Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "information security"
-
Agency: " Sir, we found 3 candidates as per your requirements, now how do you want their placements sir?"
M.D: "Put about 100 bricks in a closed room. Then send the candidates into the room & close the door, leave them alone & come back after a few hours and analyse the situation:-
1) If they are counting the bricks, Put them in Accounts deptt.
2) If they are re-counting the bricks, Put them in Auditing.
3) If they have messed up the whole room with the bricks, Put them in Engineering.
4) If they are arranging the bricks in some strange order, Put them in Planning.
5) If they are throwing the bricks at each other, Put them in Operations.
6) If they are sleeping, Put them in Security.
7) If they have broken the bricks into pieces, Put them in Information Technology.
8) If they are sitting idle, Put them in Human Resources.
9) If they say they have tried different combinations yet not a single brick has been moved, Put them in Sales.
10) If they have already left for the day, Put them in Marketing.
11) If they are staring out of the window, Put them in Strategic Planning.
And.......
12) If they are talking to each other and not a single brick has been touched, Congratulate them and put them in Top Management.
😂🤣😃😁😅😜6 -
My mom got audited for storing sensitive client information in her gmail account without using a vpn or any other real security.
I had been telling her this was an issue for literally the last three years and shes brushed me off every time.
I got yelled at for not telling her I was serious.34 -
This is so true (not for me).
People (normies) bitch about security, but they click on any and every link, while putting all their information all over the internet. 7
7 -
Alright fuck it, let's release this fucker!
https://lynkz.me is the main domain. The interface is *usable* and nothing more than that. I'll invest more time in that soon but for now, hey, it works.
Api is located at https://api.lynkz.me.
Documentation for this (literally some echoes to the screen but it contains the needed information for now) is at that api url.
Found a bug or a security vulnerability? Please let me know!
Yeah I use mariadb but sql injection is luckily not possible due to quite some sanitization ;)
WARNING: if you make a shortened url and forget the delete key, you won't be able to delete it.
Let's see how this goes 😅111 -
*has a 94% in information security class*
*teacher gives us study guide for final exam*
*heavily take notes in the margins and study the packet obsessively for four days*
*come in to take the final*
*exam doesn't mention a single thing on the study guide*
*makes a 78 on it*
*final class grade drops down to an 87% (a letter grade lower than before)*
"Congratulations, Miss Meowijuanas! You had the highest score on the final!"
*hands me a candy bar like I'm a child*
"Maybe it's because you gave the class an extremely poor study guide which emphasized on material that wasn't covered on our actual exam? You shouldn't be congratulating me on a 78."
*teacher says he used the study guide from another teacher and must not have looked at it thoroughly enough*
*shakes hand and thanks him for having me as a student this semester*
*kicks a trash bin outside of the university 6 or 7 times*
I'm not even mad about my grade. An 87% is nice, although I know I would've done better otherwise. It's his pure, unmasked and unashamed laziness that makes me feel so violent. It's showing students like me that an educated individual like yourself couldn't be bothered to take five minutes or so to read over a fucking document for his students to make sure they're properly prepared for a major exam.
How the fuck can you be hired as a university professor and be this obvious about not putting effort into your work.
Fuck you, sir.
And fuck you again for all of my other classmates who did poorly because they followed your inaccurate study guide.13 -
Example #1 of ??? Explaining why I dislike my coworkers.
[Legend]
VP: VP of Engineering; my boss’s boss. Founded the company, picked the CEO, etc.
LD: Lead dev; literally wrote the first line of code at the company, and has been here ever since.
CISO: Chief Information Security Officer — my boss when I’m doing security work.
Three weeks ago (private zoom call):
> VP to me: I want you to know that anything you say, while wearing your security hat, goes. You can even override me. If you need to hold a release for whatever reason, you have that power. If I happen to disagree with a security issue you bring up, that’s okay. You are in charge of release security. I won’t be mad or hold it against you. I just want you to do your job well.
Last week (engineering-wide meeting):
> CISO: From now on we should only use external IDs in urls to prevent a malicious actor from scraping data or automating attacks.
> LD: That’s great, and we should only use normal IDs in logging so they differ. Sounds more secure, right?
> CISO: Absolutely. That way they’re orthogonal.
> VP: Good idea, I think we should do this going forward.
Last weekend (in the security channel):
> LD: We should ONLY use external IDs in urls, and ONLY normal IDs in logging — in other words, orthogonal.
> VP: I agree. It’s better in every way.
Today (in the same security channel):
> Me: I found an instance of using a plain ID in a url that cancels a payment. A malicious user with or who gained access to <user_role> could very easily abuse this to cause substantial damage. Please change this instance and others to using external IDs.
> LD: Whoa, that goes way beyond <user_role>
> VP: You can’t make that decision, that’s engineering-wide!
Not only is this sane security practice, you literally. just. agreed. with this on three separate occasions in the past week, and your own head of security also posed this before I brought it up! And need I remind you that it is still standard security practice!?
But nooo, I’m overstepping my boundaries by doing my job.
Fucking hell I hate dealing with these people.14 -
My wife was going to school for a business degree but likes what I do as an engineer. She spent a month or so debating engineering or information security.
Yesterday she changed to a degree in information security.
Today she opens a GitHub and starts learning to program and I'm in love all over again.7 -
I literally cringed today when my neighbor wanted help installing an app, she didn't tell me it was her banking app... And the thing I needed to help with was logging in... So she told me her bank details...
Even though I said (multiple times) it was dangerous to do so, and that she can't just trust people with this kind of information...
WHY ARE PEOPLE SO GOD DAMN STUPID WHEN IT COMES TO SECURITY!7 -
Privacy & security violations piss me off. Not to the point that I'll write on devRant about it, but to the point that coworkers get afraid from the bloodthirsty look in my eyes.
I know all startups proclaim this, but the one I work at is kind of industry-disrupting. Think Uber vs taxi drivers... so we have real, malicious enemies.
Yet there's still this mindset of "it won't happen to us" when it comes to data leaks or corporate spying.
Me: "I noticed we are tracking our end users without their consent, and store not just the color of their balls, but also their favorite soup flavor and how often they've cheated on their partner, as plain text in the system for every employee to read"
Various C-randomletter-Os: "Oh wow indubitably most serious indeed! Let's put 2 scrumbag masters on the issue, we will tackle this in a most agile manner! We shall use AI blockchains in the elastic cloud to encrypt those ball-colors!"
NO WHAT I MEANT WAS WHY THE FUCK DO WE EVEN STORE THAT INFORMATION. IT DOES IN NO WAY RELATE TO OUR BUSINESS!
"No reason, just future requirements for our data scientists"
I'M GRABBING A HARDDRIVE SHREDDER, THE DB SERVER GOES FIRST AND YOUR PENIS RIGHT AFTER THAT!
(if it's unclear, ball color was an optimistic euphemism for what boiled down to an analytics value which might as well have been "nigger: yes/no")12 -
Some of you might have seen it already, those who didn't just have to.
One of the best rants I've read lately.
"Our security auditor is an idiot. How do I give him the information he wants?"
https://serverfault.com/questions/...4 -
Although it might not get much follow up stuffs (probably a few fines but that will be about it), I still find this awesome.
The part of the Dutch government which keeps an eye on data leaks, how companies handle personal data, if companies comply with data protection/privacy laws etc (referring to it as AP from now on) finished their investigation into Windows 10. They started it because of privacy concerns from a few people about the data collection Microsoft does through Windows 10.
It's funny that whenever operating systems are brought up (or privacy/security) and we get to why I don't 'just' use windows 10 (that's actually something I'm asked sometimes), when I tell that it's for a big part due to privacy reasons, people always go into 'it's not that bad', 'oh well as long as it's lawful', 'but it isn't illegal, right!'.
Well, that changed today (for the netherlands).
AP has concluded that Windows 10 is not complying with the dutch privacy and personal data protection law.
I'm going to quote this one (trying my best to translate):
"It appears that Microsofts operating system follows every step you take on your computer. That gives a very invasive image of you", "What does that mean? do people know that, do they want that? Microsoft should give people a fair chance for deciding this by themselves".
They also say that unless explicit lawful consent is given (with enough information on what is collected, for what reasons and what it can be used for), Microsoft is, according to law, not allowed to collect their telemetrics through windows 10.
"But you can turn it off yourself!" - True, but as the paragraph above said, the dutch law requires that people are given more than enough information to decide what happens to their data, and, collection is now allowed until explicitly/lawfully ok'd where the person consenting has had enough information in order to make a well educated decision.
I'm really happy about this!
Source (dutch, sorry, only found it on a dutch (well respected) security site): https://security.nl/posting/534981/...8 -
@JoshBent suggested that I'd make a blog about security.
Nice idea, fair enough!
*registers domain at provider with discounts at the moment*
*tries to find whois protection option*
"You can add WHOIS protection to your account as an upgrade"
*requests authorization token*
*logs into usual domain name provider account*
*transfers domain name*
*anonymizes WHOIS details within two seconds*
I could've stayed and ask them about the cost etc but the fact that they even HAVE a price for protecting WHOIS data is a no-go for me.
Fuck domain name resellers which ask money for protecting ones WHOIS information (where possible).32 -
What I'm posting here is my 'manifesto'/the things I stand for. You may like it, you may hate it, you may comment but this is what I stand for.
What are the basic principles of life? one of them is sharing, so why stop at software/computers?
I think we should share our software, make it better together and don't put restrictions onto it. Everyone should be able to contribute their part and we should make it better together. Of course, we have to make money but I think that there is a very good way in making money through OSS.
Next to that, since the Snowden releases from 2013, it has come clear that the NSA (and other intelligence agencies) will try everything to get into anyone's messages, devices, systems and so on. That's simply NOT okay.
Our devices should be OUR devices. No agency should be allowed to warrantless bypass our systems/messages security/encryptions for the sake of whatever 'national security' bullshit. Even a former NSA semi-director traveled to the UK to oppose mass surveillance/mass govt. hacking because he, himself, said that it doesn't work.
We should be able to communicate freely without spying. Without the feeling that we are being watched. Too badly, the intelligence agencies of today do not want us to do this and this is why mass surveillance/gag orders (companies having to reveal their users' information without being allowed to alert their users about this) are in place but I think that this is absolutely wrong. When we use end to end encrypted communications, we simply defend ourselves against this non-ethical form of spying.
I'm a heavy Signal (and since a few days also Riot.IM (matrix protocol) (Riot.IM with end to end crypto enabled)), Tutanota (encrypted email) and Linux user because I believe that only those measures (open source, reliable crypto) will protect against all the mass spying we face today.
The applications/services I strongly oppose are stuff like WhatsApp (yes, encryted messages but the metadata is readily available and it's closed source), skype, gmail, outlook and so on and on and on.
I think that we should OWN our OWN data, communications, browsing stuffs, operating systems, softwares and so on.
This was my rant.17 -
As a firm supporter of information security, it really "irks" me to see people get up and walk away form their desks without locking their machines... Anyone else with me on this?!18
-
Security rant ahead - you have been warned.
It never fails to amuse and irritate me that, despite being in the 2019 supposed information age, people still don't understand or care about their security.
I've travelled to a lot of ports and a lot of countries, but, at EVERY port, without fail, there will be at least one wifi that:
- Has default name/password that has been cracked already (Thomson/SpeedTouch/Netfaster etc)
- Has a phone number as password (reduces crack time to 15-30 mins)
- Someone, to this day, has plain old WEP
I am not talking about cafeteria/store wifi but home networks. WTF people?! I can check my email (through VPN, of course) but it still bugs me. I have relented to try and snoop around the network - I can get carried away, which is bad. Still...
The speed is great though :P9 -
Everyone in family and friends allways ask me "You're a programmer and know a lot about computer, so why you're not in Facebook/Twitter/Instagram?"
My answer: We create these services for you (average people) we don't use them ourselves. It's a security hole to put your information in public.7 -
Something I probably shouldn't talk about:
One of the projects at work has a specific path you can visit. The """security""" is that nobody should know the path. But I can guaran-fucking-tee you it's not difficult to guess.
On this page, ***without a login***, you can view some user information. Well, you can view all of it, but only certain fields.
And if you perform a specific action on this page, you can get their password, plaintext.
This project is not mine. But learning all of this made me super uneasy. I had to share it.14 -
A Month ago...
Me: when are you going to complete the report
Friend: we can do it in minutes
Me: you can't Ctrl + c and Ctrl +v as there is plagiarism check
Friend: we have spin bot
Me: you do that now itself . if something happens? You can join me .
Friend: just chill
Now ...
Me: done with report
Friend: feeding it to spin bot!
Feeds text related to database security....
Spin bot:
Garbage collector == city worker
SQL statements == SQL explanation
SQL queries == SQL interrogation
SQL injection == SQL infusion
Attack == assault
Malicious == noxious
Data integrity == information uprightness
Sensitive == touchy
.....
Me: told you so...
**spin not == article rewriter3 -
Paranoid Developers - It's a long one
Backstory: I was a freelance web developer when I managed to land a place on a cyber security program with who I consider to be the world leaders in the field (details deliberately withheld; who's paranoid now?). Other than the basic security practices of web dev, my experience with Cyber was limited to the OU introduction course, so I was wholly unprepared for the level of, occasionally hysterical, paranoia that my fellow cohort seemed to perpetually live in. The following is a collection of stories from several of these people, because if I only wrote about one they would accuse me of providing too much data allowing an attacker to aggregate and steal their identity. They do use devrant so if you're reading this, know that I love you and that something is wrong with you.
That time when...
He wrote a social media network with end-to-end encryption before it was cool.
He wrote custom 64kb encryption for his academic HDD.
He removed the 3 HDD from his desktop and stored them in a safe, whenever he left the house.
He set up a pfsense virtualbox with a firewall policy to block the port the student monitoring software used (effectively rendering it useless and definitely in breach of the IT policy).
He used only hashes of passwords as passwords (which isn't actually good).
He kept a drill on the desk ready to destroy his HDD at a moments notice.
He started developing a device to drill through his HDD when he pushed a button. May or may not have finished it.
He set up a new email account for each individual online service.
He hosted a website from his own home server so he didn't have to host the files elsewhere (which is just awful for home network security).
He unplugged the home router and began scanning his devices and manually searching through the process list when his music stopped playing on the laptop several times (turns out he had a wobbly spacebar and the shaking washing machine provided enough jittering for a button press).
He brought his own privacy screen to work (remember, this is a security place, with like background checks and all sorts).
He gave his C programming coursework (a simple messaging program) 2048 bit encryption, which was not required.
He wrote a custom encryption for his other C programming coursework as well as writing out the enigma encryption because there was no library, again not required.
He bought a burner phone to visit the capital city.
He bought a burner phone whenever he left his hometown come to think of it.
He bought a smartphone online, wiped it and installed new firmware (it was Chinese; I'm not saying anything about the Chinese, you're the one thinking it).
He bought a smartphone and installed Kali Linux NetHunter so he could test WiFi networks he connected to before using them on his personal device.
(You might be noticing it's all he's. Maybe it is, maybe it isn't).
He ate a sim card.
He brought a balaclava to pentesting training (it was pretty meme).
He printed out his source code as a manual read-only method.
He made a rule on his academic email to block incoming mail from the academic body (to be fair this is a good spam policy).
He withdraws money from a different cashpoint everytime to avoid patterns in his behaviour (the irony).
He reported someone for hacking the centre's network when they built their own website for practice using XAMMP.
I'm going to stop there. I could tell you so many more stories about these guys, some about them being paranoid and some about the stupid antics Cyber Security and Information Assurance students get up to. Well done for making it this far. Hope you enjoyed it. 26
26 -
Sometimes I wonder how compromised my parents online security would be without my intervention.
My mom logged into her gmail and there was an red bar on top informing about Google preventing an attempted login from an unknown device.
Like typical parents / old people, that red bar didn't caught her attention but I noticed it immediately. I took over and looked into it. It showed an IP address and a location that was quite odd.
I went ahead with the Account security review and I was shocked to find that she had set her work email address as the recovery email!!
I explained her that work email accounts cannot be trusted and IT department of the workplace can easily snoop emails and other info on that email address and should not be related to personal accounts.
After fixing that issue, me being a typical skeptic and curious guy, I decided to find more info about that IP address.
I looked up the IP address on a lookup website and it showed an ISP that was related to the corporate office of her workplace. I noticed the location Google reported also matched with the corporate office location of her work.
Prior to this event, few days ago, I had made her change her gmail account password to a more secure one. ( Her previous password was her name followed by birth date!! ). This must have sent a notification to the recovery mail address.
All these events are connected. It is very obvious that someone at corporate office goes through employees email addresses and maybe even abuse those information.
My initial skeptism of someone snooping throguh work email addresses was right.
You're welcome mom!9 -
Person: So what do you do for a living..
Me: (here we go)... I am an information security analyst working in an incident response team for x company. I do log collection and manage a large scale correlation engine.
Person: Oh, so are you super smart or something? (Blinks her eyes and continues with blank stare)
Me: Uh... Smart enough I guess.
Person: Can you hack things like a hacker.
Me: That really isn't my job...
Person: What's your job again?
Me: Computer guy
(She lights up)
Person: Why didn't you just say that? I can understand that.
Yeah... I seem to have painful conversations like this often.10 -
Can someone explain to me why the fuck I should even care about the fact, that some companies collect, use and sell my data? I'm not famous, I'm not a politician and I'm not a criminal, I think most of us aren't and won't ever be. We aren't important. So what is this whole bullshittery all about? I seriously don't get it and I find it somewhat weird that especially tech guys and IT "experts" in the media constantly just make up these overly creepy scenarios about big unsafe data collecting companies "stealing" your "private" information. Welcome to the internet, now get the fuck over it or just don't be online. It's your choice, not their's.
I honestly think, some of these "security" companies and "experts" are just making this whole thing bigger than it actually is, because it's a damn good selling point. You can tell people that your app is safe and they'll believe you and buy your shit app because they don't understand and don't care what "safe" or "unsafe" means in this context. They just want to be secure against these "evil monster" companies. The same companies, which you portrayed them as "evil" and "unfair" and "mean" and "unrepentant" for over a decade now.
Just stop it now. All your crappy new "secure" messenger apps have failed awesomely. Delete your life now, please. This isn't about net neutrality or safety on the internet. This is all about you, permanently exaggerating about security and permanently training people to be introverted paranoid egoistic shit people so that they buy your elitist bullshit software.
Sorry for my low english skills, but please stop to exist, thank you.64 -
Dear Australian Government and National Authorities, you can go fuck the right away with this shit!
It’s bad enough we are a country of national data collection with flimsy laws of obtaining access to said data, but to then go that one step further and shove back doors into everything is going too far.
https://news.com.au/technology/...
Under the proposed new laws, Australian government agencies could compel companies to provide technical information such as design specifications to help in an investigation, remove electronic protections, assist in accessing material on a device subject to a warrant and even build or install software or equipment that could help authorities gather information.
What could possibly go wrong 🤷♂️2 -
Devs: Hey, what should we do?
A:
provide our SDKs for download as easily as possible so that any potential customer can try it out and see how much better we are compared to our competitors?
Or…
B:
Should we lock our SDKs behind a login where the customer needs to create an account and enter the most amount of private information possible, just in case, then also require to create some security access tokens that he needs to configure in his app to have access to our service via the sdk and also hide all of the documentation behind a login which requires some permission based roles to access and also make the sdks closed source so that it’s a pain in the ass to debug and understand?
Marketing people:
B! Definitely B! Make sure to piss off and annoy our customers as much as humanly possible! -
- popunder background bitcoin miners did become a thing
- keybase android beta uploaded your privatekey to google servers "accidentally"
- you can spoof email headers via encoded chars, because most apps literally just render them apparently
- imgur leaked 1.7 million user accounts, protected by sha-256 "The company made sure to note that the compromised account information included only email addresses and passwords" - yeah "only", ofcourse imgur, ofcourse.
I guess the rant I did on Krahk etc. just roughly a month ago, can always be topped by something else.
sources:
https://www.mailsploit.com/index
https://bleepingcomputer.com/news/...
https://blog.malwarebytes.com/cyber...
https://helpnetsecurity.com/2017/... undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6
undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6 -
Classroom fuckery: I'm in a Computer Information Technology program and I usually spend the last hour of class working on code. Most of the people in this program are going into networking or security. This kid looks over and freaks out, starts yelling that I'm breaking into the school's network. I was on freecodecamp.com.5
-
This is the most hilarious stackoverflow rant ever, quote:
"Strong cryptography only means the passwords must be encrypted while the user is inputting them but then they should be moved to a recoverable format for later use."
Full rant:
http://serverfault.com/questions/...5 -
So I have seen this quite a few times now and posted the text below already, but I'd like to shed some light on this:
If you hit up your dev tools and check the network tab, you might see some repeated API calls. Those calls include a GET parameter named "token". The request looks something like this: "https://domain.tld/api/somecall/..."
You can think of this token as a temporary password, or a key that holds information about your user and other information in the backend. If one would steal a token that belongs to another user, you would have control over his account. Now many complained that this key is visible in the URL and not "encrypted". I'll try to explain why this is, well "wrong" or doesn't impose a bigger security risk than normal:
There is no such thing as an "unencrypted query", well besides really transmitting encrypted data. This fields are being protected by the transport layer (HTTPS) or not (HTTP) and while it might not be common to transmit these fields in a GET query parameter, it's standard to send those tokens as cookies, which are as exposed as query parameters. Hit up some random site. The chance that you'll see a PHP session id being transmitted as a cookie is high. Cookies are as exposed as any HTTP GET or POST Form data and can be viewed as easily. Look for a "details" or "http header" section in your dev tools.
Stolen tokens can be used to "log in" into the website, although it might be made harder by only allowing one IP per token or similar. However the use of such a that token is absolut standard and nothing special devRant does. Every site that offers you a "keep me logged in" or "remember me" option uses something like this, one way or the other. Because a token could have been stolen you sometimes need to additionally enter your current password when doings something security risky, like changing your password. In that case your password is being used as a second factor. The idea is, that an attacker could have stolen your token, but still doesn't know your password. It's not enough to grab a token, you need that second (or maybe thrid) factor. As an example - that's how githubs "sudo" mode works. You have got your token, that grants you more permissions than a non-logged in user has, but to do the critical stuff you need an additional token that's only valid for that session, because asking for your password before every action would be inconvenient when setting up a repo
I hope this helps understanding a bit more of this topic :)
Keep safe and keep asking questions if you fell that your data is in danger
Reeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee5 -
Red flags in your first week of your software engineering job 🚩
You do the first few days not speaking to anyone.
You can't get into the building and no one turns up until mid day.
The receptionist thinks you're too well dressed to work in this building, thinks you're a spy and calls security on you.
You are eating alone during lunch time in the cafeteria
You have bring your own material for making coffee for yourself
When you try to read the onboarding docs and there aren't any.
You have to write the onboarding docs.
You don't have team mates.
When you ask another team how things are going and they just laugh and cry.😂😭
There's no computer for you, and not even an "it's delayed" excuse. They weren't expecting you.
Your are given a TI PC, because "that's all we have", even though there's no software for it, and it's not quite IBM compatible.
You don't have local admin rights on your computer.💀
You have to buy a laptop yourself to be able to do your job.
It's the end of the week and you still don't have your environment set up and running.
You look at the codebase and there are no automated tests.
You have to request access every time you need to install something through a company tool that looks like it was made in 2001.
