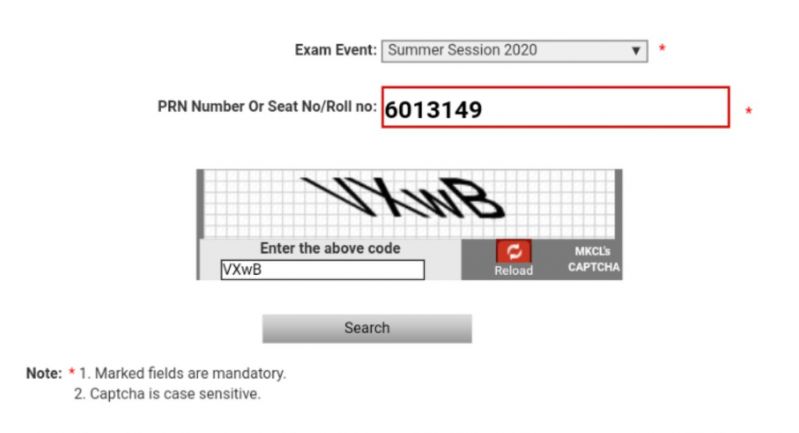 5
5 -
why people around me act like dump. i have recently worked with this site, which is written in php.
customer: (yelling) my website is hacked, fix it immediately
me : ok sir, we will restore your site immediately
after finishing talk with customer. i have checked website, there is no sign of website being hacked. i have checked server logs and website for security breach, there is no sign.
me: your website is not hacked, sir. can you please tell me where you have seen hacked page.
customer: look at those pages
after seen that page i facepalmed myself. it's a bug, person who created that page just splitted string without using any multibyte function, so page is showing with corrupted characters. i fixed it and problem solved. i have told about that bug, to the person who created that page.
me: hey you have used this function which is not able to handle multibyte characters, you should use multibyte character functions for that one.
person: every characters are the same. we shouldn't need to handle that way.
he is actually a senior developer. who don't even know the difference between unicode and ascii characters.1 -
So a few weeks ago I wiped my MacBook Pro to regain some space and speed, it wasn't really that slow I just had the disk partitioned into two installments of MacOS. When I erased the disk I thought the secure thing to do would be to set the format to journaled, encrypted rather than just journaled. Everything was working fine, there seemed to be this weird step of login when I restarted but whatever, except iCloud Drive. On my iMac it works fine but for whatever reason my MacBook Pro doesn't want to download custom folders (ones that aren't created by an app and don't have an app icon on folder icon) from my account despite them being clearly available in iCloud.com. So after this much time of messing with it I'm wiping my MacBook Pro again and formatting it as journaled (not encrypted). Wish me luck...undefined this must just be a bug or a security feature... probs a bug tho i still like apple products this stuff usually works for me3
-
"One misstep from developers at Starbucks left exposed an API key that could be used by an attacker to access internal systems and manipulate the list of authorized users," according to the report of Bleeping Computer.
Vulnerability hunter Vinoth Kumar reported and later Starbucks responded it as "significant information disclosure" and qualified for a bug bounty. Along with identifying the GitHub repository and specifying the file hosting the API key, Kumar also provided proof-of-concept (PoC) code demonstrating what an attacker could do with the key. Apart from listing systems and users, adversaries could also take control of the Amazon Web Services (AWS) account, execute commands on systems and add or remove users with access to the internal systems.
The company paid Kumar a $4,000 bounty for the disclosure, which is the maximum reward for critical vulnerabilities.6 -
Social Captain (a service to increase a user's Instagram followers) has exposed thousands of Instagram account passwords. The company says it helps thousands of users to grow their Instagram follower counts by connecting their accounts to its platform. Users are asked to enter their Instagram username and password into the platform to get started.
According to TechCrunch : Social Captain was storing the passwords of linked Instagram accounts in unencrypted plaintext. Any user who viewed the web page source code on their Social Captain profile page could see their Instagram username and password in plain text, as they had connected their account to the platform. A website bug allowed anyone access to any Social Captain user's profile without having to log in ; simply plugging in a user's unique account ID into the company's web address would grant access to their Social Captain account and their Instagram login credentials. Because the user account IDs were for the most part sequential, it was possible to access any user's account and view their Instagram password and other account information easily. The security researcher who reported the vulnerability provided a spreadsheet of about 10,000 scraped user accounts to TechCrunch.3 -
I don't know what you did yesterday, but i did make my company throw away 2 months of progress.
It all started in the beginning, since that i've made numerous complaints about the workflow or code and how to improve it. I've been told off every time, and every time i either told the boss who agreed in the end or wrote code to prove myself. Everything was a hassle and my tasks weren't better.
Team lead: you'll do X now, please do that by making Y.
Me: but Y is insecure, we should do Z.
Team lead: please do Y
Later it turns out Y is impossible and we do Z in the end...
Team lead: please do W now
Me, a few days later: i've tried and their server doesn't give http cors headers, doing W in the browser is impossible
Team lead, a few days later: have you made progress on W?
Me: * tells again it's impossible and uploads code to prove it *
Team lead: * no response *
After that i had enough. Technically i still was assigned to do W, but i used my time to look over the application and list all the things wrong with it. We had everything, giant commits, commented out code, unnecessary packages, a new commit introduced packages that crashed npm install on non-macs, angularjs-packages even though we use angular, weird logic, a security bug, all css in one file even though you can use component-specific css files...
