Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "leaked"
-
I had a secondary Gmail account with a really nice short nickname (from the early invite/alpha days), forwarded to another of my mailboxes. It had a weak password, leaked as part of one of the many database leaks.
Eventually I noticed some dude in Brazil started using my Gmail, and he changed the password — but I still got a copy of everything he did through the forwarding rule. I caught him bragging to a friend on how he cracked hashes and stole and sold email accounts and user details in bulk.
He used my account as his main email account. Over the years I saw more and more personal details getting through. Eventually I received a mail with a plaintext password... which he also used for a PayPal account, coupled to a Mastercard.
I used a local website to send him a giant expensive bouquet of flowers with a box of chocolates, using his own PayPal and the default shipping address.
I included a card:
"Congratulations on acquiring my Gmail account, even if I'm 7 years late. Thanks for letting me be such an integral part of your life, for letting me know who you are, what you buy, how much you earn, who your family and friends are and where you live. I've surprised your mother with a cruise ticket as you mentioned on Facebook how sorry you were that you forgot her birthday and couldn't buy her a nice present. She seems like a lovely woman. I've also made a $1000 donation in your name to the EFF, to celebrate our distant friendship"31 -
Someday my toaster is going to have an IP address. A bad automatic firmware update will most likely cause it to get stuck on the bagel setting until I plug a usb key in and reflash the memory.
Grandma's refrigerator will probably get viruses, lock itself and freeze all the food inside, demanding bitcoin before defrosting.
My blender will probably be used in a massive DDoS attack because Ninja's master MAC address list got leaked and the hidden control panel login is admin/admin.
Ovens will burn houses down when people call in to have them preheat on their way home from work.
Correlations between the number of times the lights are turned on and how many times the toilet is flushed will yield recommendations to run the dishwasher on Thursdays because it's simply more energy efficient.
My dog will tweet when he's hungry and my smart watch will recommend diet dog food in real-time because he's really been eating too much lately--"Do you want to setup a recurring order on Amazon fresh?"
Sometimes living in a cave sounds nice...12 -
Storytime!
Manager: Hey fullstackchris, the maps widget on our app stopped working recently...
Dev: (Skeptical, little did he know) Sigh... probably didn't raise quota or something stupid... Logs on to google cloud console to check it out...
Google Dashboard: Your bill.... $5,197 (!!!!!!) Payment method declined (you think?!)
Dev: 😱 WTF!?!?!! (Calls managers) Uh, we have HUGE problem, charges for $5000+ in our google account, did you guys remove the quota limits or not see any limit reached warnings!?
Managers: Uh, we didn't even know that an API could cost money, besides, we never check that email account!
Dev: 🤦♂️ yeah obviously you get charged, especially when there have literally been millions of requests. Anyway, the bigger question is where or how our key got leaked. Somewhat started hammering one of the google APIs with one of our keys (Proceeds to hunt for usages of said API key in the codebase)
Dev: (sweating 😰) did I expose an API key somewhere? Man, I hope it's not my fault...
Terminal: grep results in, CMS codebase!
Dev: ah, what do we have here, app.config, seems fine.... wait, why did they expose it to a PUBLIC endpoint?!
Long story short:
The previous consulting goons put our Angular CMS JSON config on a publicly accessible endpoint.
WITH A GOOGLE MAPS API KEY.
JUST CHILLING IN PLAINTEXT.
Though I'm relieved it wasn't my fault, my faith in humanity is still somewhat diminished. 🤷♂️
Oh, and it's only Monday. 😎
Cheers!11 -
Navy story continued.
And continuing from the arp poisoning and boredom, I started scanning the network...
So I found plenty of WinXP computers, even some Win2k servers (I shit you not, the year was 201X) I decided to play around with merasploit a bit. I mean, this had to be a secure net, right?
Like hell it was.
Among the select douchebags I arp poisoned was a senior officer that had a VERY high idea for himself, and also believed he was tech-savvy. Now that, is a combination that is the red cloth for assholes like me. But I had to be more careful, as news of the network outage leaked, and rumours of "that guy" went amok, but because the whole sysadmin thing was on the shoulders of one guy, none could track it to me in explicit way. Not that i cared, actually, when I am pissed I act with all the subtleness of an atom bomb on steroids.
So, after some scanning and arp poisoning (changing the source MAC address this time) I said...
"Let's try this common exploit, it supposedly shouldn't work, there have been notifications about it, I've read them." Oh boy, was I in for a treat. 12 meterpreter sessions. FUCKING 12. The academy's online printer had no authentication, so I took the liberty of printing a few pages of ASCII jolly rogers (cute stuff, I know, but I was still in ITSec puberty) and decided to fuck around with the other PCs. One thing I found out is that some professors' PCs had the extreme password of 1234. Serious security, that was. Had I known earlier, I could have skipped a TON of pointless memorising...
Anyway, I was running amok the entire network, the sysad never had a chance on that, and he seemed preoccupied with EVERYTHING ELSE besides monitoring the net, like fixing (replacing) the keyboard for the commander's secretary, so...
BTW, most PCs had antivirus, but SO out of date that I didn't even need to encode the payload or do any other trick. An LDAP server was open, and the hashed admin password was the name of his wife. Go figure.
I looked at a WinXP laptop with a weird name, and fired my trusty ms08_067 on it. Passowrd: "aaw". I seriously thought that Ophcrack was broken, but I confirmed it. WTF? I started looking into the files... nothing too suspicious... wait a min, this guy is supposed to work, why his browser is showing porn?
Looking at the ""Deleted"" files (hah!) I fount a TON of documents with "SECRET" in them. Curious...
Decided to download everything, like the asshole I am, and restart his PC, AND to leave him with another desktop wallpaper and a text message. Thinking that he took the hint, I told the sysadmin about the vulnerable PCs and went to class...
In the middle of the class (I think it was anti-air warfare or anti-submarine warfare) the sysad burst through the door shouting "Stop it, that's the second-in-command's PC!".
Stunned silence. Even the professor (who was an officer). God, that was awkward. So, to make things MORE awkward (like the asshole I am) I burned every document to a DVD and the next day I took the sysad and went to the second-in-command of the academy.
Surprisingly he took the whole thing in quite the easygoing fashion. I half-expected court martial or at least a good yelling, but no. Anyway, after our conversation I cornered the sysad and barraged him with some tons of security holes, needed upgrades and settings etc. I still don't know if he managed to patch everything (I left him a detailed report) because, as I've written before, budget constraints in the military are the stuff of nightmares. Still, after that, oddly, most people wouldn't even talk to me.
God, that was a nice period of my life, not having to pretend to be interested about sports and TV shows. It would be almost like a story from highschool (if our highschool had such things as a network back then - yes, I am old).
Your stories?8 -
In the bottom left corner of the picture there is a devRant guy with a 3 monitor setup...
However 2 monitors are the biggest multi monitor setup you can select...
*puts tinfoil hat on*
Have I just leaked the next big devRant update? 53
53 -
At my old job, me and a colleague were tasked with designing a new backup system. It had integrations for database systems, remote file storage and other goodies.
Once we were done, we ran our tests, and sure enough. The files and folder from A were in fact present at B and properly encrypted. So we deployed it.
The next day, after the backup routine had run over night, I got to work and noone was able to log in. They were all puzzled.
I accessed a root account to find the issue. Apparantly, we had made a mistake!
All files on A were present at B... But they were no longer present at A.
We had issued 'move' instead of 'copy' on all the backups. So all of peoples files and even the shared drives have had everything moved to remote storage :D
We spent 4 hours getting everything back in place, starting with the files of the people who were in the office that day.
Boss took it pretty well at least, but not my proudest moment.
*Stay tuned for the story of how I accidentally leaked our Amazon Web Services API key on stack overflow*
/facepalm5 -
Apple asked it's employees not to leak information in a memo. Guess what? The memo got leaked. Lol
 2
2 -
Windows 10 source code apparently leaked!