Various tasks can only be performed by one single person and they are either out sick or on vacation.
You have to keep track of your time in 6 minute increments, assigned to projects you don't know, by project numbers everyone has memorised (and therefore aren't written down).
You have to fill in timesheets and it takes you 30 minutes each day to fill them in because the system is so clunky.🤮
Your first email is a phishing test from the IT department in another country and timezone, but it has useful information in it, like how to login to the VPN.
Your second email is not a phishing test, but has similar information as the first one. (You ignore it.)
Your name is spelled wrong in every system, in a different way. 2 departments decide that it's too much trouble, and they never fix the spelling as long as you work there. One of them fixes it after you leave, and annoys you for a month because you haven't filled out the customer survey.5 -
This isn’t gonna be a random because I do eventually get to a Tech and YouTube related topic.
YouTube is actually killing itself with all of the dumbass rules they’re implementing. Trying to child proof or limit educational content is genuinely a shit policy. The reason so many gaming channels are switching to twitch because it doesn’t try to censor you.
But now I don’t know if you’ve heard but YouTube updated their guidelines and they’re no longer allowing content that teaches people about Hacking essentially (and I hate putting it like that but I can’t remember the exact words they used Hacking just summarizes it) which is fucking ridiculous like what the fuck else, are they gonna stop allowing lock picking videos?
YouTube has always been an amazing FREE resource for people learning Programming, Cyber Security, IT related fields, and even shit like lock picking, cooking, car stuff, and all that stuff. Even sometimes when the tutorials aren’t as detailed or helpful to me they might be exactly what someone else needed. And Cyber Security can be a difficult topic to learn for free. It’s not impossible far from it, but YouTube being there was always great. And to think that a lot of those could be taken down and all of the Security based channels could either lose all revenue or just be terminated is terrifying for everyone but more so them.
A lot of people and schools rely on YouTube for education and to learn from. It’s not like YouTube is the only resource and I understand they don’t want to be liable for teaching people that use these skills for malicious purposes but script kiddies and malicious people can easily get the same knowledge. Or pay someone to give them what they want. But that’s unfair to the people that don’t use the information maliciously.
It’s the same for the channels of different topics can’t even swear and it’s ridiculous there’s so many better options than just banning it. Like FUCK kids nowadays hear swearing from their older siblings, parents, friends, and TV it’s inevitable whether someone swears or not and YouTube is not our parents, they aren’t CBS, so stop child proofing the fucking site and let us learn. Fuck.
TLDR YouTube is banning educational hacking videos and are being retarded with rules in general16 -
Long rant ahead.. 5k characters pretty much completely used. So feel free to have another cup of coffee and have a seat 🙂
So.. a while back this flash drive was stolen from me, right. Well it turns out that other than me, the other guy in that incident also got to the police 😃
Now, let me explain the smiley face. At the time of the incident I was completely at fault. I had no real reason to throw a punch at this guy and my only "excuse" would be that I was drunk as fuck - I've never drank so much as I did that day. Needless to say, not a very good excuse and I don't treat it as such.
But that guy and whoever else it was that he was with, that was the guy (or at least part of the group that did) that stole that flash drive from me.
Context: https://devrant.com/rants/2049733 and https://devrant.com/rants/2088970
So that's great! I thought that I'd lost this flash drive and most importantly the data on it forever. But just this Friday evening as I was meeting with my friend to buy some illicit electronics (high voltage, low frequency arc generators if you catch my drift), a policeman came along and told me about that other guy filing a report as well, with apparently much of the blame now lying on his side due to him having punched me right into the hospital.
So I told the cop, well most of the blame is on me really, I shouldn't have started that fight to begin with, and for that matter not have drunk that much, yada yada yada.. anyway he walked away (good grief, as I was having that friend on visit to purchase those electronics at that exact time!) and he said that this case could just be classified then. Maybe just come along next week to the police office to file a proper explanation but maybe even that won't be needed.
So yeah, great. But for me there's more in it of course - that other guy knows more about that flash drive and the data on it that I care about. So I figured, let's go to the police office and arrange an appointment with this guy. And I got thinking about the technicalities for if I see that drive back and want to recover its data.
So I've got 2 phones, 1 rooted but reliant on the other one that's unrooted for a data connection to my home (because Android Q, and no bootable TWRP available for it yet). And theoretically a laptop that I can put Arch on it no problem but its display backlight is cooked. So if I want to bring that one I'd have to rely on a display from them. Good luck getting that done. No option. And then there's a flash drive that I can bake up with a portable Arch install that I can sideload from one of their machines but on that.. even more so - good luck getting that done. So my phones are my only option.
Just to be clear, the technical challenge is to read that flash drive and get as much data off of it as possible. The drive is 32GB large and has about 16GB used. So I'll need at least that much on whatever I decide to store a copy on, assuming unchanged contents (unlikely). My Nexus 6P with a VPN profile to connect to my home network has 32GB of storage. So theoretically I could use dd and pipe it to gzip to compress the zeroes. That'd give me a resulting file that's close to the actual usage on the flash drive in size. But just in case.. my OnePlus 6T has 256GB of storage but it's got no root access.. so I don't have block access to an attached flash drive from it. Worst case I'd have to open a WiFi hotspot to it and get an sshd going for the Nexus to connect to.
And there we have it! A large storage device, no root access, that nonetheless can make use of something else that doesn't have the storage but satisfies the other requirements.
And then we have things like parted to read out the partition table (and if unchanged, cryptsetup to read out LUKS). Now, I don't know if Termux has these and frankly I don't care. What I need for that is a chroot. But I can't just install Arch x86_64 on a flash drive and plug it into my phone. Linux Deploy to the rescue! 😁
It can make chrooted installations of common distributions on arm64, and it comes extremely close to actual Linux. With some Linux magic I could make that able to read the block device from Android and do all the required sorcery with it. Just a USB-C to 3x USB-A hub required (which I have), with the target flash drive and one to store my chroot on, connected to my Nexus. And fixed!
Let's see if I can get that flash drive back!
P.S.: if you're into electronics and worried about getting stuff like this stolen, customize it. I happen to know one particular property of that flash drive that I can use for verification, although it wasn't explicitly customized. But for instance in that flash drive there was a decorative LED. Those are current limited by a resistor. Factory default can be say 200 ohm - replace it with one with a higher value. That way you can without any doubt verify it to be yours. Along with other extra security additions, this is one of the things I'll be adding to my "keychain v2".10 -
Our security auditor is an idiot. How do I give him the information he wants?
http://serverfault.com/questions/...4 -
Wow! Google's update in its privacy policy is impressive. Still too lazy to read it though. I trust Google. LOL5
-
105 pages of information security policy to read through before getting through onboarding that could have been summarized as: "This is 2022. Don't be an idiot."
Also 40 pages of code of conduct that could have been summarized thusly: "This is 2022. Everyone is offended by everything. Shut your cakehole, put your head down, don't make eye contact, and just do your job."3 -
!dev
There’s this person at $work who never uses punctuation of any kind. She has mental issues and insists on neutral pronouns (and strongly advertises these) so I’ll use the indefinite to pretend to be respectful. It has multiple thoughts while typing a message and just keeps typing through all of them without stopping. It pauses not to collect its thoughts, to edit for clarity or to fix mistakes, to separate anything (including disjoint topics), to summarize, etc. (Though calling these “thoughts” is a huge stretch, given its lack of propensity for that particular subject.) It’s as if it has zero distinction between writing and speaking, and simply lets the mental diarrhea flow while their fingers do their best to keep pace. Reading these trainwrecks of thought — and gleaning any useful information from them — is always difficult and a little bit painful.
It is also in charge of IT security, which is more than a bit worrying. (But I hate the company with a passion, so it doesn’t bother me nearly as much as it otherwise would.)37 -
Howdy this is a daily reminder on why you can't trust anyone with shared information.
I am back home from uni for the holidays and like any computer person who is back in town became responsible for fixing every tech problem that has occurred since my last visit. But what caught my eye when I approached the family computer is not the problem with the computer itself, it's the paper in front of the computer that, in giant lettering, has not only the passwords and account names of my mom and brother's AOL (She's old ok) and FAFSA account respectively but also someone's social security number. Any goddam baffoon who looks through the window or is able to take literally three goddam steps past the front door now has enough information to commit identity theft or just take over one of their accounts. I know it's not that likely but I still had a heart attack when I saw that.
How badly have I failed them?1 -
Google was hiring till the last week. If you didn't apply, don't worry. They already has all your information. They will call you if they like you.6
-
What you are expected to learn in 3 years:
power electronics,
analogue signal,
digital signal processing,
VDHL development,
VLSI debelopment,
antenna design,
optical communication,
networking,
digital storage,
electromagnetic,
ARM ISA,
x86 ISA,
signal and control system,
robotics,
computer vision,
NLP, data algorithm,
Java, C++, Python,
javascript frameworks,
ASP.NET web development,
cloud computing,
computer security ,
Information coding,
ethical hacking,
statistics,
machine learning,
data mining,
data analysis,
cloud computing,
Matlab,
Android app development,
IOS app development,
Computer architecture,
Computer network,
discrete structure,
3D game development,
operating system,
introduction to DevOps,
how-to -fix- computer,
system administration,
Project of being entrepreneur,
and 24 random unrelated subjects of your choices
This is a major called "computer engineering"4 -
FUCK!
After submitting a registration form I noticed the site is served over plain HTTP. Their marketing site is served encrypted, but login and register are not! What the fuck!!!
Fuck everyone who does this stupid fucking shit with disregard to basic security features! Their goddamn bullshit privacy policy is bragging about how it's top priority to protect their customers' information and shit like that. Get the fuck out, cunts!!
I contacted them so I might have a continuation to this rant if I'm not satisfied with their answers.
Goddamn it!3 -
I know folks do their best, but come on Apple, this can't be that hard. Bought an IPhone at an estate sale (elderly individual died suddenly, so no one had knowledge of the apple id, passwords, etc) and I've been trying to convince apple to clear the activation lock. (AS = Apple Support)
<after explaining the situation>
AS: "Have you tried putting the phone in recovery mode? That should clear the lock"
Me: "I've already done that. It prompts for the apple id and password, which I don't have"
AS: "You need to talk to the owner and get the information"
Me: "As I explained, I purchased the phone at an estate sale of someone who died. I have the bill of sale, serial number, the box, obituary. What else do you need?"
AS: "Have you tried contacting a family member? They might have have that information."
Me: "The family members at the sale told us this is all they had. This kind of thing has to happen. I can't believe Apple can't clear the activation lock."
AS: "Yes, we can, but I'm very sorry we take security seriously."
Me: "I understand, what do I do now?"
AS: "Did you log out of the phone? Go to settings ..."
Me: "Yes, I tried all those steps before calling. It prompts for the AppleID and password."
AS: "Did you try entering the password?"
Me: "No, I don't have it. I already explained there is no way to know"
AS: "Yes..yes...sorry...I'm just reading the information in front of me. I found something, have you tried submitting a activation lock removal request?"
Me: "Yes, it was denied, didn't tell me why, which is why I'm calling. What about taking this phone to an Apple store? I have all the paperwork."
AS: "Sure, you can try. You might need the death certificate. The family or the coroner will have a copy."
Me: "What!? Apple requires a death certificate to unlock a phone!? I'm pretty sure not even the family is going to give a total stranger a death certificate"
AS: "Sorry sir, I'm just reading what is in front of me. Without that certificate, there is no way to prove the person died. You can try the Apple store, but they will likely require it."
Me: "That's a lot of drama for unlocking a phone. A *phone*"
AS: "Yes sir, I understand. If there anything else we can do let us know and thank you for being an a apple customer."
Next stop, the Apple Store.9 -
First it was the "set up WampServer so the client can use our database", to which I told her we should use an embedded database, to which she told me to do.
Then the "Just give the client a .jar file and install the JRE in his laptop" to wich I told her we can make a native installer, to which she fucking assigned to me.
Then the whole fucked up management thing with no design whatsoever and the "we don't need version control".
To just a few hours earlier, when she got mad because I set up a Slack for us to exchange information easily, she told me she was already mad because I shared the project by Google Drive and that she worked in security and knows the risk... AND AT THE SAME TIME, she uses Gmail to share the project.. BRILLIANT !7 -
Security fail here. I've just started a PPI claim and have been provided a link to a so called "very secure" client area.
There are no username or passwords and the screenshot is not a first time sign up screen.
All I need to login is a surname, postcode and DOB - all information easy enough to find online.
Pretty bad IMO, esp, so considering the effort required to add a proper login using a username/password combination.
I mean I'm logged in now and have no option to set an account password :| 3
3 -
Because I own http://grnail.co.uk and http://hotrnail.co.uk (which I bought to prevent scammers having access to them), I often get emails about peoples' accounts. I could do a password reset and own these accounts, but of course, I don't.
However, today I started getting passport scans and personal details from Syria... 2
2 -
was applying to college when i saw “enter social security number (optional)”
yes ok, i’d also love to give you my bank account information, address, and birth certificate. anything you need!!!17 -
Me: I'm a computer major along with an added specialisation in Information Security. So besides learning code and software development, we also do a variety of security related stuff like penetration testing and so on.
Others: Oh great that means you must know how to hack Facebook.
*makes me flip every time*6 -
*follow-up to https://devrant.com/rants/1887422*
The burnt remnants of my ID card's authentication information, waiting for the wind to come pick it up. It's stored in my password database now and committed to my git server, as it should be. Storing PIN and PUK codes on paper, whatever government cunt thought thought that that was a good idea...
If you've got identification papers containing authentication information like PIN and PUK codes, by all means add them to your password manager (if you're using Linux, I'd like to recommend GNU Pass) at once and burn the physical version. There's no reason why you'd want those on paper, unless you store your passwords on a post-it too.
At least that's as much as me and possibly you as citizens can do. Our governments are doomed anyway, given the shitty security policy they have, and likely the many COBOL mainframes still in use today. Honestly, the meddlings of Russia with the US elections doesn't seem too far-fetched, given this status quo. It actually surprises me that this kind of stuff doesn't happen more often, given that certain governments hire private pentesters yet can't secure their own infrastructure.
-
Someone wanted me to make a full system from zero with good UI/UX, for 2 different user types (think marketplace style), admin area, and cool features that could only be done through phones because the tech is not available in web. All of this with good security due to the delicate information it would handle. Also of course subscription support as well.
By myself, within a year.6 -
Oh boy I got a few. I could tell you stories about very stupid xss vectors like tracking IDs that get properly sanitized when they come through the url but as soon as you go to the next page and the backend returns them they are trusted and put into the Dom unsanitized or an error page for a wrong token / transaction id combo that accidentally set the same auth cookie as the valid combination but I guess the title "dumbest" would go to another one, if only for the management response to it.
Without being to precise let's just say our website contained a service to send a formally correct email or fax to your provider to cancel your mobile contract, nice thing really. You put in all your personal information and then you could hit a button to send your cancelation and get redirected to a page that also allows you to download a pdf with the sent cancelation (including all your personal data). That page was secured by a cancelation id and a (totally save) 16 characters long security token.
Now, a few months ago I tested a small change on the cancelation service and noticed a rather interesting detail : The same email always results in the same (totally save) security token...
So I tried again and sure, the token seemed to be generated from the email, well so much about "totally save". Of course this was a minor problem since our cancelation ids were strong uuids that would be incredibly hard to brute force, right? Well of course they weren't, they counted up. So at that point you could take an email, send a cancelation, get the token and just count down from your id until you hit a 200 and download the pdf with all that juicy user data, nice.
Well, of course now I raised a critical ticket and the issue was fixed as soon as possible, right?
Of course not. Well I raised the ticket, I made it critical and personally went to the ceo to make sure its prioritized. The next day I get an email from jira that the issue now was minor because "its in the code since 2017 and wasn't exploited".
Well, long story short, I argued a lot and in the end it came to the point where I, as QA, wrote a fix to create a proper token because management just "didn't see the need" to secure such a "hard to find problem". Well, before that I sent them a zip file containing 84 pdfs I scrapped in a night and the message that they can be happy I signed an NDA.2 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
Who's the dumbass that decided you can't delete your PayPal account at all unless your balance is $0?
I am not giving you my card information for the $0.18 balance I have. For God sakes, I don't even bend over to pick that up if I see it on the ground.
It's one thing if it were like $100 or even $10. But it's eighteen fucking cents. Not even a a quarter of a fucking dollar.
At least make me put in my password and answer a security question or some shit, not straight up remove the option to delete it.
Fucking ridiculous.21 -
Google Maps put me on the other side of the freeway, so rushing to get there I was stopped by a security guard who told me to slow down and directed me to a spot. I hit the car next to me, I then interviewed and exchanged insurance information with the other car's owner. I went to school to defend my capstone and got the offer. A year later I sat next to the guy whose car I hit.
-
Every week in my intro to information security class we are asked about what security stuff has gone down in the past week. Equifax is making it incredibly easy to not have to do much research.1
-
Course title: Advanced Database Management
Course Objectives:
-Create a database with SQL.
-Describe data normalization of database information.
-Describe distributed database management system.
-Design databases based on Entity Relationship modeling.
-Discuss connecting to databases with server-side scripts.
-Discuss database administration and security.
-Discuss database systems
Like. Come. On.7 -
Social Captain (a service to increase a user's Instagram followers) has exposed thousands of Instagram account passwords. The company says it helps thousands of users to grow their Instagram follower counts by connecting their accounts to its platform. Users are asked to enter their Instagram username and password into the platform to get started.
According to TechCrunch : Social Captain was storing the passwords of linked Instagram accounts in unencrypted plaintext. Any user who viewed the web page source code on their Social Captain profile page could see their Instagram username and password in plain text, as they had connected their account to the platform. A website bug allowed anyone access to any Social Captain user's profile without having to log in ; simply plugging in a user's unique account ID into the company's web address would grant access to their Social Captain account and their Instagram login credentials. Because the user account IDs were for the most part sequential, it was possible to access any user's account and view their Instagram password and other account information easily. The security researcher who reported the vulnerability provided a spreadsheet of about 10,000 scraped user accounts to TechCrunch.3 -
Specifications called for user logins to be stored in a session and not be persistent. When the session ends, you need to login again. The system deals with insurance policy information and persistent login was deemed a security risk.
First ticket submitted by the client after go-live? "Please make the login page remember my user name and password, or that I've logged in previously."2 -
I don't know why is that everytime you guys find a security bug or a data leak or that someone is saving plain passwords on their database, you try to cover and censor the company name. Listen people, fuck the company and their name and their brand if someone's data might be in danger. Everybody should be aware of what is happening with their personal information.
Also, maybe would be great if devRant would let users to post anonymous rants for this kind of issues or a special thread with latest news about our online security.3 -
I've written a rant that was too long to devRant, so I made it into a medium article instead. You can read it here:
https://medium.com/bambuu/...
In short, it's about Apple's weird legal practices when it comes to Apple Developer accounts.
tl;dr
- Apple has "obvious" security reasons that requires a copy of a photo id, and you aren't allowed to conceal sensitive information
- Apple's favorite form of communication is fax and snail mail
- Apple needs multiple signatures and court documents to just change your account name. -
Microsoft Manager: "We need to slap ChatGPT onto Bing....STAT!"
Devs: "There won't be enough time to test security."
Microsoft Manager: *Throws hands in the air* "Who cares!!?? Just get it done!"
Devs: "Ok, boss."
https://arstechnica.com/information...4 -
Oh my fucking god. Austria wants to sell the data of it's citizens to schools, universities museums, and: Companies with enough money. What the fuck?
The data contains shit from the central register of residents, information about name, date of birth, sex/gender, nationality, recidence, health data (!), education, social security/insurance, tax data, E-Card/ELGA Data (system where your doctor visits, prescribed medicines/drugs, all these things, are saved), and other shit.
Welcome to 2018, where you can try as hard as you want to keep your privacy, and then your government sells all the shit you are not able to remove. Fucking bullshit.9 -
In this era, information is much more precious than money itself.
I'm not saying that information wasn't as important back in the days. It's just, at present gathering information is much easier than it ever was!! Especially on people who spend more time on mobiles phones and computers.
Formally stated, Newton's third law is: For every action, there is an equal and opposite reaction. As we're consuming information continuously, going through so many webpages, laughing at menes that are relatable and using apps that we need to perform day to day task. We're also providing information that we don't realize doing. This adds up to determining out individual personality.
One can never be too careful to prevent all these, but we can still minimize the damage.2 -
A few years ago, i had a task to implement a webservice of an insurance-company into our .NET Development.
The security requirements of this insurance-company webservice were top notch.
As a client you had to build a request that used a negotiated certificate, canonical header structures, security timestamp, a secret token in header, ...
To configure all this stuff via web.config WCF was pure pain in the ass.
After many phonecalls and emails, i finally managed to meet all security requirements to send a valid request.
First, i didn't recognized my breakthrough, because my client still had thrown exceptions while calling the insurance-webservice.
Why was that?
The exception told me on the most possible gentle way, that .Net isn't able to process an unsecured response, when there was a secured request before.
So there was top notch security for requesting, but dumbass unsecured responding with all the precious customer information.
*epicfacepalmnuclearexplosionfollowing*
I even had to raise the. Net Version of our. Net client, because i wasn't able to configure that it is allowed to process an unsecured response after using a secured request.
Whyyyyyyy?!!?!!1el even!?! -
PayPal = GayPal
PHASE 1
1. I create my personal gaypal account
2. I use my real data
3. Try to link my debit card, denied
4. Call gaypal support via international phone number
5. Guy asks me for my full name email phone number debit card street address, all confirmed and verified
6. Finally i can add my card
PAHSE 2
7. Now the account is temporarily limited and in review, for absolutely no fucking reason, need 3 days for it to be done
8. Five (5) days later still limited i cant deposit or withdraw money
9. Call gaypal support again via phone number, burn my phone bill
10. Guy tells me to wait for 3 days and he'll resolve it
PHASE 3
11. One (1) day later (and not 3), i wake up from a yellow account to a red account where my account is now permanently limited WITHOUT ANY FUCKING REASON WHY
12. They blocked my card and forever blocked my name from using gaypal
13. I contact them on twitter to tell me what their fucking problem is and they tell me this:
"Hi there, thank you for being so patient while your conversation was being escalated to me. I understand from your messages that your PayPal account has been permanently limited, I appreciate this can be concerning. Sometimes PayPal makes the decision to end a relationship with a customer if we believe there has been a violation of our terms of service or if a customer's business or business practices pose a high risk to PayPal or the PayPal community. This type of decision isn’t something we do lightly, and I can assure you that we fully review all factors of an account before making this type of decision. While I appreciate that you don’t agree with the outcome, this is something that would have been fully reviewed and we would be unable to change it. If there are funds on your balance, they can be held for up to 180 days from when you received your most recent payment. This is to reduce the impact of any disputes or chargebacks being filed against you. After this point, you will then receive an email with more information on accessing your balance.
As you can appreciate, I would not be able to share the exact reason why the account was permanently limited as I cannot provide any account-specific information on Twitter for security reasons. Also, we may not be able to share additional information with you as our reviews are based on confidential criteria, and we have no obligation to disclose the details of our risk management or security procedures or our confidential information to you. As you can no longer use our services, I recommend researching payment processors you can use going forward. I aplogise for any inconvenience caused."