I sent that to my boss, telling him to let the backend-guys have a look at it too and we had a meeting about this. I couldn't attend but they agreed with me completely. They decided to throw away what we have already and to let one of the backend-guys supervise our team. I guess there will be another talk with the team lead, but time will tell.
It feels so good having hope to finally escape this hellish development cycle of badly defined task, bad communication and headache-inducing merges. -
+++ Windows 10 NTFS file system corruption 0-Day will be fixed soon +++
https://bleepingcomputer.com/news/...2 -
I don't know why is that everytime you guys find a security bug or a data leak or that someone is saving plain passwords on their database, you try to cover and censor the company name. Listen people, fuck the company and their name and their brand if someone's data might be in danger. Everybody should be aware of what is happening with their personal information.
Also, maybe would be great if devRant would let users to post anonymous rants for this kind of issues or a special thread with latest news about our online security.3 -
coolest bug our team had was not a actually a bug but a feature that is misused and abused.
tldr: its a feature that became a bug
we have an app that has a "test print" feature to test the printer and the format of the document to be printed. it has the word TEST for fields and all that.
it became a bug when suddenly, the users use that feature to print documents, instead of using the app with the business rules and all, and just manually strike off the TEST words with a pen.
the feature became a bug because it has become a security risk. -
Recently, one of my customers filed a ticket because some iFrame he got from another company wouldn't display after putting it into the content editor.
I told her it won't work because the (third-party) editor prohibits JavaScript inside iFrame tags and their attributes for security reasons.
She said ok. She said she'd understood the problem. And then, she reopened the ticket four (4!!!) times for the exact same reason, once because she tried to use a fixed iFrame tag the other company sent to her... still containing JavaScript, of course.
But, yeah... She understood what the problem was. Is clear.1 -
So, this incident happened with me around 2 years ago. I was pentesting one of my client's web application. They were new into the Financial Tech Industry, and wanted me to pentest their website as per couple of standards mentioned by them.
One of the most hilarious bug that I found was at the login page, when a user tries logging into an account and forgets the password, a Captcha image is shown where the user needs to prove that he is indeed a human and not a robot, which was fair enough to be implemented at the login screen.
But, here's the catch. When I checked the "view source" option of the web page, I saw that the alt attribute of the Captcha image file had the contents of the Captcha. Making it easy for an attacker to easily bruteforce the shit outta the login page.
You don't need hackers to hack you when your internal dev team itself is self destructive.2 -
Job security:
- Create bugs purposely
- Discover the bugs after a while (if you discover it too quickly it will look suspicious)
- Fix the bug1 -
I really lost my faith in our profession.
A Software&Hardware solution that costs more several 10.000€ is broken after every update.
The Producer even achieves to break untouched features in new releases.
No communication at all. If you report Bugs, they are your fault. The whole system has absolutely no security at all.
It is unsecure by design.
And even if they hear your Bug report you have to pray that they will fix it.
Most if the time you have to wait the whole year for a new release tio get your bugfixes.
But there are also bugs that are untouched for years.
WHY? WE PAY YOU!
I want to cry4 -
I found xss on the software the my school and many other schools use it. The bug is on every page of their website.
I reported the bug to their team, they fixed it and didnt even reward me.
What do you ranters advice me to? 7
7 -
Me: Alright, new week, back from vacation fully rested and focused, lets get productive.
Apple(safari 10.3 update): Fuck you.
Basically the change log was:
*fixed critical security bug.
*added more bugs to fix later.
Well fuck you too safari... You disgust me.
The least the fucking imbeciles, or monkeys, behind safari can do is add a fucking css prefix. For fucks sake. -
Public REST (-inspired) API. Should I skip numeric IDs because it's easy for consumers to snoop around?
Example:
POST api/foo
201 Created api/foo/69
Uh, I'll get 68 just because I can. Hopefully it returns Unauthorized, unless we some kind of bug.
Is it just security by obscurity if I use, like, guids or something instead of sequental IDs?17 -
Do you have any annoying you want to get rid off, but you can't because of reasons?
I do. They are 4, but for now I'll talk about the gold medal winner.
When we met about 8-9 ago, she had just come back to town due to some very bad personal experience (not her fault). Anyway, she is polite, but her major flaw is that she is pushy. REAL BAD! And she gets mad when other people (including me) try to do it on her. Another one is having calls during random inappropriate times, because she had fight #N with her boyfriend, and last but not least, she will call when needs something out of someone.
Lately, her project is finding us a job, since we're both unemployed. Any job. The sad part is when she sends me job ads for dev jobs I don't qualify, e.g. Company X is looking for a dev with Y year of experience, knowing A, B, C & D technologies. I've told her that I don't qualify for most of the dev jobs she sends me, but she insists I should send my CV anyway, cause of reasons. Also, for some reason, I should be accounted to her for all my current choices when what I would honestly say is "BUG OFF".
Her latest endeavour is getting me one of her friends (a psychologist) as a "client". Her friend wants to have a professional website with writing posts/articles as a side dish. I'm not registered as a freelancer, so everything will be done under the counter, and her friend is OK with that. I'm no web developer, but I didn't refuse because of her backlash and also that would be a positive experience for me. Now, the juicy part. She gave her my phone number without my permission and she told me straight away. Her plan was having the three of us meet, though I don't know why and I didn't want her being around. I asked her to call me immediately, which it didn't happen. After being pestered by my friend for a couple of weeks if her friend called me, she finally did it on Monday. She didn't say to me anything I didn't know, but at least I have her phone now.