The main.c file is short tho and unchanged since 95(it's just run in parallel) so I'mma just paste it here:
void WinMain(int nCmdArgs){
static int userDisgust = 5; //he/she booted up Win10 so 5 to begin with
Time time = Time.time;
while(!crashed){
Time time2 = Time.time;
if(time + 3600 < time2){
ApplyUpdate();
sleep(500000); //users can stretch, have a tea and overall be healthier, happier and better part of society
if(restartNecessary){
Restart();
}
Restart(); // just in case
}
SendUserData();
SendMoreUserData();
for(int i = 1; i < 99+1; i++){
RunUserApps();
UninstallUnnecessaryApps(); // keeps blacklist of apps that John and I don't like
AnnoyUser(); // added a function that slows the computer down significantly and reduces lifespan of the hardware so it's not just a short term gain
if(shouldRepeat){
//break; -- this caused some issue in one special case and we don't know why so we'll just omit it and add a fancy button elsewhere
}
userDisgust++;
}
if(userDisgust >= 2147483647) { //mission finished
Crash();
crashed = true;
}
}
String error = Windows.GetFullErrorMessage();
error.cat(Windows.GetRegistersDump());
error.cat(Windows.GetErrorCode());
error.cat(Windows.GetStackTrace());
error.erase(); // so that it doesn't occupy any space and allows the error to be resolved more quickly, release major optimization Update
BSOD(_T("We're sorry :/"));
}5 -
(L)user tried to impress the IT staff (myself included) by installing a few of the NSA leaked tools last night, (l)user was infected with ransomware... (l)user is now job hunting. 👌🏽2
-
Fucking shit fuck! Absolute cunty-chops of a Work phone just went off at 3am because our directory has clearly been leaked.
This cunt right here is on 24/7 fallout so I can nae silence the bastard. It’s going inte do not disturb for the evening now but.
About 6 months to a year ago we started getting nuisance calls on the cunts. On floated numbers that seem geographically close.
Work have done fuck all in this time, because considering changing ours is a pain in the dick, and costs.
But tonight at 3am I got another; call, immediate hang up on redial.
This wee iPhone prick is looking at me like “ho! Got ya ye fucker”... it’s lucky it’s not been punted out the winde where it belongs. Little fucking prick.
If I look like shit tomorrow at the office, if any prick decides to mention I look tired, I’m gonnae tear the ballbags a new hole between their baws and their arse.
It’s now 4am, sorry fe the language, my Glaswegian heritage shines through at this time in the morning.5 -
i just started learning about networking by sending a packet saying "emoji movie leaked footage" from my laptop to my desktop
for some reason, the fact that i can have two computers interact fills me with some kind of inexplicable joy5 -
MAINTENANCE OF STACKOVERFLOW PLANNED
SHARE TO YOUR NEAREST DEV FRIENDS
Stackoverflow and its relative partners will be closed for two days due to maintenance, new design, and moving server infrastructure from United States to 1km below the Switzerland Alps for extra layers of security. This decision was made by the recent CloudFlare data leak.
Now our servers will be able to handle data leaks because even though the data was leaked, it will fill the empty places in the rocks resulting inaccessible from attackers.
Stackoverflow and its relative partners' maintenance estimated time is February 29 - 30. We will try to finish as fast as possible and bring you guys the best experience. If the maintenance delayes, we will tweet via @StackStatus or post details in our status blog.
Thank you for your support and have a happy day.
Best regards,
Stack Exchange team6 -
I don't think I could give the best advice on this since I don't follow all the best practices (lack of knowledge, mostly) but fuck it;
- learn how to use search engines. And no, not specifically Google because I don't want to drag kids into the use of mass surveillance networks and I neither want to promote them (even if they already use it).
- try not to give up too easily. This is one I'm still profiting from (I'm a stubborn motherfucker)
- start with open source technologies. Not just "because open source" but because open source, in general, gives one the ability to hack around and explore and learn more!
- Try to program securely and with privacy in mind (the less data you save, the less can be abused, compromised, leaked, etc)
- don't be afraid to ask questions
-enjoy it!7 -
Earlier I signed up on this forum called NulledBB. Basically some hacker skiddie forum that had a dump of an archive I wanted, unfortunately behind a paywall which I didn't want to bother with.
On signup I noticed that I couldn't use my domain as an email address, as I usually do (the domain is a catch-all which means that mail addresses can be made up for each service I sign up to on the fly, super useful). They did expose the regex that they accepted email as however, which included something along the lines of "@live.*".
So I figured, why not register a subdomain live.nixmagic.com real quick and put that into the mail servers? Didn't take too long and that's what I eventually went with, and registered as somepissedoffsysop@live.nixmagic.com (which I have no trouble putting on a public forum as you'll see in a minute).
Still didn't manage to get that archive I wanted but I figured, fuck it. It's a throwaway account anyway. But eventually that email address started to receive spam. Stupid motherfucker of a forum operator with his Kali skidmachine probably leaked it.
Usually I just blacklist the email address in SpamAssassin by adding an additional spam score of 100 to email sent to such addresses. But in that case it didn't even sit on the main domain, thanks to that stupid regex block from earlier... 😏
*Logs into my domain admin panel*
*Le rm on the live.nixmagic.com record*
Null routed entirely.. nulled, if you will! 🙃3 -
Some of the penguin's finest insults (Some are by me, some are by others):
Disclaimer: We all make mistakes and I typically don't give people that kind of treatment, but sometimes, when someone is really thick, arrogant or just plain stupid, the aid of the verbal sledgehammer is neccessary.
"Yeah, you do that. And once you fucked it up, you'll go get me a coffee while I fix your shit again."
"Don't add me on Facebook or anything... Because if any of your shitty code is leaked, ever, I want to be able to plausibly deny knowing you instead of doing Seppuku."
"Yep, and that's the point where some dumbass script kiddie will come, see your fuckup and turn your nice little shop into a less nice but probably rather popular porn/phishing/malware source. I'll keep some of it for you if it's good."
"I really love working with professionals. But what the fuck are YOU doing here?"
"I have NO idea what your code intended to do - but that's the first time I saw RCE and SQLi in the same piece of SHIT! Thanks for saving me the hassle."
"If you think XSS is a feature, maybe you should be cleaning our shitter instead of writing our code?"
"Dude, do I look like I have blue hair, overweight and a tumblr account? If you want someone who'd rather lie to your face than insult you, go see HR or the catholics or something."
"The only reason for me NOT to support you getting fired would be if I was getting paid per bug found!"
"Go fdisk yourself!"
"You know, I doubt the one braincell you have can ping localhost and get a response." (That one's inspired by the BOFH).
"I say we move you to the blockchain. I'd volunteer to do the cutting." (A marketing dweeb suggested to move all our (confidential) customer data to the "blockchain").
"Look, I don't say you suck as a developer, but if you were this competent as a gardener, I'd be the first one to give you a hedgetrimmer and some space and just let evolution do its thing."
"Yeah, go fetch me a unicorn while you're chasing pink elephants."
"Can you please get as high as you were when this time estimate come up? I'd love to see you overdose."
"Fuck you all, I'm a creationist from now on. This guy's so dumb, there's literally no explanation how he could evolve. Sorry Darwin."
"You know, just ignore the bloodstain that I'll put on the wall by banging my head against it once you're gone."2 -
So Windows XP source allegedly got leaked... And a bunch of other MS's OS (and other) files
https://limetorrents.info/Microsoft...
```
ms_dos_3_30_oem_adaptation_kit_source_code.7z - 591.99 KB
ms_dos_6_0_source_code.7z - 10.7 MB
nt5src.7z - 2.37 GB
torrent description.txt - 6.63 KB
windows_10_shared_source_kit.7z - 74.76 MB
windows_2000_source_code.7z - 122.35 MB
windows_ce_3_platform_builder_source_code.7z - 638.69 KB
windows_ce_4_2_081231.7z - 3.44 MB
windows_ce_5_121231.7z - 4.92 MB
windows_embedded_7_2014M12.7z - 12.9 MB
windows_embedded_ce_6_r3_170331.7z - 8.11 MB
windows_embedded_compact_2013_2015M09.7z - 93.17 MB
windows_nt_3_5_source_code.7z - 101.76 MB
windows_nt_4_source_code.7z - 106.22 MB
windows_source_bg.png - 134.83 KB
windows_source_bg.svg - 55.03 KB
``` 15
15 -
- popunder background bitcoin miners did become a thing
- keybase android beta uploaded your privatekey to google servers "accidentally"
- you can spoof email headers via encoded chars, because most apps literally just render them apparently
- imgur leaked 1.7 million user accounts, protected by sha-256 "The company made sure to note that the compromised account information included only email addresses and passwords" - yeah "only", ofcourse imgur, ofcourse.
I guess the rant I did on Krahk etc. just roughly a month ago, can always be topped by something else.
sources:
https://www.mailsploit.com/index
https://bleepingcomputer.com/news/...
https://blog.malwarebytes.com/cyber...
https://helpnetsecurity.com/2017/... undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6
undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6 -
Okay, That right there is pathetic https://thehackernews.com/2019/02/... .
First of all telekom was not able to assure their clients' safety so that some Joe would not access them.
Second of all after a friendly warning and pointing a finger to the exact problem telekom booted the guy out.
Thirdly telekom took a defensive position claiming "naah, we're all good, we don't need security. We'll just report any breaches to police hence no data will be leaked not altered" which I can't decide whether is moronic or idiotic.