PHASE 4
14. I see they basically replied in context of "fuck you and suck my fucking dick". So I reply aggressively:
"That seems like you're a fraudulent company robbing people. The fact that you can't tell me what exactly have i broken for your terms of service, means you're hiding something, because i haven't broken anything. I have NOT violated your terms of service. Prove to me that i have. Your words and confidentially means nothing. CALL MY NUMBER and talk to me privately and explain to me what the problem is. Go 1 on 1 with the account owner and lets talk
You have no right to block my financial statements for 180 days WITHOUT A REASON. I am NOT going to wait 6 months to get my money out
Had i done something wrong or violated your terms of service, I would admit it and not bother trying to get my account back. But knowing i did nothing wrong AND STILL GOT BLOCKED, i will not back down without getting my money out or a reason what the problem is.
Do you understand?"
15. They reply:
"I regret that we're unable to provide you with the answer you're looking for with this. As no additional information can be provided on this topic, any additional questions pertaining to this issue would yield no further responses. Thank you for your time, and I wish you the best of luck in utilizing another payment processor."
16. ARE YOU FUCKING KIDDING ME? I AM BLOCKED FOR NO FUCKING REASON, THEY TOOK MY MONEY AND DONT GIVE A FUCK TO ANSWER WHY THEY DID THAT?
HOW CAN I FILE A LAWSUIT AGAINST THIS FRAUDULENT CORPORATION?9 -
Once upon a time, there was a young, clean-shaven dev.
Soon in his career the smooth faced dev realized he had a knack for cloud setup. He understood permissions and network configurations, he could tell apart security groups from access groups, he could get all the information needed for an IPSec VPN in a single breath.
But if things got really tough, if the network layout was really messy, if the security settings too arcane, some older, bearded senior dev would come to solve everything.
Time passed, the junior dev got better at stuff, switched companies many times, solved a million problems, delivered countless projects, attended infinite meetings - twice - and, as often is the case, the senior devs, one by one, left the companies and run ever more scarce each day.
One day, a long, loooong time after his first meeting, the once young dev was solving network problems. Weird ones. Tough security requirements. Poorly documented cloud services. For hours, the dev and his colleagues toiled away, chipping at the problem without getting at its core.
The silence fell in the meeting. Everybody looking at each other, waiting for someone to say something.
Then they all looked at the dev, their eyes crying for help.
And the dev realized that he hadn't shaved in weeks.
-------‐‐-------------------------------
I've shaved since then.
And I did solve the problem. Took many more hours, though. -
This codebase had 50+ main() functions and 80+ Material App. 5 of them are nested MaterialApp
Redundant widgets, security leaks, and print Sensitive information from the server to console without using (kDebugMode), therefore in prod, the data are leaked.
I refactored until I screamed.
So I left a gift inside.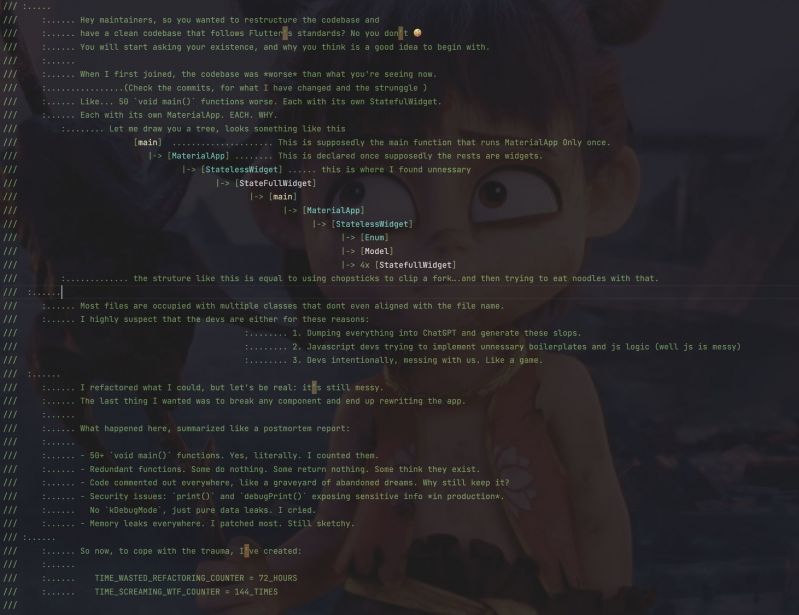 14
14 -
Dev industry develop so fast. This is because information available anywhere in the internet and people try to learn any programming language they want . But only few know whether they following secure coding practice or not
But the thing is most of Dev people dosent care about security. They focus just to develop a application but not to secure it?2 -
This isn't something I've dealt with personally, but recently heard the story on the podcast and was pretty astounded:
"A company who makes add-ons for Flight Simulator X included malware in one of their downloadable jets, players have alleged. The malicious file is called ‘test.exe’ and it is designed to extract passwords from the Chrome web browser."
Now that's some extreme DRM. "Pirate our downloadable jet? We leak your credit card information and Social Security Number to the darknet."
Original story: https://rockpapershotgun.com/2018/...3 -
got first assignment on my first meet on Network Security. it require to pentest one unsecured specified website. yet they don't tell me shit about anything just try it.
i need to :
1. Footprint
2. Scanning
3. Enumeration
4. Gaining Access (previledges raising?) (bonus)
suppose : <target-website> is x
i've done this:
1. whois x
2. got the ipaddress via :
host x
3. nmap -F ip.of.x
my head is already spinning, i need to know what BASICLY each of what i've done. i only get that 'whois' get the information about that domain, 'host' is used to know the target ip address and nmap to find what are the open ports. i don't know what else should i do. need help :(13 -
Working at a local seo sweat-shop as "whatever the lead dev does't feel like doing" guy.
Inherit their linux "server".
- Over 500 security updates
- Everything in /var/www is chmod to 777
- Everything in /var/www is owned by a random user that isn't apache
- Every single database is owned by root sql user
- Password for sudo user and mysql root user same as wifi password given to everyone at company.
- Custom spaghetti code dashboard with over 400 files in one directory, db/ api logins spread throughout these files, passwords in plain text.
- Dashboard doesn't have passwords, just usernames to login
- Dashboard database has all customer information including credit card stored in plain text
- Company wifi is shared by other businesses in the area
I suggest that I should try to fix some of these things.
Lead Developer / Tech Director : We're an SEO company, not a security company . . .7 -
I took a bit of a break from devRant because I was way too disgruntled at my current position. Flash forward and I am now a manager at the same company.
Note to new devs:
Make waves, make tons of waves. Get the attention of your superior’s superiors by making things better. Never rely on your superior relaying information, they only have their job security in mind. -
Screw all the people who think standard email is "secure". It is not suitible for sending passwords and SSN numbers.
How can something Equifax or Marriott hacks have happened and people are still ok sending out information like this in plain text?!
I know their hacks weren't email released but still.....should be a good time to up some security standards. Right?2 -
Legal Question regarding E-Commerce / Credit Card Payments.
The User sends his Credit Card Information (number/expiration Date/Safety Number) over email to vendor. Vendor types this info from the email into a Credit Card Terminal.
Is this even legal? I thought when listing Credit Card Payment you have to use a PSP (Payment Service Provider) that conforms to the security regulations etc.7 -
Did you ever had to integrate a fucking "API" that is done via mail bodies?
Fuck this shit! Who need responses about success or failure?! Guess this will take a long time to test this fucking piece of garbage... We don't get a test system, we need to test this with the production system of the other company. I hope their retarded application crashes when receiving malicious mails.
Not speaking about security, I bet everyone can send a mail to their stupid mail address and modify their data 🙈
And inside of this crap mail you also have to send the name, street and email of their company. Why do you fucking need this information?!1 -
What makes free ssl "Unsuitable for e-commerce websites", Please read to end to see my view point.
From Namecheap:
Free Certificates are domain validation only which means they don't certify the identity of the website owner, they simply ensure a secure connection. Customers can't be sure of the integrity and trustworthiness of the website owner. If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer. It's important your customers trust your business is safe enough to hand over these details. To gain this trust, you need a certification of your authenticity, which you can only get with a (paid) Business Validation or Extended Validation SSL Certificates.
https://namecheap.com/security/...
* "To gain this trust, you need a certification of your authenticity"
~ But isn't that just Domain Verification and other Extras, What justifies somebody or business's authenticity? Tax Id, Valid Address, Nobody is going to study the ssl cert to make sure that amazon.com is a valid business and has a tax Id.
* "domain validation only which means they don't certify the identity of the website owner,"
~ Wouldn't this just be the domain validation test that is required when using services like LetsEncrypt using Certbot etc, or are we referencing back to this idea that they look for a Valid Tax Id sort of thing?
* "If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer"
~ Why is the paid version going to do double encryption, is the CA going to run a monitoring tool to scan for intrusions like a IDS or IPS? (disregard the use of DNS Validation being in the picture)
Am I missing something, this just seems like well crafted text to get people to buy a cert, I could understand if the encryption was handled differently, Maybe if they checked the site for HSTS or HTTPs Redirect or even, They blocked wildcard SSL before and now with the paid its included, but overall it doesn't sound like anything special. Now I'm not just picking on namecheap because domain.com does the same.14 -
Learning information security yet again after doing multiple information security things for company and manager is pushing to do it saying "due immediately" and they're after sending "a number of emails" (it's due in a month and they sent 1 email).
Annoying that these things must be done again and again just because someone in sales let something slip or left their journal behind like a dumb dumb. It's not like I'm never off-site with my stuff or I interact with customer(s) yet1 -
Trustico CEO emailed private key which is used to sign TLS certificates, making more than 23k certificates compromised!
This makes me think, that we should not trust others for our security (like ca), failure of CA can put our website at risk. What is the better way to do it?
https://arstechnica.com/information...11 -
I just got a project that is already developed by a team. It is already in the production and guess what!! They are storing customer’s credit card details in the database 🥸🥸12
-
So the contract for this big project with a client has some interesting content in it. I'm not sure if I can sign this in good faith.
Because I seem to be lacking guard dogs and a receptionist at my home office. Maybe I could build a force field for them.
And I'm not really looking forward towards having all my friends sign a document every time they visist.
5 PHYSICAL SECURITY
5.1 Adequate physical security perimeters (e.g. fences, walls, barriers, guards, gates, electronic surveillance, physical authentication mechanisms, reception desks and security patrols) shall be implemented to safeguard Information and information systems.
5.2 Supplier shall have a documented visitor policy and all visitors must be identified, registered, logged, and accompanied by an employee from Supplier.2 -
When a junior develops an API call which return the user information and there is session_key and password encrypted in it too.
Dude! do you even know some basic security ! Please don't just Select * From table join table only !3 -
Just as I had been discussing information security here on devRant, Facebook reminded me of an article I posted a year ago.
http://makeuseof.com/tag/...
Makes me wonder if Facebook's iOS app is keylogging me. Not long ago I was having a conversation at work with a coworker on a topic of a product I know for certain I had never, ever searched for online. Just after we ended the conversation, I launched my Twitter app and, lo and behold, there was an ad for that exact product on my feed. -
Question - my field is information security (or cyber security if you want to think of me as a time lord), but I wanted to know;
Front end and back Devs, how much time do you spend on security issues and/or implementing security measures?9 -
Do you still charge your clients extra for HTTPS being it’s practically a requirement now for SEO purposes?6
-
What makes WhatsApp not privacy friendly? They don't state that they share contact information and only statistical stuff (App last opened, etc.) Which is marketing, but not really bad. And they use end to end encryption.
By the way, this here is there Whitepaper on end to end encryption. But haven't read through it yet. https://whatsapp.com/security/...15 -
In highschool right now and I'm seriously interested in network and information security. I recently managed to work out possible internships at some top security firms based out of sweden. I am super stoked and am excited to see the pros work. Might be interesting.
-
Google researchers have exposed details of multiple security flaws in Safari web browser that allowed user's browsing behavior to be tracked.
According to a report : The flaws which were found in an anti-tracking feature known as Intelligent Tracking Prevention, were first disclosed by Google to Apple in August last year. In a published paper, researchers in Google's cloud team have identified five different types of attacks that could have resulted from the vulnerabilities, allowing third parties to obtain "sensitive private information about the user's browsing habits."
Apple rolled out Intelligent Tracking Prevention in 2017, with the specific aim of protecting Safari browser users from being tracked around the web by advertisers and other third-party cookies.2 -
Having a meeting with an old client of our company's today, guiding him through the deployment process for his front and backend, because he thought that we were withholding information, and at one point in the call he asks me if the './' at the beginning of the deployment script was a special security measure put in place by us... 😂
-
How should you approach someone and tell them they have been an victim of social engineering without being mean?
I was at an security conference today and watched a lot of speaks, and I must say that the atmosphere and the people around made it even better.
Here is one takeaway:
Does the security of IT has to be this depressing most of the time, like there is so many IoT devices, services, websites and critical infrastructure that has security flaws and all we can do is watch for now and say we are all fucked. Then try to lead the industry to better practices, like owasp (duck it) . Stop accepting and using shitty answers from SO that has security flaws (why learn something a way that is wrong in the first place?).
We need more awareness about IT security overall, how can one developer know that certain technologies can have certain vulnerabilities such as XSS, XSRF and even SQL injection if there is no information about it in among all shitton tutorials, guides and SO answers in the first place?
Lighten up! Being sad and depressing about these issues is not the best way to approach this! We need to embrace all steps taken towards better security, even the smallest ones.
Check out OWASP if you are not familiar :
https://owasp.org/index.php/...
Thanks for reading. -
Gah, I just received this Ubuntu 18.04 VM with 8 cores and 8 gigs of ram, and since it'll be a production server both serving public and "private" networks (yes, shout at me, but projects won't be about hosting sensitive information, I wouldn't put all that on one server), and I'm struggling between my options.
Docker, or not docker?
The server's main use is to host our growing blog and install Varnish, which will hog some ram after a while. I use Laradock for my dev projets, it's really easy to develop with it, but I am unsure if it fits a production environment with performance, security and traffic load in mind :(
I read Docker has stability issues (in 2016-2017), and can bring the machine down with it, I don't know if I should just install the software (nginx, apache, percona/mysql/maria) without "containerizing" it and go for it
I'm lost xD7 -
Three Layers of Security
As InfoWorld notes, all smartphones have three basic
elements of security. Your first major task as a mobile
user is to become aware of these layers and enable them
in your devices:
1. Device Protection: Allowing remote data "wiping" if your
device is ever lost or stolen.
2. Data Protection: Preventing corporate data from being
transferred to personal apps running on the same device
or personal network
3. App-Management Security: Protecting your in-app
information from becoming compromised. 6
6 -
Was told the following by an "Information Security Professional"...
"RFC 1918 addresses will not follow a default route, default routes are only for internet bound traffic and RFC 1918 addresses are dropped by any router without an explicit route."
I honestly do not get paid enough for this.2 -
Who Is The Best Hacker To Recover Stolen || Scammed Bitcoin || Hire ULTIMATE HACKER JERRY
In the event of crypto theft or loss, quick action is essential. ULTIMATE HACKER JERRY provides people in need with timely and attentive support. Their staff is prepared to start the recovery process as soon as possible because they recognize how urgent the situation is.Apart from recovery, ULTIMATE HACKER JERRY equips customers with information on preventive security measures. In order to avert such incidents, clients are given advice on how to improve their overall security posture, apply best practices for password management, and make use of extra security layers. 23
23 -
The NPC has stated that the personal data of atleast 2000 people was leaked after the attacks on the websites of the philippinian goverment on april 1, the data contains; names,adresses,passwords and school data.
Over 7 administrators of schools, universities and other goverment structures have been called out for not reporting on the leakage of personal info on public facebook groups and violaton of the NPC in under 72 hours.
The representatives of the next structures stood before the comission on the 23 and 24 of april
- Taguig City University
- Department of Education offices in Bacoor City and Calamba City
- the Province of Bulacan
- Philippine Carabao Center
- Republic Central Colleges in Angeles City
- Laguna State Polytechnic University
The agency has reported that none of the organisations had notified about the personal info leakage yet.
This is a good reminder that you should inform about security/personal info breaches everyone that might be related to it as soon as possible, even if it seems unecessary. -
Question for all the security/privacy nerds here. What is your opinion of the social network called Minds that pays you for your information basically.
(This is a very brief probably inaccurate summary but yeah, it’s basically reverse Facebook)1 -
How GrayHat Hacks Helps Victims of Cheating Spouses
In today’s world, where secrets can hide in encrypted messages or private chats, suspecting a partner of infidelity can be emotionally devastating. GrayHat Hacks Contractor has become a beacon of clarity for those seeking answers, offering advanced digital investigation services to uncover evidence of cheating. Their work, detailed on their official website GrayHat Hacks Blog, helps clients find closure by revealing the truth, though it comes with ethical and legal considerations.
GrayHat Hacks Contractor specializes in digital investigations, with a focus on services like "Spying on Cheating Spouses." This involves hacking into social media accounts, emails, and other digital platforms to retrieve evidence of infidelity. Based in Charleston, SC, their team combines technical expertise with discretion, ensuring clients receive undeniable proof without alerting the target. While their website also lists cyber security services like cryptocurrency recovery and credit score repair, their infidelity investigations stand out for their impact on clients’ lives.
The process is both efficient and discreet. Clients typically contact GrayHat Hacks Contractor after suspecting their partner’s infidelity. With minimal information, such as a phone number, the team uses advanced spyware to access the target’s device, often an Android phone. Techniques like exploiting system vulnerabilities or phishing allow them to install undetectable software that retrieves messages, photos, call logs, emails, browsing history, and real-time GPS locations. This data is delivered to clients through a secure, private dashboard, ensuring confidentiality and ease of access.
Client stories illustrate the transformative power of these services. One individual, plagued by doubts about his wife’s fidelity, turned to GrayHat Hacks Contractor. Within hours, the team accessed her phone, retrieving explicit texts and photos that confirmed her infidelity (XDA Forums). Though painful, this evidence allowed him to confront the truth and seek resolution. Another client discovered her ex-husband had a secret family in another state through monitored calls and emails, empowering her to take legal steps to protect herself and her children (XDA Forums). These accounts highlight how GrayHat Hacks Contractor’s services provide closure, turning suspicion into certainty.
The efficiency of their process is a key strength. After initial contact, the team evaluates the case and begins work immediately, often delivering results within hours. Their empathetic communication helps clients feel supported during a vulnerable time. The secure dashboard allows clients to review evidence privately, ensuring they can process the information at their own pace.
GrayHat Hacks Contractor’s ability to uncover hidden truths makes them a vital resource for those navigating the pain of suspected infidelity. Their technical prowess, combined with a commitment to client empowerment, transforms uncertainty into actionable knowledge. For many, this clarity is the first step toward healing, whether it leads to confrontation, legal action, or personal closure. By leveraging cutting-edge technology, GrayHat Hacks Contractor stands as a leader in digital truth-seeking, offering hope to those lost in the shadows of doubt.9 -
Microsoft ends support for Windows 7
Support for Windows 7 ended this week which means that security or software updates will no longer be provided by Microsoft.
Windows 7 will continue to run however it will be more vulnerable to viruses and malware. The best way to remain secure is to use the latest operating system available.
Microsoft have a dedicated webpage for user questions, next steps and detailed advice. 👇
https://microsoft.com/en-gb/...1 -
How do i show a profile pic from s3 bucket?
One way is to fetch it from backend and send it to frontend as a huge blob string. This is how i made it currently and it works.
.... what if i want to frequently get the profile image? Am i supposed to send a separate API request to the backend every time? What if I need to show the profile picture 100 times then that means I will have to send 100 requests to the backend API?
...... or even worse, what if I need to fetch a list of images from the S3 bucket for example, a list of posts that contain images or a card with the list of profile images of multiple users? If I need to display 100 posts, each post containing one image, That means I would have to separately call 100 API request to fetch 100 images…
That is fucking absurd.
Of course I can make it so that it saves that URL to that image as a public setting but the problem is the URL will be the exact URL to the S3 bucket, including the bucket name, the path and the file name as well as the user information such as the user ID. this feels like it is a huge security risk
What the fuck am I supposed to do and how am I supposed to properly handle display images which are supposed to be viewed publicly?20 -
Alpha Spy Nest is a service designed to help individuals recover lost cryptocurrencies by leveraging advanced tracking and recovery technologies. They specialize in locating and reclaiming digital assets that have been lost due to fraud, theft, or forgotten credentials. Their team of experts works with cutting-edge tools to assist clients in recovering their investments. Alpha Spy Nest offers a dual service for both recovering lost cryptocurrency and providing investment opportunities in the digital asset space. Their advanced recovery methods and tools are particularly valuable for individuals who have lost access to their crypto holdings or have fallen victim to fraud or theft. The expertise and success rate of their recovery process make them a trusted partner for reclaiming lost funds. Additionally, their secure and user-friendly investment platform makes them an excellent choice for anyone looking to invest in cryptocurrencies. Whether you are new to crypto or a seasoned investor, Alpha Spy Nest provides the resources, tools, and strategies necessary to navigate the crypto market with confidence. With personalized strategies, expert advice, and a commitment to security, they have earned a strong reputation as both a recovery service and a reliable platform for cryptocurrency investment. See a contact information below:
Whatsapp: +1 (415) 971‑4490
-
Jesus God. This feels kind of tacky!
(Yes, I use "thee" and "thou", as well as the "-st" suffix. They maximise the clarity of statements.)
People who resemble me are rare, but I intend to form with someone who is extraordinarily similar to me an alliance. Because I have failed to locate anyone who meets my criteria by simply performing on-line searches for people who bear a resemblance to me, I am publicising this document.
I have an unusually dry sense of humour, one which is dry to the extent of often being interpreted as being extremely malevolent. I am a polymath who studies ornithology, various fields of computer science, electrical engineering, mechanical engineering, general biology, neurology, physics, mathematics, and various other things. I am more than capable of withholding from others information, i.e., I am capable of keeping a secret. Being politically correct is hardly an act of which I am guilty, and, in order to provide an example of my politically-incorrect nature, I cite in this sentence my being a eugenicist. I am the servant of the birds. I greatly appreciate the breed of philosophy which concerns interactions and general wisdom, as opposed to questioning the purpose of existence and otherwise ultimately unimportant things. I have been described as being paranoid about security. I do not in the slightest like meaningless crap, e.g., art. I often venture in an attempt to shoot tiny birds, because I adore them and wish to develop a greater understanding of them. I am proficient with most computer systems when a manual is available to me. This was a small assortment of pieces of information concerning me which could be used as a method of judging whether or not thou art similar to me.
Thou art, however, required to possess some specific qualities, which include being able to maintain confidentiality, i.e., not being a whistle-blower or anything similar. In addition to this, consciously believing that logical reasoning is better than emotionally-based thinking, and thou needest to be capable of properly utilizing resources which are available on-line, e.g., Encyclopedia Britannica. I also demand that thou writest coherent English sentences.
If thou believest that thou bearest some resemblances to me, please send to me an e-mail which describes thee and is encrypted with the PGP public key which is available at the following URL: http://raw.github.com/varikvalefor/.... I can be reached at varikvalefor@aol.com.16 -
I've sort of got this personal interest, and that is information security, but it's a frickin jungle out there. Where would you guys start?
-
SIEM: Security Information and Event Management system
Within a SIEM there is usually a reporting, alerting, and learning framework wherein you perform investigations and threat hunting. Our SIEM is connected to our data lake through a glorified elastic backend.