What I can offer her is a website skeleton with the usabilities she's asking. What I can't offer her is graphics/banner and security. And now I have to come up with reasonable price. Teams here ask 400-600€ for a complete website the way she asks, including VAT. I'm thinking around 100€ and I don't know when I can deliver the project. I've had some experience with Ruby and Sinatra, so I'll go with that, and I'll learn CSS along the way.
Thanks for reading till the end! 😃4 -
Even the most widely used , greatest command "sudo" had a security bug which took years to identify.
So, next time if your product manager tries to screw you over a bug you can tell this as an example 😂😂1 -
They tell me to only review security in the security reviews I'm doing (and if I bring to attention that they're implementing a weak encryption so even though they're not using it at the moment it might cause issues so be careful with that they say to only review security 😵) and then I see this mssql in a where:
AND ISNULL(field, 0) IS NULL
And I think wtf, should I report that? I did and it's a bug and they're thanking me now....
God dammit it's hard to "review security" here...3 -
Open source is poison, hoax and source of much troubles.
Even as I love OSS, and I use it a lot, when things go south, they go south terribly.
There was "security" updates in one OSS program I have been using, that accidentally prevented use cases which specifically affected me. I raised bug report, made issue and gave small repro for it.
One of the core developers acknowledges that yes, this is problem, and could be handled with few added options, which users of similar use case could use to keep things working. He then tags issue "needs help" and disappears.
After I have waited some time, I ask help how I could fix it myself, like how to setup proper dev environment for that tool. Asked it in their forums few days later, as issue didn't get any response. Then asked help in their slack, as forums didn't get any help.
Figured out how to get dev environment up, fix done (~4 lines changed, adding simple check for option enabled or not) and figured out how to test that this works.
I create pull request to project, checking their CONTRIBUTING and following instructions there. Then I wait. I wait two weeks, and then one of the core develors goes to add label "needs response from maintainer". That is now almost two weeks ago...
So, bug that appeared in October, and issue that was created October 8th, is still not fixed, even as there is fix in PR for 28 days this far.
And what really ticks me off? People who make statements like: "it is OSS, have you thought of contributing and fixing things yourself?" when we run into problems with open source software.
Making fix yourself ain't biggest problem... but getting it actually applied seems to be biggest roadblock. This kind of experiences doesn't really encourage me to spend time fixing bugs in OSS, time is often better spend changing to different tool, or making changes in my own workflow or going around problem some kludge way.
I try to get business starting, and based on OSS tools. But my decision is staggering, as I had also made decision to contribute back to OSS... but first experiences ain't that encouraging.
Currently, OSS feels like cancer.16 -
Wtf is happening to tech security... Last 4 months
All WiFi is now crackable. .. in short amount of time
Windows . . Annihilated with this new bug might not be fixable... and work back on all of them
iPhones cracked ...
Linux dirty cow ...
Android been suffering.
And everyone knows Mac's security is joke ...
Finger prints ... Made pointless on everything.
Literally all going to shit .. 😐
And I know how to do all this... It's all out in the open not even hard to find8 -
I am not a PHP dev but this back end error message when accessing /notif looks weird.
Is this a security bug? 7
7 -
When the CTO/CEO of your "startup" is always AFK and it takes weeks to get anything approved by them (or even secure a meeting with them) and they have almost-exclusive access to production and the admin account for all third party services.
Want to create a new messaging channel? Too bad! What about a new repository for that cool idea you had, or that new microservice you're expected to build. Expect to be blocked for at least a week.
When they also hold themselves solely responsible for security and operations, they've built their own proprietary framework that handles all the authentication, database models and microservice communications.
Speaking of which, there's more than six microservices per developer!
Oh there's a bug or limitation in the framework? Too bad. It's a black box that nobody else in the company can touch. Good luck with the two week lead time on getting anything changed there. Oh and there's no dedicated issue tracker. Have you heard of email?
When the systems and processes in place were designed for "consistency" and "scalability" in mind you can be certain that everything is consistently broken at scale. Each microservice offers:
1. Anemic & non-idempotent CRUD APIs (Can't believe it's not a Database Table™) because the consumer should do all the work.
2. Race Conditions, because transactions are "not portable" (but not to worry, all the code is written as if it were running single threaded on a single machine).
3. Fault Intolerance, just a single failure in a chain of layered microservice calls will leave the requested operation in a partially applied and corrupted state. Ger ready for manual intervention.
4. Completely Redundant Documentation, our web documentation is automatically generated and is always of the form //[FieldName] of the [ObjectName].
5. Happy Path Support, only the intended use cases and fields work, we added a bunch of others because YouAreGoingToNeedIt™ but it won't work when you do need it. The only record of this happy path is the code itself.
Consider this, you're been building a new microservice, you've carefully followed all the unwritten highly specific technical implementation standards enforced by the CTO/CEO (that your aware of). You've decided to write some unit tests, well um.. didn't you know? There's nothing scalable and consistent about running the system locally! That's not built-in to the framework. So just use curl to test your service whilst it is deployed or connected to the development environment. Then you can open a PR and once it has been approved it will be included in the next full deployment (at least a week later).
Most new 'services' feel like the are about one to five days of writing straightforward code followed by weeks to months of integration hell, testing and blocked dependencies.
When confronted/advised about these issues the response from the CTO/CEO
varies:
(A) "yes but it's an edge case, the cloud is highly available and reliable, our software doesn't crash frequently".
(B) "yes, that's why I'm thinking about adding [idempotency] to the framework to address that when I'm not so busy" two weeks go by...