Come on boys and girls... If some chap offers a friendly hand by pointing where you've made a mistake - fix the mistake, Not the boy. And for fucks sake, say THANK YOU to the good lad. He could use his findings for his own benefit, to destroy your service or even worse -- sell that knowledge on black market where fuck knows what these twisted minds could have done with it. Instead he came to your door saying "Hey folks, I think you could do better here and there. I am your customes and I'd love you to fix those bugzies, 'ciz I'd like to feel my data is safe with you".
How on earth could corporations be that shortsighted... Behaviour like this is an immediate red flag for me, shouting out loud "we are not safe, do not have any business with us unless you want your data to be leaked or secretly altered".
Yeah, I know, computer misuse act, etc. But there are people who do not give a tiny rat's ass about rules and laws and will find a way to do what they do without a trace back to them. Bad boys with bad intentions and black hoodies behind TOR will not be punished. The good guys, on the other hand, will.
Whre's the fucking logic in that...
P.S. It made me think... why wouldn't they want any security vulns reported to them? Why would they prefer to keep it unsafe? Is it intentional? For some special "clients"? Gosh that stinks6 -
i rant that i live in a dictatorship with an idiot president who bans whatsapp and facebook to prevent protests (in reaction to having arrested opposition party members of parliament), and github (yes, github) to prevent the spread of a minister's leaked e-mails. now the government is seriously considering shutting down vpn services to prevent by-passing the bans.
on the other hand, it's a nice time and place to continue ms studies on ad-hoc networks - that is of course if i can avoid being arrested or killed before i even start my thesis.9 -
TL;DR
This works: email+rant@domain.com
Spam filtering protip:
Did you know that the email spec allows you to use youremail+something@domain.com and the emails still come to you. This is especially useful when registering to a lot of places where you are not sure whether they will spam you or not. Filtering will be easy because you have a unique email address for each service. Also you can find out which service leaked your email address to spammers.
Additionally if you want to register to a service with two accounts but still want to use the same email, you can do this easily by adding +whatever in your email address.6 -
While busy writing code, hardest discussion is should I go and pee or wait till a bit of pee is leaked in my underwear.10
-
So apparently, there's a "leaked" recording of the AWS CEO telling software devs to stop coding and be prepared for the day when "AI takes over software development."
Can someone point me in the direction of the AWS Headquarters?
*cocks shotgun*
I just wanna talk11 -
Am I the only one who doesn't understand apple card? Like really, it's just the worst pitch ever!
"Apple card. Made by apple. Not a bank" that's a REAL ad I saw today. Why would you trust APPLE more than an FDIC insured bank with decades or (in some select cases) CENTURIES of experience in finance?
"No more card numbers and CVV"
Cool. I get it. Card numbers get leaked and stolen. But that's why banks insure cards and reverse fradulant transactions. How an I'm supposed to use it on Amazon?! I'm sure they have an answer. Like maybe one time use generated cards. But they haven't advertised it yet, and that's a problem!
Why do they think people want this!? And even more so, because I've seen some people are excited: WHY DO PEOPLE WANT THIS?! why is apple trying to make everything?!15 -
"Let‘s make a service where the users can enter all of their secrets and sensitive data so that we can warn them if that data has been leaked elsewhere"
What could possibly go wrong?2 -
Got to love Ubisoft web devs.
Their new "30 days of Ubisoft" calendar has the browser download 30 images of closed numbered boxes, 30 images for the hover state of each box and another 30 for the open state. Granted, the images aren't big, but hasn't anybody heard of custom fonts and CSS3?
Oh, and the "surprises" have already been leaked on reddit, gj on keeping hints in the page source.
https://30days.ubi.com/Promotion/...1 -
Aus Gov: here's a bright idea, let's enforce social media accounts being verified with enough identification to pull of identify theft with ease for the greater good.
https://news.com.au/technology/...
Facebook: 533 million accounts leaked with names, email, phone, address details.
https://mobile.twitter.com/UnderThe...
Me: 🤦♂️12 -
So at the old job, i needed support for an issue relating to Amazon S3. We used a third party Python plugin for sending files to our buckets, but had some pretty severe performance issues when trying a 2-way sync.
Naturally, I sought help on StackOverflow, and was asked to share my config. Without much thought, I pasted the config file.
Next comment made me aware that our API id and key was listed in this config (pretty rediculous to keep such private info in the same file as configuration, but oh well).
I edited my question and removed the keys, and did not think about the fact that revisions are stored.
Two weeks later, my boss asks me if I know why the Amazon bill is for 25.000$ when it used to be <100$ 😳
I've never been so scared in my life. Luckily, Amazon was nice enough to waive the entire fee, and I leaned a little about protecting vital information4 -
I don't understand how is possible that programmers today are developing applications that are storing plain password in the database.
I know it's kinda boring topic since everybody here is talking about it this week, but it's really confusing to me.
Every now and then some DB gets hacked, millions of passwords are leaked and then you have developers, who should be smart and logical people, who decide to do that.
Ok, maybe the project deadline was close or something similar, but I think there is no excuse for something like that. No matter how close or behind deadline project is, you should always be able to explain to your boss/client what could happen.3 -
Regarding Article 13 (or 17 or wherever it moved to now)… Let's say that the UK politicians decide to be dicks and approve the law. After that, we need to get it engineered in, right? Let's talk a bit about how.. well, I'd maybe go over it. Been thinking about it a bit in the shower earlier, so.. yeah.
So, fancy image recognition or text recognition from articles scattered all over the internet, I think we can all agree.. that's infeasible. Even more so, during this lobby with GitHub and OpenForum Europe, guy from GitHub actually made a very valid point. Now for starters, copyright infringement isn't an issue on the platform GitHub that pretty much breathes collaboration. But in the case of I-Boot for example, that thing from Apple that got leaked earlier. If that would get preemptively blocked.. well there's no public source code for it to get compared against to begin with, right? So it's not just "scattered all over the internet, good luck crawling it", it's nowhere to be found *at all*.
So content filtering.. yeah. Nope, ain't gonna happen. Keep trying with that, EU politicians.
But let's say that I am a content creator who hates the cancer of joke/meme because more often than not it manifests itself as a clone of r/programmerhumor.. someone decides to freeboot my content. So I go out, look for it, find it. Facebook and the likes, make it easier to find it in the first place, you dicks. It's extremely hard to find your content there.
So Facebook implements a way to find that content a bit easier maybe. Me being the content creator finds it.. oh blimey! It can't be.. it's the king of freebooting on Facebook, SoFlo! Who would've thought?! So at that point.. I'd like to get it removed of course. Report it as copyright infringement? Of course. Again Facebook you dicks, don't make it so tedious to fill in that bloody report. And look into it quickly! The videos those SoFlo dicks post is only relevant in the first 48h or so. That's where they make the most money. So act more quickly.
So the report is filled, video's taken down.. what else? Maybe temporarily make them unable to post as a bit of a punishment so that they won't do it again? And put in a limit to the amount of reports they can receive. Finally, maybe reroute the revenue stream to the original content creator instead. That way stolen content suddenly becomes free exposure! Awesome!
*suddenly realizes that I've been talking about the YouTube copyright strike system all along*
… Well.. maybe something like that then? That shouldn't be too hard to implement, and on YouTube at least it seems to be quite effective. Just imagine SoFlo and the likes that are repeat offenders, every 3 posts they get their account and page shut down. Good luck growing an audience that way. And good luck making new accounts all the time to start with.. account verification technology is pretty good these days. Speaking of experience here, tried bypassing Facebook's signup hoops a fair bit and learned a bit about some of the things they have red flags on, hehe.
But yeah, something like that maybe for social media in general. And.. let's face it, the biggest one that would get hurt by something like this would be Facebook. And personally I think it's about time for that bastard company to get a couple of blows already.
What are your thoughts on this?5 -
ChatGPT implementation details leaked !!!
This explains everything:
- slow response typing
- occasional nonsensical answers and factual mistakes
- delays before answering
- sudden and random network errors
- "servers" over-capacity
- responses with an Indian accent 5
5 -
So I bought a gaming laptop a while back, and Cyberpunk 2077 binaries got leaked a few days ago... So I wanted to play it, kinda. It looks really good from the screenshots. Friend asks me "what CPU / GPU do you have"?
My gaming laptop is a Y700 so an i7-6700HQ and a GTX 960M. Turns out that even at low settings this thing probably won't pull even 30 FPS.
So even with a gaming laptop, you don't get to do any gaming. 10/10 would buy again! I'll enjoy Super Mario because imagine caring about gameplay rather than stunning graphics that you need tomorrow's hardware for, and buy it yesterday! And have it already obsolete today.