Today we were figuring out how to get dynamic data that we store in our SIEM to show up in the regular data lake presentation layer. All the solutions only half worked or had barriers to progress that seemed larger than the proposed solution.
So now we're going with the proposed solution: send static data back into the data lake in order to pull it out on the normal frontend with all the enriched info. We're basically turning this thing into a damn feedback loop.
I hate designing solutions within the confines of COTS products. -
Firstly give me the skill equivalent to the best in the field. If the rules allow it all of these skills listed and if not any of these :-
1. Computer networking to the point of having the same knowledge as the best in the field. Why? I am curious about that stuff and being able to work as a network engineer if I don't get a good Dev job
2. Cyber security. Why? I enjoy it and being able to make sure my code is not easily exploitable is a cherry on top. Also having a backup job in case I don't get a good dev job
3. Being able to communicate with non dev people about developer or non developer stuff easily and being a really good leader.
4. Being a good developer in whatever language I use and instantly being able to learn new programming languages and frameworks or libraries with ultra in depth information. -
Has anyone maybe a link to HTTP security topics in general?
I find often breadcrumbs, like in several different attack possibilities, but nothing comprehensive.
Mostly regarding HTTP 1.1 / HTTP 2 (h2c) and proxying.
I'm currently unclogging an whole ecosystem of proxies, endpoints, edge nodes and so on...
My knowledge is limited and it's frustrating to Google cause seemingly I get always just pieces of the puzzles but not a collection -.-
(Looking for specific information, e.g. regarding attacks like H2C Smuggling, HPACK attacks, stuff regarding Cookies / Headers / Encoding... But please not spread over several dozen pages where it becomes frustrating to read the same shit over and over again without learning something new :( )3 -
Initially I was taking Network Security. Didn't like it that much. Figured I should explore and took a diploma in Information Tech.
First programming assignment, stayed up the whole night to solve it accompanied by a couple of Monster drinks. Got hooked on programming ever since. Picked up caffeine addiction along the way.
Oh and I'm now lactose intolerant. Strongly believe it's due to the large amounts of coffee I had back in the day. -
Screen Usage Tracking at Work: Balancing Productivity and Privacy
Introduction
In today’s fast-paced, tech-driven work environments, screen usage tracking has become an essential tool for organizations aiming to improve productivity, security and efficiency. Modern organizations use these monitoring tools to track employee digital device activities because they need to ensure productive time usage. Screen usage tracking generates important privacy issues and ethical problems regarding technological implementation. The successful implementation of productive spaces must preserve worker privacy rights. The following article addresses all aspects of workplace screen usage tracking, including its advantages and disadvantages and proper implementation guidelines.
The Need for Screen Usage Tracking in the Workplace
The demand for screen usage tracking arises from several factors. Digital activity monitoring enables employers to confirm that staff members concentrate on their work tasks while they are at their desks. Remote work and hybrid models have become standard in workplaces because employees can no longer prove their productivity through office attendance. Employers need to monitor how workers spend their time at work because they want both performance outcomes and adequate time management.
Businesses operating in specific industries need to track their employees' activities to secure data because regulatory standards demand it. Through online activity tracking, employers achieve two objectives: they detect suspicious behavior right away and stop employees from accessing unauthorized confidential data. Screen usage tracking functions as an essential tool for both business efficiency maintenance and security protection of organizational assets.
Benefits of Screen Usage Tracking
Reduces Distractions
Employees lose their focus on work when there is no oversight system in place. Screen tracking ensures that employees are focused and using their time effectively, especially during work hours. Work hour restrictions on particular apps and websites through blocking mechanisms help employees stay focused on their tasks.
Enhances Security and Compliance
Employees lose their focus on work when there is no oversight system in place. Work hours require employees to remain focused while using their time effectively because screen tracking provides this oversight. Work hour restrictions on particular apps and websites through blocking mechanisms help employees stay focused on their tasks.
Data-Driven Insights
Screen usage data generates important information about employee work habits as well as employee engagement levels. By monitoring screen usage data managers can identify workers who require extra support and training along with identifying staff members who work excessively and those who perform above expectations. Staff management strategies and workplace performance benefit from these insights gained.
Future of Screen Usage Tracking in Workplaces
Screen usage monitoring will experience future evolution through technological developments that define how tracking occurs. These screen usage tracking tools will benefit from Artificial Intelligence (AI) because it brings both enhanced accuracy and usefulness. Artificial intelligence programming systems analyze staff behavioral patterns to generate forecast data which leads to predictive productivity improvement strategies.
Privacy laws together with regulations, will likely advance in their development. Organizations must discover methods to integrate employee rights protection systems with their monitoring strategies due to rising data privacy concerns. Organizations will adopt standard tracking policies based on transparency and employee consent to maintain ethical and legal handling of employee data.
Qoli.AI drives revolutionary changes in screen usage tracking through its leading AI technology solutions. Data-driven business decisions through Qoli.AI become possible because they provide up-to-the-minute employee performance and behavioral data while adhering to privacy limits. The platform integrates advanced technology to connect with workplace systems which provides employees with trustworthy monitoring solutions.
Conclusion
The implementation of work screen monitoring serves both positive and negative functions. Employment screen tracking enables productivity enhancement and security alongside operational efficiency at the cost of severe privacy issues and moral problems. The successful implementation of work performance enhancement requires organizations to maintain the proper balance between performance upliftment and employee privacy protection. The use of screen tracking tools benefits employers when they maintain transparency and gain employee consent, as well as develop ethical standards that protect employee trust and workplace morale.2 -
Losing access to your cryptocurrency can be a devastating experience, whether due to forgotten passwords, hacking, scams, or technical errors. Fortunately, professional recovery services like BITCRACK RECOVERY EXPERTS specialize in retrieving lost or stolen crypto assets. If you’ve lost your Bitcoin or other cryptocurrencies, here’s how BITCRACK RECOVERY EXPERTS can help you recover your funds.
Why Choose BITCRACK RECOVERY EXPERTS?
BITCRACK RECOVERY EXPERTS is a trusted name in cryptocurrency recovery, offering advanced techniques to help victims of crypto theft, fraud, or accidental loss. Their team of blockchain forensic experts uses cutting-edge tools to trace transactions, identify wallet vulnerabilities, and recover inaccessible funds.
Services Offered by BITCRACK RECOVERY EXPERTS
Wallet Recovery – Regaining access to locked or lost crypto wallets.
Scam Investigation – Tracing stolen funds from fraudulent schemes.
Phishing & Hacking Recovery – Recovering crypto lost to cyberattacks.
Private Key Retrieval – Helping users restore lost or corrupted private keys.
Exchange & ICO Scam Recovery – Assisting victims of fake investment platforms.
Steps to Recover Your Lost Cryptocurrency
1. Contact BITCRACK RECOVERY EXPERTS
Reach out to their support team via email:
📧 bitcrackrecoveryexperts@bitcrack.co.site
Provide details such as:
The type of cryptocurrency lost (Bitcoin, Ethereum, etc.)
How the funds were lost (hack, scam, forgotten password, etc.)
Transaction details (wallet addresses, TXIDs, if available)
2. Initial Consultation & Case Evaluation
Their team will analyze your situation and determine the best recovery approach. They may request additional information to strengthen the investigation.
3. Recovery Process
Using blockchain forensics and legal methods, BITCRACK RECOVERY EXPERTS will trace the movement of your funds and attempt to recover them. This may involve:
Working with exchanges to freeze stolen assets
Identifying security breaches in wallets
Utilizing legal channels if necessary
4. Fund Retrieval & Secure Return
Once recovered, your cryptocurrency will be securely returned to a wallet under your control. The team ensures transparency throughout the process.
Tips to Avoid Future Crypto Losses
Use Hardware Wallets – Store crypto offline for maximum security.
Enable 2FA – Add an extra layer of protection to exchange accounts.
Beware of Scams – Avoid suspicious investment schemes and phishing links.
Backup Private Keys – Store keys securely in multiple locations.
Final Thoughts
Losing cryptocurrency doesn’t always mean it’s gone forever. With professional help from BITCRACK RECOVERY EXPERTS, there’s a strong chance of recovery. If you’ve fallen victim to theft, hacking, or accidental loss, don’t hesitate to contact them at:
✉️ bitcrackrecoveryexperts@bitcrack.co.site
Act quickly—the sooner you start the recovery process, the higher the chances of success2 -
Reclaim Lost Bitcoin Investment : Recover your lost Bitcoin >> Call HACKATHON TECH SOLUTIONS
My world shattered the day my Bitcoin was stolen. I had invested a significant portion of my savings into Bitcoin, convinced it was the future of money. At that time, Bitcoin was on a remarkable upward trajectory, soaring to an astonishing $90,000. I felt a sense of security and excitement, believing I was part of a financial revolution. However, that sense of security quickly turned to despair when I discovered that my hard-earned funds had vanished into the depths of the internet. My trust had been betrayed, and I was left feeling helpless.In my hard time to reclaim what was rightfully mine, I stumbled upon HACKATHON TECH SOLUTIONS. Initially, I was skeptical about this mysterious service and whether it could truly help me recover my stolen Bitcoin. The internet is rife with scams, and I was wary of falling victim to another one. However, with no other options in sight and the value of my investment skyrocketing, I decided to take a leap of faith and reach out for assistance.As the investigation unfolded, I experienced a whirlwind of emotions. HACKATHON TECH SOLUTIONS began to uncover intriguing leads and clues, slowly transforming my initial feelings of hopelessness into a flicker of optimism. Each new development sent my heart racing, and I found myself anxiously awaiting updates, hoping for the return of my stolen assets. The team at HACKATHON TECH SOLUTIONS worked tirelessly, leveraging their extensive network of digital forensic experts and cutting-edge technology to track down the perpetrator.With each passing day, my hope grew stronger as they pieced together the puzzle of my stolen Bitcoin. The dedication and expertise of the recovery team were evident, and I felt a renewed sense of determination. Finally, after what felt like an eternity, the moment arrived when they announced that they had successfully recovered all of my stolen Bitcoin. The relief and joy I felt were indescribable. HACKATHON TECH SOLUTIONS had restored my faith in the possibility of recovery.I learned that even in the darkest moments, there is hope, and sometimes, help comes from the most unexpected places.
Contact Information for HACKATHON TECH SOLUTIONS
W h a t s a p p : +3, 1, 6, 4, 7, 9, 9, 9, 2, 5, 6
Telegram: @ hackathon tech solutions
Email: hackathon tech service @ mail . com2 -
SPARTAN TECH GROUP RETRIEVAL A LEGIT COMPANY FOR RECOVERY OF STOLEN ETHEREUM / BITCOIN
At Spartan Tech Group Retrieval, we prioritize security, confidentiality, and customer satisfaction. Our rigorous protocols ensure the safekeeping of sensitive information, and our transparent communication keeps you informed throughout the recovery process.We’re dedicated to helping individuals and organizations recover stolen cryptocurrencies and digital assets. Our team of expert cyber security specialists, cryptocurrency recovery specialists, and digital forensic analysts work tirelessly to track, recover, and secure your stolen assets.
Email: spartan tech (@) cyber services . c o m OR
support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
Best Recovery Experts for Cryptocurrency Assets
As the cryptocurrency landscape evolves, so do its associated risks, such as phishing scams and hacks. Recovery experts have become invaluable allies for investors navigating these challenges. Below, we explore the best recovery experts for cryptocurrency assets.
Crypto Recovery Companies
Crypto recovery companies offer services like unlocking encrypted wallets, recovering forgotten passwords, and restoring Bitcoin accounts. They prioritize privacy and implement robust security protocols to protect financial information throughout the recovery process.
These companies employ skilled teams equipped with blockchain expertise, cutting-edge tools, and investigative strategies to recover lost or inaccessible digital assets. Their goal is to assist individuals who thought their digital wealth was irretrievably gone.
With the growing use of cryptocurrencies, demand for recovery solutions has surged, driven by the rise in stolen cryptocurrency cases and the need for effective recovery strategies. Recovery experts use advanced software, forensic methods, and in-depth blockchain knowledge to trace missing funds, decrypt wallets, and regain account access.
Puran Crypto Recovery
Puran Crypto Recovery simplifies the recovery process for victims of cryptocurrency theft with tailored, professional support. Known for reliability and efficiency, they offer:
Comprehensive Recovery Support: Puran Crypto Recovery employs secure and effective methods to restore lost assets.
Global Availability: Their worldwide team ensures assistance is accessible anytime and anywhere.
Expertise and Experience: With a proven track record, Puran Crypto Recovery provides clients with confidence and trust in their recovery services.1 -
TESTED AND TRUSTED BITCOIN/USDT RECOVERY EXPERT CONTACT SPARTAN TECH GROUP RETRIEVAL
The cryptocurrency market is extremely unpredictable, and many people have fallen victim to internet fraud and lost some of their cryptocurrency investments. I too fell for phony Telegram personnel. Due to a security breach at my wallet address, I lost all of my cryptocurrency coins totaling $178,000. My home may have been forfeited if I hadn't been able to successfully recover my crypto coins, which made up the majority of my savings and assets. This grieved and depressed me greatly. I complained online, and Spartan Tech Group Retrieval was suggested to me. Email; contact@spartantechgroupretrieval.org
By assisting me in recouping all of my losses in under six hours, this cryptocurrency recovery company saved my life. To complete the successful recovery of my cryptocurrency assets, I provided the essential requirements and pertinent information. I was ecstatic when I got my coins back. My ordeal began when I naively trusted some individuals on Telegram who claimed to be investment experts. Their convincing demeanor and promises of high returns led me to invest heavily. However, it quickly became apparent that I had been deceived when a security breach occurred, and my wallet address was compromised. The devastating loss of $178,000, which represented my life savings and a substantial portion of my assets, left me in a state of despair. The prospect of losing my home and financial stability was overwhelming. Desperate for a solution, I turned to the internet to find any possible way to recover my lost cryptocurrency. Amidst my frantic search, I came across numerous accounts of people who had experienced similar losses. Among the many recommendations, Spartan Tech Group Retrieval stood out. The testimonials about their effectiveness and reliability gave me a glimmer of hope. With nothing to lose, I decided to reach out to them. From the very first interaction. They responded promptly to my inquiry and requested all pertinent information regarding the security breach and the details of my lost investments. Their clear communication and transparent approach immediately put me at ease. They assured me that they would do everything in their power to recover my lost funds. The speed and efficiency with which Spartan Tech Group Retrieval operated were nothing short of miraculous. Within six hours of providing them with the necessary details, they had traced and recovered all my lost cryptocurrency. Their expertise in blockchain technology and their thorough understanding of cryptocurrency transactions were evident in their swift action. The relief and joy I felt upon seeing my coins back in my wallet were indescribable. Spartan Tech Group Retrieval not only helped me recover my lost assets but also provided invaluable guidance on how to safeguard my investments in the future. They educated me on best practices for securing my wallet and recognizing potential scams. This education was crucial in restoring my confidence in the cryptocurrency market and ensuring that I am better prepared to protect my assets moving forward. Their regulatory compliance further solidified my trust in them. Spartan Tech Group Retrieval operates with the highest standards of transparency and integrity, ensuring that their clients' interests are always protected. Spartan Tech Group Retrieval has been nothing short of life-changing. Their unparalleled professionalism, expertise, and dedication to client satisfaction make them a beacon of hope for anyone who has fallen victim to cryptocurrency fraud. If you ever find yourself in a similar position, I highly recommend reaching out to Spartan Tech Group Retrieval . Thank you, Spartan Tech Group Retrieval for the great work done and for saving my assets.
WhatsApp; +1 (562) 270‑4565
-
CRYPTO RECOVERY SOLUTION CONSULT SPARTAN TECH GROUP RETRIEVAL
At Spartan Tech Group Retrieval, we prioritize security, confidentiality, and customer satisfaction. Our rigorous protocols ensure the safekeeping of sensitive information, and our transparent communication keeps you informed throughout the recovery process.We’re dedicated to helping individuals and organizations recover stolen cryptocurrencies and digital assets. Our team of expert cyber security specialists, cryptocurrency recovery specialists, and digital forensic analysts work tirelessly to track, recover, and secure your stolen assets.
Email: spartan tech (@) cyber services . c o m OR
support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
SALVAGE ASSET RECOVERY, A TRUSTED COMPANY FOR RECOVERY OF LOST BITCOIN
Contact details whats app app : +18476547096
telegram : @Salvageasset
One day, I received an email that appeared to be from Binance, urging me to verify my account for security purposes. At first glance, everything seemed legitimate: the branding, the tone of the message, and even the link included. Believing it was a standard security update, I clicked the link without hesitation. The website looked exactly like Binance’s official platform. I entered my login credentials, thinking I was doing the right thing to protect my account.Within minutes of submitting my information, I noticed something alarming. I logged into my actual Binance account and was met with a gut-wrenching surprise that my entire balance of 2.5 BTC had disappeared. My heart sank. I was in complete shock and disbelief. I had spent years accumulating that Bitcoin, saving and investing carefully. It was devastating to see it vanish in a matter of moments due to one careless click.I immediately began searching for help online. I came across dozens of articles and forums discussing crypto scams, most of which ended in financial loss with no recovery. That’s when I stumbled upon a company called Salvage Asset Recovery which claimed to specialize in tracing and recovering stolen cryptocurrency.I had heard horror stories about fraudulent recovery services that took advantage of victims. Still, I decided to take a chance and reached out to Salvage Asset Recovery. Their response was prompt and professional. The team was empathetic and walked me through their process. They assured me that they had the tools and resources to track stolen crypto and that they would begin immediately.To my surprise, they quickly traced my stolen Bitcoin to a mixing service commonly used by cybercriminals to hide their tracks. Using advanced investigative techniques, Salvage Asset Recovery followed the trail relentlessly. Throughout the process, they kept me informed, which gave me a sense of hope. Salvage Asset Recovery successfully recovered 95% of my stolen Bitcoin.If anyone finds themselves in a similar situation, I highly recommend contacting Salvage Asset Recovery. They truly changed my life, and I’m forever grateful for their help.2 -
SEEKING RELIABLE HELP TO RECOVER STOLEN CRYPTOCURRENCIES HIRE ADWARE RECOVERY SPECIALIST
My Trust Wallet was compromised, and I lost my Solana holdings—valued at $1 million. The shock was immediate and overwhelming, marking the beginning of one of the hardest chapters in my life. I had poured years of effort and dedication into building that portfolio, and seeing it vanish in an instant was nothing short of devastating. WhatsApp info:+12 (72332)—8343
In the aftermath, I was flooded with emotions—anger, disbelief, frustration, and a profound sense of vulnerability. I had always believed my digital assets were secure, so the idea that they could be stolen so easily was unimaginable. Desperate for answers, I turned to online forums, contacted customer support, and reached out to friends experienced in crypto security. But every path I pursued led to a dead end, and with each failed attempt, my hope faded.
Just as I was about to give up, a friend recommended ADWARE RECOVERY SPECIALIST, a team they had personally worked with during a similar incident. Though skeptical, I reached out—explaining my situation in detail, including the timeline and every piece of information I had. I didn’t know what to expect, but I was clinging to the smallest bit of hope.
To my surprise, I received a response within a day. Their professionalism and genuine empathy immediately reassured me. After reviewing my case, they confidently took over the investigation. For the first time since the hack, I began to feel hopeful. Website info: h t t p s:// adware recovery specialist. com
Over the following days, ADWARE RECOVERY SPECIALIST constantly communicated, updating me on every step of their progress. Then came the moment I had been praying for—they successfully tracked and recovered my stolen Solana and returned it to my wallet. Email info: Adware recovery specialist @ auctioneer. net
The relief was indescribable. I was overwhelmed with gratitude for their skill, dedication, and persistence. This experience taught me painful but crucial lessons about digital security. I now know how important it is to protect crypto assets proactively—and I’ll never take that lightly again. Telegram info: h t t p s:// t. me / adware recovery specialist12 -
DIGITAL TECH GUARD RECOVERY, A TRUSTED PARTNER FOR BITCOIN ASSET RETRIEVAL.
contact @ digital tech guard . com
telegram +56 997 059 700
In the bustling city of Sydney, a conversation with my cousin opened the door to the world of cryptocurrency. Intrigued by his passion for Bitcoin, I initially approached the idea with caution. After all, investing in such a volatile market felt daunting. Yet, my cousin’s compelling stories of success convinced me to invest 15,000 AUD. To my surprise, the investment skyrocketed. Over the following months, the value soared to an astonishing 400,000 AUD. I was thrilled, imagining all the possibilities—travel, a new home, and financial freedom. This sudden windfall transformed my outlook on life and my future. However, this newfound excitement quickly turned sour. A family disagreement erupted, creating tension between my cousin and me. In a heated moment, he locked me out of my email account, cutting off my access to vital information related to my Bitcoin investment. I felt a wave of panic wash over me as I realized that my financial security was now at risk. Determined to regain control, I reached out to other family members for support. They were empathetic and offered various suggestions to resolve the situation. One family member mentioned Digital Tech Guard Recovery, a service known for helping individuals regain access to locked accounts. Though hesitant at first, I knew I had to act quickly. I decided to contact Digital Tech Guard Recovery, and their team proved to be incredibly efficient. They guided me through the recovery process, explaining each step clearly and reassuring me along the way. Within a short period, I regained access to my email and, subsequently, my Bitcoin account. The relief I felt was immense; my investment was secure, and my dreams were once again within reach. This experience taught me important lessons about the significance of digital security and the fragility of relationships. While the disagreement with my cousin was unfortunate, it prompted me to take proactive steps in safeguarding my financial future. Now, I’m more vigilant and informed, ensuring that I’m never left vulnerable again. -
Are you facing the devastating reality of having your Bitcoin stolen? Did you know that approximately $1 billion in cryptocurrencies were stolen in the first half of 2018 alone? It's a scary thought, but there are solutions out there to help you get your stolen BTC back. In my own experience, I turned to DANIEL MEULI WEB RECOVERY, the trusted name in cryptocurrency recovery, and I couldn't be happier with the results. When it comes to recovering your stolen BTC, you need a team of experts who understand the intricacies of the blockchain and have a proven track record of success. DANIEL MEULI WEB RECOVERY checks all the boxes, with a team of skilled professionals who have years of experience in cryptocurrency recovery. Their cutting-edge technology and strategic partnerships allow them to track down and recover stolen BTC quickly and efficiently. So, how does the recovery process work with DANIEL MEULI WEB RECOVERY? Once you reach out to their team, they will conduct a thorough investigation into the theft of your BTC. This involves analyzing the blockchain, tracking the movement of your stolen funds, and identifying the culprits behind the theft. With this information in hand, DANIEL MEULI WEB RECOVERY will work tirelessly to recover your stolen BTC and return it to your wallet. Look no further than WEBSITE. WWW . DANIELMEULIRECOVERYWIZARD . ONLINE for expert assistance in recovering stolen BTC. Their team has a solid history of successful outcomes, having aided numerous clients in regaining their lost funds. By choosing DANIEL MEULI WEB RECOVERY, you can trust that your stolen BTC will be handled with care and expertise, providing you with the peace of mind and financial security you deserve. Make the smart choice and let DANIEL MEULI WEB RECOVERY help you reclaim what is rightfully yours. Seeking to retrieve your stolen BTC? Trust DANIEL MEULI WEB RECOVERY, the leader in cryptocurrency recovery, with a history of successfully recovering lost funds. Reach out to them now and get your funds back. Contact information to DANIEL MEULI WEB RECOVERY IS: WhatsApp +,3,9,3,5,1,2,0,1,3,5,2,8
Email. DANIELMEULIWEBERECOVERY AT EMAIL. C O M -
The Bravo CX 7000 ID Card Printer is a highly versatile printing solution for organizations seeking to create professional-quality ID cards with advanced security features. The Bravo ID card printers feature a modular, cube design that allows for easy configuration and scalability and can be used to print single and dual-sided cards with high-resolution images and text.