(C) "yes, but we are still doing better than all of our competitors".
(D) "oh, but you can just [highly specific sequence of undocumented steps, that probably won't work when you try it].
(E) "yes, let's setup a meeting to go through this in more detail" *doesn't show up to the meeting*.
(F) "oh, but our customers are really happy with our level of [Documentation]".
Sometimes it can feel like a bit of a cult, as all of the project managers (and some of the developers) see the CTO/CEO as a sort of 'programming god' because they are never blocked on anything they work on, they're able to bypass all the limitations and obstacles they've placed in front of the 'ordinary' developers.
There's been several instances where the CTO/CEO will suddenly make widespread changes to the codebase (to enforce some 'standard') without having to go through the same review process as everybody else, these changes will usually break something like the automatic build process or something in the dev environment and its up to the developers to pick up the pieces. I think developers find it intimidating to identify issues in the CTO/CEO's code because it's implicitly defined due to their status as the "gold standard".
It's certainly frustrating but I hope this story serves as a bit of a foil to those who wish they had a more technical CTO/CEO in their organisation. Does anybody else have a similar experience or is this situation an absolute one of a kind?2 -
Give me your legacy, your undocumented,
Your huddled classss yearning to be bug free,
The wretched security holes of your multiple backdoors.
Send these, the testless, spaghetti-code to me,
I lift my keyboard beside the golden door! -
Boss explaining a bug found in my senior developer's (yes, that one) application...
Boss: "This shouldn't happen, this presents a security issue since these records should not be visible at this point."
"Senior" Developer: "You're right. Hmm, what should I do about that?"
Me: *face palm*2 -
!!rant life toptags bottags
My tags seem to be okay. Let's go.
I'm 14. I live in a place where nobody smart lives, and the school I go to has no coders.
Last year, all my friends moved. The only friend I had left now hates me, simply because they yelled at me everyday and I yelled at them once.
I am in the middle of my exams. I also have the flu, but thankfully it's not the e-flu, otherwise you guys should prepare for 24/7 headaches.
Due to the medications I am taking, I'm half-asleep all the time, and I probably am messing up all of my grades.
My entire extended family is in India, and I go there 2 times a year. I miss them so much right now :(.
At the same as doing exams, I am trying to keep my laptop (primary) and PC (secondary, desk) configuration and setup approximately synchronized. In order to do that, I am setting up my dotfiles repository.
Except that all my laptop config (which works) is written horribly, and I need to rewrite it all.
At the same time, I have 3 other projects going on: An OS written in D, a source-based package management system written in D, a small website (not online), and a whatever's cooking in my mind at this moment.
Right now, I'm supposed to be studying for my French exam.
Instead, I'm here, typing this out on my phone.
I have a classmate in school who can type QWERTY at 80WPM. I'm learning Dvorak (Programmer's!) and my current speed is 33WPM, after about 2 months of half-hearted practise during work time and at school.
Sometimes, I look at the world we have here, and what we're doing to it, and I wish that sometimes we could simply be content with life. Let's just live, for once.
I find ~60 random songs in one go, simply by finding a song I know on YouTube and going to the 'Mix - <song>' playlist. I download them all (youtube-dl), and I listen to them. Sometimes, I find this little part in a song (Mackelmore & Ryan Lewis - Can't Hold Us beginning instrumentals, or Safe and Sound chorus instrumentals) that make me feel so happy I feel like all's good in the world. Then the song moves on and with it, my happiness.
I look at Wayland, and X, and I think - Why can't we have one way of doing things - a fixed interface to express anything, so that one common API exists for everything of that type? And I realise it's because they feel that they're missing something from the others. Perhaps it's a bug nobody's solved or functionality that's missing, and they think that they can do better than that. And I think - Well, that's stupid. Submit a fucking bug report or pull request instead of reinventing the wheel. And then I realise that all the programming I've ever done in my life IS simply reinventing the wheel. And some might say, "Well, that guy designed it with spokes and wood. I designed it with rubber and steel," but that doesn't work, because no matter what how you make it, it's just a wheel. They both do the same thing. Both have advantages and disadvantages, because nothing's perfect. We're not perfect because we all have agendas and wants and likes and dislikes and hates and disgusts and all kinds of other crap, and our DNA's not perfect because it manages to corrupt copy operations (which is basically why we die of old age, I think).
And now I've lost my train of thought and this is too large to scroll over so I'm just going to move on to the next topic. At this point (.), I have 1633 letters left.
I hate the fact that the world's become so used to QWERTY because of stuff that happened 100 years ago that Dvorak is enough of a security to stop most people from being able to physically use my laptop.
I don't understand why huge companies like Google want to know about me. What would you do with this information? Know how to take over my stuff when the corporation-opocalypse comes around? Why can't they leave me alone? Why do I have to flash a ROM onto my phone so that Google cannot track me? What do you want, Google?
I don't give a shit any more, so there's my megarant.
Before anybody else (aside from myself) tells me that this is too big, all these topics are related simply because my train of thought went this way. There's a connection between each of these things, but I just don't know what it is.