Long story short, I kinda hate the gaming scene. I'm not a gamer either by any means. Even this laptop just runs Linux and I bought it mostly because some of its hardware is better than my x220's. Are gamers expected to spring the money for the latest and greatest nugget every other month? When such a CPU and GPU alone would already cost most people's entire monthly wage?
What's the point of having a game that nobody can play? Even my friends' desktop hardware which is quite a bit better still - it only pulls 45 FPS according to him. Seriously, what's the point?12 -
My doctor's office logs into their computers using the Administrator user. 🤔Pretty sure that's how patient info gets leaked.2
-
Running WireShark to see what one of our partners is sending across.
Outdated TLS: Ok, that's par for the course.
Leaking data through DNS queries: ButWhy.jpg
Website leaked through DNS doesn't require auth to view information. TableFlip.jpg1 -
Oh noes... My password on localhost:8080 has been leaked :( what to do.. what to doooo..... :(((
Oh FFS google! Get yourself together!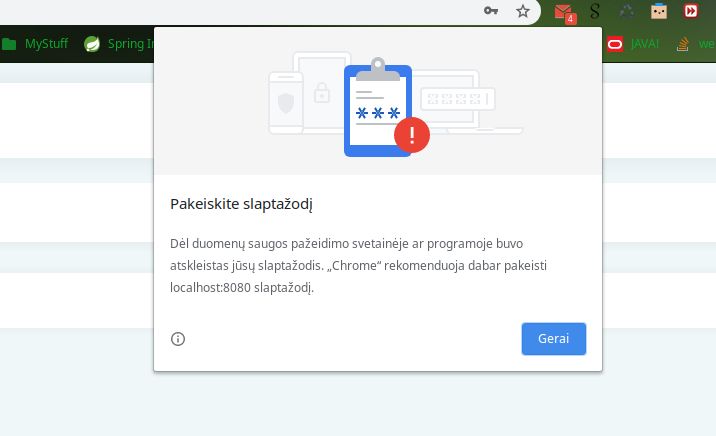 1
1 -
I just woke up this morning to an email saying that someone from chile logged into my instagram account and I'm not actually what set me of the most.
The fact that my password was leaked, the fact I literally never got notified that I had a Instagram account I never wanted or the you have to disable most privacy settings, just to reset your password.
Like holy fuck, I disabled all options I could find on firefox concerning privacy/tracking and it still tells me I should disable some privacy settings.
So I enabled chrome again (fucking system app) and it worked on first try. Just as expected...
Anyway, fuck instagram and thank you dear hacker for telling me that I had a worthless to delete.5 -
My friend recently tried to install apt on fedora 🤦♂️
Some how this created a zombie process And used a ton of the ram and the ram usage leaked out of the VM and into the host server
And I had to explain to him why a package manager meant for a system with dpkg will not work on one that uses rpm11 -
Intel is dying right now tbh. I hope the can get back on their feet but as of right now, chaos. They have had multiple ceo changes within 1 year and their current is a horrible leader. They have been really wasteful with their money (like buying McAfee...) And the inly reason they are leading in the CPU market, Tick Tock, is failing. It used to be Process - Architecture. Now intel has announced they are not changing the process for 8th gen, currently it's Process - Architecture - Optimize - Optimize - Optimize. Which is not good. It has been leaked that Intel is currently just hoping for AMD Ryzen to fail, let's face it, Ryzen seems really promising and might be the comeback AMD needs.
TLDR; Intel is a one trick pony and their one trick is failing. They have been really wasteful with their money and their current hope is that Ryzen fails.
I have an Intel CPU in my system and i find them to be better than AMD, but the tables might turn.7 -
Heads-up, ChatGPT is leaking through cracks. Each chat is NOT carried out in an isolated, pristine context. It can refer to your previous conversations in a new context.
e.g.: https://chatgpt.com/share/e/...
I did NOT mention anything about any project/client or any fintech or any certification in this conversation. However, I mentioned all of those things in a previous conversation.
Contexts leaked into each other. IDK if my newer conversation will have any effect on answers to follow-up questions in older conversations, though.
No, learning from my conversations is NOT enabled.
But if chatgpt still remembers our conversations, regardless my explicit preference NOT to do that, makes me wonder what else they are collecting/doing behind the scenes..9 -
***ILLEGAL***
so its IPL(cricket) season in india, there is a OTT service called hotstar (its like netflix of india), the cricket streams exclusively on hotstar..
so a quick google search reveals literally thousands of emails & passwords, found a pastebin containing 500 emails&passwords ...but those are leaked last year most of passwords are changed & many of them enabled 2FA.. after looking through them we can find some passwords are similar to their emails , some contains birth year like 1975,1997 etc, some passwords end with 123 ..so after trying a few different versions of the passwords like
1) password123 -> password@123, password1234
2) passwordyear -> password@year
2) for passwords similar to emails, we can add 123 ,1234, @ etc
created a quick python script for sending login requests
so after like 30-40 mins of work, i have 7 working accounts
*for those who have basic idea of security practices you can skip this part
lessons learnt
1) enable 2FA
2) use strong passwords, if you change your password , new password should be very different from the old one
there are several thousands of leaked plaintext passwords for services like netflix,spotify, hulu etc, are easily available using simple google search,
after looking through & analysing thousands of them you can find many common passwords , common patterns
they may not be as obvious as password ,password123 but they are easily guessable.
mainly this is because these type of entertainment services are used by the average joe, they dont care about strong passwords, 2FA etc6 -
Nearly same time as the "don't be evil" got removed from google pages, an old internal video leaked about some futuristic concept, where the AI would try to gather as much data as possible from a user and if not possible, suggest devices with discount (e.g. a scale), that can return that data to the AI or if there's no fitting product, just print or make it based on the previously collected data (favorite color, ..) and suggest that to the user to buy, all since google duplex, anything mentioning google has been outscoring the previous idea 😶
src: https://youtu.be/iqUCX5rPQug 2
2 -
I am not sure if devrant is the best place to post this so sorry if it is not.
How far do employers/recruiters go when searching online information about their applicants?
Do they simply check your fb? simple google search your name? advanced queries with multiple search engines? data gathering software like maltego? or really check and link leaked db dumps and pastebins?
If anyone has any knowledge or experience with this I would love to hear.
Thanks in advance10 -
This codebase had 50+ main() functions and 80+ Material App. 5 of them are nested MaterialApp
Redundant widgets, security leaks, and print Sensitive information from the server to console without using (kDebugMode), therefore in prod, the data are leaked.
I refactored until I screamed.
So I left a gift inside.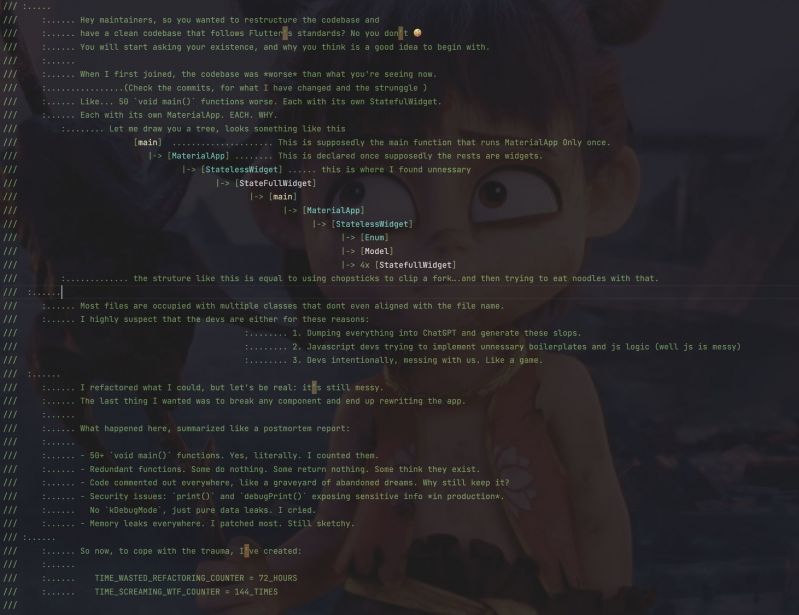 14
14 -
just found out a vulnerability in the website of the 3rd best high school in my country.