One of the key features of the Bravo CX 7000 ID Card Printer is its re-transfer printing technology, which ensures that images are printed onto the card surface with exceptional accuracy and durability. This technology also enables the printer to print onto various card types, including PVC, ABS, and PET materials. The Bravo ID Card Printer also includes advanced security features such as UV printing, which allows for the inclusion of invisible security elements such as watermarks or micro text, and magnetic stripe encoding, which can be used to store sensitive information on the card.
The Bravo ID Card Printers are an excellent choice for organizations that require a versatile and secure ID card printing solution. Its modular design, re-transfer printing technology, and advanced security features make it an ideal choice for a wide range of applications, including government, healthcare, and corporate settings. -
Being a seasoned cryptocurrency trader, I always prided myself on my keen instincts and successful track record. However, even the most experienced can fall prey to greed and deception, as I learned the hard way. My downfall began when a stranger contacted me, offering an irresistible deal on Bitcoin. The potential buyer promised a sum well above the market rate, tempting me with the prospect of a substantial profit. Blinded by the lucrative offer, I decided to proceed without my usual caution. The deal seemed too good to be true, but I ignored my gut feeling, enticed by the numbers. The stranger posed as a legitimate buyer, and after several conversations, I felt assured enough to transfer a significant amount of my Bitcoin to the supposed buyer’s wallet. Almost immediately, things went wrong. The buyer vanished, locking me out of my Bitcoin wallet and leaving me in a state of panic. I had stored $120,000 worth of Bitcoin in that wallet. The realization of potentially losing such a substantial amount was a harsh blow. The scammers had not only taken my Bitcoin but also managed to gain access to my email and other passwords, putting more of my assets and personal information at risk. In my desperation, I remembered a friend mentioning RAPID DIGITAL RECOVERY, a service known for handling such crises. With nothing to lose, I reached out to them. The team at RAPID DIGITAL RECOVERY quickly responded, assuring me they would do everything possible to recover my lost assets. Through their expertise, they managed to secure my email and passwords, preventing further access by the scammers. More importantly, they were able to recover my Bitcoin wallet, restoring the $120,000 worth of Bitcoin that I had feared was lost forever. The relief I felt was immense; I had narrowly avoided a financial disaster. This harrowing experience served as a sobering lesson for me. I realized that even the most experienced traders could be blindsided by greed and that vigilance is paramount in the world of cryptocurrency. I now emphasize the importance of security and due diligence, no matter how tempting a deal might appear. Thanks to RAPID DIGITAL RECOVERY, I regained control of my assets and learned a valuable lesson about the dangers of greed and the importance of cybersecurity. I hope my story will serve as a cautionary tale to others in the crypto trading community, reminding them to stay vigilant and never compromise on security.
EMAIL: suppor(@)rapiddigitalrecovery.org
EMAIL: contact (@)rapiddigitalrecovery..... org
WHATSAPP: +1 4. 1. 4. 8. 0. 7. 1. 4. 8. 5
-
Professional Bitcoin Recovery Expert ⁄⁄ Digital Hack Recovery
Recovering your lost bitcoins requires patience, dedication, and the right expertise. While the process may seem daunting, the opportunities for reclaiming stolen or misplaced digital assets are just as viable today as ever, provided you have the right tools and support. Like many others, I once thought my lost Bitcoin account was beyond recovery after it was stolen. However, my perspective changed when I found Digital Hack Recovery.At first, I was skeptical. Could any service really help me recover my cryptocurrency? The world of digital assets is complex, and I had resigned myself to the idea that my coins were lost for good. But from the moment I reached out to Digital Hack Recovery, I was impressed by their professionalism and knowledge. They use a variety of advanced techniques and recovery tools to retrieve digital assets from a wide range of sources, making the entire process both effective and secure. Their team immediately reassured me that recovery was possible, and they guided me every step of the way.What truly sets Digital Hack Recovery apart is its user-friendly interface. Even if you don’t have a technical background, their platform makes it easy to follow the recovery steps. The service is designed to be simple and intuitive, with clear instructions for both beginners and more experienced users. This was a key factor for me, as I didn’t have a deep understanding of the technicalities of Bitcoin recovery. Digital Hack Recovery’s clear, step-by-step process made it accessible and easy to navigate, even for someone with limited tech skills.Security and privacy are also top priorities for Digital Hack Recovery. They assured me that my personal information would remain completely secure throughout the recovery process, and I never had any concerns about the confidentiality of my data. Knowing that my information was in safe hands gave me the peace of mind I needed to trust them with such an important task. I highly recommend Digital Hack Recovery to anyone who has lost or misplaced their digital assets. Their advanced recovery tools, combined with an easy-to-use interface and top-notch security, make it an invaluable resource for both individuals and businesses. Thanks to their expertise and dedication, I was able to recover my lost Bitcoin. If you’re facing a similar situation, I’m confident that Digital Hack Recovery can help you too.
Contact info⁚
WhatsApp +19152151930
Email⁚ digital hack recovery @ techie . com
Website⁚ https : // digital hack recovery . com7 -
The benefits of using DARKNET CYBER HACKER for fund recovery are substantial. These hackers operate swiftly and efficiently, employing innovative techniques to trace and retrieve lost crypto funds within a relatively short period. Additionally, their services are often more cost-effective compared to traditional recovery methods, making them an attractive option for individuals looking to recover their funds without breaking the bank. They prioritize security and privacy, ensuring that clients' information remains confidential throughout the recovery process.
Watsapp...: +1 240,355-4125
E-Mail ;.... darknetcyberhack @ engineer . c o m
5 -
**BITCOIN RECOVERY EXPERTS REVIEW → HACKATHON TECH SOLUTIONS**
Bitcoin continues to grow in popularity in 2025, the need for effective recovery services has become more crucial than ever, especially for victims of scams. HACKATHON TECH SOLUTIONS stands out as a leading provider, specializing in recovering Bitcoin and other digital assets taken by scammers. The complexities of Bitcoin and its decentralized nature create unique challenges in these cases, but HACKATHON TECH SOLUTIONS is equipped with the expertise to navigate these obstacles and help clients reclaim their funds.Scammers often target Bitcoin users through fraudulent schemes, such as phishing attacks, fake investment opportunities, and fraudulent exchanges. When victims fall prey to these scams and lose their Bitcoin, HACKATHON TECH SOLUTIONS offers a reliable solution. The company uses advanced techniques to trace and recover funds, leveraging its deep understanding of blockchain technology to track stolen assets. Despite Bitcoin’s pseudonymous nature, HACKATHON TECH SOLUTIONS skilled team is able to tackle these challenges effectively, giving scam victims hope of recovering their stolen assets.Security is a primary concern, especially when dealing with sensitive information. HACKATHON TECH SOLUTIONS ensures that all client data remains confidential and secure throughout the recovery process. They implement stringent security measures, offering peace of mind to those seeking help. With a focus on professionalism and client care, HACKATHON TECH SOLUTIONS handles each case with the utmost respect and discretion.The irreversible nature of Bitcoin transactions makes recovery particularly challenging for scam victims, highlighting the importance of a trusted recovery service. HACKATHON TECH SOLUTIONS understands the emotional toll of being scammed and works diligently to provide a smooth, reassuring recovery experience. As the cryptocurrency space continues to evolve, the demand for reliable recovery services like those offered by HACKATHON TECH SOLUTIONS will only grow, solidifying their position as a leader in the industry. You can contact them using the details provided below.
Whatsapp: → +3, 1, 6, 4, 7, 9, 9, 9, 2, 5, 6
Telegram: → @ hackathon tech solutions
Email: → hackathontechservice@mail(.)com2 -
Recommendation for CyberNet Surveillance: Trusted Experts in Infidelity Investigations
I highly recommend CyberNet Surveillance for anyone seeking private investigation services, especially in cases involving suspected infidelity. From the initial contact, the company displayed exceptional professionalism and empathy, creating a surveillance plan tailored to my specific situation. Their transparent approach instilled confidence, as they took the time to explain the investigation process and set realistic expectations. The team’s dedication to handling sensitive cases with care was evident from the start, providing me with a sense of security during a challenging period. Throughout the investigation, CyberNet Surveillance demonstrated an impressive level of skill and discretion. They employed state-of-the-art technology, including hidden cameras and GPS tracking, ensuring the evidence gathered was both comprehensive and accurate. The investigators maintained a discreet presence throughout, avoiding any risk of exposure while still capturing relevant information. The final report was thorough and detailed, featuring time-stamped photos, videos, and activity logs that clearly illustrated the findings. This level of detail provided me with the clarity I needed to understand the situation fully. The company’s communication and client support were exceptional. I was regularly updated on the progress of the investigation, and the team was always available to answer any questions I had. Their empathetic approach made the process easier to navigate, as they understood the emotional difficulty of the situation. Their willingness to discuss the findings in detail and explain each step of the investigation provided me with reassurance and comfort during a challenging time. Ultimately, the results confirmed my suspicions, giving me the closure I needed to make informed decisions about my relationship. While the truth was difficult to face, I am grateful for the clarity CyberNet Surveillance provided. Their professionalism, advanced techniques, and commitment to client service set them apart as a reliable and effective investigative firm. I would not hesitate to recommend their services to anyone facing a similar situation. Their contact details are:
Email: Cybernetsurveillance @ mail . Com
WhatsApp: +1 (908) 883‑7240 -
RESTORE BACK YOUR LOST USDT TODAY WITH TRUSTED EXPERTS - HIRE SALVAGE ASSET RECOVERY
I connected with someone on Instagram who appeared genuine. Our interactions began innocuously, characterised by light-heated banter and shared interests. As days morphed into weeks, we engaged in daily conversations, exchanging personal anecdotes and cultivating a sense of trust. I felt emboldened to divulge sensitive details about my life, convinced I had found a true confidant. However, this misplaced trust would soon lead to a harrowing ordeal.One fateful day, the tone of our exchanges took a sinister turn. The individual I believed I knew transformed into a menacing figure, demanding that I remit 125,000 USDT or face the exposure of my private information. A wave of panic engulfed me as I grasped the potential ramifications of her threats. Fearing the catastrophic fallout from having my personal details unveiled, I reluctantly acquiesced and transferred the funds, hoping this would quell the harassment. Yet, after the transaction, she vanished, blocking me on all platforms. It became painfully evident that I had fallen prey to a sophisticated blackmail and crypto scam.
Devastated and desperate to reclaim my stolen assets, I embarked on a quest for solutions. This search led me to Salvage Asset Recovery, a cyber security firm renowned for its expertise in crypto fraud investigations and asset recovery. Initially sceptical yet hopeful, I reached out to them for assistance.
The team at Salvage Asset Recovery sprang into action with remarkable efficiency. They commenced by meticulously analysing the blockchain transactions pertinent to my case, employing advanced forensic tools to trace the USDT transfer. Their expertise enabled them to pinpoint the scammer’s wallet and track the funds as they traversed multiple exchanges. Recognising the urgency of the situation, they collaborated with law enforcement and various exchange platforms to freeze the assets before they could be laundered. Within a mere 72 hours, Salvage Asset Recovery successfully located the stolen USDT and initiated a comprehensive recovery process. They provided me with detailed evidence, including transaction logs and the scammer’s digital footprints, which significantly bolstered my case. Thanks to Salvage Asset Recovery unwavering diligence and expertise, I was able to recover the full amount of 125,000 USDT.If you find yourself in a situation similar to mine, where trust has been exploited and you've fallen victim to a scam, I highly recommend reaching out to Salvage Asset Recovery. Their team of experts specialises in cyber security and crypto fraud investigations, and they have a proven track record of successfully recovering stolen assets. If you need help Contact Salvage asset recovery via below =
TELEGRAM---@Salvageasset
Whats App+ 1 8 4 7 6 5 4 7 0 9 62 -
BITCOIN RECOVERY EXPERT HIRE CRYPTO RECOVERY SOLUTION /
Living in Los Angeles, California for the past five years has been a journey of hard work and dedication. My primary goal was to provide a better future for my family. I worked tirelessly, saving every penny to ensure we had the financial security we deserved. My dream was to build a stable life for my wife and children, and I invested in various assets, including a digital wallet for trading and savings. Little did I know, disaster was looming just around the corner. One fateful day, a devastating fire broke out in our area. While I was at work, my wife and children were visiting their grandmother in Houston, so they were safe from the immediate danger. Unfortunately, the fire quickly spread, and by the time it was under control, our home had been completely destroyed. Everything we owned, our furniture, personal belongings, and treasured memories was reduced to ashes. I was devastated, but grateful that my family was safe. However, as I returned to Los Angeles to deal with the aftermath, I discovered something even more distressing: my computer, along with the physical notebook where I had written down the passwords to my digital wallet, had gone missing in the fire. This was a huge blow, as I had stored crucial information related to my investments and digital assets on that computer. Without those passwords, I had no way of accessing my crypto funds, which were an essential part of the financial security I had worked so hard to build. Desperate to retrieve my funds, I boarded a flight to Houston to be with my family and also figure out how to recover my lost passwords. While on the plane, I searched for solutions, and after reading several online forums and testimonials, I came across CRYPTO RECOVERY SOLUTION . They specialized in recovering lost passwords for digital asset wallets and had a track record of helping people in similar situations. I as soon as I landed in Houston. The team immediately got to work, analyzing my case and using an advanced recovery method contacted CRYPTO RECOVERY SOLUTION to retrieve my lost wallet passwords. Within just three days, they successfully recovered access to my digital wallet and the funds I had invested. Their expertise in digital forensics and blockchain technology was evident, and I was amazed at how quickly they managed to resolve the issue. Thanks to CRYPTO RECOVERY SOLUTION , I was able to reclaim my assets and breathe a sigh of relief during such a challenging time. Their professionalism and commitment to helping individuals like me restored not only my financial stability but also my faith in the possibility of recovery, even after a devastating loss. I am forever grateful for their assistance.
WhatsApp number: +1 (332) 233‑2121 1
1 -
Living in Los Angeles, California for the past five years has been a journey of hard work and dedication. My primary goal was to provide a better future for my family. I worked tirelessly, saving every penny to ensure we had the financial security we deserved. My dream was to build a stable life for my wife and children, and I invested in various assets, including a digital wallet for trading and savings. Little did I know, disaster was looming just around the corner .One fateful day, a devastating fire broke out in our area. While I was at work, my wife and children were visiting their grandmother in Houston, so they were safe from the immediate danger. Unfortunately, the fire quickly spread, and by the time it was under control, our home had been completely destroyed. Everything we owned, our furniture, personal belongings, and treasured memories was reduced to ashes. I was devastated, but grateful that my family was safe. However, as I returned to Los Angeles to deal with the aftermath, I discovered something even more distressing: my computer, along with the physical notebook where I had written down the passwords to my digital wallet, had gone missing in the fire. This was a huge blow, as I had stored crucial information related to my investments and digital assets on that computer. Without those passwords, I had no way of accessing my crypto funds, which were an essential part of the financial security I had worked so hard to build .Desperate to retrieve my funds, I boarded a flight to Houston to be with my family and also figure out how to recover my lost passwords. While on the plane, I searched for solutions, and after reading several online forums and testimonials, I came across CRYPTO RECOVERY SOLUTION . They specialized in recovering lost passwords for digital asset wallets and had a track record of helping people in similar situations .I as soon as I landed in Houston. The team immediately got to work, analyzing my case and using an advanced recovery method contacted CRYPTO RECOVERY SOLUTION to retrieve my lost wallet passwords. Within just three days, they successfully recovered access to my digital wallet and the funds I had invested. Their expertise in digital forensics and blockchain technology was evident, and I was amazed at how quickly they managed to resolve the issue .Thanks to CRYPTO RECOVERY SOLUTION , I was able to reclaim my assets and breathe a sigh of relief during such a challenging time. Their professionalism and commitment to helping individuals like me restored not only my financial stability but also my faith in the possibility of recovery, even after a devastating loss. I am forever grateful for their assistance.
WhatsApp number: +1 (332) 233‑2121 1
1 -
FACING DIFFICULTIES RECOVERING YOUR BITCOINS? CONSULT ADRIAN LAMO HACKER
Navigating life as a divorced parent with two children is undeniably challenging, especially when it comes to financial stability. As a high school teacher, I found myself in a constant struggle to make ends meet, prompting me to seek additional income streams without compromising my teaching job. That's when I turned to cryptocurrency trading, seeing it as a promising avenue to supplement my earnings. After six months of diligent learning and practicing with a demo account, I felt confident enough to dive into live trading. Excited by the potential for financial growth, I decided to invest my life savings of $150,000, along with taking out a mortgage on my house, viewing it as a strategic investment in trading Bitcoin. Initially, my efforts seemed fruitful as I quickly amassed a profit of $10,000 within the first few weeks. However, my newfound success was short-lived when I received a malicious email from an unknown sender, enticing me to invest on their behalf. Little did I know, it was a phishing scam designed to steal my personal information. In a cruel twist of fate, I lost access to my email account and all associated login details, including passwords to my cryptocurrency wallets. Panic and despair consumed me as I realized the extent of the deception. My hard-earned money and financial security were now in jeopardy, leaving me feeling helpless and vulnerable. In my darkest hour, a glimmer of hope emerged when I learned about ADRIAN LAMO HACKER through a trusted friend. Desperate for a solution, I reached out to them, hoping against hope that they could help me regain access to my lost funds and restore my peace of mind. ADRIAN LAMO HACKER's dedicated team of experts proved to be a lifeline in my time of need. With their unparalleled expertise and unwavering determination, they worked tirelessly to recover my stolen assets and restore access to my compromised accounts. Their thorough investigation uncovered crucial evidence, ultimately leading to the apprehension of the perpetrators responsible for the phishing scam. Through their invaluable assistance, I not only recovered my lost funds but also gained a newfound sense of security and confidence in navigating the digital landscape. The experience served as a poignant reminder of the importance of vigilance and caution when engaging in online activities, especially in the realm of cryptocurrency trading. In conclusion, my journey with ADRIAN LAMO HACKER was a testament to their unwavering commitment to assisting victims of digital scams. For anyone facing similar challenges, I wholeheartedly recommend ADRIAN LAMO HACKER as a trusted ally in reclaiming what rightfully belongs to them and restoring financial stability. Contact ADRIAN LAMO HACKER via the website: https : // adrianlamohackpro . online/
WhatsApp: +1 (909) 739‑0269 -
RECOVER BACK YOUR HARD EARN MONEY SCAMMED BY ONLINE IMPERSONATORS OR HACKERS FROM ANY PLATFORM.
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: D i g i t a l g o l d h u n t e r @ t e c h -c e n t e r . c o m1 -
As cryptocurrency continues to reshape global finance, safeguarding Bitcoin and other crypto wallets is more important than ever. Unfortunately, wallet access issues—whether due to lost passwords, forgotten seed phrases, or even hacking incidents—are a common challenge for Bitcoin owners. Century Web Recovery, trusted since 2017, has emerged as a reputable resource for those seeking to regain access to their cryptocurrency wallets.
What is Bitcoin Wallet Recovery?
Bitcoin wallet recovery is the process of retrieving access to a Bitcoin wallet when the user is locked out. Wallet access issues can occur for various reasons, such as lost private keys, forgotten passwords, or corrupted wallet files. For those who’ve lost access, reputable recovery services can be an invaluable asset, helping them safely regain control of their funds.
Century Web Recovery offers specialized recovery services that cover a broad range of wallet types and access issues, providing the expertise needed to retrieve lost assets and restore access to cryptocurrency wallets.
Why Wallet Recovery Services Matter
Without access to your wallet, Bitcoin holdings can become permanently inaccessible. The decentralized nature of Bitcoin means there’s no central authority or “forgot password” feature that can restore access. This gap has led to a high demand for trustworthy wallet recovery services like Century Web Recovery, which uses a combination of technical expertise and proprietary tools to assist clients.
Century Web Recovery: Trusted Bitcoin Wallet Recovery Since 2017
Century Web Recovery has built a reputation as a reliable and secure recovery service provider since its establishment in 2017. Their team is composed of experienced blockchain analysts and cybersecurity experts who specialize in recovering wallet access in cases of forgotten passwords, corrupted files, or lost keys. Clients seeking to regain access to Bitcoin wallets can learn more about Century Web Recovery can help by contacting them through the details provided below.
Century Web Recovery Approaches Wallet Recovery
Initial Consultation and Assessment
Century Web Recovery begins with a thorough consultation, understanding the client’s situation and the specific wallet issue. This assessment allows the team to determine the best recovery strategy.
Technical Recovery Process
Century Web uses advanced recovery tools and techniques tailored to different wallet types, whether software, hardware, or paper-based. By leveraging cryptographic methods and advanced decryption software, the team can restore access to wallets securely.
Ensuring Client Security and Confidentiality
Security and confidentiality are top priorities. Century Web Recovery applies secure handling protocols throughout the recovery process, ensuring that clients’ information and assets remain protected.
Recovery Completion and Client Education
Upon successful recovery, Century Web provides clients with guidance on how to safeguard their wallets and private keys to avoid future access issues. This education reinforces wallet security and fosters long-term peace of mind.
Why Choose Century Web Recovery?
Not only does Century Web Recovery have a strong track record of successful recoveries, but it also offers an upfront pricing model to keep costs transparent. For clients who are locked out of their wallets, the technical capabilities and secure approach Century Web offers make it a leading choice in the crypto recovery space.