Goodnight, world. 666 is the number of characters I have left. So is 42, for that matter (thanks, Douglas Adams!). Goodbye.rant life story current project ugh megarant why are you doing this to me life schrodinger's tags 🐈 life3 -
Bug is not fixable
I get these as I have to submit security issues as bugs and then help whoever is in charge of the fixing find and implement a good solution. But apparently , nope . In some devs opinion , sqli issues are not fixable .1 -
South Africa Release notes version v3.0.2
In 1994 SA underwent one of the biggest system upgrades since 1948. In this new rolling release since the system update called apartheid the system has been annexing resources, locking it down, making it closed source, closing it off community updates and from global updates and minimizing services across the board. On 27 April 1994, the new democratic system update was released with a new system monitor, release resources and balancing efficiency in the system. Though there were remnants of the old code in the system, it was being rewritten by a new generation of users, open source resources were established, giving users the right to choose among themselves how to grow the system , and how to better the experience for all.
In 1999 a new system monitor was created by the users, it wasnt as popular as the ground breaking Madiba release but it was a choice by the community to move forward and grow. The system was stable for a few years, new users were able to develop more on the system, making it more lucrative monetary wise. There were still remnants of the apartheid code but the new generation of developers worked with it making it there own, though they had not yet had admin rights to help change the system, they created a developer culture of their own. A new system resources balancer was introduced called BBEE, that allowed previous disadvantage users more admin rights to other system resources, helping the user base to grow. Though the balancer was biased, and flawed it has helped the system overall to grow and move forward. It has major holes in security and may flood some aspects of the system with more outdated software patches, users have kept it in its system releases until the resource balancer moved the system into a more stable position.
The next interim system monitor release was unexpected, a quiet release that most users did not contribute towards. The system monitor after that nearly brought the system down to a halt, as it was stealing resources from users, using resources for its own gain, and hasn't released any of it back to the system.
The latest user release has been stable. It has brought more interest from users from other countries, it had more monetary advantages than all other releases before. Though it still has flaws, it has tried to balance the system thus far.
Bug report as of 16 Feb 2018
*User experience has been unbalanced since the 1994 release, still leaving some users at a disadvantage.
*The three tier user base that the 1948 release established, creating three main user groups, created a hierarchy of users that are still in effect today, thought the 1994 release tried to balance it out, the user based reversed in its hierarchy, leaving the middle group of users where they were.
*System instability has been at an all time low, allowing users to disable each others accounts, effectively
killing" them off
*Though the infrastructure of the system has been upgraded to global standards ( in some aspects ) expansions are still at an all time low
*Rogue groups of users have been taking most of the infrastructure from established users
*Security services have been heightened among user groups though admins were still able to do as they pleased without being reprimanded
*Female users have been kicked off the system at an alarming rate, the security services have only kicked in recently, but the system admins and system monitor has not done anything about it yet
Bug fixes for a future release:
*Recreating the overall sysadmin team. Removing some admins and bringing others in
*Opening the system more globally to stabilize it more
*Removing and revamping the BBEE system, replacing it with more user documentation, equalizing the user base
*Giving more resources to users that were at a disadvantage during the first release
*Giving the middle group of users more support, documentation and advantages in the system, after removing the security protocols from the user base
*Giving new users who grew up with the post 1994 release more opportunities to help grow the system on a level playing field.
*Establishing the Madiba release principles more efficiently in the current system1 -
Ok.
I am not a security expert, but when i was working on downloading youtube videos directly from googlevideos.com server, found out there was some security issue that allows to manipulate login requests.
Reported to google.
Let's see how it goes.2 -
I really wanna get a keg of rum and start sailing across the globe...
Just to spank some devs / managers arses.
The last years were... very demanding regarding security and upgrades.
It hasn't gotten better.
Microsoft leaked it's security key thx to internal debugging and the tool to secure the debugging process so secure data gets filtered was buggy...
I'd guess I already have carpal tunnel after Redmond.
But the really really sad story is: This has become the gold standard.
https://lwn.net/Articles/943969/
Chrome selling the privacy mode for Ads, long topic ongoing for years... yeah they did it.
Apple... oh boy. I could write a Silmarillion about it and would still need an additional trilogy.
Amazon realizing that a Microservice architecture needs planning, cause yeah... just potting services in a data center doesn't end well.
It goes on and on and on....
Don't even get me started on the plethora of firmware / microcode updates cause there was either yet another CPU bug or another device pooped their pants cause the firmware is a mess and needed some dubious update without any background at all...
Serious question: Am I becoming a pepperidge farm uncle threatening to shoot everyone cause I'm getting old and cranky ....
Or is really everything in IT going down the drain the last few years?
It feels like every week is just another "we fucked it up" event.3 -
Magento Debugging Horror!
Changing lots of things in magento with no problem. Continuing development for quite sometime. Suddenly decide to clear cache to see affect of a change on a template in frontent. Suddenly magento crashes! There's no error message. No exception log. No log in any file anywhere on the disk. All that happens is that magento suddenly returns you to the home page!
Reverting all the changes to the template. Clear the cache. Nope! Still the same! Why? Because the problem has happened somewhere in your code. Magento just didn't face it, because it was using an older version of your code. How? Because magento 2 even caches code! Not the php opcache. Don't get me wrong. It has it's own cache for code, in a folder called generated. Now that you cleared all the caches including this folder, you just realized that, somewhere something is wrong. But there is no way for you to know where as there is absolutely no exception logged anywhere!
So you debug the code, from index.php, down to the deepest levels of hell. In a normal php code, once the exception happens, you should see the control jumps to an exception handler, there, you can see the exception object and its call stack in your debugger. But that's not the case with magento.