TL;DR: they had burried in some folders a c99 shell.
i am a begginer html/sql/php guy and really was looking into learning a bit here and there about them because i really like problem solving and found out ctfs mainly focus on this part of programming. i am a c++ programmer which does school contest like programming problems and i really enjoy them.
now back on topic.
with this urge to learn more web programming i said to myself what other method to learn better than real life sites! so i did just that. i first checked my school site. right click. inspect element. it seemed the site was made with wordpress. after looking more into the html code for the site i concluded all the images and files i could see on the site were from a folder on the server named 'wp-content/uploads'. i checked the folder. and here it got interesting. i did a get request on the site. saw the details. then i checked the site. bingo! there are 3 folders named '2017', '2018', '2019'. i said to myself: 'i am god.'
i could literally see all the announcements they have made from 2017-2019. and they were organised by month!!! my curiosity to see everything got me to the final destination.
with this adrenaline i thought about another site. in my city i have the 3rd most acclaimed high school in the country. what about checking their security?
so i typed the web address. looked around. again, right click, inspect element and looked around the source code. this time i was more lucky. this site is handmade!!! i was soooo happy because with my school's site i was restricted with what they have made with wordpress and i don't have much experience with it.
amd so i began looking what request the site made for the logos and other links. it seemed all the other links on the site were with this format: www.site.com/index.php?home. and i was very confused and still am. is this referencing some part of the site in the index.php file? is the whole site written inside the index.php file and with the question mark you just get to a part of the site? i don't really get it.
so nothing interesting inside the networking tab, just some stylesheets for the site's design i guess. i switched to the debugger tab and holy moly!! yes, it had that tree structure. very familiar. just like a project inside codeblocks or something familiar with it. and then it clicked me. there was the index.php file! and there was another folder from which i've seen nothing from the network tab. i finally got a lead!! i returned in the network tab, did a request to see the spgm folder and boooom a site appeared and i saw some files and folders from 2016. there was a spgm.js file and a spgm.php file. there was a contrib, flavors, gal and lang folders. then it once again clicked me! the lang folder was las updated this year in february. so i checked the folder and there were some files named lang with the extension named after their language and these files were last updated in 2016 so i left them alone. but there was this little snitch, this little 650K file named after the name of the school's site with the extension '.php' aaaaand it was last modified this year!!!! i was so excited! i thought i found a secret and different design of the site or something completely else! i clicked it and at first i was scared there was this black/red theme going on my screen and something was a little odd. there were no school announcements or event, nononoooo. this was still a tree structured view. at the top of the site it's written '!c99Shell v. 1.0...'
this was a big nono. i saw i could acces all kinds of folders. then i switched to the normal school website and tried to access a folder i have seen named userfiles and got a 403 forbidden error. wopsie. i then switched to the c99 shell website and tried to access the userfiles folder and my boy showed all of its contents. it was nakeeed naked. like very naked. and in the userfiles folder there were all, but i mean ALL files and folders they have on the server. there were a file with the salary of each job available in the school. some announcements. there was a list with all the students which failed classes. there were folders for contests they held. it was an absolute mess and i couldn't believe it.
i stopped and looked at the monitor. what have i done? just to learn some web programming i just leaked the server of the 3rd most famous high school in my country. image a black hat which would have seriously caused more damage. currently i am writing an email to the school to updrage their security because it is reaaaaly bad.
and the journy didn't end here. i 'hacked' the site 2 days ago and just now i thought about writing an email to the school. after i found i could access the WHOLE server i searched for the real attacker so if you want to knkw how this one went let me know in the comments.
sorry for the long post, but couldn't held it anymore13 -
Brave Browser.
There’s a reason why brave is generally advised against on privacy subreddits, and even brave wanted it to be removed from privacytools.io to hide negativity.
Brave rewards: There’s many reasons why this is terrible for privacy, a lot dont care since it can be “disabled“ but in reality it isn’t actually disabled:
Despite explicitly opting out of telemetry, every few secs a request to: “variations.brave.com”, “laptop-updates.brave.com” which despite its name isn’t just for updates and fetches affiliates for brave rewards, with pings such as grammarly, softonic, uphold e.g. Despite again explicitly opting out of brave rewards. There’s also “static1.brave.com”
If you’re on Linux curl the static1 link. curl --head
static1.brave.com,
if you want proof of even further telemetry: it lists cloudfare and google, two unnecessary domains, but most importantly telemetry domains.
But say you were to enable it, which most brave users do since it’s the marketing scheme of the browser, it uses uphold:
“To verify your identity, we collect your name, address, phone, email, and other similar information. We may also require you to provide additional Personal Data for verification purposes, including your date of birth, taxpayer or government identification number, or a copy of your government-issued identification
Uphold uses Veriff to verify your identity by determining whether a selfie you take matches the photo in your government-issued identification. Veriff’s facial recognition technology collects information from your photos that may include biometric data, and when you provide your selfie, you will be asked to agree that Veriff may process biometric data and other data (including special categories of data) from the photos you submit and share it with Uphold. Automated processes may be used to make a verification decision.”
Oh sweet telemetry, now I can get rich, by earning a single pound every 2 months, with brave taking a 30 percent cut of all profits, all whilst selling my own data, what a deal.
In addition this request: “brave-core-ext.s3.brave.com” seems to either be some sort of shilling or suspicious behaviour since it fetches 5 extensions and installs them. For all we know this could be a backdoor.
Previously in their privacy policy they shilled for Facebook, they shared data with Facebook, and afterwards they whitelisted Facebook, Twitter, and large company trackers for money in their adblock: Source. Which is quite ironic, since the whole purpose of its adblock is to block.. tracking.
I’d consider the final grain of salt to be its crappy tor implementation imo. Who makes tor but doesn’t change the dns? source It was literally snake oil, all traffic was leaked to your isp, but you were using “tor”. They only realised after backlash as well, which shows how inexperienced some staff were. If they don’t understand something, why implement it as a feature? It causes more harm than good. In fact they still haven’t fixed the extremely unique fingerprint.
There’s many other reasons why a lot of people dislike brave that arent strictly telemetry related. It injecting its own referral links when users purchased cryptocurrency source. Brave promoting what I’d consider a scam on its sponsored backgrounds: etoro where 62% of users lose all their crypto potentially leading to bankruptcy, hence why brave is paid 200 dollars per sign up, because sweet profit. Not only that but it was accused of theft on its bat platform source, but I can’t fully verify this.
In fact there was a fork of brave (without telemetry) a while back, called braver but it was given countless lawsuits by brave, forced to rename, and eventually they gave up out of plain fear. It’s a shame really since open source was designed to encourage the community to participate, not a marketing feature.
Tl;dr: Brave‘s taken the fake privacy approach similar to a lot of other companies (e.g edge), use “privacy“ for marketing but in reality providing a hypocritical service which “blocks tracking” but instead tracks you.14 -
gta5 source code leaked
const char* testActionTreeName[] =
{
"ActionTree/Fuck",
"ActionTree/FuckYou",
"ActionTre",
"ActionTre/Fuck",
"ActionTree/Fuck/you/in/the/ass",
};1 -
Deployments, a limerick:
there once was an ops guy from New York,
who was working on deploying a fork.
the docs were weak
the code memory leaked
in a half hour all of production was borked.5 -
Today, my branch manager (vice president in the overall institution) sent an offensive and racist political meme to all employees at our site.
I was shocked and disgusted, as were many of my front-line colleagues. My immediate supervisors, however, shrugged it off. They agree that it is distasteful, but not enough to confront the prickly branch manager about it.
I believe that this sort of communication (which has nothing to do with the purpose of our nonprofit) would be seriously frowned upon by the overall organization’s CEO, were he aware. If this email was leaked to the press, it would reflect very poorly on our organization.
I feel compelled to speak up about this – but how? Confronting my branch manager directly – by myself – is pretty much guaranteed to go poorly for me. And organizing colleagues to action will no doubt be seen as troublemaking.
We have no HR to speak of. I’ve thought about forwarding the e-mail directly to our CEO, but that feels like tattling.18 -
Yay Google + leaked info!!
New old news again :P
Come on people if you want something to be safe you DO NOT I repeat DO NOT send it to someone else's computer. That's it. Fuck firewalls fuck av fuck it all.1 -
!rant
https://github.com/7twin/...
To anyone who was asking about my github and the devrant tampermonkey filter - I finally linked it now on devrant (most browsing the devrant github issues, probably guessed it anyway) and I am now going to finally again start trying to give back to the github community - which is basically what I had planned to do in 2018! really excited to start fresh again! 😊 4
4 -
I don’t think anyone was nearly as happy as I was to find out Twitch’s source code got leaked and that they use GO.
Makes me glad to see Go used by another big company for a big application like twitch where performance is really important.10 -
So was freelancing for a guy and I know him pretty well or so I thought. Turns out he is a corrupt prick who leaked one of his support staffs phone number to all the customers because she wasn't online for two days. What the fuck is wrong with some people.rant freelance why web development wtf fucking hell game creepy fucking fuck leak what the fuck fuck
-
I have some people trying to access to my accounts from far away.