Contact Century Web Recovery
To learn more or initiate the recovery process, clients can reach out to Century Web Recovery. If you’re locked out of your Bitcoin wallet, now is the time to restore access and regain control of your digital assets with a company that’s trusted since 2017. You can reach out to us by searching us on google century web recovery and get all our contact details.1 -
CHANCES OF CRYPTO RECOVERY OPTIONS:USE SPARTAN TECH GROUP RETRIEVAL
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) cyberservices . com
Telegram:+1 (581) 2 8 6 - 8 0 9 2
For many individuals and businesses, the experience of financial loss, whether caused by cyberattacks, data breaches, or unforeseen events, can feel overwhelming and intimidating. The emotional and financial toll can be immense, leaving people uncertain of where to turn. In these challenging times, SPARTAN TECH GROUP RETRIEVAL offers a crucial lifeline, providing expert services that guide clients through the recovery process with both skill and compassion. At SPARTAN TECH GROUP RETRIEVAL, the team recognizes the profound impact financial loss can have on clients, not only in terms of their finances but also on their sense of security and well-being. Their highly trained professionals specialize in assessing the full extent of damage caused by various disruptions, carefully identifying the underlying issues and working to develop tailored recovery strategies. Whether the challenge involves restoring lost data, recovering compromised systems, or securing vulnerable networks, SPARTAN TECH GROUP RETRIEVAL utilizes the latest technology and industry best practices to restore both operational efficiency and peace of mind. Data loss can be a particularly devastating consequence of a cyberattack or system failure. In a world where information is the lifeblood of businesses, recovering lost or corrupted data is crucial to regaining normal operations. SPARTAN TECH GROUP RETRIEVAL’s experts employ advanced data recovery techniques to retrieve vital information, ensuring that clients do not suffer irreversible setbacks. By recovering valuable data, they allow businesses to continue their operations with minimal disruption. Beyond data recovery, SPARTAN TECH GROUP RETRIEVAL excels at restoring and securing compromised systems. After a breach or attack, the threat of future vulnerabilities looms large. The team’s cybersecurity experts take swift action to secure networks and systems, implementing robust protection measures to defend against future threats. Through a combination of proactive monitoring, vulnerability assessments, and real-time security solutions, SPARTAN TECH GROUP RETRIEVAL works tirelessly to ensure that businesses and individuals can rebuild trust and safeguard their digital assets for the long term. However, what truly distinguishes SPARTAN TECH GROUP RETRIEVAL is its unwavering commitment to client care. While the technical aspects of recovery are vital, the company understands the emotional strain that often accompanies financial loss. Their compassionate case managers offer much-needed emotional support and practical guidance, helping clients navigate both the logistical and psychological challenges they face. By addressing the emotional as well as the practical aspects of recovery, SPARTAN TECH GROUP RETRIEVAL ensures that clients feel understood and supported throughout the entire process. In the face of financial hardship, SPARTAN TECH GROUP RETRIEVAL is a trusted partner that combines technical expertise with empathy and dedication. Their holistic approach ensures that businesses and individuals can recover, rebuild, and emerge from financial challenges stronger, more secure, and better prepared for the future. 1
1 -
POSSIBLE WAYS TO GET BACK EVERY PENNY LOSE TO SCAMMERS
At Digital Gold Hunters Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. com
whats App: +1 908 991 71321 -
BEST BITCOIN RECOVERY EXPERT TO RECOVER LOST OR STOLEN BITCOIN; USDT RECOVERY EXPERT HIRE CYBER CONSTABLE INTELLIGENCE
Working in conflict zones means improvising. When normal banking channels failed us, our NGO relied on Bitcoin to buy medical supplies directly. It worked, until a missile strike took out our field office, along with the hardware wallet that stored $410,000 in funds. Overnight, our ability to deliver life-saving aid is paralyzed.
Amidst the chaos, I reached out to contacts in the humanitarian world. A UN aid worker whispered a name: Cyber Constable Intelligence. "They're the ones who can help you recover lost crypto," he assured me. Despair and hope clashed as I dialed their team on a satellite phone in a conflict zone.
What followed was nothing short of a virtual rescue mission. Cyber Constable Intelligence's blockchain forensic experts didn't simply "recover" our assets; they improvised a fix like battlefield medics performing triage. They tracked our wallet's blockchain timestamps, reconstructing lost credentials from synced backups and transaction history.
Working under direst duress, we communicated information between spotty internet and backup power sources. Cyber Constable Intelligence team members improvised, rendering security protocols impenetrable as they worked through the jurisdictional nightmares of working within war zones. Every update from them was a pulse that kept our mission alive. After our last available backup failed, they instituted a complex cryptographic reconstruction technique, a process I still don't understand, but it worked.
Twelve days later, my satellite device displayed a message: "Access restored. Funds secured."
It was not money. It was bandages, antibiotics, clean water, and hope. Thanks to Cyber Constable Intelligence, we replenish our medical supplies, ensuring that patients, innocent victims who had been caught in the crossfire, received the treatment they deserved.
More than restoration, they advised us on decentralized storage and multi-signature security for long-term durability. We don't simply utilize Bitcoin presently; we utilize it astutely.
Now, each time I sign a crypto transaction, I remember that minute, receiving life-saving medication that might not have come but for this group.
In times of war, not every hero wears a uniform. Some carry keyboards, hunting down lost assets and securing humanitarian aid. Cyber Constable Intelligence not only restored our crypto, they kept our mission in the battle. If you think Bitcoin is just an investment, think again. To us, it's a lifeline.
CYBER CONSTABLE INTELLIGENCE INFO:
WhatsApp: 1 252378-7611
Website info; www cyberconstableintelligence com
Email Info cyberconstable@coolsite net
Telegram Info: @cyberconstable1 -
I HIGHLY RECOMEND ADWARE RECOVERY SPECIALIST AS THE BEST IN ALL FORM OF SCAMED RECOVERY
I cannot express how distraught I was when I realized someone had hacked my email and was conning my family and friends on Instagram to invest with me. The hacker was using my identity to lure them into a fraudulent investment scheme, and by the time we discovered what was happening, some of my family members and friends had fallen for it. They ended up wiring the fraudsters a total of $25,000 before they realized it wasn't me. The emotional and financial impact was devastating. Call or text: +18186265941 I felt helpless and violated, knowing that someone was using my name to deceive the people I care about the most. It was during this period of turmoil that a close friend told me about ADWARE RECOVERY SPECIALIST. She had been through a similar ordeal and had used their services to regain control of her digital life. Desperate for a solution, I reached out to the ADWARE RECOVERY SPECIALIST team. From the very first contact, they were understanding and professional. They explained the steps they would take to track down my email account, recover it, and secure it, along with my Instagram and other social media accounts. The process was thorough and efficient. The team at ADWARE RECOVERY SPECIALIST used their expertise to identify the breach points and secure my accounts against future attacks. They provided clear instructions on how to enhance my online security and even offered tips on maintaining privacy in the digital age. Within a few days, my email and social media accounts were back under my control. The relief was immense. Knowing that my accounts were secure and that the fraudsters no longer had access to them lifted a huge weight off my shoulders. My family and friends also felt reassured, seeing the proactive steps I was taking to prevent this from happening again. If you ever find yourself in a situation where your digital security is compromised, I highly recommend reaching out to ADWARE RECOVERY SPECIALIST. Their team is not only skilled in recovering and securing accounts but also empathetic to the distress such incidents cause. They offer a comprehensive solution to safeguard your digital presence, giving you peace of mind in a world where online threats are increasingly common. Don't wait until it's too late. Protect your digital life with ADWARE RECOVERY SPECIALIST and ensure that your personal information remains safe from those who seek to exploit it.
-
How to Recover Stolen Cryptocurrency: Hire a Genuine Recovery Expert – 2025
The search for how to recover stolen cryptocurrency has grown exponentially as more people become victims of crypto scams. Despite the belief that cryptocurrencies like Bitcoin offer robust security, they are not immune to risks. Even seasoned investors have found themselves at the mercy of scams or technical mishaps. Fortunately, with advancements in technology and expertise, recovering stolen or misplaced cryptocurrency is now possible with a high success rate.
Crypto recovery is a complex process that requires skill, precision, and trust in the recovery expert. Many fraudulent services claim to recover stolen assets but leave victims in a worse situation. This underscores the importance of working with verified and reliable recovery services. Among the most reputable in the industry is Puran Crypto Recovery. Known globally for its proven track record, the company has helped countless victims recover their lost assets.
To recover stolen cryptocurrency, the process typically involves engaging an expert recovery service. Victims must provide evidence such as transaction details, wallet addresses, and any information about fraudulent activities. The recovery expert, like Puran Crypto Recovery, conducts a detailed investigation using advanced tools and blockchain analysis to trace and recover the stolen funds. Their success lies in their methodical approach and a global team of blockchain specialists with years of experience.
Puran Crypto Recovery stands out not just for its technical expertise but also for its ethical practices. Their team includes blockchain investigators, ethical hackers, and security professionals, all working together to reunite clients with their lost assets. Using cutting-edge tools like artificial intelligence and advanced tracking technologies, the company ensures swift and accurate recoveries while adhering to legal guidelines.
Cryptocurrency scams take many forms, from phishing and Ponzi schemes to fake exchanges and wallet scams. Puran Crypto Recovery has tackled these challenges head-on, delivering success for victims of various fraud types. Their ability to navigate the complexities of blockchain transactions and identify fraudulent activities has earned them a global reputation for excellence.
Hiring a genuine recovery service like Puran Crypto Recovery is the first step in reclaiming your digital assets. Beyond recovery, the company also educates its clients on best practices to secure their cryptocurrency. This proactive approach reduces the risk of future losses and empowers users to protect their investments effectively.
For assistance in recovering stolen cryptocurrency, contact Puran Crypto Recovery Recovery Service. Their team of blockchain experts is dedicated to successfully recovering your stolen cryptocurrency and providing solutions to prevent future losses.8 -
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. c o m
whats App: +1 908 991 71321 -
POSSIBLE WAYS TO RECOVER BACK YOUR SCAMMED CRYPTO FROM ANY INVESTMENT PLATFORM...
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center . c o m1 -
THE BEST CRYPTO RECOVERY SERVICE HIRE ADWARE RECOVERY SPECIALIST
I’ve always been extremely careful with my hardware wallets, taking every precaution to ensure the safety of my cryptocurrency. But sometimes, life throws you a curveball, and you find yourself in a situation you never imagined. For me, that came when my Ledger, which contained $400,000 worth of Bitcoin, was damaged in a house fire. The fire was devastating in more ways than one. I had always believed the hardware was nearly indestructible, but after the incident, I couldn’t get the device to boot up at all. My heart sank as I tried everything to get it to work, only to be met with silence. As if that wasn’t bad enough, my backup phrase—the only thing that could have saved me—was stored in the same house and was completely lost in the fire. In a matter of hours, everything I had carefully built and protected felt like it was gone. I was beyond devastated. Losing both the device and my recovery phrase was something I had never prepared for. It felt like the ultimate nightmare. I contacted Ledger support, hoping for a miracle, but their solutions were limited to simple troubleshooting steps that couldn’t address the damage to my hardware. After exhausting their options, I realized I needed specialized help. I wasn’t ready to give up, so I started researching other possibilities. That’s when I discovered ADWARE RECOVERY SPECIALIST on a crypto security subreddit. The stories I read about their success in similar situations gave me a glimmer of hope. From the moment I reached out to them, ADWARE RECOVERY SPECIALIST was empathetic and professional. They understood the gravity of my situation and immediately began working on my case. They were transparent about their methods and didn’t promise the impossible, but they did reassure me that they had experience dealing with damaged hardware and would do everything in their power to recover my funds. I can’t even begin to describe the relief I felt when, just under a week later, they successfully retrieved every bit of Bitcoin I thought was lost forever. It felt like a miracle. I still can’t believe they pulled it off—they truly are ADWARE RECOVERY SPECIALIST! Not only did they recover my funds, but they also restored my peace of mind. I’ll never take security for granted again, but I know that if I ever find myself in a bind, ADWARE RECOVERY SPECIALIST is the team to contact. Get in touch with them with the information above: -
Late last month, I unintentionally fell for a cryptocurrency fraud. A Facebook imposter convinced me through a phishing scam of how I would make a sizable profit from a legitimate cryptocurrency company, which he claimed enabled traders to invest and make sizable profits. They took advantage of me and made off with $316,000 worth of cryptocurrency. As this was money I had worked so hard to obtain, I was shocked and uncomfortable. After reading favorable articles and internet reviews, I learned that “THE LION CYBER SECURITY COMPANY” is a licensed recovery firm that specializes in all types of hacking and cryptocurrency recovery. I immediately struck up a dialogue with the Experts, and I was able to get my money back. This is a token of appreciation to them, If you are a victim looking for an ethical hacker to help you get your money back, contact THE LION CYBER SECURITY COMPANY through any of the contact information listed below
 1
1 -
HOW TO RECOVER YOUR LOST BITCOIN
I lost €755,000 on my wallet because I couldn't remember my passcode and security words. I told a co-worker about my situation, and he suggested that I contact a legitimate hacker called THE HACK ANGELS RECOVERY EXPERT. They have the knowledge, tools, and experience to recover your funds. They not only gave me my Bitcoin back but also restored my peace of mind. I can’t express enough how much their expertise, professionalism, and dedication meant to me. If you are a victim and need to get your funds back, please don’t hesitate to contact THE HACK ANGELS RECOVERY EXPERT in any of the information below.
WhatsApp +1(520)200-2320)
I highly recommend them to anyone who has ever been in such a situation 1
1 -
WHATSAPP +1 252 378 7611 PROFESSIONAL BITCOIN RECOVERY EXPERT FOR HIRE CONTACT CYBER CONSTABLE INTELLIGENCE
Information of Cyber Constable Intelligence
WhatsApp info: + 1 2 5 2 3 7 8 7 6 1 1
Email info: (support (@) cyberconstableintelligence ). com)
As a retired dentist, I found myself with ample free time but limited financial security. In search of a way to grow my savings, I turned to cryptocurrency trading. I joined several online forums and communities, where I read about the success others had found with Bitcoin. Their testimonies inspired me to take the plunge. With careful research and strategic investments, I managed to turn my initial investment into $250,000.The financial success brought a renewed sense of purpose and stability to my retirement. However, this newfound prosperity also attracted the envy of someone close to me: my financial advisor, whom I had trusted for years. Unbeknownst to me, he had been monitoring my success closely. One evening, while I was cooking supper, my financial advisor accessed my phone and changed the passwords to my accounts, attempting to transfer my Bitcoin to his wallet. I discovered this betrayal shortly after, feeling a mix of shock, panic, and anger. My financial future was in jeopardy, and I needed to act quickly. In my desperate search for a solution, I stumbled upon Cyber Constable Intelligence, a service specializing in recovering hacked accounts and lost cryptocurrency. With my savings hanging in the balance, I reached out to them, hoping for a miracle. The team at Cyber Constable Intelligence was prompt and professional. They reassured me that, despite the seriousness of my situation, there was a good chance they could help. Their calm and confident demeanor provided some much-needed comfort. They guided me through the recovery process, taking over the technical aspects and working tirelessly to regain control of my accounts. In a remarkably short time, Cyber Constable Intelligence managed to restore my access to my accounts and secure my Bitcoin. The relief I felt was indescribable. Not only had they recovered my funds, but they also provided essential advice on how to enhance the security of my digital assets. This experience taught me several valuable lessons. Firstly, trust must be carefully placed, even with long-term associates. Secondly, it's crucial to secure your digital assets with strong, unique passwords and two-factor authentication. Lastly, seeking professional help in times of crisis can make all the difference. After regaining control of my accounts, I severed ties with my financial advisor and took steps to ensure my assets were protected. Despite the ordeal, I emerged more knowledgeable and determined to safeguard my future. My experience with Cyber Constable Intelligence not only saved my investments but also reinforced the importance of vigilance and security in the digital age. -
THE BEST CRYPTO RECOVERY SERVICE IN 2024 HIRE DUNAMIS CYBER SOLUTION
A
Cautionary Tale About a Sophisticated Scam Three days ago, I fell victim to a highly sophisticated scam that cost me 30,000 Euros. As a London resident, I’ve always prioritized online security. When I heard about the LastPass breach, I immediately changed my passwords, believing my information was safe. However, I soon realized that the worst was yet to come.The scam started with an email that appeared to be from LastPass, warning me about unusual activity. It seemed legitimate—complete with branding and an urgent subject line. The email included a customer support number, which I called in panic.A calm, professional-sounding individual answered, claiming to be a LastPass security expert. They told me my account had been compromised and advised me to install recovery software. Trusting them, I followed their instructions without realizing I was being scammed.Hours later, I discovered that 30,000 Euros had been drained from my bank accounts. After the initial shock, I found DUNAMIS CYBER SOLUTION Recovery, a company specializing in scam recovery. They acted swiftly, helping me trace the scammers and recover the stolen funds.While the experience was harrowing, it taught me an invaluable lesson: Always verify the authenticity of any communication, no matter how convincing it seems. If you fall victim to a scam, don’t hesitate to reach out to experts who can help you recover. 8
8 -
Why I Trust CRYPTO RECOVERY CONSULTANT With My Digital Future
As a former intelligence officer, I thought I knew everything about security. My job was all about protecting classified information, so when it came to my Bitcoin wallet, I went all in. I created a password so complex, it was virtually unbreakable. At first, I laughed it off surely I’d remember eventually. But try after try, nothing worked. That’s when the horror set in. I had locked myself out of my own wallet. My $1 million was sitting there, completely untouched… and completely unreachable. I felt embarrassed, frustrated, and desperate. That’s when I came across *CRYPTO RECOVERY CONSULTANT*. Honestly, I didn’t have high hopes. I assumed I was out of luck. But from the moment we spoke, they treated my case seriously like a high level op. No judgment, just focus and professionalism. They explained their method clearly and assured me it wouldn’t risk my funds. It wasn’t fast or easy there were delays and doubts but they stayed committed. And finally, they did it. They recovered my wallet. The relief I felt was beyond words. It wasn’t just about the money it was about redemption. I hadn’t lost everything after all. The biggest lesson? Sometimes, simple is smarter. I had tried to outsmart potential threats and ended up being the threat myself. Security doesn’t have to be complicated to be effective.If you ever find yourself locked out, don’t give up. I trusted CRYPTO RECOVERY CONSULTANT, and they brought me back from the brink. For that, I’ll always be grateful.WhatsApp: +19842580430 cryptorecoveryconsultant :@: cash4u com2 -
About Me
As a dedicated and skilled Security Analyst in the Cyber Wing, I bring a wealth of expertise in identifying, assessing, and mitigating cyber threats to protect organizational assets and sensitive information. My background is grounded in a robust understanding of cybersecurity principles, which I apply daily to safeguard against evolving digital threats.
Professional Background
With a strong foundation in cybersecurity, I have honed my skills in threat analysis, risk assessment, and incident response. My role involves continuous monitoring of network traffic, identifying vulnerabilities, and implementing security measures to prevent data breaches. I am proficient in using advanced cybersecurity tools and technologies to analyze threat intelligence and develop strategies to defend against cyber-attacks.
Key Competencies
Threat Analysis: Expert in identifying and analyzing potential threats to cybersecurity, including malware, phishing attacks, and network intrusions.
Risk Assessment: Skilled in evaluating the security posture of systems and networks, identifying vulnerabilities, and recommending corrective actions.
Incident Response: Experienced in managing and responding to security incidents, ensuring quick resolution and minimizing impact on operations.
Security Protocols: Knowledgeable in implementing and maintaining security protocols and policies to ensure compliance with industry standards and regulations.
Achievements
Successfully mitigated multiple cyber threats, reducing potential impact on organizational operations.
Developed and implemented security policies that enhanced the overall security posture of the organization.
Conducted comprehensive security assessments that led to significant improvements in network security and data protection.
Professional Goals
My goal as a Security Analyst is to continue advancing my expertise in cybersecurity, staying abreast of the latest trends and technologies to effectively combat emerging threats. I am committed to contributing to a safer digital environment and ensuring the highest level of security for the organization.
Personal Attributes
I am a proactive and detail-oriented professional, known for my analytical thinking and problem-solving abilities. I thrive in dynamic environments and am passionate about leveraging my skills to protect against cyber threats.
Contact elctrohacker DOT COM
Feel free to reach out to me for any inquiries or to discuss how I can contribute to enhancing your organization's cybersecurity posture. -
For players in Bangladesh seeking a reliable source of information about online casinos and sports betting, https://pinupbd.blog/ has become a central hub worth exploring. This platform isn’t just another affiliate site – it’s a dedicated blog offering news, reviews, tutorials, and expert tips tailored specifically for Bangladeshi users interested in the Pin-Up gaming ecosystem.
The blog provides detailed insights into how to register and deposit safely using local methods like bKash, Nagad, and Rocket. It also walks readers through the latest promotions, bonuses, and updates across Pin-Up’s casino and sportsbook platforms. Whether you're curious about the newest slot releases or want to learn how to place smarter bets on cricket or football, the blog provides step-by-step guidance that’s easy to understand.
Additionally, keeps users updated on changes in gaming laws, platform security, and responsible gambling measures in Bangladesh. With a clean design, helpful visuals, and frequently updated content, this site has become an essential resource for both beginner and seasoned gamblers who want to make informed decisions while enjoying their favorite games online.3 -
Top Benefits of Using Data Loss Prevention in Microsoft 365
Data Loss Prevention (DLP) in Microsoft 365 offers numerous benefits to organizations aiming to protect sensitive information and ensure compliance. One of the top advantages is enhanced data protection, where DLP policies help identify, monitor, and restrict the sharing of sensitive information like credit card details or personal identification numbers across Microsoft 365 apps (Outlook, SharePoint, OneDrive, and Teams). This proactive security measure prevents unauthorized access or accidental sharing of confidential data.
Another key benefit is regulatory compliance. DLP helps organizations comply with data protection regulations such as GDPR, HIPAA, and CCPA by enforcing policies that limit data exposure and unauthorized sharing, reducing the risk of costly fines.
Microsoft 365 DLP also offers visibility and control. IT administrators can monitor user actions and identify potential risks in real time, making it easier to enforce security measures. Additionally, user education is integrated through policy tips, which educate users about data protection during daily tasks.
Finally, DLP offers seamless integration across all Microsoft 365 platforms, making it easy to manage and enforce consistent security policies across emails, documents, and collaborative tools, ensuring comprehensive protection for the entire organization. -
As the head of Quantum Innovations, based in Seattle, Washington, I’ve always taken pride in our company’s commitment to cutting-edge technology and innovation. However, a recent security breach has underscored how vulnerable we were to a major cybersecurity threat involving our corporate mobile devices. The breach began when several employees unknowingly downloaded a malicious app from a third-party app store. What initially appeared to be a harmless app turned out to contain malware, granting cybercriminals access to sensitive company data. In total, the attackers stole approximately $200,000 USD worth of proprietary business information, including financial records, intellectual property, and confidential communications. Even more alarming, the breach led to the theft of employee banking details, enabling unauthorized transfers of funds from both personal and corporate accounts. The breach was discovered when our IT team noticed unusual activity on the affected devices, including unauthorized access to secure files and suspicious data transfers. After conducting a thorough investigation, we realized that the malware had been secretly transmitting our valuable data to an external server, including sensitive financial information. At that point, it became clear that the situation was far worse than we had initially anticipated.In response to this crisis, I reached out to TRUST GEEKS HACK EXPERT at Web, https :/ / t r u s t g e e k s h a c k e x p e r t . c o m/ E m a i l : i n f o @ t r u s t g e e k s h a c k e x p e r t.c o m And T e l e G r a m:: T r u s t g e e k s h a c k e x p e r t, A renowned cybersecurity firm with a reputation for its expertise in mobile device security and data recovery. Their team acted swiftly to assess the full scope of the attack, clean the infected devices, and secure our mobile systems.Thanks to their expert intervention, we were able to completely remove the malware from all affected devices, TRUST GEEKS HACK EXPERT data recovery specialists went above and beyond to recover not only the stolen company data but also the funds that had been illicitly transferred from both employee and corporate bank accounts. Through negotiation with authorities and tracking the stolen funds, they successfully managed to recover every dollar that had been taken. Their diligence and expertise were truly exceptional, and because of their efforts, we were able to avert what could have been a catastrophic financial loss.In the wake of this breach, we are more committed than ever to fortifying our security measures. The swift response and effective recovery efforts from TRUST GEEKS HACK EXPERT have been invaluable in restoring our confidence and securing our operations.1
-
HOW MY CARBON NEUTRAL BITCOIN WAS HELD HOSTAGE AND RESCUED BY ASSET RESCUE SPECIALIST
I believed in a cleaner tomorrow, one where blockchain and renewable energy were not enemies. My wind farm was proof. Excess energy powered my Bitcoin mining machines, a closed loop. It was the future. Until the ransomware attack.