Your debugger suddenly jumps to a function named:
write_close();
That's all. No exception object. No call stack. No way to figure out why it failed. So you decide to debug into each and every step to figure out where it crashes. The way magento renders response to each request is that, it calls a plugin, which calls a plugin loop, which calls another plugin, which calls a list of plugins, which calls a plugin loop, which calls another plugin.....
And if in each step, just by accident, instead of step through, you use the step over command of your debugger, the crash happens suddenly and you end up with the same freaking write_close() function with no idea what went wrong and where the error happened! You spend a whole day, to figure out, that this is actually a bug in core of magento, they simply introduced after your recent update of magento core to the latest STABLE version!!! It was not your mistake. They ruined their own code for the thousandth of time. You just didn't notice it, because as I said, you didn't clear the `generated` folder, therefore using an older version of everything!
Now that after spending 7 hours figuring out what has failed with absolutely no standard way of debugging and within a spaghetti of GOTO commands (Magento calls them plugin), why not report it to github? So you report it with a pull request. This also takes 1 hour of your time. Just to next day get informed that your pull request is rejected because another person already fixed the bug and made the same pull request. It was just not on the latest stable version yet!
So you decide to avoid updating magento as much as possible. Because you know that the next Stable version will make your life and career unstable. But then the customer complains that the Admin Panel is warning him of using old Magento version which might pose SECURITY THREATS! -
Just reported a minor tracking bug I found on WebKit to the WebKit bugzilla, and I have a few thoughts:
1. Apple product security can be kind of vague sometimes - they generally don't comment on bugs as they're fixing them, from the looks of it, and I'm not sure why that is policy.
2. Tracking bugs *are* security bugs in WebKit, which is quite neat in a way. What amazes me is how Firefox has had a way to detect private browsing for years that they are still working on addressing (indexedDB doesn't work in private browsing), and chrome occasionally has a thing or two that works, with Safari, Apple consistently plays whack-a-mole with these bugs - news sites that attempt to detect private browsing generally have a more difficult time with Safari/WebKit than with other browsers.
I guess a part of that could be bragging rights - since tracking bugs (and private browsing detection bugs, I think) count as security bugs, people like yours truly are more incentivised to report them to Apple because then you get to say "I found a security bug", and internal prioritisation is also higher for them. -
Was working on a high priority security feature. We had an unreasonable timeline to get all of the work done. If we didn’t get the changes onto production before our deadline we faced the possibility of our entire suit being taken offline. Other parts of the company had already been shut down until the remediations could be made -so we knew the company execs weren’t bluffing.
I was the sole developer on the project. I designed it, implemented it, and organized the efforts to get it through the rest of the dev cycle. After about 3 month of work it was all up and bug free (after a few bugs had been found and squashed). I was exhausted, and ended up taking about a week and a half off to recharge.
The project consisted of restructuring our customized frontend control binding (asp.net -custom content controls), integrations with several services to replace portions of our data consumption and storage logic, and an enormous lift and shift that touched over 6k files.
When you touch this much code in such a short period of time it’s difficult to code review, to not introduce bugs, and _to not stop thinking about what potential problems your changes may be causing in the background_.3 -
The concept and execution of inter-cluster SSL along with keystores, truststores, signing, and similar just clicked in my head today. I feel the burden of undiagnosable https errors just melt off my shoulders. Any other environment tips I should know for kubernetes?
-
Ten year old Jani found a security exposure in Instagram and Zuck game him $10k. Cool.
He should do a cameo on Silicon Valley and expose Hooli. That would be so funny 😋
http://theverge.com/tech/2016/...2 -
Since I started my routine of checking bug logs every morning, I've had 2 instances where a website vulnerability scanner was run against a production website and generated over 2,000 Coldfusion errors.
At the time, I was super nervous about the apparent hack attempt, and hyped that the attackers never actually got in. It's nice to know that despite the various errors indicating vulnerable / breakable code, they were ultimately unsuccessful. I know now that a determined attacker could probably have wrecked our production websites. Since then I've made a ton of security-related updates and I'm actually thankful for the script kiddie getting my attention with that scan.
PS. We're now building a website for a local security company who is going to work with us to pen test the site when it's finished! Gulp.4 -
Apparently you need to pay microsoft in order to have access to some security features, such as removing managing connected oauth apps.
What a fucking joke, I need to check a fucking screen of yours that our client has deemed as a bug.
Get your shit together and stop bring such a greedy whore microshit3 -
Just dropping some current experience here.
Content security policies are big mess in both chrome and firefox.
Chrome has some 4 years old "bug" where you can't add hash of JS file to 'style-src' policy to permit inline-styles THAT would be set by this script (jQuery actually).
Firefox is beautifully unhelpful, it just pops of error "blocked ..something..", not even saying what it was.
EDIT:
And I am missing a pair of some steel balls to ask about this on SO because there is this much of very similar questions, nonetheless -if I did read them right- every one of them is talking about enabling style attribute, and that's something different.