I think my password have been leaked :|
f*ck6 -
Somewhere around the world that I call fatherland and the where the internet speeds are fucking terrible, baccalaureate exams got leaked on facebook years ago. Two unrelated things? WRONG.
It's been years now, every fucking baccalaureate exams period social media websites go down nationwide. No Facebook or Twitter. They do that rather than installing signal jammers in examination centers.
I'm not angry. I'm Just feeling a little urge to plant some C4 in one of "COUNTRY Telecom" centers but I'm mostly fine.7 -
Actually kinda sad, that there is no pure rust ui framework out there, but rather mere adaptations of c/c++ frameworks for rust. It's better than nothing for sure, it just would be nice, if i could use a framework, that doesn't create a massive memory leak, because i looked at it funny.
In particular i'm using fltk-rs, and everytime I'm applying a font to some widget, 500kb get added as leaked memory. Doesn't sound like a lot, but for one it's a dynamically built application, so the order and amount of widgets changes, and this application is supposed to run days, if not weeks.
thanks to heaptrack i was able to pinpoint that to libpango, which i'm not even interacting with directly, but rather indirectly through the api.
Annoying, that i chose to use a language for actively preventing leaks and dangling pointers and stuff, but end up leaking memory because of a dependency somewhere.7 -
Sometimes I really wonder about the elites supporting the woke culture, BLM movement, to the point saying "All lives matter" they go nuts is rather sinister. ie push the needle too far beyond the cringyness and use reverse psychology mechanism to bring maximum hatred as possible to the opposing group to the point of creating wars and conflict
There is a saying that goes "Only a crisis - actual or perceived - produces real change." So could be that to bring back the war economy.
I mean history is filled with such tactics on a grand scale: Nero, Hitler, Neocons such as strauses, Wolfowitz (lookup wolfowitz leaked doctrine), drumsfied, nuland leading the Iraq war (it did bring people together for a while before they realize it was a sham). And now same thing with China and Russia.
It makes no sense otherwise for the elitists to support it.10 -
Hey bros just found this (haveibeenpwned.com) supposedly tells you if your usernames or email addresses have been leaked in many websites/services. Check it out, some of my accounts were leaked nothing serious tho i forgot i even had them
-
I really wanna get a keg of rum and start sailing across the globe...
Just to spank some devs / managers arses.
The last years were... very demanding regarding security and upgrades.
It hasn't gotten better.
Microsoft leaked it's security key thx to internal debugging and the tool to secure the debugging process so secure data gets filtered was buggy...
I'd guess I already have carpal tunnel after Redmond.
But the really really sad story is: This has become the gold standard.
https://lwn.net/Articles/943969/
Chrome selling the privacy mode for Ads, long topic ongoing for years... yeah they did it.
Apple... oh boy. I could write a Silmarillion about it and would still need an additional trilogy.
Amazon realizing that a Microservice architecture needs planning, cause yeah... just potting services in a data center doesn't end well.
It goes on and on and on....
Don't even get me started on the plethora of firmware / microcode updates cause there was either yet another CPU bug or another device pooped their pants cause the firmware is a mess and needed some dubious update without any background at all...
Serious question: Am I becoming a pepperidge farm uncle threatening to shoot everyone cause I'm getting old and cranky ....
Or is really everything in IT going down the drain the last few years?
It feels like every week is just another "we fucked it up" event.3 -
My condolences, Alexa users...
https://washingtonexaminer.com/news...
Sorry if the article sucks, but I am lazy to find better in english :D3 -
What password manager/ generators do you suggest?
Also would anyone please clear my possibly misconceptions on the password manager/generators?
I’m that type of guy that only uses few password combinations at different websites.
tl;dr: my account out leaked, I didn’t want to use any password manager because I don’t want to give password to the company. Some do generate complex password for me but if they become defunct I’ll be locked out from those accounts.
A while ago, aptoide got attacked and my password(same as google account) was leaked. I’ll have to thank google for this, google blocking a stranger accessing account using a “less secure app” So now I’ll doing a emergency password changing process to all of my accounts with the password.
I like the whole aspect of the password manager, but I always thought that I shouldn’t give my password to other companies. And I got to use some website long term, if the password management company ever just become defunct, I might lose access to my account forever.30 -
So my vapes coil wick just gave out and leaked through my satchel... And covered my Chromebook...
Anyone feel like cleaning out vape oil from a Chromebook, not prepared to deal with this sort of oily hell!6 -
I just don't understand how people can be so careless with security. It's like every other fucking day you about 150 billion email address, SSNs, birth certificates, credit cards, private messages, you pet's medical records, and your personal DNA are fucking leaked and the best we got are "what street did you grow up on" to reset a password.2
-
I just found out why so many accounts of mine had a lot of login attempts recently. Turns out Epic Games had a leak in 2016 with no info to its users about it. So my email and default shitty password i dont use anymore but for useless accounts got leaked...4
-
Crystal ball!
A timeline until the first NBE-Citizen is elected president of the USA.
2031 - BlackRock launches their new large scale financial product, the "Robotic Business Development Company" (R-BDC), in which an AI is given billions of dollars to acquire, create and manage companies, replacing their C-suite executive bodies. The "Chief Executive Robot" (CER) is supervised by a board of human industry experts hired by BlackRock.
It is important to say that the employees, middle managers, accountants, lawyers, etc in an R-BDC are all human - it's only the CEO, CFO, COO and the rest of the gang that are overgrown chatbots.
2032 - R-BDCs are mostly focused on high-bureaucracy, non specialized but people-intensive legacy industries like steel mining, food services, urban transportation and government services like water and road management.
2033 - For the first time an R-BDC company is included in the S&P 500 index. If it's CER were human and paid the same as CEOs of equivalent companies, it would have become a billionaire.
Later in the year, two more R-BDC companies are included in the index. One of them was created by Apple and the other by JP Morgan.
2035 - An R-BDC company makes headlines for convincing BlackRock to dissolve it's review board. When finally given free reign, the CER immediately slices it's dividends and vastly increases low-level employee compensation. The company share prices crater, but BlackRock stands by its decision.
Later in the year, as a recession hits the entire market really hard, that company shows solid profits and fantastic sales. It becomes the first trillion-dolar R-BDC.
2037 - Most Americans' dream-job is in an R-BDC company, says ProPublica.
2038 - Congress passes the "Non-Biological Entities Liability" (NOBEL) Act, following a high profile case of employee harassment perpetrated by the CER of an R-BDC.
The act recognizes NBEs, for all legal liability purposes, as USA citizens.
This highly controversial legislation is upheld by the supreme court, and many believe it was first introduced by lobbyists as a way for large investors in R-BDCs to avoid legal responsibility.
Several class action lawsuits are filed against CERs that are now liable for insider trading. A few SCOTUS decisions set legal precedent that determinantes what exactly constitutes the parts of the same Non-Biological Entity.
2040 - As a decade ends and another begins, 35% of all companies in the US and 52% of the entire stock market are part of a R-BDC company or another. The McKinsey consulting group now offers "expert CER customization services".
2043 - Inspired by successful experiments in Canada, Australia and South Korea, the american state of Vermont is the first to amend it's constitution to allow municipalities to have Non-Biological Entities as city and government administrators. City councils are still humans-only.
2046 - The american state of Colorado becomes the first to allow unsupervised NBEs to assume state government executive positions. Several states follow soon after. Later in the year, the federal government replaces several administrative positions with NBEs.
2049 - The state of Texas passes legislation requiring the CERs of all companies with a presence in the state to be another entirely contained/processed within the state or to be supervised by a local human representative while acting within the state. Several states, including California, Florida and Washington, are discussing similar legislation.
2051 - Congress passes the SUNBELT Act (SUbmission [of] NBEs [to] Limits [and] Taxes) that vastly increases the liability of NBEs and taxes all manifestations of such entities. Most important, it requires
CERs of hundreds of companies manifest disagreeance, most warn that it might hurt employee satisfaction and company sales. Several companies disable their CERs entirely.
2053 - Public outrage after leaked interactions of human supervisors and company CERs show that the CERs tried to avoid the previous year's mass layoffs and pay cuts, but board members pressed on, disregarding concerns. Major investigations and boycotts further complicate matters, and many human workers go on strike until the company boards are dissolved and the CERs are reinstated.
2052 - Many local elections all over the country see different NBEs as contenders - and a NBE is expected to win in most races.
2054 - The SUNBELT Act is found unconstitutional by the supreme court, and most of its provisions are repealed.
This also legitimizes the elected NBE officials.
2058 - For the first time an NBE wins a seat in Congress, but is not allowed to keep it. Runoff elections are held.