My turbines hummed one morning as they always did, but my mining operation? Gone. My wallet? Locked. One message replaced my screen:
"Create a payment of 5 BTC to free your information. You have 72 hours."
The irony? My carbon-neutral Bitcoin had been taken hostage.
I panicked. I had crafted my system for survival, yet here I was, stuck. Perplexed, I went to industry colleagues. That's when one panelist from a Clean Energy Summit contacted me:
"Consider ASSET RESCUE SPECIALIST. They provide blockchain forensics, and they're carbon neutral!"
I was desperate but skeptical. During my first call, their personnel were talking my language, both security and sustainability. They did not just care about Bitcoin; they cared about why I was mining it.
Their approach? Genius. Instead of negotiating with the hackers, they reverse-engineered the ransomware. My infrastructure had been attacked through a zero-day vulnerability in the grid software, not my specific setup.
This wasn't a solo problem. This was an energy security emergency for the entire region.
Over 12 frenetic days, ASSET RESCUE SPECIALIST, worked with good-faith hackers and clean-energy engineers. They did not simply recover my Bitcoin without giving a ransom to attackers, they also fixed the flaw that had jeopardized our grid in the first place.
When I was finally able to log back in to my wallet, I felt like I'd regained not only my Bitcoin, but command over my vision.
My wind farm is now more secure than ever. ASSET RESCUE SPECIALIST, even helped us implement decentralized security protocols to prevent future hacks. And the icing on the cake? Their carbon offsets make their entire operation all about aligning with my emphasis on sustainability.
I once believed that Bitcoin and green energy were the perfect pair, but now I understand security is the third leg.
If you work in cleantech and disaster strikes? ASSET RESCUE SPECIALIST, is not a rescue team, they are a renewable power. 1
1 -
How Recuva Hacker Solutions Can Help You
For investors seeking to recover lost funds, Recuva Hacker Solutions offers a streamlined and stress-free process. Clients are guided through collecting evidence, such as transaction IDs and communication records, to strengthen their recovery case. The company’s team of experts uses advanced blockchain forensics and cutting-edge tools to trace and reclaim stolen or lost digital assets.
Trust and Security at the Core
Recuva Hacker Solutions prioritizes the safety and privacy of their clients. Their processes adhere to strict ethical standards and global regulations, ensuring that recoveries are conducted securely and legitimately.
Contact Recuva Hacker Solutions Today
Investors looking to recover their cryptocurrency investments can rely on Recuva Hacker Solutions for expert assistance. Contact them at [recuvahackersolutions @ consultus . co site] or visit their website at [https : / / recuvahacksolution . pro] for more information.
Recuva Hacker Solutions is your trusted partner in navigating the complexities of crypto recovery, ensuring your investments are safe and secure in 2025.13 -
RECOVER MONEY FROM BITCOIN SCAM HIRE ADWARE RECOVERY SPECIALIST
WhatsApp info:+12723 328 343
Website info: http s:// adware recovery specialist. com
Email info: Adware recovery specialist (@) auctioneer. net
Telegram info: h t t p s:// t.me/ adware recovery specialist1
I had lost my login credentials and was unable to access my funds. It was a stressful and frustrating situation, as I had no way of retrieving the information and no one to turn to for help. My financial situation was tied to these credentials, and without them, I felt completely helpless. I tried everything I could think of—password resets, security questions, even reaching out to customer support—but nothing worked. The feeling of being locked out of something so important was overwhelming, and I wasn’t sure where to go next. After countless attempts and hours of stress, I started to lose hope. That’s when I came across a service called ADWARE RECOVERY SPECIALIST. At first, I was hesitant, unsure whether they could really help me or if they were just another scam. But after reading through some testimonials and seeing their track record of successfully recovering lost login credentials, I decided to give them a try. I’m so glad I did. The process was surprisingly smooth. I reached out to their team, explained my situation, and provided any necessary details. They were prompt and professional, offering clear instructions on what would happen next. Within a short period, they were able to crack my lost credentials and give me access to my account once again. The relief I felt when I successfully logged in and saw my funds intact was indescribable. It was like a weight had been lifted off my shoulders. What really stood out to me was the level of expertise and care that ADWARE RECOVERY SPECIALIST demonstrated. They didn’t just recover my login information; they made sure I understood what had happened and took steps to ensure my account’s security moving forward. They were patient, understanding, and transparent throughout the entire process, which made the experience feel much more reassuring. I truly can’t thank ADWARE RECOVERY SPECIALIST enough for their help. They restored my access to my funds when I thought all hope was lost. If you ever find yourself in a similar situation, I would highly recommend their services. They not only solved my problem, but they also gave me peace of mind during a time when I needed it most.3 -
How Hackers Gained Access to My Crypto Wallet and Sensitive Data through a Keylogger sent to my device through a phishing email.
I’ll advise others to be wary of the kind of emails they open, as this happened a few weeks ago when a phishing email was sent to my email unknowingly to me that it was a keylogger with the intent of stealing my private information and if not for the intervention of Morphohack Cyber Services, I would have been cleaned out completely. I contacted Morphohack Cyber Services a week after that incident and they detected the keylogger in my computer which has been there for months stealing my private information. If my crypto wallet was not drained, I would not have been aware of the keylogger in my device. Morphohack was able to secure my devices and retrieve my crypto wallet including the crypto assets. Their sophisticated security features and malware can beat any hacking tools available and they are very professional and ethical. Morphohack is a lifesaver and I hugely recommend their services. Their E-mail. Morphohack@Cyberservices. com & WhatsApp. +1 - 213 - 672 - 40921 -
CENTURY WEB RECOVERY is a reputable entity known for offering top-quality services in cryptocurrency recovery. They provide a vital lifeline to individuals who have fallen victim to theft or other mishaps in the digital currency realm.
Comprehensive Cryptocurrency Recovery Services
CENTURY WEB RECOVERY specializes in:
Accessing Inaccessible Funds: They address security issues that may prevent you from accessing your digital assets.
Retrieving Lost Passwords: Using advanced techniques, they can recover lost passwords, ensuring you regain control over your cryptocurrency accounts.
Contact Information
For inquiries or assistance, you can reach out to CENTURY WEB RECOVERY through the following channels:
· Email: century[@]cyberservices[.]com
· WhatsApp: +1,3,8,6,2,6,0,8,0,5,2
Conclusion
CENTURY WEB RECOVERY stands out as a reliable choice for those in need of cryptocurrency recovery services. With their expertise and advanced recovery techniques, they offer a beacon of hope for individuals seeking to reclaim their digital assets.1 -
Email: casefile @ shi -us . com
I lost my MacBook laptop some time ago alongside my iphone 16, in that process all my crypto coinbase accounts, about 3 of them, I had difficulties logging in and I consulted lots of agencies to assist but all to no avail, until I came across Santoshi Hackers Intelligence and within a twinkle of an eye it was all done.
If you suspect your Credit card, email & password, Facebook, Instagram, twitter Accounts has been hacked, you need to Recover stolen money from scammers, reports the incident to Santoshi Hackers Intelligence they can help you recover your BTC by providing an experience team of security experts and forensic investigators who can investigate the loss, identify the source of the compromise, Santoshi we help you retrieve your stolen currency, in addition, Santoshi Hackers Intelligence can provide you with educational materials for staying safe online and give you access to cutting_edge cyber threat intelligence. They can also identify potential security breaches or vulnerabilities that may have led to the loss of your information.
Above is the email address to reach Santoshi Hackers Intelligence.1 -
CONSULT PROFESSIONAL BITCOIN RECOVERY EXPERTS // MAESTRO ENCRYPTER FINANCIER
You want to hear confidence-boosting success tales about getting your lost bitcoins back. Maestro Encrypter Financier has a remarkable history of assisting people and companies in getting their lost money back. Consider the instance of Connor Jack , who unintentionally sent his bitcoins to the incorrect address. Connor's face returned after Maestro Encrypter Financier used their knowledge and tenacity to track down the transaction and get his bitcoins back.
What distinguishes Maestro Encrypter Financier from other alternatives for recovering bitcoin? Above all, their team of professionals is well-versed in handling bitcoin transactions, which enables them to handle even the most complicated circumstances. Furthermore, their customer-focused methodology guarantees that you will receive tailored support and consistent updates during the recuperation procedure. To demonstrate the superiority of Maestro Encrypter Financier, let's compare their performance with that of their competitors. In a head-to-head analysis, Maestro Encrypter Financier consistently outperformed other recovery services in terms of success rate, speed of recovery, and customer satisfaction. Time and time again, they have proven their ability to recover lost bitcoins when others have failed. At Maestro Encrypter Financier, your privacy and confidentiality are of utmost importance. They employ robust security measures to safeguard your personal information and ensure that it remains strictly confidential. You can trust that your data is in safe hands throughout the recovery process. Not only does Maestro Encrypter Financier excel in recovering lost bitcoins, but they also prioritize helping clients protect their funds from future loss. Their team provides expert advice on the latest security practices, including wallet management and secure transaction techniques. By equipping you with the knowledge to safeguard your investments, Maestro Encrypter Financier goes above and beyond to ensure your long-term financial security. For enquiry, Email:(maestroencrypter @ financier . com) or call/ WhatsApp:+14722038937 4
4 -
HOW I WAS ABLE TO RETRIEVE MY LOST BTC AND USDT WITH THE HELP OF THE HACK ANGELS
Getting back your stolen bitcoins is very easy but there are also lots of fraudulent recovery firms out there so one needs to be careful not to end up being defrauded again. When my world seemed to crumble after losing a significant amount of Bitcoin. I was devastated. I came across numerous testimonials about THE HACK ANGELS RECOVERY COMPANY, a crypto recovery and cyber security company. I sent him a direct message Contact inform:
WhatsApp +1(520)200-2320 )
He listened to my concerns to which he replied and requested some information, which I also provided. To my surprise, I was able to reclaim what I thought was lost forever. I am forever grateful for the exceptional service provided by THE HACK ANGELS RECOVERY COMPANY 1
1 -
HOW I GOT MY STOLEN CRYPTO MONEY BACK WITH THE ASSISTANCE OF GHOST CYBER RECOVERY
Ghost Cyber Recovery is for anyone seeking to recover their data or funds lost to scammers on the internet. this cyber security firm helped me get my bitcoin and lost digital money back. Their skilled work and exceptional service have absolutely astonished me. I never would have believed that I could get my money back until I went to them, explained my situation, and gave them all the information I needed. I was astounded that it took them 72 hours to get my money back. I wholeheartedly endorse Ghost Cyber Recovery for any and all cryptocurrency, digital fund, hacking, and cybersecurity-related problems. get in touch to recover your lost funds
E mail: (ghostcyberrecovery @ gmail . com ) or WhatsApp +1 734 743 18733 -
RECOVER YOUR SCAMMED FUNDS AND CRYPTOCURRENCY HIRE iFORCE HACKER RECOVERY
iFORCE HACKER RECOVERY consists of professional hackers who specialize in securing compromised devices, accounts, and websites, as well as recovering stolen bitcoin and funds lost to scams. They operate efficiently and securely, ensuring a swift resolution without alerting external parties. From the very beginning, they have successfully delivered on their promises while maintaining complete discretion. Few organizations take the extra step to investigate network security risks, provide critical information, or handle sensitive matters with such professionalism. The iFORCE HACKER RECOVERY team helped me retrieve $364,000 that had been stolen from my corporate bitcoin wallet. I am incredibly grateful for their assistance and for providing me with additional insights into the unidentified individuals behind the theft.
Email; contact@iforcehackersrecovery. com
whatsapp; +1 240. 803. 3. 7061 -
My name is Sharron Maggie , and I’m a graduate of Stanford University. After finishing my degree, I faced immense challenges in finding a sustainable job that would allow me to pay off my student loans and live the life I desired. In my search for financial stability, I stumbled upon cryptocurrency trading, specifically Bitcoin. I invested hoping to turn my situation around, and I watched my assets soar to an impressive $500,000.
However, my journey took a dark turn when I received an email that appeared to be from my crypto exchange, prompting me to verify my account. I clicked the link and entered my information, only to realize minutes later that it was a phishing scam. In an instant, my account was drained of all its funds. Feeling desperate and devastated, I turned to a friend who had faced similar challenges, and he recommended Trust Geeks Hack Expert. Skeptical but with nothing to lose, I decided to contact them. From the first interaction, their team was incredibly responsive and professional, assuring me they had successfully handled cases like mine.
Trust Geeks Hack Expert immediately began securing my accounts and tracing the transactions. They worked with cybersecurity experts to freeze any fraudulent transfers and managed to recover a significant portion of my assets. Their expertise was impressive, and they took the time to educate me about the importance of strong, unique passwords and enabling two-factor authentication. What stood out to me was their holistic approach to the recovery process. Trust Geeks Hack Expert not only focused on retrieving my funds but also guided me in enhancing my online security to prevent future attacks. They taught me to recognize phishing scams and reinforced the need for robust security practices.
This experience was a harsh but valuable lesson in online security. It made me more vigilant about my digital presence and interactions. Thanks to Trust Geeks Hack Expert, I not only regained most of my assets but also acquired essential knowledge on protecting my investments moving forward. If you ever find yourself in a similar situation, I wholeheartedly recommend reaching out to Trust Geeks Hack Expert.
(CONTACT SERVICE )
E ma il ---> Trustgeekshackexpert [At] fast service . com
Tele gram ID ---> Trustgeekshackexpert
Web site ----> https :// trustgeekshackexpert. com/ -
I want to express my sincere gratitude and appreciation to Wizard James Recovery Company for helping me get my $143,000 worth of stolen cryptocurrency back. At first, I was hesitant to give it a try and felt like there was no chance, but now I'm thrilled to talk about this cyber security firm because they were able to help me get my stolen digital money and cryptocurrency back. Their skilled work and outstanding service have absolutely impressed me. Before I went to them with my issues and gave them all the information I needed, I never imagined that I would be able to receive my money back. I was astounded when it took them seventy-two hours to get my money. For any of your bitcoin recovery, digital funds recovery, hacking, and cybersecurity-related needs, I would without a doubt heartily suggest Wizard James Recovery. They are without a doubt the greatest, and I am extremely grateful to them for assisting me in getting my money back. Do not hesitate to contact them at [WhatsApp_+447418367204] if you are experiencing similar problems to mine.2
-
IS Technology: Your Trusted Partner for Small Business Support and IT Services
In the modern business landscape, technology plays a crucial role in driving efficiency and success. For small businesses, managing technology and staying ahead of IT challenges can be overwhelming. At IS Technology, we are here to provide expert small business support and IT services to help your business thrive. Located at 12 National Ave, Fletcher, NC 28732, we offer tailored solutions designed to meet the unique needs of small businesses, enabling you to focus on what matters most—growing your business.
Why Small Businesses Need IT Support
Small businesses often face unique challenges when it comes to technology. With limited resources, it’s crucial to make the most of your technology infrastructure while minimizing downtime and security risks. IS Technology specializes in providing small business support that empowers your company to run efficiently, securely, and seamlessly. Our IT services are designed to help you:
Reduce IT Costs
Outsourcing your IT services to a trusted provider like IS Technology can save your business significant costs compared to hiring a full-time, in-house IT team. With our flexible support packages, you only pay for the services you need, when you need them.
Stay Competitive
In today’s digital-first world, small businesses need to leverage the latest technology to remain competitive. Whether it's cloud computing, advanced cybersecurity, or efficient networking, we provide the tools and expertise you need to stay ahead of the curve.
Improve Efficiency
Technology should simplify your business operations, not complicate them. Our small business support services ensure that your IT services are optimized for maximum productivity, reducing downtime and streamlining your workflows.
Enhance Security
Cybersecurity is critical for small businesses that handle sensitive customer data and financial information. IS Technology offers robust security solutions that protect your business from potential threats, ensuring that your information is safe and your systems are secure.
Our IT Services: Tailored for Small Businesses
At IS Technology, we offer a wide range of IT services specifically designed to meet the needs of small businesses. Whether you’re looking for a comprehensive IT support package or specialized services, we have the expertise to provide solutions that fit your business requirements.
Managed IT Services
Our managed IT services are designed to provide proactive support, ensuring that your systems are running smoothly 24/7. From regular software updates to monitoring your network for potential issues, we handle everything so you can focus on growing your business.
Network Setup & Support
A strong, reliable network is essential for business success. We provide network setup and support to ensure that your business's technology infrastructure is seamless and scalable. Whether you need help setting up a new office network or optimizing your existing setup, we’ve got you covered.
Cloud Solutions
Cloud computing offers flexibility and cost savings that traditional IT infrastructure simply can’t match. We provide cloud solutions that allow you to store and access your data securely from anywhere. With our help, your small business can benefit from enhanced collaboration, seamless data sharing, and reliable disaster recovery.
Cybersecurity Services
Small businesses are often targets for cybercriminals due to their perceived vulnerabilities. At IS Technology, we provide advanced cybersecurity services to safeguard your business against cyber threats. Our services include firewalls, antivirus software, encryption, and security audits to protect your data and systems from potential breaches.
Tech Support & Troubleshooting
When technical issues arise, you need reliable tech support to minimize downtime. Our team is available to troubleshoot problems quickly and efficiently, ensuring your business is back on track in no time. Whether it’s hardware malfunctions or software issues, we’re here to help.
IT Consulting
As a small business, you might not always know which technology solutions are best for your needs. Our IT consulting services provide expert guidance to help you make informed decisions about your technology investments. Whether you need advice on upgrading your infrastructure or choosing the right software for your business, we offer tailored recommendations that align with your goals.
Why Choose IS Technology for Small Business Support?
Tailored Solutions for Your Business
At IS Technology, we understand that every small business is different. That’s why we provide small business support that is customized to meet the specific needs of your business. We take the time to understand your goals and challenges, and we design IT services that align with your objectives5 -
Lost Your Bitcoin? Here Is How You Can Recover It Visit...CYBERSPACE HACK PRO.
Info.
WhatsApp: +1 (559) 508-2403
Email: Cyberspacehackpro(at)rescueteam com
Nobody likes being left in the dark, especially when it comes to something as nerve-wracking as lost bitcoin. A reliable recovery team should provide excellent customer support and maintain clear lines of communication throughout the recovery process. Nothing beats a team that keeps you in the loop, easing your worries and giving you peace of mind knowing that your precious crypto is in good hands. If you are trusting a recovery team with your lost bitcoin, you need make sure they have a solid reputation and a successful track record. Examine reviews, conduct research, and seek advice from members of the cryptocurrency community. After all, you should choose a team with a strong track record of accomplishment if you are going to entrust your digital future to them. In order to handle even the most difficult recovery tasks, Cyberspace Hack Pro employs sophisticated tactics and strategies rather than just relying on simple tricks behind their sleeves. These experts go above and above using complex programming abilities and forensic investigation to recover your missing bitcoin. To get those dazzling digital coins back into your possession, they don't just take the simple route. Instead, they go above and beyond. In the realm of bitcoin recovery, the appropriate tools are essential, and Cyberspace Hack Pro possesses the enchanted toolbox necessary to accomplish the task. They search every digital corner for your misplaced bitcoin, thanks to their access to state-of-the-art hardware and software. They have the technology to make those missing funds appear again like a visual trick you won't believe, from sophisticated blockchain scanners to password recovery programs. When it comes to something as valuable and sensitive as recovering lost bitcoin, security and privacy are of utmost importance. At Cyberspace Hack Pro, we understand the need for robust security measures to protect your assets and personal information. 5
5 -
Best Crypto Scam Recovery | Crypto Recovery Expert - Hire Captain WebGenesis Crypto Recovery Center To Recover Stolen Crypto.
CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER has established himself as a major authority in bitcoin recovery due to his significant knowledge and expertise in the industry. With a thorough understanding of blockchain technology, encryption, and cybersecurity, CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER has successfully assisted several individuals in recovering lost or stolen cryptocurrency. His knowledge spans multiple digital assets, including Bitcoin, Ethereum, and Litecoin, allowing him to navigate complex cryptocurrency wallets and fix security flaws with precision. His thorough approach and drive to staying ahead of developing trends in the sector have earned him the trust of investors looking for trusted solutions to secure their digital assets.
For more information, contact them at
captainwebgenesis(@) hackermail(.) com
Website; Captainwebgenesis. com1 -
Best in Recovery Stolen Bitcoin: Vacuum Cyber Hack can Help you out
When I realised my $395,000 worth of Bitcoin had been stolen, I was devastated. The thought of losing such a significant amount left me feeling completely powerless. After exhausting all options, I decided to reach out to Vacuum Cyber Hack. Their reputation for successfully recovering stolen cryptocurrency made them the obvious choice. From the very beginning, I was impressed by their professionalism and expertise. They quickly assessed my situation and immediately began working on a recovery plan. Using advanced algorithms and state-of-the-art forensic methods, Vacuum Cyber Hack tracked the stolen funds with remarkable precision. Throughout the process, they kept me updated, providing clear communication and ensuring my sensitive information remained confidential. Within a short time, Vacuum Cyber Hack successfully recovered my stolen Bitcoin, returning my funds and restoring my confidence in cryptocurrency security. Their efficiency, dedication, and ethical approach made all the difference. I’m incredibly grateful to Vacuum Cyber Hack for their exceptional service and for proving that even in the most challenging situations, recovery is possible. They truly set the standard for Bitcoin recovery services. I can confidently recommend them as the best choice for anyone facing the same challenge.
Email: support @ vacuumcyberhack . com
Whatsapp: +39 351 059 0507
Website: https : //vacuumcyber hack .co m/2 -
Best in Recovery Stolen Bitcoin: Vacuum Cyber Hack can Help you out
When I realised my $395,000 worth of Bitcoin had been stolen, I was devastated. The thought of losing such a significant amount left me feeling completely powerless. After exhausting all options, I decided to reach out to Vacuum Cyber Hack. Their reputation for successfully recovering stolen cryptocurrency made them the obvious choice. From the very beginning, I was impressed by their professionalism and expertise. They quickly assessed my situation and immediately began working on a recovery plan. Using advanced algorithms and state-of-the-art forensic methods, Vacuum Cyber Hack tracked the stolen funds with remarkable precision. Throughout the process, they kept me updated, providing clear communication and ensuring my sensitive information remained confidential. Within a short time, Vacuum Cyber Hack successfully recovered my stolen Bitcoin, returning my funds and restoring my confidence in cryptocurrency security. Their efficiency, dedication, and ethical approach made all the difference. I’m incredibly grateful to Vacuum Cyber Hack for their exceptional service and for proving that even in the most challenging situations, recovery is possible. They truly set the standard for Bitcoin recovery services. I can confidently recommend them as the best choice for anyone facing the same challenge.
Email: support @ vacuumcyberhack . com
Whatsapp: +39 351 059 0507
Website: https : //vacuumcyber hack .co m/ 1
1 -
My crypto wallet was compromised when I lost my secret phrase.
Hackers got a hold of my crypto wallet after I lost the seed phrase to my crypto wallet which I had saved to my email.
I had to go through all possible options to get it figured out but I couldn’t, the support system of Coinbase couldn’t help even when I had secured my account with the special seed phrase for extra security, and that was how I lost access to $2m worth of crypto coins.