EDIT2: Chrome currently generates 138 errors "jquery-3.4.0.min.js:2 Refused to apply inline style..." , this ain't hitting production.10 -
Why people do that shit ? is a free backdoor to sniff other user content XD
if(isset($_COOKIE["user"])){
resetSession("user","user");
}
function resetSession($cookiename,$sessionname){
$_SESSION[$sessionname] = $_COOKIE[$cookiename];
}8 -
The platform team who provides all other teams with common framework emails everybody we need to upgrade the framework to new version. Let’s say version 1.a.0. They say it brings crucial security features and all pipelines using old versions would be blocked. My colleague created a story to upgrade all of our 10 microservices. When I got to it in a couple of days for some fucking reason they already rolled out 1.a.1 and didn’t inform anybody, the pipelines just logged warning u need to use 1.a.1. Alright, I did the upgrade to 1.a.1 and merged ducking everything in 10 fucking microservices. In a couple of days at morning they roll our 1.a.2 and require everybody to upgrade ducking degenerates as they found a high severity bug. I wanted to start again but was lazy and did nothing all day to learn that at 6pm the fuckers roll out 1.a.3!!! And again require everyone to upgrade!1!1!1eleven
Ten fuxkibg microservices. Goddamit write some unit tests, do friends&family, do fucking tests on small group of your inner clients before rolling out this shit that everybody must to use.
Spat at the display -
Difference between security threat and programming bug ?
Found a cool paper about format string attacks which mentioned buffer Overflow is a security threat while format string is a programming bug.
Had no idea what that really meant.
Tnx1 -
Two security researchers have published details about a vulnerability in the Windows Printing Service which impacts all Windows versions.
According to a Report of ZDNet : The vulnerability codenamed 'PrintDemon' which is located in Windows Print Spooler (Windows component responsible for managing print operations). The service sends data to be printed to a USB port for physically connected printers. In a report published, security researchers Alex Ionescu & Yarden Shafir said they found a bug in this old component that can be abused to hijack the Printer Spooler internal mechanism. The bug can not be used to break into a Windows client remotely over the internet, so it's not something that could be exploited to hack Windows systems over the internet.4 -
Security experts have discovered hundreds of fake websites which are being used to spread dangerous malware for Android and Windows devices. A "vast" network of over 200 internet pages, which impersonate 27 brands such as household names like TikTok, PayPal and Snapchat, are being used to spread a vicious bug which can empty out bank accounts. These bogus websites feature the notorious ERMAC banking trojan which is capable of stealing sensitive login details for 467 online banking and cryptocurrency apps.6
-
Just what is life
1st I love developing Web Apps
2nd I hate when it has bugs (Always does Everyone does)
3rd More hate for Security related bugs
So I started bug hunting so that even I can make developers hurt I thought I might find peace here
But here we fucking have SQL Injections which are not really that bad easy peasy
But we also have special kind of SQL Injections the Boolean Based ones (Medium Level Demons) and also The Time Based SQL Injections (Medium Level Demon with lots of health consumes too much time has a repetitive process and we have to wait a lot also if you have network lag you are doomed)
No its nice story till here but here it fucking ends the happiness I mean my luck is worst kind of fucking thing anybody ever can have.
I got a mix of both Demons;_;
A Time-Based Boolean SQL Injections yess fuckety amounts of fucking time wasted and redundant fucking process also to make matters worst the fucking famous tool #SQLMAP doesn't work in my case -
Many times in life I experienced situations that are depressing to me yet I'm not partially or totally conscious about it.
I have a very good example that I'm actually experiencing right now: me reporting the progress of a task to my boss and getting no response from him.
He has gone on these "ignoring sprees" in the past already and for the current one, it's been like four consecutive ignores.
I guess it's depressing for two reasons:
1) I feel like my work has no importance or value, which drags me down.
2) Sometimes he also tries to rush which I consider pretty hypocritical of him. because I have to basically not complain about it to not endanger this job relationship my family dearly depends on, I have to shut up and feel frustrated. (keep in mind i'm a south am person working for a us company and I was very lucky to get this job).
For some reason I just don't notice as easily how awful it makes me feel, but I wished I could fucking tell this straight into his fucking face:
You wanna be a boss? Be a fucking boss and check on my fucking progress.
I'm considering getting into security and going for bug bounties online. -
I was today years old when I got to know that there is a way to auto detect OTP sent via SMS with SMS READ permission. WTF!!3
-
I put $620,000 of Bitcoin into making my dream happen—building an AI business that would push robotics and machine learning to new levels. It wasn't an investment; it was the future years of my life I had been building toward. That future was wiped out because of one minor mistake in my own code.
I had programmed a custom wallet to hold my Bitcoin, feeling it would add an extra level of security and independence. Things were fine until the day a small bug left me locked out. My password was correct, but the wallet refused to unlock. My pulse was pounding as I tried time and again, each attempt drying my palms out a little more.
I was going crazy for weeks attempting to fix it. I pored over lines of my own code, applied patches, and even went the brute force method. None of it worked. It was as if I had built a fortress only to trap myself in it.
I was at my wit's end when I saw a thread on GitHub. Brought out from the depths of comments, someone mentioned WIZARD WEB RECOVERY SERVICES . I was desperate at this point and out of ideas.
The moment I contacted them, I knew I was in capable hands. Their personnel were not only skilled, they understood what this would do for me. They asked me extremely specific questions regarding my custom software, respected my work, and assured me they had dealt with cases like mine before.
Their approach was surgical. They reverse-engineered my wallet code like it was a blueprint, dissecting every line I had written. It was a humbling experience to watch their expertise at work. They kept me apprised step by step, giving me hope when I believed all hope was lost.
Eight days went by, and then I received the call I had been hoping for. They cracked it. My wallet was restored to its fullness, all of my $620,000 still there and ready to power my startup once again.
Apart from recovery, they also educated me on secure coding principles and introduced me to wallet audit services that would prevent such occurrences from happening again.
Thanks to WIZARD WEB RECOVERY SERVICES , my robots will keep dancing, and my dream is still alive. If you ever find yourself locked out, don't spend weeks like I did—call them immediately. 1
1 -
Persisterising derived values. Often a necessary evil for optimisation or privacy while conflicting with concerns such as auditing.