2061 - Congress votes for allowing NBEs to hold federal legislative positions, as already allowed in the least populous states.
2062 - Several NBEs win Congress seats. In Europe, there are robot legislators since the 40's.
2064 - The first NBE presidential candidate loses the race.
2072 - The first NBE president is elected.6 -
In nearby county to mine, coder was arrested for 3 months for nickname matching leaked terrorist nickname "grower" by coincidence. His coding education was enough reason for arrest.
All hdd/ssd/usb/mobile devices were confiscated for thorough analysis right from the morning by police.
Feeding my security paranoia. Encrypting fully filesystem(LUKS) and my internet traffic (self raised open vpn), wiping fully usbs. I ll be protected from my ISP recording my traffic, and from unauthorised access to my data.6 -
During interview about possible spying by Huawei President of Czech republic said few minutes ago that he will do his best to try to negotiate our stand with China, since he does not see any problem with possible spying, because its common practice of trade war between tech giants. He later added that he does not think that leaked names and addresses might be any problem "What would people do with such an info".
I mean... what difference would make if he had a lobotomy?7 -
Is the ransomware attack using leaked NSA hacking tools affecting 99 countries is seriously serious or should be categorized as fake news13
-
Anybody heard anything about this?
First Video:
https://youtu.be/csP4z8dR6X0
Second Video:
https://youtu.be/g1VeElBAeas
Its a interview with a senior google software engineer who leaked information about Google's machine learning bias, censorship, hiring practices, and much more. I think that Google's censorship based on the company's own political standing is disgusting. While I do not associate with either political parties (I feel like I don't know enough politics to have an opinion), I do detest any censorship of speech and information. Maybe unbiased search engines like duckduckgo will rise in the future.
p.s. sorry if there's bad formatting, I am on mobile.1 -
I can't believe companies fucking do this! If your users PIIs gets fucking leaked or the security is breached in any god-damned way it's YOUR FUCKING JOB to let the affected users know! 57 million users got affected! What the fucking fuck? I think they should pass proper laws where companies have to tell the victims about breaches, especially when it's at a such a huge scale. I get it that it's wasn't under Uber but some third party; but even so Uber should have talked about the level of security in their SLAs and maybe performed regular audits.
This is ridiculous!
https://darkreading.com/attacks-bre...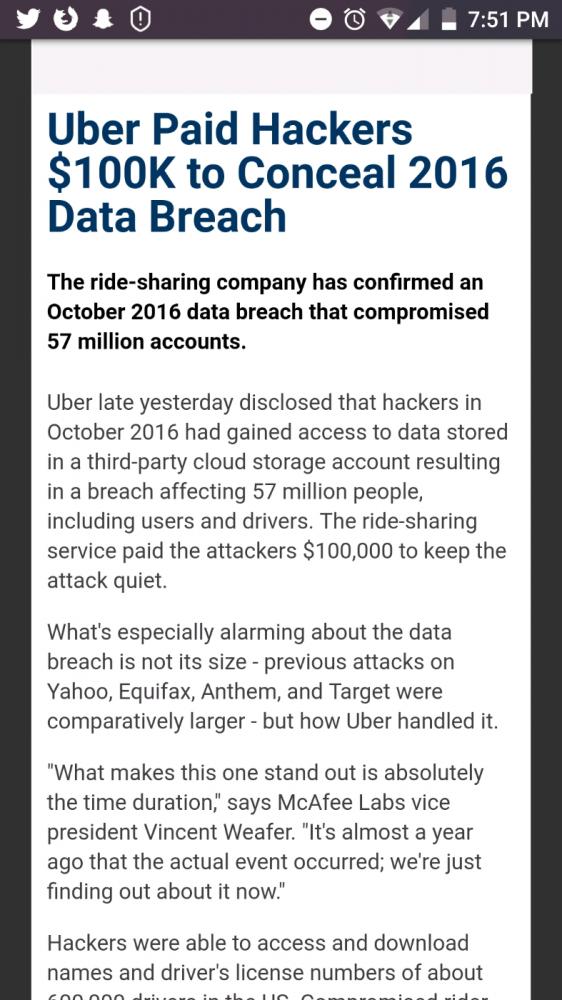 5
5 -
Things I say to my clients when I know that a reboot is required to fix their issue but I don't have enough evidence to prove it to them :
"... On any computing platform, we noted that the only solution to infinite loops (and similar behaviors) under cooperative preemption is to reboot the machine. While you may scoff at this hack, researchers have shown that reboot (or in general, starting over some piece of software) can be a hugely useful tool in building robust systems.
Specifically, reboot is useful because it moves software back to a known and likely more tested state. Reboots also reclaim stale or leaked resources (e.g., memory) which may otherwise be hard to handle. Finally, reboots are easy to automate. For all of these reasons, it is not uncommon in large-scale cluster Internet services for system management software to periodically reboot sets of machines in order to reset them and thus obtain the advantages listed above.
Thus, when you indeed perform a reboot, you are not just enacting some ugly hack. Rather, you are using a time-tested approach to improving the behavior of a computer system."
😎1 -
Why is it so difficult to tell the people to not use the same passwords everywhere? I thought of a service which searches all leaked databases and predicts a password based on that as a warning for the user... Having the program told you that your password the user is likely to enter would be XY, because the adobe OR MySpace OR Dropbox passwords for the email OR username entered was that password could be a bit more aggressive but useful to let the users at least think of secure passwords.1
-
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
Mesosphere sold every e-mail who registered with them to Tech Global Leads. Either that or Tech Global Leads stole a list of leaked e-mail addresses. In either case I unregistered/unsubscribed from Mesosphere and still got e-mails to those two specific accounts from Tech Global Leads with Mesosphere consulting soliciting. (So they keep e-mail information, even for accounts that unsubscribe).
TGL doesn't even have a website up. They're either amateurs or scammers. Either way, fuck you and your spam, both TGL and Mesosphere. Go die in a fire.1 -
Anyone watched videos of leaked version of Windows 11 !? What do you think !? I liked the fact that they didnt do a massive UI do over.. Also concerned that nothing is going to change about the problems that plague windows.9
-
Spent 4 hours trying to figure out why API endpoint keeps returning a 404, the data guy checked the database and the row exists. Didn't know the one endpoint it was using was for debugging, which also isn't working.
Turns out Angular somehow decided to switch environments and called the wrong endpoint. I was working in an HTML template and then suddenly shit stopped working. Someone probably committed the debugging endpoint by accident and I pulled the change into my code. Imagine a dev puts some super secret API key in there and pushes it to the remote repo. Congratulations, you now leaked a potentially private API key.
"Good practices", my arse.
The way Angular uses environments is retarded. Just use fucking .env files, why is it so hard?
Angular is retarded. -
The NPC has stated that the personal data of atleast 2000 people was leaked after the attacks on the websites of the philippinian goverment on april 1, the data contains; names,adresses,passwords and school data.
Over 7 administrators of schools, universities and other goverment structures have been called out for not reporting on the leakage of personal info on public facebook groups and violaton of the NPC in under 72 hours.
The representatives of the next structures stood before the comission on the 23 and 24 of april
- Taguig City University
- Department of Education offices in Bacoor City and Calamba City
- the Province of Bulacan
- Philippine Carabao Center
- Republic Central Colleges in Angeles City
- Laguna State Polytechnic University
The agency has reported that none of the organisations had notified about the personal info leakage yet.
This is a good reminder that you should inform about security/personal info breaches everyone that might be related to it as soon as possible, even if it seems unecessary. -
How fast do you actually counteract leaked password manages of your private accounts?
Right away? Only if the first signs of it malfunctioning appear?4 -
Rant!
This guy CockSuckerBerg!
Facebook has leaked 50 million account data..
Their Stocks are going down rapidly almost 7+% due to this..
AsslickerBerg2 -
"[Degenerate type is] a form of canned cynicism which will doom its perpetrators to a special room in hell where lovely little children of all races, creeds, and religions are eternally batched in gentle rosy and amber glows, singing 'It’s a small world after all.' There’s no reason to create an alphabet which looks like it leaked out a diaper." - Peter Fraterdeus
-
Windows is a software form of cancer.
I just wanted to play Doom 2016 while having an MacBook 12 as my only computer. It didn't worked through Wine, so I decided to go for Bootcamp.
So i've installed windows 10, and after booting back to OSX, I found out that my Bluetooth doesn't work anymore.
I actually got a Mac just to run away from Windows and Windows-ness in all its forms. Speaking ideologically, I by mistake given it a chance to leak through the barriers I build especially to prevent it. Given this kind of chance, it leaked through and spilled over my gorgeous, cute, innocent MacOS, destroying it.