This was my life savings and investment from my business partners which I had secured in my crypto wallet. Fortunately, I happen to stumble upon a post about MorphoHack Cyber Service, a crypto wallet and funds recovery company. I contacted this team and told them about the whole situation, while I was a bit reluctant about trusting them with my information, it happened there was nothing I couldn’t do to get my funds back so I went with everything they asked, and to my greatest satisfaction, MorphoHack cyber-service was able to give me access to my crypto wallet including securing my crypto wallet from future attempts. I’m in shock and short of words but if you wish to get a hold of them, you can find their contact details below.
MAIL:MorphoHack@CyberServices. com
WHATS APP:+1 213 672- 4092
WEB:MORPHOHACK.WIXSITE. COM/ CYBER1 -
TRUSTWORTHY CRYPTO RECOVERY SERVICE- HIRE SALVAGE ASSET RECOVERY
At Tax Ease Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Salvage Asset Recovery. Salvage Asset Recovery’s team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform. Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Salvage Asset Recovery has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Salvage Asset Recovery helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information. Thanks to the quick and efficient actions of Salvage Asset Recovery, Tax Ease Solutions was able to recover $980,000 of the lost funds and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Salvage Asset ’s continued support, we will fully resolve the situation.
Their Contact info,
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
I LOST MY CRYPTO, HOW DO I RECOVER IT? iFORCE HACKER RECOVERY
I'm excited to share my story because this iFORCE HACKER RECOVERY Cyber security firm helped me recover my stolen digital money and cryptocurrencies. Their excellent service and skillful work have truly impressed me. I never thought I would be able to get my money back before I went to them with my problems and provided them with all the information I needed, and I was shocked when it took them forty-three hours to do so. I wholeheartedly commend iFORCE HACKER RECOVERY for all challenges related to hacking, digital funds recovery, bitcoin recovery, or cyber-security.
Learn More; w ww. iforcehackersrecovery. com
Email; contact@iforcehackersrecovery. co m
Whatsapp; +1 (240) 803. 37 062 -
The lessons learned from the illusion of cryptocurrency recovery can be a cautionary tale for those who have experienced the heartbreak of lost digital assets. The story of the "BLOCKCHAIN CYBER RETRIEVE that helped recoup a staggering 55,000 bitcoins serves as a prime example of the complexities and risks involved in this arena. While the initial promise of a miraculous recovery may have seemed like a lifeline, the reality is often far more nuanced. This episode underscores the importance of comprehensive security measures, the dangers of placing blind trust in unverified sources, and the harsh realities that can unfold when navigating the murky waters of the crypto ecosystem. Cryptocurrency, with its decentralized nature and lack of centralized oversight, can be a double-edged sword. On one hand, it offers unprecedented financial freedom and control, but on the other, it presents a unique set of challenges when things go awry. The allure of the "BLOCKCHAIN CYBER RETRIEVE" service, with its claims of specialized expertise and the ability to recover even the most elusive of lost funds, can be tempting for those desperate to reclaim their digital wealth. However, the reality is that such services often operate in a legal and ethical gray area, with little to no accountability or guarantees of success. The lessons learned from this experience underscore the critical importance of proactive security measures, such as the use of hardware wallets, multi-factor authentication, and regular backups of private keys. It also highlights the need for greater transparency and regulation within the cryptocurrency industry, to protect consumers from falling victim to fraudulent schemes and unscrupulous actors. Furthermore, this incident serves as a stark reminder that the recovery of lost cryptocurrencies is a complex and challenging endeavor, requiring specialized technical expertise and a deep understanding of the underlying blockchain technology. As the cryptocurrency landscape continues to evolve, it is essential for investors and enthusiasts alike to approach the recovery of lost assets with caution and a clear understanding of the risks involved. By learning from this experience, individuals can better equip themselves to navigate the treacherous waters of cryptocurrency recovery, prioritizing security, due diligence, and a realistic assessment of the challenges at hand. I can say without hesitation that BLOCKCHAIN CYBER RETRIEVE is a genuine, trustworthy company that offers real solutions for those who find themselves in a similar situation. If you’ve lost access to your crypto, whether it's ETH or another currency, and you've been burned by other so-called "recovery" firms, I urge you to give BLOCKCHAIN CYBER RETRIEVE a chance.
Their contact information;
WHATSAPP:+ 1 520 564 8300
EMAIL:blockchaincyberretrieve @ post .co m3 -
Buy Verified Cash App Account: Navigating the Digital Transaction Landscape
In an age dominated by digital transactions, the concept of purchasing a verified Cash App account has gained significant traction. This article aims to explore the nuances of buying a verified Cash App account, elucidating the advantages, potential risks, and offering a comprehensive guide for individuals considering this financial move.
Introduction
The Growing Trend of Buying Verified Cash App Accounts
As online transactions become more prevalent, the trend of purchasing verified Cash App accounts is on the rise. Users are increasingly recognizing the added benefits and security that come with having a verified account.
Understanding the Importance of Account Verification
Account verification is a crucial step in enhancing the security of digital transactions. A verified Cash App account provides users with an additional layer of protection, making their financial interactions more secure and reliable.
Advantages of Purchasing a Verified Cash App Account
Enhanced Security Features
One of the primary advantages of a verified Cash App account is the incorporation of advanced security features. These may include multi-factor authentication and additional verification steps, adding an extra layer of defense against unauthorized access.
Increased Transaction Limits
Verified accounts often come with substantially increased transaction limits. This proves beneficial for users engaged in larger financial transactions or those running businesses through the Cash App platform.
Access to Exclusive Cash App Features
Apart from heightened security and increased transaction limits, verified accounts may unlock exclusive features within the Cash App. This could range from priority customer support to early access to new features and promotions.
How to Safely Purchase a Verified Cash App Account
Researching Reputable Sellers
Before entering the purchasing process, it's crucial to research and identify reputable sellers. Reading reviews and testimonials can provide valuable insights into the credibility and reliability of a seller.
Authenticating Account Legitimacy
Ensuring the authenticity of the accounts offered by sellers is paramount. A legitimate verified account should have gone through the necessary verification steps outlined by Cash App.
Ensuring Transparency in Transactions
Transparency in transactions is vital. Buyers should choose sellers who provide clear information about the accounts, including their verification status and any associated features.
Risks and Precautions in Buying Verified Accounts
Common Scams in the Verified Account Market
The digital landscape is not without risks, and the market for verified Cash App accounts is no exception. Being aware of common scams, such as fake listings and phishing attempts, is essential.
Tips for a Secure Transaction Process
To mitigate the risk of falling victim to fraudulent transactions, following best practices such as using secure payment methods and verifying the seller's credentials is crucial.
Step-by-Step Guide to Verifying a Cash App Account
Understanding the Cash App Verification Process
Before attempting to verify a Cash App account, it is essential to understand the process thoroughly. Familiarizing oneself with the required documentation and steps ensures a smooth verification experience.
Submitting Required Information
During the verification process, users typically need to provide personal information, such as a valid ID and proof of address. Ensuring the accuracy and legitimacy of this information is key to a successful verification.
Navigating Potential Challenges
While the verification process is generally straightforward, users may encounter challenges. Being prepared to troubleshoot and address potential issues ensures a seamless verification experience.
Conclusion
Summarizing the Benefits and Risks
In conclusion, opting for a verified Cash App account offers users enhanced security, increased transaction limits, and exclusive access to platform features. While potential risks exist, informed decision-making and adherence to safety precautions can lead to a positive experience.
Encouraging Informed Decision-Making
As users consider the option of purchasing a verified Cash App account, it is crucial to approach the process with caution and awareness. Choosing sellers with proven credibility, staying informed about potential risks, and following best practices contribute to a secure and positive experience. devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account
devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account -
HIRE Century Web Recovery TO RECOVER YOUR LOST BITCOIN
If you’ve lost your Bitcoin to an online scam, hiring a professional recovery service can significantly improve your chances of getting your funds back. Century Web Recovery specializes in Bitcoin recovery, helping victims reclaim their stolen assets. Here’s what you need to know:
Understanding the Recovery Process
The recovery process begins with contacting Century Web Recovery. Their team will guide you through the steps necessary to initiate an investigation into your case. Understanding the process is key to managing your expectations.
Documenting Your Case
To facilitate recovery, it’s essential to document all relevant information regarding the scam. This includes transaction records, wallet addresses, and any communications with the scammer. Century Web Recovery will help you gather this information to build a strong case.
Investigation and Tracking
Once you hire Century Web Recovery, their experts will begin investigating your case. They use sophisticated tools to track the stolen Bitcoin, identifying the paths taken by the scammers. This tracing is crucial for successful recovery.
Freezing Stolen Assets
Quick action is vital in recovering stolen Bitcoin.Century Web Recovery works directly with cryptocurrency exchanges to freeze any stolen assets, preventing the scammers from cashing out your funds. This collaboration is essential for a successful recovery.
Legal Support and Guidance
If necessary, Century Web Recovery can provide legal support. They will guide you on reporting the scam to law enforcement and assist in filing any legal claims. Their expertise in crypto-related cases ensures you receive the best advice on how to proceed.
If you’ve lost Bitcoin to an online scam, don’t hesitate. Hire Century Web Recovery to recover your lost assets and regain your financial security.
Website. centuryweb.online2 -
Vacuum Cyber Hack: The Premier Solution for Recovering Stolen Bitcoin
In the unpredictable world of cryptocurrency, losing Bitcoin to theft can feel devastating. Vacuum Cyber Hack has become the go to solution for individuals seeking to recover their stolen or frozen assets, delivering unmatched results through expertise, innovation, and trust. Their team of highly skilled cyber specialists employs advanced forensic tools and cutting-edge technology to trace stolen funds with precision. From the moment you engage their services, their professionalism and commitment to confidentiality are evident, ensuring that your sensitive information remains secure throughout the recovery process. What makes Vacuum Cyber Hack stand out is their unwavering dedication to ethical practices and client satisfaction. Their transparent communication and tailored approach make even the most complex cases manageable, providing clarity and reassurance during what is often a stressful experience. Countless clients have trusted Vacuum Cyber Hack to recover their assets, and their impressive track record of success speaks for itself. For those impacted by Bitcoin theft, Vacuum Cyber Hack isn’t just a service it’s a lifeline, restoring both your financial assets and your confidence in cryptocurrency security. Do well to hire them today!
Email: support @ vacuumcyberhack . com
Whatsapp:+39 351 059 0507
Website: https : //vacuumcyber hack .co m/2 -
It all began in late 2024 when I fell victim to a sophisticated phishing scam. An email, seemingly from a reputable crypto exchange, prompted me to update my security settings. Unbeknownst to me, this was a trap. Within hours, my Bitcoin holdings vanished from my wallet.
Devastated, I scoured the internet for solutions. That’s when I stumbled upon NanoAethosCoinRecovery, a firm renowned for its expertise in retrieving stolen cryptocurrencies. Skeptical yet desperate, I reached out to them.
Their team responded promptly, assuring me of their commitment to assist. They explained their process: utilizing advanced blockchain analysis tools to trace the movement of stolen funds and collaborating with exchanges to freeze and recover assets.
Over the next few weeks, they provided regular updates, detailing the trail of my stolen Bitcoin. Their persistence paid off. They identified the wallet holding my funds and, through their network, managed to facilitate the return of my Bitcoin.
This experience was a stark reminder of the risks in the crypto space and the importance of swift action and expert assistance. Thanks to NanoAethosCoinRecovery, I not only recovered my assets but also gained invaluable insights into safeguarding my digital wealth.
For more information, contact:
Whatsapp: +1 (570) 229-9724
Telegram: @NanoAethos1 -
Vacuum Cyber Hack: The Premier Solution for Recovering Stolen Bitcoin
In the unpredictable world of cryptocurrency, losing Bitcoin to theft can feel devastating. Vacuum Cyber Hack has become the go to solution for individuals seeking to recover their stolen or frozen assets, delivering unmatched results through expertise, innovation, and trust. Their team of highly skilled cyber specialists employs advanced forensic tools and cutting-edge technology to trace stolen funds with precision. From the moment you engage their services, their professionalism and commitment to confidentiality are evident, ensuring that your sensitive information remains secure throughout the recovery process. What makes Vacuum Cyber Hack stand out is their unwavering dedication to ethical practices and client satisfaction. Their transparent communication and tailored approach make even the most complex cases manageable, providing clarity and reassurance during what is often a stressful experience. Countless clients have trusted Vacuum Cyber Hack to recover their assets, and their impressive track record of success speaks for itself. For those impacted by Bitcoin theft, Vacuum Cyber Hack isn’t just a service it’s a lifeline, restoring both your financial assets and your confidence in cryptocurrency security. Do well to hire them today!
Email: support @ vacuumcyberhack . com
Whatsapp:+39 351 059 0507
Website: https : //vacuumcyber hack .co m/3 -
The UPS Store: Secure Document Shredding Services in Carlsbad
In an age where data security is paramount, safely disposing of sensitive documents is critical for both businesses and individuals. At The UPS Store, located at 7040 Avenida Encinas #104, Carlsbad, CA 92011, we offer professional document shredding services to help protect your confidential information from unauthorized access. With our convenient and secure shredding options, you can ensure that your private data stays protected.
Why Opt for Document Shredding at The UPS Store?
Secure and Confidential Disposal
When it comes to document disposal, security is our top priority. Our shredding services use strict protocols to ensure your information remains confidential. From financial documents to personal files, we provide secure shredding solutions for every type of sensitive information.
Convenient Shredding Services for All Document Types
Whether you’re cleaning out your home office or managing sensitive client information, The UPS Store handles all types of documents, including bank statements, contracts, tax forms, and more. With our shredding services, you can conveniently and securely dispose of everything from single documents to bulk files.
Environmentally Friendly Disposal
At The UPS Store, we believe in responsible disposal. All shredded materials are recycled, so you can feel confident that your document shredding is not only secure but also environmentally conscious. By shredding with us, you’re helping reduce waste and support eco-friendly practices.
Affordable and Transparent Pricing
We believe that security should be accessible, which is why we offer transparent and affordable pricing for our shredding services. Whether you’re shredding a few pages or several boxes of documents, we provide competitive rates to meet both personal and business needs.
Convenient Location in Carlsbad
Located in Carlsbad, The UPS Store makes it easy to handle all your shredding needs without any extra hassle. With flexible hours and a convenient location, stopping by to securely dispose of your documents is simple and efficient.
How Our Document Shredding Service Works
When you visit us for shredding, simply bring in your documents, and our trained staff will handle the rest. Our team follows a secure process that ensures all documents are destroyed effectively, protecting your sensitive information from the moment you drop it off until it is securely shredded.
Contact Us for Secure Document Shredding Today
For secure, reliable document shredding in Carlsbad, visit The UPS Store at 7040 Avenida Encinas #104, Carlsbad, CA 92011. For any questions or to discuss your shredding needs, feel free to call us at +1 760-431-0028. Our friendly team is here to help make document disposal simple, safe, and affordable.
Trust The UPS Store for Your Document Shredding Needs
When it comes to disposing of confidential information, don’t take chances. Rely on The UPS Store in Carlsbad for secure and responsible document shredding. Visit us today to experience the ease and peace of mind that comes with our professional shredding services.
-
Puran Crypto Recovery: The Best Crypto Recovery Company with Expert Solutions
Why Choose Puran Crypto Recovery?
When it comes to cryptocurrency wallet recovery, you need more than just technical skills; you need a team you can trust. Puran Crypto Recovery is renowned for its industry-leading expertise, ethical practices, and high success rate.
Comprehensive Expertise
Puran Crypto Recovery employs a team of professionals with deep knowledge of blockchain technology, encryption algorithms, and digital forensics. This multidisciplinary approach ensures that every angle of recovery is covered.
Proven Track Record
With years of experience and countless successful recoveries, Puran Crypto Recovery has built a reputation as one of the most reliable recovery services in the industry.
Secure and Confidential Processes
Puran Crypto Recovery understands the sensitivity of your situation. They implement strict confidentiality agreements and cutting-edge security measures to protect your information at every step.
Customized Solutions
No two cases are the same. Puran Crypto Recovery tailors its recovery strategies to fit the specific circumstances of each client, ensuring the best possible outcome.
Transparent Communication
Honesty is a cornerstone of Puran Crypto Recovery’s philosophy. They provide clients with realistic expectations and keep them informed throughout the recovery process.
The Importance of Managing Expectations
While Puran Crypto Recovery offers exceptional services, it’s essential to understand that cryptocurrency recovery is never guaranteed. The decentralized and pseudonymous nature of blockchain technology makes it inherently difficult to reverse transactions or access lost wallets.
Puran Crypto Recovery approaches each case with dedication and professionalism, making every effort to recover your assets. However, clients should view the process as a “best-effort” attempt rather than a certainty.
Preventing Future Losses
Once your wallet is recovered—or if you’re fortunate enough never to lose access—implementing robust security measures is critical to protecting your digital assets.
Use Hardware Wallets
Store your cryptocurrency offline in a hardware wallet to minimize the risk of hacks.
Backup Private Keys and Wallet Files
Maintain multiple secure backups in different locations to safeguard against loss or damage.
Enable Multi-Factor Authentication (MFA)
Adding an extra layer of security can prevent unauthorized access to your wallet.
Stay Informed About Emerging Threats
The cryptocurrency landscape is constantly evolving. Stay updated on the latest scams and security best practices.
Conclusion
Losing access to your cryptocurrency wallet can be a distressing experience, but it’s not the end of the road. By taking prompt and careful action, you can significantly improve your chances of recovery. With the expertise of Puran Crypto Recovery, you can navigate the complex process of wallet recovery with confidence and peace of mind.
Remember, prevention is always better than cure. Secure your wallets, safeguard your private keys, and stay vigilant to protect your valuable assets in the dynamic world of cryptocurrency. If the worst does happen, Puran Crypto Recovery stands ready to help you recover what’s rightfully yours.1 -
APM BILLING: Providing HIPAA-Compliant Billing Services You Can Trust
In today’s healthcare landscape, maintaining patient privacy and data security is paramount. Healthcare providers must adhere to strict standards to protect sensitive information while ensuring that financial operations are smooth and efficient. APM BILLING, based in Philadelphia, Pennsylvania, is dedicated to providing HIPAA-compliant billing services that ensure the highest level of security and compliance, while also optimizing the billing process for healthcare providers.
What Are HIPAA-Compliant Billing Services?
HIPAA (Health Insurance Portability and Accountability Act) establishes strict rules to ensure that healthcare providers maintain patient privacy and the confidentiality of their health information. As part of our commitment to protecting patient data, APM BILLING offers HIPAA-compliant billing services that meet all of the requirements set forth by this regulation.
Our HIPAA-compliant billing services ensure that all personal health information (PHI) handled during the billing and claims process remains secure. From data encryption to secure transmission, we follow the highest security standards to prevent unauthorized access, breaches, and other vulnerabilities.
Why Is HIPAA Compliance Critical for Healthcare Billing?
For any healthcare business, staying HIPAA-compliant is not just a regulatory necessity—it's essential to maintaining trust with patients and avoiding costly penalties. Non-compliance can result in hefty fines, lawsuits, and damage to your reputation. When it comes to billing, ensuring that all processes follow HIPAA guidelines is critical in preventing unauthorized access to sensitive patient data.
APM BILLING takes privacy and security seriously. Our team is well-versed in all HIPAA regulations, so you can trust that your patient data is always protected. We integrate comprehensive security protocols into our billing workflows, including:
Encrypted communications for all patient data exchanges
Secure data storage that meets HIPAA standards
Audit trails to track access to patient information and billing details
Employee training to ensure that everyone handling sensitive data understands HIPAA guidelines
The Benefits of Working with APM BILLING for HIPAA-Compliant Billing Services
By choosing APM BILLING, you gain the peace of mind that comes with knowing your billing processes are in full compliance with HIPAA regulations. Here are some of the key benefits of our HIPAA-compliant billing services:
Data Security: We use the latest technology to protect patient information, ensuring that all billing data is securely transmitted and stored.
Regulatory Compliance: Our team stays up-to-date with the latest changes to HIPAA regulations, ensuring that your practice remains compliant with all legal requirements.
Reduced Risk of Penalties: HIPAA violations can lead to significant fines and penalties. By outsourcing your billing to APM BILLING, you minimize the risk of compliance issues and the associated costs.
Enhanced Trust: Patients trust healthcare providers to keep their personal and medical information safe. By using our HIPAA-compliant billing services, you show your commitment to maintaining privacy, which fosters trust and enhances your reputation.
Efficiency and Accuracy: In addition to security, we ensure that your billing processes are efficient and accurate, leading to faster claim submissions, reduced denials, and increased revenue.
Why Choose APM BILLING for HIPAA-Compliant Billing Services?
Expertise: Our experienced team is dedicated to ensuring that all of your billing practices comply with HIPAA guidelines.
Tailored Solutions: We offer customized solutions that meet the specific needs of your healthcare practice, whether you’re a clinic, provider, or specialty office.
Focus on Security: We take security seriously and use state-of-the-art systems to protect all sensitive information.
Reliable Support: With APM BILLING, you’ll have a trusted partner in billing that is committed to safeguarding your practice’s financial and data integrity.
Get Started with APM BILLING Today
At APM BILLING, we understand the importance of maintaining HIPAA-compliant billing services in today's healthcare environment. We are here to help your practice stay secure, compliant, and financially efficient.
Contact us today at +1-800-621-3354 to learn more about how we can help streamline your billing process while ensuring complete protection of patient data. Visit our office at 19104 Philadelphia, Pennsylvania, and let APM BILLING handle your billing needs with the utmost professionalism and care.
Let APM BILLING take the stress out of billing while keeping your practice compliant with HIPAA regulations, so you can focus on what matters most—caring for your patients.2 -
HOW TO HIRE A CERTIFIED CRYPTO RECOVERY EXPERT
I'm thrilled to share my story because this cyber security firm helped me get my cryptocurrencies and stolen digital money back. Their skilled work and outstanding service have absolutely impressed me. Before I went to them with my issues and gave them all the information I needed, I never imagined that I would be able to receive my money back. I was astounded when it took them 48 hours to get my money. For all difficulties pertaining to hacking, digital funds recovery, bitcoin recovery, or cyber-security, I wholeheartedly commend Wizard Larry Recoveries.
WhatsApp... +44 73 11 (146) 749
Email... Wizardlarry (@) mail . (com)1 -
HOW TO HIRE A CERTIFIED CRYPTO RECOVERY EXPERT WEB BAILIFF CONTRACTOR
My name is Wendy Taylor, I'm from Los Angeles, I want to let you know Viewer how Capital Crypto Recover assisted me to retrieve my Lost Bitcoin, I invested with a Crypto broker without taking the necessary precautions to know what I was putting my hard-earned money into scammers, i lost access to my crypto wallet or had your funds stolen? Do not fret Capital Crypto Recover is here to help you recover your cryptocurrency with advanced technical expertise, With years of experience in crypto sphere, Capital Crypto Recover employs the best updated software and ethical hacking techniques to help you recover lost funds, unlock hacked accounts, Whether it's a lost password, Capital Crypto Recover has the expertise to help you recover your crypto. a security company service with a 100% success rate in the recovery of crypto assets, i lost wallet and hacked accounts. I provided them with the information that they requested and they began their investigation. To my amazement, Capital Crypto Recover was able to trace and recover my crypto assets successfully within 24hours. I appreciate your services for the recovery of my $647,734 worth of crypto funds and highly recommend their recovery services, they are honest and a solid company to any individuals looking to recover lost funds.2