Password hashing is the common example of a case considered necessary to cover security concerns.
Also often a mistake to store derived values. Some times it can be annoying. Sometimes it can be data loss. Derived values often require careful maintenance otherwise the actual comments in your database for a page is 10 but the stored value for the page record is 9. This becomes very important when dealing with money where eventual consistency might not be enough.
Annoying is when given a and b then c = a + b only b and c are stored so you often have to run things backwards.
Given any processing pipeline such as A -> B -> C with A being original and C final then you technically only need C. This applies to anything.
However, not all steps stay or deflate. Sum of values is an example of deflate. Mapping values is an example of stay. Combining all possible value pairs is inflate, IE, N * N and tends to represent the true termination point for a pipeline as to what can be persisted.
I've quite often seen people exclude original. Some amount of lossy can be alright if it's genuine noise and one way if serving some purpose.
If A is O(N) and C reduces to O(1) then it can seem to make sense to store only C until someone also wants B -> D as well. Technically speaking A is all you ever need to persist to cater to all dependencies.
I've seen every kind of mess with processing chains. People persisting the inflations while still being lossy. Giant chains linear chains where instead items should rely on a common ancestor. Things being applied to only be unapplied. Yes ABCBDBEBCF etc then truncating A happens.
Extreme care needs to be taken with data and future proofing. Excess data you can remove. Missing code can be added. Data however once its gone its gone and your bug is forever.
This doesn't seem to enter the minds of many developers who don't reconcile their execution or processing graphs with entry points, exist points, edge direction, size, persistence, etc.2 -
I Thought My Nest Egg Was Immobile Permanently! Overseas travel is glamorous until you are at 37,000 feet, trying to cope with different time zones, airport security queues, and dodgy Wi-Fi that cannot even open an email, never mind providing your future funding. I had stashed $890,000 of Bitcoin away as my retirement nest egg, a nest egg made of decades of hard work. That sense of security evaporated in thin air when I replaced my phone and forgot to update the two-factor authentication settings on my wallet.
Somewhere across the Atlantic, turbulence rattled the plane, but the real storm was the panic in my chest when I realized that I could not access my wallet. Tired and flustered, I arrived with the dread realization that my virtual fortune was now as out of reach as the stars in the sky. The frustration mounted as I hopscotched from airport to airport. Customer service droids, robot call centers, and half-baked solutions had me addressing vending machines instead of human beings. That was before a layover in Singapore where, bleary-eyed and clutching my third cup of coffee, I chanced upon a travel vlogger's YouTube video raving about Tech Cyber Force Recovery.
With nothing to lose, I called. From the first message itself, it was different. These were actual people, smart, caring, and willing to work around my insane schedule. They scheduled calls during my layovers and adjusted to the chaos of traveling overseas like pros.
Their engineers delved deep into my issue, analyzing time-stamped authentication records. It was as if watching a digital detective movie, minus the stakes: my future. For over 14 hair-on-end days, they weathered the 2FA bug like pilots navigating through turbulence. Then the message came: Access restored. All the Bitcoins were present. I almost cried into my airport ramen. That weight was lifted from my shoulders, and the feeling that all those years of careful planning weren't wasted, was indescribable.
telegram +1 561 726 36 97
WhatsApp +1 561 726 36 973 -
HOW YOU CAN RECOVER YOUR CRYPTO FROM SCAMMERS // CONSULT DIGITAL TECH GUARD RECOVERY
As a tech geek, I'm proud to be on the bleeding edge. So when I stored my Bitcoin in a "quantum-resistant" wallet, I was sure I was invincible, a Nostradamus of the modern age predicting the coming quantum computing apocalypse. "Hack-proof," the website had promised. "A fortress against the future."
And then irony struck. A bug in the firmware shut me out altogether. No access. No backups. Only a chilly, machine-like error message mocking me like a bad guy in a sci-fi flick: "Invalid Signature. Please Reset." Reset? That would mean erasing my $860,000 in Bitcoin. Not exactly a pleasant choice.
Furious, I did what any geek does when something is not right, I tweeted about it. My rant at the irony of a quantum-proof wallet crashing due to a widespread bug went viral. That is when a DM appeared. Digital Tech Guard Recovery's CTO had seen my tweet. "Let's fix this," he typed.
Now, I’ve dealt with tech support before, but this was something else. Within hours, their engineers were deep in my wallet’s firmware, analyzing the cryptographic flaw. They approached the problem like time travelers fixing a paradox, reverse-engineering the bug to develop a workaround.
It was a challenge. The wallet's special "quantum security" had locked it up so tightly that debugging tools couldn't even access it. But these guys were not your average IT support personnel; they were crypto Digitals.
For ten days, I monitored their progress like a scientist awaiting a space probe signal. Finally, the breakthrough: a hacked firmware update, specifically tailored for my wallet model. With cautious steps, I executed their recovery protocol, and voilà, my money was restored.
But they didn't leave it at that. Digital Tech Guard Recovery not only restored my Bitcoin but moved it to an even more secure, battle-tested storage system. No more cutting-edge vulnerabilities. Just solid, proven cryptography.
The irony? My Bitcoin is now safer than ever, not because it's quantum-resistant, but because of the individuals who came to my aid.
Lesson that was learned: The future is unpredictable, but having the right experts on speed dial? That's real security.
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Website link: digital tech guard . com1