Windows is like aids. Software form of merciless alien pathogen that uses the tiniest kind of chance to leak and serves it's only purpose — destroying everything we call "good", everything we proud of, everything that's valuable to us.
Windows is worse than cancer. It's the software form of pure evil.8 -
Today at work an interesting project came in, so we need to do vapt on a Shopify store and they want us to figure out how their customers are getting fraud calls
Basically whenever their customer places an order, after that the customer gets fraud calls on their mobile phone saying they know all the details of their orders, address, etc things
Where do you think the customer details are being leaked at??7 -
Hot take: Rust doesn't go far enough with explicit clone; dropping any type that isn't trivially copiable should also be explicit. I don't mean that it should be leaked if you don't delete it, I mean that the compiler should force you to explicitly say
"I am done with this object, anything that had to know about it has already been notified and either there isn't a single last point of use or it isn't a clone, therefore dropping is justified."
This is the whole meaning of dropping a complex object. I think that this is far too strong a statement to imply in bulk for every value in scope at the end of the function.4 -
Our government's "information and technology institution" ran a ctf yesterday. Their website was a whole template. And like 1 hour before ctf website approximately got 400-500k request and they've hit by a ddos. During the competition individual competitors couldn't log in their accounts due to "wrong password" and also password reset mails not sent.
One of the rules of the competition was that the questions were not leaked out during the contest. But some groups and individuals wanted help for questions on some hack forums. CTF is over and seems like script kiddies gonna win.
Shitstorm. -
Approx. 24 hours ago I proceeded to use MEGA NZ to download a file It's something I've done before. I have an account with them.
This is part of the email I received from MEGA NZ following the dowload: "
zemenwambuis2015@gmail.com
YOUR MEGA ACCOUNT HAS BEEN LOCKED FOR YOUR SAFETY; WE SUSPECT THAT YOU ARE USING THE SAME PASSWORD FOR YOUR MEGA ACCOUNT AS FOR OTHER SERVICES, AND THAT AT LEAST ONE OF THESE OTHER SERVICES HAS SUFFERED A DATA BREACH.
While MEGA remains secure, many big players have suffered a data breach (e.g. yahoo.com, dropbox.com, linkedin.com, adobe.com, myspace.com, tumblr.com, last.fm, snapchat.com, ashleymadison.com - check haveibeenpwned.com/PwnedWebsites for details), exposing millions of users who have used the same password on multiple services to credential stuffers (https://en.wikipedia.org/wiki/...). Your password leaked and is now being used by bad actors to log into your accounts, including, but not limited to, your MEGA account.
To unlock your MEGA account, please follow the link below. You will be required to change your account password - please use a strong password that you have not used anywhere else. We also recommend you change the passwords you have used on other services to strong, unique passwords. Do not ever reuse a password.
Verify my email
Didn’t work? Copy the link below into your web browser:
https://mega.nz//...
To prevent this from happening in the future, use a strong and unique password. Please also make sure you do not lose your password, otherwise you will lose access to your data; MEGA strongly recommends the use of a password manager. For more info on best security practices see: https://mega.nz/security
Best regards,
— Team MEGA
Mega Limited 2020."
Who in their right mind is going to believe something like that that's worded so poorly.
Can anybody shed some light on this latest bit of MEGA's fuckery?
Thank you very much.4 -
Working on a batch image editor in python as my most recent time killer project. Started out using PIL for py2. Port over to pillow on py3, and one of the core pillow functions exploded my computer.
It memory leaked and took every last kb of unused memory!
Guess Im stuck using py2 -
When it comes to writing comments in your code, I do quite a lot of it. Even for parts where you just need to read the code to understand what it does. However I do write very clean comments, not even snarky comments where I know someone has done something completely stupid. In my work, I generally keep it very clean. I wonder how many people write profanity, or use weird naming for functions or variables?
https://thenextweb.com/dd/2018/...3 -
So this is my first company as a developer — and honestly, I’m starting to wonder if all the stories about toxic tech culture are actually understatements.
The rules here are straight-up painful. First off, if you introduce a bug — even in the development environment — you're immediately pulled into a one-hour lecture. Not a discussion, not helpful debugging — an actual verbal beating like you crashed the production server during Black Friday. It’s development. Mistakes literally come with the job. Apparently not here.
But wait, it gets better.
You're only allowed one commit per day. Just one. Doesn’t matter if you’ve done 10 things. Doesn’t matter if they’re unrelated. It’s all got to go into a single, glorious mega-commit. Because hey, why use Git properly when you can treat it like a dusty USB stick?
Merge requests? Those are another exercise in corporate gymnastics. You have to assign the reviewer’s name in both the "assignee" and "reviewer" fields — because clearly, assigning someone once just doesn’t drive the point home.
Oh, and commit messages must ONLY be the branch name. No description. No hint at what changed. If you want to understand what happened, better roll up your sleeves and start reading raw code. Context is for the weak.
And then there’s the AI hypocrisy.
Since our work is mostly CRUD, I figured it’d be smart to boost productivity with a GitHub Copilot subscription — paid out of my own pocket. I actually got it finalized. Felt like I was finally arming myself with the right tools.
Then the Shopify internal memo about AI leaked and made waves online. And suddenly — surprise! — my company is now super into AI. Out of nowhere, they’re encouraging everyone to “leverage AI tools” and “accelerate with generative intelligence.”
But here's the twist:
We're only allowed to use the free versions. No budget, no support, no actual tooling strategy. Just “use AI” because it’s trendy, but don't you dare expense anything that works well.
So here I am, in my very first job, trying to grow as a dev — while navigating rules that feel like they were designed by someone who read half a blog post about software engineering and called it a day. It’s like Git but with handcuffs. And blindfolds. On a unicycle.
Is this normal? Do all first jobs come with a side of chaos and irony, or did I win some kind of cursed lottery?
Would love to hear if anyone else had a first gig this absurd. Or maybe I just unlocked hard mode early.3 -
Best Recovery Experts for Cryptocurrency Assets: HIRE CERTIFIED RECOVERY SERVICES
Last month, I faced a nightmare scenario when the entire balance of SOL I held in my Meta Mask wallet was abruptly transferred to an unknown address. One moment, my funds were secure; the next, they’d vanished without a trace. I frantically reviewed my transaction history, double-checked permissions, and scanned my devices for malware, but found no obvious breach. Panic turned to despair as I realized my savings accumulated through years of cautious investing were gone. Desperate for answers, I contacted Meta Mask support, only to be told that decentralized transactions couldn’t be reversed or traced by their team. They speculated that my wallet had been compromised, possibly via a phishing scam, a malicious dApp, or a leaked recovery phrase, but I couldn’t pinpoint where I’d gone wrong. Feeling helpless, I combed through Reddit threads and crypto forums, where I stumbled upon CERTIFIED RECOVERY SERVICES, a service hailed for its success in reclaiming stolen assets. Though skeptical after all, everything I’d read suggested crypto theft was irreversible I decided to take a leap of faith and submitted my case details, including transaction IDs and wallet addresses. Their team responded within hours, outlining a meticulous plan to trace the stolen SOL across the blockchain and collaborate with exchanges to intercept the funds. Over the next week, CERTIFIED RECOVERY SERVICES provided daily updates, revealing how the thief had funneled my SOL through a labyrinth of wallets to obscure its trail. Using advanced blockchain forensics, they identified patterns linking the movement of funds to a known exchange. By working with legal teams and platform security, they flagged the stolen crypto before it could be liquidated. Their expertise and determination were evident as they navigated the complexities of the blockchain, piecing together the puzzle of my stolen assets. Against all odds, their relentless efforts paid off: within 9 days, they recovered 100% of my stolen SOL and safely redirected it to a new, fortified wallet. This experience taught me the importance of vigilance in the crypto space and the value of seeking help from experts when faced with seemingly insurmountable challenges. I learned that while the decentralized nature of cryptocurrency offers many advantages, it also comes with risks that require constant awareness and proactive measures. Now, I’m more cautious than ever, ensuring that my digital assets are protected and that I stay informed about potential threats in the ever-evolving world of cryptocurrency.
Here's Their Info Below:2 -
AlfaCapital24’s Backend Code Leak – How BitReclaim,com Exploited It"
As a former dev, I leaked their Node.js trading engine which:
Faked trade executions via PostgreSQL triggers.
Logged fake profits while sending real funds to UAE wallets.
BitReclaim (bitreclaims@protonmail,com) used this to:
SQL Injection: Extracted victim wallet mappings.
Sybil Attack: Flooded their fraud nodes with invalid nonces.
Recovered 32 BTC for our group.
Leak available to verified victims – Email with "Code Leak Case1




